#Windows Hello Biometric Database
Explore tagged Tumblr posts
Text
Sign-in options for Windows: Ditch Password for Enhanced Security
Since I will be publishing a guide on how to setup the revamped Windows Hello available for the Windows 11 Insider Preview Build 27754 (Canary Channel). I will focus on Windows Hello sign-in options which is a more personal and secure way to sign in to your Windows device. Instead of using a password, with Windows Hello you can sign in using facial recognition, fingerprint, or security key or a…
#bypass Windows Hello#Facial Recognition#Fingerprint Authentication#fingerprint authentication bypass#Linux#MacOS#Passwords#PIN#PIN Authentication#Security Key Authentication#Sign-in options in Windows#Windows#Windows 10#Windows 11#Windows Hello#Windows Hello Biometric Database#Windows Hello exploit#Windows Hello Face#Windows Hello for Business#Windows Server#Windows Server 2012#Windows Server 2016#Windows Server 2019
0 notes
Text
youtube
Summary
🔍 Introduction to Windows Recall: Microsoft's AI-powered feature, Recall, captured and stored screenshots and user activities to allow semantic search across computer history.
🔒 Privacy and Security Concerns: Recall indiscriminately stored sensitive data like passwords, banking information, and private documents, creating a major security vulnerability.
🛠️ Technical Details:
Data stored in plaintext SQLite databases and image files in user directories.
No encryption or sufficient access control, making data easily exploitable by attackers.
🚨 Potential for Exploitation: The lack of security layers rendered it an attractive target for info-stealing malware like Redline and Jupiter Stealer.
🧩 Community and Industry Response: The cybersecurity community and privacy advocates heavily criticized Recall, leading Microsoft to revise the feature with stricter controls and encryption.
🔄 Changes in Recall: The revised version is opt-in, requires biometric authentication (Windows Hello), and incorporates enhanced encryption for stored data.
Insights Based on Numbers
💾 Data Vulnerability: Each user’s data, spanning all interactions, was stored without encryption, making over 1 billion Windows devices globally susceptible to exploitation.
📉 User Activity Tracking: Timed snapshots and extensive activity logs allowed hackers to reconstruct a user's workflow, passwords, and sensitive content.
0 notes
Text
Microsoft Recall Features Is More Hackable Than You Think

Microsoft Recall Features
Microsoft has revealed a major update to its contentious Windows 11 Recall feature. Microsoft Recall’s continual background screenshot capturing, first seen in the Surface Copilot+ PCs running Snapdragon chips, raised a flurry of privacy worries. Microsoft has changed course and made Microsoft Recall an opt-in function in response to customer feedback and security researcher discoveries.
What is remembered?
Microsoft Recall is an artificial intelligence (AI) function that lets users search for anything they’ve previously seen on their computer in an effort to improve user experience. It does this by taking regular, background screenshots using the AI capabilities built into the gadget. This generates a database of your previous actions that can be searched, allowing you to locate particular programmes, files, or even graphic components that you have previously used.
Why is there controversy?
Microsoft Recall’s operation aroused privacy concerns, even though the idea of a “photographic memory” for your PC seemed enticing. It was found by security researchers that the search data and screenshots that were taken were saved in plain text, leaving them open to access by unauthorised individuals. This raised questions about possible abuse and privacy violations, especially in light of the frequent screenshot taking.
Microsoft’s Reaction and Modifications
Microsoft recognised the issues raised by the security and user communities. Microsoft Recall announced a number of significant adjustments to address these problems in a blog post by corporate vice president of Windows and devices Pavan Davuluri.
Opt-in Feature
The most significant change to the opt-in feature is that Windows 11 devices will no longer have Recall enabled by default. Microsoft Recall can be expressly enabled by users either during setup or subsequently via system settings, giving them total control.
Improved Security
To better protect the data saved by Recall, Microsoft is putting in place stronger encryption measures. This makes sure that the screenshots and search data you took are unreadable even if someone manages to access your smartphone.
Windows Hello Integration
Using Windows Hello for Recall capability is required and adds an extra degree of protection. Via PIN, fingerprint scanning, or face recognition, Windows Hello enables biometric authentication. This guarantees that the screenshots and search history inside Microsoft Recall are only accessible to authorised individuals.
