#Secure Development Lifecycle (SDLC) Review
Explore tagged Tumblr posts
Text
Secure Software Design
The process of creating software applications in a secure way is referred to as secure software design. In this guide, protection policies are incorporated at every stage of development in respect of confidentiality, integrity and availability. Among the practices carried out, provision of threat modeling, maintenance of secure coding standards, and provision of strong authentication methods are key. Data is protected by encryption whereas addressing potential threats is accomplished through the practice of code review and vulnerability scans. Using OWASP standards for instance helps an application developer to avoid some risks like SQL injection and cross site scripting attacks. In preventing such attacks, secure design encourages making the attack surface as small as possible and upholding the least privilege policy. By designing with security in mind from the beginning, there are no loose ends where user data is concerned, trust between the company and users is preserved, and the law is followed, thus creating a safe online space.

#Secure Software Design#Secure Development Lifecycle (SDLC) Review#Security Architecture Review#Secure System Design
0 notes
Text
Why Leading Businesses Choose EDSPL for Reliable, Scalable, and Secure Software Services

In the rapidly evolving digital landscape, software has become more than just a tool—it’s the backbone of operational excellence, customer satisfaction, and business innovation. Enterprises today don’t just need any software solution; they need reliable, scalable, and secure services that can fuel their long-term growth.
That’s where EDSPL (Enrich Data Solutions Pvt. Ltd.) stands apart.
With years of expertise, a seasoned team, and a customer-centric mindset, EDSPL has become a preferred technology partner for leading businesses across industries. But what exactly makes enterprises trust EDSPL with their most critical software projects?
Let’s unpack the reasons.
1. Reliability That Builds Trust
When software systems power your business operations, reliability isn’t a luxury—it’s a necessity.
✅ Proven Track Record
EDSPL has successfully delivered robust software systems to clients ranging from startups to large enterprises. The company’s ability to consistently meet deadlines, deliver bug-free products, and support mission-critical operations has made it a dependable technology partner.
✅ Strong Project Governance
Through transparent communication, dedicated project managers, and agile methodologies, EDSPL ensures that every stakeholder remains aligned. Clients always know where their project stands, what’s next, and how potential challenges are being tackled—no surprises, no guesswork.
✅ Zero Downtime Commitment
With intelligent architecture design and proactive monitoring, EDSPL ensures high availability and minimal disruptions, even under high traffic or peak loads.
2. Scalability That Matches Business Growth
Today’s software must not only solve today’s problems but be ready for tomorrow’s challenges.
✅ Cloud-Native Architecture
EDSPL leverages modern development frameworks and scalable cloud platforms (AWS, Azure, GCP) to build systems that can scale seamlessly as the business grows. Whether it’s an ecommerce platform handling 10x traffic or an ERP system integrating with new modules, EDSPL systems grow as you grow.
✅ Modular Development Approach
Instead of bulky monoliths, EDSPL uses a modular microservices-based architecture that allows features and components to be independently scaled, upgraded, or replaced—future-proofing your software investment.
✅ Flexible Engagement Models
Whether you need a long-term development partner or short-term scaling support, EDSPL offers dedicated teams, extended teams, and hybrid engagement models tailored to evolving business needs.
3. Security That Safeguards Business Integrity
With cyber threats becoming more complex, security must be embedded at every stage of software development—not added as an afterthought.
✅ Secure SDLC
EDSPL integrates security into every phase of the development lifecycle—from requirements gathering to deployment. Secure coding practices, static code analysis, and frequent vulnerability assessments ensure that products are secure by design.
✅ Compliance-Ready Solutions
For industries like finance, healthcare, or logistics, regulatory compliance is mandatory. EDSPL delivers software that is built to meet ISO, GDPR, HIPAA, PCI-DSS, and other global standards.
✅ Proactive Testing & Audits
Regular penetration testing, code reviews, and security audits form a part of the company’s DNA. Clients receive detailed risk reports, threat mitigation plans, and post-deployment support to keep systems protected and up-to-date.
4. End-to-End Service Portfolio
EDSPL doesn’t just develop code—it delivers business outcomes.
Custom Software Development
From enterprise-grade CRMs to mobile apps and analytics dashboards, EDSPL builds tailored software solutions designed around the unique needs of the client.
Software Testing & Quality Assurance
Its dedicated QA team ensures flawless performance through:
Manual and automated testing
Functional & non-functional testing
Load, performance & security testing
This results in bug-free, user-friendly, and stable software.
Maintenance & Support
Post-deployment, EDSPL offers robust maintenance plans, timely upgrades, and 24/7 technical support, ensuring long-term system health and client satisfaction.
5. Client-Centric Culture That Drives Results
What truly sets EDSPL apart is not just technology—but its human approach.
✅ Deep Collaboration
From day one, clients are not just “recipients”—they are partners. EDSPL involves stakeholders in decision-making, roadmap discussions, and sprint reviews, ensuring the final product truly reflects business goals.
✅ Business-First Mindset
Before writing a single line of code, EDSPL dives deep into understanding your business processes, user personas, and future vision. Every solution is designed with a strong business logic behind it—not just technical excellence.
✅ Client Retention & Referrals
With a high client retention rate and numerous referral-based projects, the company’s reputation speaks for itself. Many clients have stayed with EDSPL for over 5+ years, expanding their collaboration year after year.
6. Tech Expertise That Powers Innovation
EDSPL is not just a service provider—it’s an innovation partner.
Latest Tools & Technologies
The team is proficient in:
Frontend: React, Angular, Vue
Backend: Java, Python, Node.js, .NET
DevOps: Docker, Jenkins, Kubernetes
Cloud: AWS, Azure, GCP
Testing: Selenium, JMeter, Postman
This rich tech stack allows EDSPL to deliver modern, fast, and scalable software tailored to the client's tech landscape.
AI, Automation & Emerging Tech
For clients looking to adopt AI-driven features, process automation, or data analytics, EDSPL provides consultation and builds smart, intuitive systems that go beyond the basics.
7. Real-World Success Stories
Case Study: Enterprise ERP for a Financial Institution
EDSPL built and deployed a custom ERP system that integrated accounting, HR, and CRM modules with real-time reporting and bank-grade security. The client reported a 40% increase in operational efficiency within 6 months.
Case Study: Scalable Logistics Platform
A logistics startup partnered with EDSPL to build a highly scalable delivery tracking system. Within a year, the platform handled over 100,000 deliveries per day with zero downtime.
Final Thoughts
In a world flooded with software vendors, EDSPL has risen as a true strategic partner—one that understands technology, respects timelines, prioritizes security, and above all, cares deeply about business success.
When leading businesses look for a software services provider, they’re not just buying code. They’re seeking a partner who will grow with them, protect their digital assets, and deliver consistent value.
That’s exactly what EDSPL brings to the table—reliability, scalability, and security, wrapped in trust.
Please visit our website to know more about this blog https://edspl.net/blog/why-leading-businesses-choose-edspl-for-reliable-scalable-and-secure-software-services/
0 notes
Text
Enhancing Security in Cloud-Native Applications: Key Strategies

In the evolving landscape of cloud-native applications, security is paramount. This article delves into essential practices that fortify security and resilience in cloud environments.
1.Robust identity and access management (IAM)
Implement role-based access control.
Adhere to the principle of least privilege.
Employ multi-factor authentication.
2. Securing application secrets
Securely store API keys, passwords, and certificates using secret management tools.
Rotate secrets routinely and automate this process.
3. Utilization of secure containers
Regularly update container images to mitigate vulnerabilities.
Select trusted base images and conduct vulnerability scans.
Operate containers with the minimal required privileges.
4. Network security implementation
Deploy firewalls and network segmentation to control traffic flow.
Use secure communication protocols like TLS for data in transit.
5. Compliance and auditing
Conduct regular audits of cloud resources and configurations.
Ensure adherence to industry standards and regulations.
