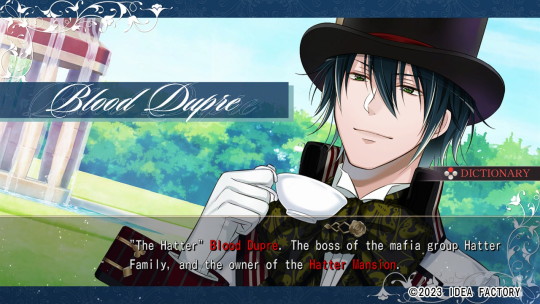
#reverse engineering
Text

Have you heard about the Polish Train company, Newag, and the bullshit it turns out they got up to?
So, the regional rail operator Koleje Dolnośląskie bought some Newag Impuls back in 2016 . In late 2021, some of them need to have major maintenance done, as they've been in service a while. So the company SPS (Serwis Pojazdów Szynowych) gets the contract to fix them. They basically take the train apart, replace a bunch of it, following all the rules in the documentation Newag gave them, and... it won't move. The train says everything is fine, the brakes are off, there's plenty of power, but you push the throttle up and it won't move.
SPS spends a while trying to figure out what the fuck is wrong, with no luck. So they hire some hackers from the Polish security group Dragon Sector. Dragon Sector figures out how to get into the code of the computer system that runs the train, and OH MY GOD.
So it turns out there's a secret train-lock system. If it's on, the train won't move. This will be triggered in some situations you might think are normal: the clocks are wrong, the serial numbers of the various parts have changed, and a firmware mismatch between the main computer and the power system. Now, the fact that it makes sense to not run the train in these situations until someone can check it? that doesn't extend to the fact the train uses a SECRET lock system, rather than just popping up an error message telling you what's wrong. There's also the problem that while these are all potential error problems, they can't be cleared by anyone with the technical manuals, which are supposed to cover everything about how to run these trains. Only Newag themselves can reset this system.
Which, you know, keeps SPS from properly fixing them. Only Newag can fix them now, but not because SPS lacks any technical ability, but because Newag sabotaged their own trains. But don't worry: it gets worse.
So now that Dragon Sector knows what's happening, they get to look at other trains. It turns out the trains aren't all running the same software, and there are other tricks in there.
One of them is a "how long has the train been stopped?" check. If the train hasn't hit 60 km/h in 10 days, the train locks itself and won't move until Newag can clear it. So, like, if a train is ever out of service, like it's going to a repair place... it'll break itself. Unless the repair place is owned by Newag.
But two of the trains go further: See, these trains have GPS built in, right? You may be able to guess where this is going...
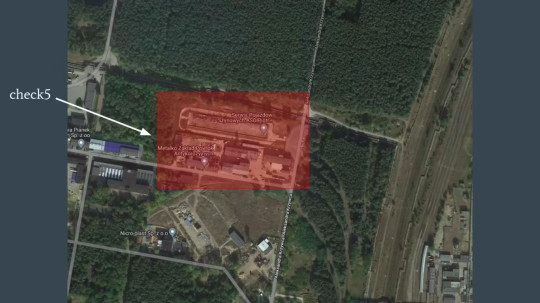
THEY JUST MAKE THE TRAIN CHECK IF IT IS PARKED AT THEIR COMPETITORS' REPAIR YARD AND BREAK ITSELF IF IT WAS.
The sheer audacity of this move. This is frighteningly bullshit anti-competition self-sabotage.
This has, obviously, made some parts of the Polish government to start investigating this. Newag may be (and hopefully will be) in a lot of trouble.
For more info, there's a great video of a presentation by the three people from Dragon Sector who did the hacking, which was presented at the 37th Chaos Communication Congress in Germany.
Ars Technica also has an article on it, but it predates the presentation so it doesn't have some of the later details.
Anyway, the good news is that in the end the hackers at Dragon Sector were able to unlock most of the trains: A few had additional trickery that they didn't want to hack around, because it might break the train's certification. For the others, they discovered undocumented "cheat codes" in the software that they could use to bypass the secret lockouts... presumably the same ones that Newag would have used when they "repaired" trains.
4K notes
·
View notes
Text
An adversarial iMessage client for Android
Adversarial interoperability is one of the most reliable ways to protect tech users from predatory corporations: that's when a technologist reverse-engineers an existing product to reconfigure or mod it (interoperability) in ways its users like, but which its manufacturer objects to (adversarial):
https://www.eff.org/deeplinks/2019/10/adversarial-interoperability
