#explanation: binary 10 is a 2 in decimal
Explore tagged Tumblr posts
Text
Bojan: Martin, are you binary? Bojan: Because to me your looks are 1 and a 0. Martin: Martin: Who are you calling a 2?
#my little brain is mush#explanation: binary 10 is a 2 in decimal#10 in binary is 1010#i do binary and decimal conversions for fun sometimes...I'm normal i swear#joker out#my jokes are awful jesus#I have more Martin jokes I could pull off#joker out bojan#joker out martin#bojan cvjetićanin#martin jurkovič#joker out incorrect quotes#incorrect quotes
22 notes
·
View notes
Text
Parity-calculating circuit!
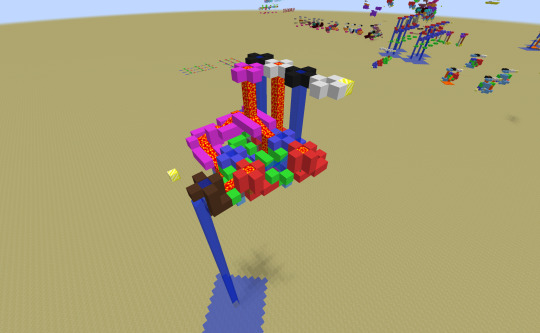
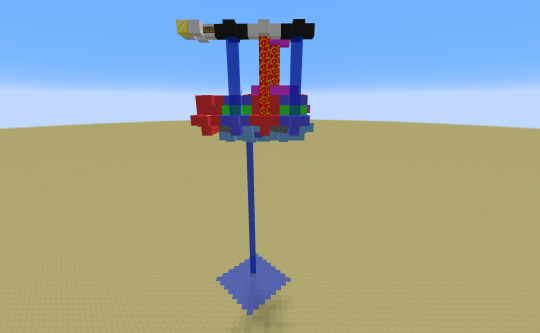

Explanation below the cut.
As even-numbered base natives (decimal, binary, hex, octal, etc.) we take for granted that determining the parity of a given integer (is it even or odd) is trivial. Just look at the last digit! parity(x) = parity(x % b), where x is some integer and b is the radix of your number system. (e.g. in decimal parity(107) = parity(107 % 10) = parity(7) = odd).
In binary this even easier, as the least-significant digit can only be either 0 or 1: even or odd.
Not so for odd-numbered bases! As a trivial counterexample, 1T0 (dec. 6) is even and has an even least significant digit (0, dec. 0); 1T (dec. 2) is even but has an odd lsd (T, dec. -1).
Fortunately, we have a slightly more roundabout way of determining parity. The parity of any given balanced ternary integer is equal to the parity of the sum of its digits, for example 1T10 [dec. 21] is odd and 1 + T + 1 + 0 = 1 [dec. 1 + -1 + 1 + 0 = 1], which is also odd.
This makes some intuitive sense if we consider five facts:
The parity of the sum of any two integers is even iff both are even or both are odd; the sum of any two integers is odd iff one is odd and the other is even.
The parity of the sum of a given set of integers is equal to the parity of the count of odd integers in that set. For example, Σ{1, 2, 3} is even because there an even number of odd numbers (specifically 2: 1 and 3), Σ{1, 2, 3, 3} is odd because there an odd number of odd numbers (specifically 3: 1, 3 and 3). Why does this work? Let's step through a bigger example: Σ{1, 2, 3, 7, 9, 2, 0, 5}. First, we'll group these numbers by their parity: (1 + 3 + 7 + 9 + 5) + (2 + 2 + 0) We know that the sum of the even numbers can only be even, so for the purpose of calculating parity we can simply ignore them. Only the sum of the odd numbers will have any bearing on the result. Second, we'll try to group the odd numbers into pairs: ((1 + 3) + (7 + 9)) + 5 Since we had an odd number of odd numbers, we are left with one unpaired number. Since the sum of odd + odd is even, these paired odds will all sum to even numbers: (4 + 16) + 5 The sum of these results can thus also only be even: 20 + 5 Odd + even = odd (20 + 5 = 25, which is odd) If there has been an even number of odd numbers, we wouldn't have had an unpaired odd number, and thus the result would have been even.
The product of any two integers is odd if both are odd, otherwise it's even. (e.g. 5 * 7 = 35, 6 * 7 = 42, 6 * 8 = 48)
Since 3 (our radix) is odd, 3 to any nonnegative power will also be odd -- exponentiation is of course merely successive multiplication. Thus, the parity of any given digit * radix-to-some-power product will be determined by the parity of that digit -- it doesn't matter what that power is. 1 * 3^0 is odd, 1 * 3^1 is odd, 1 * 3^2 is odd, 1 * 3^982908 is odd. Likewise, 0 * 3^0 is even, 0 * 3^1 is even, 0 * 3^2 is even, 0 * 3^982908 is even.
Any number can be written as a sum of products between digit values and increasing powers of the number system's radix. For example: 127 in decimal is equal to 1 * 10^2 + 2 * 10^1 + 7 * 10^0, and 11T0 in balanced ternary is equal to 1 * 3^3 + 1 * 3^2 + -1 * 3^1 + 0 * 3^0.
Let's apply this to our original example: parity(1T10) [dec. 21]. First, we re-write it as parity(1 * 3^3 + -1 * 3^2 + 1 * 3^1 + 0 * 3^0). Because 3 to any nonnegative power is odd, we can rewrite this as parity(1 * 3^0 + -1 * 3^0 + 1 * 3^0 + 0 * 3^0).
3^0 is 1, and 1 is the multiplicative identity, so we can re-write this further as parity(1 + -1 + 1 + 0). (Hey, that's the sum of the digits!)
Finally, we know from earlier that the parity of the sum of any set of integers is equal to the parity of the count of odd numbers in that set. Since there are three odd integers in this sum, and three is odd, we know that parity(1 + -1 + 1 + 0) is odd.
We can take advantage of this fact to build a (relatively) simple parity-determining circuit out of successive stages of half-adders. The first will compute 1 + -1 = 0 and 1 + 0 = 1, the second will compute 0 + 1 = 1.
But wait a minute: half-adders have carry-outs. They're not guaranteed to produce fewer digits of output than they get as input! Fortunately, we can take advantage of the fact that C_out and S will never be nonnegative and equal, and thus we can calculate their sum with an OR gate. Take 1101 [Dec. 37], then. 1 + 1 = 1T and 0 + 1 = 01, 1 OR T = 0 and 0 OR 1 = 1, 0 + 1 = 01, 0 OR 1 = 1. 1 is odd, hooray!
Here's another interesting observation: since the Sum output of a half adder is equal to (A XOR B) OR (A NAND B) and C_out is equal to (A AND B), what we're actually calculating here is ((A XOR B) OR (A NAND B)) OR (A AND B), aka (A XOR B) OR ((A NAND B) OR (A AND B)), aka (A XOR B) OR 0, aka A XOR B!
So it seems we don't actually have to bother taking the sums in the first place, any parity-preserving gate with two or more inputs will suffice. In other words, we can use any gate obeying this truth table:
| | T | 0 | 1 | |---|---|---|---| | T | 0 | a | 0 | | 0 | b | 0 | c | | 1 | 0 | d | 0 |
Where a, b, c, d ∈ {T, 1}.
XOR is one such gate, but it's not the easiest of them to construct. The pictured circuit is constructed with a (as-of-yet unnamed) gate following this truth table:
| | T | 0 | 1 | |---|---|---|---| | T | 0 | 1 | 0 | | 0 | T | 0 | T | | 1 | 0 | 1 | 0 |
And the final result is fed into an ABS gate, a single-input gate following this truth table:
| a | q | |---|---| | T | 1 | | 0 | 0 | | 1 | 1 |
9 notes
·
View notes
Link
Data Structures and Algorithms from Zero to Hero and Crack Top Companies 100+ Interview questions (Java Coding)
What you’ll learn
Java Data Structures and Algorithms Masterclass
Learn, implement, and use different Data Structures
Learn, implement and use different Algorithms
Become a better developer by mastering computer science fundamentals
Learn everything you need to ace difficult coding interviews
Cracking the Coding Interview with 100+ questions with explanations
Time and Space Complexity of Data Structures and Algorithms
Recursion
Big O
Dynamic Programming
Divide and Conquer Algorithms
Graph Algorithms
Greedy Algorithms
Requirements
Basic Java Programming skills
Description
Welcome to the Java Data Structures and Algorithms Masterclass, the most modern, and the most complete Data Structures and Algorithms in Java course on the internet.
At 44+ hours, this is the most comprehensive course online to help you ace your coding interviews and learn about Data Structures and Algorithms in Java. You will see 100+ Interview Questions done at the top technology companies such as Apple, Amazon, Google, and Microsoft and how-to face Interviews with comprehensive visual explanatory video materials which will bring you closer to landing the tech job of your dreams!
Learning Java is one of the fastest ways to improve your career prospects as it is one of the most in-demand tech skills! This course will help you in better understanding every detail of Data Structures and how algorithms are implemented in high-level programming languages.
We’ll take you step-by-step through engaging video tutorials and teach you everything you need to succeed as a professional programmer.
After finishing this course, you will be able to:
Learn basic algorithmic techniques such as greedy algorithms, binary search, sorting, and dynamic programming to solve programming challenges.
Learn the strengths and weaknesses of a variety of data structures, so you can choose the best data structure for your data and applications
Learn many of the algorithms commonly used to sort data, so your applications will perform efficiently when sorting large datasets
Learn how to apply graph and string algorithms to solve real-world challenges: finding shortest paths on huge maps and assembling genomes from millions of pieces.
Why this course is so special and different from any other resource available online?
This course will take you from the very beginning to very complex and advanced topics in understanding Data Structures and Algorithms!
You will get video lectures explaining concepts clearly with comprehensive visual explanations throughout the course.
You will also see Interview Questions done at the top technology companies such as Apple, Amazon, Google, and Microsoft.
I cover everything you need to know about the technical interview process!
So whether you are interested in learning the top programming language in the world in-depth and interested in learning the fundamental Algorithms, Data Structures, and performance analysis that make up the core foundational skillset of every accomplished programmer/designer or software architect and is excited to ace your next technical interview this is the course for you!
And this is what you get by signing up today:
Lifetime access to 44+ hours of HD quality videos. No monthly subscription. Learn at your own pace, whenever you want
Friendly and fast support in the course Q&A whenever you have questions or get stuck
FULL money-back guarantee for 30 days!
This course is designed to help you to achieve your career goals. Whether you are looking to get more into Data Structures and Algorithms, increase your earning potential, or just want a job with more freedom, this is the right course for you!
The topics that are covered in this course.
Section 1 – Introduction
What are Data Structures?
What is an algorithm?
Why are Data Structures And Algorithms important?
Types of Data Structures
Types of Algorithms
Section 2 – Recursion
What is Recursion?
Why do we need recursion?
How does Recursion work?
Recursive vs Iterative Solutions
When to use/avoid Recursion?
How to write Recursion in 3 steps?
How to find Fibonacci numbers using Recursion?
Section 3 – Cracking Recursion Interview Questions
Question 1 – Sum of Digits
Question 2 – Power
Question 3 – Greatest Common Divisor
Question 4 – Decimal To Binary
Section 4 – Bonus CHALLENGING Recursion Problems (Exercises)
power
factorial
products array
recursiveRange
fib
reverse
palindrome
some recursive
flatten
capitalize first
nestedEvenSum
capitalize words
stringifyNumbers
collects things
Section 5 – Big O Notation
Analogy and Time Complexity
Big O, Big Theta, and Big Omega
Time complexity examples
Space Complexity
Drop the Constants and the nondominant terms
Add vs Multiply
How to measure the codes using Big O?
How to find time complexity for Recursive calls?
How to measure Recursive Algorithms that make multiple calls?
Section 6 – Top 10 Big O Interview Questions (Amazon, Facebook, Apple, and Microsoft)
Product and Sum
Print Pairs
Print Unordered Pairs
Print Unordered Pairs 2 Arrays
Print Unordered Pairs 2 Arrays 100000 Units
Reverse
O(N) Equivalents
Factorial Complexity
Fibonacci Complexity
Powers of 2
Section 7 – Arrays
What is an Array?
Types of Array
Arrays in Memory
Create an Array
Insertion Operation
Traversal Operation
Accessing an element of Array
Searching for an element in Array
Deleting an element from Array
Time and Space complexity of One Dimensional Array
One Dimensional Array Practice
Create Two Dimensional Array
Insertion – Two Dimensional Array
Accessing an element of Two Dimensional Array
Traversal – Two Dimensional Array
Searching for an element in Two Dimensional Array
Deletion – Two Dimensional Array
Time and Space complexity of Two Dimensional Array
When to use/avoid array
Section 8 – Cracking Array Interview Questions (Amazon, Facebook, Apple, and Microsoft)
Question 1 – Missing Number
Question 2 – Pairs
Question 3 – Finding a number in an Array
Question 4 – Max product of two int
Question 5 – Is Unique
Question 6 – Permutation
Question 7 – Rotate Matrix
Section 9 – CHALLENGING Array Problems (Exercises)
Middle Function
2D Lists
Best Score
Missing Number
Duplicate Number
Pairs
Section 10 – Linked List
What is a Linked List?
Linked List vs Arrays
Types of Linked List
Linked List in the Memory
Creation of Singly Linked List
Insertion in Singly Linked List in Memory
Insertion in Singly Linked List Algorithm
Insertion Method in Singly Linked List
Traversal of Singly Linked List
Search for a value in Single Linked List
Deletion of a node from Singly Linked List
Deletion Method in Singly Linked List
Deletion of entire Singly Linked List
Time and Space Complexity of Singly Linked List
Section 11 – Circular Singly Linked List
Creation of Circular Singly Linked List
Insertion in Circular Singly Linked List
Insertion Algorithm in Circular Singly Linked List
Insertion method in Circular Singly Linked List
Traversal of Circular Singly Linked List
Searching a node in Circular Singly Linked List
Deletion of a node from Circular Singly Linked List
Deletion Algorithm in Circular Singly Linked List
A method in Circular Singly Linked List
Deletion of entire Circular Singly Linked List
Time and Space Complexity of Circular Singly Linked List
Section 12 – Doubly Linked List
Creation of Doubly Linked List
Insertion in Doubly Linked List
Insertion Algorithm in Doubly Linked List
Insertion Method in Doubly Linked List
Traversal of Doubly Linked List
Reverse Traversal of Doubly Linked List
Searching for a node in Doubly Linked List
Deletion of a node in Doubly Linked List
Deletion Algorithm in Doubly Linked List
Deletion Method in Doubly Linked List
Deletion of entire Doubly Linked List
Time and Space Complexity of Doubly Linked List
Section 13 – Circular Doubly Linked List
Creation of Circular Doubly Linked List
Insertion in Circular Doubly Linked List
Insertion Algorithm in Circular Doubly Linked List
Insertion Method in Circular Doubly Linked List
Traversal of Circular Doubly Linked List
Reverse Traversal of Circular Doubly Linked List
Search for a node in Circular Doubly Linked List
Delete a node from Circular Doubly Linked List
Deletion Algorithm in Circular Doubly Linked List
Deletion Method in Circular Doubly Linked List
Entire Circular Doubly Linked List
Time and Space Complexity of Circular Doubly Linked List
Time Complexity of Linked List vs Arrays
Section 14 – Cracking Linked List Interview Questions (Amazon, Facebook, Apple, and Microsoft)
Linked List Class
Question 1 – Remove Dups
Question 2 – Return Kth to Last
Question 3 – Partition
Question 4 – Sum Linked Lists
Question 5 – Intersection
Section 15 – Stack
What is a Stack?
