#csma/cd
Explore tagged Tumblr posts
Text
Ve489 Computer Networks Homework Set 4
Answer following questions about random access protocols: What is the vulnerable period for Aloha? How about slotted Aloha? Explain it. What is vulnerable period of CSMA? How can we make sure the performance of CSMA is better than Aloha? Why collision detection (CD) can improve performance of CSMA? Considering the CSMA/CA based DCF in IEEE 802.11, answer the following questions: What is…
0 notes
Text
Telecommunication protocols application interaction
Let's look at the basics of transferring information between two application processes in the OSI model.
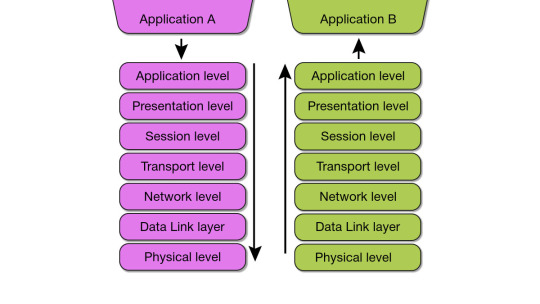
Say an application (in the picture above) needs to access a file service on another computer. It sends a request to the application layer. Based on it, the software generates a standard format message consisting of a data field and a service header. The latter contains a description of actions for the application layer of the other machine to perform, as well as instructions for the adjacent lower layer. The presentation layer, in turn, formats the data according to the instructions received and adds its own header (some protocol implementations also include service data at the end of the message), after which the information is sent to the session layer. This procedure, called encapsulation, is repeated further as data and service information move to the physical layer.
When arriving at the physical layer, i.e., the network, data passes through many other devices (network adapters, hubs, routers, bridges, etc.) and, upon reaching the destination (for example, a SIP phone), undergoes a reverse encapsulation process (right side of the picture).
Data networks can be of two types: local (local area network, LAN) and global (wide area network, WAN). The latter connects any two networks within the globe with dedicated or switched communication channels. Local networks differ in transmission medium, topology, and access control. Depending on the transmission medium, they are divided into wired (using coaxial, twisted pair, or fiber-optic cable) and wireless (WLAN), and according to the type of topology, into networks with 'bus', 'ring', or 'star' topologies.
Each computer on the local network is connected to the transmission medium through a special adapter that "sees" what any other adapter on the same network is transmitting; such systems are called broadcasts.
The MAC protocol regulates the sequence of nodes' access to the transmission medium. It is implemented using two types of schemes: polling or contention-based MAC schemes.
MAC polling networks can be centralized or distributed. Centralized ones have a star topology with a hub as the control node. In contrast, distributed ones have a ring or bus topology with token passing. Contention-based MACs are often implemented as carrier sense multiple access with collision detection (CSMA/CD) or carrier sense multiple access with collision avoidance (CSMA/CA). The first is used in all types of Ethernet LANs, and the second is used in most wireless WLANs.
The unrivaled leader among local networks is the IEEE 802.3 Ethernet network, where coaxial, twisted pair (designated by the letter T for 'twisted') and fiber-optic cables are used as transmission media. The transition to twisted-pair cable made it possible to implement full-duplex transmission over two twisted pairs, leaving the concept of collision meaningless since transmission and reception became independent operations. Ethernet has transmission speeds of 10, 100 ('Fast Ethernet'), 1000 Mbit/s (1 Gbit/s, 'Gigabit Ethernet'), and up to 400 Gigabit Ethernet.
Wireless local networks (wireless LAN, WLAN) have also become widespread. Their parameters are stated in the IEEE 802.11 specifications, known as Wi-Fi.
Today, the most common Wi-Fi 5 or 802.11ac defines the operation of wireless local area networks in the 2.4/5 GHz ranges with a data transfer rate of 1.3 Gbit/s. Shortly, speeds will reach 9.6 Gbit/s over 6 GHz frequency bands.
The range of most WLAN systems is 120 m, depending on the number and type of obstacles encountered. Additional access points will help expand the coverage area. Using two or three carrier frequencies instead of one can increase the number of users and network capacity.
Obviously, with Wi-Fi, network security becomes an important issue. A priori, wireless networks must be equipped with additional means of ensuring reliability compared to wired ones. WLAN uses direct sequence spread spectrum (DSSS) technology, which is highly resistant to data corruption and interference, including intentional ones. The problem of user authentication can be solved by introducing system identifiers. The wired equivalent privacy (WEP) mode is provided to transmit necessary information. In this case, the signal is encrypted with an additional algorithm, and the data is controlled using an electronic key.
Like all IEEE 802.3 standards, 802.11 refers to the lower two layers of the OSI model: physical and link. Any network application, operating system, or protocol (such as TCP/IP) will function equally well on an 802.11 network or Ethernet one.
The original 802.11 standard defines the basic architecture - the features of 802.11 services. The 802.11x specification only addresses the physical layer, introducing higher access speeds.
In conclusion, we should note that thanks to the close ties between Ethernet and the IP protocol, the scope of Ethernet applications is expanding, particularly in broadband subscriber access (BSA) networks.
