#SQL Server transactions
Explore tagged Tumblr posts
Text
Understanding Transaction Isolation Levels in SQL Server
Introduction Have you ever wondered what happens behind the scenes when you start a transaction in SQL Server? As a database developer, understanding how isolation levels work is crucial for writing correct and performant code. In this article, we’ll dive into the details of what happens when you begin an explicit transaction and run multiple statements before committing. We’ll explore whether…

View On WordPress
0 notes
Text
Structured Query Language (SQL): A Comprehensive Guide
Structured Query Language, popularly called SQL (reported "ess-que-ell" or sometimes "sequel"), is the same old language used for managing and manipulating relational databases. Developed in the early 1970s by using IBM researchers Donald D. Chamberlin and Raymond F. Boyce, SQL has when you consider that end up the dominant language for database structures round the world.
Structured query language commands with examples
Today, certainly every important relational database control system (RDBMS)—such as MySQL, PostgreSQL, Oracle, SQL Server, and SQLite—uses SQL as its core question language.
What is SQL?
SQL is a website-specific language used to:
Retrieve facts from a database.
Insert, replace, and delete statistics.
Create and modify database structures (tables, indexes, perspectives).
Manage get entry to permissions and security.
Perform data analytics and reporting.
In easy phrases, SQL permits customers to speak with databases to shop and retrieve structured information.
Key Characteristics of SQL
Declarative Language: SQL focuses on what to do, now not the way to do it. For instance, whilst you write SELECT * FROM users, you don’t need to inform SQL the way to fetch the facts—it figures that out.
Standardized: SQL has been standardized through agencies like ANSI and ISO, with maximum database structures enforcing the core language and including their very own extensions.
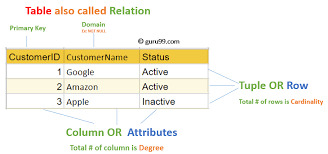
Relational Model-Based: SQL is designed to work with tables (also called members of the family) in which records is organized in rows and columns.
Core Components of SQL
SQL may be damaged down into numerous predominant categories of instructions, each with unique functions.
1. Data Definition Language (DDL)
DDL commands are used to outline or modify the shape of database gadgets like tables, schemas, indexes, and so forth.
Common DDL commands:
CREATE: To create a brand new table or database.
ALTER: To modify an present table (add or put off columns).
DROP: To delete a table or database.
TRUNCATE: To delete all rows from a table but preserve its shape.
Example:
sq.
Copy
Edit
CREATE TABLE personnel (
id INT PRIMARY KEY,
call VARCHAR(one hundred),
income DECIMAL(10,2)
);
2. Data Manipulation Language (DML)
DML commands are used for statistics operations which include inserting, updating, or deleting information.
Common DML commands:
SELECT: Retrieve data from one or more tables.
INSERT: Add new records.
UPDATE: Modify existing statistics.
DELETE: Remove information.
Example:
square
Copy
Edit
INSERT INTO employees (id, name, earnings)
VALUES (1, 'Alice Johnson', 75000.00);
three. Data Query Language (DQL)
Some specialists separate SELECT from DML and treat it as its very own category: DQL.
Example:
square
Copy
Edit
SELECT name, income FROM personnel WHERE profits > 60000;
This command retrieves names and salaries of employees earning more than 60,000.
4. Data Control Language (DCL)
DCL instructions cope with permissions and access manage.
Common DCL instructions:
GRANT: Give get right of entry to to users.
REVOKE: Remove access.
Example:
square
Copy
Edit
GRANT SELECT, INSERT ON personnel TO john_doe;
five. Transaction Control Language (TCL)
TCL commands manage transactions to ensure data integrity.
Common TCL instructions:
BEGIN: Start a transaction.
COMMIT: Save changes.
ROLLBACK: Undo changes.
SAVEPOINT: Set a savepoint inside a transaction.
Example:
square
Copy
Edit
BEGIN;
UPDATE personnel SET earnings = income * 1.10;
COMMIT;
SQL Clauses and Syntax Elements
WHERE: Filters rows.
ORDER BY: Sorts effects.
GROUP BY: Groups rows sharing a assets.
HAVING: Filters companies.
JOIN: Combines rows from or greater tables.
Example with JOIN:
square
Copy
Edit
SELECT personnel.Name, departments.Name
FROM personnel
JOIN departments ON personnel.Dept_id = departments.Identity;
Types of Joins in SQL
INNER JOIN: Returns statistics with matching values in each tables.
LEFT JOIN: Returns all statistics from the left table, and matched statistics from the right.
RIGHT JOIN: Opposite of LEFT JOIN.
FULL JOIN: Returns all records while there is a in shape in either desk.
SELF JOIN: Joins a table to itself.
Subqueries and Nested Queries
A subquery is a query inside any other query.
Example:
sq.
Copy
Edit
SELECT name FROM employees
WHERE earnings > (SELECT AVG(earnings) FROM personnel);
This reveals employees who earn above common earnings.
Functions in SQL
SQL includes built-in features for acting calculations and formatting:
Aggregate Functions: SUM(), AVG(), COUNT(), MAX(), MIN()
String Functions: UPPER(), LOWER(), CONCAT()
Date Functions: NOW(), CURDATE(), DATEADD()
Conversion Functions: CAST(), CONVERT()
Indexes in SQL
An index is used to hurry up searches.
Example:
sq.
Copy
Edit
CREATE INDEX idx_name ON employees(call);
Indexes help improve the performance of queries concerning massive information.
Views in SQL
A view is a digital desk created through a question.
Example:
square
Copy
Edit
CREATE VIEW high_earners AS
SELECT call, salary FROM employees WHERE earnings > 80000;
Views are beneficial for:
Security (disguise positive columns)
Simplifying complex queries
Reusability
Normalization in SQL
Normalization is the system of organizing facts to reduce redundancy. It entails breaking a database into multiple related tables and defining overseas keys to link them.
1NF: No repeating groups.
2NF: No partial dependency.
3NF: No transitive dependency.
SQL in Real-World Applications
Web Development: Most web apps use SQL to manipulate customers, periods, orders, and content.
Data Analysis: SQL is extensively used in information analytics systems like Power BI, Tableau, and even Excel (thru Power Query).
Finance and Banking: SQL handles transaction logs, audit trails, and reporting systems.
Healthcare: Managing patient statistics, remedy records, and billing.
Retail: Inventory systems, sales analysis, and consumer statistics.
Government and Research: For storing and querying massive datasets.
Popular SQL Database Systems
MySQL: Open-supply and extensively used in internet apps.
PostgreSQL: Advanced capabilities and standards compliance.