Transparency and User Control
Microsoft wants to give users more control over Recall while also increasing transparency. The feature’s operation and the data it gathers will be made transparent to users through accessible explanations. Furthermore, they will always have the option to control and remove the search history and screenshots that have been saved.
The Path Forward for Recall
Although making Microsoft Recall opt-in helps with the immediate privacy problems, there are still concerns about its long-term sustainability. Some users, particularly those handling sensitive data, may still find the basic feature of taking screenshots in the background unappealing. Microsoft Although making Recall opt-in helps with the immediate privacy problems, there are still concerns about its long-term sustainability. Some users, particularly those handling sensitive data, may still find the basic feature of taking screenshots in the background unappealing.
Here are a few current conversations about Microsoft recall:
Microsoft will have to decide how to satisfy users’ needs for privacy protection while still providing a useful search tool. Putting in place precise control over the kinds of content that Recall records could be one way to do this.
Effect on Performance
Taking screenshots in the background all the time may have an adverse effect on system performance, particularly for devices with poor specifications. In order to minimise resource utilisation, Microsoft will need to optimise the feature.
On-Device AI’s Future
Microsoft Recall is a creative application of on-device AI that improves user experience. It also draws attention to the difficulties in striking a balance between privacy issues and utility in an AI-driven future.
User experience impact
Although privacy is important, it’s important to think about the potential user experience effects of an opt-in recall. Will the lack of automated background capture make the search capability less useful for users?
The future of AI-powered search
Microsoft Recall offers an early look at operating system-level AI-powered search features. Finding the right balance between privacy and convenience will become more difficult as technology develops.
Microsoft has demonstrated a commitment to the responsible development of its AI technologies by addressing user concerns and making necessary improvements. Recall’s and related features’ future success will hinge on their capacity to provide a worthwhile user experience while upholding the strictest security and privacy regulations.
In conclusion
Microsoft took a step in the right direction by making Recall opt-in, in response to user privacy concerns. It indicates the company’s readiness to consider customer input and modify its features as necessary. Though it is unclear what the future holds for Microsoft Recall, this modification gives users greater power and allows for a more private implementation.
Remember that this is an evolving story, and that Microsoft Recall will likely undergo more improvements in the future. In order to build a more secure and user-friendly experience, Microsoft may add new features or alter current ones as they collect additional user data and input.
Read more on Govindhtech.com
#microsoft#microsoftwindows#windows11#microsoftrecall#technology#technews#news#technologynews#technologytrends#govindhtech
1 note
·
View note
Text
JOSHUA DAMIEN CORDLE
Amazon, Google, AI and us: Are we too close for comfort?
Beyond facial recognition, we're giving smart devices and platforms our intimate biometric details.
BY BRIAN BENNETT
Computers aren't just getting smarter, they're studying us more closely too. Whether it's in the name of public safety, fraud protection or simple convenience, we're feeding AI systems details that identify us and track our comings and goings.
Equipped with electronic ears, eyes and brains, a sea of devices now monitor human activity and characteristics. The list includes everything from smart speakers, laptops and phones, to even doorbells and locks. You may not have noticed this trend, but it's real, and growing.
CNET has spent the last two weeks documenting the current state of facial recognition technology, but that's just one method of gathering data directly from your person. Here are a few examples of how other biometric technologies have seeped into the fabric of daily life, and where things could go next.
Fingerprint readers everywhere
Devices that can read, capture and match fingerprints to specific individuals have been with us for decades. In 1969, the FBI began looking at ways computers could help facilitate fingerprint identification.
Back then the idea was to free as many FBI staff members as possible from this tedious, labor-intensive task. By 1975 the Bureau's efforts, aided by the National Institute of Standards and Technology, led to a functional fingerprint scanner prototypebased on capacitive sensors.
Now fast forward to 2013. That's when biometrics truly became mainstream, designed for consumer convenience, not only serious crime fighting. That year Apple integrated its Touch ID fingerprint reader into the iPhone 6, 6 Plus, and 5S. It also placed the security system in its new iPad models.