What and Why of Stack?
Stack Operations
Stack using Array vs Linked List
Stack Operations using Array (Create, isEmpty, isFull)
Stack Operations using Array (Push, Pop, Peek, Delete)
Time and Space Complexity of Stack using Array
Stack Operations using Linked List
Stack methods – Push, Pop, Peek, Delete, and isEmpty using Linked List
Time and Space Complexity of Stack using Linked List
When to Use/Avoid Stack
Stack Quiz
Section 16 – Queue
What is a Queue?
Linear Queue Operations using Array
Create, isFull, isEmpty, and enQueue methods using Linear Queue Array
Dequeue, Peek and Delete Methods using Linear Queue Array
Time and Space Complexity of Linear Queue using Array
Why Circular Queue?
Circular Queue Operations using Array
Create, Enqueue, isFull and isEmpty Methods in Circular Queue using Array
Dequeue, Peek and Delete Methods in Circular Queue using Array
Time and Space Complexity of Circular Queue using Array
Queue Operations using Linked List
Create, Enqueue and isEmpty Methods in Queue using Linked List
Dequeue, Peek and Delete Methods in Queue using Linked List
Time and Space Complexity of Queue using Linked List
Array vs Linked List Implementation
When to Use/Avoid Queue?
Section 17 – Cracking Stack and Queue Interview Questions (Amazon, Facebook, Apple, Microsoft)
Question 1 – Three in One
Question 2 – Stack Minimum
Question 3 – Stack of Plates
Question 4 – Queue via Stacks
Question 5 – Animal Shelter
Section 18 – Tree / Binary Tree
What is a Tree?
Why Tree?
Tree Terminology
How to create a basic tree in Java?
Binary Tree
Types of Binary Tree
Binary Tree Representation
Create Binary Tree (Linked List)
PreOrder Traversal Binary Tree (Linked List)
InOrder Traversal Binary Tree (Linked List)
PostOrder Traversal Binary Tree (Linked List)
LevelOrder Traversal Binary Tree (Linked List)
Searching for a node in Binary Tree (Linked List)
Inserting a node in Binary Tree (Linked List)
Delete a node from Binary Tree (Linked List)
Delete entire Binary Tree (Linked List)
Create Binary Tree (Array)
Insert a value Binary Tree (Array)
Search for a node in Binary Tree (Array)
PreOrder Traversal Binary Tree (Array)
InOrder Traversal Binary Tree (Array)
PostOrder Traversal Binary Tree (Array)
Level Order Traversal Binary Tree (Array)
Delete a node from Binary Tree (Array)
Entire Binary Tree (Array)
Linked List vs Python List Binary Tree
Section 19 – Binary Search Tree
What is a Binary Search Tree? Why do we need it?
Create a Binary Search Tree
Insert a node to BST
Traverse BST
Search in BST
Delete a node from BST
Delete entire BST
Time and Space complexity of BST
Section 20 – AVL Tree
What is an AVL Tree?
Why AVL Tree?
Common Operations on AVL Trees
Insert a node in AVL (Left Left Condition)
Insert a node in AVL (Left-Right Condition)
Insert a node in AVL (Right Right Condition)
Insert a node in AVL (Right Left Condition)
Insert a node in AVL (all together)
Insert a node in AVL (method)
Delete a node from AVL (LL, LR, RR, RL)
Delete a node from AVL (all together)
Delete a node from AVL (method)
Delete entire AVL
Time and Space complexity of AVL Tree
Section 21 – Binary Heap
What is Binary Heap? Why do we need it?
Common operations (Creation, Peek, sizeofheap) on Binary Heap
Insert a node in Binary Heap
Extract a node from Binary Heap
Delete entire Binary Heap
Time and space complexity of Binary Heap
Section 22 – Trie
What is a Trie? Why do we need it?
Common Operations on Trie (Creation)
Insert a string in Trie
Search for a string in Trie
Delete a string from Trie
Practical use of Trie
Section 23 – Hashing
What is Hashing? Why do we need it?
Hashing Terminology
Hash Functions
Types of Collision Resolution Techniques
Hash Table is Full
Pros and Cons of Resolution Techniques
Practical Use of Hashing
Hashing vs Other Data structures
Section 24 – Sort Algorithms
What is Sorting?
Types of Sorting
Sorting Terminologies
Bubble Sort
Selection Sort
Insertion Sort
Bucket Sort
Merge Sort
Quick Sort
Heap Sort
Comparison of Sorting Algorithms
Section 25 – Searching Algorithms
Introduction to Searching Algorithms
Linear Search
Linear Search in Python
Binary Search
Binary Search in Python
Time Complexity of Binary Search
Section 26 – Graph Algorithms
What is a Graph? Why Graph?
Graph Terminology
Types of Graph
Graph Representation
The graph in Java using Adjacency Matrix
The graph in Java using Adjacency List
Section 27 – Graph Traversal
Breadth-First Search Algorithm (BFS)
Breadth-First Search Algorithm (BFS) in Java – Adjacency Matrix
Breadth-First Search Algorithm (BFS) in Java – Adjacency List
Time Complexity of Breadth-First Search (BFS) Algorithm
Depth First Search (DFS) Algorithm
Depth First Search (DFS) Algorithm in Java – Adjacency List
Depth First Search (DFS) Algorithm in Java – Adjacency Matrix
Time Complexity of Depth First Search (DFS) Algorithm
BFS Traversal vs DFS Traversal
Section 28 – Topological Sort
What is Topological Sort?
Topological Sort Algorithm
Topological Sort using Adjacency List
Topological Sort using Adjacency Matrix
Time and Space Complexity of Topological Sort
Section 29 – Single Source Shortest Path Problem
what is Single Source Shortest Path Problem?
Breadth-First Search (BFS) for Single Source Shortest Path Problem (SSSPP)
BFS for SSSPP in Java using Adjacency List
BFS for SSSPP in Java using Adjacency Matrix
Time and Space Complexity of BFS for SSSPP
Why does BFS not work with Weighted Graph?
Why does DFS not work for SSSP?
Section 30 – Dijkstra’s Algorithm
Dijkstra’s Algorithm for SSSPP
Dijkstra’s Algorithm in Java – 1
Dijkstra’s Algorithm in Java – 2
Dijkstra’s Algorithm with Negative Cycle
Section 31 – Bellman-Ford Algorithm
Bellman-Ford Algorithm
Bellman-Ford Algorithm with negative cycle
Why does Bellman-Ford run V-1 times?
Bellman-Ford in Python
BFS vs Dijkstra vs Bellman Ford
Section 32 – All Pairs Shortest Path Problem
All pairs shortest path problem
Dry run for All pair shortest path
Section 33 – Floyd Warshall
Floyd Warshall Algorithm
Why Floyd Warshall?
Floyd Warshall with negative cycle,
Floyd Warshall in Java,
BFS vs Dijkstra vs Bellman Ford vs Floyd Warshall,
Section 34 – Minimum Spanning Tree
Minimum Spanning Tree,
Disjoint Set,
Disjoint Set in Java,
Section 35 – Kruskal’s and Prim’s Algorithms
Kruskal Algorithm,
Kruskal Algorithm in Python,
Prim’s Algorithm,
Prim’s Algorithm in Python,
Prim’s vs Kruskal
Section 36 – Cracking Graph and Tree Interview Questions (Amazon, Facebook, Apple, Microsoft)
Section 37 – Greedy Algorithms
What is a Greedy Algorithm?
Well known Greedy Algorithms
Activity Selection Problem
Activity Selection Problem in Python
Coin Change Problem
Coin Change Problem in Python
Fractional Knapsack Problem
Fractional Knapsack Problem in Python
Section 38 – Divide and Conquer Algorithms
What is a Divide and Conquer Algorithm?
Common Divide and Conquer algorithms
How to solve the Fibonacci series using the Divide and Conquer approach?
Number Factor
Number Factor in Java
House Robber
House Robber Problem in Java
Convert one string to another
Convert One String to another in Java
Zero One Knapsack problem
Zero One Knapsack problem in Java
Longest Common Sequence Problem
Longest Common Subsequence in Java
Longest Palindromic Subsequence Problem
Longest Palindromic Subsequence in Java
Minimum cost to reach the Last cell problem
Minimum Cost to reach the Last Cell in 2D array using Java
Number of Ways to reach the Last Cell with given Cost
Number of Ways to reach the Last Cell with given Cost in Java
Section 39 – Dynamic Programming
What is Dynamic Programming? (Overlapping property)
Where does the name of DC come from?
Top-Down with Memoization
Bottom-Up with Tabulation
Top-Down vs Bottom Up
Is Merge Sort Dynamic Programming?
Number Factor Problem using Dynamic Programming
Number Factor: Top-Down and Bottom-Up
House Robber Problem using Dynamic Programming
House Robber: Top-Down and Bottom-Up
Convert one string to another using Dynamic Programming
Convert String using Bottom Up
Zero One Knapsack using Dynamic Programming
Zero One Knapsack – Top Down
Zero One Knapsack – Bottom Up
Section 40 – CHALLENGING Dynamic Programming Problems
Longest repeated Subsequence Length problem
Longest Common Subsequence Length problem
Longest Common Subsequence problem
Diff Utility
Shortest Common Subsequence problem
Length of Longest Palindromic Subsequence
Subset Sum Problem
Egg Dropping Puzzle
Maximum Length Chain of Pairs
Section 41 – A Recipe for Problem Solving
Introduction
Step 1 – Understand the problem
Step 2 – Examples
Step 3 – Break it Down
Step 4 – Solve or Simplify
Step 5 – Look Back and Refactor
Section 41 – Wild West
Download
To download more paid courses for free visit course catalog where 1000+ paid courses available for free. You can get the full course into your device with just a single click. Follow the link above to download this course for free.
3 notes
·
View notes
Text
Tutorial – Arduino and Four Digit Seven Segment Display Module
This is a quick start guide for the Four Digit Seven Segment Display Module and Enclosure from PMD Way. This module offers a neat and bright display which is ideal for numeric or hexadecimal data. It can display the digits 0 to 9 including the decimal point, and the letters A to F. You can also control each segment individually if desired.
Each module contains four 74HC595 shift registers – once of each controls a digit. If you carefully remove the back panel from the enclosure, you can see the pin connections:

If you’re only using one display, use the group of pins at the centre-bottom of the board. From left to right the connections are:
Data out (ignore for single display use)
VCC – connect to a 3.3V or 5V supply
GND – connect to your GND line
SDI – data in – connect to the data out pin on your Arduino/other board
LCK – latch – connect to the output pin on your Arduino or other board that will control the latch
CLK – clock – connect to the output pin on your Arduino or other board that will control the clock signal
For the purposes of our Arduino tutorial, connect VCC to the 5V pin, GND to GND, SDI to D11, LCK to D13 and CLK to D12.
If you are connecting more than one module, use the pins on the left- and right-hand side of the module. Start with the connections from your Arduino (etc) to the right-hand side, as this is where the DIN (data in) pin is located.
Then connect the pins on the left-hand side of the module to the right-hand side of the new module – and so forth. SDO (data out) will connect to the SDI (data in) – with the other pins being identical for connection.
The module schematic is shown below:
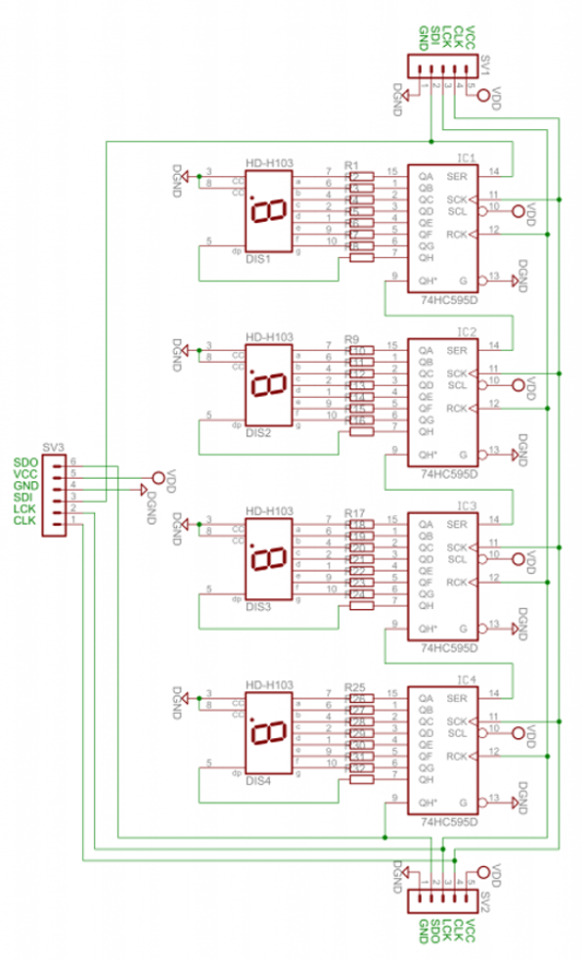
Arduino Example Sketch
Once you have made the connections to your Arduino as outlined above, upload the following sketch:
// Demonstration Arduino sketch for four digit, seven segment display with enclosure // https://pmdway.com/collections/7-segment-numeric-leds/products/four-digit-seven-segment-display-module-and-enclosure int latchPin = 13; // connect to LCK pin intclockPin = 12; // connect to CLK pin intdataPin = 11; // connect to SDI pin int LED_SEG_TAB[]={ 0xfc,0x60,0xda,0xf2,0x66,0xb6,0xbe,0xe0,0xfe,0xf6,0x01,0xee,0x3e,0x1a,0x7a,0x9e,0x8e,0x01,0x00}; //0 1 2 3 4 5 6 7 8 9 dp . a b c d e f off void setup() { //set pins to output so you can control the shift register pinMode(latchPin, OUTPUT); pinMode(clockPin, OUTPUT); pinMode(dataPin, OUTPUT); } void displayNumber(int value, boolean leadingZero) // break down "value" into digits and store in a,b,c,d { int a,b,c,d; a = value / 1000; value = value % 1000; b = value / 100; value = value % 100; c = value / 10; value = value % 10; d = value; if (leadingZero==false) // removing leading zeros { if (a==0 && b>0) { a = 18; } if (a==0 && b==0 && c>0) { a = 18; b = 18; } if (a==0 && b==0 && c==0) { a = 18; b = 18; c = 18; } if (a==0 && b==0 && c==0 && d==0) { a = 18; b = 18; c = 18; d = 18; } } digitalWrite(latchPin, LOW); shiftOut(dataPin, clockPin, LSBFIRST, LED_SEG_TAB[d]); shiftOut(dataPin, clockPin, LSBFIRST, LED_SEG_TAB[c]); shiftOut(dataPin, clockPin, LSBFIRST, LED_SEG_TAB[b]); shiftOut(dataPin, clockPin, LSBFIRST, LED_SEG_TAB[a]); digitalWrite(latchPin, HIGH); } void allOff() // turns off all segments { digitalWrite(latchPin, LOW); shiftOut(dataPin, clockPin, LSBFIRST, 0); shiftOut(dataPin, clockPin, LSBFIRST, 0); shiftOut(dataPin, clockPin, LSBFIRST, 0); shiftOut(dataPin, clockPin, LSBFIRST, 0); digitalWrite(latchPin, HIGH); } void loop() { for (int z=900; z<=1100; z++) { displayNumber(z, false); delay(10); } delay(1000); for (int z=120; z>=0; --z) { displayNumber(z, true); delay(10); } delay(1000); digitalWrite(latchPin, LOW); shiftOut(dataPin, clockPin, LSBFIRST, LED_SEG_TAB[14]); shiftOut(dataPin, clockPin, LSBFIRST, LED_SEG_TAB[13]); shiftOut(dataPin, clockPin, LSBFIRST, LED_SEG_TAB[12]); shiftOut(dataPin, clockPin, LSBFIRST, LED_SEG_TAB[11]); digitalWrite(latchPin, HIGH); delay(1000); digitalWrite(latchPin, LOW); shiftOut(dataPin, clockPin, LSBFIRST, LED_SEG_TAB[16]); shiftOut(dataPin, clockPin, LSBFIRST, LED_SEG_TAB[15]); shiftOut(dataPin, clockPin, LSBFIRST, LED_SEG_TAB[14]); shiftOut(dataPin, clockPin, LSBFIRST, LED_SEG_TAB[13]); digitalWrite(latchPin, HIGH); delay(1000); digitalWrite(latchPin, LOW); shiftOut(dataPin, clockPin, LSBFIRST, LED_SEG_TAB[0]); shiftOut(dataPin, clockPin, LSBFIRST, LED_SEG_TAB[1]); shiftOut(dataPin, clockPin, LSBFIRST, LED_SEG_TAB[2]); shiftOut(dataPin, clockPin, LSBFIRST, LED_SEG_TAB[3]+1); digitalWrite(latchPin, HIGH); delay(1000); digitalWrite(latchPin, LOW); shiftOut(dataPin, clockPin, LSBFIRST, LED_SEG_TAB[7]); shiftOut(dataPin, clockPin, LSBFIRST, LED_SEG_TAB[6]+1); shiftOut(dataPin, clockPin, LSBFIRST, LED_SEG_TAB[5]); shiftOut(dataPin, clockPin, LSBFIRST, LED_SEG_TAB[4]); digitalWrite(latchPin, HIGH); delay(1000); }
After a moment you should see the display spring into action in the same way as in the demonstration video:
youtube
How does it work?
