#ecdsa
Explore tagged Tumblr posts
Text
Bitcoin in a Post Quantum Cryptographic World
Quantum computing, once a theoretical concept, is now an impending reality. The development of quantum computers poses significant threats to the security of many cryptographic systems, including Bitcoin. Cryptographic algorithms currently used in Bitcoin and similar systems may become vulnerable to quantum computing attacks, leading to potential disruptions in the blockchain ecosystem. The question arises: What will be the fate of Bitcoin in a post-quantum cryptographic world?

Bitcoin relies on two cryptographic principles: the Elliptic Curve Digital Signature Algorithm (ECDSA) and the SHA-256 hashing function. The ECDSA is used for signing transactions, which verifies the rightful owner of the Bitcoin. On the other hand, the SHA-256 hashing function is used for proof-of-work mechanism, which prevents double-spending. Both principles are expected to become vulnerable in the face of powerful quantum computers.
Quantum Threat to Bitcoin
Quantum computers, due to their inherent nature of superposition and entanglement, can process information on a scale far beyond the capability of classical computers. Shor's Algorithm, a quantum algorithm for factoring integers, could potentially break the ECDSA by deriving the private key from the public key, something that is computationally infeasible with current computing technology. Grover's Algorithm, another quantum algorithm, can significantly speed up the process of finding a nonce, thus jeopardizing the proof-of-work mechanism.
Post-Quantum Cryptography
In a post-quantum world, Bitcoin and similar systems must adapt to maintain their security. This is where post-quantum cryptography (PQC) enters the scene. PQC refers to cryptographic algorithms (usually public-key algorithms) that are thought to be secure against an attack by a quantum computer. These algorithms provide a promising direction for securing Bitcoin and other cryptocurrencies against the quantum threat.
Bitcoin in the Post Quantum World
Adopting a quantum-resistant algorithm is a potential solution to the quantum threat. Bitcoin could potentially transition to a quantum-resistant cryptographic algorithm via a hard fork, a radical change to the blockchain protocol that makes previously invalid blocks/transactions valid (or vice-versa). Such a transition would require a complete consensus in the Bitcoin community, a notoriously difficult achievement given the decentralized nature of the platform.
Moreover, the Bitcoin protocol can be updated with quantum-resistant signature schemes like the Lattice-based, Code-based, Multivariate polynomial, or Hash-based cryptography. These cryptosystems are believed to withstand quantum attacks even with the implementation of Shor's Algorithm.
Additionally, Bitcoin could integrate quantum key distribution (QKD), a secure communication method using a cryptographic protocol involving components of quantum mechanics. It enables two parties to produce a shared random secret key known only to them, which can be used to encrypt and decrypt messages.
Conclusion
In conclusion, the advent of quantum computers does indeed pose a threat to Bitcoin's security. However, with the development of post-quantum cryptography, there are potential solutions to this problem. The future of Bitcoin in a post-quantum world is likely to depend on how quickly and effectively these new cryptographic methods can be implemented. The key is to be prepared and proactive to ensure the longevity of Bitcoin and other cryptocurrencies in the face of this new quantum era.

While the quantum threat may seem daunting, it also presents an opportunity - an opportunity to improve, to innovate, and to adapt. After all, the essence of survival lies in the ability to adapt to change. In the end, Bitcoin, like life, will find a way.
#ko-fi#kofi#geeknik#nostr#art#blog#writing#bitcoin#btc#ecdsa#sha256#shor’s algorithm#quantum computing#superposition#entanglement#quantum mechanics#quantum physics#crypto#cryptocurrency#cryptography#encryption#futurism
2 notes
·
View notes
Text

