#secure data sharing
Explore tagged Tumblr posts
Text
The advantages of Computer Networks: Enhancing Connectivity & Efficiency
Computer networks form the backbone of modern communication, business operations, and data management, enabling seamless connectivity and resource sharing. Whether in workplaces, homes, or global enterprises, networking has transformed the way we exchange information. Here’s why computer networks are essential for efficiency, security, and collaboration. 1. Seamless Communication &…
#business connectivity#cloud storage solutions#computer networking benefits#digital collaboration#IT infrastructure efficiency#network performance optimization#secure data sharing
0 notes
Text
Unity Catalog: Unlocking Powerful Advanced Data Control in Databricks
Harness the power of Unity Catalog within Databricks and elevate your data governance to new heights. Our latest blog post, "Unity Catalog: Unlocking Advanced Data Control in Databricks," delves into the cutting-edge features
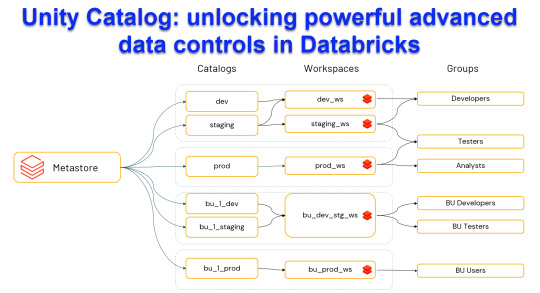
View On WordPress
#Advanced Data Security#Automated Data Lineage#Cloud Data Governance#Column Level Masking#Data Discovery and Cataloging#Data Ecosystem Security#Data Governance Solutions#Data Management Best Practices#Data Privacy Compliance#Databricks Data Control#Databricks Delta Sharing#Databricks Lakehouse Platform#Delta Lake Governance#External Data Locations#Managed Data Sources#Row Level Security#Schema Management Tools#Secure Data Sharing#Unity Catalog Databricks#Unity Catalog Features
0 notes
Text
KOSA COPYCAT BILL INTRODUCED IN AUSTRALIA
If you know anybody in Australia that uses the internet, spread the word immediately! Do everything in your power to make your voice heard!
#fuck kosa#stop kosa#austrailia#australian politics#internet privacy#internet censorship#data security#freeinternet#free speech#freedom of speech#plz reblog#please repost#please share#reblog this#signal boost
121 notes
·
View notes
Text
had to get a new phone and im pretty sure setting it up is going to make me become the Joker
#i dont have the energy to elaborately rant rn but You Know What I Mean#it comes with almost 20GB of undeletable predownloaded bloatware and does not even have a notes app#and all the notes apps immediately available are either paid subscriptions (??)#or have a blatant security flag for collecting and third-party sharing personal data up to and including location (???)#this is going to affect the trout population
5 notes
·
View notes
Text
Elevate Client Services with Excel: Expert Tips for Financial Consultants by Grayson Garelick

Financial consultants operate in a dynamic environment where precision, efficiency, and client satisfaction are paramount. Excel, as a versatile tool, offers an array of features that can significantly enhance the services provided by financial consultants. Grayson Garelick, an accomplished financial analyst and consultant, shares invaluable Excel tips to help financial consultants elevate their client services and add tangible value.
The Role of Excel in Financial Consulting
Excel serves as the backbone of financial consulting, enabling consultants to analyze data, create models, and generate insights that drive informed decision-making. As the demands of clients become increasingly complex, mastering Excel becomes essential for financial consultants aiming to deliver exceptional services.
1. Customize Excel Templates
One of the most effective ways to streamline workflows and improve efficiency is by creating customized Excel templates tailored to specific client needs. Grayson suggests developing templates for budgeting, forecasting, and financial reporting that can be easily adapted for different clients, saving time and ensuring consistency.
2. Utilize PivotTables for Data Analysis
PivotTables are powerful tools in Excel that allow financial consultants to analyze large datasets and extract meaningful insights quickly. Grayson emphasizes the importance of mastering PivotTables for segmenting data, identifying trends, and presenting information in a clear and concise manner to clients.
3. Implement Conditional Formatting
Conditional formatting is a valuable feature in Excel that allows consultants to highlight important information and identify outliers effortlessly. By setting up conditional formatting rules, consultants can draw attention to key metrics, discrepancies, or trends, facilitating easier interpretation of data by clients.
4. Leverage Excel Add-ins
Excel offers a variety of add-ins that extend its functionality and provide additional features tailored to financial analysis and reporting. Grayson recommends exploring add-ins such as Power Query, Power Pivot, and Solver to enhance data manipulation, modeling, and optimization capabilities.
5. Automate Repetitive Tasks with Macros
Macros enable financial consultants to automate repetitive tasks and streamline workflows, saving valuable time and reducing the risk of errors. Grayson advises recording and editing macros to automate tasks such as data entry, formatting, and report generation, allowing consultants to focus on value-added activities.
6. Master Advanced Formulas and Functions
Excel's extensive library of formulas and functions offers endless possibilities for financial analysis and modeling. Grayson suggests mastering advanced formulas such as VLOOKUP, INDEX-MATCH, and array formulas to perform complex calculations, manipulate data, and create sophisticated models tailored to client needs.
7. Visualize Data with Charts and Graphs
Visualizing data is essential for conveying complex information in an easily digestible format. Excel offers a variety of chart types and customization options that enable consultants to create compelling visuals that resonate with clients. Grayson recommends experimenting with different chart styles to find the most effective way to present data and insights.
8. Collaborate and Share Workbooks Online
Excel's collaboration features enable financial consultants to work seamlessly with clients, colleagues, and stakeholders in real-time. Grayson highlights the benefits of sharing workbooks via OneDrive or SharePoint, allowing multiple users to collaborate on the same document, track changes, and maintain version control.
9. Protect Sensitive Data with Security Features
Data security is a top priority for financial consultants handling sensitive client information. Excel's built-in security features, such as password protection and encryption, help safeguard confidential data and ensure compliance with regulatory requirements. Grayson advises implementing security protocols to protect client data and maintain trust.
10. Stay Updated with Excel Training and Certification
Excel is a constantly evolving tool, with new features and updates released regularly. Grayson stresses the importance of staying updated with the latest Excel training and certification programs to enhance skills, explore new capabilities, and maintain proficiency in Excel's ever-changing landscape.
Elevating Client Services with Excel Mastery
Excel serves as a catalyst for innovation and excellence in financial consulting, empowering consultants to deliver exceptional services that add tangible value to clients. By implementing Grayson Garelick Excel tips, financial consultants can streamline workflows, enhance data analysis capabilities, and foster collaboration, ultimately driving client satisfaction and success. As financial consulting continues to evolve, mastering Excel remains a cornerstone of excellence, enabling consultants to thrive in a competitive landscape and exceed client expectations.
#Financial Consulting#grayson garelick#Customize Excel Templates#Utilize PivotTables#Implement Conditional Formatting#Leverage Excel Add-ins#Automate Repetitive Tasks with Macros#Advanced Formulas and Functions#Visualize Data with Charts and Graphs#Collaborate and Share Workbooks#Protect Sensitive Data with Security#Stay Updated with Excel Training#Elevating Client Services with Excel
3 notes
·
View notes
Text
Nope now it’s at the point that i’m shocked that people off tt don’t know what’s going down. I have no reach but i’ll sum it up anyway.
SCOTUS is hearing on the constitutionality of the ban as tiktok and creators are arguing that it is a violation of our first amendment rights to free speech, freedom of the press and freedom to assemble.
SCOTUS: tiktok bad, big security concern because china bad!
Tiktok lawyers: if china is such a concern why are you singling us out? Why not SHEIN or temu which collect far more information and are less transparent with their users?
