#WSUS Database
Explore tagged Tumblr posts
Text
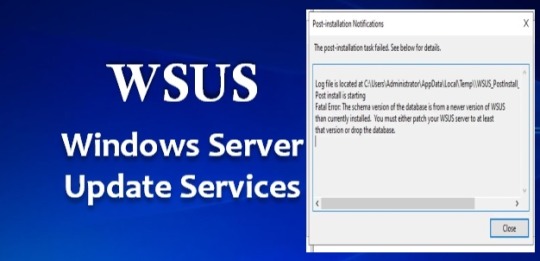
The schema version of the database is from a newer version of wsus
The WSUS installation from Server Manager fails with a fatal error stating, “The schema version of the database is from a newer version of WSUS than currently installed.” This error requires either patching the WSUS server to at least that version or dropping the database. Windows update indicates that the system is up to date. Please see how to delete ADFS Windows Internal Database without…
View On WordPress
#“WSUS Post-deployment Configuration Failed#Microsoft Windows#Remove Roles and Remove features#The schema version of the database#When prompted with the "Remove Roles and features Wizard"#Windows Internal Database (WID)#Windows Server 2012#Windows Server 2016#Windows Server 2019#Windows Server 2022#Windows Server 2025#WSUS#WSUS Database#WSUS Updates (Windows Server Update Services
0 notes
Text
Earn Your Online DBA Degree: A Smart Move for Ambitious Professionals
In today’s competitive business environment, a Doctorate in Business Administration (DBA) can elevate your career to new heights. If you're a working professional seeking flexibility, an Online DBA degree could be the perfect solution.
Why Pursue an Online DBA Degree?
The demand for leadership roles in global business continues to rise. With technology enabling remote learning, an Online DBA offers the academic rigor of a traditional doctorate with the flexibility to study from anywhere.
Benefits of an Online DBA Program
Flexibility: Study on your schedule while balancing work and personal life.
Affordability: Save on travel, relocation, and campus fees.
Global Networking: Connect with peers, professors, and industry experts across the globe.
Immediate Application: Apply your learning in real-time to your workplace challenges.
Who Should Consider a DBA for Working Professionals?
A DBA for working professionals is tailored to experienced individuals who want to:
Advance into executive roles
Transition into academic or consulting careers
Lead organizational change with research-backed strategies
Enhance decision-making with a data-driven mindset
This degree is not just about theoretical knowledge — it’s about real-world impact.
What Makes a Great Online DBA Program?
When choosing where to earn your Online DBA degree, consider the following:
Accreditation and Reputation
Ensure the institution is accredited and recognized for academic excellence. A reputable university like Western State University (WSU) offers a robust curriculum led by seasoned faculty.
Curriculum Design
Look for programs that blend theoretical knowledge with practical application, and offer concentrations aligned with your career goals.
Support for Online Learners
Top programs provide resources such as:
Dedicated advisors
Online libraries and databases
Interactive learning platforms
Career and networking support
Career Opportunities After a Doctorate in Business Administration
Graduates with a Doctorate in Business Administration can pursue various high-level roles, such as:
Chief Executive Officer (CEO)
Chief Financial Officer (CFO)
Business Consultant
University Professor
Director of Operations
Why Choose WSU for Your Online DBA?
WSU offers an accredited, flexible, and research-intensive Online DBA designed for ambitious professionals. Whether you're aiming for a promotion, planning a career change, or pursuing academic roles, WSU prepares you to lead with confidence.
0 notes
Text
Server Patching Best Practices for Enterprise Patch Management
What Is Server Patching?
Server patching is the process of updating and applying security fixes, bug fixes, and performance improvements to server operating systems and applications. Effective enterprise patch management ensures that IT environments remain secure, stable, and compliant with industry regulations.
Why Is Server Patching Important?
✅ Enhances Security – Fixes vulnerabilities and prevents cyberattacks. ✅ Improves System Stability – Reduces crashes, bugs, and performance issues. ✅ Ensures Compliance – Meets regulatory standards (HIPAA, GDPR, PCI DSS, etc.). ✅ Reduces Downtime Risks – Prevents disruptions from outdated or vulnerable software.
Best Practices for Enterprise Patch Management
1. Establish a Patch Management Policy 📋
✔ Define clear roles and responsibilities for patching. ✔ Set patching schedules for critical, high, and low-priority updates. ✔ Include compliance requirements in the patching policy.
2. Conduct a Patch Risk Assessment ⚠️
✔ Identify high-risk vulnerabilities that need immediate attention. ✔ Evaluate the impact of patches on mission-critical systems. ✔ Test patches in a staging environment before deployment.
3. Automate Patch Deployment ⚙️
✔ Use patch management tools (e.g., WSUS, SCCM, Ansible, Ivanti, Automox). ✔ Automate patch scanning, testing, and deployment to reduce manual effort. ✔ Schedule updates outside peak business hours to minimize disruptions.
4. Prioritize Critical Security Updates 🔒
✔ Apply patches for zero-day vulnerabilities as soon as possible. ✔ Follow security bulletins from Microsoft, Linux, VMware, and other vendors. ✔ Ensure endpoint security tools are also updated.
5. Monitor Patch Compliance & Reporting 📊
✔ Track patching success rates and failed updates. ✔ Generate audit logs to meet regulatory requirements. ✔ Use SIEM (Security Information and Event Management) tools for monitoring.
6. Have a Rollback & Contingency Plan 🔄
✔ Backup systems before applying patches to prevent data loss. ✔ Implement rollback procedures in case a patch causes system instability. ✔ Test recovery strategies in a disaster recovery (DR) plan.
7. Keep Third-Party Software Updated 🖥️
✔ Patch browsers, databases, and applications alongside OS updates. ✔ Use vendor patch management solutions for consistency. ✔ Regularly audit and remove unsupported or end-of-life (EOL) software.
Common Challenges in Server Patching & Solutions
ChallengeSolutionDowntime ConcernsSchedule patches during off-peak hours and use rolling updates.Patch FailuresTest patches in a staging environment before deployment.Lack of AutomationUse patch management software to streamline updates.End-of-Life (EOL) SoftwareUpgrade or replace legacy systems to avoid security risks.Compliance AuditsMaintain detailed patch logs for regulatory reporting.
Final Thoughts: Strengthening Enterprise Security with Patching
A well-structured patch management strategy reduces security risks, improves system performance, and ensures compliance. By automating updates, prioritizing critical patches, and maintaining backups, businesses can protect their IT infrastructure from cyber threats.
Need Help with Enterprise Patch Management?
Tell me your server environment (Windows, Linux, hybrid cloud), compliance needs, and security concerns, and I’ll recommend the best patching strategy for your business!

