#Signature of a keystore
Explore tagged Tumblr posts
Text
How we can check SHA1 or Signature of APK and Keystore file
How we can check SHA1 or Signature of APK and Keystore file

In this post, I will explain to you how we can check which key store is used to sign your APK file. For this process, we are going to use Java 7’s Key and Certificate Management Tool ( keytool) to check the signature of a Keystore or an APK without extracting any files. This technique is very simple and very useful.
How to Check Signature of an APK
To check the Signature of your app you can…
View On WordPress
0 notes
Text
Java se development kit 10 install fails

JAVA SE DEVELOPMENT KIT 10 INSTALL FAILS INSTALL
JAVA SE DEVELOPMENT KIT 10 INSTALL FAILS UPDATE
JAVA SE DEVELOPMENT KIT 10 INSTALL FAILS PATCH
JAVA SE DEVELOPMENT KIT 10 INSTALL FAILS FULL
JAVA SE DEVELOPMENT KIT 10 INSTALL FAILS CODE
That gave me the idea to make sure the Windows installer service was running or that it might be an installer problem, but that didn't help either. But then instead of terminating, the temp file started running as a separate process, and after another short time the Windows installer started.
JAVA SE DEVELOPMENT KIT 10 INSTALL FAILS INSTALL
I tested the installer on a clean install virtual machine and it behaved the same way at the start. I managed to save the temp file before it got deleted and tried to run it directly but it also does nothing, albeit more quickly because it terminates right away. After another short time the JDK process terminates and the temp files and folders are deleted. The file in the temp directory with the same name is 190,569,048 bytes. The setup file is called jdk-8u74-windows-i586 and is 190,853,720 bytes long. After a short time this file disappears and is replaced by a file with the same name as the setup file, but with a slightly different size. Within that folder it creates a file jds*.tmp, where the * is again a number. When I double click the setup file it creates a folder in my temp directory called jds*.tmp, where the * is a number that varies.
JAVA SE DEVELOPMENT KIT 10 INSTALL FAILS FULL
This is not an issue because I am using the Administrator account, all permissions for all files and folders are set to Full Control, and there is no anti-virus. I researched the error and most of the suggestions had to do with accounts and permissions. But when I try to install it nothing happens. So I downloaded the latest Java SE Development Kit 8u74 from Oracle myself. The only additional information given in the log file is "Process returned error: 0x80048646". Everything worked except for Java SE Development Kit 7.0.550.13. I first installed Office, then I installed Visual Studio 2015. For a more complete list of the bug fixes included in this release, see the JDK 10.0.1 Bug Fixes page.I am setting up a clean install of Windows 7 Ultimate 32-bit.
JAVA SE DEVELOPMENT KIT 10 INSTALL FAILS PATCH
This release contains fixes for security vulnerabilities described in the Oracle Critical Patch Update. To improve the strength of SSL/TLS connections, 3DES cipher suites have been disabled in SSL/TLS connections in the JDK via the Security Property.
JAVA SE DEVELOPMENT KIT 10 INSTALL FAILS CODE
The secure validation mode is enabled either by setting the property .secureValidation to true with the .setProperty() method, or by running the code with a SecurityManager. The secure validation mode of the XML Signature implementation has been enhanced to restrict EC keys less than 224 bits by default. XML Signatures Signed with EC Keys Less Than 224 Bits Disabled.The default pattern allows, , $Type, and but rejects all the others.Ĭustomers storing a SecretKey that does not serialize to the above types must modify the filter to make the key extractable. The filter pattern uses the same format as jdk.serialFilter. If the system property is also supplied, it supersedes the security property value defined here. If it is not configured or if the filter result is UNDECIDED (for example, none of the patterns match), then the filter configured by jdk.serialFilter is consulted. If this filter is configured, the JCEKS KeyStore uses it during the deserialization of the encrypted Key object stored inside a SecretKeyEntry. These applications can use the Cipher API directly as an alternative to using this class.Ī new security property named has been introduced. Because of this behavior, this class may not be suitable for use with decryption in an authenticated mode of operation (for example, GCM) if the application requires explicit notification when authentication fails. These exceptions are not re-thrown, so the client is not informed that integrity checks have failed. The specification of has been clarified to indicate that this class catches BadPaddingException and other exceptions thrown by failed integrity checks during decryption. For more information, see JRE Expiration Date.
JAVA SE DEVELOPMENT KIT 10 INSTALL FAILS UPDATE
After either condition is met (new release becoming available or expiration date reached), the JRE will provide additional warnings and reminders to users to update to the newer version. This JRE (version 10.0.1) will expire with the release of the next critical patch update scheduled for July 17, 2018.įor systems unable to reach the Oracle Servers, a secondary mechanism expires this JRE (version 10.0.1) on August 17, 2018. Critical patch updates, which contain security vulnerability fixes, are announced one year in advance on Critical Patch Updates, Security Alerts and Third Party Bulletin. The JRE expires whenever a new release with security vulnerability fixes becomes available.

0 notes
Text
Keystore explorer command line

#Keystore explorer command line password
alias is an option to mention an Alias Name for your key entry keytool -genkey -keystore keystore.jks -alias ssl -keyalg RSA -sigalg SHA256withRSA -validity 365 -keysize 2048 jks file that will initially only contain the private key using the keytool utility. While we create a Java keystore, we will first create the. Share the certificate or root certificates to the system that uses the SSL to communicate to your system/application.Import the primary/server certificate, root, and intermediate CA certificates to keystore.Generate a signed primary/server certificate from the Certificate Authority.Generate a CSR (Certificate Signing Request) from keystore.Create a keystore that contains a private key.Steps to Process the Keystore, CSR, and the Signed Certificate Prints the content of a certificate request
#Keystore explorer command line password
Imports one or all entries from another keystore to a keystoreĬhanges the key password of an entry in keystore Import a certificate or a certificate chain to keystore Generates a certificate from a certificate request The various keytool options are listed below: KEYTOOL OPTIONS RSA, DES).Ī Keytool keystore contains the private key and any certificates necessary to complete a chain of trust and establish the trustworthiness of the primary certificate.Īll certificates in a Java keystore are associated with a unique alias, which will be used as a pointer to later perform any of the keytool operations to import, export, delete, and/or change certificates and keys. Keytool also enables users to administer secret keys used in symmetric encryption/decryption (e.g. It protects private keys with a password. The Java keystore is implemented as a file by default. Java keytool stores the keys and certificates in what is called a keystore. It also allows users to cache the public keys (in the form of certificates) of their communicating peers. It allows users to administer their own public/private key pairs and associated certificates for use in self-authentication (where the user authenticates themselves to other users/services) or data integrity and authentication services using digital signatures. Keytool is a key and certificate management JDK utility that helps in managing a keystore of private/public keys and associated certificates.

0 notes
Text
Omniplayer vip lifetime

Omniplayer vip lifetime for mac#
Omniplayer vip lifetime mod apk#
Omniplayer vip lifetime manual#
Omniplayer vip lifetime android#
Omniplayer vip lifetime software#
– Fixed an issue where error “Unsupported compression method 95” might be displayed when decompressing ZIP files – Fixed problem that whole word match option of text editor text search does not work when replacing all – Fixed issue that text editor undo function would undo twice at one time under certain circumstances – Fixed problem that text editor’s detection modification or deletion dialog box would pop up repeatedly – Fixed problem that most of text editors cause crash – Text editor restores json’s comment function – Upper left corner of text editor temporary file name is no longer italicized – Added double confirmation switch before exiting from text editor Now I can only wait for the official QQ update.
Omniplayer vip lifetime android#
PS: Regarding the problem that multiple files cannot be shared to QQ at the same time on Android 11, after analysis, it is found that QQ is not adapted to the latest system specifications (it is adapted to receive a single file, but it is not adapted to receive multiple files, it is estimated that development user forgot it), and I can’t change back to old specification, which will cause problems with applications that adapt to the new specification.
View / edit / delete / add classes, methods, domains, permanent.
Work with ZIP (compression / unpacking).
Decompilation / Compiling XML VIP (for a free 200-line limit).
Batch operations (delete, copy, move, rename).
Fast transfer of unique strings to the desired localization.
Support for several dictionaries in the translator (UTF-8 without BOM) VIP.
Support for keystore and jks VIP signatures.
Portrait mode (landscape only in places).
Omniplayer vip lifetime mod apk#
Money Clicker Mod APK v2.3.27 (Money) Songs of Conquest v0.77.3 Songs of Conquest v0.77.1 Roadwarden Build 9484750 Nobody Saves the World: Complete (+ Frozen Hearth DLC + Bonus OST + Windows 7 Fix, MULTi10) Zooba Mod APK v3.38.0 (No Ads)ĭownload Setup + Crack Download Crack Only MT Manager VIP Features:
Omniplayer vip lifetime for mac#
App Switcher 2.2.0 + Activator 4MacOS Microsoft Office 2021 for Mac LTSC v16.65 VL + Activator 4MacOS Large Files Finder 1.5.0 + Activator 4MacOS Master of Typing 3 – Practice 3.3.14 + Activator 4MacOS GraphicConverter 11.6.3 (5602) + Activator 4MacOS ForkLift 3.5.8 + Activator 4MacOS Claris FileMaker Pro 19.5.4.401 + Activator 4MacOS Cisdem Duplicate Finder 6.1.0 + Activator 4MacOS BeLight Art Text 4.1.3 (938) fix + Activator 4MacOS AYVY 1.20.0 + Activator 4MacOS Whateverland (MULTi11) VARIOUS DAYLIFE MULTi13 REPACK-KaOs Vampire Survivors v0.11.304 Valheim v0.211.4 Timberborn v0.2.8.0 Timberborn v0.2.7.2 Flip Diving v3.5.60 (Unlimited Coins) There Is No Light #DRIVE Mod APK v3.0.27 (Unlimited Money) The Wandering Village v0.1.32 Buddy Toss Mod APK v1.5.0 (Money) The Wandering Village v0.1.30 Last Pirate: Survival Island Mod APK v1.4.12 (Money) The Wandering Village (v) Live or die: Survival Mod APK v0.3.471 (Free Craft) Pepi Wonder World Mod APK v7.0.14 (Unlocked) The Infected v13.0.8 The Death (Build 9537454, MULTi5) Driving Zone: Japan Mod APK v3.21.41 (Unlimited Money) Technicity (v1.0d, MULTi7) Demolition Derby 2 Mod APK v1.6.97 (Unlimited Coins) Surviving the Aftermath v1.
They can therefore have a complete overview of their work in one place.Yoink 3.6.83 + Activator 4MacOS Wondershare Filmora X 11.7.0 + Activator 4MacOS WidsMob Montage 2.24 + Activator 4MacOS VideoPad Professional 12.04 + Activator 4MacOS Sublime Text 4.0 Build 4135 Dev + Activator 4MacOS SponsorBlock for YouTube 5.0.3 + Activator 4MacOS 3DF Zephyr 6.509 + Activator 3DCoat 2022.46 (圆4) + Activator Speedy Duplicate Finder 1.4.0 + Activator 4MacOS Soulver 3.6.1 + Activator 4MacOS Smart File Renamer 1.4.0 + Activator 4MacOS Scrutiny 12.4.4 + Activator 4MacOS rcmd Everything is displayed on a single monitor or a dual screen so that DJ’s do not need to look around for information. News or weather forecasts may be standard text files that can be displayed on an auxiliary text window. Mixes/cross fades between songs are made possible by the use of two completely independent stereo tracks for broadcasting. All the operator then needs to do is to push a button to start broadcasting this title.
Omniplayer vip lifetime manual#
In manual mode, the title at the top of the list is automatically assigned to either of the two stereo tracks available. The operator can modify this list at any time by “dragging and dropping” titles from the Database explorer. The log can contain different types of events:Īnything that has to be played or announced on the air can be included in this log. LogEditor is the OmniPlayer application for scheduling. MultiPlayer loads the log clock-by-clock if it has been programmed using the LogEditor application.
Omniplayer vip lifetime software#
The radio playout software is versatile, yet easy to use. The MultiPlayer application can serve live assist and automated radio broadcasting.