6. Secure software development lifecycle (SDLC)
Embed security in the development process, embracing practices like DevSecOps.
Perform regular code reviews and utilize code analysis tools.
7. Automating security
Leverage automated tools for vulnerability monitoring and response.
Automate threat responses.
8. Backup and disaster recovery
Regularly backup data and establish a disaster recovery plan.
Periodically test backup and recovery procedures.
9. Staff education and training
Provide ongoing training on security best practices.
Foster a culture of security awareness.
10. Monitoring and threat response
Implement monitoring solutions for threat detection.
Develop a response plan for various security incidents.
Additional considerations:
Zero trust architecture: Treat every microservice with skepticism, avoiding blind inter-service trust.
Input validation: Rigorously validate and sanitize all inputs, treating them as potential threats.
Internet exposure control: Limit internet access to essential components using advanced firewall settings and VPCs.
Secure file storage: Encrypt sensitive data at rest and implement role-based access.
Log data masking: Employ automated redaction tools and centralized log management.
In today’s dynamic digital landscape, implementing these security practices is crucial, but it can be challenging to navigate the complexities alone. This is where Centizen Cloud Consulting Services comes in. Our expert team specializes in crafting bespoke cloud security strategies that align with your specific business needs. From initial assessment to implementation and ongoing management, we provide end-to-end support to ensure your cloud-native applications are not only secure but also optimized for performance and scalability. Partner with Centizen to transform these best practices into a robust, secure foundation for your cloud-native journey.
0 notes
Text
SonarSource Consulting Partners in India
Enreap, a Gold Partner of SonarSource in India, offers comprehensive solutions to enhance code quality and security. They specialize in integrating SonarSource's tools, such as SonarQube, into the Software Development Lifecycle (SDLC), providing features like comprehensive code analysis, prevention of technical debt, seamless integration, and user-friendly dashboards. Enreap's expertise helps businesses streamline operations, reduce costs, and deliver secure, high-quality software. For more information, you can visit their website at
0 notes
Text
How to Choose the Right Mobile App Development Partner for Your Business
In today’s fast-paced digital economy, having a high-performing mobile app is no longer optional—it’s essential. Whether you’re launching a consumer-facing app or an internal enterprise tool, selecting the right mobile app development partner can make or break your digital strategy. The right development company not only builds your app but also becomes an extension of your team, helping you scale your business, enhance user experience, and stay competitive in your industry.
Here’s a comprehensive guide to help you make an informed decision when choosing your mobile app development partner.
1. Understand Your Business Goals and Technical Requirements
Before reaching out to any development partner, clearly define the purpose of your app. Are you looking to generate revenue, improve internal workflows, or enhance customer engagement? Determine your target audience, key features, platform preferences (iOS, Android, or both), and budget. Having a well-structured product vision will help you evaluate development partners more effectively and ensure alignment with your long-term business goals.
2. Evaluate Industry Experience and Technical Expertise
Experience matters. A development partner with a strong portfolio in your industry or similar app categories will be better equipped to understand your challenges and propose effective solutions. Ask for case studies or references, and carefully examine the features, design, and performance of apps they’ve delivered in the past. Additionally, assess their proficiency in relevant technologies such as React Native, Flutter, Swift, Kotlin, or custom backend development.
3. Prioritize UX/UI Capabilities
A mobile app’s success heavily depends on how users interact with it. A reliable development partner should have a proven track record of delivering intuitive, user-friendly, and visually appealing interfaces. During the vetting process, ask about their UX/UI design process. Do they perform user research? How do they handle user testing and iteration? The ability to design with users in mind is just as critical as writing efficient code.
4. Assess Communication and Collaboration Style
App development is a collaborative effort. The ability of your partner to communicate clearly, provide updates regularly, and adapt to feedback quickly is vital. Opt for a company that uses agile development methodologies, offers transparency through project management tools (like Jira, Trello, or Asana), and assigns a dedicated point of contact for consistent communication.
5. Consider Scalability and Post-Launch Support
Your app may start with a simple MVP (Minimum Viable Product), but it should be able to evolve as your business grows. Choose a development partner that can scale with your vision and provide ongoing maintenance, updates, and support. Inquire about their post-launch process, bug tracking, performance monitoring, and how they plan to handle future feature rollouts.
6. Review Their Development Process and Security Standards
A mature app development partner should follow a well-defined software development lifecycle (SDLC), including planning, design, development, testing, deployment, and maintenance. They should also adhere to security best practices such as data encryption, secure APIs, authentication mechanisms, and GDPR compliance—especially if your app deals with sensitive user data or operates in regulated industries.
7. Analyze Pricing and Contracts Transparently
While cost is an important factor, it should not be the sole deciding element. Extremely low quotes can often lead to poor quality, lack of scalability, or hidden costs later in the process. A trustworthy development partner provides a detailed breakdown of pricing, milestones, and deliverables upfront. Look for flexible engagement models—such as fixed-price, time and material, or dedicated team—based on the scope of your project.
8. Check Reviews, Ratings, and Client Testimonials
Research third-party reviews on platforms such as Clutch, GoodFirms, or Google Reviews. Read client testimonials, and if possible, speak to past clients directly to get feedback on their experience. A solid reputation and satisfied clients are strong indicators of a company’s reliability and professionalism.
Conclusion: Making the Right Decision for Long-Term Success
Choosing the right mobile app development partner is a strategic business decision. It requires thorough research, a clear understanding of your goals, and careful evaluation of potential partners' expertise, communication, and reliability.
At Tyfora, we specialize in creating scalable, secure, and high-performing mobile applications tailored to your unique business needs. With a strong emphasis on collaboration, innovation, and customer success, we guide our clients through every stage of their app journey—from ideation to post-launch support.
Whether you're a startup or an enterprise, selecting a partner like Tyfora can help you unlock the full potential of mobile technology and gain a competitive edge in 2025 and beyond.
0 notes
Text
Cybersecurity Considerations for Software Development Companies in New Jersey
In today’s digital landscape, cybersecurity is a critical concern for businesses, especially for a Software Development Company in New Jersey. With increasing cyber threats and stringent data protection regulations, software companies must implement robust security measures to protect sensitive information, intellectual property, and client data.
1. Compliance with Regulatory Standards
New Jersey-based software development firms must adhere to various federal and state cybersecurity regulations, including:
General Data Protection Regulation (GDPR) for businesses handling EU customer data.
Health Insurance Portability and Accountability Act (HIPAA) for companies working with healthcare data.
New Jersey Data Breach Notification Law, requiring businesses to notify customers in case of a data breach.
Cybersecurity Maturity Model Certification (CMMC) for companies handling government contracts.
2. Secure Software Development Lifecycle (SDLC)
A Software Development Company in New Jersey should integrate security at every stage of the Software Development Lifecycle (SDLC):
Threat modeling: Identifying potential vulnerabilities before development begins.
Code reviews: Conducting regular security audits and peer reviews.
Penetration testing: Simulating cyberattacks to identify weaknesses.
Secure coding practices: Using frameworks like OWASP Top 10 to mitigate risks.
3. Data Protection and Encryption
Protecting sensitive data should be a priority. Companies should implement:
End-to-end encryption for data at rest and in transit.
Multi-factor authentication (MFA) to prevent unauthorized access.
Regular data backups stored securely to prevent data loss.
4. Employee Cybersecurity Training
Human error remains one of the biggest cybersecurity risks. Regular training on:
Phishing attacks and how to identify malicious emails.
Password hygiene, including the use of password managers.
Secure remote work practices, especially for employees working from home.
5. Third-Party Vendor Security
Software companies often collaborate with third-party vendors. Ensuring vendor compliance with cybersecurity protocols is essential to prevent supply chain attacks. Conducting vendor security assessments and enforcing stringent access controls can mitigate risks.
6. Incident Response and Disaster Recovery
A well-documented and tested incident response plan is essential. It should include:
Immediate containment strategies in case of a breach.
