#contract management software features
Explore tagged Tumblr posts
Text
9 Must-Have Features for Your Contract Management Software in 2023

Contracts are one of the foundational elements of a stable business operation. They form the basis on which any business relationship is formed. Thus, contract management is important for any enterprise regardless of industry or size.
With enterprises growing fast, powered by modern technological advancement, contract management has grown exponentially from what it used to be. A cloud-based contract management system helps businesses avoid manual contract procedures and manage them effortlessly.
Most businesses invest in contract management software without analyzing what features they need. Even though you may have good contract management software features, poorly negotiated and managed contracts could negatively affect business relationships.
Do your contract management software features align with your contracting requirements? Are your contract management software’s features simplifying contract management? Is there any room for improvement?
If you’re looking to revamp your existing contract management system or deploy a new automated contract management system, it is essential to understand the business needs and check the features that would fulfil the requirements.
Read More : https://www.vuram.com/blog/nine-features-your-contract-management-software-must-have-in-2022/
➤ Next best reads for you:
Blogs:
5 Ways Contract Lifecycle Management Mitigates Contract Risks & Costs
5 Signs You Need A New Approach To Contract Management
10 Reasons Why You Shouldn’t Ignore Contract Management System
News:
Adopting an empathy-first approach to nurture equity
Rising star recognition from ISG provider lens
Transforming customer onboarding with hyperautomation
#Contract Management#Contract Management Software#Contract Management Features#Contract Management System
0 notes
Text
An adversarial iMessage client for Android
Adversarial interoperability is one of the most reliable ways to protect tech users from predatory corporations: that's when a technologist reverse-engineers an existing product to reconfigure or mod it (interoperability) in ways its users like, but which its manufacturer objects to (adversarial):
https://www.eff.org/deeplinks/2019/10/adversarial-interoperability
"Adversarial interop" is a mouthful, so at EFF, we coined the term "competitive compatibility," or comcom, which is a lot easier to say and to spell.
Scratch any tech success and you'll find a comcom story. After all, when a company turns its screws on its users, it's good business to offer an aftermarket mod that loosens them again. HP's $10,000/gallon inkjet ink is like a bat-signal for third-party ink companies. When Mercedes announces that it's going to sell you access to your car's accelerator pedal as a subscription service, that's like an engraved invitation to clever independent mechanics who'll charge you a single fee to permanently unlock that "feature":
https://www.techdirt.com/2023/12/05/carmakers-push-forward-with-plans-to-make-basic-features-subscription-services-despite-widespread-backlash/
Comcom saved giant tech companies like Apple. Microsoft tried to kill the Mac by rolling out a truly cursèd version of MS Office for MacOS. Mac users (5% of the market) who tried to send Word, Excel or Powerpoint files to Windows users (95% of the market) were stymied: their files wouldn't open, or they'd go corrupt. Tech managers like me started throwing the graphic designer's Mac and replacing it with a Windows box with a big graphics card and Windows versions of Adobe's tools.
Comcom saved Apple's bacon. Apple reverse-engineered MS's flagship software suite and made a comcom version, iWork, whose Pages, Numbers and Keynote could flawlessly read and write MS's Word, Excel and Powerpoint files:
https://www.eff.org/deeplinks/2019/06/adversarial-interoperability-reviving-elegant-weapon-more-civilized-age-slay
It's tempting to think of iWork as benefiting Apple users, and certainly the people who installed and used it benefited from it. But Windows users also benefited from iWork. The existence of iWork meant that Windows users could seamlessly collaborate on and share files with their Mac colleagues. IWork didn't just add a new feature to the Mac ("read and write files that originated with Windows users") – it also added a feature to Windows: "collaborate with Mac users."
Every pirate wants to be an admiral. Though comcom rescued Apple from a monopolist's sneaky attempt to drive it out of business, Apple – now a three trillion dollar company – has repeatedly attacked comcom when it was applied to Apple's products. When Apple did comcom, that was progress. When someone does comcom to Apple, that's piracy.
Apple has many tools at its disposal that Microsoft lacked in the early 2000s. Radical new interpretations of existing copyright, contract, patent and trademark law allows Apple – and other tech giants – to threaten rivals who engage in comcom with both criminal and civil penalties. That's right, you can go to prison for comcom these days. No wonder Jay Freeman calls this "felony contempt of business model":
https://pluralistic.net/2023/11/09/lead-me-not-into-temptation/#chamberlain
Take iMessage, Apple's end-to-end encrypted (E2EE) instant messaging tool. Apple customers can use iMessage to send each other private messages that can't be read or altered by third parties – not cops, not crooks, not even Apple. That's important, because when private messaging systems get hacked, bad things happen:
https://en.wikipedia.org/wiki/2014_celebrity_nude_photo_leak
But Apple has steadfastly refused to offer an iMessage app for non-Apple systems. If you're an Apple customer holding a sensitive discussion with an Android user, Apple refuses to offer you a tool to maintain your privacy. Those messages are sent "in the clear," over the 38-year-old SMS protocol, which is trivial to spy on and disrupt.
Apple sacrifices its users' security and integrity in the hopes that they will put pressure on their friends to move into Apple's walled garden. As CEO Tim Cook told a reporter: if you want to have secure communications with your mother, buy her an iPhone:
https://finance.yahoo.com/news/tim-cook-says-buy-mom-210347694.html
Last September, a 16-year old high school student calling himself JJTech published a technical teardown of iMessage, showing how any device could send and receive encrypted messages with iMessage users, even without an Apple ID:
https://jjtech.dev/reverse-engineering/imessage-explained/
JJTech even published code to do this, in an open source library called Pypush:
https://github.com/JJTech0130/pypush
In the weeks since, Beeper has been working to productize JJTech's code, and this week, they announced Beeper Mini, an Android-based iMessage client that is end-to-end encrypted:
https://beeper.notion.site/How-Beeper-Mini-Works-966cb11019f8444f90baa314d2f43a54
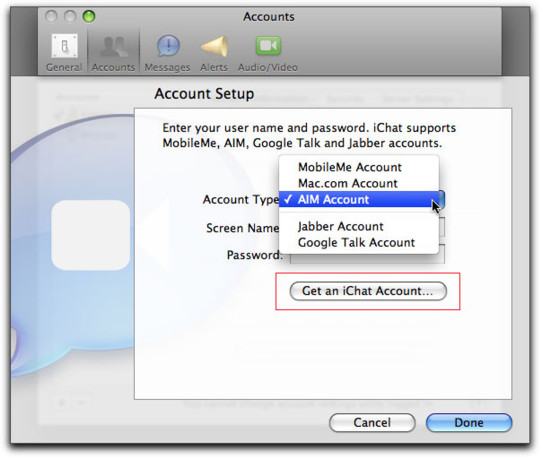
Beeper is known for a multiprotocol chat client built on Matrix, allowing you to manage several kinds of chat from a single app. These multiprotocol chats have been around forever. Indeed, iMessage started out as one – when it was called "iChat," it supported Google Talk and Jabber, another multiprotocol tool. Other tools like Pidgin have kept the flame alive for decades, and have millions of devoted users:
https://www.eff.org/deeplinks/2021/07/tower-babel-how-public-interest-internet-trying-save-messaging-and-banish-big
But iMessage support has remained elusive. Last month, Nothing launched Sunchoice, a disastrous attempt to bring iMessage to Android, which used Macs in a data-center to intercept and forward messages to Android users, breaking E2EE and introducing massive surveillance risks:
https://www.theverge.com/2023/11/21/23970740/sunbird-imessage-app-shut-down-privacy-nothing-chats-phone-2
Beeper Mini does not have these defects. The system encrypts and decrypts messages on the Android device itself, and directly communicates with Apple's servers. It gathers some telemetry for debugging, and this can be turned off in preferences. It sends a single SMS to Apple's servers during setup, which changes your device's bubble from green to blue, so that Apple users now correctly see your device as a secure endpoint for iMessage communications.
