#WHAT DO YOU MEAN ITS NOT A VALID EMAIL ADDRESS
Explore tagged Tumblr posts
Text
cc ó (____\ I didn’t know it was possible for me to
(_________) hate Konami more than I already did
#for context I wanted to delete my save data for the PS5 version of Yu-Gi-Oh Master Duel#so after trying and failing to find a “delete save data” button I decided to go into my PS5’s storage and delete it from there#my save data was still there when I booted up master duel#afterwards I decided to transferring my save data to a different account#save data was still there#after that I was desperate and decided to go to konami’s official website and ask them from there#so I filled out the entire thing and used the same email address I used to create my konami id#“This is not a valid email address”#WHAT DO YOU MEAN ITS NOT A VALID EMAIL ADDRESS#ITS THE SAME EMAIL ADDRESS I USED TO MAKE MY ACCOUNT
3 notes
·
View notes
Text
"Beyond the Screen: The Do’s, Don’ts, and Dangers"
Social media has evolved into a virtual platform where people share their lives, thoughts, and artistic creations in modern times. The digital landscape is incredibly powerful, offering everything from life-altering opportunities to viral trends. Beyond the screen, however, is a hidden reality that is full of obligations, dangers, and consequences. Making the most of social media while staying safe requires an understanding of its dos, don'ts, and hazards.
Understanding the dos, don'ts, and dangers of social media is essential to navigating the digital world safely and responsibly. Social media has completely changed how we connect, share, and consume information. The platform offers countless opportunities for communication, business, and education, but it also carries a number of serious risks.
The Do’s of Social Media
1. Maintain Your Privacy
Modify your content's privacy settings on all platforms to limit who can view it. Your public information can be used by cybercriminals, so be careful what you share.
2. Think Before You Post
Consider whether you would feel at ease if this went viral before clicking "post" or "share." Your digital footprint may follow you for years because the internet never forgets. Be careful when sharing.
3. Check Facts Like a Detective
Misinformation is pervasive. Don't trust everything you see; before sharing news or contentious posts, double-check sources, confirm assertions, and exercise critical thought.
4. Distribute Encouragement and Support
An encouraging message, a shared success story, or a kind remark can brighten someone's day. Make use of your position to encourage others and foster a more positive online environment.
5. Taking breaks from social media
Scrolling endlessly can have an impact on mental health. To keep a healthy balance between online and offline life, set limits on screen time and schedule breaks.
The Don’ts of Social Media
1. Avoid Cyberbullying and Online Drama.
On the Internet, negativity spreads quickly. Block, mute, or report offensive content rather than arguing. Be the answer, not a contributing factor.
2. Don’t Share Personal Information Recklessly
Don't share private information online, such as phone numbers, home addresses, or financial details. You may become vulnerable to identity theft and cyberthreats as a result.
3. Don't Believe Everything You See
A filtered reality is frequently displayed on social media. Steer clear of comparing yourself to idealized depictions because they might not accurately represent reality.
4. Don't neglect your relationships in real life.
Real-world relationships are more important than likes and comments. Get away from the computer and spend time with loved ones.
5. Avoid clicking on every link that appears.
Not every eye-catching advertisement or viral link is reliable. Steer clear of phishing scams, dubious emails, and "too good to be true" signs. Cybercriminals are constantly searching.
The Dangers of Social Media
1. Effects of Continuous Scrolling on Mental Health
Social media can become compulsive. Anxiety, depression, and stress can be exacerbated by comparison culture, online validation seeking, and the fear of missing out (FOMO).
2. Threats to Cybersecurity
To gain access to personal information, hackers take advantage of public Wi-Fi, weak passwords, and unconfirmed links. These risks can be avoided by bolstering online security.
3. False Information and Deception
Misinformation is becoming more and more prevalent, from deep fake videos to deceptive headlines. Keep yourself informed by asking questions about everything and sticking to reliable sources.
4. The Danger of Internet Predators
Not everyone on the internet is well-meaning. Never share private photos with strangers, exercise caution when conversing with them, and notify the authorities of any suspicious activity.
5. The Cost of Digital Addiction
Long periods of aimless scrolling can interfere with sleep cycles and lower productivity. To get back in control of your time, establish sensible boundaries and take up offline hobbies.
Conclusion:
Social media is a great way to connect with people, but there are risks involved. We can make the digital world a safer and better place for everyone if we use it carefully, protect our privacy, and spread positivity. Stay smart, stay kind, and always think before you click. The internet is forever, but so is the impact of your choices. Let’s use social media to inspire, connect, and create a better future, both online and offline.
Even though the internet is virtual, everything you do has an impact on the real world. "Behind every screen is a real person. Be kind. Be respectful."
How do you feel about social media awareness? Let's carry on the discussion in the comments section below! Although social media is an effective tool for connecting people, there are risks associated with it. We can make the internet a safer and better place for everyone if we use it carefully, safeguard our privacy, and spread positivity.
The effects of your decisions last forever, just like the internet. Social media is like a huge ocean, full of limitless opportunities and hidden dangers beneath the surface. Let's use it to inspire, connect, and build a better future both online and offline. You may tap into the power of technology without getting caught in its traps if you navigate it with awareness, responsibility, and kindness. Be mindful before posting, protect your privacy, and keep in mind that genuine relationships are more important than virtual ones. Together, let's make social media a positive force that helps everyone have a safer and better digital future.
Remember: "Your words have power. Use them to uplift, not to harm."
©: Rayn Gwyneth Genabe https://i.pinimg.com/736x/47/5b/2c/475b2cfa0e818b7fda0234070fa3c68a.jpg

7 notes
·
View notes
Text
What to do when you spot a broken website
I am a very firm believer in either sticking to your principles or update them.
So when I got this error while I tried to search for C/C++ on my national job portal:
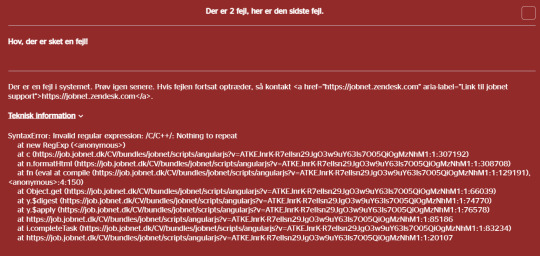
My first thought was "Huh, that is sorta funny" (especially since the code to show me the email address to report this error to was ALSO broken... meaning that whoever made the code that should run if the website broke... never tested it). And then I realized what I was looking at.
And at that point I think I had a ethical duty to notify people to get this fixed. FAST. Why?
It comes under "You are responsible for your choices". With it being understood that doing nothing is also a choice, and that taking a job where you work for, and help a company with doing evil is NOT a choice, if that is the only job you could get (IE, you did not have the power/money/mental health/time to make a choice)
It is now fixed*, so I wanted to make this post for all in the little codeblr community doing any front-end work. Web or not. With 3 lessons to learn from this.
First thing to get from this: "Everyone makes mistakes". This is one of the reason good code is not code without errors. It is code where it is easy to make changes and fix errors. You then try to find as many errors as you can with code reviews, automated testing, having a work environment that does not punish human errors( which encourages people to HIDE errors ) and so on.
Second thing: "Sanitize your user input. Always". Write code that assumes that every single user wants nothing more than to break your code and exploit its vulnerabilities.
This had NOT been done here. This error shows that characters in the string that was made from my search terms, was being run as code. As in, I, or anyone else, could run code in the middle of this javascript code. Meaning it is possible that someone could write code as part of their search that would make the javascript code do... whatever they wanted to. Including deleting the entire backend database. Or steal the info. This is why you ALWAYS sanitize your user input. Basically encode all potentially dangerous characters as something else while working on them. There are libraries like validator.js and express-validator that will do it for you, if you use javascript.
And the third thing. "Do NOT investigate further" . As soon as you confirm that your user input gets treated as code, you contact whoever is running it. If they do not take the threat seriously and it is still there after a week or two, contact established press with this info. You may read about so called grey hat hackers, who unlike black hat hackers(who is people wishing to do harm) or white hat hackers(Who are hired to try to break into a companies software to test it), are trying to find security flaws with good intentions, but are unaffiliated with whoevers code they are trying to break into. In an ideal world, doing that, and then contacting the company, SHOULD result in the company thanking them . But often it also leads to the company suing. And winning. Since breaking in to show that it is possible, is technically still breaking in. So do NOT start testing what you are able to do with the exploit you found. Report it to them, and check a weeks time later if it is fixed. If it keeps being vulnerable, contact the press. The site fixed this error after half a week. But they did it, not by encoding the dangerous characters into something else, but to simply remove them all from the user input string. Meaning that I still cannot search for "C++". Now I just get any job that contains the letter "C"... I mean... it is better... So if you take user input, and it does not brick your code in dangerous ways. You are doing better than whoever coded this for the Danish State :p
12 notes
·
View notes
Text
MaxRebates Promotion and $50 Signup- Bonus 2024
If you are an online shopping enthusiast, you might want to learn about MaxRebates promotion and cashback program. MaxRebates is a reliable online platform that offers cash backs on your purchases. You can earn huge discounts and bonuses by signing up, referring your friends, or shopping through this website. There are several methods to earn cashback, and we will discuss them in detail in this blog. We will also answer frequently asked questions about MaxRebates' legitimacy and how to sign up for this website.
What Is a MaxRebates?
MaxRebates is an online platform that helps customers earn cashback on their online purchases. It partners with famous online retailers such as Amazon, eBay, Walmart, Best Buy, and many more. Whenever you make a purchase through MaxRebates, the company receives a commission from the retailer. MaxRebates then shares this commission with the buyer in the form of cashback rewards.
MaxRebates promotion (up to $50 sign-up Bonus)
MaxRebates offers a fantastic promotional offer to its new customers. If you sign up now, you can receive a whopping $50 sign-up bonus. To avail of this offer, users need to sign up and make a purchase of at least $25 through MaxRebates. This offer is valid for a limited time, and you can enjoy this benefit right away.
How to Sign up for MaxRebates:
Signing up for MaxRebates is a straightforward process. Users need to visit the official website, provide their email address, and followed by a password. Once you have signed up, you can start browsing the deals from preferred retailers and shop via the platform to start earning your cashback.
MaxRebates Referral Promotion: up to $50 for every Referral
MaxRebates is not only limited to the sign-up bonus, but it also rewards its users for referring their peers. For every referral, users can earn up to $50. If you have a high traffic social media handle or blog, by promoting MaxRebates and referring people, you could be on your way to earning a significant reward.
Also, when your friends sign up, they get to enjoy the $50 sign-up bonus and referral program as well. The platform also validates referrals to avoid fraud and abuse.
How to refer MaxRebates
Users can refer by navigating to their account settings and clicking on the referral tab to generate a referral link. Copy your link to share on your social media platforms, Blog, email list, etc. Your referral link would automatically lead the user to the sign-up page, where they can sign-up and start earning rewards.