First we define which digital output pins are used for latch, clock and data on lines four to six. On line eight we have created an array which contains values that are sent to the shift registers in the module to display the possible digits and letters. For example, the first – 0xfc – will activate the segments to display a zero, 0x7a for the letter C, and so on.
From line 20 we’ve created a custom function that is used to send a whole number between zero and 9999 to the display. To do so, simply use:
void displayNumber(value, true/false);
where value is the number to display (or variable containing the number) – and the second parameter of true or false. This controls whether you have a leading zero displayed – true for yes, false for no.
For example, to display “0123” you would use:
displayNumber(123, true);
… which results with:

or to display “500” you would use:
displayNumber(500, false);
… which results with:

To turn off all the digits, you need to send zeros to every bit in the shift register, and this is accomplished with the function in the sketch called
allOff();
What about the decimal point?
To turn on the decimal point for a particular digit, add 1 to the value being sent to a particular digit. Using the code from the demonstration sketch to display 87.65 you would use:
digitalWrite(latchPin, LOW); shiftOut(dataPin, clockPin, LSBFIRST, LED_SEG_TAB[5]); shiftOut(dataPin, clockPin, LSBFIRST, LED_SEG_TAB[6]); shiftOut(dataPin, clockPin, LSBFIRST, LED_SEG_TAB[7]+1); // added one for decimal point shiftOut(dataPin, clockPin, LSBFIRST, LED_SEG_TAB[8]); digitalWrite(latchPin, HIGH);
… which results with:

In-depth explanation of how the module is controlled
As shown in the schematic above, each digit is controlled by a 74HC595 shift register. Each shift register has eight digital outputs, each of which control an individual segment of each digit. So by sending four bytes of data (one byte = eight bits) you can control each segment of the display.
Each digit’s segments are mapped as follows:

And the outputs from each shift register match the order of segments from left to right. So outputs 0~7 match A~G then decimal point.
For example, to create the number seven with a decimal point, you need to turn on segments A, B, C and DP – which match to the shift register’s outputs 0,1,2,8.
Thus the byte to send to the shift register would be 0b11100001 (or 225 in decimal or 0xE1 in hexadecimal).
Every time you want to change the display you need to re-draw all four (or more if more than one module is connected) digits – so four bytes of data are sent for each display change. The digits are addressed from right to left, so the first byte send is for the last digit – and the last byte is for the first digit.
There are three stages of updating the display.
Set the LCK (latch) line low
Shift out four bytes of data from your microcontroller
Set the LCK (latch) line high
For example, using Arduino code we use:
digitalWrite(latchPin, LOW); shiftOut(dataPin, clockPin, LSBFIRST, 0b10000000); // digit 4 shiftOut(dataPin, clockPin, LSBFIRST, 0b01000000); // digit 3 shiftOut(dataPin, clockPin, LSBFIRST, 0b00100000); // digit 2 shiftOut(dataPin, clockPin, LSBFIRST, 0b00010001); // digit 1 digitalWrite(latchPin, HIGH);
This would result with the following:

Note how the bytes in binary match the map of the digits and their position. For example, the first byte sent was for the fourth digit, and the segment A was turned on. And that’s all there is to it – a neat and simple display.
This post brought to you by pmdway.com – everything for makers and electronics enthusiasts, with free delivery worldwide.
To keep up to date with new posts at tronixstuff.com, please subscribe to the mailing list in the box on the right, or follow us on twitter @tronixstuff.
Tutorial – Arduino and Four Digit Seven Segment Display Module was originally published on PlanetArduino
1 note
·
View note
Text
Python Numbers
In this article, you'll find out about the various numbers utilized in Python, how to change over from one data type to the next, and the numerical tasks upheld in Python.
Number Data Type in Python
Python upholds integers, floating-point numbers and complex numbers. They are defined as int, buoy, and complex classes in Python.
Integers and floating points are isolated by the presence or nonappearance of a decimal point. For instance, 5 is an integer though 5.0 is a floating-point number.
Complex numbers are written in the structure, x + yj, where x is the genuine part and y is the imaginary part.
We can utilize the type() capacity to realize which class a variable or a worth has a place with and isinstance() capacity to check in the event that it has a place with a specific class.
How about we take a gander at a model:
a = 5
print(type(a))
print(type(5.0))
c = 5 + 3j
print(c + 3)
print(isinstance(c, complex))
At the point when we run the above program, we get the following yield:
<class 'int'>
<class 'float'>
(8+3j)
Valid
While integers can be of any length, a floating-point number is exact simply up to 15 decimal places (the sixteenth spot is inaccurate).
The numbers we manage each day are of the decimal (base 10) number framework. Be that as it may, software engineers (for the most part inserted developers) need to work with binary (base 2), hexadecimal (base 16) and octal (base 8) number frameworks.
In Python, we can address these numbers by suitably placing a prefix before that number. The following table records these prefixes.
Number System Prefix
Binary '0b' or '0B'
Octal '0o' or '0O'
Hexadecimal '0x' or '0X'
Here are a few models
# Output: 107
print(0b1101011)
# Output: 253 (251 + 2)
print(0xFB + 0b10)
# Output: 13
print(0o15)
At the point when you run the program, the yield will be:
107
253
13
Type Conversion
We can change over one type of number into another. This is otherwise called compulsion.
Activities like expansion, deduction pressure integer to coast verifiably (consequently), in the event that one of the operands is glide.
>>> 1 + 2.0
3.0
We can see over that 1 (integer) is forced into 1.0 (glide) for expansion and the outcome is additionally a floating point number.
We can likewise utilize worked in capacities like int(), buoy() and complex() to change over between types expressly. These capacities can even change over from strings.
>>> int(2.3)
2
>>> int(- 2.8)
- 2
>>> float(5)
5.0
>>> complex('3+5j')
(3+5j)
While converting from buoy to integer, the number gets shortened (decimal parts are eliminated).
Python Decimal
Python worked in class skim plays out certain estimations that may astonish us. We as a whole realize that the amount of 1.1 and 2.2 is 3.3, however Python appears to conflict.
>>> (1.1 + 2.2) == 3.3
What is happening?
Incidentally, floating-point numbers are carried out in PC equipment as binary divisions as the PC just understands binary (0 and 1). Because of this explanation, the majority of the decimal divisions we know, can't be precisely put away in our PC.
We should take a model. We can't address the division 1/3 as a decimal number. This will give 0.33333333... which is infinitely long, and we can just surmised it.
Incidentally, the decimal division 0.1 will bring about an infinitely long binary part of 0.000110011001100110011... and our PC just stores a finite number of it.
This will just rough 0.1 however never be equivalent. Thus, it is the impediment of our PC equipment and not a blunder in Python.
>>> 1.1 + 2.2
3.3000000000000003
To defeat this issue, we can utilize the decimal module that accompanies Python. While floating-point numbers have accuracy up to 15 decimal places, the decimal module has client settable exactness.
We should see the distinction:
import decimal
print(0.1)
print(decimal.Decimal(0.1))
Yield
0.1
0.1000000000000000055511151231257827021181583404541015625
This module is utilized when we need to do decimal computations as we learned in school.
It additionally saves importance. We realize 25.50 kg is more exact than 25.5 kg as it has two huge decimal spots contrasted with one.
from decimal import Decimal as D
print(D('1.1') + D('2.2'))
print(D('1.2') * D('2.50'))
Yield
3.3
3.000
Notice the trailing zeroes in the above model.
We may ask, why not carry out Decimal without fail, instead of buoy? The main explanation is effectiveness. Floating point activities are done should quicker than Decimal tasks.
When to utilize Decimal instead of buoy?
We for the most part utilize Decimal in the following cases.
At the point when we are making financial applications that need definite decimal portrayal.
At the point when we need to control the degree of accuracy required.
At the point when we need to carry out the thought of critical decimal spots.
Read our Latest Blog: Tuples in Python
Python Fractions
Python gives tasks involving partial numbers through its portions module.
A portion has a numerator and a denominator, the two of which are integers. This module has support for levelheaded number math.
We can make Fraction objects in different manners. How about we view them.
import portions
print(fractions.Fraction(1.5))
print(fractions.Fraction(5))
print(fractions.Fraction(1,3))
Yield
3/2
5
1/3
While creating Fraction from drift, we may get some surprising outcomes. This is because of the defective binary floating point number portrayal as examined in the past area.
Luckily, Fraction permits us to instantiate with string too. This is the favored choice when using decimal numbers.
import parts
# As buoy
# Output: 2476979795053773/2251799813685248
print(fractions.Fraction(1.1))
# As string
# Output: 11/10
print(fractions.Fraction('1.1'))
Yield
2476979795053773/2251799813685248
11/10
This data type upholds every fundamental activity. Here are a couple of models.
from parts import Fraction as F
print(F(1, 3) + F(1, 3))
print(1/F(5, 6))
print(F(- 3, 10) > 0)
print(F(- 3, 10) < 0)
Yield
2/3
6/5
Bogus
Valid
Python Mathematics
Python offers modules like math and random to do diverse mathematics like geometry, logarithms, likelihood and measurements, and so on
import math
print(math.pi)
print(math.cos(math.pi))
print(math.exp(10))
print(math.log10(1000))
print(math.sinh(1))
print(math.factorial(6))
Yield
3.141592653589793
- 1.0
22026.465794806718
3.0
1.1752011936438014
720
Here is the full rundown of capacities and properties accessible in the Python math module.
import random
print(random.randrange(10, 20))
x = ['a', 'b', 'c', 'd', 'e']
# Get random decision
print(random.choice(x))
# Shuffle x
random.shuffle(x)
# Print the rearranged x
print(x)
# Print random component
print(random.random())
At the point when we run the above program we get the yield as follows.(Values might be diverse because of the random conduct)
18
e
['c', 'e', 'd', 'b', 'a']
0.5682821194654443
Read Full Article: Python Numbers
0 notes
Text
Ancient Egyptian Multiplication
This time on Questions You Never Knew You Had: How did the ancient Egyptians do multiplication?
I’m glad you asked! The ancient Egyptians had plenty of uses for multiplication--from architecture to financial transactions to any other requirement of an advanced civilization of the time. That being said, mathematics definitely wasn’t developed to the point it is today, and this kind of advanced arithmetic was generally reserved to the few educated scribes.
But how did they do it already? Suppose you’ve misplaced your calculator, so you ask a well-educated ancient Egyptian scribe to multiply the numbers 157 and 73. He would begin by constructing two columns and entering the larger number in the left and the smaller number in the right like this:
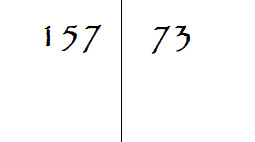
Now, the ancient Egyptians weren’t particularly good at immediately seeing the product between two relatively large numbers like these, but, to be fair, neither am I. However, they were wonderful at doubling quantities or cutting them in half. So, our scribe would double the number on the left side and half the number on the right side to get the result:

At this point you stop the scribe and remind him that the half of 73 is actually 36.5, but he finds the concept of having a whole number as well as the unit half in this circumstance to be kind of absurd, so you just let him carry on.
And carry on he does, doubling the left and halving the right until he reaches the unit:
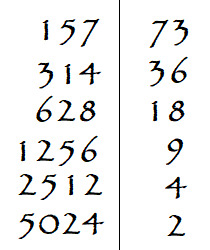
You respectfully point out that the product of 157 and 73 is not, in fact, 10048. “Or course it’s not,” he replies. “That’s only a part of it!”
He then proceeds to record every row in which there is an odd number in the right column (the ancient Egyptians, it seems, recognized difference between odd and even numbers). Then, he takes each corresponding left-column number and adds them--adding is easy, after all! Finally, he arrives at the result:
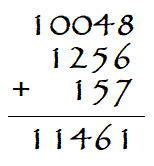
The product of 157 and 73 is 11461! You are very impressed! But how does he do it? How was he able to arrive at the product of two difficult numbers with only doubling and halving, not to mention the rounding of the decimal terms?
I’d encourage you to take some time to ponder and reflect. When you’re ready, an explanation is below the cut!
The Solution
I’d first like to note that our understanding of this method is primarily from documents containing worked examples, probably used for teaching new students the method. We don’t have evidence that the ancient Egyptians actually understood why the method worked (rigorous proof wouldn’t really come along until the Greeks); we just know that they recognized that it happened to work, so they just rolled with it!
That’s being said, here’s an explanation that has since been devised! We’ll begin with breaking down our current method of multiplication.
If I was multiply 157 and 73 on paper, I would probably use this method:

which, happily, yields the correct answer. This method works because what it is essentially doing is saying 157 × 73 = 157 ( 70 + 3 ) = 157 × 70 + 157 × 3.
Or, if you’d prefer, you could write 157 × 73 = 157 × 3 + 1570 × 7.
But all the number 7 is is 73 divided by 10 and then rounded down to the next whole number. Isn’t that a neat parallel? For fun, let’s construct two columns as we did before, except this time we’ll multiply and divide by 10 instead of 2. We then multiply the left column quantities with the one’s place of the corresponding right column quantity, and we find that we get the same answer!