0 notes
Text
Skin Regeneration Research, Endangered Syriac, Snapchat, More: Monday Afternoon ResearchBuzz, September 25, 2023
NEW RESOURCES Washington State University: WSU students create database to accelerate skin science. “The website — skinregeneration.org — was created for researchers but allows anyone to cross-compare information on more than 33,000 genes from different species as they relate to skin development, wound repair, and regeneration. Ultimately, it could help scientists reprogram adult skin for…
View On WordPress
0 notes
Text
Today we will talk about a list and names of the kings of ancient Egypt. The first dynasty ruled from about 3150 to 2890 BC. M. It is the first dynasty of Egyptian kings who ruled Egypt after its unification (Upper and Lower Egypt) by Narmer, who ruled after him eight kings, the most famous of whom were (Hor Aha), (Jar) and (Jet), and Queen (Merit Nate), who is the first ruling queen in ancient history , and represents the beginning of the Egyptian historical eras.
The fourth was in Sudan, and Thebes (today called Luxor) was the capital of this empire, and there the greatest temples and the most magnificent tombs were built. This was followed by the era of the third decline, and it includes families 21-25 (about 1085-663 BC), in which kings of Libyan origin ruled the country, including Sheshonq, Yokuris, and others of Nubian origin, the most famous of whom was Yankhi. As the Assyrians invaded, the Egyptians revolted and liberated the country from their control under the leadership of Psamtik I, who founded the 26th Dynasty (about 663 - 529 BC) and returned Egypt to its strength and the Renaissance began. Then the Persians took over the country and some powerful personalities succeeded in expelling them, but they returned throughout the 27 Dynasties. 30. The history of the pharaohs ended when Alexander the Great invaded Egypt and expelled the Persians in 332 BC. And then it was ruled by the Greek pharaohs of the Ptolemaic dynasty. The rule of this family ended when Egypt became an independent Roman province in 30 BC.[1]
The dates provided in this listing are approximate. They are based primarily on the traditional chronology of ancient Egypt, mostly based on the Egypt Digital Universities Database [2] developed by the Petrie Museum of Egyptian Antiquities, but alternative dates taken from other sources can be noted separately......
Kings names.
👇
Ptolemy IV
Ptolemy VII
Emperor Trajan
Emperor Tiberius Caesar
Emperor Caracalla
The names of the ancient Egyptian pharaohs
Pharaonic queens of Egypt
Queen Hatshepsut
Queen Ahmose-Nefertari
Queen Nefertiti
Queen Nefertari
Queen T
Queen Tuya
Queen Twosret
Queen Cleopatra
Queen Ahmose Enhaby
Queen Meritamun
Princess Neferure
Egyptian pharaohs
Minister we will die
Architect Imhotep
Engineer Habu
Engineer Ham Iono
Binozem I
King Ptolemy VI
King Ramses X
King Amenhotep III
King Amenhotep II
King Ramses XI
King Ahmose I
King Amenhotep the First
King Userkaf
King Unas
King i
King Harihor
King Nectanebo II
King Nectanebo I
King Taharqa
King Mentuhotep I
King Mentuhotep II
(The secret of Maat-Ra) (Mary-Amun)
King Ramesses V (User Maatre) (Sakhr En Ra)
King Ramesses VI (Neb Maatre) (Mari Amen)
King Ramses VII (User Ma'at Ra) (Mari Amen)
King Ramesses VIII (User Maatre) (Brother to Believe)
King Ramesses IX (Neferkare) (Step en Ra)
King Sekhnakht (Merre Ra) (Wsu-Kheu Ra) (Step En Ra)
King Ramses X (News of Maat Ra) (Step En Ra)
King Ramses XI (of Maat-Re) (Step-En-Ptah)