0 notes
Text
Free App Builder Online
Free App Builder Sites If you've ever before desired to develop an app after thinking up a dazzling principle, you're in the perfect place. Producing an app all on your own isn't very easy, yet you obtain a talented child to induce it only to start. You have to take into consideration whether developing a tissue app are going to undoubtedly benefit others and additionally certainly not merely generate one to mention you have really performed one.
Free App Builder And Publisher
Best White Label App Builder
All you have to recognize is actually the way Android apps operate, as well as our company'll handle the rest. As soon as your app is actually completely evaluated and also prepared to go, you can easily publish as well as market the app, and analyze the user information. If you're seeking to develop mobile apps for profit therefore you wish an approach.
As quickly as you've published your app, you would certainly have to ensure it is actually discoverable. You require to remember that you still have to offer your app. Apps continue to be actually young, yet presently quite usual. An App is actually an application that needs to be actually downloaded and install and install as well as also installed on a cellphone, rather than being helped make inside an online web browser. The app could draw web content as well as also relevant information on the net, superior type to an on the internet website, or even it might download and also put in the world wide web information to make certain that it could be retrieved without an on the internet hookup. Thus, right now you know just how to help make an app, I will recommend that you get going investigating app advertising techniques to make sure that you are able to modify the world one app at one time! You are mosting likely to discover just how to develop all types of Android apps coming from todo lists to mobile activities and also social platforms.
The popular main reason why most of apps don't obtain incredible recognition in the app market is poor design. You would need to pay the pointed out 99$, merely when you want to release your app. After the app manages, you ought to comprehend your user interface turn up on the screen. Online DOM updates rapidly and additionally just as soon as the App isn't being taken advantage of real DOM is updated. Creating a mobile app to market a business, product or service is actually a no-brainer.
Free App Builder Sites
Based upon your skill-set amount, you must possess an app operating successfully regular or even much less. It's definitely relatively very easy to advertise an app consisting of all the growths in advancement making it practical for considerable amounts of folks if you want to see it. If you prefer to create an Android app, after that you are going to desire to discover Java.
You ought to recognize your app as received the upcoming screenshot. Particularly, you will certainly determine just how to generate an app which might certainly not give you numerous bucks. An app is a simple, skillful and also inexpensive solution for ensuring your own self. Thankfully, there are tons of excellent apps on the market to help you and also your youngsters know to code, if it be to develop an app or maybe to know to call upon a robotic.
If you can't build an app, you might constantly hire a tissue app developer to accomplish the job for you. If you develop an app that isn't including worth afterwards no person is going to definitely desire to install it or even utilize it. Through Mobiroller, you might manufacture vibrant apps.
If you've enrolled your app working with the debug signature in the course of development, you may must take a new Android readying to your application whenever you are good to go to post the app. Having an app for your firm is developing quite necessary. The moment you get this done, the platform will build a basic app along with components that are actually based upon your present web content. Your Android App is about to install. Prior to you start producing Android App you need to find out Object Oriented Java. It is possible to effortlessly make an Android app by working with an app-creation platform like Como. When you make Android app along with React Native you only require to maintain a solitary code and also code will certainly generate indigenous Android app together with iOS app.
Free App Builder Reviews
Lots of user interfaces will enable you to move details from your website. You will certainly do away with the connection if you go out the app for at the very least a couple of seconds. You will definitely be able to establish a connection devoid of dildo linked on each side. It focuses on the internet as well as residence systems. To receive your app's web content indexed through Google, use the specific URLs in your app which you utilize on your website as well as verify that you possess each your app and your website. That kind of details is actually merely stashed on your unit. This checklist suggests a lot of the symbols, labels, and also shades that retail stores may wish to change.
As opposed to what you might have heard, you don't require to hire a developer or devote countless dollars to create an app for your organization. The platform was made to serve inter OS partnerships! Based upon your app's usage cases, a number of these components might gain additional feeling than others. The app trademark is a SHA-256 hash value that's put on each Android app when it is actually constructed. App trademarks are inhibited a keystore. Multi-purpose Interfaces This design is actually ideal for bistros, yet it is actually functional as well as enables you to utilize it to set up an app for essentially all type of organisation. It covers the guidelines of the foreign language and items superb examples (like source code).
The Androidian If you're excited to dedicate a small money to accelerate your know-how of the platform, I definitely propose Google's Android Nanodegree. Making your very own app will assist you save money, so it is a viable alternative for everybody. Maintain your association ready to opt for revenue pouring in. Enterprise Level Back End This form of user interface functions through putting together a mobile app that you are able to utilize to tout your customers, drive your sights, connect to your social media accounts, send out mail asks for, and also a whole lot even more. Any sort of released product that's various to the on the internet channel is going to appear in the app. It permits you to promote your brand name and reach more customers. It assists a vast array of movies also.
Best Free App Builder 2018
You may use any type of on the internet stations. Based on your criteria, you may use a various on-line network for each apps, or even you may make use of the precise same online channel for the 2 apps. An individual can easily likewise modify the General User Interference of the Kodi program utilizing the strongly enhanced and also easy to utilize setups supplied in the program. Account quality is of harsh top quality as all online videos are offered in High interpretation. Kodi APK holds a substantial amount of add-ons that's helped make by their area of users. You might likewise download and install the additionals needed for seeing completely free of cost flicks and TV programs.
For More Detail Click Here: https://sites.google.com/site/bestwhitelabelappbuilder/
1 note
·
View note
Text
فول دامپ XML تست شده هارد هواوی Huawei Y7 Prime Dual (2018) - LDN-L21

فول دامپ XML تست شده هارد هواوی Huawei Y7 Prime Dual (2018) - LDN-L21
Huawei Y7 Prime Dual (2018) - LDN-L21 Full Emmc XML Dump __________________________________________ در این مطلب برای شما فول دامپ هواوی Y7 Prime Dual مدل LDN-L21 آماده کرده ایم که پس از رایت به راحتی گوشی کامل بالا می آید . _________________________________________________ هارد های مورد استفاده و تست شده گوشی LDN-L21 eMMC: FTBC 32G BUT MY DUMB EMMC B512 16G _________________________________________________

