#Windows Defender Firewall with Advanced Security
Explore tagged Tumblr posts
Text
10 Steps to Securely Configuring Windows 10
Windows 10 is the most popular operating system in the world, but it also comes with some security risks. If you want to protect your data and privacy, you need to configure Windows 10 for security. Here are 10 steps you can follow to make your Windows 10 more secure. Update Windows 10 regularly – Windows 10 updates often include security patches and bug fixes that can prevent hackers from…

View On WordPress
#2FA#Backup#BitLocker#Cybersecurity#MFA#Virtual Private Network#VPN#Windows 10#Windows Defender#Windows Defender Firewall with Advanced Security
0 notes
Text
Perhaps the most effective tip that worked for me is blocking your TS4 executable file in Windows Firewall or whatever your firewall app is.
As someone who experienced lag despite having a GPU (an AMD Radeon RX 6700 XT) that is capable of even more advanced games, I still sometimes had lag even in a vanilla game and Reshade off until I did this.
Now, even with Ultra settings, over 50GB of CC, Reshade with MXAO on constantly, and even Graphics Rules tweaks that increase quality, I get almost zero lag in even medium-to-large lots. For larger lots, there's a bit of FPS drop, but it's still playable. If you have a less powerful GPU, the results will be more modest, but it should still be an improvement
You may need to turn this rule off if you want to access the gallery depending on your other firewall settings, but in my experience, the Gallery and SDX drops still work after this rule.
My hunch is that a big cause of lag spikes is EA (to the surprise of no one) "phoning home" constantly, and with a game like TS4 that doesn't need to be online constantly, we can do away with this.
How do you do this? This is super simple.
1. Go to your Windows start menu and type "Windows Defender Firewall with Advanced Security".
2. Once you are in the application, click on New Rule.
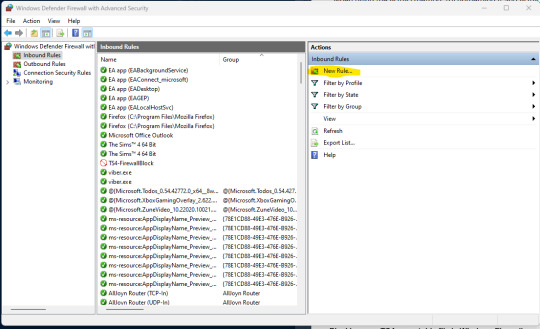
3. Click on Program once the wizard asks you to select a rule type, then click Next.
4. Navigate to your executable folder using the Browse button, then click Next. Depending on where you install it, this would be different.

5. Make sure to select the Block the connection option, then click Next.

6. Leave the settings for the Profile as the defaults, then click Next.
7. Type some kind of descriptive name, then click Finish.

Enter your game again, then profit.
Keeping Lag to a Minimum...
I was chatting about a few things I do to combat lag over on discord and realised I do quite a bit of maintenance to reduce lag/load times. I decided to write em all down and before I knew it, I had a big ol' list. Here's hoping it helps!

Save/File Tips:
Clear your caches (located in the same spot as your mod folder fyi) I usually delete the onlinethumbnailcache, avatarcache and localthumbcache caches every time I exit the game, the main one to delete regularly is the localthumbcache file, they're just temporary files but it can get pretty big after a while.. if you're having any mod issues, particularly ui ones, it's always worth deleting that to see if it helps.
Remove any saves you're not using from your saves folder, and keep an eye on save file sizes. In my experience, any saves over around 30-40mb start to get a bit laggy. Things that bump this size up are the amount of townies in game and the amount of lots/objects in the world.
Regarding the above point, I regularly bulldoze lots I don't need anymore, just to save the game from having to cope with extra shit to load in the background and reduce save file bloat.
Similarly, I delete a lot of unnecessary townies. Also, try to keep the amount of outfits on townies to a minimum, ain't no townie need four swimsuit outfits, the game will thank you..
If you have cheats enabled you can usually shift-click/delete object on things like random coffee cups or stray cupcakes sims foolishly drop around the world (or eat em.. whatever tickles ur pickle) just get rid!
Whilst we're keeping objects in game to a minimum.. I try to clear sims inventories now and then, including townies. You can do this via mccc even if you're not currently playing that household by heading to MC Cleaner -> Sell Sim Inventory/Sell Household Inventory. RANDOM LUMPS OF CLAY BEGONE!
Think of a save file like a lot.. the more objects in it, the laggier it gets! Try your best to remove anything or anyone unnecessary where you can.
Hit "Save As" instead of "Save" now and then - the more you overwrite a save, the more chance it has of going wonky, treat your game to a fresh one now and then and remove the old one from your saves folder (maybe don't delete it right away in case you wanna roll back, keep it somewhere safe).
If you can (although ik it can be a pain) set up a new/fresh save, you'd be surprised how bogged down old ones can get! For legacy players, it's usually best to do this whenever you have a small family to save yourself some pain, since you can just save the household and take em to a new save (you will lose sims inventories/household inventories/relationships with sims outside the household tho so beware! Pictures/other collectables can be saved to a lot however, and you can always cheat back relationship bits etc.. bit of a last resort but new saves are shiny and fast!)
Make sure your Screenshots/Video folders are empty - move em somewhere else, it works, trust me. If you have a lot of custom music installed try n' clear some of those out too.. the smaller that Sims 4 directory is, the better.
Delete any last exceptions/last crashes (same spot as your mod folder again) you don't need em unless you're planning to upload em somewhere for help.
Settings Etc:
If you get a bad lag spike, opening the main menu and/or saving can randomly stop this. If it doesn't, try exiting the game, clearing your localthumbcache and restarting.
Clearing all notifications from the game panel can also help.
If you can, close all other apps and background apps you don't need whilst playing, ts4 is super memory hungry so it can definitely help.
The GraphicsRules Override file by Simp4Sims can reduce lag/latency and make your game look a little better in the process!
Srslysims Simulation Lag Fix mod can help reduce lag too (if you've altered the game speed via mccc tho, don't use this unless you plan on resetting it to default).
If you aren't keen on, or barely use a pack, consider disabling it.
Not ideal, especially for those of us taking screenshots, but lowering the graphics settings whilst playing definitely helps.
If you use re/g-shade, consider switching it off whilst playing and only turn it on for screenshots.
A clean and tidy pc/laptop runs better in general. Remove anything you're not using/don't need anymore to free up space, remove temp files, clean up your folders now and again etc etc.. especially that dreaded mod folder, speaking of...
Managing Mods:
SORT OUT YOUR MODS FOLDER FOR THE LOVE OF GOD.. skdsjdjs it doesn't have to be immaculate but at the very least try n' clear it out now n' then. Also try to separate your script mods/overrides from the rest, patch days don't need to be so stressful ;-;
Personally, I don't merge my mods; if something breaks it's much harder to pinpoint! It makes it easier to find/delete specific mods too.. and let's face it, there's usually one or two items in that set you could do without lmaooo.. also, don't think it helps much tbh! Yeah you could say the game doesn't have to work as hard to load merged files but that's debatable, it's still the same amount of items/polys at the end of the day ¯\(°_o)/¯
If you like merging files and/or see results from doing so, you can merge stuff you definitely know you're never getting rid of, especially CAS/BB stuff.. but steer clear of merging gameplay/script mods! If a merged file seems to be the culprit when using the 50/50 method, try unmerging it and 50/50ing it again! You might not need to get rid of everything if something's borked.
Bulk Rename Utility can be used to remove all spaces and special characters from your mod files, the game doesn't particularly like loading those so it'll thank you.
The Sims 4 Mod Manager is a great way to sort through your mods, you can easily see, move and delete files from here (not great for build/buy, poses etc as thumbnails are usually missing, but great for CAS stuff). An extra hint with this that I've noticed is that if any of my mods get renamed with [D1] at the beginning after looking through them via the mod manager, it means it's a duplicate file so you can get rid.
I also use the Sims 4 Tray Importer to help me sort through mods. Simply save a sim/lot with any cc you don't want and find it in the importer, you can then go through all the cc in the cc tab and delete/sort it (I also use this to sort cc if a bunch has the wrong tags etc, makes it easier to find in my folders by saving em to a lot or w/e - it also spots duplicates which is handy).
It's a ballache, but the 50/50 method is tried and tested if you're having issues.
I like to keep an abandoned cc folder tucked away somewhere, that way you can remove mods willy nilly without stressing about losing them. If you change your mind, you can always grab it back!
3K notes
·
View notes
Photo

AMD Ryzen 5 6-Core 3.7GHz 4600G AM4 Vega7 8GB 500GB SSD Strategize and reach your targets easily with the PCBuilder AMD Ryzen 5 4600G Home Master Windows 11 Desktop PC. This pre-built desktop PC is designed for use at home or in the office and is powered by an AMD Ryzen 5 4600g CPU with Radeon built-in graphics. It also comes with an A520 chipset motherboard, 8GB of high-speed DDR4 memory, and a 2.5″ SATA SSD. Built with efficiency in mind so you can reach your deadlines on time, this pre-built PC has everything you need to hit those daily targets. With Microsoft Windows 11 already installed, you can also run the latest versions of all your apps with more features and better security. Its Radeon built-in graphics are also a great option for presentations and video content or editing. The Home Master features a Ryzen 4000 G-Series CPU and DDR4 memory, which will ensure that every task gets completed quickly and efficiently. With 6 cores and 8GB of DDR4 memory, no task is too much for it to handle. Data can be transferred, and applications can be loaded at lightning-quick speeds thanks to the included 2.5″ SATA SSD. This makes using apps like Microsoft Word and Excel run even more smoothly, so you can get more work done. All the components are held together with a high-performance AM4 Motherboard with Lightning Gen 3 support. The motherboard delivers an efficient and productive experience with stable functionality and maximum performance. Everything is protected and held together inside a sleek-looking Micro-ATX Chassis. This modern-looking compact chassis is easy to maintain and upgrade, while its smaller form factor is great for saving some space in the home or office. The Home Master comes installed with Windows 11 which has easy-to-use tools that can help you optimize your screen space and maximize your productivity. It features great tools like Microsoft Edge, the new and improved Microsoft Store, Snap Layouts to arrange your open windows into grids, Desktops for better organization, as well as Widgets. Windows Security also offers advanced protections to defend against today’s ever-changing cyber threats. This includes device encryption, find my device, firewall and network protection, internet protection, parental controls, secure boot, and Windows Hello among other features. Norton Security Software is designed to protect your connected device as well as your personal information and offers more powerful layers of protection from ever-changing threats. It can protect your PC or Mac from viruses, ransomware, malware, and other online threats while you bank, shop and browse the internet. It ensures that your personal device is protected from unauthorized access to your personal files and the financial information it stores with the Smart Firewall. FEATURES: Keep your components protected in the sleek-looking PCBuilder Bunker M-ATX Chassis Six-Core AMD Ryzen 5 4600G CPU with a boost clock of up to 4.2GHz Radeon built-in graphics designed for videos and presentations High-quality and reliable performance with DDR4 Desktop Memory Get lightning-fast storage with a 2.5″ SATA SSD Durable and versatile AM4 Micro-ATX Motherboard Microsoft Windows 11 Operating System SPECIFICATIONS: Operating System: Microsoft Windows 11 Home Software: Norton Security Software AMD Ryzen 5 4600G 6-Core 3.7GHz AM4 CPU Cores: 6 Cores Base Clock Speed: 3.7GHz Boost Clock Speed: 4.2GHz GPU Cores: 7 Socket: AM4 A520 Chipset AM4 Micro-ATX Motherboard Socket: AM4 Form Factor: Micro-ATX 8GB DDR4 3200MHz Desktop Memory Memory Capacity: 8GB Data Transfer Rate: 3200MHz Generation: DDR4 500GB 2.5″ SATA SSD Capacity: 500GB 300W ATX Non-Modular Power Supply Rated Output Power: 300W Cooling: 120mm Silent Fan PCBuilder Bunker M-ATX Chassis Type: Micro-ATX Mid Tower Side Panel: Steel Expansion Slots: 4 Dimension: 38 x 21 x 38 cm WHAT’S IN THE BOX: PCBuilder AMD Ryzen 5 4600G HOME MASTER Windows 11 Desktop PC x1 1.8m Power Cable x1 Please note that the images displayed are for illustrative purposes only. Components will be supplied as per the technical specifications in this listing. 3DMark FPS & Time Spy benchmark scores are estimates only.
