#best database software
Explore tagged Tumblr posts
Text
Transform Your Data with Northwest Database Scrubbing
Learn from the masters of data scrubbing at Northwest Database Services. Unlock the full potential of your data effortlessly with our proven techniques. Data scrubbing, also known as data cleansing or data cleaning, refers to the process of identifying and correcting errors, inconsistencies, and inaccuracies in a dataset. This process is crucial for maintaining data integrity and ensuring the reliability of analysis and decision-making based on that data.
0 notes
Text
"AI" this and "AI" that, NONE OF IT IS INTELLIGENT, WE HAVE NOT MADE INTELLIGENCE YET, WHY ARE WE LYING, DO WORDS MEAN NOTHING
#it's at best “machine learning” if it could even be considered learning#this is semantics but it's important semantics because words have meaning and we have to stop giving software more power than they deserve#I'm more on the side of “self-evolving programs” for what to call these things#like chat gpt is a self-evolving program which processes a database and simulates human speech based off that database#this is what being an english major has turned me into#artificial intelligence
3 notes
·
View notes
Text
Streamline Your Ministry with the Best Church Management Software
In today’s digital age, churches and ministries can greatly benefit from embracing technology to manage their daily operations. Whether it’s organizing events, tracking donations, or maintaining member databases, Church Management Software has become an essential tool for church leaders.
Why Use Church Management Software?
Managing a church involves much more than just Sunday services. From maintaining accurate records of your congregation to coordinating volunteers and scheduling activities, the right software can simplify your operations and enhance your outreach.
Finding the Best Church Management Software
Choosing the right solution depends on your church’s specific needs. Here’s a helpful church management software comparison to guide you in selecting the platform that aligns with your ministry goals.
Key Features of Church Management Solutions
Database Management: Keep track of member information efficiently with the Best Church Database Software.
Event Coordination: Plan and promote events seamlessly.
Donation Tracking: Record contributions and provide easy-to-access statements for members.
Communication Tools: Stay connected with your congregation through announcements and newsletters.
Customizable CMS: A Church CMS allows you to tailor the platform to meet your unique needs.
Explore Church Management Solutions Today
Discover how ChMeetings can support your ministry with its powerful tools. As one of the most trusted platforms, it offers intuitive features and scalability for churches of all sizes. Check out the Best Church Management Software to see how it can transform your ministry
0 notes
Text

Discover how Data PODs empower users with decentralized data control through blockchain technology, ensuring privacy and security for your data.
0 notes
Text
Understanding Data Encryption and Classification for Effective Data Rights Management
Introduction:
Nowadays, data security has become a top priority. As the data is generated and shared more exponentially, the safeguarding of sensitive information has become more challenging while being crucial. Data encryption and classification are the two major aspects of data rights, and they play a leading part in protecting information from involuntary or Best geofence storage service and in compliance with privacy laws.

What is Data Encryption?
Data encryption is like putting your information in a safe, but it is a digital safe. This process entails encoding the plain text into an illegible text referred to as ciphertext with a specific algorithm and key. This procedure makes sure that even if somebody who's not authorized is granted access to the data, they will still not be able to decrypt it without the corresponding decryption key.
Imagine that you want to send a secret message to your friend. Instead of writing the message clearly, you mix it up using some secret code that only you and your friend know. Without the key, any interposition would only yield nonsensical letters.
What is Data Classification?
Data classification is grouping the data according to its level of sensitivity and significance. It also allows organizations to categorize their data holdings and decide which data needs to be protected at what level. Classification is usually done by tagging data with a label that identifies its security requirements or handling process.
Data classification is like putting your stuff into different boxes. All your important documents might go into a folder, another for pictures and one for miscellaneous notes. Every folder is labelled to indicate what paperwork is inside of it and how you should handle it.
Effective Data Rights Management
Encrypting and classifying data are crucial in the context of the formulation of advice on the management of data rights with the objective of attaining maximum data protection and regulatory compliance. Here's how they work together, Here's how they work together:
Data Identification:
This high classification facilitates to define the sensitive data that needs to be encrypted conveniently. By splitting the data into groups according to the application of encryption technologies, information systems can address the shortage of encryption means and distribute the resources in a reasonable way.
Access Control:
Encryption is a safeguard against unpermitted access, and people with classification rights choose who to give access to encoded information. The access controls can build on data classification labels so that only the laid-out clearance users, possessing the proper clearance can unscramble the cipher and access sensitive information.

Conclusion:
The use of data encryption and classification forms part of comprehensive data rights management plans. Encryption works to make Best Database Backup Services only accessible to authorized people. While at the same time, sensitivity labels can be used to classify easy-to-reach data from data that requires more protection. Organizations can provide an appropriate environment for data if they combine these approaches. They can take care of risks, protect confidential information, and be consistent with data privacy regulations.
#Best object storage software#Best Database backup Services#IT Security services#Cyber security company
0 notes
Text
Streamlining Operations: Exploring the Best Employee Management Software Solutions
In the ever-evolving landscape of business operations, the significance of efficient employee management cannot be overstated. As organizations grow and adapt, the need for robust and versatile employee management software becomes increasingly essential. Such software not only aids in organizing HR tasks but also enhances productivity, streamlines processes, and fosters a positive work culture.
Amidst the plethora of options available, several standout employee management software solutions have gained acclaim for their comprehensive features, user-friendly interfaces, and ability to address diverse organizational needs. Let's delve into some of the top contenders in this field:
BambooHR: Renowned for its simplicity and functionality, BambooHR is a user-friendly HR software designed for small to medium-sized businesses. It offers a comprehensive suite of tools for HR tasks, including applicant tracking, onboarding, performance management, and time-off tracking. The intuitive interface and customizable dashboards make it a favored choice for HR professionals seeking a seamless experience.
Zenefits: Recognized for its all-in-one HR platform, Zenefits offers solutions for HR, payroll, benefits, time tracking, and compliance. Its user-friendly interface simplifies complex HR processes, allowing businesses to manage their workforce efficiently. Zenefits' integration capabilities with various third-party applications make it adaptable to diverse business needs.
Workday: Ideal for larger enterprises, Workday is a cloud-based HR and finance management software known for its robust functionalities. It encompasses HR planning, talent management, payroll, and analytics. Workday's strength lies in its ability to handle complex organizational structures while providing real-time insights for strategic decision-making.
ADP Workforce Now: Catering to businesses of all sizes, ADP Workforce Now offers a comprehensive suite of HR solutions covering payroll, talent management, time and attendance tracking, and benefits administration. Its scalability and customizable features make it suitable for organizations experiencing growth or change.
