#data security in cloud
Explore tagged Tumblr posts
Text
Time for a new edition of my ongoing vendetta against Google fuckery!
Hey friends, did you know that Google is now using Google docs to train it's AI, whether you like it or not? (link goes to: zdnet.com, July 5, 2023). Oh and on Monday, Google updated it's privacy policy to say that it can train it's two AI (Bard and Cloud AI) on any data it scrapes from it's users, period. (link goes to: The Verge, 5 July 2023). Here is Digital Trends also mentioning this new policy change (link goes to: Digital Trends, 5 July 2023). There are a lot more, these are just the most succinct articles that might explain what's happening.
FURTHER REASONS GOOGLE AND GOOGLE CHROME SUCK TODAY:
Stop using Google Analytics, warns Sweden’s privacy watchdog, as it issues over $1M in fines (link goes to: TechCrunch, 3 July 2023) [TLDR: google got caught exporting european users' data to the US to be 'processed' by 'US government surveillance,' which is HELLA ILLEGAL. I'm not going into the Five Eyes, Fourteen Eyes, etc agreements, but you should read up on those to understand why the 'US government surveillance' people might ask Google to do this for countries that are not apart of the various Eyes agreements - and before anyone jumps in with "the US sucks!" YES but they are 100% not the only government buying foreign citizens' data, this is just the one the Swedes caught. Today.]
PwC Australia ties Google to tax leak scandal (link goes to: Reuters, 5 July 2023). [TLDR: a Russian accounting firm slipped Google "confidential information about the start date of a new tax law leaked from Australian government tax briefings." Gosh, why would Google want to spy on governments about tax laws? Can't think of any reason they would want to be able to clean house/change policy/update their user agreement to get around new restrictions before those restrictions or fines hit. Can you?
SO - here is a very detailed list of browsers, updated on 28 June, 2023 on slant.com, that are NOT based on Google Chrome (note: any browser that says 'Chromium-based' is just Google wearing a party mask. It means that Google AND that other party has access to all your data). This is an excellent list that shows pros and cons for each browser, including who the creator is and what kinds of policies they have (for example, one con for Pale Moon is that the creator doesn't like and thinks all websites should be hostile to Tor).
#you need to protect yourself#anti google#anti chrome#anti chromium#chromium based browsers#internet security#current events#i recommend firefox#but if you have beef with it#here are alternatives!#so called ai#anti artificial intelligence#anti chatgpt#anti bard#anti cloud ai#data scraping
101 notes
·
View notes
Text
It's just so phenomenally stupid to be sitting here trying to do everyday shit and planning for the work week ahead when it doesn't even matter anymore. Laundry groceries meal prep cleaning who the fuck cares. The lucky ones with the means to do so will get to escape the country and the rest get to deal with everything becoming too exorbitantly expensive to be able to live and also having no healthcare. Plus vaccines being outlawed (it just happened in Idaho!) and a brewing H5N1 pandemic everyone is going to ignore oh yeah and also Trump executing everyone who doesn't agree with him. Why the fuck am I having to do emails and spreadsheets at a time like this??
#me trying to figure out what i need to do before january 20th to protect myself and being overwhelmed lmao#hoard cash encrypt data find servers overseas to store my cloud stuff find secure messaging apps AHH
14 notes
·
View notes
Text
Secure Configurations on your Technology

Ensuring secure configurations on your technology is crucial to protect against cyber threats and vulnerabilities. Here are some tips to make sure your configurations are secure:
-Change Default Settings: Always change default usernames and passwords on your devices.
-Enable Firewalls: Use firewalls to block unauthorized access to your network.
-Regular Updates: Keep your software and firmware up to date to patch any security holes.
-Strong Passwords: Use complex and unique passwords for all your accounts and devices.
-Disable Unnecessary Services: Turn off services and features you don't use to reduce potential entry points for attackers.
-Monitor and Audit: Regularly monitor and audit your configurations to ensure they remain secure.
Stay vigilant and keep your technology secure! #CyberSecurity #SecureConfigurations #StaySafe – www.centurygroup.net
#Cybersecurity#managed it services#data backup#Secured Configuration#cloud technology services#phishing
3 notes
·
View notes
Text
OSS Security, Myth, or Major Concern?
Open Source Software (OSS) is inside some of the most essential companies and applications for society worldwide. However, a persistent stigma around OSS security continues to hinder both innovation and widespread adoption. When it came to asking people what their main concern about OSS is, 53% said security.
Many people become worried when they see that the code base is open to anyone or that it could be unmaintained or written by people with bad coding habits. There is also concern that companies may neglect to track updates to the source code, leaving them with outdated versions that pose security risks. But are these concerns truly valid? And if so, does that necessarily make proprietary software safer than OSS? Let's look a little deeper into some of the main security concerns in OSS and then look at why OSS may be a lot safer than people think.
One of the main reasons people feel that OSS is unsafe is because the code base is not proprietary, meaning that anyone can look at all of the code that makes up the application. This worries people because if attackers can look at the code of an application, they believe that it would be very easy to find its vulnerabilities. Another reason people are often worried about the security of OSS is whether or not the code is maintained. Although rare, people fear that the contributors to the software they are using will either stop maintaining certain parts of their software or leave the project entirely. Another worry is that even if the code is being maintained, the company using the software might not update to the latest versions that are being put out.
Outdated software, whether it is from the contributors not maintaining their software, or the company not acquiring the new updates, can lead to significant security risks. When a new update of software comes out companies will often publicly post the bugs and issues they fixed, which is informing all attackers what was wrong with the older versions. Some people also believe that those contributing to OSS are often immature and have bad developer practices. If the contributors were to have bad coding habits they could cause a lot of vulnerabilities such as hardcoding credentials or improper error handling.
While these concerns hold some validity, discussions around OSS security often overlook that many of these risks also apply to proprietary software. Let's start with some security risks that don’t apply to proprietary software. An open code base is something unique to OSS, however, I believe that this aspect of OSS benefits its level of security more than it compromises it.
