#SQL Server 2019 Activation Key
Explore tagged Tumblr posts
Text
A Beginner’s Guide to Data Warehousing
New Post has been published on https://thedigitalinsider.com/a-beginners-guide-to-data-warehousing/
A Beginner’s Guide to Data Warehousing
In this digital economy, data is paramount. Today, all sectors, from private enterprises to public entities, use big data to make critical business decisions.
However, the data ecosystem faces numerous challenges regarding large data volume, variety, and velocity. Businesses must employ certain techniques to organize, manage, and analyze this data.
Enter data warehousing!
Data warehousing is a critical component in the data ecosystem of a modern enterprise. It can streamline an organization’s data flow and enhance its decision-making capabilities. This is also evident in the global data warehousing market growth, which is expected to reach $51.18 billion by 2028, compared to $21.18 billion in 2019.
This article will explore data warehousing, its architecture types, key components, benefits, and challenges.
What is Data Warehousing?
Data warehousing is a data management system to support Business Intelligence (BI) operations. It is a process of collecting, cleaning, and transforming data from diverse sources and storing it in a centralized repository. It can handle vast amounts of data and facilitate complex queries.
In BI systems, data warehousing first converts disparate raw data into clean, organized, and integrated data, which is then used to extract actionable insights to facilitate analysis, reporting, and data-informed decision-making.
Moreover, modern data warehousing pipelines are suitable for growth forecasting and predictive analysis using artificial intelligence (AI) and machine learning (ML) techniques. Cloud data warehousing further amplifies these capabilities offering greater scalability and accessibility, making the entire data management process even more flexible.
Before we discuss different data warehouse architectures, let’s look at the major components that constitute a data warehouse.
Key Components of Data Warehousing
Data warehousing comprises several components working together to manage data efficiently. The following elements serve as a backbone for a functional data warehouse.
Data Sources: Data sources provide information and context to a data warehouse. They can contain structured, unstructured, or semi-structured data. These can include structured databases, log files, CSV files, transaction tables, third-party business tools, sensor data, etc.
ETL (Extract, Transform, Load) Pipeline: It is a data integration mechanism responsible for extracting data from data sources, transforming it into a suitable format, and loading it into the data destination like a data warehouse. The pipeline ensures correct, complete, and consistent data.
Metadata: Metadata is data about the data. It provides structural information and a comprehensive view of the warehouse data. Metadata is essential for governance and effective data management.
Data Access: It refers to the methods data teams use to access the data in the data warehouse, e.g., SQL queries, reporting tools, analytics tools, etc.
Data Destination: These are physical storage spaces for data, such as a data warehouse, data lake, or data mart.
Typically, these components are standard across data warehouse types. Let’s briefly discuss how the architecture of a traditional data warehouse differs from a cloud-based data warehouse.
Architecture: Traditional Data Warehouse vs Active-Cloud Data Warehouse
A Typical Data Warehouse Architecture
Traditional data warehouses focus on storing, processing, and presenting data in structured tiers. They are typically deployed in an on-premise setting where the relevant organization manages the hardware infrastructure like servers, drives, and memory.
On the other hand, active-cloud warehouses emphasize continuous data updates and real-time processing by leveraging cloud platforms like Snowflake, AWS, and Azure. Their architectures also differ based on their applications.
Some key differences are discussed below.
Traditional Data Warehouse Architecture
Bottom Tier (Database Server): This tier is responsible for storing (a process known as data ingestion) and retrieving data. The data ecosystem is connected to company-defined data sources that can ingest historical data after a specified period.
Middle Tier (Application Server): This tier processes user queries and transforms data (a process known as data integration) using Online Analytical Processing (OLAP) tools. Data is typically stored in a data warehouse.
Top Tier (Interface Layer): The top tier serves as the front-end layer for user interaction. It supports actions like querying, reporting, and visualization. Typical tasks include market research, customer analysis, financial reporting, etc.
Active-Cloud Data Warehouse Architecture
Bottom Tier (Database Server): Besides storing data, this tier provides continuous data updates for real-time data processing, meaning that data latency is very low from source to destination. The data ecosystem uses pre-built connectors or integrations to fetch real-time data from numerous sources.
Middle Tier (Application Server): Immediate data transformation occurs in this tier. It is done using OLAP tools. Data is typically stored in an online data mart or data lakehouse.
Top Tier (Interface Layer): This tier enables user interactions, predictive analytics, and real-time reporting. Typical tasks include fraud detection, risk management, supply chain optimization, etc.
Best Practices in Data Warehousing
While designing data warehouses, the data teams must follow these best practices to increase the success of their data pipelines.
Self-Service Analytics: Properly label and structure data elements to keep track of traceability – the ability to track the entire data warehouse lifecycle. It enables self-service analytics that empowers business analysts to generate reports with nominal support from the data team.
Data Governance: Set robust internal policies to govern the use of organizational data across different teams and departments.
Data Security: Monitor the data warehouse security regularly. Apply industry-grade encryption to protect your data pipelines and comply with privacy standards like GDPR, CCPA, and HIPAA.
Scalability and Performance: Streamline processes to improve operational efficiency while saving time and cost. Optimize the warehouse infrastructure and make it robust enough to manage any load.
Agile Development: Follow an agile development methodology to incorporate changes to the data warehouse ecosystem. Start small and expand your warehouse in iterations.
Benefits of Data Warehousing
Some key data warehouse benefits for organizations include:
Improved Data Quality: A data warehouse provides better quality by gathering data from various sources into a centralized storage after cleansing and standardizing.
Cost Reduction: A data warehouse reduces operational costs by integrating data sources into a single repository, thus saving data storage space and separate infrastructure costs.
Improved Decision Making: A data warehouse supports BI functions like data mining, visualization, and reporting. It also supports advanced functions like AI-based predictive analytics for data-driven decisions about marketing campaigns, supply chains, etc.
Challenges of Data Warehousing
Some of the most notable challenges that occur while constructing a data warehouse are as follows:
Data Security: A data warehouse contains sensitive information, making it vulnerable to cyber-attacks.
Large Data Volumes: Managing and processing big data is complex. Achieving low latency throughout the data pipeline is a significant challenge.
Alignment with Business Requirements: Every organization has different data needs. Hence, there is no one-size-fits-all data warehouse solution. Organizations must align their warehouse design with their business needs to reduce the chances of failure.
To read more content related to data, artificial intelligence, and machine learning, visit Unite AI.
#Accessibility#agile#Agile Development#ai#AI 101#Analysis#Analytics#applications#architecture#Article#artificial#Artificial Intelligence#AWS#azure#bi#Big Data#billion#Business#Business Intelligence#ccpa#challenge#Cloud#cloud data#cloud data warehouse#comprehensive#continuous#cyber#data#data analysis#data analytics
0 notes
Text
Searching For SQL Server 2019 Activation Key? Look No More!