"Adversarial interop" is a mouthful, so at EFF, we coined the term "competitive compatibility," or comcom, which is a lot easier to say and to spell.
Scratch any tech success and you'll find a comcom story. After all, when a company turns its screws on its users, it's good business to offer an aftermarket mod that loosens them again. HP's $10,000/gallon inkjet ink is like a bat-signal for third-party ink companies. When Mercedes announces that it's going to sell you access to your car's accelerator pedal as a subscription service, that's like an engraved invitation to clever independent mechanics who'll charge you a single fee to permanently unlock that "feature":
https://www.techdirt.com/2023/12/05/carmakers-push-forward-with-plans-to-make-basic-features-subscription-services-despite-widespread-backlash/
Comcom saved giant tech companies like Apple. Microsoft tried to kill the Mac by rolling out a truly cursèd version of MS Office for MacOS. Mac users (5% of the market) who tried to send Word, Excel or Powerpoint files to Windows users (95% of the market) were stymied: their files wouldn't open, or they'd go corrupt. Tech managers like me started throwing the graphic designer's Mac and replacing it with a Windows box with a big graphics card and Windows versions of Adobe's tools.
Comcom saved Apple's bacon. Apple reverse-engineered MS's flagship software suite and made a comcom version, iWork, whose Pages, Numbers and Keynote could flawlessly read and write MS's Word, Excel and Powerpoint files:
https://www.eff.org/deeplinks/2019/06/adversarial-interoperability-reviving-elegant-weapon-more-civilized-age-slay
It's tempting to think of iWork as benefiting Apple users, and certainly the people who installed and used it benefited from it. But Windows users also benefited from iWork. The existence of iWork meant that Windows users could seamlessly collaborate on and share files with their Mac colleagues. IWork didn't just add a new feature to the Mac ("read and write files that originated with Windows users") – it also added a feature to Windows: "collaborate with Mac users."
Every pirate wants to be an admiral. Though comcom rescued Apple from a monopolist's sneaky attempt to drive it out of business, Apple – now a three trillion dollar company – has repeatedly attacked comcom when it was applied to Apple's products. When Apple did comcom, that was progress. When someone does comcom to Apple, that's piracy.
Apple has many tools at its disposal that Microsoft lacked in the early 2000s. Radical new interpretations of existing copyright, contract, patent and trademark law allows Apple – and other tech giants – to threaten rivals who engage in comcom with both criminal and civil penalties. That's right, you can go to prison for comcom these days. No wonder Jay Freeman calls this "felony contempt of business model":
https://pluralistic.net/2023/11/09/lead-me-not-into-temptation/#chamberlain
Take iMessage, Apple's end-to-end encrypted (E2EE) instant messaging tool. Apple customers can use iMessage to send each other private messages that can't be read or altered by third parties – not cops, not crooks, not even Apple. That's important, because when private messaging systems get hacked, bad things happen:
https://en.wikipedia.org/wiki/2014_celebrity_nude_photo_leak
But Apple has steadfastly refused to offer an iMessage app for non-Apple systems. If you're an Apple customer holding a sensitive discussion with an Android user, Apple refuses to offer you a tool to maintain your privacy. Those messages are sent "in the clear," over the 38-year-old SMS protocol, which is trivial to spy on and disrupt.
Apple sacrifices its users' security and integrity in the hopes that they will put pressure on their friends to move into Apple's walled garden. As CEO Tim Cook told a reporter: if you want to have secure communications with your mother, buy her an iPhone:
https://finance.yahoo.com/news/tim-cook-says-buy-mom-210347694.html
Last September, a 16-year old high school student calling himself JJTech published a technical teardown of iMessage, showing how any device could send and receive encrypted messages with iMessage users, even without an Apple ID:
