#Windows 0-day exploit
Explore tagged Tumblr posts
Link
🚨 URGENT SECURITY ALERT! 🚨 A critical Windows zero-day exploit is putting millions at risk. Homeland Security is urging immediate action! This isn't a drill; hackers can steal your data, compromise your system, and even steal your identity. Learn what this means and how to protect yourself NOW: http://tezlinks.blogspot.com/2024/12/urgent-windows-0-day-exploit-patch-your.html #cybersecurity #windows #zeroday #securityalert #patchnow #computersafety #datasecurity #homelandsecurity
#Windows 0-day exploit#Urgent Windows Security Patch#Windows System Vulnerability#Zero-day threat patch#Homeland Security Alert ``` Urgent Windows Security Patch#Windows 0-Day Exploit#Zero Day Vulnerability#Patch Now#Windows Security Alert ```
0 notes
Note
I know this isn’t canon in undertale or this au, but just imagining Papyrus knowing about resets to an extent because part of him was split across time and space, and he just hides that from everyone so he can be “everyone’s good old innocent Papyrus with 0 problems” is such a fun idea to me.
I HAVE SO MANY THOUGHTS ON THIS THOUGH- BECAUSE WHAT IF IT WAS CANON???
Excuse me while I use this to make an analysis of Papyrus’ character- i didn’t choose this life. This happened to me.
PAPYRUS AND RESETS.

The main question I ask on the debate of if Papyrus is aware of resets or not, is…if Papyrus, as we know him…doesn’t know about resets…Then would learning about that…change ANYTHING about the way he is now?
The most obvious trait of Papyrus is that he’s INCREDIBLY optimistic. He’s one to go in with his head held high, and keep it raised for basically his entire life. Everything he does is incredibly light hearted, and this leads to a lot of accidental flanderization and misremembering of his character. But to get more into that, I wanna address how Papyrus and Sans contrast and are foils to one another. They are complete polar opposites…and yet… SO alike. In their little bits they do in the Snowdin Forest puzzles, Sans doesn’t take anything seriously, while Papyrus takes EVERYTHING seriously, but in the end it’s all light hearted. I know some of that comes from just the games general tone, but I like to think some of it is part of their genuine character.
Analyzing characters in Undertale can sometimes be a tad frustrating in that way, since its hard to tell which jokes have meaning and which jokes are just jokes.
But back to my original point, Papyrus sometimes gets very mad, sometimes very confused, but seems to either flip on a switch with anger, or just roll with confusion, as seen with Papyrus being “mad” at Sans, or confused at what Undyne is saying on certain phone calls. He’s just naturally a very happy person.
Thats where the common trope of Papyrus lying about everything and actually being a completely different person from whats shown in the game comes in. I think thats inherently a tad silly, since “I lied.” is a bit of a lazy twist. THATS NOT TO SAY HES NOT DEFINITELY GOT SOME WEIRD SUSPICIOUS THINGS ABOUT HIM Its just to throw all of his actions in the game out the window in favor of “he was acting” “he was lying” is not how I like to analyze him (but if you do, more power to ya :D) (Some also argue that Sans is just like that, but I disagree since in the geno route when its properly revealed just how much he knows about resets, it completely makes sense and is more like an answer to a question we had for the longest time. WHAT does he know?? cause he clearly knows something. Additionally, in that fight, Sans doesn’t at all come across as a completely different person, its more like we’re getting to know him better. See a side that he’s buried for the longest time since he never thought it would come to this. Or at least hopes to god it wouldn’t)
Papyrus’ optimism/pacifism both comes across as naive, and extremely admirable. It takes different forms in different settings and perspectives, Flowey dismisses it as stupid, but thats because he’s Flowey- Sans genuinely admires it for several reasons which ill get into later! And Undyne…uhh…honestly i cant tell how she feels about that, just that she cares an awful lot about him and thinks itll get him killed one day (*cries vehemently*)
But my main point here is in the usual game/pacifist route, its very clearly established that Papyrus has a heart of gold and sometimes that can get exploited on how he is the one constant moving factor to help the route actually happen in helping Flowey set everything up. It’s lowkey giving foreshadowing on how he may be the knight in deltarune because of- OKAY OKAY- PUT DOWN THE GUN
Getting exploited is one of the downsides we see in the pacifist route, but in the geno, we get a VERY clear look into how far he is willing to take his faith in others. His willingness to see good in people is tested, and its established he doesn’t have a single distrustful bone in his body, always believing in people to change. It’s never “too late”. Even after you kill him too
This is HOW Papyrus would know about resets comes in
The King Papyrus ending is a moment in the game that I have many opinions on that disagree with a LOT with a big portion of the fandom (at least last time I checked)
Papyrus not being told about his friend's death, leads to 2 big assumptions about his GENERAL CHARACTER THAT I DISAGREE WITH. Sans lies to Papyrus on a daily basis, and Papyrus doesnt understand what death is. These are things that work in to fit every day life, and are proven by happening WHEN ALL OF HIS FRIENDS ARE DEAD 😭
I feel these are more a result of Papyrus’ unwavering trust, which can be certainly admired in a lot of ways, but of course, used, too. Even if people agree with me on that unwavering trust part, people still use that as ammunition for Sans lying to him being an often occurrence. But- Sans… right now- is being put in a REALLY bad spot. Telling his brother to his face that all his friends are dead isn't something I think anyone wants to do. So, him lying to Papyrus isn’t exactly proof that he thinks little of him in any way, it's more his desire to protect a person he loves from knowing a horrible truth, and having the opportunity to do so on a silver fukn platter. But even then it feels like Papyrus still knows…he’d just rather accept whatever Sans tells him. Thats Papyrus’ ONE AND ONLY FLAW
Papyrus also seems like he naturally thinks very black and white? and by black and white I mean only white.
The common consensus on his character is he only SEES good, but just like the assumption of how things work in daily life being attached to how these characters act when someone comes down and kills all their loved ones, I think thats working on a very surface level character-moral-compass. Its not that he only sees the good, its that he believes in the good no matter what. There may be bad, but good can and will, prevail
Papyrus sees and knows that people have the ABILITY to lie, he just also believes they are telling the truth when they say something like “I promise this is 100% true” because he still trusts everyone, and trusts himself to handle whatever happens as a result.
Papyrus sees that the world may never truly have an ending, but he believes that things will turn out eventually.
Papyrus is not stupid, he’s optimistic.

