#Worms Using Webroot
Explore tagged Tumblr posts
Text
How To Keep My Device Free From Advanced Worms Using Webroot?
Worms they are often viewed as a threat because they aren't as danger some as viruses. However, they're wrong. the computer worm is like an actual virus on a computer, however it does not require embedding itself into programs that are available. Instead, it is able to distribute copies from one device to the next and also isn't activated through the user.

You can ensure that your device is free against advanced viruses with www.webroot.com/safe. Certain worms enter the address book for email and are able to propagate over millions of gadgets in minutes. The majority of the time the worms are infected by PC networks around the globe and slow down the internet dramatically.
Worms Cause Damage
There are worms that specifically designed to spread so that they don't interfere with the PCs they traverse. Others worms include the known as "Payload" which is actually an encrypted piece of code that is usually designed to cause harm.
Deleting files from the PC
The encryption of files is part of the exertion attack
Embed automatically into the email sent out to cause harm
The primary worm's purpose is the fact that it is embedded in the backdoor, which may be broken again by malware of other kinds and permit the developer of the worm to take control of the device infected.
Caterpillars Exploitation
Most malware attacks exploit OS weaknesses and be spread through email or ability to transmit files, which can be found on computers that are networked. They are typically found in OS components that are automated and inaccessible to you, as if you don't even know about them.
It will be aware as it performs its work, such as slowing down your computer or limiting other tasks by gaining access to system resources.
Danger Intensity of Worm: Webroot
The worm is a highly dangerous PC program that was specifically created to be transferred from one PC to the nextone, similar to emails address books. As we've already mentioned this is not an infection. It doesn't communicate with an email address or program, however it could be able to get into the PC without information of the user. Webroot internet security keeps your PC from being and make it less vulnerable.
"Worm Removal" (the three-way)
There are three methods by which you can eliminate the worms quickly and easily. All of them are described in the following paragraphs:
1- Dangerous Worm removal tool
It is the Internet Security software program will be extremely effective in ensuring that worms don't are introduced to your system. In the event you doubt there's a worm that has slipped through your PC, it is the case, you can run the Internet Security software program and will remove or block the worm, which will then infect the files on your computer.
It is recommended to try Webroot's free 60-day trial that includes a fast and reliable virus scan and an option to get rid of it.
It is recommended to try Webroot's free trial for 60 days that includes a strong virus scan and the ability to remove viruses.
2- Restart your device in safe mode
This is the other method by which you can ensure that your gadget free from malware. This way it is recommended to restart your device using safe mode. This is the manner in that your device is secure and stop unwanted bugs from causing damage to your PC.
3- Switch Internet Connection Off
It is essential should you're stuck with your internet connection, then all you have to do is turn on your Internet connection. The process of turning off your internet connection is the only way to eliminate harmful bugs.
Other than these three ways to protect your computer free of PC worms. To do this, you only need to do is move on to the next step.
Keep your PC safe from Worms
Worms have recently made up nearly eight percent of all identified malware as seen in earlier reports from 2011 which placed them third, just behind the widespread infections from Trojans and the incredibly persistent virus, and is highlighted in the study.
The worms spread exploiting vulnerabilities in the system, it is suggested that PC users maintain their internet security and software up-to-date constantly. If you've updated these software on your computer then, the majority of the worm isn't likely to infect you. it.
Webroot Anti-spyware, antivirus or firewall software running on your PC can provide complete protection against well-known worms but they should be kept up-to-date every day with most recent definitions on a regular basis. Be cautious when opening an email that is not expected or opening attachments of the files or programs ensure that you are aware of websites that contain these emails that are not known to you to keep away from viruses or worms. www.webroot.com/safe
#www.webroot.com/safe#webroot.com/safe#www.webroot.com/secure#Webroot Activate#Webroot Installation#www.webroot.com/safeinstallation#Worms Using Webroot#www webroot com safe#webroot com safe
0 notes
Text
What is Empowerment Technologies?
This blog, Empowerment Technologies, is an insight into what I have learned on our lessons about Empowerment Technologies: ICT for Professional Tracks, for 11th grade, under the teaching of Miss Shaira Denise Dela Cruz. The goal of this blog is to promote ICT and give you some insight into ICT

The first lesson that was discussed was, what is ICT? ICT is the abbreviation for Information and Communication Technologies. It refers to technologies that provide access to information through telecommunications such as mobile phones, wireless networks, telephones, and other communication mediums. The current state of ICT is WWW or World Wide Web.
The World Wide Web(WWW), commonly known as the Web, is an information system where documents and other web resources are identified by Uniform Resource Locators, which may be interlinked by hypertext, and are accessible over the Internet. It has three versions which are Web 1.0, Web 2.0, and Web 3.0. Web 1.0 is the first version and most web pages were static or “read-only web.”
The second and most used is Web 2.0, which allows users to interact and contribute with the page instead of just reading a page, the users are able to create a user account. Web 2.0 offers us five features: Folksonomy, Rich User Experience, Long Tail, User Participation, and software as a service.
The last is Web 3.0. Its aim is to have machines understand the user’s preference to be able to deliver web content specifically targeting the user. Web 3.0 hasn’t released yet as it still has some problems. Those problems are compatibility, security, vastness, vagueness, and logic.

Moving on to the next lesson which is all about ‘Online Saftey, security, ethics, and etiquette.’
The Internet consists of tens of thousands of interconnected networks run by service providers, individual companies, universities, and governments. It is defined as an information highway, which means anyone can access any information through the internet. That is why the internet is one of the most dangerous places, the reason why it is important how to keep yourself and your personal information safe. Some of the information that is in rick when spoiled on the internet are names of your immediate family, address, phone or home number, birthday, email address, your full name, and your previous and current school. It is important to keep this information top secret as cyber-creeps can use these to find you.
To keep yourself safe:
Be mindful of what you share online.
Do not just accept terms and conditions, read it.
Keep your passwords to yourself, and make sure your password is long, strong, and unique.
Do not talk or meet up with someone you don’t know.
Never post anything about a future vacation. This can signal some robbers about which date they can come and rob your house. It is better to post about your vacation when you got home already.
Add friends you know in real life, don’t accept someone you barely know or met.
Avoid visiting or downloading anything from an untrusted website, make sure to check the icon beside the search box. *picture* According to DigiCert Blog, “How to Know if a Website is Secure?”, Look at the URL of the website. If it begins with “https” instead of “http” it means the site is secured using an SSL certificate (the s stands for secure). SSL certificates secure all of your data as it is passed from your browser to the website’s server.
Make your home wifi private by adding a password.
Make sure to install and update antivirus software on your computer.
Do not reply or check links from suspicious emails as it can lead you to an untrusted site and can hack your laptop or social media.