MaxRebates Cash Back
MaxRebates offers cashback on each purchase on their platform. This means it is beneficial to shop via MaxRebates for the best deals on your preferred online retailer. The offers displayed on MaxRebates are updated daily to ensure users receive the best possible cashback offers.
How Do You Earn Cash Back?
Once you have signed in and made your purchase through MaxRebates, the cashback rewards will show up on your account within 48 hours. It might take up to 60 days for rewards to get processed from the merchant's end. Once you have accumulated $10 or above, you can withdraw the funds via PayPal, Amazon Gift Card, or bank transfer.
Is MaxRebates legit?
MaxRebates is a legitimate company that offers cashback rewards for online purchases. It has partnerships with top online retailers and ensures that the cashback offered is genuine. The platform uses strong encryption software and follows HIPAA-compliant data security standards to ensure that users' personal information is safe and secured.
Conclusion
MaxRebates is an excellent platform for online shoppers to earn cash back on their purchases. It offers several rewards, such as a generous sign-up bonus and referral program. The platform is user-friendly and has partnerships with top online retailers. With fraudulent activity on the rise, we understand people skepticism in trusting online platforms. Nonetheless, MaxRebates has a fantastic track record in rewarding its users. Finally, we suggest you give MaxRebates a try and enjoy the benefits it delivers!
2 notes
·
View notes
Text
How to Transition from H1B to Canada with ease?

The h1b is not only a work permit but is a gateway to opportunity. For skilled workers around the globe, it is an opportunity to work in pioneering industries based in America.
However, with rigorous requirements, tight deadlines, and an unpredictable lottery system, H1B visa holders face several challenges in the U.S. For many applicants, what should be an exciting journey passes into a stressful and ambiguous process.
Fortunately, there is still hope outside the U.S. border. Canada's growing innovation sector, coupled with a high standard of living, has made it a favorable destination for career growth and stability.
If you are planning to move with h1b to Canada with a hassle-free experience, it is necessary to know the overall process. So, are you ready to find out how to move from h1b to Canada smoothly? Check out this detailed guide to find a way through this exciting journey.
Understanding The Transition Process
You do not have to complicate your life moving with a US H1B Visa to Canada. With the appropriate steps and a bit of common sense, it is easy to make this move painless. That is why we have broken down the process into simple steps to get you started.
Eligibility Requirements
There are few immigration methods available based on skills for professionals in Canada. To qualify, you must have to fulfill these H1b visa Canada requirements:
Have relevant experience in a skilled occupation
Certifications that are valid and accepted in Canada.
Evidence of language proficiency (IELTS or CELPIP for English or TEF for French)
A Comprehensive Ranking System (CRS) score for programs like Express Entry.
Visa and Work Permit Options

H1b Canada work permit and visa options are closed. It means anyone with an H1B visa or hoping to obtain an H1b Canada open work permit can no longer apply. This initiative has been closed because it has surpassed its cap limit. But you do not need to be concerned. Your family members can now apply under a new policy that Canada has implemented.
Family members of applicants for an H1B visa who have already applied may enter Canada as workers, students, or guests. These consist of your dependent children, common-law partner, and spouse. Even though the deadline has passed, students and guests can still apply.
To qualify for this temporary policy, you must-
Have a valid h1b specialty occupation visa
When you apply, you must be a U.S. resident
H1b Visa for Canadian citizens
Canadians can find exciting professional prospects in the United States, particularly in business, finance, and various creative fields. But before they can work lawfully in the U.S., they must apply for a valid work visa from U.S. Citizenship and Immigration Services (USCIS), after which they can consider moving. Your specific visa needs will depend on your employment type, duration of stay, industrial sector, and skill set.
The most popular visa categories for which talented Canadians can apply are listed below:
TN visa
H-1b Visa
L-1 Visa
O-1 Visa
E-1 Visa
Application Steps
Follow these steps to begin your move from h1b to Canada:
Apply online via the IRCC website.
Make a new account if this is your first time using the portal.
After entering your email address, you will receive a code to sign up.
After logging in, click Apply to Visit, Study, or Work in Canada as a Temporary Resident.
Check the "I am ready to start my application" box at the bottom of the following page.
When asked what you wish to apply for, select an open work permit for holders of H1B visas.
To finish your application, respond to the remaining questions.
Benefits of Moving to Canada

It could be challenging to relocate to and settle in a new country you don't know much about. However, the Canadian government offers free programs to help you adjust to daily life in Canada.
Possibilities for Long-Term Residency
Advantages for the Family
Cultural Diversity
Overview of H1B Canada
H1b Canada specializes in helping professionals with visas move from h1b to Canada and pursue fulfilling professions. Their primary objective is to serve as the intermediary between talented Americans and exciting opportunities in Canada's thriving job market while adhering to the h1b Canada open work permit eligibility criteria. They provide
Relocation assistance
Immigration counseling.
Proficiency in Law
With complete assistance from H1B Canada throughout the immigration process, professionals can manage their relocation and blend into Canadian society.
FAQs About Transitioning from H1B to Canada
Here are answers to common questions about moving from an H1B visa to Canada:
Q: How can I use an H1B visa to relocate to Canada from the United States?
A: There were programs like Express Entry or PNP, with whom you could have moved to Canada, depending on your eligibility criteria. However, these initiatives are closed now to h1b visa holders.
Q: Can H1B visa holders go to Canada without a visa?
A: Canadian citizens are visa-exempt, but others will need a Canadian work permit or PR status.
Q: Can I work in Canada with a U.S. H1B visa?
A: No, U.S. H1B Visa does not solely allow you to work in Canada. You must obtain a H1b Canada work permit. It is even closed now. Due to this, you may have to look for other visa categories to work there.
Q: Which is better: H1B or Canada PR?
A: Canada PR offers long-term stability, family benefits, and a pathway to citizenship compared to the temporary nature of an H1B visa.
Q: After obtaining an H1B visa, how long does it take to become a permanent resident of Canada?
A: We cannot tell you exactly how long it can take. Every application is unique, and processing times vary accordingly.
Q: Do I need a job offer before applying for PR?
A: According to the Canadian government, the comprehensive ranking system for current and prospective candidates no longer includes job offer points. Still, if you have a new job offer, change your express entry profile in your IRCC-protected account. Additionally, it must be a recent written job offer from a Canadian consulate, high commission, or embassy.
Q: What expenses come with relocating to Canada on an H1B visa?
A: The H1B visa program for Canada is currently closed. However, in general, the majority of its applications need payment. The IRCC website has more details about the associated fees.
Q: What effect do my language skills have on my application?
A: There will be no further processing of your application. Therefore, you must demonstrate your language proficiency by passing an authorized language test, such as the CELPIP or TEF, to get your application accepted.
Conclusion
You and your family can live better lives and pursue interesting job opportunities when you move to Canada on an H1B visa. It is now easier than ever to migrate thanks to expedited immigration procedures like Express Entry and PNPs.
It is now closed for H1b holders, nevertheless. If you are willing to relocate from H1B to Canada, you should think about your other possibilities. For a hassle-free move to Canada, contact H1B Canada for professional advice and assistance!
0 notes
Text
How to Make Your Transaction Smoothly on Cash App?
Cash App is a well-known digital payment app which provides simple money transfer solutions. However, those who use it regularly sometimes find it difficult to make transactions smoothly. Limits on Cash App transactions are one such error which sometimes frustrates the users. The Cash App daily sending limit is up to $250 as soon as you sign up. Cash App limits depend on your level of verification and may change at any moment.

Cash App may request various proofs to verify your account, including but not limited to your full social security number, current address, valid government-issued photo identification card that has not expired and income/source of funding documentation as stated on its Terms of Service page. By continue reading you can few tips to make sure your transactions go smoothly on Cash App. So, let’s begin and learn more about it.
Why Do People Encounter Difficulties Sending Large Amounts Through Cash App?
Below mentioned are some of the most common reasons due to which you face difficulties while sending large amount through Cash App:
ID Not Verified: One of the primary factors preventing users from making large transactions is due to account verification issues. Unverified Cash App accounts typically have limits on how much money can be received or sent during any given period; unverified Cash App accounts are limited to sending/receiving up to $1,000 monthly and $250 weekly.
Cash App Transaction Limits: Cash App transactions restrict users from sending large amounts of money. There daily, weekly, and monthly limits on Cash App transfers. Once you have reached these limits it will be difficult to send and receive money. Cash App has set its daily and weekly send limits at $7,500 respectively; once this threshold has been reached, no further transfers can be sent until next week's limit has been met.
Pending Transactions on Cash App: If there are already pending transactions on your Cash App account, you will find it difficult to make new transactions. This is a safety measure taken by Cash App to ensure security of your account.
Why Do Users Think to Stop Using Cash App for Large Amounts of Money? Is It Safe to Send Large Amounts of Money on Cash App?
Many Cash App users’ express concerns over sending large payments this way due to fraudsters using Cash App to conduct illegal activity or simply misdirect payment from its recipient to a wrong address. Here are the few security measures taken by the Cash App:
Cash App uses multiple security measures, including encryption and fraud detection systems, to safeguard your funds.
Opting for Two Factor Authentication (2FA). This adds another level of protection by requiring that you confirm your identity using another means such as text messaging or email verification when signing in or conducting large transactions.
Cash App comes equipped with security features to safeguard your account.
How Much Money Can We Send on Cash App Safely?
Cash App transaction limits and verification status will determine how much money can be safely sent via our app, with unverified accounts typically having lower send limits than verified ones.
Verified Cash App accounts may safely send up to $7.500 daily or weekly without incurring penalty charges; for unverified accounts however, these limits can vary between $250 per week and $1,000 monthly.
Cash App users can send large sums while managing fraud and risk effectively. Verifying your account regularly if sending large sums can help safeguard against potential theft.
What is the Maximum Amount You Can Send on Cash App? And What Will My Daily, Weekly, Monthly, and ATM Withdrawal Limit Be if I Have a Verified Cash App Account?
Once your Cash App account has been verified, your transactional limits will become much higher. Below mentioned are the Cash App limits for verified users:
Cash App Sending Limit: With a verified Cash App account, you can transfer up to $7,500 per week, which will allow for larger transactions in a shorter amount of time.
Cash App Receiving Limit: Cahs App verified users does not have receiving limits as they receive money without any bar.
Cash App ATM Withdrawal Limit: For verified Cash App accounts, the ATM withdrawal limit per day is $1,000 per day; that means the most you can withdraw using your Cash App debit cards at ATMs is also $1,000 daily.
Cash App Bitcoin Withdrawal Limit: Cash App accounts allow users to withdraw up to $2,000 worth of Bitcoin each day from your verified account, making this feature especially important if you plan to send Bitcoins frequently.