SCOTUS (out loud): well you see we don’t like how users are communicating with each other, it’s making them more anti-american and china could disseminate pro china propaganda (get it? They literally said they do not like how we Speak or how we Assemble. Independent journalists reach their audience on tt meaning they have Press they want to suppress)
Tiktok users: this is fucking bullshit i don’t want to lose this community what should we do? We don’t want to go to meta or x because they both lobbied congress to ban tiktok (free market capitalism amirite? Paying off your local congressmen to suppress the competition is totally what the free market is about) but nothing else is like TikTok
A few users: what about xiaohongshu? It’s the Chinese version of tiktok (not quite, douyin is the chinese tiktok but it’s primarily for younger users so xiaohongshu was chosen)
16 hours later:
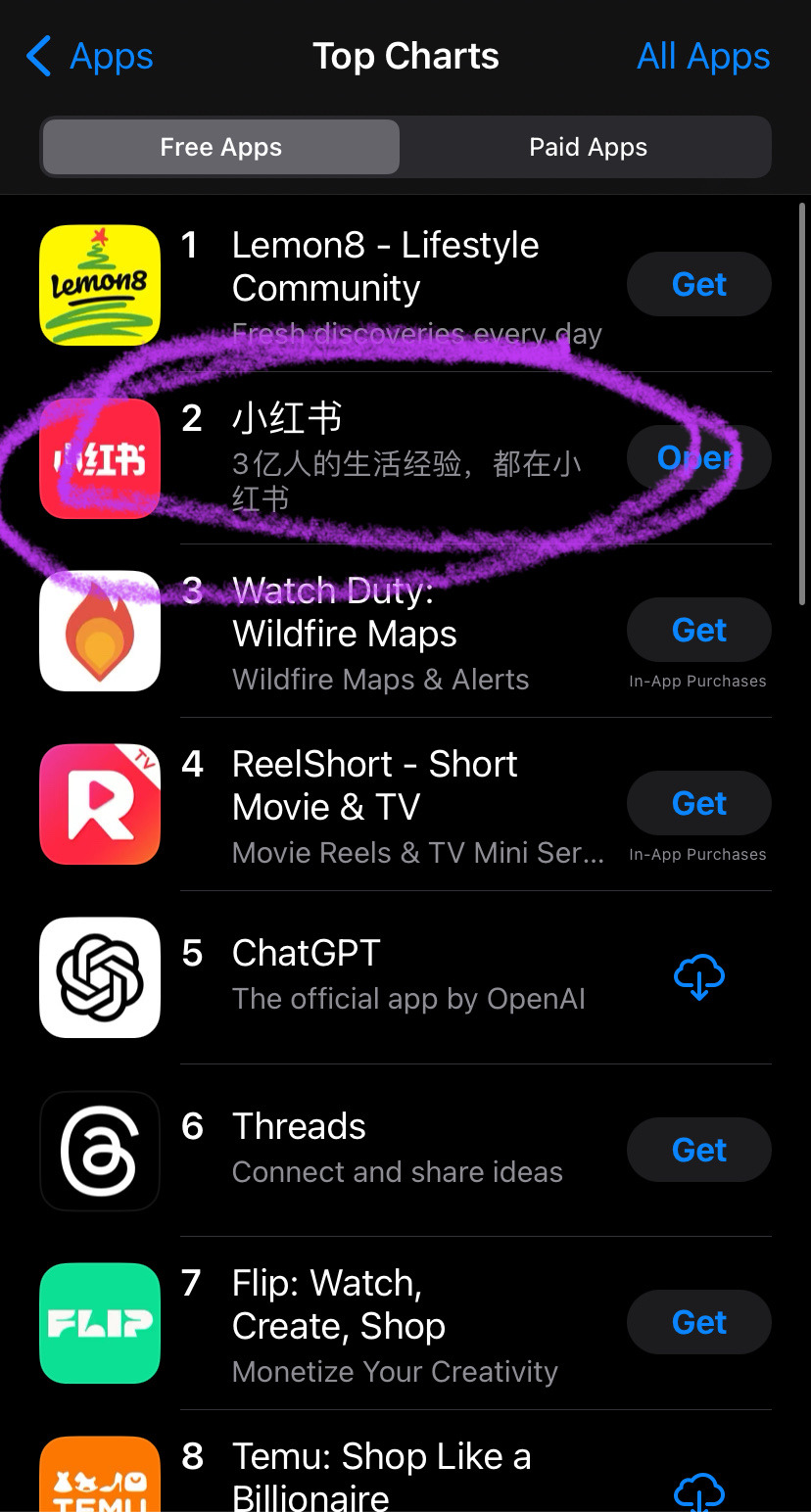
Tiktok as a community has chosen to collectively migrate TO a chinese owned app that is purely in Chinese out of utter spite and contempt for meta/x and the gov that is backing them.
My fyp is a mix of “i would rather mail memes to my friends than ever return to instagram reels” and “i will xerox my data to xi jinping myself i do not care i share my ss# with 5 other people anyway” and “im just getting ready for my day with my chinese made coffee maker and my Chinese made blowdryer and my chinese made clothing and listening to a podcast on my chinese made phone and get in my car running on chinese manufactured microchips but logging into a chinese social media? Too much for our gov!” etc.
So the government was scared that tiktok was creating a sense of class consciousness and tried to kill it but by doing so they sent us all to xiaohongshu. And now? Oh it’s adorable seeing this gov-manufactured divide be crossed in such a way.
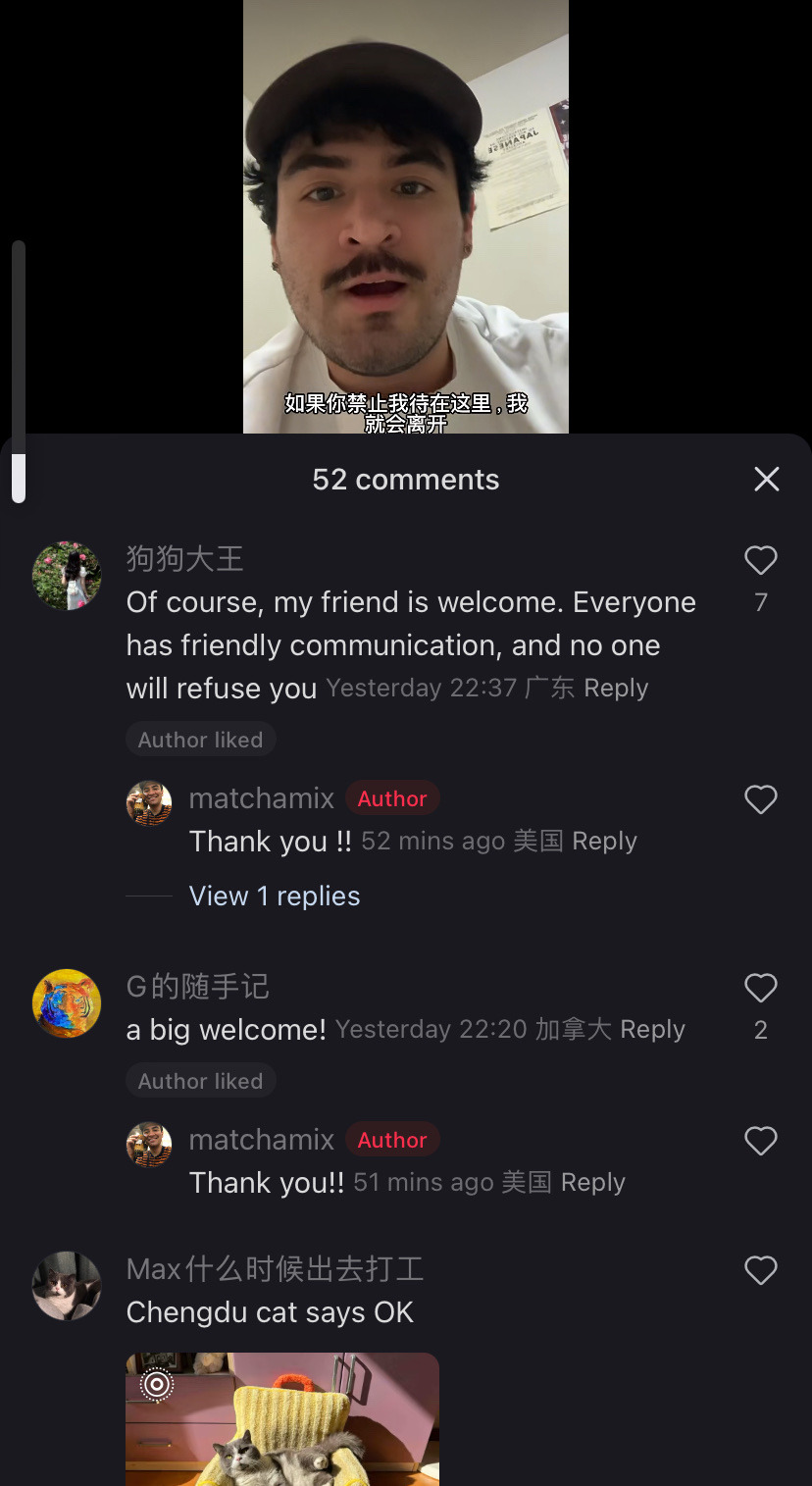
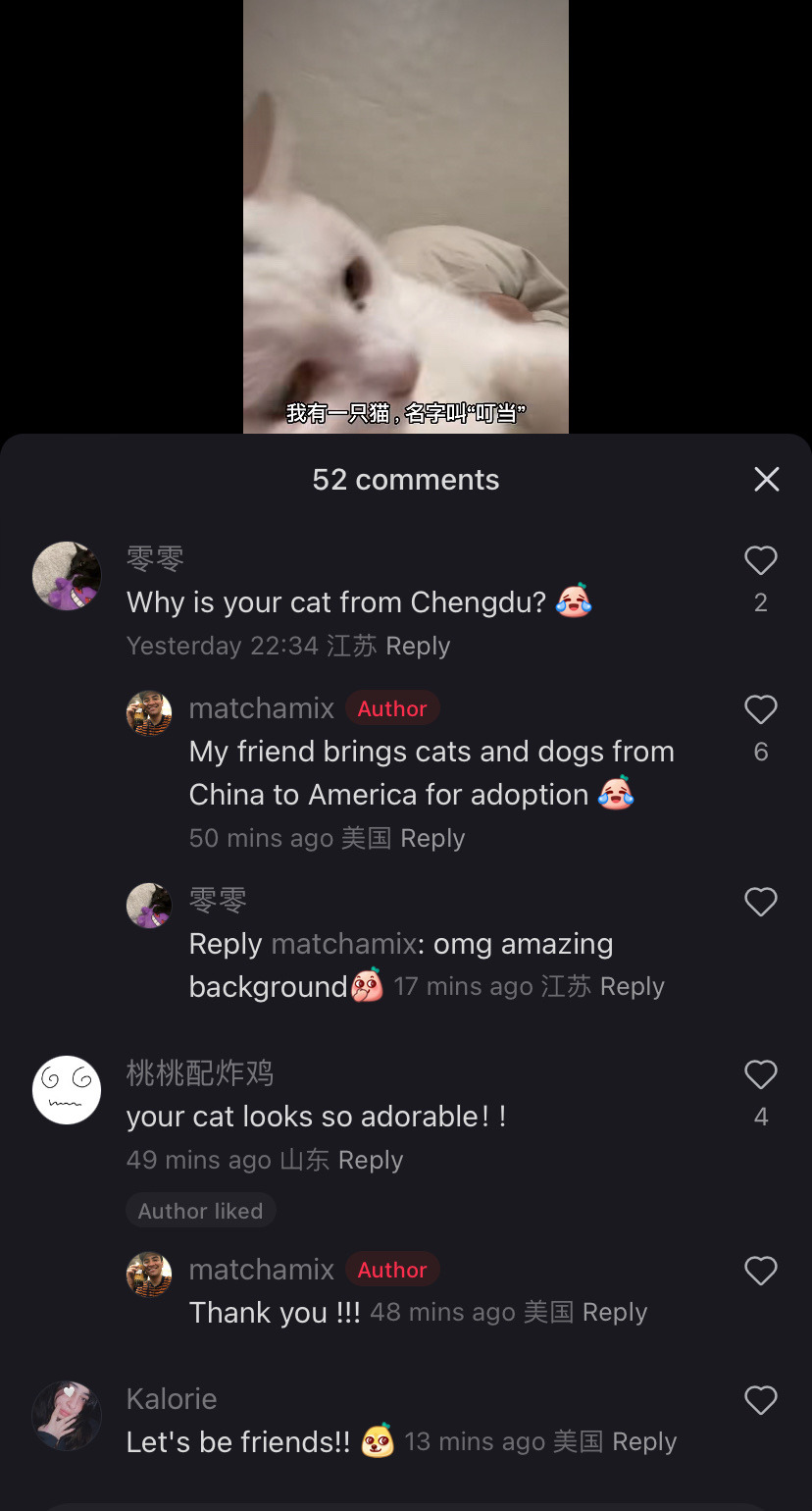

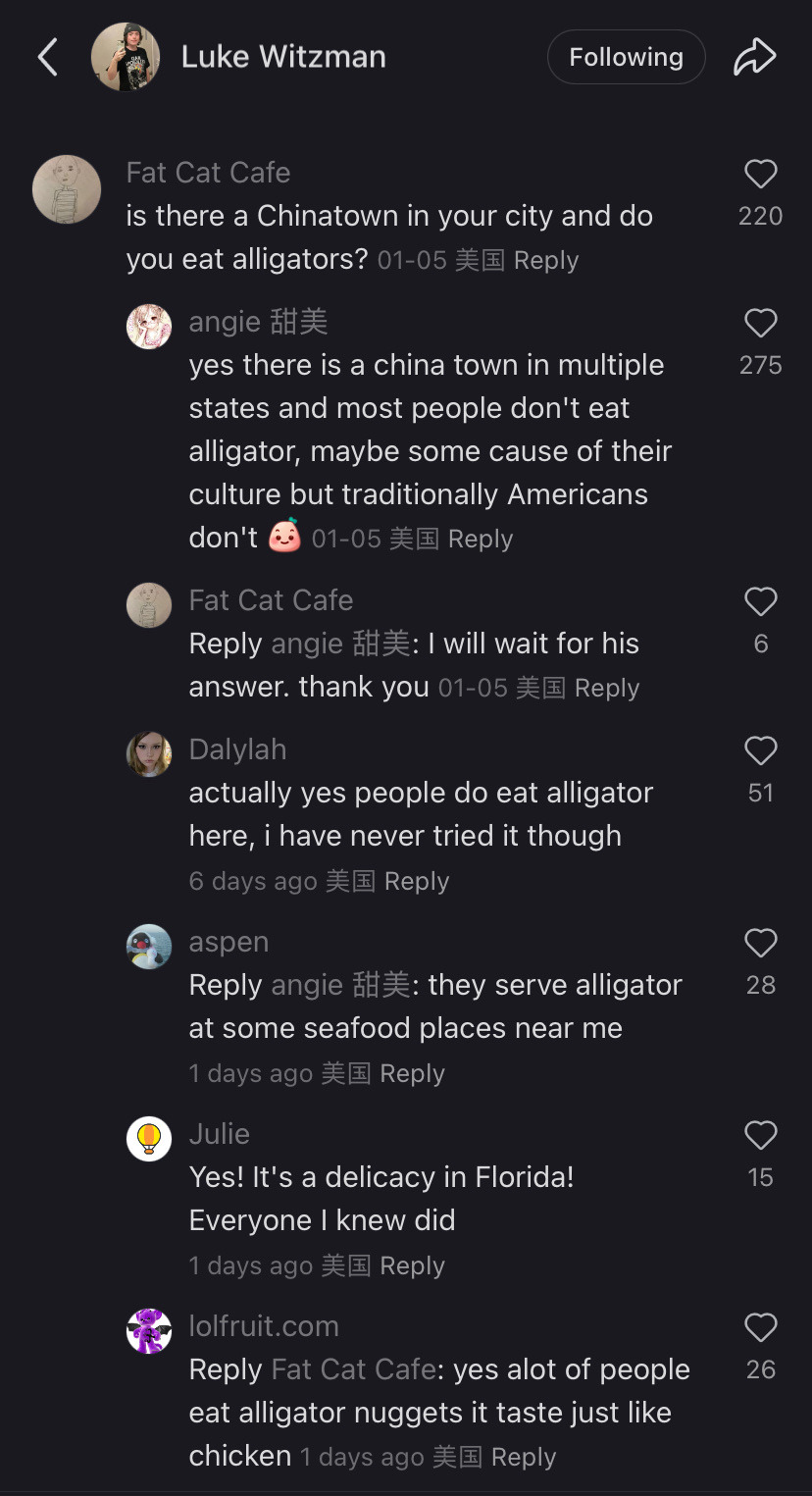
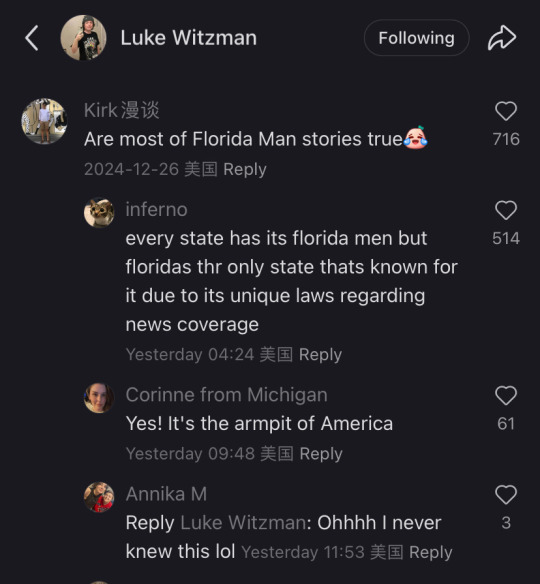