and also autistic
#undertale#papyrus#papyrus undertale#analysis#yap#same difference#im fucking CRAZY about this man#im crazy#im crazy im crazy#im crazyy#im normal#IMCRAZY#brothers (sobs in a violent fit of rage)#Ask me more about undertale#ill yap so much more im happy to do so#im *very happy*#AND DELTARUNE#I HAVE SO MUCH TO SAY ABOUT HIS DELTARUNE IMPLICATIONS#LIKE DUDES EVERYTHING ABOUT THIS MAN IS UNDERGROUND BASED#ROYAL GUARD AND PUZZLES TO GET THROUGH EVERY DAY LOFE#ALSO HES NOT OUTSIDE??#THATS LIKE THE COMPLETE OPPOSITE OF WHAT HE WOILD DO#HED BE OUTSIDE#UP AND ABOUT THE TOWN#BUT WHERE IS HE???#AND EVEN IF HE WASNT#HE WOULD *ABSOLUTELY* ANSEWR IF SOMEONE KNOCKED ON THE DOOR#*but he doesnt*#IS HE OKAY?????#no
136 notes
·
View notes
Text
Week in review: Microsoft patches exploited Windows CLFS 0-day, WinRAR MotW bypass flaw fixed

Source: https://www.helpnetsecurity.com/2025/04/13/week-in-review-microsoft-patches-exploited-windows-clfs-0-day-winrar-motw-bypass-flaw-fixed/
3 notes
·
View notes
Text
You cannot exploit the roots. They are authorized. Windows 0-day was exploited by North Korea to install advanced rootkit https://arstechnica.com/security/2024/08/windows-0-day-was-exploited-by-north-korea-to-install-advanced-rootkit/
2 notes
·
View notes
Text
0 notes
Text
⚡ Weekly Recap: Windows 0-Day, VPN Exploits, Weaponized AI, Hijacked Antivirus and More
http://i.securitythinkingcap.com/TK8Fc4
0 notes
Photo