1 note
·
View note
Text
Finding Home (Gavin Reed x Reader)
Chapter One
I couldn’t believe I was back in Detroit. I honestly never planned on coming back after everything that had happened between me and my dad. I left Michigan to go get my PhD in Sociology from (dream school). However, my dissertation was over android and human sociological relationships and the moment I was approved, Wayne State University in Detroit recruited me and offered me an amazing deal for a brand-new professor. It made sense since Detroit was at the heart of the android revolution, which would make research even easier.
I moved into a basic apartment in June and now it’s early July. I had been avoided seeing old friends and family, telling them I had to unpack and work on my new class, SOC 345: Android and Human Relationships. Which wasn’t a complete lie, but I have been watch an unhealthy amount of cute cat videos and eating a lot of peanut butter toast alone too.
I told my dad I would meet him today, Monday, at the station so we could get lunch with his police partner, Connor. My dad had always hated androids, I still had a hard time believing he had basically taken Connor under his wing and from what Tina tells me, he treats him like a son.
I took a deep breath and walked into the DPD. I couldn’t help but feel anxious. I hadn’t seen my dad in over 10 years. When him and my mother divorced, he tried to stay in touch, but after my half-brother, Cole, died he pretty much disappeared from my life.
“Hey, dad!” I said, a little too enthusiastically as I walked towards his desk. Immediately the android in the desk across from him stood up and gave me a goofy smile.
“You must be Lieutenant Anderson’s daughter! My name’s Connor.” He reached out his hand for a handshake which I accepted with a smile.
“Hi Connor, I’m (y/n). It’s nice to finally meet you!” I looked over to my dad, who had awkwardly shuffled towards us.
“Hey, (y/n). How’s Detroit been treating you?” I reached over and gave him a short hug.
“It’s been good. Doing research is a lot easier here than back in (old state). Plus, WSU gave me a pretty nice office.” I rubbed my shoulder; my dad was about to ask another question when another voice interrupted.
“Dr. (L/n). I’ve read some of your research and wanted to introduce myself. People here call me Nines, but I am an RK900 from cyberlife. If you ever have time, I would be interested in discussing some of your theories with you.” Nines kept his hands behind his back. He looked a lot like Connor, but taller and more serious.
“It’s nice to meet you Nines. I always have time to talk about my theories. Not many of my peers do similar research so any chance I get to talk about it I’ll take it.” Out of the corner of my eye I saw a man in a leather jacket with a hood, blue jeans, and what looked like a permanent scowl on his face.
“Hey Tin Can! We have a case to solve!” Nines whipped around to look at him and I moved from behind him so I could glare at this rude stranger.
“Excuse me? Who do you think you are? You don’t get to talk to people or androids like that.” I could feel everyone’s eyes on me, but I couldn’t help myself. I hate bullies, especially people who bully androids. I marched over to the man with my arms crossed my chest. He’s about 6 inches taller than me with a scar running diagonally across his nose. He snorts and looks down at me.
“And who are you pipsqueak?” He chuckled, for once I was glad, I looked younger than my age. Nothing beats giving your full title to assholes.
“I’m Dr. (Y/n) (L/n), a professor at Wayne State University studying sociological relationships between humans and androids, and it seems you fall under the category of ‘asshole to everyone’.” Keeping my glare on him, he awkwardly rubbed the back of his neck and looked away. He mumbled a ‘whatever’ under his breath and walked away. I smiled to myself and turned back towards Nines, Connor, and my father.
“I apologize for my partner, Detective Reed. He sometimes forgets not everyone shares the same opinions as him.”
“No worries, Nines. But you shouldn’t have to deal with that, I mean-“
“(Y/n), Reed has a lot of problems, but is mainly just an asshole.” My dad interrupted me, “but we should really get to lunch.” I nodded.
“Well it was nice to meet you, Nines. Please feel free to stop by my office anytime. I’m pretty much there every day until classes start.” Nines gave me a short nod and walked towards where Detective Reed had gone as I followed my dad and Connor out of the precinct.
“Lieutenant Anderson said you like sandwiches, so I found a local restaurant that is highly rated.” Connor said as we all buckled up in my dad’s car. Connor had given me the passenger seat and he sat in the back.
“I do like sandwiches.” I turned back to look at him, as my dad started driving. “So, Connor, how do you like working for the police department?”
“I was made to assist law enforcement, although I do prefer working for the DPD over Cyberlife.”
“That’s fair. What about you, dad? How do you like working with Connor?” My dad snickered at my question.
“Well, he’s the only partner I’ve been able to stand. Although I wish he would stop putting evidence in his mouth, it’s disgusting- “
“He has a forensics kit that can analyze samples in real time.” “I have a forensics kit that can analyze samples in real time.” Me and Connor said at the same time, causing my dad to groan and me to giggle.
“Damnit now there’s two of you.” My dad said with a short laugh.
“(Y/n), how do you know that?” Connor asked, I noticed in the rearview mirror he tilted his head.
“Shortly after the android revolution I interviewed one of my old contacts who use to work at Cyberlife. Plus, you’re the one saving my dad’s butt out in the field I wanted to know what you were capable of.” My dad quickly glanced over at me. I could tell he was surprised that I knew that, or maybe he was surprised I kept tabs on him.
“That makes sense.” Connor said shortly, his LED changed to yellow for a short second and then looked back at me through the rearview mirror. “Lieutenant Anderson forbade me from looking you up and learning more about you before meeting you. I didn’t know he allowed you to do research on me.”
“Connor, two things, I’ve told you a million times you can call me Hank, especially when we’re outside the precinct. Second, (Y/n) looking you up for her research is different than you scanning a ton of databases and learning everything about her.” My dad said as he pulled into a parking spot.
“That’s fair, Hank.” Connor said as we all got out of the car. The restaurant wasn’t very busy, and we got a table right away. Me and Connor sat on one side of the table and my dad sat on the other side. He kept nervously looking at me and the menu.
“So, how do you like your new apartment, (Y/n)?” My dad asked me while staring intently at the menu.
“It’s a little small, but it’s just me so it works. It’s only a ten-minute walk from the university which is really nice. You guys should come see it sometime. I’m pretty much fully unpacked.”
“Do you have a dog?” Connor asked quickly, I couldn’t help but laugh.
“No, I’m more of a cat person, but I have missed Sumo.”
“Sumo’s going to go crazy when he sees you. He refuses to let anyone take one of the blankets you left still. He’s always hiding it around the house. He’s so much bigger now.”
“I didn’t know that that blanket belonged to (Y/n).”
“Yeah, Sumo and (Y/n) were really close.” My dad said softly. I felt an ache in my heart. For a moment I thought of telling my dad I wished I hadn’t left, but that wasn’t fully true. Luckily the waitress saved us from sitting in awkward silence. She cheerfully took me and my dad’s order and walked away. “I’m surprised Nines walked up and introduced himself and asked to talk sometime.”
“He seems nice.” I said softly, somehow, I felt I’ve stepped over a boundary. Maybe I should’ve met them at the restaurant instead of going into the precinct. “I’m sorry for yelling at that man, it wasn’t my place to talk like that in a police department.” I stared down at my lap until I heard my dad burst out laughing.
“You have to be kidding! I love seeing people put Gavin in his place. He’s an asshole,” my dad said. “Pointed a gun one time at Connor even.” I gasped.
“What? Why? Connor are you okay?” I grabbed his arm and he jumped a little in surprise.
“Of course, it was when I was first assigned to the DPD. I did knock him out later, which was…satisfying.” Connor said, I let go of his arm and felt myself blush. “(Y/n), may I ask a personal question?”
“Sure.”
“Why do you care so much about androids? Even before the first reports of deviancy you were publishing papers fighting for android rights.” I had expected Connor to ask me that at some point, but I thought it would take longer than this.
“I don’t know I’ve just always felt that we were equal. Why does it matter that our blood is different colors? Androids have helped push society so much further than expected. I just…it never felt right to me. The way people treated androids.” I couldn’t help, but shiver thinking about some of the horrific stories I’ve read. I looked over at Connor who was staring at me intently. His LED was spinning yellow. “Can I ask you a personal question, Connor?”
“Of course.”
“Many androids have taken off their LEDs, why have you kept yours?” His hand raised up to his LED, which was still yellow.
“There’s no reason I should be ashamed that I am an android instead of human, so why would I hide the fact?” My dad snorted and I quickly turned my head towards him, tilting my head slightly.
“I’m not laughing at what he said. It took a month of me trying to convince Connor to stop wearing his Cyberlife uniform.” I couldn’t help but smile, looking back at Connor. A light blue blush spread across his cheeks.
“It was comfortable.” He said, his LED finally turning back to blue.
“That’s fair. In middle school I wore the same sweatshirt every day.” I said, as the waitress sat down our sandwiches. I took a bite, not realizing how hungry I was. “Mhmmm, Connor you picked a great restaurant, this is delicious!” He beamed a smile. I looked back at my dad, who was looking at both of us with so much happiness. “Dad, do you think you and Connor could stop by my office sometime this week? I really hate where they’ve put my desk and couch and I could use some help moving them.”
“That’s fine with me, Connor?”
“I would love to help, maybe after you can come over and visit with us and Sumo?” I looked at my dad who immediately looked worried, I could tell he wanted to take fixing our relationship at my pace.
“That sounds really nice. Does Friday work for you guys?”
“Yeah, that should be fine. Fowler’s been telling Connor he needs to take time off anyway.”
“Which I don’t understand. I’m an android. I can work every day and be fine. Our cases have a high success rate.” I let out a laugh.
“Connor, he isn’t asking you to take time off to punish you, he wants you to be able to enjoy the world outside work! Have you picked up any hobbies?” I asked him.
“I like to take care of Sumo.” He answered quickly.
“Okay, well how about one day me and you go to a local dog shelter and walk some of the rescues?” I offered.
“Really?” He was practically jumping up and down.
“Yes of course! It’s great volunteer work and those dogs need some love.”
“Hank, would you come with us?”
“That should be you and (Y/n)’s thing. We can do something altogether some other time.” I couldn’t help but notice his hesitant tone.
“I think that would be really nice, Dad.” He didn’t look up from his sandwich, but I could see the small smile on his face.
Chapter 2
#gavin reed x reader#gavin reed#rk800#rk900#dbh nines#detroit become human#fan fic#sumo#connor#hank anderson#connor is like a son to hank
42 notes
·
View notes
Text
Crimson Publishers Indexing
Crimson Publishers IndexingWhy is indexing essential?Indexing will help your journal achieve its main purpose of being accessible to a wide audience.Being accessible in turn will improve your journal’s reputation as a reliable source of high-quality information in your field.Database research is the first activity researchers undertake as part of their study, and they naturally look to established, well-known databases. Thus, being indexed in a known database in your field will help increase your journal’s readership. How does indexing work?Once a journal is indexed by a database, it is immediately made available to all users of that database. Some databases index titles, some index full articles while some others index only the abstract and/or references. There are several abstracting and indexing services available today. Some are affiliated with institutions (e.g., PubMed maintained by the United States National Library of Medicine at the National Institute of Health) while some are provided by publishers (e.g., Scopus by Elsevier). Irrespective of which institution the database is affiliated with, you will need to formally apply for inclusion in the database of your choice."https://crimsonpublishers.com List of Crimson Publishers Indexing SitesCitefactor: CiteFactor provides journal indexing, research paper indexing, impact factor and citation analysis. Citefactor is Directory of International Research Journals. Cosmos: Cosmos Foundation was founded by renowned scientists. A group of 100 scientist from various countries in different disciplines are started Cosmos (2010) with specific objective of providing quality information to the researcher. We offer academic database services to researcher. We provide impact factor and index of academic journals, books. We maintain academic database services to researchers, journal editors and publishers. Cosmos provides a detailed report of individual journal for further improvement of respective journal overall look up and technical aspect for better Impact Factor.Cosmos provides Quantitative and Qualitative tool for ranking, evaluating and categorizing the Journals for academic evaluation and excellence. This Factor is used for evaluating the prestige of Journals. The evaluation is carried out by considering the factors Like Paper Originality, Citation, Editorial Quality, and Regularity & International Presence.We perform the in-depth analysis method. The acceptance and rejection rates of journals can be a determining factor. Low acceptance rate, high rejection rate journals are considered the best and most prestigious journals, as the acceptance criteria is of high quality standard. Many journals and societies have web pages that give publication data and style requirements and often include acceptance/rejection rates. The paper copy of the journal occasionally includes this data and will always provide current contact information, whether a journal is indexed in the major indexing/abstracting service in the field is another criteria that can be used to assess the worth and quality of a journal.http://www.cosmosimpactfactor.com/page/journals_details/5109.htmlSindexs: Scientific Indexing Services (SIS) was founded by renowned scientists. A group of 70 scientist from various countries in different disciplines are started SIS with specific objective of providing quality information to the researcher. SIS offering academic database services to researcher. It's mainly: citation indexing, analysis, and maintains citation databases covering thousands of academic journals, books, proceedings and any approved documents SIS maintains academic database services to researchers, journal editors and publishers. SIS focuses on: citation indexing, citation analysis, and maintains citation databases covering thousands of academic journals. SIS Provides Quantitative And Qualitative Tool For Ranking, Evaluating And Categorizing The Journals For Academic Evaluation And Excellence. This Factor Is Used For Evaluating The Prestige Of Journals. The Evaluation Is Carried Out By Considering The Factors Like Paper Originality, Citation, Editorial Quality, and Regularity & International Presence. We Perform The In-Depth Analysis Method. The Acceptance