#cybersecurity service provider
Text

Unleashing Robust Cyber Protections with Expert Services
Sara Technologies Inc. is committed to fortifying your digital space and ensuring you are entirely safe from cyber-attacks and data breaches. Our Cyber Security Service Providers are at the frontier of cyber defense and offer tailored solutions to meet your specific needs.
0 notes
Text

Benefits of Application Security
Cyber Security Works is a leading cybersecurity services company that provides risk-based vulnerability management and penetration services. We are at the cusp of hyper-digitization. What began as a wave of digital transformation across the globe 5 years back is making way for more digitization. Cloud is the cornerstone of that hyper-digitized world – A world of opportunities and a revamped workspace. The wave of hyper-digitization backed by the cloud has increased security risks. Skillmine lets your business overcome these risks with our range of services including cloud managed security services and cybersecurity consulting services.
Website: https://skill-mine.com/service/cyber-security-services/
0 notes
Text
Discover why cybersecurity is crucial for the business to remain technologically sound and still reach its goals. Read more on the LAN Infotech blog.
#cybersecurity#cyber security risk assessment#cybersecurity consulting#cyber security audit checklist#cyber security checklist#cybersecurity services#cybersecurity service provider
0 notes
Text
How Managed Service Providers Unlock Scalability and Streamline IT Operations
Driving Growth: How Managed Service Providers Unlock Scalability and Streamline IT Operations

Read blog: https://centurygroup.net/driving-growth-how-managed-service-providers-unlock-scalability-and-streamline-it-operations/
#managedserviceprovider #msp #cybersecurity #centurygroup #managedservices #managedsecurity #datasecurity #itconsultingservices #cyberattack #voipsolution #informationsecurity #manageditsolutions #manageditservice #managedservice
#Managed Service provider#IT MSP#cybersecurity#voip solutions#managed it services#cloud technology services
2 notes
·
View notes
Text
Best Managed Service Provider Company in Noida and USA - RevSyntech
Explore RevSyntech, the best-managed service provider company in Noida, delivering a full range of IT solutions, including network management, cloud services, cybersecurity, and IT support. We offer customized services to optimize business efficiency, cut costs, and strengthen security.
In the USA, RevSyntech stands out as a top managed service provider, offering expert IT services designed to keep your business operations seamless and secure. Rely on our experienced team for tailored solutions that meet your specific needs. Read more -
Managed Service Provider, IT Solutions, Best Managed Service Provider Company in Noida, Managed Service Provider in USA, Cloud Solutions, Cybersecurity, IT Support
#Managed Service Provider#IT Solutions#Best Managed Service Provider Company in Noida#Managed Service Provider in USA#Cloud Solutions#Cybersecurity#IT Support
0 notes
Text
Understanding Cloud Computing: An Advanced Guide

Discover how cloud computing can revolutionize your business with our advanced guide! Learn about scalable resources, cost efficiency, and the flexibility that cloud computing offers. Dive deep into cloud architecture, explore security benefits, and stay ahead of the competition by leveraging Microsoft Azure. Whether you're in healthcare, retail, or finance, Azure's powerful tools like Virtual Machines and Kubernetes can enhance your business operations.
Unlock the power of cloud computing with our comprehensive guide! Dive into essential topics like:
Understanding Cloud Architecture: Learn the structure and components of cloud systems.
Security in the Cloud: Explore best practices and benefits.
Microsoft Azure Deep Dive: Get insights into IaaS, PaaS, SaaS, and serverless computing.
Real-World Use Cases: See how industries like healthcare, retail, and finance leverage Azure.
Ready to transform your IT infrastructure? Learn more in our blog and see how Azure can give you the edge you need.
Read more here: Understanding Cloud Computing: An Advanced Guide
#azure ai#azure services#cloud computing#azure computing#cloud Services#Azure Cloud Computing#understanding cloud computing#cybersecurity#managed it services#cyber security#it services in las vegas#managed it service provider#usa#it services#it services new york
1 note
·
View note
Text
Shield Your Digital World: The Ultimate Guide to VPN Security with NordVPN
In today’s digital age, protecting your online data has become more important than ever. With the rise of cyber threats and privacy concerns, many people are turning to Virtual Private Networks (VPNs) as a solution. But what exactly is a VPN, how does it work, and is it safe? In this beginner-friendly guide, we’ll answer these questions and more, as well as explore the top features of NordVPN, a leading VPN service.
#super vpn#vpn#best vpn#vpn service#free vpn#clone vpn#database#cybersecurity#data privacy#cyberattack#microsoft#vps hosting#hosting#hosting provider#hosting services#webhosting#hosting the shadow#windows vps server#vps34 in1#vps server hosting#vps server germany#vps windows server#dedicated server#vps server in saudi arabia#reseller#nord vpn
0 notes
Text
Future Challenges of Network Peering with Proxy Service Providers in the Age of DDoS and Other Forms of Mass Service Disruption Attacks
Learn about the future challenges of network peering with proxy service providers in combating DDoS and mass service disruption attacks. This comprehensive guide covers key players, proxy types, attack vectors, and strategies for network administrators.
Introduction
In the ever-evolving landscape of network security, the rise of Distributed Denial of Service (DDoS) attacks and other forms of mass service disruption attacks have become significant concerns for network security and infrastructure administrators. These malicious activities not only disrupt services but also pose severe threats to the integrity and availability of networks. One of…
#cybersecurity#ddos-attacks#ddos-mitigation#future-threats#infrastructure-security#network-peering#network-security#Networking#proxy-service-providers#proxy-types
0 notes
Text

