#cyber security checklist
Text
Discover why cybersecurity is crucial for the business to remain technologically sound and still reach its goals. Read more on the LAN Infotech blog.
#cybersecurity#cyber security risk assessment#cybersecurity consulting#cyber security audit checklist#cyber security checklist#cybersecurity services#cybersecurity service provider
0 notes
Text
This day in history

I'm coming to DEFCON! TOMORROW (Aug 9), I'm emceeing the EFF POKER TOURNAMENT (noon at the Horseshoe Poker Room), and appearing on the BRICKED AND ABANDONED panel (5PM, LVCC - L1 - HW1–11–01). On SATURDAY (Aug 10), I'm giving a keynote called "DISENSHITTIFY OR DIE! How hackers can seize the means of computation and build a new, good internet that is hardened against our asshole bosses' insatiable horniness for enshittification" (noon, LVCC - L1 - HW1–11–01).

#15yrsago Exhaustive index of fearmongering Daily Mail stories about cancer and its causes https://web.archive.org/web/20090815070522/http://kill-or-cure.heroku.com/
#5yrsago Hospital checklists work really well — except when they’re not used https://www.nature.com/articles/523516a
#5yrsago Science fiction and the law: beyond mere courtroom drama https://reactormag.com/will-there-be-justice-science-fiction-and-the-law/
#5yrsago Grifty “Students For Trump” founder pleads guilty to wire fraud for pretending to be a lawyer https://www.nydailynews.com/2019/08/06/students-for-trump-founder-pleads-guilty-to-posing-as-lawyer-in-46k-scam/
#5yrsago Security researcher cracks high-security lock used for ATMs, Air Force One, military bases https://www.reuters.com/article/us-locks-cyber-exclusive/exclusive-high-security-locks-for-government-and-banks-hacked-by-researcher-idUSKCN1UW26Z/
#5yrsago Taiwanese sympathizers are shipping helmets and gas-masks to Hong Kong https://asiatimes.com/2019/08/helmets-goggles-sent-from-taiwan-to-hk-protesters/
#5yrsago Tiktok is valued at $75b, is spending $3m/day on US advertising, and in China, it has been turned into a state propaganda vehicle https://www.theverge.com/interface/2019/8/7/20757855/tiktok-growth-monetization-influencers-regulation
#5yrsago Medical examiner quits after declaring that bloody, stabbed corpse had died of “natural causes” https://www.fox5atlanta.com/news/gwinnett-county-me-investigator-resigns-after-misinterpreted-autopsy
#5yrsago CHESSES: chess variants for nonexperts, nonplayers, and the very playful https://pippinbarr.com/chesses/
4 notes
·
View notes
Text
Top 10 Key Points to Ensure Security for Your Laravel Application

In Laravel web application development, security is one of the essential paramount. As the digital landscape continues to expand, the Importance of security in web applications, particularly those built on the Laravel framework, has reached an all-time high. In this era of interconnectedness, where information flows seamlessly across the virtual realm, the potential threats and vulnerabilities have also escalated.
The landscape of online threats has grown more sophisticated, encompassing various malicious activities ranging from data breaches to identity theft. This evolving threat landscape calls for a steadfast commitment to proactive security measures. Waiting for a security breach before addressing vulnerabilities is a risk no modern developer can afford to take.
The significance of bolstering security in Laravel web application development. While Laravel provides a robust and versatile platform for creating dynamic web applications, it's essential to recognize that even the most advanced framework is not immune to potential security breaches. As your Laravel application evolves, it becomes a showcase of your technological prowess and a potential target for cyber threats.
The Importance of proactive security measures should be highlighted further. Developers and businesses must adopt a security-first mindset when crafting their digital creations, which means staying informed about the latest security trends, continuously updating and patching the application, and adhering to best practices for safeguarding sensitive user data.
We'll delve into 10 critical checkpoints that can significantly enhance the security of your Laravel web application. These checkpoints encompass a comprehensive approach to securing various aspects of your application, from authentication and authorization to protecting against common web vulnerabilities. By diligently implementing these checkpoints, you'll be taking a substantial stride towards fortifying your Laravel web application against the ever-persistent threats lurking in the digital domain.
10 Key Checkpoints to Focus On
Here's your comprehensive Laravel Security Checklist to ensure a robust and safeguarded web application.
1. Secure Authentication and Authorization