Gusto: Gusto stands out for its user-friendly payroll and HR software designed primarily for small businesses. It streamlines payroll processes, benefits administration, and compliance, simplifying administrative tasks and enabling businesses to focus on growth and employee engagement.
Paychex Flex: Tailored for midsize to large enterprises, Paychex Flex provides a suite of HR and payroll solutions. It offers features such as time and attendance tracking, benefits administration, and employee self-service tools. Its scalability and robust reporting capabilities make it an attractive choice for growing organizations.
SAP SuccessFactors: As part of the SAP suite, SuccessFactors is an enterprise-level HR software that offers comprehensive talent management solutions. It covers performance management, learning and development, recruiting, and workforce analytics. Its integration with other SAP modules provides a holistic approach to HR management within large organizations.
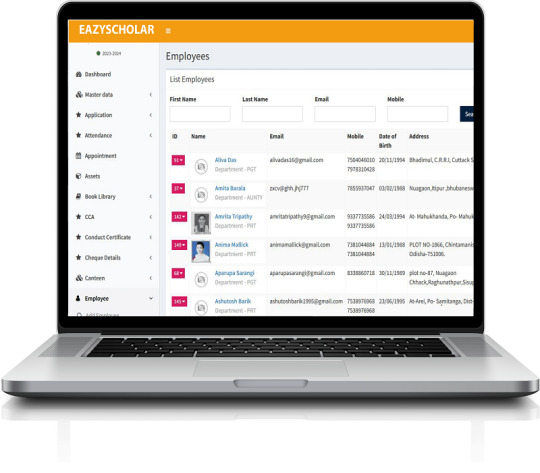
Kronos Workforce Ready: Kronos offers Workforce Ready, a unified HR, payroll, and talent management solution designed for businesses of all sizes. Its cloud-based platform provides functionalities for timekeeping, scheduling, HR administration, and compliance, making it an efficient choice for managing a diverse workforce.
In selecting the best employee management software for a particular organization, several factors must be considered:
Scalability: The software should be scalable to accommodate the organization's growth without compromising performance or functionality.
Usability: An intuitive interface and user-friendly features are crucial for widespread adoption and smooth integration into existing workflows.
Integration Capabilities: Compatibility with other systems and applications is vital for seamless data flow and efficient operations.
Customization: The ability to tailor the software to meet specific business needs ensures optimal utilization and efficiency.
Data Security and Compliance: Robust security measures and adherence to industry regulations are paramount to protect sensitive HR information.
Moreover, it's essential to assess the software's support and training resources to ensure a smooth implementation process and ongoing assistance.
In conclusion, the choice of employee management software greatly influences an organization's HR operations and overall efficiency. Each software solution mentioned offers unique strengths catering to different organizational sizes and requirements. Careful evaluation and consideration of these factors are imperative in selecting the best-suited software to optimize employee management and drive business success.
0 notes
Text

Employee Database Management System
An Employee Database Management System is a software tool that efficiently stores, organizes, and manages employee information within an organization. It enables HR professionals to securely maintain records of employees, including personal details, employment history, salary data, and performance evaluations. This system streamlines HR tasks and ensures data accuracy.
#Employee Database Management System#best employee management software#Employee Management Software#employee management system
0 notes
Text
Essential Things You Need to Know About Staff Management Software in 2023
In today's fast-paced digital era, the significance of effective staff management cannot be overstated. Staff management software has quickly become an integral part of efficient business operations in various industries. With the continuous evolution of technology, 2023 has brought forth new updates, features, and trends to watch out for. Here's what you need to know about staff management software this year.
Remote Work Adaptability:
With the increase in remote work due to the ongoing pandemic, staff management software now offers features that adapt to this new work model. Tools for virtual meetings, remote project management, and digital timesheets have become standard.
Employee Wellbeing and Engagement:
Employee mental health has gained more focus. In 2023, staff management software increasingly includes features promoting employee wellbeing, such as mood tracking, mental health resources, and wellness programs. Simultaneously, gamification strategies are being utilized to improve employee engagement and satisfaction.
Security and Data Privacy:
As we handle more sensitive data digitally, the importance of cybersecurity has skyrocketed. In 2023, staff management software has stepped up its game with enhanced data encryption, multi-factor authentication, and regular software updates to ward off potential cybersecurity threats.
Integration and Customization:
Integration with other systems such as CRM, payroll, and HRIS is more seamless than ever. Furthermore, staff management software now offers greater customization options to cater to the unique needs of each organization.
Eco-Friendly Practices:
More businesses are looking for ways to reduce their carbon footprint. Paperless management, energy-efficient operations, and other eco-friendly features are more common in staff management software in 2023.
Conclusion:
Staff management software in 2023 is about more than just efficiency and productivity; it's about creating a conducive and sustainable work environment that values employees' mental health and respects data privacy. As technology evolves, we can expect these systems to become even more intelligent, versatile, and user-friendly, becoming an indispensable tool in the modern workplace.
#staff management software#employee work management system#staff management system#employee management system#employee payroll management system#employee database management software#best staff management software#temporary staff management software#temporary staffing uk#medical staffing solutions timesheet#employee management software
1 note
·
View note
Text
It looks like you’re trying to create a mini ao3 for book reviews. You’d need their tag wrangling system or a great database with pre-set searches. And in that later option, Obsidian could be the way, if you embrace its wiki-like aspect.
I use Obsidian as my note taking and writing bible app, and it’s great, really great. I can sort a lot of my life in there. But, as a published website, it will really look like a wiki page with a lot of interlinks, and a menu that is more like a file explorer. You won’t have a scroll through my blog thingy. Visitors will need to jump link from link. And to make it great for them you will need to setup your pages very carefully, including your Homepage, probably using a lot of Dataview tables.
Dataview is a free plugin that allows for database searches based on criteria you can fully define. Note it has a bit of a learning curve, but if you use it a lot you should master it in no time (unlike me).
Does anyone have any suggestions for the best platform for building a website with a robust tagging/filtering system, preferably usable by someone whose website programming experience caps out at working off of a giant HTML book in like 2007?
#softwares and tools#tools and softwares#obsidian uses markdown language#which is easy to learn#publishing will require a subscription#obsidian.md is the website#imo a wordpress website might be better#i would keep the database private (maybe in obsidian)#but only to draw the best recs#in published posts#not as a searchable database for visitors
136 notes
·
View notes
Text
The Data Migration Services
Ever wonder how data moves from one system to another without any problems? That is how data migration works its magic. It is the process of moving data between various computer systems, formats, and storage types. It is impossible to overestimate the significance of this service given how much businesses depend on timely and accurate data to run effectively.
Northwest Database Services Overview
Northwest Database Services is a leading provider of data migration services. They specialize in helping businesses move their data securely and efficiently. With years of experience in the industry, they have gained a reputation for excellence and reliability.

