#Computer Network Engineer
Explore tagged Tumblr posts
Text
in retrospect while Discovery is incredibly plot and drama heavy I really appreciate how well it’s been able to hold onto the technobabble mystery of it all throughout. I know that the burn is widely considered to be a low point for the show but for a low Su’Kal as a stand-alone plot was really good? And s4 brought it back to a season long ethics and science exploration which was nice. It may have made sacrifices to be more serialized but whoever decided that it would do so on a ship focused on experimental science was brilliant because so far it’s been a good balance
#disco is like half engineering station half everything else#good or bad someone is always sciencing it up#even if they’re screaming at each other while doing it#star trek discovery#a mushroom network absorbed peoples consciousnesses and at one point reincarnated someone#big drama big science#I really do love this show#it’s aged so well for me like in retrospect the cringiest bits are fun#like Michael saving the day by doing the equivalent of booting up windows 97 on a computer from 2022#is Star Trek not supposed to be dumb plots and silly solutions with weird science mysteries#I don’t think Disco is failing just because it takes a pause and stops taking itself seriously every once in a while
24 notes
·
View notes
Text
Cyborg receives space data

Pixel art for today based on videogame Metal Stoker for game console PC Engine. It is something like science fiction cybernetical action. It is even has a intro with a cyborg. Such. Count it as a second Quake. According to game screens, it is flying-shooting videogame about a future.
And this is drawing about the same theme. About theme with cyborg intro. So, I draw my own cyborg. Cyborg makes a connection with his main computer using wires. And he was impressed with data, that he received. Into his mind, it was a flow of data, a lot of running process. From a different electronic calculations machine, all the data goes by network protocol into main computer. And with wires cyborg just establish connection with his main computer. To collect data. And analyze them.
Amazing data! – says cyborg. Cyborg speaks – Fascinating!
What, it is interesting data. So interesting how planets moves. Which, it is interesting asteroid. It has interesting components. And what a data goes from a second planet near the sun. Red dwarf. Wow! It is very interesting!

Dima Link is making retro videogames, apps, a little of music, write stories, and some retro more.
WEBSITE: http://www.dimalink.tv-games.ru/home_eng.html ITCHIO: https://dimalink.itch.io/ GAMEJOLT: https://gamejolt.com/@DimaLink/games
BLOGGER: https://dimalinkeng.blogspot.com/
#8 bit#16 bit#pc engine#megadrive#snes#retro game#pixel art#pixels#pixel aesthetic#80s#cyborg#sci fi#quake 2#lots of data#cyber#future#space#digital art#planets#asteroids#red dwarf#wires#computers#machines#network protocl#programmer#ms dos
9 notes
·
View notes
Text
reminder to stay hidrated


6 notes
·
View notes
Text
I do find it so funny that I will graduate college days away from my birthday. Like my birthday is literally in between the end of the semester ("graduation") and commencement
It really will be like a joint graduation & birthday party for me lmao
#speculation nation#i dont really do birthday parties anymore. havent in a long time. mostly just go out and do smth fun around my bday. ya kno#also have cake but like not in a party way. just like. here's cake lol#but im probably only gonna graduate from college once. which means i might as well live it up and all.#invite all sorts of extended family and people who have known me. etc etc.#actually it just kinda sunk in that i am. Computer and Information Technology (Systems Analysis and Design focus) w a minor in Communication#like those are words. it's a lot of words but actually it really is pretty accurate?? like that's indeed what ive been studying.#now how much i *remember* is another question. considering how long ive taken to get thru school lol#but that's what people will see on my degree. that's my Thing. graduated in Computer Systems and Talking.#idk it's just weird to have spent so much of my life on this and like That's the culmination. it took so much work.#even beyond a normal 4 years. i switched my major *twice*. switched my minor too.#first year engineering to undecided liberal arts (as a temp major trying to switch to computer science bc i couldnt stay in FYE)#but then computer science sucked so i switched to trying to get into computer & info tech. which is different. and better.#and ive been in it long enough now that ive kinda forgotten but it did take some fuckin work to switch into it.#like i had to take certain classes first & i couldnt take them during the semesters that in-major students would take them#and i had to have my gpa up to a certain level etc etc. so many hoops to jump thru. i think it took me at least a year. or more. idr#but i made it in and thats my major. thats my thing. computers and information systems and communication.#doesnt FEEL like im an almost-graduate. but then i think about all the things ive taken and learned.#and maybe i dont remember a lot of the more specific things from these classes. but i took core lessons away from each one.#wont be able to recite the theories but i can live them. and thats the point of an education i guess.#anyways im gonna have to start job searching before too long and eughhbb. need to get my license first tho probably.#which i will... i will.... i have so many things to deal with... my life will be So Different in a year...#it will require me to put in the work now. but i can do it. and then a year from now. i'll hopefully be in a better spot.#living somewhere else. graduated from college. with a license and a car. maybe even an IT job of some kind.#kind of scared of trying to find a Big Boy Job. aka a job that requires a degree and networking and all that shit.#rather than just showing up and being like Hi i can do this job. i am not a total drain of a person. hire me please 👍#hfkahfks so many things to think about. and through it all i am still dealing with DEADLINES...!!!!#but yeah this is why my writing has largely been put on hold. idk i have a lot of things im dealing with rn.