#COMPUTERS#DESKTOPS#GAMING_DESKTOPS#3.7_GHZ#4600G#500GB_SSD#6_CORE#8GB_DDR4_RAM#AMD#PREBUILT#RYZEN_5#WINDOWS_11_HOME
0 notes
Text
Maximize Business Performance with a Dedicated Server with Windows – Delivered by CloudMinister Technologies
In the era of digital transformation, having full control over your hosting environment is no longer optional—it’s essential. Businesses that prioritize security, speed, and customization are turning to Dedicated servers with Windows as their go-to infrastructure solution. When you choose CloudMinister Technologies, you get more than just a server—you get a strategic partner dedicated to your growth and uptime.
What is a Dedicated Server with Windows?
A Dedicated server with Windows is a physical server exclusively assigned to your organization, running on the Windows Server operating system. Unlike shared hosting or VPS, all the resources—CPU, RAM, disk space, and bandwidth—are reserved solely for your use. This ensures maximum performance, enhanced security, and total administrative control.
Key Benefits of a Dedicated Server with Windows
1. Total Resource Control
All server resources are 100% yours. No sharing, no interference—just consistent, high-speed performance tailored to your workload.
2. Full Administrative Access
You get full root/administrator access, giving you the freedom to install applications, manage databases, configure settings, and automate processes.
3. Better Compatibility with Microsoft Ecosystem
Run all Microsoft applications—SQL Server, Exchange, SharePoint, IIS, and ASP.NET—without compatibility issues.
4. Advanced Security Options
Use built-in Windows security features like BitLocker encryption, Windows Defender, and group policy enforcement to keep your data safe.
5. Remote Desktop Capability
Access your server from anywhere using Remote Desktop Protocol (RDP)—ideal for managing operations on the go.
6. Seamless Software Licensing
With CloudMinister Technologies, Windows licensing is bundled with your plan, ensuring legal compliance and cost savings.
7. Scalability Without Downtime
Need to upgrade? Add more RAM, switch to SSDs, or increase bandwidth—without migrating to another server or experiencing downtime.
Why Choose CloudMinister Technologies for Windows Dedicated Servers?
At CloudMinister Technologies, we combine performance with personalized service. Our infrastructure is engineered to support the demands of startups, growing businesses, and large enterprises a like.
Our Competitive Edge:
100% Custom Configurations Choose your ideal specs or consult with our engineers to build a server optimized for your application or business model.
Free Server Management We manage your OS, patches, updates, firewalls, backups, and security—so you can focus on your business, not your backend.
High Uptime Guarantee With our 99.99% uptime commitment and redundant systems, your server stays online—always.
Modern Data Centers All servers are housed in Tier III or higher data centers with 24/7 surveillance, redundant power, cooling, and robust firewalls.
Rapid Deployment Get your Dedicated server with Windows up and running quickly with pre-configured setups or same-day custom deployment.
Dedicated 24/7 Support Our expert team is available any time, day or night, to troubleshoot, consult, or provide emergency support.
Additional Features to Boost Your Operations
Automated Daily Backups Protect your data and ensure business continuity with secure, regular backups.
DDoS Protection Stay secure with advanced protection from distributed denial-of-service attacks.
Multiple OS Choices Prefer Windows 2016, 2019, or 2022? Choose what suits your stack best.
Control Panel Options Get support for cPanel, Plesk, or a custom dashboard for simplified server management.
Private VLAN and IPMI Access Enjoy better isolation and direct console access for advanced troubleshooting.
Call to Action: Start with CloudMinister Technologies Today
Your business deserves more than just a server—it deserves a partner who understands performance, uptime, and scalability. With a Dedicated server with Windows from CloudMinister Technologies, you're guaranteed a seamless hosting experience backed by unmatched support and reliability.
Don’t wait for slow speeds or security issues to hold you back.
Upgrade to a Dedicated Windows Server today.
Visit www.cloudminister.com to view plans Or contact our solutions team at [email protected] to discuss your custom setup.
0 notes
Text
Google Chrome માટે ઈન્ટરનેટ કેવી રીતે બ્લોક કરવું?
https://youtu.be/F_C8rQ1qG4w 🌐 Google Chrome માટે ઈન્ટરનેટ કેવી રીતે બ્લોક કરવું? જો તમે Google Chrome પર ઇન્ટરનેટ એક્સેસ બંધ કરવા માંગતા હો, તો તમે તે ખૂબ સરળતાથી કરી શકો છો. 📴 આ પ્રક્રિયા ખાસ કરીને બાળકો માટે પેરેન્ટલ કંટ્રોલ માટે અથવા વિશિષ્ટ વેબસાઇટ્સ બ્લોક કરવા માટે ઉપયોગી છે. 😎 🟢 Windows Firewall દ્વારા Chrome માટે ઈન્ટરનેટ બ્લોક કરવું સ્ટેપ 1: Start Menu માં Control Panel ઓપન કરો. સ્ટેપ 2: System and Security પર ક્લિક કરો. સ્ટેપ 3: Windows Defender Firewall સિલેક્ટ કરો. સ્ટેપ 4: ડાબી બાજુ Advanced Settings પર ક્લિક કરો. 🔥 Inbound/Outbound Rule બનાવવી સ્ટેપ 5: Outbound Rules પર જાઓ અને New Rule પર ક્લિક કરો. સ્ટેપ 6: Program સિલેક્ટ કરો અને Next કરો. સ્ટેપ 7: This Program Path પસંદ કરો અને નીચેનો પાથ નાખો: "C:Program FilesGoogleChromeApplicationchrome.exe" સ્ટેપ 8: Block the Connection પસંદ કરો અને Next કરો. સ્ટેપ 9: તમને Domain, Private, Public પ્રોફાઇલ્સ દેખાશે – બધા સિલેક્ટ કરો અને Next કરો. સ્ટેપ 10: Rule નું નામ Block Chrome રાખો અને Finish કરો. ✅ Done! હવે Google Chrome પર ઇન્ટરનેટ એક્સેસ બંધ થઈ ગયું છે. 🚫 સપષ્ટ કરો કે Chrome માટે બ્લોકિંગ ચાલુ છે કે નહીં સ્ટેપ 1: Command Prompt (CMD) ઓપન કરો. સ્ટેપ 2: આ કમાન્ડ ટાઇપ કરો: netsh advfirewall show allprofiles સ્ટેપ 3: ચેક કરો કે Firewall Rules સફળતાપૂર્વક લાગુ થઈ છે કે નહીં. ⚡️ વિશિષ્ટ વેબસાઇટ બ્લોક કરવા માટે Hosts File નો ઉપયોગ સ્ટેપ 1: C:WindowsSystem32driversetchosts ફાઇલ ઓપન કરો. સ્ટેપ 2: ફાઇલના અંતમાં આ લાઈન ઉમેરો: 127.0.0.1 www.facebook.com 127.0.0.1 www.youtube.com સ્ટેપ 3: Save કરો અને Chrome રીષ્ટાર્ટ કરો. ✅ Done! હવે આ વેબસાઇટ્સ Chrome પર ઓપન નહીં થાય. ❗️ ટ્રબલશૂટિંગ ટિપ્સ: - Firewall Rule ચાલુ છે કે નહીં એ ચેક કરો. - Chrome Path યોગ્ય છે તેની ખાતરી કરો. - Hosts File Save કરતા પહેલા Administrator Privileges ચેક કરો. 🎥 ટેક્નોલોજી શીખવી હવે થઈ ગઇ વધુ સરળ! જો તમને આ માહિતી ઉપયોગી લાગી હોય, તો અમારા YouTube ચેનલને સબ્સ્ક્રાઇબ કરો અને વધુ પેરેન્ટલ કંટ્રોલ ��ને સિક્યોરિટી ટિપ્સ શીખતા રહો! 🔔😊 👉🏼 સબ્સ્ક્રાઇબ કરો અને તમારું ડેટા સુરક્ષિત રાખો! આભાર! 🙌🏼 Read the full article
1 note
·
View note
Text
buy windows 7 Free - buy windows 7 all licence
Introduction
In the digital age, having a reliable operating system is crucial for individuals and businesses alike. Windows 7, released by Microsoft, continues to be a popular choice among users for its user-friendly interface and robust features.
Compatibility and Performance
One of the key advantages of buying Windows 7 is its compatibility with a wide range of hardware and software. Whether you are a casual user or a professional, Windows 7 offers smooth performance and seamless integration with various applications.
Security Features
Windows 7 boasts advanced security features to protect your personal information and data. With built-in firewall and Windows Defender, users can feel confident that their devices are secure from malware and other online threats.
