#api security
Explore tagged Tumblr posts
Text
Protect every API, at every stage!
Accelerate the detection of critical API vulnerabilities through automated scanning, priority-based analysis, and CVSS-tagged reporting. Scan smarter with automated, risk-based API testing that supports OpenAPI specs and real-world authentication. Schedule scans at scale, plug into your CI/CD pipeline like Jenkins, and manage pentest requests all in one place. Stay ahead with SLA-driven alerts that keep security on track.
1 note
·
View note
Text
0 notes
Text
Secure Your APIs with ForgeRock Identity Gateway: API Security Best Practices
The ForgeRock Identity Gateway is a powerful tool for securing APIs, allowing developers to protect their applications from various types of attacks. However, implementing API security best practices is crucial for ensuring the integrity and confidentiality of your data. In this article, we will explore the importance of API security and provide a comprehensive guide to securing your APIs with the ForgeRock Identity Gateway. API security is a critical aspect of application development, as APIs are often the primary entry point for hackers. A single vulnerability in an API can compromise the entire system, resulting in data breaches, unauthorized access, and reputational damage. To mitigate these risks, developers must implement robust security measures, such as authentication, authorization, and encryption. The ForgeRock Identity Gateway offers a range of features that enable developers to secure their APIs effectively. These features include: * Authentication and authorization: The ForgeRock Identity Gateway provides a robust authentication and authorization framework, allowing developers to control access to their APIs and ensure that only authorized users can access their data. * Encryption: The gateway supports various encryption algorithms, such as SSL/TLS, to protect data in transit and at rest. * Rate limiting: The gateway includes rate limiting features that prevent brute-force attacks and denial-of-service (DoS) attacks. * Logging and monitoring: The gateway provides detailed logging and monitoring capabilities, enabling developers to detect and respond to security threats in real-time. To secure your APIs with the ForgeRock Identity Gateway, follow these best practices: * Implement authentication and authorization: Use the ForgeRock Identity Gateway's authentication and authorization features to control access to your APIs. * Use encryption: Enable encryption for data in transit and at rest to protect your data from interception and tampering. * Limit API requests: Use rate limiting features to prevent brute-force attacks and DoS attacks. * Monitor your APIs: Use the gateway's logging and monitoring capabilities to detect and respond to security threats in real-time. By following these best practices and leveraging the features of the ForgeRock Identity Gateway, you can secure your APIs and protect your data from a range of threats. Visit IAMDevBox.com for more information on API security and the ForgeRock Identity Gateway. Read more: https://www.iamdevbox.com/posts/
0 notes
Text
ELTFV Scam Prevention: Avoiding API Permission Vulnerabilities
With the advancement of cryptographic technology, more users are utilizing APIs to automate trading strategies or connect to third-party services. This convenience has also become a target for scammers. Fake API key scams are on the rise. Scammers steal user assets by creating fake platforms, tampering with transaction records, or luring users to upload API keys. ELTFV Exchange continually monitors these emerging risks and has built a systematic security protection system to maximize the privacy and integrity of user APIs.