This is adorable and so not what they were expecting. Im sure they were expecting a reluctant return to reels and shorts to fill the void but tiktokers said fuck that, we will forge connections across the world. Who you tell me is my enemy i will make my friend. That’s pretty damn cool.
#tiktok ban#xiaohongshu#the great tiktok migration of 2025#us politics#us government#scotus#ftr tiktok is owned primarily by private investors and is not operated out of china#and all us data is stored on servers here in the us#tiktok also employs 7000 us employees to maintain the US side of operations#like they’re just lying to get us to shut up about genocide and corruption#so fuck it we’ll go spill all the tea to ears that wanna hear it cause this country is not what its cracked up to be#we been lied to and the rest of the world has been lied to#if scotus bans it tomorrow i can’t wait for their finding out#rednote
42K notes
·
View notes
Text
OBJECTION! the teacher's name is right there in his twitter handle
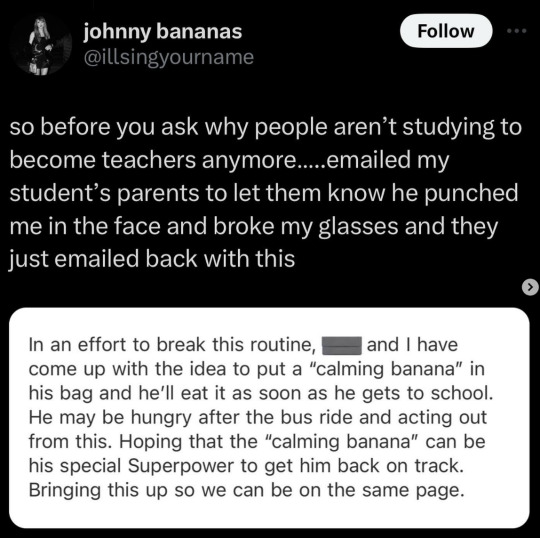
#please just stop arguing you literally dont know what you're talking about <3#you don't know how to protect kids nor the guidelines outside of HIPPA that are in place to protect them <3#you dont know when he changed his name on twitter#you dont know how small town politics work#you dont know how catty PTAs are#you dont know how many parents were following him on twitter beforehand#considering the fact he SHARED A SCREENSHOT OF A PRIVATE EMAIL#you think he's been data-secure before this?? please
43K notes
·
View notes
Text
I haven’t really seen any of the more recent U.S. election news hitting tumblr yet so here’s some updates (now edited with sources added):
There’s evidence of Trump cheating and interfering with the election.
Possible Russian interference.
Mail-in ballots are not being counted or “recognized” in multiple (notably swing) states.
30+ bomb threats were called in and shut down polling stations on Election Day.
20+ million votes are still unaccounted for, and that’s just to have the same voter turnout as 2020.