https://jjtech.dev/reverse-engineering/imessage-explained/
JJTech even published code to do this, in an open source library called Pypush:
https://github.com/JJTech0130/pypush
In the weeks since, Beeper has been working to productize JJTech's code, and this week, they announced Beeper Mini, an Android-based iMessage client that is end-to-end encrypted:
https://beeper.notion.site/How-Beeper-Mini-Works-966cb11019f8444f90baa314d2f43a54
Beeper is known for a multiprotocol chat client built on Matrix, allowing you to manage several kinds of chat from a single app. These multiprotocol chats have been around forever. Indeed, iMessage started out as one – when it was called "iChat," it supported Google Talk and Jabber, another multiprotocol tool. Other tools like Pidgin have kept the flame alive for decades, and have millions of devoted users:
https://www.eff.org/deeplinks/2021/07/tower-babel-how-public-interest-internet-trying-save-messaging-and-banish-big
But iMessage support has remained elusive. Last month, Nothing launched Sunchoice, a disastrous attempt to bring iMessage to Android, which used Macs in a data-center to intercept and forward messages to Android users, breaking E2EE and introducing massive surveillance risks:
https://www.theverge.com/2023/11/21/23970740/sunbird-imessage-app-shut-down-privacy-nothing-chats-phone-2
Beeper Mini does not have these defects. The system encrypts and decrypts messages on the Android device itself, and directly communicates with Apple's servers. It gathers some telemetry for debugging, and this can be turned off in preferences. It sends a single SMS to Apple's servers during setup, which changes your device's bubble from green to blue, so that Apple users now correctly see your device as a secure endpoint for iMessage communications.
Beeper Mini is now available in Google Play:
https://play.google.com/store/apps/details?id=com.beeper.ima&hl=en_US
Now, this is a high-stakes business. Apple has a long history of threatening companies like Beeper over conduct like this. And Google has a long history deferring to those threats – as it did with OG App, a superior third-party Instagram app that it summarily yanked after Meta complained:
https://pluralistic.net/2023/02/05/battery-vampire/#drained
But while iMessage for Android is good for Android users, it's also very good for Apple customers, who can now get the privacy and security guarantees of iMessage for all their contacts, not just the ones who bought the same kind of phone as they did. The stakes for communications breaches have never been higher, and antitrust scrutiny on Big Tech companies has never been so intense.
Apple recently announced that it would add RCS support to iOS devices (RCS is a secure successor to SMS):
https://9to5mac.com/2023/11/16/apple-rcs-coming-to-iphone/
Early word from developers suggests that this support will have all kinds of boobytraps. That's par for the course with Apple, who love to announce splashy reversals of their worst policies – like their opposition to right to repair – while finding sneaky ways to go on abusing its customers:
https://pluralistic.net/2023/09/22/vin-locking/#thought-differently
The ball is in Apple's court, and, to a lesser extent, in Google's. As part of the mobile duopoly, Google has joined with Apple in facilitating the removal of comcom tools from its app store. But Google has also spent millions on an ad campaign shaming Apple for exposing its users to privacy risks when talking to Android users:
https://www.theverge.com/2023/9/21/23883609/google-rcs-message-apple-iphone-ipager-ad
While we all wait for the other shoe to drop, Android users can get set up on Beeper Mini, and technologists can kick the tires on its code libraries and privacy guarantees.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2023/12/07/blue-bubbles-for-all/#never-underestimate-the-determination-of-a-kid-who-is-time-rich-and-cash-poor
#pluralistic#multiprotocol#interoperability#adversarial interop#beeper#reverse engineering#blue bubbles#green bubbles#e2ee#end to end encrypted#messaging#jjtech#pypushbeeper mini#matrix#competitive compatibility#comcom
1K notes
·
View notes
Text