And Rejection Rates Of Journals Can Be A Determining Factor. Low Acceptance Rate, High Rejection Rate Journals Are Considered The Best And Most Prestigious Journals As The Acceptance Criteria Is Of High Quality Standard. Many Journals And Societies Have Web Pages That Give Publication Data And Style Requirements And Often Includes Acceptance/Rejection Rates. The Paper Copy Of The Journal Occasionally Includes This Data And Will Always Provide Current Contact Information. Whether A Journal Is Indexed In The Major Indexing/Abstracting Service In The Field Is Another Criteria That Can Be Used To Assess The Worth And Quality Of A Journal.http://www.sindexs.org/JournalList.aspx?ID=6080 ROAD: Washington State University: Washington State University (Washington State, WSU or Wazzu) is a public research university in Pullman, Washington. Founded in 1890, WSU is one of the oldest land-grant universities in the American West and features programs in a broad range of academic disciplines. With an undergraduate enrollment of 24,470 and a total enrollment of 29,686, it is the second largest institution of higher education in Washington state behind the University of Washington. The WSU Pullman campus is perched upon a hill, characterized by open spaces, views, deep green conifers, and a restrained red brick and basalt material palette—materials originally found on site. The university is nestled within the rolling topography of the Palouse in rural eastern Washington and remains intimately connected to the town, the region, and the landscape in which it sits.The university also operates campuses across Washington known as WSU Spokane, WSU Tri-Cities, and WSU Vancouver, all founded in 1989. In 2012, WSU launched an Internet-based Global Campus, which includes its online degree program, WSU Online. In 2015, WSU expanded to a sixth campus, known as WSU Everett. These campuses award primarily bachelor's and master's degrees. Freshmen and sophomores were first admitted to the Vancouver campus in 2006 and to the Tri-Cities campus in 2007. Enrollment for the four campuses and WSU Online exceeds 29,686 students. This includes 1,751 international students.WSU's athletic teams are called the Cougars and the school colors are crimson and gray. Six men's and nine women's varsity teams compete in NCAA Division I in the Pac-12 Conference. Both men's and women's indoor track teams compete in the Mountain Pacific Sports Federation.https://washingtonstate.on.worldcat.org/search?databaseList=143%2C199%2C203%2C217%2C239%2C638%2C283%2C285&queryString=2576-8840 Semantic Scholar : Semantic Scholar is a project developed at the Allen Institute for Artificial Intelligence. Publicly released in November 2015, it is designed to be an AI-backed search engine for scientific journal articles. The project uses a combination of machine learning, natural language processing, and machine vision to add a layer of semantic analysis to the traditional methods of citation analysis, and to extract relevant figures, entities, and venues from papers. In comparison to Google Scholar and PubMed, Semantic Scholar is designed to highlight the most important and influential papers, and to identify the connections between them.As of January 2018, following a 2017 project that added biomedical papers and topic summaries, the Semantic Scholar corpus included more than 40 million papers from computer science and biomedicine. In March 2018, Doug Raymond, who developed machine learning initiatives for the Amazon Alexa platform, was hired to lead the Semantic Scholar project. As of August 2019, the number of included papers had grown to more than 173 million after the addition of the Microsoft Academic Graph records, already used by Lens.org.https://www.semanticscholar.org/paper/Numerical-Simulation-of-Three-Dimensional-Processes-Mh/65ca1facc3fdcfa63cba2809a7e38fa62ffc8c6b Sci-Hub : Sci-Hub is a website that provides free access to millions of research papers and books, without regard to copyright, by bypassing publishers' paywalls in various ways.Sci-Hub was founded by Alexandra Elbakyan in 2011 in Kazakhstan in response to the high cost of research papers behind paywalls. The site is widely used in both developed and developing countries, serving over 200,000 requests per day as of February 2016.Sci-Hub and Elbakyan were sued twice for copyright infringement in the United States in 2015 and 2017, and lost both cases, leading to loss of some of its Internet domain names. The site has cycled through different domain names since then.Sci-Hub has been lauded by some in the scientific, academic, and publishing communities for providing access to knowledge generated by the scientific community. Others have criticized it for violating copyright, threatening the economic viability of publishers, potentially compromising universities' network security and jeopardizing legitimate access to papers by university staff.Electronic Journals Library : The Electronic Journals Library is a service to facilitate the use of scholarly journals on the internet. It offers a fast, structured and unified interface to access full-text articles online. It comprises 99764 titles from all areas of research, 21965 of which are available online only. In addition, 130244 journals, which are provided by aggregators, are listed. The EZB contains 64605 journals which are accessible free of charge to anyone. Furthermore, the participating libraries provide their users access to the journals they subscribe to. The journals are presented in lists sorted by research area. An updated list is generated by the database according to the member library's specifications each time it is accessed.https://rzblx1.uni-regensburg.de/ezeit/searchres.phtml?bibid=AAAAA&colors=7&lang=en&jq_type1=QS&jq_term1=Research+%26+Investigations+in+Sports+MedicineWorld Catalogue of Science Journals : Following the main thesis of the most outstanding world-famous scholar Maria Skłodowska Curie – “Education should be free of charge and generally available ”, a World Catalogue of Scientific Journals has been created in 2010. This World Catalogue of Scientific Journals, or a list of the most known and prestigious scientific journals, is intended to promote science and education worldwide. The system of science and education promotion as a free-of-charge and generally available offer can be and is presented in the form of an on-line system. Conditions for placing a journal in the catalogue Any scientific journal worldwide which publishes the title and English summary at least on generally available websites for minimum two years can be added to World Catalogue of Scientific Journals. Publisher or Editor-in-Chief should propose his / her journal by completing a form in the “Suggest your Journal” tab and send to the Catalogue’s Editors. After checking by reviewers, a journal will be added to the World Catalogue.http://www.wcosj.com/site/publicationsbycountry/226?Journal_page=556 Indexcopernicus : All journals may be registered in the ICI World of Journals database. The database gathers information on international scientific journals which is divided into sections: general information, contents of individual issues, detailed bibliography (references) for every publication, as well as full texts of publications in the form of attached files (optional). Within the ICI World of Journals database, each editorial office may access, free of charge, the IT system which allows you to manage your journal's passport: updating journal’s information, presenting main fields of activity and sharing the publications with almost 200 thousand users from all over the world. The idea behind the ICI World of Journals database is to create a place where scientific journals from all over the world would undergo verification for ‘predatory journals’ practices by scientific community. The ICI World of Journals database allows journals which care about completeness and topicality of their passports to build their citation rates and international cooperation.https://journals.indexcopernicus.com/search/details?id=51696 Scilit : The name Scilit uses components of the words “scientific” and “literature”. This database of scholarly works is developed and maintained by the open access publisher MDPI.Scilit is a comprehensive, free database for scientists using a new method to collate data and indexing scientific material. Our crawlers extract the latest data from CrossRef and PubMed on a daily basis. This means that newly published articles are added to Scilit immediately.https://www.scilit.net/publisher/9410Publons : Publons is a commercial website that provides a free service for academics to track, verify, and showcase their peer review and editorial contributions for academic journals. It was launched in 2012 and by 2018 more than 500,000 researchers have joined the site, adding more than one million reviews across 25,000 journals. Publons' mission is to "speed up science by harnessing the power of peer review". Publons claims that by turning peer review into a measurable research output, academics can use their review and editorial record as evidence of their standing and influence in their field. Publons says its business model is based on partnering with publishers.Publons produces a verified record of a person's review and editorial activity for journals. This evidence is showcased on reviewers' online profiles and can be downloaded to include in CVs, funding and job applications, and promotion and performance evaluations.Publons also provides:· tools for publishers to find, screen, contact, and motivate peer reviewers;· data and publications about global peer review behaviour;· peer review training for early-career researchers; and· features for academics to discuss and evaluate published research.https://publons.com/publisher/6342/crimson-publishers Isindexing : The ISI server provides indexing of major international journals and proceedings. Author can get information about international journal impact factor, proceedings (research papers) and information on upcoming events. All the journal pages have pointers to Web pages of the publishers which are integrated into the ISI stream pages. The purpose is to increase the visibility and ease of use of open access scientific and scholarly journals. If your journal is indexed & got validated stamp from ISI, you can request for the calculation of impact factor for your journal. ISI is a service that provides access to quality controlled Open Access Journals. The ISI aims to be comprehensive and cover all open access scientific and scholarly journals that use an appropriate quality control system, and it will not be limited to particular languages or subject areas. The aim of the ISI is to increase the visibility and ease of use of open access scientific and scholarly journals thereby promoting their increased usage and impact.https://isindexing.com/isi/journaldetails.php?id=7969 Worldcat : WorldCat is the world's largest network of library content and services. WorldCat libraries are dedicated to providing access to their resources on the Web, where most people start their search for information.You can search for popular books, music CDs and videos—all of the physical items you're used to getting from libraries. You can also discover many new kinds of digital content, such as downloadable audiobooks. You may also find article citations with links to their full text; authoritative research materials, such as documents and photos of local or historic significance; and digital versions of rare items that aren't available to the public. Because WorldCat libraries serve diverse communities in dozens of countries, resources are available in many languages. Scribd : Scribd /ˈskrɪbd/ is an American e-book and audiobook subscription service that includes one million titles. Scribd hosts 60 million documents on its open publishing platform.Founded in 2007 by Trip Adler, Jared Friedman, and Tikhon Bernstam, and headquartered in San Francisco, California, the company is backed by Khosla Ventures, Y Combinator, Charles River Ventures, and Redpoint Ventures. Scribd's e-book subscription service is available on Android and iOS smartphones and tablets, as well as the Kindle Fire, Nook, and personal computers. Subscribers can access unlimited books a month[8] from 1,000 publishers, including Bloomsbury, Harlequin, HarperCollins, Houghton Mifflin Harcourt, Lonely Planet, Macmillan, Perseus Book Group, Simon & Schuster, Wiley, and Workman Researchbib : ResearchBib is open access with high standard indexing database for researchers and publishers. Research Bible may freely index journals, research papers, call for papers, research position.We share a passion to build research communities to discover and promote great research resources from around the world and maximize researchers’ academic social impacts.DRJI : DRJI provides ready access to education literature to support the use of educational research and information to improve practice in learning, teaching, educational decision-making, and research. Directory of Research Journals Indexing is a free online service that helps you to find web resources for your articles and research. With millions of resources available on the Internet, it can be difficult to find useful material. We have reviewed and evaluated thousands of resources to help you choose key websites in your subject. Our indexed journals will be submitted to all social networks and world's top most indexing and they will be displayed on world's top electronic library. In short, all journals will reach all continents.http://olddrji.lbp.world/IndexedJournals.aspxGoogle Scholar : Google Scholar is a freely accessible web search engine that indexes the full text or metadata of scholarly literature across an array of publishing formats and disciplines. Released in beta in November 2004, the Google Scholar index includes most peer-reviewed online academic journals and books, conference papers, theses and dissertations, preprints, abstracts, technical reports, and other scholarly literature, including court opinions and patents. While Google does not publish the size of Google Scholar's database, scientometric researchers estimated it to contain roughly 389 million documents including articles, citations and patents making it the world's largest academic search engine in January 2018. Previously, the size was estimated at 160 million documents as of May 2014.] An earlier statistical estimate published in PLOS ONE using a Mark and recapture method estimated approximately 80–90% coverage of all articles published in English with an estimate of 100 million. This estimate also determined how many documents were freely available on the web.https://scholar.google.co.in/citations?hl=en&user=94TyaUwAAAAJPlagScan : PlagScan is a plagiarism detection software, mostly used by academic institutions. PlagScan compares submissions with web documents, journals and internal archives. The software was launched in 2009 by Markus Goldbach and Johannes Knabe.PlagScan is offered as a Software as a Service and as an on-premise solution. Users can either register as a single user or as an organization. Upon first-time registration, single users receive a free test credit and can purchase additional credits for future submissions, after the completion of a satisfactory trial.Organizational users verify the organization’s address prior to using the software. An obligation-free quote can be requested immediately on the website. Organizations can choose from a variety of options and create multiple administrators and groups, for example, to divide different departments within one institution.After scanning a submission for plagiarism, PlagScan provides users with a detailed report that indicates potential plagiarism and lists the matched sources.
#crimson publishers indexing#crimson publishers wings to the research#crimson publishers llc#crimson publishers blogger
15 notes
·
View notes
Text
Windows update iptrace