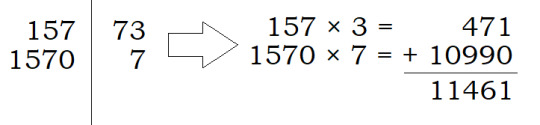
In fact, these two methods are equivalent for any given positive integers.
Now, I claim that the Egyptian method does essentially the same thing, except it secretly uses a base-two system! If you’re unfamiliar with base-two (binary), instead of having a 1′s place, 10′s place, 100′s place, etc. each holding a digit from 0 to 9 like our base-10 system, binary has a 1′s place, 2′s place, 2^2′s place, 2^3′s place, etc. where the allowable digits are only 0 and 1.
So, let’s get to converting 157 and 73 into binary!
157 = 2^7 + 2^4 + 2^3 + 2^2 + 2^0, so in base-2: 157 = 10011101
73 = 2^6 + 2^3 + 2^0, so in base-2: 73 = 1001001
Now, in base-2, we can use the same logic to say that 10011101 × 1001001 = 10011101 × 1 + 10011101 × 1000 + 10011101 × 1000000. But then, we can use our equivalent two column method:
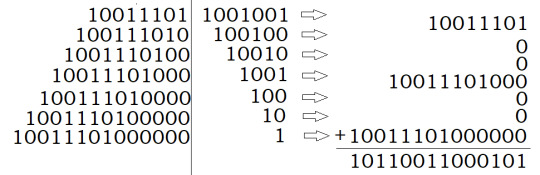
Where, in this case we’re multiplying and dividing by 2 rather than 10 since we’re in a base-2 number system.
Then, converting back to base-10, 10110011000101 = 2^0 + 2^2 + 2^6 + 2^7 + 2^10 + 2^11 + 2^13 = 11461. (!)
Moreover, this method is equivalent to the original Egyptian method because in base-2, having a one in the one’s place corresponds to having an odd number! Isn’t that wild?
So, I hope you found this ridiculously long post interesting or at least learned something. I learned about this method in a Math History course I’m in, but I’m definitely not any kind of expert in the the history of mathematics, so if you find that I made any errors or false claims, or if you would like to add something more, I welcome your comments!
If you’ve read this far, thank you! Until next time!
Other posts in the series:
[Multiplication][Division][Fractions][ref]
#math#mathblr#history#ancient egypt#egypt#multiplication#arithmetic#algebra#binary#at long last#I have made this post#I've been looking forward to posting it#and I hope you find it interesting!#(feedback is welcome)#mine
132 notes
·
View notes
Text
300+ TOP MAPREDUCE Interview Questions and Answers
MAPREDUCE Interview Questions for freshers experienced :-
1. What is MapReduce? It is a framework or a programming model that is used for processing large data sets over clusters of computers using distributed programming. 2. What are 'maps' and 'reduces'? 'Maps' and 'Reduces' are two phases of solving a query in HDFS. 'Map' is responsible to read data from input location, and based on the input type, it will generate a key value pair,that is, an intermediate output in local machine.'Reducer' is responsible to process the intermediate output received from the mapper and generate the final output. 3. What are the four basic parameters of a mapper? The four basic parameters of a mapper are LongWritable, text, text and IntWritable. The first two represent input parameters and the second two represent intermediate output parameters. 4. What are the four basic parameters of a reducer? The four basic parameters of a reducer are Text, IntWritable, Text, IntWritable.The first two represent intermediate output parameters and the second two represent final output parameters. 5. What do the master class and the output class do? Master is defined to update the Master or the job tracker and the output class is defined to write data onto the output location. 6. What is the input type/format in MapReduce by default? By default the type input type in MapReduce is 'text'. 7. Is it mandatory to set input and output type/format in MapReduce? No, it is not mandatory to set the input and output type/format in MapReduce. By default, the cluster takes the input and the output type as 'text'. 8. What does the text input format do? In text input format, each line will create a line off-set, that is an hexa-decimal number. Key is considered as a line off-set and value is considered as a whole line text. This is how the data gets processed by a mapper. The mapper will receive the 'key' as a 'LongWritable' parameter and value as a 'Text' parameter. 9. What does job conf class do? MapReduce needs to logically separate different jobs running on the same cluster. 'Job conf class' helps to do job level settings such as declaring a job in real environment. It is recommended that Job name should be descriptive and represent the type of job that is being executed. 10. What does conf.setMapper Class do? Conf.setMapperclass sets the mapper class and all the stuff related to map job such as reading a data and generating a key-value pair out of the mapper.

MAPREDUCE Interview Questions 11. What do sorting and shuffling do? Sorting and shuffling are responsible for creating a unique key and a list of values.Making similar keys at one location is known as Sorting. And the process by which the intermediate output of the mapper is sorted and sent across to the reducers is known as Shuffling. 12. What does a split do? Before transferring the data from hard disk location to map method, there is a phase or method called the 'Split Method'. Split method pulls a block of data from HDFS to the framework. The Split class does not write anything, but reads data from the block and pass it to the mapper.Be default, Split is taken care by the framework. Split method is equal to the block size and is used to divide block into bunch of splits. 13. How can we change the split size if our commodity hardware has less storage space? If our commodity hardware has less storage space, we can change the split size by writing the 'custom splitter'. There is a feature of customization in Hadoop which can be called from the main method. 14. What does a MapReduce partitioner do? A MapReduce partitioner makes sure that all the value of a single key goes to the same reducer, thus allows evenly distribution of the map output over the reducers. It redirects the mapper output to the reducer by determining which reducer is responsible for a particular key. 15. How is Hadoop different from other data processing tools? In Hadoop, based upon your requirements, you can increase or decrease the number of mappers without bothering about the volume of data to be processed. this is the beauty of parallel processing in contrast to the other data processing tools available. 16. Can we rename the output file? Yes we can rename the output file by implementing multiple format output class. 17. Why we cannot do aggregation (addition) in a mapper? Why we require reducer for that? We cannot do aggregation (addition) in a mapper because, sorting is not done in a mapper. Sorting happens only on the reducer side. Mapper method initialization depends upon each input split. While doing aggregation, we will lose the value of the previous instance. For each row, a new mapper will get initialized. For each row, inputsplit again gets divided into mapper, thus we do not have a track of the previous row value. 18. What is Streaming? Streaming is a feature with Hadoop framework that allows us to do programming using MapReduce in any programming language which can accept standard input and can produce standard output. It could be Perl, Python, Ruby and not necessarily be Java. However, customization in MapReduce can only be done using Java and not any other programming language. 19. What is a Combiner? A 'Combiner' is a mini reducer that performs the local reduce task. It receives the input from the mapper on a particular node and sends the output to the reducer. Combiners help in enhancing the efficiency of MapReduce by reducing the quantum of data that is required to be sent to the reducers. 20. What happens in a TextInputFormat? In TextInputFormat, each line in the text file is a record. Key is the byte offset of the line and value is the content of the line. For instance,Key: LongWritable, value: Text. 21. What do you know about KeyValueTextInputFormat? In KeyValueTextInputFormat, each line in the text file is a 'record'. The first separator character divides each line. Everything before the separator is the key and everything after the separator is the value. For instance,Key: Text, value: Text. 22. What do you know about SequenceFileInputFormat? SequenceFileInputFormat is an input format for reading in sequence files. Key and value are user defined. It is a specific compressed binary file format which is optimized for passing the data between the output of one MapReduce job to the input of some other MapReduce job. 23. What do you know about NLineOutputFormat? NLineOutputFormat splits 'n' lines of input as one split. 24. What is the difference between an HDFS Block and Input Split? HDFS Block is the physical division of the data and Input Split is the logical division of the data. 25. After restart of namenode, Mapreduce jobs started failing which worked fine before restart. What could be the wrong ? The cluster could be in a safe mode after the restart of a namenode. The administrator needs to wait for namenode to exit the safe mode before restarting the jobs again. This is a very common mistake by Hadoop administrators. 26. What do you always have to specify for a MapReduce job ? The classes for the mapper and reducer. The classes for the mapper, reducer, and combiner. The classes for the mapper, reducer, partitioner, and combiner. None; all classes have default implementations. 27. How many times will a combiner be executed ? At least once. Zero or one times. Zero, one, or many times. It’s configurable. 28. You have a mapper that for each key produces an integer value and the following set of reduce operations Reducer A: outputs the sum of the set of integer values. Reducer B: outputs the maximum of the set of values. Reducer C: outputs the mean of the set of values. Reducer D: outputs the difference between the largest and smallest values in the set. 29. Which of these reduce operations could safely be used as a combiner ? All of them. A and B. A, B, and D. C and D. None of them. Explanation: Reducer C cannot be used because if such reduction were to occur, the final reducer could receive from the combiner a series of means with no knowledge of how many items were used to generate them, meaning the overall mean is impossible to calculate. Reducer D is subtle as the individual tasks of selecting a maximum or minimum are safe for use as combiner operations. But if the goal is to determine the overall variance between the maximum and minimum value for each key, this would not work. If the combiner that received the maximum key had values clustered around it, this would generate small results; similarly for the one receiving the minimum value. These sub ranges have little value in isolation and again the final reducer cannot construct the desired result. 30. What is Uber task in YARN ? If the job is small, the application master may choose to run them in the same JVM as itself, since it judges the overhead of allocating new containers and running tasks in them as outweighing the gain to be had in running them in parallel, compared to running them sequentially on one node. (This is different to Mapreduce 1, where small jobs are never run on a single task tracker.) Such a job is said to be Uberized, or run as an Uber task. 31. How to configure Uber Tasks ? By default a job that has less than 10 mappers only and one reducer, and the input size is less than the size of one HDFS block is said to be small job. These values may be changed for a job by setting mapreduce.job.ubertask.maxmaps , mapreduce.job.uber task.maxreduces , and mapreduce.job.ubertask.maxbytes It’s also possible to disable Uber tasks entirely by setting mapreduce.job.ubertask.enable to false. 32. What are the ways to debug a failed mapreduce job ? Commonly there are two ways. By using mapreduce job counters YARN Web UI for looking into syslogs for actual error messages or status. 33. What is the importance of heartbeats in HDFS/Mapreduce Framework ? A heartbeat in master/slave architecture is a signal indicating that it is alive. A datanode sends heartbeats to Namenode and node managers send their heartbeats to Resource Managers to tell the master node that these are still alive. If the Namenode or Resource manager does not receive heartbeat from any slave node then they will decide that there is some problem in data node or node manager and is unable to perform the assigned task, then master (namenode or resource manager) will reassign the same task to other live nodes. 34. Can we rename the output file ? Yes, we can rename the output file by implementing multiple format output class. 35. What are the default input and output file formats in Mapreduce jobs ? If input file or output file formats are not specified, then the default file input or output formats are considered as text files. MAPREDUCE Questions and Answers pdf Download Read the full article
0 notes
Text
On how to abuse Python 3
This was a code-golf explanation for a friend that seemed like a good post here.
[[print("".join(['█ '[y+x&1]for x in range(w)]))for y in range(int(input("h")))]for w in[int(input("w"))]]
The above 113-character one-line code is prints a pretty little checkerboard, of which the length and width is given by the user.
█ █ █ █ █ █ █ █ █ █ █ █ █ █ █ █ █ █ █ █ █ █ █ █ █ █ █ █ █ █ █ █ █ █ █ █ █ █ █ █ █ █ █ █ █ █ █ █ █ █
Time to break it down I guess.
The code abuses PEP 202, or as it is most known, list comprehensions, the syntax of which is as follows: [expression for element in list if condition], where if condition is optional.
A list comprehension is simply a concise way to derive a new list from a list, and a given transformation (expression, in this case), and it is nestable (meaning expression can be another list expression) It is equivalent to the following.
transformed_list = [] for element in list: if condition: transformed_list.append(expression)
The top-level list comprehension is the following:
[second_level for w in[int(input("w"))]]
The list comprehension is not assigned to any variable whatsoever, since the printing is already done within the list comprehension. If you were to run this in a Python console, the result would be [None], as print() is not a function that returns a value. The list being read is a list with 1 element, int(input("w")) (which takes an input and casts it to an integer). This means there will be 1 iteration, where variable w is equal to int(input("w")).
Why? Well simply put it is equivalent to the following:
w = int(input("w")) second_level_comprehension
It is only assigning an input to a variable, without the use of another line, or a semi-colon (which is technically cheating in my eyes).
However, we are still stuck with this:
w = int(input("w")) [print("".join(third_level_list_comprehension))for y in range(int(input("h")))]
Or without the list comprehension:
w = int(input("w")) for y in range(int(input("h"))): print("".join(third_level_list_comprehension))
Simple enough, a range loop counting up to the user-defined height, so we can assume that what is given to print() is the string that would become the row. How is that being generated? str.join(list) creates a string from list, joining its elements with variable str seperating them. What would be list in this situation?
['█ '[y+x&1]for x in range(w)]
This list comprehension is a bit of a doozy, even after expansion, it would be rather tricky to grasp for a Python newcomer.
row = [] for x in range(w): row.append('█ '[y+x&1])
But since we are joining the list at the end, it's actually this:
row = "" for x in range(w): row += '█ '[y+x&1]
Just what is being appended here?
The code is actually selecting a character from string '█ ' for a given condition; y+x&1.
row = "" for x in range(w): if y+x&1: row += ' ' else: row += '█'
What does it mean?
Let's go back to when I was writing this code.
Obviously we want alternating characters between each row and column of the output. Since integers counting up always alternate between odd and even, perhaps we could use the modulo operator when deciding which character to choose.
Modulo is taking the remainder from dividing 2 numbers in elementary school, where we were all too stupid to understand fractions. So if we do 10 modulo 3, we end up with 1, because the result of 10 divided by 3 would be 3 remainder 1.
So we end up with this condition: n%2 == 1. These conditions would return true if n was odd.
But wait! We have to deal with something else! For the 0th column and 0th row, we want a black square; 1st and 0th, we want white; 1st and 1st, we want black.
So for both x and y, we want black if both of them are even; white if only one of them is odd; and black again if both of them are odd.
Wait a minute, this is XOR!
Much like and, or, not, xor is a binary operation. a xor b would be (a and not b) or (not a and b). The truth table (the table of outputs for given inputs) is as follows:
a b a xor b True True False True False True False False False
Python's xor operator is simply the character ^ utting it all together we get this: (x % 2 == 1) ^ (y % 2 == 1).
That's terrible, less characters!
(x%2)^(y%2)
We need the brackets here because % comes before ^ in operator precedence, much like how multiplication comes before addition in PEMDAS.
But what if we don't need brackets? Time to do some bit-twiddling.
Let's talk about how binary digits work.
From right to left, binary digits (or bits) goes up in powers of two, much like how decimal digits go up in powers of ten.
...3210 ...1111 ^^^^ │││╰─ 2 to the power of 0 = 1 ││╰── 2 to the power of 1 = 2 │╰─── 2 to the power of 2 = 4 ╰──── 2 to the power of 3 = + 8 ──── Decimal value = 15
Wait a minute, that first bit on the right makes the number odd! We can use the binary AND operator! The binary AND operator (Python's &) only returns 1 if both inputs are one, similar to Python's and, only for every bit between 2 numbers, returning a different number:
a b a and b 1 1 1 1 0 0 0 0 0
So from there, we can do this: (x&1)^(y&1).
Even with &, we still need the brackets...