Benefits of Choosing Northwest Database Services for Data Migration
Choosing Northwest Database Services for your data migration needs comes with several benefits. Firstly, their team of experts has extensive experience in handling complex data migration projects. They also prioritize security, ensuring that your data remains safe throughout the migration process. Lastly, their services are cost-effective, providing excellent value for your investment.
Types of Data Migration Services Offered
Northwest Database Services offers a wide range of data migration services to meet the diverse needs of their clients. Some of the most common types of migration services they offer include:
Best Practices for Successful Data Migration
To ensure a successful data migration, it's essential to follow best practices such as thorough planning, regular backups, and rigorous testing and validation.

Case Studies: Successful Data Migration Projects by Northwest Database Services
Northwest Database Services has successfully completed numerous data migration services projects for clients across various industries. These case studies showcase their expertise and the positive impact of their services on businesses.
Customer Testimonials
Here's what some of their satisfied clients have to say about their experience with Northwest Database Services.
Get In More Information :
Business Name: Northwest Database Services
Website: https://nwdatabase.com/
Phone: 3608418168
0 notes
Text
When the claims representative, whom I’ll call Steven, sat down at his computer around 7:15 A.M. last week, he had already been awake for an hour and a half. The morning routine for him and his family is best described as “fend for yourself,” he said. That day, he waited for his older son to shower before taking his turn; neither he nor his wife had time for breakfast. He had joined the Social Security Administration two decades ago, and came to specialize in one of its more complex and lesser-known functions: providing a form of welfare called Supplemental Security Income, or S.S.I., to people who are disabled or extremely poor. But the S.S.A. is so understaffed that Steven does a bit of everything. “My job is to be kind of like an octopus,” he said. The agency’s administrative budget had not kept up with its rising workload as more people aged into retirement. Now news outlets were reporting that President Donald Trump and Elon Musk, via Musk’s DOGE outfit, planned to fire up to half of the agency’s sixty-thousand-odd employees. (The S.S.A. later said that its goal was to lose seven thousand.) DOGE had also gained access to S.S.A. databases. “We don’t know how long we’ll be here,” Steven said. “Some people are really pissed. Others are sad and emotional. Others are making plans.” A couple days earlier, Trump had delivered a long self-congratulatory speech to Congress, in which he accused the S.S.A. of “shocking levels of incompetence and probable fraud.”
Steven lives in a Midwestern town near where he was born and raised, which means that he occasionally recognizes a relative or a family friend in a case file and has to recuse himself. Three days a week, he’s at a cubicle in a regional field office, one of twelve hundred across the U.S. The other two days, he works from home, at a plastic folding table in the corner of his bedroom. He was on the early shift. His laptop was propped up on a neon-green bin, the kind typically used to store Legos or crayons. It was flanked by two large monitors, creating a triptych. All around him were piles of kids’ clothes and books. Near his left foot was a tiny metal car; he had taped yellow notecards reading “clock,” “fan,” and “shelf” to a clock, fan, and shelf for the benefit of his youngest child, who was learning to read. Steven’s wife made drop-offs at kindergarten and day care, then came home. She has her own office setup downstairs.
The day officially started when Steven logged on to a dozen software programs. One had a blocky monochrome interface that looked like it was from the late nineties. Another was labelled “Workload Action Center,” in a light-brown, slanted font of a similar vintage. Steven kept a list of his passwords, which he had to routinely update, on a scrap of paper next to his keyboard. He scanned something called a “Tickle List” that highlighted urgent cases. His primary task was to conduct nonmedical “redetermination” interviews (code: “RZ”)—part of the S.S.A.’s process for insuring that current recipients are still eligible to receive benefits. More than seven million Americans of all ages count on S.S.I., and sixty-eight million seniors receive earned retirement payments. Social Security is the largest government program in the country and most recipients’ main source of income. It was envisioned by Frances Perkins during the Great Depression. “Redeterminations are the highest priority,” Steven said. “We should have three to five people on them at every office. Sometimes there’s only one.”
He put on a wireless headset that connected to his laptop and an online phone system. The first redetermination call was with a parent who was receiving S.S.I. on behalf of a disabled child. “Hi, this is Steven, from Social Security Administration,” he said. “I’m just calling to see if you’re able to do the redetermination appointment.” His stomach growled. The bottom-right corner of his center screen flickered with notifications. He stayed with the caller. Date of birth? Marriages? Job placements? He clicked “yes” and “no” bubbles and typed in numbers. He had much of the script memorized. “Any items held for potential value?” he asked. “Promissory notes, real property or business property, or ABLE accounts?” S.S.I. is allocated based on an applicant’s income, assets, family size, and other factors. It often takes a year, and the help of a lawyer, to get a decision. (Earlier in Steven’s career, the time frame had been three to six months.) If an application is rejected, the case can be appealed to an administrative-law judge, and the wait for those hearings is around two years.
“That was the last amount verified,” Steven continued. “Has that changed?” While waiting for the program to advance to the next screen, he glanced at e-mails on his rightmost monitor. There were more from headquarters and human resources and the employees’ union than usual. Since November, three S.S.A. commissioners or acting commissioners had come and gone: Martin O’Malley, Carolyn W. Colvin, and Michelle King. The guy in charge now was Leland Dudek, whom Trump had elevated from a middle-management role for his eagerness to help DOGE access S.S.A. files, a vast library of individual medical, housing, family, and financial records. Dudek announced plans to eliminate six out of ten regional headquarters; several directors left the agency. In an all-staff e-mail, Dudek wrote:
Criticism, contempt, stonewalling, and defensiveness are the four forces that can end any relationship and weaken any institution. . . .
Elections have consequences. . . .
Now, under President Trump, we follow established precedent: we serve at the pleasure and direction of the President. Only the Courts or Congress can intervene.
The latest e-mail from headquarters stated that, “effective today,” employees were prohibited from engaging in “Internet browsing” of “general news” or “sports” on “government-furnished equipment.”
Steven was almost done with the redetermination. Hard cases, like an overpayment that needed to be clawed back, could “make the conversation longer, vulgar.” This one was easy; the payments, of around a thousand dollars per month, would continue. “You will receive a summary statement regarding the information that we discussed,” he said. He moved on to a second call. This one, too, involved a young adult whose caretaker—in this case, a nonprofit organization—was the payee. “Hello. This is Steven from Social Security. How are you?” His cellphone buzzed. Since Trump’s reëlection, he had been in a prolific, darkly humorous group chat with fellow S.S.A. workers in the Midwest. He referred to them as his sisters and brothers. The incoming message was a link to a news story about the imminent closure of S.S.A. field offices in the area. One man in the chat, who voted Republican but had grown skeptical of Trump, wrote, “Fucking unbelievable. . . . This would devastate our agency’s ability to serve the public.”