2025年02月06日 11時36分 ロシアが圧縮・解凍ツール「7-Zip」の脆弱性を悪用してウクライナを攻撃していたことが発覚
圧縮・解凍ツール「7-Zip」のアーカイブ作成機能にWindowsの保護を無効化する脆弱(ぜいじゃく)性が存在していることが明らかになりました。問題を報告したセキュリティ企業のトレンドマイクロによると、脆弱性がロシアによるウクライナへの攻撃に悪用されていたそうです。
CVE-2025-0411: Ukrainian Organizations Targeted in Zero-Day Campaign and Homoglyph Attacks | Trend Micro (US) https://www.trendmicro.com/en_us/research/25/a/cve-2025-0411-ukrainian-organizations-targeted.html
7-Zip 0-day was exploited in Russia’s ongoing invasion of Ukraine - Ars Technica https://arstechnica.com/security/2025/02/7-zip-0-day-was-exploited-in-russias-ongoing-invasion-of-ukraine/
2024年9月25日に、トレンドマイクロの脅威ハンティングチームが7-Zipに存在するゼロデイ脆弱性「CVE-2025-0411」を特定しました。
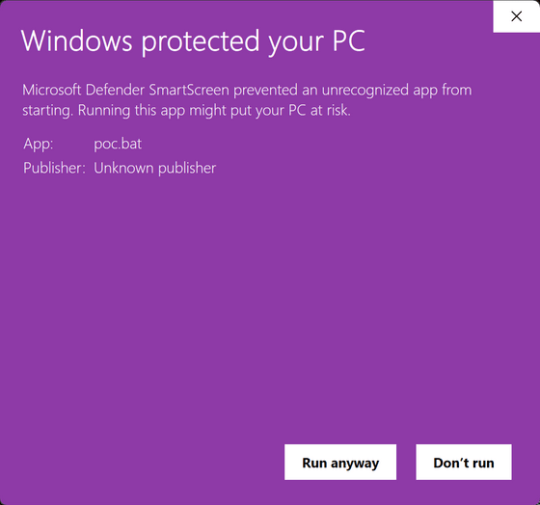
ユーザーがインターネットなどの信頼できないソースからファイルをダウンロードすると、WindowsはMark-of-the-Web(MoTW)と呼ばれるセキュリティ機能を作動させます。この機能は、ダウンロードされたすべてのファイルに「Zone.Identifier」タグを配置して、Windows Defender SmartScreenによる追加の監視とファイルの実行方法ならびにタイミングに関する制限を行うというもの。Windows Defender SmartScreenが「潜在的に危険なアプリケーションが存在する」と判断した場合、ユーザーには以下のような警告が表示されます。
しかし、CVE-2025-0411では、脅威アクターは7-Zipのアーカイブ作成機能を用いてコンテンツを二重にアーカイブすることにより、MoTWを無効化することが可能です。実際にロシアのサイバー犯罪グループは、アーカイブ内に実行ファイルを埋め込み、そのアーカイブを別のアーカイブに埋め込むことで攻撃を行っていました。
トレンドマイクロの研究者であるピーター・ジルナス氏は「CVE-2025-0411の根本原因は、バージョン24.09以前の7-Zipが、二重カプセル化されたアーカイブのコンテンツにMoTW保護を適切に施していなかったことです。これにより、脅威アクターはMoTWを受けられない悪意のあるスクリプトや実行可能ファイルを含むアーカイブを作成できるようになり、Windowsユーザーは攻撃に対して脆弱になります」と報告しています。
また、攻撃をより巧妙に偽装するために、実行可能ファイルの拡張子は「ホモグリフ」と呼ばれるものでレンダリングされていました。これらは、特定のASCII文字と同一または類似しているように見えるものの、実際は全く違う文字というもの。一例として、ASCII文字の「C」とキリル文字の「С」があります。
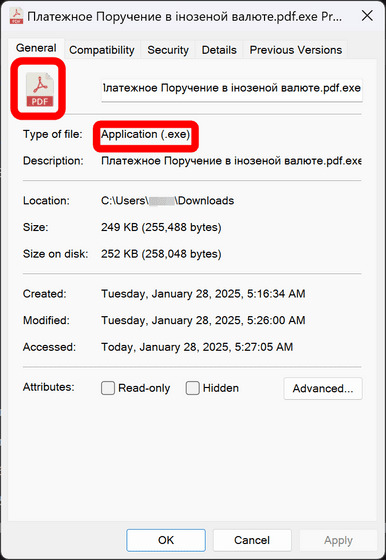
CVE-2025-0411を悪用した脅威アクターは、脅威アクターはキリル文字の「С」を使用して「.doc」ファイルに見せかけたドキュメントファイルの内部アーカイブを作成しました。これを開くと、アーカイブ内のJavaScriptファイル(.js)やWindowsスクリプトファイル(.wsf)、およびWindowsショートカットファイル(.url)がMoTW保護なしで実行されてしまいます。以下の画像は一見するとPDFファイルに見えるものの、実際はアプリケーション(.exe)を実行してしまう悪質なファイルの例。
トレンドマイクロによる調査の結果、ウクライナの複数の政府機関やウクライナの地方自治体と企業を標的とした悪意のあるメールが送信されていることが発覚しました。脅威アクターは二重にアーカイブ化されたファイルをこれらの標的への電子メールに添付して攻撃に使用しました。以下は標的となったウクライナの政府機関。トレンドマイクロは「今回の攻撃の影響を受けたのは、サイバーセキュリティに精通しておらず、大規模な政府機関なら持っているはずの包括的なサイバー戦略のためのリソースが不足している小規模な地方自治体などが多かったです」と述べています。
・ウクライナ国家行政庁(SES) ・ザポリージャ自動車製造工場(PrJSC ZAZ) ・キエフパストラン ・SEA Company ・ヴェルホヴィナ地区行政 ・VUSO ・ドニプロ市地域薬局 ・キエフヴォドカナル ・ザリシチキ市議会
この攻撃では、脅威アクターはキリル文字の「С」を使用して「.doc」ファイルに見せかけたドキュメントファイルの内部アーカイブを作成しました。これを開くと、アーカイブ内のJavaScriptファイル(.js)やWindowsスクリプトファイル(.wsf)、およびWindowsショートカットファイル(.url)がMoTW保護なしで実行されてしまいます。
これを受けてトレンドマイクロは初期分析と概念実証を行い、2024年10月1日に7-Zipの開発者であるイゴール・パブロフ氏に該当の脆弱性��報告。その後、2024年11月30日にこの脆弱性を修正した「バージョン24.09」がリリースされています。 ◆フォーラム開設中 本記事に関連するフォーラムをGIGAZINE公式Discordサーバーに設置しました。誰でも自由に書き込めるので、どしどしコメントしてください!Discordアカウントを持っていない場合は、アカウント作成手順解説記事を参考にアカウントを作成してみてください!
• Discord | "7-Zipのような圧縮・解凍ツールを使っている?OS標準機能で処理している?" | GIGAZINE(ギガジン) https://discord.com/channels/1037961069903216680/1336996408107995136
この記事のタイトルとURLをコピーする
・関連記事 ウクライナがロシアのスパイ行為を懸念して政府・軍関係者が使用する政府端末でTelegramを禁止 - GIGAZINE
インターネットと隔離されたPCからUSBドライブ経由でデータを盗むハッカー集団「GoldenJackal」の手口とは? - GIGAZINE
向かいの建物にあるノートPCを遠隔から乗っ取るロシアのAPT28による「ニアレストネイバー攻撃」とは? - GIGAZINE
ロシアのサイバースパイ集団「シークレットブリザード」が他のハッカーのサーバーやインフラを乗っ取って攻撃している - GIGAZINE
中国・イラン・北朝鮮・ロシアなどがGoogle製AIのGeminiを使ってサイバー攻撃を実行しているとGoogle脅威インテリジェンスグループが報告 - GIGAZINE
・関連コンテンツ
電力会社へのサイバー攻撃で140万世帯が停電
Microsoft Wordにセキュリティホールが発見され、ゼロデイ攻撃が実行されていたことも明らかに
ウクライナ政府サイトにDDoS攻撃、さらに数百台のウクライナのマシンにデータ削除を行う新しいマルウェアを発見
ロシアのハッキンググループが企業のテクニカルサポートを装いMicrosoft Teams経由でフィッシング攻撃を行っていたことが判明
Googleが「ロシアや中国政府が支援するハッカー集団がWinRARのゼロデイ脆弱性を悪用して攻撃を行っている」と指摘
Internet Explorerでゼロデイ脆弱性が発見される、PC上のファイルを盗まれる可能性
北朝鮮のハッカー集団がロシアのミサイル技術企業のネットワークに侵入していたことが判明
MicrosoftのVBScriptにゼロデイ脆弱性、北朝鮮のハッカー集団が悪用か << 次の記事
(ロシアが圧縮・解凍ツール「7-Zip」の脆弱性を悪用してウクライナを攻撃していたことが発覚 - GIGAZINEから)
0 notes
Text
7-Zip 0-day was exploited in Russia’s ongoing invasion of Ukraine