Oracle DB: Commercial, especially scalable, agency-degree.
SQL Server: Microsoft’s relational database.
SQLite: Lightweight, file-based database used in cellular and desktop apps.
Limitations of SQL
SQL can be verbose and complicated for positive operations.
Not perfect for unstructured information (NoSQL databases like MongoDB are better acceptable).
Vendor-unique extensions can reduce portability.
Java Programming Language Tutorial
Dot Net Programming Language
C ++ Online Compliers
C Language Compliers
2 notes
·
View notes
Text
Why Tableau is Essential in Data Science: Transforming Raw Data into Insights

Data science is all about turning raw data into valuable insights. But numbers and statistics alone don’t tell the full story—they need to be visualized to make sense. That’s where Tableau comes in.
Tableau is a powerful tool that helps data scientists, analysts, and businesses see and understand data better. It simplifies complex datasets, making them interactive and easy to interpret. But with so many tools available, why is Tableau a must-have for data science? Let’s explore.
1. The Importance of Data Visualization in Data Science
Imagine you’re working with millions of data points from customer purchases, social media interactions, or financial transactions. Analyzing raw numbers manually would be overwhelming.
That’s why visualization is crucial in data science:
Identifies trends and patterns – Instead of sifting through spreadsheets, you can quickly spot trends in a visual format.
Makes complex data understandable – Graphs, heatmaps, and dashboards simplify the interpretation of large datasets.
Enhances decision-making – Stakeholders can easily grasp insights and make data-driven decisions faster.
Saves time and effort – Instead of writing lengthy reports, an interactive dashboard tells the story in seconds.
Without tools like Tableau, data science would be limited to experts who can code and run statistical models. With Tableau, insights become accessible to everyone—from data scientists to business executives.
2. Why Tableau Stands Out in Data Science
A. User-Friendly and Requires No Coding
One of the biggest advantages of Tableau is its drag-and-drop interface. Unlike Python or R, which require programming skills, Tableau allows users to create visualizations without writing a single line of code.
Even if you’re a beginner, you can:
✅ Upload data from multiple sources
✅ Create interactive dashboards in minutes
✅ Share insights with teams easily
This no-code approach makes Tableau ideal for both technical and non-technical professionals in data science.
B. Handles Large Datasets Efficiently
Data scientists often work with massive datasets—whether it’s financial transactions, customer behavior, or healthcare records. Traditional tools like Excel struggle with large volumes of data.
Tableau, on the other hand:
Can process millions of rows without slowing down
Optimizes performance using advanced data engine technology
Supports real-time data streaming for up-to-date analysis
This makes it a go-to tool for businesses that need fast, data-driven insights.
C. Connects with Multiple Data Sources
A major challenge in data science is bringing together data from different platforms. Tableau seamlessly integrates with a variety of sources, including:
Databases: MySQL, PostgreSQL, Microsoft SQL Server
Cloud platforms: AWS, Google BigQuery, Snowflake
Spreadsheets and APIs: Excel, Google Sheets, web-based data sources
This flexibility allows data scientists to combine datasets from multiple sources without needing complex SQL queries or scripts.
D. Real-Time Data Analysis
Industries like finance, healthcare, and e-commerce rely on real-time data to make quick decisions. Tableau’s live data connection allows users to:
Track stock market trends as they happen
Monitor website traffic and customer interactions in real time
Detect fraudulent transactions instantly
Instead of waiting for reports to be generated manually, Tableau delivers insights as events unfold.
E. Advanced Analytics Without Complexity
While Tableau is known for its visualizations, it also supports advanced analytics. You can:
Forecast trends based on historical data
Perform clustering and segmentation to identify patterns
Integrate with Python and R for machine learning and predictive modeling
This means data scientists can combine deep analytics with intuitive visualization, making Tableau a versatile tool.
3. How Tableau Helps Data Scientists in Real Life
Tableau has been adopted by the majority of industries to make data science more impactful and accessible. This is applied in the following real-life scenarios:
A. Analytics for Health Care
Tableau is deployed by hospitals and research institutions for the following purposes:
Monitor patient recovery rates and predict outbreaks of diseases
Analyze hospital occupancy and resource allocation
Identify trends in patient demographics and treatment results
B. Finance and Banking
Banks and investment firms rely on Tableau for the following purposes:
✅ Detect fraud by analyzing transaction patterns
✅ Track stock market fluctuations and make informed investment decisions
✅ Assess credit risk and loan performance
C. Marketing and Customer Insights
Companies use Tableau to:
✅ Track customer buying behavior and personalize recommendations
✅ Analyze social media engagement and campaign effectiveness
✅ Optimize ad spend by identifying high-performing channels
D. Retail and Supply Chain Management
Retailers leverage Tableau to:
✅ Forecast product demand and adjust inventory levels
✅ Identify regional sales trends and adjust marketing strategies
✅ Optimize supply chain logistics and reduce delivery delays
These applications show why Tableau is a must-have for data-driven decision-making.
4. Tableau vs. Other Data Visualization Tools
There are many visualization tools available, but Tableau consistently ranks as one of the best. Here’s why:
Tableau vs. Excel – Excel struggles with big data and lacks interactivity; Tableau handles large datasets effortlessly.
Tableau vs. Power BI – Power BI is great for Microsoft users, but Tableau offers more flexibility across different data sources.
Tableau vs. Python (Matplotlib, Seaborn) – Python libraries require coding skills, while Tableau simplifies visualization for all users.
This makes Tableau the go-to tool for both beginners and experienced professionals in data science.
5. Conclusion
Tableau has become an essential tool in data science because it simplifies data visualization, handles large datasets, and integrates seamlessly with various data sources. It enables professionals to analyze, interpret, and present data interactively, making insights accessible to everyone—from data scientists to business leaders.
If you’re looking to build a strong foundation in data science, learning Tableau is a smart career move. Many data science courses now include Tableau as a key skill, as companies increasingly demand professionals who can transform raw data into meaningful insights.
In a world where data is the driving force behind decision-making, Tableau ensures that the insights you uncover are not just accurate—but also clear, impactful, and easy to act upon.
#data science course#top data science course online#top data science institute online#artificial intelligence course#deepseek#tableau
3 notes
·
View notes
Text
Log Shipping (or LS) in SQL Server is a disaster recovery solution that automates the backup, copy, and restore of transaction logs from a primary server to a secondary server. Let's Explore Deeply:
https://madesimplemssql.com/log-shipping-in-sql-server/
Follow us on FB: https://www.facebook.com/profile.php?id=100091338502392
&
Join our Group: https://www.facebook.com/groups/652527240081844
2 notes
·
View notes
Text
Scaling Secrets: The Architecture That Made 1 Million Users Possible.
