#application container
Explore tagged Tumblr posts
Text






Why is Wandasho's little unit symbol not orange? All of the other unit symbols are their unit colors, why is WxS being singled out instead of, like, Niigo as the "outcast" group? This clown unit continues to baffle me.
#project sekai#pjsk#prsk#wonderlands x showtime#I mean this in the nicest way I possibly can as a person who doesn't really care about WxS.#Also when I was inserting all the images WxS's crown took a good minute to load.#What indecipherable horrors are contained within their logo?#In the same vein of oddity as the rest of WxS#their unit color is the default orange in Google's suite of vaguely creative-adjacent applications.#ristois notes
23 notes
·
View notes
Text
it is cosmically massive in the face of your mortal insignificance, and it has only ever turned its gaze on an individual to destroy them. it doesn't know how to love you. it has never attempted such a thing before.
it does not know how to gentle its hands to hold you, for it has only ever needed claws. it never wanted to avoid breaking anyone before you. when it tries, it will fail. it will unintentionally leave gashes as deep as the ones that were deliberately carved into you.
does the intent make all the difference, or is a wound a wound? are there enough scraps of you left to survive the carnage of its learning curve?
#jacob hale#sayer#sayer podcast#i am sayer#im fine im fine im fine im fine#sage speaks#sage original post#gore imagery cw#greatest hits#containment breaches are welcome if this feels applicable to your blorbos#but you have to listen to sayer in exchange that's the rule#(/hj) listen to sayer.
212 notes
·
View notes
Text
trans men please please please keep up with your pelvic health. find a provider who will listen to you and see you as you are. you have the right to good quality and affirming care
get your annual physical exam. regular std testing. pap smears. all of it
#i just got diagnosed with cervical precancer and i am so grateful for the care i am receiving#i know not everyone has access to the same resources i do but even when its hard even when you get desdnamed at the check in desk even when#its scary and new even when its dysphoria inducing you are deserving of a long and healthy life and that starts with regular care#if i had been too nervous to go to the gyn like i had been in previous years there is a chance it would have gone undetected#and become invasive#obvs if you don’t have the applicable parts maybe this doesn’t apply to you#saying this now in case this post leaves containment#scout.txt
22 notes
·
View notes
Text
aaarghh. i hope i get an interview for this position at my friend’s job. i would really like to get an interview at least lets all manifest this for me…
#the application closes on friday and idk how fast it will be but.Arrgghg#i hope it doesnt take forever esp after my last almost job getting stuck behind a hiring freeze#i still have another cover letter to finish for the container store#but i would. i Would very much perfer if i got this job me thinks#news with isaac
13 notes
·
View notes
Text
i dont like art tutorials that keep hammering in the idea that “circles are soft cute and friendly squares are sturdy and confident and triangles are MEAN and EVIL and FUCKED UP” because like,,,, it kinda feels like discrimination against triangles man
#pinyatalk#art talk#I mean shape language has its applications and it’s REALLY useful in certain ways. but i prefer having a “subtler” approach to shape design#over having the shapes being the MAIN defining thing of the character’s design. which is what a lot of art tutorial channels try to push.#I think over-reliance on shapes to carry the rest of the design by kinda leads to more “stereotypical and cliche” looking characters yknow.#there’s so much more than shape to think about when making a character. shapes are merely a simple spice to add something more to the dish.#shapes are kinda more abstract vibes than these horoscope-esque “shape personalities” people keep talkin about. they contain multitudes.#Not to rag on people who have very shapey artstyles! it can look SOOOO frickin good if you get the know-how!#It’s just that even if you’re very into shapes you probably shouldn’t shove yourself into a strict box of ONLY using triangles for villains#good guys can also be triangles.#idk. play with shapes. PLAY WITH EMMM
9 notes
·
View notes
Text

Hello from the frog in my planner
#the job I’ve had since 2018 will be over in two weeks#I’ve applied to so many jobs in the last month I can’t keep all the rejections straight anymore#so I’m distracting myself with planning out a container garden for my patio out back#I’ll be okay if I can’t find a job for a while in fact a break will be nice#which I know is incredibly lucky#but I will need a job eventually#just playing the waiting game now with the other half dozen applications#toad rambles
4 notes
·
View notes
Text
i really think who a person chooses as their favorite character has deep psychological implications but i canNOT examine those themes in myself or else i’ll explode. i will explode
#doesn’t apply to Casual Likers of things yk#this is like applicable to ppl who obsess over stuff#does that make sense#also applies to who you have as your main f/o but i feel this might breach containment so i left it HEIDNDJXC#.mei chats
29 notes
·
View notes
Text
oh my god writing essays is so harddddd
#working on the mlis application essay but i'm being me about it#honestly the issue isn't the essay itself it's#1. this is an Application Essay i have a lot effing riding on this#like this paper needs to convince people i can write#and 2. the word limit is So low. it's 1000 words. the prompt contains three questions#like how am i meant to actually thoroughly answer these questions in ONE THOUSAND WORDS#i'm at 300 right now and sstill only part 1
6 notes
·
View notes
Text
what shatters you ?