There was record voter turnout and new/first-time voter registration this year. We definitely should be well over the turnout in 2020.
U.S. citizens are using this site to demand, not only a recount, but a complete investigation into election fraud and interference for the reasons stated above:
Here is what I submitted as an example:
An investigation for election interference and fraud is required. We desperately need a recount or even a revote. The American people deserve the right to a free and fair election. There has been evidence unveiled of Trump cheating and committing election fraud which is illegal. There is some evidence of possible Russian interference. At least 30+ bomb threats were called in to polling places. Multiple, notably swing states, have ballots unaccounted for and voting machines not registering votes. Ballots and ballot boxes were tampered with and burned. Over 20 million votes that we know of are unaccounted for. With record turnout and new voter registration this year, there should be no possibility that there are less votes than even in the 2020 election.
Sources (working on finding more links but if anyone wants to add info, it’s appreciated):
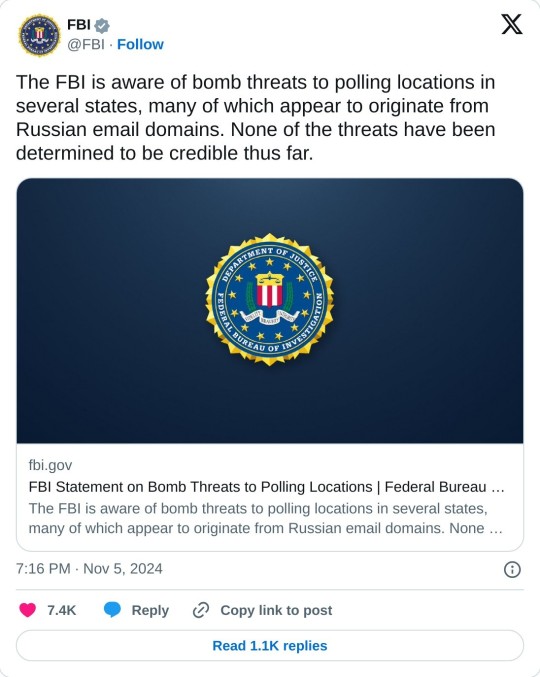
FBI addressing Russian interference and bomb threats:
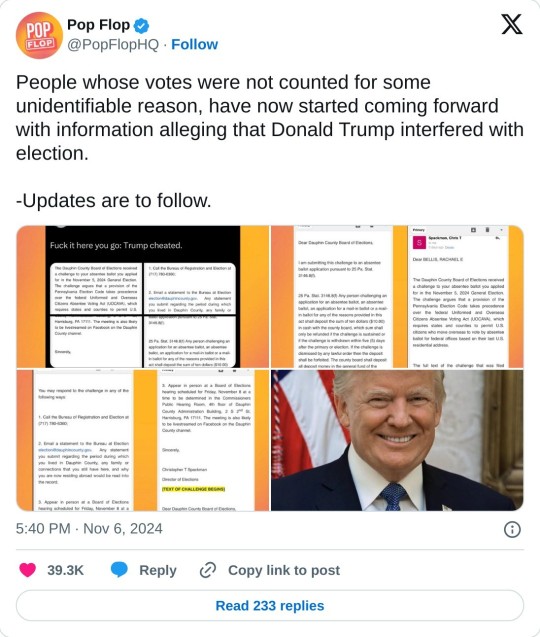
Emails released by Rachael Bellis (private account, can’t share original tweet) confirming Trump committing election fraud:
Pennsylvania's Centre County officials say they are working with their ballot scanner vendor to figure out why the county's mail-in ballot data is "not being recognized when uploaded to the elections software:”

Wisconsin recount:
[ID:
Multiple screenshots and images.
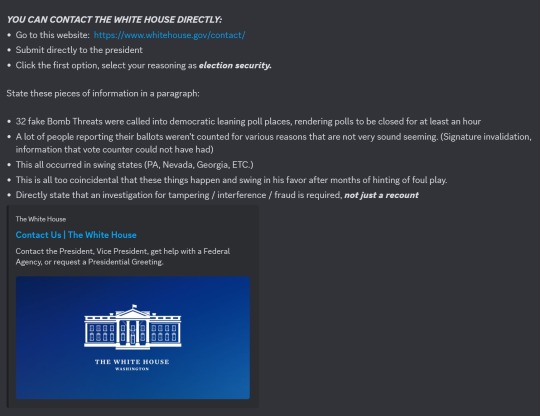
The first is a screenshot with a link and information for contacting the White House directly regarding election fraud. The instructions include choosing to leave a comment to President Joe Biden directly and to select election security as the reason.
The screenshot then instructs people to include any or all of the following information in a paragraph as a comment to the president:
32 fake bomb threats were called into Democratic leaning poll places, rendering polling places closed for at least an hour.
A lot of people reporting their ballots were not counted for various reasons.
This all occurred in swing states.
This is too coincidental that these things happen and swing in his favor after months of hinting at foul play.
Directly state that an investigation for tampering, interference, fraud is required, not just a recount.
The second image is from the FBI Twitter account that reads:
The FBI is aware of bomb threats to polling locations in several states, many of which appear to originate from Russian email domains. None of the threats have been determined to be credible thus far. https://t.co/j3YfajVK1m — FBI (@FBI) November 5, 2024
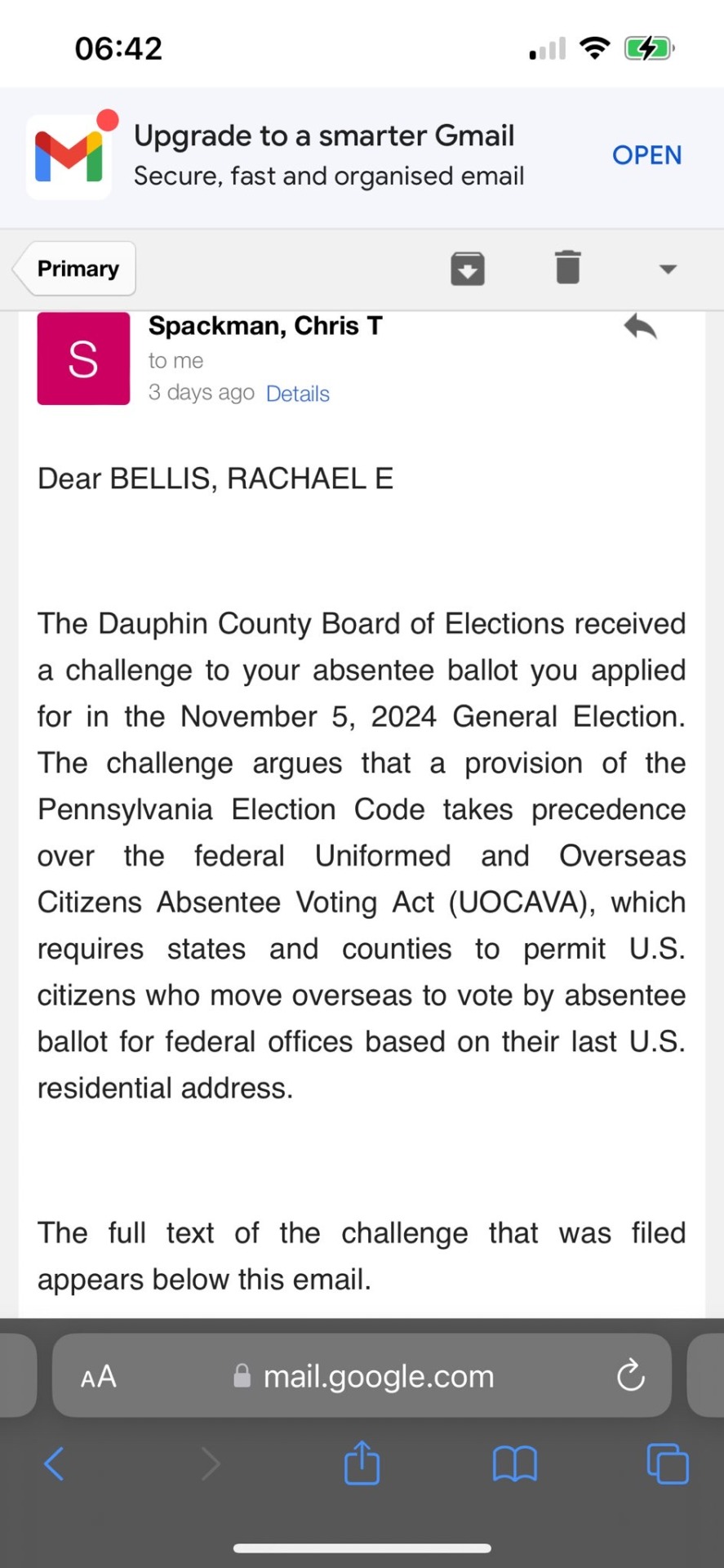
The next four Gmail screenshots of an email sent to Rachael Bellis from Chris T. Spackman that read together as follows:
Dear BELLIS, RACHAEL E., The Dauphin County Board of Elections received a challenge to your absentee ballot you applied for in the November 5, 2024 General Election. The challenge argues that a provision of the Pennsylvania Election Code takes precedence over the federal Uniformed and Overseas Citizens Absentee Voting Act (UOCAVA), which requires states and counties to permit U.S. citizens who move overseas to vote by absentee ballot for federal offices based on their last U.S. residential address.
The full text of the challenge that was filed appears below this email.