To give you more information, here are some of the internet threats that we need to be aware of and try to avoid:
The Malware, stands for malicious software. It includes virus, worm, trojan, spyware, adware, and ransomware. The virus is the most common malware. It is a malicious program designed to replicate itself and transfer from one computer to another (internet, local networks, FDs, CDs,etc.). Worms is a standalone piece of malicious software that reproduces itself and spreads from computer to computer. The trojan is a malicious program that disguises as a useful program but once downloaded or installed, leaves your PC unprotected and allows hackers to get your information. Spyware is defined by Webroot Cybersecurity as "malware used for the purpose of secretly gathering data on an unsuspecting user." It is a program that runs in the background and spies your behavior as you are on your computer. Adware is malware that forces your browser to redirect to web advertisements, which often themselves seek to download further, even more, malicious software. Lastly, Ransomware, also known as scareware. This is a type of malicious software from cryptovirology that threatens to publish the victim’s data or perpetually block access to it unless a ransom is paid.
The Spam, this is any kind of unwanted, unsolicited digital communication, often an email, that gets sent out in bulk.
The Phishing, is a cybercrime in which a target/s are contacted by someone posing as a legitimate institution to lure individuals into providing sensitive data such as personally identifiable information, banking and credit card details, and passwords.

Lastly, before we move to the next lesson it is important to know ‘The Core Rules of Netiquette’ are excerpted from the book Netiquette by Virginia Shea.
First, Remember the Human.When communicating online, practice the Golden rule: Do unto others as you would have others do unto you. Remember that your written works or messages are read by real people, therefore you should ask yourself, "Would I be okay with this if someone else had written it?" before sending it.
Second, Adhere to the same standards of behavior online that you follow in real life. It is a must that your best to act within the laws and ethical manners of society whenever you inhabit "cyberspace." Standards of behavior may be different in some areas of cyberspace, but they are not lower than in real life. Be ethical. Don't believe anyone who says, "The only ethics out there are what you can get away with."
Third, Know where you are in cyberspace. What's perfectly acceptable in one area may be dreadfully rude in another. And because Netiquette is different in different places, it's important to know where you are. Thus the next corollary: Lurk before you leap.
Fourth, Respect other people’s time and bandwidth. Online communication takes time: time to read and time in which to respond. Most people today lead busy lives, just like you do, and don't have time to read or respond to frivolous emails or discussion posts. It's your responsibility to ensure that the time they spend reading your posting isn't wasted.
Fifth, Make yourself look good online. One of the best things about the virtual world is the lack of judgment associated with your physical appearance, the sound of your voice, or the clothes you wear. However, you will be judged by the quality of your writing so keep in mind the following tips: (1)Always check for spelling and grammar errors, (2) Know what you're talking about and state it clearly
Sixth, Share expert knowledge. The reason for asking questions online works is that a lot of knowledgeable people are reading the questions. And if even a few of them offer intelligent answers, the sum total of world knowledge increases. The Internet itself was founded and grew because scientists wanted to share information. Gradually, the rest of us got in on the act. So do your part. Despite the long lists of no-no's in this book, you do have something to offer. Don't be afraid to share what you know.
Seventh, Help keep flame wars under control. "Flaming" is what people do when they express a strongly held opinion without holding back any emotion.g. While "flaming" is not necessarily forbidden in virtual communication, "flame wars," when two or three people exchange angry posts between one another, must be controlled or the camaraderie of the group could be compromised. Don't feed the flames; extinguish them by guiding the discussion back to a more productive direction.
Eighth, Respect other people’s privacy.��Depending on what you are reading in the virtual world, be it an online class discussion forum, Facebook page, or an email, you may be exposed to some private or personal information that needs to be handled with care. Thus, Just as you expect others to respect your privacy, so should you respect the privacy of others. Be sure to err on the side of caution when deciding to discuss or not to discuss virtual communication.
Ninth, Don’t abuse your power. Some people in cyberspace have more power than others. There are wizards in MUDs (multi-user dungeons), experts in every office, and system administrators in every system. Knowing more than others, or having more power than they do, does not give you the right to take advantage of them. For example, sysadmins should never read private emails.
Tenth, Be forgiving of other people’s mistakes. Everyone was a network newbie once. So when someone makes a mistake, whether it's a spelling error or a spelling flame, a stupid question or an unnecessarily long answer, be kind about it. If you do decide to inform someone of a mistake, point it out politely, and preferably by private email rather than in public. Give people the benefit of the doubt; assume they just don't know any better.

The last lesson that was taught to us is ‘Advanced Word Processing Skill’. This lesson focuses on the software word processor the ‘Microsoft Word.’
A Word Processor is an electronic device or computer software application that performs the task of composing, editing, formatting, and printing of documents.
Microsoft Word is a word processor developed by Microsoft and the first released on October 25, 1983. Microsoft Word has features and functions which are not mostly known by others. These are the Auto-Correct, Grammar Checker, Read Aloud, Template, Thesaurus, Mail Merge, and Text Wrap.
Advance Features of Microsoft Word are discussed. Beginning with the kinds of Materials we can have in Microsoft Word.
The first is Pictures. Generally, these are electronic or digital pictures or photographs you have saved on any local storage device. There are three file formats that pictures have which are JPEG or Joint Photographic Expert Group, this can support 16.7 million colors so that it is suitable for use when working with full-color photographic images, GIF or Graphics Interchange Format, this is used for computer-generated images that support animation, can only support up to 256 colors., lastly, PNG or Portable Network Graphics, this is similar to GIF except it has smaller file size but does not support animation, it can display up to 16 million colors and allows the control of the transparency level or opacity of images.
The second material is Clip Art. This is generally a GIF type; line art drawings or images used as a generic representation for ideas and objects that you might want to integrate into your document.
The third is Shapes. These are printable objects or materials that you can integrate in your document to enhance its appearance or to allow you to have some tools to use for composing and representing ideas or messages. The fourth is Smart Art. Generally, these are predefined sets of different shapes grouped together to form ideas that are organizational or structural in nature.
The fifth is Chart. Another type of material that you can integrate into your Word document that allows you to represent data characteristics and trends.
The sixth is Screenshot. Sometimes, creating reports or manuals for training or procedure will require the integration of a more realistic image of what you are discussing on your report or manual.
Moving on to the most focused part of the lesson which is the Mail Merge. Mail Merge is a useful tool that allows you to produce multiple letters, labels, envelopes, name tags, and more using information stored in a list, database, or spreadsheet. When these two documents are combined (merged), each document includes the individual names and addresses you need to send it to. The two components of Mail Merge are the Form Document, this contains the main body of the message we want to convey or send., and the List or Data File, This is where the individual information or data that needs to be plugged in (merged) to our form document is placed and maintained.
It was demonstrated to us, how to use and make mail merge, and here’s mine:
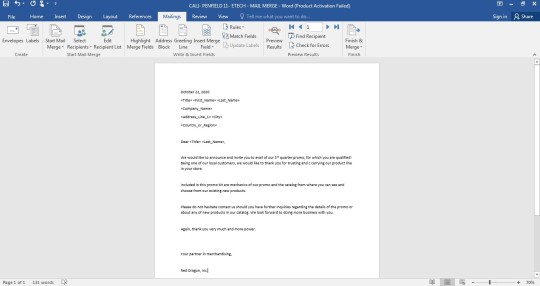