🌈 Double Coin Karada
~ 32m of 6mm jute
#shibari#decorative rope#decorative knot#double coin knot#karada#let's see it from the back#body tie#rope art#fiber art#reverse engineering#tbt#rope memories#built on my mannequin Rue#mannequin
255 notes
·
View notes
Text


Well, it took me about an hour to throw this texture together and it took me all of five minutes to get it into game; a default replacement base horse texture to cure this poor creature of its default EA textures. This first beta run is probably leaning too Alpha for my Maxis Match tastes (but tbf, the assets I used were also more realistic than stylized, so that's likely why) but still, neat to know it can be done and rather quickly.
I also overrode the muscle definition texture (which is literally just a slightly-more defined diffuse; if you use the muscle definition w/ the fuzzy coat thickness on, you can't even see it LMAO) to be the same texture as the base but for future base replacements, it could definitely be done to have a custom base and a custom muscled base too. This also doesn't affect foals (because they have a different base texture, I kind of sussed it out and just ignored it when default-replacing).
Eh, it's good enough progress for tonight. I am more excited about fur presets allowing me to have multiple 'new base textures' in the game. I'm looking forward to having a stock "coat" preset for my muscle gods that gives them a buffer body texture & a lanky "coat" preset for my warmbloods that gives them more slender textures.
Anyhoo, since I'm bottlenecked on making any hair or tack, I'm probably going to explore stencils and paint mode tomorrow and custom coat colours. I have a few horse OCs I plan to try and drop-kick in.
205 notes
·
View notes
Text
the outlines in kirby's return to dream land deluxe are very interesting, theyre definitely the cleanest 3d outlines i have ever seen anyone do
visually theyre just the model but darkened and expanded out a bit, and instead of clipping into any geometry they simply fade out and seem aware of the other outlines and models in the scene, merging together perfectly


im VERY surprised no one else has done this, because the way they pulled it off is actually EXTREMELY simple
(this will go into kinda technical graphics rendering talk)
the first clue is that looking into the code used for rendering reveals that the game draws the outlines after the rest of the scene has been drawn
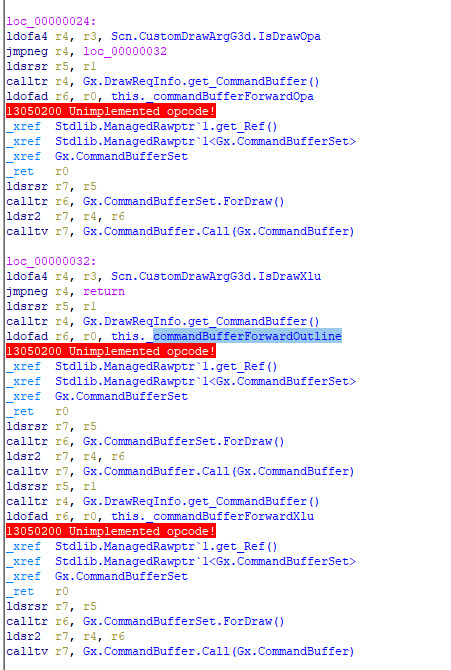
specifically, the order that objects are drawn from this function is:
opaque models (deferred rendering)
decals (deferred)
opaque models (forward rendering, essentially just fully rendering every single model)
outline models (forward)
transparent models (forward)
interestingly, outline models count as transparent, disabling transparency rendering will also disable outlines
the next hint about how it works comes directly from this enum listing all of the passes the game draws
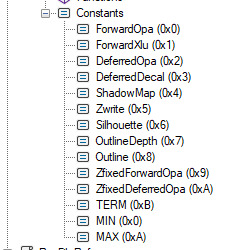
the most important part of this is "OutlineDepth" and "Outline", which reveals that the outlines render their own depth buffer!! this contains essentially how far away each pixel is from the camera, in ingame/world space units
looking into the models themselves, all of the models for characters have duplicated meshes that use a material specifically for outlines
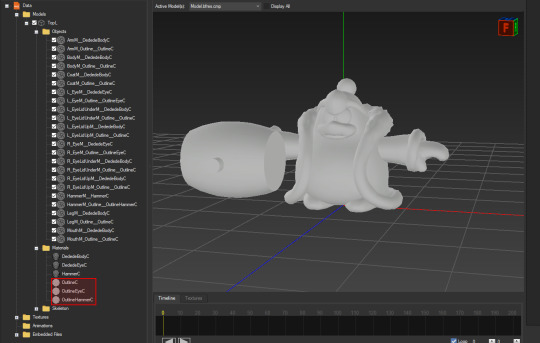
using this information alone, its very easy to recreate the outlines in blender!!