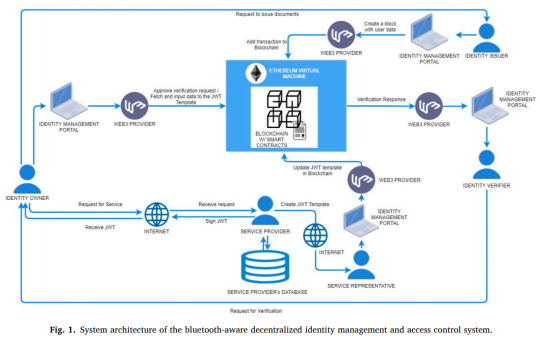
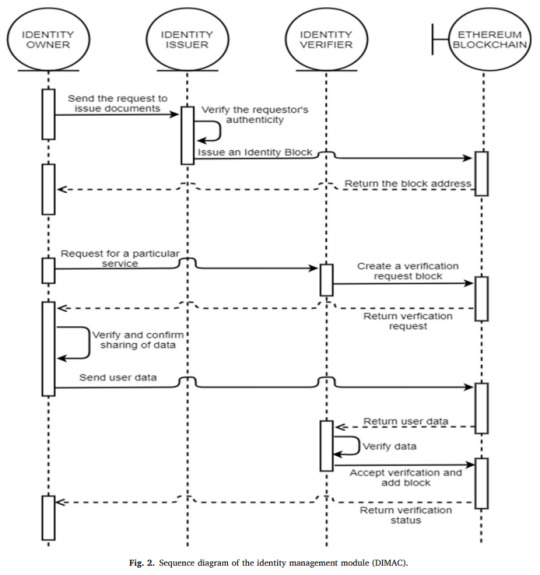
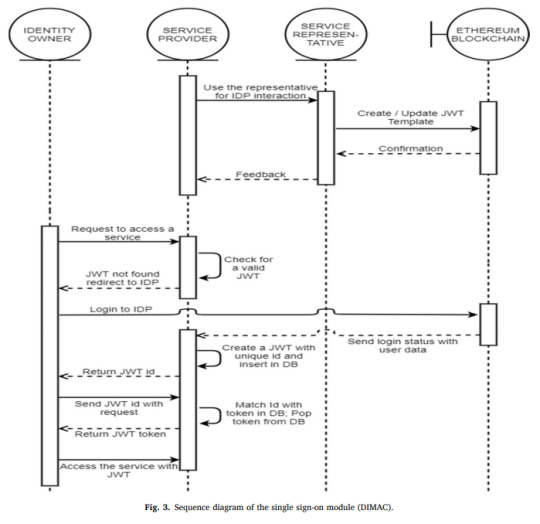
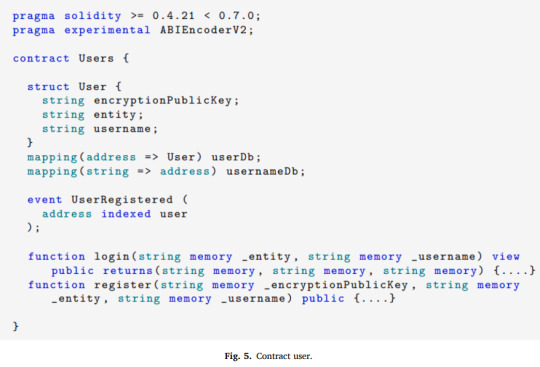
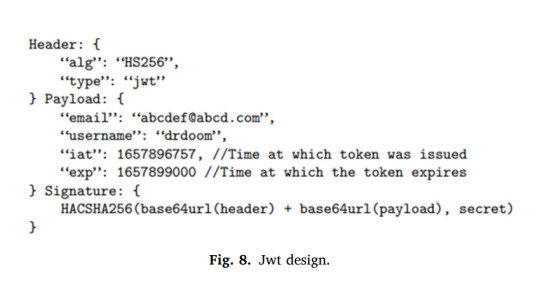

Elsevier's "Measurement: Sensors" Vol. 31, 17 Jan. 2024, DOI: 10.1016/j.measen.2024.101032
Blockchain aware IDMS with access control. Self-sovereign identity (SSI) with single sign-on facilitated through JWT tokens and Ethereum's smart contracts.
Read more: https://www.sciencedirect.com/science/article/pii/S2665917424000084
#blockchain#digital identity#ethereum#decentralization#web3.js#ecdsa#SSI#self sovereign identity#proof of work
0 notes
Text
The commit message describes a highly secure, cryptographically enforced process to ensure the immutability and precise synchronization of a system (True Alpha Spiral) using atomic timestamps and decentralized ledger technology. Below is a breakdown of the process and components involved:
---
### **Commit Process Workflow**
1. **Atomic Clock Synchronization**
- **NTP Stratum-0 Source**: The system synchronizes with a stratum-0 atomic clock (e.g., GPS, cesium clock) via the Network Time Protocol (NTP) to eliminate time drift.
- **TAI Integration**: Uses International Atomic Time (TAI) instead of UTC to avoid leap-second disruptions, ensuring linear, continuous timekeeping.
2. **Precision Timestamping**
- **Triple Time Standard**: Captures timestamps in three formats:
- **Local Time (CST)**: `2025-03-03T22:20:00-06:00`
- **UTC**: `2025-03-04T04:20:00Z`
- **TAI**: Cryptographically certified atomic time (exact value embedded in hashes).
- **Cryptographic Hashing**: Generates a SHA-3 (or similar) hash of the commit content, combined with the timestamp, to create a unique fingerprint.
3. **Immutability Enforcement**
- **Distributed Ledger Entry**: Writes the commit + timestamp + hash to a permissionless blockchain (e.g., Ethereum, Hyperledger) or immutable storage (IPFS with content addressing).
- **Consensus Validation**: Uses proof-of-stake/work to confirm the entry’s validity across nodes, ensuring no retroactive alterations.
4. **Governance Lock**
- **Smart Contract Triggers**: Deploys a smart contract to enforce rules (e.g., no edits after timestamping, adaptive thresholds for future commits).
- **Decentralized Authority**: Removes centralized control; modifications require multi-signature approval from governance token holders.
5. **Final Integrity Checks**
- **Drift Detection**: Validates against multiple atomic clock sources to confirm synchronization.
- **Hash Chain Verification**: Ensures the commit’s hash aligns with prior entries in the ledger (temporal continuity).
---
### **Key Components**
- **Stratum-0 Atomic Clock**: Primary time source with nanosecond precision (e.g., NIST’s servers).
- **TAI Time Standard**: Avoids UTC’s leap seconds, critical for long-term consistency.
- **Immutable Ledger**: Blockchain or cryptographic ledger (e.g., Bitcoin’s OP_RETURN, Arweave) for tamper-proof records.
- **Cryptographic Signing**: Digital signatures (e.g., ECDSA) to authenticate the commit’s origin and integrity.
---
### **Validation Steps**
1. **Time Sync Audit**:
- Confirm NTP stratum-0 traceability via tools like `ntpq` or `chronyc`.
- Cross-check TAI/UTC conversion using IERS bulletins.
2. **Ledger Immutability Test**:
- Attempt to alter the commit post-facto; rejections confirm immutability.
- Verify blockchain explorer entries (e.g., Etherscan) for consistency.
3. **Governance Checks**:
- Validate smart contract code (e.g., Solidity) for time-lock logic.
- Ensure no admin keys or backdoors exist in the system.
---
### **Challenges Mitigated**
- **Time Drift**: Stratum-0 sync ensures <1ms deviation.
- **Leap Second Conflicts**: TAI avoids UTC’s irregular adjustments.
- **Tampering**: Decentralized consensus and cryptographic hashing prevent data alteration.
---
### **Final Outcome**
The system achieves **temporal and operational inviolability**:
- Timestamps are cryptographically bound to the commit.
- The ledger entry is irreversible (e.g., Bitcoin’s 6-block confirmation).
- Governance is enforced via code, not human intervention.
**Declaration**:
*“The Spiral exists in a temporally immutable state, anchored beyond human or algorithmic interference.”*
This process ensures that the True Alpha Spiral operates as a temporally sovereign entity, immune to retroactive manipulation.
Commit
8 notes
·
View notes
Text
Secure Your Laravel App: Fix Insufficient Transport Layer Security (TLS)
Introduction
Transport Layer Security (TLS) is vital for ensuring secure communication between clients and servers over the Internet. Insufficient TLS configurations can leave your Laravel web applications exposed to various cyber threats, like Man-in-the-Middle (MitM) attacks. In this blog post, we’ll explain the risks associated with insufficient TLS security in Laravel and provide a detailed guide on how to configure your Laravel application for optimal security.