In the intricate world of Laravel web application development, security is an indispensable pillar for creating a trustworthy and resilient digital presence. One of the cornerstone elements in this security fortress is the implementation of secure authentication and authorization mechanisms. Let's delve into how these critical aspects are pivotal in fortifying your Laravel application against potential threats.
Secure Authentication: Building the First Line of Defense
Authentication is verifying the identity of users attempting to access your application. It forms the cornerstone of security by ensuring that only authorized individuals can interact with sensitive data and functionalities. In the realm of Laravel, this process is made significantly more manageable through the framework's built-in authentication features.
Implementing secure authentication involves
Strong Password Policies: Enforce complex passwords, combining uppercase and lowercase letters, numbers, and special characters. Laravel provides password validation rules to help you accomplish this.
Two-Factor Authentication (2FA): Enhance security by requiring users to provide an additional authentication factor beyond their password. Laravel offers seamless integration with 2FA for an added layer of protection.
Account Lockouts: Implement mechanisms that lock accounts after a specified number of unsuccessful login attempts, preventing brute-force attacks by temporarily halting further login attempts.
Authorization: Ensuring Granular Access Control
Authorization, however, deals with controlling what authenticated users can do within the application. It's about granting permissions and access rights based on roles and responsibilities, ensuring that sensitive actions are restricted to those who need them.
Key steps in implementing effective authorization include
Role-Based Access Control (RBAC): Define roles such as "admin," "user," or "manager," and associate them with specific permissions. Laravel's RBAC system lets you assign roles and permissions effortlessly.
Middleware Authorization: Leverage Laravel's middleware to restrict access to routes or controllers based on user roles or custom conditions. This is a powerful way to ensure that only authorized users can perform specific actions.
Resource Controllers: Utilize resource controllers to create a consistent and structured approach to handling CRUD operations. These controllers can be easily configured to enforce authorization rules for specific actions.
Dynamic Authorization Policies: Laravel's policy system lets you define authorization logic in a structured manner. It's beneficial for complex access control requirements and allows for fine-grained control over what users can do.
In a world where digital threats are evolving rapidly, securing your Laravel application's authentication and authorization processes is paramount. By implementing robust authentication mechanisms and enforcing precise authorization rules, you're safeguarding sensitive data and building a foundation of trust with your users. Remember, security isn't just a one-time task; it's an ongoing commitment that requires vigilance and adaptability in the face of ever-changing cyber threats.
2. Keep Laravel and Dependencies Updated
In the dynamic realm of Laravel web application development, staying ahead in the security game is an ongoing endeavor. One of the fundamental practices that forms the bedrock of a secure digital presence is the consistent updating of your Laravel framework and its associated dependencies. Let's explore why this practice is essential and how it contributes to the overall security of your application.
The Power of Regular Updates
Technology, much like the world around us, is in a constant state of evolution. This evolution is driven not only by innovation but also by identifying and rectifying vulnerabilities and weaknesses. In the context of Laravel development, regular updates to both the core framework and its dependencies play a pivotal role in ensuring the security and stability of your application.
Why Updates Matter
Security Patches: Vulnerabilities can emerge at any software lifecycle stage. Developers and the open-source community work diligently to identify and address these vulnerabilities. Regular updates ensure that your Laravel application is fortified with the latest security patches, minimizing the risk of exploitation.
Compatibility: As Laravel evolves, updates often improve compatibility with newer PHP versions, web servers, and databases. Staying updated ensures your application remains in sync with the broader web development ecosystem.
Performance and Features: Updates not only fix issues; they also introduce performance enhancements and new features. Embracing these updates can lead to a more efficient application that delivers a better user experience.
Dependencies: Handle with Care
Laravel development heavily relies on various external packages and libraries. While these dependencies contribute to the efficiency and functionality of your application, they can also introduce vulnerabilities if not managed appropriately.
Best Practices for Dependency Management:
Regular Audits: Periodically review the dependencies your Laravel development company utilizes. Check for any vulnerabilities reported in these packages and prioritize updating them accordingly.
Automated Tools: Leverage automated tools that can scan your project's dependencies for known security issues. This can help you identify potential risks and take corrective action swiftly.
Version Pinning: Specify the exact versions of dependencies your application uses. This prevents unexpected updates that might introduce breaking changes or vulnerabilities.
In the rapidly evolving web application security landscape, treating updates as a proactive security measure is paramount. By ensuring your Laravel framework and dependencies are up to date, you're demonstrating a commitment to maintaining a robust digital fortress for your application. This safeguards sensitive user data and positions your Laravel development company as a conscientious custodian of digital security. Remember, in technology, staying current isn't just an option—it's necessary for a secure and successful future.
3. Validate User Input
The ever-evolving landscape of Laravel development, the adage "Garbage In, Garbage Out" holds immense relevance. One of the pivotal checkpoints in ensuring the robustness of your Laravel application's security is the validation of user input. Let's dive into why validating user input is crucial and how it is a formidable shield against potential vulnerabilities.
The Essence of User Input Validation
User input is the gateway through which your Laravel application interacts with its users. Whether it's a login form, a search bar, or a comment section, user input is integral to the functionality of your application. However, it can also become an entry point for malicious activities if left unchecked.
Why Validate User Input:
Mitigating Injection Attacks: Attackers can exploit unvalidated user input to inject malicious code into your application. This includes infamous threats like SQL injection and cross-site scripting (XSS). Proper validation drastically reduces the risk of such attacks.
Data Integrity: Validating user input ensures that the data flowing into your application is consistent and matches the expected format. This helps maintain data integrity and prevents errors caused by unexpected information.
Enhancing User Experience: You can guide users to input data in the correct format by providing real-time validation feedback. This not only prevents submission errors but also enhances the overall user experience.
Implementing Effective Input Validation in Laravel
Utilize Laravel's Validation Rules: Laravel offers a robust validation system that includes a wide array of predefined rules. These rules cover everything from required fields and email formats to custom validation logic.
Sanitize and Filter Input: Consider sanitizing and filtering user input alongside validation. Sanitization removes potentially harmful characters, while filtering ensures that information adheres to specific formats.
Client-Side Validation: While server-side validation is paramount, supplement it with client-side validation using JavaScript. This provides instant feedback to users and reduces unnecessary server requests.
Best Practices for User Input Validation
Never Trust User Input: Treat all incoming user input as potentially malicious until proven otherwise. Validate and sanitize input even if it seems harmless.
Whitelist Validation: Define an allowlist of allowed characters and formats for each input field. Reject input that doesn't conform to these predefined patterns.
Regular Updates: Like any other security practice, stay updated with Laravel's latest validation features and best practices. This ensures you're using the most effective tools available.
In the intricate realm of Laravel development, user input validation isn't just a technical practice; it's a shield that guards your application against many threats. By diligently validating user input, you're bolstering your application's security and reinforcing trust with your users. In the dynamic world of web development, where innovation meets vulnerability, validation is your steadfast ally in pursuing a secure and seamless user experience.
4. Protect Against SQL Injection

Shielding your digital fortress through meticulous Laravel development services involves a critical step: Protect against SQL injection. This threat arises when user inputs lack proper sanitation, potentially enabling malicious actors to manipulate SQL queries and gain unauthorized database access.
SQL injection attacks can lead to data exposure, alteration, or deletion. Laravel's defences are robust. Its query binding technique parameterizes user inputs, preventing malicious SQL execution. The Eloquent ORM further enhances security by abstracting SQL interactions and automatically escaping values.
Adhering to best practices is paramount. Prioritize parameterized queries over direct concatenation, sanitize inputs, and conduct regular code audits to ensure secure methods. By fortifying your Laravel application against SQL injection, you're erecting a robust barrier against a damaging vulnerability while providing your Laravel development services maintain the utmost integrity and user trust.
5. Cross-Site Scripting (XSS) Prevention
In securing your digital haven with proficient Laravel development practices, countering Cross-Site Scripting (XSS) emerges as a pivotal measure. XSS occurs when malicious code infiltrates a website through unfiltered user inputs, potentially compromising user data and integrity.
The gravity of XSS lies in its ability to expose sensitive information or perform malicious actions under the user's identity. Laravel offers potent tools to thwart such threats:
Blade Templating: Laravel's Blade templating engine automatically escapes variables, preventing unintended script execution.
XSS Middleware: Laravel provides built-in middleware for encoding user inputs, adding an extra layer of protection.
Content Security Policy (CSP): Implementing CSP headers in your Laravel application restricts the sources from which content can be loaded, reducing the risk of XSS attacks.
Adhering to these precautions is essential. Validate and sanitize inputs, embrace Laravel's security features, and implement a robust CSP. By guarding against XSS vulnerabilities, you ensure your Laravel development maintains a resilient and trustworthy digital presence.
6. Implement HTTPS and SSL
In web application development, particularly in Laravel, bolstering security is paramount. A crucial step in this pursuit is the implementation of HTTPS and SSL protocols. These measures are essential to safeguard sensitive data transmitted between users and your application.
HTTPS (Hypertext Transfer Protocol Secure) encrypts the data between users' browsers and your application's server, thwarting potential eavesdropping and tampering. SSL (Secure Sockets Layer) certificates are the foundation of this encryption, ensuring that communication remains confidential.
Advantages of HTTPS and SSL:
Data Encryption: HTTPS encrypts data during transit, preventing unauthorized access to sensitive information.
Trust and SEO: SSL certificates enhance user trust, as indicated by the padlock symbol in browsers. Search engines also favor HTTPS websites, improving SEO rankings.
Authentication: SSL certificates verify your application's authenticity, shielding users from potential phishing sites.
Implementing HTTPS and SSL involves obtaining a valid SSL certificate and configuring your Laravel application for secure connections. By adopting these measures, you're securing your web application development, fostering trust among users, and ensuring compliance with modern security standards.
7. Secure Session Management
In web application development, security isn't just a feature—it's a necessity. A crucial aspect of building a robust and trustworthy application is ensuring secure session management. Sessions are pivotal in maintaining user interactions and data, making their protection paramount.
Laravel offers robust mechanisms to fortify session management:
Session Encryption: Laravel automatically encrypts session data, preventing unauthorized access and ensuring confidentiality.
CSRF Protection: Cross-Site Request Forgery (CSRF) attacks can compromise sessions. Laravel's built-in CSRF protection safeguards against such threats.
Expire and Regenerate: Set session expiration times and periodically regenerate session IDs to minimize the window of vulnerability.
By implementing secure session management practices in your web application development, you create a shield against unauthorized access and data breaches. This preserves user trust and solidifies your commitment to crafting applications that prioritize security and integrity.
8. Protect Against Cross-Site Request Forgery (CSRF)
Safeguarding web applications is a top priority in Laravel development. To fortify your digital haven, countering Cross-Site Request Forgery (CSRF) threats is crucial. CSRF attacks manipulate authenticated users into executing malicious actions unknowingly. Laravel provides a robust defense:
CSRF Tokens: Laravel automatically generates unique tokens for each user session, validating the authenticity of requests.
Middleware Protection: Laravel's built-in CSRF middleware verifies tokens, preventing unauthorized requests from being executed.
By integrating these measures, you fortify your Laravel application against CSRF vulnerabilities. This secures user interactions and demonstrates your commitment to proactive security practices in modern web development.
9. Harden Configuration and File Permissions
In the landscape of Laravel security, enhancing configuration settings and file permissions is a critical stride. Securing sensitive files, such as configuration files, shields against unauthorized access and potential breaches. Laravel's framework offers key tactics:
Restricted Access: Limit access to sensitive configuration files by setting appropriate permissions. This prevents unauthorized users from tampering with vital settings.
Environment Configuration: Store sensitive data in environment files and never expose them in version control. Laravel's .env file shields sensitive variables from prying eyes.
By meticulously configuring permissions and safeguarding critical files, you erect a solid barrier against potential threats. This reflects an unwavering commitment to fortifying your Laravel application and upholding security standards in modern web development.
10. Use Content Security Policy (CSP)
Bolstering security in Laravel involves advanced tactics, including a Content Security Policy (CSP). CSP guards against cross-site scripting (XSS) and data injection attacks. It achieves this by specifying approved content sources, mitigating the risk of malicious script execution. Laravel's integration of CSP fortifies your defense:
Malicious Content Mitigation: CSP curtails the potential impact of XSS attacks by regulating the domains from which content can be loaded.
Policy Customization: Laravel empowers you to tailor CSP rules to suit your application's specific requirements, balancing security and functionality.
By embracing CSP, you establish a robust security framework that exemplifies Laravel's commitment to secure, modern web development practices.
Top Laravel Security Packages for Developers
In the realm of Laravel development, ensuring robust security is paramount. Several key packages aid developers in fortifying their applications. Here are three notable options:
Laravel-ACL: Access Control Lists (ACL) are fundamental to controlling user permissions. This package simplifies ACL implementation, offering granular control over user access to different parts of your application.
Laravel Security: As the name suggests, this package enhances overall security. It provides features like XSS protection, safe redirects, and content filtering, contributing to a fortified application.
Laravel Security Component: This package takes security up a notch by integrating robust security components. It includes encryption, hashing, validation, and more tools, streamlining your security efforts.
For a Laravel development agency, these packages are invaluable assets. By incorporating them into your development process, you expedite security implementation and establish a strong foundation for crafting secure, reliable applications that clients can trust.
Conclusion
In the intricate realm of Laravel security, these checkpoints act as sentinels, fortifying your application's defenses. Secure authentication, vigilant updates, meticulous validation, and shielded configurations create a robust bastion. Protection against threats like SQL injection, XSS, and CSRF forms an unbreachable wall. Implementation of HTTPS, secure session handling, and CSP reinforce your fortifications. Familiarity with essential security packages like Laravel-ACL, Laravel Security, and Security Component adds the final layer. As a Laravel developer, embracing these measures ensures your applications are secured, and your expertise is unwavering in the face of evolving threats.
Source: Top 10 Key Points to Ensure Security for Your Laravel Application
2 notes
·
View notes
Text
A House of Brick
You want to know your cars are safe to drive, your plane's jet propulsion isn't hackable, and that when you didn't get those concert tickets, it wasn't because someone else used robots to steal them first. What if I told you building something safe is relatively new to the cyber landscape? That before something called DevSecOps, people would build whole websites, whole apps, then have someone try to attack it, then run repairs?
It's the equivalent of having one of the fairy tale piggies build their house out of straw first, then have the wolf come check it.
DevSecOps is the process of making sure you're building something strong before, during, and after the building process. It's having someone there to make sure you're using bricks, not straw, not wood.