⸻ exhaustion

you have tried to be atlas for far too long. your legs tremble and shoulders creak beneath the weight of the world you carry. every step forward is a battle , yet you soldier on . . . for what ? when will you learn that you are allowed to lower your heavy burdens ?
tagged by : @amourem ( peekaboo ) tagging : i'm late so feel free to if you haven't already !
#* ✦ 𝐈𝐕. ❮ isms ❯ ⸻ ❝#* ✦ 𝐕𝐈. ❮ muses ❯ ⸻ ❝ 「 osamu dazai 」#* ✦ 𝐗𝐈𝐈. ❮ dash games ❯ ⸻ ❝#dazai is so complex that i feel like any of these choices are applicable#like he's undoubtedly sorrowful and he's experienced betrayal#but i think exhaustion is definitely a part that's overlooked#the fact he was in a fishing container surrounded by chemical waste for most of his developmental years#and even now he probably doesn't get nearly enough sleep aside from the occasional forty winks#but him also trying to save the world from the invasion by going against the one opponent that he knows only he could face#and on top of that he doesn't even have time to address the issues that are personal to him#or rather he avoids them and pretends he isn't impacted#or perhaps he feels like he doesn't deserve to be distraught and regretful over them in fact he deserves to feel this way#much to think about
6 notes
·
View notes
Text
pvc electric red and blue wire #smartratework#tumblr
#flowers#aesthetic#alternative#grunge#1950s#cute#japan#60s#70s#80s#|| Smart Rate Work#Manufacturing encompasses a diverse array of processes and technologies aimed at producing a wide range of products#from everyday essentials to specialized components. Take wires#for instance: these are typically manufactured through drawing processes#where metal rods or strips are pulled through dies to reduce their diameter and achieve the desired thickness. This method ensures uniformi#crucial for applications in electronics#construction#and industrial settings.#On the other hand#the production of bottles involves molding techniques such as blow molding or injection molding. Blow molding heats plastic resin into a mo#used extensively for beverage containers and packaging. Injection molding#meanwhile#injects molten plastic into a mold under high pressure#ideal for producing intricate shapes with precision#like medical vials or automotive parts.#Both wire and bottle manufacturing rely heavily on materials science#engineering precision#and quality control measures to meet stringent specifications. Advances in automation#robotics#and sustainability practices are transforming these industries
2 notes
·
View notes
Text
#No jesus option because that would sweep plus Soooo many people celebrate secular xmas it's not applicable to the wider holiday imo#moi.txt#polls#poll#xmas#christmas#reblog to break containment please
4 notes
·
View notes
Text
see like. i kind of understand where the people who say "oh but if you put something online you agree for it to be critiqued" re fics but. but. i promise that if you got persistent criticism on your work, for example, art (your anatomy is bad you have no sense of posing properly your color theory is off you are blatantly copying style from this anime, etc). you would stop being amicable to that viewpoint and block the critiquer real quick
giving constructive criticism takes knowledge and study, and i bet my ass most of yall have never taken a creative writing class
#again! not applicable to works that contain blatant bigotry. that is self explanatory i should think#but still i like giving people the benefit of the doubt. being hostile hardly ever pays off#im saying this because i used to be that kind of asshole and i was too autistic to notice it