Picture this: you launch an app, thinking it'll be a cool side project. But then, something unexpected happens—boom, a viral post, a feature takes off, and suddenly, you're not just handling a few hundred users… you're scrambling to manage 1 million.
It’s every startup’s dream, right? But when reality hits, it's more like a nightmare.
How do you keep your app running smoothly as it rockets to 1 million users? Is there a magic formula, or are you just riding on sheer luck? Spoiler: It’s the architecture—the unsung hero of scaling that most people never talk about.

Let’s dive into the secret sauce that makes all that user growth possible without your app crumbling into oblivion. Trust us, it’s not as simple as throwing money at servers. This is how the pros do it.
Choosing the Right Tech Stack: Building a House with Strong Foundations Okay, first things first: Tech stack matters. Like, a lot. You wouldn't try to build a skyscraper on sand, right? So why would you choose a tech stack that can't handle the weight of millions of users?
The magic happens when you combine the right tools, like a killer backend framework and a database that grows with you.
Backend Frameworks like Node js or Go are the go-to for handling tons of requests. They’re built for speed and efficiency—perfect for a fast-growing app.
For databases, you’ve got to pick wisely. NoSQL (think MongoDB or Cassandra) can handle huge amounts of unstructured data, while SQL (like PostgreSQL or MySQL) is your best friend if you need relationships and transactions in your data.
Caching with tools like Redis or Memcached? A must. Speeding things up by storing frequently accessed data right where it’s needed is a game changer.
Pro Tip: Always choose a tech stack that can scale horizontally, meaning you can add more servers as you grow, rather than upgrading a single, overworked one. (That’s vertical scaling—it's not ideal.)
Horizontal Scaling: More Servers, More Power, No Drama When your app starts attracting millions of users, you’ll quickly discover that vertical scaling—just adding more juice to a single server—doesn’t cut it. It’s like trying to get 10,000 people into a restaurant that only has 10 tables.
Horizontal scaling is where the magic happens. You add more servers to handle the load. It’s like spreading out your resources instead of cramming them into one spot.
Here’s how it works:
A load balancer (like HAProxy or Nginx) distributes the traffic evenly across servers, so no single server crashes from a flood of traffic.
With auto-scaling, your system can automatically add or remove servers based on demand. Got a huge spike in traffic? The system scales up. A quieter day? It scales down. Simple, smart, and flexible.
Outcome: Your app keeps running fast, even when things get crazy.
Sharding: Breaking Up Your Database So It Doesn’t Break You As your app grows, your database grows with it. But here’s the thing: Databases can’t just keep growing forever. At some point, they get too big to handle efficiently. So, how do you keep things running smoothly?
Enter sharding. Think of it like slicing a giant cake into manageable pieces. Instead of storing everything on one massive database, you break it down into smaller, more manageable chunks (called shards).
This way, no one shard gets overloaded. Requests are distributed across multiple database instances, which dramatically speeds things up.
Pro Tip: You can shard your database by horizontal partitioning (e.g., splitting it based on user regions or data types). This reduces database bottlenecks and keeps everything running smoothly.
Microservices: Because One Big App Is a Disaster Waiting to Happen Remember when apps used to be monolithic? Everything was packed into one giant codebase, and you couldn’t change anything without breaking the whole thing. It was a developer's nightmare, and it didn’t scale.
Instead of trying to make one giant app work for everyone, microservices break your app down into smaller, independent pieces. Each microservice does one thing really well, and you can scale those individual pieces separately.
For example, you can have separate services for:
User authentication
Payments
Notifications
Search
These can all run independently, and you can scale them up or down based on specific needs. No more overloading the entire app when just one piece needs more power.
Pro Tip: Use API gateways to handle communication between your microservices and route traffic where it needs to go. This keeps things organized and efficient.
CDNs: Because Speed Kills (In a Good Way) Speed is everything when you’ve got millions of users. Think about it: If your app’s taking more than a few seconds to load, users will bounce faster than you can say “goodbye.” So, how do you speed things up? The answer is simple: CDNs (Content Delivery Networks).
A CDN caches static content (like images, CSS files, and scripts) on multiple servers around the world. So, no matter where your users are, they’re always getting content from the closest server to them. Faster load times = happy users.
Pro Tip: Use Cloudflare or AWS CloudFront to distribute your static assets. This also reduces the load on your primary servers, leaving more resources for dynamic content.
Asynchronous Processing: Don’t Make Your Users Wait Nobody likes waiting. So when your app has background tasks (like sending emails, processing payments, or generating reports), don’t make your users wait around for them to finish.
Instead of handling these tasks synchronously (i.e., right during the user’s request), you process them asynchronously in the background.
This keeps your app responsive, letting users go about their business while those tasks run in the background.
How it works:
Use message queues (like RabbitMQ or Kafka) to send tasks to a queue.
Then, set up worker processes to pull tasks from the queue and process them at their own pace.
Outcome: Your app is faster and more responsive, which means a better experience for your users.
Proactive Monitoring: Because You Don’t Want to Be Caught Off Guard Here’s a brutal truth: things will break. It’s not if—it’s when. The key is to catch issues early before they cause a domino effect of failures.
Proactive monitoring with tools like Prometheus, Datadog, or New Relic keeps an eye on your app’s health in real-time. You’ll get alerts for anything that seems off—like a spike in response times or a server that’s about to crash—so you can fix it before it affects users.
Pro Tip: Set up alerting systems that notify you about potential issues (e.g., high traffic, slow queries). This lets you scale or fix things on the fly.
Failover and Redundancy: Plan for the Worst, Hope for the Best A million users means that even a single point of failure can cause major issues. That’s why you need redundancy and failover built into your architecture. Think of it like a safety net.
Have multiple data centers in different locations.
Replicate your databases and services to ensure that if one fails, the others can pick up the slack.
Use health checks to automatically route traffic to healthy servers.
Outcome: Your app stays up and running 24/7—even if something goes wrong. Users stay happy, and you sleep easy.
The Million-User Blueprint: Scale Smart, Scale Right Getting to 1 million users isn’t magic. It’s a combination of smart design, the right tech stack, and the architecture that lets you scale gracefully. Horizontal scaling, microservices, sharding, CDNs, and asynchronous processing are just a few of the building blocks that power apps with massive user bases.
So, the next time your app goes viral, don’t panic. Instead, focus on scaling smart with these strategies. Because handling 1 million users doesn’t just require hard work—it requires building the right foundation from the start.