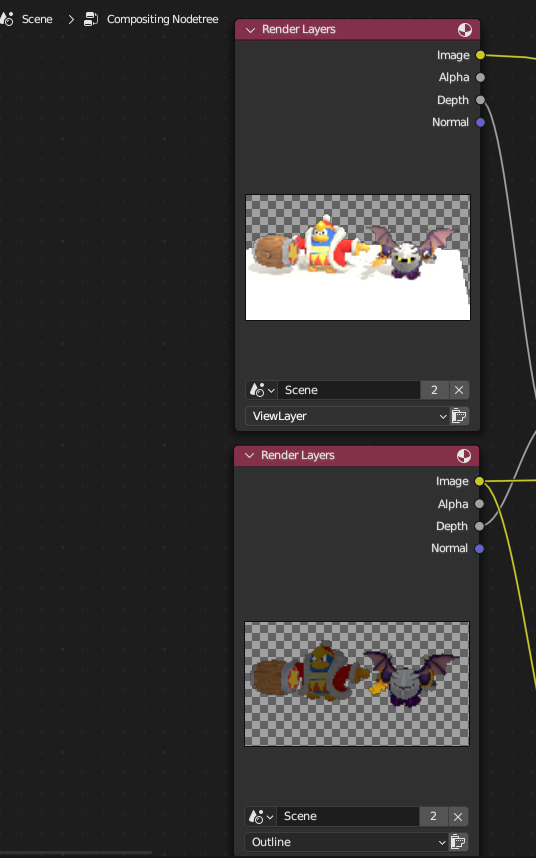
this is achieved in the same way, by rendering the raw scene and the outlines in two separate images using blender's render layers feature, with the outlines being significantly darkened, using only the diffuse texture, and the meshes themselves expanded slightly using geometry nodes
the rest of the models are rendered normally with PBR
determining where the outlines are drawn is just the result of some extremely simple math using the depth buffer of each layer
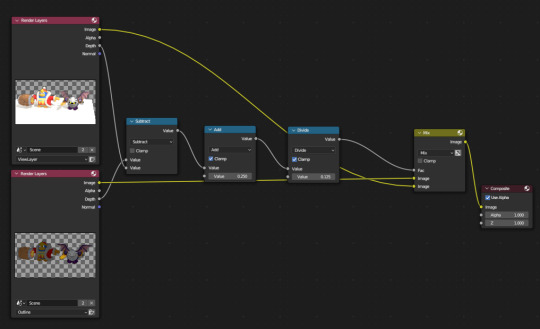
if you would like to see the result of this math, this is the "outline mask buffer":

as a bonus, if we gaussian blur the outline we can achieve a similar look to the game's promo art as well!! however, this doesnt look super good, improving on how this looks specifically most likely requires more tinkering in image editing software like photoshop

211 notes
·
View notes
Text
[Spade no Kuni no Alice] Machine Translation Patches (White & Black) Download
White World Screenshots



Black World Screenshots

This is a machine translation patch which was created by running the dialog files for both games through Google translate. The game should be mostly understandable but there will occasional nonsense translations or cut off lines. very basic JP knowledge makes some of the translation oddities easier to understand.
Patch should work on emulator and modded Switch
Patch Downloads:
White: DL
Black: DL
Please note that the patch for White World is much larger since the game has one large asset bundle that contains all the code/levels rather than multiple smaller ones like Black World.
100% Save Data Downloads:
White: DL
Black: DL
Installation instructions are included in the patch README file
Some mistranslation/oddity examples, some are kinda funny. (These are old screenshots from before I fixed the color of character dialog boxes and backlog portraits, they are fixed in the actual patch)




#spade no kuni no alice#snkna#hnkna#heart no kuni no alice#alice in the country of hearts#patch#otome game#machine translation#mod#reverse engineering
64 notes
·
View notes
Text
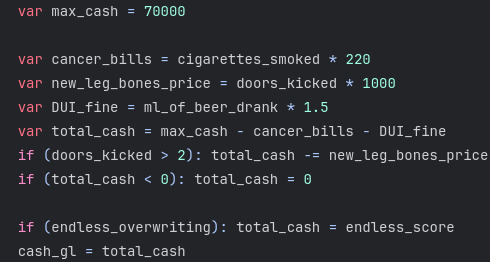
This is a reason why we lose money in story mode? Fair enough...
21 notes
·
View notes
Text
THEY PUT A PAYWALL ON A BOMB?????!!!!!!!!!!
Hilarious!!!!!