xml-boot-repair-dr-emmc.org __________________________________________ Loader Info: HWID: 0x0004F0E100150041 SWID: 0x0000000000000003 HASH: 0x6BC369511DA9CADB3A7AF61574F89DB385003D6241BDD1FF573DBA61BF6AE119 CPU: MSM8937 CERT Cnt: 3 Wait.. Loader Sent, Run FireHose.. Get Memory Type.. Detected Memory: EMMC FireHose Config Info: MSM8937, Memory: eMMC, Ver: 1 Ext Info: 0x00002000/0x00004000/0x00001000/0x00001000 FireHose Configure OK Get Protocol Type.. Detected Generic FireHose Type.. Reading EMMC ROM's Info.. EMMC ROM #1 -> 30535680 / 14.56 GB EMMC ROM #2 -> 8192 / 4.00 MB EMMC ROM #3 -> 8192 / 4.00 MB Memory Type: EMMC Physical Partitions: 3 Packet Size: 16384 Sector Size: 512 EMMC Vendor: 0x15 -> SAMSUNG EMMC NAME: RE1BMB BOOT OK, FireHose Ready.. Selected Primary Memory Type: EMMC Run Main Engine.. Scanning GUID Partition Table from ROM1 GUID Partition Table is Found. Max Parts: 56 GPT: GPT Size: 17.00 KB GPT: SBL1 Size: 512.00 KB GPT: RPM Size: 512.00 KB GPT: TZ Size: 2.00 MB GPT: DEVCFG Size: 256.00 KB GPT: DSP Size: 16.00 MB GPT: KEYSTORE Size: 512.00 KB GPT: FRP Size: 512.00 KB GPT: MOTA Size: 512.00 KB GPT: DIP Size: 1.00 MB GPT: SYSCFG Size: 512.00 KB GPT: LKSECAPP Size: 128.00 KB GPT: APDP Size: 256.00 KB GPT: MSADP Size: 256.00 KB GPT: DPO Size: 8.00 KB GPT: FSC Size: 1.00 KB GPT: SSD Size: 8.00 KB GPT: BOOTFAIL_INFO Size: 2.00 MB GPT: PAD0 Size: 7.09 MB GPT: ABOOT Size: 4.00 MB GPT: CMNLIB Size: 1.00 MB GPT: CMNLIB64 Size: 1.00 MB GPT: KEYMASTER Size: 1.00 MB GPT: PAD1 Size: 10.50 MB GPT: FSG Size: 4.00 MB GPT: DDR Size: 32.00 KB GPT: SEC Size: 16.00 KB GPT: DEVINFO Size: 1.00 MB GPT: LIMITS Size: 32.00 KB GPT: PAD2 Size: 9.42 MB GPT: OEMINFO Size: 64.00 MB GPT: MISC Size: 4.00 MB GPT: MODEMST1 Size: 4.00 MB GPT: MODEMST2 Size: 4.00 MB GPT: RRECORD Size: 8.00 MB GPT: NFF Size: 8.00 MB GPT: MCFG Size: 4.00 MB GPT: MODEM Size: 96.00 MB GPT: ERECOVERY_KERNEL Size: 56.00 MB GPT: ERECOVERY_RAMDISK Size: 32.00 MB GPT: ERECOVERY_VENDOR Size: 16.00 MB GPT: KERNEL Size: 56.00 MB GPT: RAMDISK Size: 16.00 MB GPT: RECOVERY_RAMDISK Size: 32.00 MB GPT: RECOVERY_VENDOR Size: 16.00 MB GPT: CACHE Size: 128.00 MB GPT: ODM Size: 32.00 MB GPT: PERSIST Size: 32.00 MB GPT: LOG Size: 64.00 MB GPT: PATCH Size: 32.00 MB GPT: VERSION Size: 32.00 MB GPT: VENDOR Size: 608.00 MB GPT: PRODUCT Size: 192.00 MB GPT: CUST Size: 192.00 MB GPT: SYSTEM Size: 2.56 GB GPT: USERDATA Size: 10.25 GB GPT: BACKUP_GPT Size: 16.50 KB Reading Table Completed Scanning GUID Partition Table from ROM2 GPT Signature Not Found. Break.. Scanning GUID Partition Table from ROM3 GPT Signature Not Found. Break.. Reading Initial Data. Please Wait.. Partition #6 - mount as -> 16.00 MB, Type: EXT4 Partition #38 - mount as -> 96.00 MB, Type: FAT16 Partition #46 - mount as -> 128.00 MB, Type: EXT4 Partition #47 - mount as -> 32.00 MB, Type: EXT4 Partition #48 - mount as -> 32.00 MB, Type: EXT4 Partition #49 - mount as -> 64.00 MB, Type: FAT16 Partition #51 - mount as -> 32.00 MB, Type: EXT4 Partition #52 - mount as -> 608.00 MB, Type: EXT4 Partition #53 - mount as -> 192.00 MB, Type: EXT4 Partition #54 - mount as -> 192.00 MB, Type: EXT4 Partition #55 - mount as -> 2.56 GB, Type: EXT4 Partition #56 - mount as -> 10.25 GB, Type: F2FS EmptyCheck: EMPTY -> ROM_1 -> Part #15 - EMPTY -> ROM_1 -> Part #16 - EMPTY -> ROM_1 -> Part #17 - EMPTY -> ROM_1 -> Part #18 - EMPTY -> ROM_1 -> Part #19 - EMPTY -> ROM_1 -> Part #24 - EMPTY -> ROM_1 -> Part #29 - EMPTY -> ROM_1 -> Part #30 - EMPTY -> ROM_1 -> Part #32 - EMPTY -> ROM_1 -> Part #36 - EMPTY -> ROM_1 -> Part #37 - EMPTY -> ROM_1 -> Part #50 - EmptyCheck: Done Android Info: Brand = Android Device = msm8937_64 Product = msm8937_64 Platform = msm8937 CPU ABI = arm64-v8a Android Version = 8.0.0 Security Patch = 2018-06-01 Android Info: Vendor = unknown CPU ABI = arm64-v8a Android Version = 8.0.0 Firm Version = System 8.0.0.062(000U) Inc. Version = eng.root.20180626.015500 Firm Date = Tue Jun 26 01:55:00 CST 2018 Security Patch = 2018-06-01 Scanner Thread Terminated Elapsed: 00:00:19:434 Found 57 Partition(s).. Scan Done. Init Main Engine... Use Qlm EMMC Device: Qualcomm HS-USB QDLoader 9008 (COM240) Reader Engine Initialized.. 0/OK Source: Qualcomm 9008 EMMC/UFS/AUTO Generation: GPT Config: 1011111111101111 Operation Done: , Elapsed: _________________________________________________ فایل قابل رایت با کلیه باکس های پروگرم هارد فول دامپ XML تست شده هارد هواوی Huawei Y7 Prime Dual (2018) - LDN-L21 _________________________________________________ اطلاع از جدیدترین محصولات و برخورداری از محصولات رایگان و کدهای تخفیف در : ->>کانال تلگرام فروش فایل ماکانال تلگرام فروش ابزار ، ایسی و باکس Read the full article
0 notes
Text
TYPES OF CRYPTO WALLETS

A crypto wallet is an app for generating, managing, and storing cryptographic keys - your public and private key. You can check your balance, receive, and send funds with a wallet.
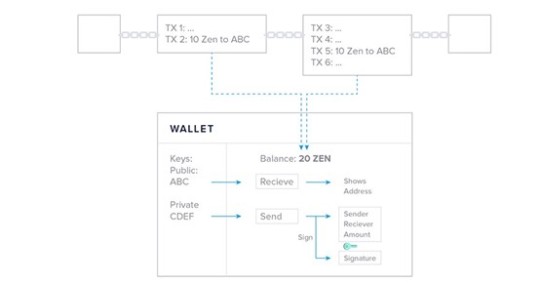
Your Mnemonic Phrase
Your mnemonic phrase is a backup of your private key that is used by most wallets. It is a list of random words given to you when creating a wallet, usually 12 or 24. If you break or lose a device with a wallet - no matter if mobile, desktop or hardware wallet - your mnemonic phrase is usually your last line of defense against a loss of funds.
This implies, that any attacker that gets their hands on your recovery phrase will be able to do the same. Therefore, you must protect your mnemonic phrase as well as you would protect your funds themselves.
Important Note: You should write the phrase of words down on paper or save them in any analog format you see fit, but do not save them as a text file on your computer or a screenshot. You don’t want to make it too easy for any potential attacker to steal your money.
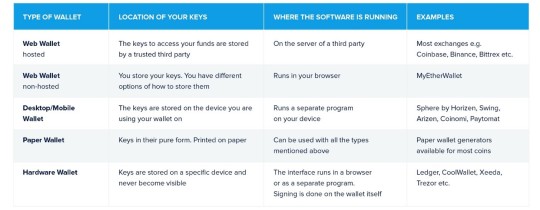
The Different Types of Wallets
In this article, we want to give you an overview of what types of wallets there are and help you find the right wallet for you.
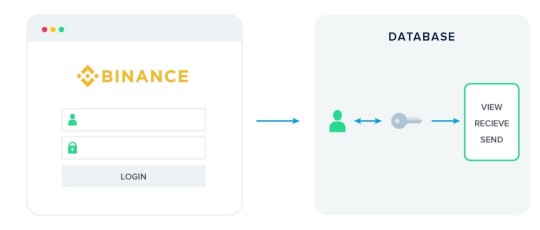
Hosted Web Wallets
We can distinguish between hosted and non-hosted web wallets. With hosted web wallets, your keys are stored online by a trusted third party. These parties are mostly exchanges such as Coinbase, Binance or Bittrex. When you create an account with these entities they will create an entry in their internal database linking your account to a set of key pairs for the different coins they have listed.
An advantage with a hosted web wallet is the option to recover your password in case you forget or misplace it. Losing your private keys (together with your mnemonic phrase) leads to a loss of funds in all other cases.
While this may sound reassuring, there are some drawbacks with hosted wallets (also called hot wallets/cloud wallets). Remember: if you don’t control your keys, you don’t control your funds. There is always a third party risk, no matter how trustworthy the party might seem. First, they are a more attractive target for hackers than individuals because their honeypot is much bigger. Second, a sudden change in regulation might not allow them to have you withdraw your funds in a worst-case scenario. It is unlikely, but definitely not impossible. Thirdly, there is always a chance of an entity going bankrupt or stealing money. With the major exchanges like the ones mentioned above this risk seems small, but it does exist. Just ask former Mt. Gox customers. For the reasons above we do advise everybody to store the keys to their funds themselves. This means storing them in a wallet where you have control over your private keys. There is a responsibility that comes with being in charge of the safety of your funds yourself, but enabling you to do this is one of the main motivations for the existence of cryptocurrencies!
You will need to keep some funds on an exchange permanently if you plan to trade often. If you want to do this right, then your level of expertise should be exceeding this article by far anyways.
Non-Hosted Web Wallets
Besides hosted web wallets there is also a range of non-hosted web wallets. The most popular non-hosted web wallet is likely MyEtherWallet, which can store Ether (ETH) and all ERC-20 tokens (tokens that are “living” on the Ethereum blockchain). Those wallets provide an interface to check your funds or create transactions in your web browser, but you have to provide the keys with each login.
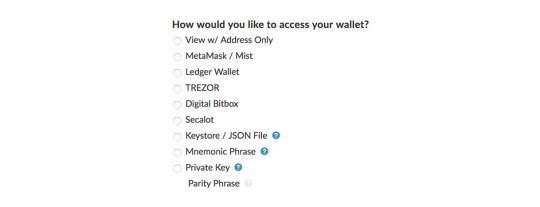
There is a range of options to access your wallet with MyEtherWallet (often abbreviated as MEW). The first option requires your address but only lets you view your funds.
MetaMask is a browser plugin that provides the option to make ETH payments within your browser and the ability to login to MEW. It also provides a function detecting phishing sites and warning you when you are about to open one. The next couple of options, Ledger Wallet, Trezor, Digital Bitbox, and Secalot are hardware wallets. We will get to those later in the article.
Accessing your wallet with a keystore /.json file is possible but not recommended. The file contains your private key and when you create your wallet you have the option to download it. If it gets into the wrong hands they will have access to your funds so saving it on your desktop is not the ideal solution. If you want to use this method, you should encrypt the .json file and store it on a separate device like a USB drive. To use it, connect the drive, decrypt the file, then select the file in your browser and voila. After that, you can disconnect your storage medium of choice again.
The last two options are more or less the same with regards to safety. You can either enter your private key directly or your mnemonic phrase (which yields your private key when hashed) which is both problematic if your machine is compromised.
In conclusion, a non-hosted web wallet is quite convenient and just as secure, as the method, you choose to provide your keys with.
Desktop and Mobile Wallets
If you start off with the question “where are your keys?” the desktop and mobile wallet will give you the same answer: on the device. Phones and tablets are more powerful than ever, the difference between a desktop and a mobile wallet is marginal. It is also arguable whether one is safer than the other.
By now you know the tasks a wallet performs: viewing, receiving and sending. If you want to use crypto for everyday transactions there is almost no way around keeping some funds in a mobile wallet. As mentioned before, when creating your wallet you will get a mnemonic phrase that you should keep safe. Usually, there is a PIN, password or Face-/Touch-ID protection to access the wallet. You should never keep more funds in a mobile wallet than you are willing to lose. It’s the same as with cash: you don’t carry around all your money in a wallet. You withdraw as much as you are comfortable handling in cash and keep the rest in your account (or under the mattress :P).
With desktop and mobile wallets, there is a choice between single- and multi-currency wallets. Those should be rather self-explanatory terms. The former allows you to store one coin, while the latter supports multiple currencies. Some of the more popular examples for desktop include Electrum and Exodus. For mobile, there are Mycelium or Paytomat to name just a few.