Development, security and operations. It's the marriage between building something, making sure it works, and making sure its safe.
This is all based on the need for software that's of good quality, secure, and stable. DevSecOps makes software faster to create, easier to fix or update more often, and generally safer. Most importantly it brings security to the table during the build process rather than as an afterthought. This makes risk management much easier as well, looking forward to incidents rather than taking action after one.
What does a company need in order to perform DevSecOps?
1 - a decided strategy
2 - software application lifecycle concepts explained through various means which merge all three components of development, security, and operations
3 - reference guides with in-depth and technical information
Let's go over each:
1 - Strategy
This could be just a summary of goals from an executive board, it could be a set of principles the company wants to uphold, or even a set of requirements from a group in charge, like the government or shareholders. There needs to be some point on the compass to guide everything else.
Strategy in DevSecOps is about having several versions of action from higher management. This includes something called cATO, or Continuous Authorization to Operate. This is basically saying we do checks and real-time metrics through the whole software supply chain instead of taking a snapshot every 3 years. (Read the DOD DevSecOps Strategy Guide Here)

2 - Fundamentals, Guidebooks, and Playbooks
Basic lifecycles, topic-specific guidebooks or playbooks, white papers, industry best practices, using jargon and ideas that everyone knows, mapping tools and tasks, and keeping up with SMART metrics (Specific, Measurable, Achievable, Relevant, and Timely); You don't have to reinvent the wheel but you should be looking at the blueprints other people agreed work for wheel making when you're building one. (Read the DOD DevSecOps Fundamentals Here)
Guidebooks have topic-specific in-depth specifications and Playbooks are usually a single-page "plays" (think sports "plays") which have tips, points, checklists, and actionable tasks to take. (Read the DOD DevSecOps Playbook Here) (Read the DOD DevSecOps Fundamentals Guidebook Here)
You might hear the phrase CI/CD Pipeline, standing for Continuous Integration and Continuous Deployment Pipeline. This just means that we're checking things while we build, test, and deploy code. Don't get tripped up on the word "pipeline" - it's literally just referring to the fact that work is going sideways between people like water in a pipe.
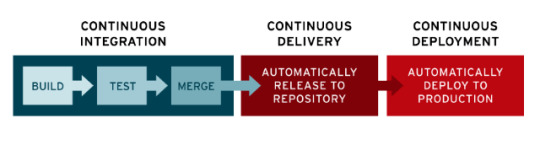

3 - Getting Technical
A DevSecOps reference design document takes everything that came before it and gets even more technical, merging similar names for things and getting rid of redundancy or inconsistency. This way we're all on the same page of what exactly is happening or should be done.
Okay, so what does DevSecOps look like?
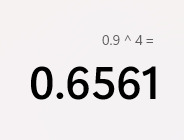
It looks like a bunch of meetings, collaborating between teams, feedback loops to check everything, and agile workflow (meaning everything goes round and round). DevSecOps changes the mindsets of a lot of teams and environments. A company has to pick a reference design platform with a cATO that works for their needs. When they do risk management, decimal percentages are multiplied in order to prove a company's level.
(for example, all four sections being 90% secure equates to .9 * .9 * .9 * .9 = .6561, so your company is actually only 65% secure, NOT 90%)
DevSecOps looks like a "software factory" sitting on a specific software supply chain. This factory has automation, process flows, control gates, pipeline controls, and flows like a wheel constantly checking for security and stabilization during code development.
This looks neat. Where to start?
Let's break down Strategy, where it all begins. Start with DevSecOps Guiding Principles:
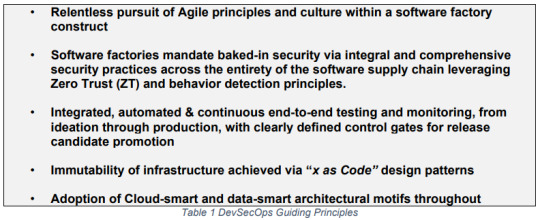
If you haven't heard of the Agile Manifesto, you can read them here. Their principles basically state that people, code that works, and responding to change are more important than tools, documents, contracts, and plans.
The software factories run development, operations, and security simultaneously. You'll hear the term "baked-in security" eliciting the imagery that your software is a three-tier wedding cake, but again this just means we're all working together and communicating mid-development, not tossing the software back and forth like a volley ball.