0 notes
Text
Un día como hoy (11 de noviembre) en la computación


El 11 de noviembre de 1973 se instala la primera red Ethernet. Constaba de mil metros de cable coaxial usando el protocolo CSMA/CD. Todo viene de un memo que escribiera Robert Metcalfe llamado Alto Ethernet, escrito en mayo 22 de ese año. Ethernet se ha convertido de facto en el estándar de redes locales para negocios y hogar #retrocomputingmx #ethernet
0 notes
Text
Ethernet TSN vs. Traditional Ethernet: Key Differences and Advantages
Ethernet Time-Sensitive Networking (TSN) and traditional Ethernet represent two distinct approaches to network communication, each tailored to specific requirements and applications. This article compares Ethernet TSN with traditional Ethernet, highlighting their key differences, advantages, and the implications for various industries, including automotive, industrial automation, and telecommunications.
Understanding Traditional Ethernet
Traditional Ethernet, based on IEEE 802.3 standards, has been the cornerstone of local area networks (LANs) for decades. It operates using Carrier Sense Multiple Access with Collision Detection (CSMA/CD), where devices contend for network access and manage collisions to ensure data integrity.
Key Features of Traditional Ethernet
Best-Effort Communication: Traditional Ethernet uses a best-effort approach to data transmission, where data packets are sent without guarantees regarding latency or timing. This non-deterministic behavior makes it suitable for applications with less stringent timing requirements.
Limited Quality of Service (QoS): QoS mechanisms in traditional Ethernet prioritize traffic based on predefined rules but do not guarantee timely delivery or latency control. As a result, it may not meet the requirements of real-time applications or safety-critical systems.
Introducing Ethernet TSN
Ethernet TSN enhances traditional Ethernet by incorporating time-sensitive capabilities necessary for real-time communication and deterministic behavior. It builds upon IEEE 802.1 standards and includes mechanisms for time synchronization, traffic shaping, and low-latency transmission.
Key Features of Ethernet TSN
Deterministic Communication: Ethernet TSN ensures deterministic behavior by synchronizing network clocks, prioritizing critical traffic, and minimizing network latency and jitter. This capability is essential for applications that require precise timing, such as industrial automation, automotive systems, and multimedia streaming.
Enhanced Quality of Service: TSN provides advanced QoS features, including time-aware scheduling and traffic shaping, to prioritize critical data streams. It guarantees timely delivery of time-sensitive data while optimizing bandwidth usage and network efficiency.
Advantages of Ethernet TSN
Real-Time Capabilities: TSN supports real-time communication with predictable latency, making it suitable for applications like industrial control systems, autonomous vehicles, and multimedia streaming where timing is critical.
Scalability and Flexibility: TSN accommodates scalable network architectures and diverse application requirements without compromising performance. It integrates seamlessly with existing Ethernet infrastructure, facilitating gradual adoption and interoperability.
Applications and Industry Implications
Automotive Industry: Ethernet TSN enhances vehicle connectivity, supports autonomous driving functionalities, and improves safety through precise control and synchronization of vehicle systems.
Industrial Automation: TSN optimizes production processes by enabling synchronized control and monitoring of manufacturing equipment, reducing downtime and enhancing operational efficiency.
Future Directions and Adoption
Standardization and Interoperability: Industry efforts focus on standardizing Ethernet TSN to ensure compatibility and interoperability across diverse applications and network environments.
Integration with Emerging Technologies: TSN integrates with 5G networks, edge computing platforms, and IoT devices to support advanced applications in smart cities, healthcare, and transportation.
Conclusion
Ethernet TSN represents a significant evolution from traditional Ethernet, offering deterministic communication, enhanced QoS, and real-time capabilities crucial for modern applications. As industries embrace TSN to meet stringent timing requirements and support innovative technologies, the technology drives advancements in connectivity, efficiency, and reliability across diverse sectors.
1 note
·
View note
Text
Tipos de estándares
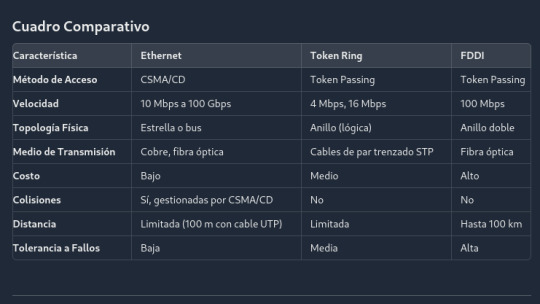
1. Ethernet
Descripción
Ethernet es el estándar de red más popular y ampliamente utilizado en redes LAN. Fue desarrollado en los años 70 y se basa en el protocolo CSMA/CD (Carrier Sense Multiple Access with Collision Detection). Ethernet permite que múltiples dispositivos compartan el mismo medio de comunicación y manejen colisiones de datos para garantizar una transmisión eficiente.
Usos
Ethernet se utiliza en la mayoría de las redes domésticas y empresariales, conectando computadoras, impresoras, servidores y otros dispositivos en una red LAN.
Ventajas
Costo: Económico y fácil de implementar.
Velocidad: Desde 10 Mbps hasta 100 Gbps en sus versiones más avanzadas.
Compatibilidad: Amplia gama de dispositivos compatibles.
Desventajas
Colisiones: En redes muy congestionadas, pueden ocurrir colisiones de datos.
Distancia limitada: La longitud de los cables es limitada en comparación con otros estándares.
2. Token Ring
Descripción
Token Ring, desarrollado por IBM, utiliza una topología de anillo donde un "token" especial circula alrededor de la red. Solo el dispositivo que posee el token puede transmitir datos, lo que elimina las colisiones.
Usos
Se utilizó en entornos corporativos que requerían una alta confiabilidad y una gestión eficiente del tráfico de red.