And from there, we learn about how to add in binary, and use it to our advantage. Addition in binary is similar to decimal addition in elementary, add the numbers in one column, and carry over to the next column. Here, it's XOR the bits in one column, and carryover to the next bit. In Logic Design (essentially how CPU's work with only transistors), this process is a half-bit adder, and its truth table below:
a b sum (a xor b) carryover (a and b) 1 1 1 1 1 0 1 0 0 0 0 0
With this, you could chain the half-bit adder to create a full-bit adder, in order to create adders that can handle binary numbers of 64 bits, but that's beside the point.
Sum is xor. The carryover doesn't matter, as we only care about one bit in the result: the first bit. So we can easily do this instead:
(x+y)%2
Again, we still need the brackets, because modulo comes before addition in Python...
Hey, we can still use the & trick can't we? As & comes before +, we wouldn't need brackets!
x+y&1
Nice.
(Yes, I do realize that what I am complicating "odd plus odd makes even", but let me have this chance to teach you about binary please.)
Enough digressing, the simplified code of the if statement is as follows:
row = "" for x in range(w): if (x % 2) ^ (y % 2): row += ' ' else: row += '█'
And putting it all together, we get this:
w = int(input("w")) for y in range(int(input("h"))): row = "" for x in range(w): if (x % 2) ^ (y % 2): row += ' ' else: row += '█' print(row)
Mangled into this:
[[print("".join(['█ '[y+x&1]for x in range(w)]))for y in range(int(input("h")))]for w in[int(input("w"))]]
2ez4me
0 notes
Photo
original article
As the author notes in the comments, most of this is true of any language that uses floating point numbers: Python, C++, Ruby...
Another gem from the comments: open up your browser console and try
> 0.4+0.5 == 0.3+0.6
and it will return false! How big is the discrepancy? About one part in 10-16.
This is why you should never directly compare floating point numbers for equality, but rather, always compare whether the difference between them is smaller than some ‘close enough’ value, usually called 'epsilon'. For example, rather than a==b to test equality, you would calculate (a-b)<epsilon, with epsilon chosen depending on your particular problem and precision of your floating point numbers.
Another, more serious problem is that if you’re doing floating point calculations over and over again, these small errors can grow into bigger errors.
This problem isn’t because Javascript is a badly designed programming language. (Javascript might be a badly described programming language, people will argue forever about that, but this isn’t a reason why). A computer only has finitely many bits to represent a continuous infinity of real numbers in any interval. You can’t represent all the real numbers on a computer. This leads to various approximation schemes.
Integers are easy enough: with n bits of data, you get all the integers in some finite interval from -2n-1 to 2n-1-1, almost always stored as two’s complement binary numbers, which is an elegant way to represent negative numbers in binary. Or if you don't need negative numbers, you've got 0 to 2n-1. If you add together two integers (or multiply etc.) and the answer happens to lie outside of that range, you’re in trouble: an underflow or overflow error.
When you want fractions, you have some choices. You are always going to be representing some set of rational numbers - the question is, which rational numbers?
If you allocate n bits of data for your number, you can only ever distinguish between 2n different numbers. So each representation scheme chooses a particular set of numbers; it's a matter of tradeoffs.
Fixed point numbers split up the interval into finitely many pieces. Whatever range you pick, it’s split into 2n pieces; any other number must be rounded to the nearest fixed point. In an intuitive sense, it’s like dropping all the numbers after the nth decimal place. If you add together two numbers and they fall outside the fixed point range, however, you’ve got a problem (overflow or underflow). It's also the case that we often worry more about precision with small numbers than large numbers. The difference between 600000 and 600000.25 is less important to us in many situations than the difference between 0 and 0.25.
Adding and subtracting fixed point numbers together is not the only way we can have problems. If we multiply fixed point numbers together, even if the result is in the range of numbers we cover, we can lose precision, because the answer might require more bits than we have available. For example suppose we had a 2 bit floating point number in the range from 0 to 1: we can represent 0 (.00), 0.25 (.01), 0.5 (.10), and 0.75 (.11). If we multiply 0.25 and 0.5 the answer is 0.125, which would require three bits to represent (.001), so we have to choose which bits to discard! While this example is a little artificial because we're using absurdly few bits, the problem remains.
The answer to this Stack Exchange post gives a good explanation of how fixed-point numbers would fail in a realistic problem.

Floating point numbers are based on the idea that the precision you want is proportional to the size of your number. This is similar to scientific notation: if you’ve ever seen a number like 1.60×10−19 C, you have a certain number of decimal places, and then an exponent which expresses how big or small the overall number is. Because we’re using three decimal places, we’re implicitly saying we’re accurate to about one part in one hundred. (If we want to be more precise, we can list the actual error).
The nice thing is that, if you’re multiplying two numbers together, the answer has about the same precision as the starting two numbers; you can use the same number of decimal places. So floating point numbers divide their bits up into two parts: the first part, called the significand, gives the first few decimal digits, and then the second part, the exponent, says how big the number is.
So when we go to represent real numbers on a computer, if we don’t need absolute precision, and we want to multiply large and small numbers together, floating point numbers are actually a very good choice!
As shown in the picture up there, the computer can represent a lot of different numbers close to zero, and fewer numbers further out. The reason it looks weird is because, the way computers are built, it is vastly easier to use binary numbers than decimal numbers. ‘0.1’ looks like a simple number to us as a decimal number, but it would require an infinitely long string of digits as a binary number: 0.00011001100110011...2, so the computer has to round it off in this kind of representation. Conversely, the binary number 0.0012 converts to 0.125 in decimal.
Another option, similar to floating point, is to store the logarithm of a number (as a fixed-point number). Similar to floating point, this is good for multiplying numbers - but it's much less good for adding numbers. And there's also level-index numbers, which extend floating point out a bit further. This article covers all the kinds we've seen so far pretty well.
The other option is to store the numerator and denominator of your rational number as integers: the so-called rational data type. Many programming languages offer libraries to support this kind of number. I believe the major drawback here is speed and storage, so this kind of representation tends to only be used in number theory where the need for precision overrides these concerns.
There would also be redundancy in this kind of representation. For example, suppose we had a three-bit numerator and three-bit denominator (using positive integers only). (001,010) [(1,2)] and (010,100) [(2,4)] represent the same rational number (1/2)! While six bits would give you 26=64 different numbers in a fixed-point or floating-point representation, you would not be able to represent so many numbers as numerator-denominator pairs.
So there's a good reason why Javascript is so weird: it's the result of various tradeoffs between precision, speed and storage space. Javascript could be criticised for only providing floating-point numbers - most languages offer at least an integer type and a floating point type (often, several). However, most of the time, a 64-bit floating point number works well enough. For integers less than 253-1, you are not losing precision either compared to an integer type (just space and speed!); it's not a terrible choice for a web language.

#programming#computer science#maths#i know you probably know all about this gadit and op but i think it's interesting and want to share this stuff with followers!
2K notes
·
View notes
Text
5 MILLENIUM PROBLEMS
Everything becomes solveable with this introduction to a new understanding of a forgotten (or overlooked) math. One that had no real-life example up until computer science as discrete mathematics, linearly, resonantly and equivocally can be interpreted by all preceding relationships to different mathematics such as TRIG, GEO, ALG, CALC, PEMDAS, BIN, ORD, SET & now I present to you, LOG.
The missing piece for a new generation of .... problems. lol~
LOG(A) = 1 or 0 (or) 1 and 0
BASE 2PI*R for any explanations.
or
BASE 1 for any explanations. And A is equal to 2PI*R
so that tangents are recognized up to 2 decimal points, 1 more than LOG Base 10.
Reminds one of [-B +- ([B^2 - 4AC]^1/2)/]2A To be re-formatted later to show you it’s resemblance to solving A^2 + B^2 = C^2
Will be done with this by 7/24/2017 I think~
Ah, Prime numbers are around LOG[2PI*R + 1] (1) = 1
If you didn’t scroll further. There is a school of thought... my thought.... that also thinks the solution can exist as LOG[2PI*R + 1] (2PI*R) = 1 & 0. However, this assumes you believe that a BASE can exist only as an integer.... which is obviously not true. We shove 1/0′s all over the place in math all the time and overlook it during Calculus.
Without further ado~
BSD
T* LOG[2PI*R] (2PI*R) = 1 * T
LOG[1](2PI*R) = 1
I can’t explain anything unless if you look at the RHIEMANN Solution.
Elliptic Curve
Y^2 = X^3 + AX + B
LOG[2PI*R] (Y^2) = LOG[2PI*R] (X^3 + AX + B)
2 * LOG [2PI*R] (Y) = LOG[2PI*R](X^3 + AX + B)
LOG[2PI*R]( Y ) =1/2 (LOG[2PI*R](X^3 + AX + B)
Y = 1/2 (LOG[2PI*R](X^3 + AX + B)
* LOG[2PI*R] (Y) ^ -1
The conjecture is not held~
Reason why. If you look closely.
(1/0)^S makes a big difference when calculating RHIEMANN.
S as 1, is a significant value now.
S as anything else is a significant value now.
Easy right?
RHIEMANN
S*[LOG(1) - LOG(N)]
S*[0 - LOG[BASE](N)] per integer of a base, [2PI*R]
LOG[BASE EQUATION = 2PI*R) (2PI*R) = 1 == PRIMES
Easy right?
P=NP
1 - 0 = LOG(2*PI*R) (2*PI*R + 1)
I forget why I do this +1 here. Solving 5 of these at a time keeps throwing me off.
1 - 0 = LOG[2PI*R[(2*PI*R) = LOG[2PI*R](2PI*R)
Keeps checking until the highest and longest sequence of terms is accounter for. If I write anymore, you won’t pay attention~
(other millenium problems have or (1 or 0) or (1&0) Pretty cool right?
LET 1, a distance from 0 upon every single axis, be the value of completeness.
It is possible to calculate completeness.
Polynomial Function in any base, binary to canary (aha, a bird) * time.
HODGE
T*LOG[2PI*R](2PI*R) = 1 or LOG[2PI*R](2PI*R)^T = 1
This is the same as
1 - 0 = 1/T*LOG[2PI*R](2PI*R)
The funny thing is that, R is already a base away from everything. T is a period away from everything. Or was it 1/2? Depends on your understanding, I won’t tell you which one is right. You know that this is the correct way of doing this depending on your geometric series shape for cycles. 0 - 1 = 1/T * (LOG[2PI*R[(2PI*R))
Algebraic cycles if you like to see it as frequency.
But if you like to see it as a multiplier of the completely reduced original algebraic expression.
T on both sides is correct.
PARTICLE-WAVE
1/(2Y)^2
The prize will require “ Progress in establishing the existence of the Yang-Mills theory and a mass gap will require the introduction of fundamental new ideas both in physics and in mathematics. “ clay mathematics YANG-MILLS MASS GAP.
Mass Gap is not a fundamental, therefore I will start where they started. Gaussian and Particle Wave Theory.
It’s kind of funny because this one looks like all sorts of messed up to me.
L = 1/(4g^s) Integral (T*r F^*F) differential what?
First of all, the first law of Physics is Newton’s First Law of Motion. An Object in Motion stays in Motion. The object in question is a slant about a wave. Is it not? Can an object fit it’s sinusoidal curve? No.
Here is proof. LOG[2PI*R](2PI*R) = 1.... 1 What said another guy in the back.
How can the very object, of unknown dimension, be called to move sinuisoidally in 1/4thG steps let alone 1/4thG^2 steps. It moves slowly? A wave is meant to move sinusoidally. If the circle in itself is already inside. Then doesn’t it have angular momentum? So we’re talking about a piece of mass within a particle wave, that tells me that it has some spinning particle in it based off it’s gravitation. But doesn’t the very notion of suspended particles look stupid? yeah...
So where is the missing mass? Our integrated overlapping not knowing the constant between mv/mv momentum (angular momentum) waves and a particle’s (property) a natural resonance through a field.
Easy~~!
P.S.
I mean just look at this picture they have

How many axises are there? If you can’t pass this. You will not want to start from my zero axis theorem. There are 0,1,2,R,Infinite Axises in what seems like 3 different bases. Okay.
All in the same flavor of TRUE ZERO (AXIS) THEOREM, I named that myself :D
If I missed one please check any permutation of
(T)[Zi] LOG [BASE(Zii)](Ziii) = (Ziv)(T)
Where the Z’s can equal [1,0,-1,2PI*R]
Nothing else.
1 note
·
View note
Text
NCERT Class 12 Computer Science C Chapter 14 Networking and Open Source Concepts
NCERT Class 12 Computer Science - C++ :: Chapter 14 Networking and Open Source Concepts
UNIT – V : NETWORKING & OPEN SOURCE SOFTWARE
TOPIC-1 Communication Technoiogies
Very Short Answer Type Questions [1 mark each]
Question 1:What is Web Hosting?Answer:Web hosting is the service that makes our website available to be viewed by others on the Internet. A web host provides space on its server, so that other computers around the world can access our website by means of a network or modem.
Question 2:What is the difference between packet & message switching ?Answer:
Packet SwitchingMessage switchingThere is a tight upper limit on the block size. A fixed size of packet is specified.In message switching there was no upper limit.All the packets are stored in main memory in switching office.In message switching packets are stored on disk. This increases the performance as access time is reduced.
Question 3: Which protocol in used in creating a connection with a remote machine ?Answer:Telnet : It is an older internet utility that allow us to log on to remote computer system. It also facilitates for terminal emulation purpose.
Question 4:Which protocol is used to create a connection with a remote machine? Give any two advantage of using Optical Fibers.Answer:Telnet Two advantage of using Optical Fibers are
Capable of extremely high speed.
No Electromagnetic interference.
Extremely low attending
Question 5:What is cloud computing ?Answer:The sharing of computer resources (dedicated, time-shared, or dynamically shared servers) and related infrastructurer components (load balancers, firewalls, network storage, developer tools, monitors and management tools) to facilitate the deployment and operation of web and network based applications. Cloud computing relies on sharing of resources to achieve coherence and economies of scale, similar to a utility (like the electricity grid) over a network.
Question 6:Write two characterstics of Wi-Fi.Answer:
It is wireless network.
It is for short range.
Question 7:Expand the following :
GSM
GPRS
Answer:
GSM – Global System for Mobile Communication.
GPRS – General Packet Radio Service.
Question 8:Which type of network out of LAN, PAN and MAN is formed, when you connect two mobiles using Bluetooth to transfer a videoAnswer:PAN
Question 9:Write one characterstic each for 2G and 3G mobile technologies.Answer:2G networks primarily involve the transmission of voice information while 3G technology provides the additional advantage of data transfer.
Question 10:What is the difference between Packet switching and circuit switching techniques ?Answer:In circuit switching, a dedicated path exists from source to destination while in packet switching, there is no fixed path.
Question 11:Write two advantages of using an optical fibre cable over an Ethernet cable to connect two service stations, which are 200 m away from each other.Answer:Advantages of optical fibre :
Faster speed than ethernet
Lower Attenuation
Question 12:Identify the Domain name and URL from the following :https://ift.tt/2Rc5dG8Answer:Domain name – income.inURL – https://ift.tt/2Rc5dG8
Question 13:Write one advantage of bus topology of network. Also illustrate how four (4) computers can be connected with each other using bus topology of network.Answer:Advantage (benefits) of Linear Bus Topology is that the cable length required for this topology is the least compared to the other networks.Bus Topology of Network:
Question 14:Give one suitable example of each URL and Domain Name.Answer:URL: http://waltons.inDomain Name: gmail.com
Question 15:Write one advantage of star topology of network ? Also, illustrate how five (5) computers can be connected with each other using star topology of network.Answer:Advantage (benefits) of star toplogy:Easy to replace, install or remove hosts or other devices.