Regular Updates and Support
By purchasing Windows 7, users can benefit from regular updates and support from Microsoft. This ensures that your operating system remains up-to-date and protected against new vulnerabilities.
Legality and Reliability
Buying Windows 7 from authorized sources guarantees its legality and reliability. Avoid the risks associated with free download or nulled versions, which may contain malicious software or lack essential features.
Conclusion
In conclusion, purchasing Windows 7 offers users a range of benefits including compatibility, security, updates, and peace of mind. Invest in a legitimate copy of Windows 7 to ensure a smooth and secure computing experience.
https://allcdkey.tumblr.com
0 notes
Text
Supporting and Troubleshooting Windows 11 Course in Australia: A Complete Guide
Windows 11 has become the operating system of choice for businesses and individuals, offering advanced security, enhanced performance, and a modern interface. However, managing and troubleshooting Windows 11 in a professional environment requires specialized skills. The Supporting and Troubleshooting Windows 11 Course in Australia is designed to equip IT professionals with the knowledge and hands-on experience needed to support and resolve issues in Windows 11 systems efficiently.
Why Enroll in a Supporting and Troubleshooting Windows 11 Course?
With the transition from older Windows versions to Windows 11, IT support teams must adapt to new technologies, security features, and system configurations. Here’s why taking this course is beneficial:
1. Stay Updated with Windows 11 Technology
Learn about the latest Windows 11 features and enhancements.
Understand changes in system architecture and security protocols.
Gain insights into compatibility issues and best practices for troubleshooting.
2. Enhance Your IT Support Skills
Develop expertise in diagnosing and resolving Windows 11 issues.
Master tools like Windows Recovery, Event Viewer, and Command Prompt.
Improve efficiency in handling system crashes, performance issues, and network problems.
3. Increase Job Opportunities and Career Growth
IT professionals with Windows 11 troubleshooting skills are in high demand.
Employers prefer certified experts for desktop support, system administration, and IT helpdesk roles.
The course prepares you for industry-recognized certifications that boost your resume.
Key Topics Covered in the Course
The Supporting and Troubleshooting Windows 11 Course is comprehensive and designed for IT professionals, covering the following crucial areas:
1. Windows 11 Installation and Configuration
Setting up and customizing Windows 11.
Managing user accounts and permissions.
Understanding Windows Update and Feature Management.
2. Troubleshooting Boot and Startup Issues
Identifying and resolving boot failures and startup delays.
Using Advanced Startup Options and Safe Mode.
Repairing the Windows bootloader and system files.
3. Performance Optimization and System Monitoring
Using Task Manager, Resource Monitor, and Performance Monitor.
Troubleshooting slow performance and high CPU/RAM usage.
Managing background applications and startup processes.
4. Network Connectivity and Troubleshooting
Configuring and troubleshooting Wi-Fi, VPN, and Ethernet connections.
Understanding TCP/IP, DNS, and Firewall settings.
Resolving common connectivity issues and IP conflicts.
5. Security and Access Management
Implementing BitLocker encryption and Windows Defender policies.
Managing user authentication and account recovery.
Preventing and troubleshooting malware and ransomware attacks.
6. Hardware and Peripheral Troubleshooting
Diagnosing driver and compatibility issues.
Troubleshooting printer, scanner, and peripheral device failures.
Using Device Manager and Windows Troubleshooters.
7. Data Recovery and Backup Solutions
Configuring OneDrive and local backup solutions.
Recovering lost data using Windows File History and Recovery Tools.
Preventing data loss through effective backup strategies.
Who Should Take This Course?
The Supporting and Troubleshooting Windows 11 Course is ideal for:
IT Support Specialists – Handling user support and troubleshooting requests.
System Administrators – Managing enterprise Windows 11 environments.
Helpdesk Technicians – Assisting with hardware, software, and network issues.
Technical Consultants – Offering Windows 11 support for business clients.
Benefits of Certification in Windows 11 Troubleshooting
Earning a certification after completing this course offers several advantages:
Better Job Prospects: Companies prefer certified IT professionals.
Higher Salary Potential: Skilled troubleshooting experts earn more.
Enhanced Problem-Solving Skills: Learn real-world troubleshooting techniques.
Industry Recognition: Gain credibility as a Windows 11 support specialist.
Choosing the Right Training Provider in Australia
When selecting a training provider for the Supporting and Troubleshooting Windows 11 Course in Australia, consider these factors:
Accreditation: Ensure the provider is recognized by Microsoft.
Hands-on Labs: Look for courses offering real-world troubleshooting scenarios.
Flexible Learning Options: Online, classroom, or hybrid training formats.
Certification Preparation: Providers offering exam support and practice tests.
Student Reviews: Check ratings and testimonials for course quality.
Final Thoughts
The Supporting and Troubleshooting Windows 11 Course in Australia is an essential step for IT professionals looking to expand their expertise in Windows 11 support. With a structured curriculum covering installation, performance tuning, security, and network troubleshooting, this course provides the necessary skills to manage and resolve issues efficiently.
0 notes
Text
Mastering Windows Server 2019 Administration: A Guide for IT Professionals
Windows Server 2019, Microsoft’s robust and versatile server operating system, has become a cornerstone for organizations across various industries. Released as an evolution of the popular Windows Server 2016, it brings a suite of powerful features aimed at improving security, efficiency, and ease of management. Effective Windows Server 2019 administration involves understanding its capabilities, configuring its key settings, and leveraging its tools to meet organizational needs. This article explores the essentials of Windows Server 2019 administration, covering crucial components, best practices, and tips to help administrators make the most of this powerful system.
Key Features of Windows Server 2019
Windows Server 2019 builds upon its predecessors with several new features designed to optimize performance and security in modern data centers. Here are a few highlights that make it a standout choice for administrators:
Hybrid Cloud Support: With Azure integration, Windows Server 2019 offers seamless hybrid capabilities that allow administrators to connect on-premises servers with cloud services. This provides flexibility in managing workloads and extends the reach of IT infrastructure beyond physical boundaries.
Enhanced Security: Security remains a core focus of Windows Server 2019, with advanced features like Shielded Virtual Machines, Windows Defender ATP, and enhanced threat detection through Windows Defender Exploit Guard. These tools help protect against modern cybersecurity threats while reducing system vulnerabilities.
Improved Hyper-Converged Infrastructure (HCI): The HCI improvements in Windows Server 2019 enable administrators to manage storage, networking, and compute resources within a unified infrastructure, simplifying the management of virtualized environments.
Linux Integration: In recognition of the growing presence of Linux in enterprise environments, Windows Server 2019 offers built-in support for Linux containers, which allows administrators to run Linux-based applications and tools directly on Windows Server.
Storage Migration Services: Migrating servers to a new OS can be challenging, especially when dealing with critical data. The Storage Migration Service in Windows Server 2019 makes it easier to move servers from older systems by automatically transferring files, shares, and security configurations.

Core Responsibilities of Windows Server 2019 Administrators
Effective Windows Server 2019 administration requires a combination of technical skills and a solid understanding of organizational needs. Below are some of the primary responsibilities for administrators.
1. Setting Up and Configuring Servers
Setting up Windows Server 2019 begins with proper installation, followed by configuring network settings, Active Directory (AD), and role-based access. Administrators need to define specific roles for each server, such as DNS, DHCP, or file servers, to ensure streamlined operations. They also configure AD Domain Services to manage networked resources and enable centralized user management.
2. User and Access Management
One of the most critical aspects of server administration is managing user accounts and permissions. Windows Server 2019 simplifies this process through Active Directory, where administrators can create, modify, and control access for users, groups, and devices within the network. Properly setting up permissions and implementing Group Policies ensures that users have the right access levels while protecting sensitive data.
3. Implementing Security Protocols
Windows Server 2019 includes multiple layers of security to safeguard data and network resources. Security features such as Windows Defender, Credential Guard, and Exploit Guard help protect against threats. Configuring firewall settings, setting up intrusion detection, and implementing multi-factor authentication are all part of a comprehensive security protocol for ensuring data integrity and preventing unauthorized access.
4. Monitoring and Maintaining Performance
Performance monitoring is an ongoing task for Windows Server administrators. Using built-in tools like Windows Performance Monitor and Task Manager, administrators can track CPU usage, memory, disk activity, and network performance. Windows Admin Center provides a centralized dashboard for monitoring server health and performance, allowing administrators to identify issues and bottlenecks before they impact users.
5. Managing Backup and Recovery
Data backup and recovery plans are crucial for any organization, especially when downtime can lead to significant financial losses. Windows Server 2019 provides administrators with robust tools like Windows Server Backup and Volume Shadow Copy Service to schedule regular backups. In case of data loss or corruption, these tools enable quick recovery of data, minimizing downtime and ensuring business continuity.
6. Implementing Virtualization and Containerization
With Hyper-V, Windows Server 2019 supports extensive virtualization capabilities, allowing administrators to run multiple virtual machines on a single physical server. This enables efficient use of hardware resources and reduces operational costs. Additionally, container support allows administrators to deploy applications in isolated environments, making it easier to manage dependencies and streamline deployment.
Best Practices for Windows Server 2019 Administration
To ensure smooth and efficient server management, administrators should follow these best practices:
Regular Patching and Updating: Regular updates help keep the system secure and enhance performance. Using Windows Update and Windows Server Update Services (WSUS) ensures that servers are protected with the latest security patches.
Monitor Log Files: Log files can provide valuable insights into system health, user activities, and security events. Regularly monitoring logs can help detect unauthorized access attempts and resolve issues before they escalate.
Automate Routine Tasks: Automation tools like PowerShell scripts allow administrators to streamline repetitive tasks, such as user account management and data backups, saving time and reducing human error.
Create a Disaster Recovery Plan: Having a well-documented disaster recovery plan is crucial. This should include steps for data recovery, server restoration, and emergency contact information.
Conclusion
Windows Server 2019 is a powerful platform that offers extensive capabilities for managing and securing enterprise IT environments. Effective administration requires a deep understanding of its features, from hybrid cloud support and virtualization to advanced security and user management. By mastering these core components, administrators can ensure their organization’s infrastructure is reliable, secure, and scalable.
Adopting best practices, such as regular patching, automation, and disaster recovery planning, will further enhance an administrator’s ability to manage the server environment effectively. As businesses continue to rely on digital resources, Windows Server 2019 administrators play a crucial role in ensuring that the backbone of these systems is well-managed, resilient, and prepared for the future.