There is a law called Linus’s Law named after Linus Torvalds (The creator of Linux) that says “Many eyes make any bug shallow”. This law refers to the thought that with enough contributors and coding enthusiasts looking at your code, a small amount of them might try and exploit the vulnerabilities they find, but the majority will alert the developers or fix it themselves. I believe in this law and that with many eyes looking at a codebase, vulnerabilities are more likely to be found but also addressed and remediated quickly.
Another concern of those who feel that OSS is unsafe fear that companies may not keep up to date with the source code updates. Although this is a valid concern, it is not an issue with OSS, it is a problem with a company's internal processes. This should not be listed as a security concern of OSS because it is up to the individual to regularly update the newest software that is available.
All of these reasons for OSS being unsafe or safe can be debated and argued about, but physical data is much harder to ignore. The Coverity Scan Open Source Report is an annual report that analyzes the quality and security of OSS. This report states that the average OSS is of a higher quality than proprietary software. This data not only proves that contributors to OSS do not have bad coding habits, but it also proves that OSS, even though not perfect, is of a higher standard when it comes to security than proprietary software.
I believe the stigma that OSS is unsafe has limited the level of innovation and progress society has made in all realms of software. Who knows how many beneficial pieces of software could’ve been created if it weren't for this stigma, and how that software would affect the world?
The misconception that OSS is inherently unsafe has discouraged its adoption in many sectors, which limits opportunities for societal progress. This hesitancy has most likely curbed the development of groundbreaking solutions in areas like healthcare, education, and environmental sustainability, where open-source innovation could provide affordable and scalable tools for global challenges.
Addressing these misconceptions opens the door to greater innovation, allowing open-source communities to create secure, high-quality software that meets society's evolving needs.
2 notes
·
View notes
Text

The Comprehensive Guide to Web Development, Data Management, and More
Introduction
Everything today is technology driven in this digital world. There's a lot happening behind the scenes when you use your favorite apps, go to websites, and do other things with all of those zeroes and ones — or binary data. In this blog, I will be explaining what all these terminologies really means and other basics of web development, data management etc. We will be discussing them in the simplest way so that this becomes easy to understand for beginners or people who are even remotely interested about technology. JOIN US
What is Web Development?
Web development refers to the work and process of developing a website or web application that can run in a web browser. From laying out individual web page designs before we ever start coding, to how the layout will be implemented through HTML/CSS. There are two major fields of web development — front-end and back-end.
Front-End Development
Front-end development, also known as client-side development, is the part of web development that deals with what users see and interact with on their screens. It involves using languages like HTML, CSS, and JavaScript to create the visual elements of a website, such as buttons, forms, and images. JOIN US
HTML (HyperText Markup Language):
HTML is the foundation of all website, it helps one to organize their content on web platform. It provides the default style to basic elements such as headings, paragraphs and links.
CSS (Cascading Style Sheets):
styles and formats HTML elements. It makes an attractive and user-friendly look of webpage as it controls the colors, fonts, layout.
JavaScript :
A language for adding interactivity to a website Users interact with items, like clicking a button to send in a form or viewing images within the slideshow. JOIN US
Back-End Development
The difference while front-end development is all about what the user sees, back end involves everything that happens behind. The back-end consists of a server, database and application logic that runs on the web.
Server:
A server is a computer that holds website files and provides them to the user browser when they request it. Server-Side: These are populated by back-end developers who build and maintain servers using languages like Python, PHP or Ruby.
Database:
The place where a website keeps its data, from user details to content and settings The database is maintained with services like MySQL, PostgreSQL, or MongoDB. JOIN US
Application Logic —
the code that links front-end and back-end It takes user input, gets data from the database and returns right informations to front-end area.

Why Proper Data Management is Absolutely Critical
Data management — Besides web development this is the most important a part of our Digital World. What Is Data Management? It includes practices, policies and procedures that are used to collect store secure data in controlled way.
Data Storage –
data after being collected needs to be stored securely such data can be stored in relational databases or cloud storage solutions. The most important aspect here is that the data should never be accessed by an unauthorized source or breached. JOIN US
Data processing:
Right from storing the data, with Big Data you further move on to process it in order to make sense out of hordes of raw information. This includes cleansing the data (removing errors or redundancies), finding patterns among it, and producing ideas that could be useful for decision-making.
Data Security:
Another important part of data management is the security of it. It refers to defending data against unauthorized access, breaches or other potential vulnerabilities. You can do this with some basic security methods, mostly encryption and access controls as well as regular auditing of your systems.
Other Critical Tech Landmarks
There are a lot of disciplines in the tech world that go beyond web development and data management. Here are a few of them:
Cloud Computing
Leading by example, AWS had established cloud computing as the on-demand delivery of IT resources and applications via web services/Internet over a decade considering all layers to make it easy from servers up to top most layer. This will enable organizations to consume technology resources in the form of pay-as-you-go model without having to purchase, own and feed that infrastructure. JOIN US
Cloud Computing Advantages:
Main advantages are cost savings, scalability, flexibility and disaster recovery. Resources can be scaled based on usage, which means companies only pay for what they are using and have the data backed up in case of an emergency.
Examples of Cloud Services:
Few popular cloud services are Amazon Web Services (AWS), Microsoft Azure, and Google Cloud. These provide a plethora of services that helps to Develop and Manage App, Store Data etc.
Cybersecurity
As the world continues to rely more heavily on digital technologies, cybersecurity has never been a bigger issue. Protecting computer systems, networks and data from cyber attacks is called Cyber security.
Phishing attacks, Malware, Ransomware and Data breaches:
This is common cybersecurity threats. These threats can bear substantial ramifications, from financial damages to reputation harm for any corporation.
Cybersecurity Best Practices:
In order to safeguard against cybersecurity threats, it is necessary to follow best-practices including using strong passwords and two-factor authorization, updating software as required, training employees on security risks.
