#WhatsApp Message Extensions
Explore tagged Tumblr posts
Text
#WhatsApp in Google Ads#Google Ads#Message Extensions#WhatsApp Business#WhatsApp API#Digital Advertising#Google ads message assets#WhatsApp Business API integration#WhatsApp Message Extensions#Turain Software
0 notes
Text
🟩 Monday morning - events from Israel
ISRAEL REALTIME - Connecting to Israel in Realtime
( VIDEO - IDF bombing Hezbollah hidden Hezbollah rocket launch sites in south Lebanon villages, this video from Tyre. Note the secondary explosions. )
♦️IDF MESSAGE to South Lebanese: If you are near a building where there are Hezbollah weapons, stay away from the village until further notice.
♦️Intense bombing by the IDF Air Force from the early hours of the morning. Continued increase of force. Dozens of villages and towns were attacked from the morning hours in southern Lebanon. The Lebanese counted over 150+ air force strikes that lasted about an hour and a quarter.
.. Videos from Lebanon show intense explosions and major secondary explosions - meaning rockets hit.
♦️IDF spox: the IDF is now widely attacking Hezbollah terror targets in Lebanon. The targets: Hezbollah launch sites. We detected Hezbollah's preparations to attack the citizens of the State of Israel and that is why we attacked. For twenty years Hezbollah distributed weapons in southern Lebanon, placing missiles in peoples homes.
♦️A GENERAL’S ANALYSIS: Brigadier General (resp.) Yossi Kuperverser writes: "The repeated failures of Iran and Hezbollah to obtain revenge by promoting terrorist attacks against senior Israeli officials, may lead them to try to save their damaged honor by extensive military action, which in turn will lead to escalation and justify strong Israeli action."
❗️IDF: Following the IDF Spokesperson's statement, attached is a video that reveals the attempt by Hezbollah terrorists to launch cruise missiles from a house in Lebanon: https://bit.ly/3ZCK3Fp - these missiles have range over all of Israel and a 300 kg warhead, very destructive.
▪️IRAN AFRAID OF RADIOS.. Reuters report: The Revolutionary Guards have ordered all their men to immediately stop using all electronic radios for fear that they too will be captured by Israel. An extensive operation began to test all devices.
▪️CHINA.. calls on its citizens to leave Israel as soon as possible. China manages port operations at one of the Haifa ports, and multiple major construction projects in the country including the Tel Aviv light rail.
▪️RELIGIOUS POLITICS.. United Torah Judaism to the Prime Ministers Office: Strongly demand that Netanyahu not fly back to Israel on Shabbat after he flies to the US to speak at the UN. "If Netanyahu can't fly without staying on Shabbat, let him not fly"
▪️TEACHERS STRIKE DEAL.. Teachers' salaries will increase by NIS 1,200 in relation to the scope of the position.
▪️DEAL NEWS.. The Americans submitted drafts of their new mediation proposal to Hamas - and were refused.
⭕Overnight a large explosion was heard in the city of al-Shadadi, where American forces are located near the Iraq-Syria border. The US Al Shadadi base was reportedly under rocket attack, alarms sounded at the base.
⭕DRONE BARRAGE from Hezbollah this morning at near-border towns in the near.
🔅 SHARE US WITH A FRIEND! Send the URL below —>
🔅Telegram - https://t.me/Israel_Realtime_Updates
🔅WhatsApp - https://chat.whatsapp.com/BfOkwWZoUvOEmGZ7Z5sj5C
🔸X (twitter) - https://x.com/IsraelRealtime
🔸Facebook - https://www.facebook.com/profile.php?id=61558471625976
#Israel#October 7#HamasMassacre#Israel/HamasWar#IDF#Gaza#Palestinians#Realtime Israel#Hezbollah#Lebanon
28 notes
·
View notes
Text
Secure person frets about modern security
(...)
Internet of Things. More like @internetofshit. Whenever possible, avoid "smart" devices, which are essentially incredibly insecure, internet-connected computers that gather tons of data, get hacked all the time, and that people willingly place into their homes. These things have microphones, and they routinely send data back to the mothership for analytics and to "improve customer experience" lol ok.
As an example, in my younger and naive years I once purchased a CO2 monitor from China that demanded to know everything about me and my precise physical location before it would tell me the amount of CO2 in my room. These devices are a huge and very common attack surface on your privacy and security and should be avoided.
Messaging. I recommend Signal instead of text messages because it end-to-end encrypts all your communications. In addition, it does not store metadata like many other apps do (e.g. iMessage, WhatsApp). Turn on disappearing messages (e.g. 90 days default is good). In my experience they are an information vulnerability with no significant upside.
Browser. I recommend Brave browser, which is a privacy-first browser based on Chromium. That means that basically all Chrome extensions work out of the box and the browser feels like Chrome, but without Google having front row seats to your entire digital life.
Search engine. I recommend Brave search, which you can set up as your default in the browser settings. Brave Search is a privacy-first search engine with its own index, unlike e.g. Duck Duck Go which basically a nice skin for Bing, and is forced into weird partnerships with Microsoft that compromise user privacy. As with all services on this list, I pay $3/mo for Brave Premium because I prefer to be the customer, not the product in my digital life. I find that empirically, about 95% of my search engine queries are super simple website lookups, with the search engine basically acting as a tiny DNS. And if you're not finding what you're looking for, fallback to Google by just prepending "!g" to your search query, which will redirect it to Google.
Credit cards. Mint new, unique credit cards per merchant. There is no need to use one credit card on many services. This allows them to "link up" your purchasing across different services, and additionally it opens you up to credit card fraud because the services might leak your credit card number. I like and use privacy dot com to mint new credit cards for every single transaction or merchant. You get a nice interface for all your spending and notifications for each swipe. You can also set limits on each credit card (e.g. $50/month etc.), which dramatically decreases the risk of being charged more than you expect. Additionally, with a privacy dot com card you get to enter totally random information for your name and address when filling out billing information. This is huge, because there is simply no need and totally crazy that random internet merchants should be given your physical address. Which brings me to...
Address. There is no need to give out your physical address to the majority of random services and merchants on the internet. Use a virtual mail service. I currently use Earth Class Mail but tbh I'm a bit embarrassed by that and I'm looking to switch to Virtual Post Mail due to its much strong commitments to privacy, security, and its ownership structure and reputation. In any case, you get an address you can give out, they receive your mail, they scan it and digitize it, they have an app for you to quickly see it, and you can decide what to do with it (e.g. shred, forward, etc.). Not only do you gain security and privacy but also quite a bit of convenience.