0 notes
Text
The Power of Dedicated Windows Servers: Speed, Stability, and Security
In today's digital landscape, businesses, whether small startups or large enterprises, are increasingly reliant on technology to ensure the seamless operation of their websites, applications, and services. One of the cornerstones of ensuring these digital services run smoothly is the choice of hosting solutions. Among the most powerful and reliable options available is the dedicated Windows server.
A dedicated server offers a host of advantages over shared hosting solutions, and when paired with the robust features of the Windows operating system, it can unlock a world of benefits. Let’s explore the speed, stability, and security that dedicated Windows servers bring to the table.
1. Unmatched Speed and Performance
When it comes to digital operations, speed is critical. A slow website or application can result in frustrated customers, lost revenue, and a damaged brand reputation. A dedicated Windows server is specifically tailored for high performance.
Unlike shared hosting, where multiple clients share resources, a dedicated server provides exclusive use of all its resources. This means that the server’s full processing power, memory, and bandwidth are available to your business, enabling fast load times and handling spikes in traffic effortlessly. Whether you’re running a high-traffic eCommerce store, a complex web application, or a data-intensive service, the raw processing power of a dedicated Windows server ensures that your platform operates at peak performance.
Additionally, Windows servers are optimized to support Windows-based applications. If your software stack is built on Windows technologies such as ASP.NET, MS SQL, or IIS, a dedicated server guarantees seamless performance with no compatibility issues.
2. Unwavering Stability
Stability is another critical factor in hosting solutions. Businesses cannot afford to have frequent downtimes, as even short outages can disrupt customer trust and business operations. With a dedicated Windows server, you gain a level of stability that is hard to beat.
Since you are the only one utilizing the server's resources, there are fewer chances of performance degradation due to overcrowded servers or noisy neighbors (other users consuming too many resources). The hardware is dedicated solely to your use, which significantly reduces the chances of issues like server crashes or resource bottlenecks that are common in shared hosting environments.
Furthermore, Windows servers are known for their robust infrastructure and uptime guarantees. Managed hosting providers often include proactive monitoring, so any issues are addressed before they escalate into major problems. With regular system updates and patch management, your server remains in top working condition, ensuring your operations run smoothly 24/7.
3. Top-Notch Security
Security is a top priority for businesses that rely on online platforms. A dedicated Windows server offers superior security features to safeguard your data, applications, and customers.
Since your server is not shared with others, the risk of cross-contamination or security vulnerabilities from other users is eliminated. You have full control over your firewall settings, user permissions, and access levels, enabling you to customize the security features to meet your business needs.
Windows servers come with a wealth of built-in security tools, including Windows Defender Antivirus, BitLocker encryption, and Active Directory for managing user roles. Moreover, the Windows ecosystem offers timely and regular security updates, patches, and hotfixes that are crucial in keeping your server safe from emerging threats. These updates can be automated, ensuring that your server is always protected against the latest vulnerabilities.
In addition to these built-in features, dedicated servers can be configured with advanced security protocols such as SSL certificates, DDoS protection, and multi-factor authentication, further enhancing the security of sensitive business data.
4. Full Control and Customization
A dedicated Windows server gives you full control over your environment, allowing you to customize your setup according to your exact specifications. This is particularly valuable for businesses that require specific configurations, applications, or software stacks.
From configuring server hardware to choosing the specific versions of Windows Server you want to use, the customization options are virtually limitless. You can install any software or application that is compatible with Windows, giving you a high level of flexibility that is unmatched in shared hosting or virtual private server (VPS) environments.
5. Scalable for Growth
As your business grows, so too will your IT infrastructure needs. Dedicated Windows servers offer scalability, allowing you to easily add resources as needed. Whether it's increasing storage, upgrading your CPU, or adding RAM to handle increased traffic, dedicated servers can grow with your business.
Many providers offer managed services where you can easily scale up or down based on your specific requirements. This flexibility ensures that you don't pay for more resources than you need, while still being able to handle growth without experiencing a decrease in performance.
Conclusion
The power of dedicated Windows servers cannot be overstated. With their ability to provide speed, stability, and security, they are the ideal solution for businesses that require a reliable, high-performance hosting environment. Whether you’re looking to ensure fast load times, maintain uninterrupted uptime, or protect your critical data, a dedicated Windows server provides the foundation for achieving these goals and more.
If you are considering a hosting solution for your business, the dedicated Windows server offers the ideal balance of performance, control, and security. Its scalability ensures that as your business grows, your IT infrastructure can scale accordingly, while offering you a stable and secure environment to operate in. With a dedicated server, you can focus on growing your business while leaving the technical complexities to the experts.
0 notes
Text
Unmasking TeslaCrypt: A Deep Dive into Ransomware Analysis and Prevention

TeslaCrypt, a notorious ransomware trojan that emerged in early 2015, primarily targeted Windows systems, encrypting files and demanding Bitcoin ransom payments. Initially focusing on gaming files, including saves and profiles from popular titles like Minecraft and Call of Duty, TeslaCrypt's scope expanded to encompass a wide range of file types in later versions.
Distribution and Encryption Methods
TeslaCrypt spread through various vectors, including exploit kits (notably the Angler exploit kit), malicious email attachments, and compromised websites. The ransomware employed robust encryption algorithms such as AES-256 and RSA-2048, generating unique encryption keys for each infected machine, making decryption without paying the ransom extremely challenging. To combat TeslaCrypt and similar threats, cybersecurity professionals employ a range of sophisticated analysis techniques: File Identification and Entropy Analysis Utilizing tools like TrIDNET and Detect It Easy (DIE), analysts can identify file types and detect potential packing. In the case of TeslaCrypt, high entropy values (close to 8) in certain file sections indicated packed or obfuscated content, a common trait in sophisticated malware.


Packer Detection PEStudio proved invaluable in detecting signs of packing. The analysis of TeslaCrypt revealed a suspiciously low number of imported functions and libraries, often a telltale sign of packed executables attempting to conceal their true functionality.

PEstudio Libraries detected Unpacking Techniques To reveal TeslaCrypt's hidden code, analysts employed a combination of tools: - xdbg32 (x64dbg): This powerful debugger allowed for setting breakpoints on critical functions like VirtualAlloc, enabling analysts to intercept memory allocation calls used for unpacking. - Process Hacker: Once the unpacking process was identified in xdbg32, Process Hacker facilitated the dumping of allocated memory regions, capturing the unpacked payload. - 010 Hex Editor: This tool was crucial for manually searching and correcting MZ and PE headers in the dumped memory, a necessary step in reconstructing the unpacked executable.
In-Depth Analysis with Ghidra
After successful unpacking, the TeslaCrypt binary was imported into Ghidra, a sophisticated disassembler and reverse engineering tool. This step allowed for a detailed analysis: - Encryption mechanisms, including the implementation of AES-256 and RSA-2048 algorithms. - File targeting patterns, helping to identify the types of files at risk. - Command and Control (C2) communication, revealing how TeslaCrypt interacted with its controllers. - Ransom note generation processes. - Persistence mechanisms are used to maintain a foothold on infected systems.

Analysis using Ghidra
Defending Against TeslaCrypt and Similar Threats
Understanding TeslaCrypt's inner workings through these analysis techniques enables the development of robust defense strategies: Proactive Measures - Regular, offline backups to ensure data recovery in case of infection. - Keeping systems and software up-to-date with the latest security patches. - Implementing strong endpoint protection and detection solutions. - Conducting ongoing user training on phishing awareness and safe browsing practices. Network Security - Deploying and maintaining firewalls and intrusion detection systems. - Implementing network segmentation to limit potential malware spread. - Regular vulnerability scanning and prompt patching of identified weaknesses. The battle against ransomware like TeslaCrypt requires a multifaceted approach combining advanced analysis techniques, robust security measures, and continuous education.By leveraging tools such as xdbg32, Process Hacker, and Ghidra, security professionals can unravel the complexities of these threats, ultimately developing more effective defenses and response strategies. Read the full article
0 notes
Text
Why Should You Choose Plesk Hosting?

When selecting a web hosting solution, the choice of control panel plays a vital role in determining the overall user experience, efficiency, and flexibility of managing your website. Plesk, one of the leading control panels in the industry, has gained immense popularity due to its ease of use, extensive features, and robust security. If you're considering switching to or starting with Plesk, this article will explore why it’s considered one of the best Plesk hosting options available today. Here, we’ll delve into the key benefits of choosing Plesk hosting and how it can enhance your web hosting experience.
1. User-Friendly Interface
Plesk is celebrated for its clean and intuitive interface, making it an ideal choice for both beginners and seasoned professionals. The dashboard is designed with user experience in mind, offering a simplified and well-organized layout. Whether you need to manage websites, configure email accounts, set up databases, or handle DNS settings, Plesk’s interface guides you through each step without overwhelming you with technical jargon. For those new to hosting, the straightforward navigation and clear instructions make it easy to get started quickly, which is why Plesk is recognized as the best Plesk hosting solution for hassle-free management.
2. Cross-Platform Compatibility
One of the standout features of Plesk is its compatibility with both Linux and Windows servers. Unlike some control panels that are limited to a specific operating system, Plesk provides full support across platforms, making it a versatile choice for various hosting environments. This cross-platform compatibility is especially beneficial if you’re managing a mix of technologies, like WordPress sites on Linux and ASP.NET applications on Windows. This flexibility ensures that no matter what your hosting requirements are, Plesk can accommodate them, solidifying its position as the best Plesk hosting option for diverse needs.
3. Integrated WordPress Toolkit
For those managing WordPress websites, Plesk offers a powerful WordPress Toolkit that simplifies the process of handling multiple WordPress sites from a single dashboard. The toolkit allows you to install, clone, and manage your WordPress installations with ease. You can perform one-click updates, implement security hardening, and even create staging environments for testing changes before going live. These features streamline WordPress management and reduce the technical complexity involved in running multiple sites, making Plesk an attractive choice for anyone seeking the best Plesk hosting for WordPress.
4. Robust Security Features
In today’s digital landscape, security is a non-negotiable priority. Plesk hosting offers built-in security features designed to protect your websites and data. With automatic SSL certificate management via Let’s Encrypt, a Web Application Firewall (WAF), and integrated anti-virus and anti-spam tools, Plesk provides comprehensive protection against threats. Plesk also offers advanced security measures like two-factor authentication (2FA) and fail2ban to defend against brute force attacks. The combination of these features ensures that your hosting environment is safeguarded, making Plesk one of the best Plesk hosting options for security-conscious users.