Artificial Intelligence and Machine Learning
Artificial Intelligence (AI) and Machine Learning (ML) represent the fastest-growing fields of creating systems that learn from data, identifying patterns in them. These are applied to several use-cases like self driving cars, personalization in Netflix.
AI vs ML —
AI is the broader concept of machines being able to carry out tasks in a way we would consider “smart”. Machine learning is a type of Artificial Intelligence (AI) that provides computers with the ability to learn without being explicitly programmed. JOIN US
Applications of Artificial Intelligence and Machine Learning: some common applications include Image recognition, Speech to text, Natural language processing, Predictive analytics Robotics.
Web Development meets Data Management etc.
We need so many things like web development, data management and cloud computing plus cybersecurity etc.. but some of them are most important aspects i.e. AI/ML yet more fascinating is where these fields converge or play off each other.
Web Development and Data Management
Web Development and Data Management goes hand in hand. The large number of websites and web-based applications in the world generate enormous amounts of data — from user interactions, to transaction records. Being able to manage this data is key in providing a fantastic user experience and enabling you to make decisions based on the right kind of information.
E.g. E-commerce Website, products data need to be saved on server also customers data should save in a database loosely coupled with orders and payments. This data is necessary for customization of the shopping experience as well as inventory management and fraud prevention.
Cloud Computing and Web Development
The development of the web has been revolutionized by cloud computing which gives developers a way to allocate, deploy and scale applications more or less without service friction. Developers now can host applications and data in cloud services instead of investing for physical servers.
E.g. A start-up company can use cloud services to roll out the web application globally in order for all users worldwide could browse it without waiting due unavailability of geolocation prohibited access.
The Future of Cybersecurity and Data Management
Which makes Cybersecurity a very important part of the Data management. The more data collected and stored by an organization, the greater a target it becomes for cyber threats. It is important to secure this data using robust cybersecurity measures, so that sensitive information remains intact and customer trust does not weaken. JOIN US
Ex: A healthcare provider would have to protect patient data in order to be compliant with regulations such as HIPAA (Health Insurance Portability and Accountability Act) that is also responsible for ensuring a degree of confidentiality between a provider and their patients.
Conclusion
Well, in a nutshell web-developer or Data manager etc are some of the integral parts for digital world.
As a Business Owner, Tech Enthusiast or even if you are just planning to make your Career in tech — it is important that you understand these. With the progress of technology never slowing down, these intersections are perhaps only going to come together more strongly and develop into cornerstones that define how we live in a digital world tomorrow.
With the fundamental knowledge of web development, data management, automation and ML you will manage to catch up with digital movements. Whether you have a site to build, ideas data to manage or simply interested in what’s hot these days, skills and knowledge around the above will stand good for changing tech world. JOIN US
#Technology#Web Development#Front-End Development#Back-End Development#HTML#CSS#JavaScript#Data Management#Data Security#Cloud Computing#AWS (Amazon Web Services)#Cybersecurity#Artificial Intelligence (AI)#Machine Learning (ML)#Digital World#Tech Trends#IT Basics#Beginners Guide#Web Development Basics#Tech Enthusiast#Tech Career#america
4 notes
·
View notes
Text
What is ISO 27017 Compliance and It’s Role in Cloud Security?
ISO 27017: 2015 standard is a comprehensive framework for cloud security that focuses on providing guidance for information technology controls and security techniques specifically tailored for cloud services. It offers additional controls beyond those in ISO/IEC 27002, with a total of 37 controls based on ISO 27002 and 7 exclusive controls.
2 notes
·
View notes
Text

Summer Internship Program 2024
For More Details Visit Our Website - internship.learnandbuild.in
#machine learning#programming#python#linux#data science#data scientist#frontend web development#backend web development#salesforce admin#salesforce development#cloud AI with AWS#Internet of things & AI#Cyber security#Mobile App Development using flutter#data structures & algorithms#java core#python programming#summer internship program#summer internship program 2024
2 notes
·
View notes
Text
Cloud and Data: A sidewalk!
In a world where 10 million data generate each hour, is there any business identity without data? Apart from the hypothetical world that pushes businesses to adopt a plan that is enriched towards an unattainable goal for objectives stepping forward through the wave of optimism, can any spectrum of business meet the goal without a shower of data?
Read the full blog.
2 notes
·
View notes
Text
Sigzen Technologies: Transforming Challenges into Opportunities with Robust Backup and Disaster Recovery Solutions
In today’s fast-paced digital world, where data plays a crucial role in business operations, having a reliable Backup Solution and Disaster Recovery plan is paramount. Sigzen Technologies emerges as a leader in this space, offering cutting-edge solutions that not only safeguard critical data but also transform challenges into opportunities for businesses. Automated Backup An automated backup…

View On WordPress
#Business Continuity Strategies#Cloud Backup Excellence#Data Protection Standards#Data Security Leaders#Sigzen Tech Solutions
2 notes
·
View notes
Text
A Complete Guide to Mastering Microsoft Azure for Tech Enthusiasts
With this rapid advancement, businesses around the world are shifting towards cloud computing to enhance their operations and stay ahead of the competition. Microsoft Azure, a powerful cloud computing platform, offers a wide range of services and solutions for various industries. This comprehensive guide aims to provide tech enthusiasts with an in-depth understanding of Microsoft Azure, its features, and how to leverage its capabilities to drive innovation and success.
Understanding Microsoft Azure
A platform for cloud computing and service offered through Microsoft is called Azure. It provides reliable and scalable solutions for businesses to build, deploy, and manage applications and services through Microsoft-managed data centers. Azure offers a vast array of services, including virtual machines, storage, databases, networking, and more, enabling businesses to optimize their IT infrastructure and accelerate their digital transformation.