Meanwhile, the redetermination call was getting tricky. A new source of income seemed to be complicating the calculation of resources. Steven put the nonprofit on hold and logged into Equifax. He walked across the room to grab a plastic bottle of water and took a swig. “I’m trying really not to go off the deep end,” he said. If his office closed, and the neighboring offices closed, many people would have no way of getting benefits. For one thing, applications for Social Security cards and certain forms of S.S.I. had to be submitted in person.
Steven worried about his own well-being, too. His kids were on his health insurance. He and his wife had to take care of his father. S.S.A.’s human-resources division had sent an e-mail titled “Organizational Restructuring—Availability of Voluntary Reassignment, Early Out Retirement, and Separation Incentive Payments to ALL ELIGIBLE EMPLOYEES—No Component or Position Exceptions,” which seemed to pressure workers to leave. “A lot of this stuff is intentionally degrading,” Steven said. “They’re trying to do whatever they can to get people to resign.” Recently, he and other field-office staff were told that their jobs were safe because they were “mission critical.” That was reassuring, but only “a little bit.”
When the Equifax search proved inconclusive, Steven told the nonprofit, “I’ll have to put this on the back burner for a bit until I can get some info.” All three of his screens were noisy. In Microsoft Teams, a supervisor was asking for updates on specific cases. Another window showed the names of people waiting in the lobby of the field office, in real time. He stared at a name in the queue. “This one, I’ve been playing phone tag with her,” Steven said. He opened a chat to alert a colleague at the office.
The work is surprisingly personal. A Social Security file contains a lot of intimate information. From a quick glance, Steven can tell where a recipient was born, what language they speak, whether they’d been involved in the child-welfare system, if they are married, whether that marriage had ended as a result of divorce or death. He has some colleagues whose “attitudes suck to high heaven,” caused by a mix of stress and a suspicion of the poor. “I love helping people,” he said. “You’re the first contact for them.”
Next, Steven had to get “on the phones.” Fielding random calls on the S.S.A. hotline isn’t technically part of his job, but he didn’t question the assignment. For several weeks, everyone had been required to help out. “Good morning. Social Security. This is Steven,” he said. “What is your Social Security number, please? All right, starting with your name and date of birth . . .” He wrapped up his first few calls rather quickly. He sent out a missing tax document, scheduled a father for an in-person appointment to get a Social Security card for his baby, and confirmed bank information for a recipient’s direct deposit. A fourth call, involving a lost check, was more complicated. He rubbed his forehead with his thumbs and forefingers.
Steven later received two mass e-mails. The first reminded all S.S.A. employees to send their “mandatory weekly assignment”—the “What Did You Do Last Week” e-mail, with five bullet points summarizing what they had worked on—directly to the government’s Office of Personnel Management, not to anyone in their actual agency. The second one was yet another plea for workers to quit or take early retirement. It warned that some who opted to remain in “non-mission critical positions” might be reassigned to S.S.A. call centers. No definition of “non-mission critical” was offered.
“I just keep wondering, How long can I be doing this?” Steven said. Many years before Trump and DOGE, there was a period when he could not sleep. “The job would cause me to wake up in the middle of the night,” he said. “You know how your brain can’t shut stuff off, or you’re just dreading going in the next day?” He was troubled by certain cases—a girl who had been abused in foster care, only to end up with a grandmother who stole her S.S.I. checks. He was also haunted by the need to reach case quotas, never explicitly stated but often implied. “Cutting corners happens in this industry, when representatives are trying to just get something off their list,” he said. “So then it’s like, ‘I got that done.’ But did you really help the person?” His latest sources of worry were a news article in which O’Malley, the former S.S.A. commissioner, predicted “system collapse and an interruption of benefits” within “thirty to ninety days” and an affidavit by a former agency official that described DOGE’s violation of privacy protocols and the likelihood of “critical errors that could upend SSA systems.”
Steven has never been a zealot for anything except his favorite football team, but now he believes that he and his co-workers are part of an “underground movement” to prevent the destruction of Social Security. Trump and Musk, and more conventional Republicans, talk obsessively about rooting out fraud at the S.S.A. Mistakes and overpayments do occur, but the agency’s inspector general recently found that less than one per cent of benefits distributed between 2015 and 2022 were improper. Steven believes that mass layoffs will result in vulnerable Americans not getting the money they’re entitled to. “We service people at their best and worst times,” he said. “People heading into retirement, surviving spouses, widows, widowers. It used to be we’d get complaints from the public. We’d start off a call by apologizing. ‘We’re understaffed!’ ” Now, he went on, “people are apologizing to us.” ♦
33 notes
·
View notes
Text
Shamir Secret Sharing
It’s 3am. Paul, the head of PayPal database administration carefully enters his elaborate passphrase at a keyboard in a darkened cubicle of 1840 Embarcadero Road in East Palo Alto, for the fifth time. He hits Return. The green-on-black console window instantly displays one line of text: “Sorry, one or more wrong passphrases. Can’t reconstruct the key. Goodbye.”
There is nerd pandemonium all around us. James, our recently promoted VP of Engineering, just climbed the desk at a nearby cubicle, screaming: “Guys, if we can’t get this key the right way, we gotta start brute-forcing it ASAP!” It’s gallows humor – he knows very well that brute-forcing such a key will take millions of years, and it’s already 6am on the East Coast – the first of many “Why is PayPal down today?” articles is undoubtedly going to hit CNET shortly. Our single-story cubicle-maze office is buzzing with nervous activity of PayPalians who know they can’t help but want to do something anyway. I poke my head up above the cubicle wall to catch a glimpse of someone trying to stay inside a giant otherwise empty recycling bin on wheels while a couple of Senior Software Engineers are attempting to accelerate the bin up to dangerous speeds in the front lobby. I lower my head and try to stay focused. “Let’s try it again, this time with three different people” is the best idea I can come up with, even though I am quite sure it will not work.
It doesn’t.
The key in question decrypts PayPal’s master payment credential table – also known as the giant store of credit card and bank account numbers. Without access to payment credentials, PayPal doesn’t really have a business per se, seeing how we are supposed to facilitate payments, and that’s really hard to do if we no longer have access to the 100+ million credit card numbers our users added over the last year of insane growth.
This is the story of a catastrophic software bug I briefly introduced into the PayPal codebase that almost cost us the company (or so it seemed, in the moment.) I’ve told this story a handful of times, always swearing the listeners to secrecy, and surprisingly it does not appear to have ever been written down before. 20+ years since the incident, it now appears instructive and a little funny, rather than merely extremely embarrassing.