Beeper Mini is now available in Google Play:
https://play.google.com/store/apps/details?id=com.beeper.ima&hl=en_US
Now, this is a high-stakes business. Apple has a long history of threatening companies like Beeper over conduct like this. And Google has a long history deferring to those threats – as it did with OG App, a superior third-party Instagram app that it summarily yanked after Meta complained:
https://pluralistic.net/2023/02/05/battery-vampire/#drained
But while iMessage for Android is good for Android users, it's also very good for Apple customers, who can now get the privacy and security guarantees of iMessage for all their contacts, not just the ones who bought the same kind of phone as they did. The stakes for communications breaches have never been higher, and antitrust scrutiny on Big Tech companies has never been so intense.
Apple recently announced that it would add RCS support to iOS devices (RCS is a secure successor to SMS):
https://9to5mac.com/2023/11/16/apple-rcs-coming-to-iphone/
Early word from developers suggests that this support will have all kinds of boobytraps. That's par for the course with Apple, who love to announce splashy reversals of their worst policies – like their opposition to right to repair – while finding sneaky ways to go on abusing its customers:
https://pluralistic.net/2023/09/22/vin-locking/#thought-differently
The ball is in Apple's court, and, to a lesser extent, in Google's. As part of the mobile duopoly, Google has joined with Apple in facilitating the removal of comcom tools from its app store. But Google has also spent millions on an ad campaign shaming Apple for exposing its users to privacy risks when talking to Android users:
https://www.theverge.com/2023/9/21/23883609/google-rcs-message-apple-iphone-ipager-ad
While we all wait for the other shoe to drop, Android users can get set up on Beeper Mini, and technologists can kick the tires on its code libraries and privacy guarantees.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2023/12/07/blue-bubbles-for-all/#never-underestimate-the-determination-of-a-kid-who-is-time-rich-and-cash-poor
#pluralistic#multiprotocol#interoperability#adversarial interop#beeper#reverse engineering#blue bubbles#green bubbles#e2ee#end to end encrypted#messaging#jjtech#pypushbeeper mini#matrix#competitive compatibility#comcom
1K notes
·
View notes
Text
Leverage Redemption Fic Recs
This list will include all ratings and tags, so read at your own discretion! :)
Happy LevRed Season Finale!!
Find Previous Leverage Lists here! (Leverage, Tap Out Job, Carnival Job, Rundown Job)
Our Unexpected Family Reunion by cminerva, GlassFullOfSass - Rated G
In which Harry meets more of the extended Leverage family.
The Job-Gone-Wrong Job by Grammar_Beane - Not Rated
Eliot’s voice came out tense. “Breanna’s gone. Her comms are dead.” Parker’s eyes widened, but she allowed no other tension to enter her body. “Okay. Plan doesn’t change much. Sophie. Go in. Find Breanna.” “I can’t.” Sophie’s voice grew cold as she saw the man standing at the front door. “Jim Sterling’s here.” --- The job was going perfectly. Until it wasn't. Now everyone's in an unfamiliar role, Breanna's been captured, and it's all resting on Harry Wilson to save her.
Not An Emotion by nerdsandthelike - Rated T
Breanna: Did you hack Lockheed Martin?! For me?!!
Hardison: No, I hacked Lockheed Martin because they’re shitty people who deserve to have their corruption exposed to the world. I downloaded their R&D software and drone specs for you.
How each member of the Leverage Redemption team shows Breanna affection.
After Date Night by Grammar_Beane - Rated T
The Leverage OT3 gets patched up after date night. – – – “Does this sort of thing happen every date night?” “No,” Eliot replied, at the same time Parker said, “Yep!” “It might be becoming a theme,” Hardison admitted.
Three of Twelve Job by WhenICantWrite - Rated G
The one where Eliot fights a lion
Parker's Peculiar Polyculians by Singing_Siren - Rated T
Emotions are… fiddly. She can’t grab onto them, hold them close, and inspect them like she does the stuff she steals. What’s the difference between attraction and love? Is it sex? That seems too simple, and emotions are never simple. Sophie taught her that. But Hardison taught her that things don’t have to be complicated, that going with the flow isn't as bad as she thought it would be. “You know,” Parker starts, “before I met you all, things were so much simpler.” What was it Eliot said when they were conning those Nana-Haters? ‘Parker has a very binary sense of right and wrong.’ Before the team got together, she saw the world in black and white. Now she can see shades of gray. There are even hints of color when she closes her eyes. (or: the aftermath of the Polygeist Job, featuring a Parker who's been through enough therapy to detangle some of her feelings)
The Habeas Corpus Job by hyacinthgirlboy - Rated T
Harry knows where he stands with this crew. Breanna is their little sister. He’s just a guy who handles their contracts sometimes. And yet here he is, drinking their bourbon in their house when something had gone horribly wrong, and it had been his fault. A mark's clever fakeout causes Harry to spiral a little. Breanna and Sophie are there to clear up any misconceptions.
Drive by ziazippy5379 - Rated G
Harry is driving the girls back from a college visit.
irredeemable by idkimoutofideas - Rated T
“Take that one as collateral,” Fisher said, jerking his chin at Harry. A guard stepped forward and grabbed Harry’s arm, yanking him to his feet. Harry shouted in surprise, and Eliot rose with him, shoulder checking Harry out of the way with a growl—Harry wasn’t sure how he managed to stand, given the blood staining his jeans. Eliot offers to be the hostage when he and Harry are kidnapped together. BTHB: take me instead
the textbook definition by tziporim (ferns) - T
Breanna’s burning the digital midnight oil when Harry shows up looking like a kicked dog.
Old Friends by Singing_Siren - Rated G
“Sophie,” Parker whispers harshly, her left eye twitching an erratic rhythm. Every muscle in her body tenses up like she’s about to break into a sprint, and it takes everything in her not to give into that instinct. Ooh, she wants to get closer. But she can’t! She shouldn’t. “Cameras.” A sensation not unlike a freefall builds in her stomach as she watches the two people that just entered. Blonde hair, a familiar laugh, Maggie Collins with a boring man on her arm and an elegant dress that sparkles in the light of the chandelier. There's a beat as Sophie no doubt nudges Harry out of the way to check the screens herself. “Oh no,” she says eloquently.
Holidays by Anonymous - Rated G
Or, Breanna really likes Halloween, and Harry wants to help her have a great one.
tulips and carnations (and a knife) by oopshenangians - Rated T
Eliot doesn't want to dress up as a knight again. But, if Parker and Hardison and Breanna are all going, then he'll go too. To make sure they're safe, of course. And if he finds a way to secretly confess some feelings to Parker and Hardison along the way? Well, it's just to keep the limbo they've made. And Eliot is very happy to stay in the limbo as long as he needs. based on a Tumblr post by @batserebus over there
After the Job by JMount74 - Rated T
When the job is done there is time to rest, recoup and reflect...before the next one comes along...
won't tell anybody that you turn the world around by crazyness_overpowers - Rated G
Parker asks a question, Breanna reveals an assumption, and Eliot tries not to freak out. Then Parker and Eliot talk about what Breanna's assumption might mean. -- The conversation that happens immediately after "Hey guys? Are we a polycule?", a coda to Redemption 3.09: The Polygiest Job.
#veryace recs#leverage#leverage redemption#parker leverage#eliot spencer#harry wilson#breanna casey#sophie devereaux#leverage redemption s3#leverage redemption fic recs#ao3 fic recs#fanfic recs#ao3
25 notes
·
View notes
Text
The recent installation of Elon Musk ally Thomas Shedd atop the federal IT structure has thrown an agency in charge of servicing much of the US government’s technical infrastructure into disarray.
Over the last few days, workers at the Technology Transformation Services (TTS), which is housed within the General Services Administration (GSA), have been summoned into what one source called “sneak attack” meetings to discuss their code and projects with total strangers—some quite young—who lacked official government email addresses and have been reticent to identify themselves. TTS workers have also received confusing transition guidance and a sudden DC office visit from Musk.
It was announced last week that Shedd, who previously worked as a software engineer for eight years at Tesla, Musk’s electric car company, would be the new TTS director. In emails to TTS staff, Shedd reinforced the Trump administration’s commitment to cutting costs and maximizing efficiency—something Musk’s Department of Government Efficiency, or DOGE, has been charged with carrying out.