Spictera, a premier cybersecurity company, delivers top-notch protection against cyber threats. Specializing in advanced threat detection and response, Spictera provides tailored solutions to safeguard your digital assets. Trust Spictera for comprehensive cybersecurity services that ensure the integrity and security of your business operations.
0 notes
Text
IT Services | Charter Global
At Charter Global, we’re dedicated to propelling businesses forward in today’s rapidly changing landscape by offering innovative solutions that harness the power of technology and people. Our experienced teams collaborate closely with clients to tailor solutions that drive precise results, utilizing the latest advancements to provide opportunities for growth, efficiency, and success. Whether it’s transforming operations, enhancing customer experiences, or staying ahead of the curve, our experts are committed to helping you succeed. Reach out today to discover how our cutting-edge service solutions can unlock limitless possibilities for your company.
#IT Services#Managed IT Services#IT Consulting#IT Support Services#Cloud Computing Services#Cybersecurity Services#Network Management#IT Outsourcing#Best IT Services for Small Businesses#Affordable IT Services#IT Services Near Me#Top IT Service Providers#IT Services for Healthcare
0 notes
Text

Partnering with the Best Cyber Security Service Providers
In today's digital world, safeguarding data is non-negotiable, and so is choosing a top Cyber Security Service Provider. At Sara Technologies Inc., we combine threat intelligence with proactive defense strategies, including state-of-the-art encryption, real-time monitoring, and unparalleled intrusion detection.
0 notes
Text
a failed update from billion-dollar cybersecurity firm crowdstrike has crashed windows machines worldwide today (july 19th 2024), leaving everything from airport terminals to checkout machines to delivery apps to banks stuck with a blue screen of death. here's a screenshot from downdetector (au) to illustrate:


the issue appears to be with crowdstrike falcon, a form of antivirus software widely used in the corporate world -- with emphasis on the world. there have been reports from the us, uk, australia, germany, india, france, japan and more. places affected include (but are not limited to) supermarkets, banks, basically every airline, public transport networks, major broadcasters, emergency services, corporate offices, healthcare providers and stock exchanges.