3 notes
·
View notes
Text
About the use of network.
Note:Just as I was about to log out(at about 27.09.2024 23.32), my network connection software was disconnected and malfunctioned, and it was restored just a few minutes later.
Need more test.If necessary,I will trace and find out the reason why. If there is virus or hackers that attacked my computer,and stealed my data,I will feedback my computer datas to anti-virus companise,Let their engineers help me to find out the reason and deal with it.
Bangjia Zheng Specially Recording.
27.09.2024 evening and 28.09.2024 early morning.
#About the use of network.#Note:Just as I was about to log out(at about 27.09.2024 23.32)#my network connection software was disconnected and malfunctioned#and it was restored just a few minutes later.#Need more test.If necessary#I will trace and find out the reason why.#If there is virus or hackers that attacked my computer#and stealed my data#I will feedback my computer datas to anti-virus companise#Let their engineers help me to find out the reason and deal with it.#Bangjia Zheng Specially Recording.#27.09.2024 evening and 28.09.2024 early morning.
2 notes
·
View notes
Text
New AI noise-canceling headphone technology lets wearers pick which sounds they hear - Technology Org
New Post has been published on https://thedigitalinsider.com/new-ai-noise-canceling-headphone-technology-lets-wearers-pick-which-sounds-they-hear-technology-org/
New AI noise-canceling headphone technology lets wearers pick which sounds they hear - Technology Org
Most anyone who’s used noise-canceling headphones knows that hearing the right noise at the right time can be vital. Someone might want to erase car horns when working indoors but not when walking along busy streets. Yet people can’t choose what sounds their headphones cancel.
A team led by researchers at the University of Washington has developed deep-learning algorithms that let users pick which sounds filter through their headphones in real time. Pictured is co-author Malek Itani demonstrating the system. Image credit: University of Washington
Now, a team led by researchers at the University of Washington has developed deep-learning algorithms that let users pick which sounds filter through their headphones in real time. The team is calling the system “semantic hearing.” Headphones stream captured audio to a connected smartphone, which cancels all environmental sounds. Through voice commands or a smartphone app, headphone wearers can select which sounds they want to include from 20 classes, such as sirens, baby cries, speech, vacuum cleaners and bird chirps. Only the selected sounds will be played through the headphones.
The team presented its findings at UIST ’23 in San Francisco. In the future, the researchers plan to release a commercial version of the system.
[embedded content]
“Understanding what a bird sounds like and extracting it from all other sounds in an environment requires real-time intelligence that today’s noise canceling headphones haven’t achieved,” said senior author Shyam Gollakota, a UW professor in the Paul G. Allen School of Computer Science & Engineering. “The challenge is that the sounds headphone wearers hear need to sync with their visual senses. You can’t be hearing someone’s voice two seconds after they talk to you. This means the neural algorithms must process sounds in under a hundredth of a second.”
Because of this time crunch, the semantic hearing system must process sounds on a device such as a connected smartphone, instead of on more robust cloud servers. Additionally, because sounds from different directions arrive in people’s ears at different times, the system must preserve these delays and other spatial cues so people can still meaningfully perceive sounds in their environment.
Tested in environments such as offices, streets and parks, the system was able to extract sirens, bird chirps, alarms and other target sounds, while removing all other real-world noise. When 22 participants rated the system’s audio output for the target sound, they said that on average the quality improved compared to the original recording.