“I’ve spent my entire career in Silicon Valley,” Shedd wrote in an introductory email to staff last Thursday and obtained by WIRED. “If we work together and execute well we will be able to navigate the policies, leverage our technical expertise and be a critical part of accelerating technology adoption across agencies to enable great gains in efficiency.”
TTS helps develop the platforms and tools that underpin many government services, including analytics tools and API plugins that agencies can use to deploy tech faster. This means that the group has access to troves of government data and systems across agencies. That access is useful for standardizing the many, not always interoperable, systems that the federal government uses, but could also provide invaluable information to a private company or be weaponized against government employees and citizens.
Early Wednesday morning, rumors began to spread at TTS that employees would be receiving surprise one-on-one meeting notifications from management. During these brief meetings, employees would, according to a staff email that Shedd sent later on Tuesday, be asked to identify their biggest “wins” and the most significant “blockers” preventing them from working as efficiently as possible. The email linked to a Google Form questionnaire for employees to fill out ahead of their scheduled meetings. The invites included people without official GSA email accounts who were using Gmail addresses as well as official government accounts, multiple sources told WIRED.
“These should be items that you completed,” a screenshot of the form obtained by WIRED said. “It is OK to have a mix of big projects and small wins (examples: fixed a critical bug, shipped XYZ feature, saved this amount on a renegotiated contract, ect [sic] … If you are an engineer or designer please include a link to a PR [pull request] or a screenshot of one of your wins from the past 3 months.”
The email is reminiscent of one that Musk sent early in his Twitter days, demanding that employees email a one-page description of what they had accomplished the previous month and how it differed from their goals.
Rather than convening with Shedd in these meetings, TTS employees were instead surprised to be met with people they had never seen or worked with before.
“It was a very confusing call because I expected to be meeting you, and I was instead met by two people reluctant to identify themselves,” one TTS employee told Shedd in an open Slack channel, one of several reviewed by WIRED. “They had not seen the information I submitted in my form, so I was left trying to explain things without the visuals/links I had submitted,” one wrote.
“Also had the same exact experience,” another employee added. “The individual I had met with had no idea about the google form I submitted and when I did reference it, I was met with avoidance.”
In a Slack message to TTS staff on Thursday morning viewed by WIRED, Shedd apologized for the vague and sudden meeting invites, and for including unnamed individuals in the meetings who joined with Gmail addresses.
“They are each in the onboarding process of obtaining a GSA laptop and PIV card. I take full responsibility for the actions of each of them in the calls. I’ve asked them to start the calls with their first name and confirming that they are an advisor to me,” Shedd said in a screenshot of the Slack message viewed by WIRED.
Shedd told employees that the people on the calls were “vetted by me, and invited into the call.” He said they were physically present with him at the GSA headquarters, and that he had “badged them all into the building.” This implies that those joining the calls did not currently have official government IDs issued to agency staff.
At least two of these individuals appeared to be “college students with disturbingly high A-suite clearance,” one TTS source told WIRED. (A-suite clearances tie employees to the GSA administrator’s office.)
One person says they were brought into a review with Edward Coristine, a recent high school graduate who spent several months at Neuralink, Musk’s brain-computer interface company, whom WIRED has previously identified as a person working at the Office of Personnel Management (OPM) and reporting directly to its new chief of staff, the former xAI employee Amanda Scales. He has not responded to requests for comment from WIRED, and OPM has declined to comment.
“We do not have any additional personnel announcements at this time.” a GSA spokesperson told WIRED on Thursday.
It’s typical for TTS workers to work in tandem with other agencies across government, with many of their projects containing data external to GSA and subject to sensitivity agreements. Being required to share specific technical achievements, though, spooked some employees who feared they could breach these agreements.
“The team is correct in feeling nervous sharing details about other agencies in these calls and should continue to follow the normal guidance which is to not share sensitive information,” Shedd wrote in the GSA Slack on Thursday. “The point of these calls is to talk through interesting example problems/wins and dig into how that win was realized. A chance for you to brag about how you solved a problem.”
This week, it appears that TTS has become the primary target of these meetings, but members of the US Digital Services—which a Trump executive order has rebranded as Musk’s DOGE—also met with management to go over their recent work last week. The DOGE meetings were conducted similarly in structure to the TTS ones, according to The Washington Post.
Like many other agencies, GSA has been making changes to DEI initiatives that have put workers on edge. On January 23, TTS deputy director Mukunda Penugonde announced that as part of the GSA’s new initiative to curtail DEIA programs, the agency would be shutting down its “Diversity Guild meeting series” and the “#g-diversity Slack channel effective today,” in an email reviewed by WIRED.
Musk was seen at the GSA office near the White House on Thursday, but it’s unclear what he was doing there. Shedd was scheduled to lead a meeting with around 40 TTS program supervisors Thursday afternoon. On Wednesday, WIRED reported that Musk has been telling his friends that he’s been sleeping at the DOGE office in DC.
Of all parts of the government, TTS, perhaps even more so than DOGE, is well positioned to get inside agencies’ technology and data, including government spending data, explaining why it’s such a focus for the new administration.
“TTS represents the consolidation of 20-plus years of tech and data expertise, brought together by the hard work of hundreds (if not thousands) of civil servants,” Noah Kunin, a cofounder of 18F, a team of designers and engineers within the GSA that help government agencies build and deploy new tech products, and a former infrastructure director at GSA, tells WIRED. “They have the products, platforms, and people to do this work right, within the confines of current law, and fast.”
8 notes
·
View notes
Text
I think some ppl (autistic and not) are confused by why/how not understanding hierarchy and subtle cues impacts workplace performance or makes employment difficult. So going to list some times I got in trouble for those traits at my various positions, from retail to internships to now. I had a contracting position for about a year where I was shielded from this bullshit by a frankly amazing boss, but the reality is work is political and it's difficult for many autistic people.
- in grocery store job, was told to load bags as heavy as my Grandma could carry them. Took this literally and got in trouble for loading my bags too heavy (strong grandma).
- Did not understand store politics and was scheduled fewer hours for not gossiping with and sucking up to management.
- as an intern, was shunned after I explained to a group of devs (who were much more experienced than me but had almost no experience with the software we were working with) that the feature they were talking about building from scratch came out of the box
- same internship, did not understand that they expected *me* to implement a solution we talked in hypothetical terms about in a meeting. Got in trouble the subsequent week when I hadnt done it
- there was an unspoken agreement amongst the interns to not really do any work to keep expectations low. I did not pick up on this and was bullied by the other interns for it.
- first job after college, was bullied by coworker one level above me for doing my job well (she felt threatened)
- first job, was told in annual performance review that I performed too high level for my title and that I should stop. Also got told I ask too many questions. (Questioning any process is seen as hostile, even if it's for the benefit of the company or team)
- first job, found a release stopping bug when asked to test a page, was ignored when I brought it up and brushed off by seniors. Later, the bug did in fact shut down the release.
- current job, recent new manager on another team asked me two questions in about a week. The first I scheduled a call to help him with at his request and looped in another team member that I knew had more subject matter expertise. Second question I didn't know the answer to and didn't know who did so I directed him to our team channel. My thought was this familiarizes him with our team and the different subject matters we are experts in. Next week he makes a "joking" comment in a meeting with a bunch of people and my boss that I must not like him because I keep brushing him off. I realize too late that since he is at the same level as my boss he expected me to hunt down the answers he wanted with no background provided or info about who our team members are and what they do (hierarchy)
- current job, interviewing for a senior and they became upset in interviews when I knew more about something than they did or corrected them about something.
- all jobs, noticing coworkers treat me less warmly because I don't do small talk well.
- all jobs, feeling like it's an injustice and unfair that higher up people are more listened to and sucked up to than anyone else at the company.
- all jobs, not understanding that you are supposed to lie about how busy you are
- all jobs, being told I speak out of turn for responding when asked for an opinion in a group meeting, as only those in the meeting "allowed" to respond to those opinion questions are supposed to.
6 notes
·
View notes
Text
What is the difference between CPQ & RLM?