If you got your first coins on an exchange, I would recommend you to transfer your funds out of the exchange (hosted web wallet) onto a desktop, paper, or hardware wallet. Send a fraction first to make sure everything works as planned. If your first transaction works then you can send the rest. You are now protected from third-party risk, but have full responsibility for your funds yourself.
Paper Wallets
Grabbing our golden thread again and asking “where are the keys” give you a simple answer with a paper wallet: in your hand! A paper wallet is your public and private key pair printed on paper. Almost every cryptocurrency offers a paper wallet generator. To create a key pair you generally first have to create some entropy (a term for disorder), in other words: you want your keys to be as random as possible. This is mostly done automatically, but sometimes you will find features were you have to randomly move your mouse or hit keys on your keyboard to create randomness.
When printing your paper wallet you shouldn’t use a shared printer like the one in your office. In a best-case scenario, the printer doesn’t even have an internet connection. Printers usually keep a copy of the files they printed last, and an attacker might exploit this. You will end up with something looking like this after printing the wallet.

There is only one thing left to do: send your coins to the public key. After that, you have a perfect gift or long term storage for your coins. The main risk with a paper wallet is you actually losing or destroying the wallet by accident. If you don’t have a mnemonic phrase to recover the private key you are at risk of losing all funds on the wallet by accident. So choose wisely where to store your paper wallet. Print several copies if you feel uncomfortable having only one and store all of them in separate, safe places.
Hardware Wallets
Moving on to everybody’s darling: hardware wallets. With a hardware wallet, your keys are stored on the device in something called the “secure element”. The secure element is a place to store data (here, keys) that cannot be directly accessed by your computer or any other device even when it is connected. Although it does look like a simple USB drive, it can actually do a little more than just providing storage for your keys. To use a hardware wallet you usually have a few options of which interface to use with it. Like MyEtherWallet, a few other wallets offer hardware wallet support. Additionally, you have the native wallet apps provided by the producer. In the case of Ledger, for example, the native App is called Ledger Live.
How Does a Hardware Wallet Work?
The interface generates an address when you want to receive funds. Using this feature is pretty straightforward: if you click the receive button the process runs in the background and the address is displayed for you to share with the sender. If you want to send money the app creates the raw transaction that needs to be signed. The unsigned transaction is now sent to your hardware wallet, where it gets signed with your private key. The signature is then returned to your computer and the complete transaction including the signature broadcasted to the network.
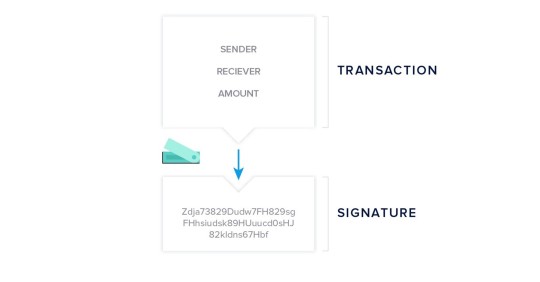
Your private key(s) do not leave the device, so they are not visible to the computer you are using your hardware wallet with at any time. This is why a hardware wallet is considered the most secure way of storing crypto, especially large amounts.
If your device ever breaks, you have your mnemonic phrase as a backup. At the risk of being repetitive: your mnemonic phrase, under all circumstances, must stay private and in a secure location. A copy at a trusted family member or in a bank vault might be a good idea in case of a fire, flooding or a playing dog.
Summary
There are many ways to store your cryptocurrencies. Usually, there is a trade-off between convenience and security. The most important question is: where are the keys? A wallet is only a piece of software, an interface, that helps you perform the basic functions of cryptocurrencies: view your balance, create an address to receive funds, and create transactions to send funds.
With a hosted online wallet you are trusting a third party to handle your keys. You have the option to recover your password if misplaced, but there is always a significant third-party risk. If you don’t control your keys, you don’t control your funds!
With desktop, mobile, paper or hardware wallets you own the keys and nobody but yourself is responsible for keeping them safe. If your device breaks you have a mnemonic/recovery phrase to recover access to your money. The menmonic phrase is as sensible as your private key itself and if it gets in the wrong hands, your money can be stolen. This is should not scare you, but make you cautious.
If you have questions and requests, ), leave comments below the article.
0 notes
Text
Adobe Flash Player Asking For Password Mac
Install the Adobe AIR Runtime. Steps to follow on Windows: 1. Go to C: Program Files (x86) Common Files Adobe AIR Versions 1.0. While holding the “Ctrl” key, select the Adobe AIR Application Installer.exe -> Right click on it -> Run as Administrator. Do not take your finger off the “ctrl” key until you see the window open up. A new malware by the name of Snake enters your Mac by asking you to install Adobe Flash Player. If your Mac asks to install Adobe Flash Player, it can possibly be a Malware. Malware for MacOS is dubbed as 'Snake' By. This virus asks for the administrator’s password. It’s normal because the original flash player by Adobe also. When version 10.3.181.14 of Adobe Flash Player was released it installed the Flash Player Settings Manager in Control Panel. Local Storage Settings can be managed through this console. There are three options Allow, Ask before using local storage and Block. Noooo it at one point caused 83% of mac crashes back on Mavericks DON'T INSTALL IT, anyway flash is going out of fashion and less people develop for it (I had to convert all my web-apps to HTML5 because the lack of interest in flash). Flash Player is alerting you that information might be shared between two sites and is asking if you want to allow or deny such access. In the question shown above, (site1) represents the name of the person or company who created the application that is trying to access another site, represented by (site2). There's yet another flaw in the Adobe Flash Player browser plugin that needs to be urgently patched. The good news is that Google Chrome, Microsoft Internet Explorer 10 and 11, and Microsoft Edge.
Enable Flash player in the TOR browser bundle on Mac (Macbook Pro or Macbook Air): You need to follow these steps, sometimes things get updated but the way is same, so you may need to exert some brain energy while doing the steps mentioned below, I can’t spoon feed you but I can guide you to achieve your purpose, if you still get confused then ask me in the comments. But if your only sole purpose is to play videos on the tor, then this method is safe and you can play your videos behind a college, work or office proxy. Browser for mac adobe flash player ipad.
This technote addresses the installation issue of Adobe AIR applications after 30th Oct 2017 that is signed with SHA1 certificate. It is applicable to both Windows and Mac.
Issue
When you install your AIR application, the installation fails with the below error. The error dialog is a generic installation failure message that could occur for various reasons. One of them is due to signature validation failure.
Who should use this solution?
If your developed AIR application fails to install after 30th Oct 2017.
Issue confirmation
Follow the steps below to verify if the signature validation failure is the cause of the installation failure:
Open the application installation logs. The location of the log files for different platforms is mentioned in the article: https://helpx.adobe.com/air/kb/logging-air-2-desktop-application.html
If the installation log contains the error: “Package signature validation failed”, it indicates that the application is signed with SHA1 certificate.
Set your system date to a date prior to 30th Oct 2017, and try to install the application again. Successful installation confirms that your application is impacted by the signature validation issue.
Solution
You will have to re-sign your Adobe AIR application. Follow the steps below to re-sign your application:
Rename your Adobe AIR application by changing its extension from .air to .zip. In case you don’t see the extension in the filename, enable the filename extension before renaming the application.
Extract the .zip file renamed in Step 1.
Go to the extracted folder and perform the following modifications (in the order specified):
Move xml present inside META-INFAIR folder to the root of the extracted folder.
Delete “META-INF” folder.
Delete “mimetype” file located in the root of the extracted folder.
Download the latest AIR SDK for your platform from http://www.adobe.com/devnet/air/air-sdk-download.html.
Locate the AIR SDK archive file downloaded in Step 4 and extract the AIR SDK Compiler (if on Windows) or mount the AIR SDK Compiler dmg (if on Mac).
Open the command prompt and change the current working directory to the root directory of the extracted AIR application directory.
Use the command below to re-package the AIR application with a new certificate:
<AIR_SDK_compiler_path>binadt -package -storetype pkcs12 -keystore <app_signing_certficate_path> myApp.air application.xml .
Command line parameters:
AIR_SDK_compiler_path – Location of AIR SDK compiler extracted or mounted in Step 5.
app_signing_certficate_path – Fully qualified path of your application signing certificate. Make sure you are using SHA256 certificate.
myApp.air – Name of the application to be packaged.
application.xml – The file that was moved in Step 3.A
When prompted, enter the password of your application signing certificate.
Note: Do not ignore the . (dot) at the end of the packaging command above. It is used to package all the resources present in your existing application. For more details on packaging AIR applications, refer https://help.adobe.com/en_US/air/build/WS901d38e593cd1bac1e63e3d128cdca935b-8000.html.
Workaround
AIR applications with the above-mentioned issue can be installed using two methods.
Using keyboard shortcuts:
Install the Adobe AIR Runtime
Steps to follow on Windows:
1. Go to C:Program Files (x86)Common FilesAdobe AIRVersions1.0 Adobe flash player free download.
Is adobe flash player dangerous for mac. Snake has to be welcomed into your operating system by you. There isn't someone shooting corrupted files through your ethernet cable directly into your software.
Adobe Flash Player Asking For Password Mac
2. While holding the “Ctrl” key, select the Adobe AIR Application Installer.exe -> Right click on it -> Run as Administrator. Do not take your finger off the “ctrl” key until you see the window open up.
3. Select and open the AIR application to be installed.
Steps to follow on Mac:
1. Go to /Applications/Utilities
2. While holding the “command” key, double click on the Adobe AIR Application Installer. Do not take your finger off the “command” key until you see the window open up.
3. Select and open the AIR application to be installed.
The Adobe AIR Application should be installed successfully.
Using the new -ignoreExpiredCertificateTimestamp directive while launching AIR Application installer using Command Prompt/Terminal
Install the Adobe AIR Runtime
Steps to follow on Windows:
1. Open a command prompt as Administrator.
2. Run the following command:
“C:Program Files (x86)Common FilesAdobe AIRVersions1.0Adobe AIR Application Installer.exe” – ignoreExpiredCertificateTimestamp
3. Window opens up.
4. Select and open the AIR application to be installed.
Steps to follow on Mac:
1. Open Terminal.
2. Run the following command:
/Applications/Utilities/Adobe AIR Application Installer.app/Contents/MacOS/Adobe AIR Application Installer/ -ignoreExpiredCertificateTimestamp
3. Window opens up.
4. Select the AIR application to be installed.
Adobe AIR Applications gets installed successfully.
Lesson 14: Should I Still Use Adobe Flash Player?
Adobe Flash Player Asking For Password
/en/internetsafety/driving-safely-with-mobile-devices/content/
Should I still use Adobe Flash Player?
Whenever you use the Internet, your browser uses small applications called plug-ins to display certain types of content. For example, the Adobe Flash Player plug-in can be used to play videos, games, and other interactive content. Although Flash Player has long been one of the most well-known plug-ins, it has become much less popular in recent years.
There are a few reasons for this decline in popularity. Because Flash Player is a relatively old plug-in, it has become increasingly vulnerable to online threats like viruses and hackers. Most web browsers have even started disabling Flash Player content by default for security reasons.
Also, because Flash Player was designed for desktop computers, it's not very good at displaying content on mobile devices, including smartphones and tablets. Some mobile browsers, including Safari for iOS, can't even use Flash Player.