In some cases, the system struggled to distinguish between sounds that share many properties, such as vocal music and human speech. The researchers note that training the models on more real-world data might improve these outcomes.
Source: University of Washington
You can offer your link to a page which is relevant to the topic of this post.
#A.I. & Neural Networks news#ai#Algorithms#amp#app#artificial intelligence (AI)#audio#baby#challenge#classes#Cloud#computer#Computer Science#data#ears#engineering#Environment#Environmental#filter#Future#Hardware & gadgets#headphone#headphones#hearing#human#intelligence#it#learning#LED#Link
2 notes
·
View notes
Text
You glossed over the part where we add just enough impurities to silicon so it acts differently depending on how much you electrocute it, wired it up and called it a “transistor”
Then combine several transistors into a configuration that simulates logic, and called it a “gate”
Then line up anywhere from thousands to Trillions of gates to make the individual computer components that emergently do math, remember things, look things up, or organize things
Then use all manner of algorithms and optimizations so that they can multitask, be easily programmed, generate realistic environments, simulate physics, simulate a brain, communicate around the world, or do anything else we ask of them.
I studied this stuff for 5 years, I know this stuff better than the layman, and there’s STILL so much here that I can’t comprehend! Some systems’ processing power is measured in gigaflops, aka how many BILLIONS of decimal calculations they can make per second! Flash memory still seems like magic to me, it needs neither magnetism nor electricity to store a LOT of data! What’s more, a typical 32gb flash drive has roughly 256 BILLION transistors! In something the size of your thumbnail! What the fuck?
I guess in conclusion, computers might as well be magic, no matter how much you know about them. The scalability has gone so far that I don’t think humans can really process the level of complexity here anymore.
Computers are very simple you see we take the hearts of dead stars and we flatten them into crystal chips and then we etch tiny pathways using concentrated light into the dead star crystal chips and if we etch the pathways just so we can trick the crystals into doing our thinking for us hope this clears things up.
#sorry to ramble I’m just so passionate about this in particular#computers#computer science#computer engineering#electrical engineering#neural networks
112K notes
·
View notes
Text
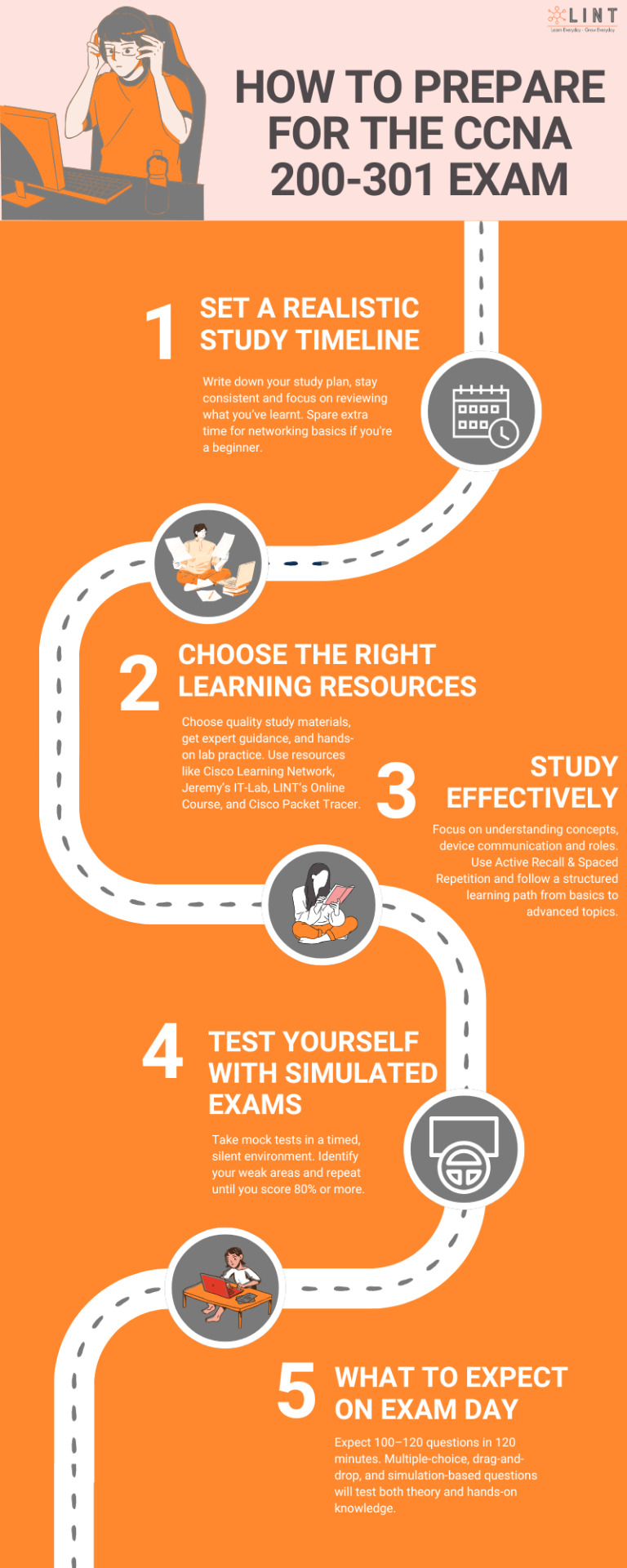
Your CCNA 200-301 Game Plan: Study Smarter, Not Harder
Studying for the CCNA 200-301? Don’t just wing it—follow a focused plan that actually gets results. This easy-to-follow infographic breaks down everything you need: how to map out your time, where to find quality learning tools, how to absorb info efficiently, and what to expect when you sit for the real exam. It’s a straight-talking guide that helps you avoid overwhelm and build solid networking skills step by step.
source: linttec.com
0 notes
Text
Computer Networking for Beginners: A Complete Starter Guide