Email. I still use gmail just due to sheer convenience, but I've started to partially use Proton Mail as well. And while we're on email, a few more thoughts. Never click on any link inside any email you receive. Email addresses are extremely easy to spoof and you can never be guaranteed that the email you got is a phishing email from a scammer. Instead, I manually navigate to any service of interest and log in from there. In addition, disable image loading by default in your email's settings. If you get an email that requires you to see images, you can click on "show images" to see them and it's not a big deal at all. This is important because many services use embedded images to track you - they hide information inside the image URL you get, so when your email client loads the image, they can see that you opened the email. There's just no need for that.
Additionally, confusing images are one way scammers hide information to avoid being filtered by email servers as scam / spam.
VPN. If you wish to hide your IP/location to services, you can do so via VPN indirection. I recommend Mullvad VPN. I keep VPN off by default, but enable it selectively when I'm dealing with services I trust less and want more protection from.
DNS-based blocker. You can block ads by blocking entire domains at the DNS level. I like and use NextDNS, which blocks all kinds of ads and trackers. For more advanced users who like to tinker, pi-hole is the physical alternative.
Network monitor. I like and use The Little Snitch, which I have installed and running on my MacBook. This lets you see which apps are communicating, how much data and when, so you can keep track of what apps on your computer "call home" and how often. Any app that communicates too much is sus, and should potentially be uninstalled if you don't expect the traffic. I just want to live a secure digital life and establish harmonious relationships with products and services that leak only the necessary information. And I wish to pay for the software I use so that incentives are aligned and so that I am the customer. This is not trivial, but it is possible to approach with some determination and discipline.... (ete etc)
4 notes
·
View notes
Text

Hello there! Do you need a website to sell you items?
This is #Holiday season and Online #shoppers are super active !
Hello there!
Do you need a website, either an ecommerce website to sell and showcase your product or services or a portfolio website or custom website for
* Real estate *Furniture *Agriculture *Religion *Non Organization *Electronics *School website
or the following Niches
* Hair hair extension & wig website
* Furniture website
* Christmas & Halloween website
* Fashion & Clothing
* Book website
* Company website
Are you the following Countries and you a website?
* UNited states
* United Kingdoms
* Belgium
* Oman
* Netherlands
* France
* South Africa
* Russia
* Italy
* Spain
* Dubai
* Kuwait
* Qatar
* Canada
My team and I will provide a suitable and profitable website for your business at a very affordable rate
contact me on fiverr :
https://www.fiverr.com/s/0b53Rra
Whatsapp: https://wa.me/message/HOJTU6DL3Q5FF1
Get a Profitable shopify store Today!!!! #Shopify #BElgium #OMan #Arab #France #India #SouthAfrica #NIgeria #Norway #Spain #Italy #Dubai #Kuwait #Qatar #China #Japan #USA #UK #Greece #Lebanon #Iceland #NewYork #paypal #Furniture #Homedecor #Handicraft #Antique #Groscery #Electronics #Christmas #Halloween #BlackFriday #Order #Trade #BTC #LOndon #Africa #Safari #Apple #Ecommerce #Store #Blackownedbusiness #Instagram #facebook #tumblr
#Shopify#BElgium#OMan#Arab#France#India#SouthAfrica#NIgeria#Norway#Spain#Italy#Dubai#Kuwait#Qatar#China#Japan#USA#UK#Greece#Lebanon#Iceland#NewYork#paypal#Furniture#Homedecor#Handicraft#Antique#Groscery#Electronics#Christmas
7 notes
·
View notes
Text
WhatsApp Uncovers Paragon Spyware Campaign Across 24+ Countries

Meta's WhatsApp has revealed that Paragon Solutions, an Israeli spyware company, targeted approximately 90 users—including journalists and civil society members—across more than two dozen countries. The spyware, known as Graphite, was deployed through "zero-click" attacks, allowing it to infiltrate devices without any user interaction.
Details of the Attack
The targeted individuals received notifications from WhatsApp confirming their inclusion in the attack. The spyware's "zero-click" attack methodology means that the targets did not need to interact with malicious content to be compromised. Graphite allows extensive access to infected devices, including reading encrypted messages.
Paragon Solutions' Background
Paragon Solutions, an Israeli firm, has previously marketed its spyware as ethical, claiming to sell only to stable democratic governments. However, this incident raises concerns about the company's practices and the potential misuse of its technology.
WhatsApp's Response
In response to the attack, WhatsApp issued a cease-and-desist letter to Paragon Solutions and disrupted the hacking effort. The incident has been reported to law enforcement and Citizen Lab, a Canadian internet watchdog.
Implications for Privacy and Security
This incident underscores the ongoing challenges in protecting user privacy and security against sophisticated spyware attacks. It highlights the need for robust security measures and accountability in the commercial spyware industry.
4 notes
·
View notes
Text
I am not doing well.
At all.
Yesterday was my birthday. I turned 42. I live at house number 42. As a life-long Hitchhiker's Guide fan, this is a birthday I've looked forward to for years (for my brother's 42nd a couple of years ago, I bought him a bowl of jet-black petunias, with a whale toy nestled amongst them. I was wondering how he would top it) but I cancelled my birthday this year.
Last year, my family drove down to visit us. My side of the family isn't large. Both sets of grandparents are dead, my mum was an only child, my dad's brother - who never had kids of his own - died when I was about 4. My brother is single and doesn't want kids or a partner. So my side of the family is me, my parents, my brother.
And we're close.
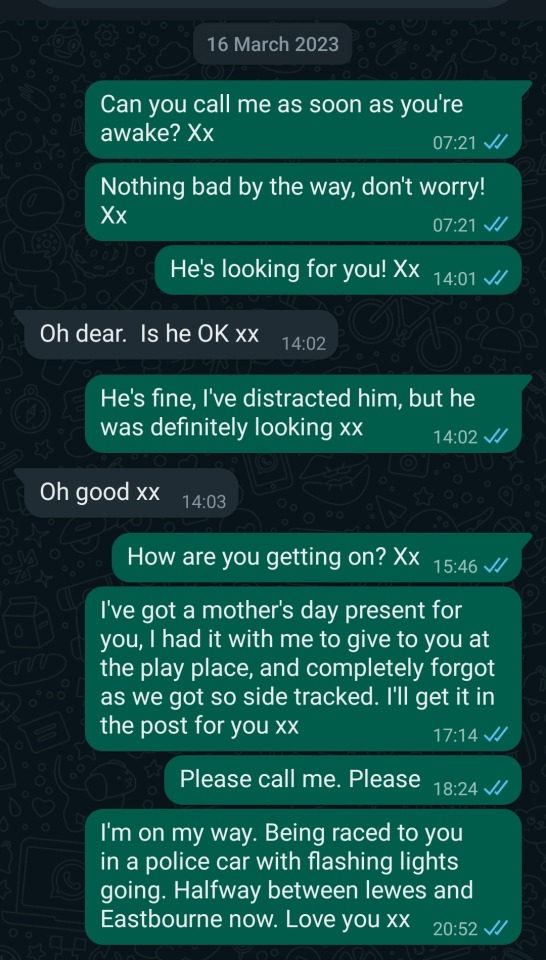
So yeah... they drove down to see me for my birthday. They stayed a couple of nights. They were going to leave shortly after breakfast on the morning of March 16th, but I persuaded them to stay just a little longer. To come with us to soft play, and then go after lunch.