Question 16:Identify the type of topology on the basis of the following :(a) Since every node is directly connected to the server, a large amount of cable is needed which increases the installation cost of the network.(b) It has a single common data path connecting all the nods.Answer:(a) Star Topology(b) Bus Topology
Question 17:Expand the following :(a) VOIP(b) SMTPAnswer:(a) Voice Over Internet Protocol(b) Simple Mail Transfer Protocol
Question 18:Daniel has to share the data among various computers of his two offices branches situated in the same city. Name the network (out of LAN, WAN, PAN and MAN) which is being formed in this process.Answer:MAN
Question 19:ABC International School is planning to connect • all computers, each spread over a distance of 50 metres. Suggest an economic cable type having high speed data transfer to connect these computers.Answer:Optical Fibre Cable.
Question 20:Mahesh wants to transfer data within a city at very high speed. Write the wired transmission medium and type of network.Answer:Wired transmission medium – Optical fibre cable Type of network – MAN.
Question 21:Which device is used to connect all computers inside a lab ?Answer:Hub or Switch
Question 22:Which device is used to connect all computers to the internet using telephone wire ?Answer:RJ – 45. It is an eight wired connectors used to connect computers on a LAN.
Question 23:What is Wi-Fi Card ?Answer:Wi-Fi cards are small and portable cards that allow the computer to connect to the internet through a wireless network. The transmission is through the use of radio waves.
Question 24:Explain the purpose of a router.Answer:A router establishes connection between two network and it can handle network with different protocols. Using a routing table, routers make sure that the data packets are travelling through the best possible paths to reach their destination.
Question 25:Identify the type of topology from the following.(a) Each node is connected with the help of a single cable(b) Each node is connected with the help of independent cable with central switching.Answer:(a) Bus topology(b) Star topology
Question 26:What is the difference between LAN and MAN ?Answer:LAN : It is Local Area Network. The diameter is not more than a single building.WAN : It is Metropolitan Area Network. LAN spans a few kms while MAN spans 5-50 km diameter and is larger than a WAN.
Short Answer Type Questions-I [2 marks each]
Question 1:Write any 1 advantage and 1 disadvantage of Bus topology.Answer:Advantage : Since there is a single common data path connecting all the nodes, the bus topology uses a very short cable length which considerably reduces the installation cost. Disadvantage : Fault detection and isolation is difficult. This is because control of the network is not centralized in any particular node. If a node is faulty on the bus, detection of fault may have to be performed at many points on the network. The faulty node has then to be rectified at that connection point.
Question 2:SunRise Pvt. Ltd. is setting up the network in the Ahmedabad. There are four departments named as MrktDept, FinDept, LegalDept, SalesDept.Distance between varioud buldings is as given:
MrktDept to FinDept80 mMrktDept to LegalDept180 mMrktDept to SalesDept100 mLegalDept to SalesDept150 mLegalDept to FinDept100 mFinDept to SalesDept50 m
Number of Computers in the buildings :
MrktDept20LegalDept10FinDept08SalesDept42
(i) Suggest a cable layout of connections between the Departments and specify the topology.Star Topology should be used.(ii) Suggest the most suitable building to place the server by giving suitable reason.Answer:As per 80 – 20 rule, server should be placed in MrktDept because it has maximium no. of computers.(iii) Suggest the placement of (i) modem (ii) Hub/ Switch in the network.Answer:Each building should have hub/switch and moderm in case Internet connection is required.(iv) The organization is planning to link its sale counter situated in various part of the same city, which type of network out of LAN, WAN, MAN will be formed ? Justify.Answer:MAN (Metropolitan Area Network) as MAN network can be carried out in a city network.
Question 3:Name the protocol(i) Used to transfer voice using packet switched network.Answer:VAns.VOIP (Voice Over Internet Protocol)(ii) Used for chatting between 2 group or between 2 individuals.Answer:IRC (Internet Relay Chat)
Question 4:What is an IP Address ?Answer:IP address is a unique identifier for a node or host connection on an IP network. An IP address is a 32 bit binary number usually represented as 4 decimal values, each representing 8 bits, in the range 0 to 255 (know as octets) separated by decimal points. This is known as “dotted decimal” notation.Example : 140.179.220.200
Question 5:What is HTTP ?Answer:HTTP is a protocol that is used for transferring hypertext (i.e., text,graphic,image,sound,video,e tc,) between 2 computers and is particularly used on the world wideWeb (WWW).[1 mark for definition/explanation]
Question 6:Explain the importance of Cookies.Answer:When the user browses a website, the web server sends a text file to the web browser. This small text file is a cookie. They are usually used to track the pages that we visit so that information can be customised for us for that visit.
Question 7:How is 4G different from 3G?Answer:3G technology adds multimedia facilities such as video, audio and graphics applications whereas 4G will provide better than TV quality images and video-links.
Question 8:Illustrate the layout for connecting 5 computersin a Bus and a Start topology of Networks.Answer:Bus topologyOr any valid illustration of Bus and Star Topology.
Question 9:What is a spam mail ?Answer:Spam is the abuse of electronic messaging systems (including most broadcast media, digital delivery systems) to send unsolicited bulk messages indiscriminately.
Question 10:Differentiate between FTP and HTTPAnswer:FTP is a protocol to transfer files over the InternetHTTP is a protocol which allows the use of HTML to browse web pages in the World Wide Web.
Question 11:Answer:following, which is the fastest
wired and
wireless medium of communication ?
Answer:
Wired – Optical Fiber
Wireless – Infrared OR Microwave
Question 12:What is Worm ? How is it removed ?Answer:A worm is a self-replicating computer program. It uses a network to send copies of itself to other computers on the network and it may do so without any user intervention.Most of .the common anti-virus (anti-worm) remove worm.
Question 13:Out of the following, which all comes under cyber crime ?(i) Stealing away a brand new computer from a showroom.(ii) Getting in someone’s social networking account without his consent and posting pictures on his behalf to harash him.(iii) Secretly copying files from server of a call center and selling it to the other organization.(iv) Viewing sites on a internet browser.Answer:(ii) & (iii)
Question 14:Perfect Edu Services Ltd. is an educational organization. It is planning to setup its India campus at Chennai with its head office at Delhi. The Chennai campus has 4 main buildings – ADMIN, ENGINEERING, BUSINESS and MEDIA. [O.D, 2015]You as a network expert have to suggest the best network related solutions for their problems raised in (i) to (iv), keeping in mind the distances between the buildings and other given parameters.Shortest distances between various buildings.
ADMIN To ENGINEERING55 mADMIN to BUSINESS90 mADMIN to MEDIA90 mENGINEERING to BUSINESS55 mENGINEERING to MEDIA90 mBUSINESS to MEDIA45 mDELHI Head Office to CHENNAI Campus2175 km
Number of Computers Installed at various buildings are as follows :
ADMIN110ENGINEERING75BUSINESS40MEDIA12DELHI Head Office20
(i) Suggest the most appropriate location of the server inside the Chennai campus (out of the 4 buildings), to get the best connectivity for maximum no. of computers. Justify your answer.Answer:ADMIN (Due to maximum number of computers)ORMedia (Due to shorter distance from the other buildings)(ii) Suggest and draw the cable layout to efficiently connect various buildings within the Chennai Campus for connecting the computers.Answer:Anyone of the following(iii) Which hardware device will you suggest to be procured by the company to be installed to protect and control the internet uses within the campus ?Answer:Firewall OR Router(iv) Which of the following will you suggest to establish the online face-to-face communication between the people in the Admin Office of Chennai Campus and Delhi Head Office ?Answer:Cable TV
Question 15:What kind of data gets stored in cookies and how is it useful ?Answer:When a Website with cookie capabilities is visited, its server sends certain information about the browser, which is stored in the hard drive as a text file. It is as way for the server to remember things about the visited sites.
Question 16:Differentiate between packet switching over message switching ?Answer:Packet Switching : Follow store and forward principle for fixed packets. Fixes an upper limit for packet size.Message Switching : Follows store and forward principle for complete message. No limit on block size.
Question 17:Out of the following, which is the fastest(i) wired and(ii) wireless medium of communication ?Infrared, Coaxial Cable, Ethernet Cable, Microwave, Optical FiberAnswer:(i) Wired : Optical Fiber(ii) Wireless : Infrared OR Microwave
Question 18:What is Trojan Horse ?Answer:A Trojan Horse is a code hidden in a program, that looks safe but has hidden side effects typically causing loss or theft of data, and possible system harm.
Question 19:Out of the following, which all comes under cyber crime ?
Stealing away a brand new hard disk from a showroom.
Getting in someone’s social networking account without his consent and posting on his behalf.
Secretly copying data from server of an organization and selling it to tire other organization.
Looking at online activities of a friends blog.
Answer:(ii) & (iii)
Question 20:Write any two differences between twisted pair and coaxial pair cable.Answer:
Twisted PairCo-axial CableTheir bandwidth is not as high as coaxial cables.It has high bandwidth.A twisted pair consists of two copper wires twisted around each other (each has its own insulation around it) like a double helix.A coaxial cable consists of a copper wire core covered by an insulating material and a layer of conducting material over that.
Question 21:Write one advantage of Bus Topology of network, also, illustrate how 4 computers can be connected with each other using star topology of network.Answer:Cable length required for his topology is the least compared to other networks.ORAny other correct advantage of Bus Topology of network.Illustration of 4 computers connected with each other using star topology of network.
Short Answer Type Question-II [3 marks]
Question 1:Uplifting Skills Hub India is a knowledge and skill community which has an aim to uplift the standard of knowledge and skills in the society. It is planning to setup its training centres in multiple towns and villages pan India with its head offices in the nearest cities. They have created a model of their network with a city, a town and 3 villages as follows.As a network consultant, you have to suggest the best network related solutions for their issues/problems raised in (i) to (iv) keeping in mind the distance between various locations and given parameters.Shortest distance between various location :
VILLAGE 1 to B_TOWN2 KMVILLAGE 2 to B_TOWN1.0 KMVILLAGE 3 to B_TOWN1.5 KMVILLAGE 1 to VILLAGE 23.5 KMVILLAGE 1 to VILLAGE 34.5 KMVILLAGE 2 to VILLAGE 32.5 KMA CITY Head Office to B HUB25 KM
Number of Computers installed at various locations are as follows :
B_TOWN120VILLAGE 115VILLAGE 210VILLAGE 315A_CITY OFFICE6
Note :
• In Villages, there are community centres, in which one room has been given as training center to this organization to install computers.• The organization has got financial support from the government and top IT companies.
Suggest the most appropriate location of the SERVER in the BHUB (out of the 4 locations), to get the best and effective connectivity. Justify your answer.
Suggest the best wired medium and draw the cable layout (location to location) to efficiently connect various locations within the B HUB.
Which hardware device will you suggest to connect all the computers within each location of B_HUB ?
Which service/protocol will be most helpful to conduct live interactions of Experts from Head Office and people at all locations of B HUB ?
Answer:(i) B-TOWN can house the server as it has the maximum no. of computers.(ii) Optical fibre cable is the best for this star topology.(iii) Switch(iv) VoIP
Long Answer Type Questions [4 marks each]
Question 1:Indian School in Mumbai is starting up the network between its different wings. There are Four Buildings named as SENIOR, JUNIOR, ADMIN and HOSTEL as shown below.:The distance between various buildings is as follows:
ADMIN TO SENIOR200mADMIN TO JUNIOR150mADMIN TO HOSTEL50mSENIOR TO JUNIOR250mSENIOR TO HOSTEL350mJUNIOR TO HOSTEL350m
Number of Computers in Each Building :
SENIOR130JUNIOR80ADMIN160HOSTEL50
(b1) Suggest the cable layout of connections between the buildings.(b2) Suggest the most suitable place (i.e., building) to house the server of this school, provide a suitable reason.(b3) Suggest the placement of the following devices with justification, i Repeater i Hub/Switch(b4) The organisation also has inquiry office in another dty about 50-60 km away in hilly region. Suggest the suitable transmission media to interconnect to school and inquiry office out of the following : i Fiber optic cable, i Microwave, i RadiowaveAnswer:(b1)
(b2) Server can be placed in the ADMIN building as it has the maxium number of computer.(b3) Repeater can be placed between ADMIN and SENIOR building as the distance is more than 110 m.(b4) Radiowaves can be used in hilly regions as they can travel through obstacles.
Question 2:Vidya Senior Secondary Public School in Nainital is setting up the network between its different wings. There are 4 wings named as SENIOR(S), JUNIOR(J), ADMIN(A) and HOSTEL(H).Distance between various wings are given below :
Wing A to Wing S100 mWing A to Wing J200 mWing A to Wing H400 mWing S to Wing J300 mWing S to Wing H100 mWing J to Wing H450 m
WingNumber of Computers
Wing AWing SWing JWing H
201505025
(ii) Name the most suitable wing where the Server should be installed. Justify your answer.(iii) Suggest where all Hub(s)/Switch(es) should be placed in the network.(iv) Which communication medium would you suggest to connect this school with its main branch in Delhi ?Answer:(i) Star Topology
(ii) Server should be in Wing S as it has the maximum number of computers.(iii) All Wings need hub/switch as it has more than one computer.(iv) Since the distance is more, wireless transmission would be better. Radiowaves are reliable and can travel through obstacles
Question 3:Trine Tech Corporation (TTC) is a professional consultancy company. The company is planning to set up their new offices in India with its hub at Hyderabad. As a network adviser, you have to understand their requirement and suggest them the best available solutions. Their queries are mentioned as (i) to (iv) below.Physical Locations of the blocks of TTC
Block to Block distances (in Mtrs.)
Block (From)Block (To)DistanceHuman ResourceConference110Human ResourceFinance40ConferenceFinance80
Expected Number of Computers to be installed in each block
BlockComputersHuman ResourceFinanceConference2512090
What will be the most appropriate block, where TTC should plan to install their server?
Draw a block diagram showing cable layout to connect all the buildings in the most appropriate manner for efficient communication.
What will be the best possible connectivity out of the following, you will suggest to connect the new setup of offices in Bangalore with its London based office.• Satellite Link• Infrared• Ethernet Cable
Which of the following device will be suggested by you to connect each computer in each of the buildings?• Switch• Modem• Gateway
Answer:(i) Finance block because it has maximum number of computers.(ii)
(iii) Satellite link(iv) Switch
Question 4:Tech Up Corporation (TUC) is a professional consultancy company. The company is planning to set up their new offices in India with its hub at Hyderabad. As a network adviser, you have to understand their requirement and suggest them the best available solutions. Their queries are mentioned as (i) to (iv) below.Physical Locations of the blocks of TUC
Block to Block distances (in Mtrs.)
Block (From)Block (To)DistanceHuman ResourceConference60Human ResourceFinance120ConferenceFinance80
Expected Number of Computers to be installed in each block
BlockComputersHuman ResourceFinanceConference2512090
What will be the most appropriate block, where TUC should plan to install their server?
Draw a block to block cable layout to connect all the buildings in the most appropriate manner for efficient communication.