Revenue Cycle Management Services

In today's fast-moving healthcare and enterprise environments, understanding the difference between CPQ and RLM is essential, especially when these tools impact operations like Revenue Cycle Management. Although both the CPQ and RLM help to optimize processes, they serve very different functions but are aligned toward the business segment.
CPQ – Configure, Price, Quote:
CPQ stands for Configure, Price, Quote. It's a sales tool that helps companies quickly and accurately generate quotes for products or services they are offering. CPQ is a valuable product in industries with complex pricing models or customizable offerings—such as medical equipment, software solutions, or enterprise services.
With CPQ, sales teams can:
Select product features and (configure) as per its requirements
Apply pricing rules and discounts (price) for better product briefing
Generate accurate proposals or quotes (quote) for better outcomes
By automating this process, CPQ reduces errors, speeds up the sales cycle and which eventually boost up the revenue as the ultimate goal, and ensures that pricing is consistent and aligned with company policies and as per its set standards and desired objectives.
RLM – Revenue Lifecycle Management:
On the other hand, revenue Lifecycle Management (RLM) focuses and starves to look at managing and optimizing things at every stage of the revenue process. In healthcare, this is closely tied to Revenue Cycle Management—as a system that oversees the patient billing, insurance claims, payments, and collections.
RLM looks at the broader picture, including:
Contract management
Billing and invoicing
Revenue recognition or recollection
Renewals and upsells of listings
RLM ensures and seeks that the revenue is tracked, reported, and optimized as per the given concern from when a contract begins until the revenue is fully realized or settled out. In healthcare, it's critical for improving financial health, assuring compliance, and reducing revenue leakage as a protective measure.
Key Differences -
CPQ is sales-focused, helping generate quotes and close deals faster as a better option for the users to roll out.
RLM is revenue-focused, ensuring smooth handling and assessment of all financial processes post-sale and after it gets done.
CPQ comes into play at the beginning of the customer journey, while RLM continues throughout the customer lifecycle as they both work as a part of the set system.
Many advanced providers and professionals experts of Revenue Cycle Management, like Suma Soft, IBM, Cyntexa, and Cignex, offer tailored RLM solutions and Revenue Cycle Management services that integrate with CPQ systems. This creates a seamless flow from quoting to revenue realization, making operations more efficient and profitable.
#it services#technology#saas#software#saas technology#saas development company#revenue cycle management#revenuegrowth
2 notes
·
View notes
Text
Freelancer Pro AI Honest Review (with Discount)
If you're looking to streamline your freelancing business, boost productivity, and land more clients, Get Freelancer Pro AI is a game-changer.

This tool is designed to help freelancers automate tasks, create professional proposals, and manage projects efficiently. Here's my honest review after testing it out:
What is GetFreelancerPro AI?
GetFreelancerPro AI is an AI-powered software tailored for freelancers. It helps you:
Automate client communication with AI-generated responses.
Create winning proposals in minutes.
Track projects and deadlines effortlessly.
Generate invoices and contracts with ease.
It’s perfect for freelancers in any niche, whether you're a writer, designer, developer, or consultant.
Key Features
AI Proposal Generator: Craft professional, customized proposals in seconds.
Client Management: Organize client details, project requirements, and deadlines in one place.
Automated Invoicing: Create and send invoices with just a few clicks.
Task Automation: Save time by automating repetitive tasks like follow-ups and reminders.
Templates Library: Access pre-built templates for proposals, contracts, and emails.
Pros
User-Friendly Interface: Even if you're not tech-savvy, the platform is easy to navigate.
Time-Saving: Automating tasks frees up hours to focus on actual work.
Affordable Pricing: With the discount link (GetFreelancerPro AI Discount), it’s a steal for the value it provides.
Versatile: Works for freelancers across various industries.
Cons
Learning Curve: While it’s user-friendly, mastering all features might take a little time.
Internet Dependency: Being a cloud-based tool, you’ll need a stable internet connection.
Who is it For?
GetFreelancerPro AI is ideal for:
New freelancers who want to start strong.
Experienced freelancers looking to scale their business.
Anyone tired of manual, time-consuming tasks.
Final Verdict
GetFreelancerPro AI is a must-have tool for freelancers who want to work smarter, not harder. It simplifies the administrative side of freelancing, allowing you to focus on what you do best—delivering quality work to clients.
Don’t miss out on the discount! Use this link to grab it at a lower price:
👉 GetFreelancerPro AI Discount
If you’re serious about growing your freelancing career, this tool is worth every penny. Highly recommended!
Disclaimer: This is an honest review based on my experience. I may earn a commission if you purchase through the provided link.
#ai generated#freelancer pro ai#content creator#web development#artists on tumblr#app development#website#website development#web developers#web design
2 notes
·
View notes
Text
Binance clone script — Overview by BlockchainX
A Binance Clone Script is a pre-built, customizable software solution that replicates Binance's features, connect with BlockchainX

What is Binance Clone Script
A Binance clone script refers to the ready-made solution of the Binance platform that deals with core functions parallel to the widely acclaimed cryptocurrency exchange platform associated with Binance. It enables companies to establish their own platforms like Binance, perfectly parameterized in terms of functionality and user interface of world-famous exchanges. The clone script provides display flexibility with built-in functionality such as spot trading software, futures trading configurations, and wallet systems that are extremely secure.
Basically, it reduces development costs and latency because things like these are already built. And as this is a startup for many young entrepreneurs, they can have saved on their capital to expand or grow their business.
The script is blessed as its feature set caters to future demands in the field. One can enjoy a safe trading experience to customers while ensuring that every peculiarity of Binance’s success opens up to investors of the script.
How does the Binance clone script work?
The Binance clone script works to provide a ready-made platform that replicates Binance’s core features, such as user registration, wallet management, trade and enables users to create accounts, deposit or withdraw cryptocurrency, and trade digital assets through an interface easily and safely. The platform supports various trading methods such as market orders, limit orders and forward trading. It has built-in security features like two-factor authentication (2FA) to save the user money. Admin dashboards allow platform owners to manage users, manage tasks, and set up billing. The script can be tailored to your brand, connecting liquidity sources to make trading more efficient. In short, the Binance clone script provides everything needed to create a fully functional crypto exchange.
key features of a Binance Clone Script
The key features of a Binance Clone Script are designed to make your cryptocurrency exchange platform secure, user-friendly, and fully functional. Here’s a simple overview of these features:
User-Friendly Interface
Multi-Currency Support
Advanced Trading Engine
Secure Wallet System
KYC/AML Integration
Admin Dashboard
Security Features
Trading Options
These features help ensure that your Binance-like exchange is efficient, secure, and ready for the growing crypto market.
Technology Stack Used by BlockchainX
Technology stack used for developing the Binance clone script involves the most advanced technology combination that ensures that the platform must have so much security, scalability, and performance to make it a platform that is secure, scalable, and high-performance as well. Here are a few key technologies and their brief descriptions:
Blockchain Technology:
The underlying part of the cryptocurrency exchange is Blockchain because it ensures the safe and decentralized processing of transactions.
Normally executed on either Ethereum or BSC (Binance Smart Chain) to carry out smart contracts and token transfers.
Programming Languages:
Frontend: For frontend, React or Angular could be engaged in actualization of the user interface leading to a responsive and interactive experience on the various devices.
Backend: In backend, languages like Node.js, Python, or Ruby on Rails can be applied on how internal logic is being run by server and arbitration of user interaction with the module is foremost.
Databases:
These two databases, MySQL or Postgresql, are typically used in user information storage, transaction records, and other exchange information.
NoSQL such as MongoDB or other databases might be used for horizontal scalability and high-volume transaction storage.
Smart Contracts:
It is used to generate and send out smart contracts for auto-trading, token generation, and other decentralized functionalities.
Blockchain Wallets:
Fundamentally, this automatically links famous wallet systems such as MetaMask, Trust Wallet, or Ledger for the secure storage and transactions of cryptocurrency.
Advantages of using a Binance Clone Script
Here are the advantages of using a Binance Clone Script:
Faster Time-to-Market
Cost-Effective
Customizable Features
Liquidity Integration
Multiple Trading Options
So, when entering the marketplace of the cryptocurrencies it would be the most possible work of something to pay off at a rapid pace: the Binance Clone Script proves so.