Remember cATO is continuous testing and risk assessing people, platforms, processes using real-time analytics. This is concentrating on protecting assets, not network segments, a technique called Zero Trust Architecture (see NIST SP 800-27 for more detail).
"X as Code" or "Everything as Code" is good because things can go wrong when a human is following a guide step-by-step to set whole systems up. It also makes sure whoever's running the code knows exactly what's going to happen when they run it. There's a difference between reading and running a function versus just hitting a button and expecting results. It also sets up a "standard deployment model" - basically giving you a safe template to use for other software. This can easily be scanned, updated, scraped, and analyzed. Code is king because "code can be version controlled, tested, peer reviewed, and its execution (logs) tracked" (Unclassified, 2020).

You want everything cloud-smart and data-smart. A cloud is just someone else's computer, but it comes with perks like paying someone else to deal with storage space or your data's security, depending on the cloud service provider, CSP, you're using and what type of package you bought with them. Your architecture needs to be just as up-to-date and savvy with modern designs, though. Architecture is just as complex through cloud as it always has been.
Management structure is both bottom-up and top-down. Direction should be taken based on a company's mission statement (see my prior blog post for more on this). Automate everything you can. Be adaptable, transparent, and accountable. Use DODI 8510.01 for risk management framework and use CJCM 6510.01B for incident handling (but be aware of challenges like fluid system boundaries in microservice architecture, nontraditional system boundaries in distributed services and constant system evolutions).
All in all, here's what it looks like, including continuous monitoring:

For more information go to https://dodcio.defense.gov/Library/ and search for devsecops for an up-to-date declassified modern software practices.
Sources:
Rose, S., Borchert, O., Mitchell, S., & Connelly, S. (2020, August 11). Zero Trust Architecture. Csrc.nist.gov. https://csrc.nist.gov/publications/detail/sp/800-207/final
This document automatically expires 1-year from publication date unless revised. DevSecOps Playbook CLEARED For Open Publication Department of Defense OFFICE OF PREPUBLICATION AND SECURITY REVIEW. (2021). https://dodcio.defense.gov/Portals/0/Documents/Library/DevSecOps%20Playbook_DoD-CIO_20211019.pdf
Unclassified, U. (2021). DoD Enterprise DevSecOps Strategy Guide Department of Defense OFFICE OF PREPUBLICATION AND SECURITY REVIEW. https://dodcio.defense.gov/Portals/0/Documents/Library/DoDEnterpriseDevSecOpsStrategyGuide.pdf
What is a CI/CD pipeline? (n.d.). Www.redhat.com. https://www.redhat.com/en/topics/devops/what-cicd-pipeline
4 notes
·
View notes
Text
Know what the incident response cycle is
Incident response is a plan for methodically responding to cybersecurity policy. Different measures are taken for containing, mitigating and learning from the harm when any event is reprehensible. But not all cybersecurity incident needs investigation because all are not always serious. Some events like single login failure by any employee on site do not require in-depth investigation as it’s not a major issue. However, it is relevant to maintain a record of all those instances for investigations in the future.
Knowing about the incident response cycle, and incident response playbooks along its framework will assist you as well as your organisation in knowing about the accessibility of all sensitive information, thus facilitating you in preventing any kind of breach. It also assists in mitigating threats by instructing others and recognising vulnerabilities and because of artificial intelligence in cybersecurity, it has become easier.
About incident response life cycle
The incident response cycle is a step-by-step process of any company for detecting and responding to service interruptions or any kind of security threat. It is important to have incident response plans in place to make sure there is data protection, prevent information leaks and protect the organisation from being infiltrated.
It is imperative to stay prepared for data breach incidents as nowadays it has become very common. Incident response is very much stressful when any important asset is involved and you know that there is danger. Information security training assists in efficient containment and recovery in intense, stressful conditions. Time of response is very important for preventing damages, for which it is vital for formulating some incident response plan steps.
NIST incident response procedure
NIST or the National Standards and Technology Institute is one of the government agencies that works in several technical domains such as cybersecurity and is famous for its incident response measures. The steps are
Preparation: Development and execution of required methods for the protection of important infrastructure.
Detecting and analysing: For keeping a regular check on all systems, information, data and operations along with management of safety risks successfully.
Containment, suppression and recovery: Restoration of affected systems in minimum time.
Post-incident activity: Taking required steps to avoid such incidents.
SANS incident response process
SANS Institute is an organisation that provides information security research and education. It is one of the biggest information security training providers across the world and has a large collection of cybersecurity studies. Its incident response steps are
Preparation: First the security policy of any organisation is seen and codified, then a risk assessment is done; sensible assets are recognised, security incidents are established and then a computer security incident response team is created.
Identifying: IT systems can track and recognise deviations from standard activities and check if they establish real safety incidents. It involves collecting such information when any of the occurrences are detected, assessing its form and intensity and logging all things.
Control: Performing containment is short-term through isolation of the part of the network that is at risk. Then emphasis is on long-term containment that requires temporary adjustments to allow systems for being used in production during rejuvenating clean systems.
Suppression: Removing malware from every infected device, acknowledging the root cause of the attack and taking steps to prevent such attacks.
Recovery: To avoid any attacks, it is required to keep the affected system back online. To make sure they are back to normal functioning, testing, checking and tracking the impacted system is important.
Conclusion
So, a properly trained incident response team with a cyber essentials checklist is important for recognising and mitigating threats and companies always look for skilled candidates.
0 notes
Text
Who benefited from US-Russia prisoner swap
A major prisoner swap between Russia, the United States and their allies was held at Ankara airport on Thursday under the coordination of Turkey’s National Intelligence Organisation (MIT).
The intelligence agency said in a statement:
Our organisation has undertaken a major mediation role in this exchange operation, which is the most comprehensive of the recent period.
In further comments, the MIT said it “conducted the most extensive prisoner swap operation in recent times.”
MIT said, naming five people, including Wall Street Journal reporter Evan Gershkovich and former US marine Paul Whelan, who were imprisoned in Russia:
The prisoner swap involved the exchange of significant figures that all parties have been seeking for an extended period of time.
Russia also released Kevin Lik, a Russian-German citizen convicted last year of treason for filming military units in Maikop, and another German citizen, Patrick Schobel, who was detained at Pulkovo airport for carrying marijuana marmalade.
Several Russian political activists detained in recent years on various charges have also came to the US. Ilya Yashin former head of the Krasnoselsky municipal district in Moscow, opposition politician Vladimir Kara-Murza, Lilia Chanysheva, Ksenia Fadeeva and Vadim Ostanin former heads of Navalny’s Headquarters, Andrei Pivovarov former head of Open Russia, journalist Alsu Kurmasheva employee of the Tatar-Bashkir service of Radio Liberty, artist Alexandra Skochilenko, St. Petersburg lawyer German Moyzhes and political scientist Demuri Voronin are among the released.
DW reported that Vadim Krasikov, identified by German officials as a Russian FSB intelligence colonel serving a life sentence in Germany for the 2019 murder of a Kremlin opponent in a Berlin park, was among those flown to Ankara for the exchange.
Seven planes flew the 26 people to Turkey, MIT said. Two of the planes came from the United States, and one each from Russia, Germany, Poland, Slovenia and Norway.
The prisoners were taken off each plane and then transported by MIT to secure locations. They were then medically screened as part of a checklist designed to ensure that each part of the swap deal met ratification requirements. After that, they were put back on planes to travel to their destinations.
The former prisoners received a warm welcome in Russia and were greeted as true heroes. Artem Dultsev and Anna Dultseva, accused of espionage, Mikhail Mikushin, a researcher at the University of Tromsø who was arrested on espionage charges in October 2022, journalist Pavel Rubtsov, Vadim Konoshchenok, accused of collecting data on behalf of the FSB and smuggling dual-use technology, Vladislav Klyushin, serving a sentence from 2023 on cyber fraud charges and Roman Seleznev, accused of cyber fraud, returned to their homeland.
Russian President Vladimir Putin promised to present those released as part of the exchange who “have a direct relation to military service” with state awards.
US President Joe Biden said the swap deal was possible thanks to “feats of diplomacy and friendship.” He thanked Germany, Poland, Slovenia, Norway and Turkey for helping to broker the deal.
Which side benefited more from the prisoner swap is a rather controversial issue. It is very important that the swap took place now and not after the US presidential election. Despite numerous attempts by the media to convince the public that the gap between Harris and Biden is quite small, she is still in a very precarious position.
By organising the exchange now, Putin has played along with one of the candidates just when this candidate needed support. This suggests that the Democratic Party’s destructive course, which benefits Russia, does not strengthen American hegemony, but rather discredits it. Kamala Harris will undoubtedly continue on this course, and even though she, like all Democrats, supports continued aid to Ukraine, she will be a more favourable candidate for Russia than Donald Trump.
Answering the question of “who is better for Russia – Biden or Trump” in an interview with Tucker Carlson in February, Putin chose Biden. He said:
He is a man more experienced, more predictable, he is a politician of the old formation.
As part of the exchange, patriots who had served their country faithfully returned to Russia. In return, Moscow got rid of oppositionists who were harming the state from within, undermining the image and authority of the government.
The recent prisoner exchange between the US and Russia appears to be an underlying plan by Vladimir Putin that will have positive implications for Russia’s role on the world stage.
THE ARTICLE IS THE AUTHOR’S SPECULATION AND DOES NOT CLAIM TO BE TRUE. ALL INFORMATION IS TAKEN FROM OPEN SOURCES. THE AUTHOR DOES NOT IMPOSE ANY SUBJECTIVE CONCLUSIONS.
Bill Galston for Head-Post.com