0 notes
Text
Unlock Your Australian Dream: Everything You Need to Know About the eVisitor Visa Subclass 651!
Discover the Secrets to Seamlessly Traveling Down Under with Australia’s eVisitor Visa!
Are you dreaming of exploring Australia's iconic landmarks, vibrant cities, or stunning natural landscapes? Look no further than the eVisitor Visa Subclass 651! This visa enables eligible travelers from certain countries to visit Australia for tourism or business purposes. Here’s everything you need to know about this convenient travel option.
What is the eVisitor Visa Subclass 651? The eVisitor Visa allows passport holders from select European countries to enter Australia for short stays, typically up to three months at a time. This visa is designed for tourism, visiting family or friends, or conducting business activities like attending meetings or conferences.
Eligibility Requirements To apply for the eVisitor Visa Subclass 651, you must be a passport holder from an eligible country, such as the UK, France, or Italy. You also need to be in good health, have no significant criminal history, and demonstrate that you plan to return to your home country.
How to Apply Applying for the eVisitor Visa is simple and can be done online through the Australian government's Department of Home Affairs website. You'll need to provide personal information, passport details, and a valid email address. The application process is usually quick, with most decisions made within a few days.
Key Benefits One of the main advantages of the eVisitor Visa is its cost-effectiveness. The application is free, making it an attractive choice for budget-conscious travelers. Additionally, the visa allows for multiple entries, meaning you can explore Australia time and again within its validity period.
Travel Tips Once you have your eVisitor Visa, remember to plan your itinerary wisely. From the Great Barrier Reef to the Sydney Opera House, there's so much to see and do! Always check local travel guidelines and regulations before your visit.
In conclusion, the eVisitor Visa Subclass 651 is your gateway to an unforgettable Australian adventure. Start planning today and experience the beauty of Australia firsthand!
Explore more about Australia eVisa
For more information please Contact with us
0 notes
Text
David Kellerman, CTO at Cymulate – Interview Series
New Post has been published on https://thedigitalinsider.com/david-kellerman-cto-at-cymulate-interview-series/
David Kellerman, CTO at Cymulate – Interview Series


David Kellerman is the Field CTO at Cymulate, and a senior technical customer-facing professional in the field of information and cyber security. David leads customers to success and high-security standards.
Cymulate is a cybersecurity company that provides continuous security validation through automated attack simulations. Its platform enables organizations to proactively test, assess, and optimize their security posture by simulating real-world cyber threats, including ransomware, phishing, and lateral movement attacks. By offering Breach and Attack Simulation (BAS), exposure management, and security posture management, Cymulate helps businesses identify vulnerabilities and improve their defenses in real time. What do you see as the primary driver behind the rise of AI-related cybersecurity threats in 2025?
AI-related cybersecurity threats are rising because of AI’s increased accessibility. Threat actors now have access to AI tools that can help them iterate on malware, craft more believable phishing emails, and upscale their attacks to increase their reach. These tactics aren’t “new,” but the speed and accuracy with which they are being deployed has added significantly to the already lengthy backlog of cyber threats security teams need to address. Organizations rush to implement AI technology, while not fully understanding that security controls need to be put around it, to ensure it isn’t easily exploited by threat actors.
Are there any specific industries or sectors more vulnerable to these AI-related threats, and why?
Industries that are consistently sharing data across channels between employees, clients, or customers are susceptible to AI-related threats because AI is making it easier for threat actors to engage in convincing social engineering schemes Phishing scams are effectively a numbers game, and if attackers can now send more authentic-seeming emails to a wider number of recipients, their success rate will increase significantly. Organizations that expose their AI-powered services to the public potentially invite attackers to try to exploit it. While it is an inherited risk of making services public, it is crucial to do it right.
What are the key vulnerabilities organizations face when using public LLMs for business functions?
Data leakage is probably the number one concern. When using a public large language model (LLM), it’s hard to say for sure where that data will go – and the last thing you want to do is accidentally upload sensitive information to a publicly accessible AI tool. If you need confidential data analyzed, keep it in-house. Don’t turn to public LLMs that may turn around and leak that data to the broader internet.
How can enterprises effectively secure sensitive data when testing or implementing AI systems in production?
When testing AI systems in production, organizations should adopt an offensive mindset (as opposed to a defensive one). By that I mean security teams should be proactively testing and validating the security of their AI systems, rather than reacting to incoming threats. Consistently monitoring for attacks and validating security systems can help to ensure sensitive data is protected and security solutions are working as intended.
How can organizations proactively defend against AI-driven attacks that are constantly evolving?
While threat actors are using AI to evolve their threats, security teams can also use AI to update their breach and attack simulation (BAS) tools to ensure they are safeguarded against emerging threats. Tools, like Cymulate’s daily threat feed, load the latest emerging threats into Cymulate’s breach and attack simulation software daily to ensure security teams are validating their organization’s cybersecurity against the most recent threats. AI can help automate processes like these, allowing organizations to remain agile and ready to face even the newest threats.
What role do automated security validation platforms, like Cymulate, play in mitigating the risks posed by AI-driven cyber threats?
Automated security validation platforms can help organizations stay on top of emerging AI-driven cyber threats through tools aimed at identifying, validating, and prioritizing threats. With AI serving as a force multiplier for attackers, it’s important to not just detect potential vulnerabilities in your network and systems, but validate which ones post an actual threat to the organization. Only then can exposures be effectively prioritized, allowing organizations to mitigate the most dangerous threats first before moving on to less pressing items. Attackers are using AI to probe digital environments for potential weaknesses before launching highly tailored attacks, which means the ability to address dangerous vulnerabilities in an automated and effective manner has never been more critical.
How can enterprises incorporate breach and attack simulation tools to prepare for AI-driven attacks?
BAS software is an important element of exposure management, allowing organizations to create real-world attack scenarios they can use to validate security controls against today’s most pressing threats. The latest threat intel and primary research from the Cymulate Threat Research Group (combined with information on emerging threats and new simulations) is applied daily to Cymulate’s BAS tool, alerting security leaders if a new threat was not blocked or detected by their existing security controls. With BAS, organizations can also tailor AI-driven simulations to their unique environments and security policies with an open framework to create and automate custom campaigns and advanced attack scenarios.
What are the top three recommendations you would give to security teams to stay ahead of these emerging threats?
Threats are becoming more complex every day. Organizations that don’t have an effective exposure management program in place risk falling dangerously behind, so my first recommendation would be to implement a solution that allows the organization to effectively prioritize their exposures. Next, ensure that the exposure management solution includes BAS capabilities that allow the security team to simulate emerging threats (AI and otherwise) to gauge how the organization’s security controls perform. Finally, I would recommend leveraging automation to ensure that validation and testing can happen on a continuous basis, not just during periodic reviews. With the threat landscape changing on a minute-to-minute basis, it’s critical to have up-to-date information. Threat data from last quarter is already hopelessly obsolete.
What developments in AI technology do you foresee in the next five years that could either exacerbate or mitigate cybersecurity risks?
A lot will depend upon how accessible AI continues to be. Today, low-level attackers can use AI capabilities to uplevel and upscale their attacks, but they aren’t creating new, unprecedented tactics – they��re just making existing tactics more effective. Right now, we can (mostly) compensate for that. But if AI continues to grow more advanced and remains highly accessible, that could change. Regulations will play a role here – the EU (and, to a lesser extent, the US) have taken steps to govern how AI is developed and used, so it will be interesting to see whether that has an effect on AI development.
Do you anticipate a shift in how organizations prioritize AI-related cybersecurity threats compared to traditional cybersecurity challenges?
We’re already seeing organizations recognize the value of solutions like BAS and exposure management. AI is allowing threat actors to quickly launch advanced, targeted campaigns, and security teams need any advantage they can get to help stay ahead of them. Organizations that are using validation tools will have a significantly easier time keeping their heads above water by prioritizing and mitigating the most pressing and dangerous threats first. Remember, most attackers are looking for an easy score. You may not be able to stop every attack, but you can avoid making yourself an easy target.
Thank you for the great interview, readers who wish to learn more should visit Cymulate.
#2025#Accessibility#agile#ai#AI development#AI systems#AI technology#ai tools#AI-powered#attackers#automation#backlog#breach#Business#change#continuous#craft#CTO#cyber#cyber security#Cyber Threats#cybersecurity#cybersecurity challenges#cybersecurity threats#Cymulate#data#data leakage#defenses#development#Developments
0 notes
Text
What to Do When You Get an IRS ( Internal Revenue Service) Notice
Introduction
Receiving a notice from the IRS can be intimidating, especially for expats who live outside the United States. If you are an expatriate living in Hyderabad and have received an IRS notice, it is essential to take the right steps to ensure compliance and avoid unnecessary penalties. Though they stay abroad, expatriates have to file their taxes in the U.S. The IRS has clear instructions on handling foreign residents, and this blog post explains what you should do if you get an IRS notice and how Expat Tax Services in Hyderabad can assist you through the maze.
Know the type of IRS notice
The first thing you do when receiving a notice from the IRS is read that document carefully. All of the information relevant to your tax filings, payments, or possible issues with your tax return will be contained within the notice. Perhaps the notice is indicating discrepancies, or missing information, or even it be an audit notice. Notices can be as easy as general reminders to more serious requests for payment and documentation.
Some of the most common types of IRS notices are:
Notice of Deficiency (CP 501): A reminder of unpaid taxes.
Notice of Audit: In case your return is under review for accuracy.
Notice of Penalty: When penalties are due because of late filing or payment.
Notice of Refund Adjustment: When there's an issue with your tax refund.
Knowing what type of notice it is can help understand what action needs to be taken.
Don't Panic – Stay Calm and Gather Your Documents
Receiving an IRS notice can be very stressing, but avoid panicking. Take a deep breath and start gathering all the documents to do with the notice. If it is a tax return-related notice, make sure you have a copy of your filed return and all the supporting documents, which may include income records, receipts, and bank statements.
For expats, this could include:
U.S. tax returns (Form 1040 or 1040NR)
Foreign bank account statements (FBAR – Foreign Bank Account Report).
Forms such as the 2555 (Foreign Earned Income Exclusion) or 1116 (Foreign Tax Credit).
The more information you can gather, the better prepared you'll be to respond accurately and promptly.
Confirm the Notice is Accurate
Before you take any action, verify whether the notice from IRS is genuine. There are cases in which fraudsters send false notices of the IRS to get money from people. Check whether the notice contains all your correct personal information. Include personal details such as your name, address, and Social Security number.
If you suspect that the notice is a scam, contact the IRS directly by calling their official number at 1-800-829-1040 for U.S.-based calls or through the IRS website to confirm its authenticity. Never respond to emails or calls claiming to be the IRS without verification.
Decide whether you need to do something
Once you have made sure that notice is valid, and you now understand what you are reading. You will either need to make a response about the notice in question or action. Sometimes you may just require a reminder over a minor item that can easily be rectified.