They left mine at about 2pm. My little boy gets very distressed when people leave, so they had to sneak out (hence why they were originally going to leave after breakfast, straight from the hotel, so they didn't upset him.) As predicted, he got upset, and I texted mum. She answered straight away.
Anyway. She always gives me updates when she's on the road.
"We've just crossed the bridge. We're stuck in traffic. We've stopped for a coffee." And after an hour and three quarters, when I hadn't heard from her, I sent her a WhatsApp asking how they were getting on, then carried on playing with my 4 year old.
An hour later, I realised she hadn't replied. I checked my phone - the WhatsApp had been delivered but not opened. I didn't think anything of it immediately. Then half an hour after that, I saw that I'd forgotten to give mum her mother's day present, and messaged her again.
About another half hour after that message I realised what the time was, and started to worry. They ahould have been home, and still none of my WhatsApps had been opened. I called her. It rang and rang, with no answer. I tried my brother's phone. The same happened. I called Dad. Same again. I called and called and called, and by now panic was setting in.
So I began looking online for traffic updates. Any reason at all why they may be held up, unable to answer their phones. I saw that there had been an accident on the M25 around the time they were due to get there, and obviously my mind jumped to the worst. But the more I looked into that accident, it didn't seem to fit. Traffic reports said it involved a van and a lorry, and besides, if they were held up in traffic, they'd still be answering their phones, surely?
I looked at google maps, and the a21 looked completely blocked. Dark red for miles. I went on a local "what's happening" facebook group and there were several posts saying the same thing. Avoid the A21. Serious head-on collision. A stolen car being chased by police had ploughed into a white Audi, with three passengers. Two elderly. Judging by the suitcases, they'd been or were going on holiday.
I cannot begin to explain the horror of reading that. We began calling every single hospital we could think of, trying to track them down, and finally found them in Brighton. My mother-in-law raced over to us. The plan was that she would take me, my husband, and my son over to my sister-in-law's (which was on route) drop my son off there, then take me and my husband to hospital.
Just as my MIL arrived, the police turned up to tell me there had been an accident. I think they were very confused that I seemed to know more about it already than they did.
Anyway. The next 2 months were literal hell. My dad was in a coma, and at 80 years old, was walking a knife's edge between life and death. His list of injuries was extensive. From top to bottom, he had a broken shoulder blade, broken collarbone, every single bone in his right arm was broken, his elbow completely shattered, he had 5 broken ribs, his spine was fractured in two places, his pelvis was shatterd, his femur broken. One lung was punctured and collapsed, he had internal bleeding into stomach, his renal artery was damaged.
My mum and brother fared better. My brother had quite severe concussion and extensive bruising, but nothing else, my mum also had bruising and a small tear in her liver, but they were otherwise conscious.
After a week, both my mum and brother were discharged from hospital. We found a 2nd hand mattress that we set up in our living room, so that me, my husband, and my son could sleep in there, my brother taking my son's room, and my mum taking ours until dad could come home.
And he seemed to be miraculously improving.
But after a week, we received a phone call at around 3am. Dad had taken a turn for the worse. His heart had stopped twice, and they had made the decision to not resuscitate should it happen again. We should get to the hospital to say goodbye. We were told it wasn't a matter of 'if' but 'when.'
We stayed by his side for 36 hours, telling him stories. Remembering happy memories. And after those 36 hours, I remember the doctor's exact words. "I don't understand what miracle has happened here, but I think you are safe to go home."
My dad is a miracle. He improved. He woke up. 6 weeks later, he was well enough to be moved to a hospital closer to home.
But the trauma of those two months will always stay with me. I can no longer celebrate my birthday because the association and guilt that I was the one who made them stay later, and it was because of me that they were there in the first place, are too intertwined. I have been officially diagnosed with suffering from PTSD as a result of it. Yesterday was awful, but I know tomorrow will be even worse.
Tell your loved ones that you love them. I am fortunate to still be able to do so, but that can be taken away from us in a heartbeat
11 notes
·
View notes
Text
WhatsApp AI: Revolutionizing Communication and Beyond

In today’s fast-paced world, communication plays a pivotal role in personal and professional spheres. Enter WhatsApp AI, a game-changer that is reshaping how individuals, businesses, and organizations interact. Leveraging artificial intelligence to enhance WhatsApp’s capabilities is transforming it from a simple messaging app to a robust tool for automation, customer engagement, and personalized experiences. Let’s dive into the world of WhatsApp AI and explore how it is influencing various aspects of our lives.
What is WhatsApp AI?
At its core, WhatsApp AI refers to integrating artificial intelligence technologies into WhatsApp to enhance its functionalities. This includes chatbots, machine learning algorithms, and natural language processing (NLP) models that make interactions smarter, faster, and more intuitive. AI can automate tasks, provide instant responses, and even offer data-driven insights, making WhatsApp a go-to platform for more than just chatting.
The Role of AI in WhatsApp
The application of AI in WhatsApp extends across various domains, such as:
1. Chat Automation with WhatsApp Chatbots
WhatsApp chatbots powered by AI are revolutionizing customer service. These bots can handle multiple inquiries simultaneously, provide 24/7 support, and deliver accurate information instantly. Whether it’s answering FAQs, processing orders, or troubleshooting, businesses can rely on AI-driven chatbots to improve efficiency and customer satisfaction.
2. Personalized Communication
WhatsApp AI enables personalized messaging by analyzing user behavior and preferences. This is particularly useful for businesses running marketing campaigns. Instead of sending generic messages, companies can tailor their communication to individual needs, boosting engagement and conversion rates.
3. Language Translation
Breaking language barriers is another significant advantage of WhatsApp AI. AI-powered translation tools integrated into WhatsApp can instantly translate messages into various languages, fostering seamless communication between users across the globe.
4. Smart Notifications and Reminders
AI can also help users stay organized by offering smart notifications and reminders based on their habits and schedules. For instance, it can remind users of upcoming meetings, tasks, or appointments in a personalized and timely manner.
5. E-commerce Integration
AI has transformed WhatsApp into a mini e-commerce hub. With AI-driven solutions, businesses can showcase products, guide users through purchase decisions, and complete transactions—all within the app.
Benefits of WhatsApp AI
Efficiency: Automating repetitive tasks allows businesses to save time and allocate resources more effectively.
Scalability: Businesses can handle a large volume of interactions without compromising on quality.
Cost-Effectiveness: AI reduces the need for extensive human intervention, cutting operational costs.