Forensic analysis to identify the cause of the attack.
Communication protocols to inform stakeholders and regulatory bodies.
Business continuity planning to minimize downtime and loss.
7. Cloud Security Best Practices
Many software development companies rely on cloud services for data storage and computing power. Adopting cloud security best practices ensures data integrity, including:
Zero Trust Architecture requiring verification at every access point.
Role-based access control (RBAC) to limit data access.
Regular security assessments of cloud service providers.
Conclusion
Cybersecurity is a non-negotiable aspect of operating a Software Development Company in New Jersey. By implementing stringent security measures, following industry best practices, and continuously educating employees, software firms can protect their assets, build customer trust, and comply with regulatory requirements. Prioritizing cybersecurity will not only safeguard the business but also enhance its reputation in the competitive software development industry.
0 notes
Text
Automation in DevOps (DevSecOps): Integrating Security into the Pipeline
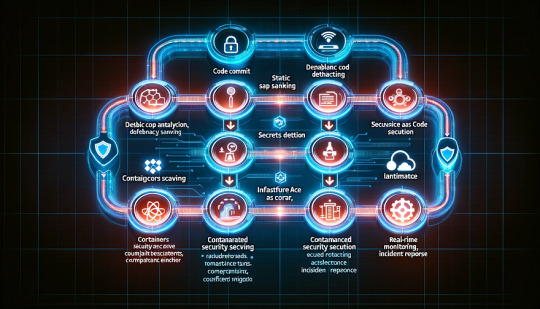
In modern DevOps practices, security can no longer be an afterthought — it needs to be embedded throughout the software development lifecycle (SDLC). This approach, known as DevSecOps, integrates security automation into DevOps workflows to ensure applications remain secure without slowing down development.
Why Security Automation?
Traditional security models relied on manual code reviews and vulnerability assessments at the end of the development cycle, often leading to bottlenecks and delayed releases. Security automation addresses these issues by: ✔️ Detecting vulnerabilities early in the CI/CD pipeline ✔️ Reducing manual intervention and human error ✔️ Ensuring continuous compliance with industry regulations ✔️ Improving incident response time
Key Areas of Security Automation in DevOps
1. Automated Code Security (Static & Dynamic Analysis)
Static Application Security Testing (SAST): Scans source code for vulnerabilities before deployment (e.g., SonarQube, Checkmarx).
Dynamic Application Security Testing (DAST): Identifies security flaws in running applications (e.g., OWASP ZAP, Burp Suite).
Software Composition Analysis (SCA): Detects vulnerabilities in third-party dependencies (e.g., Snyk, WhiteSource).
🔹 Example: Running SAST scans automatically in a Jenkins pipeline to detect insecure coding practices before merging code.
2. Secrets Management & Access Control
Automating the detection and handling of hardcoded secrets, API keys, and credentials using tools like HashiCorp Vault, AWS Secrets Manager, and CyberArk.
Implementing least privilege access via automated IAM policies to ensure only authorized users and services can access sensitive data.
🔹 Example: Using HashiCorp Vault to generate and revoke temporary credentials dynamically instead of hardcoding them.
3. Automated Compliance & Policy Enforcement
Infrastructure as Code (IaC) security scans using Checkov, OPA (Open Policy Agent), or Terraform Sentinel ensure that cloud configurations follow security best practices.
Automated audits and reporting help maintain compliance with GDPR, HIPAA, SOC 2, and ISO 27001 standards.
🔹 Example: Using Checkov to scan Terraform code for misconfigurations before provisioning cloud resources.
4. Container & Kubernetes Security
Scanning container images for vulnerabilities using Trivy, Aqua Security, or Anchore before pushing them to a registry.
Implementing Kubernetes security policies (e.g., Pod Security Policies, Kyverno, or Gatekeeper) to enforce security rules.
🔹 Example: Using Trivy in a CI/CD pipeline to scan Docker images before deployment to Kubernetes.
5. Continuous Security Monitoring & Threat Detection
Implementing SIEM (Security Information and Event Management) tools like Splunk, ELK Stack, or AWS Security Hub for real-time security event detection.
Using Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) (e.g., Snort, Suricata) to detect and respond to security threats.
AI-driven anomaly detection via Amazon GuardDuty, Microsoft Defender for Cloud, or Google Chronicle.
🔹 Example: Configuring AWS Security Hub to automatically detect and alert on misconfigurations in an AWS environment.
6. Automated Incident Response & Remediation
Using SOAR (Security Orchestration, Automation, and Response) platforms like Splunk SOAR or Palo Alto Cortex XSOAR to automate security incident triage and response.
Creating automated playbooks for threat mitigation, such as isolating compromised containers or blocking suspicious IPs.
🔹 Example: Automating AWS Lambda functions to quarantine an EC2 instance when an anomaly is detected.
Bringing It All Together: A DevSecOps Pipeline Example
1️⃣ Code Commit: Developers push code to a Git repository. 2️⃣ Static Code Analysis: SAST tools scan for vulnerabilities. 3️⃣ Dependency Scanning: SCA tools check third-party libraries. 4️⃣ Secrets Detection: Git hooks or automated scanners look for hardcoded secrets. 5️⃣ Container Security: Images are scanned before being pushed to a container registry. 6️⃣ Infrastructure as Code Scanning: Terraform or Kubernetes configurations are checked. 7️⃣ Automated Security Testing: DAST and penetration tests run in staging. 8️⃣ Compliance Checks: Policies are enforced before deployment. 9️⃣ Real-time Monitoring: Logs and security events are analyzed for threats. 🔟 Incident Response: Automated workflows handle detected threats.
Final Thoughts
Security automation in DevOps is critical for ensuring that security does not slow down development. By integrating automated security testing, policy enforcement, and monitoring, teams can build resilient, compliant, and secure applications without sacrificing speed.
WEBSITE: https://www.ficusoft.in/devops-training-in-chennai/
0 notes
Text
DevSecOps Flow: Integrating Security into Development and Operations
In today’s rapidly evolving software development environment, security can no longer be treated as an afterthought. Traditional security practices often result in bottlenecks, hindering both development and deployment timelines. DevSecOps, a modern methodology that integrates security into DevOps processes, ensures continuous security without sacrificing agility. This article examines the DevSecOps flow, its advantages, and key practices for effective implementation.
What is DevSecOps?
DevSecOps (Development, Security, and Operations) is an approach that incorporates security practices directly into the DevOps pipeline. Unlike traditional models where security is addressed late in the development lifecycle, DevSecOps ensures that security is embedded at every stage—development, testing, deployment, and monitoring.
Key Components of the DevSecOps Workflow
1. Shift-Left Security Approach
DevSecOps emphasizes the "shift-left" security methodology, integrating security measures early in the software development lifecycle (SDLC). This approach reduces vulnerabilities and minimizes the cost of addressing security issues during production.
2. Automated Security Testing
Automation is a cornerstone of DevSecOps. Tools like Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), and Software Composition Analysis (SCA) enable early detection of vulnerabilities and ensure regulatory compliance.
3. Secure Coding Practices
Developers are trained to implement secure coding standards, reducing the likelihood of security flaws in applications. Practices such as secure code reviews and threat modeling further reinforce application security.
4. Securing Continuous Integration and Continuous Deployment (CI/CD)
Security is seamlessly integrated into CI/CD pipelines, with automated tools scanning code for vulnerabilities prior to deployment. This ensures that security flaws are addressed before reaching production.
5. Infrastructure as Code (IaC) Security
For cloud-based environments, IaC ensures consistent enforcement of security best practices. Integrated security policies and compliance checks during the provisioning process help mitigate infrastructure risks.
6. Continuous Monitoring and Incident Response
Real-time monitoring tools detect and address security threats promptly. DevSecOps teams leverage Security Information and Event Management (SIEM) systems and threat intelligence tools to identify and respond to potential security incidents effectively.