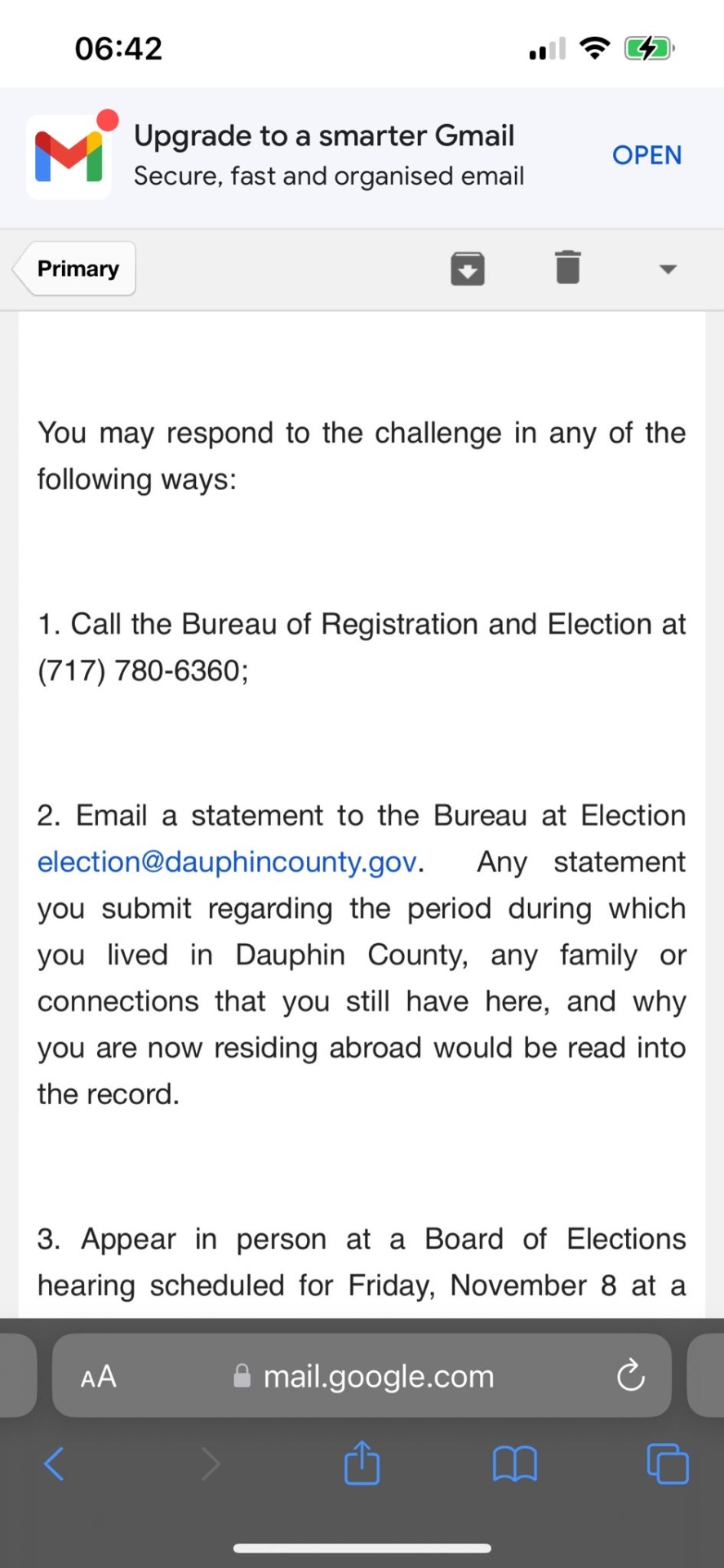
You may respond to the challenge in any of the following ways:
1. Call the Bureau of Registration and Election at (717) 780-6360;
2. Email a statement to the Bureau at Election [email protected]. Any statement you submit regarding the period during which you lived in Dauphin County, any family or connections that you still have here, and why you are now residing abroad would be read into the record.
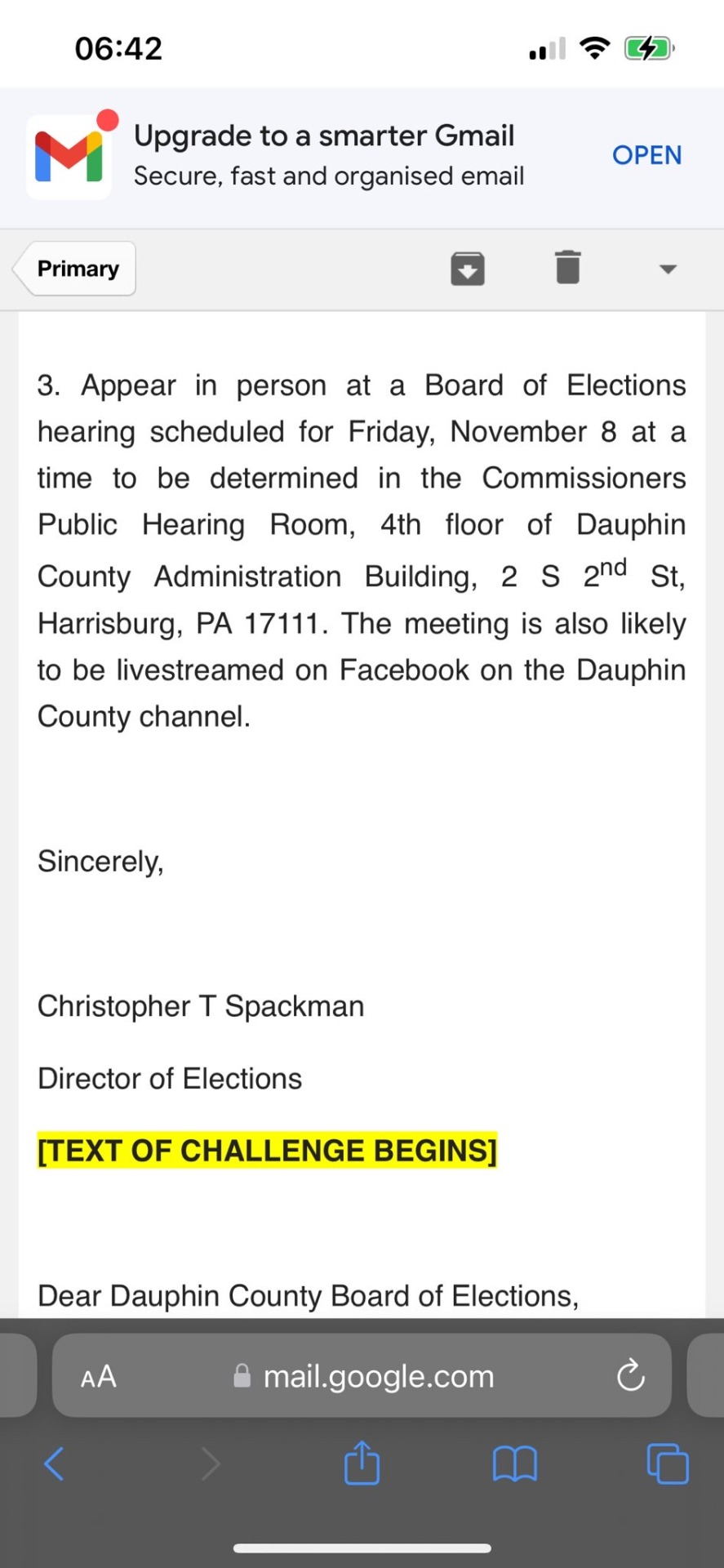
3. Appear in person at a Board of Elections hearing scheduled for Friday, November 8 at a time to be determined in the Commissioners Public Hearing Room, 4th floor of Dauphin County Administration Building, 2 S 20d St, Harrisburg, PA 17111. The meeting is also likely to be livestreamed on Facebook on the Dauphin County channel.