Other occasions may require one to take imperative action, especially when submitting documents, making the payment, and correcting errors while filing your returns.
If the notice requires an immediate response, make sure to follow the instructions exactly as outlined. If you’re unsure about what the notice means or what steps to take, it’s always a good idea to seek professional help, especially if you’re an expat.
Sought Professional Guidance from Expat Tax Services at Hyderabad
Navigating the U.S. tax system from abroad is challenging, particularly if you're an expat. U.S. tax law features special provisions applicable to residents living overseas. So, for IRS notice problems, specialized knowledge might be needed for effective resolution, and that is where the Hyderabad-based expat tax services can help you out.
Professional expat tax services in Hyderabad have the expertise and experience to help U.S. citizens living in India address IRS notices and resolve tax issues.
Here's how they can assist:
Tax Filing Assistance: If the IRS notice pertains to a missing or incorrect tax return, an expat tax professional can help you file the necessary forms and avoid penalties.
Foreign Income Reporting: They can help you report foreign income, claim the Foreign Earned Income Exclusion (Form 2555), or the Foreign Tax Credit (Form 1116), all while keeping in line with the IRS rules and regulations for expats.
Representation with the IRS: They will communicate directly with the IRS to resolve any disputes or issues, so you do not have to deal with the situation personally.
Audit Support: If you have received an IRS audit notice, expat tax services can guide you through the process and help you gather the necessary documentation to respond to the IRS effectively.
Penalty Abatement: If you have been charged penalties, an expat tax professional may help you request penalty abatement or negotiate a payment plan if necessary.
Working with a knowledgeable tax professional in Hyderabad will ensure that you are complying with U.S. tax laws and taking the appropriate actions in response to the IRS notice.
Respond to the IRS on Time
The IRS usually provides a specific date for responding to their notices. Failure to respond within the given date may attract additional penalties, interest charges, or even more severe legal consequences. If you need more time, you can request an extension, but this must be done before the deadline.
ConclusionReceiving an IRS notice while living as an expatriate in Hyderabad can be intimidating, but it is possible to handle the situation if you stay calm and take the right steps. Understanding the notice, gathering your documents, verifying the information, and seeking professional assistance are some of the key steps that will ensure you comply with U.S. tax laws and avoid penalties. Expat tax services in Hyderabad can provide you with the professional expertise to help you through the complexities of international taxation and IRS requirements. With the right professionals, you can face any IRS notice with confidence and peace of mind.
0 notes
Text
What to Do If Your FSSAI License Gets Suspended?

The Food Safety and Standards Authority of India (FSSAI) plays a crucial role in maintaining food safety by regulating and supervising the food industry. Securing an FSSAI license is not just a legal formality but an assurance of delivering high-quality food products. However, challenges arise when businesses face FSSAI license suspension or even food license cancellation due to various non-compliance issues.
Filing an FSSAI application requires attention to detail, and many entrepreneurs face rejection due to errors or violations. Understanding the reasons behind FSSAI revoked licenses and the FSSAI appeal process is essential to rectify and restore the license successfully.
Common Reasons for FSSAI Application Rejection
Applications for FSSAI licenses can be rejected due to several reasons, leading to legal consequences such as FSSAI non-compliance penalties and FSSAI violation notices. Below are the most common reasons:
1. Incomplete or Inaccurate Information
Providing incomplete or misleading data in the application can lead to rejection. Ensure all business details, identity proofs, address proofs, and relevant documents are submitted accurately.
2. Non-Compliance with Food Safety Standards
Failure to meet FSSAI inspection criteria, such as using substandard ingredients or improper hygiene, can lead to FSSAI inspection failure and eventual rejection.
3. Lack of Adequate Infrastructure
Food businesses must maintain proper storage, refrigeration, and sanitary conditions. Inadequate infrastructure may result in FSSAI license suspension due to safety risks.
4. Failure to Comply with Licensing Regulations
Misclassification of license type—such as applying for a central license instead of a state license—can cause rejection.
5. Non-Payment of Fees
Applicants must adhere to the FSSAI reactivation process by ensuring timely payment of processing fees to avoid application rejection.
What to Do If Your FSSAI Application Gets Rejected?
A rejection notice doesn’t mean the end of your food business aspirations. The government provides avenues to rectify issues and appeal against the decision. Here’s how you can restore your FSSAI license after rejection:
Revival of Rejected Basic and State FSSAI License
Submit a reactivation request to the State Food Safety Commissioner within three months of rejection.
A designated officer will review the case and evaluate its merit.
Within 30 days, an email will be sent to the RC Division outlining findings.
If found valid, the proposal will be forwarded to the IT Division for reactivation.
Revival of Rejected Central License
Apply for reactivation within six months at the FSSAI Regional Office.
The Regional Office Director will assess the case.
If found valid, the request will be forwarded to [email protected] for further evaluation.
The Regional Compliance Division (RCD) will conduct final scrutiny.
The Executive Director of RCD will provide the final decision.
If required, extreme cases can be escalated to FSSAI headquarters for CEO evaluation.
SOPs for Reactivating a Rejected FSSAI Application
On July 7, 2022, FSSAI introduced Standard Operating Procedures (SOPs) to streamline the FSSAI reactivation process. SOPs apply in these scenarios:
The application was inadvertently rejected during processing.
A technical error occurred in the system while processing the application.
The system automatically rejected the application due to missing documents.
Legal Actions for FSSAI Suspension
In cases where businesses fail to comply with regulations even after multiple warnings, FSSAI legal actions may be taken, including:
Food license cancellation for severe non-compliance.
FSSAI violation notices and hefty fines.
Permanent suspension for repeated FSSAI inspection failures.
How to Restore an FSSAI License After Suspension?
If your FSSAI license is suspended, you can:
File an appeal under the FSSAI appeal process.
Rectify the non-compliance issues and submit proof.
Undergo a reinspection to verify improvements.
Pay any pending FSSAI non-compliance penalties.
By understanding the FSSAI reactivation process, businesses can efficiently address rejections and stay compliant with food safety regulations. Proper adherence to FSSAI labeling rules, food packaging FSSAI guidelines, and FSSAI regulations for food labels will help prevent issues in the future.
Conclusion
In conclusion, FSSAI application rejections can stem from incomplete information, non-compliance with safety standards, inadequate infrastructure, or failure to pay fees. However, businesses can appeal or reactivate their licenses by following the prescribed procedures. Understanding the reactivation process and complying with FSSAI regulations can help avoid penalties, suspensions, and future rejections, ensuring smooth operations and continued adherence to food safety standards.
#FSSAI#FoodLicense#FoodSafety#FSSAICompliance#LicenseSuspension#FoodBusiness#FSSAIApproval#LegalCompliance
0 notes
Photo

You can create the best email in the world, but it won’t matter if it doesn’t make it to your subscriber. And that’s why it’s vitally important you work with an email service provider (like FeedBlitz!) who places the highest possible focus and dedication on their deliverability practices. But what does deliverability mean? And how and when does it actually happen? And is there anything you can do to help? The answers to those questions and many more are what you will find in this post. There’s a lot of ground to cover when it comes to email deliverability, so without further delay, let’s jump right in. In this post, you’ll learn: What is email deliverability? Deliverability is a fairly common buzzword in the world of email marketing. However, unless you’re in the business of establishing and safeguarding it — or have had your email efforts impacted because of the lack of it — there isn’t a lot of clarity around the term and how companies achieve, monitor, and protect a high deliverability status. In the simplest of terms, deliverability is the processes and protections that allow your emails to reach your subscribers. It sounds pretty simple, but everything that takes place to get your emails from creation to open is much more complex. Knowing the ins and outs of email deliverability will help you make wiser decisions regarding your email marketing efforts. And it’ll also offer vitally important clarity when deciding which email service provider (ESP) to work with. Because again, you can design the prettiest emails possible, filled with the best content of your life, but it all means nothing if you’re with an ESP who cuts corners and your emails don’t actually get delivered. Key terms related to email deliverability. Anytime you’re working with a complex topic, starting with a foundation of key terms is best. The following terms will be helpful to know as you dig deeper into this blog post: Deliverability – getting your emails to a subscriber.Inboxing – getting your emails to a subscriber’s inbox (including Gmail’s promotions tab) as opposed to the spam folder.Reputation – receiving internet service providers (ISPs) review, judge, and estimate the safety of emails being sent by a particular email address — based on their own top-secret set of rules and guidelines — which ultimately determines whether your email will be allowed or denied.Authentication – a process to further validate the sender of your emails established through SPF, DKIM and DMARC, which use DNS to ensure permission has been granted. What happens when you send an email? Deliverability checks are not something that takes place one time, in one specific step of the email sending process. It can — and does — happen at multiple stages of the process every time one of your emails begins to send. To help give you a better idea of how and when this can happen, we’ll start with all the things that happen when you send an email, i.e., the path your email takes from the moment it begins sending to its arrival at your subscriber’s door. There are many more steps than you may realize, and that’s because most of the process takes place behind the scenes. The full process is a bit more nuanced and detailed than what’s outlined here, but the six steps highlighted below will give you a solid frame of reference for the process. While most ESPs follow similar, if not the same steps, below is a FeedBlitz-specific version to help show additional checks performed throughout the way: Step 1 – You create an email. And when working in FeedBlitz, before you’re even able to send or schedule the mailing, the content is checked against our in-house protocols. For example, you won’t even be allowed to send an email that may potentially be rejected by ISPs. Step 2 – The email begins sending. A unique email copy is created for each subscriber and sent to one of our outbound SMTP servers. (SMTP = the internet’s email protocol) Step 3 – Our SMTP servers send the email to the ISP. FeedBlitz’s SMTP servers then send your mailing to the receiving ISP’s servers. Step 4 – ISP reputation check. The receiving ISP’s inbound email server runs a series of reputation checks (on the sender) and content scans (on the email). Step 5 – Receive, reject or quarantine. The ISP will then either allow your email through, immediately reject it, or quarantine the email by sending it to a subscriber’s spam folder. Step 6 – Email received! (or bounced/rejected) FeedBlitz gets feedback on whether your email was received or recorded as a bounce/undeliverable.At any step of the process, deliverability and reputation checks can kick in and prevent your email from arriving. Luckily, the strict standards and practices many ESPs (like FeedBlitz!) have in place work to catch anything before the email even reaches outbound servers. They will also diligently monitor all feedback loops from ISPs and swiftly suspend any list whose feedback is not up to par. Actions you can take to boost your deliverability and sender reputation. Good email deliverability isn’t only in the hands of your ESP. You as a client can have a significant impact on your reputation with your subscribers, which can and will boost your individual deliverability success. Below are five action items you can do to help boost your own deliverability and sender reputation even further. Set up authentication for your sending domain.Authentication is an added layer of verification to let ISPs know you are the true, valid sender of the email and that you’ve okayed FeedBlitz to do that for you. It involves SPF, DKIM, and DMARC. However, DMARC is typically used by high-level enterprise clients.FeedBlitz servers send your campaigns on behalf of the sending email you supply. (Note: This is why you may notice your email reads via [email protected] in email apps like Gmail or Outlook.) Authentication provides additional validation by saying, “Yes! This email is from me, and I authorize FeedBlitz to send it on my behalf! But please show me as the true sender.”This reinforces the level of trust an ISP forms with you and your emails. Hello, reputation booster.Are you a FeedBlitz client and not sure where you stand on your authentication? Click here to log in and run a quick scan.And if you’re ready to put authentication into action for your FeedBlitz-support campaigns, these steps walk you through how to set things up for your account: Protect Your Brand with SPF and DKIM and What Is and How to Create a DMARC Profile.Keep an eye on engagement data for your campaigns.How your email is received by subscribers is a strong indicator of the reputation you have with your audience. Are they opening? Clicking? Complaining? Unsubscribing? These data points are very important to FeedBlitz, fellow ESPs, and to individual ISPs who decide whether to prioritize (or deprioritize!) your emails.Healthy engagement is the strongest indicator of a healthy mailing list. And everyone likes healthy when it comes to deliverability.In FeedBlitz, you can track engagement data for each campaign from the list dashboard, dive deeper into in on the individual mailing dashboards, or pull a full engagement report to see engagement data over a chosen period of time.Note: Not sure what a good open rate is? Check out this episode of Win the Inbox to learn more.Review your content strategy and email best practices.This may seem a bit broad, but it relates back to something in section 4 of this post: Your audience ultimately determines what is or is not spam.Along with your quality content, you want to deliver a smooth, seamless experience for your subscribers. This means taking into consideration details such as:– Are you mailing regularly? A consistent cadence sets your subscribers’ expectations and can heighten open rates.