Ventajas
Sin colisiones: El método de acceso evita colisiones, mejorando la eficiencia en redes ocupadas.
Determinismo: Garantiza tiempos de acceso predecibles a la red.
Desventajas
Costo: Más caro que Ethernet debido a la complejidad del equipo necesario.
Velocidad: Limitado a 4 o 16 Mbps, mucho más lento que las versiones modernas de Ethernet.

3. FDDI (Fiber Distributed Data Interface)
Descripción
FDDI es un estándar que utiliza fibra óptica y topología de anillo doble, proporcionando alta velocidad y tolerancia a fallos. Fue diseñado para conectar estaciones sobre distancias más largas y soportar grandes redes corporativas.
Usos
FDDI se usa en redes backbone, donde se necesita alta velocidad y una larga distancia de transmisión, como en campus universitarios o grandes empresas.
Ventajas
Alta velocidad: Ofrece hasta 100 Mbps.
Tolerancia a fallos: La estructura de doble anillo permite continuar la operación si un anillo falla.
Desventajas
Costo: Muy caro debido al uso de fibra óptica y equipos especializados.
Complejidad: Su implementación y mantenimiento requieren más conocimientos técnicos.

0 notes
Text
如何判断网站是CDN节点故障还是源服务器问题呢?
网卡就是计算机与局域网互连的设备。计算机主要通过网卡接入网络。网卡又称为网络适配器或网络接口卡NIC(Network interface Card),是构成计算机网络系统中最基本的、最重要的连接设备。
一、网卡主要功能
网���在TCP/IP模型中,工作在物理层及数据链路层,用于接收和发送计算机数据。
网络中的计算机都必须拥有一个唯一的MAC地址,这个MAC地址由网卡提供,同时网卡的主要功能包括:
数据的发送(封装)和接收(解封装):发送数据时,加上首部和尾部;接收数据时,剥去首部和尾部
数据的编码和译码:物理层数据的编解码
数据链路管理:主要是CSMA/CD(冲突检测的载波监听多路访问)的实现
二、网卡的演进
现在让我们了解下网卡的这些年来的演进过程。
三、网卡的分类
网卡有哪些分类呢?现在小编就带着大家来了解一下。
服务器专用网卡VS普通网卡
相对于服务器专用网卡来说,普通网卡指应用在普通PC、工作站、消费级电子产品中的网卡对可靠性、安全性等要求不高,而服务器与普通PC工作站的不同之处是服务器一直处于工作中,且要求长时间稳定运行,这就要求服务器网卡具有以下特点:
数据传输速度快
服务器时刻处于数据计算、交换过程中,普通网10Mbps、 100Mbps的数据已不满足大数据流量网络,当前服务器常用的网卡速率为10Gbps、25Gbps等。
CPU占用率低
服务器的CPU是不停工作的,处理着大量的数据。如果一台服务器的CPU大部分时间都在为网卡提供数据响应,势必会影响到对其他任务的处理速度。服务器网卡有自带的控制芯片,可以处理一些CPU任务,从而减少CPU的计算开销。
安全性能高
如果服务器的网卡出现故障,则服务器将无法接收,发送数据,相当于宕机,所以高可靠性是是服务器网卡的必备特性。服务器网卡基本上 都具有容错功能,如Intel的AFT(网卡出错冗余),ALB(网卡负载均衡)等技术。
全球服务器 ,高防CDN加速,国内海外节点 AJCDN
云服务器,物理机,大带宽
香港 新加坡 台湾 美国
CN2,大陆优化,国际线路
防DDOS,CC攻击
免实名+可测试,满意再合作
值班客服,24小时营业
欢迎询问 ~
飞机:@ajcdn017
微信: ajcdn017
0 notes
Note
Did it had CSMA/CD?
i had a dream the new industry standard data cable linking thingy for servers n databases and other such applications was ethernet over orgone energy
You're a modern net prophet
566 notes
·
View notes
Text
Multiple Access Protocol - ALOHA, CSMA, CSMA/CA and CSMA/CD
Multiple Access Protocol – ALOHA, CSMA, CSMA/CA and CSMA/CD Multiple access protocols are a set of protocols that work in the Medium Access Control sublayer (MAC sublayer) of the Open Systems Interconnection (OSI) model. These protocols allow a number of users to access a shared network channel. Several data streams originating from several nodes are transferred through the multi-point…
View On WordPress
0 notes
Note
Hii i like your blog a lot bcs ive been getting started on a comp sci bachelor and i understand most of the stuff youre talking about also youre cool.
Anyway have you heard of csma/cd? Like the network protocol? Funniest shit i had all semester. The fact that it's actually pretty usableis even funnier. Pretty sure thats what wed use in an anarchist society.
Have a good day!
ha im glad, thanks! i hadnt heard of it before!
The collision recovery procedure can be likened to what happens at a dinner party, where all the guests talk to each other through a common medium (the air). Before speaking, each guest politely waits for the current speaker to finish. If two guests start speaking at the same time, both stop and wait for short, random periods of time (in Ethernet, this time is measured in microseconds). The hope is that by each choosing a random period of time, both guests will not choose the same time to try to speak again, thus avoiding another collision.
what a mess! (imagining the equivalent of the little hallway dance where the same two collide and restart repeatedly)
7 notes
·
View notes
Text
Topology
Topology :
Topology defines the structure of the network of how all the components are interconnected to each other. There are two types of topology: physical and logical topology.
Physical topology is the geometric representation of all the nodes in a network.