Oops!
#dougie rambles#personal stuff#star trek lower decks#star trek#lower decks#ferengi#bomb#paywall#gifs#Genesis device#long night of solace#halo reach#my poor attempt at a joke#no context#this sounded funnier in my head#shitpost#reverse engineering#nick locarno#robert duncan mcneill#tom paris#except not really#what
42 notes
·
View notes
Text

23 notes
·
View notes
Text


MorphOS - DoomRPG
8 notes
·
View notes
Text
ROBLOX 2007 and 2008 RBXGS/RCCService leaks
Yesterday, multiple internal ROBLOX applications ranging from 2007 to 2008 were found and released.
Most of these are RBXGS, which is what ROBLOX originally used for their game servers. It requires a 2003 Windows Server with IIS (Internet Information Services) installed on it to run.
One of these (0.3.784.0, dated 5/13/2008) is another application called RCCService. It fulfills mostly the same purpose that RBXGS did such as rendering avatars and hosting games. RCCService is still used by ROBLOX today. It can be installed and run on your PC without modification.
After a little setup, I was able to render some avatars with it.
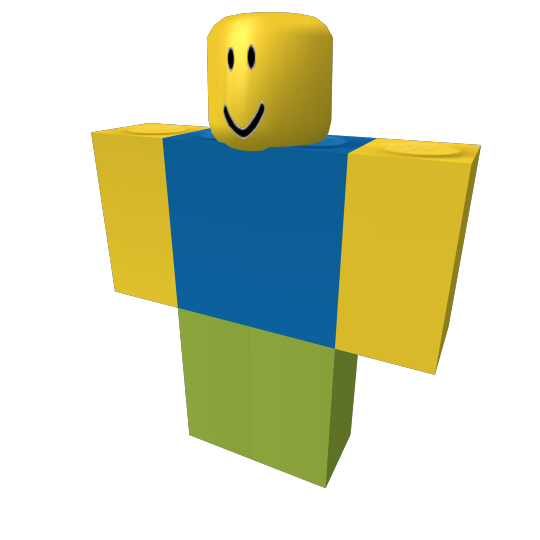
Here's a noob in 4k. We can render in any size we want.

This one is 64x64 large. We can modify any of the properties of the character.

A character with colors, a transparent arm, a missing leg, and a fucked up head. It's looking great! We can also add T-Shirts...

Shirts and pants...

Fucked up faces (they weren't supported in 2008)...

And with a little bit of troubleshooting, hats.

Here's builderman

We can render more than just avatars. We can render parts...
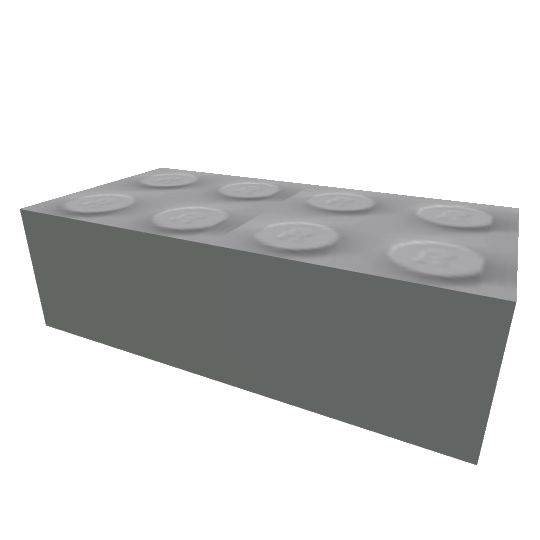
and Places. I could probably do entire models too.