Have you recently entered the world of technology and are currently wondering what computer networking for beginners really means? Whether you are trying to set up a Wi-Fi network at home, connect many devices within your own office, or just trying to figure how the internet works, the crux of computer networking is to make your understanding of where you begin. This guide will take you through everything you require in simple terms-no tech jargon but just straightforward explanations that will help get your connections up and running and make you feel more confident.
What is Computer Networking?
It is simply connecting computer devices to share data and services like in a plumbing system at home where the water flows from one point to the other. That is the way data networking looks like.
What Is Networking All About?
That is, you would print from the laptop without having to plug in anything, because that is how networking works-it connects computers and other devices to the internet such as sending emails, browsing the web, or playing a multiplayer game.
Types of Computer Networks
Here are the types of networks which are most commonly found:
Local Area Network (LAN) - Small areas like houses or offices.
WAN (Wide Area Network): It covers considerable distances such as cities and countries (the reverse of the WAN is obviously the internet).
MAN: Metropolitan Area Network; this includes the entire city or a large campus.
PAN (Personal Area Network): This reminds us of Bluetooth connections.
Basic Networking Devices
A few basic devices must be known to create- or understand-a network:
Router: A device that directs data across networks.
Switch: A device that connects multiple devices within the same network.
Modem: A device that connects the network to the internet.
Access Point: A device that facilitates wireless connections.
Wired vs. Wireless Networks
Wired networks, use cables (like Ethernet), offer great speed and stability.
Wireless networks, or Wi-Fi networks, provide flexibility and convenience, without the hassle of physical cables.
Conclusion
Networking sounds a bit scary, but mastering the basic concepts makes it all easy thereafter. Computer networking is what keeps us all connected in this digital world-from our homes, schools, and out to our workplaces. Start small, and you'll be building and troubleshooting networks in no time!
For more information or to join our latest computer courses, contact TCCI – Tririd Computer Coaching Institute at +91 98256 18292 or visit http://tccicomputercoaching.com/
#computer classes near me#Computer Courses in Bopal Ahmedabad#Computer Networking Course in Bopal Ahmedabad#Copmputer Engineering Coaching Classes in Ahmedabad#TCCI - Tririd Computer Coaching Institute
0 notes
Text
Keep NUST's Network Running Smoothly: Network Administrator Opportunity! - March 2025
The National University of Science and Technology (NUST) is seeking a skilled and proactive Network Administrator to join their Information and Communication Technology Services (ICTS) Department! If you’re passionate about maintaining and optimizing network infrastructure, ensuring seamless operations, and providing excellent technical support, this is an excellent opportunity. About the…

View On WordPress
#art#Bulawayo Jobs#CCNA#Comp TIA#Computer Science Jobs#Electronic Engineering Jobs#Hot Zimbabwe Jobs#ICT Jobs#Information Technology Jobs#JNCIA#Job Opportunity#Linux#MCSA#MCSE#Network Administrator Jobs#Networking Jobs#NUST Jobs#open-source#Power Shell#python#RHCE#technology#University Jobs#VMware#Zimbabwe Jobs
0 notes
Text
DESIGN AN ENHANCED INTRUSION DETECTION MODEL IN A CLOUD COMPUTING ENVIRONMENT.