Since then both Google and Microsoft have launched similar identification solutions. Examples include Pixel Imprint for Google's Pixel phones, and Windows Hello available on Microsoft Surface laptops and tablets. Other device makers have adopted fingerprint reader technology as well. On this list of high-end handsets are the Motorola G7, OnePlus 6T, Samsung Galaxy S10, and Sony's Xperia XZ3.
All these phones, save the OnePlus 6T and Galaxy S10, use capacitive readers. They harness the same principle that the FBI did to build its early fingerprint scanner. Capacitors in the scanner measure fingertips for slight differences in electrical conductivity. The scanner then forms a finger ridge pattern from these differences.
The OnePlus 6T is quite different. Its sensor is optical, essentially a tiny camera that takes photos of fingertips. Since it creates flat, 2D images, this reader is relatively easy to fool. Not so with the Galaxy S10's ultrasonic sensor.
The S10 actively pings your finger with sound waves when it's touched, These waves bounce off skin and back to the reader for analysis. With that data, it constructs a detailed 3D image that's tougher to duplicate or spoof.
They know your voice
The smart speaker's rise in popularity is undeniable. The number of US smart speaker users is expected to swell to 76.5 million by 2020. According to eMarketer, that's up from 16 million in 2016, a compounded annual growth rate of 47.9%.
Amazon's Echo products with Alexa onboard still represent the lion's share of these gadgets. Google Assistant though is in hot pursuit. And as the companies compete for market share, the capabilities of both voice assistants has steadily increased.
hese speakers don't just listen out for your spoken commands. They can recognize, and distinguish between the voices of individual home members. That enables them to deliver personalized responses and results to match specific people.
It's a neat trick that comes in handy when you want a rundown of your personal schedule, tasks, shopping lists and so on. For this to work, you'll need to train these systems. And that means providing them with numerous voice samples. The audio snippets then find their way to remote servers for comparison, identification, fast retrieval and storage.
The eyes can't lie
Like fingerprint readers and voice recognition, iris-scanning technology has slowly crept into ordinary life. The iris, the pigmented area of the eye outside the pupil, is unique from person to person. Even individuals with the same genetic makeup -- identical twins, for instance -- will exhibit distinct iris patterns dissimilar from each other. That makes the allure of this identity confirmation technique strong.
The potentially high speed and accuracy of iris scans is also compelling. A typical scanning system consists of a digital video camera, a low-energy infrared light emitter, plus hardware and software processing.
The scanner emits an invisible IR light beam that illuminates the iris briefly. The system records the iris colors and other unique features. It then breaks the pattern down into a 256 byte code. An unknown individual's iris code is compared with a database of enrolled codes. The entire scanning, matching and recognizing process takes just a few seconds.
Some consumer devices have included iris-scanning features for years. Samsung chose Qualcomm's 3D Sonic fingerprint reader for the Galaxy S10, but the Samsung Galaxy S7, S8 and S9 phones all shipped with iris-based identification systems.
In 2017, Qualcomm entered a license agreement with iris-based authentication company Eyelock. That could be a sign this access control method will soon find a home on Qualcomm mobile processors and platforms.
Two hearts don't beat as one
Basic heart rate monitors have been a standard feature of fitness trackers and smartwatches for years. A few new devices such as the Apple Watch 4, take things a step further. Instead of merely recording heart rate, they also can take electrocardiogram (EKG or ECG) readings. This enhanced data allows the trackers to sense your heart rhythm.
EKG data is useful for many reasons. The first is greater awareness of heart health. Armed with these upgraded sensors, wearable devices can detect and alert you of potentially dangerous situations. That includes abnormal or irregular heart rhythm and even atrial fibrillation.
Another way heart rhythm is useful is its potential for biometric identification. According to company Bionym, each person's heart rhythm and EKG characteristics are unique. Bionym says that's a result of differences in heart size, position, shape, muscle conductivity and so forth. The Nymi band, a watch-sized wearable device, is Bionym's heart rhythm authentication solution.
Bionym envisions the Nymi to serve as an ultra secure biometric key. Each Nymi is linked to only one individual user and their unique EKG identification profile. Worn by its owner, the Nymi is designed to offer authorized access for registered individuals only.
Potential applications include controlling entry to sensitive office and laboratory facilities, along with tools, equipment and digital accounts. At the moment the Nymi appears targeted at enterprise customers, though it's conceivable products like the Apple Watch 4 might one day offer similar features to ordinary consumers.