Ready to scale? Let’s get building! 🚀
0 notes
Text
How to Improve Database Performance with Smart Optimization Techniques
Database performance is critical to the efficiency and responsiveness of any data-driven application. As data volumes grow and user expectations rise, ensuring your database runs smoothly becomes a top priority. Whether you're managing an e-commerce platform, financial software, or enterprise systems, sluggish database queries can drastically hinder user experience and business productivity.
In this guide, we’ll explore practical and high-impact strategies to improve database performance, reduce latency, and increase throughput.
1. Optimize Your Queries
Poorly written queries are one of the most common causes of database performance issues. Avoid using SELECT * when you only need specific columns. Analyze query execution plans to understand how data is being retrieved and identify potential inefficiencies.
Use indexed columns in WHERE, JOIN, and ORDER BY clauses to take full advantage of the database indexing system.
2. Index Strategically
Indexes are essential for speeding up data retrieval, but too many indexes can hurt write performance and consume excessive storage. Prioritize indexing on columns used in search conditions and join operations. Regularly review and remove unused or redundant indexes.
3. Implement Connection Pooling
Connection pooling allows multiple application users to share a limited number of database connections. This reduces the overhead of opening and closing connections repeatedly, which can significantly improve performance, especially under heavy load.
4. Cache Frequently Accessed Data
Use caching layers to avoid unnecessary hits to the database. Frequently accessed and rarely changing data—such as configuration settings or product catalogs—can be stored in in-memory caches like Redis or Memcached. This reduces read latency and database load.
5. Partition Large Tables
Partitioning splits a large table into smaller, more manageable pieces without altering the logical structure. This improves performance for queries that target only a subset of the data. Choose partitioning strategies based on date, region, or other logical divisions relevant to your dataset.
6. Monitor and Tune Regularly
Database performance isn’t a one-time fix—it requires continuous monitoring and tuning. Use performance monitoring tools to track query execution times, slow queries, buffer usage, and I/O patterns. Adjust configurations and SQL statements accordingly to align with evolving workloads.
7. Offload Reads with Replication
Use read replicas to distribute query load, especially for read-heavy applications. Replication allows you to spread read operations across multiple servers, freeing up the primary database to focus on write operations and reducing overall latency.
8. Control Concurrency and Locking
Poor concurrency control can lead to lock contention and delays. Ensure your transactions are short and efficient. Use appropriate isolation levels to avoid unnecessary locking, and understand the impact of each level on performance and data integrity.
0 notes
Text
Data hacks and identity theft have been making the headlines in recent years, making the security of your website more important than ever before. This is especially true if you handle financial transactions through your company's site, as you'll be processing your customers' sensitive financial data. Fortunately, you have many tools available to you to help ensure your website is as secure as possible. ScanMyServer ScanMyServer provides a comprehensive report of vulnerabilities throughout your website and on your server. It can identify PHP code injection, SQL injection, blind SQL injection, HTTP header injection and other scripting vulnerabilities. This service is free, and there is no registration required to test your site. You'll receive your results via email and can download a security badge to display on your site for your customers' peace of mind. Vega Vega is a security scanner designed for use with web applications. It provides an easy-to-use interface that makes the process as streamlined as possible, even for those who are unfamiliar with web security testing. It can help identify cross-site scripting, SQL injection and other application vulnerabilities. This open source application is backed by a powerful API for even greater customization and capability. Metasploit Metasploit makes use of the latest ethical hacking techniques to detect website vulnerabilities. This is what is known as penetration testing and has become more and more popular in recent years. If ethical hackers can break through your website's security protocols, then data thieves undoubtedly will be able to as well. Identifying these vulnerabilities early on can help you make the changes needed to secure your site from the latest threats. Sucuri Sucuri is a free website scanner that can detect viruses and malware. It can also identify and website errors or broken code, as well as out-of-date software. It can even alert you if your website has been blacklisted. This tool is compatible with a variety of popular website-building platforms, including WordPress, Drupal, Magento, Joomla and more. Qualys SSL Server Test This tool analyzes the configuration of your SSL web server and is designed specifically for secure (https) websites. You'll get in-depth analysis of your URL to help you identify vulnerabilities. This includes your site's expiration day, SSL/TLS version, overall security rating, protocol details and more. This is another free service, and neither your personal information nor your test results are used for any purpose other than to provide you with the analysis you have requested. Wapiti Wapiti scans for a variety of vulnerabilities in web applications. Similar to penetration testing, this application injects data to see if various scripts are vulnerable to attacks. It is capable of detecting file disclosure and inclusion vulnerabilities, site configuration issues, and a variety of injection complications. It is important to note, though, that while free, this is a command-line application. This may be a bit difficult for beginners to get the hang of and is better suited to advanced users. Wireshark Wireshark is another penetration testing application. It specializes in analyzing network protocols, getting into the tiniest details of your packet information and decryption. It's compatible with all the major operating systems, including Windows, OS X, Linux, Solaris and more. The application is free to download and can be viewed through a user interface or in TTY-mode TShark utility. Skipfish Skipfish crawls through your website, one page at a time, to detect any vulnerabilities in the code. This open source web application is free to download and use, and it is optimized for HTTP handling. It is capable of handling up to 2,000 requests per second without putting a strain on your CPU. Compatible with Windows, MacOS X, Linux and FreeBSD operating systems, this security application can detect even subtle flaws, like blind injection vectors.
Detectify Detectify is a suite of more than 100 automated security tests for your website. In total, it checks for over 700 distinct vulnerabilities. The team of ethical hackers behind the platform continually update the scans to detect the latest threats as they emerge, keeping your website secure in real time. You can test Detectify for free for 21 days, after which you'll have to pay a recurring membership fee for the ongoing security service. Siteguarding Siteguarding is a free online tool for detecting viruses, malware, phishing, injected spam, defacement and more. It can also help you clean and remove these threats from your website to ensure your security. The company also provides web hosting services, for a complete web security management package. These are just a few of the many website security options you have available to you, so there is no excuse for not having your website provide the latest security protections for your customers. Try out a few scans today to identify areas where your company website might be vulnerable so that you can regain control.Ken Lynch is an enterprise software startup veteran, who has always been fascinated by what drives workers to work and how to make work more engaging. Ken founded Reciprocity to pursue just that. He has propelled Reciprocity's success with this mission-based goal of engaging employees with the governance, risk, and compliance goals of their company in order to create more socially minded corporate citizens. Ken earned his BS in Computer Science and Electrical Engineering from MIT.