Should I stop using it?
Although you don't need to completely stop using Flash Player, you should use caution. Most browsers have an Ask to Activate or Ask First setting for Flash, which we recommend using. This keeps Flash disabled most of the time, but it gives you the option to temporarily enable it when you're on a site that you know and trust.
Keeping Flash Player up to date
Because older versions of Flash are vulnerable to online threats, you'll want to make sure you're always using the most recent version. If you're not running the most recent version, you might see an error message instead of your content.
However, we don't recommend updating the plug-in directly from a warning message like this. Some misleading advertisements are cleverly disguised as warning messages, but they won't actually take you to an update page. That's why it's best to download the update directly from the Adobe website.
It's also worth pointing out that some browsers update all of your plug-ins automatically, including Flash Player. If you're using a browser like Internet Explorer, you'll probably need to update your plug-ins manually.
Adobe flash player 10 1 download free download - Adobe Flash Player, Macromedia Flash Player Uninstaller, and many more programs. Best Video Software for the Mac. Download free Adobe Flash Player software for your Windows, Mac OS, and Unix-based devices to enjoy stunning audio/video playback, and exciting gameplay. Mar 22, 2015 Re: Can't install Flash player on Mac 10.10.1 Lexilix Mar 22, 2015 7:37 PM ( in response to martinaio ) Had the same problem (stalling at 25% or 30%). Adobe flash player for mac 10.10.1. Flash is the standard for engaging PC experiences – 99% of PCs worldwide have Flash Player installed and 85% of the top 100 websites use Flash. Approximately 75% of online videos are viewed and 70% of web games are delivered using Adobe Flash technology.
How to update Adobe Flash player:
Navigate to https://get.adobe.com/flashplayer/ in your web browser.
Locate and select the Download or Install button. Flash Player may also try to install additional software, so be sure to deselect any offers like this before downloading. In the image below, we've deselected the McAfee Security Scan Plus option.
Locate and double-click the installation file (it will usually be in your Downloads folder). Note that you'll need to close your web browser before you can install the plug-in.
Follow the instructions that appear. Flash Player will be updated to the most recent version.
In many cases, your browser will open automatically to a new page to confirm the installation. This means the plug-in is ready to use whenever you need it.
0 notes
Text
Download Java MSI

Download Java MSI. Java logo 512x512 for Microsoft EndPoint Configuration Manager (SCCM/MECM/MEMCM) deployments:

Java 8.0.2510.8
TLS Application-Layer Protocol Negotiation Extension JEP 244 has enhanced the Java Secure Socket Extension (JSSE) to provide support for the TLS Application-Layer Protocol Negotiation Extension (RFC 7301). New methods have been added to the javax.net.ssl classes SSLEngine, SSLSocket, and SSLParameters to allow clients and servers to negotiate an application layer value as part of the TLS handshake. Added Support for PKCS#1 v2.2 Algorithms Including RSASSA-PSS Signature The SunRsaSign and SunJCE providers have been enhanced with support for more algorithms defined in PKCS#1 v2.2, such as RSASSA-PSS signature and OAEP using FIPS 180-4 digest algorithms. New constructors and methods have been added to relevant JCA/JCE classes under the java.security.spec and javax.crypto.spec packages for supporting additional RSASSA-PSS parameters. WebEngine Limits JavaScript Method Calls for Certain Classes JavaScript programs that are run in the context of a web page loaded by WebEngine can communicate with Java objects passed from the application to the JavaScript program. JavaScript programs that reference java.lang.Class objects are now limited to the following methods:getCanonicalName getEnumConstants getFields getMethods getName getPackageName getSimpleName getSuperclass getTypeName getTypeParameters isAssignableFrom isArray isEnum isInstance isInterface isLocalClass isMemberClass isPrimitive isSynthetic toGenericString toString No methods can be called on the following classes:java.lang.ClassLoader java.lang.Module java.lang.Runtime java.lang.System java.lang.invoke.* java.lang.module.* java.lang.reflect.* java.security.* sun.misc.* New Oracle Specific JDK 8 Updates System Property to Fallback to Legacy Base64 Encoding Format Oracle JDK 8u231 upgraded the Apache Santuario libraries to v2.1.3. This upgrade introduced an issue where XML signature using Base64 encoding resulted in appending or to the encoded output. This behavioral change was made in the Apache Santuario codebase to comply with RFC 2045. The Santuario team has adopted a position of keeping their libraries compliant with RFC 2045. Oracle JDK 8u221 using the legacy encoder returns encoded data in a format without or . Therefore, a new Oracle JDK 8 Updates only system property, - com.sun.org.apache.xml.internal.security.lineFeedOnly, is made available to fall back to legacy Base64 encoded format. Users can set this flag in one of two ways: -Dcom.sun.org.apache.xml.internal.security.lineFeedOnly=trueSystem.setProperty("com.sun.org.apache.xml.internal.security.lineFeedOnly", "true") This new system property is disabled by default. It has no effect on default behavior nor when com.sun.org.apache.xml.internal.security.ignoreLineBreaks property is set. Later JDK family versions might only support the recommended property: com.sun.org.apache.xml.internal.security.ignoreLineBreaks x86 msiexec.exe /i "jre1.8.0_251.msi"/qn JU=0 JAVAUPDATE=0 AUTOUPDATECHECK=0 RebootYesNo=No WEB_JAVA=1 x64 msiexec.exe /i "jre1.8.0_25164.msi" /qn JU=0 JAVAUPDATE=0 AUTOUPDATECHECK=0 RebootYesNo=No WEB_JAVA=1 REMOVEOLDERJRES=1 For uninstall use: x86 msiexec /x {26A24AE4-039D-4CA4-87B4-2F32180251F0} /qn /norestart x64 msiexec /x {26A24AE4-039D-4CA4-87B4-2F64180251F0} /qn /norestart Java MSI x86 download Java MSI x64 download
Java MSI 8.0.2410.7
Release Highlights IANA Data 2019c JDK 8u241 contains IANA time zone data version 2019c. New Feature: Allow SASL Mechanisms to Be Restricted A security property named jdk.sasl.disabledMechanisms has been added that can be used to disable SASL mechanisms. Any disabled mechanism will be ignored if it is specified in the mechanisms argument of Sasl.createSaslClient or the mechanism argument of Sasl.createSaslServer. The default value for this security property is empty, which means that no mechanisms are disabled out-of-the-box. New Feature: SunPKCS11 Provider Upgraded with Support for PKCS#11 v2.40 The SunPKCS11 provider has been updated with support for PKCS#11 v2.40. This version adds support for more algorithms such as the AES/GCM/NoPadding cipher, DSA signatures using SHA-2 family of message digests, and RSASSA-PSS signatures when the corresponding PKCS11 mechanisms are supported by the underlying PKCS11 library. Other notes: New Checks on Trust Anchor Certificates New checks have been added to ensure that trust anchors are CA certificates and contain proper extensions. Trust anchors are used to validate certificate chains used in TLS and signed code. Trust anchor certificates must include a Basic Constraints extension with the cA field set to true. Also, if they include a Key Usage extension, the keyCertSign bit must be set. Other notes: Exact Match Required for Trusted TLS Server Certificate A TLS server certificate must be an exact match of a trusted certificate on the client in order for it to be trusted when establishing a TLS connection. Other notes: Added LuxTrust Global Root 2 Certificate LuxTrust root certificate has been added to the cacerts truststore Other notes: Added 4 Amazon Root CA Certificates Amazon root certificate has been added to the cacerts truststore Bug Fixes: Support for OpenType CFF Fonts Previously, Oracle JDK 8 did not include OpenType CFF fonts (.otf fonts) into the standard logical fonts (such as "Dialog" and "SansSerif"). This resulted in missing glyphs when rendering text. In the most extreme cases where only CFF fonts were installed on the system, a Java exception could be thrown. Several Linux distributions were affected by this issue because they rely on CFF fonts to support some languages, which is common for CJK (Chinese, Japanese, and Korean) languages. Oracle JDK 8 now uses these CFF fonts, and this issue has been resolved. Bug Fixes: Better Serial Filter Handling The jdk.serialFilter system property can only be set on the command line. If the filter has not been set on the command line, it can be set can be set with java.io.ObjectInputFilter.Config.setSerialFilter. Setting the jdk.serialFilter with java.lang.System.setProperty has no effect. For Configuration Manager deployments (or another authomated deployments) use: x86 msiexec.exe /i "jre1.8.0_241.msi"/qn JU=0 JAVAUPDATE=0 AUTOUPDATECHECK=0 RebootYesNo=No WEB_JAVA=1 x64 msiexec.exe /i "jre1.8.0_24164.msi" /qn JU=0 JAVAUPDATE=0 AUTOUPDATECHECK=0 RebootYesNo=No WEB_JAVA=1 REMOVEOLDERJRES=1 For uninstall use: x86 msiexec /x {26A24AE4-039D-4CA4-87B4-2F32180241F0} /qn /norestart x64 msiexec /x {26A24AE4-039D-4CA4-87B4-2F64180241F0} /qn /norestart Java MSI x86 download Java MSI x64 download
Java MSI 8.0.2310.11
Release Highlights IANA Data 2019b JDK 8u231 contains IANA time zone data version 2019b. For more information, refer to Timezone Data Versions in the JRE Software. New Feature: New jdk.jceks.iterationCount System Property A new system property has been introduced to control the iteration count value used for the jceks keystore. The default value remains at 200000 but values between 10000 and 5000000 may be specified. The new system property name is jdk.jceks.iterationCount and the value supplied should be an integer in the accepted range. The default value will be used if a parsing error is encountered.New Feature: New Java Flight Recorder (JFR) Security Events Four new JFR events have been added to the security library area. These events are disabled by default and can be enabled via the JFR configuration files or via standard JFR options.Removed Features and Options: Removal of T2K Rasterizer and ICU Layout Engine From JavaFX. The T2K rasterizer and ICU layout engine have been removed from JavaFX.Other notes: GTK3 Is Now the Default on Linux/Unix. Newer versions of Linux, Solaris, and other Unix flavor desktop environments use GTK3, while still supporting GTK2. Previously, the JDK would default to loading the older GTK2 libraries. However, in this release, it defaults to loading GTK3 libraries. Loading is typically triggered by using the Swing GTK Look And Feel. The old behavior can be restored by using the system property: -Djdk.gtk.version=2.2Other notes: Remove Obsolete NIST EC Curves from the Default TLS Algorithms. This change removes obsolete NIST EC curves from the default Named Groups used during TLS negotiation. The curves removed are sect283k1, sect283r1, sect409k1, sect409r1, sect571k1, sect571r1, and secp256k1. To re-enable these curves, use the jdk.tls.namedGroups system property. The property contains a comma-separated list within quotation marks of enabled named groups in preference order.For example: java -Djdk.tls.namedGroups="secp256r1, secp384r1, secp521r1, sect283k1, sect283r1, sect409k1, sect409r1, sect571k1, sect571r1, secp256k1" ... For System Center Configuration Manager deployments (or another authomated deployments) use: x86 msiexec.exe /i "jre1.8.0_231.msi"/qn JU=0 JAVAUPDATE=0 AUTOUPDATECHECK=0 RebootYesNo=No WEB_JAVA=1 x64 msiexec.exe /i "jre1.8.0_23164.msi" /qn JU=0 JAVAUPDATE=0 AUTOUPDATECHECK=0 RebootYesNo=No WEB_JAVA=1 REMOVEOLDERJRES=1 For uninstall use: x86 msiexec /x {26A24AE4-039D-4CA4-87B4-2F32180231F0} /qn /norestart x64 msiexec /x {26A24AE4-039D-4CA4-87B4-2F64180231F0} /qn /norestart Java MSI x86 download Java MSI x64 download Read the full article
#Java#MECM#MEMCM#MicrosoftEndpointConfigurationManager#MSI#SystemCenter#SystemCenterConfigurationManager#Windows#Windows10
0 notes
Text
Know more about Samsung Blockchain in details