Improved User Experience: Real-time responses and personalized communication enhance user satisfaction.
Data Insights: AI tools analyze interactions to provide valuable insights for businesses to make data-driven decisions.
Real-World Applications
1. Customer Support
From handling complaints to tracking orders, WhatsApp AI is becoming a trusted assistant for customers and companies alike.
2. Healthcare
Hospitals and clinics use WhatsApp AI to schedule appointments, share reports, and send reminders to patients, ensuring a seamless healthcare experience.
3. Education
Educational institutions are leveraging AI-powered WhatsApp tools for administrative tasks, such as fee reminders, class schedules, and assignment submissions.
4. Travel and Hospitality
Travel agencies use WhatsApp AI to send ticket details, itinerary updates, and hotel booking confirmations, making the travel experience hassle-free.
5. Retail
Retailers are integrating AI into WhatsApp to showcase products, manage inventory, and guide customers through their shopping journey.
The Future of WhatsApp AI
As artificial intelligence continues to evolve, the scope of WhatsApp AI is bound to expand. Future innovations may include even more advanced conversational AI, predictive analytics for proactive customer engagement, and seamless integration with other apps and services. The possibilities are limitless, and the potential for growth is immense.
2 notes
·
View notes
Text
Case Studies of Successful Mobile Apps: What Makes Them Stand Out
Successful Mobile Apps
The development of mobile applications has become an essential component of modern life.The mobile app market is saturated with millions of apps, but only a few manage to achieve significant success. Understanding what makes these apps stand out can provide valuable insights for developers and entrepreneurs looking to create their own successful applications. In this blog, we will analyze some of the most successful mobile apps and uncover the key factors behind their success.
1. WhatsApp: Revolutionizing Communication
Overview: WhatsApp is a cross-platform messaging app that allows users to send text messages, voice messages, make voice and video calls, and share images, documents, and user locations.
Key Success Factors:
User-Centric Design: WhatsApp's interface is simple and easy to use, ensuring a seamless user experience.
Reliability: WhatsApp provides reliable and fast messaging, even in areas with poor internet connectivity.
Cross-Platform Availability: The app is available on multiple platforms, including iOS, Android, and web, ensuring broad accessibility.
Encryption: WhatsApp’s end-to-end encryption ensures user privacy and security, which has built trust among users.
2. Instagram: Visual Storytelling
Overview: Instagram is one of the best mobile app development projects that has changed the way people share photos and interact with each other online.Instagram is a photo and video-sharing social networking service that allows users to share their moments with followers and discover content from all over the world.
Key Success Factors:
Visual Appeal: Instagram’s focus on high-quality images and videos has made it a favorite for visual storytelling.
User Engagement: Features like Stories, Reels, and IGTV keep users engaged and encourage content creation.
Influencer Marketing: Instagram has become a hub for influencers and brands, driving significant engagement and revenue through sponsored posts.
Continuous Innovation: Regular updates and new features keep the platform fresh and exciting for users.
3. Uber: Transforming Transportation
Overview: Uber is a ride-hailing app that connects passengers with drivers of vehicles for hire and ridesharing services.
One of the main reasons for the success of the Uber mobile app is its simplicity and user-friendliness. The app is user-friendly and provides users with an easy way to arrange their transportation. Moreover, the app’s real-time tracking features provide users with peace of mind.
Key Success Factors:
Convenience: Uber offers a hassle-free way to book rides with just a few taps on a smartphone.
Real-Time Tracking: Users can track their ride in real-time, providing a sense of safety and reliability.
Cashless Payments: The app integrates cashless payment options, making transactions smooth and efficient.
Dynamic Pricing: Uber’s surge pricing model ensures availability of rides during peak times, balancing supply and demand.
4. Spotify: Personalized Music Streaming
Overview: Spotify is a music streaming app that gives users access to millions of songs, podcasts, and videos from artists all over the world.
Key Success Factors:
Personalization: Spotify’s algorithm provides personalized music recommendations based on user preferences and listening history.
Extensive Library: A vast library of music and podcasts ensures that there is something for everyone.
User-Friendly Interface: The app’s intuitive interface makes it easy for users to discover and enjoy music.
Social Features: Spotify allows users to share music and playlists, fostering a community of music lovers.
5. TikTok: Short-Form Video Entertainment
Overview: TikTok is a social media platform for creating, sharing, and discovering short-form videos, ranging from 15 seconds to three minutes.
Key Success Factors:
Virality: TikTok’s algorithm promotes content based on engagement rather than follower count, allowing anyone to go viral.
Creativity: A wide array of editing tools, filters, and effects encourages creativity and content creation.
Community Building: Challenges and trends foster a sense of community and participation among users.
Global Reach: TikTok has a broad international user base, making it a global phenomenon.
Conclusion
Mobile application development has become an integral part of our day-to-day lives. Analyzing these successful mobile apps reveals several common factors that contribute to their success: user-centric design, continuous innovation, reliability, personalization, and strong engagement strategies. By incorporating these elements into your own app development process, you can increase the chances of creating a successful mobile application.
If you’re ready to take the next step,XICONET can bring your idea of mobile app development into reality with years of professional experience and learning. We have developed several flawlessly engineered mobile apps for start-ups and enterprises with great feedback. Consider partnering with experienced developers who can bring your vision to life. Book a 30-min call with our experts, and we can get started right away!
2 notes
·
View notes
Text

New Cyborg 009 stickers were just released for LINE yesterday! LINE is a messaging app similar to whatsapp and also has an extensive sticker library for users. Unfortunately stickers tend to be only usable in app unless the publisher releases them on other stores. While these are the newest addition to the LINE sticker shop they are far from the only! There are four other Cyborg 009 sticker sets as well.
6 notes
·
View notes
Text
Reply.io is a sales engagement platform designed to help sales teams automate and manage their outreach efforts through multiple communication channels. It aims to streamline the process of engaging with prospects and customers, thereby increasing productivity and efficiency.
Below is a detailed review of its features and functionalities:
Key Features
Multi-Channel Outreach:
Email Campaigns: Automate and personalize email sequences to reach prospects effectively.
Phone Calls: Integrates with VoIP services to facilitate direct calling from the platform, including features like call recording and logging.
Social Media: Allows outreach via LinkedIn, including automated message sequences.
SMS and WhatsApp: Supports text-based outreach through SMS and WhatsApp for more direct communication channels.
Automation and Sequencing:
Automated Workflows: Create automated workflows that sequence multiple touch points across different channels.
Conditional Logic: Use conditional steps to branch sequences based on recipient behavior, such as email opens or replies.
Task Automation: Automate repetitive tasks such as follow-ups, reminders, and updating CRM records. Personalization and AI:
Email Personalization: Use dynamic fields to personalize email content, increasing engagement rates.