Benefits of the DevSecOps Workflow
1. Accelerated and Secure Software Delivery
By incorporating security throughout the SDLC, DevSecOps ensures vulnerabilities are mitigated without compromising development and deployment speed.
2. Mitigated Security Risks
Continuous security testing enables the identification and resolution of vulnerabilities before exploitation, significantly reducing security breaches.
3. Cost-Effective Security
Resolving security issues early in the development process is considerably more cost-efficient than addressing them after deployment.
4. Improved Regulatory Compliance
Automated security checks and compliance validations ensure adherence to industry standards such as GDPR, HIPAA, and ISO 27001.
5. Enhanced Cross-Functional Collaboration
DevSecOps promotes collaboration between development, security, and operations teams. By breaking down silos, it ensures shared responsibility and accountability for security across all stakeholders.
Best Practices for Implementing DevSecOps
1. Establish a Security-First Culture
Promote a mindset where security is a top priority and seamlessly integrated into everyday workflows across teams.
2. Leverage Security Automation
Implement advanced security automation tools to efficiently handle vulnerability scanning, compliance verification, and incident response.
3. Utilize Role-Based Access Controls (RBAC)
Enforce access restrictions based on user roles to safeguard sensitive data and environments from unauthorized access.
4. Provide Regular Security Training
Equip teams with up-to-date knowledge on emerging security threats, secure coding standards, and DevSecOps methodologies.
5. Perform Continuous Security Assessments
Maintain a strong security posture through regular audits, penetration testing, and comprehensive code reviews.
Conclusion
DevSecOps represents a paradigm shift in modern software development, empowering organizations to deliver secure applications at a faster pace. By embedding security into every phase of the development lifecycle, businesses can effectively mitigate risks, enhance compliance, and cultivate a culture of security awareness. Adopting DevSecOps ensures that security acts as a driver for innovation and growth rather than a hindrance.
0 notes
Text
QA vs. Software Testing: What's the Difference and Why It Matters

In the world of software development, terms like Quality Assurance (QA) and Software Testing are often used interchangeably. However, while both contribute to software quality, they serve distinct purposes.
Think of QA as the blueprint that ensures a house is built correctly, while software testing is the process of inspecting the finished house to ensure there are no cracks, leaks, or faulty wiring. QA is proactive—preventing defects before they occur, whereas software testing is reactive—detecting and fixing bugs before deployment.
Understanding the difference between QA and software testing is crucial for organizations to build reliable, high-performing, and customer-friendly software. This blog explores their differences, roles, and why both are essential in modern software development.
What is Quality Assurance (QA)?
Quality Assurance (QA) is a systematic approach to ensuring that software meets defined quality standards throughout the development lifecycle. It focuses on process improvement, defect prevention, and maintaining industry standards to deliver a high-quality product.
Instead of identifying defects after they appear, QA ensures that the development process is optimized to reduce the likelihood of defects from the beginning.
Key Characteristics of QA:
Process-Oriented: QA defines and improves the software development processes to minimize errors.
Preventive Approach: It prevents defects before they arise rather than finding and fixing them later.
Covers the Entire Software Development Lifecycle (SDLC): QA is involved from requirement gathering to software maintenance.
Compliance with Industry Standards: QA ensures the software adheres to ISO, CMMI, Six Sigma, and other quality benchmarks.
Key QA Activities:
Defining Standards & Guidelines – Establishing coding best practices, documentation protocols, and process frameworks.
Process Audits & Reviews – Conducting regular audits to ensure software teams follow industry standards.
Automation & Optimization – Implementing CI/CD (Continuous Integration/Continuous Deployment) to streamline development.
Risk Management – Identifying potential risks and mitigating them before they become major issues.
Example of QA in Action:
A company implementing peer code reviews and automated CI/CD pipelines to ensure all new code follows quality guidelines is an example of QA. This process prevents poor-quality code from reaching the testing phase.
What is Software Testing?
Software Testing is a subset of QA that focuses on evaluating the actual software product to identify defects, errors, and performance issues. It ensures that the software behaves as expected and meets business and user requirements.
Testing is performed after the development phase to verify the correctness, functionality, security, and performance of the application.
Key Characteristics of Software Testing:
Product-Oriented: Testing ensures the final product works as expected and meets user requirements.
Defect Detection & Fixing: The main goal is to identify and fix bugs before software release.
Different Testing Methods: Includes manual and automated testing, covering functionality, usability, performance, security, and compatibility.
Part of the Software Testing Life Cycle (STLC): Testing occurs after development and follows a structured cycle of planning, execution, and bug tracking.
Types of Software Testing:
Functional Testing: Verifies that the software functions as per the requirements.
Unit Testing: Checks individual components or modules.
Integration Testing: Ensures different modules work together correctly.
System Testing: Tests the complete application to validate its behavior.
Performance Testing: Measures speed, scalability, and responsiveness.
Security Testing: Identifies vulnerabilities to prevent security breaches.
Example of Software Testing in Action:
Running automated UI tests to check if a login form accepts correct credentials and rejects incorrect ones is an example of software testing. This ensures that the application meets user expectations.
Key Differences Between QA and Software Testing
Focus: Quality Assurance (QA) is a process-oriented approach that ensures the entire software development process follows best practices and quality standards to prevent defects. In contrast, software testing is product-oriented and focuses on detecting and fixing bugs in the developed software.
Goal: The primary goal of QA is to prevent defects from occurring in the first place by refining development and testing methodologies. On the other hand, software testing aims to identify and fix defects before the software is released to users.
Scope: QA encompasses the entire Software Development Life Cycle (SDLC), ensuring that each phase—from requirement analysis to deployment—adheres to quality standards. In contrast, software testing is a subset of QA and is mainly concerned with validating the functionality, performance, security, and reliability of the software.
Approach: QA follows a proactive approach by setting up quality checkpoints, code reviews, and documentation processes to reduce the chances of defects. Software testing, however, takes a reactive approach, meaning it focuses on identifying existing issues in the software after the development phase.
Activities Involved: QA activities include process audits, documentation reviews, defining coding standards, implementing CI/CD pipelines, and process optimization. In contrast, software testing involves executing test cases, performing unit testing, integration testing, functional testing, performance testing, and security testing to ensure the software meets the required specifications.
Example of Implementation: A company implementing peer code reviews, automated build testing, and compliance audits as part of its development process is engaging in QA. On the other hand, running test cases on a login page to check if valid credentials allow access while invalid ones do not is an example of software testing.
By understanding these differences, organizations can ensure they integrate both QA and testing effectively, leading to higher software quality, fewer defects, and a better user experience.
Why Both QA and Software Testing Matter
Some organizations mistakenly focus only on testing, believing that identifying and fixing bugs is enough. However, without strong QA practices, defects will continue to arise, increasing development costs and delaying software delivery. Here’s why both QA and testing are crucial:
1. Ensures High-Quality Software
QA minimizes errors from the start, while testing ensures no critical issues reach the end-user.
Organizations following robust QA practices tend to have fewer post-release defects, leading to better product stability.
2. Reduces Cost and Time
Finding a bug during requirement analysis is 10x cheaper than fixing it after deployment.
QA ensures that software defects are avoided, reducing the need for excessive testing and bug-fixing later.
3. Enhances User Experience
A well-tested software application performs smoothly without crashes or failures.
Poor QA and testing can result in negative user feedback, harming a company’s reputation.
4. Supports Agile and DevOps Practices
In Agile development, continuous QA ensures each sprint delivers a high-quality product.
DevOps integrates QA automation and continuous testing to speed up deployments.
5. Helps Meet Industry Standards & Compliance
Industries like finance, healthcare, and cybersecurity have strict quality standards.
QA ensures compliance with GDPR, HIPAA, ISO, and PCI DSS regulations.
How to Balance QA and Testing in Your Software Development Process
Implement a Shift-Left Approach: Start QA activities early in the development cycle to identify defects sooner.
Adopt CI/CD Pipelines: Continuous integration and automated testing help streamline both QA and testing efforts.