5. Extensive Extension Marketplace
One of Plesk’s key advantages is its rich library of extensions, allowing you to customize and enhance your hosting experience. The Plesk Extension Marketplace offers a wide range of tools, from performance optimization plugins and backup solutions to SEO tools and marketing automation. These extensions enable you to tailor Plesk to meet your specific needs without requiring additional software installations. Whether you’re looking to improve website performance, integrate with third-party services, or streamline your operations, Plesk’s extension ecosystem makes it a highly versatile and adaptable hosting solution.
6. Easy Server Management and Monitoring
Managing your server resources effectively is crucial to ensuring optimal website performance. Plesk simplifies server management by providing detailed insights into resource usage, allowing you to monitor CPU, RAM, and disk space consumption. The control panel also offers automated monitoring and alerts, helping you stay on top of potential issues before they escalate. Additionally, Plesk allows you to automate routine tasks such as backups, updates, and maintenance, freeing up your time to focus on growing your online presence. This efficient management makes Plesk one of the best Plesk hosting platforms for both small businesses and large enterprises.
7. Scalability for Growing Businesses
As your business grows, your hosting requirements are likely to evolve. Plesk is built with scalability in mind, offering seamless options to scale up your resources, add more websites, or deploy additional applications. Whether you’re starting with a small blog or running a high-traffic e-commerce site, Plesk’s flexibility allows you to scale without disruptions. This adaptability makes it the best Plesk hosting choice for businesses planning long-term growth, as it ensures you can expand your hosting environment in line with your needs.
8. Comprehensive Backup and Restore Solutions
Data loss can be devastating, which is why Plesk includes automated backup and restore features to safeguard your data. With Plesk, you can schedule regular backups of your websites, databases, and server settings, ensuring that you always have a recovery point in case of an unexpected issue. The control panel also provides a straightforward restore process, allowing you to roll back changes or recover lost data with just a few clicks. The peace of mind that comes from knowing your data is securely backed up makes Plesk hosting a reliable option for anyone concerned with data protection.
9. Developer-Friendly Environment
Plesk isn’t just for beginners; it also caters to developers and IT professionals with a host of advanced tools. Plesk supports multiple programming languages and frameworks, including PHP, Node.js, Ruby, and Python, providing a versatile development environment. The control panel also integrates with Docker and Git, allowing developers to deploy and manage containers or version control with ease. Additionally, Plesk’s support for APIs and CLI tools makes it easier for developers to automate and manage tasks programmatically. These developer-centric features position Plesk as the best Plesk hosting choice for tech-savvy users who require more control and customization.
10. Reliable 24/7 Support and Community Resources
Even with a user-friendly interface and powerful tools, there may still be times when you need help. Plesk hosting comes with access to 24/7 customer support, ensuring that you can resolve issues quickly whenever they arise. Whether you have technical questions or need assistance with specific configurations, the support team is there to assist you. In addition to official support, Plesk has a large community of users, developers, and hosting experts who share knowledge, tips, and solutions through forums, blogs, and social channels. The availability of both professional support and community-driven resources makes Plesk hosting an ideal solution for users who value consistent support.
Conclusion
Plesk has emerged as one of the most reliable and feature-rich control panels available, offering a comprehensive solution for web hosting management. Whether you’re a beginner looking for simplicity or an advanced user in need of powerful tools, Plesk caters to a wide range of needs. From its user-friendly interface and robust security features to its scalability and developer-friendly tools, Plesk offers everything required to manage websites and servers effectively.
As discussed in this article, the reasons to choose Plesk hosting go beyond just its ease of use. Its versatility, extensive extension marketplace, and cross-platform compatibility make it one of the best Plesk hosting solutions for individuals, businesses, and developers alike. Whether you’re managing WordPress sites, scaling your business, or developing complex applications, Plesk’s flexibility and reliability ensure that it meets your requirements.
If you’re in search of a hosting control panel that offers a balanced mix of power, simplicity, and security, then Plesk should be at the top of your list. By opting for the best Plesk hosting solution, you can streamline your website management, enhance security, and scale your hosting environment effortlessly. Plesk’s comprehensive suite of features and dedicated support make it a smart choice for anyone serious about their online presence.
Choosing Plesk hosting isn’t just about picking a control panel; it’s about selecting a robust, scalable, and user-friendly platform that grows with your needs. Whether you’re launching a new website or managing a portfolio of sites, Plesk provides the tools, security, and flexibility to ensure your hosting experience is seamless and successful.
0 notes
Text
The importance of managed hosting security for your clients’ web security needs
Cyberattacks, data breaches, and other criminal activities are a constant concern in today's digital environment. One of your main duties as a best web hosting provider is to ensure that others' websites are always safe from these security concerns and attacks.
Regretfully, there are instances when it's simpler to say than achieve. It can be difficult to constantly maintain the best web hosting security, especially if you're a small web hosting provider managing several clients and websites. Furthermore, unless you work in online security, you may not be aware of the precise features or tools that your clients want for the highest level of safety.

Presenting best managed hosting, a special service that strengthens your clients' websites with a complete, multi-layered security plan in addition to providing them with a web address.
Benefits of managed hosting security-
By relying on a managed web hosting provider for the technical and security needs of your clients' websites, you leverage specialized expertise and advanced tools aimed at defending against the latest cyber threats. Here are some features and benefits you can anticipate with best managed hosting security:
Attentive observation
Threats can arise at any time and without notice in an online environment.
Providers of managed hosting services are aware of this and are constantly alert. They monitor websites and servers for any odd or suspicious activities.
For instance, you will profit from having a fully staffed team and level 3 technicians at data centres monitoring your clients' servers and networks around the clock when you are a web hosting provider. This ensures that possible security risks are found early on and eliminated before they become more significant and cause harm.
This kind of attention to detail is usually absent from unmanaged hosting situations. Numerous risks may remain hidden until it's too late if proactive monitoring isn't done.
Security measures designed for a platform
The best web hosting provider adjusts security procedures and defences—like intrusion detection systems, firewalls, and DDoS protection—to the particular needs and weaknesses of any platform or website.
For instance, specific security settings that address known vulnerabilities in this content management system (CMS) will be applied to WordPress hosting websites.
Thus, you have a customized cybersecurity solution that is suited for your particular platform as opposed to a one-size-fits-all strategy that may leave security gaps.
Backups done automatically
A business owner never wants to have to start again after losing data, whether from a technical malfunction, user error, or hacker assault.
However, because most managed hosting security services include automated daily and on-demand backups, the risks of data loss are significantly reduced. These two functions serve as backups to guarantee that no important files, data, or projects belonging to you or your clients are ever lost.
Dedicated expert support
Dedicated professional support is just another exceptional advantage of managed hosting. The majority of service providers provide 24/7 customer support via a variety of channels, including live chat, email, and phone. To put it briefly, assistance is always just a button push away.
Additionally, the majority of managed web servers have support staff with training and experience in a variety of technical fields, such as operating systems like Windows and Linux and other content management systems like WordPress and Joomla.
Therefore, a skilled expert who is familiar with your particular ecosystem is prepared and glad to help, regardless of the platform or system powering your clients' websites.
Monitoring compliance
If your clients work in an industry or territory where compliance with privacy and security regulations is mandatory, you must ensure that your hosting environment complies with these rules. Managed hosting companies may assist in ensuring that your websites are compliant, as they typically have expertise in implementing these standards.
Cost Savings
The financial consequences of cyberattacks are extremely severe. For instance, IBM reports that the average cost of a data breach worldwide in 2023 was an astounding $4.45 million. In addition to immediate monetary losses, collateral damages may also occur, including damaged reputations, lost business, and even legal action.
By making an investment in managed hosting security, you and your clients are protected from a wide range of unanticipated costs, such as legal fees, post-breach clean-ups, and revenue losses due to downtime.
Furthermore, you won't need to engage a sizable in-house staff or contract out the work to a third party when your clients' security is being monitored and maintained by a specialized security team from the managed hosting provider. The money you save might be applied to other aspects of your company.
Peace of mind
You may lose focus on important business matters if you are preoccupied with concerns about your clients' websites' security all the time. You can relax knowing that your client's websites are in skilled and safe hands with managed to host security. You can refocus your energies on other crucial issues and redirect your energy with this peace of mind.
Threats against which managed hosting security works effectively-
Websites owned by your clients can be shielded from a variety of risks by using managed hosting security. Among them are:
Phishing attacks: Phishing is the practice of tricking targets into disclosing critical personal data, such as by building fake websites that mimic real ones. Although managed hosting cannot stop fraudsters or scammers from trying to deceive customers, it can provide SSL certificates, which enable users to verify a website's authenticity.
Brute force attacks: In these, attackers try different passwords, credentials, or other authentication details until they figure out the correct combination.
Distributed Denial of Service (DDoS) attacks: In a DDoS attack, a web server is overloaded with traffic, preventing authorized users from accessing it.
Malware attacks: Malicious software intended to breach, harm, or take over a network or website is known as malware. Outdated CMS and programs with documented security flaws that have been patched but not updated are common attack vectors. Ransomware, worms, trojans, malware, and viruses are a few examples. Managed hosting companies conduct routine malware scans to guarantee the early identification and elimination of these applications.
SQL injection: In this kind of attack, malicious SQL code is inserted into the input fields of the online application. The attacker might then be able to access, alter, or retrieve data from the website's database.
How to pick a highly secure managed hosting provider?
Selecting the best managed hosting provider for your requirements might be challenging with the wide range of options available.
Determine your clients' security needs
Every client has different security demands, and vice versa. Thus, the selection process of a managed hosting company begins by outlining its security requirements precisely. Consider the following inquiries for yourself:
What kinds and volumes of data do your customers manage?
Are there any compliance requirements that they must follow?
What volume of traffic do they usually receive?
Which threats are most relevant to their line of business?
By doing this, you can make sure that the provider you choose is exactly suited to the unique requirements of your client.
Compile a list of possible suppliers
After determining your clients' security requirements, you must now assemble a list of possible suppliers.
First, use your professional network. Industry colleagues and associates can provide priceless advice based on first-hand knowledge.
Next, explore internet resources, including tech groups, specialized blogs, and industry forums. These might assist you in locating respectable suppliers that are worthy of your consideration.
Perform preliminary investigation
The next thing to do is conduct some basic research after you have a list of potential providers.
Start by perusing consumer feedback and rankings on independent discussion boards. Evaluate the public's overall opinion or emotion regarding each supplier.
An indication of a provider's integrity and resilience might be found in how they have handled previous issues.
Look into transparency as well; it's important. Evaluate the transparency of each provider's infrastructure, security protocols, operational standards, and even pricing.