Know more about Samsung Blockchain in details
Samsung Blockchain SDK, which will be discharged inside this year, carries engineers and customers to the blockchain world by giving a full arrangement of capacities that the Decentralized App (DApp) or Blockchain App needs. The SDK encourages engineers to oversee blockchain accounts effectively and to make an exchange simpler by preoccupied exchange APIs for each sort of coins. The SDK offers an installment portal for cryptographic money settlement with its UI. To utilize this installment arrangement, DApp needs an equipment wallet. With this, Samsung Blockchain SDK joins clients not exclusively to the Samsung KeyStore yet additionally to some other outer cold wallets also.

Know more about Samsung Blockchain in details Features can be changed without notice at the season of Samsung Blockchain SDK last revelation (connected all through the whole this record) Read about Vedanta, YES Bank, MonetaGo use blockchain to digitally issue CP in Asia The Samsung Blockchain SDK allows: Generation, storage, management of accounts Restore all valid accounts following BIP-44 and BIP-32 The facilitation of a payment activity showing information to be signed and ensuring that authorization of digital signatures for purchases is done by secured cold wallet with the internal hardware wallet interface of Blockchain SDK. Enablement of cold wallets like Samsung KeyStore or other external cold wallets. (Currently 1 device is allowed at an instance) Creation of transaction and returning the result of transfer to a blockchain node (tx ID) Developers’ mode: set your own HD path and restore customized HD-wallet, get/set RPC
Know more about Samsung Blockchain in details
In the event that you are a band together with Samsung, the extra highlights are accessible: Blockchain specific program (Android WebView supplier) for web DApps; Samsung Blockchain SDK gets blockchain exchange and popups an installment sheet The help of getting exchange history by Samsung Blockchain Proxy Node's off the chain database Presently, there are 2 sorts of SDKs: Samsung Blockchain SDK and Samsung Blockchain KeyStore SDK. Samsung Blockchain SDK incorporates a large portion of sub-SDKs' capacities and will be discharged before the finish of 2019. In the mean time, Samsung Blockchain KeyStore SDK is centered around key stockpiling and it is accessible at this point. Read about Kakao Blockchain is 15x faster than Ethereum Read the full article
0 notes
Link
On Wednesday, Feb. 20, the mobile phone manufacturing giant Samsung Electronics released its flagship smartphone, the Galaxy S10. Crypto enthusiasts will be pleased to hear that the new phone comes with the company’s proprietary Samsung Knox security system which stores blockchain-based private keys.
Also Read: This ‘Faketoshi’ Signature Tool Lets Anyone Become Satoshi Nakamoto
Galaxy S10 Houses Private Keys
The relationship between Samsung and cryptocurrencies is official as the firm has released its latest Galaxy series that comes with a security system specifically designed to house digital currencies. This Wednesday, the South Korean electronics manufacturer announced the launch of the new Galaxy S10s which will be available in stores and online on March 8 throughout select markets. The smartphone is the first HDR10+ certified device, offers access to next-generation Wi-Fi 6 and features an Exynos 9820 chip. But cryptocurrency enthusiasts will be very pleased to hear that the phone will come with pre-installed hardware called Samsung Knox which is aimed at protecting blockchain assets.
“The Galaxy S10 is built with defense-grade Samsung Knox, as well as secure storage backed by hardware, which houses your private keys for blockchain-enabled mobile services,” explains the firm’s announcement.
Samsung Galaxy S10 series. The company has also introduced a foldable phone which will likely support Samsung’s Knox security.
Samsung had tried to keep the cryptocurrency focused hardware system under the radar for months, but had problems with leaks. For instance, on Dec. 19, a Norwegian television station unintentionally aired the smartphone’s first commercial. Then on Jan. 27, leaked photos had shown images of the ‘Samsung Blockchain Keystore,’ which reportedly will start off by supporting ethereum (ETH) and bitcoin core (BTC). Samsung had previously filed for a smartphone crypto wallet trademark on Dec. 28, 2018. The “Samsung Crypto Wallet,” trademark UK00003363431 explains the wallet is meant for smartphones, tablets, portable computers, and other types of devices. The software is for “use as a cryptocurrency wallet for cryptocurrency transfers and payments using distributed ledger technology,” the trademark details.
Leaked photographs of Samsung’s Blockchain Keystore.
Samsung Follows the Blockchain Phone Trend
The company’s trademark Samsung Knox mobile security solution is meant for securing important data like passwords and private keys. The Knox website emphasizes that individuals and organizations use smartphones every day for banking and accessing business information. Knox is meant to protect that data if it falls into the wrong hands the company claims. Interestingly, Samsung’s security software has a white paper that says Knox is used widely throughout industries such as government, finance and healthcare.
Samsung’s entry into the blockchain space follows the smartphone giant HTC and the first cryptocurrency-centric smartphone called Exodus. Then there’s Sirin Labs’ Finney phone being sold at the company’s flagship store in London for $999. Samsung also released the Galaxy Fold this week which may have the built-in Samsung Blockchain Keystore and can fold in half.
What do you think about the new Galaxy series which houses private keys for blockchain-enabled mobile services? Let us know what you think about this subject in the comments section below.
Image credits: Samsung, and Twitter.
At news.Bitcoin.com all comments containing links are automatically held up for moderation in the Disqus system. That means an editor has to take a look at the comment to approve it. This is due to the many, repetitive, spam and scam links people post under our articles. We do not censor any comment content based on politics or personal opinions. So, please be patient. Your comment will be published.
Tags in this story
Bitcoin, Blockchain, Blockchain Assets, Blockchain Phones, blockchain-enabled mobile services, Cryptocurrency, Digital Assets, electronics, Ethereum, Finney Phone, HTC, N-Featured, private keys, Samsung, Samsung Galaxy, Samsung Knox, Siren Labs, smartphones, South Korea
Jamie Redman
Jamie Redman is a financial tech journalist living in Florida. Redman has been an active member of the cryptocurrency community since 2011. He has a passion for Bitcoin, open source code, and decentralized applications. Redman has written thousands of articles for news.Bitcoin.com about the disruptive protocols emerging today.
(function(d, s, id) { var js, fjs = d.getElementsByTagName(s)[0]; if (d.getElementById(id)) return; js = d.createElement(s); js.id = id; js.src = 'https://connect.facebook.net/en_US/sdk.js#xfbml=1&version=v3.2'; fjs.parentNode.insertBefore(js, fjs); }(document, 'script', 'facebook-jssdk'));
0 notes
Text
Ontology [ONT] released its desktop wallet, OWallet v0.8.1; supports Windows and Mac
On 8th August, Ontology, on their official Twitter handle announced the release of their official desktop wallet, OWallet v0.8.1. They also mentioned that the wallet supports both Windows and Mac operating systems as well.
Ontology’s tweet | Source: Twitter
According to Ontology’s document, the OWallet v0.8.1 is composed of three separate wallets, each performing a particular function. They are:
Individual Wallet
Shared Wallet
Ledger Wallet
Firstly, the Individual wallet in the OWallet application is an essential wallet that users can access which only requires a signature to verify or validate a transaction. This wallet’s user interface composes of all the necessary information regarding the transactions on the Ontology Mainnet.
The Individual wallet also performs other functions like designing a new wallet, importing and exporting the wallet, claiming ONG, and, sending and receiving assets.
The second type of wallet being the Shared wallet, enables more than one client or user to access the funds but it requires multiple signatures in order to verify the transaction. In this case, when the wallet is designed, a set of ‘copayers’ are provided with similar keys to access the shared wallet. These users are at complete liberty to set the rules for their transaction using the wallet.
Additionally, the user interface of this wallet will include ONG and ONT balances and its prices in USD, the name of all the participant, their wallet addresses, a complete set of transaction information as well as send and receive operations.
Finally, the Ledger wallet provides an option that enables a user to switch between the MainNet and TestNet, choose a language, Chinese or English and also to select a location upon which, they can save the keystore. But, this is only possible if the users first import Ledger onto their OWallet.
A Twitterati named Asif replied to this announcement saying:
“Man you guys r seriously building a solid foundation. Where did this experience come from? Mainland Chinese government? Mmmm”
Another Twitterati had another view regarding this news:
“It’s awful. Still have to download a desktop program when using ledger. Windows 10 thinks it’s a virus!!”
However, the OWallet v0.8.1 does not support NEP-5 ONT token swap.
The post Ontology [ONT] released its desktop wallet, OWallet v0.8.1; supports Windows and Mac appeared first on AMBCrypto.
Ontology [ONT] released its desktop wallet, OWallet v0.8.1; supports Windows and Mac published first on https://medium.com/@smartoptions
0 notes
Text
Generate JKS KeyStore From Existing Keystore & Use it in Android Apps
Generate JKS KeyStore From Existing Keystore & Use it in Android Apps
Note: This tutorial only works when you already have a keystore.
Go to the location where your keystores are; or open CMD, use cd [path to the keystore(s)] to go to the location.
In this folder, on the CMD, or Gitbash, or other Terminals, type following command (for keytool.exe, see Facebook API: Key Hash for Android App):
"C:\Program Files (x86)\Java\jre1.8.0_251\bin\keytool" -importkeystore…
View On WordPress
0 notes
Text
App Hash Key Helper extension for Xamarin Android apps!
App Hash Key Helper extension for Xamarin Android apps!
Remember my last post “Generating App Hash key for SMS Retriever API for (Xamarin incl.)…” where I shared with you guys how to successfully generating the App hash key in both MacOs and Windows environments without any hassle?
Now this is the next step of it! making the whole process much easier specially for Xamarin Android development!
Previously…
So earlier we looked at how we could generate…
View On WordPress