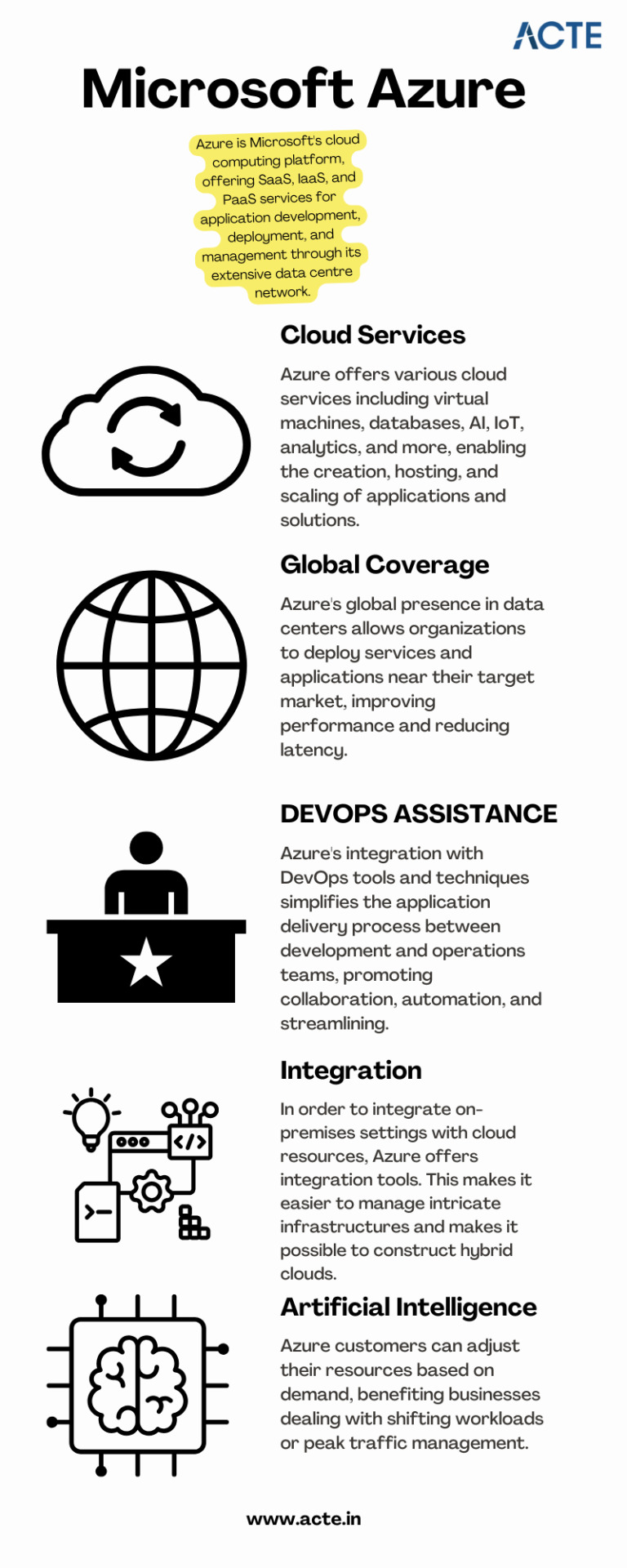
Cloud Computing and its Significance
Cloud computing has revolutionized the IT industry by providing on-demand access to a shared pool of computing resources over the internet. It eliminates the need for businesses to maintain physical hardware and infrastructure, reducing costs and improving scalability. Microsoft Azure embraces cloud computing principles to enable businesses to focus on innovation rather than infrastructure management.
Key Features and Benefits of Microsoft Azure
Scalability: Azure provides the flexibility to scale resources up or down based on workload demands, ensuring optimal performance and cost efficiency.
Vertical Scaling: Increase or decrease the size of resources (e.g., virtual machines) within Azure.
Horizontal Scaling: Expand or reduce the number of instances across Azure services to meet changing workload requirements.
Reliability and Availability: Microsoft Azure ensures high availability through its globally distributed data centers, redundant infrastructure, and automatic failover capabilities.
Service Level Agreements (SLAs): Guarantees high availability, with SLAs covering different services.
Availability Zones: Distributes resources across multiple data centers within a region to ensure fault tolerance.
Security and Compliance: Azure incorporates robust security measures, including encryption, identity and access management, threat detection, and regulatory compliance adherence.
Azure Security Center: Provides centralized security monitoring, threat detection, and compliance management.
Compliance Certifications: Azure complies with various industry-specific security standards and regulations.
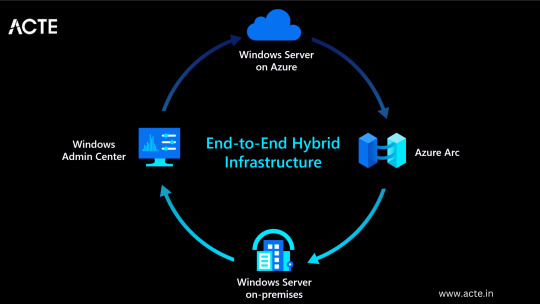
Hybrid Capability: Azure seamlessly integrates with on-premises infrastructure, allowing businesses to extend their existing investments and create hybrid cloud environments.
Azure Stack: Enables organizations to build and run Azure services on their premises.
Virtual Network Connectivity: Establish secure connections between on-premises infrastructure and Azure services.
Cost Optimization: Azure provides cost-effective solutions, offering pricing models based on consumption, reserved instances, and cost management tools.
Azure Cost Management: Helps businesses track and optimize their cloud spending, providing insights and recommendations.
Azure Reserved Instances: Allows for significant cost savings by committing to long-term usage of specific Azure services.
Extensive Service Catalog: Azure offers a wide range of services and tools, including app services, AI and machine learning, Internet of Things (IoT), analytics, and more, empowering businesses to innovate and transform digitally.