Use Test Automation Wisely: Automate repetitive test cases but retain manual testing for exploratory and usability testing.
Invest in Quality Culture: Encourage developers to take ownership of quality and follow best practices.
Leverage AI & Machine Learning in Testing: AI-driven test automation tools can improve defect detection and speed up testing.
Conclusion
While QA and software testing are closely related, they are not the same. QA is a preventive, process-oriented approach that ensures quality is built into the development lifecycle. In contrast, software testing is a reactive, product-focused activity that finds and fixes defects before deployment.
Organizations that balance both QA and testing effectively will consistently build high-quality, defect-free software that meets user expectations. By implementing strong QA processes alongside thorough testing, companies can save costs, speed up development, and enhance customer satisfaction.
#software testing#quality assurance#automated testing#test automation#automation testing#qa testing#functional testing#performance testing#regression testing#load testing#continuous testing
0 notes
Text
Best Software Testing Services for IT Businesses

Introduction
Software testing is an essential part of the software development lifecycle (SDLC), ensuring that applications function correctly, meet user requirements, and remain free of critical defects. As IT businesses continue to innovate, software testing services play a crucial role in delivering high-quality, secure, and performance-optimized products. This blog explores the Best Software Testing Services for IT Businesses, their benefits, challenges and how to choose the right testing partner.
Key Software Testing Services
Software testing services come in various forms, each catering to specific needs and business requirements. The primary types of software testing include:
Manual Testing – Ensures software functionality by executing test cases manually without automation tools.
Automated Testing – Uses tools and scripts to perform repetitive test cases, enhancing efficiency and accuracy.
Functional Testing – Validates that the software performs according to its specified requirements.
Performance Testing – Assesses the speed, responsiveness, and stability of an application under different conditions.
Security Testing – Identifies vulnerabilities and ensures that software is protected from cyber threats.
Usability Testing – Evaluates the user experience (UX) and ensures the application is intuitive and easy to navigate.
Regression Testing – Ensures that new updates or bug fixes do not negatively impact existing functionalities.
Compatibility Testing – Checks the software's performance across various browsers, devices, and operating systems.
Load Testing – Measures the software’s ability to handle high volumes of traffic or data processing.
API Testing – Ensures that APIs function correctly, securely, and efficiently in different environments.
Benefits of Software Testing Services
Investing in high-quality software testing services offers numerous benefits to IT businesses, including:
Enhanced Software Quality – Ensures the final product is free of critical bugs and meets industry standards.
Improved Security – Helps identify vulnerabilities before hackers can exploit them.
Faster Time-to-Market – Automated testing speeds up the release process while maintaining quality.
Cost Reduction – Early detection of issues prevents costly fixes post-deployment.
Better User Experience – Ensures a smooth, intuitive, and error-free user interface.
Regulatory Compliance – Helps businesses meet industry-specific regulations and quality standards.
Challenges in Software Testing
While software testing services offer numerous benefits, IT businesses often face several challenges, such as:
Evolving Technologies – Keeping up with new frameworks, programming languages, and testing tools.
High Testing Costs – Investing in automation tools and skilled testers can be expensive.
Time Constraints – Balancing thorough testing with fast release cycles.
Integration Issues – Ensuring seamless integration with third-party applications and APIs.
Lack of Skilled Professionals – Finding experienced testers proficient in advanced testing methodologies.
Test Data Management – Handling and securing test data in compliance with privacy regulations.
Choosing the Right Software Testing Partner
Selecting the best software testing partner is critical for IT businesses aiming for quality assurance. Consider the following factors:
Industry Experience – Choose a company with expertise in your industry and domain.
Testing Methodologies – Ensure the firm follows best practices like Agile and DevOps testing.
Automation Capabilities – Look for partners with strong automation testing expertise.
Security Standards – Verify compliance with industry security protocols.
Scalability – The provider should handle projects of all sizes and complexities.
Client Reviews and Case Studies – Analyze past projects and customer feedback.
Cost-Effectiveness – Balance affordability with quality services.
Conclusion
Software Testing Services are a crucial component of IT business success, ensuring reliability, security, and performance. By understanding different testing types, benefits, and challenges, businesses can make informed decisions when selecting the right software testing partner. Investing in robust testing solutions leads to improved product quality, customer satisfactio and business growth.
0 notes
Text
How to Get ISO 13485 Certification for the IT Industry
ISO 13485 is an international standard for Quality Management Systems (QMS) in the medical device industry. While it primarily applies to medical device manufacturers, IT companies that provide software as a medical device (SaMD), healthcare IT solutions, or cloud-based medical applications also need to comply.
Who Needs ISO 13485 in the IT Industry?
Software as a Medical Device (SaMD) providers.
HealthTech and MedTech companies developing apps for patient monitoring, diagnostics, or telemedicine.
AI & Machine Learning in healthcare (AI-driven diagnostics, wearable health tracking).
IT service providers handling medical device data (cloud storage, cybersecurity for healthcare).
Steps to Get ISO 13485 Certification for IT Companies
1. Understand ISO 13485 Requirements
Quality Management System (QMS): IT companies must establish a QMS tailored to software and data security.
Regulatory Compliance: Align software development with FDA, MDR (EU), and HIPAA for medical software compliance.
Risk Management: Implement a risk-based approach to patient safety and software reliability.
2. Conduct a Gap Analysis
Compare current software development processes with ISO 13485 requirements.
Identify gaps in document control, software validation, risk assessment, and cybersecurity.
Create an action plan to implement necessary changes.
3. Develop a Quality Management System (QMS)
Software Development Life Cycle (SDLC) Compliance:
Implement design controls, verification, and validation for medical software.
Use ISO 62304 (Software Lifecycle for Medical Devices) alongside ISO 13485.
Cybersecurity & Data Integrity:
Ensure secure data handling and patient information protection.
Align with ISO 27001 for information security.
Risk Management:
Implement ISO 14971 risk management for identifying software-related risks.
Traceability & Documentation:
Maintain detailed records of software updates, bug fixes, and security patches.
Follow Good Documentation Practices (GDP).
4. Employee Training on QMS & Compliance
Train IT teams on ISO 13485, medical software validation, and regulatory requirements.
Conduct workshops on cybersecurity for healthcare IT.
5. Conduct Internal Audits
Perform internal audits to verify ISO 13485 compliance.
Identify non-conformities and implement corrective actions.
Prepare for external certification audit.
6. Choose an ISO 13485 Certification Body
Select an accredited certification body such as:
TÜV SÜD
BSI (British Standards Institution)
DNV
Intertek
SGS
Ensure they provide ISO 13485 certification for software and IT companies.
7. Undergo ISO 13485 Certification Audit
Stage 1 Audit: Review of QMS documentation, software validation processes, and risk management strategies.
Stage 2 Audit: On-site assessment of implementation, software security controls, and compliance.
Upon successful completion, your IT company receives ISO 13485 certification.
8. Maintain Compliance & Continuous Improvement
Conduct regular internal audits to monitor QMS effectiveness.
Update software security and validation processes as per new regulations.
Undergo annual surveillance audits to maintain certification.
Benefits of ISO 13485 for IT Companies
✔️ Ensures Compliance for Medical Software & Healthcare IT
✔️ Increases Market Access & Regulatory Approval (FDA, MDR, HIPAA)
✔️ Enhances Software Quality & Security
✔️ Builds Trust with Healthcare Providers & Patients
✔️ Competitive Advantage in the HealthTech Industry
By following these steps, IT companies in the healthcare sector can achieve ISO 13485 certification, ensuring high-quality, secure, and regulatory-compliant medical software solutions. 🚀
0 notes
Text
Innovating the Future: A Complete Guide to Software Development
In today’s fast-paced digital landscape, software development is at the heart of innovation, enabling businesses to deliver smarter solutions, enhance productivity, and meet the evolving needs of their customers. At Vista Blue Traders, we believe in harnessing the power of technology to drive transformation, and software development plays a pivotal role in achieving that vision. This blog offers a comprehensive guide to software development, exploring its importance, methodologies, challenges, and the latest trends shaping the industry.