How to Get Started with BlockchainX’s Binance Clone Script
It is quite a straightforward process to begin working with a BlockchainX Binance Clone Script-this involves the first step of getting in touch with the company for an initial consulting period to understand more about what you require, need, or customize for the site, and what your goals are. When BlockchainX has an understanding of your needs, they offer a detailed list of what a proposal would entail before they can start the work; afterward, they will estimate the costs needed to do the project. Once both sides accept both the presentations and all features and timelines are agreed with, BlockchainX starts working on the development process of building a Binance Clone Script tailored to the brand, user interface, and other features.
After the entire platform is created, it passes through severe testing to ensure that everything functions excellently. Deployment follows the thorough test. BlockchainX customizes your user interface and more extensions, after deployment. BlockchainX also commits to supporting and sustaining your exchange so that it runs successfully and securely.
Conclusion:
At the end, your confusion may as well be cut short. Yes, the Binance Clone Script will be a resilient solution to spark up the exchange platforms synthesizing user-generated cryptocurrency dreams in the blockchain, even without bankroll when it comes to developing the app. Turning with BlockchainX expertise, you can make an adjustment and scale a powerful platform stocked with the likes of Binance that produced Blockchains, while still containing some specific set-ups for your masterpiece. More amazing features are exclusive to the clone script, moreover, such as support for multiple currencies, high-end security, real-time data, and a smooth user interface that completes the trading process for your users without any glitch.
This solution gives easy access to ready-made solutions. It could have quality Depending on the time you conveniently let BlockchainX’s be and use both exchanges or any variation of the two permutations. After all, who decides to couple up with a one-experienced Crypto Exchange developer who is struggling to offer anything new.
#binance clone script#binance clone script development#binance clone script development service#blockchain technology#blockchain#cryptocurrency#cryptocurrencies
2 notes
·
View notes
Text
Top Trends in Software Development for 2025
The software development industry is evolving at an unprecedented pace, driven by advancements in technology and the increasing demands of businesses and consumers alike. As we step into 2025, staying ahead of the curve is essential for businesses aiming to remain competitive. Here, we explore the top trends shaping the software development landscape and how they impact businesses. For organizations seeking cutting-edge solutions, partnering with the Best Software Development Company in Vadodara, Gujarat, or India can make all the difference.

1. Artificial Intelligence and Machine Learning Integration:
Artificial Intelligence (AI) and Machine Learning (ML) are no longer optional but integral to modern software development. From predictive analytics to personalized user experiences, AI and ML are driving innovation across industries. In 2025, expect AI-powered tools to streamline development processes, improve testing, and enhance decision-making.
Businesses in Gujarat and beyond are leveraging AI to gain a competitive edge. Collaborating with the Best Software Development Company in Gujarat ensures access to AI-driven solutions tailored to specific industry needs.
2. Low-Code and No-Code Development Platforms:
The demand for faster development cycles has led to the rise of low-code and no-code platforms. These platforms empower non-technical users to create applications through intuitive drag-and-drop interfaces, significantly reducing development time and cost.
For startups and SMEs in Vadodara, partnering with the Best Software Development Company in Vadodara ensures access to these platforms, enabling rapid deployment of business applications without compromising quality.
3. Cloud-Native Development:
Cloud-native technologies, including Kubernetes and microservices, are becoming the backbone of modern applications. By 2025, cloud-native development will dominate, offering scalability, resilience, and faster time-to-market.
The Best Software Development Company in India can help businesses transition to cloud-native architectures, ensuring their applications are future-ready and capable of handling evolving market demands.
4. Edge Computing:
As IoT devices proliferate, edge computing is emerging as a critical trend. Processing data closer to its source reduces latency and enhances real-time decision-making. This trend is particularly significant for industries like healthcare, manufacturing, and retail.
Organizations seeking to leverage edge computing can benefit from the expertise of the Best Software Development Company in Gujarat, which specializes in creating applications optimized for edge environments.
5. Cybersecurity by Design:
With the increasing sophistication of cyber threats, integrating security into the development process has become non-negotiable. Cybersecurity by design ensures that applications are secure from the ground up, reducing vulnerabilities and protecting sensitive data.
The Best Software Development Company in Vadodara prioritizes cybersecurity, providing businesses with robust, secure software solutions that inspire trust among users.
6. Blockchain Beyond Cryptocurrencies:
Blockchain technology is expanding beyond cryptocurrencies into areas like supply chain management, identity verification, and smart contracts. In 2025, blockchain will play a pivotal role in creating transparent, tamper-proof systems.
Partnering with the Best Software Development Company in India enables businesses to harness blockchain technology for innovative applications that drive efficiency and trust.
7. Progressive Web Apps (PWAs):
Progressive Web Apps (PWAs) combine the best features of web and mobile applications, offering seamless experiences across devices. PWAs are cost-effective and provide offline capabilities, making them ideal for businesses targeting diverse audiences.
The Best Software Development Company in Gujarat can develop PWAs tailored to your business needs, ensuring enhanced user engagement and accessibility.
8. Internet of Things (IoT) Expansion:
IoT continues to transform industries by connecting devices and enabling smarter decision-making. From smart homes to industrial IoT, the possibilities are endless. In 2025, IoT solutions will become more sophisticated, integrating AI and edge computing for enhanced functionality.
For businesses in Vadodara and beyond, collaborating with the Best Software Development Company in Vadodara ensures access to innovative IoT solutions that drive growth and efficiency.
9. DevSecOps:
DevSecOps integrates security into the DevOps pipeline, ensuring that security is a shared responsibility throughout the development lifecycle. This approach reduces vulnerabilities and ensures compliance with industry standards.
The Best Software Development Company in India can help implement DevSecOps practices, ensuring that your applications are secure, scalable, and compliant.
10. Sustainability in Software Development:
Sustainability is becoming a priority in software development. Green coding practices, energy-efficient algorithms, and sustainable cloud solutions are gaining traction. By adopting these practices, businesses can reduce their carbon footprint and appeal to environmentally conscious consumers.
Working with the Best Software Development Company in Gujarat ensures access to sustainable software solutions that align with global trends.
11. 5G-Driven Applications:
The rollout of 5G networks is unlocking new possibilities for software development. Ultra-fast connectivity and low latency are enabling applications like augmented reality (AR), virtual reality (VR), and autonomous vehicles.
The Best Software Development Company in Vadodara is at the forefront of leveraging 5G technology to create innovative applications that redefine user experiences.
12. Hyperautomation:
Hyperautomation combines AI, ML, and robotic process automation (RPA) to automate complex business processes. By 2025, hyperautomation will become a key driver of efficiency and cost savings across industries.
Partnering with the Best Software Development Company in India ensures access to hyperautomation solutions that streamline operations and boost productivity.
13. Augmented Reality (AR) and Virtual Reality (VR):
AR and VR technologies are transforming industries like gaming, education, and healthcare. In 2025, these technologies will become more accessible, offering immersive experiences that enhance learning, entertainment, and training.
The Best Software Development Company in Gujarat can help businesses integrate AR and VR into their applications, creating unique and engaging user experiences.
Conclusion:
The software development industry is poised for significant transformation in 2025, driven by trends like AI, cloud-native development, edge computing, and hyperautomation. Staying ahead of these trends requires expertise, innovation, and a commitment to excellence.
For businesses in Vadodara, Gujarat, or anywhere in India, partnering with the Best Software Development Company in Vadodara, Gujarat, or India ensures access to cutting-edge solutions that drive growth and success. By embracing these trends, businesses can unlock new opportunities and remain competitive in an ever-evolving digital landscape.
#Best Software Development Company in Vadodara#Best Software Development Company in Gujarat#Best Software Development Company in India#nividasoftware
5 notes
·
View notes
Text
Launch Your Crypto MLM Business in Just 5 Days!

In today’s fast-evolving digital world, cryptocurrency-based multi-level marketing (MLM) models are gaining immense popularity. Entrepreneurs are increasingly embracing these models to create sustainable revenue streams. However, the key to staying ahead in this competitive space lies in executing a well-structured, technology-driven plan. With Crypto MLM Software, business owners can set up their MLM operations smoothly and efficiently within a few days. In fact, Plurance, a top-rated cryptocurrency MLM software development company, offers tailored solutions to launch your business in just five days.