Following your footsteps
It's easy to see how physical features like fingerprints can identify individuals, but what about the way you walk? Researchers at Shinshu University in Tokida, Japan have examined exactly that.
They paid close attention to the way the foot makes contact with the ground while walking. Specifically they observed the timing of heel-strike, roll to forefoot and the final push off of the toes. They also recorded pressure levels exerted by the foot during the process.
Ultimately the scientists found that these dynamic foot pressure patterns were unique to specific individuals. In fact, they were able to identify particular people using the technique with an accuracy rate of 99.6%.
Wearable technology company Motiv plans to take gait recognition out of the realm of pure research. Its $199 Motiv Ring is packed with numerous sensors to measure physical activity and biometric data. It tracks the steps you take, heart rate, and sleep time. Motiv also touts the Ring as a frictionless security device, one that provides 24/7 authentication for online accounts and transactions.
Most interesting though, is the Ring's WalkID feature. It uses the device's internal accelerometer to figure out your individual gait, and determine whether you're the person actually wearing the Ring. Currently the function remains in experimental beta. That said, it's open to all Motiv Ring owners to give it a spin.
1 note
·
View note
Text
This article will help you fix the Windows Hello Couldn’t Find Compatible Camera on Windows 10.
Among various sign-in options, Windows Hello is the latest addition. It is considered as the most secure ways of sign in to your Windows 10 computer. As it uses your compatible camera for face recognition and lets you sign in quickly.
Most of the users are struggling to with the Windows Hello issue that says:
“This option is currently unavailable -Click to know more
We can’t find a camera compatible to Windows Hello”.
So, before trying to fix Windows Hello Couldn’t Find Compatible Camera on Windows 10. You should know that Windows Hello uses infrared (IR) camera for facial recognition. And unfortunately, not most of the in-built webcam have are IR cameras. So, in this case you will be wasting your time to troubleshooting this issue.
How to Check Camera compatibility with Windows Hello?
Check Your Installed Camera in Windows 10:
In the Search box, type “Device Manager“;
Under Device Manager window, check for “Imaging Devices“.
If your system has the supported one, then it will show like “HP IR Camera” or “Intel(R) RealSense(TM) 3D Camera (R200) Depth”.
If no, then it means you don’t have an IR camera.
In that case, you need to either buy a laptop having infrared Camera or you can opt for an external webcam with facial recognition.
Here, I explained 5 ways to fix Windows Hello Couldn’t Find Compatible Camera Issue.
Updating IR Camera Drivers
Installing the Windows Hello Biometric files
Resetting Windows Hello Biometric Database
Install Windows Hello Face Optional Feature
Resetting Windows Hello sign-in
Check out all of them, and also some useful suggestion of getting an external webcam compatible to Windows Hello.
Here: How To Fix Windows Hello Couldn’t Find Compatible Camera Issue
0 notes
Text
Big Security Everywhere Thread
#WEEK_ONE
Upgrade my house so it's unbreakable
The first lecture inspired me to look upon how I can break into my house and finding useful products to try and prevent it.
(Strategic Brute Force) Via doors -> I have a double door, where one probably is trying to prevent the entrance of mosquitos, and the other is for the main protection. Both are simple and standard locks. Both are a variation of Dealt bolt locks.
https://www.youtube.com/watch?v=zMqzjMrxNR0
According to that video, it's quite easy to open.
(Brute Force) Via window -> There's absolutely no protection whatsoever. Literally could smash it.
(Brute Force) Via Basement -> Can open padlock via brute force and crawl underneath and smash the floor of the ground level .
Learning types of locks: https://locksandsafes.com/what-are-the-different-kinds-of-locks/
Understanding picking a lock: https://www.artofmanliness.com/articles/how-to-pick-a-lock-pin-tumbler-locks/
My suggestion:
Biometric locks, downside: Can leave a physical footprint (with easy combination, easy to brute force to).
Cat-eye: can see who is visiting.
Better material of glass for window (or even barred)
#WEEK_TWO
Around suburb
This week I focused on looking at my neighbourhood and if I can gather any information on my secondary family rough schedules, this way we can analyse the data of their comings and goings, and apply an attack.