#Android#App Hash key#AppSignatureHelper#Hash String#Helper Class#Hex Signature#Keystore#Keytool#MacOS#SMS Retriever API#Visual Studio#Windows#Xamarin Android
0 notes
Link
みなさんこんにちは。今��です。 今年のDreamforceではmyシリーズとしていくつかの重要な発表がありましたが、今回の記事ではmyIoTを裏で支えるPlatformEventについてサンプルアプリの開発を通じて触れてみたいと思います。(myIoTではデバイスなどからのストリームデータの受け口としてPlatformEventが使われます。) PlatformEventはSummer’17でGAになった比較的新しい機能です。これまでSalesforceから外部システムとのインテグレーションには、Outbound Message、Apex Callout、Streaming API、あるいは外部システムからSOAPやRest APIなどを使って定期的にポーリングするなどで行われてきました。各々の手段には、起動条件の柔軟性/ファイアーウォールを超えたアクセス/耐障害性/実行の効率性/負荷の分散性など、それぞれメリット・デメリットがありました。PlatformEventはMQ(Message Queueing)方式によるシステム統合が行える新たな手段として注目できます。 サンプルアプリのシナリオ Salesforceと外部システム間で注文データを連携させるシナリオとします。Salesforceには注文カスタムオブジェクトがあり、注文カスタムオブジェクトにはステータスを持っています。このステータスが「出荷依頼」となった時、ApexトリガでメッセージをPublishします。外部システムはJavaで実装し、「出荷依頼」となったメッセージがほぼリアルタイムにSubscirbeできることを確認します。 Salesforce側のカスタマイズと開発 プラットフォー��イベントにメッセージをPublishするための設定と開発には新たな作法などなく、これまでの知見で対応できます。Publishにはプロセスビルダーも使用することが出来ますが、今回はApexトリガで行います。 ①注文ヘッダオブジェクトの作成 オブジェクト定義 設定項目 設定値 オブジェクト名 注文 API参照名 DemoOrder__c レコード名 注文No. データ型 自動採番 表示形式 {00000000} カスタム項目 項目名 API参照名 データ型 設定値 ステータス Status__c 選択リスト 受注,出荷依頼,出荷済み,請求依頼,請求済み プラットフォームイベント プラットフォームイベント定義 設定項目 設定値 オブジェクト名 注文イベント API参照名 DemoOrderEvent__e カスタム項目 項目名 API参照名 データ型 設定値 注文No. OrderNumber__c テキスト(255) Apexトリガで注文オブジェクトの注文No.を設定 ステータス Status__c テキスト(255) Apexトリガで注文オブジェクトのステータスを設定 ③Apexトリガの作成 ApexトリガのAPIバージョンは40.0以上を指定 (); for(DemoOrder__c od : Trigger.new){ if(!String.isEmpty(od.Status__c) && od.Status__c == '出荷依頼'){ DemoOrderEvent__e ev = new DemoOrderEvent__e(); ev.OrderNumber__c = od.Name; ev.Status__c = od.Status__c; events.add(ev); } } if(!events.isEmpty()){ EventBus.publish(events); } } DemoOrderTrigger.trigger 証明書の作成&接続アプリケーション設定 JavaアプリからSalesforceのプラットフォームイベントをSubscribeする上でアクセストークンが必要になります。今回のサンプルアプリでは OAuth 2.0 JWT Bearer Token Flow を使用してアクセストークンを取得することにします。 ①自己署名証書の作成とエクスポート サンプルなのでいわゆるオレオレ証明書を作成します。作成にはJavaに付属するkeytoolを使用します。 1. 鍵の生成のコマンド #!/bin/sh keytool -genkeypair -alias keystore -keyalg RSA -keysize 2048 -keystore keystore.jks -storetype JKS -validity 90 -keypass keypassword -storepass storepassword genkey.sh #!/bin/sh keytool -v -export -file mycert.cer -keystore keystore.jks -storepass storepassword -alias keystore export.sh 新規接続アプリケーション 設定項目 設定値 接続アプリケーション名 OAuth JWT Sample API参照名 OAuth_JWT_Sample 取引先責任者メール 任意のメールアドレス OAuth設定の有効化 チェック デバイスフローで有効化 ※1 チェック コールバックURL ※2 https://login.salesforce.com/services/oauth2/success デジタル署名を使用 チェック ファイルを選択 手順2でエクスポートした証明書ファイルを選択(ex. mycert.cer) 選択したOAuth範囲 データへのアクセスと管理(api)、基本情報へのアクセス(id, profile, email, address, phone) ※1: チェックするとコールバックURLにデフォルト値が設定されるため便宜上チェックしています ※2: コールバックは行いませんが設定が必須のため設定します 接続アプリケーションの設定を保存し、詳細ページに表示されるコンシュマ��鍵の値を控えておきます。続いてOAuthポリシーの設定を行うため、Manageボタンをクリックします。 OAuthポリシーセクションの許可されているユーザの設定値を「管理者が承認したユーザは事前承認済み」を選択します。さらに、この接続アプリケーションを使用できるプロファイルの割り当てを行います。今回は「システム管理者」を選択します。この設定によりJWTを使用してパスワードを使うことなくアクセストークンが取得できるようになります。 Javaアプリ開発(Subscriber) PlatformEventからメッセージをSubscribeするためにはCometDなどを使って行います。また、Salesforceへの接続にはアクセストークンが必要となるため、トークンの取得にはJWTを使って行うことにします。 CometDを使った実装としては、EMP-Connectorが提供されています。実開発ではこちらをベースに開発するのが良いと思いますが、今回はより簡易な実装サンプルとして開発を進めたいと思います。 Mavenプロジェクトの作成&pom.xmlの編集 サンプルでは”consumerexample”というプロジェクト名でMavenプロジェクトを作成し、pom.xmlを以下のように記述します。依存関係として、"jackson-databind"を使いJSONの解析しJavaのオブジェクトへバインド、"cometd-java-client"を使ってCometDクライアントの実装を行います。 <project xmlns="http://maven.apache.org/POM/4.0.0" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation="http://maven.apache.org/POM/4.0.0 http://maven.apache.org/xsd/maven-4.0.0.xsd" 4.0.0 com.gmail.jimaoka.platformevent consumerexample 0.0.1-SNAPSHOT jar consumerexample http://maven.apache.org UTF-8 junit junit 3.8.1 test com.fasterxml.jackson.core jackson-databind 2.9.2 org.cometd.java cometd-java-client 3.1.2 pom.xml クラス作成 以下のクラスを作成します。 クラス名 説明 App.java Mainクラス OAuthService.java OAuth2 Bearer token flowで認証を行うクラス OAuthResponse.java Salesforceからレスポンスされるアクセストークンなどを保持するクラス PlatformEventService.java SalesforceのPlatformEventをSubscribeするクラス App.java Mainクラスです。1.JWT Beare Tokenを作成、 2. OAuth2.0で認証、3. PlatformEventのSubscribeを開始を行います。 package com.gmail.jimaoka.platformevent.consumerexample; import com.gmail.jimaoka.platformevent.consumerexample.client.PlatformEventService; import com.gmail.jimaoka.platformevent.consumerexample.oauth.OAuthResponse; import com.gmail.jimaoka.platformevent.consumerexample.oauth.OAuthService; public class App { public static void main( String[] args ){ OAuthService oauthService = new OAuthService(); try { String jwtBeareToken = oauthService.getJWTBeareToken(); System.out.println("jwtBeareToken:" + jwtBeareToken); OAuthResponse oauthResponse = oauthService.getOAuthResponse(jwtBeareToken); System.out.println("access_token:" + oauthResponse.getAccess_token()); PlatformEventService pevService = new PlatformEventService(oauthResponse.getInstance_url(), oauthResponse.getAccess_token()); pevService.start(); } catch (Exception e) { System.out.println("exception"); e.printStackTrace(); } } } App.java OAuthService.java JWT Beare tokenの作成、 Salesforceに対して認証を行いレスポンスされるアクセストークン等をJavaオブジェクトに設定します。 package com.gmail.jimaoka.platformevent.consumerexample.oauth; import java.io.FileInputStream; import java.io.FileNotFoundException; import java.io.IOException; import java.security.InvalidKeyException; import java.security.KeyStore; import java.security.KeyStoreException; import java.security.NoSuchAlgorithmException; import java.security.PrivateKey; import java.security.Signature; import java.security.SignatureException; import java.security.UnrecoverableKeyException; import java.security.cert.CertificateException; import java.text.MessageFormat; import java.util.Base64; import org.eclipse.jetty.client.HttpClient; import org.eclipse.jetty.client.api.ContentResponse; import org.eclipse.jetty.util.ssl.SslContextFactory; import com.fasterxml.jackson.databind.ObjectMapper; public class OAuthService { private static final String END_POINT = "https://login.salesforce.com/services/oauth2/token"; private static final String AUDIENCE = "https://login.salesforce.com"; // 接続アプリケーションのコンシュマー鍵の値を設定 private static final String CLIENT_ID = "3MVG9yZ.WNe6byQCanC7xsqg81Nfl068RgH1FBkktUix_dgDHv2wRVxxxxxxxxxxxxx"; private static final String GRANT_TYPE = "urn:ietf:params:oauth:grant-type:jwt-bearer"; public String getJWTBeareToken() throws KeyStoreException, NoSuchAlgorithmException, CertificateException, FileNotFoundException, IOException, UnrecoverableKeyException, InvalidKeyException, SignatureException{ String header = "{\"alg\":\"RS256\"}"; String claimTemplate = "'{'\"iss\": \"{0}\", \"sub\": \"{1}\", \"aud\": \"{2}\", \"exp\": \"{3}\"'}'"; StringBuffer token = new StringBuffer(); token.append(Base64.getUrlEncoder().encodeToString(header.getBytes("UTF-8"))); token.append("."); String[] claimArray = new String[4]; claimArray[0] = CLIENT_ID; // 認証を行うSalesforceユーザID claimArray[1] = "[email protected]"; claimArray[2] = AUDIENCE; claimArray[3] = Long.toString((System.currentTimeMillis() / 1000) + 300); MessageFormat claims = new MessageFormat(claimTemplate); String payload = claims.format(claimArray); token.append(Base64.getUrlEncoder().encodeToString(payload.getBytes("UTF-8"))); KeyStore keystore = KeyStore.getInstance("JKS"); // 鍵のパス keystore.load(new FileInputStream("./keystore/keystore.jks"), "storepassword".toCharArray()); PrivateKey privateKey = (PrivateKey)keystore.getKey("keystore", "keypassword".toCharArray()); Signature signature = Signature.getInstance("SHA256withRSA"); signature.initSign(privateKey); signature.update(token.toString().getBytes("UTF-8")); String signedPayload = Base64.getUrlEncoder().encodeToString(signature.sign()); token.append("."); token.append(signedPayload); return token.toString(); } public OAuthResponse getOAuthResponse(String jwtBeareToken) throws Exception { SslContextFactory sslContextFactory = new SslContextFactory(); HttpClient httpClient = new HttpClient(sslContextFactory); httpClient.start(); ContentResponse response = httpClient.POST(END_POINT) .param("grant_type", GRANT_TYPE) .param("assertion", jwtBeareToken) .send(); httpClient.stop(); ObjectMapper objectMapper = new ObjectMapper(); OAuthResponse oauthResponse = objectMapper.readValue(response.getContentAsString(), OAuthResponse.class); return oauthResponse; } public OAuthResponse getOAuthResponse() throws Exception { return getOAuthResponse(getJWTBeareToken()); } } OAuthService.java OAuthResponse.java Salesforceからレスポンスされるアクセストークン、インスタンスURLなどの情報を保持するためのクラスです。 package com.gmail.jimaoka.platformevent.consumerexample.oauth; public class OAuthResponse { private String access_token; private String scope; private String instance_url; private String token_type; private String id; public String getAccess_token() { return access_token; } public void setAccess_token(String access_token) { this.access_token = access_token; } public String getScope() { return scope; } public void setScope(String scope) { this.scope = scope; } public String getInstance_url() { return instance_url; } public void setInstance_url(String instance_url) { this.instance_url = instance_url; } public String getToken_type() { return token_type; } public void setToken_type(String token_type) { this.token_type = token_type; } public String getId() { return id; } public void setId(String id) { this.id = id; } } OAuthResponse.java PlatformEventService.java CometDエンドポイントへの接続、およびチャネルをSubscribeします。 package com.gmail.jimaoka.platformevent.consumerexample.client; import org.cometd.client.BayeuxClient; import org.cometd.client.transport.LongPollingTransport; import org.eclipse.jetty.client.HttpClient; import org.eclipse.jetty.client.api.Request; import org.eclipse.jetty.util.ssl.SslContextFactory; public class PlatformEventService { private static final String COMETD_ENDPOINT = "/cometd/41.0"; private static final String CHANNEL = "/event/DemoOrderEvent__e"; private String instanceUrl; private String accessToken; private HttpClient httpClient; private BayeuxClient client; public PlatformEventService(String instanceUrl, String accessToken){ this.instanceUrl = instanceUrl; this.accessToken = accessToken; } public void start() throws Exception{ SslContextFactory sslContextFactory = new SslContextFactory(); httpClient = new HttpClient(sslContextFactory); httpClient.start(); LongPollingTransport httpTransport = new LongPollingTransport(null, httpClient){ @Override protected void customize(Request request) { request.header("Authorization", "Beare " + accessToken); } }; client = new { if(message.isSuccessful()){ System { System.out.println(message.toString()); }); } public void stop() throws Exception{ if(client != null){ client.disconnect(); } if(httpClient != null){ httpClient.stop(); } } } PlatformEventService.java 動作確認 Javaアプリを起動し、Salesforce上で注文レコードを作成&編集します。注文レコードのステータスを"出荷依頼"とした際に、Javaを起動したコマンドラインに受診したメッセージが表示されれば成功です! おわりに PlatformEventを試す簡単なサンプルアプリを紹介しましたが如何でしたでしょうか? サンプルアプリの開発を通じてPlatformEventの動作を知り、Salesforceと外部システムのインテグレーションがより柔軟にできる可能性を感じてもらえたら幸いです。 関連する記事
0 notes
Text
Download Java MSI