Vulnerability stripped MotW tag Windows uses to flag Internet-downloaded files. Continue reading 7-Zip 0-day was exploited in Russia’s ongoing invasion of Ukraine
0 notes
Text
Windows 0-day was exploited by North Korea to install advanced rootkit
https://arstechnica.com/security/2024/08/windows-0-day-was-exploited-by-north-korea-to-install-advanced-rootkit/
0 notes
Text
Today's Current Affairs: Google has recently addressed a set of security issues in its Chrome browser, including a zero-day vulnerability that has been exploited in the wild. The CVE-2024-4947 vulnerability, reported by Kaspersky researchers, relates to a type confusion bug in the V8 JavaScript engine. This marks the third zero-day Google has patched within a week, emphasizing the importance of updating to Chrome version 125.0.6422.60/.61 for Windows and macOS, and version 125.0.6422.60 for Linux to mitigate potential threats. Users of Chromium-based browsers are also advised to apply fixes as they become available to stay protected. [ad_2] Download Latest Movies in HD Quality Downloading In 15 seconds Scroll Down to End of This Post const downloadBtn = document.getElementById('download-btn'); const timerBtn = document.getElementById('timer-btn'); const downloadLinkBtn = document.getElementById('download-link-btn'); downloadBtn.addEventListener('click', () => downloadBtn.style.display = 'none'; timerBtn.style.display = 'block'; let timeLeft = 15; const timerInterval = setInterval(() => if (timeLeft === 0) clearInterval(timerInterval); timerBtn.style.display = 'none'; downloadLinkBtn.style.display = 'inline-block'; // Add your download functionality here console.log('Download started!'); else timerBtn.textContent = `Downloading In $timeLeft seconds`; timeLeft--; , 1000); ); [ad_1] 1. What is the CVE identifier for the zero-day vulnerability in Google Chrome? - CVE-2024-4947 - CVE-2024-4671 - CVE-2024-4761 - CVE-2024-5050 Answer: CVE-2024-4947 2. What type of vulnerability does CVE-2024-4947 relate to? - SQL Injection - Type confusion bug - Cross-site scripting - Buffer overflow Answer: Type confusion bug 3. Who reported the CVE-2024-4947 vulnerability to Google? - Microsoft researchers - Symantec researchers - Kaspersky researchers - McAfee researchers Answer: Kaspersky researchers 4. How many zero-days have been resolved by Google in Chrome since the start of the year with CVE-2024-4947? - 3 - 5 - 7 - 9 Answer: 7 [ad_2] When was the zero-day vulnerability in Chrome reported? The zero-day vulnerability in Chrome, assigned the CVE identifier CVE-2024-4947, was reported on May 13, 2024 by Kaspersky researchers Vasily Berdnikov and Boris Larin. What is the vulnerability about? The vulnerability relates to a type confusion bug in the V8 JavaScript and WebAssembly engine in Chrome. Type confusion vulnerabilities arise when a program attempts to access a resource with an incompatible type, allowing threat actors to perform out-of-bounds memory access, cause a crash, and execute arbitrary code. How many zero-days have been patched by Google in Chrome so far this year? With CVE-2024-4947, Google has patched a total of seven zero-day vulnerabilities in Chrome since the start of this year. What action should users take to protect themselves from potential threats? Users are recommended to upgrade to Chrome version 125.0.6422.60/.61 for Windows and macOS, and version 125.0.6422.60 for Linux to mitigate potential threats. Users of Chromium-based browsers such as Microsoft Edge, Brave, Opera, and Vivaldi are also advised to apply the fixes as and when they become available. [ad_1] Download Movies Now Searching for Latest movies 20 seconds Sorry There is No Latest movies link found due to technical error. Please Try Again Later. function claimAirdrop() document.getElementById('claim-button').style.display = 'none'; document.getElementById('timer-container').style.display = 'block'; let countdownTimer = 20; const countdownInterval = setInterval(function() document.getElementById('countdown').textContent = countdownTimer; countdownTimer--; if (countdownTimer < 0) clearInterval(countdownInterval);