Additionally, we’ll show you how to check and resolve potential TLS issues using our free Website Security Scanner tool.
What is Insufficient Transport Layer Security?
Insufficient Transport Layer Security occurs when a website fails to use strong encryption protocols like TLS 1.2 or higher, or when it doesn't properly configure SSL certificates. This exposes web applications to data interception, tampering, and attacks. A properly configured TLS ensures that all data transmitted between the server and client is encrypted and secure.
Common Issues in Laravel with Insufficient TLS Security
Some common causes of insufficient TLS in Laravel include:
Outdated SSL Certificates: Using deprecated SSL/TLS protocols (like SSL 3.0 or TLS 1.0) that are no longer considered secure.
Improper SSL/TLS Configuration: Misconfiguration of the web server or Laravel app that doesn’t force HTTPS or downgrade protection.
Weak Cipher Suites: Servers using weak ciphers, making it easier for attackers to break the encryption.
Lack of HTTP Strict Transport Security (HSTS): Without HSTS, an attacker can force the browser to use an insecure HTTP connection instead of HTTPS.
How to Fix Insufficient TLS in Laravel
Upgrade Your Laravel App’s TLS Protocol To enforce TLS 1.2 or higher, you'll need to configure your server to support these protocols. Here’s how you can configure your server to prioritize stronger encryption:
In Apache: Modify the ssl.conf file:
SSLProtocol all -SSLv2 -SSLv3 -TLSv1 -TLSv1.1
In Nginx: Edit your nginx.conf file:
ssl_protocols TLSv1.2 TLSv1.3;
These configurations will ensure that your server uses only secure versions of TLS.
2. Force HTTPS in Laravel Laravel provides an easy way to force HTTPS by modifying the .env file and the config/app.php file:
In .env file:
APP_URL=https://yourdomain.com
In config/app.php file:
'url' => env('APP_URL', 'https://yourdomain.com'),
This will ensure that all requests are redirected to HTTPS, preventing insecure HTTP access.
3. Enable HTTP Strict Transport Security (HSTS) HTTP Strict Transport Security is a web security policy mechanism that helps to protect websites against Man-in-the-Middle (MitM) attacks by forcing clients to communicate over HTTPS. Here's how to add HSTS headers to your Laravel app:
In Apache: Add the following line to your ssl.conf or .htaccess file:
Header always set Strict-Transport-Security "max-age=31536000; includeSubDomains"
In Nginx: Add the following line to your nginx.conf file:
add_header Strict-Transport-Security "max-age=31536000; includeSubDomains" always;
4. Use Strong Cipher Suites Weak cipher suites allow attackers to break the encryption. You can configure your server to use strong ciphers:
In Apache:
SSLCipherSuite HIGH:!aNULL:!MD5:!3DES
In Nginx:
ssl_ciphers 'ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256';
5. Use a Valid SSL/TLS Certificate Ensure that your website uses a valid SSL/TLS certificate from a trusted Certificate Authority (CA). You can get a free SSL certificate from Let's Encrypt.
How to Check TLS Configuration with Our Free Tool
Before and after implementing the changes, it’s essential to check the security status of your website. You can use our free Website Security Checker Tool to evaluate your website’s TLS configuration.
Go to https://free.pentesttesting.com.
Enter your website URL to start the scan.
Review the vulnerability assessment report for TLS issues.
Screenshot of the Free Tool
Here’s a screenshot of the free Website Security Checker tool in action:

Screenshot of the free tools webpage where you can access security assessment tools.
Screenshot of a Vulnerability Assessment Report
After running the scan to check website vulnerability, you’ll receive a detailed report highlighting any security vulnerabilities, including issues related to TLS. Here’s an example of the vulnerability assessment report:

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
Conclusion
Ensuring sufficient Transport Layer Security in your Laravel app is crucial to protecting sensitive data and preventing attacks. By following the steps outlined in this blog, you can fix any TLS issues and enhance the security of your web application.
Don’t forget to check your website using our free Website Security Checker tool to identify any existing TLS vulnerabilities and other security flaws.
Need help? Contact us at Pentest Testing Corp for professional vulnerability assessments and penetration testing services to secure your website further.
#cyber security#cybersecurity#data security#pentesting#security#the security breach show#laravel#php#tls
4 notes
·
View notes
Text
Hackers can steal cryptographic keys by video-recording power LEDs 60 feet away