Learning Path for Microsoft Azure
To master Microsoft Azure, tech enthusiasts can follow a structured learning path that covers the fundamental concepts, hands-on experience, and specialized skills required to work with Azure effectively. I advise looking at the ACTE Institute, which offers a comprehensive Microsoft Azure Course.

Foundational Knowledge
Familiarize yourself with cloud computing concepts, including Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS).
Understand the core components of Azure, such as Azure Resource Manager, Azure Virtual Machines, Azure Storage, and Azure Networking.
Explore Azure architecture and the various deployment models available.
Hands-on Experience
Create a free Azure account to access the Azure portal and start experimenting with the platform.
Practice creating and managing virtual machines, storage accounts, and networking resources within the Azure portal.
Deploy sample applications and services using Azure App Services, Azure Functions, and Azure Containers.
Certification and Specializations
Pursue Azure certifications to validate your expertise in Azure technologies. Microsoft offers role-based certifications, including Azure Administrator, Azure Developer, and Azure Solutions Architect.
Gain specialization in specific Azure services or domains, such as Azure AI Engineer, Azure Data Engineer, or Azure Security Engineer. These specializations demonstrate a deeper understanding of specific technologies and scenarios.
Best Practices for Azure Deployment and Management
Deploying and managing resources effectively in Microsoft Azure requires adherence to best practices to ensure optimal performance, security, and cost efficiency. Consider the following guidelines:
Resource Group and Azure Subscription Organization
Organize resources within logical resource groups to manage and govern them efficiently.
Leverage Azure Management Groups to establish hierarchical structures for managing multiple subscriptions.
Security and Compliance Considerations
Implement robust identity and access management mechanisms, such as Azure Active Directory.
Enable encryption at rest and in transit to protect data stored in Azure services.
Regularly monitor and audit Azure resources for security vulnerabilities.
Ensure compliance with industry-specific standards, such as ISO 27001, HIPAA, or GDPR.
Scalability and Performance Optimization
Design applications to take advantage of Azure’s scalability features, such as autoscaling and load balancing.
Leverage Azure CDN (Content Delivery Network) for efficient content delivery and improved performance worldwide.
Optimize resource configurations based on workload patterns and requirements.
Monitoring and Alerting
Utilize Azure Monitor and Azure Log Analytics to gain insights into the performance and health of Azure resources.
Configure alert rules to notify you about critical events or performance thresholds.
Backup and Disaster Recovery
Implement appropriate backup strategies and disaster recovery plans for essential data and applications.
Leverage Azure Site Recovery to replicate and recover workloads in case of outages.
Mastering Microsoft Azure empowers tech enthusiasts to harness the full potential of cloud computing and revolutionize their organizations. By understanding the core concepts, leveraging hands-on practice, and adopting best practices for deployment and management, individuals become equipped to drive innovation, enhance security, and optimize costs in a rapidly evolving digital landscape. Microsoft Azure’s comprehensive service catalog ensures businesses have the tools they need to stay ahead and thrive in the digital era. So, embrace the power of Azure and embark on a journey toward success in the ever-expanding world of information technology.
#microsoft azure#cloud computing#cloud services#data storage#tech#information technology#information security
6 notes
·
View notes
Text
Cyber Security Services Company | Data Security Solutions

In today’s fast-paced digital world, businesses increasingly rely on technology to store, process, and transmit sensitive data. As companies across industries harness the power of the internet, the need for robust cybersecurity services has never been more crucial. Data breaches and cyberattacks are growing threats from small startups to large corporations that can have devastating consequences. That’s where a cybersecurity company specializing in data protection services and cybersecurity management comes into play.
This blog explores the importance of cybersecurity management, the types of services offered by a cybersecurity services company, and how data protection services and endpoint security services can help businesses protect their sensitive information.
Understanding the Growing Importance of Cybersecurity
The digital transformation that businesses have undergone in recent years has revolutionized operations, providing significant benefits like improved efficiency, better customer engagement, and more streamlined processes. However, this transformation has also opened new doors for cybercriminals who exploit vulnerabilities in systems and networks to steal data, launch attacks, and disrupt operations.
With data breaches and cyberattacks on the rise, organizations must safeguard sensitive information from unauthorized access, manipulation, and theft. Whether it’s customer data, intellectual property, or financial records, securing these assets is paramount to maintaining trust, compliance with regulations, and protecting brand reputation.
Cybersecurity solutions providers play a key role in defending organizations from these threats. Cybersecurity isn’t just a technical need—it’s a business priority that can help prevent costly disruptions, legal ramifications, and loss of customer confidence. This is where the role of a cybersecurity consulting firm becomes indispensable.
What Is a Cybersecurity Services Company?
A cybersecurity services company specializes in identifying, mitigating, and preventing cyber threats. They provide tailored solutions to ensure businesses’ information and infrastructure are well-protected from a wide range of security risks. These companies are essential partners in safeguarding businesses from cyberattacks and ensuring the security of sensitive data and systems.
Key Services Provided by a Cybersecurity Services Company

Cybersecurity companies offer a range of services designed to safeguard businesses from evolving threats. These services include:
Threat Detection & Prevention Services: Cybersecurity companies deploy advanced monitoring tools and techniques to detect vulnerabilities, anomalous activities, and potential threats before they cause harm. This includes setting up firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS).
Risk Management: Cybersecurity firms assess vulnerabilities and design strategies to safeguard businesses from both internal and external threats. A cyber risk management company helps ensure that businesses are prepared for any potential cyber risks.
Cybersecurity Audits & Assessments: Regular security audits and penetration testing are vital for identifying weaknesses in a company’s infrastructure. These audits ensure no part of the system remains unprotected.
Compliance Support: For businesses in regulated industries, cybersecurity compliance services help ensure adherence to standards like GDPR, HIPAA, and PCI DSS. Companies in these industries can also benefit from IT security services companies that provide guidance and support for meeting compliance requirements.