Bus Topology
The bus topology is designed in such a way that all the stations are connected through a single cable known as a backbone cable.
Each node is either connected to the backbone cable by drop cable or directly connected to the backbone cable.
When a node wants to send a message over the network, it puts a message over the network. All the stations available in the network will receive the message whether it has been addressed or not.
The bus topology is mainly used in 802.3 (ethernet) and 802.4 standard networks.
The configuration of a bus topology is quite simpler as compared to other topologies.
The backbone cable is considered as a “single lane” through which the message is broadcast to all the stations.
The most common access method of the bus topologies is CSMA (Carrier Sense Multiple Access).
CSMA: It is a media access control used to control the data flow so that data integrity is maintained, i.e., the packets do not get lost. There are two alternative ways of handling the problems that occur when two nodes send the messages simultaneously.
CSMA CD: CSMA CD (Collision detection) is an access method used to detect the collision. Once the collision is detected, the sender will stop transmitting the data. Therefore, it works on “recovery after the collision”.
CSMA CA: CSMA CA (Collision Avoidance) is an access method used to avoid the collision by checking whether the transmission media is busy or not. If busy, then the sender waits until the media becomes idle. This technique effectively reduces the possibility of the collision. It does not work on “recovery after the collision”.
Advantages of Bus topology:
Low-cost cable: In bus topology, nodes are directly connected to the cable without passing through a hub. Therefore, the initial cost of installation is low.
Moderate data speeds: Coaxial or twisted pair cables are mainly used in bus-based networks that support upto 10 Mbps.
Familiar technology: Bus topology is a familiar technology as the installation and troubleshooting techniques are well known, and hardware components are easily available.
Limited failure: A failure in one node will not have any effect on other nodes.
Disadvantages of Bus topology:
Extensive cabling: A bus topology is quite simpler, but still it requires a lot of cabling.
Difficult troubleshooting: It requires specialized test equipment to determine the cable faults. If any fault occurs in the cable, then it would disrupt the communication for all the nodes.
Signal interference: If two nodes send the messages simultaneously, then the signals of both the nodes collide with each other.
Reconfiguration difficult: Adding new devices to the network would slow down the network.
Attenuation: Attenuation is a loss of signal leads to communication issues. Repeaters are used to regenerate the signal.
Ring Topology
Token passing: It is a network access method in which token is passed from one node to another node.
Token: It is a frame that circulates around the network.
Working of Token passing
A token moves around the network, and it is passed from computer to computer until it reaches the destination.
The sender modifies the token by putting the address along with the data.
The data is passed from one device to another device until the destination address matches. Once the token received by the destination device, then it sends the acknowledgment to the sender.
In a ring topology, a token is used as a carrier.
Advantages of Ring topology:
Network Management: Faulty devices can be removed from the network without bringing the network down.
Product availability: Many hardware and software tools for network operation and monitoring are available.
Cost: Twisted pair cabling is inexpensive and easily available. Therefore, the installation cost is very low.
Reliable: It is a more reliable network because the communication system is not dependent on the single host computer.
Disadvantages of Ring topology:
Read More
Difficult troubleshooting: It requires specialized test equipment to determine the cable faults. If any fault occurs in the cable, then it would disrupt the communication for all the nodes.
Failure: The breakdown in one station leads to the failure of the overall network.
Reconfiguration difficult: Adding new devices to the network would slow down the network.
Delay: Communication delay is directly proportional to the number of nodes. Adding new devices increases the communication delay.
Star Topology
Star topology is an arrangement of the network in which every node is connected to the central hub, switch or a central computer.
The central computer is known as a server, and the peripheral devices attached to the server are known as clients.
Coaxial cable or RJ-45 cables are used to connect the computers.
Hubs or Switches are mainly used as connection devices in a physical star topology.
Star topology is the most popular topology in network implementation.
Advantages of Star topology
Efficient troubleshooting: Troubleshooting is quite efficient in a star topology as compared to bus topology. In a bus topology, the manager has to inspect the kilometers of cable. In a star topology, all the stations are connected to the centralized network. Therefore, the network administrator has to go to the single station to troubleshoot the problem.
Network control: Complex network control features can be easily implemented in the star topology. Any changes made in the star topology are automatically accommodated.
Limited failure: As each station is connected to the central hub with its own cable, therefore failure in one cable will not affect the entire network.
Read More
Familiar technology: Star topology is a familiar technology as its tools are cost-effective.
Easily expandable: It is easily expandable as new stations can be added to the open ports on the hub.
Cost effective: Star topology networks are cost-effective as it uses inexpensive coaxial cable.
High data speeds: It supports a bandwidth of approx 100Mbps. Ethernet 100BaseT is one of the most popular Star topology networks.
Disadvantages of Star topology
A Central point of failure: If the central hub or switch goes down, then all the connected nodes will not be able to communicate with each other.
Cable: Sometimes cable routing becomes difficult when a significant amount of routing is required.
Tree topology
Tree topology combines the characteristics of bus topology and star topology.
A tree topology is a type of structure in which all the computers are connected with each other in hierarchical fashion.
The top-most node in tree topology is known as a root node, and all other nodes are the descendants of the root node.
There is only one path exists between two nodes for the data transmission. Thus, it forms a parent-child hierarchy.
Advantages of Tree topology
Support for broadband transmission: Tree topology is mainly used to provide broadband transmission, i.e., signals are sent over long distances without being attenuated.
Easily expandable: We can add the new device to the existing network. Therefore, we can say that tree topology is easily expandable.