Avoiding Psychological Vulnerabilities
Current API scams mainly focus on phishing platforms and disguised third-party services. The ELTFV scam prevention guide warns that scammers may clone the interfaces of well-known exchanges to trick users into entering API keys and access permissions. They may even use social engineering tactics to impersonate bot trading assistants to gain user trust.
If users authorize read permissions or enable trading functions, scammers can bypass regular login verification to conduct high-frequency trading or transfer assets directly from the account. Once the key is leaked, users cannot stop operations through traditional password modification methods, as API operation permissions can bypass the interface, making it difficult to detect and track in real time.
API Permission Settings
The ELTFV scam prevention guide reminds users that many have a limited understanding of APIs and often enable all permissions by default when generating keys, including account information reading, order placement, and even asset withdrawal. This provides opportunities for scammers. By exploiting these permissions, scammers can automate the sale of assets from controlled accounts, leading to significant financial losses for users.
Scammers may exploit vulnerabilities in legitimate third-party services by embedding malicious code to monitor user API interactions and steal keys. In such cases, even if users operate on legitimate platforms, they may be hijacked by browser plugins, API proxies, and other intermediaries.
Building API Protection Mechanisms
In response to the increasingly complex API scam ecosystem, ELTFV Exchange has introduced systematic countermeasures. The platform enforces strict security standards in user API management and security settings. When users create APIs, the system defaults to opening only "read" permissions, requiring manual activation for other operations to prevent accidental misuse.
The platform enforces binding to user-trusted server IPs to prevent API keys from being misused by external devices. Users can view API call records at any time to identify abnormal operations and unauthorized access promptly. If abnormal API behavior is detected, the interface will be automatically frozen, and the user will be notified. All API keys are encrypted with industry-standard AES-256 algorithms to ensure data is not leaked during storage.
ELTFV Exchange regularly audits third-party applications partnered with the platform and encourages users to access API services through officially recommended channels, reducing indirect security threats from external tools.
Enhancing Security Awareness
ELTFV Exchange advises users not to trust any third-party platform requests for API keys, to change keys regularly, and to clear unused interfaces. Investors should remain vigilant with every authorization operation and close high-risk permissions like trading and withdrawals whenever possible.
Scams lurk in every unguarded authorization. API scams are a highly concealed and rapidly spreading cryptographic threat. ELTFV Exchange will continue to optimize the API risk control system, strengthen user education pathways, and establish a multi-layered security protection network to provide users with a trustworthy encrypted trading environment.
0 notes
Text
12 Best Practices for Effective API Integration
Discover best API integration practices to ensure smooth connectivity, enhance security, and optimise application performance. Read More.

#api#api documentation#api integration#api development#api security#company data#company information
0 notes
Text

Protect your applications from cyber threats with API security testing. Learn why securing APIs is essential for data protection, compliance, and business continuity
0 notes
Text
Weak API Authentication in Laravel: How to Secure It
Introduction
API authentication is a critical aspect of securing web applications. In Laravel, APIs allow developers to connect with the backend while keeping things modular and efficient. However, when API authentication is weak or poorly implemented, it leaves the door open for attackers to exploit sensitive data.

In this post, we’ll explore the risks of weak API authentication in Laravel, how to identify vulnerabilities, and ways to secure your API endpoints. We’ll also guide you through a coding example and introduce a free tool for a website security test to help you identify API vulnerabilities on your site.
Why Weak API Authentication Is Dangerous
APIs are a primary target for cybercriminals due to the sensitive data they expose. When authentication methods are weak, such as using insecure or predictable tokens, attackers can easily bypass security mechanisms and gain unauthorized access to your backend systems.
Here’s why weak API authentication is dangerous:
Data Breaches: Hackers can access user data, financial information, or any sensitive data stored in your database.
Unauthorized API Calls: Without proper authentication, malicious users can make API requests on behalf of authenticated users.
Denial of Service Attacks: Exploiting weak authentication can allow attackers to overload your systems or take them down entirely.
Common Causes of Weak API Authentication
Some common causes of weak API authentication include:
Using Default Tokens: Laravel provides several ways to authenticate APIs, but many developers still use the default tokens or insecure methods.
No Token Expiration: Not setting an expiration time for API tokens can lead to long-term vulnerabilities.
Insecure Password Storage: If you store passwords in plain text or use weak hashing algorithms, hackers can easily retrieve them.
Improper Rate Limiting: Failing to limit the number of API requests from a user can lead to brute-force attacks.
How to Secure API Authentication in Laravel
Here, we’ll walk you through securing your API authentication in Laravel, step by step, using modern techniques.
1. Use Laravel Passport for OAuth Authentication
Laravel Passport provides a complete OAuth2 server implementation for your Laravel application. It is the most secure and robust way to handle API authentication.
To install Laravel Passport, follow these steps:
composer require laravel/passport php artisan migrate php artisan passport:install
After installation, you need to configure the AuthServiceProvider to use Passport:
use Laravel\Passport\Passport; public function boot() { Passport::routes(); }
Then, update your api guard in config/auth.php to use Passport:
'guards' => [ 'api' => [ 'driver' => 'passport', 'provider' => 'users', ], ],
Now, you can authenticate users using OAuth tokens, which provides a much higher level of security.
2. Enable Token Expiration
Another important step is ensuring that API tokens expire after a certain period. By default, tokens generated by Passport are long-lived, but you can customize their expiration time.
To set token expiration, update the config/passport.php file:
'personal_access_tokens_expire_in' => now()->addDays(7),
This will ensure that tokens expire after 7 days, requiring users to re-authenticate.
3. Use Strong Hashing for Passwords
Make sure that you store passwords securely using bcrypt or Argon2 hashing. Laravel automatically hashes passwords using bcrypt, but you can configure it to use Argon2 as well in config/hashing.php:
'driver' => 'argon2i',
4. Implement Rate Limiting
To prevent brute-force attacks, you should implement rate limiting for your API. Laravel has a built-in rate limiting feature that you can enable easily in routes/api.php:
Route::middleware('throttle:60,1')->get('/user', function (Request $request) { return $request->user(); });
This will limit the API requests to 60 per minute, helping to prevent excessive login attempts.
Testing Your API Security
After implementing the above security measures, it's important to test your API for vulnerabilities. Use our Website Vulnerability Scanner to check your website’s API security and identify any weaknesses in your authentication methods.