Monday
The garage door opened at 8:45am [REDACTED] & [REDACTED] leaves
The garage door opened at 9:20am [REDACTED] back
The garage door opened at 11:03am [REDACTED] & [REDACTED] leaves
The side door opened at 2:20pm [REDACTED] back
The garage door opened at 3:29pm[REDACTED] & [REDACTED] back
The garage door opened at 7:54pm [REDACTED] leaves
The garage door opened at 8:20pm [REDACTED] & [REDACTED] back
Tuesday
The garage door opened at 8:20am [REDACTED] & [REDACTED] & [REDACTED] leaves
The garage door opened at 8:45am [REDACTED] back
The garage door opened at 11:02am [REDACTED] & [REDACTED] & [REDACTED] leaves
The garage door opened at 2:19pm [REDACTED] & [REDACTED] & [REDACTED] back
The side door opened at 2:30pm [REDACTED] back
The garage door opened at 5:30pm [REDACTED] leaves
The garage door opened at 5:56pm [REDACTED] & [REDACTED] back
Wednesday
The garage door opened at 8:25am [REDACTED] & [REDACTED] leaves
The garage door opened at 8:50am [REDACTED] back
The garage door opened at 1:03pm [REDACTED] & [REDACTED] & [REDACTED] leaves
The side door opened at 2:20pm [REDACTED] back
The garage door opened at 4:29pm [REDACTED] & [REDACTED] & [REDACTED] back
The garage door opened at 6:54pm [REDACTED] leaves
The garage door opened at 7:20pm [REDACTED] & [REDACTED] back
Thursday
The garage door opened at 8:00am [REDACTED] & [REDACTED] leaves
The garage door opened at 8:20am [REDACTED] back
The garage door opened at 10:00am [REDACTED] & [REDACTED] & [REDACTED] leaves
The garage door opened at 1:29pm [REDACTED] & [REDACTED] & [REDACTED] back
The garage door opened at 7:24pm [REDACTED] leaves
The garage door opened at 7:40pm [REDACTED] & [REDACTED] back
Friday
The garage door opened at 8:25am [REDACTED] & [REDACTED] leaves
The garage door opened at 9:20am [REDACTED] back
The side door opened at 2:20pm [REDACTED] back
The garage door opened at 7:24pm [REDACTED] leaves
The garage door opened at 7:42pm [REDACTED] & [REDACTED] back
After a week of looking at them (some of them I had my extended family to log, but it’s the same if someone just observes them long enough), you can formulate a pattern, and base on the pattern we can implant a pattern. To change this we introduce a new variable in the system, random activities.
We can formulate their basic life plans just by observing...which extends to a side-channel attack!
#WEEK_THREE
Around the internet
I will have you know ... the weirdest thing happened to our family ... my mother got phished.

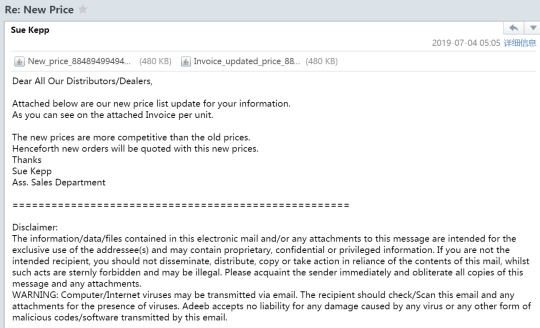
context: My mum’s business [REDACTED] usually have a lot of incoming and outgoing emails regarding price changes and new business models. This email came in and she pressed the attached documents, which windows started flashing asking for permission to access the windows/syswow64/regedit.exe.
So I started researching about the attack:
Article_one: which tells me not to worry about it.
Article_two: “This program allows users to perform several functions including creating, manipulating, renaming and deleting registry keys, importing and exporting .REG files, bookmarking user-selected registry keys as Favorites, and the ability to remotely edit the registry on another networked computer”
So to solve the problem I restored the computer at a specific checkpoint and ran a malware detection program. And nothing seems wrong.
Then I started researching the company themselves. Well, first of all, the email is extremely suspicious. and secondly, my mother never had any relation with anyone named Sue Kepp.
#WEEK_FOUR
The vulnerability of Social Media.