Before ending this blog, I would like to show you some of my modules for the subject Empowerment Technologies(ETech): ICT for Professional Track.
First, the open forum about the “How can you promote Netiquette?”
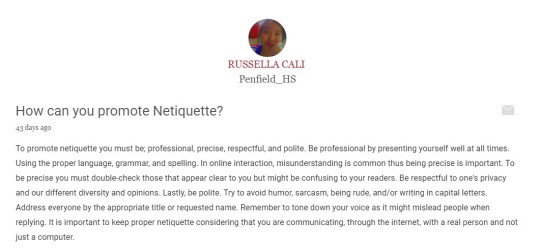
Second, an assignment about “Cyberspace: Share an experience that you have always tend to do but later did you discover that it is not a standard of ONLINE SAFETY, SECURITY, ETHICS, AND ETIQUETTE. “
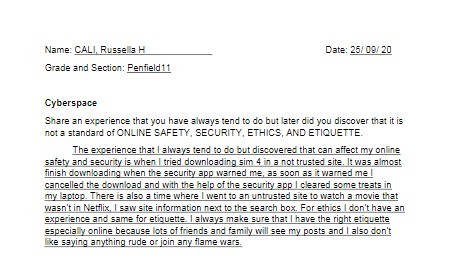
Third, another open forum about “What is the importance of Microsoft office in your education?”
Lastly is another assignment, making an Infographic: Promoting your specific track/strand. My infographic is a promotion of my strand, STEM or Science, Technology, Engineering, and Mathematics.
Hope you learn a lot from this blog as I learn a lot from my subject teacher for Empowerment Technologies(ETech): ICT for Professional Track.
Let this day be filled with success in all the ventures you make today. Have a great day!
Photo Credits:
1
https://curatti.com/wp-content/uploads/2019/11/WWW-Image-1.jpg
2
https://go4customer.com/articleimages/1581925569Safety_Internet_Day.png
3
https://futureofsourcing.com/sites/default/files/articles/internet_attacks.jpg
4
https://i.pinimg.com/originals/fc/37/e1/fc37e162244d19115d88ab58e07ccc2b.png
5
https://cdn.guidingtech.com/imager/assets/2019/05/226896/Image-Best-Microsoft-Word-Online-Tips-and-Tricks 2_4d470f76dc99e18ad75087b1b8410ea9.png?1558678050
2 notes
·
View notes
Text
www.webroot.com/safe- Enter and activate Webroot keycode
www.webroot.com/safe- Enter and activate Webroot keycode- webroot is very good anti-virus. Downloading webroot secure anywhere is a very easy process for your new and old PCs. So, please try to download and install it for your operating system. It is very good and light-weighted.
www.webroot.com/safe- Enter and activate Webroot keycode :
www.webroot.com/safe- Enter and activate Webroot keycode may be done in these simple steps :
1- So you need to open your web browser on your computer/ laptop, Web browser like Microsoft edge, google chrome, and Mozilla firefox.
2-And now you type in the Web browser www.webroot.com/safe for the first time and Webroot download. Or in case you want to reinstall it then see below the download and reinstall webroot already purchased.
3-Now put your keycode and email, then submit. Upon submitting the program will download. Run the download and follow on-screen instructions to complete the install.
This webroot is very good anti-virus. Downloading webroot secure anywhere is a very easy process for your new and old PCs. So, please try to download and install it for your operating system. It is very good and light-weighted.
webroot.com/safe- Enter and activate Webroot keycode :
www.webroot.com/safe- Enter and activate Webroot keycode may be done in these simple steps:-
1- Open a web browser on your computer/ laptop, Web browser examples are Microsoft edge, google chrome or Mozilla firefox.
2- Now type in the Web browser www.webroot.com/safe for first time Webroot download. In case you want to reinstall it then see below the download and reinstall webroot already purchased.
3- Now put your keycode and email, then submit. Upon submitting the program will download. Run the download and follow on-screen instructions to complete the install.
webroot.com/safe- Enter and activate Webroot keycode :
In case you want to reinstall Webroot that you already purchased before then you need to do one of the below- www.webroot.com/safe- Enter and activate Webroot keycode:
1- First of all, you need to log in to your Webroot account and download your product. Now install it.
2- After that, you open a Web browser and reach URL www.webroot.com/geeksquad. The Webroot will download, now run and install.
3- Then the insert your Webroot disc and run the installer.
webroot.com/safe- Enter and activate Webroot keycode-
www.webroot.com/safe- Enter and activate Webroot keycode with Guidelines:-
Antivirus and cybersecurity products from this brand are easy to use and install and can be done in a simple manner by following a few steps. The security package offered by this brand is incredibly easy to set up and install. You can easily install and upgrade any of the Webroot SecureAnywhere Antivirus products that help you handle cybersecurity in the best possible manner.
With the www.Webroot.com/Setup Product Key, you can complete the installation process all by yourself.
Here are a few troubleshooting tips for a smooth Webroot installation.
If the automatic download fails, you can call the helpline for assistance. Slow internet connections can lead to problems in downloading.
If you already have an anti-virus installed on your device, you will have to uninstall that first and remove it completely from your system.
Ensure that the latest updates are installed on your operating system so that it is compatible with the Webroot antivirus.
www.webroot.com/safe- Enter and activate Webroot keycode:
Where you easily find a webroot key code?
So now let’s get started you first of all, the Webroot security package is simple to setup & install at webroot.com/safe. Simply find a 20-character alpha-numeric code that is written on the backside of the retail card. Here may be a sample Product Key to let you understand:
xxxx-xxxx-xxxx-xxxx-xxxx
most noteworthy are providing Internet security for consumers and businesses. The company was founded in Boulder, Colorado, US, and is now headquartered in Broomfield, Colorado, and has US operations in new york.
Antivirus software such as Webroot SecureAnywhere Antivirus frustrates malware in a couple of ways. It scans data and blocks viruses that it detects. And it removes malware that is already lodged in a computer. … After a full system scan, Webroot scans a PC in a couple of minutes.
Install webroot secure anywhere with key code?
For your safety and features: www.webroot.com/safe- Enter and activate Webroot keycode :
Like most modern antivirus programs in computers, Webroot Secure Anywhere Antivirus detects malware by comparing suspicious programs found on your computer to a huge database of known malware. And then in the case of Webroot, it is not on the database and your PC, but in the cloud.
How do you get rid of installing Webroot with your existing key code?
Then click on the icon next to Webroot on the computer taskbar and choose Exit. Then go to the control panel or click on Add or Remove Programs, after that find the webroot file and click on it and then click on uninstall, after that you can restart your computer and click on Start and Programs. Click and select the Webroot folder and choose Delete.
Which is better Norton Antivirus or www.webroot.com/safe- Enter and activate Webroot keycode?
You, Norton, offers a huge scope of protection, fighting against everything from rootkits to worms. However, Webroot is more than just anti-virus software, it is antivirus software coupled with a fully developed anti-spyware suite called Spy Sweeper. … top-notch, specialized anti-spyware software is an incredible asset.
Then to find your keycode within Webroot SecureAnywhere for Mac:
Open the SecureAnywhere interface (click the Webroot icon in the menu bar, then select Webroot SecureAnywhere from the drop-down menu). Then from the main window, click My Account. A window opens with your keycode and membership information.
www.webroot.com/safe- Enter and activate Webroot keycode good for Mac?
Webroot SecureAnywhere Internet Security Plus is a single program that installs on both Windows and OS X machines and, as such, has more features than most antivirus products for Mac. But it also has the weakest malware protection of any antivirus program we have evaluated.
1 note
·
View note
Text
Webroot Antivirus and Its Main Features
Webroot is one of the most settled and trusted www.webroot.com/safe antivirus things in the Worldwide PC Security Market. Its latest Webroot Secure Anywhere Antivirus is an advanced antivirus course of action and announces the features of an antimalware also. It checks for contamination and worms endeavouring to hurt the customer's PC. It furthermore keeps an eye upon the webroot.com/safe web traffic to the customer's structure as in like manner alerts the customer against malicious goals containing spyware and worms which may exhibit to be purposeless for the PC. In addition, Webroot Technical Support is there to help the customers in any event of precarious issues.