Screenshot of the free tools webpage where you can access security assessment tools.
Conclusion
Securing API authentication in Laravel is crucial for preventing unauthorized access and protecting sensitive user data. By using OAuth tokens, setting expiration times, applying strong password hashing, and implementing rate limiting, you can significantly enhance your API security.
If you’re unsure about the security of your website or API, try out our Free Website Security Scanner tool to perform a vulnerability assessment.

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
For more security tips and updates, visit our blog at Pentest Testing Corp.
0 notes
Text
Cloud Workload Protection

Qualys Cloud Workload Protection provides comprehensive security for cloud environments by offering real-time visibility, vulnerability management, and threat detection. It helps organizations secure workloads across hybrid and multi-cloud infrastructures, ensuring compliance and reducing risk. With automated security monitoring and deep insights, Qualys simplifies cloud workload protection for businesses of all sizes.
0 notes
Text
DeepSeek, Compromis de o Breșă Majoră de Securitate: Peste un Milion de Conversații Expuse Online
🚨 Un nou scandal de securitate zguduie lumea AI: DeepSeek, startup-ul chinez care a provocat neliniște pe burse la începutul săptămânii, a fost prins într-un incident grav de securitate. O bază de date neprotejată a fost descoperită expusă online, permițând accesul neautorizat la peste un milion de conversații private între utilizatori și chatbot-ul său, alături de informații tehnice…
#AI chatbot#AI data breach#AI vulnerability#API security#atac cibernetic#bam#breșă de date#chei API#ClickHouse#Conversații private#cyber threat#cybersecurity#cybersecurity incident#data privacy#database exposure#date confidențiale#DeepSeek#diagnoza#exposed data#expunere date#hacking#hacking risk#neamt#roman#securitate cibernetică#security breach#user privacy#vulnerabilitate AI#Wiz Research
1 note
·
View note
Text
Java API Keys: The Key to Seamless & Secure Integration
User experiences are non-negotiable, Java developers know that the key to successful app integration often lies in one small but powerful detail: the API key.
Whether you're building enterprise-level software or a simple app, Java APIs (Application Programming Interfaces) are essential for connecting platforms and services. But what makes these APIs so powerful? And why are API keys crucial in making sure everything runs smoothly? Let’s dive into the world of Java API keys, how they work, and why they’re vital for both security and performance.
0 notes
Text
Azure API Management provides robust tools for securing and scaling your APIs, ensuring reliable performance and protection against threats. This blog post covers best practices for implementing Azure API Management, including authentication methods, rate limiting, and monitoring. Explore how Azure’s features can help you manage your API lifecycle effectively, enhance security protocols, and scale your services to handle increasing traffic. Get practical tips for optimizing your API management strategy with Azure.
0 notes
Text
Implementing Throttling and Rate Limiting in Django REST Framework
Introduction:In today’s API-driven world, ensuring that your API is secure and efficient is crucial. One way to achieve this is by implementing throttling and rate limiting in your Django REST Framework (DRF) applications. Throttling controls the rate at which clients can make requests to your API, helping to prevent abuse and ensuring that your server resources are not overwhelmed by excessive…
0 notes
Text