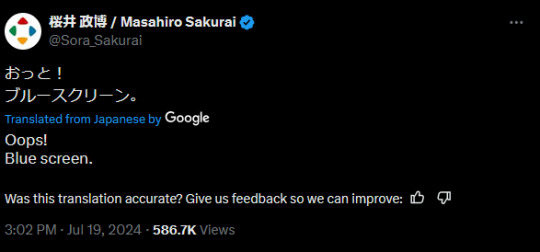


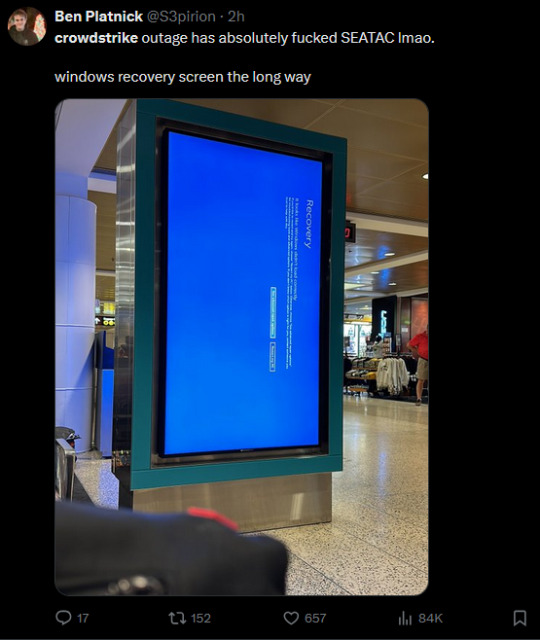

(woolies pic via archiestaines9 on twitter; s3pirion; akothari. yes that is masahiro sakurai of smash bros fame)
emergency service lines are currently experiencing problems within the american states of alaska, arizona, indiana, minnesota, new hampshire and ohio. similar problems likely plague other areas of the world, they just haven't been reported on yet. australian emergency services are operating, and critical infrastructure remains stable. be sure to check in with the local news stations still online for more updates.
welcome to y2k............................. 2!!!!!!!!!!!!!

13K notes
·
View notes
Text
Everyday Practices for Office Cybersecurity
New Post has been published on https://www.aheliotech.com/blog/everyday-practices-for-office-cybersecurity/
Everyday Practices for Office Cybersecurity
Cybersecurity is a critical aspect of our digital lives, and implementing strong everyday practices is essential for protecting sensitive information from cyber threats. While robust cybersecurity packages may seem appealing, it is more efficient to work with your Managed Service Provider to implement the services needed for your organization. Part of that begins with applying everyday practices that enhance your cybersecurity posture. Below, we have provided some suggestions for Best Practices.
Strong Passwords: Create complex passwords that use a mix of letters, numbers and special characters. Avoid using easily guessable information like birthdays or frequently used words such as the names of pets or children.
Update Software Regularly: Keep all software up to date with the latest security patches. Cyber attackers often exploit vulnerabilities in outdated software to gain unauthorized access.
Beware of Links: Think before clicking on links, especially those in unsolicited emails or messages. Phishing attacks commonly use deceptive links to steal personal information. Contact AhelioTech for more information about Phishing training services.
Enable Multi-Factor Authentication (MFA): MFA adds an extra layer of security by requiring a second form of verification, such as a text message or an authentication app, in addition to a password.
Conduct Cybersecurity Audits: For businesses, it is beneficial to conduct regular audits to assess and improve cybersecurity measures. Schedule your audit with AhelioTech today.
Educate and Train Staff: AhelioTech offers services that train on cybersecurity best practices and current cyber threats that can help employees recognize and prevent potential security breaches.
Backup Data: Whether you decide to store backups on or off site, it is crucial to regularly backup important data to secure locations. This practice helps in quickly restoring information in case of a ransomware attack or data loss.
Implement a Firewall: A firewall can monitor incoming and outgoing network traffic to prevent unauthorized access to your network.
Use VPNs for Secure Connections: A Virtual Private Network (VPN) can provide a secure connection to the internet, especially when accessing the network remotely.
Practice Cyber Hygiene: Just like personal hygiene, cyber hygiene involves regular check-ups and maintenance to ensure the health of your digital environment.
By integrating these practices into daily routines, individuals and organizations can significantly reduce their vulnerability to cyberattacks and protect their digital assets. While cyber-attacks are always evolving, security measures are as well. It is crucial to stay informed about the latest cybersecurity trends and threats, as cyber attackers continually evolve their tactics. Cybersecurity is not a one-time effort but a continuous process of improvement and vigilance.
0 notes
Text
Top 10 Cloud Computing Security Issues and Solutions in 2024
Cloud computing has become the cornerstone of modern businesses, providing unparalleled flexibility, scalability, and efficiency. However, with its myriad benefits come inherent security challenges that must be addressed to safeguard sensitive data and ensure operational integrity. In this comprehensive guide, we’ll delve into the top 10 cloud computing security issues facing businesses in 2024, along with practical solutions to mitigate these risks effectively.
Data Breaches and Unauthorized Access
Insider Threats
Insecure APIs
Data Loss and Leakage
Compliance Challenges
Cloud Misconfigurations
Distributed Denial of Service (DDoS) Attacks
Inadequate Identity and Access Management (IAM)
Vendor Lock-In
Emerging Threats and Zero-Day Vulnerabilities
0 notes
Text
How IT Services from an MSP Drive Long-Term Financial Benefits?