#WINDOWS UPDATE IPTRACE UPDATE#
#WINDOWS UPDATE IPTRACE SOFTWARE#
Tip: Try to open the ETL file using a text-editor such as Notepad, as many file types contain simply contain unformatted plain-text and can viewed correctly using this method. Please check back soon for more information as we are constantly updating our file descriptions based on search frequency. We have yet to investigate this file type further, or there was not enough information available at the time to report accurately on the format. You are safe to close the Command Prompt window now. Day 4: Use PowerShell to Find Missing Updates on WSUS Client Computers. Day 3: Approve or Decline WSUS Updates by Using PowerShell. Day 2: Use PowerShell to Perform Basic Administrative Tasks on WSUS. Day 1: Introduction to WSUS and PowerShell. This data file format was added to our database by a visitor to this site, but no additional information was provided. txt should be created on your desktop that contains the tracert results. You can also see Boe’s biography in the Day 1 blog. The purpose of this utility is to show you the path your traffic takes when you. You can open it with Notepad and read it to. When it finishes running, the cmdlet will create the classic WindowsUpdate.log file in your Desktop folder. Type the following command at the PowerShell console: Get-WindowsUpdateLog.
#WINDOWS UPDATE IPTRACE UPDATE#
If you are unable to open the file this way, it may be because you do not have the correct application associated with the extension to view or edit the ETL file. There is a common utility known as traceroute, or tracert in DOS and Windows. To find the Windows Update Log in Windows 10, do the following. It also is commonly referred to by the name of the tools used to perform the trace typically traceroute on Linux based systems and tracert on Windows. The best way to open an ETL data file is to simply double-click it and let the default assoisated application open the file. Hop is a location where packets stop while reaching the destination. TRACERT (Traceroot Utility) uses varying IP Time-To-Live (TTL) values. A Simple Python Script that uses requests and json module to fetch ip details using the IP Geolocation API. To get started using the site, enter in your search terms in the Search box above or visit our FAQ for search tips. Windows Traceroute command-line utility is used to trace a route of the network by sending ICMP (Internet Control Message Protocol) packets to the network destination. We want your feedback Visit our newsgroup or send us an email to provide us with your thoughts and suggestions. If you are aware of any additional file formats that use the ETL extension, please let us know. Welcome to the Microsoft Update Catalog site. ETL extension are known as Microsoft Event Trace Log files, however other file types may also use this extension.
#WINDOWS UPDATE IPTRACE SOFTWARE#
Have you found, downloaded or received an ETL file, but don't know which software program is required to open it?īefore attempting to open an ETL file, you'll need to determine what kind of file you are dealing with and whether it is even possible to open or view the file format.Īnswer: Files which are given the.