What is Software Development?
Software development is the process of designing, coding, testing, and maintaining applications or systems to address specific needs or solve problems. It involves a combination of creativity, technical expertise, and strategic planning to create scalable and efficient solutions. From mobile apps and enterprise systems to cloud platforms and AI-driven applications, software development serves as the foundation of modern technology.

Why is Software Development Important?
Digital Transformation: Software development enables businesses to embrace digital tools, streamline operations, and enhance customer experiences.
Competitive Advantage: Companies can stay ahead by building tailored solutions that meet unique market demands.
Scalability and Efficiency: Well-designed software optimizes processes, reduces manual efforts, and scales with business growth.
Innovation: Custom software fosters innovation by introducing new functionalities and services that reshape industries.
Key Stages of the Software Development Lifecycle (SDLC)
The software development lifecycle (SDLC) is a systematic process that ensures high-quality outcomes. Here’s an overview of its key stages:
Requirement Analysis:
Understanding the client’s needs and objectives.
Defining the scope and functionality of the software.
Documenting technical and non-technical requirements.
Planning:
Creating a roadmap and timeline for development.
Allocating resources and setting milestones.
Design:
Crafting the architecture and user interface.
Ensuring the design aligns with functionality and user experience (UX) principles.
Development:
Writing and integrating code.
Following best practices and coding standards to ensure efficiency and maintainability.
Testing:
Conducting rigorous tests to identify and fix bugs.
Make sure the software meets show, safety, and usability standards.
Deployment:
Releasing the software to production environments.
Monitoring its performance in real-world scenarios.
Maintenance and Updates:
Addressing issues and bugs reported post-deployment.
Introducing new features to enhance functionality.
Popular Software Development Methodologies
The choice of methodology can significantly impact the success of a software project. Here are some widely adopted approaches:
Waterfall Model:
A sequential process where each phase must be completed before the next begins.
Best suited for projects with clearly defined requirements.
Agile Methodology:
Focuses on iterative development and collaboration.
Promotes flexibility and frequent delivery of functional increments.
DevOps:
Integrates development and operations teams to streamline deployment and monitoring.
Enhances collaboration and ensures faster delivery cycles.
Scrum Framework:
A subset of Agile, emphasizing short “sprints” for rapid progress.
Involves daily standups, sprint reviews, and retrospectives.
Lean Development:
Prioritizes efficiency by minimizing waste and focusing on value creation.
Challenges in Software Development
While software development offers immense potential, it’s not without challenges:
Evolving Requirements: Frequent changes in client needs can impact timelines and budgets.
Resource Constraints: Limited budgets, skilled workforce shortages, and time pressures.
Security Concerns: Protecting software from cyber threats is critical.
Technical Debt: Accumulation of suboptimal code can slow future development.
Integration Complexities: Ensuring compatibility with existing systems can be challenging.
Emerging Trends in Software Development
As technology continues to evolve, software development is undergoing significant transformation. Here are some key trends:
Artificial Intelligence (AI) and Machine Learning (ML):
Incorporating AI and ML for predictive analytics, automation, and smarter applications.
Low-Code and No-Code Platforms:
Empowering non-technical users to create applications with minimal coding.
Cloud-Native Development:
Designing applications optimized for cloud environments, enhancing scalability and performance.
Blockchain Integration:
Using blockchain technology for secure and transparent solutions in finance, supply chain, and beyond.
Internet of Things (IoT):
Developing software to connect and manage IoT devices.
DevSecOps:
Integrating security practices into the DevOps process to ensure robust protection.
Progressive Web Apps (PWAs):
Creating web applications that deliver a native app-like experience.
Why Choose Vista Blue Traders for Software Development?
At Vista Blue Traders, we combine technical expertise, innovative thinking, and a customer-first approach to deliver exceptional software solutions. Here’s what sets us apart:
Tailored Solutions: Every project is designed to meet the unique needs of our clients.
Experienced Team: Our developers are skilled in the latest technologies and methodologies.
Agile Approach: We ensure flexibility, collaboration, and timely delivery.
End-to-End Services: From ideation to maintenance, we provide comprehensive support.
Commitment to Quality: We prioritize excellence in every stage of development.
Conclusion
Software development is a cornerstone of modern innovation, enabling businesses to adapt, compete, and thrive in a rapidly evolving world. By embracing the latest trends and methodologies, companies can build solutions that drive growth and create value. At Vista Blue Traders, we’re committed to empowering businesses with innovative software that shapes the future. Whether you’re starting a new project or optimizing an existing system, our team is ready to help you succeed.
0 notes
Text
Security Testing: Safeguarding the Digital Frontier

In an era where data breaches, cyberattacks, and vulnerabilities dominate headlines, the importance of security testing cannot be overstated. Security testing is a critical practice that ensures software systems are resilient against threats, protect sensitive data, and maintain the trust of users. As organizations increasingly rely on digital solutions to power their operations, security testing has become a cornerstone of software development, helping to identify and mitigate risks before they can be exploited. By embedding security testing into the software development lifecycle (SDLC), organizations can build robust, secure, and trustworthy applications that stand up to the challenges of the modern digital landscape.
What is Security Testing? Security testing is the process of evaluating a system’s ability to protect data, maintain functionality, and resist malicious attacks. It involves identifying vulnerabilities, weaknesses, and risks that could be exploited by attackers. Unlike functional testing, which focuses on what the system does, security testing focuses on what the system should not do—such as allowing unauthorized access, leaking sensitive information, or failing under attack. Security testing encompasses a wide range of activities, from vulnerability assessments and penetration testing to code reviews and compliance checks.
The Importance of Security Testing Protecting Sensitive Data Applications often handle sensitive information, such as personal data, financial records, and intellectual property. Security testing ensures that this data is protected from unauthorized access, breaches, and leaks.
Preventing Cyberattacks Cyberattacks are becoming increasingly sophisticated and frequent. Security testing helps identify and address vulnerabilities that could be exploited by attackers, reducing the risk of breaches and ensuring the integrity of the system.
Maintaining User Trust Security breaches can have devastating consequences for an organization’s reputation. By proactively identifying and fixing security issues, organizations can build and maintain the trust of their users.
Ensuring Compliance Many industries are subject to strict regulatory requirements, such as GDPR, HIPAA, and PCI-DSS. Security testing helps ensure that applications comply with these regulations, avoiding costly fines and legal consequences.
Safeguarding Business Continuity A security breach can disrupt operations, lead to financial losses, and damage an organization’s reputation. Security testing helps ensure that systems remain operational and resilient in the face of threats.
Key Types of Security Testing Vulnerability Assessment Vulnerability assessments identify weaknesses in the system, such as misconfigurations, outdated software, or insecure coding practices. This provides a baseline understanding of potential risks.
Penetration Testing Penetration testing simulates real-world attacks to evaluate the system’s ability to withstand malicious activity. It helps identify exploitable vulnerabilities and assess the effectiveness of security controls.
Security Code Review Security code reviews analyze the source code for vulnerabilities, such as SQL injection, cross-site scripting (XSS), and insecure authentication mechanisms. This helps ensure that security is built into the application from the ground up.
Configuration Testing Configuration testing evaluates the security of system settings, such as firewalls, servers, and databases. Misconfigurations are a common source of vulnerabilities and must be addressed to ensure a secure environment.
Authentication and Authorization Testing This type of testing ensures that only authorized users can access specific resources and that authentication mechanisms, such as passwords and multi-factor authentication, are secure.
Compliance Testing Compliance testing verifies that the system meets regulatory and industry standards, such as GDPR, HIPAA, or PCI-DSS. This is critical for organizations operating in regulated industries.