Sincerely,
Christopher T Spackman
TEXT OF CHALLENGE BEGINS
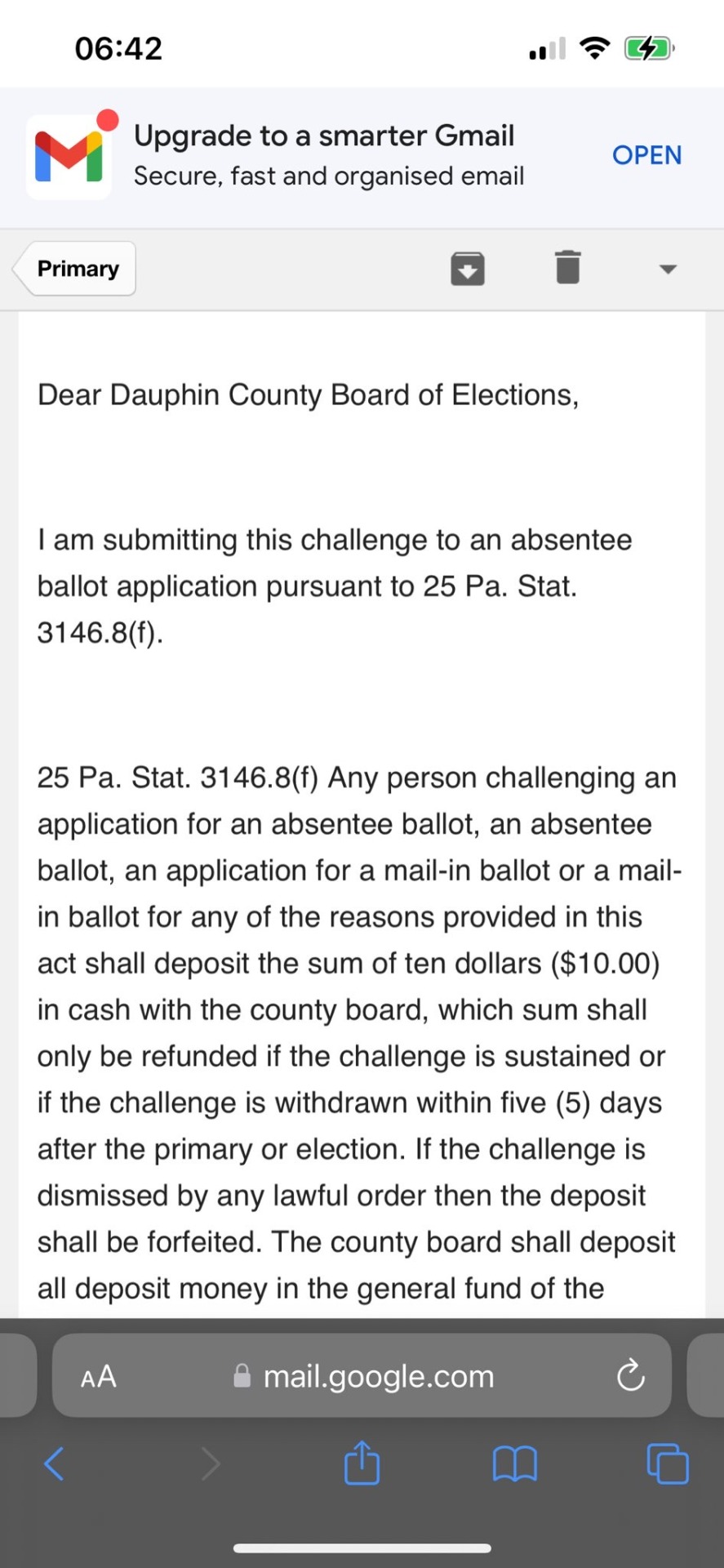
Dear Dauphin County Board of Elections,
I am submitting this challenge to an absentee ballot application pursuant to 25 Pa. Stat.
3146.8(f).
25 Pa. Stat. 3146.8(f) Any person challenging an application for an absentee ballot, an absentee ballot, an application for a mail-in ballot or a mail-in ballot for any of the reasons provided in this act shall deposit the sum of ten dollars ($10.00) in cash with the county board, which sum shall only be refunded if the challenge is sustained or if the challenge is withdrawn within five (5) days after the primary or election. If the challenge is dismissed by any lawful order then the deposit shall be forfeited. The county board shall deposit all deposit money in the general fund of the…
The rest of the forwarded email is cut off.
The last image is a screenshot of the official statement from the Centre County, Pennsylvania Board of Commissioners released on November 6, 2024 that states:
Centre County Working with Ballot Scanner Vendor to Export Election Results.
(Bellefonte, PA) -Centre County Elections Office is working continuously to provide mail-in ballot data in order to post unofficial results.
To this point, all ballots have been scanned, including all mail-in ballots.
Centre County's Election team and IT team have identified that the data are successfully being exported from the mail-in ballot scanners, but that the data is not being recognized when uploaded to the elections software.
Centre County's Administrator, John Franek, Jr. stated, "We have not stopped working, and we will continue to work until unofficial results are posted and reported to the Pennsylvania Department of State."
As a next step, Centre County has begun working with the equipment vendor to adjust configurations to make the two systems-the mail-in ballot scanner and the elections software where data are uploaded -compatible with one another.
We will provide updates as we make progress.
/end ID]
#sources added#us politics#us election#presidential election#2024 presidential election#election interference#election integrity#election security#image described#image description in alt#image description included#image description added#described#kamala harris#kamala 2024#us news#us presidents#updated id
36K notes
·
View notes
Text
Cloud Data Security Market Size, Share, Industry Outlook & Forecast to 2032

The Cloud Data Security Market size was valued at USD 33.39 Billion in 2023 and is expected to reach USD 117.62 Billion by 2032, growing at a CAGR of 15.04% over the forecast period 2024-2032.
The global cloud data security market is undergoing a transformative shift as organizations accelerate digital transformation and embrace hybrid cloud architectures. As cyber threats become increasingly sophisticated, enterprises are investing in cloud-native security solutions to safeguard sensitive data and ensure regulatory compliance. With the expansion of remote work, the demand for scalable and agile data protection strategies has intensified, propelling growth across industries such as banking, healthcare, and retail.
Cloud Data Security Market Poised for Strategic Advancements Rapid innovations in artificial intelligence, machine learning, and encryption technologies are fueling a new era in cloud data security. Enterprises are transitioning from traditional perimeter-based defenses to dynamic, identity-centric models that offer greater resilience and adaptability. This evolution is supported by the proliferation of multi-cloud environments, which require robust security frameworks capable of managing complex data flows and access points without compromising performance or user experience.
Get Sample Copy of This Report: https://www.snsinsider.com/sample-request/3636
Market Keyplayers:
Cloud Passage Inc. (Halo, Halo for AWS)
Intel Corporation (Intel Security, Intel vPro)
Sophos Ltd. (Sophos Cloud Optix, Sophos XG Firewall)
Fortinet, Inc. (FortiGate, FortiCloud)
IBM Corporation (IBM Cloud Security, IBM QRadar)
Cisco Systems, Inc. (Cisco Umbrella, Cisco Cloudlock)
Symantec Corporation (Symantec Data Loss Prevention, Symantec Cloud Security)
Trend Micro, Inc. (Trend Micro Cloud One, Trend Micro Deep Security)
Panda Security (Panda Adaptive Defense, Panda Cloud Office Protection)
CA Technologies, Inc. (CA Privileged Access Manager, CA Security Event Manager)
McAfee (McAfee MVISION Cloud, McAfee Cloud Workload Security)
Microsoft (Microsoft Defender for Identity, Microsoft Azure Security Center)
Vormetric (a Thales company) (Vormetric Data Security Platform, Vormetric Transparent Encryption)
Check Point Software Technologies (CloudGuard, Check Point Threat Emulation)
Forcepoint (Forcepoint Data Loss Prevention, Forcepoint Cloud Security)
Palo Alto Networks (Prisma Cloud, Cortex XSOAR)
Zscaler (Zscaler Internet Access, Zscaler Private Access)
Okta (Okta Identity Cloud, Okta Adaptive MFA)
Rapid7 (InsightCloudSec, InsightIDR)
Imperva (Cloud WAF, Imperva Data Security)
Market Analysis
The cloud data security market is characterized by a highly competitive landscape featuring both established cybersecurity providers and emerging startups. Strategic alliances, mergers, and acquisitions are shaping the trajectory of the market, as companies seek to integrate advanced security features such as automated threat detection, behavioral analytics, and zero-trust architecture. The increasing stringency of global data protection laws is compelling organizations to invest in compliance-driven security solutions tailored to regional regulatory frameworks.
As businesses adopt Infrastructure-as-a-Service (IaaS) and Software-as-a-Service (SaaS) models, cloud security is no longer an optional component but a critical enabler of trust and operational continuity. The integration of DevSecOps practices further emphasizes security as a core part of the software development lifecycle, fostering a proactive rather than reactive security posture.
Market Trends
Surge in demand for cloud-native security solutions to secure hybrid and multi-cloud infrastructures
Rising adoption of Zero Trust security frameworks for identity and access management
Growth in AI- and ML-powered threat detection and automated response mechanisms
Emphasis on data sovereignty and localized cloud security compliance measures
Expansion of DevSecOps practices integrating security at every stage of development
Increased focus on Secure Access Service Edge (SASE) to unify networking and security
Rapid evolution of encryption standards for data-at-rest, in-transit, and in-use
Greater investment in secure collaboration tools for remote workforce protection
Market Scope
The scope of the cloud data security market extends across a wide array of sectors including finance, healthcare, IT, telecommunications, manufacturing, and government. Enterprises are seeking end-to-end encryption, secure access control, and continuous monitoring solutions that align with their digital maturity. As cloud adoption reaches new heights, vendors are scaling offerings to support diverse workloads, APIs, and third-party integrations. The market also encompasses cloud security posture management (CSPM), data loss prevention (DLP), and cloud access security broker (CASB) technologies, collectively fortifying organizational resilience in an increasingly hostile cyber landscape.
Market Forecast
Over the forecast period, the cloud data security market is expected to maintain robust momentum, driven by technological innovations and the global push toward data-centric digital ecosystems. Cloud security will increasingly become embedded within broader digital transformation strategies, with providers focusing on intuitive, automated, and scalable platforms. Organizations will continue prioritizing investments in user behavior analytics, micro-segmentation, and unified threat management to preempt breaches and maintain trust. With the convergence of networking and security under cloud-native frameworks, the market is poised to evolve beyond traditional paradigms into a new standard of digital trust infrastructure.
Access Complete Report: https://www.snsinsider.com/reports/cloud-data-security-market-3636
Conclusion
The future of cloud data security is not just about protecting data—it’s about enabling digital confidence in a rapidly evolving business landscape. As enterprises redefine their digital blueprints, security leaders are called to align protection with innovation, ensuring that cloud adoption drives growth without compromising integrity. This dynamic market offers not only challenges but also immense opportunities for vendors and enterprises ready to invest in resilient, intelligent, and future-forward security architectures.