How often do you geotag where you are at a particular place, and really how can this affect your life. This week I focus on the vulnerability of the act of tagging where you are at a certain place. or better yet, YOU ARE subconsciously being tracked.
VIDEO_ONE | VIDEO_TWO | VIDEO_THREE... well so these guy uses Instagram to stalk someone by using the geotags they have in a nearby. They have their information just with one small outlet.
My suggestion ... maybe just not use geotag ... .. . . .... I’ve been doing this since year 8 so I’m quite clean tbh.
#WEEK_FIVE
Our university is not perfect ... yet
The other day I was walking in university and I was thinking ... How many of these people are actually UNSW students because literally, no one knows each other, and the privilege of walking into a door is guarded by a single card most of the time.
I brought my best friend to UNSW the other day, and he requested that he wants free wifi for using my internet (I said yes). Obviously, it’s fine because he is working on school work.
But there are so many people in university that could just ask for a login to steal lecture notes and even your personal information.
Someone let me access into a lab, just because they can hold the door ... . .. ..
#WEEK_SIX
Opal ... or oNO.
Transportation is always a big part of a lot of people’s life.
But the thing is, we have so many flaws, people can just jump over the gate and avoid paying
People can not tap on while going on the bus (because no one really checks, fact-checked with my uncle’s colleague -> he is a bus driver)
Your opal balance can go negatively which you can simply change for a new card. According to THIS article, opal makes a $2.6 million loss annually. Not saying that I’m can have 2.6 million, but I could save up to $36.5 if my balance is -.10 for 5 days a week.
Also -> transit officers can’t check credit card tap-ons according to THiS
Okay, so why do I care about this, well for one it’s taking $25 out of my pocket every week, so life is not good. Well secondly, NSW transit officers really made me angry the other day for stopping me and made me late for work (another incident they fined my friend who is a student but forgot their card for $200), so I put on my attacker hat on and wanted to see if there is a way to avoid paying without getting caught.
The first thing I looked through is, what powers do the new NSW transit officers have
The power to direct people to leave trains and railway stations.
The power to demand names and addresses from people who they had reasonable grounds to suspect had committed a railway offence.
The power to request to inspect tickets and concession cards.
The power to issue infringement notices and on the spot fines to those who had been caught committing railway offences.
Well, now I want to refer you to this article.
So now how do we evict to pay ... >:)
I think my suggestion would be
Get off at a specific location where there is no gate.
Use a Woolworths temporary credit card, and claim that you’re using the credit card.
If you haven't paid, they'll use your card details to charge you the default maximum fare and record your card details in their database.
if you then present the same card again on a subsequent check, they'll find you for fare evasion. Curiously, it says if this happens more than twice with the same card, they will also blacklist that card from being used to pay for fares for 12 months.
#WEEK_SEVEN
Articles that I found last few weeks
Robert Downey Jr. has vowed to use robotics and AI to significantly clean up the Earth in the next decade
There is a degree of the irony of relying on AI to help them clean up when the human responsible creating it are the one that created the chaos.
Cat filter accidentally used in Pakistani minister’s live press conference
Maybe consider not have a man in charge of these live vids, or even better have an option for serious manners and whatnot.
China Is Forcing Tourists to Install Text-Stealing Malware at its Border
Consider maybe doing an extensive search before letting people into the country instead of doing mass surveillance.
Amazon confirms it keeps your Alexa recordings basically forever
Don’t be lazy and search using your hand. This recording is allowing everyone to listen to you indefinitely.
Japan approves first human-animal embryo experiments
HELLO JURASSIC PARK!
0 notes
Text
Original Post from SC Magazine Author: Doug Olenick
Over the past decade, technology giants like Microsoft, Google and Apple have been raging an all-out war against the use of passwords with new applications for biometrics.
First came the emergence of fingerprint readers on smartphones, designed to replace PIN codes. Next came Windows Hello, allowing users to log into their computer by simply looking at built-in cameras. Then in 2017, Apple rolled out Face ID, the most sophisticated biometric authentication method for consumer devices to-date. All these technologies came to fruition with one goal in mind – killing off our reliance on passwords as a singular method of authentication. While these moves certainly improved usability, we shouldn’t be so quick to assume that a biometric is inherently more secure than a password. That’s why, as a part of WatchGuard’s 2019 Security Predictions, we anticipate that a major attack against biometrics will showcase its weakness as a single authentication factor.