Finally, but just as importantly, compare and ascertain whether the suppliers on your list have security and compliance certifications. Certifications may strongly indicate a provider's dedication to security. Make sure to confirm that these certifications are legitimate.
Shortlist providers
Reduce the number of suppliers on your list to a select few who appear to match your main requirements based on the results of your investigation.
Generally speaking, the companies on your list have to have excellent ratings, a track record of successfully managing security problems, a wide range of service options, and a clear dedication to user protection.
Compare and analyze the features
Now that the list has been reduced, let's compare them in more detail. Examine the security offerings of each shortlisted provider in further detail.
What DDoS defense mechanisms and technologies do they provide? How thorough are their methods for defending against malware? Do they also offer SSL certificates, which are essential for guaranteeing your clients' data transit security? What about backups and firewall security? Examine these attributes carefully for every supplier and draw appropriate conclusions.
Remember that mishaps can still occur even with the best security. Having a committed support staff on hand can be really helpful in that situation.
Therefore, compare the technical support that each provider offers, including availability and the stated response time, in addition to the specific security features.
Compare pricing
Once you have a solid understanding of each provider's characteristics, you can examine their pricing structures.
Here are some things to think about asking:
Exist any undisclosed expenses or fees?
Are the listed costs within your means?
Is scalability implemented economically? Put differently, will the hosting package be able to grow with your clients' company without becoming too expensive?
Do the prices make sense, given the variety and complexity of security features available?
A crucial reminder is to consider more than just the statistics when evaluating costs. Low-cost plans may have features that are not necessary or security flaws. On the other hand, a high price does not guarantee an unbreakable security suite.
The idea of value needs to be highlighted: What are the rewards, both material and immaterial, that you are getting out of your investment? Make sure the solution you're paying for is complete and genuinely serves the interests of you and your clients rather than just a brand name or flashy features.
Decide and go on board
Now that all the required investigation, evaluation, and contrast have been completed, the stage is ready to make an informed decision. Select the managed hosting company that best meets your security requirements, financial constraints, and business objectives.
After that, you just need to get in touch with the supplier to start the onboarding procedure.
Conclusion-
Making the move from unmanaged to managed hosting could significantly impact your company.
It's an investment that not only provides the best level of protection for your clients' digital assets but also frees up important time and resources that you can use for your main company operations.

Dollar2host Dollar2host.com We provide expert Webhosting services for your desired needs Facebook Twitter Instagram YouTube
0 notes
Text
Ngày nay, mạng wifi công cộng là rất phổ biến và được tìm thấy ở khắp mọi nơi. Thông thường, chúng ta sẽ không suy nghĩ kỹ trước khi kết nối vì nó miễn phí, nhưng thứ miễn phí đó có thể khiến chúng ta phải trả giá rất nhiều. Các điểm truy cập hoặc Wi-Fi công cộng chưa bao giờ an toàn như Wi-Fi gia đình hoặc cơ quan vì nó miễn phí cho tất cả mọi người. Bất kỳ middle man có kinh nghiệm nào cũng có thể đột nhập vào wifi và theo dõi hoạt động duyệt web của bạn. Tin tặc cũng có thể truy cập máy tính của bạn thông qua wifi công cộng và đánh cắp dữ liệu nhạy cảm. Vì vậy, tốt nhất bạn nên bảo vệ PC chạy Windows 11 của mình trước khi kết nối với Wi-Fi công cộng. 7 cách tốt nhất để bảo vệ PC của bạn trên Wi-Fi công cộng Do đó, trong bài viết này, mình sẽ liệt kê một số cách để bảo vệ PC Windows của bạn trên Wi-Fi công cộng. Đây là những mẹo chung, nhưng chúng thực hiện khá tốt công việc của mình. 1. Luôn sử dụng VPN Như chúng ta đã biết, vai trò của ứng dụng VPN là mã hóa lưu lượng truy cập của bạn và khiến bạn ẩn danh. Vì VPN định tuyến lại lưu lượng truy cập của bạn thông qua các máy chủ riêng của nó trải rộng trên nhiều khu vực, các bên trung gian sẽ không thể truy cập hoặc lấy cắp dữ liệu quý giá của bạn. Do mã hóa chất lượng cao, tội phạm mạng sẽ mất khoảng một tháng để đánh chặn dữ liệu của bạn. VPN hoạt động như một lớp bảo mật bổ sung và mọi người phải được kết nối với địa chỉ IP của máy chủ riêng trước khi sử dụng Wi-Fi công cộng. 2. Cập nhật hệ điều hành của bạn Sử dụng Windows 11, bạn có thể nhận thấy rằng hầu hết các bản cập nhật hệ thống đều bao gồm các bản sửa lỗi, bản vá và cải tiến bảo mật. Cập nhật bảo mật là điều cần thiết mà bạn không bao giờ nên bỏ qua. Mặc dù cập nhật hệ điều hành kịp thời không loại bỏ hoàn toàn nguy cơ bị tấn công, nhưng nó thực sự gây khó khăn cho tội phạm mạng. Vì vậy, tốt nhất là bạn nên cập nhật Windows 11. Để cập nhật Windows 11, hãy đi tới Settings > Windows Update > Check for Updates và tải xuống các bản cập nhật có sẵn. 3. Tắt Network Discovery & Sharing Khi bật tính năng network discovery, máy tính của bạn có thể nhìn thấy các máy tính và thiết bị mạng khác. Tương tự, thiết bị của bạn sẽ hiển thị với các máy tính mạng khác. Vì vậy, nếu đang sử dụng wifi công cộng, tốt nhất bạn nên tắt tùy chọn này. 1. Đầu tiên, mở tìm kiếm Windows 11 và nhập Control Panel. Sau đó, mở Control Panel. 2. Trên Control Panel, nhấp vào tùy chọn Network and Internet. 3. Nhấp vào Network and Sharing center trên trang tiếp theo. 4. Trên menu bên trái, nhấp vào tùy chọn Change Advanced sharing settings. 5. Bây giờ, chọn Turn off network discovery. 6. Trong phần File and printer sharing, hãy chọn Turn off file and printer sharing. 4. Bật Tường lửa & Bảo vệ Mạng Cả Windows 10 và Windows 11 đều có hệ thống Tường lửa. Hệ thống tường lửa được bật theo mặc định, nhưng chương trình chống vi-rút của bên thứ ba thường tắt hệ thống này. Vai trò của tường lửa là bảo vệ PC của bạn khỏi các mối đe dọa và tin tặc không xác định. Nó phát hiện và ngăn chặn các sự kiện độc hại hoặc tin tặc truy cập trái phép vào PC của bạn. 1. Trước hết, hãy mở ứng dụng Windows Security trên Windows 11 của bạn. 2. Tiếp theo, nhấp vào tùy chọn Firewall & network protection. 3. Trên màn hình tiếp theo, nhấp vào tùy chọn Public Network. 4. Trên màn hình tiếp theo, bật Microsoft Defender Firewall. 5. Tắt wifi khi bạn không sử dụng Trong khi kết nối với WiFI Công cộng, chúng ta được cung cấp một tùy chọn để ghi nhớ mạng. Thao tác này được thực hiện để kích hoạt kết nối wifi tự động. Nếu bạn đã bật kết nối wifi tự động, bộ điều hợp wifi của bạn sẽ tự động kết nối với mạng công cộng mà nó đã từng được kết nối. Tin tặc có thể cố gắng theo dõi các lần gõ phím hoặc lịch sử duyệt web của bạn nếu sự kiện này xảy ra bằng cách cài đặt các ứng dụng độc hại. Các ứng dụng và dịch vụ như vậy chạy ngầm trong nền và cố gắng kết nối với internet để trao đổi dữ liệu. Vì vậy, tốt nhất bạn nên tắt kết nối Wi-Fi khi không sử dụng. Nó sẽ bảo vệ PC và sẽ tiết kiệm pin của bạn.
6. Luôn sử dụng HTTPS Bạn có thể dễ dàng phát hiện một trang web an toàn bằng cách chỉ cần nhìn vào dấu HTTPS trên thanh địa chỉ. Nếu bạn không sử dụng VPN, đừng mở các trang web không được bảo vệ bằng HTTPS. Trong khi nhập các chi tiết nhạy cảm như mật khẩu, hãy đảm bảo rằng trang web có kết nối được mã hóa. Do đó, nếu bạn đang cố gắng truy cập một trang web trên Mạng công cộng, hãy đảm bảo rằng URL của trang web bắt đầu bằng HTTPS. Nếu bạn đang sử dụng Google Chrome, bạn có thể buộc trình duyệt web luôn sử dụng các kết nối an toàn. 1. Đầu tiên, hãy mở trình duyệt Google Chrome và nhấp vào dấu ba chấm. 2. Từ danh sách các tùy chọn, chọn Settings. 3. Trên trang Settings, nhấp vào tùy chọn Security & Privacy. 4. Sau đó, ở bên phải, nhấp vào tùy chọn Security. 4. Tìm và bật tùy chọn 'Always use secure connections' trong Security. 7. Cập nhật chương trình chống vi-rút/bảo mật Internet của bạn Nhiều chương trình chống vi-rút và phần mềm bảo mật internet cung cấp tính năng bảo vệ wifi của bạn. Ngoài ra, nhiều chương trình bảo mật ngày nay đi kèm với một VPN tích hợp. Vì vậy, bạn nên cập nhật chương trình bảo mật của mình, đặc biệt là trước khi kết nối với Wi-Fi công cộng. Đây là một số cách để bảo vệ máy tính của bạn khi sử dụng wifi công cộng. Mình hy vọng bài viết này sẽ giúp được bạn.
0 notes
Text
is windows built in vpn good
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
is windows built in vpn good
Windows built-in VPN features
Title: Exploring the Power of Windows Built-in VPN Features
In today's digital landscape, safeguarding online privacy and security is paramount. With cyber threats looming large, individuals and businesses alike seek reliable solutions to protect their data. Fortunately, Windows users have access to robust built-in VPN (Virtual Private Network) features that offer enhanced security and privacy.
One of the key advantages of utilizing Windows built-in VPN features is the seamless integration with the operating system. Users can easily set up and configure VPN connections without the need for third-party software, making it convenient and user-friendly.
Windows offers support for various VPN protocols, including PPTP, L2TP/IPsec, SSTP, and IKEv2, providing flexibility and compatibility with a wide range of VPN services. Whether you're connecting to a corporate network or accessing geo-blocked content, Windows VPN features ensure a secure and reliable connection.
Moreover, Windows VPN includes advanced encryption algorithms that encrypt data traffic, preventing unauthorized access and safeguarding sensitive information from prying eyes. This encryption helps maintain confidentiality and integrity, ensuring that user data remains secure during transmission.