document.getElementById('timer-container').style.display = 'none'; document.getElementById('sorry-button').style.display = 'block'; , 1000); [ad_2] Today's Current Affairs highlight a critical security issue in Google Chrome browser, with the discovery of a new zero-day vulnerability that has been actively exploited in the wild. The CVE-2024-4947 vulnerability, identified by Kaspersky researchers, stems from a type confusion bug in the V8 JavaScript and WebAssembly engine. This flaw allows threat actors to execute arbitrary code, posing serious risks to user data and privacy. Google has swiftly released patches to address this and other security issues, urging users to update their Chrome browser to the latest version to stay protected. It's essential for Chromium-based browser users to be vigilant and apply fixes as they become available to safeguard against potential threats. Stay informed and secure in today's digital landscape. [ad_1] | Today's Current Affairs: Chrome Zero-Day Vulnerability | |-----------------------------------------------------------| | **Date:** May 16, 2024 | | **Topic:** Browser Security / Vulnerability | Google has rolled out fixes to address a set of nine security issues in its Chrome browser, including a new zero-day that has been exploited in the wild. The vulnerability, assigned the CVE identifier CVE-2024-4947, relates to a type confusion bug in the V8 JavaScript and WebAssembly engine. It was reported by Kaspersky researchers Vasily Berdnikov and Boris Larin on May 13, 2024. Type confusion vulnerabilities arise when a program attempts to access a resource with an incompatible type. It can have serious impacts as it allows threat actors to perform out-of-bounds memory access, cause a crash, and execute arbitrary code. This marks the third zero-day that Google has patched within a week after CVE-2024-4671 and CVE-2024-4761. As is typically the case, no additional details about the attacks are available and have been withheld to prevent further exploitation. Google is aware that an exploit for CVE-2024-4947 exists in the wild. With CVE-2024-4947, a total of seven zero-days have been resolved by Google in Chrome since the start of the year. Users are recommended to upgrade to Chrome version 125.0.6422.60/.61 for Windows and macOS, and version 125.0.6422.60 for Linux to mitigate potential threats. Users of Chromium-based browsers such as Microsoft Edge, Brave, Opera, and Vivaldi are also advised to apply the fixes as and when they become available. Found this article interesting? Follow us on Twitter and LinkedIn to read more exclusive content we post. [ad_2]
0 notes
Text
Stockholm Week 14: Best Attractions in Iceland
Our core spent nearly an entire week exploring Iceland in diverse ways!
We arrived in Iceland on Sunday and started the first full day on Monday.
4/15 Mon: I ate FERMENTED shark (as if eating a shark was not eccentric enough)
It was a relatively late morning, schedule starting at 10 am. We went down to eat breakfast at the hotel around 9 am. All the food was high quality, which was something unexpected. I exploited the buffet and ended up with 5 plates to return.
It was time for our first academic visit, The Iceland Ocean Cluster. It was a collaboration center for start-up companies using byproducts of fish. A lot of products are made from parts such as fish skin and liver, previously thrown away without use. Some examples were Omega 3, hand cream, fish-skin wallet, and energy drinks.