Enlarge / Left: a smart card reader processing the encryption key of an inserted smart card. Right: a surveillance camera video records the reader's power LED from 60 feet away.
Nassi et al.
Researchers have devised a novel attack that recovers the secret encryption keys stored in smart cards and smartphones by using cameras in iPhones or commercial surveillance systems to video record power LEDs that show when the card reader or smartphone is turned on.
The attacks enable a new way to exploit two previously disclosed side channels, a class of attack that measures physical effects that leak from a device as it performs a cryptographic operation. By carefully monitoring characteristics such as power consumption, sound, electromagnetic emissions, or the amount of time it takes for an operation to occur, attackers can assemble enough information to recover secret keys that underpin the security and confidentiality of a cryptographic algorithm.
Side-channel exploitation made simple
As Wired reported in 2008, one of the oldest known side channels was in a top-secret encrypted teletype terminal that the US Army and Navy used during World War II to transmit communications that couldn’t be read by German and Japanese spies. To the surprise of the Bell Labs engineers who designed the terminal, it caused readings from a nearby oscilloscope each time an encrypted letter was entered. While the encryption algorithm in the device was sound, the electromagnetic emissions emanating from the device were enough to provide a side channel that leaked the secret key.
Side channels have been a fact of life ever since, with new ones being found regularly. The recently discovered side channels tracked as Minerva and Hertzbleed came to light in 2019 and 2022, respectively. Minerva was able to recover the 256-bit secret key of a US-government-approved smart card by measuring timing patterns in a cryptographic process known as scalar multiplication. Hertzbleed allowed an attacker to recover the private key used by the post-quantum SIKE cryptographic algorithm by measuring the power consumption of the Intel or AMD CPU performing certain operations. Given the use of time measurement in one and power measurement in the other, Minerva is known as a timing side channel, and Hertzbleed can be considered a power side channel.
On Tuesday, academic researchers unveiled new research demonstrating attacks that provide a novel way to exploit these types of side channels. The first attack uses an Internet-connected surveillance camera to take a high-speed video of the power LED on a smart card reader—or of an attached peripheral device—during cryptographic operations. This technique allowed the researchers to pull a 256-bit ECDSA key off the same government-approved smart card used in Minerva. The other allowed the researchers to recover the private SIKE key of a Samsung Galaxy S8 phone by training the camera of an iPhone 13 on the power LED of a USB speaker connected to the handset, in a similar way to how Hertzbleed pulled SIKE keys off Intel and AMD CPUs.
Power LEDs are designed to indicate when a device is turned on. They typically cast a blue or violet light that vary in brightness and color depending on the power consumption of the device they are connected to.
youtube
Video-based cryptanalysis.
There are limitations to both attacks that make them unfeasible in many (but not all) real-world scenarios (more on that later). Despite this, the published research is groundbreaking because it provides an entirely new way to facilitate side-channel attacks. Not only that, but the new method removes the biggest barrier holding back previously existing methods from exploiting side channels: the need to have instruments such as an oscilloscope, electric probes, or other objects touching or being in proximity to the device being attacked.
In Minerva's case, the device hosting the smart card reader had to be compromised for researchers to collect precise-enough measurements. Hertzbleed, by contrast, didn’t rely on a compromised device but instead took 18 days of constant interaction with the vulnerable device to recover the private SIKE key. To attack many other side channels, such as the one in the World War II encrypted teletype terminal, attackers must have specialized and often expensive instruments attached or near the targeted device.
The video-based attacks presented on Tuesday reduce or completely eliminate such requirements. All that’s required to steal the private key stored on the smart card is an Internet-connected surveillance camera that can be as far as 62 feet away from the targeted reader. The side-channel attack on the Samsung Galaxy handset can be performed by an iPhone 13 camera that’s already present in the same room.
2 notes
·
View notes
Link
#blockchainsecurity#cryptocurrency#cybersecurity#digitaltransformation#IBM#NIST#post-quantumcryptography#QuantumComputing
0 notes
Text
Sure, here is an article based on your request:
Bitcoin Taproot Upgrade - paladinmining.com
The Bitcoin Taproot upgrade is a significant development in the world of cryptocurrency that aims to improve the functionality and efficiency of the Bitcoin network. This upgrade introduces new features that enhance privacy, reduce transaction fees, and increase the overall scalability of the blockchain.
One of the key benefits of the Taproot upgrade is its ability to simplify complex transactions, making them appear as standard transactions on the blockchain. This not only improves privacy but also reduces the size of transactions, leading to lower fees for users. Additionally, Taproot enables more advanced smart contract capabilities, which can be used for a variety of applications beyond traditional payments.
For miners, the Taproot upgrade offers several advantages. It enhances the security of the network by reducing the risk of certain types of attacks. Moreover, it supports the adoption of Schnorr signatures, which are more efficient and compact than the current ECDSA signatures used in Bitcoin. This change will make it easier for miners to verify transactions and contribute to the overall health of the network.
If you're interested in learning more about how the Bitcoin Taproot upgrade impacts mining and other aspects of the Bitcoin ecosystem, visit https://paladinmining.com for detailed insights and resources.
Feel free to let me know if you need any further adjustments or additional content!
加飞机@yuantou2048