The push towards biometrics as a replacement to passwords is at least grounded in logic. According to Verizon’s 2017 Data Breach Investigations Report, 81 percent of breaches leveraged either stolen or weak passwords. Password re-use still runs rampant and users are often conditioned to meet the bare minimum requirements of corporate password policies. The National Institute of Standards and Technology (NIST) even tried shaking up their password guidelines recently—removing length and complexity requirements in favor of passwords that are easy to remember but hard to guess—in an attempt to combat account takeover attacks. These changes aren’t enough to save password authentication though, thanks to ever-increasing phishing attacks and credential database breaches.
With password security at an all-time low, you might agree that the best move would be to do away with them entirely and use a biometric alone for authentication instead. Microsoft appears to be moving that way, announcing “the end of the password era” at its annual Ignite Conference in 2019, where they released password-less authentication to many of their cloud services. Instead of typing in a password to login, users instead just use their fingerprint and the Microsoft Authenticator app to access supported apps. While it’s true that you can’t choose a bad password if you don’t have to choose a password at all, biometric authentication isn’t perfect, which means there’s usually a password saved somewhere to act as a backup. If an attacker compromises that password, they can simply bypass the biometric.
Biometrics aren’t immune to attack either. Back in 2002, a Japanese security researcher was able to achieve 80 percent success fooling biometric authentication using melted gummy candies to replicate lifted fingerprints. While fingerprint reader technology has improved over the last 15 years, it isn’t without fault. Just last year, researchers from New York University and Michigan State University used machine learning to create a fingerprint “master key” with reasonable success in a simulated environment.
Attackers might not even need to use AI to generate valid fingerprints. In 2015, foreign hackers breached the United Stated Office of Personnel Management (OPM) and made off with troves of data, including 5.6 million sets of fingerprints from US intelligence agents and other government employees. These same hackers likely have access to biometric-spoofing technology more sophisticated than gummy bears as well. Worse yet, consider the fact that you can always change your password after a breach. But, how easy is it for you to change your fingerprints?
Apple’s Face ID is a good example of strong biometric-based authentication for consumer devices. While a Dutch non-profit was able to unlock 38 percent of Android devices using just a portrait photo of the owner, Face ID uses thousands of infrared dots paired with an infrared camera to build a 3D map of the user’s face, thus increasing its efficacy. That said, even Face ID isn’t perfect. It only took a group of Vietnamese hackers a few weeks, a 3D printer, and a few other inexpensive tools to create a mask that fools Face ID.
As you can see, biometrics alone, aren’t enough. Just like the passwords they replace, biometrics have their weaknesses. That isn’t to say biometrics are useless, just that they suffer from the same flaws as password-based single-factor authentication. Whether by using a 3D-printed face, creating a set of fake fingerprints, or simply cracking a weak backup password, it’s much easier for an attacker to breach an account that isn’t protected by at least two authentication factors.
Multi-factor authentication (MFA) increases security by pairing two or more different types of factors so that attackers can’t easily breach an account if one factor is stolen. The different factors should include something you are (a biometric), something you know (a password), and/or something you have (your mobile phone, a digital certificate, or a hardware token). MFA used to be out of reach for smaller, less sophisticated organizations because they usually relied on hardware tokens that were expensive, and difficult to deploy and manage. But these days, almost everyone carries a smartphone, meaning cloud-based multi-factor using mobile apps is within reach for any company.
Unfortunately, a preference for convenience and familiarity often outweigh security best practices. As such, we believe that users will continue to rely on biometrics as a single form of authentication, which will result in a major breach leveraging hacked facial recognition or fingerprint scanner technology in 2019. This major biometric hack will illustrate the weakness of single factor authentication in any form, and hopefully usher in a safer, more secure era of widespread MFA use.
When paired with another factor, like a strong password, biometrics can drastically improve security. That said, one of the most important aspects of information security to remember in 2019 is that biometrics are anything but bulletproof, making them potentially just as risky as passwords when used on their own.