5 notes
·
View notes
Note
For the writer's asks: 13, 16, & 20
tyyy, questions are here
13. What feedback did you receive for your writing that stuck with you? Answered here :3
16. Where do you find inspiration to write?
Is it cliché to say everywhere? There's always a little narrator somewhere in my head, and when I see something that I like, or touch it, or eat it, or hear it- I squirrel it away. I always want to be writing and always sort of am whether I want to or not because there are so many words! But also in a more practical structural based way, I would say by asking myself questions. Sometimes from inside out- What would cause Valentine to purposefully break from Arasaka? Sometimes from the outside in- How could Valentine post DE end up interacting with Johnny? * 20. Do you have one piece of advice for your fellow writers? Don't be afraid to experiment- it feels bad to fall short, but you'll learn a lot, and you can always save the attempt and analyze it later or re-do it. For some reason this article is Medium-walled but I'm a big believer in the 1000 pots process. If you try to make the best pot every time from the moment you start writing it's going to be discouraging and hard. If you tell yourself you're going to end up churning a lot of 50% quality pots and learning about what Not To Do it takes a lot of the pressure off and makes it fun to dick around and do weird hobby stuff. Have fun!
#ask meme#I love process I could talk about process forever because of the way that it is#* If you want to get the application into an unexpected state you're going to have a do a lot of fuzzing#sometimes you get lucky and find a super admin override#this makes the application very vulnerable but also is kind of handy isn't it#anything is possible it's just a matter of engineering the correct conditions in the right environment#works on my machine i'll put this in a container and ship it
3 notes
·
View notes
Text
Why Does High-temperature Liquefied Iron Nucleus Produce a Huge Magnetic Field?
Bar Magnet Heating Will Lose Magnetism, Why Does High-temperature Liquefied Iron Nucleus Produce a Huge Magnetic Field? The atoms in the magnet are arranged neatly in accordance with certain rules, which is why magnets have magnetic reasons. When heating the magnet, the arrangement of the atom is disrupted and the magnetic is reduced. When heating to 770 ° C, the magnet loses magneticity. Why…
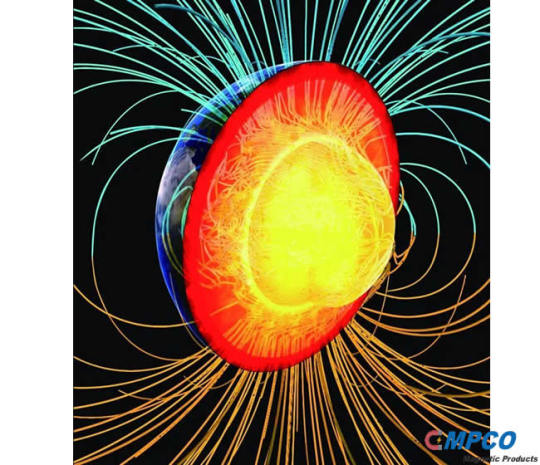
View On WordPress
#AI Magnets#Cerium Magnets#cerium-containing magnets#Grain Boundary Diffusion#high-performance magnetic materials#Magnet Maker#magnetic field#magnetic fields#magnetic force#magnetic material#Magnetic Materials#Magnetic Phenomena#magnetic properties#magnetic treatment#Magneticity#NdFeB Magnet#NdFeB permanent magnet#NdFeB Surface Treatment#Neodymium iron boron#Neodymium Magnet Applications#Permanent Magnet Materials#Permanent Magnets#Rare Earth Magnets#rare earth permanent magnet#Sintered NdFeB#Sintered NdFeB Magnets#Super Magnets
2 notes
·
View notes
Text
Ensuring Resilient Security for Autonomous AI in Healthcare
New Post has been published on https://thedigitalinsider.com/ensuring-resilient-security-for-autonomous-ai-in-healthcare/
Ensuring Resilient Security for Autonomous AI in Healthcare


The raging war against data breaches poses an increasing challenge to healthcare organizations globally. As per current statistics, the average cost of a data breach now stands at $4.45 million worldwide, a figure that more than doubles to $9.48 million for healthcare providers serving patients within the United States. Adding to this already daunting issue is the modern phenomenon of inter- and intra-organizational data proliferation. A concerning 40% of disclosed breaches involve information spread across multiple environments, greatly expanding the attack surface and offering many avenues of entry for attackers.