What will be the best possible connectivity out of the following you will suggest to connect the new setup of offices in Bangalore with its London based office?• Infrared• Satellite Link• Ethernet Cable
Which of the following devices will be suggested by you to connect each computer in each of the buildings?• Gateway• Switch• Modem
Answer:(i) Human resource block because it has maximum number of computers.(ii)(iii) Satellite link(iv) Switch
Question 5:G.R.K International Inc. is planning to connect its Bengaluru Office Setup with its Head Office in Delhi. The Bengaluru Office G.R.K. inter-national Inc. is spread across and area of approx. 1 square kilometer, consisting of 3 blocks – Human Resources, Academics and Administration.You as a network expert have to suggest answers to the four queries (i) to (iv) raised by them.Note : Keep the distance’ between blocks and no. of computers in each block in mind, while providing them the solutions.
Shortest distances between various blocks :
Human Resources to Administration100 mHuman Resources to Academics65 mAcademics to Administration110 mDelhi Head Office to Bengaluru Office Setup2350 km
Number of Computers installed at various blocks are as follows:
BLOCKNo. of ComputersHuman Resources155Administration20Academics100Delhi Head Office20
Suggest the most suitable block in the Bengaluru Office Setup, to host the server. Give a suitable reason with your suggestion.
Suggest the cable layout among the various blocks within the Bengaluru Office Setup for connecting the Blocks.
Suggest a suitable networking device to be installed in each of the blocks essentially required for connecting computers inside the blocks with fast and efficient connectivity.
Suggest the most suitable media to provide secure, fast and reliable data connectivity between Delhi Head Office and the Bengaluru Office Setup.
Answer:
(i) Human Resources because it has maximum number of computers.(ii)
(iii) Switch(iv) Satellite link
Question 6:Rovenza Communications International (RCI) is an online corporate training provider company for IT related courses. The company is setting up their new campus in Kolkata. You as a network expert have to study the physical locations of various blocks and the number of computers to be installed. In the planning phase, provide the best possible answers for the queries (i) to (iv) raised by them.Block to Block Distances (in Mtrs.)
FromToDistance
Administrative BlockAdministrative BlockFinance Block
Finance Block FacultyRecording Block FacultyRecording Block
6012070
Expected Computers to be installed in each block
BlockComputers
Administrative BlockFinance BlockFaculty Recording Block
3020100
Suggest the most appropriate block, where RCI should plan to install the server.
Suggest the most appropriate block to block cable layout to connect all three blocks for efficient communication.
Which type of network out of the following is formed by connecting the computers of these three blocks?• LAN• MAN• WAN
Which wireless channel out of the following should be opted by RCI to connect to students from all over the world?• Infrared• Microwave• Satellite
Write two advantages of using open source software over proprietary software.
Which of the following crime(s) does not come under cybercrime ?
Copying some important data from a computer without taking permission from the owner of-the data.
Stealing keyboard and mouse from a shop.
Getting into unknown person’s social networking account and start messaging on his behalf.
Answer:(i) Faculty Recording Block.(ii) Bus Topology(iii) LAN(iv) Satellite connection(v) Advantages of open source over proprietary software :• Open source software’s source code is available, can be modified copied & distributed while propritary software can’t be change.• Open source is free while propriatary is paid.(vi) (ii) Stealing keyboard & mouse from-a shop.
Question 7:(a) What is the difference between domain name and IP address?(b) Write two advantages of using an optical fibre cable over an Ethernet cable to connect two sendee stations, which are 190 m away from each other.(c) Expertia Professsional Global (EPG) is an online, corporate training provider company for IT related courses. The company is setting up their new campus in Mumbai. You as a network expert have to study the physical locations of various buildings and the number of computers to be installed. In the planning phase, provide the best possible answer for the queries (i) to (iv) raised by them.Building to Building Distances (in Mtrs.)
FromToDistance
Administrative BuildingAdministrative BuildingFinance Building
Finance BuildingRecording Studio BuildingFaculty Studio Building
6012070
Expected Computers to be installed in each Building:
BuildingComputers
Administrative BuildingFinance BuildingFaculty Studio Building
2040120
Suggest the most appropriate building, where EPG should plan to install the server.
Suggest the most appropriate building to building cable layout to connect all three buildings for efficient communication.
Which type of network out of the following is formed by connecting the computers of these three buildings?• LAN• MAN• WAN
Which wireless channel out of the following should be opted by EPG to connect to students of all over the world?• Infrared• Microwave• Satellite
Answer:(a) Domain Name is alphanumeric address of a resource over network IP address is a Numeric Address of a resoure in a Network. Example :Domain NameWWW.Gabsclasses.comIP Address102.112.0.153(b) Optical fibre Advantages :(i) Faculty Studio Building.(ii) Bus Topology.Faculty FinanceAdministrative BuildingStudio Building(iii) LAN(iv) Satellite
Question 8:To provide telemedicine faculty in a hilly state, a computer network is to be setup to connect hospitals in 6 small villages (VI, V2, …, V6) to the base hospital (H) in the state capital. This is shown in the following diagram.No village is more than 20 km away from the state capital.Imagine yourself as a computer consultant for this project and answer the following questions with justification :
Out of the following what kind of link should be provided to setup this network :
Microwave link,
Radio Link,
Wired Link ?
What kind of network will be formed; LAN, MAN, or WAN ?
Many times doctors at village hospital will have to consult senior doctors at the base hospital. For this purpose, how should they contact them: using email, sms, telephone, or video conference ?
Out of SMTP and POP3 which protocol is used to receive emails ?
What are cookies in the context of computer networks?
Rajeshwari is trying for on-line subscription to a magazine. For this she has filled in a form on the magazine’s web site. When the clicks submit button she gets a message that she has left e-mail field empty and she must fill it. For such checking which type of script is generally executed; client side script or server-side script ?
Mention any one difference between free-ware and free software.
Answer:(i) Radio Link(ii) MAN(iii) e-mail(iv) POP3(v) Cookies are files that store user information that is used to identify the user when he logs into the system.(vi) Server-side script.(vii) Freeware is a software that has the user to get unlimited usage. Free software may be free for a certain period’only.
Question 9:Work a lot Consultants are setting up a secured network for their office campus at Gurgaon for their day-to-day office and web- based activities. They are planning to have connectivity between three buildings and the head office situated in Mumbai. Answer the questions (i) to (iv) after going through the building positions in the campus and other details, which are given below:Distances between various buildings :
Building “GREEN” to Building “RED”110 mBuilding “GREEN” to Building “BLUE”45 mBuilding “BLUE” to Building “RED”65 mGurgaon Campus to Head Office1760 km
Number of computers
Building “GREEN”32Building “RED”150Building “BLUE”45Head Office10
Suggest the most suitable place (i.e., building) to house the server of this organization. Also give a reason to justify your suggested location.
Suggest a cable layout of connections between the buildings inside the campus.
Suggest the placement of the following devices with justification:
Repeater.
Switch.
The organization is planning to provide a high speed link with its head office situated in Mumbai using a wired connection. Which of the following cables will be most suitable for this job ?
Optical Fibre
Coaxial Cable
Ethernet Cable
Answer:(i) The most suitable place to install server is building “RED” because this building has maximum computer which reduce communication delay.(ii) Cable layout is Bus topology(iii) Since the cabling distance between buildings GREEN, BLUE and RED are quite large, so a repeater, would ideally be needed along their path to avoid loss of signals during the course of data flow in there routes.(2) In the layout a switch each would be needed in all the building, to interconnect the group of cables from the different computers in each building.(iv) Optical fibre.
Question 10:Granuda Consultants are setting up a secured network for their office campus at Faridabad for their day to day office and web based activities. They are planning to have connectivity between 3 building and the head office situated in Kolkata. Answer the questions (i) to (iv) after going through the building positions in the campus and other details, which are given below :Distances between various buildings :
Building “RAVI” to Building “JAMUNA”120 mBuilding “RAVI” to Building “GANGA”50 mBuilding “GANGA” to Building “JAMUNA”65 mFaridabad Campus to Head Office1460 km
Number of computers
Building “RAVI”25Building “JAMUNA”150Building “GANGA”51Head Office10
Suggest the most suitable place (i.e., block) to house the server of this organization. Also give a reason to justify your suggested location.
Suggest a cable layout of connections between the buildings inside the campus.
Suggest the placement of the following devices with justification:
Repeater
Switch
The organization is planning to provide a high speed link with its head office situated in the KOLKATA using a wired connection. Which of the following cable will be most suitable for this job ?
Optical Fibre
Coaxial Cable
Ethernet Cable
Answer:(i) The most suitable place to install server is in building “JAMUNA” because this building has maximum computer which reduce the communication delay.(ii) Cable layout. (Bus topology).(iii) (1) Since the cabling distance between buildings RAVI, GANGA and JAMUNA are quite large, so a repeater, would ideally be needed along their path to avoid loss of signals during the course of data flow in these routes.(2) In the layout a switch would be needed in all the building, to interconnect the group of cables from the different computers in each building.(iv) Optical fibre.
Question 11:Rehaana Medicos Center has set up its new center in Dubai. It has four buildings as shown in the diagram given below :Distances between various buildings are as follows:
Accounts to Research Lab55 mAccounts to Store150 mStore to Packaging Unit160 mPackaging Unit to Research Lab60 mAccounts to Packaging Unit125 mStore to Research Lab180 m
Number of computers
Accounts25Research Lab100Store15Packaging Unit60
As a network expert, provide the best possible answer for the following queries :
Suggest a cable layout of connections between the buildings.
Suggest the most suitable place (i.e. buildings) to house the server of this origanization.
Suggest the placement of the following device with justification :(a) Repeater(b) Switch/Hub
Suggest a system (hardware/sofware) to prevent unauthorized access to or from the network.
Answer:(i) Layout 1(ii) The most suitable place/building to house the server of this organization would be in Research Lab, building as this building contains the maximum number of computers.(iii) (a) For layout I, since the cabling distance between Accounts to Store is quite large, so a repeater would ideally be needed along their path to avoid loss of signals during the course of data flow in this route. For layotat2, since the cabling distance between Store to Research Lab is quite large, so a repeater would ideally be placed.(b) In both the layouts, a Flub/Switch each would be needed in all the buildings to interconnect the group of cables from the different computers in each building.(iv) Firewall
Question 12:Who is a hacker ?Answer:A computer enthusiast, who uses his computer . programming skills to intentionally access a computer without authorization is known as hacker. A hacker accesses the computer without the intention of destorying data or maliciously harming the computer.
Question 13:The following is a 32 bit binary number usually represented as 4 decimal values, each representing 8 bits, in the range 0 to 255 (know as octets) separated by decimal points. 140.179.220.200What is it? What is its importance?Answer:It is an IP Address. It is used to identify the computers on a network.
TOPIC-2Network Security and Web Service
Very Short Answer Type Questions [1 mark each]
Question 1:Define firewall.Answer:A system designed to prevent unauthorized access to or from a private network is called firewall. It can be implemented in both hardware and software or combination of both.
Question 2:Write any two examples of Server side Scripts.Answer:
ASP
PHP
Question 3:What is the difference between E-mail & chat?Answer:
Chat occurs in near real time, while E-mail doesn’t.
Chat is a 2-way communication which require the permission of both parties, while E-mail is a 1-way communication.
Question 4:Write names of any two popular open source software, which are used as operating systems.Answer:
Kernels
Unix
Linux
Question 5:What is the difference between video conferencing and chat.Answer:In conference, we can include more than one person and it allows text, video and audio while chat is one-to-one communication.
Question 6:Expand the following abbreviations :
HTTP
VOIP
Answer:
HTTP-Hyper Text Transfer Protocol.
VOIP-Voice Over Internet Protocol.
Question 7:What is the difference between HTTP and FTP?Answer:Hyper Text Transfer Protocol deals with Transfer of Text and Multimedia content over internet while FTP (File Transfer Protocol) deals with transfer of files over the internet.
Question 8:What out of the following, will you use to have an audio-visual chat with an expert sitting in a far-away place to fix-up a technical issue ?
VOIP
Email
FTP
Answer:(i) VOIP
Question 9:Name one server side scripting language and one client side scripting language.Answer:Client Side :
JAVASCRIPT
VBSCRIPT
Server Side :
ASP
JSP
Question 10:Which out of the following comes under cyber crime ?
Operating someone’s internet banking account, without his knowledge.
Stealing a keyboard from someone’s computer.
Working on someone’s Computer with his/ her permission.
Answer:(i) Operating someone’s internet banking account, without his knowledge.
Question 11:Name two proprietary softwares along with their application.Answer:
MS-Office – All office applications MS-Word, MS-Excel, MS-PowerPoint.
Visual Studio – Visual Basic, Visual C+ + softwares for application development.
Question 12:Name some cyber offences under the IT Act.Answer:
Tampering with computer source documents
Hacking.
Publishing of information which is obscene in electronic form.
Question 13:What are the 3 ways of protecting intellectual property ?Answer:
Patents
Copyrights
Trademark
Question 14:When a user browses a website, the web server sends a text file to the web browser. What is the name of this ?Answer:Cookies.
Short Answer Type Questions – I [2 mark each]
Question 1:Define the following :
Firewall
VoIP
Answer:(i) Firewall : A system designed to prevent unauthorized access to or from a private network is called firewall. It can be implemented in both hardware and software or combination of both.(ii) VoIP : Voice -over-Internet Protocol(VoIP) is a methodology and group of technologies for delivering voice communications and multimedia sessions over Internet Protocol(IP) networks, such as the Internet.
Question 2:Give the full form of the following terms.
XML
FLOSS
HTTP
FTP
Answer:
XML: Extensible Markup Language.
FLOSS: Free-Libre Open Source Software.
HTTP: Hyper Text Transfer Protocol.
FTP: File Transfer Protocol.
Question 3:Differentiate between WORM and VIRUS in Computer terminology.Answer:VIRUS directly effects the system by corrupting the useful data. A computer virus attaches itself to a program or file enabling it to spread from one computer to another.A worm is similar to a virus by design and is considered to be sub class of a virus. Worm spread from computer to computer, but unlike a virus, it has the capability to travel without any human action.
Abbrevations :Question 4:Expand the following
GSM
GPRS.
Answer:
GSM : Global System for Mobile Communication.
GPRS : General Packet Radio Service.
Question 5:Expand the following abbreviations :
HTTP
VOIP
Answer:
HTTP : Hyper Text Transfer Protocol.
VOIP : Voice Over Internet Protocol.
Question 6:Give the full form of :
FOSS
HTTP
Answer:
FOSS : Free Open Source Software.
HTTP : Hyper Text Transfer Protocol.
Question 7:Write the full forms of the following :
GNU
XML
Answer:
GNU : GNU’s Not Unix
XML : Extensible Markup Language.
Question 8:Expand the following terminologies :
GSM
WLL
Answer:
GSM : Global System for Mobile Communication
WLL : Wireless Local Loop.
Question 9:Give the full forms of the following terms :
CDMA
TDMA
FDMA
Answer:
CDMA : Code Division Multiple Access
TDMA : Time Division Multiple Access
FDMA : Frequency Division Multiple Access
Question 10:Expand the following abbreviations :
FTP
TCP
SMTP
VOIP
Answer:
FTP : File Transfer Protocol
TCP : Transmission Control Protocol.
SMTP : Simple Mail Transfer Protocol.
VOIP : Voice Over Internet Protocol.
Short Answer Type Questions-II [3 marks each]
Question 1:Give two examples of PAN and LAN type of networks.Answer:
PANLAN(i) Personal Area Network(ii) Spans a few metersExample :Bluetooth using 2 moblies and laptops sharing files.(i) Local Area Network(ii) Spans upto a km.Example :System in a lab in a school, systems at home.