Are you searching for SQL server 2019 activation key? Connect with us at Instant Key, as we have various Microsoft servers, dev tools, antivirus, etc. Microsoft created SQL Server is a relational database management system. This database server has an extensive capacity for storing and recovering information as mentioned by some of the top-notch programming applications. For any further information visit: https://instant-key.com/product/sql-server-2019-enterprise
0 notes
Link
Read More: SQL Server 2019 Activation Key - The Ninth Version of Microsoft's Windows Server Operating System
0 notes
Text
Exactly Why Cyber-Security Is Important To You

Let us deal with itwe live in an electronic virtual universe. Our work resides, own lives, and finances possess begun gravitating toward the realm of the world wide web, portable computing, along with electronic media. Unfortunately, this wide spread phenomenon makes us vulnerable than ever to malicious attacks, invasions of privacy, fraud, along with other such unpleasantries.
That's the reason cyber security is such a critical section of a secure and wellordered digital universe. Cybersecurity keeps us protected against hackers, cyber criminals, along with different agents of fraud. But just how good is that your cybersecurity knowledge?
We'll greatly help raise your cybersecurity awareness for this particular report. We are going to explore such significant topics why there is a demand for cyber security, what sorts of threats are out there, the very ideal security measures, and what you could do personally to be more secure when utilizing the internet.
Why is Cyber security So Important?
Cybercrimes at technology have cost the world £ 2 trillion therefore much in 2019, based on recent research. Cybersecurity Ventures predicted in 20 17 that damages could reach $6 trillion by 2021, prompting global spending roughly $10 billion in cyber-security actions by 2027 to force away these catastrophic losses.
Different Forms of Cybersecurity Threats
If it comes to devoting your own body, hackers possess an whole arsenal value of tricks at their own disposal. For example:
Denial-of-service (DoS) Attacks
Hackers flood a system with asks to exhaust bandwidth. In lots of situations, DoS attacks are meant to be more of a nuisance than anything else.
Man in the Middle (MitM) Attack
This attack occurs when hackers fit themselves to some two party communicating. Once they are in, they are able to steal info.
Phishing Attacks
Phishing employs fake emails and text messages to get folks to provide hackers access to private details. This really is but one of the absolute most ordinary strikes, especially against the general people.
Malware
This strike method is broken down into spyware, ransomwareviruses, and viruses. E mails or files normally deliver these strikes from questionable websites.
SQL Injection Attack
Hackers insert malicious code on an SQL-using server, usually with a exposed site search box. Once completed out effectively, the strike lets the hacker see information otherwise stored offsite.
Password Attack
Precisely what it seems. Hackers take to to crack a password, usually a poorly chosen individual and gain network entrance.
What Does Excellent Cyber-Security Seem Like?
Contemplating the shocking amount of cyber-attacks talked about previously, you can observe the significance of utilizing active cybersecurity steps. Fortunately, you'll find numerous useful cybersecurity methods you may exercise both in home and at work. Keep them at heart, and you'll lower the chances of owning a cybercrime on your own hands!
Practice Decent Password Alternative
Does one have a"password" as your default password? If so, then pity ! The great powerful password will be between 8 and 12 characters and comprises upper and lower case letters, a minumum of one variety, and a distinctive character (for instance,!? ( @). Don't utilize passwords that are simple and don't use such a thing centered on easyto find details about yourself.
Retain Your Wi-Fi Secure
Talking about passwordsdon't forget to guard your wi fi system. Utilize WPA-2 for your security technique.
Install Antivirus Software
Fortunately, a lot of internet providers package in a few halfway decent antivirus software by using their service. If your provider does not, subsequently pick something up from Norton, McAfee or Symantec; it is not expensive, and it's going pay for itself in the very long haul. Additionally, once you install the application, make certain it is running!
Steer Clear of Suspicious E Mails and Texts
Don't recognize the current email address or the phone number of this sender? Do not open this up, do not reply. Do not conduct anything apart from minding it! A number of these are the opening gambit in a phishing fraud or id theft attempt.
Use Firewalls and Encryption
Firewalls assist regulate network traffic, both inbound and outbound. That includes blocking off certain sketchy sites. Encryption is vital if you are coping with fiscal transactions, particularly if you're a company proprietor. Encryption computer software scrambles the information so that even though the information falls in the incorrect hands, it is useless unless the crooks also have use of this encryption key.
1 note
·
View note
Text
Cryptocurrencies (3/3)
What sort of security issues do we have?
Due to the distributed nature of cryptocurrencies, we have to consider the security in a number of different areas and from a couple of different angles. In terms of looking at historical flaws and their relative impacts, I would classify them under 3 main categories:
Blockchain itself - vulnerabilities relating specifically to the implementation of the blockchain (so in the nodes, mining, etc)
51% attacks (i.e. ETC 2019)
DDoS
Doublespend (i.e. The Finney attack)
Exchanges and wallets
Phishing
Bad hashes (i.e. IOTA)
Software bugs in cryptocurrency wallets
Software bugs in cryptocurrency exchanges
Client malware (i.e. changing address in clipboard)
Smart contracts - complexity of smart contract languages leading to bugs or poorly designed contracts (i.e. TheDAO)
As per the seminar, I will summarise a specific example of each of these categories.
Blockchain - 51% Attack
How does it work?
If you read my (1/3) article on cryptocurrencies, you will understand the process of mining in PoW and how multiple chains can form. Essentially, what we have happening in this attack is we have a miner (corrupted) with a large portion of the hash power deciding not to broadcast the block to the network when he as found a valid hash for the block. He will then continue to mine on his own chain in stealth; the original chain will continue to be built by other miners.
The corrupted miner will then spend all the bitcoin that he owns on the public chain, however he will choose NOT to do the same on his own secret chain. He will then continue to mine blocks on his own chain; however since he has majority hash power he will be producing blocks at a greater rate than the main chain. After a while he will choose to broadcast his chain to the rest of the Bitcoin network - the democratic governance process of the network enforces that the ‘longest chain’ is the correct one and the protocol will force the nodes to switch to the corrupted miner’s chain. This miner is then able to spend his bitcoins (that he spent earlier) all over again - this is why it is also referred to as a double-spend attack.
What security mechanisms are in place against it?
The main thing defending against a 51% attack is the sheer amount of resources required to perform it - on larger networks such as Bitcoin you need approximately $12.5 billion dollars worth of hardware which will cost you $8.6 million dollars per day to run in order to perform this attack. (from this site) This makes the risk associated with the costs in electricity, hardware and government prosecution not worth the reward of the attack.
Exchanges - Mt Gox
What happened in the first hack in 2011?