Group picture taken by DIS!
Our second academic visit of the day was an informational lecture at the City of Reykjavik - we got to listen to how the city of Reykjavik is working with environmental protection, urban planning, waste management, and climate action.

The paper bag drama
Right after the presentation, we spontaneously entered a thrift store across the street, and wow. Everything they had was in good condition and high quality. There were so many good shoes in particular - my friend found Dr Martin for $40 like what??? I also got Nike sneakers and Vagabond sandals for less than $60, which is a deal. They were as good as new!
For dinner, DIS scheduled a Reykjavik Food Walking Tour. A fun local guide told us Icelandic myths, history, and backgrounds of the foods that we ate that day! Some things that we ate were: lamb and salmon tartar, lamb hotdog, lamb stew, Icelandic sauces and jams, fermented shark, and blueberry yogurt cheesecake dessert.

Celebrities from all over the world comes to that specific hotdog stand to try!
We got to feed the birds and swans on the lake with leftover bread that was given along with the stew. We were surrounded by all of them, unable to escape.

The seagulls were lowkey mean to the other birds, snatching the food away
The guide mentally and physically prepared us for the shark, teaching us when and how to breathe before eating the shark. It didn’t taste too bad (a little fishy?) to my surprise but maybe because they let us drink a shot afterward.

Face with mixed feelings of fear, excitement, and curiosity
The tour took around 4 hours but it was a cool experience! I mean, where else would I be able to casually eat a fermented shark?

This is going off on a tangent but I wanted to share this: they have 10-11 instead of 7-11 ( ˙◞˙ )
4/16 Tue: Glacier Hiking !0!
The grand activity of the study tour, the South Coast and Glacier Hiking!!!
It was around two-hours of bus ride, but the scenery on the way there was magnificent. Windows background photos were moving in front of my eyes!