– Is your branding all connected? From your website to your email template, the colors, the images, etc.? This helps with brand recognition, emphasizing you are someone the subscriber knows, likes, and trusts. (Again, better engagement is the result!)– Are you sending the content your audience signed up to receive? This can be a big determining factor in the frequency of how often a subscriber opens your emails. Deliver on what you promised when they signed up!– Is your template accessible for different audiences? This is where font size, color contrast, alt text for images come into play. The easier your email is to read and engage with, the wider your audience can become.That’s a small selection of things to consider, but it’s a great start to creating a smooth experience for your subscribers.Subscribe to your own list.Somewhat related to actionable #3 above, subscribing to your own mailing list not only ensures the end-to-end subscriber experience is up to your standards but also lets you know immediately if your emails are potentially being routed to somewhere other than the inbox.This also falls into best practices as you’re able to view test emails across different platforms and devices before hitting send.Again, the idea is to make sure your subscribers are having a seamless experience with every campaign you send, so it’s always best to check on different devices and email agents when possible.Remove people who are no longer opening or clicking your emails.While FeedBlitz handles unsubscribes and bounces for you automatically, if there“s one thing the team recommends the most to clients across the board, it’s removing inactive subscribers. This keeps your list — and engagement data — healthy.If a subscriber hasn’t opened or clicked one of your mailings in 60+ days, chances are they’ve lost interest. So instead of keeping them on your list with the mindset of “a bigger list is a better list!” set them free and move forward.In FeedBlitz, there are two ways you can go about this: one would be to send a re-engagement campaign and check if these inactive subscribers are still interested in sticking around, and the other would be to identify and remove them in one fell swoop. The choice is yours. Just remember, the name of the game is healthy, engaged mailing lists! Some of these action items you can work on and complete right away, and others you may choose to take a week or month to focus on. Either way, the suggestions outlined above will not only have a positive impact on your deliverability but also on the relationships you have with your subscribers. How FeedBlitz safeguards and boosts deliverability. In this section, you will learn some of the secrets, standards and practices FeedBlitz has in place to protect and boost email deliverability. These practices not only keep our clients’ emails going but allow us to consistently maintain our industry-leading deliverability rate of 99.8%. When an ESP works hard to safeguard their reputation, they’re also working hard to safeguard yours. It’s important to take deliverability practices into consideration if you’re comparing ESPs to see which is a good fit for you. While an ESP may not go into great detail on their in-house practices, you’re welcome to use the six items outlined below as a guideline for questions to ask. Without going into too much detail — we do have to protect some industry secrets, and we’re highly aware that bad actors read this to learn how to try and skirt the rules — below are six deliverability-related items you may find interesting. (Or, at the very least, you may find them insightful if you’ve ever had a list suspended or mailing halted!) We own all of our servers.That means when you’re sending with FeedBlitz, you’re not sharing a server with anyone who hasn’t been well-vetted or anyone who also isn’t being monitored 24/7/365. We have complete control over our infrastructure.Owning our own servers is hugely important. Some ESPs do not own their servers, and ultimately, they do not have full control over their reputation management. This leaves you vulnerable to your emails being potentially stopped if an unknown bad actor sends from the shared server your emails are sending from, the entire server, and everyone on it, is taken down.When this happens, the server’s IP can be added to a blocked list which is monitored by ISPs (who then reject your emails, not letting them through the door), as well as third-party lists many ISPs check as well — all because of emails you didn’t even send!One bad apple really can ruin the barrel in these situations…which is why FeedBlitz doesn’t cut corners when it comes to protecting deliverability. Feedback loops and changes with major ISPs (i.e., Gmail, Yahoo, Comcast, etc.) are constantly monitored.Meaning, we keep very close tabs on things such as how your audience interacts with your emails, any rejections or bounces which come through, oddly large groups of hard bounces, and velocity-based triggers. Resulting in your email having the best chance of getting through to your subscriber.As part of the monitoring process, if one of our servers is being throttled by an ISP, your campaigns will be quickly routed away from the machines in question so they can continue sending while further research is completed on the server and IP.If an ISP has cleared out a batch of old or undeliverable emails, we’ll confirm this is correct and not merely a glitch in the email ecosystem.Every email list and every subscriber is checked before they’re even allowed in the door.And that is not an understatement. It doesn’t matter if you have 10 subscribers or 10 million subscribers, each and everyone is checked against our own set of internal block lists, matched against 3rd party known purchased or rented lists, and will result in immediate suspension — and quite possibly being blocked from FeedBlitz all together — if an email address returns as a spam trap.We ruthlessly guard imports to protect the reputation of all FeedBlitz clients. If a list is suspended due to a blocked import or poor quality metrics (more on this below), it will remain suspended for at least 24 hours while the import file is being reviewed. After reviewing, the deliverability team will evaluate whether or not the import will be allowed to proceed and if the list will be reinstated.To put it plainly, we check receipts on each and every subscriber you try to bring into our home so our clients can rest easy knowing everyone is held to the same high level of quality control.Before you’re able to leave the editor, your emails go through the same content filters ISPs will run when deciding whether to allow or deny your email entry to the subscriber.Step four in the process listed above is where the destination ISP runs a series of checks to then decide what to do with your email.FeedBlitz created a series of content-based checks within the Visual Mailing Editor (VME) to mirror those an ISP will run.And while the industry has evolved quite a bit, and there is less emphasis on the presence of common spam/trigger words when it comes to deciding whether to allow your email through or not, it is still a factor to take into consideration.These content scans are also a safeguard against making sure your account has not been compromised.It’s frustrating, but bad emails can still come from good places, and that’s why multiple checks and balances are in place throughout the email creation and sending process to help ensure the success of your efforts.Important note: Because reputation extends to the links in your emails as well, this is why FeedBlitz doesn’t even allow an email that links out to a bad IP to be sent. We’re always looking out for you!How your subscribers engage with your mailings has a big effect.Just because a mailing passes our filters, ultimately, it’s up to your audience to decide whether or not it’s spam.Even if your email isn’t flagged as spam, ISPs (and FeedBlitz!) track all feedback from subscribers in how they interact with your mailings.This includes opens, clicks, and unsubscribes. It all has an impact on your deliverability. ISPs keep just as close tabs on this as we do. For example, when emails aren’t opened frequently, a subscriber’s ISP makes note of this and can demote or deprioritize them.FYI: If a mailing comes back with a lot of unsubscribes or complaints, it’s suspended in FeedBlitz for at least 24 hours while our team conducts a thorough review.This all works to keep your reputation and the reputation of all FeedBlitz clients in as good of standing as possible. And as you’ve probably picked up on by now, we don’t play around when it comes to sending reputations.New practices are regularly implemented.As the world of email evolves, so do we. Our team continually adjusts our in-house practices and protocols, as well as implementing new items. For example…– In April of 2022, we informed clients our deliverability team was increasing our email capacity by 40% by warming up a new batch of servers. Deliverability ✅– Large lists with a very low open rate (
0 notes
Photo

You can create the best email in the world, but it won’t matter if it doesn’t make it to your subscriber. And that’s why it’s vitally important you work with an email service provider (like FeedBlitz!) who places the highest possible focus and dedication on their deliverability practices. But what does deliverability mean? And how and when does it actually happen? And is there anything you can do to help? The answers to those questions and many more are what you will find in this post. There’s a lot of ground to cover when it comes to email deliverability, so without further delay, let’s jump right in. In this post, you’ll learn: What is email deliverability? Deliverability is a fairly common buzzword in the world of email marketing. However, unless you’re in the business of establishing and safeguarding it — or have had your email efforts impacted because of the lack of it — there isn’t a lot of clarity around the term and how companies achieve, monitor, and protect a high deliverability status. In the simplest of terms, deliverability is the processes and protections that allow your emails to reach your subscribers. It sounds pretty simple, but everything that takes place to get your emails from creation to open is much more complex. Knowing the ins and outs of email deliverability will help you make wiser decisions regarding your email marketing efforts. And it’ll also offer vitally important clarity when deciding which email service provider (ESP) to work with. Because again, you can design the prettiest emails possible, filled with the best content of your life, but it all means nothing if you’re with an ESP who cuts corners and your emails don’t actually get delivered. Key terms related to email deliverability. Anytime you’re working with a complex topic, starting with a foundation of key terms is best. The following terms will be helpful to know as you dig deeper into this blog post: Deliverability – getting your emails to a subscriber.Inboxing – getting your emails to a subscriber’s inbox (including Gmail’s promotions tab) as opposed to the spam folder.Reputation – receiving internet service providers (ISPs) review, judge, and estimate the safety of emails being sent by a particular email address — based on their own top-secret set of rules and guidelines — which ultimately determines whether your email will be allowed or denied.Authentication – a process to further validate the sender of your emails established through SPF, DKIM and DMARC, which use DNS to ensure permission has been granted. What happens when you send an email? Deliverability checks are not something that takes place one time, in one specific step of the email sending process. It can — and does — happen at multiple stages of the process every time one of your emails begins to send. To help give you a better idea of how and when this can happen, we’ll start with all the things that happen when you send an email, i.e., the path your email takes from the moment it begins sending to its arrival at your subscriber’s door. There are many more steps than you may realize, and that’s because most of the process takes place behind the scenes. The full process is a bit more nuanced and detailed than what’s outlined here, but the six steps highlighted below will give you a solid frame of reference for the process. While most ESPs follow similar, if not the same steps, below is a FeedBlitz-specific version to help show additional checks performed throughout the way: Step 1 – You create an email. And when working in FeedBlitz, before you’re even able to send or schedule the mailing, the content is checked against our in-house protocols. For example, you won’t even be allowed to send an email that may potentially be rejected by ISPs. Step 2 – The email begins sending. A unique email copy is created for each subscriber and sent to one of our outbound SMTP servers. (SMTP = the internet’s email protocol) Step 3 – Our SMTP servers send the email to the ISP. FeedBlitz’s SMTP servers then send your mailing to the receiving ISP’s servers. Step 4 – ISP reputation check. The receiving ISP’s inbound email server runs a series of reputation checks (on the sender) and content scans (on the email). Step 5 – Receive, reject or quarantine. The ISP will then either allow your email through, immediately reject it, or quarantine the email by sending it to a subscriber’s spam folder. Step 