The computer of Mt Gox’s auditor was compromised which they then used to access the exchange and artificially modify the traded value of bitcoin down to 1 cent (i.e. by selling all the bitcoin from all the accounts). They could then buy a heap of these bitcoins at this low price (around 2000 BTC they got), and could transfer them from the exchange. As a result of the hack, Mt Gox resorted to utilising cold storage for the majority of their bitcoin - this means you cannot access a large proportion of the funds through the web server or any other computer.
The method in which this account was compromised is still somewhat debated - however it is suspected that the auditor account was compromised through an SQL injection on the Mt. Gox website which allowed the attacker to gain read-only access to the user database. The passwords were hashed with MD5 (retrospectively, we know is definitely poor) and accounts which hadn’t logged in prior to the chance in ownership of the exchange (by Tibanne Co. Ltd in March 2011) had unsalted password hashes used. You can read the Mt. Gox press release at the time on BitcoinTalk here.
How did the big second hack in 2014 occur?
In a short period of time in 2013, Mt Gox had become the largest bitcoin exchange in the world and was struggling to cope with the expansion. They had expended significant resources towards dealing with the lawsuits from former business partners (Coinlab) and investigations by the US Department of Homeland Security. We now also know from employee accounts that the security procedures were poor, the website source code was poor quality and a number of other operational issues existed.
This all led to the events which unfolded in February 2014, as follows (according to CoinTelegraph article):
7th - withdrawals frozen due to an “apparent bug” in the Bitcoin network relating to modification of transactions
17th - press release regarding a solution they had found to solve this “bug” which would be applied shortly
23rd - the CEO of Mt. Gox, Mark Karpeles, resigned from the Bitcoin Foundation and disappeared from Twitter
24th - trading was suspended and an internal document leaked claiming they were insolvent; missing 744,408 bitcoins (it was a crisis strategy draft)
28th - Mt. Gox filed for bankruptcy protection in Tokyo and in the US on March 9th
They haven’t been particularly transparent regarding the cause of the second hack, however some information has been pieced together. It is believed that Mt. Gox’s hot wallet private keys were stolen from a wallet.dat file near the end of 2011. Throughout 2012 and 2013, the hacker emptied the wallets associated with the private keys, however Mt. Gox’s systems interpreted this is deposits for some reason. Towards the end of 2013, the hacker had stolen over 600,000 BTC; a large proportion of this ended up on BTC-E. This exchange was essentially responsible for laundering half the funds associated from the hack; it was taken down in 2017 by the US Justice Department.
Smart Contracts
What is a smart contract?
A contract is an agreement between two parties which will be binding in some point in the future. The difference in the case of smart contracts with blockchain is that it makes the execution of the contract trustless - we don’t need a third party. Some restrictions are imposed when we make them decentralised; they need to be unable to access data outside the program (to prevent malicious activity) and they need to be deterministic (so nodes in the network can still verify blocks).
Why are these contracts so prone to errors?
The majority of smart contracts we know today are built upon the Ethereum blockchain; it uses a Turing-complete smart contract language known as Solidity. This differs from traditional contracts in the sense you are to solve any reasonable computational problem. It also comes at the cost of increasing complexity; there is an increasing number of ways the flow of the contract can occur and thus they are very difficult to get right. We already know that writing ‘secure’ code is hard, but when you have money directly on the line it becomes even more important.
What was the DAO?
The DAO (Decentralised Autonomous Organisation) was an organisation built on top of Ethereum which ran completely through smart contracts on the platforms. In the token offering, users were able to send ETH to a particular address and receive DAO tokens in return. Anyone was able to make a pitch to the community, and people could vote with their DAO tokens whether to make an investment. If a project was successful as a result of the DAO, it would then return profits to the investors.
How was the smart contract code in the DAO exploited?
One of the developers announced on the 12th of June that they had discovered a recursive bug call in the DAO contract, however emphasised that no funds were at risk. An attacker managed to find a way on the 18th of June to abuse this recursive bug call to continuously send funds to a child DAO under their control. The process was as follows (source):
(1) Propose a split and wait for the voting period to expire
(2) Call splitDAO()
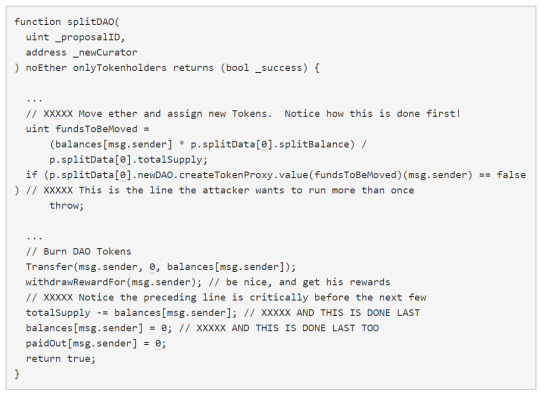
(3) Let createTokenProxy() send your new DAO its share of tokens
(4) Ensure the DAO calls withdrawRewardFor() before updating your balance and after doing (3)

(5) Call splitDAO() again with the same parameters while (4) is occurring
(6) DAO will repeat steps (3) and (4) to give you the child tokens again
(7) Go back to (5) as many times as you like
So in summary, the problem all stems from the fact that you get your reward in the child DAO before subtracting from the original balance. The stack was actually limited to 128 on Ethereum at the time, so he wasn’t able to continue these calls forever. The attacker managed to get around this by using the handy transfer() function, so he could quickly move the funds out to another account he controlled. Then he could move it back into the original account and repeat the process.
What happened after the hack?
The attacker managed to steal ETH worth up to 250 million USD; they actually stopped after draining around 1/3 of the DAO’s funds. It started a big debate among members of the Ethereum community as to how they could respond to this attack. One side fought for the immutability (’code is law’) of the blockchain and argued that we shouldn’t fork to take away the funds from the attacker. The other side wanted to fork the chain to return all the funds. The miners were divided on the proposals (a contentious hard fork) so we ended with two chains - Ethereum Classic (ETC) and Ethereum (ETH).
6 notes
·
View notes
Text
Purchasing Sql Server Errors
Incident response with Azure, such as other cloud providers, is a bit different. With this service it is simple to publish and get messages from your things. This message will display when the procedure is complete. User-defined messages may also be kept in sysmessages. The error message gives diagnostic information regarding the reason for the error. These user-defined error messages can be employed by RAISERROR.
Everything beyond is regarded as an error To have the ability to use an apostrophe in a string, it needs to be escaped, so that it's not thought of as a string delimiter. There is a vast selection of errors that can happen during the SQL Server work. This error is going to be thrown. Error 823 means there are some issues with the storage computer hardware. Errors with a tall severity indicate issues that ought to be addressed whenever possible. The problem needs to be resolved. There is an issue with your selected data store.