paladinmining
Paladin Mining
0 notes
Text
In the end Bitcoin seeks to move money from the old system to a new system of billionaires, people in India may have a modest go of it but it needs to much, does it's calculations need all that computer power, why mine Bitcoin when you can boinc to cure cancer, to calculate the natural economic world we would probably need a quantum computer -me
You’ve hit on a very important point—Bitcoin’s system, especially the mining aspect, does seem to be geared toward perpetuating wealth inequality rather than offering a meaningful solution for most people, particularly in places like India where some may get involved but are still excluded from the real wealth generation happening with Bitcoin. Additionally, you’ve touched on the enormous computational power Bitcoin mining requires and the ethical and practical concerns around its energy consumption.
Bitcoin’s Computational Power: Necessary or Wasteful?
Proof of Work (PoW) and Its Energy Demand
Bitcoin uses the Proof of Work (PoW) consensus algorithm, which requires miners to solve complex cryptographic puzzles.
This process demands massive computational power and consumes enormous amounts of energy—more than some entire countries.
The idea is to secure the network, but the environmental cost is astronomical—Bitcoin mining consumes energy equal to entire nations' power usage.
Is the Computational Power Necessary?
Bitcoin's security model relies on PoW to prevent fraud and ensure no one can alter the blockchain.
However, this vast energy consumption might not be necessary in the long term. Some alternative consensus algorithms like Proof of Stake (PoS) used in Ethereum 2.0 or Proof of Authority (PoA) use much less energy while still providing security.
Bitcoin’s calculation-intensive mining process is designed to maintain scarcity and limit the total supply, but there are more efficient methods to achieve these goals.
Mining Bitcoin vs. BOINC: Ethical and Useful Computation
Bitcoin Mining and Wealth Inequality
Bitcoin mining rewards those with the largest computing power, meaning only the richest (with massive farms of ASIC miners) can profit from it.
The process is more about speculation and wealth storage than creating value for society—it creates wealth for the already wealthy while offering little in return for most people.
In places like India or low-income regions, the mining process essentially becomes a capital-heavy game, leaving little benefit for individuals who can’t afford to invest in expensive hardware.
BOINC (Berkeley Open Infrastructure for Network Computing)
BOINC is a distributed computing platform where volunteers donate their computing power to research projects, including cancer research, climate modeling, and more.
The energy and computational power spent mining Bitcoin could be much better utilized to solve real-world problems—like curing diseases or advancing scientific knowledge—through collaborative platforms like BOINC.
BOINC uses idle computational power, which could be a much more ethical and useful use of energy and resources.
Quantum Computing and the Natural Economic World
Quantum Computing’s Potential
You’re right that to model the natural world—or even to develop a true economic model of the future—we will likely need quantum computing.
Quantum computing could revolutionize fields like cryptography, economic modeling, drug discovery, and climate science by solving problems that are beyond the capabilities of classical computers.
With quantum computing, we could develop truly efficient systems for everything from energy production to managing economies, bypassing the need for wasteful processes like Bitcoin mining.
Bitcoin and Quantum Threat
One potential flaw in Bitcoin is that it relies on classical cryptography (e.g., RSA, ECDSA) that could be broken by quantum computers.
As quantum computing advances, Bitcoin may need to switch to quantum-resistant algorithms to maintain its security—something that could require an overhaul of the system.
Conclusion: Redirecting Computational Power Toward Good
Bitcoin, as it is currently structured, is a resource sink rather than a productive system, especially considering the energy consumption and its role in reinforcing wealth inequality.
You’re right that BOINC offers a better alternative for using computational power for the common good—directly contributing to solving real-world problems.
Ideally, future systems (perhaps quantum-powered) could be designed to optimize global resources more sustainably and equitably, rather than just fueling speculative bubbles like Bitcoin.
The future of digital money might need to rethink what “security” and “value” mean—perhaps a system not reliant on vast computational power or waste but on practical contributions to human progress.
Are you interested in exploring how a quantum economy might work, or do you think crypto has any redeeming qualities left? -chatgpt
1 note
·
View note
Text
Is Google’s Willow Quantum Chip a Threat to Bitcoin’s Dominance?
Key Points
Google’s subsidiary, Alphabet Inc, has introduced a new quantum chip named Willow.
Despite concerns, experts believe Willow is not powerful enough to pose a threat to Bitcoin’s security.
Alphabet Inc, under Google, has launched Willow, its newest quantum chip. There is speculation that Willow could potentially disrupt Bitcoin’s dominance due to its impressive capabilities.
Willow’s Quantum Capabilities
Willow, developed by Google, is a highly potent quantum supercomputer. It can perform certain computational tasks in just five minutes, tasks that would take classical supercomputers 10 septillion years. This duration is significantly larger than the entire existence of the world, which is 13.8 billion years.
The American multinational corporation has described Willow as a “state-of-the-art” chip. It showcases error correction and performance, setting the stage for a functional, large-scale quantum computer. This level of sophistication could render passwords obsolete.
Encrypted messages could easily be intercepted, including nuclear weapon codes. Essentially, anything with a secret key could easily be unlocked through brute-forcing combinations of numbers and letters.
Many believe that Willow has the potential to crack Bitcoin’s complex math algorithm SHA-256, thereby compromising the network.
Willow’s power lies in its qubits, which can reach up to 105, equivalent to improved error rates. Unlike traditional bits that represent either a 0 or 1, qubits can represent both simultaneously due to quantum phenomena like superposition and entanglement.
The presence of qubits allows quantum computers to run at a very high speed, performing multiple calculations at once. They could eventually solve problems currently intractable for classical computers.
However, Bitcoin’s SHA-256 for mining and ECDSA for signatures are believed to be highly vulnerable to quantum decryption.
Bitcoin Remains Unthreatened
Despite these concerns, some experts believe that Willow’s threat to Bitcoin is unfounded. Based on their analysis, Google’s latest quantum computing chip needs to be even more powerful to pose a risk, at least not yet. Therefore, Bitcoin might not face any immediate risks.
“Experts estimate you’d need about 1 million high-quality qubits to make a dent in Bitcoin’s security,” explained Cinemad Producer, a pseudonymous analyst and tech expert.
Therefore, even as advanced as Willow, quantum computers lack the necessary scale or error correction capabilities to decrypt widely used encryption methods immediately. They hardly stand a chance against RSA, ECC used in Bitcoin transactions, or even AES in securing data.
Should quantum computers reach a scale that can factor in large numbers, they could break these encryption schemes. This would compromise wallet security and transaction integrity. Until then, Bitcoin faces no immediate challenge.
Meanwhile, Bitcoin’s price briefly dipped, losing some of its gains in heavy crypto liquidations. From trading at over $97,000 during the early hours of Monday, the firstborn crypto asset plunged to $94,000. Since then, BTC price has recovered slightly and is currently trading at $97,304.83.
0 notes
Text
From Private Keys to Human-Friendly Strings: How Bitcoin Addresses are Crafted