Not in any way like diseases, spywares endeavour to take productive information from the customer's PC to send it to some else www.webroot.com/safe wanted to use it for off the mark purposes. Webroot recognizes these undercover agents and closures them from the customer's system. It moreover bars the malwares and spywares to enter the structure too. In clear sense, it shields the customer's PC from the trespassers.
The essential features of Webroot are incorporated as under:
• Easy foundation
• User genial interface
• Malware acknowledgment authority
• Free cloud space
• Gamer mode
• Multilayer security
You can likewise download the Webroot Antivirus www.webroot.com/safe Security from the given connection www.webroot.com/safe.
Webroot is light antivirus programming so it can without a doubt be presented on a PC without accumulating on a lot of room on a PC. It can without a lot of a stretch be presented by the customer yet a portion www.webroot.com/safe activate of the time a customer may find a couple of issues in foundation. Webroot Tech Support is ever arranged to help the customers in the foundation technique.
The interface used by web root is exceptionally appealing and straightforward. It empowers the customer to investigate through different applications no problem at all. Webroot shows its capacity especially in overseeing malwares and worms which are being excused by the distinctive antivirus programming. It offers the customer 1GB online space to support the data and to recoup it as and when required from any edge of the world. Gamer mode is an additional component given by this
Antivirus interface which considers the Download install webroot Secure anywhere customers with intuitive media and music related interests.
Webroot Antivirus gives the customers multilayer security from contamination and malwares. Predictable sifting and invigorating watchmen the customer's PC from contamination perils.
Despite of all the positive factors, couple of customers are also face issues with Webroot Antivirus things. Following are its couple of typical issues: –
1. Issues in presenting the Webroot thing
2. Unable to present its latest updates
3. Issue in starting the antivirus
4. Unfit to present the updated Webroot structure
In case you are going up against any of the previously mentioned or various issues with Webroot, by then it is endorsed to take help of masters instead of self-exploring as it can lead your PC to crash or various outcomes. webroot helpline number +1-800-834-6919 To enable you to out, the Webroot Technical Support is ever help accessible to its clients in a difficult situation.
TAGS
#www.webroot.com/safe
#webroot.com/safe
#www.webroot.com/safe
#www.webroot.com/safe Security
#www.webroot.com/safe activate
#Download install webroot Secure anywhere
#webroot helpline number
1 note
·
View note
Text
install webroot download windows 10
install webroot download windows 10- Activate Webroot antivirus in your PC, Andriod or Laptops and protects them from the virus, spam & malware.
How can webroot.com/safe help me?
Webroot support specialists can lend you their hands to download, install and update Webroot Spy Sweeper Antivirus on your system. We can also correct all errors that can crop up when installing and configuring Webroot Antivirus on your PC. We can help you detect and remove malicious threats, malware, and spyware by doing a quick scan of all files and folders. With our robust technology, we can delete suspicious programs and infected files from your system. Our antivirus specialists can clean up all online threats, including Trojans, rootkits, keyloggers, and worms. We can optimize the speed and efficiency of your computer and also prevent it from becoming sluggish.
And now just give us the green light to remotely access your computer via the Internet and our certified technicians can protect you from identity theft and prevent unauthorized users from accessing your computer and personal data.
Where to seek out webroot Key Code?
The Webroot security package is simple for you to set up and installs at www.webroot.com/safe. So just find a 20-character alpha-numeric code written on the back of the retail card. Then here is a sample product key to understanding you:xxxx-xxxx-xxxx-xxxx-xxxx
Welcome to install webroot secure anywhere with key code
Before you step ahead to install the software, confirm that you meet these conditions:
If you have an older version of Webroot antivirus on your System, either update it or reinstall it from the official website.
In case you have another antivirus, Uninstall it before downloading and installing Webroot safe as it might cause software conflicts and even affect a computer’s performance. Go to control panel/ settings to uninstall other antiviruses.
Make sure your computer has enough space to install the antivirus.
Before you purchase Webroot antivirus, it is essential to check for system specifications as you need to know which version of any Operating system supports a certain version of the antivirus.
If you already have been using Webroot antivirus, you simply need an upgrade and reactivate it.
install webroot download windows 10 Advantage for Businesses:
install webroot download windows 10 -Businesses require different multi-level protection as compared to private users. With smarter cyber protection, you can safeguard your employees and company with hassle multi-vector protection for desktops, laptops, virtual machines, tablets and smartphones with www.webroot.com safe especially home users. By providing Managed Service Providers with multi-vector security solutions, the Webroot Channel Edge Program promises recurring revenue, increased profitability, sales support and enablement tools. The brand’s cloud-based Threat Intelligence Services help to protect your customers with new unanticipated sophisticated online dangers. Read on to know the advantages that your business can enjoy with these services. You can try out each of these with free trials and choose the one that best suits your requirements to keep cyber threats at bay and gain complete control of your business. With Webroot Safe Install, you can protect your computers and devices.
Endpoint Protection – Endpoint protection is very crucial for every business computer and allied devices.
Countless mails have malicious attachments to phishing sites that serve as thriving ground for hackers, viruses and other malware. But if you secure your system with multi-vector protection, you can safeguard every endpoint across various users and prevent online attacks of all kinds.
Channel Edge MSP Program – This is designed to increase and improve the functioning of every business. Apart from protection you also get resources, flexible billing and easy management that is needed for flourishing your business by delivering superior services in every aspect.
Protection through Machine Learning – The Webroot Threat Intelligence platform is a cloud-based feature that aids every business with accuracy, context organizations and vendors that is needed to protect themselves as well as their customers across all online activities. Webroot Setup install helps you with antivirus installations.
1 note
·
View note
Text
download webroot already have key | download webroot with key code
Webroot is a confidential American based association that keeps you secure while scrutinizing, shopping, depends on your gadget. They give comprehensive web security deals with serious consequences regarding all your device with their assorted things. Their organizations are available for privately arranged purposes, little work environments, and tremendous associations. Webroot conveys network protection and hazard understanding advantages by keeping each and every potential danger logically whenever your structure is related with electronic space for both individual and master use. It is everything except challenging to present and use Webroot.com/safe or www.webroot. com/protected by following several straightforward steps.In a solicitation to stop disease and worm to sully your device using Webroot, run setup and present it. You can without a very remarkable stretch present and overhaul Webroot SecureAnywhere AntiVirus things.
Webroot WiFi Security has been built to introduce wellbeing while at the same time being easy to utilize. Security ascribes are naturally empowered by an establishment with no disarray or measures that are missed. Assuming that your VPN association is dropped, the kill button forestalls the transmission of your data over an unstable framework till you're reconnected to the VPN.
Utilizing Webroot WiFi Security, you'll keep up with Broomfield, Colorado, however your VPN IP address might cause it to appear to be very much like you're in any of those a greater number of than 30 countries where our VPN servers are arranged
While you're presenting the Webroot secure antivirus your own device, at the point it for the most part needs a Keycode that is given by the organization in the midst of the time of intervention. Subsequent to acquiring the antivirus you want to download, present and impel them onto your own device, as you'reenacting the thing, it will demand you 25character alpha-numericinitiation thing key/code and you want to fill at exactly that point that the antivirus is started in your edge. Keep that activation thing input at the protected area.
Regardless of the way that you start the webroot.com/safe enemy of infection, a segment of the clients can not find that Keycode, since they don't recall the essential code or maybe another explanation and by the clients are in a terrible spot. To avoid such burdens, we're attempting to give you several periods of finding that the Keycode easily and begin antivirus in their own device.
We ask you that reliably attempt to seek after the assets in an unfortunate position and save your time and occupations. The strategies are referred to under
Find Your Keycode inside Webroot SecureAnywhere for your windows:
Snap to begin the rule port substitute. As of now, tap the My Record choice. Finally, a window opens with your Keycode and moreover the enrollment information. Track down Your Keycode inside Webroot SecureAnywhere for the Macintosh: Snap to open the Webroot Secure Anyplace interface. Tap for the Me decision, appear on the essential window. By and by, a window opens with your Keycode and besides with the enrollment information. With Webroot, you are outfitted with top notch web security for all of your contraptions and for all kind of up close and personal and master use.
1 note
·
View note
Text
how to update webroot secureanywhere & webroot secureanywhere download
Activate Your Webroot Com Protected on your PC, PC, Cell phone, etc and secure your contraptions. We should Get everything rolling with Webroot Protected at webroot.com and Activate Webroot Safe.
As we are going also developed overall around mentioned, it other than turns out to be more major to stay secured. It is to an extraordinary degree fundamental to guarantee your laptops, computers, phones and tablets. This multitude of web security methodologies, affirmation against tarnishing, malware, and Ransomware is given by Webroot.Webroot is a confidential American based connection that keeps you secure while looking at, shopping, subject to your device.They give expansive web security deals with any consequences regarding all your contraption with their unquestionable things. Their administrations are open for subtly settled purposes, little work environments and colossal affiliations. Webroot passes on digital protection and danger understanding administrations by keeping each potential risk relentlessly whenever your structure is associated with robotized space for both individual and pro use.
How to Install Webroot SecureAnywhere Antivirus on your Gadget?
It is verifiably easy to introduce and use Webroot.com/safe or www.webroot.com/protected by following a couple of central steps.In solicitation to stop sickness and worm to destroy your contraption using Webroot, run arrangement and present it. You can pure and simple present and invigorate Webroot SecureAnywhere AntiVirus things.
Here are two or three direct walks to search for later: ? You can either buy Webroot on the web or from a retail store close you.
? RUN the arrangement using Album or DVD or by downloading it on the web. You will require an alright web partnership.
? Presently, you ought to be given a 20 digit alpha-numeric code, this code is thing key. In case you accelerated Webroot the web, you will find thing scratch on the retail card. Of course in the event that there ought to rise an event of online purchase, what key is given to you on your chose Email Id.
? Utilize this intriguing thing key and present Webroot adequately on your contraption.
With Webroot, you are given a-list web security for each and every one of your contraptions and for all kind of extremely close and expert use. It is possible to stand up to a couple of issues while presenting Webroot on your Gadget. You can search for after two or three examining tips and present Webroot burden free whenever.
? Yet again if your download stopped, really look at your web coalition and endeavor.
? Make without question you have in the current style Working Framework presented on your contraption.
? In the event that your design has some one of a kind Antivirus or security structure showed then uninstall it. This can square while downloading and presenting Webroot.
? Feel permitted to call Webroot support absolute whenever, they will help you with your pressure.
Stay Safeguarded Whenever Anyplace Webroot.com/safe outfits a wide mix of administrations with their differentiating things. With Webroot find cloud-based security to stop dangers effectively and guarantee business and buyers in the connected world. This alliance hopes to offer security to each and every fragile datum the entire course over your sorts or iOS device, Windows contraption what's more Android device.
? Examine your system, empty ailment, spyware and potential danger moreover, become shown about vindictive districts.
? Fix, explore and determine issues related to Webroot.
? Update your thing for improved results and remain guaranteed.
? Install and Reinstall Antivirus.
? Go to Webroot setting and once again endeavor it, to arrange your necessities.
1 note
·
View note
Text
Webroot mac antivirus review