AI-Powered Suggestions: AI tools provide suggestions for improving email content and outreach strategies.
Personalized Videos: Integrates with video messaging tools to include personalized video content in emails.
Integration and API:
CRM Integration: Seamlessly integrates with major CRM systems like Salesforce, HubSpot, and Pipedrive, ensuring data synchronization.
API Access: Provides API access for custom integrations and automations, allowing for greater flexibility.
Third-Party Tools: Connects with various other tools such as Zapier, Slack, and Google Apps to enhance functionality.
Analytics and Reporting:
Campaign Analytics: Detailed analytics on email open rates, reply rates, click-through rates, and more.
A/B Testing: Test different versions of emails to determine which performs better.
Team Performance: Track team performance metrics to identify areas for improvement and optimize outreach efforts.
Contact Management:
Lead Management: Centralized database for managing contacts and leads, with segmentation and filtering options.
Enrichment: Automatic data enrichment to enhance lead profiles with relevant information.
Prospect Importing: Easily import contacts from CSV files or directly from integrated CRM systems.
Pros Comprehensive Multi-Channel Outreach: Supports a variety of communication channels, providing a holistic approach to sales engagement.
Advanced Automation and Sequencing: Powerful automation features help streamline workflows and increase efficiency.
Deep Personalization: Tools for email and video personalization improve engagement and response rates.
Robust Integration Capabilities: Seamless integration with CRM systems and other third-party tools enhances data synchronization and workflow automation.
Detailed Analytics: Comprehensive reporting and analytics provide insights into campaign performance and team productivity.
Cons Complexity: The extensive features and customization options can be overwhelming for new users, requiring a learning curve to fully utilize the platform.
Cost: Pricing can be relatively high, especially for smaller businesses or startups with limited budgets.
Limited Free Tier: The free tier offers limited functionality, which may not be sufficient for more extensive outreach needs.
Reply.io is a powerful and versatile sales engagement platform that offers a comprehensive suite of tools for multi-channel outreach, automation, and personalization. Its robust integration capabilities and detailed analytics make it an excellent choice for sales teams looking to optimize their engagement strategies and improve productivity. However, the complexity and cost may pose challenges for smaller organizations or those new to such platforms. Overall, Reply.io provides significant value for businesses seeking to enhance their sales outreach and engagement efforts.
4 notes
·
View notes
Text
Case Study on China
The Great Firewall of China

The Chinese government has voiced worries about the internet since 1998, viewing it as a potential source of social and political challenges to the regime's cultural values and ideology (Cawford, 2023). In response, China's Ministry of Public Security (MPS) directed the Golden Shield project, which was started in 1998 and finished in 2006 (Open Society Institute, n.d.). This initiative is a regulatory framework accompanied by an extensive system of internet censorship. According to Kerner, the western media has called it "The Great Firewall of China”, implying that it encompasses a set of tools, services, and regulations that the government of the People’s Republic of China uses to prevent access to specific online information by individuals who are physically inside its boundaries.
If you've read this far, you might be wondering how the Great Firewall of China blocks content.

The Great Firewall of China uses various methods to block content. It inspects internet traffic entering and leaving China, blocking entire domains and IP address ranges. Additionally, when a user attempts to search for the blocked keywords and phrases, the Great Firewall will block and redirect the website query in a way that does not let the user access the requested information. Additionally, the firewall also actively scans network connections for potential proxy IPs used to bypass it, such as VPNs or Tor privacy networks (Kerner, n.d.).
Criticism and Concerns of the Great Firewall of China
The Chinese government has come under criticism from numerous human rights organisations for the extensive and invasive state monitoring methods used by the Great Firewall. Critics argued that China has restricted its citizens' freedom of access to information sources by enforcing the Great Firewall's strict censorship (Gisonna, 2023). To illustrate, Google holds less than a 2% market share in China, primarily due to government restrictions, with Baidu being the dominant search engine service (Seth, 2022). In March 2009, the Chinese government also banned access to YouTube after the dissemination of videos regarding security personnel beating protestors in Tibet, a region of China (Zed Biz, 2023).
According to Gisonna (2023), in spite of the Great Firewall facing criticism, numerous technology firms have yielded to the Chinese government's self-censorship guidelines, adapting their products to align with Chinese regulations. For example, Microsoft Corporation has produced an altered version of its web search engine, Bing.
China’s powerful app - WeChat

WeChat was developed by Chinese technology giant Tencent Group and was first introduced in 2011 (Sapra, 2019).
As per Zhang (2018), WeChat has evolved beyond its original purpose as a messaging and social networking app. Tencent has effectively transformed WeChat into a super app, serving as a comprehensive platform where users can seamlessly access a multitude of authorized third-party services. These services range from tasks like ride-hailing, purchasing movie tickets, ordering food delivery, booking hotels, paying bills, and many other functionalities. Long story short, it is nearly impossible to do anything without access to WeChat nowadays (Sapra, 2019).
Tencent (2018) argued that “WeChat aims to embed itself in every moment of the user's daily life, from morning till night, anytime, anywhere.”
Why WeChat fails when expanding abroad?
The majority of features of WeChat were constrained due to the absence of collaboration with local suppliers to offer those services. This is why WeChat is losing its competitive edge and transforming into merely another messaging application (Seppam, 2023).
Simultaneously, as per Medium (2019), WeChat's failure can be attributed to its delayed entry into the foreign market. By the time WeChat ventured into the international market in April 2012, WhatsApp had already surpassed its innovation period, spanning from 2009 to 2011. This indicates that WeChat faced limited growth opportunities to capture the global market.
Social Credit System in China

China's social credit system comprises databases and initiatives designed to monitor and evaluate the reliability of individuals, businesses, government entities, and the judiciary (Lee, 2020). It was formally introduced to the public in 2014 with the unveiling of the Outline for the Construction and Planning of the Social Credit System. In addition to looking at financial history and activity, that similar to credit rating systems in other nations, it also considers things like unethical behaviour and legal infractions (Koty & Huld, 2023).
A credit score may benefit from making good contributions to society through the establishment of social programmes, donations to charitable organisations, or other corporate social responsibility (CSR) initiatives. A high credit score may grant access to discounted public housing or priority medical care. Conversely, engaging in such undesirable behaviour as dishonest or unlawful taxation, misleading customer behaviour, and so forth, may result in a low rating and adverse outcomes including being barred from trains and aeroplanes (Lee, 2020).
Is the social credit system a way to instill good behaviour and provide safety to citizens?
From my point of view, the opinions on this question are diverse. Supporters argue that the Social Credit System could potentially improve overall societal conduct by promoting trust and integrity. They suggest that by rewarding responsible behaviour and penalising misconduct, the system could contribute to a safer and more orderly society.