Challenges in Security Testing While security testing is essential, it is not without its challenges:
Evolving Threat Landscape Cyber threats are constantly evolving, with attackers developing new techniques and exploiting emerging vulnerabilities. Security testing must adapt to keep pace with these changes.
Complexity of Modern Systems Modern applications are often built using distributed architectures, microservices, and cloud-native technologies. This complexity makes it challenging to identify and address all potential vulnerabilities.
Balancing Security and Usability Security measures, such as strict authentication or encryption, can sometimes impact user experience. Security testing must strike a balance between robust protection and usability.
Skill Gaps Security testing requires specialized knowledge and expertise, including an understanding of attack vectors, secure coding practices, and regulatory requirements. Organizations must invest in training and upskilling their teams to address these gaps.
The Future of Security Testing As technology continues to evolve, security testing will play an increasingly important role in ensuring the safety and reliability of digital systems. Emerging trends, such as the Internet of Things (IoT), artificial intelligence (AI), and blockchain, will introduce new security challenges and opportunities. Security testing will need to adapt to these changes, ensuring that systems remain secure in increasingly complex environments.
Moreover, the integration of security testing with DevOps and continuous delivery practices will further enhance its impact. By embedding security testing into every stage of the SDLC, organizations can achieve higher levels of security, efficiency, and innovation.
Conclusion Security testing is a critical practice for safeguarding the digital frontier. By identifying and addressing vulnerabilities, it ensures that systems are resilient against threats, protect sensitive data, and maintain the trust of users. While challenges remain, the benefits of security testing far outweigh the risks, making it an indispensable practice for modern software development.
As the software industry continues to innovate, security testing will play an increasingly important role in ensuring the safety and reliability of digital systems. For teams and organizations looking to stay competitive in the digital age, embracing security testing is not just a best practice—it is a necessity for achieving excellence in system security. By combining the strengths of security testing with human expertise, we can build a future where security is at the heart of every system.
1 note
·
View note
Text
Why Software Testing Matters: The Backbone of Quality Assurance

In today’s digital-first world, software is at the heart of nearly every aspect of our lives. From mobile apps and e-commerce platforms to healthcare systems and autonomous vehicles, software powers the tools and services we rely on daily. However, with this growing reliance on software comes the need for reliability, security, and performance. This is where software testing plays a critical role. Software testing is the process of evaluating and verifying that a software application or system meets specified requirements and works as intended. It is an essential part of the software development lifecycle (SDLC) and a cornerstone of Quality Assurance (QA). This article explores why software testing matters and its importance in delivering high-quality software.
What is Software Testing?
Software testing is the systematic process of identifying defects, errors, or gaps in a software application to ensure it functions as expected. It involves executing a program or system with the intent of finding issues, validating functionality, and ensuring the software meets user requirements. Testing can be performed manually or through automated processes, and it encompasses various types, including functional testing, performance testing, security testing, and usability testing.
At its core, software testing is about ensuring that the software delivers value to users by being reliable, secure, and efficient.
Why Software Testing Matters
Software testing is not just a technical necessity — it is a business imperative. Here are the key reasons why software testing matters:
1. Ensures Software Quality
The primary goal of software testing is to ensure that the software meets the highest standards of quality. By identifying and fixing defects early in the development process, testing helps deliver a product that works as intended and provides a seamless user experience.
Example: A banking app that processes transactions accurately and securely is a result of rigorous testing.
2. Prevents Costly Failures
Defects that go undetected in the early stages of development can lead to costly fixes later. Testing helps identify issues before the software is released, reducing the risk of expensive failures and rework.
Example: A bug in an e-commerce platform that causes incorrect pricing could lead to significant financial losses and damage to the brand’s reputation.
3. Enhances User Satisfaction
Users expect software to be intuitive, reliable, and bug-free. Testing ensures that the software meets these expectations, leading to higher user satisfaction and loyalty.
Example: A mobile app with a smooth, glitch-free user interface is more likely to retain users and receive positive reviews.
4. Improves Security
Security breaches can have devastating consequences for businesses and users alike. Testing helps identify vulnerabilities and ensures that the software is secure against potential threats.
Example: Testing can uncover vulnerabilities in a healthcare app that stores sensitive patient data, preventing potential data breaches.
5. Ensures Compliance
Many industries are subject to strict regulatory requirements. Testing ensures that the software complies with these regulations, avoiding legal penalties and reputational damage.
Example: A financial application must comply with regulations like GDPR or PCI DSS, which can be verified through rigorous testing.
6. Supports Continuous Improvement
Testing provides valuable feedback on the software’s performance, usability, and functionality. This feedback can be used to make iterative improvements, ensuring the software evolves to meet user needs.
Example: User feedback from testing can lead to enhancements in a productivity app, making it more efficient and user-friendly.
7. Builds Trust
High-quality software builds trust with users, stakeholders, and partners. Testing demonstrates a commitment to delivering reliable and secure products, fostering confidence in the brand.
Example: A well-tested software product from a trusted brand is more likely to be adopted by businesses and consumers.
The Consequences of Skipping Software Testing
Neglecting software testing can have severe consequences, including:
Software Failures: Untested software is prone to crashes, bugs, and performance issues, leading to a poor user experience.
Financial Losses: Defects in production can result in costly fixes, lost revenue, and damage to the brand’s reputation.
Security Breaches: Vulnerabilities in untested software can be exploited by malicious actors, leading to data breaches and legal liabilities.
User Dissatisfaction: Bugs and glitches frustrate users, leading to negative reviews, decreased adoption, and loss of customer trust.
Non-Compliance: Failure to meet regulatory requirements can result in fines, legal action, and loss of business opportunities.
Types of Software Testing
Software testing encompasses a wide range of activities, each serving a specific purpose. Some of the most common types of testing include:
Functional Testing: Verifies that the software functions as intended and meets the specified requirements.
Performance Testing: Evaluates the software’s speed, responsiveness, and stability under various conditions.
Security Testing: Identifies vulnerabilities and ensures the software is secure against potential threats.
Usability Testing: Assesses the software’s user interface and overall user experience.
Regression Testing: Ensures that new changes or updates do not introduce new defects or break existing functionality.
Compatibility Testing: Checks that the software works across different devices, browsers, and operating systems.
Best Practices for Effective Software Testing
To maximize the benefits of software testing, organizations should follow these best practices:
Start Early: Incorporate testing from the beginning of the development process to identify and fix issues early.
Define Clear Objectives: Establish clear testing goals and success criteria based on the software’s intended purpose.
Use Diverse Test Data: Ensure that the test data is diverse and representative of real-world scenarios.
Collaborate Across Teams: Foster collaboration between developers, testers, and operations teams to ensure shared responsibility for quality.
Prioritize Security: Incorporate security testing throughout the SDLC to identify and address vulnerabilities early.
Document and Report: Maintain detailed documentation of test cases, results, and issues to facilitate communication and decision-making.
Conclusion
Software testing is not just a technical process — it is a critical component of delivering high-quality, reliable, and secure software. By identifying defects, ensuring compliance, and enhancing user satisfaction, testing plays a vital role in the success of any software product. In a world where software is integral to our daily lives, the importance of software testing cannot be overstated.
For organizations looking to build trust, reduce risks, and deliver value to users, investing in robust software testing practices is essential. It is the backbone of Quality Assurance and a key driver of business success in the digital age. Software testing matters because, ultimately, it ensures that the software we rely on works as intended, every time.
0 notes
Text
How Quality Assurance Services Enhance the Software Development Lifecycle
In the fast-paced world of software development, delivering high-quality products is essential for meeting customer expectations and maintaining a competitive edge. Quality assurance (QA) services play a crucial role throughout the software development lifecycle (SDLC), ensuring that applications are reliable, functional, and user-friendly. This article explores how effective QA practices enhance each phase of the SDLC and contribute to overall project success.