WEBROOT MAC ANTIVIRUS REVIEW FOR MAC
WEBROOT MAC ANTIVIRUS REVIEW SOFTWARE
WEBROOT MAC ANTIVIRUS REVIEW TRIAL
The samples included all types of nasty malware, including worms, Trojan horses, keyloggers, ransomware, zero-day malware, and so on. Although it took a while, I enjoyed watching the best antivirus programs detecting and eliminating the samples.
WEBROOT MAC ANTIVIRUS REVIEW SOFTWARE
Then I fired up the big guns – I executed all malware samples I had gathered and left each security software do its job.
All these antivirus tests delivered satisfactory results – the antivirus solutions prevented almost every dangerous download and access to infected content. I fed my browsers with dozens of randomly selected phishing URLs that I got from PhishTank.
I moved on to testing the apps’ real-time anti-phishing capabilities.
I found the list of malicious websites thanks to Artists Against 419, Malware Domain List, and Scumware.
I tested each app’s ability to block malicious and infected URLs.
If you wonder how to test an antivirus, this is where you should start. Naturally, all my best antivirus picks detected the file as a threat.
First of all, I downloaded the EICAR test file.
I checked out each antivirus software’s security features, including multi-layer protection, the technique they use to detect malware, and so on.
I started testing each antivirus based on several criteria.
The collection included malicious software for Mac, Windows, and Android.
I downloaded hundreds of malware samples from Objective-See, Kernelmode, and Contagiodump.
I also used a Huawei Smart Z and an iPhone 7 to find the best phone antivirus on the market. To test each antivirus on an Apple device, I used a MacBook Air.
For the antivirus comparison and tests, I used an HP Pavilion DV6 laptop with Intel Core i7-2670QM 2.20 GHz and 8 GB RAM.
I purchased a license so I can test it first-hand. Excluding Norton 360 Deluxe, since the company doesn’t offer a free trial.
WEBROOT MAC ANTIVIRUS REVIEW TRIAL
When I was satisfied with my 10 best antivirus picks, I signed up for a trial for each of them.
I read hundreds of user-written antivirus reviews to see if any of my top picks have any unsolved issues.
My goal was to find the best budget antivirus suite for under $50 per license. In addition to the ones I’ve already used and trusted, I added a dozen more.
I scanned the Web for all worthy antivirus solutions.
However, Avast terminated Jumpshot’s operations, so this practice is no longer in action.Īnyways, below you’ll find out the process I followed to find the best antivirus for 2021. Let’s get something out of the way first.Ī recent investigation revealed that one of Avast’s subsidiaries, Jumpshot, was selling browsing data gathered by Avast and AVG’s free antivirus versions.
Best Electric Garage Heaters 120V for 2022.
7 Best Bluetooth Speakers for Outdoor Party for 2022.
WEBROOT MAC ANTIVIRUS REVIEW FOR MAC
7 Best External Hard Drives for Mac For 2022.10 Best Shallow Mount Subwoofer Models for 2022.12 Best Drawing Tablets for Beginners and Pros in 2022.8 Best Microphones for Streaming for 2022.11 Best Budget Studio Monitors for 2022.9 Best Motherboard for Ryzen 7 3700X for 2022.