Another notable feature of Windows built-in VPN is its seamless integration with other Windows security features, such as Windows Firewall and Windows Defender. This layered approach to security enhances overall protection against online threats, malware, and phishing attacks.
Furthermore, Windows VPN offers automatic connection options, allowing users to establish VPN connections automatically when connecting to unsecured networks, such as public Wi-Fi hotspots. This proactive approach helps mitigate security risks and ensures continuous protection against potential threats.
In conclusion, Windows built-in VPN features provide a robust and reliable solution for users seeking to enhance their online privacy and security. With its seamless integration, advanced encryption, and automatic connection options, Windows VPN offers peace of mind in an increasingly interconnected world.
Windows VPN reliability
Title: Assessing the Reliability of Windows VPN Services
As virtual private networks (VPNs) continue to gain popularity for ensuring online privacy and security, the reliability of VPN services, especially those on the Windows platform, becomes a critical consideration for users. Windows VPNs offer a convenient solution for safeguarding internet connections on devices running the Windows operating system, but their reliability can vary significantly based on several factors.
One key aspect affecting the reliability of Windows VPNs is the quality of the VPN provider. Established providers with robust infrastructure and advanced encryption protocols tend to offer more reliable services compared to lesser-known or free VPNs. Users should research and select a reputable VPN provider known for its reliability and commitment to user privacy.
Another factor influencing Windows VPN reliability is the server network. VPNs with a wide network of servers distributed across various locations typically provide better reliability and faster connection speeds. Users should choose VPNs with servers strategically located to ensure reliable performance, especially during peak usage times.
Furthermore, the effectiveness of VPN protocols employed by Windows VPN services significantly impacts their reliability. Protocols like OpenVPN, IKEv2, and WireGuard are known for their reliability and security, offering users a dependable shield against online threats. Users should prioritize VPNs that support these robust protocols for enhanced reliability.
Additionally, the compatibility of Windows VPNs with different devices and operating systems can affect their reliability. VPNs that offer dedicated apps for Windows and provide seamless integration with other platforms ensure a consistent and reliable user experience across devices.
In conclusion, while Windows VPNs offer a convenient solution for enhancing online security and privacy, their reliability hinges on various factors such as the quality of the VPN provider, server network, supported protocols, and device compatibility. By carefully evaluating these factors, users can select a Windows VPN service that offers reliable performance and peace of mind.
Windows VPN performance
Windows VPN performance can greatly impact the user experience when browsing the internet or accessing restricted content online. A VPN, or Virtual Private Network, provides users with a secure and private connection to the internet by encrypting their data and masking their IP address. However, the performance of a VPN on Windows devices can vary depending on several factors.
One crucial factor that affects Windows VPN performance is the server location. The distance between the user and the VPN server can impact connection speed and latency. Users may experience slower performance if the VPN server is located far away from their physical location. Choosing a server closer to your actual location can improve VPN performance and speed.
Additionally, the type of encryption used by the VPN can also influence performance. While strong encryption protocols provide better security, they can also slow down connection speeds. Users can experiment with different encryption settings to find a balance between security and performance that meets their needs.
Moreover, the overall quality of the VPN service provider plays a significant role in Windows VPN performance. Reputable VPN providers offer a large network of servers, high-speed connections, and reliable performance. Users should research and select a VPN provider with a proven track record of delivering fast and stable connections.
In conclusion, Windows VPN performance is influenced by server location, encryption protocols, and the quality of the VPN service provider. By considering these factors and making informed decisions, users can optimize their VPN experience and enjoy secure and efficient browsing sessions.
Windows VPN security
Title: Enhancing Windows VPN Security: Best Practices and Tips
In today's digital landscape, safeguarding your online activities has become paramount, especially with the increasing threats to privacy and security. For Windows users, employing a Virtual Private Network (VPN) is a fundamental step towards enhancing online security. However, merely using a VPN isn't sufficient; understanding how to optimize its security features is crucial. Here are some best practices and tips to bolster Windows VPN security:
Choose a Reliable VPN Service: Opt for a reputable VPN provider known for robust security protocols and a strict no-logs policy. Research and compare different providers before making a decision.
Enable Kill Switch: Most VPNs offer a kill switch feature that automatically disconnects your internet connection if the VPN connection drops. This prevents your data from being exposed to prying eyes during potential disruptions.
Utilize Strong Encryption: Ensure that your VPN employs strong encryption standards like AES-256, which provides an extra layer of security by encrypting your data packets.
Regularly Update VPN Software: Keep your VPN client up to date to patch any security vulnerabilities and ensure optimal performance.
Use Multi-Factor Authentication (MFA): Where possible, enable MFA for accessing your VPN account. This adds an extra layer of security by requiring an additional form of verification, such as a code sent to your mobile device.
Avoid Public Wi-Fi: Exercise caution when using public Wi-Fi networks, as they are often insecure and susceptible to cyber threats. Always connect to your VPN when accessing the internet on public networks.
Enable DNS Leak Protection: DNS leaks can compromise your privacy by revealing your browsing history. Enable DNS leak protection in your VPN settings to prevent this from happening.
By implementing these measures, Windows users can significantly enhance the security of their VPN connections, thereby safeguarding their online activities and protecting their sensitive data from potential threats. Remember, proactive security measures are key to staying one step ahead in the ever-evolving landscape of cybersecurity.
Windows VPN user experience
Title: Enhancing User Experience: A Deep Dive into Windows VPNs
In today's interconnected digital landscape, safeguarding online privacy and security is paramount. Virtual Private Networks (VPNs) have emerged as indispensable tools for individuals and businesses alike, offering encrypted connections and anonymous browsing. Among the plethora of VPN options available, Windows VPNs stand out for their seamless integration with the operating system, providing users with a streamlined and intuitive experience.
One of the key advantages of Windows VPNs is their ease of setup and configuration. With just a few clicks, users can establish a secure connection, allowing them to browse the web anonymously and access geo-restricted content effortlessly. Windows' built-in VPN client simplifies the process even further, eliminating the need for third-party software and reducing potential compatibility issues.
Moreover, Windows VPNs offer a range of features designed to enhance user experience. From automatic server selection to split tunneling, these functionalities empower users to customize their VPN experience according to their specific needs. Additionally, Windows' robust security features complement VPN encryption, providing users with comprehensive protection against cyber threats.
Furthermore, Windows VPNs boast impressive performance and reliability. With optimized protocols and server networks, users can enjoy fast and stable connections, ensuring smooth browsing, streaming, and gaming experiences. Whether accessing sensitive information or streaming content from across the globe, Windows VPNs deliver consistent performance without compromising speed or reliability.
In conclusion, Windows VPNs offer a user-friendly and feature-rich experience, making them an ideal choice for individuals and businesses seeking to enhance their online privacy and security. With seamless integration, advanced features, and reliable performance, Windows VPNs empower users to navigate the digital world with confidence and peace of mind.
0 notes
Text
do you need windows 10 pro for vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
do you need windows 10 pro for vpn
Windows 10 Pro VPN compatibility
Windows 10 Pro boasts extensive compatibility with various VPN services, offering users enhanced privacy, security, and access to geo-restricted content. With its robust networking capabilities, Windows 10 Pro seamlessly integrates with leading VPN providers, ensuring a smooth and secure browsing experience for users.
One of the key advantages of using a VPN on Windows 10 Pro is its broad support for different protocols, including OpenVPN, L2TP/IPsec, IKEv2/IPsec, and PPTP. This versatility allows users to connect to VPN servers using their preferred protocol, depending on their specific requirements for security and performance.
Moreover, Windows 10 Pro's built-in VPN client simplifies the setup process, making it easy for users to configure and manage their VPN connections directly from the operating system's settings. Whether connecting to a VPN for remote work, accessing region-locked content, or securing sensitive data while browsing on public Wi-Fi networks, Windows 10 Pro offers the flexibility and reliability needed to ensure a secure and private online experience.
Additionally, Windows 10 Pro's compatibility with third-party VPN applications further expands users' options, allowing them to choose from a wide range of VPN services tailored to their individual needs. Whether opting for a free VPN solution or subscribing to a premium service with advanced features, Windows 10 Pro accommodates diverse preferences and requirements, empowering users to safeguard their online activities effectively.
In conclusion, Windows 10 Pro's robust VPN compatibility makes it an ideal choice for users seeking to enhance their online privacy and security. With support for various protocols and seamless integration with leading VPN providers, Windows 10 Pro offers a reliable and versatile platform for accessing the benefits of VPN technology.
Benefits of Windows 10 Pro for VPN
Windows 10 Pro is a popular operating system choice for many users due to its advanced features and functionalities. When it comes to VPN (Virtual Private Network) usage, Windows 10 Pro offers several benefits that can enhance security, privacy, and overall user experience.
One of the key advantages of using Windows 10 Pro for VPN is the built-in support for various VPN protocols, including OpenVPN, L2TP/IPsec, and IKEv2. This makes it easier for users to set up and configure VPN connections without the need for third-party software.
Moreover, Windows 10 Pro provides robust security features that help protect your data and online activities while using a VPN. The operating system includes Windows Defender Firewall, which helps filter network traffic and prevent unauthorized access. Additionally, features like BitLocker drive encryption can further secure your data in case of device theft or loss.
Another benefit of using Windows 10 Pro for VPN is its compatibility with a wide range of VPN services available in the market. Whether you prefer a subscription-based VPN service or set up your VPN server, Windows 10 Pro offers flexibility and support for different VPN configurations.
In conclusion, Windows 10 Pro is a reliable and secure operating system that offers several benefits for VPN users. From built-in VPN protocol support to advanced security features, Windows 10 Pro can enhance your VPN experience and provide peace of mind when browsing the internet or accessing sensitive information online.
Windows 10 Pro vs
When it comes to choosing an operating system for your computer, Windows 10 Pro stands out as a popular choice, offering a range of features and functionalities that cater to both personal and professional users. However, it's essential to understand the differences between Windows 10 Pro and other editions to make an informed decision.
One of the primary distinctions is between Windows 10 Pro and Windows 10 Home. While both versions share many core features, Windows 10 Pro includes additional functionalities designed to meet the needs of business users and IT professionals. These include advanced security features such as BitLocker encryption, which helps protect sensitive data from unauthorized access, and Windows Update for Business, allowing for greater control over system updates and deployments.
Another key difference is in terms of networking capabilities. Windows 10 Pro offers enhanced networking features, such as the ability to join a domain or access Remote Desktop, making it ideal for businesses with complex IT infrastructures or remote work requirements.