DESIGN AN ENHANCED INTRUSION DETECTION MODEL IN A CLOUD COMPUTING ENVIRONMENT ABSTRACT Cloud computing is a new type of service that provides large-scale computing resources to each customer. Cloud computing systems can be easily threatened by various cyberattacks because most cloud computing systems provide services to so many people who are not proven to be trustworthy. Therefore, a cloud…
#a transformer based network intrusion detection approach for cloud security#CLOUD COMPUTING ENVIRONMENT#cloud computing journal pdf#cloud computing research#cloud computing research paper#cloud intrusion detection system#DESIGN AN ENHANCED INTRUSION DETECTION MODEL IN A CLOUD COMPUTING ENVIRONMENT.#ENHANCED INTRUSION DETECTION MODEL#google scholar#introduction to cloud engineering#intrusion detection in cloud computing#INTRUSION DETECTION MODEL#intrusion detection model in cloud computing environment example#intrusion detection model in cloud computing environment pdf#journal of cloud computing
0 notes
Text
Are you ready to become an Computer Network and System Engineer?

Are you a skilled engineer seeking a new opportunity? We are looking for a dedicated Computer Network and System Engineer (ANZSCO 263111) to design, implement, and manage secure network and system infrastructures. Your expertise will ensure operational efficiency and reliability across complex platforms.
✅ Key Responsibilities:
Analyze, design, and optimize network performance.
Configure and maintain network systems.
Troubleshoot and resolve issues promptly.
Monitor network integrity and efficiency.
Develop and document program code based on client specifications.
✅ Skill Requirements:
Bachelor’s degree or equivalent experience.
ACS (Australian Computer Society) assessment required.
Expertise in system creation, network programming, and inventory maintenance.
✅ Visa Opportunities:
Eligible candidates can apply for various visas under the General Skilled Migration Program, including:
189 Skilled Independent Visa
190 Skilled Nominated Visa
491 Skilled Regional (Provisional) Visa
✅ Why Choose CDR Australia Writer?
Our professional team specializes in guiding engineers through the migration process by providing high-quality CDR reports, career episode writing, and RPL assessments, ensuring you meet all requirements efficiently.
✅ Let’s Connect!
Ready to take the next step in your career? Contact us today or visit our website for more information on how we can assist you in achieving your migration goals!
0 notes
Text
Explore the Exciting Tech World with Emmanuel Katto in Dubai!
Meet Emmanuel Katto: Your Dubai Tech Enthusiast!
Hello! I’m Emmanuel Katto, a dedicated technology blogger residing in the vibrant city of Dubai. Join me as I uncover the latest insights and trends in the ever-evolving tech landscape, making sure you stay informed and inspired!
Exploring Technology Trends
Living in Dubai, a hub of innovation, inspires me to delve into the latest gadgets, software, and tech advancements. Whether it's emerging technologies like artificial intelligence, smart home devices, or the newest apps, I strive to keep you informed and engaged.
Making Tech Accessible
One of my primary goals is to simplify complex tech concepts. I believe that technology should be accessible to everyone, regardless of their background. Through my blog, I aim to break down intricate ideas into easily digestible content, ensuring that readers can grasp and enjoy the information.
Join Me on This Journey
As we navigate the fascinating world of technology together, I invite you to explore my blog. From in-depth reviews to insightful articles about tech's impact on our daily lives, there’s something for everyone.
Stay tuned for the latest updates and trends in technology from your go-to Dubai tech blogger, Emmanuel Katto!
Feel free to reach out if you have any topics you’d like me to cover or questions about the tech world. Let's embark on this exciting journey together!