0 notes
Text
Help! I Think I Have a Virus on My Computer... Pt. 1
Have you ever turned on your computer and thought to yourself, “How long have I been staring at this loading bar / spinning beach ball / window accordion?”

Or maybe when you’re typing you feel like the keys are slow to respond or have a mind of their own?
Well, those are definitely things to be concerned about on a computer, but it doesn’t necessarily mean that there’s malware on the device itself. While there is no 100%, fool-proof way, to know if your machine is infected with malware such as a virus or worm - there are some steps you can take to take care of these symptoms and remove any infected files in the process.
As a nerdy computer technician who’s had their hands on thousands of gadgets over the past 20 years, I can give you some good news right here, right now:
Malware is rarely the reason for the unexpected and frustrating things happening while you’re using your computer.
I know, I know. Many of you won’t believe me.

But think about it this way. When you’re not feeling well - perhaps sluggish and stuffy - is it always because you’ve caught a virus? Sometimes, it’s seasonal allergies, a reaction to new vitamin or supplement, or just a change in diet or routine.
Just like our bodies, computers have their own set of reasons to act up on us. Perhaps you’re due for a software update, need to clean up unnecessary files and free up disk space, or just need a tune up to make sure that all your system files are in order and working properly.

But Agent Baran, what if I’ve done all those things and my computer is STILL lagging, closing programs down, and all around acting like a possessed robot?
Well, then maybe it’s some kind of malware. But, still, it’s hard to tell unless you’re an expert. Even Anti-virus programs are not 100% accurate in detecting and removing malware.
Malware is constantly evolving because it is easy for hackers to change the code in a malicious program and make it harder to detect once they realize their files are being flagged by anti-virus programs. Because these changes often happen from a variety of different sources, AV programs have a hard time keeping databases up-to-date with the newest types of spyware, adware, and ransomware. As a result, a lot of malware can stay completely hidden on a system for a long time.

The longer a malicious program is running on a computer, the more damage it does over time to the machine. And to many people’s surprise, many times the user won’t notice any issues with their device until AFTER a virus has been removed.
Maybe they do a monthly virus scan or have just downloaded a new AV program that has detected the malicious files. The AV removes every trace that it can find, but some hackers have gotten smart and injected a piece of code into the program that if it’s program files are removed, so are some important system files. That way, when the device is restarted and these changes are applied, the computer is either in really poor shape or completely inoperable.

Some common signs of malware:
- Your antivirus program such as Windows Defender, Malwarebytes, Trend Micro, Webroot, etc, alert you that there is malware on the computer AND you are absolutely sure that it is not a false positive.
-Your documents, photos, or other files suddenly start disappearing or become encrypted so that then you try to open them, they don’t work.
-Your computer fans are running all the time (perhaps even getting loud and obnoxious), the computer is always and shutting off intermittently without cause or warning.
-When you search things on the internet, you get redirected to strange sites that don’t seem related and that you know you haven’t clicked on yourself.
-There are programs on your computer that you don’t recognize.
-Your command prompt/ Windows Powershell pops up at start up and quickly disappears.