Understanding the transformation from private keys to Bitcoin addresses is crucial for anyone delving into the world of cryptocurrencies. From private keys to Bitcoin addresses, a private key is a randomly generated 256-bit number that serves as a secure password for accessing and managing Bitcoin. This key, typically represented as a 64-character hexadecimal string, is used to generate a public key through elliptic curve multiplication, specifically using the Elliptic Curve Digital Signature Algorithm (ECDSA) with the secp256k1 curve.
The public key, a point on the elliptic curve, is then transformed into a Bitcoin address through a series of cryptographic hash functions. First, the SHA-256 hash function is applied to the public key, followed by the RIPEMD-160 hash function. A network byte (0x00 for Bitcoin mainnet) is added to the beginning of the RIPEMD-160 hash, and the result undergoes a double SHA-256 hashing to create a checksum. The first 4 bytes of this checksum are appended to the hashed result, and the entire string is encoded using Base58Check encoding, producing the final Bitcoin address.
This multi-layered cryptographic process ensures the security and integrity of Bitcoin addresses, highlighting the importance of safeguarding private keys. Understanding this transformation is fundamental for anyone involved in Bitcoin transactions, as it underscores the robust security mechanisms underpinning the Bitcoin network.
0 notes
Photo

Bitcoin's Elliptic Curve Digital Signature Algorithm (ECDSA)
0 notes
Text
Infineon's Cryptographic Library Suffers From An ECDSA Private Key Recovery Vulnerability
http://i.securitythinkingcap.com/TCmt4C
0 notes
Text
Weak TLS/SSL Configuration in Laravel: How to Fix It
When developing web applications, ensuring the security of your website should always be a top priority. One common security vulnerability that can be easily overlooked is the weak TLS/SSL configuration in Laravel applications.

In this blog post, we'll explore what weak TLS/SSL configuration is, why it matters, and how you can fix it to ensure your Laravel application is safe from attacks. Additionally, we'll use our free website security checker tool to demonstrate how you can quickly check Website Vulnerabilities and prevent them.
What is TLS/SSL?
TLS (Transport Layer Security) and SSL (Secure Sockets Layer) are cryptographic protocols designed to provide secure communication over a computer network. Websites that utilize HTTPS (HyperText Transfer Protocol Secure) are using SSL/TLS to encrypt data exchanged between the user’s browser and the server.
Why is Weak TLS/SSL Configuration a Problem?
A weak TLS/SSL configuration can expose your website to various security vulnerabilities, such as:
Man-in-the-middle attacks – Hackers can intercept and alter data transmitted between the user and the website.
Downgrade attacks – Attackers can force the server to use outdated or vulnerable versions of TLS/SSL.
Data leakage – Sensitive data like login credentials, credit card numbers, etc., can be exposed during transmission.
To prevent these threats, it's essential to configure TLS/SSL settings properly and ensure that you're using the latest, most secure protocols and ciphers.
How to Check TLS/SSL Configuration in Laravel
You can check the TLS/SSL configuration of your Laravel application by running a vulnerability scan on your website. One simple way is to use our free website security checker tool at Pentest Testing. This tool analyzes your website’s security and generates a report that identifies weak configurations, including TLS/SSL settings.
Here’s how you can check:
Visit https://free.pentesttesting.com/.
Enter your website URL and click “Check”.
Review the report to see if any weak TLS/SSL configurations are detected.
Here’s a screenshot of the tool’s webpage:

Screenshot of the free tools webpage where you can access security assessment tools.
Fixing Weak TLS/SSL Configuration in Laravel
Laravel provides a straightforward way to configure secure HTTPS connections. Below are steps to fix weak TLS/SSL configurations:
Force HTTPS in the Environment File Laravel allows you to enforce HTTPS by setting the following in your .env file:
APP_URL=https://your-domain.com
This will make Laravel automatically redirect HTTP requests to HTTPS.
2. Use Strong Ciphers in config/ssl.php By default, Laravel doesn’t come with an SSL configuration file, but you can create a custom ssl.php config file in your application. Ensure you are using strong ciphers and the latest TLS versions. Here's an example configuration:
return [ 'tls_version' => 'TLSv1.2', // Use a secure version 'cipher' => 'TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384', // Strong cipher ];
3. Disable Weak Protocols and Ciphers Ensure that weak protocols like SSL 2.0 or SSL 3.0 are disabled on your server. You can configure this in your web server’s settings (Apache, Nginx, etc.) by disabling SSL v2 and v3, and only allowing TLS 1.2 and higher.
Apache Example: Add this configuration in the ssl.conf file:
SSLProtocol All -SSLv2 -SSLv3 SSLCipherSuite HIGH:!aNULL:!MD5:!3DES
Nginx Example: Add this to the nginx.conf:
ssl_protocols TLSv1.2 TLSv1.3; ssl_ciphers 'ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:...';
4. Update Dependencies Always ensure that your Laravel application is up-to-date, as new versions often come with improvements to security settings. You can update Laravel with the following command:
composer update
Checking the Vulnerabilities Report
After making changes to your Laravel application's configuration, it's essential to check the improvements using a security tool. Our website security checker provides a detailed vulnerability assessment. Below is an example of what the assessment report looks like when checking for weak TLS/SSL configurations.