On the other hand, critics express concerns about privacy violations, the potential for abuse of power, and the impact on individual freedoms. The system involves extensive surveillance and data collection, raising worries about government intervening into citizens' lives. There are fears that the system could be used for social and political control, suppressing dissent, and restricting individual freedoms.
In general, the goal of China's social credit system is to ensure that residents and companies doing business there adhere to local laws and regulations (Velocity Global, 2023). It is important to strive for a balance between the potential benefits of improved societal behaviour and the protection of individual rights.
References:
Crawford, D. (2023, February 3). What is the Great Firewall of China and how does it work. Proton VPN Blog. https://protonvpn.com/blog/great-firewall-china/
Gisonna, N. (2023, September 21). Great Firewall. Encyclopedia Britannica. https://www.britannica.com/topic/Great-Firewall
Kerner, S. M. (n.d.). Great firewall of China. WhatIs.com. https://www.techtarget.com/whatis/definition/Great-Firewall-of-China
Koty, A. C. & Huld, A. (2023, March 24). China’s social credit system: What businesses need to know. China Briefing News. https://www.china-briefing.com/news/chinas-social-credit-system-how-it-works/
Lee, A. (2020, August 9). What is China’s social credit system and why is it controversial? South China Morning Post. https://www.scmp.com/economy/china-economy/article/3096090/what-chinas-social-credit-system-and-why-it-controversial
Medium. (2019, November 19). Identify and explore why “WeChat” failed internationally. https://medium.com/@uncigolini/identify-and-explore-why-wechat-failed-internationally-605cff5043d9
Sapra, B. (2019, December 21). This Chinese super-app is Apple’s biggest threat in China and could be a blueprint for Facebook’s future. Here’s what it’s like to use WeChat, which helps a billion users order food and hail rides. Business Insider. https://www.businessinsider.com/chinese-superapp-wechat-best-feature-walkthrough-2019-12
Seppam, M. (2023, April 5). How China’s Super-App WeChat Failed in USA and Europe. Why do other successful local apps fail when expanding abroad? https://www.linkedin.com/pulse/how-chinas-super-app-wechat-failed-usa-europe-why-do-other-seppam/
Seth, S. (2022, December 31). Baidu vs. Google: What's the Difference. Investopedia. https://www.investopedia.com/articles/investing/051215/baidu-vs-google-how-are-they-different.asp#:~:text=Google%20has%20a%20strong%2C%20dominant,government%20has%20restricted%20its%20use.
Velocity Global. (2023, October 6). The Chinese Social Credit System: What to know as a business owner. https://velocityglobal.com/resources/blog/chinese-social-credit-system/
Zhang, M. (2018, March 26). China’s WeChat: The Power of the Super App. Medium. https://medium.com/@miaozhenzhang666/chinas-wechat-the-power-of-the-super-app-dc144657625e
4 notes
·
View notes
Text
Today was a teacher only day, so I had Max and Wax with me at my office. Max had organised to go to the new Spiderman movie with friends so at 11am I left work to drop him off and then work the rest of the day from home.
On the way my phone rang, but I'm driving so I didn't answer and Wax declined the call for me so it would go to voicemail and we could continue our conversation.
With Max deposited with his friends I go into a bookstore with Wax to listen to the message left. But first I have to set up my phone voicemail and add a PIN. Okay. Sure.
The message, when I finally get to it, is from my dad's Meals on Wheels service. They'd like me to call them back asap and leave a 9 digit number and then a 5 digit extension. It is not the number that has appeared on my phone.
I am at a food court in a mall and trying to get lunch for Wax and now trying to figure out how to memorise this number to call it back when my phone rings.
"When the driver went to deliver your dad's lunch today yesterday's lunch was still there."
Heart stops.
Stomach to the floor.
Sudden gasp and immediate tears brimming.
"We knocked and there was no answer, and we rang, and there was no answer."
Me: Okay. Thanks for letting me know. I'm just around the corner and will go visit.
I ring him and get no answer. I message him on his phone, through Messenger and also through WhatsApp.
I still need to get food. And then drive. And then let Hubs and my brother know.
Just in case.
I get to my dad's house and I have forgotten my keys. I bang on the front door. No answer so I walk around to the back door which is unlocked.
I call out and I get an answer.
He's okay. Alive. Not well. But alive.
He's 78 and very resistant to his 40+ year old children telling him what to do. He tells me he's made an appointment to see the doctor on Tuesday (Monday is a public holiday).
I want him to see a doctor today. His leg does NOT look good. I have a friend (Uncle Max in fact) who is a GP so I message him... This convinces my dad to go to the emergency room. He's now got antibiotics and a follow up appointment.
All's well that ends well.
Except he's forgetting his medications and is also forgetting things in the short term. So I have emailed to start the assessment process to get him some home help if we can...
7 notes
·
View notes
Text
⚠️ IRAN PREPARES, HOME FRONT CHANGES, SPECIAL FORCES VIDEOS - Tuesday afternoon - events from Israel
...‼️The United States detects preparations in Iran for a missile attack on Israel. (Amit Segal - Ch. 12)
⚠️HOME FRONT COMMAND.. as of today (Tuesday), at 14:00: added restrictions in new and wide areas throughout the country until Sat. Oct 5, 20:00. The reason for this change is the item above.
.. Restriction on activities and gatherings: Carmel (Haifa and wide area), Wadi Ara, Menashe, Samaria (West Bank), Sharon (Central cities), Dan (Tel Aviv), Yarkon, Shefala (Beit Shemesh and wide area), Jerusalem (and wide area), and Shfela.
.. Educational activities can ONLY be held in a place where you can reach a protected space in time with capacity in case of an alert.
.. Gatherings and services can be held with a limit of up to 30 people in an open area and up to 300 people in closed spaces.
.. Workplaces can operate in a building or place where you can reach a protected space in time with capacity in case of an alert.
.. Infographic: https://IDFANC.activetrail.biz/ANC0110202493864
.. Police: The Israel Police is prepared to implement the directives of the Home Front Command to the general public, following the change in the defense policy in the last hour. Civil discipline saves lives.
❗️PUBLIC ROSH HASHANA PRAYER EVENTS CANCELLED.. The impression is that this is a warning about a more specific and immediate event, not about a general escalation from Lebanon.
.. Mass hataras nedarim at the Hotel cancelled.
.. Event at the Sultan’s Pool cancelled.
.. The Rabbi of the Western Wall and Holy Places Rabbi Shmuel Rabinovitz calls on the public to take cautionand observe the mitzvah "and be very careful for your souls" - to obey the instructions of the Home Front Command and not to come to the Western Wall plaza tonight.
.. Message passed on to the Hasidim in Gur: Do not come today for prayers to the city. and prepare for the possibility that they will not be able to come to Jerusalem for the holiday.