0 notes
Text
How Oracle GoldenGate works
Oracle GoldenGate operates by capturing changes directly from the transaction logs of source databases. It supports both homogeneous and heterogeneous environments, enabling real-time data replication across different types of databases, such as Oracle, MySQL, SQL Server, PostgreSQL, and more. Oracle GoldenGate Data Flow Explanation Target DatabaseThis is the destination where the replicated…
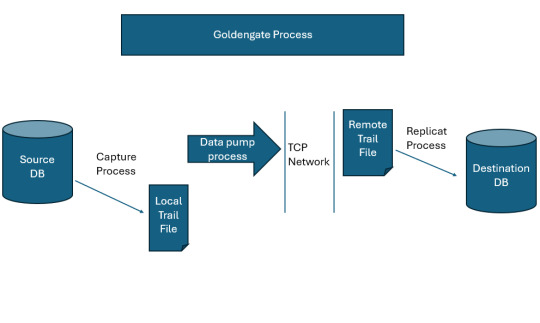
View On WordPress
0 notes
Text
Which Computer Course Is Most in Demand in India Right Now?

India's technology landscape is one of the most dynamic in the world, characterized by rapid digital transformation, a thriving startup ecosystem, and a robust IT services sector. This constant evolution means that the demand for specific computer skills is always shifting. If you're considering enhancing your skills or embarking on a new career path, understanding which computer courses are currently most in demand is crucial.
While "demand" can fluctuate slightly based on region and industry, several core technological areas consistently show high growth and require specialized training. Based on current industry trends, here's a look at the computer courses generating significant buzz and opening up numerous opportunities across India in 2025.
Top Computer Courses Highly Sought After in India
1. Artificial Intelligence (AI) & Machine Learning (ML)
AI and ML are no longer just buzzwords; they are at the core of innovation in almost every sector, from healthcare and finance to e-commerce and manufacturing. In India, the adoption of AI technologies is accelerating, leading to a strong demand for professionals who can develop, implement, and manage AI systems.
Why in Demand: Automation, data analysis, predictive modeling, smart solutions, and the push for digital transformation in various industries.
Key Skills Learned: Python programming, machine learning algorithms, deep learning, natural language processing (NLP), computer vision.
2. Data Science & Big Data Analytics
With the explosion of data generated daily, the ability to collect, process, analyze, and interpret large datasets is invaluable. Data scientists and analysts help businesses make informed decisions, identify trends, and predict future outcomes.
Why in Demand: Every organization, regardless of size, is grappling with data. The need for professionals who can extract meaningful insights is paramount.
Key Skills Learned: Python/R programming, SQL, statistical modeling, data visualization, Big Data technologies (Hadoop, Spark).
3. Full-Stack Web Development
As businesses increasingly establish and expand their online presence, the demand for versatile web developers who can handle both the front-end (what users see) and back-end (server-side logic) of applications remains consistently high.
Why in Demand: Digitalization of businesses, e-commerce boom, proliferation of web-based applications, and the need for seamless user experiences.
Key Skills Learned: HTML, CSS, JavaScript (with frameworks like React, Angular, Vue.js), Node.js, Python (Django/Flask), Ruby on Rails, databases (SQL, MongoDB).
4. Cybersecurity
With the increasing number of cyber threats and data breaches, organizations across India are investing heavily in cybersecurity measures. Professionals who can protect sensitive data, prevent attacks, and ensure network security are critically needed.
Why in Demand: Growing digital transactions, increased online data storage, and the imperative for robust data protection laws.
Key Skills Learned: Network security, ethical hacking, cryptography, risk management, incident response, security tools.
5. Cloud Computing (AWS, Azure, Google Cloud)
Cloud adoption is no longer a luxury but a necessity for many Indian businesses seeking scalability, flexibility, and cost efficiency. Expertise in major cloud platforms is a highly sought-after skill.
Why in Demand: Cloud migration, managing cloud infrastructure, deploying applications in the cloud, cost optimization.
Key Skills Learned: Specific cloud platforms (AWS, Azure, GCP), cloud architecture, virtualization, containerization (Docker, Kubernetes).
6. DevOps
DevOps practices streamline software development and IT operations, leading to faster, more reliable software delivery. Professionals with DevOps skills are crucial for modern software companies aiming for efficiency and continuous integration/delivery.
Why in Demand: Need for faster product cycles, automation of development pipelines, and improved collaboration between teams.
Key Skills Learned: CI/CD tools (Jenkins, GitLab CI), scripting (Python, Bash), configuration management (Ansible), containerization (Docker, Kubernetes), cloud platforms.
Factors Driving Demand in India
Several factors contribute to these trends:
Digital India Initiative: Government push for digitalization across all sectors.
Startup Boom: A vibrant startup ecosystem constantly innovating and requiring new tech talent.
Global Capability Centers (GCCs): International companies setting up R&D and tech operations in India.
Remote Work Flexibility: Opening up opportunities across different regions and cities.
How to Choose the Right Course for You
While these courses are in high demand, the "best" one for you depends on your interests, aptitude, and career goals.
Assess Your Interest: Are you passionate about data, building applications, or securing systems?
Research Career Paths: Understand the daily tasks and long-term prospects associated with each field.
Look for Practical Training: Opt for computer courses that emphasize hands-on projects and real-world scenarios. Many computer training institute in Ahmedabad and other cities offer programs with strong practical components.
Consider Faculty and Curriculum: Ensure the instructors have industry experience and the curriculum is up-to-date with the latest trends.
Check for Placement Support: If securing a job quickly is a priority, inquire about career services or placement assistance.
Investing in an in-demand computer course is a strategic move for your future career. By aligning your learning with current industry needs, you significantly enhance your employability and open doors to exciting opportunities in India's booming tech sector.
Contact us
Location: Bopal & Iskcon-Ambli in Ahmedabad, Gujarat
Call now on +91 9825618292
Visit Our Website: http://tccicomputercoaching.com/
0 notes
Text
Multiple Transaction Log Files Per Database?
Learn when to use multiple transaction log files per SQL Server database and the pros and cons.
Are you wondering whether it’s a good idea to have more than one transaction log file per database in SQL Server? In this article, we’ll explore the pros and cons of using multiple log files and explain when it can make sense. We’ll also show you how to remove extra log files if needed. By the end, you’ll have a clear understanding of SQL Server transaction log best practices. What are…

View On WordPress
#database performance#multiple log files#shrink transaction log#sql server transaction log#transaction log best practices
0 notes
Text
DBMS Tutorial Explained: Concepts, Types, and Applications

In today’s digital world, data is everywhere — from social media posts and financial records to healthcare systems and e-commerce websites. But have you ever wondered how all that data is stored, organized, and managed? That’s where DBMS — or Database Management System — comes into play.