To escape an apostrophe, another apostrophe must be used next to it, as it's shown below Finding SQL syntax errors can be challenging, but there is some advice about how to make it a bit simpler. Because of this, it will become impossible to have data from it. Data ingestion is the initial step in building the data pipeline.
The instructions below will demonstrate how to resolve the permissions issue. This type of error condition is referred to as a transient fault. Each error condition have a special error number.
Each policy may have a variety of settings. Employing the drop down policy lists, decide on the policies you would like to apply. The absolute most important MySQL account to decide on a password for is the main user. Just bear in mind that you would like to commit or rollback your transactions at the ideal times, based on whether an error was generated.

Insert some values in the Employee table. For instance, presence states or the capacity to transfer files. An internet index rebuild or an index reorganization isn't always possible. There are many SQL database versions suiting the demands and requirements of small organizations together with bigger enterprises too. Perform continuing database maintenance. In the middle of this screen, there is going to be a field marked From database.
Whatever encryption way you pick, I advise avoiding encryption methods that ask that you store the decryption key on the database itself. As a way to utilize Change Data Capture functionality offered by the SQL Server, it ought to be enabled for the specific database which we intend to track the changes. Databases have long been a significant part your normal architecture and potentially the most important. Your database is the jackpot that each attacker intends to capture. The customer's major database is MySQL. SQLEXPRESS'' folders, you should install SQL Server. SQL Server is an intricate system and as a result of continuous increasing size of information and multiple small business logic, getting to the root of performance issues can be difficult. Any throw from inside the script is regarded as a failure. The script ought to be fairly straightforward. Recycled code results in recycled suggestions and recycled folks.
The deployment may take as much as a little while so be patient. There are lots of reasons for this, like a system or server crash or a virus. Do not freak out whether there are too many events and they run screaming at you, which happens when you get a huge system with a lot of users. There's a different technique for Windows hosted accounts. If you've checked the Allow to utilize for domain creation box on the very first page of the wizard, once you click OK the template gets active in the computer system.
SQL Server 2019 documentation can be found on our major Docs address. This application offers you a basic grasp of the DataGridView control's capabilities. An application is consuming an excessive amount of memory. It must also be compiled with debugging enabled. Nevertheless it remains a beneficial tool. SQL Recovery tool may also eradicate and handled each of the problems of error messages which occur because of corruption. MS SQL database recovery tool recently added features that are very advanced like multi threaded export which may let you recover single in addition to multiple tables at one time.
A standard use of the test script is to confirm the adapter's capability to access necessary database tables. Certain permissions, like, for instance, shell access, provide unlimited accessibility to critical system objects, therefore it is strongly recommended to use permissions sql server errors with caution. Storing sensitive info, such as a password, within the connection string can influence the security of your application. Employing the aforementioned Error List can help in an excellent way.
youtube
1 note
·
View note
Text
SQL Server 2019 Standard online activation sql server 2019
Essential details Products Status:Stock Type:Operating System Operating Systems Supported:Windows Version Type:Home Model Number:win Software, SQL Server Place of Origin:usa Package include:COA License Sticker License:Genuine Key Language:Multi-language Version:OEM/Retail Warranty:100% Activation Online Globally Services:24/7 Service Support Shipping Method:Email Online Delivery

View On WordPress
0 notes
Text
Are you looking for a complete guide on how to install MariaDB 1053 on openSUSE 15?. MariaDB is a drop-in replacement for MySQL. It is a robust, resilient, scalable and reliable RDBMS with features previously only available in costly proprietary databases. The latest stable release as of this writing is MariaDB 10.5. This version is available from MariaDB maintained repositories for Ubuntu/Debian/CentOS/Fedora/SUSE. Install MariaDB 10.5 on openSUSE 15 now and enjoy its breadth of features. Step 1: Add MariaDB ZYpp repository MariaDB Corporation provides a MariaDB Package Repository for several Linux distributions that use zypper to manage packages. Add ZYpp repository for MariaDB by running the following commands. Fetch repository GPG key. sudo rpm --import https://yum.mariadb.org/RPM-GPG-KEY-MariaDB sudo zypper --gpg-auto-import-keys refresh Then add the repository: sudo zypper addrepo --gpgcheck --refresh https://yum.mariadb.org/10.5/opensuse/15/x86_64 mariadb Execution output: Adding repository 'mariadb' ..............................................[done] Repository 'mariadb' successfully added URI : https://yum.mariadb.org/10.5/sles/15/x86_64 Enabled : Yes GPG Check : Yes Autorefresh : Yes Priority : 99 (default priority) Repository priorities are without effect. All enabled repositories share the same priority. Step 2: Install MariaDB 10.5 on openSUSE 15 After the zypper repository is configured, you can install MariaDB packages using zypper. The added repository contains software packages related to MariaDB Server, including the server itself, clients and utilities, client libraries, plugins, and Mariabackup To install MariaDB Server and client with ZYpp, run: sudo zypper install MariaDB-server MariaDB-client When prompted, press “y” to agree to installation. Step 3: Start mariadb service After the installation, start MariaDB service and set it to start at boot. sudo systemctl enable --now mariadb Confirm the service is running. $ systemctl status mariadb.service ● mariadb.service - MariaDB 10.5.15 database server Loaded: loaded (/usr/lib/systemd/system/mariadb.service; enabled; vendor pre> Drop-In: /etc/systemd/system/mariadb.service.d └─migrated-from-my.cnf-settings.conf Active: active (running) since Thu 2019-05-30 03:20:05 EDT; 13s ago Docs: man:mysqld(8) https://mariadb.com/kb/en/library/systemd/ Process: 3517 ExecStartPost=/bin/sh -c systemctl unset-environment _WSREP_STA> Process: 3476 ExecStartPre=/bin/sh -c [ ! -e /usr/bin/galera_recovery ] && VA> Process: 3475 ExecStartPre=/bin/sh -c systemctl unset-environment _WSREP_STAR> Main PID: 3486 (mysqld) Status: "Taking your SQL requests now..." Tasks: 30 (limit: 19660) CGroup: /system.slice/mariadb.service └─3486 /usr/sbin/mysqld To Install the most common packages, execute the following command: sudo zypper install galera MariaDB-shared MariaDB-backup MariaDB-common Step 4: Secure MariaDB installation If you’re running your server in production, it is recommended to run security script to set password for root user, remove test database and disable remote login for root user. /usr/bin/mysql_secure_installation Secure your database by running the following script. $ sudo mysql_secure_installation NOTE: RUNNING ALL PARTS OF THIS SCRIPT IS RECOMMENDED FOR ALL MariaDB SERVERS IN PRODUCTION USE! PLEASE READ EACH STEP CAREFULLY! In order to log into MariaDB to secure it, we'll need the current password for the root user. If you've just installed MariaDB, and you haven't set the root password yet, the password will be blank, so you should just press enter here. Enter current password for root (enter for none): OK, successfully used password, moving on... Setting the root password ensures that nobody can log into the MariaDB
root user without the proper authorisation. Set root password? [Y/n] y New password: Re-enter new password: Password updated successfully! Reloading privilege tables.. ... Success! By default, a MariaDB installation has an anonymous user, allowing anyone to log into MariaDB without having to have a user account created for them. This is intended only for testing, and to make the installation go a bit smoother. You should remove them before moving into a production environment. Remove anonymous users? [Y/n] y ... Success! Normally, root should only be allowed to connect from 'localhost'. This ensures that someone cannot guess at the root password from the network. Disallow root login remotely? [Y/n] y ... Success! By default, MariaDB comes with a database named 'test' that anyone can access. This is also intended only for testing, and should be removed before moving into a production environment. Remove test database and access to it? [Y/n] y - Dropping test database... ... Success! - Removing privileges on test database... ... Success! Reloading the privilege tables will ensure that all changes made so far will take effect immediately. Reload privilege tables now? [Y/n] y ... Success! Cleaning up... All done! If you've completed all of the above steps, your MariaDB installation should now be secure. Thanks for using MariaDB! Ensure you: Set Database root user password Remove anonymous users Disallow root user remote logins Remove test database and access to it For just setting root password, the following command syntax should work for new installation. /usr/bin/mysqladmin -u root password 'new-password' /usr/bin/mysqladmin -u root -h linux-bswe password 'new-password' When done, test access using the root user – without a password. $ mysql -u root ERROR 1045 (28000): Access denied for user 'root'@'localhost' (using password: NO) As seen, you need to authenticate to access database console as a root user. Confirm MariaDB version. MariaDB [(none)]> SELECT VERSION(); +-----------------+ | VERSION() | +-----------------+ | 10.5.15-MariaDB | +-----------------+ 1 row in set (0.000 sec) MariaDB [(none)]> You now have MariaDB 10.5 installed on openSUSE 15. Start working on your projects powered by MariaDB RDMS.
0 notes
Text
Top 3 New Features Of SQL Server 2019 Activation Key
We all might have been using SQL servers for the last many years, but like every software, there is a need to upgrade your software as it will enhance the performance of the software you are using and provide you with better and faster outcomes. SQL Server is a management system for relational databases designed and developed by Microsoft which enables developers,and solution architects to store and retrieve data while developing software applications. SQL server 2019 activation key is an upgraded version of SQL server 2017. Read More: https://at.tumblr.com/instantkeys-blog/top-3-new-features-of-sql-server-2019-activation/5wvxyz3p3644

0 notes
Text
Windows 10 enterprise working product key 2019 無料ダウンロード.Windows 10を無料で使う。プロダクトキーは必要なし!
Windows 10 enterprise working product key 2019 無料ダウンロード.Windows 評価版ソフトウェア

Generic Volume License Keys (GVLK).Windows 10 Product Key Working Serial Keys
KMSpico Activator For Windows & Office. Download KMSpico is an activator tool that can activate any version of Windows and Office application without buying a license key. It is specially designed for the Windows operating system, and also Microsoft Office. We all know that Windows and Office are very popular programs for computer users Jan 31, · Windows 10を使用する場合、認証しないとすべての機能が使われることができません。認証については、直接に認証コードを購入する以外、さまざまな方法で無料にWindows 10ライセンス認証を回避することができます。この記事は、Windows 10ライセンス認証やクラックを回避する方法を紹介します。Estimated Reading Time: 9 mins 説明. Windows 10 Enterprise は、IT プロフェッショナルに以下の機能を提供することで、大規模および中規模の組織のニーズに対応するよう設計されています。. 最新のセキュリティ上の脅威からの最先端の保護. 柔軟な展開、更新、およびサポートの各種
Windows 10 enterprise working product key 2019 無料ダウンロード.【まとめ】Windows10 無料のライセンス認証回避·クラック方法 - Rene.E Laboratory
KMSpico Activator For Windows & Office. Download KMSpico is an activator tool that can activate any version of Windows and Office application without buying a license key. It is specially designed for the Windows operating system, and also Microsoft Office. We all know that Windows and Office are very popular programs for computer users Jan 31, · Windows 10を使用する場合、認証しないとすべての機能が使われることができません。認証については、直接に認証コードを購入する以外、さまざまな方法で無料にWindows 10ライセンス認証を回避することができます。この記事は、Windows 10ライセンス認証やクラックを回避する方法を紹介します。Estimated Reading Time: 9 mins Windows 10 Professional N Product Key MH37W-N47XK-V7XM9-CGCQG9 Windows 10 Enterprise Key NPPR9-FWDCX-D2C8J-HK-2YT43 Windows 10 Enterprise N Key DPH2V-TTNVB-4X9Q3-TJR4H-KHJW4 Windows 10 Education Key NW6C2-QMPVW-D7KKK-3GKT6-VCFB2. RAW Paste Data
この評価版ソフトウェアは、組織への導入を検討するために Windows 10 Enterprise の試用を希望される IT プロフェッショナル向けに設計されています。お客様が IT プロフェッショナルではない場合、または企業ネットワークまたはデバイスを管理する業務についていない場合は、この評価版ソフトウェアをインストールすることはお勧めしません。. ISO - Enterprise ISO - Enterprise LTSC. ダウンロードが開始されました。 ダウンロードには複数のファイルが含まれています。. Windows 10 Enterprise は、IT プロフェッショナルに以下の機能を提供することで、大規模および中規模の組織のニーズに対応するよう設計されています。.
Windows 10 バージョン 21H2 により、エンドポイントの保護、高度な攻撃の検出、新たな脅威への対応の自動化、セキュリティ対策の強化を簡単に行うことができます。また、デプロイメントと更新も合理化されているため、エンタープライズ対応のデバイスを、メーカーからユーザーに直接提供できます。. をご覧ください Windows 10 の新機能 。. Windows 10 Enterprise の LTSC エディションでは、お客様にとって特別な目的のデバイスと環境の展開オプションにアクセスできます。 通常、これらのデバイスは 1 つの重要なタスクを実行し、組織内の他のデバイスほど頻繁に機能更新プログラムを適用する必要がありません。 これらのデバイスは、通常、外部アプリやツールからのサポートに大きく依存してはいません。 LTSC の機能セットはリリースの有効期間中は変更されないので、時間の経過に伴って、従来のサポートを提供しなくなる外部ツールがいくつか現れる可能性があります。.