The Advantage of Crypto MLM Platforms
Crypto MLM platforms combine the power of network marketing with blockchain technology, offering transparency, security, and quick transactions. Entrepreneurs leveraging ready-made cryptocurrency MLM software avoid the risks and complications associated with building platforms from scratch. Instead, they can focus on market penetration and team-building strategies, ensuring rapid scaling.
In a fast-paced sector like cryptocurrency, time is money. The ability to deploy a robust MLM platform in a matter of days gives businesses a significant edge, especially as early market entry can attract users looking for trustworthy opportunities.
Why Choose Plurance for Cryptocurrency MLM Software Development?
Building a sustainable MLM business requires more than just an idea—it demands a technology partner capable of understanding the intricacies of the crypto world. This is where Plurance excels. As an industry-leading cryptocurrency MLM software development company, Plurance combines expertise with cutting-edge technology to deliver feature-rich, scalable, and customizable solutions.
Here’s why Plurance stands out:
Customizable Plans and Smart Contracts
Plurance integrates flexible compensation structures such as binary, matrix, or unilevel plans with blockchain-based smart contracts. This ensures automated payouts and reduces human intervention, increasing trust and efficiency within the MLM ecosystem.
Quick Deployment with Ready-Made Cryptocurrency MLM Software
For entrepreneurs on a tight timeline, Plurance offers ready-made cryptocurrency MLM software. These plug-and-play solutions are pre-tested, secure, and come with all essential features, enabling you to launch your platform within five days.
User-Friendly Dashboards
A smooth user experience is crucial to retaining members in MLM businesses. Plurance provides interactive dashboards for both administrators and users, simplifying everything from membership tracking to commission distribution.
Advanced Security Features
Plurance places a premium on security. Its MLM software includes multi-factor authentication (MFA), anti-fraud mechanisms, and encrypted wallets, ensuring your business and users are protected from malicious activities.
Scalability and Future-Readiness
Plurance’s development approach ensures that your MLM platform can grow along with your business. Whether you need to add new features or integrate additional cryptocurrencies, the software is built to handle future upgrades seamlessly.
The 5-Day Launch Blueprint
Day 1: Initial Consultation and Requirement Gathering
Day 2: Platform Customization and Integration of Smart Contracts
Day 3: Quality Testing and Security Assessment
Day 4: User Onboarding and Training
Day 5: Final Launch and Go-Live Support
By the fifth day, you are ready to manage and grow your network with a platform that offers unparalleled reliability and performance.
Conclusion
The world of MLM is transforming with the rise of cryptocurrencies, and fast execution is the key to staying competitive. With Plurance’s cryptocurrency MLM software development solutions, businesses can achieve a hassle-free launch within five days. The combination of blockchain technology, customizable plans, and ready-made cryptocurrency MLM software ensures your platform is ready to attract, engage, and reward users from day one.
#Cryptocurrency MLM Software#Crypto MLM Software#White Label Crypto MLM Software#Cryptocurrency MLM Software Development#Cryptocurrency MLM Software Development Company#blockchain#cryptocurrency#crypto
2 notes
·
View notes
Text
What is Freight Brokerage & Freight Forwarding Software
What is Freight brokerage and freight forwarding software?
Freight brokerage software allows a shipper to find carriers, manage the rates or tariffs as well as the contracts, and even track shipments. This eliminates the difficulties involved in the procedure and helps in making the admittance of new companies efficient as well as easy by automating these tasks. Freight forwarding software on another hand covers everything to do with shipping, from documents to storage and most importantly legal compliance with trade laws. Therefore, while brokerage software is primarily into matching shippers with carriers, forwarding is a software that handles the entire shipping process. Considering these disparities makes the functioning of transport brokers more effective and has a strong effect on the outcomes of their cooperation with clients.

Differences between Freight Forwarding & Freight Brokerage
Aspect
Freight Forwarding
Freight Brokerage
Primary Role
Manages the whole shipping process
Connects shippers with carriers
Physical Possession
Takes physical possession of the cargo
Does not take possession of the cargo
Services Provided
Handles documentation, storage, and transportation
Arranges transport contracts between shippers and carriers
Scope of Operations
Provides end-to-end logistics solutions
Focuses on negotiating and arranging transport
Customer Interaction
Simplifies trade regulations and logistics for businesses
Primarily negotiates and arranges transportation
Benefits of Using Freight Forwarding and Brokerage Software
Operational Efficiency
Freight forwarding and brokerage software significantly streamline operations, automating tasks such as load board management and carrier selection, which reduces manual efforts and enhances efficiency. Real-time tracking and automated notifications ensure smooth operational flow, minimising delays and errors.
Cost Savings
Implementing this software leads to direct cost savings by optimising route selection and reducing idle times, thereby cutting down on fuel and maintenance expenses. Automated invoice management and accurate rate calculations prevent financial discrepancies and reduce administrative costs.
Scalability
The software adapts to business growth, allowing easy integration of additional modules as needed. This flexibility supports expanding operational demands without the need for significant system overhauls, making it a future-proof investment.
Improved Tracking and Visibility
Advanced tracking features provide real-time data on shipments, enhancing visibility across the supply chain. This transparency helps in better managing expectations and reduces the risk of shipment delays.
Better Customer Service
Freight software enhances customer service by providing detailed tracking information and efficient issue resolution processes. This increases customer satisfaction and fosters loyalty.
Data Insights and Reporting
Comprehensive analytics tools offered by these software systems enable detailed performance monitoring and decision-making support. Insights gained from real-time data help in identifying inefficiencies and improving overall business strategies.
Conclusion
All these digital solutions are not only expected to improve flexibility in the operational processes but also to maximise cost efficiency and customer experience. To them they hold the potential of offering even more optimization, helping logistics specialists fine-tune solution provision. It’s important for organisations to adopt these technologies as they provide a competitive advantage through optimisation and valuable business intelligence. In this case, the integration of such systems is a business strategy well embraced by companies in the transport commission agent business due to ever changing market opportunities in the expanding global economy. Overall, the use of advanced freight software is not a trend but a revolution for FDI that opens the future of global logistics facilitating transnational business.
2 notes
·
View notes
Text
Ideal Customer Persona: Marketing Director Mark
About Them
Name: Mark Thompson
Role: Marketing Director
Industry: SaaS (Software as a Service)
Company Size: Mid-sized (100-500 employees)
Demographics:
Age: 35-45 years old
Education: Bachelor's in Marketing or Business, often with an MBA
Location: Urban areas with a tech industry presence (e.g., San Francisco, New York, Austin)
Experience: 10+ years in marketing, 3-5 years in a leadership role
Professional Background:
Strong understanding of digital marketing, analytics, and customer acquisition strategies
Experienced in leading cross-functional teams and managing marketing budgets.