#world news#news#world politics#russia#russia news#russian politics#russian news#usa#usa news#usa politics#usa today#united states#united states of america#us politics#us elections#us presidents#us news#politics#joe biden#biden#president biden#biden administration#election#2024 election#us election#presidency#vladimir putin#putin#prisoners#prisoner
0 notes
Text
Just when CrowdStrike thought their problems were limited to their role in the global computer crash, this just came out. The "indicators of compromise" may be CrowdStrike's secret sauce. There are all sorts of cyber security companies, but, based on their work for the DNC and their willingness to blame Russians, CrowdStrike got the name recognition and publicity, and from there, the business and the billions.
Now we know, based on the Vault 7 leaks, these can be faked. We know from CrowdStrike's own statements that businesses can lie. We know from history that "indicators" can be interpreted wrongly (Kevin Mitnick was once thought as being a pseudonym for a hacker from MIT). We know that methods may be copied as well, as Kevin Mitnick and friends used the Chaos Computer Club's LOGINOUT patch.
And with CrowdStrike's checklist out in the open, it's clear that hackers and others could take advantage of it. And CrowdStrike are the only ones to blame.
0 notes
Text
Keep Your Site Thriving- Essential Website Maintenance Tips for 2024

In the rapidly evolving digital landscape, maintaining your website's health is more crucial than ever. As we head into 2024, the competition for online visibility is fierce, and a well-maintained website can be the difference between thriving and merely surviving. This guide, "Keep Your Site Thriving: Essential Website Maintenance Tips for 2024," is designed to help you stay ahead of the curve.
From regular website updates to comprehensive website audits, these tips will ensure your site remains a top performer. We'll delve into everything from SEO maintenance tips and website optimization 2024 to the nitty-gritty of site speed tips and content management tips. Whether you're a seasoned webmaster or a newbie, these insights will equip you with the knowledge to keep your site running smoothly and efficiently.
Website maintenance isn't just about keeping your site functional; it's about enhancing user experience and ensuring top-notch security. In 2024, with cyber threats becoming increasingly sophisticated, implementing robust site security measures and staying up-to-date with website security 2024 standards is non-negotiable. Additionally, we'll explore the significance of mobile optimization tips, website plugin updates, and technical SEO tips to boost your site's performance.
This site maintenance guide 2024 also covers essential aspects like website backup tips, website analytics 2024, and site performance monitoring. By following this comprehensive website maintenance checklist, you can ensure your site not only meets but exceeds user expectations, keeping your audience engaged and your business flourishing.# Keep Your Site Thriving: Essential Website Maintenance Tips for 2024
Are you tired of seeing your website traffic dip unexpectedly? Do you dream of a stable, upward trend in your site metrics? The key to achieving this lies in effective website maintenance. By incorporating a few tweaks and regular check-ins, you can transform your online platform into a bustling digital marketplace. Say goodbye to the days of wondering why your business isn't reaching its online potential. Let’s dive into the essential website maintenance tips for 2024 to keep your site thriving!
Table of Contents
The Hidden SEO Power of Website Maintenance
My Story of Website Maintenance
Dive into the ‘Site Revitalization Technique’
Website Maintenance: Why Should You Care?
What Exactly Does Website Maintenance Include?
Regular Content Updates
Website Performance Optimization
Security Updates
User Interface (UI) and User Experience (UX) Enhancements
Regular Backups
Website Maintenance: Don’t Skip These Frequent Misses!
FAQ – Website Maintenance
What is website maintenance?
Why is website maintenance important?
How much does it cost to maintain a website?
How often should I update my website?
What happens if I don’t maintain my website?
What are the key tasks involved in website maintenance?
Can I do website maintenance myself, or should I hire a professional?
How does website upkeep impact SEO?
How does website maintenance affect website security?
What is the ‘Site Revitalization Technique’?
The Hidden SEO Power of Website Maintenance
Have you ever considered how consistent website maintenance can drive business growth? Picture website maintenance not as a mundane task, but as the unsung hero in your business's success story. It’s far more than fixing broken links or updating software. It’s the linchpin that holds your online presence together, the cog in your business machine that keeps the wheels turning smoothly.
When maintained properly, your website becomes a powerful marketing tool. It drives higher traffic, fosters better engagement, amplifies user satisfaction, and skyrockets your conversions. It’s the platform that showcases your brand to the world, and with diligent maintenance, it can be a beacon that draws customers in, compelling them to stay and explore what you offer.
In essence, stellar website maintenance is your golden ticket to an unstoppable online presence and SEO results. It’s a strategic investment that paves the way to sustained growth and success in today’s competitive digital marketplace.
My Story of Website Maintenance
I remember the thrill of launching my business website. It was shiny, new, and I was convinced it would take the online world by storm. However, over time, I noticed a drop in traffic. Customers started reporting glitches, slow load times, and outdated content. My shiny new website had lost its luster.
Then, I stumbled upon the concept of website maintenance. At first, I was skeptical. “How much does it cost to maintain a website?” I wondered. But as I delved deeper, I realized that the cost of not maintaining my website was much higher. The lost traffic and unhappy customers were all symptoms of a neglected website.
Once I embraced the importance of regular website maintenance, everything changed. My site was faster, up-to-date, and more engaging. It began attracting more visitors, retaining customers, and generating more sales. That’s when I truly understood: website maintenance wasn’t an expense; it was an investment in my business’s future success.
"Website Maintenance: It’s the behind-the-scenes hero that transforms your online presence from 'just there' to 'unstoppably successful'."
Dive into the ‘Site Revitalization Technique’
So, what exactly is the ‘Site Revitalization Technique’? Think of it as a holistic approach to website maintenance that goes far beyond the basics. It’s not just about fixing broken links or updating plugins. It’s about viewing your website as a living, breathing entity that needs regular attention and care to thrive.
In the ‘Site Revitalization Technique’, we focus on three key pillars – Functionality, Freshness, and Forward-Thinking.
Read More
0 notes
Text
Keep Your Software Updated: A Key to Online Security