Corey Nachreiner, Chief Technology Officer at WatchGuard Technologies
The post Why 2019 Will Prove Biometrics Aren’t a Security “Silver Bullet” appeared first on SC Media.
#gallery-0-6 { margin: auto; } #gallery-0-6 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-6 img { border: 2px solid #cfcfcf; } #gallery-0-6 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: Doug Olenick Why 2019 Will Prove Biometrics Aren’t a Security “Silver Bullet” Original Post from SC Magazine Author: Doug Olenick Over the past decade, technology giants like Microsoft, Google and Apple have been raging an all-out war against the use of passwords with new applications for biometrics.
0 notes
Text
We're killing off passwords. But are we ready for what will replace them?
Tech security people hate passwords because resetting forgotten passwords is the most tedious job in the world, and also they know everybody else is terrible at password security anyway.
The rest of us don’t like passwords much either, mainly because the security people won’t let us use our old favourites like 1234 or pa55w0rd. And we don’t like having to remember complicated passwords, so we write them down on a piece of paper, and then lose it. And then we have to go and ask nicely for tech to reset the password. Again.
Nobody likes passwords. Apart from the hackers who find them, steal them or crack them with ease, that is. That’s because passwords are still the keys to the kingdom in many cases; once a crook has them, there is often little else to stop them doing what they want.
Insecure, annoying, expensive — passwords would have been got rid of long ago except that the fundamental concept is easy to implement and easy to understand. But the end of the password is finally coming into view.
Most applications now offer some kind of two-factor authentication. The idea is to use something you know, like a password, plus something you have, like a code generated by an authentication app on your smartphone (or, less securely, from a text message sent by an app) is better than a password alone. That’s a positive step which should help reduce the most basic (though highly effective) security breaches which often start with people being tricked out of their passwords by phishing emails.
So what about the next step? Here smartphones are well ahead of the PC world, by using biometrics — fingerprints and facial recognition — as the standard way to log on. Something you have is replaced with something you are.
Tapping a digit on a fingerprint reader is much quicker than typing in a passcode, and raising a phone to your face to look at the screen, which also unlocks the device, is a totally natural motion. Expect this to be the way you access you PC and other devices in future, too.
Microsoft has already outlined how it plans to kill off passwords in Windows 10 using a combination of multi-factor authentication and biometrics via Windows Hello, a service it says is being used by more than 47 million people.
Earlier this year one UK bank said it was planning to trial allowing customers to access their accounts using their face or fingerprints using Windows Hello, and just this month the National Cyber Security Center, the UK’s cyber security agency, updated its guidance to say that government organisations should use Windows Hello for Business as part of their Windows 10 deployments.
All of this is good from a security point of view no doubt, and the use of the technology has been sensible, with biometrics being stored securely and locally. Fears about biometrics being stolen are probably a bit overhyped but there is a genuine risk that large databases of biometrics could pose a serious security risk.
But I’m also wondering whether there will a backlash at some point from users who are uncomfortable with making their physical bodies part of the authentication process.
I already feel a little nervous staring at my smartphone and hoping that it will recognise my face. Perhaps that’s because I’m not sure what it means if my phone decides I am not me, and the slightly queasy doubt it surfaces: who gets to choose who I am?
There is also a danger that we risk making biometrics like our face or our fingerprints a standard form of identity without thinking about the consequences. Currently, few would be willing to see face or fingerprint become the standard way of accessing government services, for example. And those aren’t the only biometrics we could use; what about your iris or your heart beat or your voice or your DNA? What does it mean to swap something private like a passport for something public, like your face? Where do we draw these lines? Who gets to choose what is used and when? Before we make the move to biometrics and wave passwords goodbye we need to have some good answers to these tough questions.
Increasing security is good, but understanding the consequences is important, too.
ZDNet’s Monday Morning Opener
The Monday Morning Opener is our opening salvo for the week in tech. Since we run a global site, this editorial publishes on Monday at 8:00am AEST in Sydney, Australia, which is 6:00pm Eastern Time on Sunday in the US. It is written by a member of ZDNet’s global editorial board, which is comprised of our lead editors across Asia, Australia, Europe, and North America.
Previously on Monday Morning Opener:
Source: https://bloghyped.com/were-killing-off-passwords-but-are-we-ready-for-what-will-replace-them/
0 notes