Before we get back to that fateful night, we have to go back another decade. In the summer of 1991, my family and I moved to Chicago from Kyiv, Ukraine. While we had just a few hundred dollars between the five of us, we did have one secret advantage: science fiction fans.
My dad was a highly active member of Zoryaniy Shlyah – Kyiv’s possibly first (and possibly only, at the time) sci-fi fan club – the name means “Star Trek” in Ukrainian, unsurprisingly. He translated some Stansilaw Lem (of Solaris and Futurological Congress fame) from Polish to Russian in the early 80s and was generally considered a coryphaeus at ZSh.
While USSR was more or less informationally isolated behind the digital Iron Curtain until the late ‘80s, by 1990 or so, things like FidoNet wriggled their way into the Soviet computing world, and some members of ZSh were now exchanging electronic mail with sci-fi fans of the free world.
The vaguely exotic news of two Soviet refugee sci-fi fans arriving in Chicago was transmitted to the local fandom before we had even boarded the PanAm flight that took us across the Atlantic [1]. My dad (and I, by extension) was soon adopted by some kind Chicago science fiction geeks, a few of whom became close friends over the years, though that’s a story for another time.
A year or so after the move to Chicago, our new sci-fi friends invited my dad to a birthday party for a rising star of the local fandom, one Bruce Schneier. We certainly did not know Bruce or really anyone at the party, but it promised good food, friendly people, and probably filk. My role was to translate, as my dad spoke limited English at the time.
I had fallen desperately in love with secret codes and cryptography about a year before we left Ukraine. Walking into Bruce’s library during the house tour (this was a couple years before Applied Cryptography was published and he must have been deep in research) felt like walking into Narnia.
I promptly abandoned my dad to fend for himself as far as small talk and canapés were concerned, and proceeded to make a complete ass out of myself by brazenly asking the host for a few sheets of paper and a pencil. Having been obliged, I pulled a half dozen cryptography books from the shelves and went to work trying to copy down some answers to a few long-held questions on the library floor. After about two hours of scribbling alone like a man possessed, I ran out of paper and decided to temporarily rejoin the party.
On the living room table, Bruce had stacks of copies of his fanzine Ramblings. Thinking I could use the blank sides of the pages to take more notes, I grabbed a printout and was about to quietly return to copying the original S-box values for DES when my dad spotted me from across the room and demanded I help him socialize. The party wrapped soon, and our friends drove us home.
The printout I grabbed was not a Ramblings issue. It was a short essay by Bruce titled Sharing Secrets Among Friends, essentially a humorous explanation of Shamir Secret Sharing.
Say you want to make sure that something really really important and secret (a nuclear weapon launch code, a database encryption key, etc) cannot be known or used by a single (friendly) actor, but becomes available, if at least n people from a group of m choose to do it. Think two on-duty officers (from a cadre of say 5) turning keys together to get ready for a nuke launch.
The idea (proposed by Adi Shamir – the S of RSA! – in 1979) is as simple as it is beautiful.
Let’s call the secret we are trying to split among m people K.
First, create a totally random polynomial that looks like: y(x) = C0 * x^(n-1) + C1 * x^(n-2) + C2 * x^(n-3) ….+ K. “Create” here just means generate random coefficients C. Now, for every person in your trusted group of m, evaluate the polynomial for some randomly chosen Xm and hand them their corresponding (Xm,Ym) each.
If we have n of these points together, we can use Lagrange interpolating polynomial to reconstruct the coefficients – and evaluate the original polynomial at x=0, which conveniently gives us y(0) = K, the secret. Beautiful. I still had the printout with me, years later, in Palo Alto.
It should come as no surprise that during my time as CTO PayPal engineering had an absolute obsession with security. No firewall was one too many, no multi-factor authentication scheme too onerous, etc. Anything that was worth anything at all was encrypted at rest.
To decrypt, a service would get the needed data from its database table, transmit it to a special service named cryptoserv (an original SUN hardware running Solaris sitting on its own, especially tightly locked-down network) and a special service running only there would perform the decryption and send back the result.
Decryption request rate was monitored externally and on cryptoserv, and if there were too many requests, the whole thing was to shut down and purge any sensitive data and keys from its memory until manually restarted.
It was this manual restart that gnawed at me. At launch, a bunch of configuration files containing various critical decryption keys were read (decrypted by another key derived from one manually-entered passphrase) and loaded into the memory to perform future cryptographic services.
Four or five of us on the engineering team knew the passphrase and could restart cryptoserv if it crashed or simply had to have an upgrade. What if someone performed a little old-fashioned rubber-hose cryptanalysis and literally beat the passphrase out of one of us? The attacker could theoretically get access to these all-important master keys. Then stealing the encrypted-at-rest database of all our users’ secrets could prove useful – they could decrypt them in the comfort of their underground supervillain lair.
I needed to eliminate this threat.
Shamir Secret Sharing was the obvious choice – beautiful, simple, perfect (you can in fact prove that if done right, it offers perfect secrecy.) I decided on a 3-of-8 scheme and implemented it in pure POSIX C for portability over a few days, and tested it for several weeks on my Linux desktop with other engineers.
Step 1: generate the polynomial coefficients for 8 shard-holders.
Step 2: compute the key shards (x0, y0) through (x7, y7)
Step 3: get each shard-holder to enter a long, secure passphrase to encrypt the shard
Step 4: write out the 8 shard files, encrypted with their respective passphrases.
And to reconstruct:
Step 1: pick any 3 shard files.
Step 2: ask each of the respective owners to enter their passphrases.
Step 3: decrypt the shard files.
Step 4: reconstruct the polynomial, evaluate it for x=0 to get the key.
Step 5: launch cryptoserv with the key.
One design detail here is that each shard file also stored a message authentication code (a keyed hash) of its passphrase to make sure we could identify when someone mistyped their passphrase. These tests ran hundreds and hundreds of times, on both Linux and Solaris, to make sure I did not screw up some big/little-endianness issue, etc. It all worked perfectly.
A month or so later, the night of the key splitting party was upon us. We were finally going to close out the last vulnerability and be secure. Feeling as if I was about to turn my fellow shard-holders into cymeks, I gathered them around my desktop as PayPal’s front page began sporting the “We are down for maintenance and will be back soon” message around midnight.
The night before, I solemnly generated the new master key and securely copied it to cryptoserv. Now, while “Push It” by Salt-n-Pepa blared from someone’s desktop speakers, the automated deployment script copied shard files to their destination.