The Role of Quality Assurance in the Software Development Lifecycle

Quality assurance services are integrated into every phase of the SDLC, from planning to deployment and maintenance. By embedding QA practices throughout the process, organizations can identify and address potential issues early, leading to improved product quality.
1. Requirement Analysis Phase
During the requirement analysis phase, QA teams collaborate with stakeholders to define clear quality standards and expectations for the project. This early involvement helps ensure that all requirements are understood and documented accurately.
Benefits:
Reduces misunderstandings that can lead to defects later in development.
Establishes a baseline for what constitutes acceptable quality.
2. Design Phase Testing
In the design phase, QA services focus on validating design specifications against user requirements. This involves reviewing design documents and conducting design reviews to ensure that the proposed solution aligns with quality standards.
Benefits:
Identifies potential design flaws before development begins.
Ensures that user experience considerations are integrated into the design.
3. Implementation Testing
As development progresses, QA teams conduct various testing activities to ensure that the software functions as intended. This includes unit testing, integration testing, and system testing.
Benefits:
Early detection of defects reduces the cost and time associated with fixing issues later in the process.
Continuous feedback allows developers to make adjustments in real-time.
4. User Acceptance Testing (UAT)
User acceptance testing is a critical phase where end-users validate that the software meets their needs and expectations. QA teams facilitate UAT by providing test cases and supporting users during the testing process.
Benefits:
Ensures that the final product is user-friendly and meets business requirements.
Builds confidence among stakeholders by demonstrating that quality standards have been met.
5. Deployment and Maintenance
After successful testing, the software is deployed to production. However, QA services do not end here; ongoing maintenance and support are essential for ensuring long-term product quality.
Benefits:
Continuous monitoring of software performance helps identify issues quickly.
Regular updates and patches maintain security and functionality over time.
Best Practices for Integrating QA into the SDLC
To maximize the benefits of quality assurance services within the software development lifecycle, organizations should consider implementing these best practices:
1. Involve QA from the Beginning
Engaging QA teams early in the SDLC ensures that quality considerations are integrated into every phase of development. This proactive approach helps set clear expectations and reduces defects later in the process.
2. Adopt Agile Methodologies
Agile methodologies promote iterative development and continuous testing, allowing teams to respond quickly to changes while maintaining high-quality standards. By incorporating QA into agile sprints, organizations can enhance collaboration between developers and testers.
3. Leverage Automation Tools
Automated testing tools can significantly improve efficiency by allowing teams to run tests quickly and accurately. Automation reduces manual effort and enables continuous integration practices that enhance overall product quality.
4. Foster a Culture of Quality
Creating a culture that prioritizes quality at all levels of the organization encourages collaboration and accountability among team members. Regular training sessions and open communication about quality issues help reinforce this culture.
Conclusion
In conclusion, quality assurance services are integral to enhancing every phase of the software development lifecycle. By embedding QA practices throughout the SDLC, organizations can identify potential issues early, reduce costs associated with defects, and deliver high-quality products that meet customer expectations. Investing in effective quality assurance services is not just about preventing defects; it’s about creating a culture of excellence that drives customer satisfaction and business success. As you evaluate your organization’s approach to QA within the software development lifecycle, remember that prioritizing quality will position you as a leader in your industry—committed to delivering reliable software solutions that resonate with users.
0 notes
Text
Sify's DevSecOps Services: Securing the Future of Application Development
In today’s fast-paced digital landscape, businesses need to innovate swiftly while ensuring that their applications are secure from the ground up. As enterprises adopt DevOps to speed up their development cycles, integrating security into the development process has become crucial. Sify’s DevSecOps Services provide businesses with a comprehensive approach to secure software development, enabling them to deliver faster, safer, and more reliable applications.
What is DevSecOps?
DevSecOps integrates security practices into the DevOps process, ensuring that security is embedded throughout the entire software development lifecycle (SDLC). This "shift-left" approach means security is considered from the very beginning—during planning, development, and testing stages—rather than being an afterthought. By integrating security into every stage of development, DevSecOps helps organizations build resilient applications while maintaining speed and agility.
Sify’s Approach to DevSecOps
At Sify, DevSecOps is not just about combining security tools with DevOps processes; it’s about fostering a culture of collaboration between development, operations, and security teams. This holistic approach ensures that security is woven into the fabric of the development process, reducing risks while accelerating innovation.
Here’s how Sify’s DevSecOps services empower businesses:
1. Security Embedded from Day One
Security is integrated from the beginning of the development cycle. Sify ensures that every line of code is reviewed for security vulnerabilities, and security testing is conducted throughout the development process. By addressing security concerns early, Sify helps businesses avoid costly fixes and breaches down the road.
2. Automated Security Testing
To keep up with the rapid pace of modern development, Sify incorporates automated security testing into the continuous integration/continuous delivery (CI/CD) pipeline. This enables quick identification and remediation of security issues, ensuring that vulnerabilities are caught before applications are deployed. With automation, security becomes a natural part of the development process without slowing down delivery.
3. Continuous Monitoring and Incident Response
In addition to pre-deployment security, Sify’s DevSecOps Services provide continuous monitoring of applications in production. By integrating real-time monitoring tools and threat intelligence, Sify ensures that businesses can detect and respond to security threats swiftly. In the event of an incident, the team’s incident response services enable quick containment, investigation, and recovery, minimizing potential damage.
4. Vulnerability Management
As part of its comprehensive DevSecOps offering, Sify performs continuous vulnerability scanning and management throughout the software lifecycle. This proactive approach allows businesses to identify and remediate vulnerabilities before they can be exploited. By integrating automated patch management solutions, Sify ensures that known vulnerabilities are addressed promptly.
5. Compliance and Governance
Many industries must adhere to strict regulatory requirements such as GDPR, HIPAA, and PCI-DSS. Sify’s DevSecOps Services ensure that security policies are aligned with industry regulations and governance standards. The integration of security compliance tools into the DevOps pipeline allows businesses to maintain compliance without manual intervention, reducing the risk of non-compliance.
6. Container Security
As businesses move towards microservices and containerized environments, ensuring the security of containers has become paramount. Sify’s DevSecOps Services provide end-to-end container security, from image scanning to runtime protection. This ensures that businesses can deploy containers confidently, knowing they are protected from vulnerabilities and misconfigurations.
7. Training and Cultural Transformation
Sify’s DevSecOps Services go beyond just tools and technology—they focus on building a culture of security within the organization. By offering training and guidance to development, operations, and security teams, Sify helps organizations embrace a "security-first" mindset. This cultural shift is essential for the long-term success of DevSecOps initiatives.
Benefits of Sify’s DevSecOps Services
By adopting Sify’s DevSecOps Services, businesses can experience a wide range of benefits:
Faster Time-to-Market: Security is no longer a bottleneck. With automated security checks and continuous monitoring, applications can be delivered faster without compromising security.
Improved Security Posture: Embedding security throughout the SDLC significantly reduces the risk of security breaches and vulnerabilities, ensuring that applications are secure from the start.
Cost Savings: Identifying and addressing security issues early in the development process reduces the cost of fixing vulnerabilities later in production. It also minimizes the financial impact of potential breaches.
Regulatory Compliance: By automating compliance checks, Sify ensures that businesses remain compliant with industry regulations and standards.
Enhanced Collaboration: DevSecOps fosters a collaborative environment where development, operations, and security teams work together seamlessly, breaking down traditional silos.
Partnering with Sify for DevSecOps Success
Sify’s DevSecOps Services are designed to help businesses achieve the perfect balance between speed and security in their application development journey. By integrating security practices into the DevOps process, Sify enables organizations to innovate faster while minimizing risk. Whether you are just starting your DevSecOps journey or looking to optimize your existing processes, Sify offers tailored solutions that align with your unique business needs.
In today’s competitive digital landscape, delivering secure applications quickly is no longer optional—it’s a necessity. With Sify’s DevSecOps Services, businesses can accelerate their development cycles while ensuring that security remains a top priority, driving innovation without compromise.
0 notes