6 – Email received! (or bounced/rejected) FeedBlitz gets feedback on whether your email was received or recorded as a bounce/undeliverable.At any step of the process, deliverability and reputation checks can kick in and prevent your email from arriving. Luckily, the strict standards and practices many ESPs (like FeedBlitz!) have in place work to catch anything before the email even reaches outbound servers. They will also diligently monitor all feedback loops from ISPs and swiftly suspend any list whose feedback is not up to par. Actions you can take to boost your deliverability and sender reputation. Good email deliverability isn’t only in the hands of your ESP. You as a client can have a significant impact on your reputation with your subscribers, which can and will boost your individual deliverability success. Below are five action items you can do to help boost your own deliverability and sender reputation even further. Set up authentication for your sending domain.Authentication is an added layer of verification to let ISPs know you are the true, valid sender of the email and that you’ve okayed FeedBlitz to do that for you. It involves SPF, DKIM, and DMARC. However, DMARC is typically used by high-level enterprise clients.FeedBlitz servers send your campaigns on behalf of the sending email you supply. (Note: This is why you may notice your email reads via [email protected] in email apps like Gmail or Outlook.) Authentication provides additional validation by saying, “Yes! This email is from me, and I authorize FeedBlitz to send it on my behalf! But please show me as the true sender.”This reinforces the level of trust an ISP forms with you and your emails. Hello, reputation booster.Are you a FeedBlitz client and not sure where you stand on your authentication? Click here to log in and run a quick scan.And if you’re ready to put authentication into action for your FeedBlitz-support campaigns, these steps walk you through how to set things up for your account: Protect Your Brand with SPF and DKIM and What Is and How to Create a DMARC Profile.Keep an eye on engagement data for your campaigns.How your email is received by subscribers is a strong indicator of the reputation you have with your audience. Are they opening? Clicking? Complaining? Unsubscribing? These data points are very important to FeedBlitz, fellow ESPs, and to individual ISPs who decide whether to prioritize (or deprioritize!) your emails.Healthy engagement is the strongest indicator of a healthy mailing list. And everyone likes healthy when it comes to deliverability.In FeedBlitz, you can track engagement data for each campaign from the list dashboard, dive deeper into in on the individual mailing dashboards, or pull a full engagement report to see engagement data over a chosen period of time.Note: Not sure what a good open rate is? Check out this episode of Win the Inbox to learn more.Review your content strategy and email best practices.This may seem a bit broad, but it relates back to something in section 4 of this post: Your audience ultimately determines what is or is not spam.Along with your quality content, you want to deliver a smooth, seamless experience for your subscribers. This means taking into consideration details such as:– Are you mailing regularly? A consistent cadence sets your subscribers’ expectations and can heighten open rates.– Is your branding all connected? From your website to your email template, the colors, the images, etc.? This helps with brand recognition, emphasizing you are someone the subscriber knows, likes, and trusts. (Again, better engagement is the result!)– Are you sending the content your audience signed up to receive? This can be a big determining factor in the frequency of how often a subscriber opens your emails. Deliver on what you promised when they signed up!– Is your template accessible for different audiences? This is where font size, color contrast, alt text for images come into play. The easier your email is to read and engage with, the wider your audience can become.That’s a small selection of things to consider, but it’s a great start to creating a smooth experience for your subscribers.Subscribe to your own list.Somewhat related to actionable #3 above, subscribing to your own mailing list not only ensures the end-to-end subscriber experience is up to your standards but also lets you know immediately if your emails are potentially being routed to somewhere other than the inbox.This also falls into best practices as you’re able to view test emails across different platforms and devices before hitting send.Again, the idea is to make sure your subscribers are having a seamless experience with every campaign you send, so it’s always best to check on different devices and email agents when possible.Remove people who are no longer opening or clicking your emails.While FeedBlitz handles unsubscribes and bounces for you automatically, if there“s one thing the team recommends the most to clients across the board, it’s removing inactive subscribers. This keeps your list — and engagement data — healthy.If a subscriber hasn’t opened or clicked one of your mailings in 60+ days, chances are they’ve lost interest. So instead of keeping them on your list with the mindset of “a bigger list is a better list!” set them free and move forward.In FeedBlitz, there are two ways you can go about this: one would be to send a re-engagement campaign and check if these inactive subscribers are still interested in sticking around, and the other would be to identify and remove them in one fell swoop. The choice is yours. Just remember, the name of the game is healthy, engaged mailing lists! Some of these action items you can work on and complete right away, and others you may choose to take a week or month to focus on. Either way, the suggestions outlined above will not only have a positive impact on your deliverability but also on the relationships you have with your subscribers. How FeedBlitz safeguards and boosts deliverability. In this section, you will learn some of the secrets, standards and practices FeedBlitz has in place to protect and boost email deliverability. These practices not only keep our clients’ emails going but allow us to consistently maintain our industry-leading deliverability rate of 99.8%. When an ESP works hard to safeguard their reputation, they’re also working hard to safeguard yours. It’s important to take deliverability practices into consideration if you’re comparing ESPs to see which is a good fit for you. While an ESP may not go into great detail on their in-house practices, you’re welcome to use the six items outlined below as a guideline for questions to ask. Without going into too much detail — we do have to protect some industry secrets, and we’re highly aware that bad actors read this to learn how to try and skirt the rules — below are six deliverability-related items you may find interesting. (Or, at the very least, you may find them insightful if you’ve ever had a list suspended or mailing halted!) We own all of our servers.That means when you’re sending with FeedBlitz, you’re not sharing a server with anyone who hasn’t been well-vetted or anyone who also isn’t being monitored 24/7/365. We have complete control over our infrastructure.Owning our own servers is hugely important. Some ESPs do not own their servers, and ultimately, they do not have full control over their reputation management. This leaves you vulnerable to your emails being potentially stopped if an unknown bad actor sends from the shared server your emails are sending from, the entire server, and everyone on it, is taken down.When this happens, the server’s IP can be added to a blocked list which is monitored by ISPs (who then reject your emails, not letting them through the door), as well as third-party lists many ISPs check as well — all because of emails you didn’t even send!One bad apple really can ruin the barrel in these situations…which is why FeedBlitz doesn’t cut corners when it comes to protecting deliverability. Feedback loops and changes with major ISPs (i.e., Gmail, Yahoo, Comcast, etc.) are constantly monitored.Meaning, we keep very close tabs on things such as how your audience interacts with your emails, any rejections or bounces which come through, oddly large groups of hard bounces, and velocity-based triggers. Resulting in your email having the best chance of getting through to your subscriber.As part of the monitoring process, if one of our servers is being throttled by an ISP, your campaigns will be quickly routed away from the machines in question so they can continue sending while further research is completed on the server and IP.If an ISP has cleared out a batch of old or undeliverable emails, we’ll confirm this is correct and not merely a glitch in the email ecosystem.Every email list and every subscriber is checked before they’re even allowed in the door.And that is not an understatement. It doesn’t matter if you have 10 subscribers or 10 million subscribers, each and everyone is checked against our own set of internal block lists, matched against 3rd party known purchased or rented lists, and will result in immediate suspension — and quite possibly being blocked from FeedBlitz all together — if an email address returns as a spam trap.We ruthlessly guard imports to protect the reputation of all FeedBlitz clients. If a list is suspended due to a blocked import or poor quality metrics (more on this below), it will remain suspended for at least 24 hours while the import file is being reviewed. After reviewing, the deliverability team will evaluate whether or not the import will be allowed to proceed and if the list will be reinstated.To put it plainly, we check receipts on each and every subscriber you try to bring into our home so our clients can rest easy knowing everyone is held to the same high level of quality control.Before you’re able to leave the editor, your emails go through the same content filters ISPs will run when deciding whether to allow or deny your email entry to the subscriber.Step four in the process listed above is where the destination ISP runs a series of checks to then decide what to do with your email.FeedBlitz created a series of content-based checks within the Visual Mailing Editor (VME) to mirror those an ISP will run.And while the industry has evolved quite a bit, and there is less emphasis on the presence of common spam/trigger words when it comes to deciding whether to allow your email through or not, it is still a factor to take into consideration.These content scans are also a safeguard against making sure your account has not been compromised.It’s frustrating, but bad emails can still come from good places, and that’s why multiple checks and balances are in place throughout the email creation and sending process to help ensure the success of your efforts.Important note: Because reputation extends to the links in your emails as well, this is why FeedBlitz doesn’t even allow an email that links out to a bad IP to be sent. We’re always looking out for you!How your subscribers engage with your mailings has a big effect.Just because a mailing passes our filters, ultimately, it’s up to your audience to decide whether or not it’s spam.Even if your email isn’t flagged as spam, ISPs (and FeedBlitz!) track all feedback from subscribers in how they interact with your mailings.This includes opens, clicks, and unsubscribes. It all has an impact on your deliverability. ISPs keep just as close tabs on this as we do. For example, when emails aren’t opened frequently, a subscriber’s ISP makes note of this and can demote or deprioritize them.FYI: If a mailing comes back with a lot of unsubscribes or complaints, it’s suspended in FeedBlitz for at least 24 hours while our team conducts a thorough review.This all works to keep your reputation and the reputation of all FeedBlitz clients in as good of standing as possible. And as you’ve probably picked up on by now, we don’t play around when it comes to sending reputations.New practices are regularly implemented.As the world of email evolves, so do we. Our team continually adjusts our in-house practices and protocols, as well as implementing new items. For example…– In April of 2022, we informed clients our deliverability team was increasing our email capacity by 40% by warming up a new batch of servers. Deliverability ✅– Large lists with a very low open rate (
0 notes
Photo

You can create the best email in the world, but it won’t matter if it doesn’t make it to your subscriber. And that’s why it’s vitally important you work with an email service provider (like FeedBlitz!) who places the highest possible focus and dedication on their deliverability practices. But what does deliverability mean? And how and when does it actually happen? And is there anything you can do to help? The answers to those questions and many more are what you will find in this post. There’s a lot of ground to cover when it comes to email deliverability, so without further delay, let’s jump right in. In this post, you’ll learn: What is email deliverability? Deliverability is a fairly common buzzword in the world of email marketing. However, unless you’re in the business of establishing and safeguarding it — or have had your email efforts impacted because of the lack of it — there isn’t a lot of clarity around the term and how companies achieve, monitor, and protect a high deliverability status. In the simplest of terms, deliverability is the processes and protections that allow your emails to reach your subscribers. It sounds pretty simple, but everything that takes place to get your emails from creation to open is much more complex. Knowing the ins and outs of email deliverability will help you make wiser decisions regarding your email marketing efforts. And it’ll also offer vitally important clarity when deciding which email service provider (ESP) to work with. Because again, you can design the prettiest emails possible, filled with the best content of your life, but it all means nothing if you’re with an ESP who cuts corners and your emails don’t actually get delivered. Key terms related to email deliverability. Anytime you’re working with a complex topic, starting with a foundation of key terms is best. The following terms will be helpful to know as you dig deeper into this blog post: Deliverability – getting your emails to a subscriber.Inboxing – getting your emails to a subscriber’s inbox (including Gmail’s promotions tab) as opposed to the spam folder.Reputation – receiving internet service providers (ISPs) review, judge, and estimate the safety of emails being sent by a particular