While each of us took turns carefully entering our elaborate passphrases at a specially selected keyboard, Paul shut down the main database and decrypted the payment credentials table, then ran the script to re-encrypt with the new key. Some minutes later, the database was running smoothly again, with the newly encrypted table, without incident.
All that was left was to restore the master key from its shards and launch the new, even more secure cryptographic service.
The three of us entered our passphrases… to be met with the error message I haven’t seen in weeks: “Sorry, one or more wrong passphrases. Can’t reconstruct the key. Goodbye.” Surely one of us screwed up typing, no big deal, we’ll do it again. No dice. No dice – again and again, even after we tried numerous combinations of the three people necessary to decrypt.
Minutes passed, confusion grew, tension rose rapidly.
There was nothing to do, except to hit rewind – to grab the master key from the file still sitting on cryptoserv, split it again, generate new shards, choose passphrases, and get it done. Not a great feeling to have your first launch go wrong, but not a huge deal either. It will all be OK in a minute or two.
A cursory look at the master key file date told me that no, it wouldn’t be OK at all. The file sitting on cryptoserv wasn’t from last night, it was created just a few minutes ago. During the Salt-n-Pepa-themed push from stage, we overwrote the master key file with the stage version. Whatever key that was, it wasn’t the one I generated the day before: only one copy existed, the one I copied to cryptoserv from my computer the night before. Zero copies existed now. Not only that, the push script appears to have also wiped out the backup of the old key, so the database backups we have encrypted with the old key are likely useless.
Sitrep: we have 8 shard files that we apparently cannot use to restore the master key and zero master key backups. The database is running but its secret data cannot be accessed.
I will leave it to your imagination to conjure up what was going through my head that night as I stared into the black screen willing the shards to work. After half a decade of trying to make something of myself (instead of just going to work for Microsoft or IBM after graduation) I had just destroyed my first successful startup in the most spectacular fashion.
Still, the idea of “what if we all just continuously screwed up our passphrases” swirled around my brain. It was an easy check to perform, thanks to the included MACs. I added a single printf() debug statement into the shard reconstruction code and instead of printing out a summary error of “one or more…” the code now showed if the passphrase entered matched the authentication code stored in the shard file.
I compiled the new code directly on cryptoserv in direct contravention of all reasonable security practices – what did I have to lose? Entering my own passphrase, I promptly got “bad passphrase” error I just added to the code. Well, that’s just great – I knew my passphrase was correct, I had it written down on a post-it note I had planned to rip up hours ago.
Another person, same error. Finally, the last person, JK, entered his passphrase. No error. The key still did not reconstruct correctly, I got the “Goodbye”, but something worked. I turned to the engineer and said, “what did you just type in that worked?”
After a second of embarrassed mumbling, he admitted to choosing “a$$word” as his passphrase. The gall! I asked everyone entrusted with the grave task of relaunching crytposerv to pick really hard to guess passphrases, and this guy…?! Still, this was something -- it worked. But why?!
I sprinted around the half-lit office grabbing the rest of the shard-holders demanding they tell me their passphrases. Everyone else had picked much lengthier passages of text and numbers. I manually tested each and none decrypted correctly. Except for the a$$word. What was it…
A lightning bolt hit me and I sprinted back to my own cubicle in the far corner, unlocked the screen and typed in “man getpass” on the command line, while logging into cryptoserv in another window and doing exactly the same thing there. I saw exactly what I needed to see.
Today, should you try to read up the programmer’s manual (AKA the man page) on getpass, you will find it has been long declared obsolete and replaced with a more intelligent alternative in nearly all flavors of modern Unix.
But back then, if you wanted to collect some information from the keyboard without printing what is being typed in onto the screen and remain POSIX-compliant, getpass did the trick. Other than a few standard file manipulation system calls, getpass was the only operating system service call I used, to ensure clean portability between Linux and Solaris.
Except it wasn’t completely clean.
Plain as day, there it was: the manual pages were identical, except Solaris had a “special feature”: any passphrase entered that was longer than 8 characters long was automatically reduced to that length anyway. (Who needs long passwords, amiright?!)
I screamed like a wounded animal. We generated the key on my Linux desktop and entered our novel-length passphrases right here. Attempting to restore them on a Solaris machine where they were being clipped down to 8 characters long would never work. Except, of course, for a$$word. That one was fine.
The rest was an exercise in high-speed coding and some entirely off-protocol file moving. We reconstructed the master key on my machine (all of our passphrases worked fine), copied the file to the Solaris-running cryptoserv, re-split it there (with very short passphrases), reconstructed it successfully, and PayPal was up and running again like nothing ever happened.
By the time our unsuspecting colleagues rolled back into the office I was starting to doze on the floor of my cubicle and that was that. When someone asked me later that day why we took so long to bring the site back up, I’d simply respond with “eh, shoulda RTFM.”
RTFM indeed.
P.S. A few hours later, John, our General Counsel, stopped by my cubicle to ask me something. The day before I apparently gave him a sealed envelope and asked him to store it in his safe for 24 hours without explaining myself. He wanted to know what to do with it now that 24 hours have passed.
Ha. I forgot all about it, but in a bout of “what if it doesn’t work” paranoia, I printed out the base64-encoded master key when we had generated it the night before, stuffed it into an envelope, and gave it to John for safekeeping. We shredded it together without opening and laughed about what would have never actually been a company-ending event.
P.P.S. If you are thinking of all the ways this whole SSS design is horribly insecure (it had some real flaws for sure) and plan to poke around PayPal to see if it might still be there, don’t. While it served us well for a few years, this was the very first thing eBay required us to turn off after the acquisition. Pretty sure it’s back to a single passphrase now.
Notes:
1: a member of Chicagoland sci-fi fan community let me know that the original news of our move to the US was delivered to them via a posted letter, snail mail, not FidoNet email!
522 notes
·
View notes
Text
A quiet place to work - pt. 1
As you entered the bullpen this morning there was pure chaos. Everyone was upset that they couldn't work. That was the reason why they called you at 7am and ordered you to immediately come to the office.
“Hey, McGee! What have you broken this time?” you asked him nearing his desk.
“Me? Nothing. But nobody can work anymore because of this error we get if we do anything in our software.”
He showed you the error on the screen for you to read. You read it two times then furrowed your brows and murmured “that's a database error.”
Gibbs and director Shepard had come to you and were not amused.
“Y/N! Nobody can work anymore. Fix the error as soon as possible!” Jenny ordered loudly.
“Any idea what's the cause of the problem?” Gibbs asked.
He was not amused, but relatively quiet compared to the director.
You took a deep breath and answered
“I don't have any clue right now. I have to run a few tests and protocols to analyze this.”
“How long?” Gibbs stated.
You shrugged your shoulders “don't know. Depends on what the problem is, when I find it and how it can be solved.”