Whether you’re a student, software developer, aspiring data analyst, or just someone curious about how information is handled behind the scenes, this DBMS tutorial is your one-stop guide. We’ll explore the fundamental concepts, various types of DBMS, and real-world applications to help you understand how modern databases function.
What is a DBMS?
A Database Management System (DBMS) is software that enables users to store, retrieve, manipulate, and manage data efficiently. Think of it as an interface between the user and the database. Rather than interacting directly with raw data, users and applications communicate with the database through the DBMS.
For example, when you check your bank account balance through an app, it’s the DBMS that processes your request, fetches the relevant data, and sends it back to your screen — all in milliseconds.
Why Learn DBMS?
Understanding DBMS is crucial because:
It’s foundational to software development: Every application that deals with data — from mobile apps to enterprise systems — relies on some form of database.
It improves data accuracy and security: DBMS helps in organizing data logically while controlling access and maintaining integrity.
It’s highly relevant for careers in tech: Knowledge of DBMS is essential for roles in backend development, data analysis, database administration, and more.
Core Concepts of DBMS
Let’s break down some of the fundamental concepts that every beginner should understand when starting with DBMS.
1. Database
A database is an organized collection of related data. Instead of storing information in random files, a database stores data in structured formats like tables, making retrieval efficient and logical.
2. Data Models
Data models define how data is logically structured. The most common models include:
Hierarchical Model
Network Model
Relational Model
Object-Oriented Model
Among these, the Relational Model (used in systems like MySQL, PostgreSQL, and Oracle) is the most popular today.
3. Schemas and Tables
A schema defines the structure of a database — like a blueprint. It includes definitions of tables, columns, data types, and relationships between tables.
4. SQL (Structured Query Language)
SQL is the standard language used to communicate with relational DBMS. It allows users to perform operations like:
SELECT: Retrieve data
INSERT: Add new data
UPDATE: Modify existing data
DELETE: Remove data
5. Normalization
Normalization is the process of organizing data to reduce redundancy and improve integrity. It involves dividing a database into two or more related tables and defining relationships between them.
6. Transactions
A transaction is a sequence of operations performed as a single logical unit. Transactions in DBMS follow ACID properties — Atomicity, Consistency, Isolation, and Durability — ensuring reliable data processing even during failures.
Types of DBMS
DBMS can be categorized into several types based on how data is stored and accessed:
1. Hierarchical DBMS
Organizes data in a tree-like structure.
Each parent can have multiple children, but each child has only one parent.
Example: IBM’s IMS.
2. Network DBMS
Data is represented as records connected through links.
More flexible than hierarchical model; a child can have multiple parents.
Example: Integrated Data Store (IDS).
3. Relational DBMS (RDBMS)
Data is stored in tables (relations) with rows and columns.
Uses SQL for data manipulation.
Most widely used type today.
Examples: MySQL, PostgreSQL, Oracle, SQL Server.
4. Object-Oriented DBMS (OODBMS)
Data is stored in the form of objects, similar to object-oriented programming.
Supports complex data types and relationships.
Example: db4o, ObjectDB.
5. NoSQL DBMS
Designed for handling unstructured or semi-structured data.
Ideal for big data applications.
Types include document, key-value, column-family, and graph databases.
Examples: MongoDB, Cassandra, Redis, Neo4j.
Applications of DBMS
DBMS is used across nearly every industry. Here are some common applications:
1. Banking and Finance
Customer information, transaction records, and loan histories are stored and accessed through DBMS.
Ensures accuracy and fast processing.
2. Healthcare
Manages patient records, billing, prescriptions, and lab reports.
Enhances data privacy and improves coordination among departments.
3. E-commerce
Handles product catalogs, user accounts, order histories, and payment information.
Ensures real-time data updates and personalization.
4. Education
Maintains student information, attendance, grades, and scheduling.
Helps in online learning platforms and academic administration.
5. Telecommunications
Manages user profiles, billing systems, and call records.
Supports large-scale data processing and service reliability.
Final Thoughts
In this DBMS tutorial, we’ve broken down what a Database Management System is, why it’s important, and how it works. Understanding DBMS concepts like relational models, SQL, and normalization gives you the foundation to build and manage efficient, scalable databases.
As data continues to grow in volume and importance, the demand for professionals who understand database systems is also rising. Whether you're learning DBMS for academic purposes, career development, or project needs, mastering these fundamentals is the first step toward becoming data-savvy in today’s digital world.
Stay tuned for more tutorials, including hands-on SQL queries, advanced DBMS topics, and database design best practices!
0 notes
Text

Key WooCommerce Security Tips for 2025
1. Use Strong Passwords and Enable Two-Factor Authentication (2FA)
A weak password is often the first point of vulnerability for any website. To protect your WooCommerce store, ensure that you and your team members use strong, unique passwords for all accounts related to your store. Additionally, enabling two-factor authentication (2FA) adds an extra layer of protection, requiring a second verification step when logging in.
While 2FA may seem like an added hassle, it is a powerful tool that prevents unauthorized access, even if someone obtains your password. Implementing 2FA will drastically reduce the likelihood of a security breach.
2. Keep WordPress, WooCommerce, and Plugins Updated
Regular updates to WordPress, the WooCommerce plugin, and any other installed plugins are critical for maintaining security. These updates often include security patches to fix newly discovered vulnerabilities. By updating your software regularly, you ensure that your store is protected against the latest threats.
If you don't have the time or expertise to handle updates yourself, consider seeking WooCommerce Development Services to keep your store secure and functioning smoothly. A professional team can handle the updates while ensuring no disruption to your store’s operations.
3. Implement SSL Encryption for Secure Transactions
SSL (Secure Socket Layer) certificates encrypt sensitive data that flows between the server and the user’s browser. This encryption ensures that your customers’ personal and financial details are protected. In 2025, having an SSL certificate isn’t just a security measure—it’s also essential for maintaining customer trust and improving your site’s SEO ranking.
If you're unsure how to integrate SSL encryption, a WooCommerce Developer can help set it up to ensure secure transactions and smooth customer experiences.
4. Install a Web Application Firewall (WAF)
A Web Application Firewall (WAF) acts as a barrier between your WooCommerce store and malicious traffic. It filters out harmful requests, preventing hackers from exploiting vulnerabilities in your site’s code. Implementing a WAF can block attacks such as SQL injection, cross-site scripting (XSS), and brute-force login attempts, which are common methods used by cybercriminals.
To configure the best WAF for your store, you can work with professionals who specialize in website security.