You can do a lot with it if you mess around. You could also implement it into your own website to render avatars automatically and host 2008 games.
Using 2008 RCC to host games also results in more security over self hosted servers.
Player IPs are not exposed if someone attempts to grab them. It only shows the Server IP
Servers automatically shut down if a DLL is injected into a client
RCC checks the version of clients trying to join, and will refuse to connect if it does not match. This can be bypassed if you change the version of the client with a program, though
There are still RCE vulnerabilties in the client, however, so I'd be wary.
Another huge discovery in the RBXGS are PDB files. These files contain symbols (function names), where they are, and line information. Using this makes it much easier to reverse engineer. This means that we might see a reverse engineered 2007 or 2008 ROBLOX source available at one point, if someone decides to make it.
If you wish to check these out for your self, you can download them here.
36 notes
·
View notes
Note
hiya foone! i'm working on the surprisingly lofty task of modding barbie fashion show 2004 and i've been told twice to ask if you have any leads on how to get to the game files. i don't know how to simplify it because i'm so in over my head at this point. here is the thread
okay so here's how you reverse engineer an arbitrary game, the quick version:
Research. Who made the game? what else did they make? Maybe they made a game with the same engine, and someone already figured out that one? (not that I saw on a quick look, but you may be able to dig deeper) Also, look in the game files. There's a PowerRender.dll and a sipEngine.bc file. Nothing for sipEngine, but PowerRender has a hit on the internet archive, maybe that download includes some info on how it encodes files?
Look at the files (with a hex editor, like HxD). KAR files seem to be the main storage mechanism, and they've got a RIFF header. RIFF is a standard, though they're not using it exactly. But this might help. Another thing you can spot in the KAR files is a bunch of english strings (CreditsTb.kar is lousy with them). That's a good sign: it means the files aren't compressed, so you don't have to figure out the compression method.
Static analysis of the EXE. Get Ghidra and load up the EXE. Find where it opens files (CreateFileA/CreateFileW on windows), trace back from there. Check the strings. Hey look, function FUN_004e6260 is called with "KAResource.kar". so FUN_004e6260 is probably a function to load arbitrary resource files. Dig through that, figure out how it works.
Dynamic analysis of the EXE. Stick it in a debugger and see what it does. Set a breakpoint on CreateFileA/W and follow the execution. I don't have a good recommendation for what tool to use here, I'm from the past. I've used Ollydbg a lot but it hasn't been updated in 9 years.
Hijack the EXE and make it do your work for you. One thing I noticed while looking around was references to Python. This game apparently embeds a python interpreter, version 2.2. Maybe you can find where it loads the code from, or inject your own code?
Anyway those are some introductory ideas. feel free to ask any follow-up questions, but this hopefully gives you some idea of where to start?
Good luck!
443 notes
·
View notes
Text
i had someone reach out to me recently about a DRM i cracked a bit ago... it was the author who wrote it 😳
https://www.sc3d.com/post/uncracking-pacman/
give it a read!! it has some great insight into why the DRM was made the way it was
6 notes
·
View notes
Text

Here's a collage of a few of the steps I took in reverse engineering this double coin karada if it's useful to anyone - I began with 4 lengths of 8m rope draped behind the neck of my mannequin, then I created the coin knot rows across the front of the torso, and secured everything in the back as cleanly as I could.
This isn't a tutorial, but if you'd like a full tutorial, let me know and I'd love to share my take on this ubiquitous, decorative build!
#shibari#karada#double coin knot#collage#rope tutorial#reverse engineering#rope art#learning the ropes
92 notes
·
View notes
Text



Decided to try default-replacing the default EA 'fur' (since we can't add more till MorphMaker is updated!) with the SSO Curly Horse texture and,,, mmmm.......
It has a normal map as well to make the curls pop a bit <: it'll get released, uh, eventually LMAO
157 notes
·
View notes
Text
There was no other way even in the divine book. The nakedness had to be revealed. To be so intensely tempted that sin was the only evolutionary consequence. Whoever shows me a different path to felicity is either a liar or taking me through a nonexistent unnatural method to experience the divine. Yes, my eyes are willing to cry an ocean of tears but at first I must first taste and devour every forbidden fruit that's ripened in you...
Random Xpressions
8 notes
·
View notes