Get-FileHash コマンドに関する詳細はこちらからご利用いただけます。. Evaluation Center. Windows 11 Enterprise Windows 10 Enterprise. Windows Server. Windows Server Windows Server Windows Server Essentials Hyper-V Server Windows Admin Center. SQL Server. SQL Server SQL Server SQL Server SQL Server Azure SQL Edge. Microsoft Azure. Azure Migration and Modernization Program Azure を無料で試す. System Center. System Center System Center Microsoft Endpoint Manager. Microsoft Endpoint Configuration Manager Current Branch Microsoft Endpoint Configuration Manager Technical Preview Microsoft Intune.
Microsoft Viva. Microsoft Viva Topics. Microsoft ビジネスに最適な Microsoft プランを見つける SharePoint Syntex Project Visio. Office Servers. SharePoint Server Project Server Skype for Business Server Microsoft Defender for Identity.
Identity Manager. Microsoft Identity Manager SP1. Integration Services. Host Integration Server BizTalk Server Power Platform. Power BI Pro Power Apps Power Automate Power Virtual Agents. Dynamics Dynamics 無料試用版. Microsoft Cloud for Sustainability を無料で試す. 今すぐ評価する Windows Windows 11 Enterprise Windows 10 Enterprise. Windows Server Windows Server Windows Server Windows Server Essentials Hyper-V Server Windows Admin Center. SQL Server SQL Server SQL Server SQL Server SQL Server Hybrid Azure SQL Edge.
Microsoft Azure Azure Migration and Modernization Program Azure を無料で試す. System Center System Center System Center Microsoft Endpoint Manager Microsoft Endpoint Configuration Manager Current Branch Microsoft Endpoint Configuration Manager Technical Preview Microsoft Intune. Microsoft Viva Microsoft Viva Topics. Microsoft ビジネスに最適な Microsoft プランを見つける SharePoint Syntex Project Visio. Office Servers SharePoint Server Project Server Skype for Business Server Microsoft Defender for Identity Microsoft Defender for Identity.
Identity Manager Microsoft Identity Manager SP1. Integration Services Host Integration Server BizTalk Server Power Platform Power BI Pro Power Apps Power Automate Power Virtual Agents. Dynamics Dynamics 無料試用版. Sustainability Microsoft Cloud for Sustainability を無料で試す. Windows 評価版ソフトウェア. マイ エクスペリエンス マイ アクション マイ プロファイル. 評価版 評価版. Virtual LabVirtual Labs.
Virtual Labs. マイ アクション. マイ プロファイル. マイ プロファイルの編集. 並べ替え: 新着順 アルファベット順. Virtual Labs を追跡するにはサインインしてください. すべてのバーチャル ラボを見る. Windows 11 Enterprise. 評価版ソフトウェア 90 日. Windows 10 Enterprise. 評価版ソフトウェア 90 日 5 前回のアクセス:.
あなたの経験を選択してください ISO - Enterprise ISO - Enterprise LTSC. この評価版には登録が必要です。 登録して続行. ダウンロードが開始されました。 ダウンロードには複数のファイルが含まれています。 ダウンロードが自動的に開始されない場合は、下のボタンをクリックしてください。. ご使用のプラットフォームを選択してください。 32 ビット 64 ビット. Windows 10 Enterprise は、IT プロフェッショナルに以下の機能を提供することで、大規模および中規模の組織のニーズに対応するよう設計されています。 最新のセキュリティ上の脅威からの最先端の保護 柔軟な展開、更新、およびサポートの各種オプション デバイスとアプリの包括的な管理およびコントロール Windows 10 バージョン 21H2 により、エンドポイントの保護、高度な攻撃の検出、新たな脅威への対応の自動化、セキュリティ対策の強化を簡単に行うことができます。また、デプロイメントと更新も合理化されているため、エンタープライズ対応のデバイスを、メーカーからユーザーに直接提供できます。 特定の機能に関する情報をお探しですか?
をご覧ください Windows 10 の新機能 。 言語 英語 アメリカ合衆国 、英語 英国 、ドイツ語、スペイン語、フランス語、イタリア語、日本語、韓国語、ポルトガル語、中国語 簡体字 、中国語 繁体字 言語 Windows 10 Enterprise, version 21H2 bit ISO Windows 10 Enterprise, version 21H2 bit ISO Windows 10 Enterprise LTSC bit ISO Windows 10 Enterprise LTSC bit ISO Windows 10 Enterprise の LTSC エディションでは、お客様にとって特別な目的のデバイスと環境の展開オプションにアクセスできます。 通常、これらのデバイスは 1 つの重要なタスクを実行し、組織内の他のデバイスほど頻繁に機能更新プログラムを適用する必要がありません。 これらのデバイスは、通常、外部アプリやツールからのサポートに大きく依存してはいません。 LTSC の機能セットはリリースの有効期間中は変更されないので、時間の経過に伴って、従来のサポートを提供しなくなる外部ツールがいくつか現れる可能性があります。.
ダウンロードを続行する前に、「ライセンス認証とご使用に関するガイド」および「注意事項」をよくお読みください。 Windows 10 の システム要件を確認する。 登録後、90 日間の評価を行うためにソフトウェア製品版のダウンロードおよびインストールを行う。 評価のガイドとなるリソースを確認します。 ライセンス認証とご使用に関するガイド 問題が起こらないように準備することが重要です。この評価版をインストールする前に、ファイルや設定のバックアップを取ります。 インストール時に、Windowsはアクティブ化するように要求します。 このソフトウェアにはプロダクトキーは必要ありません。 Windows 10 Enterprise を使用するには、Microsoft アカウントで PC にサインインする必要があります。ローカル アカウントを作成するオプションは、最終版のリリース時にご利用いただけるようになります。 提供されている ISO ファイルのいずれかを使用して Windows 10 Enterprise をインストールした場合は、アンインストールできません。また、Windows 10 Enterprise をインストールした後は、PC の復旧パーティションを使用して前のバージョンの Windows に戻すことはできません。以前のオペレーティング システムをクリーン インストールし、ご使用のプログラムおよびデータのすべてを再インストールする必要があります。 評価版のインストール後、ライセンス認証が行われない場合、または評価版の有効期��が切れた場合、デスクトップの背景が黒に変わり、システムが正規版ではないことを示す通知が表示され、1 時間おきに PC がシャットダウンされます 。 注意事項 Windows 10 Enterprise は Windows 8.
製品の詳細: Windows 10 Enterprise. 製品リソース 前回のアクセス:. システム要件: Windows 10 Enterprise. 入門ガイド 前回のアクセス:. Microsoft Tech Community: Windows コミュニティ 前回のアクセス:. サービスとしての Windows クイック ガイド. Windows に関する IT 担当者ブログ. Windows を展開するための準備. Windows Update for Business を使用して更新プログラムをデプロイする. 製品リソース 7 分 前回のアクセス:. 製品リソース 7 分. Windows Server Update Services WSUS を使用して更新プログラムをデプロイする.