Use Case
How they use our product:
To manage and optimize digital marketing campaigns across multiple channels (e.g., social media, email, SEO)
To gain insights into customer behavior and campaign performance through advanced analytics and reporting tools
To streamline and automate repetitive marketing tasks
What they’re trying to achieve:
Increase lead generation and conversion rates
Enhance brand visibility and engagement
Improve ROI on marketing spend
Gain a competitive edge through data-driven decision-making
Previous Solution & Pain Points
Previous Solution:
A combination of multiple marketing tools (e.g., email marketing platforms, social media schedulers, web analytics tools)
Manual processes for campaign management and performance tracking
Pain Points:
Fragmented data across different tools leading to inefficiencies and inaccuracies
Time-consuming manual processes
Difficulty in measuring the true impact of marketing efforts on revenue
Challenges in personalizing marketing campaigns at scale
Benefits
Main Benefits from Using Our Product:
Integrated Platform: Unified solution that brings all marketing tools and data into one platform
Automation: Streamlined workflows for campaign management, reducing manual effort
Advanced Analytics: Comprehensive reporting and analytics that provide actionable insights
Scalability: Ability to personalize campaigns at scale, driving better engagement
Improved ROI: More efficient use of marketing budgets through data-driven optimization
Buying Trigger
What Causes Them to Seek Out Our Product:
Need to consolidate marketing tools for better efficiency
Growth in company size leading to more complex marketing needs
Desire to improve marketing performance and accountability
Feedback from the executive team demanding better metrics and ROI
Frustration with current tools' limitations and lack of integration
Buying Process
Typical Process People Go Through to Buy Our Product:
Research: Initial online research to identify potential solutions, reading reviews and case studies
Evaluation: Shortlisting a few platforms, attending demos, and comparing features and pricing
Consultation: Internal discussions with the marketing team and other stakeholders (e.g., IT, finance)
Trial: Requesting a free trial or pilot program to test the product
Decision: Final decision made by the Marketing Director, often in consultation with the executive team
Approval: Securing budget approval and negotiating contracts
Choice Factors
Things They’re Looking for in a Product Like Ours:
Ease of Use: Intuitive interface and easy onboarding process
Integration: Seamless integration with existing tools and systems
Scalability: Ability to grow with the company and handle increasing volumes of data and users
Support: Reliable customer support and resources for troubleshooting and optimization
Value: Competitive pricing and clear ROI
Innovation: Regular updates and new features that keep the platform ahead of industry trends
5 notes
·
View notes
Text
How to Improve Supplier Management using ERP software in India
Introduction:
In today's highly competitive business landscape, effective supplier management plays a crucial role in the success of manufacturing companies in India. Managing suppliers efficiently can significantly impact the overall productivity, cost-effectiveness, and customer satisfaction of a business. Thankfully, advancements in technology have introduced powerful solutions like Enterprise Resource Planning (ERP) software, which can revolutionize supplier management. In this blog, we will explore the benefits of utilizing ERP software and how it can enhance supplier management for manufacturing companies in India.

Understanding ERP Software:
ERP software integrates various business processes, including finance, inventory management, production planning, and supplier management, into a centralized system. This integration eliminates silos and provides real-time visibility into every aspect of the supply chain, enabling companies to make informed decisions quickly. ERP software acts as a comprehensive tool to streamline operations, enhance efficiency, and improve collaboration with suppliers.
Benefits of ERP Software for Supplier Management:
Streamlined Procurement Process:
ERP software simplifies the procurement process by automating tasks such as supplier selection, purchase order generation, and tracking. It centralizes supplier information, including contact details, performance metrics, and transaction history, making it easier to manage supplier relationships. This streamlining of procurement activities leads to better communication, reduced errors, and faster response times.
Improved Supplier Performance Monitoring:
By utilizing ERP software, manufacturing companies in India can monitor supplier performance more effectively. Key performance indicators (KPIs) such as delivery time, quality, and compliance can be tracked in real-time. This allows businesses to identify underperforming suppliers and take necessary actions, such as renegotiating contracts or seeking alternative options. Timely identification of issues ensures smoother operations and enhances customer satisfaction.
Enhanced Inventory Management:
ERP software provides accurate inventory tracking and forecasting capabilities, enabling companies to maintain optimal inventory levels. By integrating supplier data, businesses can automate replenishment processes, reducing stock-outs and excess inventory. Additionally, ERP software helps in analyzing supplier lead times and identifying potential delays, minimizing production disruptions and ensuring timely deliveries.
Efficient Communication and Collaboration:
Successful supplier management relies on seamless communication and collaboration between manufacturers and suppliers. ERP software facilitates efficient communication channels, enabling secure and real-time information exchange. It offers features like automated notifications, instant messaging, and document sharing, fostering transparency and improving collaboration with suppliers. This streamlined communication ensures that all parties are aligned, reducing misunderstandings and delays.
Choosing the Right ERP Software Provider in India:
When considering ERP software for supplier management, it is essential to select a reliable and experienced provider. Several ERP software providers in India cater specifically to the needs of manufacturing companies. Some popular options include SAP, Oracle, Microsoft Dynamics, and Tally ERP. Before finalizing a provider, businesses should evaluate their requirements, budget, scalability, and support services to ensure a seamless implementation and ongoing assistance.

Conclusion:
In the fast-paced manufacturing industry of India, effective supplier management is a key differentiator for success. Leveraging ERP software can significantly enhance supplier management processes, optimizing procurement, improving supplier performance monitoring, and fostering collaboration. By implementing an appropriate ERP solution from reliable providers in India, manufacturing companies can streamline operations, reduce costs, and gain a competitive edge in the market.
Remember, ERP software is not a one-size-fits-all solution. It is crucial to conduct a thorough evaluation of your company's requirements and choose the ERP system that best aligns with your specific business needs. With the right ERP software in place, manufacturing companies in India can unlock new levels of efficiency, profitability, and growth in their supplier management processes.
#ERP software providers in India#ERP for manufacturing company in India#ERP software Companies in Ahmedabad#ERP solution providers in Ahmedabad#ERP software in Ahmedabad#ERP software providers in Surat#ERP software in Surat#ERP solution providers in Surat#ERP software company in Surat#ERP software Companies in Gujarat#ERP solution providers in Gujarat#ERP for manufacturing company in Gujarat#manufacturer#business process#STERP#shantitechnology
8 notes
·
View notes
Text

Anduril Is Helping The Air Force To Develop Its Loyal Wingman Drone
Anduril is one of five companies now working on the Collaborative Combat Aircraft program, which is a top priority for the Air Force.
Joseph TrevithickPUBLISHED Jan 25, 2024 12:33 PM EST
Defense contractor Anduril has formally announced that it is one of five companies working on the US Air Force's Collaborative Combat Aircraft (CCA) advanced drone program.
Anduril
Anduril has become the first contractor to formally announce that it supporting the U.S. Air Force's Collaborative Combat Aircraft advanced uncrewed aircraft program. This comes as the service says this program is progressing slower than it would like due to budgetary issues and amid emerging concerns about the cost and capabilities of the future drones.
A brief press release Anduril put out today says it is one five vendors the Air Force has chosen to help develop its future Collaborative Combat Aircraft (CCA). The service said last year that a number of companies were under contract to conduct CCA-related work, but declined to name any of them. Last month, Breaking Defense reported that Boeing, General Atomics, Lockheed Martin, and Northrop Grumman were the other four contractors working on the CCA program, citing anonymous sources. That story added that some of these companies could be eliminated in a down-select later this year.

A rendering of Anduril's stealthy Fury drone. The company has not yet disclosed how exactly it is contributing to the CCA program. Anduril
When contacted for more information about exactly how it is now contributing to the CCA development effort, Anduril told The War Zone that it could not currently provide any more details "given sensitivities," which it did not elaborate on. We have also reached out to the Air Force for additional information.
Last year, Anduril did notably acquire small aviation firm Blue Force Technologies, which had been developing an advanced drone called Fury that has long seemed very much in line with the Air Force's CCA requirements. You can read more about the Fury, its expected capabilities, its origins, and Anduril's plans for the design in great detail in this feature The War Zone published last September.
youtube
Anduril also produces Lattice, which it describes as an "artificial intelligence-enabled software platform that enables teams of autonomous systems to dynamically collaborate to achieve complex missions, under human supervision." This could also be very relevant to the CCA program.
youtube
The CCA program is presently focused on the development and acquisition of at least one type of advanced "loyal wingman"-esque drone with a high degree of autonomy. These uncrewed aircraft are expected initially to operate closely together with stealthy Air Force F-35A Joint Strike Fighters and the future crewed sixth-generation Next Generation Air Dominance (NGAD) combat jet. The drones could potentially operate together with other types of aircraft, including non-stealthy fourth-generation fighters and the B-21 Raider stealth bomber, or independently, in the future. CCA is another element of the larger NGAD family of programs, which also includes new weapons, sensors, networking and battle management suites, advanced jet engines, and more.
"We commend Secretary Kendall and the U.S. Air Force for their leadership and commitment to integrating new technologies into the force," Anduril said in its release today. "We are honored to be the only non-traditional defense company selected to be a part of the CCA program."