Incident Response & Disaster Recovery: Even with robust security measures, breaches can still occur. Incident response services help businesses respond quickly and effectively to limit damage. Additionally, cybersecurity audit services and vulnerability assessment companies help identify and prevent potential attacks before they materialize.
Employee Training & Awareness: Cybersecurity management companies often provide training programs to raise awareness about phishing, password hygiene, and safe online behavior, reducing human error and improving security.
Types of Data Security Solutions Offered by Cybersecurity Companies

At the core of every cybersecurity service is data protection. Cybersecurity solutions providers offer several key solutions to help businesses secure their information:
Encryption: Encryption ensures that even if data is accessed by cybercriminals, it remains unreadable without the decryption key. Cloud security companies offer encryption solutions to protect data stored in the cloud, safeguarding sensitive information during transit and while at rest.
Access Control & Authentication: Multi-factor authentication (MFA) and role-based access control (RBAC) are implemented to ensure only authorized personnel can access sensitive systems.
Data Loss Prevention (DLP): Data protection services monitor data transfers and emails to prevent unauthorized sharing or leakage of confidential information.
Firewalls & Network Security: Firewalls act as the first line of defense by filtering traffic and blocking harmful activities. Network security services providers ensure that your network is properly configured with firewalls, VPNs, and network segmentation to protect data from external attacks.
Backup & Disaster Recovery: A comprehensive backup and recovery plan ensures that lost or compromised data can be restored with minimal disruption to business operations. Cloud security companies play a key role in providing reliable cloud-based backup and recovery services.
Endpoint Security: With more employees working remotely, endpoint security services are becoming essential. Cybersecurity firms implement solutions to protect mobile devices, laptops, and tablets from threats.
Why Partner with a Cybersecurity Services Company?
Businesses of all sizes can benefit from the specialized expertise of a cybersecurity consulting firm. Here are some reasons why partnering with one is essential:
Expertise and Experience
Cybersecurity is a complex field requiring in-depth knowledge of emerging threats and security solutions. A cybersecurity services company brings years of experience and expertise to the table, ensuring best practices and cutting-edge tools are used to protect your data.
Cost Efficiency
Building an in-house cybersecurity team can be costly. By outsourcing to a cybersecurity solutions provider, businesses gain access to expert resources and advanced technologies without the need to invest in full-time staff.
Proactive Protection
Rather than waiting for a breach to occur, a cybersecurity management company helps you adopt a proactive approach by identifying and neutralizing potential threats before they can impact your business.
Regulatory Compliance
Staying compliant with regulations like GDPR, HIPAA, and CCPA can be challenging. A cybersecurity services company ensures your business complies with relevant data protection laws, avoiding legal complications and fines. These companies provide cybersecurity compliance services to meet the highest standards of data protection.
Business Continuity
Cybersecurity services also encompass disaster recovery planning, ensuring that your business can continue to operate smoothly after a cyber attack or natural disaster. Security operations center services ensure continuous monitoring, offering peace of mind that any security breaches are quickly detected and neutralized.
Conclusion: Protect Your Business with a Cybersecurity Services Company
As cyber threats continue to evolve, businesses must take proactive steps to protect their sensitive data and maintain customer trust. Partnering with a reputable cybersecurity consulting firm ensures that you have the right tools, expertise, and strategies in place to prevent cyberattacks, secure your data, and maintain regulatory compliance.
Whether it’s through penetration testing, endpoint security services, or incident response services, a cybersecurity services company plays a crucial role in keeping your data safe and your business running smoothly.
Investing in cybersecurity solutions today can help prevent significant financial and reputational damage in the future. Don't wait until it's too late—reach out to a trusted cybersecurity services company today to protect your data and your business's future.
#Cyber Security Services Company | Data Security Solutions#Cybersecurity Management Company#Managed Cyber Security Services#Cyber Security Company#Cyber Security Services#Endpoint Security Services#Cybersecurity Solutions Provider#Cyber Security Consulting Firm#Network Security Services#Cybersecurity Audit Services#IT Security Services Company#Cloud Security Company#Data Protection Services#Cybersecurity Compliance Services#Security Operations Center Services#Threat Detection Services#Penetration Testing Company#Incident Response Services#Vulnerability Assessment Company#Cyber Risk Management Company#Information Security Services
0 notes
Text
Python Courses in Ahmedabad with Weekend & Part-Time Options for Working Experts
In a fast-growing tech world, learning Python is necessary for working professionals who want to be trained without sacrificing their primary job duties. Thus, flexible study options are available in Ahmedabad for those who wish to learn Python over the weekend or part-time.
Flexible education options are tailored to fit specific time schedules for full-time professionals and the many commitments they must manage personally. Whether you are looking to get into a career in technology or just attempting to upgrade your skills, weekend and part-time courses in Python can provide just the flexible direction your career needs without sacrificing time management.
Well-structured modules, practical projects, and high-industry relevance help learners to gradually improve their programming skills while not having to disrupt their weekly routines.
Learn Basic Skills from Python Courses in Ahmedabad
Weekend and Part-Time Python Courses in Ahmedabad would be suitable for beginners who are interested in establishing a strong programming background. This straightforward course encompasses the significant concepts of variables, loops, functions, and OOP. An industry-oriented teaching approach would enable the students to implement knowledge in practice and develop applications of a real-time nature.
Get Certified by Enrolling in Python Enhancement Training Within Ahmedabad
The individual professional would now be easily trained through structured Python Training in Ahmedabad while certainly granting it more than an advanced exposure to rigorous topics, such as data analysis, API connection, and even foundational frameworks. This enables the already-presented knowledge of Python to students and professionals who want to improve their problem-solving and development skills.
Obtain Real-world Experience through a Python Internship in Ahmedabad
So, collecting solid credentials might be a good idea for registering for a Python Internship in Ahmedabad. Internships take someone through the project-based training model, imitating work conditions. There, trainees apply what they have learned in the classroom to real-life problems, thus gaining confidence and preparation for the industry.