Download Java MSI. Java logo 512x512 for Microsoft EndPoint Configuration Manager (SCCM/MECM/MEMCM) deployments:

Java MSI 8.0.2410.7
Release Highlights IANA Data 2019c JDK 8u241 contains IANA time zone data version 2019c. New Feature: Allow SASL Mechanisms to Be Restricted A security property named jdk.sasl.disabledMechanisms has been added that can be used to disable SASL mechanisms. Any disabled mechanism will be ignored if it is specified in the mechanisms argument of Sasl.createSaslClient or the mechanism argument of Sasl.createSaslServer. The default value for this security property is empty, which means that no mechanisms are disabled out-of-the-box. New Feature: SunPKCS11 Provider Upgraded with Support for PKCS#11 v2.40 The SunPKCS11 provider has been updated with support for PKCS#11 v2.40. This version adds support for more algorithms such as the AES/GCM/NoPadding cipher, DSA signatures using SHA-2 family of message digests, and RSASSA-PSS signatures when the corresponding PKCS11 mechanisms are supported by the underlying PKCS11 library. Other notes: New Checks on Trust Anchor Certificates New checks have been added to ensure that trust anchors are CA certificates and contain proper extensions. Trust anchors are used to validate certificate chains used in TLS and signed code. Trust anchor certificates must include a Basic Constraints extension with the cA field set to true. Also, if they include a Key Usage extension, the keyCertSign bit must be set. Other notes: Exact Match Required for Trusted TLS Server Certificate A TLS server certificate must be an exact match of a trusted certificate on the client in order for it to be trusted when establishing a TLS connection. Other notes: Added LuxTrust Global Root 2 Certificate LuxTrust root certificate has been added to the cacerts truststore Other notes: Added 4 Amazon Root CA Certificates Amazon root certificate has been added to the cacerts truststore Bug Fixes: Support for OpenType CFF Fonts Previously, Oracle JDK 8 did not include OpenType CFF fonts (.otf fonts) into the standard logical fonts (such as "Dialog" and "SansSerif"). This resulted in missing glyphs when rendering text. In the most extreme cases where only CFF fonts were installed on the system, a Java exception could be thrown. Several Linux distributions were affected by this issue because they rely on CFF fonts to support some languages, which is common for CJK (Chinese, Japanese, and Korean) languages. Oracle JDK 8 now uses these CFF fonts, and this issue has been resolved. Bug Fixes: Better Serial Filter Handling The jdk.serialFilter system property can only be set on the command line. If the filter has not been set on the command line, it can be set can be set with java.io.ObjectInputFilter.Config.setSerialFilter. Setting the jdk.serialFilter with java.lang.System.setProperty has no effect. For Configuration Manager deployments (or another authomated deployments) use: x86 msiexec.exe /i "jre1.8.0_241.msi"/qn JU=0 JAVAUPDATE=0 AUTOUPDATECHECK=0 RebootYesNo=No WEB_JAVA=1 x64 msiexec.exe /i "jre1.8.0_24164.msi" /qn JU=0 JAVAUPDATE=0 AUTOUPDATECHECK=0 RebootYesNo=No WEB_JAVA=1 REMOVEOLDERJRES=1 For uninstall use: x86 msiexec /x {26A24AE4-039D-4CA4-87B4-2F32180241F0} /qn /norestart x64 msiexec /x {26A24AE4-039D-4CA4-87B4-2F64180241F0} /qn /norestart Java MSI x86 download Java MSI x64 download
Java MSI 8.0.2310.11
Release Highlights IANA Data 2019b JDK 8u231 contains IANA time zone data version 2019b. For more information, refer to Timezone Data Versions in the JRE Software. New Feature: New jdk.jceks.iterationCount System Property A new system property has been introduced to control the iteration count value used for the jceks keystore. The default value remains at 200000 but values between 10000 and 5000000 may be specified. The new system property name is jdk.jceks.iterationCount and the value supplied should be an integer in the accepted range. The default value will be used if a parsing error is encountered.New Feature: New Java Flight Recorder (JFR) Security Events Four new JFR events have been added to the security library area. These events are disabled by default and can be enabled via the JFR configuration files or via standard JFR options.Removed Features and Options: Removal of T2K Rasterizer and ICU Layout Engine From JavaFX. The T2K rasterizer and ICU layout engine have been removed from JavaFX.Other notes: GTK3 Is Now the Default on Linux/Unix. Newer versions of Linux, Solaris, and other Unix flavor desktop environments use GTK3, while still supporting GTK2. Previously, the JDK would default to loading the older GTK2 libraries. However, in this release, it defaults to loading GTK3 libraries. Loading is typically triggered by using the Swing GTK Look And Feel. The old behavior can be restored by using the system property: -Djdk.gtk.version=2.2Other notes: Remove Obsolete NIST EC Curves from the Default TLS Algorithms. This change removes obsolete NIST EC curves from the default Named Groups used during TLS negotiation. The curves removed are sect283k1, sect283r1, sect409k1, sect409r1, sect571k1, sect571r1, and secp256k1. To re-enable these curves, use the jdk.tls.namedGroups system property. The property contains a comma-separated list within quotation marks of enabled named groups in preference order.For example: java -Djdk.tls.namedGroups="secp256r1, secp384r1, secp521r1, sect283k1, sect283r1, sect409k1, sect409r1, sect571k1, sect571r1, secp256k1" ... For System Center Configuration Manager deployments (or another authomated deployments) use: x86 msiexec.exe /i "jre1.8.0_231.msi"/qn JU=0 JAVAUPDATE=0 AUTOUPDATECHECK=0 RebootYesNo=No WEB_JAVA=1 x64 msiexec.exe /i "jre1.8.0_23164.msi" /qn JU=0 JAVAUPDATE=0 AUTOUPDATECHECK=0 RebootYesNo=No WEB_JAVA=1 REMOVEOLDERJRES=1 For uninstall use: x86 msiexec /x {26A24AE4-039D-4CA4-87B4-2F32180231F0} /qn /norestart x64 msiexec /x {26A24AE4-039D-4CA4-87B4-2F64180231F0} /qn /norestart Java MSI x86 download Java MSI x64 download Read the full article
#Java#MECM#MEMCM#MicrosoftEndpointConfigurationManager#MSI#SystemCenter#SystemCenterConfigurationManager#Windows#Windows10
0 notes