The specific mention of being a "non-traditional defense company" here is noteworthy. Large established defense contractors like Lockheed Martin, Northrop Grumman, Boeing, General Atomics, and Raytheon have largely dominated the discussion about CCA-relevant developments in recent years.
youtube
Anduril regularly highlights its position as a 'disruptor' in the U.S. defense industrial space and its novel developmental, production, and general business practices, as you can read more about here. The company has steadily expanded its portfolio, with focuses on artificial intelligence software and smaller drones, since its founding in 2017.
The Air Force has also been touting its efforts to make use of novel contracting and other processes to help accelerate the CCA program. Air Force Lt. Gen. Richard Moore, Jr, the Deputy Chief of Staff for Plans and Programs, spoke about this just yesterday at a public event hosted by the Center for Strategic & International Studies (CSIS) think tank in Washington, D.C.
"The thing about this that's innovative with CCAs, in particular, is the Secretary [of the Air Force Frank Kendall] asked us: 'Please don't go to industry and give them a requirement. The last thing in the world we want to do is tell them what to build. We want to go to them with questions and we want to find out what they can do. What is the art of the possible and what is it that they could provide? And let's allow the envelope to expand by not constraining it with a requirement," Moore said.
"I think what we're starting to see now is that there are a lot of thoughts out there, some of them ... not necessarily from the large defense primes [traditional prime contractors], that really will will be beyond what we would have conceived had we decided to write a requirement," Moore added. "So it is exciting to see what's coming. And I think the the way that this is innovative is something that will transition to other programs. I don't think that this is one and done, because I think that we're going to find it to be wildly successful."
Moore also specifically mentioned "non-traditional sources" supporting the CCA program that had emerged through the Small Business Innovation Research (SBIR) program. SBIR is a U.S. government contracting mechanism that focuses on smaller deals with smaller companies to help foster technical innovation. The initial work on the Fury drone was through SBIR contracts.
All of this being said, the Air Force has made clear that it is not moving ahead with CCA as fast as it wants. The service has blamed this primarily on broader budgetary disputes between President Joe Biden's administration and Congress that are currently impacting the U.S. government as a whole. Secretary of the Air Force Frank Kendall has been particularly outspoken over the years about the problems that short-term spending packages, commonly called continuing resolutions (CR), rather than full annual budgets, impose on the U.S. military broadly.
"We're going to be limited in terms of forward progress based on the CR," Kristyn E. Jones, the senior official currently performing the duties of the Under Secretary of the Air Force, also said at yesterday's CSIS event, speaking alongside Lt. Gen. Moore. "CCA, as I mentioned – you know, we've made some progress being able to award contracts to some of the initial designers, but we can't ramp that."
The Air Force has said in the past that it wants to acquire at least 1,000 CCAs, and likely many more, and that it wants to begin major production of the drones within the next five years. At present, the expected cost of a single CCA is estimated to be around one quarter to one third of the unit price of an F-35 stealth fighter. This would put the price point for one of these future drones at between roughly $20.5 million and $27.5 million, based on public data about current F-35 unit prices.

An F-35A, at center, flies together with a Kratos XQ-58 Valkyrie drone, at left, and an F-22 Raptor stealth fighter, at right, during a test. USAF
The 1,000 CCA figured is based around a notional concept of operations involving a pair of the drones operating together with each of 200 NGAD combat jets and 300 F-35As. The Air Force has also previously said that a single crewed aircraft could oversee more CCAs in the future.
In addition, despite Moore's comments about the Air Force trying not to set firm requirements for the future CCAs, the service is clearly working to define several key parameters. From what has been disclosed so far, the CCA effort looks to be leaning toward designs with less range and higher performance than had previously been envisioned, and that will be at the high end of the expected unit cost range as a result. This, in turn, has already prompted Congress to voice concerns about the direction of the program.
The Air Force has made clear that the CCA program, however it might continue to evolve, is central to its future operational vision. The service sees the drones as especially critical for providing advanced capabilities in high volumes at a relatively low cost, a concept it currently refers to as "affordable mass." This kind of capacity is seen as particularly essential for success in any future high-end conflict, such as one against China in the Pacific.
In the meantime, much about the overall CCA program still seems to be in flux. The Air Force does now seem be working to coalesce the effort around a core group of contractors, including Anduril.
Contact the author: [email protected]
5 notes
·
View notes
Text
Key Software Systems LLC
In 1999 Key Resource Solutions was contracted by a courier company to write a dispatch software solution. At the time Key Resource Solutions was servicing Fortune 500 companies like: Waterford Crystal, CNA Insurance, All State, and the U.S. DOD. Key Software Systems, LLC was born out of that contract in 2000, along with its fledgling product, Xcelerator. From there, controlled steady growth enabled Xcelerator to become a recognized leader in logistics software due to the advanced technology, easy to use features, and strong business model. Once Xcelerator took hold in the market; mobile workforce communication began to expand and grow into new areas driven by shippers requiring Signature Capture, Barcode Scanning and GPS. At this time Key Software Systems spun off MobileTek, LLC as a sister company which is owned and operated by the same Key Software Systems team. MobileTek specializes in developing Mobile Software Solutions deployed on handheld devices, smart phones, and tablets. MobileTek is positioned to be one point of contact for customers needing hardware, software, and support of their mobile technology. Now introducing Nexus. Nexus provides Shippers and 3PLs a connectivity-based solution designed to consolidate integrations, increase visibility to key metrics, optimize efficiency throughout the delivery process and maximize brand management across their nationwide deliveries being performed by Final Mile Carriers. The customizable nature of Nexus ensures that business rules and requirements are aligned with the needs of each Shipper and 3PL and the expectations of the customers they serve. We are proud members of the following associations: ECA, CLDA, CDA, TCLA, FMA, NYSMCA, OSTA, XLA, and AEMCA. AS a member of these associations, we support, sponsor, and attend all major events to gain industry knowledge, expand on existing relationships with customers, and establish new relationships and partnerships with shippers and carriers. Key Software’s Principals, combined, have over 45 years of software development and IT experience with a mission to continuously provide the strongest and newest technologies coupled with old fashioned “the client first” service.
https://twitter.com/KeySoftwareSys
https://www.linkedin.com/company/key-software-systems/
2 notes
·
View notes
Text
SAP SD Training in Hyderabad
How are the processes for order management, pricing, and invoicing handled by SAP SD?
Businesses across various industries face numerous challenges when it comes to managing their order processes effectively. The complexity of pricing and billing, coupled with the need for streamlined order management, can often result in errors, delays, and increased costs. Recognizing this, Version IT has developed a cutting-edge solution with SAP SD that promises to simplify and optimize these critical business operations.
The SAP SD software, integrated with industry best practices, offers businesses a comprehensive suite of tools and functionalities to manage the entire order lifecycle efficiently. With real-time tracking and management capabilities, the solution empowers businesses to handle complex pricing structures, promotions, and discounts seamlessly. It also transforms the billing process, ensuring accurate and timely invoices, and providing customers with transparent and detailed billing information. SAP SD Training in Hyderabad best location for you.
Key features of SAP SD software include:
1. Order Management: Seamlessly manage sales orders, contract renewals, and returns, while ensuring accurate pricing, inventory availability, and delivery schedules.
2. Pricing Optimization: Utilize advanced pricing algorithms to create and manage complex pricing structures, promotions, and discounts, ensuring competitiveness and profitability.
3. Efficient Billing: Automate the billing process, generating accurate and detailed invoices, while providing customers with real-time access to billing information.
4. Analytics and Reporting: Utilize comprehensive analytics and reporting functionalities to gain valuable insights into sales performance, customer behavior, and revenue trends.
Version IT aims to empower businesses of all sizes to strengthen customer relationships, optimize revenue streams, and improve operational efficiency through the implementation of its SAP SD software.
We believe that effective order management, pricing, and billing are not just essential business operations, but also crucial touchpoints for customer satisfaction. "With our innovative SAP SD software, we aim to revolutionize these processes, enabling businesses to achieve seamless operations, streamlined pricing strategies, and enhanced customer service."
About Version IT:
Version IT is a leading provider of advanced technology solutions, dedicated to helping businesses achieve their operational goals. With a team of highly skilled professionals and a commitment to innovation

2 notes
·
View notes