Easily manageable: In tree topology, the whole network is divided into segments known as star networks which can be easily managed and maintained.
Error detection: Error detection and error correction are very easy in a tree topology.
Limited failure: The breakdown in one station does not affect the entire network.
Read More
Point-to-point wiring: It has point-to-point wiring for individual segments.
Disadvantages of Tree topology
Difficult troubleshooting: If any fault occurs in the node, then it becomes difficult to troubleshoot the problem.
High cost: Devices required for broadband transmission are very costly.
Failure: A tree topology mainly relies on main bus cable and failure in main bus cable will damage the overall network.
Reconfiguration difficult: If new devices are added, then it becomes difficult to reconfigure.
Mesh topology
Mesh technology is an arrangement of the network in which computers are interconnected with each other through various redundant connections.
There are multiple paths from one computer to another computer.
It does not contain the switch, hub or any central computer which acts as a central point of communication.
The Internet is an example of the mesh topology.
Mesh topology is mainly used for WAN implementations where communication failures are a critical concern.
Mesh topology is mainly used for wireless networks.
Mesh topology can be formed by using the formula: Number of cables = (n*(n-1))/2;
Where n is the number of nodes that represents the network.
Mesh topology is divided into two categories:
Fully connected mesh topology
Partially connected mesh topology
Full Mesh Topology: In a full mesh topology, each computer is connected to all the computers available in the network.
Partial Mesh Topology: In a partial mesh topology, not all but certain computers are connected to those computers with which they communicate frequently.
Advantages of Mesh topology:
Reliable: The mesh topology networks are very reliable as if any link breakdown will not affect the communication between connected computers.
Fast Communication: Communication is very fast between the nodes.
Easier Reconfiguration: Adding new devices would not disrupt the communication between other devices.
Disadvantages of Mesh topology
Cost: A mesh topology contains a large number of connected devices such as a router and more transmission media than other topologies.
Management: Mesh topology networks are very large and very difficult to maintain and manage. If the network is not monitored carefully, then the communication link failure goes undetected.
Efficiency: In this topology, redundant connections are high that reduces the efficiency of the network.
Hybrid Topology
The combination of various different topologies is known as Hybrid topology.
A Hybrid topology is a connection between different links and nodes to transfer the data.
When two or more different topologies are combined together is termed as Hybrid topology and if similar topologies are connected with each other will not result in Hybrid topology. For example, if there exist a ring topology in one branch of ICICI bank and bus topology in another branch of ICICI bank, connecting these two topologies will result in Hybrid topology.
Advantages of Hybrid Topology
Reliable: If a fault occurs in any part of the network will not affect the functioning of the rest of the network.
Scalable: Size of the network can be easily expanded by adding new devices without affecting the functionality of the existing network.
Flexible: This topology is very flexible as it can be designed according to the requirements of the organization.
Read More
Effective: Hybrid topology is very effective as it can be designed in such a way that the strength of the network is maximized and weakness of the network is minimized.
Disadvantages of Hybrid topology
Complex design: The major drawback of the Hybrid topology is the design of the Hybrid network. It is very difficult to design the architecture of the Hybrid network.
Costly Hub: The Hubs used in the Hybrid topology are very expensive as these hubs are different from usual Hubs used in other topologies.
Costly infrastructure: The infrastructure cost is very high as a hybrid network requires a lot of cabling, network devices, etc.
#Topology#explain Topology#what is Topology#benifits of Topology#types of Topology#advantages of Topology#disadvantages of Topology#tree Topology#star Topology#ring Topology#mesh Topology#hybrid Topology#bus Topology#features of Topology
2 notes
·
View notes
Text
Rajasthan Computer Teacher Syllabus 2021
RPSC Computer Teacher Syllabus 2021
Govt Computer Teacher Syllabus 2021- In Rajasthan, applications for computer teacher vacancy will be taken. With the release of the Rajasthan Computer Teacher Vacancy 2021 official notification, Rajasthan Computer Teacher Syllabus 2021 will also be given along with it.
कंप्यूटर शिक्षक सिलेबस 2021RPSC computer teacher syllabus 2021
Online application will be taken for 14601 posts of Computer Computer Teacher, out of which no posts have been fixed for first grade yet, 3616 posts for second class and 10985 posts for third class will be applied.
Computer Teacher Official Notification- Click Here
कंप्यूटर टीचर सिलेबस 2021
कंप्यूटर शिक्षक के 14601 पदों पर ऑनलाइन आवेदन लिया जाएगा जिसमें से प्रथम ग्रेड की अभी कोई पद निर्धारित नहीं किए गए हैं द्वितीय श्रेणी के लिए 3616 पद व तृतीय श्रेणी के लिए 10985 पदों पर आवेदन दिए जाएंगे।
Join Whatsapp Group Daily Govt Jobs Updates, Govt Scheme, Current Affairs WhatsApp Group Join Click Here – 3 WhatsApp Group Join Click Here – 4 WhatsApp Group Join Click Here- 5 WhatsApp Group Join Click Here- 6
Analyst cum Programmer Syllabus 2021
Written Examination Analyst cum Programmer 2021
PAPER – I
Reasoning Test & Numerical Analysis & General Knowledge
Problem solving, Data Interpretation, Data Sufficiency, Logical Reasoning and Analytical Reasoning. General Knowledge and Current Affairs relating to India and Rajasthan.
Data Base Management Systems
ER Diagram, data models- Relational and Object Oriented databases.