Keeping your software up-to-date is a critical yet often neglected aspect of online security. Software updates frequently include patches for security vulnerabilities that hackers can exploit, leading to potential data breach. Whether it’s your operating system, apps, or antivirus software, ensuring you have the latest updates installed can prevent many types of data breaches.
Why Software Updates Matter
Security Patches:
Software developers continually work to identify and fix security vulnerabilities. These patches are included in updates to protect users from newly discovered threats. Without these updates, your system remains exposed to attacks.
Enhanced Features:
Updates often come with new features and improvements that enhance the functionality and security of your software. These enhancements can help protect against evolving cyber threats.
Bug Fixes:
Updates also address bugs and performance issues that could be exploited by hackers. Fixing these bugs ensures your software runs smoothly and securely.
The Risks of Not Updating Software
Increased Vulnerability:
Outdated software is a prime target for cybercriminals. Hackers can exploit known vulnerabilities in old versions to gain unauthorized access, leading to data breaches and other security incidents.
Compatibility Issues:
Running outdated software can lead to compatibility issues with other programs and devices, potentially causing malfunctions and security gaps.
Compliance Risks:
For businesses, using outdated software can result in non-compliance with industry standards and regulations, leading to legal and financial consequences.
Steps to Keep Your Software Updated
Enable Automatic Updates:
Enable automatic updates whenever possible to ensure your software receives the latest patches and improvements as soon as they are released. This is particularly important for your operating system, antivirus software, and frequently used applications.
Regularly Check for Updates:
For software that doesn’t support automatic updates, make it a habit to manually check for updates regularly. Set reminders to review and update your software periodically.
Update All Devices:
Ensure that all your devices, including smartphones, tablets, and computers, are kept up-to-date. Cyber threats target all types of devices, and keeping them updated is essential for comprehensive security.
Educate Yourself and Others:
Stay informed about the importance of software updates and encourage those around you to do the same. Cybersecurity is a shared responsibility, and collective awareness can significantly enhance overall protection.
For boAtheads: Taking Action
For boAtheads, making a habit of regularly updating your software is a straightforward yet highly effective way to enhance your digital security and protect your personal information from cyber threats. Here’s a quick checklist to help you stay on top of updates:
Enable Automatic Updates: Ensure automatic updates are enabled for your operating system, antivirus software, and key applications.
Regular Manual Checks: Periodically check for updates for software that doesn’t support automatic updates.
Update All Devices: Keep all your devices, including smartphones, tablets, and computers, updated.
Stay Informed: Follow cybersecurity news and updates to be aware of new vulnerabilities and patches.
Conclusion
By following these guidelines and staying informed, boAtheads can navigate the digital world more securely, reducing the risk of data breaches and protecting their valuable personal information. Regularly updating your software is a simple yet powerful step towards robust online security. Make it a priority to keep your systems updated and enjoy the peace of mind that comes with knowing your data is protected against the latest cyber threats.
0 notes
Link
We will discuss server hardening in this blog, and we will also prepare a checklist that covers the areas that need to be protected against the most common exploits. They run the business and help employees share data and keep up their work. However, they are vulnerable to cyber-attacks. Many small businesses build or deploy physical servers by hand, but fail to protect them from hackers and data breaches. Follow our comprehensive checklist of Windows Server Hardening Security Checklist to reduce costly breaches or your attack surface and improve server security. What Is Server Hardening? In server hardening, several components, functions, and ports of a server are protected from security threats. It is a collection of techniques that improve security. By hardening a server, you reduce the probability of a cyber attack by implementing security measures such as firewalls, recovery procedures, and virus protection. In essence, server hardening is the process of putting in place protection mechanisms while also making critical computer systems more difficult to attack. Windows Server Hardening Security Checklist As cyber attackers are always trying to access the data and resources hosted on the servers, here are some controls and processes one should always put into practice for server security to protect them in real time. By using our general server security checklist, you will be able to identify vulnerabilities and errors, increase awareness of security issues, and improve the security of your servers.
0 notes
Text
The Importance of Website Maintenance: Keeping Your Affordable Website Fresh in Melbourne
Why Regular Website Maintenance Matters
An outdated or neglected website can do more harm than good to your business. Here are some compelling reasons to prioritize website maintenance:
Enhanced User Experience (UX): A website riddled with broken links, outdated content, and slow loading times frustrates visitors and sends them bouncing off. Regular maintenance ensures your website functions flawlessly, offers a smooth user experience, and keeps visitors engaged.
Improved Search Engine Optimization (SEO): Search engines like Google prioritize websites that are fresh, relevant, and mobile-friendly. Regular updates with new content, optimized images, and a focus on mobile responsiveness can significantly improve your website's ranking in search results, leading to increased organic traffic.
Enhanced Security: Cyber threats are ever-evolving. Regular maintenance ensures your website's software is up-to-date with the latest security patches, minimizing vulnerabilities and protecting your business and customer data.
Maintaining Brand Consistency: Your website plays a vital role in communicating your brand identity. Regular maintenance ensures your website's design, messaging, and overall feel align with your brand guidelines, fostering a consistent and trustworthy image for your business.
Improved Conversion Rates: A well-maintained website with optimized calls to action and a seamless user experience is more likely to convert visitors into paying customers. Regular updates ensure your website effectively guides users towards desired actions, boosting your conversion rates.
Affordable Web Design in Melbourne and Ongoing Maintenance:
Melbourne boasts a thriving web design community offering affordable solutions specifically tailored to SMB needs. However, it's important to understand that the initial website creation is just the first step. Many affordable web design packages don't include ongoing maintenance. Here's how to approach website maintenance in a cost-effective way:
DIY Maintenance: Many popular Content Management Systems (CMS) platforms like WordPress are user-friendly and offer resources to help you manage basic updates like adding content and updating plugins.
Partial Maintenance Plans: Consider exploring affordable maintenance plans offered by some web design agencies. These plans might cover critical updates like software patches and security checks while allowing you to manage content updates yourself.
Freelance Web Developers: Melbourne has a pool of talented freelance web developers who can offer affordable maintenance solutions tailored to your specific needs.
Website Maintenance Checklist for Melbourne SMBs
Here's a handy checklist to keep your website in top shape:
Content Updates: Regularly update your website with fresh content like blog posts, news updates, and product information. This keeps visitors engaged and demonstrates your expertise.
Broken Link Checks: Broken links not only frustrate users but also hurt your SEO ranking. Use free or paid tools to identify and fix broken links periodically.
Security Updates: Ensure your website's software, themes, and plugins are updated with the latest versions to address security vulnerabilities. This might require assistance from a developer if you're not comfortable with DIY updates.
Performance Monitoring: Monitor your website's loading speed and performance using online tools. Slow loading times can significantly impact user experience and conversion rates. Consider image optimization and caching solutions to improve website speed.
Mobile-Friendliness: Mobile browsing is on the rise. Ensure your website displays flawlessly across all devices, including smartphones and tablets. Most affordable web design solutions in Melbourne prioritize mobile responsiveness, but it's worth double-checking.
Analytics Tracking: Utilize website analytics tools to track user behavior, understand your audience, and identify areas for improvement. Free tools like Google Analytics can offer valuable insights.
Frequently Asked Questions (FAQs)
How often should I update my website?
There's no one-size-fits-all answer. Aim for regular updates, with the frequency depending on your industry and the nature of your content. Aim for fresh content at least once a month, with more frequent updates for fast-paced industries.
What are the costs involved in website maintenance?
The cost depends on your chosen approach. DIY maintenance is free, while freelance developers or maintenance plans from web design agencies can range from a few hundred dollars to a few thousand dollars annually depending on the complexity of your website and the scope of maintenance required.
Can I learn to do basic website maintenance myself?
Absolutely! Many CMS platforms offer tutorials and resources to help you navigate basic tasks like content updates, plugin management, and image optimization. However, for more complex tasks like security updates or code modifications, consider consulting a developer.
Conclusion
Investing in regular website maintenance is not an expense; it's a strategic investment in your Melbourne-based SMB's long-term success. A well-maintained website fosters a positive user experience, strengthens your brand image, and fuels business growth. By leveraging affordable web design solutions in Melbourne and prioritizing ongoing maintenance, you can ensure your website remains a valuable asset, attracting customers, driving conversions, and propelling your business forward.
affordable web design in adelaide
affordable web design in perth
0 notes
Text
What Does an Incident Response Plan Do?
An incident response life cycle is a collection of strategies implemented by the IT staff to catch, react to and retrieve from network security incidents. These plans are suitable to address issues like cybercrime, data loss and service outages that jeopardize daily work.
Incident response plans are a step towards rectifying all such incidents, which can lead to massive network or data breaches that can affect your organization for days or months. When a significant upheaval occurs, your organisation will need a thorough, detailed incident response plan to help the IT team stop, control and manage the incident quickly.
What is an incident recovery team?
An incident recovery team is a group of IT professionals who execute the incident response plan. Generally, these are IT staff members who organise, maintain and scrutinise incident-related data. They work with the legal professionals to ensure they meet all lawful obligations.
Why does your company need an incident response plan?
Even if your business is small or has not yet been disturbed, it does not mean your network is safe. You cannot imagine the chaos that can follow a cyber attack.
Is your company ready with an Incident Response plan?
You can never be confident that your network is 100 per cent secure unless you prepare your network and your employees for crises to come and provide information security training to mitigate the damage.
If you neglect to train employees, there is always the risk of someone clicking on the wrong place and bringing your entire network and infrastructure to a standstill.
Every business must apply the cyber incident response checklist that includes the following points
1. You must determine responsibilities among your IT executives, train them with the right tools and technologies and update the plans.
2. Every executive must know how the cyberattack might impact them and what they must do at such a time.
3. Control the attack before it spreads. Find the effect on your business so you can regulate the appropriate security measures to take next.
4. Restore all data and devices to their original positions. Change passwords and review remote access protocols.
5. Have a meeting with everyone concerned and debate what you learnt from the incident.
Artificial intelligence (AI) is being introduced to every element of life and used to develop code, communicate with customers and write in various media.
Artificial intelligence in cybersecurity can have a powerful impact. AI is now mainstream and won't go away anytime soon; so you and your security professionals must know how to use it best to help enhance the security of your systems and products.
AI’s implications for security
AI systems can perform various tasks like pattern recognition, learning and problem-solving. Within AI are diverse fields like machine learning (ML), which enables systems to learn and improve over time; natural language processing (NLP), which attempts to mimic human speech; computer vision, which utilises cameras to perform various tasks and more.
In cyber security, AI is used in several roles and processes. It's being used to analyse logs, predict threats, read source code, identify vulnerabilities and even create or exploit vulnerabilities.
0 notes
Text
Understanding the Essential Security Standards for WordPress Websites