“Work quickly. Everything is stopped at the moment and that can't be.” Madam director ordered and went to her office slightly annoyed.
You watched her go, rolled your eyes, sat at your table and began to work.
While you tried to concentrate your colleagues constantly came and disturbed you when they asked about the status of things.
Your phone was constantly ringing too and you did your best to ignore it. After 1 hour of nearly constantly ringing Jenny stood in front of your desk and seemed to be angry.
“I've tried to call you multiple times,” she said. “Yep. I've ignored you,” you just answered matter of factly. You didn't look up and just tipped away on your keyboard.
Jenny on the other hand huffed and stormed away again.
Tim tried to be invisible and Gibbs grinned. Tony was smiling widely, coming to you stating “wow, Y/N. Finding a whole new respect for you.”
You stopped typing and looked at him without saying a word. He laughed, held his hands up and retreated to his desk.
After another 30 minutes the director came again to ask the status of the progress. She huffed, fumed and yelled at you “you are still not getting to the phone when I call you! I can't WORK!!!”
You just looked up, reached behind the phone and held up the loose plug, saying calmly but slightly annoyed “I pulled out the plug.”
Everyone was quiet, the atmosphere was tense and Gibbs was watching the events with interest and grinned from one ear to the other. At least he seemed to be having fun.
Now Jenny was losing it and yelled again “you can’t do that! You have to be available!”
You stood up, leaned on your desk and replied as calmly as possible “yes, I can do that. It was very easy. Just pulled the plug. And I AM available. Otherwise you couldn't be standing here in front of me and snapping at me.”
A quiet snort could be heard from Tony and Gibbs, who were giving you mentally a medal. Tim has taken cover behind his computer.
Jenny then snapped “you are just as impossible as Gibbs! He is really rubbing off on you!”
“Why? Because maybe he just wants to do his work in peace and concentrate?”
Madam director gasped and opened and closed her mouth like a fish, not knowing what to respond.
You stood up, put your hands on your hips and said slowly and threateningly “you can call me every minute and get on my nerves because you can’t work. But the only thing you’ll achieve is to tear me out of concentration and slow down the analysis and correction. If you want to contribute something productive, you can get me some fresh coffee. Working without coffee is bordering on physical assault”
You were about to explode, so you tried to compose yourself and keep as calm as possible. She was your big boss after all.
So you pushed your cup into her hand, sat down and said “and now let me do my work in peace.”
With that this conversation was closed for you and you got back to concentrate on the problem and ran further protocols and tests.
Jenny stomped away indignantly, the colleagues laughed loudly and Gibbs patted you on the shoulder “well done. I didn't know you could be so dangerous.” You were amazed and perplexed hearing these words from your boss.
“Let me do my job and correct this shit” you huffed.
He laughed briefly, smiled and replied “come with me, I know a place where you can work in peace and nobody will bother you. There's good coffee too.”
You looked stunned at him, smiled and answered “I'm in.”
You both packed your things and went to Gibbs’ Truck. “Were are we going to?” you asked curiously. “Wait and see” Gibbs answered, smiling.
In fact, he was driving to his house, you noticed in surprise. “Come inside and let's get some coffee” he stated.
“Uhm….” You couldn't say a word.
“Now. Come on” he ordered you rolling with his eyes.
Quickly you got out of his car and followed him inside. He was standing in the kitchen and made some coffee. As he heard you enter he turned around “make yourself at home. You can sit in the dining room or in the basement. Just take a seat where you think you can work with concentration.”
So you took residence at the dining room table and started your laptop. Until you opened the needed programs a mug came into your view and the coffee smelled heavenly. You looked up at your smirking boss who told you “coffee with a lot of milk, I think it is, right?”
You were speechless that he knew this and just nodded “thanks”.
“You're welcome. I'm down in the basement. Call, if you need something.”
“Okay, will do.”
“Good.”
So Gibbs went downstairs and you began to work on the problem again.
But after half an hour you had a feeling of being lonely, took your laptop and walked down the stairs that led to the basement, where Gibbs was working on his boat.
Seeing you standing there he stopped in his work and watched you “you need something?”
“Hm, yes. I'm feeling a little bit lonely up there. Can I work here?”
He laughed briefly “sure. You can sit on the workbench over there” he said and pointed to it.
You smiled, walked to the place he showed you and whispered “thank you.”
So the two of you worked in the basement and enjoyed the company and the silence.
After another half an hour you cried out “I've got it!!!”
Gibbs watched you intently and waited for your explanation.
“I've found the reason for the error. Someone had interrupted a saving process and therefore corrupted the database. But thankfully I can repair this easily.”
“Good” was the only response you got, but you were nonetheless working on the repair again, typing away.
A short while later you had done the repair, tested it and everything was good once more. The problem was solved and inwardly you patted yourself on your shoulder.
So Gibbs and you drove back to the office to check, if everyone else could work again, too. And yes, they could. You were sooo happy!!!
Only one task was left. You had to go to the director to inform her. You sighed and started to go to her, but you were held back by your upper arm.
“I'm coming with you. Don't let yourself go in there alone.”
Entering her office Jenny growled “these are exactly the two I wanted to see. They're both the same.”
“It was a database error, but I could repair it. Just let me check quickly, if everything's okay on your computer. Then you can go back to work again.”
You checked the system and everything was fine once more.
“Thank you.”
“That's my job.” You said.
“I'm sorry for my behavior earlier. I have a due date to keep.” Jenny admitted.
“It's okay, but when I can't work because I'm interrupted all the time, the correction needs more time.”
“Understand.” Jenny said and hung her head.
Gibbs and you left her office. On the way to your desks, he pulled you aside and whispered in your ear
“Dinner. Tonight. Straight after work. I want to know more about you.”
If you want to know where the dinner leads, you have to read Chapter 2. 😊😉
----------------------------------------------
Here you will find the other chapter of this story
Back to the overview of this story
Back to the main Masterlist
Back to the alternative Masterlist
-----------------------------------------------
#ncis#jethro gibbs x reader#gibbs#leroy jethro gibbs#gibbs x reader#leroy jethro gibbs x reader#ncis fanfiction#ncis x reader#ncis reader insert#leroy jethro gibbs fanfiction#jethro gibbs fanfiction#gibbs fanfiction#jethro gibbs#mark harmon
143 notes
·
View notes
Note
Hello! I'm currently an MLIS student (no focus yet), and I've been thinking about getting a History MA as well. I've been told that doubling up on Master's degrees can be a hindrance in getting work as it makes it look like you can't commit to one field, but I noticed that you have an MLIS and a History MA. How were you able to make that work? Was it because of the overlap of topics you were studying?