The growing autonomy of generative AI brings an era of radical change. Therefore, with it comes the pressing tide of additional security risks as these advanced intelligent agents move out of theory to deployments in several domains, such as the health sector. Understanding and mitigating these new threats is crucial in order to up-scale AI responsibly and enhance an organization’s resilience against cyber-attacks of any nature, be it owing to malicious software threats, breach of data, or even well-orchestrated supply chain attacks.
Resilience at the design and implementation stage
Organizations must adopt a comprehensive and evolutionary proactive defense strategy to address the increasing security risks caused by AI, especially inhealthcare, where the stakes involve both patient well-being as well as compliance with regulatory measures.
This requires a systematic and elaborate approach, starting with AI system development and design, and continuing to large-scale deployment of these systems.
The first and most critical step that organizations need to undertake is to chart out and threat model their entire AI pipeline, from data ingestion to model training, validation, deployment, and inference. This step facilitates precise identification of all potential points of exposure and vulnerability with risk granularity based on impact and likelihood.
Secondly, it is important to create secure architectures for the deployment of systems and applications that utilize large language models (LLMs), including those with Agentic AI capabilities. This involves meticulously considering various measures, such as container security, secure API design, and the safe handling of sensitive training datasets.
Thirdly, organizations need to understand and implement the recommendations of various standards/ frameworks. For example, adhere to the guidelines laid down by NIST’s AI Risk Management Framework for comprehensive risk identification and mitigation. They could also consider OWASP’s advice on the unique vulnerabilities introduced by LLM applications, such as prompt injection and insecure output handling.
Moreover, classical threat modeling techniques also need to evolve to effectively manage the unique and intricate attacks generated by Gen AI, including insidious data poisoning attacks that threaten model integrity and the potential for generating sensitive, biased, or inappropriately produced content in AI outputs.
Lastly, even after post-deployment, organizations will need to stay vigilant by practicing regular and stringent red-teaming maneuvers and specialized AI security audits that specifically target sources such as bias, robustness, and clarity to continually discover and mitigate vulnerabilities in AI systems.
Notably, the basis of creating strong AI systems in healthcare is to fundamentally protect the entire AI lifecycle, from creation to deployment, with a clear understanding of new threats and an adherence to established security principles.
Measures during the operational lifecycle
In addition to the initial secure design and deployment, a robust AI security stance requires vigilant attention to detail and active defense across the AI lifecycle. This necessitates for the continuous monitoring of content, by leveraging AI-driven surveillance to detect sensitive or malicious outputs immediately, all while adhering to information release policies and user permissions. During model development and in the production environment, organizations will need to actively scan for malware, vulnerabilities, and adversarial activity at the same time. These are all, of course, complementary to traditional cybersecurity measures.
To encourage user trust and improve the interpretability of AI decision-making, it is essential to carefully use Explainable AI (XAI) tools to understand the underlying rationale for AI output and predictions.
Improved control and security are also facilitated through automated data discovery and smart data classification with dynamically changing classifiers, which provide a critical and up-to-date view of the ever-changing data environment. These initiatives stem from the imperative for enforcing strong security controls like fine-grained role-based access control (RBAC) methods, end-to-end encryption frameworks to safeguard information in transit and at rest, and effective data masking techniques to hide sensitive data.
Thorough security awareness training by all business users dealing with AI systems is also essential, as it establishes a critical human firewall to detect and neutralize possible social engineering attacks and other AI-related threats.
Securing the future of Agentic AI
The basis of sustained resilience in the face of evolving AI security threats lies in the proposed multi-dimensional and continuous method of closely monitoring, actively scanning, clearly explaining, intelligently classifying, and stringently securing AI systems. This, of course, is in addition to establishing a widespread human-oriented security culture along with mature traditional cybersecurity controls. As autonomous AI agents are incorporated into organizational processes, the necessity for robust security controls increases. Today’s reality is that data breaches in public clouds do happen and cost an average of $5.17 million , clearly emphasizing the threat to an organization’s finances as well as reputation.