Additionally, Windows 10 Pro includes support for virtualization through Hyper-V, allowing users to run multiple operating systems on the same hardware simultaneously. This feature is particularly useful for developers, IT administrators, and power users who need to test software or create isolated environments.
In summary, while Windows 10 Pro shares many similarities with other editions of Windows 10, its additional features and functionalities make it a preferred choice for users with specific needs, such as business users, IT professionals, and power users. Understanding these differences can help you choose the version of Windows 10 that best suits your requirements and maximizes your productivity.
Security features in Windows 10 Pro for VPN
Windows 10 Pro offers a range of robust security features designed to enhance VPN (Virtual Private Network) functionality and protect users' privacy and data. One key feature is the built-in support for VPN protocols such as PPTP, L2TP/IPsec, SSTP, and IKEv2, allowing users to establish secure connections to remote networks. This ensures that data transmitted between the user's device and the VPN server is encrypted, safeguarding it from interception by malicious actors.
Additionally, Windows 10 Pro includes a feature known as VPN Reconnect, which automatically re-establishes the VPN connection in case of disruption, ensuring uninterrupted access to the network resources. This feature is particularly useful for users who rely on VPNs for remote work or accessing sensitive information.
Furthermore, Windows 10 Pro includes a powerful firewall that can be configured to restrict incoming and outgoing network traffic, providing an additional layer of security for VPN connections. Users can customize the firewall settings to allow or block specific apps and services, thereby controlling which applications are allowed to communicate over the VPN connection.
Moreover, Windows 10 Pro offers BitLocker encryption, which can be used to encrypt the entire hard drive or specific files and folders. This feature ensures that data stored on the device is protected even if the device is lost or stolen, enhancing the overall security of VPN connections.
In conclusion, Windows 10 Pro provides a comprehensive set of security features that enhance VPN functionality and help users maintain privacy and security while accessing network resources remotely. By leveraging these features, users can enjoy a secure and seamless VPN experience on their Windows 10 Pro devices.
Setting up VPN on Windows 10 Pro
Setting up a VPN on Windows 10 Pro is a straightforward process that can enhance your online privacy and security. A VPN, or Virtual Private Network, creates a secure connection between your device and the internet, encrypting your data and hiding your IP address from prying eyes. This is particularly useful when using public Wi-Fi networks or accessing geo-restricted content.
To set up a VPN on Windows 10 Pro, follow these easy steps:
Go to the Start menu and select Settings.
Click on Network & Internet, then VPN.
Select Add a VPN connection.
In the VPN provider field, choose Windows (built-in).
Under Connection name, enter a name for your VPN connection.
In the Server name or address field, enter the address of the VPN server you want to connect to.
Choose the VPN type (e.g., PPTP, L2TP/IPsec, or SSTP) and enter the appropriate details.
Enter your username and password for the VPN connection.
Click Save to save your VPN settings.
Once you have set up your VPN connection, you can easily connect to it by clicking on the network icon in the system tray and selecting your VPN connection. Your internet traffic will now be encrypted and your online activities more secure.
Setting up a VPN on Windows 10 Pro is a simple way to protect your online privacy and security while browsing the web. Whether you're at home, in the office, or on the go, using a VPN can help keep your data safe from hackers and other threats.
0 notes
Text
do norton vpn and security come together
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
do norton vpn and security come together
Norton VPN features
Norton VPN is a robust tool designed to ensure your online privacy and security. Packed with a range of features, it offers comprehensive protection for your internet activities.
One standout feature of Norton VPN is its ability to encrypt your data, keeping it safe from prying eyes. With advanced encryption protocols, including AES-256, it creates a secure tunnel for your online traffic, preventing hackers, ISPs, and other third parties from intercepting your data.
Moreover, Norton VPN offers a vast network of servers worldwide, allowing you to browse the internet anonymously from virtually anywhere. Whether you're at home, traveling, or using public Wi-Fi, you can connect to a server of your choice and enjoy unrestricted access to content while keeping your real IP address hidden.
For users concerned about streaming content from geo-restricted platforms, Norton VPN has you covered. Its servers are optimized for streaming, ensuring smooth playback of your favorite movies, TV shows, and sports events, regardless of your location. Additionally, Norton VPN bypasses censorship and firewalls, granting you access to the global internet without limitations.
Furthermore, Norton VPN prioritizes user privacy by adhering to a strict no-logs policy. This means that it doesn't track or store your online activities, ensuring that your browsing history remains private and secure.
In terms of usability, Norton VPN offers user-friendly apps for various devices, including Windows, Mac, Android, and iOS. With just a few clicks, you can connect to a server, toggle settings, and customize your VPN experience according to your preferences.
Overall, Norton VPN stands out for its robust security features, global server network, streaming capabilities, privacy protection, and user-friendly interface, making it a reliable choice for safeguarding your online presence.
Norton security integration
Norton Security Integration: Enhancing Data Security and Protection
In today's digital landscape, safeguarding sensitive data is paramount, and integrating Norton security solutions proves to be a robust defense mechanism against cyber threats. Norton, a renowned name in the cybersecurity realm, offers a suite of tools and features that fortify data security across various platforms and devices.
By integrating Norton security software, individuals and businesses benefit from real-time protection against malware, ransomware, phishing attacks, and other online risks. The seamless integration of Norton solutions ensures that all endpoints, networks, and systems are shielded from evolving cyber threats, providing users with peace of mind and a secure digital environment.
Moreover, Norton security integration extends beyond traditional antivirus protection, offering advanced features such as firewall protection, VPN services, identity theft prevention, and secure cloud storage options. These robust layers of security work in unison to create a comprehensive defense infrastructure that mitigates risks and safeguards data integrity.
Furthermore, the user-friendly interface of Norton security solutions makes integration and management hassle-free, allowing users to customize settings, perform scans, and receive real-time alerts effortlessly. Whether it's securing personal devices or fortifying an entire network, Norton's versatile security suite caters to the diverse security needs of individuals and organizations alike.
In conclusion, Norton security integration is a proactive approach towards enhancing data security and protection in an increasingly digital world. By leveraging Norton's cutting-edge technologies and comprehensive security features, users can defend against cyber threats effectively and uphold the confidentiality and integrity of their valuable data.
Unified Norton VPN and security
Title: The Integration of Norton VPN and Security: A Unified Approach to Online Protection
In an era where online security is paramount, Norton has taken a significant step forward by integrating its VPN service with its renowned security suite. This move marks a strategic shift towards offering users a unified solution for protecting their digital lives.
Norton's VPN, known for its robust encryption and secure browsing capabilities, now seamlessly integrates with its comprehensive security software. This integration not only simplifies the user experience but also enhances overall protection against cyber threats.
One of the key benefits of this unified approach is the ability to safeguard sensitive information across all online activities. Whether browsing the web, accessing public Wi-Fi networks, or conducting online transactions, users can trust that their data remains encrypted and secure.
Moreover, the integration of Norton VPN and security streamlines management for users, eliminating the need to juggle multiple applications. With a single interface for both VPN and security features, users can easily monitor and control their protection settings without any hassle.
Another advantage is the enhanced privacy offered by Norton's VPN, which masks users' IP addresses and encrypts their internet traffic. By rerouting connections through secure servers worldwide, Norton VPN ensures anonymity and protects against prying eyes.
Furthermore, Norton's comprehensive security suite provides advanced features such as antivirus protection, firewall, and identity theft prevention. By combining these capabilities with VPN functionality, users benefit from a holistic approach to online security.
In conclusion, the integration of Norton VPN and security represents a significant advancement in protecting users' online privacy and data. By offering a unified solution, Norton empowers users to navigate the digital world with confidence, knowing that their information is safe and secure.
Compatibility of Norton VPN and security
Norton VPN is a popular choice for individuals seeking enhanced online privacy and security. However, when it comes to compatibility with other security software, users may have concerns. The good news is that Norton VPN is designed to work seamlessly with various security programs, ensuring comprehensive protection for your online activities.
Norton VPN is compatible with most antivirus software, including Norton Antivirus, McAfee, AVG, and Avast, among others. This compatibility ensures that your device remains secure from various online threats while benefiting from the added layer of privacy provided by the VPN service. Additionally, Norton VPN can be used alongside firewalls and other security tools without any conflicts, allowing for a multi-layered approach to safeguarding your digital presence.
For individuals using Norton VPN on multiple devices, compatibility is essential. The service is compatible with Windows, macOS, Android, and iOS operating systems, making it a versatile choice for users across different platforms. This cross-platform compatibility ensures that you can enjoy secure and private browsing experiences on all your devices without compromising on safety.
In conclusion, Norton VPN offers robust security and privacy features while maintaining compatibility with a wide range of security software and devices. By combining the benefits of a VPN with other security tools, users can create a strong defense against online threats and enjoy peace of mind while browsing the internet.
Norton VPN and security bundle
Title: Enhancing Online Security with Norton VPN and Security Bundle
In an era where digital threats lurk around every virtual corner, safeguarding your online presence is paramount. Norton, a renowned name in cybersecurity, offers a comprehensive solution with its VPN and security bundle. By combining the power of Norton Secure VPN and Norton 360, users can enjoy enhanced protection and privacy across their digital activities.
Norton Secure VPN serves as the first line of defense by encrypting your internet connection, shielding sensitive data from prying eyes. Whether you're browsing the web, accessing public Wi-Fi, or streaming content, Norton Secure VPN establishes a secure tunnel that masks your online activities, preventing unauthorized access and potential breaches.
Complementing the VPN service is Norton 360, a robust security suite designed to combat evolving cyber threats. With features such as real-time threat protection, secure VPN, password manager, and dark web monitoring, Norton 360 offers comprehensive defense against malware, phishing attempts, and identity theft. Its intuitive interface and automatic updates ensure hassle-free security management, allowing users to stay protected without compromising usability.
Together, the Norton VPN and security bundle provide a holistic approach to online security, addressing both privacy concerns and cybersecurity threats. Whether you're a casual internet user, a remote worker, or a digital nomad, investing in reliable protection is essential to safeguarding your digital identity and sensitive information.
Moreover, Norton's commitment to innovation and continuous improvement means that users can trust their digital safety to a brand that consistently evolves to meet the challenges of an ever-changing threat landscape.
In conclusion, the Norton VPN and security bundle offer peace of mind in an increasingly digital world. By prioritizing privacy, security, and user convenience, Norton empowers individuals to navigate the online realm with confidence, knowing that their digital footprint is protected by industry-leading solutions.
0 notes