#intelligence#feature#artificial intelligence#silicon valley#infrastructure#opensource#networking#tools#companies#engineering#technology#tech#big tech#information technology#technews#techinnovation#technoblade#tbb tech#phones#computer#laptop#electronics#emmanuel katto#emmanuel katto dubai#emmanuelkattodubai#dubai#dubailife#dubairealestate#uae#abudhabi
1 note
·
View note
Text

India's IT sector is thriving, driven by factors like Tier II city growth, focus on automation, and cloud adoption. Data security and fostering a skilled workforce are crucial for future success. AI, ML, and continuous innovation will propel India to be a global IT leader. Emphasis on efficiency, upskilling, and responsible use of technology will shape the sector's future, contributing significantly to India's economic growth.
Case-Study : Information Technology Scope and Adoption in India’s IT Sector: A Project Report https://maction.com/nproject/case-study-information-technology-scope-and-adoption-in-indias-it-sector-a-project-report/
#informationtechnology#technology#it#cybersecurity#tech#computerscience#programming#business#coding#innovation#software#python#information#computer#informationsecurity#security#technologynews#java#networking#hacking#programmer#linux#technologyrocks#coder#technologythesedays#cloudcomputing#education#engineering#itservices#newtechnology
0 notes
Text
Shaktiman Mall, Principal Product Manager, Aviatrix – Interview Series
New Post has been published on https://thedigitalinsider.com/shaktiman-mall-principal-product-manager-aviatrix-interview-series/
Shaktiman Mall, Principal Product Manager, Aviatrix – Interview Series
Shaktiman Mall is Principal Product Manager at Aviatrix. With more than a decade of experience designing and implementing network solutions, Mall prides himself on ingenuity, creativity, adaptability and precision. Prior to joining Aviatrix, Mall served as Senior Technical Marketing Manager at Palo Alto Networks and Principal Infrastructure Engineer at MphasiS.
Aviatrix is a company focused on simplifying cloud networking to help businesses remain agile. Their cloud networking platform is used by over 500 enterprises and is designed to provide visibility, security, and control for adapting to changing needs. The Aviatrix Certified Engineer (ACE) Program offers certification in multicloud networking and security, aimed at supporting professionals in staying current with digital transformation trends.
What initially attracted you to computer engineering and cybersecurity?
As a student, I was initially more interested in studying medicine and wanted to pursue a degree in biotechnology. However, I decided to switch to computer science after having conversations with my classmates about technological advancements over the preceding decade and emerging technologies on the horizon.
Could you describe your current role at Aviatrix and share with us what your responsibilities are and what an average day looks like?
I’ve been with Aviatrix for two years and currently serve as a principal product manager in the product organization. As a product manager, my responsibilities include building product vision, conducting market research, and consulting with the sales, marketing and support teams. These inputs combined with direct customer engagement help me define and prioritize features and bug fixes.
I also ensure that our products align with customers’ requirements. New product features should be easy to use and not overly or unnecessarily complex. In my role, I also need to be mindful of the timing for these features – can we put engineering resources toward it today, or can it wait six months? To that end, should the rollout be staggered or phased into different versions? Most importantly, what is the projected return on investment?
An average day includes meetings with engineering, project planning, customer calls, and meetings with sales and support. Those discussions allow me to get an update on upcoming features and use cases while understanding current issues and feedback to troubleshoot before a release.
What are the primary challenges IT teams face when integrating AI tools into their existing cloud infrastructure?
Based on real-world experience of integrating AI into our IT technology, I believe there are four challenges companies will encounter:
Harnessing data & integration: Data enriches AI, but when data is across different places and resources in an organization, it can be difficult to harness it properly.
Scaling: AI operations can be CPU intensive, making scaling challenging.
Training and raising awareness: A company could have the most powerful AI solution, but if employees don’t know how to use it or don’t understand it, then it will be underutilized.
Cost: For IT especially, a quality AI integration will not be cheap, and businesses must budget accordingly.
Security: Make sure that the cloud infrastructure meets security standards and regulatory requirements relevant to AI applications
How can businesses ensure their cloud infrastructure is robust enough to support the heavy computing needs of AI applications?
There are multiple factors to running AI applications. For starters, it’s critical to find the right type and instance for scale and performance.
Also, there needs to be adequate data storage, as these applications will draw from static data available within the company and build their own database of information. Data storage can be costly, forcing businesses to assess different types of storage optimization.