In addition to revolutionary innovations, AI’s future depends on developing resilience with a foundation of embedded security, open operating frameworks, and tight governance procedures. Establishing trust in such intelligent agents will ultimately decide how extensively and enduringly they will be embraced, shaping the very course of AI’s transformative potential.
#access control#Advice#Agentic AI#agents#ai#AI AGENTS#AI in healthcare#ai security#AI systems#API#applications#approach#Attack surface#attackers#attention#autonomous#autonomous ai#awareness#Bias#breach#Business#challenge#change#chart#CitiusTech#classical#clouds#compliance#comprehensive#container
0 notes
Text
Cybercriminals are abusing Google’s infrastructure, creating emails that appear to come from Google in order to persuade people into handing over their Google account credentials. This attack, first flagged by Nick Johnson, the lead developer of the Ethereum Name Service (ENS), a blockchain equivalent of the popular internet naming convention known as the Domain Name System (DNS). Nick received a very official looking security alert about a subpoena allegedly issued to Google by law enforcement to information contained in Nick’s Google account. A URL in the email pointed Nick to a sites.google.com page that looked like an exact copy of the official Google support portal.
As a computer savvy person, Nick spotted that the official site should have been hosted on accounts.google.com and not sites.google.com. The difference is that anyone with a Google account can create a website on sites.google.com. And that is exactly what the cybercriminals did. Attackers increasingly use Google Sites to host phishing pages because the domain appears trustworthy to most users and can bypass many security filters. One of those filters is DKIM (DomainKeys Identified Mail), an email authentication protocol that allows the sending server to attach a digital signature to an email. If the target clicked either “Upload additional documents” or “View case”, they were redirected to an exact copy of the Google sign-in page designed to steal their login credentials. Your Google credentials are coveted prey, because they give access to core Google services like Gmail, Google Drive, Google Photos, Google Calendar, Google Contacts, Google Maps, Google Play, and YouTube, but also any third-party apps and services you have chosen to log in with your Google account. The signs to recognize this scam are the pages hosted at sites.google.com which should have been support.google.com and accounts.google.com and the sender address in the email header. Although it was signed by accounts.google.com, it was emailed by another address. If a person had all these accounts compromised in one go, this could easily lead to identity theft.
How to avoid scams like this
Don’t follow links in unsolicited emails or on unexpected websites.
Carefully look at the email headers when you receive an unexpected mail.
Verify the legitimacy of such emails through another, independent method.
Don’t use your Google account (or Facebook for that matter) to log in at other sites and services. Instead create an account on the service itself.
Technical details Analyzing the URL used in the attack on Nick, (https://sites.google.com[/]u/17918456/d/1W4M_jFajsC8YKeRJn6tt_b1Ja9Puh6_v/edit) where /u/17918456/ is a user or account identifier and /d/1W4M_jFajsC8YKeRJn6tt_b1Ja9Puh6_v/ identifies the exact page, the /edit part stands out like a sore thumb. DKIM-signed messages keep the signature during replays as long as the body remains unchanged. So if a malicious actor gets access to a previously legitimate DKIM-signed email, they can resend that exact message at any time, and it will still pass authentication. So, what the cybercriminals did was: Set up a Gmail account starting with me@ so the visible email would look as if it was addressed to “me.” Register an OAuth app and set the app name to match the phishing link Grant the OAuth app access to their Google account which triggers a legitimate security warning from [email protected] This alert has a valid DKIM signature, with the content of the phishing email embedded in the body as the app name. Forward the message untouched which keeps the DKIM signature valid. Creating the application containing the entire text of the phishing message for its name, and preparing the landing page and fake login site may seem a lot of work. But once the criminals have completed the initial work, the procedure is easy enough to repeat once a page gets reported, which is not easy on sites.google.com. Nick submitted a bug report to Google about this. Google originally closed the report as ‘Working as Intended,’ but later Google got back to him and said it had reconsidered the matter and it will fix the OAuth bug.
11K notes
·
View notes