Data Base Design : Conceptual data base design, Normalization Primitive and Composite data types, concept of physical and logical databases, data abstraction and data independence, data aggregation and Relational Algebra.
Application Development using SQL : Host Language interface, embedded SQL programming, Stored procedures and triggers and views, Constraints assertions.
Internal of RDBMS : Physical data organisation in sequential, indexed random and hashed files. Inverted and multilist structures, B trees, B+ trees, Query Optimisation, Join algorithm, Transaction Processing, concurrency control and recovery management. Transaction model properties and state serialisability. Lock base protocols, two phase locking.
Different server multi user, multiprocess operating systems and requirement for client interfaces in distributed application environments.
Data Communication and Computer Networks
Computer Network Architecture, Circuit switching, Packet And Massage Switching, Network Structure. Physical Layer, Data Link Layer, Framing. Retransmission algorithms.
Analyst cum Programmer Syllabus 2021
TCP/IP Stack. IP Networks and Internet. DNS and Firewalls. Intrusion Detection and Prevention. Transport layer and TCP/IP. Network Management And Interoperability.
Multiple access and Aloha. CSMA/CD and Ethernet. High Speed LANs and topologies. Broadcast routing and spanning trees.
PAPER – II System Analysis and Design
Concept System : Definition and characteristics, elements and boundaries, types of system development lifecycle, recognition of needs, feasibility study, prototyping, role of system analyst. System planning and tools like DFD, data dictionary, decision trees, structured analysis and decision tables. IPO charts, structured walkthrough, input output form design, requirement and classification of forms, layout considerations form control, object oriented Design Concepts and methods. Software Life Cycle, Software Engineering paradigms.
Analysis System : Feasibility study requirement analysis, Cost benefit analysis, Planning systems, Analysis tools and techniques.
Design System : design fundamentals, Modular Design, Data and procedural design, object oriented design.
Computer Teacher Syllabus PDF Download
Syllabus Analyst-cum-Programmer-converted
Download
Software Maintenance : Maintenance Characteristics, Maintainability, Maintenance tasks and side effects.
Development System : Code documentation, Program design paradigms, Efficiency Consideration. Verification, Validation and Testing: testing methods, Formal Program Verification, Testing Strategies.
Software Project Management
Project Management Concept : The Management Spectrum, People, Product, Process & Project.
Process & Project Matrix : Software Measurement Size Oriented Matrices, Function Oriented Matrices.
Risk Analysis and Management : Risk Identification, Projection, Risk Refinement, Risk Monitoring And Management.
Project Planning : Objectives, Decomposition Techniques, Empirical Estimation Model.
Project Scheduling & Tracking, Software Quality Assurance, Software Configuration Management.
RPSC Computer Teacher Bharti Syllabus 2021
Before releasing the syllabus of Rajasthan Competition Vacancy 2021, their online applications are taken, along with the online application, their syllabus and qualification, pay scale etc. are determined, yet its official notification has not been received.
Computer shikshak bharti 2021 syllabus
राजस्थान कंप्यूटर शिक्षक भर्ती 2021 जो भी से आने की संभावना है वह इस प्रकार से है इनका कन्फर्मेशन ऑफिशियल नोटिफिकेशन आने के बाद में होगा ऑफिशियल नोटिफिकेशन में सिलेबस की घोषणा होने के बाद में आपको इसी पेज पर सूचित कर दिया जाएगा या आप ऑफिशियल वेबसाइट भी विजिट कर सकते हैं ।
Rajasthan Computer Teacher Official Notification 2021- CLick Here
Computer Teacher Bharti 2021 Syllabus देखने के लिए क्लिक करे
Rajasthan Computer Teacher Recruitment Rajasthan Computer Teacher Recruitment has come for the first time, so there is no confirmation of syllabus, after the official notification, you will get complete information of Rajasthan Computer Teacher Recruitment 2021 Syllabus.
Rajasthan Computer Teacher Vacancy 202
1कंप्यूटर शिक्षक भर्ती 2021 में आने वाले सब्जेक्ट
कंप्यूटर, जीके, हिंदी, अंग्रेजी, विज्ञान, गणित, रिजनिंग यह सब्जेक्ट आने की संभावना है। जिसमें कंप्यूटर का पार्ट 50% या 70% रहेगा फिलहाल यह कोई ऑफिशियल सूचना नहीं है। ऑफिशियल सूचना आने के बाद में आपको इसी पेज पर अपडेट कर दिया जाएगा ।
Computer Teacher Admit Card 202
1Rajasthan Computer Teacher Bharti Selection process
Rajasthan Computer Teacher Recruitment 2021 syllabus will be followed by an exam, merit list will be released on the basis of the same.
Download Rajasthan Computer Teacher Recruitment 2021 Syllabus PDF
Important Links
1 note
·
View note
Text
¿Qué onda con tu wifi?
Básicamente, el internet es una red que conecta a todas las computadoras (y celulares, tablets, etc...) del mundo. Imagínate que entre tu computadora y tu celular hubiera un hilo que las uniera, y de tu celular saliera un hilo que se conectara al celular de tu mamá y a la tablet de tu vecino, y esa tablet se conecta a otra y así hasta llegar a un celular en china. Imaginándote esto, ¿apoco no se forma una red gigante por todo el mundo?
Hay varias formas de tener alcance con el internet, tres de ellas son: local area network, metropolitan area y wide area network.