Another consideration is network bandwidth. If every employee in the company uses the same AI application at once, the network bandwidth needs to scale – otherwise, the application will be so slow as to be unusable. Likewise, companies need to decide if they will use a centralized AI model where computing happens in a single place or a distributed AI model where computing happens closer to the data sources.
With the increasing adoption of AI, how can IT teams protect their systems from the heightened risk of cyberattacks?
There are two main aspects to security every IT team must consider. First, how do we protect against external risks? Second, how do we ensure data, whether it is the personally identifiable information (PII) of customers or proprietary information, remains within the company and is not exposed? Businesses must determine who can and cannot access certain data. As a product manager, I need sensitive information others are not authorized to access or code.
At Aviatrix, we help our customers protect against attacks, allowing them to continue adopting technologies like AI that are essential for being competitive today. Recall network bandwidth optimization: because Aviatrix acts as the data plane for our customers, we can manage the data going through their network, providing visibility and enhancing security enforcement.
Likewise, our distributed cloud firewall (DCF) solves the challenges of a distributed AI model where data gets queried in multiple places, spanning geographical boundaries with different laws and compliances. Specifically, a DCF supports a single set of security compliance enforced across the globe, ensuring the same set of security and networking architecture is supported. Our Aviatrix Networks Architecture also allows us to identify choke points, where we can dynamically update the routing table or help customers create new connections to optimize AI requirements.
How can businesses optimize their cloud spending while implementing AI technologies, and what role does the Aviatrix platform play in this?
One of the main practices that will help businesses optimize their cloud spending when implementing AI is minimizing egress spend.
Cloud network data processing and egress fees are a material component of cloud costs. They are both difficult to understand and inflexible. These cost structures not only hinder scalability and data portability for enterprises, but also provide decreasing returns to scale as cloud data volume increases which can impact organizations’ bandwidth.
Aviatrix designed our egress solution to give the customer visibility and control. Not only do we perform enforcement on gateways through DCF, but we also do native orchestration, enforcing control at the network interface card level for significant cost savings. In fact, after crunching the numbers on egress spend, we had customers report savings between 20% and 40%.
We’re also building auto-rightsizing capabilities to automatically detect high resource utilization and automatically schedule upgrades as needed.
Lastly, we ensure optimal network performance with advanced networking capabilities like intelligent routing, traffic engineering and secure connectivity across multi-cloud environments.
How does Aviatrix CoPilot enhance operational efficiency and provide better visibility and control over AI deployments in multicloud environments?
Aviatrix CoPilot’s topology view provides real-time network latency and throughput, allowing customers to see the number of VPC/VNets. It also displays different cloud resources, accelerating problem identification. For example, if the customer sees a latency issue in a network, they will know which assets are getting affected. Also, Aviatrix CoPilot helps customers identify bottlenecks, configuration issues, and improper connections or network mapping. Furthermore, if a customer needs to scale up one of its gateways into the node to accommodate more AI capabilities, Aviatrix CoPilot can automatically detect, scale, and upgrade as necessary.
Can you explain how dynamic topology mapping and embedded security visibility in Aviatrix CoPilot assist in real-time troubleshooting of AI applications?
Aviatrix CoPilot’s dynamic topology mapping also facilitates robust troubleshooting capabilities. If a customer must troubleshoot an issue between different clouds (requiring them to understand where traffic was getting blocked), CoPilot can find it, streamlining resolution. Not only does Aviatrix CoPilot visualize network aspects, but it also provides security visualization components in the form of our own threat IQ, which performs security and vulnerability protection. We help our customers map the networking and security into one comprehensive visualization solution.
We also help with capacity planning for both cost with costIQ, and performance with auto right sizing and network optimization.
How does Aviatrix ensure data security and compliance across various cloud providers when integrating AI tools?
AWS and its AI engine, Amazon Bedrock, have different security requirements from Azure and Microsoft Copilot. Uniquely, Aviatrix can help our customers create an orchestration layer where we can automatically align security and network requirements to the CSP in question. For example, Aviatrix can automatically compartmentalize data for all CSPs irrespective of APIs or underlying architecture.