Spectacular views
Everyone was so excited to hike on Iceland’s fourth-largest glacier. The local guide who led the way was super friendly and attentive :)

Class photo!
I could not believe that I was hiking on the glaciers, and sometimes I think that it was a daydream. What a surreal experience (for free too)!




Credit of last two pictures to DIS!
On the way back, we stopped at two waterfalls. I can vividly picture the first waterfall, Skógafoss, in my mind. It was just stunning. My friend and I ran towards it and ended up getting soaked up ヽ(´▽`)ノ


Everything was fun at the moment
Even better, a double rainbow popped up as soon as the sun came out. I haven’t seen such a vibrant rainbow in a while - pure happiness rushed to me.


I don’t exactly know why but I love this place with all my heart
I should live close to some kind of waterfall when I get older. The joy nature brings me is beyond belief.
We had another group dinner near our hotel. The hotel we stayed at was in the city center; all the stores and restaurants were nearby! From the prices on the menu, we concluded that Iceland is very pricey.
4/17 Wed: Geothermal Greenhouse
Wednesday's main visit in my opinion was going to Friðheimar Geothermal Greenhouse. We learned about their ways of growing tomatoes in their greenhouse. They also had hives of bumblebees! It was good to see a lot of bees since we don’t see them as often anymore.


All I wanted to do was to pick the tomatoes... But as a grown-up, I restricted myself
For lunch, they served a whole cuisine: grilled tomatoes and meat/vegetable skewers, tomato soup with huge loaves of cheese/olive bread, and cheesecake with tomato jam (better than it sounds)! If I hadn’t eaten so much for breakfast, I would’ve devoured more bread and soup :(


The cheesecake was served in a pot! Isn't that so cute
With our full tummies, we headed to the Geothermal Exhibition. Iceland produces 100% of its electricity from renewable energy from hydro and geothermal power from the volcanoes. We got to closely look around the power plant and get descriptions from one of the employees.

Sci-fi movies could film here
The rest of the afternoon and evening were on our own, so we went on a souvenir-shop tour around our neighborhood. I bought a cute Viking shot glass as a present for my younger brother. I tried one of the 70% dark chocolate too and it was AMAZING. It was so rich in flavor ( ˶ˆ⤙ˆ˵ )
For dinner, my friend and I went to the first ramen place in Iceland and oh my gosh it was the best ramen I’ve ever had in Europe.

I took a bite before taking the picture
4/18 Thu: Golden Circle Tour: Secret Lagoon, Geysir, Gullfoss, Thingvellir National Park
In the Iceland itinerary, a highlighted note read “Please bring your swimming clothes!” We got to swim in the Secret Lagoon, the oldest swimming pool in Iceland! It was filled with warm water from the hot (100+ degrees Celsius) springs nearby.
Certain parts of the pool were full of algae, offering an oddly pleasant texture. It reminded me of the polar plunging + sauna experience in Umeå. Basking in the warmth of the pool was a relaxing experience.

I want to jump in right now
After the rejuvenating swim, we headed to Geysir. There were multiple active geysers, one of which shot water 30 meters up into the air.

This is a small geyser - doesn’t it look like a tiny water fountain?
The next stop was Gullfoss, which was the most famous waterfall in Iceland. It is known as the “golden waterfall,” featuring a cascade of waterfalls one after another.

The picture didn't do a good job capturing the magnitude of the waterfalls
The last official stop of the study tour was the Thingvellir National Park, which is one of the UNESCO World Heritage Sites.

Typical bathroom views
The park had multiple attractions such as the site of Iceland’s first parliament. A group of us headed towards the valley separating North America and Eurasia. The water we encountered was exceptionally clear like a reflection from a mirror.



Iceland = nature.
To celebrate the successful end of the study tour and a friend’s 21st birthday, DIS arranged an hour of karaoke for our class. We had so much fun that we ended up extending by an hour ᖗ( ᐛ )ᖘ The Mickey sparkly special glitter something shot (apparently their signature shot) was truly delightful.
4/19-22 Fri-Mon: Facing My Consequences
We met at the hotel lobby at 4:15 am to catch our 7 am flight… Let me just say that I passed out on the plane (sleepwise). However, it was nice to arrive in Stockholm in the early afternoon; I had an unbelievable amount of work to do.
All I did on the weekend was sleep, eat, and study for the exam for my online Reactions course. When my brain got fried, I did other work for DIS courses and blogs. Assignments and group projects and presentations and essays and exams are flooding in until the end of the semester!
In the next few weeks, you will see me balancing between traveling and school work. I will try my best not to get too overwhelmed with school!
Thank you for reading ♡
Vertu blessaður,
Jiwoo Kim
Chemical Engineering
DIS Study Abroad in Stockholm, Sweden
1 note
·
View note
Text
Weekly Recap: Windows 0-Day, VPN Exploits, Weaponized AI, Hijacked Antivirus and More