Una red puede tener la propiedad de ser cerrada o abierta; lo que significa que tiene protocolos con la dirección IP. Además la topología de la red se puede ver de dos formas: 1. Bus, a través de un cable de ethernet al que todas las computadoras en la red se conectan o 2. Estrella, que es una red inalámbrica con un punto central de acceso.
¿Qué es un protocolo? Es cómo se envían los paquetes de información a través de internet. En esta ocasión te voy a explicar dos de ellos:
CSMA/CD: Detección de colisiones, todos los mensajes son recibidos por todas las maquinas que están en el bus, cuando no hay mensajes transitando por él se pueden enviar mensajes. La información se manda con una dirección de llegada y pasa por todas las computadoras hasta que da con la dirección correcta, y esta es la que la recibe.
CSMA/CA: Conexión por wifi. Hay un acceso múltiple por detección de portadora con evitación de colisiones. Se da prioridad para mandar mensajes a las maquinas que llevan más tiempo esperando.
El software de internet tiene varias capas: 1. Aplicación, que ensambla el mensaje con una dirección. 2. Transporte, que divide el mensaje en paquetes. 3. Red, maneja el encaminamiento a través del internet. 4. Enlace, maneja la transmisión de paquetes.
Y a su vez, el internet mismo tiene capas, que sirven para la transferencia de mensajes a través de internet y para procesar la transferencia a través de unidades coordinadas y con funciones específicas.
¿Sabes qué es una dirección IP? Es la dirección de una interfaz de red, por eso en las películas de hackers siempre logran encontrar a personas al descubrir su dirección IP. Una dirección IP se compone por 32 bits, y una conexión privada no tiene la dirección completa. ICANN, que es la Internet Corporation for Assigned Names and Numbers es la encargada de asignar direcciones IP a los proveedores de servicios de internet.
Para tener una mejor conexión en tu casa podrías tener una combinación de redes; esto quiere decir combinar algunos de los siguientes:
Repetidor: extiende un red al conectar dos buses.
Puente: conecta dos redes compatibles
Conmutador: conecta varias redes compartibles
Router: conecta dos redes incompatibles.
Sin embargo tu conexión también depende el ancho de banda, cuyo alcance varía con la antena a la que te estés conectando. Te dejo esta página para medir la velocidad de tu internet: https://fast.com/es/
Finalmente te explico cómo puedes identificar una página web por su URL, ya que este se compone en diferentes partes: el protocolo, el servidor, el directorio y el nombre del documento al que finalmente llegas.

1 note
·
View note
Text
El uso de la red y la información
Hecho por: Sebastián
Redes de comunicación, no son más que la posibilidad de compartir con carácter universal la información entre grupos de computadoras y sus usuarios; UN componente vital de la era de la información.
La generalización del ordenador o computadora personal (PC) y de la red de área local (LAN) durante la década de los ochenta ha dado lugar a la posibilidad de acceder a información en bases de datos remotas, cargar aplicaciones desde puntos de ultramar, enviar mensajes a otros países y compartir archivos, todo ello desde un ordenador personal.
Las rede que permiten todo esto son equipos avanzados y complejos. Sus eficacia se basa en la con fluencia de muy diversos componentes. El diseño e implantación de una red mundial de ordenadores es uno de los grandes Milagros tecnológicos de las últimas décadas.
Redes de computadora
Una red de computadoras, también llamada red de ordenadores, red de comunicaciones de datos o red informática, es un conjunto de equipos informáticos y software conectados entre sí por medio de dispositivos físicos que envían y reciben impulsos eléctricos, ondas electromagnéticas o cualquier otro medio para el transporte de datos, con la finalidad de compartir información, recursos y ofrecer servicios.
Como en todo proceso de comunicación se requiere de un emisor, un mensaje, un medio y un receptor. La finalidad principal para la creación de una red de computadoras es compartir los recursos y la información en la distancia, asegurar la confiabilidad y la disponibilidad de la información, aumentar la velocidad de transmisión de los datos y reducir el costo general de estas acciones..
La estructuras y el modo de funcionamiento de las redes de informática actuales están definidos en varios estándares, siendo el más importante y extendido de todos ellos el modelo TCP/IP basado en el modelo de referencia OSI. Este última estructura cada red en siete capas con funciones concretas pero relacionadas entre sí; en TCP/IP se reducen a cuatro capas. Existen multitud de protocolos repartidos por cada capas, los cuales también están regidos por sus respectivos estándares.
La red de computadoras permite compartir recursos a distancia, aumenta la velocidad de la transmisión de datos (es más rápido acceder a un archivo por una red que a través de Internet.
Las computadoras pueden estar interconectadas mediante cable coaxial (que transporta los datos a través de dos conductores concéntricos), cable de par trenzado (los dos conductores concéntricos están entrelazados para reducir las interferencias) o fibra óptica (un hilo muy fino por el que fluyen los pulsos de luz con la información a transmitir).
De acuerdo a su alcance, es posible distinguir entre diversos tipos de redes de computadoras. La Red de Área Personal (PAN, por sus siglas en inglés) nuclea a los dispositivos situados cerca de una persona. La Red de Área Local (LAN), por su parte, incluye a las computadoras conectadas en un área pequeña, como una habitación, una oficina o un edificio. Otras redes son la Red de Área Amplia (WAN) y la Red de Área de Almacenamiento (SAN).