5. Backup Your Store Regularly
Data loss is one of the most detrimental effects of a cyberattack. If your store is compromised or experiences a system failure, having a recent backup ensures that you can restore your website with minimal downtime and data loss. Regular backups also give you peace of mind knowing that even in the worst-case scenario, you can recover your site quickly.
To streamline this process, WordPress Support Services often include backup solutions, providing continuous backups to keep your store secure and your data safe.
6. Limit Login Attempts
Brute force attacks involve hackers attempting to guess your login credentials by trying different combinations repeatedly. One effective way to prevent these attacks is by limiting the number of failed login attempts before temporarily locking out the user. This drastically reduces the chances of a hacker successfully gaining access to your store.
This is a simple yet effective security measure, and integrating it into your site can be done by a WooCommerce Developer who can ensure the right settings are in place to block these types of attacks.
Ongoing Maintenance and Monitoring for WooCommerce Security
Maintaining a secure WooCommerce store is an ongoing process. Regular security checks, audits, and proactive monitoring are essential to keep your site protected. Without routine maintenance, new vulnerabilities can arise, and hackers will always find new ways to exploit them.
By leveraging WordPress Website Maintenance Services, you can ensure that your store is continually monitored and updated, helping to safeguard it from emerging threats.
Conclusion
In 2025, the security of your WooCommerce store should be a top priority. By adopting strong passwords, implementing SSL certificates, enabling two-factor authentication, and keeping your software up to date, you can significantly reduce the risk of a breach.
For more advanced security measures and ongoing support, working with WooCommerce Development Services and WordPress Support Services ensures that your site remains secure, protected from the latest threats, and optimized for performance.
Let’s work together to make sure your WooCommerce store is as secure as possible in 2025 and beyond.
0 notes
Text
🚀 Unlock the Power of SQL TRUNCATE 🚀
Looking to quickly remove all records from a table without affecting its structure? 🤔
SQL TRUNCATE is the go-to command! It’s faster and more efficient than DELETE because it:
✅ Removes all data from a table in a snap ✅ Doesn’t log individual row deletions, improving performance ✅ Resets auto-increment counters (in some databases) ✅ Doesn't fire triggers (like DELETE does)
⚠️ Warning: You can’t roll it back once executed (unless inside a transaction).
Syntax:
TRUNCATE TABLE student;
Perfect for situations where you need a fresh start! 🧹
Want to dive deeper into SQL TRUNCATE and see how it can optimize your workflow? Check out the full post below! 🔗👇
0 notes
Text
Cybersecurity Companies in India: Safeguarding the Nation’s Digital Future

Why Cybersecurity Matters Now More Than Ever
Cybersecurity threats are no longer confined to multinational corporations or tech-heavy sectors. Today, even small and mid-sized businesses in India are being targeted by ransomware, phishing schemes, malware, and social engineering attacks. According to recent studies, India experiences thousands of attempted cyber breaches every day—making it one of the top five countries facing cyber threats globally.
What Do Cybersecurity Companies in India Offer?
India’s cybersecurity service providers offer a comprehensive suite of solutions tailored to different industries, business sizes, and security needs. Their services commonly include:
1. Network Security
Secures internal infrastructure from unauthorized access, intrusion attempts, and malware infiltration. Firewalls, intrusion detection/prevention systems, and network monitoring tools are commonly used.
2. Cloud Security
With cloud adoption on the rise, protecting cloud environments has become essential. Cybersecurity firms offer encryption, identity management, and data loss prevention (DLP) solutions to ensure safe cloud operations.
3. Endpoint Protection
Cyber attackers often target endpoints like employee laptops, mobile phones, and servers. Cybersecurity companies deploy antivirus, anti-malware, and device management solutions to keep these entry points secure.
4. Threat Intelligence and Monitoring
Through AI, analytics, and real-time monitoring, providers identify and neutralize threats before they cause damage. Continuous threat assessment helps prevent data breaches and system outages.
5. Application Security
Web and mobile applications are frequent targets for attacks like SQL injection, cross-site scripting, and zero-day exploits. Cybersecurity firms conduct security testing and implement robust application firewalls.
6. Penetration Testing and Vulnerability Assessments
These simulate cyberattacks to uncover weak points in a company’s system. Regular audits help businesses stay proactive rather than reactive.
7. Security Awareness Training
People are often the weakest link in security. Cybersecurity companies provide training modules to educate employees on safe online practices, phishing prevention, and password hygiene.
8. Regulatory Compliance
As data protection regulations grow stricter—both in India and globally—businesses need help meeting compliance standards like GDPR, ISO 27001, and India's IT Act. Cybersecurity companies help implement and maintain compliant systems.
Sectors Relying Heavily on Cybersecurity Companies in India
1. Finance & Banking: The BFSI sector is a prime target due to the volume of transactions and sensitive financial data. Cybersecurity companies help in deploying advanced fraud detection and secure payment systems.
2. Healthcare: From patient records to medical devices, hospitals and clinics now require HIPAA-compliant digital protection.
3. E-commerce & Retail: With high volumes of customer data and payment processing, online retailers need 24/7 protection against fraud and data theft.
4. Government & Defense: National security, smart city projects, and citizen data management make the public sector a key client for cybersecurity solutions.
5. IT & SaaS Companies: These businesses often act as custodians of client data, and maintaining trust means maintaining security at every layer.
The Rise of Local Expertise
One of the standout trends in India’s cybersecurity landscape is the growth of homegrown expertise. Indian companies are now building cutting-edge technologies for encryption, blockchain security, AI-driven threat detection, and cloud-native protection. With an understanding of local regulations, languages, and business practices, they are better equipped to serve the Indian market than many global players.
The rise of startup hubs, government incentives, and increasing demand from Tier 2 and Tier 3 cities has also created an ecosystem that supports the growth of cybersecurity talent and innovation.
Challenges Faced by Cybersecurity Companies in India
While the sector is growing, challenges remain:
Shortage of skilled professionals: There’s a demand-supply gap in cybersecurity experts, which often leads to increased service costs.
Rapidly evolving threats: Attackers use sophisticated and ever-changing tactics, requiring constant R&D investment.
SME Awareness: Small businesses often underestimate the need for cybersecurity, exposing them to preventable risks.
Legacy systems: Many organizations still run outdated systems that are difficult to secure.
Despite these hurdles, Indian cybersecurity providers continue to adapt and innovate to stay ahead of attackers.
Future Outlook: What Lies Ahead?
The future of cybersecurity in India looks promising. With the Digital India initiative, the rise of 5G, and growing adoption of AI and IoT, the need for cybersecurity will only intensify. Companies will increasingly turn to advanced technologies like zero-trust architectures, machine learning for threat prediction, and blockchain for data integrity.