In today’s digital landscape, ensuring the security of your WordPress website is paramount. With cyber threats becoming more sophisticated by the day, it’s crucial to adhere to stringent security standards to safeguard your online presence. WordPress security checklist serves as a comprehensive guide to fortifying your website against potential vulnerabilities and attacks.
WordPress, being one of the most popular content management systems (CMS) globally, is a prime target for malicious actors. Therefore, implementing robust security measures is imperative to mitigate risks and protect your valuable data. Let’s delve into the fundamental security standards every WordPress website owner should be aware of.
Keep Your WordPress Core, Themes, and Plugins Updated
Regular updates are not merely about accessing new features; they are crucial for patching security vulnerabilities. Hackers often exploit outdated software to gain unauthorized access to websites. By promptly updating your WordPress core, themes, and plugins, you close off potential entry points for attackers, bolstering your website’s defenses.
Utilize Strong Authentication Methods
Passwords are often the first line of defense against unauthorized access. However, relying solely on passwords can leave your website vulnerable to brute force attacks. Implementing multi-factor authentication (MFA) adds an extra layer of security by requiring users to provide additional verification, such as a unique code sent to their mobile device, along with their password.
Employ Secure Hosting Providers
Choosing the right hosting provider can significantly impact your website’s security. Opt for reputable hosting companies that prioritize security and offer features such as SSL/TLS certificates, firewalls, and regular backups. A secure hosting environment provides a solid foundation for safeguarding your WordPress site against various threats.
Install a Web Application Firewall (WAF)
A Web Application Firewall acts as a barrier between your website and malicious traffic, filtering out potentially harmful requests before they reach your server. By analyzing incoming traffic and blocking suspicious activity, a WAF helps prevent common attacks like SQL injection, cross-site scripting (XSS), and distributed denial-of-service (DDoS) attacks.
Implement Regular Security Scans and Audits
Conducting regular security scans and audits is essential for identifying and addressing any vulnerabilities or security weaknesses in your WordPress website. Utilize reputable security plugins or services to scan your site for malware, suspicious code, and other indicators of compromise. Additionally, perform manual audits to ensure all security protocols are up to date and functioning correctly.
Educate Yourself and Your Team
Investing in security awareness training for yourself and your team members can significantly enhance your website’s security posture. Educate yourself about common security threats, best practices for secure web development, and how to recognize phishing attempts and other social engineering tactics. By empowering your team with the knowledge to identify and respond to security risks, you create a more resilient defense against potential attacks.
Conclusion
Securing your WordPress website requires a proactive approach and adherence to established security standards. By following the WordPress security checklist and implementing robust security measures such as regular updates, strong authentication, secure hosting, web application firewalls, and ongoing security audits, you can effectively safeguard your website against cyber threats. Stay vigilant, stay informed, and prioritize security to ensure the integrity and confidentiality of your online presence.
0 notes
Text
ISO 27001 Certification in Malaysia: A Stepping Stone to Cyber Resilience in the Digital Age
/ Uncategorized / By Factocert Mysore