Why Opt for Weekend and Part-Time Learning?
Weekend and part-time courses are the best options for one who is an employee. It gives the possibility to take some commitment time off so that a certain amount of time may be used to obtain any new skill while still keeping a part of the work commitment. Such learning does not have a time-honoured, rigidly scheduled learning process for a student.
The weekend and part-time, flexible Python course is a brilliant opportunity for professionals in Ahmedabad who are seeking to enhance their skills without the interruption of their careers. Whether you wish to begin from scratch or are keen to improve your programming skills, this type of course offers the most essential practical knowledge and support in the modern tech-driven world. Step forward in your career by availing of training from experts; visit Highsky IT Solutions and enrol today.
#linux certification ahmedabad#red hat certification ahmedabad#linux online courses in ahmedabad#data science training ahmedabad#rhce rhcsa training ahmedabad#aws security training ahmedabad#docker training ahmedabad#red hat training ahmedabad#microsoft azure cloud certification#python courses in ahmedabad
0 notes
Text
Top Certifications That Can Land You a Job in Tech
Published by Prism HRC – Leading IT Recruitment Agency in Mumbai
Breaking into the tech industry doesn’t always require a degree. With the rise of online learning and skill-based hiring, certifications have become the new ticket into some of the highest-paying and most in-demand jobs. Whether you're switching careers or upskilling to stay ahead, the right certification can boost your credibility and fast-track your job search.
Why Certifications Matter in Tech
Tech employers today are less focused on your college background and more interested in what you can actually do. Certifications show you're committed, skilled, and up-to-date with industry trends a huge plus in a fast-moving field like IT.
Let’s explore the top certifications in 2025 that are actually helping people land real tech jobs.

1. Google IT Support Professional Certificate
Perfect for: Beginners starting in tech or IT support This beginner-friendly course, offered through Coursera, teaches you everything from troubleshooting to networking. It’s backed by Google and respected across the industry.
Tip: It’s also a great way to pivot into other IT roles, including cybersecurity and network administration.
2. AWS Certified Solutions Architect – Associate
Perfect for: Cloud engineers, DevOps aspirants With cloud computing continuing to explode in 2025, AWS skills are hotter than ever. This cert proves you know how to design secure, scalable systems on the world’s most popular cloud platform.
Real Edge: Many employers prioritize candidates with AWS experience even over degree holders.
3. Microsoft Certified: Azure Fundamentals
Perfect for: Beginners interested in Microsoft cloud tools Azure is a close second to AWS in the cloud market. If you’re looking for a job at a company that uses Microsoft services, this foundational cert gives you a leg up.
4. CompTIA Security+
Perfect for: Cybersecurity beginners If you're aiming for a job in cybersecurity, this is often the first certification employers look for. It covers basic network security, risk management, and compliance.
Why it matters: As cyber threats grow, demand for cybersecurity professionals is rising rapidly.
5. Google Data Analytics Professional Certificate
Perfect for: Aspiring data analysts This course teaches data analysis, spreadsheets, SQL, Tableau, and more. It’s beginner-friendly and widely accepted by tech companies looking for entry-level analysts.
Industry Insight: Data skills are now essential across tech, not just for analysts, but for marketers, product managers, and more.
6. Certified ScrumMaster (CSM)
Perfect for: Project managers, product managers, team leads Tech teams often use Agile frameworks like Scrum. This certification helps you break into roles where communication, leadership, and sprint planning are key.
7. Cisco Certified Network Associate (CCNA)
Perfect for: Network engineers, IT support, and infrastructure roles If you’re into hardware, routers, switches, and network troubleshooting, this foundational cert is gold.
Why it helps: Many entry-level IT jobs prefer CCNA holders over generalists.

8. Meta (Facebook) Front-End Developer Certificate
Perfect for: Front-end developers and web designers This cert teaches HTML, CSS, React, and design systems. It’s hands-on and offered via Coursera in partnership with Meta.
The bonus? You also get portfolio projects to show in interviews.
How to Choose the Right Certification
Match it to your career goal – Don't do a cert just because it’s popular. Focus on the role you want.
Check job listings – Look at what certifications are frequently mentioned.
Time vs Value – Some certs take weeks, others months. Make sure the ROI is worth it.
- Based in Gorai-2, Borivali West, Mumbai - www.prismhrc.com - Instagram: @jobssimplified - LinkedIn: Prism HRC
#Tech Certifications#IT Jobs#Top Certifications 2025#Cloud Computing#Cybersecurity#Data Analytics#AWS Certification#Microsoft Azure#CompTIA Security+#Prism HRC#IT Recruitment#Mumbai IT#Skill-Based Hiring#Future of Tech#Mumbai IT Jobs#Google IT Support#Google Data Analytics
0 notes
Text
Trending Final Year Projects for 2025
Choose from the latest and most in-demand project topics across engineering and technology domains.
#cyber security projects for final year students#cyber security projects for final year#web development projects for final year#final year projects for cse#python projects for final year students#network security projects for final year students#cyber security final year project#data science final year projects#app development projects for final year#cloud computing projects for final year students#best web development projects for final year students#web development project for final year#final year project for cyber security#cloud computing final year project#aws projects for final year github#best computer science projects for final year#best computer science final year projects#best final year projects for it students#best major project for cse#best project for computer science final year#best projects for it final year#best python projects for final year students#cloud based final year projects#cloud computing based projects for final year#cloud computing projects final year#cloud projects for final year students
0 notes
Text
The advantages of Computer Networks: Enhancing Connectivity & Efficiency
Computer networks form the backbone of modern communication, business operations, and data management, enabling seamless connectivity and resource sharing. Whether in workplaces, homes, or global enterprises, networking has transformed the way we exchange information. Here’s why computer networks are essential for efficiency, security, and collaboration. 1. Seamless Communication &…
#business connectivity#cloud storage solutions#computer networking benefits#digital collaboration#IT infrastructure efficiency#network performance optimization#secure data sharing
1 note
·
View note
Text
Cloud Data Security Market Size, Share, Industry Outlook & Forecast to 2032

The Cloud Data Security Market size was valued at USD 33.39 Billion in 2023 and is expected to reach USD 117.62 Billion by 2032, growing at a CAGR of 15.04% over the forecast period 2024-2032.