Summer Savings with IT Efficiency: How IT Services from an MSP Drive Long-Term Financial Benefits- Read Blog: https://centurygroup.net/summer-savings-with-it-efficiency-how-it-services-from-an-msp-drive-long-term-financial-benefits/
#managedservices #cybersecurity #informationtechnology #msp #itsupport #itservices #managedserviceprovider #manageditservices #itsolutions #tech #cloudcomputing #datacenter #itoutsourcing #entrepreneur #disasterrecovery #security #smallbusinessit #managedit #cloudservices
#IT Services#Managed Services#Cybersecurity#Managed Service Provider#Managed IT Solutions#phishing#cloud technology services#atlanta business#data backup
1 note
·
View note
Text
Leveraging Technical Advisory Services for IT Strategy and Digital Transformation
In today's rapidly evolving technological landscape, businesses face the constant challenge of staying ahead of the curve. The convergence of IT strategy, digital transformation, cloud solutions, and cybersecurity has become imperative for organizations striving to remain competitive and secure in the digital age. The Pixid AI paradigm shift necessitates a strategic approach, where technical advisory services play a pivotal role in guiding enterprises through their digital journey.
IT Strategy:
Crafting robust IT advisory services in Australia is the cornerstone of any successful digital transformation initiative. Technical advisory services offer invaluable insights into aligning IT objectives with overarching business goals. By conducting comprehensive assessments of existing IT infrastructures, these services help identify gaps, redundancies, and areas for optimization. Moreover, they provide strategic recommendations tailored to the organization's unique needs, ensuring that IT investments deliver maximum value and support long-term growth objectives.
Digital Transformation:
Embracing digital transformation is no longer a choice but a necessity for businesses seeking to thrive in the digital economy. Technical advisory services serve as trusted partners in this transformative journey, digital transformation consulting services in New Zealand offering expertise in leveraging emerging technologies to drive innovation, enhance operational efficiency, and deliver superior customer experiences. From legacy system modernization to the adoption of cutting-edge digital solutions, these services provide end-to-end support, ensuring a seamless transition to the digital-first mindset.
Cloud Solutions:
The widespread adoption of cloud computing has revolutionized the way businesses operate, offering unprecedented scalability, flexibility, and cost-efficiency. However, navigating the complex landscape of cloud service providers in New Zealand requires careful planning and expertise. Technical advisory services assist organizations in formulating cloud strategies tailored to their specific needs, whether it involves public, private, or hybrid cloud environments. By evaluating factors such as workload requirements, security considerations, and regulatory compliance, these services enable enterprises to harness the full potential of cloud technologies while mitigating risks.
Cybersecurity:
As digital ecosystems expand, so do the threats posed by cyberattacks and data breaches. Protecting sensitive information and safeguarding digital assets are paramount concerns for businesses across all industries. Technical advisory services offer proactive cybersecurity solutions designed to identify vulnerabilities, mitigate risks, and fortify defenses against evolving threats. Cybersecurity consulting services in Australia provide ongoing monitoring and incident response capabilities, these services help organizations stay one step ahead in the cybersecurity arms race.
The convergence of IT strategy, digital transformation, cloud solutions, and cybersecurity underscores the need for strategic guidance and expertise. Technical advisory services play a crucial role in helping organizations navigate this complex landscape, empowering them to embrace digital innovation while mitigating risks and maximizing opportunities for growth. By partnering with experienced advisors, businesses can chart a course towards a digitally-driven future with confidence and resilience.
#technical advisory services in new zealand#digital transformation services in new zealand#digital transformation consulting services in new zealand#interim cto services in new zealand#technical due diligence services in new zealand#cloud service providers in new zealand#cybersecurity consulting services in australia#IT advisory services in australia#IT due diligence services in australia
0 notes