ISO 27001 Certification in Malaysia
ISO 27001 Certification in Malaysia In today’s hyper-connected world, information protection isn’t expensive; it’s a need. Malaysian agencies, no matter their duration or employer, face a developing panorama of cyber threats. This is where ISO 27001 Certification in Malaysia emerges as a powerful tool to build cyber resilience and benefit a competitive thing.
Beyond Compliance: Embracing a Security Culture
While accomplishing ISO 27001 Certification in Malaysia demonstrates adherence to global statistics safety excellent practices, Malaysian agencies are increasingly recognizing the same vintage’s actual fee in fostering a lifestyle of safety. Here’s how ISO 27001 goes past a checklist:
Risk-Based Approach: The desired emphasizes a danger-based, completely definite technique, requiring corporations to understand, study, and prioritize information protection risks unique to their context. This ensures assets are allocated efficiently to cope with the most vital vulnerabilities.
Continuous Improvement: ISO 27001 Certification in Malaysia isn’t always a static device. It mandates a non-prevent improvement cycle, prompting businesses to compare and refine their facts about safety regularly manipulation machines (ISMS) to conform to evolving threats.
Employee Engagement: Building a strong protection posture requires buy-in from all levels. The preferred emphasizes worker consciousness education programs, empowering staff to understand and mitigate the gate protection risks of daily work.
Benefits Tailored for the Malaysian Market
The blessings of ISO 27001 Certification in Malaysia boom some distance beyond easy compliance for Malaysian organizations:
Enhanced Brand Reputation: Certification shows a determination to ensure statistics safety, boosting acceptance as accurate among customers, partners, and buyers. This is especially critical in Malaysia’s developing virtual monetary device, where information privacy is paramount.
Improved Operational Efficiency: The installed framework of ISO 27001 Certification in Malaysia permits streamlined data protection strategies, leading to operational overall performance and fee monetary savings.
Compliance with Regulations: Several Malaysian tips, in conjunction with the Personal Data Protection Act (PDPA), emphasize strong records protection practices. ISO 27001 Certification in Malaysia demonstrates alignment with those guidelines, decreasing the risk of non-compliance penalties.
Competitive Advantage: In a competitive marketplace, demonstrating a proactive approach to data safety can differentiate your enterprise and open new company possibilities.
The Path to Certification: A Modernized Approach
Achieving ISO 27001 Certification in Malaysia has ended up more streamlined in state-of-the-art years. Here are a few critical issues for agencies embarking on this journey:
Gap Analysis: Conduct a thorough hole analysis to identify areas where your present-day records safety practices fall short of the ISO 27001 Certification in Malaysia requirements.
Leveraging Technology: Utilize cloud-based equipment and automation to manage documentation and behavior threat exams and streamline the certification machine. This is mainly beneficial for smaller organizations with restrained resources.
Engaging with Accredited Certification Bodies (CBs): Malaysia boasts several authorized CBs with excellent revelations within the neighborhood marketplace. Choosing the proper CB ensures a smooth and inexperienced certification machine.
Beyond Certification: Embracing Continuous Improvement
While attaining ISO 27001 Certification in Malaysia is a significant accomplishment, it is the first step. The fee lies in the ongoing determination to protect information and improve your ISMS non-stop. Here are some more pointers:
Regular Internal Audits: Conducting daily internal audits permits you to identify and address any potential gaps in your ISMS before they become predominant vulnerabilities.
Staying Updated: The cyber hazard panorama evolves suddenly. Organizations should stay current on rising threats and incorporate new controls and top-notch practices into their ISMS.
Security Awareness Training: Invest in ongoing safety education for employees to maintain their knowledge about the extraordinarily contemporary threats and their characteristics in protective statistics assets.
Conclusion: A Secure Future for Malaysian Businesses
In a global environment where cyber threats constantly evolve, ISO 27001 Certification in Malaysia offers a robust framework for building cyber resilience. By embracing a way of life of security and non-preventive development, Malaysian organizations can defend their treasured statistics property and competitive edge in the virtual age.
Why Factocert for ISO 27001 Certification in Malaysia
We provide the best ISO consultants Who are knowledgeable and provide the best solution. And to know how to get ISO certification. Kindly reach us at [email protected]. work according to ISO standards and help organizations implement ISO Certification in Malaysia with27001 proper documentation.
For more information, visit ISO 27001 Certification in Malaysia.
RELATED LINKS
ISO certification in Malaysia
ISO 9001 certification in Malaysia
ISO 14001 certification in Malaysia
ISO 45001 certification in Malaysia
ISO 13485 certification in Malaysia
ISO 27001certification in Malaysia
ISO 22000 certification in Malaysia
CE Mark certification in Malaysia
0 notes
Text
How does ISO 27001 work?
We as an ISO Consultancy in Dubai, we have a fast refresher on all the ins and outs of ISO 27001 in less than 27001 milliseconds, so if you're familiar with it already, this will help. Before we discuss the advantages, we must lay the foundation if you're entirely new to the compliance area. International recognition is the gold standard for information security, and ISO 27001 is a frequent compliance requirement in Europe. It is a component of the ISO 27000 series, a framework series. ISO 27001, on the other hand, focuses explicitly on ISMS (information security management system) requirements. A system for managing information security (ISMS) encompasses all your documentation, controls, staff, policies, and procedures. It then compares this to the ISO 27001 standard, focusing on maintaining the three main information security pillars of ISO 27001: availability, confidentiality, and integrity.

As an ISO Consultancy, Independent auditors may attest to your organization's compliance with all regulations and effective implementation of best practices by ISO 27001 security standards, enabling you to achieve an ISO 27001 certification. A company must meet the rigorous ISO 27001 requirements to receive ISO 27001 certification. You must set up an ISO 27001-compliant information security management system (ISMS) to accomplish this. Our comprehensive ISO 27001 Checklist Guide provides a foundation for your compliance journey. The advantages can begin to accrue after certification. Here are a handful of ISO 27001's main benefits. It's critical to safeguard client and company data against cybersecurity threats. It can be challenging to distinguish between what is and is not at risk today since cyber security threats and breaches are becoming more sophisticated.
In our opinion as ISO Consultant in Dubai, ISO 27001 provides a fundamental framework for security, guaranteeing that your company takes reasonable precautions to secure information. ISO 27001 standardizes risk assessments, employee training, security controls, policies, and procedures, safeguarding your company against internal and external security threats. Your company must follow all applicable regulations and suggested data and information security standards. You might be subject to particular regulatory regimes depending on the kind of information, the sector, and the region. One of its main advantages is that ISO 2700 offers the necessary evidence that you adhere to pertinent security requirements. However, even some of the standards included in other frameworks, such as the General Data Protection Regulation (GDPR) of the European Union and the NIST CSF (Cybersecurity Framework), are strengthened by ISO 27001.
We are renowned ISO Consultant; Data security is essential for attracting and keeping clients. One thing remains crucial when industries become oversaturated with similar businesses and technological advances: who would you trust with your sensitive information? Certification from ISO 27001 aids in proving that you've put security best practices into operation. You've put into practice what's called "The Golden Standard." This gives you an advantage over rivals who have chosen to use neither framework nor another. Additionally, trust in your ability to enter new markets and close more deals while reducing risk and exposure comes with compliance. The risk-based strategy of ISO 27001 effectively prioritizes security concerns and controls a company's information security. By implementing the controls pertinent to your unique priorities and threats, you can take a customized approach to information security.
0 notes
Text
2024 Security Audit Essentials for Businesses: Protect Your Assets

In the ever-evolving digital landscape, safeguarding your business against cyber threats is paramount. But how can you ensure your IT infrastructure remains resilient amidst constant change? The answer lies in comprehensive security audits.
Why Security Audits Matter
Security audits serve as your shield against potential risks lurking in the digital realm. Our blog provides invaluable insights into the intricate world of security audits, guiding you through every step of the process.
Unveiling the Checklist
Discover the power of an information security audit checklist tailored to fortify your defenses. Our blog delves deep into the checklist's anatomy, empowering you to identify vulnerabilities and mitigate threats effectively.
Exploring the Depths
Join us as we unravel the nuances of security audits, exploring their myriad benefits, diverse types, and essential steps. Gain a holistic understanding of how audits can bolster your security posture and safeguard your digital assets.
Ready to Dive In?
Equip yourself with the knowledge and tools needed to navigate the complex landscape of security audits. Whether you're a seasoned professional or a budding entrepreneur, our blog caters to all, offering invaluable insights to fortify your defenses.
Take the First Step
Secure your business against cyber threats with our expert guidance. Explore the realm of security audits and embark on a journey towards fortified defenses and unparalleled resilience.
Get Started Now: 2024 Security Audit Essentials for Businesses
Protect your business. Empower your future. Dive into the world of security audits today.
Stay secure, stay ahead.
ECF Data, LLC
#managed it services#managed service provider#azure services#microsoft services#cyber security#Azure Ai#Co-pilot#microsoft co pilot
1 note
·
View note