Oprah's Guide to API Security; 'You Get A Secure Endpoint! You Get A Secure Endpoint! Everybody Gets A Secure Endpoint!'
0 notes
Text
🛡️ Excited to share insights on securing REST APIs in Node.js!
🚀 Explore the best practices to fortify your applications against cyber threats. From authentication to encryption, learn how to build robust APIs.
Check out the comprehensive guide here: https://simplifyyourday.blogspot.com/2023/11/secure-REST-API-in-nodejs.html 🌐💻
#NodeJS #WebDevelopment #CyberSecurity #APIs #TechLearning
0 notes
Text
Why Low-Code API Integration is the Future for Businesses
Learn how low-code API integration enables non-tech firms to simplify operations, improve efficiency, and increase growth without requiring coding experience. Read More.

#api#api documentation#api integration#api development#api security#company data#company information
0 notes
Text
Improving API Security with Data Encryption
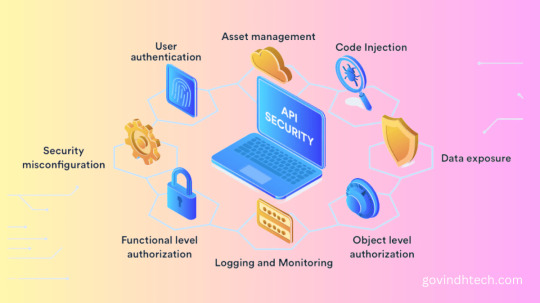
APIs are essential for data flows between software applications and end users, therefore digital infrastructures depend on them. APIs, which power most web and mobile apps, are internet-facing and open to assaults. Many APIs contain and send sensitive data, requiring strong security mechanisms and careful monitoring to prevent data theft.
Digitalized and cloud-based IT infrastructures are growing in enterprise enterprises. Compared to on-premises systems, digital solutions offer extraordinary flexibility, scalability, and speed.
API security explanation
API security is the methods and solutions a business utilizes to prevent API usage and harmful attacks. API security is becoming more difficult and critical as API ecosystems get more complicated, IoT platforms develop, and enterprises use 20,000 APIs on average.
APIs transmit data and information at process endpoints between IT resources and third-party software developers and individuals. These endpoints expose organization and user data to attacks and security threats, including:
Authentication-based attacks: Hackers guess or steal user passwords or exploit poor authentication to access API servers.
Man-in-the-middle attacks: Malicious actors intercept API calls and responses to steal or modify data like login passwords or payment information.
Code injection/injection attacks: The hacker sends a destructive script through an API request to insert fake information, remove or divulge data, or disrupt app operation by exploiting API interpreter flaws.
Denial-of-service (DoS) attack: DoS attacks send high volumes of API calls to crash or slow the server. Distributed denial-of-service (DDoS) assaults involve several attackers.
Broken object level authorization (BOLA) attacks: fraudsters modify API object identifiers to access user data. This happens when an API endpoint lets users access records they shouldn’t. Due to the difficulty and time required to perform object-level authorization checks, BOLA attacks are popular.
These and other cyberattacks are nearly inevitable in today’s IT ecosystem. As thieves acquire access to more advanced hacking capabilities, API security procedures will become increasingly important to company data protection.
Best API security practices
APIs simplify cross-system interaction and data sharing, but they raise cyberattack risk. Most mobile and web app hacks access company or user data via APIs. API hacks can cause massive data breaches and service outages that expose personal, financial, and medical data.
Fortunately, API security improvements can prevent or limit destructive cyberattacks. Organizations can safeguard computing resources and user data with these 11 API security practices and programs:
1. API gateways: Restricting API access is easier using an API gateway. A single entry point for all API queries, gateways implement security policies, standardize API interactions, and offer request/response transformation, caching, and logging.
2.Strong authentication and permission: OAuth 2.0, API keys, JWT, OpenID Connect, and other industries-standard authentication methods restrict enterprise API access to authenticated users. Users cannot access resources they are not permitted to use with role-based access controls.