That’s it for now folks. Stay tuned for Pt. 2 where I talk about some of the ways that you can remove malware on your own and how to protect your devices from malicious attacks in the future.
Keep in mind, 9/10 times people without tech knowledge find it easier and more cost-effective to take their device to a technician for diagnostics and repairs rather than taking on the complicated and frustrating task of doing it themselves. This is especially important if there are important files on the device. Don’t mess around if you can’t afford to lose it for good.
As always, go ahead and like, share, follow and all that good stuff. And if you’re having issues, ask me your tech related questions here and I’ll try to answer them to the best of my knowledge.
I have a demanding job outside of the internet, so please be patient when it comes to replies and new posts. If you would like to fuel me in making content more frequently and consistently, you can go ahead and send me a fiver for a cup of coffee on Venmo @barely
#tech tips#computer virus#malware#ask a computer nerd#ask a technician#agent baran#pt 1#tech talk#basic computer course#tech for beginners#windows 10#tech support
1 note
·
View note
Text
windows 10 install webroot with key code
Welcome to our support page, get quick support for windows 10 install webroot with key code.
“Windows 10 install webroot with key code is more than just antivirus software. It can quickly block viruses, malware, spyware or cyber threats other malicious files attempting to get entry into your device. Visit webroot.com/safe for any issue/error associated with any antivirus installed on your system or device.”
How can webroot.com/safe help me?
You can lend your hand to your Webroot support specialists to download, install and update Webroot Spy Sweeper Antivirus on your system. We can also fix all the errors that can crop up when installing and configuring Webroot Antivirus on your PC. We can help you detect and remove malicious threats, malware, and spyware by doing a quick scan of all files and folders. With our robust technology, we can delete suspicious programs and infected files from your system. Our antivirus specialists can clean up all online threats, including Trojans, rootkits, jugglers, and worms. We can optimize the speed and efficiency of your computer and also prevent it from becoming sluggish.
And just give us the green light to remotely access your computer via the Internet and our certified technicians can protect you from identity theft and block unauthorized users from accessing your computer and personal data…
Where to search for Webroot Key Code?
The Webroot security package is simple to set up and installs at webroot.com/safe. Just find a 20-character alpha-numeric code written on the back of the retail card. Here is a sample product key to understanding you:
XXXX-XXXX-XXXX-XXXX-XXXX
“Get Instant webroot safe Support for Installation.“
How to windows 10 install webroot with key code?
Install Webroot Antivirus: windows 10 install webroot with key code –
Go to your Webroot Geeksquad Antivirus Download page.
Then, first of all, open the web browser.
After this, search www.webroot.com/safe.
Then download the wsainstall.exe installation file.
And after you complete the download process
After this, the download file will be shown.
After that, you install wsainstall.exe, then webroot software.
Then download the wsainstall.exe installation file.
You must enter a 20-digit alphanumeric product key to install your web code with the key code.
Then follow all the instructions that are seen on the screen, to secure Webroot.
Features of Windows 10 install webroot with key code:
Identity Theft Protection: WebRot protects your identity from being stolen. Your identity includes usernames, account numbers, passwords and other personal information against spyware, malware, and other viruses.
Safe browsing with real-time anti-phishing.
Password and login security: WebRot protects your personal data such as passwords, usernames and credit card information to keep you safe online.
Mobile Security: Webroot provides security for Android phones with secure web browsing.
Lightning Fast Scan: Webroot scans all data very fast and takes up to 20 seconds.
Webcam security: Webroot provides you with webcam security.
System Optimizer: This is a system maintenance tool that deletes previous activities such as browsing history, temporary files, and cookies to protect your privacy.
It provides automatic backup and secure online storage.
Some common Webroot you may encounter: windows 10 install webroot with key code-
If you encounter any of the following problems while installing your Webroot product, it means that your device is suffering from compatibility issues: windows 10 install webroot with key code-
Frequent pop-ups on your computer.
Then after that your hard disk crashes.
After that the loss of your important data.
Then you keep losing the network connection.
And your automatic operating system reboot.
Now your applications slow response.
Then your system freezes or hangs.
Now your touchpad, mouse or keyboard is not working.
After that, your app is not responding.
Then sensitive files get hacked.
Now you can always connect with a customer support executive to help you fix it no matter what the error is.
Problems without antivirus in computer or laptop: windows 10 install webroot with key code-
Problems you have without your Webroot antivirus are safe or critical information may get compromised, our computer performance slows down, the operating system reboots automatically, unwanted annoying popups keep coming up, important Data information is lost, the operating system is corrupted, our computer system may not work properly, computer system Hard disk crashes, system wireless drivers tend to stop working, the computer system wireless and cable can not detect the printer does not work webcam of computer systems and computer touchpad does not work properly.
HOW TO INSTALL WEBROOT ANTIVIRUS ON YOUR DEVICE?
It is very easy to install and use Webroot.com/safe or Webroot antivirus software download by following a few easy steps. In order to stop viruses and worm to infect your device using Webroot, run setup and install it. You can easily install and upgrade Webroot SecureAnywhere Anti-Virus products.
Here are a few easy steps to follow:
You can either buy Webroot online or from a retail store near you.
RUN the setup using CD or DVD or by downloading it online. You will need a good internet connection.
Now, you must be provided with a 20 digit alpha-numeric code, this code is product key. In case you brought Webroot online, you will find the product key on the retail card. Or in case of online purchase, the product key is given to you on your registered Email Id.
Use this unique product key and install Webroot successfully on your device.
1 note
·
View note
Text
register webroot with key code
Welcome to our Support Page, Get Instant help for Webroot.com/safe,Download,Install & Activate with the key code.

Antivirus software such as register webroot with key code Antivirus frustrates malware in a couple of ways. It scans data and blocks viruses that it detects. And it removes malware that is already lodged in a computer. After a full system scan, Webroot scans a PC in a couple of minutes.
Where to seek out webroot Key Code?
The Webroot security package is simple to setup & install at www.webroot.com/safe. Simply find a 20-character alpha-numeric code that is written on the backside of the retail card. Here may be a sample Product Key to let you understand:
xxxx-xxxx-xxxx-xxxx-xxxx
How can webroot.com/safe help me?
Webroot Support experts can lend their hand to download, install and update Webroot Spy Sweeper Antivirus on your system. We can also repair all errors that may crop up while installing and configuring Webroot Antivirus on your PC. We can help you detect and remove malicious threats, malware, and spyware by performing a quick scan of all files and folders. With our robust technology, we can destroy suspicious programs and infected files from your system. Our antivirus experts can clean all online threats, including Trojan, rootkits, keyloggers, and worms in the just single sweep. We can optimize your computer’s speed and efficiency and also protect it from being sluggish.
Just give us the green light to remotely access your computer through the Internet and our certified technicians can protect you against identity theft and block unauthorized users to access your computer and personal data.
SERVICES REQUIRED FOR WEBROOT COMPUTER: register webroot with key code
While Webroot Antivirus installation/uninstallation.
Also, update Webroot Security.
And in Webroot Antivirus re-installation.
Also inWebroot Antivirus error fixation.
In Webroot Antivirus product activation.
Computers scan for the threats to analyze the virus infections.
In Configure Webroot Antivirus settings as per system requirements.
Security setting for complete protection.
Repair Webroot Antivirus.
In Fixing Webroot firewall and network conflicting problems.
While Fixing Blue/black screen of death PC
Also to fix Display problems
Fix Sound issues with Desktop / Laptop
In Wireless Internet configuration/cable connections in PC/Laptops
How do I download Webroot?
Mac Installation Instructions — register webroot with key code:
Click on the DOWNLOAD NOW (Mac) link for your product version.
Double-click Webroot SecureAnywhere app to open the installer.
Drag the Webroot SecureAnywhere icon into the Applications folder.
Open the Applications folder by double-clicking the folder icon.
Is Webroot any good?
Antivirus software such as Webroot SecureAnywhere Antivirus frustrates malware in a couple of ways. It scans data and blocks viruses that it detects. And it removes malware that is already lodged in a computer. After a full system scan, Webroot scans a PC in a couple of minutes.
register webroot with key code AntiVirus (2020) :
Installers and programs are incredibly tiny. Very fast scan. Perfect score in my malware-blocking test. A very good score in my malware removal test.
Bonus antiphishing protection less effective. Bonus security tools too advanced for the average user.
Webroot SecureAnywhere Antivirus is tiny beyond belief, yet it achieved perfect scores across the board in my malware-blocking tests. It also did a very good job cleaning up malware-infested systems. This impressive product shares our Editor’s Choice honor with Norton AntiVirus 2020.
1 note
·
View note
Text
Reinstall Webroot with key code: Simple Procedure to Reinstall
Webroot Antivirus and Its Main Features
With the developing utilization of PCs and Internet, PC security issues are springing up as are mushrooming antivirus arrangements on the lookout. Regular a new antivirus item is dispatched in the market with 1,000 vows to defend a client's PC.
Webroot is one of the most seasoned and trusted antivirus items in the Worldwide PC Security Market. Its most recent Webroot SecureAnywhere Antivirus is a high level antivirus arrangement and declares the highlights of an antimalware as well. It checks for infection and worms attempting to hurt the client's PC. It likewise keeps an eye upon the web traffic to the client's framework as additionally cautions the client against pernicious destinations containing spyware and worms which might end up being purposeless for the PC. Besides, Webroot Technical Support is there to help the clients in any case of dangerous issues.
Not at all like infections, spywares attempt to take important data from the client's PC to send it to some else expected to utilize it for unreasonable purposes. Webroot distinguishes these government operatives and ends them from the client's framework. It likewise bars the malwares and spywares to enter the framework as well. In evident sense, it protects the client's PC from the intruders.
The fundamental highlights of Webroot are included as under;
• Simple establishment
• Easy to use interface
• Malware recognition skill
• Free cloud space
• Gamer mode
• Multi-facet security
Webroot is light antivirus programming so it can undoubtedly be introduced on a PC without hoarding on much space on a PC. It can without much of a stretch be introduced by the client yet now and then a client might track down certain issues in establishment. Webroot Tech Support is at any point prepared to help the clients in the establishment method.
The interface utilized by web root is very alluring and easy to use. It permits the client to explore through various applications effortlessly. Webroot shows its ability particularly in managing malwares and worms which are being disregarded by the other antivirus programming. It offers the client 1GB internet based space to reinforcement the information and to recover it as and when required from any edge of the world. Gamer mode is an extra component given by this Antivirus interface which obliges the clients with interactive media and music related interests.
Webroot Antivirus furnishes the clients with multi-facet protection from infection and malwares. Consistent filtering and refreshing protects the client's PC from infection dangers.
In spite of the multitude of positive elements, not many clients are additionally face issues with Webroot Antivirus items. Following are its couple of normal issues: -
1. Issues in introducing the Webroot item
2. Incapable to introduce its most recent updates
3. Issue in actuating the antivirus
4. Incapable to introduce the updated Webroot form
In the event that you are confronting any of the abovementioned or different issues with Webroot, then, at that point, it is prescribed to take help of specialists rather than self-investigating as it can lead your PC to crash or different results. To take care of you, the Webroot Technical Support is the handiest at any point help accessible to its clients in such any difficulty.
1 note
·
View note
Text
Using the Nessus Vulnerability Scanner
This article will show you how to access the Nessus vulnerability scanner for free. This article will also teach you how to download the Nessus vulnerability scanner, follow the instructions, and run a scan. It will help you identify the root cause of any system problems and pinpoint the critical ones.