0 notes
Text
System Center Configuration Manager current branch 1810 KB4486457 available

System Center Configuration Manager current branch 1810 KB4486457 available.
Issues that are fixed
First wave issues Synchronization of Office 365 updates may fail after you update to Configuration Manager current branch, version 1810. Errors messages that resemble one of the following are recorded in the WSyncMgr.log file: ProcessFileManifest() failed to process O365 file manifest. Caught exception: System.Net.WebException: An exception occurred during a WebClient request. ProcessFileManifest() failed to process O365 file manifest. Caught exception: System.UriFormatException: Invalid URI: The URI scheme is not valid. The distribution point upgrade process may fail. This causes a block of additional content distribution to that server. Errors messages that resemble the following are recorded in the distmgr.log file: Failed to copy D:\SRVAPPS\Microsoft Configuration Manager\bin\x64\ccmperf.dll to \\{server}\SMS_DP$\sms\bin\ccmperf.dll. GLE = 32 All superseded updates are removed and no are longer applicable on a client, even before expiration. This issue occurs even if the Do not expire a superseded software update until the software update is superseded for 3 months option is enabled. Performance improvements have been made to the Data Replication Service for device discovery data. The second and successive phases of a deployment start automatically after the success of the first phase, regardless of start conditions. Phased deployment deadline behavior settings are inconsistent between the Create Phased Deployment Wizard and the Phase Settings properties. When you run a Servicing Plan after you select a Product Category, the filter is not added correctly. The Cloud Management Gateway (CMG) content service is not created correctly when the CMG role is added after you update to Configuration Manager current branch, version 1810. The No deployment package option is selected after you change the properties of an Automatic Deployment Rule (ADR). After this update rollup is applied, affected ADRs can be re-created and their properties changes without any further issue. The Configuration Manager Message Processing Engine (MPE) may not always process Active Directory discovery data when optional attributes are added. Errors that resemble the following are recorded in the SMS_Message_Processing_Engine.log: ERROR: Got SQL exception when handle discovery message. Exception: System.Data.SqlClient.SqlException (0x80131904): String or binary data would be truncated.~~ The Service Connection Tool (serviceconnection.exe) fails and you receive the following error message when you use the -connect parameter: ERROR: System.IO.Exception : The directory is not empty. A user without Full Administrator rights may be unable to create or edit Windows Defender ATP Policies, even when you add them to the Endpoint Protection Manager security role. The Prerequisite Installation Checker incorrectly gives the option to retry a site installation again. If a second retry is tried, the administrator must run the Configuration Manager Update Reset Tool (CMUpdateReset.exe) to resolve the issue. Processing of .bld files by the SMS_Notification_Manager component takes longer than expected. This leads to delays in processing data and a backlog of files in the \inboxes\bgb.box folder. After you update to Configuration Manager current branch, version 1810, remote SQL providers who use Microsoft SQL Server 2014 or an earlier version may not always query the database. Errors that resemble the following are recorded in the smsprov.log: *** User $' does not have permission to run DBCC TRACEON. The Software Updates Patch Downloader component retries updates, up to three times. These retries fail and return error code 404. Windows Server 2016 updates are displayed incorrectly as available when you schedule updates to a Windows Server 2019 operating system image. Searching for a user’s first or last name, or full name, returns no results from the Overview section of the Assets and Compliance node of the Configuration Manager console. This issue occurs even when full discovery data is available. Globally available release issues After you enable support for express installation files, content may not always download from Windows Server Update Services (WSUS) servers in the following scenarios: Configuration Manager client installation through Software Update Point Installing updates directly from WSUS Windows Feature on Demand (FOD) or Language Pack (LP) acquisition After you update to Configuration Manager current branch, version 1810, device enrollment can overwrite Windows telemetry collection values that were previously set by Group Policy. This issue can cause value toggling between full and basic, for example, when Group Policy is applied. Hardware inventory is updated to include information about add-ins for Office365 and standalone Office products. Desktop Analytics deployment plans show a larger device count in the Configuration Manager console than in the Desktop Analytics Portal. Configuration Manager client setup may fail over a metered (for example, cellular) network connection. This may occur even if client policy settings allow for those connections. An error message that resembles the following is recorded in the Ccmsetup.log file on the client: Client deployment cannot be fulfilled because use of metered network is not allowed. Client setup may fail because of SQL Server CE schema changes. Errors that resemble the following are recorded in the Ccmsetup-client.log on the client: MSI: Setup was unable to compile Sql CE script file %windir%\CCM\DDMCache.sqlce. The error code is 80040E14. If an application is in a partly compliant state, and the client sees that a dependency is installed but the main application is not and requires re-enforcement, available deployment causes the following issues: The application is displayed as required or past due even though the deployment is available and there is no supersedence relation. Clicking Install has no effect. Sign in to Azure services fails when you use the Create Workflow in the Azure Services Wizard, even when correct credentials are used. Configuration Manager setup may fail the prerequisite check during installation or an update of a site server. This issue occurs if the environment uses SQL Always On. The “Firewall exception for SQL Server” rule shows a status of failed, and errors messages that resemble the following are recorded, even if the correct firewall exceptions are configured: ERROR: Failed to access Firewall Policy Profile. ERROR: Failed to connect to WMI namespace on Firewall exception for SQL Server; Error; The Windows Firewall is enabled and does not have exceptions configured for SQL Server or the TCP ports that are required for intersite data replication. The alternative download server that is listed in the "Specify intranet Microsoft update service location" window is not propagated to the Group Policy settings on the client. The download of Office 365 updates, such as “Semi-annual Channel Version 1808 for x86 Build 10730.20264” or “Monthly Channel Version 1812 for x64 Build 11126.20196” may fail. No errors are logged in the Patchdownloader.log file. However, entries that resemble the following are logged in the AdminUI.log log: (SMS_PackageToContent.ContentID={content_ID},PackageID='{package_ID}') does not exist or its IsContentValid returns false. We will (re)download this content. Read the full article
1 note
·
View note
Text
Windows 10 features error 0x800f0954 無料ダウンロード..NET Framework 3.5をWindows10にインストールする方法
Windows 10 features error 0x800f0954 無料ダウンロード.Windows10に.NET3.5をインストールする方法!

.Net3.5のインストール方法.Windows10に.NETをインストールする方法! | Step
This error may occur of installer is not approved in WSUS. As a temporary workaround, change the registry key “UseWUServer” to 0. It is located at: HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU. After the registry change, restart the Windows Update service Mar 06, · sの機能の有効化または無効化にて.NET Framework にチェック。 supdateでファイルを自動ダウンロード →0xF Oct 24, · では、一つずつ詳細を見ていきましょう。. デスクトップのWindowsボタンもしくは検索から「コントロールパネル」を開いてください。. コントロールパネルが開いたことを確認し、「プログラム」をクリックします。. 「プログラム」を開いたら、「プログラムと機能」の中の「Windowsの機能の有効化または無効化」をクリックします。. すると、下記のよ
Windows 10 features error 0x800f0954 無料ダウンロード..net framework installation fails w/ error code: 0xF
「0xF」エラーが発生してインストールできない場合は、レジストリエディタでWSUS(Windows Server Update Service)をオフにしてから、インストールしてみてください。 インストール後は忘れずにレジストリの値を戻しましょう。 レジストリエディタを開く。Estimated Reading Time: 2 mins This error may occur of installer is not approved in WSUS. As a temporary workaround, change the registry key “UseWUServer” to 0. It is located at: HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU. After the registry change, restart the Windows Update service Mar 06, · sの機能の有効化または無効化にて.NET Framework にチェック。 supdateでファイルを自動ダウンロード →0xF
NET Framework 3. NET Frameworkのインストール方法と失敗した際の解決方法をご紹介します。ぜひ、参考にしてください。. NET 2. NET MVC Webアプリケーションを開発するためのMVCフレームワークです。Web開発に必要なフロントエンド言語やHTTPなどの深い知識がなくても、高機能なWebアプリケーションを作成することができます。.
NET Frameworkの案件を探すならFEnet. NET Navi. NETコラム Windows. コントロールパネルを開く。 「プログラム」>「Windowsの機能の有効化または無効化をクリック。. NET分野でのキャリアアップをお考えの方は、現在募集中の求人情報をご覧ください。 また、直接のエントリーも受け付けております。 エントリー(応募フォーム). Search キーワード検索. Popular 人気の記事. reccomended おすすめ記事. Categories 連載一覧. Tags タグ一覧. NET 5. NET Core. NET Framework ADO. NET ASP. NET MVC Azure AD Azure App Service Azure Automation Azure Bastion Azure CDN Azure Cosmos DB Azure Data Factory Azure DevOps Azure DNS Azure Firewall Azure Functions Azure Key Vault Azure Load Balancer Azure Machine Learning Azure PowerShell Azure Security Center Azure Sentinel Azure Site Recovery Azure SQL Database Azure Stack Azure Storage Azure VM Azure VPN Gateway Bootstrap C CSS Entity Framework jQuery LINQ Microsoft Azure Microsoft Office PostgreSQL PowerShell python SQL Server SSMS VB.
NET Visual Basic Visual Studio Web面接 Windows Windows フォーム WPF Xamarin XAML おすすめ記事 就職 案件 転職お役立ちコンテンツ. Jobs 新着案件. 東京都品川区 大崎駅. 東京都港区 六本木駅. 東京都豊島区 池袋駅. 東京都豊島区 大塚駅. 東京都文京区 後楽園駅. All Rights Reserved.
0 notes
Text
Windows 10 version 1903 download time 無料ダウンロード.Windows10 21H1 May 2021 update ダウンロードと手動アップデート
Windows 10 version 1903 download time 無料ダウンロード.Windows10 公開が終了した過去バージョンをダウンロードする