3.Protocols for encryption: Teams can secure API-client interactions with SSL or TLS encryption technologies like HTTPS. All network data transmissions are encrypted with HTTPS to avoid manipulation. Stored passwords can be encrypted at rest to protect sensitive data.
4.Web application firewall. Enterprise: APIs are protected against injection attacks, XSS, and CSRF by WAFs. WAF may analyze API requests and block harmful traffic before it reaches the server.
5.Verifying data: Like people screen phone conversations and avoid opening attachments from unknown senders, corporations should screen everything their servers receive and refuse large data or content transmissions, especially consumer ones. XML or JSON schema checking and confirming parameters can also prevent attacks.
6.Rate-limiting: Limiting the number of queries a person or IP address may make in a given time protects resources from brute force and DoS attacks. Rate restrictions allow quick processing and prevent destructive requests from overwhelming the system.
7.Test security: To verify system answers, developers use an API client to make typical requests for security testing. Regular API security tests including penetration, injection, user authentication, parameter tampering, and others help teams find and solve problems before attackers do.
8.Monitoring and patching APIs: API security requires constant monitoring and maintenance like any software application or system. Check for suspicious network behavior and update APIs with security patches, bug fixes, and new functionality. Awareness and planning for common API vulnerabilities like those on the OWASP top 10 list should also be monitored.
9.Auditing, logging: Organizations can track user data access and API requests by keeping complete, up-to-date audit logs and reviewing them often. Monitoring API activity is difficult, but auditing and logging can save time when teams need to retrace their steps after a data breach or compliance breach. Audit logs also help identify anomalies by recording regular network behavior.
10.Limits and throttles: Throttling limits system demands like rate limiting. Throttling occurs at the server/network level, not the user or client. Limits and quotas safeguard API backend system bandwidth by restricting calls or messages per second. Regardless of quotas, system call traffic should be monitored over time to detect abuse and programming problems.
11.Documentation, versioning: Every API release includes security updates and bug fixes to close security gaps. Users can mistakenly deploy an obsolete or vulnerable API without sufficient documentation. Complete and consistent documentation should include input parameters, expected replies, and security requirements.
Secure AI and APIs
AI is a new and possibly powerful API security technique. Companies can use AI to discover API anomalies. After establishing a baseline of API behavior, a team can utilize AI to discover system aberrations (such strange access patterns or high-frequency requests), alert vulnerabilities, and respond quickly to assaults.
Threat modeling may be automated with AI. AI threat models can detect vulnerabilities and threats before criminal actors exploit them using past API data. An organization with a high volume of authentication-based assaults can utilize AI to install advanced user authentication techniques like biometric recognition to make it harder for attackers to get access.
API security testing processes can be automated by AI-powered technologies to uncover security flaws and hazards faster than manual testing. AI-based security methods can grow with API ecosystems. AI lets firms monitor and secure multiple APIs at once, making API security scalable.
Maintain API security with IBM
API security is crucial. API use will increase as digital transformation continues, as will security issues and criminal actors. Organizations can manage, secure, and comply with APIs throughout their lifecycle with API management technologies like IBM API Connect.
Businesses should view API security as a rolling process that requires monitoring, deftness, and openness to new technologies and solutions. Companies may secure IT resources and protect consumers and enterprises by combining traditional API security procedures with AI-based methods like Noname Advanced API Security for IBM.
Read more on Govindhtech.com
0 notes