The global cloud data security market is undergoing a transformative shift as organizations accelerate digital transformation and embrace hybrid cloud architectures. As cyber threats become increasingly sophisticated, enterprises are investing in cloud-native security solutions to safeguard sensitive data and ensure regulatory compliance. With the expansion of remote work, the demand for scalable and agile data protection strategies has intensified, propelling growth across industries such as banking, healthcare, and retail.
Cloud Data Security Market Poised for Strategic Advancements Rapid innovations in artificial intelligence, machine learning, and encryption technologies are fueling a new era in cloud data security. Enterprises are transitioning from traditional perimeter-based defenses to dynamic, identity-centric models that offer greater resilience and adaptability. This evolution is supported by the proliferation of multi-cloud environments, which require robust security frameworks capable of managing complex data flows and access points without compromising performance or user experience.
Get Sample Copy of This Report: https://www.snsinsider.com/sample-request/3636
Market Keyplayers:
Cloud Passage Inc. (Halo, Halo for AWS)
Intel Corporation (Intel Security, Intel vPro)
Sophos Ltd. (Sophos Cloud Optix, Sophos XG Firewall)
Fortinet, Inc. (FortiGate, FortiCloud)
IBM Corporation (IBM Cloud Security, IBM QRadar)
Cisco Systems, Inc. (Cisco Umbrella, Cisco Cloudlock)
Symantec Corporation (Symantec Data Loss Prevention, Symantec Cloud Security)
Trend Micro, Inc. (Trend Micro Cloud One, Trend Micro Deep Security)
Panda Security (Panda Adaptive Defense, Panda Cloud Office Protection)
CA Technologies, Inc. (CA Privileged Access Manager, CA Security Event Manager)
McAfee (McAfee MVISION Cloud, McAfee Cloud Workload Security)
Microsoft (Microsoft Defender for Identity, Microsoft Azure Security Center)
Vormetric (a Thales company) (Vormetric Data Security Platform, Vormetric Transparent Encryption)
Check Point Software Technologies (CloudGuard, Check Point Threat Emulation)
Forcepoint (Forcepoint Data Loss Prevention, Forcepoint Cloud Security)
Palo Alto Networks (Prisma Cloud, Cortex XSOAR)
Zscaler (Zscaler Internet Access, Zscaler Private Access)
Okta (Okta Identity Cloud, Okta Adaptive MFA)
Rapid7 (InsightCloudSec, InsightIDR)
Imperva (Cloud WAF, Imperva Data Security)
Market Analysis
The cloud data security market is characterized by a highly competitive landscape featuring both established cybersecurity providers and emerging startups. Strategic alliances, mergers, and acquisitions are shaping the trajectory of the market, as companies seek to integrate advanced security features such as automated threat detection, behavioral analytics, and zero-trust architecture. The increasing stringency of global data protection laws is compelling organizations to invest in compliance-driven security solutions tailored to regional regulatory frameworks.
As businesses adopt Infrastructure-as-a-Service (IaaS) and Software-as-a-Service (SaaS) models, cloud security is no longer an optional component but a critical enabler of trust and operational continuity. The integration of DevSecOps practices further emphasizes security as a core part of the software development lifecycle, fostering a proactive rather than reactive security posture.
Market Trends
Surge in demand for cloud-native security solutions to secure hybrid and multi-cloud infrastructures
Rising adoption of Zero Trust security frameworks for identity and access management
Growth in AI- and ML-powered threat detection and automated response mechanisms
Emphasis on data sovereignty and localized cloud security compliance measures
Expansion of DevSecOps practices integrating security at every stage of development
Increased focus on Secure Access Service Edge (SASE) to unify networking and security
Rapid evolution of encryption standards for data-at-rest, in-transit, and in-use
Greater investment in secure collaboration tools for remote workforce protection
Market Scope
The scope of the cloud data security market extends across a wide array of sectors including finance, healthcare, IT, telecommunications, manufacturing, and government. Enterprises are seeking end-to-end encryption, secure access control, and continuous monitoring solutions that align with their digital maturity. As cloud adoption reaches new heights, vendors are scaling offerings to support diverse workloads, APIs, and third-party integrations. The market also encompasses cloud security posture management (CSPM), data loss prevention (DLP), and cloud access security broker (CASB) technologies, collectively fortifying organizational resilience in an increasingly hostile cyber landscape.
Market Forecast
Over the forecast period, the cloud data security market is expected to maintain robust momentum, driven by technological innovations and the global push toward data-centric digital ecosystems. Cloud security will increasingly become embedded within broader digital transformation strategies, with providers focusing on intuitive, automated, and scalable platforms. Organizations will continue prioritizing investments in user behavior analytics, micro-segmentation, and unified threat management to preempt breaches and maintain trust. With the convergence of networking and security under cloud-native frameworks, the market is poised to evolve beyond traditional paradigms into a new standard of digital trust infrastructure.
Access Complete Report: https://www.snsinsider.com/reports/cloud-data-security-market-3636
Conclusion
The future of cloud data security is not just about protecting data—it’s about enabling digital confidence in a rapidly evolving business landscape. As enterprises redefine their digital blueprints, security leaders are called to align protection with innovation, ensuring that cloud adoption drives growth without compromising integrity. This dynamic market offers not only challenges but also immense opportunities for vendors and enterprises ready to invest in resilient, intelligent, and future-forward security architectures.
About Us:
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Contact Us:
Jagney Dave - Vice President of Client Engagement
Phone: +1-315 636 4242 (US) | +44- 20 3290 5010 (UK)
0 notes