email address — based on their own top-secret set of rules and guidelines — which ultimately determines whether your email will be allowed or denied.Authentication – a process to further validate the sender of your emails established through SPF, DKIM and DMARC, which use DNS to ensure permission has been granted. What happens when you send an email? Deliverability checks are not something that takes place one time, in one specific step of the email sending process. It can — and does — happen at multiple stages of the process every time one of your emails begins to send. To help give you a better idea of how and when this can happen, we’ll start with all the things that happen when you send an email, i.e., the path your email takes from the moment it begins sending to its arrival at your subscriber’s door. There are many more steps than you may realize, and that’s because most of the process takes place behind the scenes. The full process is a bit more nuanced and detailed than what’s outlined here, but the six steps highlighted below will give you a solid frame of reference for the process. While most ESPs follow similar, if not the same steps, below is a FeedBlitz-specific version to help show additional checks performed throughout the way: Step 1 – You create an email. And when working in FeedBlitz, before you’re even able to send or schedule the mailing, the content is checked against our in-house protocols. For example, you won’t even be allowed to send an email that may potentially be rejected by ISPs. Step 2 – The email begins sending. A unique email copy is created for each subscriber and sent to one of our outbound SMTP servers. (SMTP = the internet’s email protocol) Step 3 – Our SMTP servers send the email to the ISP. FeedBlitz’s SMTP servers then send your mailing to the receiving ISP’s servers. Step 4 – ISP reputation check. The receiving ISP’s inbound email server runs a series of reputation checks (on the sender) and content scans (on the email). Step 5 – Receive, reject or quarantine. The ISP will then either allow your email through, immediately reject it, or quarantine the email by sending it to a subscriber’s spam folder. Step 6 – Email received! (or bounced/rejected) FeedBlitz gets feedback on whether your email was received or recorded as a bounce/undeliverable.At any step of the process, deliverability and reputation checks can kick in and prevent your email from arriving. Luckily, the strict standards and practices many ESPs (like FeedBlitz!) have in place work to catch anything before the email even reaches outbound servers. They will also diligently monitor all feedback loops from ISPs and swiftly suspend any list whose feedback is not up to par. Actions you can take to boost your deliverability and sender reputation. Good email deliverability isn’t only in the hands of your ESP. You as a client can have a significant impact on your reputation with your subscribers, which can and will boost your individual deliverability success. Below are five action items you can do to help boost your own deliverability and sender reputation even further. Set up authentication for your sending domain.Authentication is an added layer of verification to let ISPs know you are the true, valid sender of the email and that you’ve okayed FeedBlitz to do that for you. It involves SPF, DKIM, and DMARC. However, DMARC is typically used by high-level enterprise clients.FeedBlitz servers send your campaigns on behalf of the sending email you supply. (Note: This is why you may notice your email reads via [email protected] in email apps like Gmail or Outlook.) Authentication provides additional validation by saying, “Yes! This email is from me, and I authorize FeedBlitz to send it on my behalf! But please show me as the true sender.”This reinforces the level of trust an ISP forms with you and your emails. Hello, reputation booster.Are you a FeedBlitz client and not sure where you stand on your authentication? Click here to log in and run a quick scan.And if you’re ready to put authentication into action for your FeedBlitz-support campaigns, these steps walk you through how to set things up for your account: Protect Your Brand with SPF and DKIM and What Is and How to Create a DMARC Profile.Keep an eye on engagement data for your campaigns.How your email is received by subscribers is a strong indicator of the reputation you have with your audience. Are they opening? Clicking? Complaining? Unsubscribing? These data points are very important to FeedBlitz, fellow ESPs, and to individual ISPs who decide whether to prioritize (or deprioritize!) your emails.Healthy engagement is the strongest indicator of a healthy mailing list. And everyone likes healthy when it comes to deliverability.In FeedBlitz, you can track engagement data for each campaign from the list dashboard, dive deeper into in on the individual mailing dashboards, or pull a full engagement report to see engagement data over a chosen period of time.Note: Not sure what a good open rate is? Check out this episode of Win the Inbox to learn more.Review your content strategy and email best practices.This may seem a bit broad, but it relates back to something in section 4 of this post: Your audience ultimately determines what is or is not spam.Along with your quality content, you want to deliver a smooth, seamless experience for your subscribers. This means taking into consideration details such as:– Are you mailing regularly? A consistent cadence sets your subscribers’ expectations and can heighten open rates.– Is your branding all connected? From your website to your email template, the colors, the images, etc.? This helps with brand recognition, emphasizing you are someone the subscriber knows, likes, and trusts. (Again, better engagement is the result!)– Are you sending the content your audience signed up to receive? This can be a big determining factor in the frequency of how often a subscriber opens your emails. Deliver on what you promised when they signed up!– Is your template accessible for different audiences? This is where font size, color contrast, alt text for images come into play. The easier your email is to read and engage with, the wider your audience can become.That’s a small selection of things to consider, but it’s a great start to creating a smooth experience for your subscribers.Subscribe to your own list.Somewhat related to actionable #3 above, subscribing to your own mailing list not only ensures the end-to-end subscriber experience is up to your standards but also lets you know immediately if your emails are potentially being routed to somewhere other than the inbox.This also falls into best practices as you’re able to view test emails across different platforms and devices before hitting send.Again, the idea is to make sure your subscribers are having a seamless experience with every campaign you send, so it’s always best to check on different devices and email agents when possible.Remove people who are no longer opening or clicking your emails.While FeedBlitz handles unsubscribes and bounces for you automatically, if there“s one thing the team recommends the most to clients across the board, it’s removing inactive subscribers. This keeps your list — and engagement data — healthy.If a subscriber hasn’t opened or clicked one of your mailings in 60+ days, chances are they’ve lost interest. So instead of keeping them on your list with the mindset of “a bigger list is a better list!” set them free and move forward.In FeedBlitz, there are two ways you can go about this: one would be to send a re-engagement campaign and check if these inactive subscribers are still interested in sticking around, and the other would be to identify and remove them in one fell swoop. The choice is yours. Just remember, the name of the game is healthy, engaged mailing lists! Some of these action items you can work on and complete right away, and others you may choose to take a week or month to focus on. Either way, the suggestions outlined above will not only have a positive impact on your deliverability but also on the relationships you have with your subscribers. How FeedBlitz safeguards and boosts deliverability. In this section, you will learn some of the secrets, standards and practices FeedBlitz has in place to protect and boost email deliverability. These practices not only keep our clients’ emails going but allow us to consistently maintain our industry-leading deliverability rate of 99.8%. When an ESP works hard to safeguard their reputation, they’re also working hard to safeguard yours. It’s important to take deliverability practices into consideration if you’re comparing ESPs to see which is a good fit for you. While an ESP may not go into great detail on their in-house practices, you’re welcome to use the six items outlined below as a guideline for questions to ask. Without going into too much detail — we do have to protect some industry secrets, and we’re highly aware that bad actors read this to learn how to try and skirt the rules — below are six deliverability-related items you may find interesting. (Or, at the very least, you may find them insightful if you’ve ever had a list suspended or mailing halted!) We own all of our servers.That means when you’re sending with FeedBlitz, you’re not sharing a server with anyone who hasn’t been well-vetted or anyone who also isn’t being monitored 24/7/365. We have complete control over our infrastructure.Owning our own servers is hugely important. Some ESPs do not own their servers, and ultimately, they do not have full control over their reputation management. This leaves you vulnerable to your emails being potentially stopped if an unknown bad actor sends from the shared server your emails are sending from, the entire server, and everyone on it, is taken down.When this happens, the server’s IP can be added to a blocked list which is monitored by ISPs (who then reject your emails, not letting them through the door), as well as third-party lists many ISPs check as well — all because of emails you didn’t even send!One bad apple really can ruin the barrel in these situations…which is why FeedBlitz doesn’t cut corners when it comes to protecting deliverability. Feedback loops and changes with major ISPs (i.e., Gmail, Yahoo, Comcast, etc.) are constantly monitored.Meaning, we keep very close tabs on things such as how your audience interacts with your emails, any rejections or bounces which come through, oddly large groups of hard bounces, and velocity-based triggers. Resulting in your email having the best chance of getting through to your subscriber.As part of the monitoring process, if one of our servers is being throttled by an ISP, your campaigns will be quickly routed away from the machines in question so they can continue sending while further research is completed on the server and IP.If an ISP has cleared out a batch of old or undeliverable emails, we’ll confirm this is correct and not merely a glitch in the email ecosystem.Every email list and every subscriber is checked before they’re even allowed in the door.And that is not an understatement. It doesn’t matter if you have 10 subscribers or 10 million subscribers, each and everyone is checked against our own set of internal block lists, matched against 3rd party known purchased or rented lists, and will result in immediate suspension — and quite possibly being blocked from FeedBlitz all together — if an email address returns as a spam trap.We ruthlessly guard imports to protect the reputation of all FeedBlitz clients. If a list is suspended due to a blocked import or poor quality metrics (more on this below), it will remain suspended for at least 24 hours while the import file is being reviewed. After reviewing, the deliverability team will evaluate whether or not the import will be allowed to proceed and if the list will be reinstated.To put it plainly, we check receipts on each and every subscriber you try to bring into our home so our clients can rest easy knowing everyone is held to the same high level of quality control.Before you’re able to leave the editor, your emails go through the same content filters ISPs will run when deciding whether to allow or deny your email entry to the subscriber.Step four in the process listed above is where the destination ISP runs a series of checks to then decide what to do with your email.FeedBlitz created a series of content-based checks within the Visual Mailing Editor (VME) to mirror those an ISP will run.And while the industry has evolved quite a bit, and there is less emphasis on the presence of common spam/trigger words when it comes to deciding whether to allow your email through or not, it is still a factor to take into consideration.These content scans are also a safeguard against making sure your account has not been compromised.It’s frustrating, but bad emails can still come from good places, and that’s why multiple checks and balances are in place throughout the email creation and sending process to help ensure the success of your efforts.Important note: Because reputation extends to the links in your emails as well, this is why FeedBlitz doesn’t even allow an email that links out to a bad IP to be sent. We’re always looking out for you!How your subscribers engage with your mailings has a big effect.Just because a mailing passes our filters, ultimately, it’s up to your audience to decide whether or not it’s spam.Even if your email isn’t flagged as spam, ISPs (and FeedBlitz!) track all feedback from subscribers in how they interact with your mailings.This includes opens, clicks, and unsubscribes. It all has an impact on your deliverability. ISPs keep just as close tabs on this as we do. For example, when emails aren’t opened frequently, a subscriber’s ISP makes note of this and can demote or deprioritize them.FYI: If a mailing comes back with a lot of unsubscribes or complaints, it’s suspended in FeedBlitz for at least 24 hours while our team conducts a thorough review.This all works to keep your reputation and the reputation of all FeedBlitz clients in as good of standing as possible. And as you’ve probably picked up on by now, we don’t play around when it comes to sending reputations.New practices are regularly implemented.As the world of email evolves, so do we. Our team continually adjusts our in-house practices and protocols, as well as implementing new items. For example…– In April of 2022, we informed clients our deliverability team was increasing our email capacity by 40% by warming up a new batch of servers. Deliverability ✅– Large lists with a very low open rate (
0 notes
Text
How Accurate Data Drives Better Business Outcomes...