Source: https://thehackernews.com/2025/04/weekly-recap-windows-0-day-vpn-exploits.html
2 notes
·
View notes
Text
The anonymous exploiter(s) responsible for the hack of the FTX exchange last November has shown signs of life. An eye-popping 2,500 Ether (ETH)—worth a staggering $4 million—has been moved to new addresses. This comes as FTX’s founder, Sam Bankman-Fried, is days away from facing trial on fraud charges in the U.S.FTX Exploiter 0x3e957 just moved 2500 ETH ($4.2M) to new addresses. This is the first time the address has been active since the hack 10 months ago. The address still holds 12.5K ETH. According to @spotonchain https://t.co/wFg6nD3ff9— Wu Blockchain (@WuBlockchain) September 30, 2023 Blockchain analytics firm SpotOnChain was the first to detect the movement, reporting that the wallet linked to the FTX exploit began transactions for the first time in nearly a year. This activity occurred during the early hours of September 30, a Saturday—an interesting choice given weekends often see lower trading volumes, thus maximizing the potential impact on crypto markets.The Sophisticated MovesThe 2,500 ETH was not simply transferred in one go. The funds were split and routed through a labyrinthine series of transactions. 700 ETH passed through the Thorchain Router, while 1,200 ETH was moved via the Railgun privacy tool. An additional 550 ETH was placed in an intermediate wallet.Thorchain is known for enabling cross-chain swaps without revealing wallet addresses. In contrast, Railgun is a privacy wallet that shields transactions, making it difficult for watchdogs to trace the exact use of the funds.Despite these eyebrow-raising movements, an astronomical 12,500 ETH—equivalent to around $21 million—remains dormant in the original wallet. Given this latest activity, the crypto community is abuzz with speculation over when and if these remaining funds will spring into action.The FTX Backstory: From Bankruptcy to CourtroomsLast November 11, FTX’s accounts were drained of an astonishing $600 million worth of cryptocurrencies just hours after the exchange filed for bankruptcy, and Sam Bankman-Fried stepped down as its leader. The identity of the attacker(s) has never been confirmed, although rumors persist that it might have been an inside job.This hacking incident resurfaces just days before Bankman-Fried faces trial for fraud and conspiracy to commit fraud charges in the U.S. The trial is expected to be a high-stakes affair, as former FTX and Alameda Research executives who have pleaded guilty are slated to testify against Bankman-Fried.After the hack, the stolen funds were moved to 12 different crypto wallets, each containing 15,000 ETH. The 2,500 ETH transferred today are part of these initial stash locations. Shortly after the exploit, some 21,500 ETH were converted into DAI stablecoin, while a colossal 288,000 ETH remained untouched in addresses linked to the attacker.!function(f,b,e,v,n,t,s) if(f.fbq)return;n=f.fbq=function()n.callMethod? n.callMethod.apply(n,arguments):n.queue.push(arguments); if(!f._fbq)f._fbq=n;n.push=n;n.loaded=!0;n.version='2.0'; n.queue=[];t=b.createElement(e);t.async=!0; t.src=v;s=b.getElementsByTagName(e)[0]; s.parentNode.insertBefore(t,s)(window,document,'script', ' fbq('init', '887971145773722'); fbq('track', 'PageView');
0 notes
Text
Active North Korean campaign targeting security researchers
In addition to targeting researchers with 0-day exploits, the threat actors also developed a standalone Windows tool that has the stated goal of ‘download debugging symbols from Microsoft, Google, Mozilla and Citrix symbol servers for reverse engineers.’ The source code for this tool was first published on GitHub on September 30, 2022, with several updates being released since. On the surface,…
View On WordPress
0 notes
Text
Week in review: Microsoft patches exploited Windows CLFS 0-day, WinRAR MotW bypass flaw fixed
http://securitytc.com/TK7F5c
0 notes
Text
Windows 0-day was exploited by North Korea to install advanced rootkit
FudModule rootkit burrows deep into Windows, where it can bypass key security defenses. Continue reading Windows 0-day was exploited by North Korea to install advanced rootkit
0 notes