Government efforts like the National Cyber Security Policy and incentives for cybersecurity startups further indicate a national-level push toward a secure digital future.
Conclusion
Cybersecurity is no longer a luxury—it’s a necessity for every business in today’s digital age. As threats evolve, so must our defenses. Fortunately, a strong ecosystem of cybersecurity companies in India is rising to meet the challenge.
Whether you run a small startup or a large enterprise, now is the time to invest in intelligent, scalable, and responsive cybersecurity solutions. The cost of ignoring it could be far greater than the investment required to stay protected.
Call to Action
Protect your business before it’s too late. If you're looking for a reliable, scalable, and industry-compliant cybersecurity partner, explore how leading cybersecurity companies in India can secure your digital journey. Start with a security assessment today—because prevention is always better than breach.
0 notes
Text
Reasons Your Office Needs Web Application Firewall (WAF) Solutions

To Defend Against Forgery Attacks
Web application firewalls help defend your website against cross-site request forgery (CSRF) attacks. At the individual level, these attacks may mislead you into using your credentials to complete an unauthorized action, such as transferring money or changing passwords. At the administrative level, such threats can infiltrate your server and take complete control over your website.
To Block Unauthorized Data Access
A reliable WAF solution will detect malicious SQL injections, an attack threat actors use to access databases and steal or destroy information. Often, the attacker will spoof an identity, make themselves an administrator, modify data, or retrieve information using a well-thought-out SQL command execution. Sometimes, the perpetrators may distract database administrators with a DDoS attack so that you would not notice they are already accessing sensitive information.
To Prevent Website Outages
Web application firewall solutions implement protective measures against distributed denial-of-service (DDoS) attacks. These attacks aim to overwhelm the target website by flooding it with internet traffic and rendering it inaccessible (as would have happened with the Philippine Congress website in 2024 if they did not have a reliable IT team on board). The right WAF will mitigate such threats by acting as a reverse proxy and protecting your server from harmful traffic. Custom rules to filter said traffic also increase the chance of preventing DDoS attacks from succeeding.
To Stop Online Impersonators
A solid WAF security will protect your web applications from malicious actors who pose as someone else. When attackers attempt to execute impersonations through cross-site request forgery and SQL-injecting attacks, a reliable web application firewall detects such methods, filtering out unusual, dubious elements before they damage or shut down your website.
To Avoid Transaction Interruptions
Many government websites in the Philippines are used for essential transactions. Your constituents complete activities such as checking their social security status, booking a passport application appointment, securing an NBI certificate, and downloading tax-related documents via government web applications. Hackers and attackers would want to hamper these processes, inconveniencing both your agency and the people you serve.
To Protect Your Reputation
Website downtimes will make your users complain, especially if they are in the middle of completing an online transaction. As these inconveniences pile up, they may affect your reputation and erode public trust. Web application firewalls can help prevent this downgrade by consistently mitigating website threats.
Do you want to learn more? Read about What is the difference between a firewall and a WAF .
0 notes
Text
Bhojon Nulled Script 3.0

Bhojon Nulled Script – The Ultimate Restaurant Management Solution If you're searching for a seamless, high-performance restaurant management system without spending a fortune, look no further than the Bhojon Nulled Script. Designed to simplify and elevate your restaurant operations, Bhojon delivers the perfect combination of user-friendly features, sleek UI, and top-tier functionality—all available for free through our platform. Why Choose Bhojon Nulled Script? The Bhojon Nulled Script is a complete digital restaurant management package that automates your day-to-day activities while offering a professional web presence. Whether you’re managing a local diner or a chain of restaurants, Bhojon gives you the tools you need to control operations efficiently, streamline orders, manage staff, and track sales effortlessly—all under one intuitive interface. Detailed Product Description Developed with the modern restaurateur in mind, Bhojon is packed with a range of robust features to ensure full control over your restaurant’s ecosystem. It includes everything from point-of-sale (POS) capabilities and inventory management to food ordering systems and multi-branch handling. And now, with the Bhojon Nulled Script, you can enjoy these premium features without paying premium prices. The script includes both frontend and backend modules, ensuring customers and staff can interact with the system efficiently. The responsive design ensures flawless performance on desktops, tablets, and smartphones, keeping your business connected at all times. Technical Specifications Language: PHP (Laravel Framework) Database: MySQL Compatibility: Cross-browser and mobile-responsive Modules: POS, Online Order, Inventory, Reporting, Admin Dashboard Multi-branch Support: Yes Features and Benefits POS System: Easy-to-use point-of-sale functionality for quick and accurate transactions. Multi-language Support: Serve customers in their preferred language with built-in localization options. Delivery & Dine-in Modules: Manage takeaway, delivery, and dine-in orders effortlessly. Comprehensive Reporting: Gain valuable insights into sales, customer behavior, and staff performance. Inventory Management: Keep track of stock levels and avoid shortages with smart inventory tools. Staff Role Management: Define roles and responsibilities clearly within the system. Use Cases The Bhojon Nulled Script is ideal for: Independent Restaurants Food Chains & Franchises Cafés & Coffee Shops Cloud Kitchens Food Trucks How to Install and Use Bhojon Nulled Script Download the Bhojon from our secure website. Unzip the package and upload the contents to your web server. Create a MySQL database and import the provided SQL file. Update the database credentials in the .env file. Run the installation script by visiting your domain in a browser. Log in to your admin dashboard and configure your restaurant settings. In just a few steps, you’ll have a fully operational restaurant management system at your fingertips. FAQs Is the Bhojon Nulled Script safe to use? Yes. Our version of the Bhojon Nulled Script is clean, tested, and regularly updated to ensure stability and security. Can I use Bhojon for multiple restaurants? Absolutely. Bhojon supports multi-branch functionality, allowing you to manage multiple restaurant locations from a single dashboard. Is technical support included? As this is a nulled script, official support is not included. However, we provide comprehensive documentation and community forums for assistance. Do I need coding skills to use it? No. Bhojon is designed for ease of use, with an intuitive interface and detailed setup instructions that require no programming knowledge. Download Bhojon Nulled Script Now Don't let budget constraints limit your restaurant's potential. Download the Bhojon today and experience the power of premium restaurant management tools—completely free of cost. Explore more powerful tools like the All in One SEO Pack Pro to further boost your website’s performance and visibility.
For a full-featured WordPress theme designed for multipurpose use, check out kallyas NULLED—a flexible, visually stunning theme perfect for business websites.
0 notes