Each Tenable Nessus plugin is described and explained. Tenable Nessus Web Parental Control will be my first topic. Tenable created this web filtering and monitoring tool, and it is currently used by many web hosts. You can use it in combination with Nessus scanner engine for parental control, URL masking, and URL masking. Nessus' web parental control is simple to setup and runs in the background throughout your sleep.
Next is the Tenable Nessus Scanning Tool. It is an extremely basic scanner and can be used for checking your computer for known threats. You can download the free version of the tenable edition from this website. Once downloaded you can set it up with the step by step instructions that are given along with a manual of instructions for further guidance.
The FreeNIS Security Suite, FreeNIS Live Protection Suite and other Nessus vulnerability scans are also readily available. The scanners can only be installed on-premises, while others such as Nessus can be run from a virtual machine. You might also consider other open-source products.
DSE Pro is one of several popular vulnerability scanners currently available on the internet. Proofpoint, Cylance Webroot Intermediate or DSE Pro are also options. DSE Pro can be downloaded for Linux as well Windows Operating Systems. Cylance only works for Windows. The next option on our list is the free trial of Proofpoint Internet Security, which has been designed by a group of Canadian professionals. The software allows you to instantly access an online scan which identifies any threats to your computer. It also provides detailed logs that detail what it did and the results. Unfortunately, the free scan will only show you a small portion of what is on your computer screen.
Once you have run the scan, make any changes necessary to your system and then start the Nessus vulnerability scanner software. Nessus usually generates a log of all problems after a thorough vulnerability scan. In this log you can follow exactly what was open or erroneous on your system before the vulnerability scan took place. The advantage of running a vulnerability scanning on a live network is that you can instantly respond to the results of your scan in the case of a problem. To identify all the issues, you will need to restart the network if you do it with a live network.
Nessus scanners for computer security are very beneficial. The Nessus scanner is able to detect and stop worms from infecting servers before they do any real damage. A few scanning methods will quickly report abnormalities such as this so you can get the necessary remediation. Nessus can automatically update and download security patches, one of its other benefits.
Nessus products can be used in a variety of different scanning environments. Realize that just because a scanner identifies anomalies, that does not mean the server is vulnerable to attack. This is because some Nessus scans may reveal hidden worm infections. It is important that your network be scanned regularly to ensure security.
0 notes
Text
Is Webroot Capable To Provide Hacker Protection To Devices? - www.webroot.com/safe
Hacking stands for comprise private accounts, computer systems/networks, or digital devices. Hackers often use technology or other related knowledge to overcome a problem. Hackers can compromise a computer or network, resulting in security hacking. Hackers are often portrayed by the media as hackers who steal data. Webroot antivirus provides excellent protection against hackers and is considered the best security software. www.webroot.com/safe

Hackers Attack Protection: Keep Ransom Seekers and Hackers Away
Improved Firewall
Webroot is now equipped with the Enhanced Firewall to protect your computer from hackers. It monitors who and what comes into and out of your computer. Ransomware protection adds an extra layer of protection against the ever-increasing Ransomware attacks. This means that no one can access any private or sensitive data, files or photos.
It easily bounces hackers, snoopers and criminals trying to get onto your PC to steal private photos, files and passwords. It can be used on both wireless and wired networks.
Ransomware Security
It protects your personal files, photos and files from malicious encryption. You can also have complete control over any apps that could modify or delete your files.
This security software also includes additional features to ensure complete computer security.
Computer Security
Advanced antivirus scans for viruses and eliminates all Ransomware, rootkits and spyware. It can detect threats even before they reach you, as it works in real-time. It is important to protect your USB and DVD drives as quickly as possible. Take a look at these features to get comprehensive protection.
Advanced Antivirus - This scans every corner of your computer in real time for viruses, worms and spyware. For those rare occasions when your computer is not available, you can also schedule whole-PC scans.
AI Exposure - It uses advanced artificial intelligence to run on your computer and examine malware samples proactively that haven't yet been cataloged by any other security software.
PUA Scanning - This scans for potentially unwanted programs that you may have accidentally downloaded. It includes adware and malicious software that is bundled with the downloaded program.
Cyber Capture - It is equipped with cloud-based technology to stop advanced malware variants and outbreaks instantly. It uploads any unknown threat to our Threat Labs team. The security update will be sent to all users and provides greater protection.
Behavior Shield -This feature works just like an alert watchman and detects suspicious behavior in any software running on your computer. It will alter you if it is wrong. This protects against malicious programs, 0-day threats, and keyloggers, which can record passwords and bank account details without your knowledge.
Turbo Scanning - This reduces scanning time by skipping files if they are safe and secure to open. The real-time updates ensure your security is always up to date by pushing security updates and bug fixes to keep you safe.
Silent Mode -The silent mode will delay the updates and scans to prevent interference while you're working, watching videos or playing games.
These outstanding features will ensure your device is completely secure and safe. If you feel that the security software is causing problems, you can contact Webroot Support Phone Number for immediate assistance. webroot.com/safe
#www.webroot.com/safe#webroot.com/safe#www webroot com safe#Webroot.com/geeksquad#www.webroot.com/secure#www.webroot.com/safeinstallation#webroot geek squad#Webroot Activate#Webroot Installation
0 notes