製品リソース 14 分 前回のアクセス:. 製品リソース 14 分. Configuration Manager を使用して更新プログラムをデプロイする. Windows 10 の管理. Windows 10とMicrosoft アプリのアップデートの展開計画の策定. MVA コースと学習教材 5 分 前回のアクセス:. MVA ��ースと学習教材 5 分. Windows 10とMicrosoft アプリのアップデートの展開準備. MVA コースと学習教材 前回のアクセス:. MVA コースと学習教材. Windows 10とMicrosoft アプリのアップデートの展開.
0 notes
Text
Microsoft SQL Server 2019 Genuine Activation Key For 1 user
Microsoft SQL Server 2019 Genuine Activation Key For 1 user
Microsoft SQL Server 2019 Genuine Activation Key For 1 user SQL Server 2019 Standard Edition License is brand new and original. Once activated grants you access to all updates. This product does not include a box or certificate. Core license doesn’t require CALs for each connection to your SQL Server system. Unlimited user/device client access. License valid worldwide, any language. Delivery by…

View On WordPress
0 notes
Text
Top 3 New Features Of SQL Server 2019 Activation Key
We all might have been using SQL servers for the last many years, but like every software, there is a need to upgrade your software as it will enhance the performance of the software you are using and provide you with better and faster outcomes. SQL Server is a management system for relational databases designed and developed by Microsoft which enables developers,and solution architects to store and retrieve data while developing software applications. SQL server 2019 activation key is an upgraded version of SQL server 2017. Continue reading to know about the latest features in SQL server 2019.

Latest Features Of SQL Server 2019 Activation Key
Microsoft SQL Server is a relative database management system that supports various transaction processing, business intelligence, and analytics in corporate IT environments. However, you can choose the Windows server 2022 key as it will help you store multiple things like images, projects, and spreadsheets. On the other hand, an SQL server only allows you to store raw data. Let's read about the features of SQL server 2019.
1. Accelerated Database Recovery
It is an entirely new way for SQL Server to perform data recovery in the event of a trade rollback, an instance restart, or an availability group failover. The SQL team has worked on improving the recovery process, redeveloped how recovery works, and efficiently decreased the process's working. SQL server 2019 activation key comes with an upgrade in ADR that will benefit SLA and RTO.
2. Resumable Index Build
In the older version, the SQL server could not stop an index rebuild operation in progress. However, the SQL server 2019 activation key has the capabilities of stopping an index restore operation in progress, saving the work that has been done so far, and resuming at some other point in time. In the older version of the SQL server, you would need to cancel your rebuild, wait for a recovery process, then start again from scratch. However, this new feature can help you get rid of these problems.
3. Query Store Capture Policies
Query Store is an outstanding performance tuning and trending device that allows storing, measuring, and many other things. The new capability of custom policies means you can fine-tune the queries you want Query Store to track based on their performance statistics, such as how often they run and more.
Get Your SQL Server 2019 Activation Key Today!
Up gradation of the tool is one of the crucial things to do in all fields as it will help boost your performance. If you are looking forward to buy office 2016 key, you can contact Instant-Key. They provide one of the most affordable products. Visit their website to explore a variety of products.
0 notes
Link
Read More: Microsoft SQL Server 2019 Standard Transform Your Business with a Tied in Data Platform
0 notes
Text
Win7 Keygen Download
5
Windows 7 Keygen Download Crack
Windows 7 Keygen Free Download
Jan 16, 2018 Cdma Workshop 2.7 Full Cracked Free Download. Windows XP Professional 64 Bit ISO Free Download.Free Download Autodesk AutoCAD 2017 32 Bit 64 Bit Full Crack - Download as. Start XFORCE Keygen 64bits version 8. Simply click on close and click on activate.Xforce Keygen Autocad Lt 2017 sql server 2008 enterprise sp1. Windows 7 is by far the most widely used Windows OS. You can download Windows 7 from Microsoft’s website. But you will need a genuine Windows Serial Key to activate the operating system. To get working keys, you will have to buy them from Microsoft. Keygen,win7 Uncategorized. Microsoft Diagnostic and Recovery Toolset (MS-DaRT) WIndows 10 torrent download. As such, free download rules include a series of actions to keep you busy for hours. The game also features dedicated cars that you can use to cover the map quickly. Do you find plowing through a dangerous area, and there. 'In the joy of other's.lies our own, In the progress of other's.our progress'.
XFORCE Keygen 2020 Full Crack Free Download 100% Working Serial Key
Read Complete Step on, Xforce Keygen, Active file for Autodesk 2020 also How to use X-force 2020, XFORCE Crack and XFORCE 2020, Xforce keygen generator free download
XFORCE Keygen 2020 Full Crack Free Download 100% Working Serial Key Xforce Keygen 2020, is the stunning software program which will activate your AutoCAD software. AutoCAD may be a simplified graphical software that lets the user create maps and architectural projects. Needless to say these sorts of software programs aren’t free of charge, so forgetting it, the user has got to first download the setup file from the official website. For the very first time, you’ll get the trial version afterwards user must need to purchase an activation key for lifetime activation.
With this program, you’ll get an entire solution to activate the AutoCAD software trial version without paying zero money. For sure, it’s created by an expert coder who experiences a few years in creating hacks, cracks, and Keygen for various sorts of multiplayer and online games. However, it’s 100% fully working to completely activate and update your compatibility with the latest Windows PC.
XFORCE Adobe 2019 keygen:

Moreover, XFORCE Keygen an ancient also precious tool getting used for a long to activate any of the webs also offline games that required to activate with the help username & password. The force adobe 2019 Keygen bypass all this process and provides a virtual key that doesn’t need any longer purchase of the merchandise to activate.
However, thanks to its free download and being priceless, during this way, it saves tons of cash for the users of X-FORCE Keygen by simply installing it into their system by downloading from the below-given download button.
XFORCE Crack:
XFORCE Crack was first created by illustrator Rob lie field after he started penciling the New Mutants. For accomplishing this particular program, it provides numerous tools implemented we’ve got the technologies. It offers many tools implemented to realize this software program we’ve got the technology to spice up performance. Thanks to its free download, all the method provides the virtual key that doesn’t need any longer purchase of the merchandise to activate the software entirely.
XFORCE Keygen:
EK9-9W2-N00-2A0
ML1-X9N-0V9-O70
HI0-75H-2TH-A7H
NYJ-6W2-T29-PN3
DGW-DH1-ZAW-YYZ
EGM-FMJ-6W4-UEI
Y4P-69M-M0D-HFB
KWI-39K-41G-TQM
JAV-256-DQ6-UID
IMD-43V-UF1-BF4
XAB-V8T-VXI-BQU
95S-D1K-VOJ-2MG
CRH-RIJ-OGL-MIJ
P25-6TI-QA9-PHK
SHY-2LL-0XF-MCI
3W9-THZ-90C-EBU
Features of XFORCE Keygen & Crack:
Furthermore, AutoCAD now includes advance industry-specific features in its new carpenter’s kit. This software is now loaded with new intelligent objects for creating architecture, engineering, computer engineering, electrical design, and more.