▪️SPECIAL OPS.. Since the beginning of the war, the IDF has conducted dozens of targeted operations in areas near the border in southern Lebanon in order to dismantle Hezbollah’s terrorist capabilities and infrastructure. The soldiers identified and breached underground access points near the border area, exposed extensive weapon caches, assembly areas for terrorist operative operations, and more. During these operations, the troops also collected valuable intelligence and methodically dismantled the weapons and compounds, including underground infrastructure and advanced weaponry of Iranian origin.
The troops also uncovered and destroyed underground infrastructure, struck thousands of targets and hundreds of weapons storage facilities, tons of explosives, and hundreds of living areas for operatives, command centers and more.
Footage of IDF raids on terror targets in Lebanese territory: https://bit.ly/3ZLNw4x
Footage of the destruction of terrorist infrastructure in the area of the border: https://bit.ly/4gM9wCs
There are many more videos linked here -> https://t.me/idfofficial/10605
❗️TZAV 8.. IDF: In accordance with the situational assessment, the IDF is calling up four additional reserve (combat) brigades for operational missions in the northern arena.
▪️AIR TRAVEL.. The airport is working as usual at the moment and there is no change in the airspace.
.. Israir is expected to operate flights using six leased planes over the holidays, to help maintain aviation continuity.
🔅 SHARE US WITH A FRIEND! Send the URL below —>
🔅Telegram - https://t.me/Israel_Realtime_Updates
🔅WhatsApp - https://chat.whatsapp.com/EjYDi9it88kDyyI1lyeHkT
🔸X (twitter) - https://x.com/IsraelRealtime
🔸Facebook - https://www.facebook.com/profile.php?id=61558471625976
❗️IRAN MISSILE THREAT - Tuesday afternoon - events from Israel
ISRAEL REALTIME - Connecting to Israel in Realtime
( VIDEO - Home Front advice for holiday synagogue service - make sure to know the path to a protected space, have enough time and capacity. And what about the children? )
⭕HEZBOLLAH JUST FIRED 4 LONG RANGE MISSILES AT TEL AVIV.. a few minutes ago - they missed, hitting the sea. No alarms due to the wide miss.
‼️The United States detects preparations in Iran for a missile attack on Israel. On this basis, Israel has raised Home Front restrictions in the center and Jerusalem areas.
.. The Pentagon: Satellite images show that Iran has prepared a large number of ballistic missiles to attack Israel.
.. IDF reminds: defenses are NOT perfect, you MUST follow Home Front commands and take shelter when instructed.
.. The US Embassy in Israel asked its employees to stay at home and be prepared to go to shelters.
.. British Foreign Secretary Lammy announced that Britain is negotiating with its Iranian counterparts and calls on that country to exercise restraint in the midst of growing tensions in the region.
.. Reuters: Oil prices jumped 3% amid reports that Iran is planning to attack Israel.
📌HOME FRONT COMMAND..�� center, Tel Aviv and wide surrounding areas, Jerusalem and wide surrounding areas, Samaria
.. Educational activities can ONLY be held in a place where you can reach a protected space in time with capacity in case of an alert.
.. Gatherings and services can be held with a limit of up to 30 people in an open area and up to 300 people in closed spaces.
.. Workplaces can operate in a building or place where you can reach a protected space in time with capacity in case of an alert.
📌PUBLIC ROSH HASHANA PRAYER EVENTS CANCELLED..
.. Mass hataras nedarim at the Western Wall cancelled.
.. Event at the Sultan’s Pool cancelled.
.. The Rabbi of the Western Wall and Holy Places Rabbi Shmuel Rabinovitz: do not to come to the Western Wall plaza tonight.
.. Message to Hasidim in Gur: Do not come for prayers to the city.
❗️SPORT EVENT CANCELLED - Soccer / Football between Beitar Yerushalayim and Maccabi Haifa.
🔹IDF spokesman: "Iranian firing on the State of Israel will have consequences - I will not say more than that."
🔹IDF spokesman Brigadier General Hagari: "IDF fighters found a "plan for the occupation of the Galilee" by Hezbollah terrorists in Lebanese territory.”
🔹US Central Command: 3 additional US aircraft squadrons are on their way to the area, and one of them has already arrived.
🔹The US continues to transfer military equipment non-stop to the region. Huge military transport planes land in Jordan and Syria almost non-stop.
🔹Haifa Municipality: In light of the unusual security situation, the city council meeting scheduled for tonight is postponed.
🔹Russia to Israel: withdraw the troops from southern Lebanon immediately.
♦️ONGOING TARGETED ATTACKS in Lebanon cities.
♦️TARGETED ATTACK in Khan Yunis, Gaza on a vehicle.
♦️SYRIAN RADAR.. A radar position of Syria that attacked and destroyed a short time ago by the Air Force in southern Syria.
#Israel#October 7#HamasMassacre#Israel/HamasWar#IDF#Gaza#Palestinians#Realtime Israel#Hezbollah#Lebanon
12 notes
·
View notes
Text
Malaysians engagement with politics on social media, yay or nah?
In the era of digitalization, the impact of social media on democracy and political engagement is unquestionable. The use of social media platforms is a significant advancement in communication technology that has the potential to improve various aspects of human behavior (Lee et al., cited in Abdullah et al. 2021). Citizens of a diverse nation actively engage in political conversation, share ideas, and build the narrative of the country's democratic path on digital platforms, which resonate with the beating heartbeat of the nation. According to Leong 2015, The Internet is widely acknowledged for its capacity to significantly augment democratic processes and practices by enabling easy access to extensive information. So, what are the impact that the dynamic interaction between social media and Malaysia's political scene on democracy?

Within the domain of Malaysian politics, social media serves as a dynamic space where many platforms influence and create political discussions. While the government still maintains strict control over opposing media, political activists now have a new platform to spread their message thanks to the Internet without having to worry as much about laws (Wok & Mohamed 2017). Individuals have the ability to establish separate political groups on the internet, publish and spread political matters via blogs, and share political videos on their social media platforms. According to Weiss (2012), the political effects of these types of media are shaped by the dynamic and interactive nature of these forms. Additionally, social media platforms like Facebook, Twitter, and instant messaging applications such as WhatsApp serve a vital role in providing information and enabling political engagement. According to Abdullah et al. (2021), it is discussed that the reasons and processes behind the use of online platforms for political information-seeking, which serve as a substitution for traditional offline methods of communication, such as talking with friends, asking questions, sharing beliefs or information, and engaging in practices related to political matters.