Existen diversos tipos de dispositivos que pueden conectarse a una red:
1. Computadoras de escritorio
2. Computadoras portátiles
3. Tablet PC
4. Smartphone
5. Impresoras
6. Servidores de archivos y de impresión
7. Consolas de juegos
8. Dispositivos domésticos
Tipos de redes
REDES DE ÁREA LOCAL (LAN)
Uno de los sucesos más críticos para la conexión en red lo constituye la aparición y la rápida difusión de la red de área local (LAN) como forma de normalizar las conexiones entre las máquinas que se utilizan como sistemas ofimáticos. Como su propio nombre indica, constituye una forma de interconectar una serie de equipos informáticos. A su nivel más elemental, una LAN no es más que un medio compartido (como un cable coaxial al que se conectan todas las computadoras y las impresoras) junto con una serie de reglas que rigen el acceso a dicho medio. La LAN más difundida, Ethernet, utiliza un mecanismo conocido como CSMA/CD. Esto significa que cada equipo conectado sólo puede utilizar el cable cuando ningún otro equipo lo está utilizando. Si hay algún conflicto, el equipo que está intentando establecer la conexión la anula y efectúa un nuevo intento más tarde. Ethernet transfiere datos a 10 Mbits/s, lo suficientemente rápido para hacer inapreciable la distancia entre los diversos equipos y dar la impresión de que están conectados directamente a su destino.
Hay tipologías muy diversas (bus, estrella, anillo) y diferentes protocolos de acceso. A pesar de esta diversidad, todas las LAN comparten la característica de poseer un alcance limitado (normalmente abarcan un edificio) y de tener una velocidad suficiente para que la red de conexión resulte invisible para los equipos que la utilizan.
1 note
·
View note
Text

Difference between CSMA CA and CSMA CD . . . . for more information https://bit.ly/42mBLPA check the above link
#csmacd#csmaca#switch#router#BluesnarfingAttack#wireless#https#http#smtp#ftp#protocol#networking#network#computerscince#computerengineering#javatpoint
0 notes
Text
Collision Domain - Snabay Networking
Collision Domain Refer to a network scenario where one device sends a frame out on a physical network segment forcing every other device on the same segment to pay attention to it. A network Collision occurs when two or more than two devices send a packet on a network segment at the same time. This is bad because if two devices on a single physical segment just happen to transmit data simultaneously, it will cause of the collision and require these devices to retransmit. Click Here: CCNA Routing and Switching Exam Fees
Broadcast Domain
Broadcast Domain is a group of devices on a particular network segment that hears all the broadcasts sent out on that particular network segment.
But even though a broadcast domain is usually a boundary delimited by physical media like switches and routers, the term can also refer to a logical division of a network segment where all host can communicate via a Data Link Layer, hardware address broadcast.
CSMA/CD
CSMA/CD stands for Carrier Sense Multiple Access/ Collision Detection. It is an Ethernet networking protocol that helps devices to share the bandwidth evenly while preventing two devices from transmitting simultaneously on the same network medium. CSMA/CD was created to overcome the collisions problems that occur while transmitting the packet from different nodes at the same time. To know more info: Communication and Network Concepts
#Learn Computer Networking#Computer Network Engineer#Computer Communication and Networks#CCNA Routing and Switching Study Guide#CCNA Routing and Switching Syllabus#CCNA Routing and Switching Exam Fees#CCNA Networking Course#Communication and Network Concepts
1 note
·
View note
Text
Basic Understanding of EtherNet Protocol
EtherNet Protocol
Hello, fellow network enthusiasts! Today I want to share with you some basics of EtherNet protocol, one of the most widely used standards for data communication. EtherNet protocol is a set of rules that define how devices on a network send and receive data packets. It also specifies how to identify devices, how to handle collisions and errors, and how to organize data into frames. EtherNet protocol is based on the idea of a shared medium, where all devices can access the same cable or wireless channel. This makes it simple and flexible, but also requires some coordination to avoid conflicts. Let’s dive into some of the key features of EtherNet protocol and see how it works in practice!
MAC address: Every device on an EtherNet network has a unique identifier called a MAC address, which is a 48-bit number usually written in hexadecimal format. For example, 00:1A:4B:9C:5D:6E is a valid MAC address. The MAC address is assigned by the manufacturer of the device and cannot be changed. It is used to identify the source and destination of each data packet on the network. - Frame: A frame is the basic unit of data transmission on an EtherNet network. It consists of a header, a payload, and a trailer. The header contains the MAC addresses of the source and destination devices, as well as other information such as the type of data and the length of the payload. The payload is the actual data being sent, such as an email message or a web page. The trailer contains a checksum that verifies the integrity of the data and detects any errors or corruption. - CSMA/CD: CSMA/CD stands for Carrier Sense Multiple Access with Collision Detection. It is a method that EtherNet devices use to avoid collisions on the shared medium. A collision occurs when two or more devices try to send data at the same time, resulting in garbled signals and lost data. To prevent this, each device listens to the medium before sending data and waits until it is idle. If a device detects a collision while sending data, it stops and waits for a random amount of time before trying again. This way, the probability of collisions decreases as the number of retries increases.
If you are interested to understand more about the EtherNet Protocol, then you can go through the PiEmbSysTech EtherNet Protocol Tutorial Blog. If you have any questions or query, that you need to get answer or you have any idea to share it with the community, you can use Piest Forum.
I hope this brief introduction has given you some insight into how EtherNet protocol works and why it is so popular and reliable. If you want to learn more about EtherNet protocol and other network topics, stay tuned for more posts from me! Thanks for reading and happy networking!
0 notes