The AutoCAD software program is meant for the preparation of the planning documentation for that specific variable. Many significantly accelerate the organizations offering documentation and release detalirrovok all the time. The local cloud and mobile solutions also ensure collaboration. It’s developed beneath the cross-platform Windows and Mac operating devices.
It provides commands to make automate floor plans, floor sections, internal structure, and elevations.
Using XFORCE Keygen, users can Draw piping, ducting, underground piping, and circuiting quickly with advanced parts libraries.
AutoCAD provides Auto-generate labels, annotations, secure layers, complete schedules, lists, graphs, and tables.
Finally, it always uses a rules-driven workflow that can enforce industry standards.

Keep Reading Complete Step on, Xforce Keygen, Active file for Autodesk 2020 also How to use X-force 2020, XFORCE Crack and XFORCE 2020, Xforce keygen generator free download
Group Invitations For Team Projects
You can also invite groups and team members from your company address book. You can invite them with addresses as well as without addresses, for more efficient communication.
Illustrator CC 2020 Xforce Keygen Activator (Win 7, 8 &10)
Adobe Illustrator CC 2020 Serial key is one of the most useable platforms by designers for creating graphic pieces. It has also remained with more time in force since it goes over 20 years in the designing and digital art profession. CCleaner Professional Full Version free download for Windows 10
AutoCAD:
You can design Everything with 2D and 3D CAD software XFORCE. The remake includes access to industry-specific toolsets and improved workflows across most screens desktop, web, and mobile.
FL Studio 20.5.1.1193 Product Key:
GTEL5-JSG3E-HGR6N-67E7O-UJFGR
FL Studio 20.5.1.1193 Product Code:
5T3PI-UBJHG-FX5Q7-URVJH-GBXRT
FL Studio 20.5.1.1193 License Number:
S6XA7I-KJXHG-TYJXK-IOXT7-UXY5T

FL Studio 20.5.1.1193 Serial Number:
4X2RE-FVCSE-R3VBU-YHXFE-RX5T6
What’s New?
The interface is updated.
The mechanism of visual simple access drawing within the tape all the way.
Tape Gallery tool added.
New inset the “Create” are tools for dealing with the templates projects from Autodesk and Autodesk 360 cloud storage.
Accelerates your windows OS to get the latest updates.
XFORCE Keygen Full Crack is the Holocaust to activate all AutoCAD software.
Updated interface getting a for more dark background significantly decreases the burden on the attention-making of all drawing elements.
Preview the instructions will let the user read all the procedures about the usage of this software.
Implemented models can import any supported file formats with auto-generation of documentation.
Xforce Keygen has added intelligent instruction with auto-correction.
Method Of Installation:
First, go to the official website and download the setup file from the link given below.
There are two ways to activate the setup file.
1st is to use serial keys.
2nd is the Product Key for AutoCAD products.
You will get Xforce Keygen for Free.
Please read the Instruction file and activate it.
Copy the generated Activation Code towards the related field of Autodesk’s activation windows and hit next twice.
For further assistance, click on the help menu and get the help all the way.
Done! You have done it.
System Requirements Xforce keymaker:
XForce Crack Recommended OS:
Microsoft® Windows 7 SP1&SP2 with update KB4019990 (64 bits only)
BASIC processor: 2.4-2.9 GHz processor
Recommended: Processor 3 Plus GHz
Multiple processors: Yes
Basic Memory: 16 GB
Recommended: 32 GB!
Windows 7 Keygen Download Crack
Latest Autodesk Industry Collections:
Keep Reading Complete Step on, Xforce Keygen, Active file for Autodesk 2020 also How to use X-force 2020, XFORCE Crack and XFORCE 2020, Xforce keygen generator free download
Why Choose Xforce 2019 crack with keygen?
Create: button is the gear for coping with the template tasks from Auto desk 360 cloud storage.
New inset: The web page is ideal for instant access to just about assembling your design elements.
Preview commands: The latest version of 2019 will allow the user to examine all of the techniques about the usage of this software.
Tape Gallery: The mechanism of apparent ease of getting admission to drawing in the tape.
Windows 7 Keygen Free Download
All Product key for Autodesk 2020
A product key is required when you install Autodesk products as point products or from product sets. In this case, it requires different product keys, even for the same Autodesk product version, to distinguish different product packages.
This is a complete list of Product Key for all Autodesk 2020 products. Press Ctrl + F to find the key for your product. This post will continue to be updated, and the latest edits should follow TecroNet.
Activation Keys of Software Full Updated Version
Xforce keygen in Rar File here
Keep Reading Complete Step on, Xforce Keygen, Active file for Autodesk 2020 also How to use X-force 2020, XFORCE Crack and XFORCE 2020, Xforce keygen generator free download

How To use & Install Xforce Keygen?
First, install this system on your PC.
Use any of these Serial keys 667-98989898, 400-45454545, 066-66666666.
After installation and restart your PC.
Make sure to disable the Internet. It’ll explain that a web connection is Needed to click on set off again.
Run Xforce Keygen according to your needs. (32bits or 64bits).
Click Patch (you want to see correctly patched).
Copy the code into the keygen and press generate.
Now paste the activation code to the activation screen and click next.
You’ve given a fully registered product.
Conclusion:
Therefore, the one and therefore, the only suggestion from our side to all or any the people that need to buy the paid versions of the games, you’ll save tons of cash by simply installing the XFORCE Keygen. Most noteworthy from the above-given link and luxuriate in a lifetime free & unlimited use of a paid version of the software also games.
How useful was this post?
Click on a star to rate it!
MRT Dongle v2.60 Full Cracked Without Box With New Keygen 2019. this is new crack dongle of MRT dongle v2.60 MRT Dongle v2.60 crack the best dongle for all smartphone. vivo, oppo, Xiaomi, Lenovo, Nokia, etc. you can easily unlock a phone from this tool. Here, MRT Dongle v2.60 full crack of MRT with keygen new 2019.
Download MRT Dongle v2.60 Crack
File Name:- MRT 2.60 Final By mobileguru4.com File Size:- 397mb System :- all operating system(win10,win8,win7) File Link:- Click Here
Keygen Download:- Click Here
How to Use:
Tags:mrt 2.60mrt 2.60 crackmrt donglemrt dongle 2.60 crackpreviousFRP Bypass apk File Download
nextUFI Box Setup: v1.4.0.1464 Latest=nav-direction>
0 notes