(for extra context, I'm in the U.S. and I would be looking at an MA in late antique or medieval history)
The unvarnished truth is that there are way more people with degrees in our field than there are jobs, especially in blue states. Anything you have that can put you ahead of the pack, including a subject-specific MA, is good. Especially now that, as universities have so effectively cannibalized themselves, we have a glut of PhDs who can’t get TT positions horning in on the GLAM (Galleries, Libraries, Archives, and Museums) professions.
As for my career and the doubling up; it worked until it didn’t—in this profession it’s very difficult to move up or get a pay raise unless you’re willing to become a manager; and the pay in this field has NOT kept pace with COL or inflation.
To best position yourself in the job market, you need to get your MA in a modern field. Late Antiquity and Medieval GLAM jobs in this country are few and far between, and the competition is typically PhDs.
A Masters in some aspect of US history will be the best for you to build a case for yourself as a successful candidate. Also, learning database science, and as much coding and software as you can before you finish your degree.
Sorry for the cynicism. I have ten years of experience in this field plus the masters degrees and I haven’t even been contacted for an interview in over a year.
ETA: all of this said, if some random 35 year old had given me this advice when I was just starting grad school at the (too young, imo) age of 22, I would have blown it off as the rantings of a lazy, bitter failure so, ymmv. (Here, I would say “ah the arrogance of youth,” but I’ve always been stubborn and pig headed about my goals lol)
35 notes
·
View notes
Text
Ok I've had a very random train of thoughts and now wanna compile it into post.
Some MM characters computer-related (???) headcanons lol
Riley:
Has above average knowledge of Excel/Google sheets due to studying finance, but after four years with no practise forgot most of it.
The "Sooon, I have a problem" person in their family. Actually, surprisingly good and patient at explaining computer stuff to older people.
Has a higher responsibility of doing taxes (finance, after all). Even he never fails to do them right, Ed always double checks. Sometimes they get into argument, where inevitably Riley proves he is right but his father would never admit it.
Warren, Leeza, Ooker and other teens:
Also nothing outstanding in terms of skills, except few of them have interest in IT.
They have bunch of small local Discord servers and one big main server with some very stupid name.
Few times Bev tried to bring up importance of parental control over this "new and rapidly growing young community", but thanks God no one took her concerns seriously
Leeza moderates it and her moder role called "Mayor-mini". Like father like daughter.
All teens local jokes and memes were bourn/spread though that server.
Bev:
Rumors says she sacrificed her humanity to obtain such powers with Microsoft software package.
Can build up Access database from scratch, using basic SQL commands, assemble primitive, but surprisingly sufficient interface to it and synchronize it with Excel in span of one day or less.
In her laptop there're every pupil's personal file, countless Excel tables, several automatised document accounts, Google calendar with precisely planned schedule for next several months (for school, church, island and personal matters) and probably Pentagon files.
Probably can find all Pi numbers with Excel formulas.
Never lets anyone to her laptop.
Spends her free time at different forums, mostly gardening-related.
Wade:
Made a very fucking poor decision to let Bev do all the legwork with digital document accounting.
Now has no idea how some of things even work, so just goes with a flow and does what Bev tells.
No wander she got away with embezzlement.
Knows about kid's server. Very proud of Leeza for managing it :)
Because of that, he knows one or two memes from there, but keeps them in secret.
Has hobby of fixing office equipment. Does it with Sturge in spare time due to Dupuytren's contracture not letting him operate his hand fully.
Sarah:
There's no good medical technicians on island, so when something goes wrong with equipment electronics - tries to fix it herself to best of her ability.
Always monitors electronic e-shops for spare details or equipment. Grows more and more addicted to it.
Frequently updates her selection of sites with useful medical information, because Erin asked her for help guiding teens though puberty. For that receives glances from Bev, but doesn't give a shit.
Has reputation of cool aunt among kids, so she was one and only adult invited to main Discord server. Didn't accept it (doesn't even have Discord acc), but still grateful for trust.
Plays solitaire a lot.
John:
Back when he was playing Paul, Bev asked him to do something with Excel. In conclusion, poor bastard had to learn basic computer skills and Excel in span of several days. Now he is traumatized for rest of his life.
Will do all the work manually just to not touch laptop again.
Upsets very easly when does something wrong.
Doesn't own laptop. Don't give that man laptop, he will cry.
By his own will uses it only to watch baseball. Always asks someone to help with that.
#midnight mass#midnight mass headcanons#beverly keane#idk I just felt silly and wanted to write it down#riley flynn#warren flynn#leeza scarborough#wade scarborough#sarah gunning#john pruitt#monsignor pruitt#father paul hill
24 notes
·
View notes
Text
Streamlining Your Institute Library: Embracing the Best Library Management Software
In managing an institute library efficiently is crucial for academic success. Traditional library management systems are rapidly being replaced by sophisticated digital solutions designed to enhance accessibility, organization, and overall user experience. One such key player in revolutionizing library management is the implementation of the best library management software.
The best library management software brings a plethora of benefits to institute libraries, simplifying tasks, reducing human errors, and fostering a seamless user experience.
Efficient Cataloging and Organization:
The heart of any library is its catalog, and managing it effectively is paramount. The best library management software enables automated cataloging, making it easy to organize books, journals, and other resources systematically. With user-friendly interfaces and intuitive search features, finding and accessing materials becomes a breeze for both staff and students.

Real-time Inventory Tracking:
Say goodbye to the challenges of manual inventory tracking. Digital library solutions provide real-time updates on the availability of resources, allowing librarians to monitor stock levels effortlessly. This not only saves time but also ensures that users have accurate information about the availability of materials.
Enhanced User Experience:
A well-designed library management software prioritizes the user experience. Students and faculty members can conveniently access the library's resources from anywhere, whether on campus or remotely. The software's user-friendly interface encourages engagement, making it easy for users to explore the catalog, check out materials, and even reserve items online.
Data Security and Analytics:
Security is a top concern in the digital age, especially when it comes to valuable educational resources. The best library management software offers robust security features to protect sensitive information and prevent unauthorized access. Additionally, these systems often come equipped with analytics tools, allowing institutions to gather insights into library usage patterns, popular resources, and other valuable data to inform decision-making.
In conclusion, embracing the best library management software is a transformative step toward modernizing institute libraries. From efficient cataloging and real-time inventory tracking to enhancing the overall user experience, these digital solutions pave the way for a more streamlined and technologically advanced approach to library management. As educational institutions continue to evolve, investing in such solutions becomes not only a necessity but a strategic move toward ensuring a dynamic and resourceful learning environment.
#Best Library Management Software#Library Management System Software#Library Management System#Online Library Management System#employee database management system
0 notes