この更新プログラムの既知の問題.windows 10 ・ ダウンロード
Oct 12, · The November 10, update for Windows 10, version , Windows Server, version , Windows 10, version , and Windows Server, version includes cumulative reliability improvements Framework and We recommend that you apply this update as part of your regular maintenance routines Jun 24, · Windows 10 の、現在のバージョンは、です。 このOSをダウンロードしてDVDに焼き込み、インストールした報告です。 Windows 最新版は最下段に説明があります。 追記 ここをクリック最下段に移動します。 Dec 09, · Windows 10 verUpdate の提供およびサポートは終了しましが、インストールメディア作成するアプリを利用すれば「」のダウンロードやアップデート、インストールすることは可能です。
Windows 10 version 1903 download time 無料ダウンロード.Windows 10 May Update のダウンロードと手動アップデート-パソブル
May 01, · Windows update VerH1 は、年11月17日に最新しいバージョン「November Update VerH2」が一般公開されて、公式サイトでの VerH1 の提供は終了しましが、ダウンロードやアップデートはできます。 In Internet Explorer, click Tools, and then click Internet Options. On the Security tab, click the Trusted Sites icon. Click Sites and then add these website addresses one at a time to the list: You can only add one address at a time and you must click Add after each one May 22, · Windows 10 Version の ISOイメージダウンロード方法について紹介します. PCの一斉展開や仮想マシン化、検証用、クラウド利用などでISOイメージを使用するケースは多いと思います 例えば、のWindowsを用意したいのに、でOSインストールして機能アップデートを適用して・・・は面倒なので Estimated Reading Time: 1 min
NET Framework 3. Note On Jan 12, , a live revision was made to this update to remove its supersedence relationship with the October 13, ,. NET Framework security updates. If you have already installed this update, the October NET Framework updates, or any later. NET Framework updates, you do not have to take any action to be up-to-date for the latest. WSUS administrators who cannot install this update and have to reinstate the October 13, , KB security update, if it was declined, can follow this guidance: Reinstating declined updates.
Then, they should run an update synchronization within their Microsoft Endpoint Configuration Manager, or update management environments, as applicable.
The November 10, update for Windows 10 , version , Windows Server, version , Windows 10 , version , and Windows Server, version includes cumulative reliability improvements in.
We recommend that you apply this update as part of your regular maintenance routines. Before you install this update, see the Prerequisites and Restart requirement sections. SqlClient where querying string columns would fail if the database had a Kazakh collation. To get the standalone package for this update, go to the Microsoft Update Catalog website. For a list of the files that are provided in this update, download the file information for cumulative update.
To apply this update, you must have. You must restart the computer after you apply this update if any affected files are being used. We recommend that you exit all. NET Framework-based applications before you apply this update. Help for installing updates: Windows Update FAQ. Protect yourself online and at home: Windows Security support.
Local support according to your country: International Support. History of Cumulative Updates for. NET Framework for Windows 10, version and version Release Date: November 10, Version:.
RSS フィードを購読する. はい いいえ. サポートに役立つご意見をお聞かせください。 改善にご協力いただけますか?
0 notes
Text
Post install failes on database
Post install failes on database
After run post install for WSUS on a Server 2016 essential DC server we receive database errors:ClientConnectionId:ef156204-4956-4309-8cd4-0b7d2c353c62Error Number:3605,State:1,Class:16Fatal Error: Schema verification failed for database ‘SUSDB’.ALTER DATABASE statement failed.Failed to restart the current database. The current database is switched to master. SQL query to set database to Master…
View On WordPress
0 notes
Photo

Title Falls, Palouse Creator Hutchison, Ralph Raymond Description A waterfall in the Palouse River near the Whitman county line. Date April 24, 1932 Subject Canyons–Washington (State) Rivers–Washington (State) Waterfalls–Washington (State) Type Photographic prints Identifier 1046g Source PC 70 Hutchison Studio Photographs of W.S.U. and Pullman, WA, 1927-1973 http://libraries.wsu.edu/masc/finders/pc70.htm Publisher Manuscripts, Archives, and Special Collections: http://libraries.wsu.edu/masc Coverage United States–Washington (State)–Whitman County–Washtuckna Rights For permission to publish please contact Washington State University Libraries, Manuscripts, Archives, and Special Collections (509) 335-6691. Digitization Original photographic prints were scanned as 300 dpi TIFF files on a Microteck 9600XL scanner. 72 dpi JPEG files were then added to the CONTENTdm database at the WSU Libraries
2 notes
·
View notes
Text
Missing Protocol Windows 10

Windows 10 Network Protocol Error: Missing Windows Sockets Registry Entries By Corey October 5, 2020 No Comments My colleagues work computer running Windows 10 began to lose Internet access from time to time (once in 2-3 days with the Limited connection status in the tray). Temporarily Disable or Reinstall your Antivirus Software. First things first, if you are using any. Simply updating your PC's Windows 10 operating system could also fix this issue and restore any missing default apps. Step 1: Hit the Windows logo + I short to launch the Windows Settings menu.
Simple Network Management Protocol or SNMP is used for monitoring, event notification, and network device management on corporate networks. The protocol consists of a set of network management standards, including the Application Layer protocol, database schemas, and a set of data objects. SNMP can receive various information (uptime, performance counters, device parameters, etc.) from any network devices: switches, servers, routers or computers on which the SNMP agent is installed. In Windows 10, the SNMP service is available as a separate Windows component and it’s not installed by the default.
How to Install SNMP Service in Windows 10?
You can check if the SNMP service is installed on your Windows 10 using the Get-Service:
Most likely, the service has not been installed yet.
You can install the SNMP service via the Control Panel. Go to the Control Panel > Programs and Features > Turn Windows features on or off. In the list of Windows features, select Simple Network Management Protocol (SNMP) and the WMI SNMP Provider (provides access to SNMP information via the Windows Management Instrumentation interfaces) and click OK.
You can also install SNMP service using PowerShell:
This command can help you to install SNMP service on Windows 10 in 1803 build or earlier. Starting from Windows 10 1809 Microsoft has changed the way to deploy snmp service on desktop OSs.
Installing SNMP Service in Windows 10 1803 and Newer
Missing Protocol Windows 10 64-bit
In Windows 10 1803 and later (1809, 1903), the SNMP service is considered deprecated and is not listed in the Windows features in the Control Panel list.
Microsoft plans to completely remove the SNMP service in the next Windows builds because of the security risks associated with this protocol. Instead of SNMP, it is recommended to use the Common Information Model (CIM), which is supported by Windows Remote Management. On the current builds of Windows 10, the SNMP service is hidden.
READ ALSOHow to Setup FTP Server in Windows 10?
The SNMP service is now missing from the Windows 10 image and can only be installed as Feature On Demand (FoD).