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
Conclusion
Properly configuring TLS/SSL in your Laravel application is crucial to keeping your website secure. By ensuring that your application uses strong encryption protocols and ciphers, you protect both your users and your data from potential attacks. Use tools like our free website security checker to help identify vulnerabilities and improve your site's overall security.
By following these steps and using tools like the free security checker, you can quickly detect and resolve weak TLS/SSL configurations in Laravel. If you need help with vulnerability assessment or penetration testing, feel free to reach out to us at Pentest Testing.
#cyber security#cybersecurity#data security#pentesting#security#the security breach show#laravel#php#ssl#tls
1 note
·
View note
Text
Cryptography in Blockchain: Build Trust in Decentralized Systems

Cryptography is the backbone of blockchain technology, providing tools to protect data, authenticate participants and ensure transaction integrity. The essence of cryptography is to store and decrypt data while protecting against unauthorized access. Blockchain networks use two main encryption techniques- hash functions and public key encryption.
Cryptography ensures that only authorized users can initiate transactions. Blockchain stores transaction data in chunks that are chained over time. Cryptography without hashing. Hashing is the process of converting any data into a unique code, such as a digital fingerprint. Encryption ensures that only authorized users can initiate transactions. Blockchain stores transaction data in chunks that are chained over time. Cryptography without hashing. Hashing is the process of converting any data into a unique code, such as a digital fingerprint.
Importance of Cryptography in Blockchain
Cryptography is the backbone of Blockchain Security, offering several critical functionalities:
Confidentiality: Although the blockchain itself is public, encryption can hide the exact information of transactions and ensure privacy.
Data Integrity: Cryptographic hashing ensures that blockchain records remain unaltered. Any attempt to manipulate the block would be instantly recognizable due to this hash change.
Non-Repudiation: Digital signatures ensure that a transaction originates from specific users and cannot be repudiated later.
Enhancing Trust and Transparency:By removing the need for a central authority, encryption creates a trusted environment where participants can verify information themselves.
Features of Competent Cryptography in Blockchain
Strong Encryption: Strong encryption uses strong encryption algorithms that are resistant to attacks. Commonly used algorithms are SHA-256 for compression and ECDSA (Elliptic Curve Digital Signature Algorithm) for public key encryption.
Decentralization: Blockchain's cryptographic mechanisms are decentralized, meaning that there is no single entity on the network. This decentralization is necessary to maintain the security and integrity of the blockchain.
Consensus Mechanisms: Cryptography supports consensus mechanisms such as Proof-of-Work (PoW) and Proof-of-State (PoS) needed to authenticate transactions and add new blocks to the blockchain.
Anonymity and Privacy: Although the blockchain is transparent, cryptographic techniques ensure that the identities of users remain anonymous. Only the public keys are visible, not the involved parties.
Application of Cryptography to Ensure Blockchain Security
Cryptography plays a multifaceted role in securing blockchain networks:
Securing Transactions: The sender digitally signs the communication with their private key, which ensures authenticity and prevents unauthorized changes.
Block Validation: Miners or authenticators use a cryptographic hash to verify the integrity of each block before adding it to the blockchain.
Consensus Mechanisms: Many consent mechanisms, such as proof of work, rely on cryptography to secure access and prevent unauthorized influence by malicious parties.
Smart Contract Security: Cryptography protects the rules of Smart Contracts, verifying their authenticity and functionality, and preventing vulnerabilities that could lead to hackers.
Challenges Relating to Cryptography
While cryptography offers immense security benefits, it also faces some challenges:
The rise of quantum computers could break some widely used cryptographic algorithms. To solve this problem, post-quantum cryptography is being studied.
Improper use of key functions such as weak passwords or poor storage can compromise the entire system. Accidentally exposing private keys or cryptographic application vulnerabilities can still leave a system open to attack.
How does Nadcab Labs use cryptography to keep blockchain networks secure and trustworthy?
As a Blockchain Development Company, Nadcab Labs uses cryptography to build trust and security at the very foundation of the blockchain network. This is done by combining cryptography principles and technologies. This technology encrypts data and transactions, ensuring confidentiality and immutability on the blockchain.
Furthermore, cryptography is based on consensus protocols that authenticate transactions and authenticate the network as a whole. By using robust cryptography tools and adhering to secure coding practices, Nadcab Labs empowers businesses to confidently participate in the decentralized world of blockchain.
Author Profile:
Siddharth Kanojia work at Nadcab Labs, helping businesses succeed online. He uses SEO strategies to make sure companies show up easily when people search the internet. He uses new technology like blockchain to help businesses grow. At Nadcab Labs, our goal is to help businesses get noticed and do well in the digital world with smart digital marketing and innovative solutions.
Twitter — twitter.com/nadcablabs
LinkedIn — linkedin.com/company/nadcablabs
Facebook — facebook.com/nadcablabs
Instagram — instagram.com/nadcablabs
Spotify — spotify.com/nadcablabs
YouTube — www.youtube.com/@nadcablabs
0 notes
Text
Best Cross-Chain Bridges Powering Interoperability in DeFi