Political entities in Malaysia effectively utilize social media to reinvent normal campaigning and communication within the fast-changing digital world. An example would be in the 2008 general election, political group Barisan National had its leaders prioritized the creation of their online presence by utilizing websites, blogs, and social media platforms such as Twitter and Facebook to engage with young voters (Mohsin & Raha, cited in Leong 2015). Additionally, they established online e-government portals to facilitate public participation, feedback, and the delivery of services. Along with social media, it helps enable the spread of political messages and offers a direct means of communication, which surpasses traditional campaign techniques by providing immediacy. Social media plays a crucial role for politicians in shaping their public image and providing transparency to users by sharing information to the public, and the online presence of political leaders will demonstrate their interactions with voters, which is a crucial aspect in attracting voters (Hamid et al. 2018). The rise of social media has given politicians a powerful tool to effectively connect with and involve younger voters. Nevertheless, this ease of access also has dangers, since the platform's unrestricted nature exposes politicians to the possibility of intentional sabotage.

Although social media has a significant impact on making information accessible to everyone, it also presents a series of difficulties, most notably demonstrated by the quick spread of false or misleading information. In a rarer occurrence, a study found out that political parties were using cyber- warfare tactics during the general election in 2013, to discredit and derail their messages, reducing the impact and influence each party has in the election (Mill, cited in Leong 2015). Thus, imploding and increase of cyber troopers and social media users whose purpose was to counter any opposition media content. According to Leong (2015), the internet was filled with manipulation, overstatement, and misinterpretation of information for political purposes, thus infecting the competence and rationality of citizens. Thus far, the government has been actively trying to minimize the spread of false political content, or any information that could negatively impact the nation's reputation. According to Weiss (2012), a blogger was charged and had possible penalization when they were caught publishing false information on their blog.

In conclusion, the mutual beneficial relationship between Malaysians and social media has brought forth a major and significant shift in the political landscape of the nation. The connection between technology and politics, particularly shown by the active participation of citizens, has fundamentally changed the old models of political communication. It is argued that politicians and parties are transitioning from the conventional one-sided, hierarchical method of communication to a more interactive approach of communication (Leong 2015). In the era of digitalization, where knowledge is easily accessible, it is crucial for everyone, especially the younger people, to participate actively in political discussions. Participation in these discussions provides citizens with the information to affect the political landscapes that will impact the future direction of the nation.

References:
Abdullah, N.H., Hassan, I., Fazil Ahmad, M., Hassan, N.A. and Ismail, M.M 2021, ‘Social media, youths and political participation in Malaysia: A review of literature' International Journal of Academic Research in Business and Social Sciences, Forthcoming, viewed 15 November 2023, < http://dx.doi.org/10.2139/ssrn.3849948>.
Leong, P. P. Y 2015,’Political Communication in Malaysia: A study on the Use of New Media in Politics’, JeDEM - eJournal of eDemocracy and Open Government, 7(1), pp, 46–71, viewed 15 November 2023, < http://dx.doi.org/10.29379/jedem.v7i1.372>.
Wok, S. and Mohamed, S 2017,’Internet and social media in Malaysia: Development, challenges and potentials’ In The evolution of media communication, IntechOpen, viewed 15 November 2023, <http://dx.doi.org/10.5772/intechopen.68848>.
Weiss, M.L 2012, ‘Politics in cyberspace: New media in Malaysia. Berlin: Friedrich-Ebert-Stiftung', fesmedia Asia,viewed 15 November 2023, <https://library.fes.de/pdf-files/iez/09068.pdf>.
Hamid, Nur Nadhirah Ab, and Safawi Abdul Rahman 2018, ‘Impact of social media on Malaysia’s election landscape’, International Journal of Academic Research in Business and Social Sciences, vol. 8, no. 9 : 275-284, viewed 15 November 2023, <http://dx.doi.org/10.6007/IJARBSS/v8-i9/4590>.
2 notes
·
View notes
Text
The Rise of WhatsApp Commerce: A New Dimension of Shopping
In the fast-paced world of digital innovation, the intersection of communication and commerce has given rise to a new paradigm—WhatsApp Commerce. This transformative approach leverages the ubiquitous messaging platform, WhatsApp, to redefine the shopping experience. At the forefront of this evolution is Cordelia, a cutting-edge solution that seamlessly integrates with WhatsApp to propel businesses into a new dimension of customer engagement and transactions.
WhatsApp, with its extensive user base and global reach, has become more than just a messaging app; it is now a dynamic marketplace. The fusion of communication and commerce on this platform opens up unprecedented opportunities for businesses to connect with their audience directly.
Cordelia, as a key player in this landscape, serves as the bridge between businesses and the vast potential of WhatsApp Commerce. Here’s how Cordelia can revolutionize your approach to online retail:
Streamlined Customer Interaction:
Cordelia enhances the conversational experience by providing businesses with tools to streamline customer interactions. Through automated responses and intelligent chatbots, customer queries are addressed promptly, fostering a seamless and efficient communication channel.
Personalized Shopping Experience:
Leveraging customer data and preferences, Cordelia enables businesses to deliver highly personalized shopping experiences. Tailored product recommendations, exclusive offers, and targeted promotions can be effortlessly integrated into the conversation, enhancing customer satisfaction and loyalty.
Secure Transactions:
Security is paramount in any online transaction. Cordelia ensures a secure environment for financial transactions within the WhatsApp platform. With end-to-end encryption and robust payment gateways, customers can shop with confidence, knowing their sensitive information is protected.
Order Tracking and Updates:
Ensuring customers stay in the loop about their orders is essential for crafting a positive shopping experience. Cordelia facilitates real-time order tracking and updates, allowing customers to stay in the loop and reducing uncertainties associated with online purchases.
Effortless Inventory Management:
Cordelia simplifies inventory management by seamlessly integrating with business systems. This ensures that product availability and information are always up-to-date, preventing any discrepancies and enhancing the overall efficiency of the sales process.
Analytics and Insights:
Understanding customer behavior is key to refining business strategies. Cordelia provides robust analytics and insights into customer interactions, preferences, and purchase patterns. This data-driven approach empowers businesses to make informed decisions and continually optimize their WhatsApp Commerce strategy.
In conclusion, the rise of WhatsApp Commerce marks a paradigm shift in the way businesses engage with their customers. Cordelia, as a powerful ally in this evolution, brings forth a suite of features and capabilities that not only streamline operations but elevate the entire shopping experience.
As businesses navigate the dynamic landscape of e-commerce, embracing WhatsApp Commerce with Cordelia becomes a strategic imperative—a gateway to a new dimension of customer-centric, secure, and personalized online transactions. The future of shopping has arrived, and with Cordelia, your business is poised to thrive in this exciting era of digital commerce.
2 notes
·
View notes
Text
[ID: A meme titled “If John Lennon had Whatsapp” with the following messages;
Yoko Ono: Fucking KILL YOURSELF!
Paul McCartney: I need 90 quid for lash extensions luv xoxo
George Harrison: Fucking KILL YOURSELF!
Bob Dylan: Fucking KILL YOURSELF!
Ringo Starr: Ringo! /End ID.]

6K notes
·
View notes