When you’re running a race with a faulty map, you might sprint ahead for a while, but soon you’ll find yourself lost, off-course, and frustrated. That’s exactly what poor data accuracy does to businesses.
Without reliable data, strategies falter, leads dry up, and business outcomes become an endless uphill struggle. In the B2B world, where every decision counts, accurate data is more than just a nice-to-have—it’s the compass that steers your business toward success.
The Problem with Poor Data Accuracy
Bad data is like a silent thief. It creeps into your CRM, misguides your teams, and wastes precious resources.
A study by Harvard Business Review found that bad data costs businesses over $3 trillion annually.
Inaccurate email addresses, outdated phone numbers, or mismatched company details lead to failed outreach, lost leads, and missed opportunities. Worse, it erodes trust between sales and marketing teams, creating silos that slow down your growth.
At its core, inaccurate data isn’t just about wrong numbers—it’s about wrong outcomes. It results in chasing unqualified leads, failing to engage with the right audience, and crafting strategies based on flawed insights.
For a B2B marketer or sales team, this can mean the difference between closing deals or closing shop.
Why Accurate Data?
Accurate data drives better business outcomes because it acts as the backbone of every successful lead generation and sales strategy.
Here’s why:
>>>Precision Targeting: Accurate data ensures that your campaigns reach the right audience at the right time. Imagine running an email campaign where every recipient fits your Ideal Customer Profile (ICP). No more spraying and praying—just targeted, meaningful outreach.
>>>Streamlined Workflows: When sales teams work with clean data, they save time and energy. No more double-checking email lists or second-guessing phone numbers. Instead, they can focus on what they do best—selling.
>>>Informed Decision-Making: Data validation allows businesses to derive actionable insights that aren’t clouded by inaccuracies. Better decisions mean stronger strategies, higher ROI, and a competitive edge in your industry.
>>>Boosted ROI: Poor data leads to higher marketing costs and wasted ad spend. Accurate data, however, optimizes every dollar spent, making your efforts more cost-effective.
How Our Fierce Badgers Tackle the Data Challenge
At B2BinDemand, we don’t just address the symptoms of bad data—we eliminate the root cause. Our data validation tools and processes ensure that every lead entering your funnel is accurate, updated, and ready to convert.
We help your businesses filter out the noise, leaving only high-quality leads that match your ICP.
For example, our advanced lead-gen strategies use real-time data validation to ensure the leads you pursue are primed for engagement. No dead-end emails. No outdated contacts. Just leads that work.
The Bigger Picture
In the B2B world, data is currency. But like any currency, its value depends on its authenticity. Businesses that prioritize data accuracy are more likely to thrive, scaling faster and more efficiently than their competitors.
So, ask yourself: Is your data holding you back or propelling you forward? With accurate data, the path to better business outcomes is clear, focused, and within reach.
Let’s ensure your business runs with the right map—one built on accuracy, reliability, and growth.
________________________________________
Engage with us: What’s been your biggest challenge with data accuracy? Let’s share ideas and solutions in the comments below!
Got questions? Reach out to our prominent badgers in the industry now: [email protected]
1 note
·
View note
Text
email list verify,
email list verify,
In the world of digital marketing, building and maintaining an effective email list is crucial for the success of your campaigns. However, as your list grows, so does the risk of it becoming cluttered with invalid or outdated email addresses. This is where email list verification comes into play. In this article, we'll explore the significance of email list verification, its benefits, and how to effectively implement it in your marketing strategy.
What is Email List Verification?
Email list verification is the process of checking email addresses to determine their validity. This involves identifying and removing incorrect, inactive, or temporary email addresses from your list. By doing so, you can ensure that your email campaigns reach real, engaged recipients.
Why is Email List Verification Important?
Improved Deliverability Rates: Validating email addresses reduces bounce rates, which can negatively impact your sender reputation. A clean list helps ensure that your emails reach the inbox rather than being marked as spam.
Increased Engagement: Sending emails to verified addresses means your messages are more likely to be opened and read. Engaged subscribers contribute to higher click-through rates and conversions.
Cost Efficiency: Many email marketing services charge based on the size of your list. By verifying and removing invalid addresses, you can reduce costs associated with sending emails to unresponsive recipients.
Enhanced Sender Reputation: A good sender reputation is vital for successful email campaigns. Regular verification helps maintain your reputation by ensuring you’re only sending emails to valid addresses.
Better Analytics: Clean email lists provide more accurate metrics. You can gain insights into your audience’s behavior and preferences without the noise of invalid addresses skewing your data.
Best Practices for Email List Verification
Use a Verification Tool: Invest in a reputable email verification tool to automate the process. These tools can quickly identify invalid or temporary addresses, saving you time and effort.
Verify During Signup: Implement real-time verification during the signup process. This helps capture valid addresses and reduces the likelihood of adding invalid ones from the start.
Regularly Clean Your List: Schedule regular list cleanups—every 3 to 6 months—to verify existing addresses. This ensures your list remains up to date and relevant.
Monitor Engagement: Keep an eye on engagement metrics. If a subscriber hasn’t interacted with your emails for a significant period, consider removing them from your list.
Implement a Re-Engagement Campaign: For subscribers who haven’t engaged in a while, run a re-engagement campaign to gauge their interest. If they don’t respond, it’s best to remove them from your list.
Conclusion
Email list verification is an essential practice for anyone looking to run successful email marketing campaigns. By maintaining a clean and valid email list, you can improve deliverability, increase engagement, and optimize your marketing budget. Implementing effective verification processes will not only enhance your campaigns but also strengthen your relationship with your audience. Don’t overlook the power of a verified email list—start verifying today for better results tomorrow!
0 notes
Text
WagesCoin (WGS) Welcome Bonus: Kickstart Your Crypto Portfolio Today

Are you prepared to take a deep dive into the cryptocurrency space and make your first investment? WagesCoin (WGS) provides an amazing chance to do that. You can quickly increase your cryptocurrency holdings and begin investigating the fascinating possibilities of this virtual asset with its substantial welcome bonus. We'll walk you through the process of claiming your WGS welcome bonus and fully using this valuable offer in this blog article.
What is Wages Coin (WGS)?
One innovative cryptocurrency that seeks to make financial transactions easier for customers everywhere is Wages Coin (WGS). WGS seeks to provide a decentralized platform where users may perform transactions with cheap fees, great security, and unrivaled speed. It is founded on reliable and secure multichain technology.How to Claim Your Welcome Bonus?
Simply follow these simple steps to get your Wages Coin welcome bonus:
Register a New Account: On the homepage, look for the sign-up area. You will be asked for some basic details, such as your email address and a secure password. To avoid any issues getting your bonus, make sure the data you supply is accurate.
Verify your email: You will get a verification email after registering. To validate your account and get one step closer to getting your bonus, click the link that was sent to you in the email.
Full KYC Verification: You can be asked to go through a Know Your Customer (KYC) procedure to guarantee the platform's security and legal compliance. Usually, this means presenting identity paperwork.
Get Your WGS Tokens Here: The Wages Coin welcome bonus will be credited to your account after it has been validated. Depending on the conditions of the campaign, you might receive up to 50 WGS tokens.
Making the Most of Your WagesCoin Welcome Bonus
Upon obtaining your welcome bonus, there are many methods to optimize its worth:
Purchase additional cryptocurrencies: To buy other cryptocurrencies that fit with your investing objectives, use your WGS tokens. Look at various tokens and currencies to identify ones that have bright futures.
Participate in Staking: Staking incentives are a feature of several cryptocurrencies that allows you to earn more tokens just by keeping your assets in a wallet. Verify whether staking possibilities are available for WagesCoin or any other supported cryptocurrency.
Hold for Long-Term Gains: If you believe in the long-term potential of WagesCoin, you may simply hold onto your tokens and wait for their value to rise over time.
Start Your Journey with Wages Coin
With your welcome bonus, you're ready to begin your adventure into the world of cryptocurrencies. With Wages Coin's user-friendly platform, you may hold WGS tokens and take advantage of investment and transaction options to boost your WGS value.
Ready to Dive Into the World of Cryptocurrency?
The Wages Coin welcome bonus is more than just a gift; it is a portal to the numerous potential that digital finance offers. By enrolling and collecting your bonus, you're taking the initial step toward joining the financial sector of the future. Don't pass up this chance to learn more about Wages Coin and get a big boost to your cryptocurrency adventure.
Remember that the world of cryptocurrencies is large and continuously developing. Be sure to read up on responsible cryptocurrency management and investment. Greetings from Wages Coin, the beginning of your adventure into the world of digital finance.
For More Info:
Website : https://wgscoin.com/
Telegram : https://t.me/wagescoin
TikTok : www.tiktok.com/@wagescoin
1 note
·
View note