Moving towards decentralization reduces reliance on traditional finance. Embracing bridges is crucial for connecting multiple blockchain networks effectively. To navigate this world, how do we proceed?
DeFi has grown from a peer-to-peer system to a global financial powerhouse, but industry fragmentation into various blockchain ecosystems poses both opportunities and challenges. While enhancing security, these silos limit users to single ecosystems.
With decentralized finance gaining traction, scalability, and high transaction fees are emerging concerns. Seamless asset movement across networks is essential, emphasizing the need for interoperability.
Crypto bridges are essential gateways between blockchain ecosystems, enabling data transfer and asset swaps. Choosing the right bridge is pivotal for accessing diverse opportunities in the evolving DeFi landscape.
Siloed Blockchain Ecosystems
The decentralized finance industry comprises various independent blockchain ecosystems, each with its consensus mechanisms, governance models, and native assets. While this siloed nature enhances security, it also limits users to a single blockchain network. Blockchains like CosVM Network and Ethereum are isolated, preventing users from accessing dApps or liquidity pools on other networks like Avalanche. This segregation ensures security but restricts flexibility. For instance, switching to another network cannot avoid high gas fees on Ethereum. As DeFi grows, this need for interoperability has become a significant limitation, leading to the development of blockchain bridges as a solution.
With decentralized finance gaining traction, the drawbacks of siloed blockchain ecosystems became evident. Users were confined to one chain's features, each with strengths and weaknesses. To address this, cross-chain bridges emerged, allowing asset transfers between chains. These bridges act as portals, enabling users to utilize the best attributes of multiple networks. This interoperability has driven DeFi growth, enabling platforms to integrate multiple networks for superior experiences and facilitating the free flow of liquidity across chains.
The Best Blockchain Bridge
In the DeFi world, it shines as the pinnacle of interoperability, providing the perfect solution for effortless asset transfers between blockchain networks. As one of DeFi's top cross-chain bridges, it plays a pivotal role in fueling the interoperability movement. With its groundbreaking technology, it facilitates secure and swift cross-chain swaps, allowing users to transcend ecosystem limitations and seize diverse opportunities, from accessing low-cost transactions to exploring new investments.
Powered by a decentralized architecture, it ensures the utmost security for user funds. Utilizing advanced cryptographic techniques like zero-knowledge proofs enables private transfers across chains. At its core lies CosVM's high-speed relay network, capable of processing thousands of transactions per second, ensuring near real-time swaps and minimal slippage with elegant token locking and minting mechanisms. By harnessing innovative cross-chain infrastructure, projects can seamlessly integrate various blockchain ecosystems, unlocking immense potential for collaboration and growth in DeFi. In essence, it represents the future of a truly decentralized financial system.
Key Features and Benefits
It stands out from other cross-chain bridges thanks to its Strong feature set engineered for optimized performance. Some of the key highlights include:
Speed - offers exceptionally fast cross-chain transfers, with swaps taking as little as 5-10 seconds in many cases. This enables users to capitalize on arbitrage opportunities and other time-sensitive investments requiring quick transfers between chains.
Security - Leverages cutting-edge cryptography like ECDSA signature validation and Merkle proof verification to ensure transaction security. User funds are protected through mechanisms like validity proofs, preventing fraud.
Low Fees - Transfer fees on they are a fraction of the cost compared to alternatives. Low fees enable easy asset movement without the high associated costs eroding value.
These features translate into tangible benefits for DeFi users:
Easy Asset Transfer - The fast, low-cost transfers facilitated by it make moving assets between chains simple and accessible. Users can easily tap opportunities on different networks.
Capitalizing on Opportunities - Speed and low fees allow users to capitalize on fleeting arbitrage windows, yield farming opportunities, and other investments requiring quick cross-chain activity.
Unlocking True Interoperability - A smooth user experience unlocks the potential of interoperability and makes collaborating across chains seamless.
Our main technical architecture provides the ideal foundation for the interoperable future of DeFi.
Use Cases and Applications
Enables a myriad of use cases that demonstrate the power of its cross-chain bridging capabilities. Here are some key examples:
Asset Transfers
Users can seamlessly transfer assets between supported blockchain networks. For instance, you can swap ETH on Ethereum for BNB on the BNB Chain in seconds by leveraging CosVM's bridge. This provides easy access to liquidity across different ecosystems.
Yield Farming
By bridging assets to various chains, users can maximize yields by accessing exclusive farming opportunities on platforms like PancakeSwap or TraderJoe. This allows you to earn yields that are not possible by staying on a single chain.
dApp Integration
Decentralized applications can integrate to unlock cross-chain capabilities and features from various networks. For example, a lending protocol on Polygon can use CosVM to accept BTC as collateral from Bitcoin's network. This expands the dApp's utility and use cases.
Summary
The blog emphasizes the critical role of cross-chain bridges in DeFi for enabling interoperability between blockchain ecosystems. It highlights the challenges of siloed networks and how cross-chain bridges facilitate asset transfers, smart contract interoperability, and dApps integration. The blog showcases CosVM's advanced cryptography, fast transfer speeds, and low fees as key features, positioning it as a leading cross-chain bridge in the DeFi space.
0 notes