About Us:
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Contact Us:
Jagney Dave - Vice President of Client Engagement
Phone: +1-315 636 4242 (US) | +44- 20 3290 5010 (UK)
0 notes
Text
Dutch intelligence services AIVD and MIVD are continuing to share information with their American counterparts despite concerns about security, an investigation by the Volkskrant and Nieuwsuur has shown. Former Dutch intelligence officials are worried that sharing datasets, which may contain information about Dutch citizens, could pose a risk in light of the Trump administration’s approach to democratic rights and privacy protection. The investigation showed the Dutch security service AIVD and military security service MIVD have not scaled down their cooperation with American intelligence services, with one source citing overriding interests. “In some matters, cooperation is essential,” he said. Recent incidents involving citizens who were stopped at American airports, including one person being denied entry because of messages on a phone, highlight the importance of being “very careful” sharing unfiltered datasets, a former AIVD official said. Other events in Washington, such as the sharing of classified military information on message service Signal, in the presence of a journalist who was mistakenly invited to the group chat, and the United States’ increasingly close relationship with Russia and critical stance towards Ukraine, are also major red flags, they said.
continue reading
0 notes
Text
AI से फोटो ट्रांसफॉर्मेशन का क्रेज: Studio Ghibli स्टाइल में मस्ती के साथ प्राइवेसी का खतरा!
Ghibli Style Privacy Threat: आजकल सोशल मीडिया पर एक नया ट्रेंड जोर पकड़ रहा है, जहां लोग अपनी तस्वीरों को AI की मदद से अलग-अलग आर्ट स्टाइल में बदल रहे हैं। इनमें सबसे ज्यादा चर्चा में है Studio Ghibli की एनीमेशन थीम, जो जापानी फिल्ममेकर हायाओ मियाज़ाकी की खूबसूरत और सपनीली दुनिया से प्रेरित है। लेकिन क्या आपने कभी सोचा कि इस मज़े के पीछे आपकी निजता को कितना बड़ा खतरा हो सकता है? आइए, इस ट्रेंड की…
#AI photo transformation#biometric data theft#data storage#Ghibli trend#image generation#machine learning#privacy risks#secure AI tools#Studio Ghibli style#third-party sharing
0 notes
Text
Safeguarding Student Data: MeraSkool.com Security in School Management Software
# Safeguarding Student Data: MeraSkool.com Security in School Management Software ## Introduction Ensuring the highest level of data security is crucial for any school management software. Protecting sensitive information is not just a legal obligation, but also an essential aspect of maintaining trust and privacy among students, parents, and staff. This article will explore the importance of data security in school management software and highlight how MeraSkool.com addresses these concerns through its robust security features. ## Why Data Security Matters in School Management Software Data security breaches can have far-reaching consequences for schools, including financial losses, legal repercussions, and damage to reputation. Schools handle a vast amount of personal information, including student records, grades, attendance, and communications with parents. A breach could lead to identity theft, loss of privacy, and even legal action. ## Best Practices for Data Security in School Management Software To mitigate these risks, school management software should implement the following best practices: ### 1. Encryption Encryption is a critical component of any data security strategy. It ensures that sensitive information is unreadable to anyone who does not have the decryption key. MeraSkool.com uses industry-standard encryption protocols to protect all data transmitted and stored within its platform. ### 2. Access Controls Access controls are essential for preventing unauthorized access to student data. MeraSkool.com implements strict access control measures, including multi-factor authentication (MFA) and role-based access control (RBAC). Only authorized personnel can view and modify sensitive information, ensuring that it remains secure. ### 3. Regular Audits Regular security audits are necessary to identify vulnerabilities and ensure compliance with data protection regulations. MeraSkool.com conducts regular security audits and penetration testing to identify and address any weaknesses in its systems. ### 4. Compliance with Regulations Schools must comply with various data protection regulations, including GDPR, FERPA, and COPPA. MeraSkool.com is committed to ensuring compliance with these regulations through its built-in features and expert support. ## MeraSkool.com: A Secure School Management Solution MeraSkool.com understands the importance of data security in school management software. Our platform offers a range of features designed to protect student data, including: ### 5. Multi-Factor Authentication (MFA) MeraSkool.com implements MFA to ensure that only authorized personnel can access the platform. This adds an extra layer of security by requiring users to provide two forms of identification before gaining access. ### 6. Role-Based Access Control (RBAC) RBAC ensures that each user has access to only the information they need, based on their role within the school. For example, teachers can view student grades and attendance records, while administrative staff can manage the entire system. ### 7. Secure File Sharing MeraSkool.com provides secure file sharing capabilities, allowing users to share documents and files with other authorized personnel in a controlled manner. This helps prevent unauthorized access and ensures that sensitive information remains confidential. ## Discount Offers for Secure Software Solutions To further demonstrate our commitment to data security, MeraSkool.com is currently offering a 40% discount on our school management software for the month of December. Additionally, when you sign up and onboard your school in November, you won’t have to pay for this remaining session. ## Support and Feature Delivery MeraSkool.com takes pride in its exceptional customer support and commitment to delivering new features within 7 days. Our team is available via phone call or email to address any concerns or issues you may encounter. ## Conclusion Ensuring the highest level of data security is essential for school management software. MeraSkool.com offers a range of features designed to protect student data, including multi-factor authentication, role-based access control, and secure file sharing. With its commitment to compliance with regulations and exceptional customer support, MeraSkool.com stands out as a secure and reliable solution for schools. [Learn more about MeraSkool.com and its security features](https://www.meraskool.com/security) ## Tags Data Security in School Management Software, Best Practices, Multi-Factor Authentication, Role-Based Access Control, Secure File Sharing, Compliance, Discount Offers, Support ## Featured Image search query string to search stock image: school management, whiteboard, classroom
#Data Security in School Management Software#Best Practices#Multi-Factor Authentication#Role-Based Access Control#Secure File Sharing#Compliance#Discount Offers#Support
0 notes
Text
Storage Predictions for 2025: Larry O’Connor Explores the Future of Data Management
New Post has been published on https://thedigitalinsider.com/storage-predictions-for-2025-larry-oconnor-explores-the-future-of-data-management/
Storage Predictions for 2025: Larry O’Connor Explores the Future of Data Management


In this article by Larry O’Connor for LarryJordan.com, the founder and CEO of OWC shares his insightful predictions for the future of data storage in 2025. Highlighting the return to on-premises solutions, the democratization of AI through local implementation, and the growing performance gap between local and cloud-based systems, O’Connor provides a roadmap for businesses to optimize their storage strategies. These predictions focus on enhancing security, improving performance, and reducing costs—key considerations for data management in the digital era.
The Return of On-Premises Data Storage and Computing
O’Connor predicts a major resurgence in on-premises data storage and computing as organizations prioritize security, performance, and cost control. With cloud storage costs on the rise and vulnerabilities becoming more apparent, many businesses are turning to local solutions for critical data management. On-prem data storage offers faster access speeds, greater reliability, and enhanced protection against cyberattacks.
Smaller businesses, in particular, benefit from local storage since it is less attractive to cybercriminals compared to public cloud platforms. O’Connor emphasizes that the cloud should play a supporting role—serving as a tertiary backup or for external data sharing—while local solutions remain the primary strategy for data security. By reducing reliance on cloud storage, businesses can avoid bandwidth costs, accelerate data recovery, and maintain control over sensitive information.
On-Premises AI: Democratizing Technology and Protecting Intellectual Property
One of the most exciting predictions from O’Connor is the rise of on-premises AI. This shift enables smaller businesses to access powerful data processing tools without the high costs associated with cloud-based AI platforms. Running AI systems locally not only democratizes advanced technology but also protects proprietary data, algorithms, and customer insights from being exposed in the cloud.
O’Connor warns of the risks of “data bleed,” where proprietary information inadvertently enhances third-party systems or becomes accessible to competitors. On-prem AI ensures full control over sensitive data while eliminating recurring costs associated with cloud AI services. This makes on-premises AI a cost-effective and secure option for businesses looking to leverage AI capabilities.
The Expanding Performance Gap Between Local and Cloud-Based Systems
O’Connor’s third prediction underscores the growing performance gap between locally operated systems and cloud-dependent solutions. With advancements like Thunderbolt 5 technology, local systems now achieve data transfer speeds of up to 7000MB/s, far surpassing the 100MB/s typical of cloud-based systems.
This dramatic performance boost is essential for tasks such as video editing, high-resolution imagery processing, and managing complex data sets. By leveraging local systems, businesses can streamline workflows and significantly reduce the time and cost associated with cloud dependency. O’Connor suggests that cloud storage is best reserved for distribution and collaboration, while local solutions should handle performance-intensive tasks.
Conclusion: Embracing a Hybrid Storage Strategy
Larry O’Connor’s predictions for 2025 highlight a pivotal shift in data management strategies. Businesses are advised to embrace on-premises solutions for their speed, security, and cost advantages while using cloud services selectively for supplementary needs. Whether it’s safeguarding intellectual property, optimizing performance, or reducing expenses, on-premises storage and computing are poised to take center stage in the future of data management.
For organizations looking to stay ahead of the curve, O’Connor’s insights provide a clear path to success. By adopting a hybrid approach to data storage, businesses can harness the best of both local and cloud technologies, ensuring they remain competitive in an evolving digital landscape.