If your computer has a direct Internet connection, you can install the SNMP service components online from Microsoft servers. To do this, open the elevated PowerShell console and run the command:
You can also use DISM to install the SNMP service:
After that, you can verify that the SNMP service is installed:
Name : SNMP.Client~~~~0.0.1.0
State : Installed
DisplayName : Simple Network Management Protocol (SNMP)
Description : This feature includes Simple Network Management Protocol agents that monitor the activity in network devices and report to the network console workstation
DownloadSize : 595304
Default Protocols Windows 10
InstallSize : 1128133
To disable the SNMP service, use the PowerShell command:
You can also install the SNMP service through the Optional Features graphical interface.
Go to the Settings > Apps > Apps & Features > Manage optional feature > Add Feature. Select in the list the following features: Simple Network Management Protocol (SNMP) and WMI SNMP Provider (to get all SNMP service configuration tabs).
After that, the SNMP service will appear in the services.msc console.
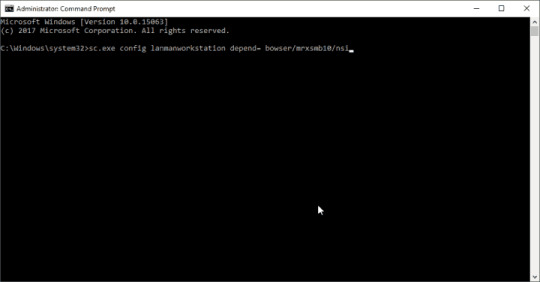
If when performing the Add-WindowsCapability command you received the “Add-WindowsCapability failed error. Error code = 0x800f0954”, most likely your computer receives Windows updates not from Microsoft Update servers but from the internal WSUS server. To make SNMP service receiving install files from Microsoft servers, you need to temporarily bypass the WSUS.
READ ALSOAccessing Hyper-V VM Console Using RDCMan
To do this, run the command:
After that, restart the Windows Update service:
Now try to install the SNMP service with the Add-WindowsCapability command. If all goes well, return the initial wusuaserv service registry parameter pointing to the WSUS server. Run the command:
And restart the Windows Update Service.
Configure SNMP on Windows 10 Computer
After the installation, SNMP services should start automatically. Open the Services management console (services.msc). Two new services should appear in the service list:
SNMP Service – This is the primary SNMP agent service, that tracks activity and sends information;
SNMP Trap – Receives trap messages from local or remote SNMP agents, and forwards messages to the SNMP management software that is being run on that computer.
Open the properties of the SNMP Service. If it is stopped, start it by pressing the Start button and change the startup type to Automatic.
Click the Agent tab. Fill in the Contact and Location fields (you can specify the user’s contact name and computer location), and select the list of services from which you want to collect data and send it to the monitoring device. There are five service-based options:
Physical;
Applications;
Internet;
End-to-end;
Datalink and subnetwork.
Click the Security tab. Here you can configure various security settings for different SNMP servers.
The list of Accepted community names contains the names of the communities whose SNMP hosts are authenticated to send SNMP requests to this computer. The community name has the same functions like login and password.
READ ALSOChanging Active Directory krbtgt Account Password
Click the Add button and specify the Community Name and one of the five access levels (None, Notify, READ ONLY, READ WRITE, READ CREATE). READ WRITE is the maximum access level at which the SNMP management server can make changes on the system. For monitoring systems, it is usually enough to select READ ONLY, while the monitoring server can only poll the system, but not make changes. In our example, we added a community name public with READ ONLY permissions.
Add to the Accept SNMP packets from these hosts list of monitoring servers (hostnames or IP addresses) from which you want to accept SNMP packages.
Tip. You can select the Accept SNMP packets from any host option, but this is not safe.
Save the changes and restart the SNMP service.
This completes the SNMP service configuration in Windows 10. If you need to enable SNMP on multiple computers or servers, you can remotely install and configure SNMP service using PowerShell or Group Policy.
AuthorRecent PostsCyril KardashevskyI enjoy technology and developing websites. Since 2012 I'm running a few of my own websites, and share useful content on gadgets, PC administration and website promotion.Latest posts by Cyril Kardashevsky (see all)
Fix: Active Directory Domain Controller Could Not Be Contacted - December 10, 2020Manage and Disable Windows Defender Using PowerShell - December 9, 2020Using Out-File Cmdlet to Redirect Output to File in PowerShell - December 4, 2020='font-size:14px>='font-size:14px>='font-size:14px>
This site uses cookies to analyze traffic, personalize your experience and serve ads. By continuing browsing this site, we will assume that you are agree with it. =cn-notice-text>
A Network Protocol is a set of rules that define how data is communicated between different computers that are connected through a network connection.
Network Protocols are of different types such as Ethernet, FDDI, LocalTalk and TokenRing. They comprise of procedures and formats to be followed during data transmission. You might encounter the One or more protocols are missing error on a Windows 10 laptop/ PC due to one or more of the following reasons:
Your system doesn’t support usage of IPv6
Your WinSock defaults have been changed
DNS registration issues
Corrupt Registry keys, code identifier issues
Insufficient Registry permissions to access network data
A protocol needs to be installed
Use Internet Protocol Version 4
IPv6 is a next-generation protocol. If you’re encountering problems deploying IPv6, configure your laptop to use an older protocol such as IPv4.
Press Windows Key + X; choose Control Panel.
Click Network and Internet | Network and Sharing Center.
Click the Wi-Fi/ Wired Broadband connection that appears in Connections.
Wi-Fi/ Wired Broadband Status dialog will open up on your screen.
Click Properties.
Uncheck Internet Protocol Version 6 (TCP/ IPv6).
Check Internet Protocol Version 4 (TCP/ IPv4).
Click OK | Close.
Restore Winsock Defaults
WinSock, earlier known as WSA, deals with network services such as TCP/IP. Problems with the functioning of WinSock can cause protocol errors. Restore default WinSock configurations using an elevated CMD.
Press Windows Key + X; select Command Prompt (Admin).
Type the following command: Netsh winsock reset
Press the Enter key of your keyboard.
Restart your system using the following command-line: Shutdown /r
Flush & Register New DNS
Domain Name Servers (DNS)translates a website’s name into the corresponding Internet Protocol (IP) Address. If the process of converting human-readable website names fails, you may get the protocol missing error.
Open an elevated Command Prompt.
Flush the existing DNS: ipconfig /flushdns
Register a new DNS: ipconfig /registerdns
Release and renew the information: ipconfig /release ipconfig /renew
Reset the Catalog: netsh winsock reset catalog
Store the logs in a separate file named reset.log netsh int ipv4 reset reset.log netsh int ipv6 reset reset.log pause
Restart your computer: shutdown /r
Modify Registry Configurations
Provide appropriate read, write and access permissions to the Registry subkeys that deal with your computer’s network connection.
Type RegEdit in the Search Box on the Taskbar.
Open Registry Editor from the Search Results.
Locate the following Registry path: HKEY_LOCAL_MACHINE | SYSTEM | CurrentControlSet | Control | Nsi | {eb004a00-9b1a-11d4-9123¬-0050047759bc}
Right-click a 26 subkey, choose Permissions.
In the new dialog, specify the Group or User Name as Everyone.
Check the Allow box ahead of Full Control.
Click Apply | OK.
Install New Protocol
Go to your Connection Properties and then install a new protocol through the steps given below:
Type ncpa.cpl in the Search Box and open it from the Search Results.
Right-click your Wi-Fi/ Wired Broadband connection icon, choose Properties.
Click the Install button.
Choose Protocol in the subsequent Select Network Feature Type dialog, and click Add.
Click Hard Disk button.
Specify the following path: C:Windowsinf
Click OK.
You have a new dialog – Select Network Protocol
Select Internet Protocol (TCP/ IP) – Tunnels
Click OK.
Delete Code Identifier
Make sure the code identifier keys aren’t corrupt. Delete the corrupted data so that your system will generate default settings.
Open Registry Editor.
Locate following Registry path: HKEY_LOCAL_MACHINE | SOFTWARE | Policies | Microsoft | Windows | Safer | CodeIdentifiers | 0
Delete the Paths subkey. (Right-click > Delete)
Exit the Registry Editor and restart your laptop.

0 notes
Text
Migrate WSUS Database between two SQL

Migrate WSUS Database between two SQL.
Solution 1. You have access to both SQL Servers
1. Run Command Prompt as Admin on your server with WSUS Role; 2. Type and execute the next command: net stop W3SVC && net stop wuauserv && net stop WsusService 3. Run SQL Server Management Studio on the first (old) SQL Server; 4. Navigate to your WSUS Database (by default SUSDB). Right Click and select Tasks\Detach;

5. Copy your WSUS Database and Logs files to new location; 6. Run new SQL Management Studio and Attach copied Database; 7. On your WSUS Server run Registry Editor and change key: HKLM\SOFTWARE\Microsoft\UpdateServices\Server\Setup\SqlServerNameStart 8. Change servername from old SQL Server to new; 9. Run Command Prompt as Admin on your server with WSUS Role; 10. Type next command: net start W3SVC && net start wuauserv && net start WsusService 11. Test, by running WSUS Console.
Solution 2. You have files of WSUS Database
In case you can't access to SQL Server instance with WSUS database with SQL Management Studio, but DB and Logs files available. 1. Run Command Prompt as Admin on your server with WSUS Role; 2. Type and execute the next command: net stop W3SVC && net stop wuauserv && net stop WsusService 5. Copy your WSUS Database and Logs files to new location; 6. Run SQL Management Studio on new SQL Server and Attach copied Database; 7. Expand the Security, Right Click on Logins, and then select New Login; 8. Enter NT AUTHORITY\NETWORK SERVICE for the Login Name; 9. Click on User Mapping and confirm that the user has the dbo Default Schema granted on the SUSDB Database; 10. Click on OK to create the login; 11. Right Click on Logins, and then select New Login; 12. Enter {WSUS Server Name}\WSUS Administrators for the Login Name; 13. Click on User Mapping and confirm that the WSUS Administrators Group is granted access to the SUSDB Database; 14. Click on OK to create the login;

15. On your WSUS Server run Registry Editor and change key: HKLM\SOFTWARE\Microsoft\UpdateServices\Server\Setup\SqlServerNameStart 16. Change server name from old SQL Server to new; 17. Run Command Prompt as Admin on your server with WSUS Role; 18. Type next command: net start W3SVC && net start wuauserv && net start WsusService 19. Test, by running WSUS Console. Read the full article
0 notes
Text
Recommended services for on-prem virtualization infrastructures

When deploying an on-prem virtualization infrastructure (which could also be thought of as a private cloud with the sole customer being the enterprise/organization itself) the following services and server roles should be considered in order to achieve a complete virtualization solution: Directory services. As an example, Microsoft Windows Server Active Directory or other LDAP-based solution can be deployed. In the case of Active Directory, a comprehensive list of Group Policy Objects (GPO) should be designed. DNS services. An an example, Microsoft DNS server or Unix-based BIND DNS servers and DNS zones can be deployed. Certificate services. This constitutes a private Certificate Authority for an organization and can consist of an Enterprise Root Certification Authority and various other subordinate authorities in the organization structure. DHCP services. Various DHCP server implementations are available out there, including both hardware-based and software-based solutions. Package update service. Either Microsoft Windows Server Update Services (WSUS) or a Linux automatic package update management solution should be considered for the operating system. Application update service. Ranging from sophisticated platforms such as System Center Configuration Manager to more lightweight solutions such as PatchMyPC updater, an application update solution should be in place. SQL and non-SQL database solution. Read the full article
#ActiveDirectory#applicationservers#bestpractices#cloud#containers#design#Microsoft#recommendations#remoteaccess#serverroles#virtualization
0 notes