It is important to note that all of these AI engines are inside a public subnet, which means they have access to the internet, creating additional vulnerabilities because they consume proprietary data. Thankfully, our DCF can sit on a public and private subnet, ensuring security. Beyond public subnets, it can also sit across different regions and CSPs, between data centers and CSPs or VPC/VNets and even between a random site and the cloud. We establish end-to-end encryption across VPC/VNets and regions for secure transfer of data. We also have extensive auditing and logging for tasks performed on the system, as well as integrated network and policy with threat detection and deep packet inspection.
What future trends do you foresee in the intersection of AI and cloud computing, and how is Aviatrix preparing to address these trends?
I see the interaction of AI and cloud computing birthing incredible automation capabilities in key areas such as networking, security, visibility, and troubleshooting for significant cost savings and efficiency.
It could also analyze the different types of data entering the network and recommend the most suitable policies or security compliances. Similarly, if a customer needed to enforce HIPAA, this solution could scan through the customer’s networks and then recommend a corresponding strategy.
Troubleshooting is a major investment because it requires a call center to assist customers. However, most of these issues don’t necessitate human intervention.
Generative AI (GenAI) will also be a game changer for cloud computing. Today, a topology is a day-zero decision – once an architecture or networking topology gets built, it is difficult to make changes. One potential use case I believe is on the horizon is a solution that could recommend an optimal topology based on certain requirements. Another problem that GenAI could solve is related to security policies, which quickly become outdated after a few years. AGenAI solution could help users routinely create new security stacks per new laws and regulations.
Aviatrix can implement the same security architecture for a datacenter with our edge solution, given that more AI will sit close to the data sources. We can help connect branches and sites to the cloud and edge with AI computes running.
We also help in B2B integration with different customers or entities in the same company with separate operating models.
AI is driving new and exciting computing trends that will impact how infrastructure is built. At Aviatrix, we’re looking forward to seizing the moment with our secure and seamless cloud networking solution.
Thank you for the great interview, readers who wish to learn more should visit Aviatrix.
#agile#ai#AI and cloud#AI and cloud computing#AI engines#AI integration#ai model#ai tools#Amazon#amp#APIs#applications#architecture#assets#automation#Aviatrix#awareness#AWS#azure#B2B#biotechnology#bug#Building#call center#certification#Cloud#cloud computing#cloud data#cloud infrastructure#cloud network
1 note
·
View note
Text
RN42 Bluetooth Module: A Comprehensive Guide
The RN42 Bluetooth module was developed by Microchip Technology. It’s designed to provide Bluetooth connectivity to devices and is commonly used in various applications, including wireless communication between devices.
Features Of RN42 Bluetooth Module
The RN42 Bluetooth module comes with several key features that make it suitable for various wireless communication applications. Here are the key features of the RN42 module:
Bluetooth Version:
The RN42 module is based on Bluetooth version 2.1 + EDR (Enhanced Data Rate).
Profiles:
Supports a range of Bluetooth profiles including Serial Port Profile (SPP), Human Interface Device (HID), Audio Gateway (AG), and others. The availability of profiles makes it versatile for different types of applications.
Frequency Range:
Operates in the 2.4 GHz ISM (Industrial, Scientific, and Medical) band, the standard frequency range for Bluetooth communication.
Data Rates:
Offers data rates of up to 3 Mbps, providing a balance between speed and power consumption.
Power Supply Voltage:
Operates with a power supply voltage in the range of 3.3V to 6V, making it compatible with a variety of power sources.
Low Power Consumption:
Designed for low power consumption, making it suitable for battery-powered applications and energy-efficient designs.
Antenna Options:
Provides options for both internal and external antennas, offering flexibility in design based on the specific requirements of the application.
Interface:
Utilizes a UART (Universal Asynchronous Receiver-Transmitter) interface for serial communication, facilitating easy integration with microcontrollers and other embedded systems.
Security Features:
Implements authentication and encryption mechanisms to ensure secure wireless communication.
Read More: RN42 Bluetooth Module
#rn42-bluetooth-module#bluetooth-module#rn42#bluetooth-low-energy#ble#microcontroller#arduino#raspberry-pi#embedded-systems#IoT#internet-of-things#wireless-communication#data-transmission#sensor-networking#wearable-technology#mobile-devices#smart-homes#industrial-automation#healthcare#automotive#aerospace#telecommunications#networking#security#software-development#hardware-engineering#electronics#electrical-engineering#computer-science#engineering
0 notes