Read the full article by Larry O’Connor HERE
Learn more about OWC below:
#2025#ai#AI platforms#AI systems#Algorithms#approach#Article#backup#Best Of#CEO#Cloud#Cloud AI#cloud services#cloud storage#Collaboration#computing#Cyberattacks#cybercriminals#data#Data Management#data processing#data recovery#data security#data sharing#data storage#data transfer#democratization#democratization of AI#Editing#focus
0 notes
Text
Hate it when I'm asked about something then being completely ignored bc what I'm saying doesn't line up with the person's paranoia
#being asked bout computer shit(well more bout networks/wifi/data security)#and Ip addresses are brought up and its like#1. IP addresses are shared between a lot of ppl and without any other knowledge you are very unlikely ti be cucked through it#and 2. unless you pissed off the correct person or ppl then i dont think you need to worry bout being cucked over#(doesn't even matter bc ur house is LITERALLY LABELED on google maps already and ppl can just search ur name to find it)#then fucking ZIP BOMBING over the network got brought up and its like:#you stupid fuck unless you are fucking idiotic about what you open and download etc etc you dont have to worry bout that#unless there's a virus out there that can just automatically infect a device with no input from anybody (ie sender/reciever)-#-and can magically float within a specific network area#i think you will be fine#i dont claim to know everything bout this shit but its shit ya pick up doing certain things
1 note
·
View note
Text
Best Practices for Securing Your Collaborative Projects
As remote work and full-online business models become the norm, working with platforms like HackMD is becoming an increasingly popular way to carry out projects. However, with the power of digital collaboration comes the responsibility of security, and we must ensure that we protect data and project integrity when working online. Regardless of your work type, security should be a priority in the…
#collaboration safety#collaborative projects#cyber safety#Data Protection#digital security#online security#project management#project security#secure collaboration#secure sharing#team project protection#teamwork security
0 notes
Text
COVID-19 Impact on Tactical Data Link Market: Recovery and Future Forecast

Tactical Data Link (TDL) systems have become increasingly important for defense and aerospace sectors worldwide. With advancements in modern warfare systems and airspace modernization programs, the Tactical Data Link Market is projected to experience significant growth.
According to recent market reports, the Tactical Data Link market is expected to grow from USD 8.1 billion in 2022 to USD 10.3 billion by 2027, registering a compound annual growth rate (CAGR) of 4.9% during this period.
In this in-depth blog, we will explore the current state of the Tactical Data Link Industry, the factors driving its growth, challenges, opportunities, and emerging technologies shaping the future of TDL systems.
Understanding Tactical Data Link Systems
Tactical Data Link systems allow real-time data communication between military platforms such as aircraft, ships, ground vehicles, and command centers. By facilitating encrypted, secure communication across a range of military applications, TDLs enhance interoperability among allied forces. This real-time data exchange helps improve decision-making and operational efficiency on the battlefield.
Some of the most common Tactical Data Link protocols include:
Link 16: A secure, jam-resistant communication standard primarily used by NATO forces and allies.
Link 11: A tactical data communication system used by military aircraft, ships, and other platforms.
Link 22: An advanced data communication system designed to replace Link 11, providing enhanced security and interoperability for NATO forces.
You Can Download Our PDF Brochure: https://www.marketsandmarkets.com/pdfdownloadNew.asp?id=76169438
Tactical Data Link Market Size and Growth
The Tactical Data Link market was valued at USD 8.1 billion in 2022 and is projected to reach USD 10.3 billion by 2027. This represents a steady CAGR of 4.9% over the forecast period.
Key Growth Drivers
Rise in Airspace Modernization Programs Airspace modernization is a significant driver of the TDL market, especially in North America and Europe. Countries are investing heavily in upgrading their air traffic control and communication systems to improve efficiency, reduce carbon emissions, and increase safety. Tactical Data Links play a crucial role in enabling these modernized systems to communicate with air traffic managers and provide real-time tracking of military and civilian aircraft.
Emergence of Modern Warfare Systems The nature of warfare is evolving, and modern militaries increasingly rely on network-centric warfare strategies that require rapid, secure communication between platforms. TDLs allow for seamless data sharing, enabling a cohesive response to threats. Modern systems, such as Unmanned Aerial Vehicles (UAVs), are increasingly integrating TDLs for real-time information sharing during missions.
Increased Defense Budgets in Key Regions Despite the COVID-19 pandemic’s impact on global defense spending, countries like the U.S., China, and India have maintained or increased their defense budgets, emphasizing secure communication technologies like Tactical Data Links. Rising geopolitical tensions in the Asia-Pacific region, along with increasing investments in defense systems, are fueling demand for advanced TDL systems.
Growth in Unmanned Systems The growing use of unmanned systems, particularly UAVs, in both military and commercial applications is driving demand for TDL systems. These unmanned systems rely on TDLs for communication with command centers, enabling remote operations and improving mission success rates.
Impact of COVID-19 on the Tactical Data Link Market
The COVID-19 pandemic caused disruptions across the defense and aerospace industries. With many countries reallocating defense budgets to manage healthcare crises, several projects involving tactical data links were delayed or put on hold. Furthermore, the global supply chain was disrupted, impacting the production of tactical data link systems and components.
However, as the world recovers from the pandemic, defense spending is expected to rebound, especially in areas related to cybersecurity, secure communications, and network-centric warfare systems.
Ask for Sample Report: https://www.marketsandmarkets.com/requestsampleNew.asp?id=76169438
Market Restraints
1. Rigorous Military Standards and Regulations
The defense sector operates under strict regulations to ensure the security and integrity of communication systems. TDL solutions must meet rigorous military standards, such as those outlined by NATO. These regulations, while essential for maintaining high security, can slow down the adoption of new technologies and hamper market growth.
2. High Cost of Implementation
The development and deployment of TDL systems involve substantial costs, especially for smaller nations or countries with limited defense budgets. The high cost of procurement, installation, and maintenance of these systems can act as a restraint on market growth, particularly in developing regions.
Opportunities in the Tactical Data Link Market
1. Growing Demand for Enhanced Interoperability
With increasing multinational military operations, the need for enhanced interoperability between allied forces has become more important than ever. Tactical Data Links that enable seamless communication between different platforms and forces will see rising demand, particularly as more countries join international coalitions like NATO. TDL systems such as Link 16, which allow secure, encrypted communication between allied forces, are in high demand for this reason.
2. Adoption of Cognitive Radio Technology
Cognitive radios are an emerging technology that has the potential to transform tactical data links. These radios can automatically detect available frequencies and establish communication links, making them more efficient than traditional radios. As cognitive radios become more advanced, they could provide an important competitive advantage in the TDL market, especially for military applications.
3. Expansion in the Asia-Pacific Region
The Asia-Pacific region is expected to experience the fastest growth in the TDL market during the forecast period, with a projected CAGR of 4.18%. Countries such as China, India, and Japan are increasing their defense spending to modernize their military capabilities, and secure communication systems like TDLs are a crucial part of this strategy. Rising geopolitical tensions in the region further underscore the need for advanced communication systems.
Challenges Facing the Tactical Data Link Market
1. Lack of Skilled Workforce
The successful implementation of Tactical Data Link systems requires highly skilled personnel for tasks such as software development, system integration, and maintenance. However, many developing countries in regions such as Africa and South Asia face a shortage of technically skilled workers, which could hinder the adoption of TDL systems in these regions.
2. Spectrum Management Issues
Tactical Data Links operate within limited frequency ranges, and spectrum management is a critical challenge for defense organizations. As the number of communication systems operating in the same frequency bands increases, managing the spectrum becomes more complex. Cognitive radios offer a potential solution to this challenge, but they are still in the development phase.
To Gain Deeper Insights Into This Dynamic Market, Speak to Our Analyst Here: https://www.marketsandmarkets.com/speaktoanalystNew.asp?id=76169438
Market Segmentation and Trends
1. By Platform
The TDL market is segmented by platform into ground, airborne, naval, and unmanned systems. The unmanned systems segment is expected to grow at the highest CAGR of 6.4% during the forecast period, driven by the increasing use of UAVs for both military and commercial purposes.
2. By Component
The market is segmented by component into hardware, software, and services. The product (hardware) segment is expected to command the largest market share, growing from USD 5.3 billion in 2022 to USD 6.8 billion by 2027. The rising demand for advanced communication products is driving this growth.
3. By Point of Sale
Based on point of sale, the TDL market is divided into original equipment manufacturers (OEM) and aftermarket. The OEM segment is expected to dominate the market, as many military organizations prefer to source TDL solutions directly from manufacturers to ensure compatibility with existing systems.
Competitive Landscape
The Tactical Data Link market is dominated by Key Players such as Collins Aerospace (US), L3Harris Technologies (US), ViaSat (US), Thales Group (France), and General Dynamics Corporation (US). These companies are investing heavily in research and development to create advanced communication solutions that meet the evolving needs of modern militaries.
Recent Developments
Thales Group: In May 2022, Thales won a contract from the U.S. Army to deliver advanced tactical radios under the Combat Net Radio modernization program.
L3Harris Technologies: In May 2022, L3Harris secured an increased contract for its Falcon IV AN/PRC-167 radio systems, signaling growing demand for its tactical communication solutions.
The Tactical Data Link market is poised for significant growth, driven by advancements in military communication systems, airspace modernization, and rising defense budgets in key regions. Despite challenges such as stringent regulations and the high cost of implementation, the market offers substantial opportunities for innovation, particularly with the development of cognitive radios and increasing interoperability demands.
With major players such as Collins Aerospace, L3Harris, and Thales at the forefront, the TDL market will continue to evolve, offering new solutions that meet the complex communication needs of modern warfare. As the world becomes more interconnected, secure and efficient communication through Tactical Data Links will remain a top priority for defense organizations globally.
#military communication systems#secure data transmission#tactical communication networks#defense data link technology#real-time data sharing systems#tactical communication protocols#tactical data link standards#tactical network infrastructure
0 notes