Question 2:Which protocol helps us to browse through web pages using internet browsers ? Name any one internet browser.Answer:HTTPGoogle Chrome is a browser
Question 3:Write two advantages of 4G over 3G Mobile Telecommunication Technologies in terms of speed and services.Answer:4G has very high data rates upto 100 Mbps.It covers a wider lange than 3G
Question 1:Write two characteristics of Web 2.0Answer:Web 2.0
dynamic and interactive websites
Only the changed part is reloaded so faster.
via Blogger https://ift.tt/33jC7ua
0 notes
Photo

PHP Integers, Floats and Number Strings
Working with numbers in PHP seems to be a trivial concept but it can be quite confusing. It looks easy at first because PHP provides automatic type conversion. For example, you can assign an integer value to a variable and the type of that variable will be an integer. On the next line, you can assign a string to the same variable and the type will change to a string. Unfortunately, this automatic conversion can sometimes break your code.
There are a lot of types for numeric values as well. In this tutorial, you'll learn about integers and floats in PHP, as well as the functions which can be used to determine the type of numbers that we are dealing with and convert between them. You'll also learn how to convert integers and floats to and from numerical strings.
Different Types of Numbers in PHP
Integers
The most basic type of number in PHP is the integer. As you might already know, integers are numbers without any decimal part. For example, 2 is an integer and so is 235298 or -235298. On the other hand, 2.0 and 3.58 are floats. We will discuss them in more detail later.
One important thing to remember is that it is not necessary that a number be of type int if it does not have a decimal part. For example, 16 * 2.5 is exactly 40 but the type of this result will still be a float. When you are multiplying numbers, the final result will be of type float if at least one of the operands was a float. It doesn't matter if the final number has a decimal part or not.
Also, the maximum possible value an integer can have in PHP on your system can be obtained using the constant PHP_INT_MAX. A value greater in magnitude than the value returned by PHP_INT_MAX will be stored as a float even if it looks like an integer.
Generally, you would expect the result of multiplication of two variables of type int to be of type int. However, it is not true in case of overflow. Multiplication of five or six different numbers can easily take you outside the bounds of int type. For example, the result of 128*309*32*43*309 is a float on my system because it exceeds the value of PHP_INT_MAX which is 2147483647.
You can use the is_int($value) function to check if a number is of type integer. There are two aliases of this function called is_integer($value) and is_long($value). Both of them will give the same result.
Floats
The next most common type of number that you will deal with is a float. Unlike integers, which were simply numbers without decimal points in most cases, a number of type float can be represented in a variety of ways. The values 3.14, 12.0, 5.87E+10 and 3.56E-5 are all floats.
PHP will automatically convert a number to type float whenever decimals or very large numbers are involved. The float type can commonly store numbers with magnitude approximately equal to 1.7976931348623E+308. However, this is platform dependent.
The value 1.7976931348623E+308 may seem like a very large value—and it is!—but floats have a maximum precision of only about 14 digits. Any number with more digits than that will lose its precision. That means you can store a very large number, but you won't be able to keep the information about its exact value—in many cases, a float is only an approximation.
There are two functions which can be used to determine if the value you are dealing with is a float. These functions are is_float() and is_double(). Actually, is_double() is just an alias of is_float() so you can use any one of them and get the same result.
Infinity and NaN
There are two more kinds of numerical values that you might have to deal with when writing programs related to Mathematics. These values of infinity and NaN (not a number). Both these values require a little explanation because they are different from what you might expect.
Infinity in PHP is different from infinity in real life. In PHP, any numerical value above approximately PHP_FLOAT_MAX on a platform is considered infinity. So, 1.8e308 will give you float(INF) on var_dump(). You can check if a numerical value is finite or infinite using the is_finite() and is_infinite() functions.
Similarly, NaN stands for Not a Number but it doesn't check if a value is numerical or not. The value NaN is used for result of mathematical operations which are not possible in mathematics. For example, log(-1) will be NaN. Similarly, acos(5) will also be NaN. You can check if the value returned by a mathematical operation is not number by using the function is_nan().
Numerical Strings in PHP
Just like PHP dynamically change the type of different numbers based on how their values are used or assigned, it can also infer the value of different numerical strings for you to convert them to numbers.
The function is_numeric() can help you determine if a string or variable is indeed numeric or not. This function will return true for numbers written in octal, binary or hexadecimal notation. It will also return true if the numbers are written in exponential notation like +16.52e39.
Starting from PHP 7.0.0, when you pass a string to is_numeric(), it only returns true if the string consists of an optional sign, some digits, an optional decimal and an optional exponential part. This means that a numerical string written in hexadecimal or binary format will return false from PHP 7.0.0 onward.
PHP will implicitly cast any valid numerical string to a number when need arises. The following examples should help you understand this process better.
<?php $num = "3258712" + 12380; // Output: int(3271092) var_dump($num); $num = "3258712" + "12380"; // Output: int(3271092) var_dump($num); $num = 3258712 + "12380"; // Output: int(3271092) var_dump($num); $num = 3258712 * "12380"; // Output: float(40342854560) var_dump($num); $num = 3258712 / "12380"; // Output: float(263.2239095315) var_dump($num); $num = 3258712 / "8"; // Output: int(407339) var_dump($num); $num = "53.9e4" + 10; // Output: float(539010) var_dump($num); $num = "398.328" + 10; // Output: float(408.328) var_dump($num); $num = "398328" + 0xfedd24; // Output: int(17101084) var_dump($num); $num = 398328 + "0xfedd24"; // Output: int(398328) var_dump($num); ?>
As you can see, all valid numerical string were converted to their respective values before addition or other operations were performed. The type of $num in the end depends on its final value.
In the last case, the hexadecimal string "0xfedd24" is not converted to its decimal value because PHP 7 does not consider it to be a valid numerical string.
Casting Strings and Floats to Integers
Every now and then, you will need to cast one type of numerical values into another. PHP has a variety of functions and techniques to do so. Most of the time, the conversion will be implicit and you won't have to worry about it. However, if you have to do the conversion explicitly techniques mentioned here will definitely help.
You can use (int) or (integer) to convert any value to an integer. In case of floats, the values will always be rounded towards zero. Another way to cast strings and floats to integers is with the help of intval() function. Both (int) and intval() work in exactly the same manner.
<?php $float_a = 3598723.8258; $int_cast = (int)$float_a; // Output: 3598723 echo $int_cast; $string_a = "98723.828"; $int_cast = (int)$string_a; // Output: 98723 echo $int_cast; $string_b = "987233498349834828"; $int_cast = (int)$string_b; // Output: 2147483647 echo $int_cast; $float_b = 21474836473492789; $int_cast = (int)$float_b; // Output: -6507212 echo $int_cast; ?>
You should note that casting overflowing strings to integers will set the final value to the maximum permissible integer value. However, casting a float whose value is more than the maximum permissible integer value will result in the value oscillating between -2147483648 and 2147483647!
In certain situations, you might need to deal with very large numbers without loosing any precision. For example, it is impossible to get accurate result of multiplication of 987233498349834828 and 3487197512 using the * operator. It will give you 3.4426781992086E+27 after float conversion. Calculating the actual answer, which is 3442678199208600117812547936, will require use of libraries like BCMath. BCMath works by storing numbers as strings and doing arithmetic operations on them manually. Just remember that if you use BCMath, you will be dealing with strings instead of integers and floats.
Certain libraries will want you to only pass numbers of type int to their methods but you might unknowingly supply them a float value. This might happen because the value seems like an int because it doesn't have a decimal part. This would almost certainly result in an error if the library uses a function like is_int() to check if the passed number is of integer type. In such cases, it is always wise to first cast that number to int using either (int) or intval() and then pass it to any functions or methods of the library.
One example of when such a situation could come up would be when you are dealing with Mathematical functions like floor() and ceil() etc. floor() and ceil() will always return a float, even if you pass them an int!
<?php $int_a = 15*12; // Output: int(180) var_dump($int_a); $num = floor($int_a); // Output: float(180) var_dump($num); ?>
One problem with casting floats to integers is that you will lose the decimal part of the numbers. This may or may not be desirable. In such cases, you can use functions like floor() and only cast the number to int type if its actual value is equal to the value returned by floor().
<?php $number = 16*2.5; if(floor($number) == $number) { $fraction->setNumerator((int)$number); } else { echo 'Did not set the numerator.'; doSomethingElse(); } ?>
Let's say you have a library which allows you to do fractional arithmetic and it throws exceptions when you pass a number to its setNumerator() method that is not of type int. A variety of operations might turn a number in type float even if it is still an integer within the minimum and maximum bounds of type int. Using something like the code above will help you deal with such cases easily.
Final Thoughts
This tutorial has covered different ways in which PHP stores numbers and how you can determine if a number of a particular type. For example, you can use functions like is_int() and is_float() to determine the type of a number and proceed accordingly.
As you saw in the tutorial, PHP supports automatic type conversion. This means that sometimes smaller integers like 5 or 476 could have been stored as floats without you realizing it. Using these numbers in functions which only accept int values might result in exceptions or errors. We learned that a simple solution to this problem is be to explicitly cast such numbers to int if they don't have a decimal part and their values don't change upon casting.
After reading this tutorial, you should be able to determine the type of a number or the final type of a result after using a variety of operations using predefined functions and also explicitly cast them to a specific type after doing some checks.
As always, if you have any questions or additional tips, you are welcome to comment.
by Monty Shokeen via Envato Tuts+ Code https://ift.tt/2FbgPpp
0 notes
Text
Computer Fundamentals - Objective Questions (MCQ) with Solutions & Explanations
Computer Fundamentals - Objective Questions (MCQ) with Solutions & Explanations
Following are the objective questions from Computer Fundamentals Section. Computer Fundamentals section includes the topics such as history of computers, generation of computers, classification of computers, Computer Peripherals, Storage Devices, Computer Security Systems, Computer Viruses, Computer Networking, System Analysis and Design and so on.
Updated: January25, 2018 Basic Computer Awareness General Knowledge GK : Following are the objective questions from Computer Fundamentals Section. Computer Fundamentals section includes the topics such as history of computers, generation of computers, classification of computers, Computer Peripherals, Storage Devices, Computer Security Systems, Computer Viruses, Computer Networking, System Analysis and Design and so on. It tests general knowledge on common terms and concept of computer. Keeping in view of this, we have added some most frequently asked questions on Computer Fundamentals in MCQ format for your proper practice. Take this online practice tests / quiz and you will have an idea what kind of questions are expected under computer awareness in general knowledge section. All questions are selected in a manner so that it becomes easy to understand the topic. You will find these commonly asked solved questions (with answer) really helpful. Just practice. This section contains computer science multiple choice questions and answers on computer science topics like fundamental of computers, computer hardware input and output devices, programming languages, network, internet, emails etc. These questions are specially designed for students, working professionals and job seekers. This quiz will be helpful too for those guys who are preparing for banking sectors. As a number of aspirants have been asking us to share complete MCQs and other materials of Computer Knowledge, here we are sharing all the pdf files I have. These files consists a lot of computer mcqs. These will be very useful for all competitive exams. Downlaod it and prepare well. All the Best...!!! 1. A type of core store that has a lower access time than the devices used for working store in the same processor is known as a. Core memory b. Buffer c. Fast core d. Address register 2. Which of the following is an acronym for electronic delay storage automatic calculator? a. UNIVAC b. EDSAC c. EDVAC d. Abacus 3. Which of the following is form of semi conductor memory in which it is possible to change the contents of selected memory locations by applying suitable electrical signals? a. CAM b. ROM c. EPROM d. Abacus 4. A disk storage medium in the form of an assembly containing a single rigid magnetic disk permanently is a. Fixed disk b. Disk cartridge c. Card punch d. Card reader 5. A memory that is capable of determining whether a given datum is contained in one of its address is a. ROM b. PROM c. CAM d. RAM 6. A method of implementing a memory management system is a. Buddy system b. Bridgeware c. Broadband coaxial system d. All of the above 7. A plastic card similar to a credit card but having some memory and a microprocessor embedded within it is a. Punched paper tape b. Chip card c. Card punch d. Magnetic tape 8. A device that operates under the control of another device is called a. Stem b. Slave c. Simulator d. Emulator 9. Actual data processing operations are performed in the arithmetic logic section, but not in the …. Storage section of a processor unit a. Primary b. Accumulator c. Buffer d. Secondary 10. The use of spooler programs and/or …. Hardware allows personal computer operators to do the processing work at the same time a printing operation is in progress a. Registered mails b. Memory c. CPU d. Buffer 11. Which most popular input device is used today for interactive processing and for the one line entry of data for batch processing? a. Mouse b. Magnetic disk c. Visual display terminal d. Card punch 12. User programmable terminals that combine VDT hardware with built-in microprocessor is a. Kips b. PC c. Mainframe d. Intelligent terminals 13. The number of characters that can be stored in given physical space is a. Word length b. Byte c. Data density d. Field 14. the storage capacity of a disk system depends on the bits per inch of track and the tracks per inch of a. Cylinder b. Hum c. Cluster d. Surface 15. The disk drive component used to position read/write heads over a specific track I known as a. Acoustic couples b. Access arm c. Cluster d. All of the above 16. condensing output data to exhibit specific information is a. calculating b. recording c. merging d. summarizing 17. which chips using special external equipment can reprogram a. ROM b. PROM c. SAM d. RAM 18. A storage device whe3re the access time is depended upon the location of the data is a. Random access b. Serial access c. Sequential access d. Transaction access 19. Which number system is commonly used as a shortcut notation for groups of four binary digits? a. Binary b. Decimal c. Octal d. Hexadecimal 20. Interface electronic circuit is used to interconnect I/O devices to a computer’s CPU or a. ALU b. Memory c. Buffer d. Register Answers: 1. A type of core store that has a lower access time than the devices used for working store in the same processor is known as d. Address register 2. Which of the following is an acronym for electronic delay storage automatic calculator? b. EDSAC 3. Which of the following is form of semi conductor memory in which it is possible to change the contents of selected memory locations by applying suitable electrical signals? c. EPROM 4. A disk storage medium in the form of an assembly containing a single rigid magnetic disk permanently is b. Disk cartridge 5. A memory that is capable of determining whether a given datum is contained in one of its address is c. CAM 6. A method of implementing a memory management system is a. Buddy system 7. A plastic card similar to a credit card but having some memory and a microprocessor embedded within it is a. Punched paper tape 8. A device that operates under the control of another device is called b. Slave 9. Actual data processing operations are performed in the arithmetic logic section, but not in the …. Storage section of a processor unit a. Primary 10. The use of spooler programs and/or …. Hardware allows personal computer operators to do the processing work at the same time a printing operation is in progress d. Buffer 11. Which most popular input device is used today for interactive processing and for the one line entry of data for batch processing? a. Mouse 12. User programmable terminals that combine VDT hardware with built-in microprocessor is d. Intelligent terminals 13. The number of characters that can be stored in given physical space is c. Data density 14. the storage capacity of a disk system depends on the bits per inch of track and the tracks per inch of d. Surface 15. The disk drive component used to position read/write heads over a specific track I known as b. Access arm 16. condensing output data to exhibit specific information is d. summarizing 17. which chips using special external equipment can reprogram b. PROM 18. A storage device whe3re the access time is depended upon the location of the data is b. Serial access 19. Which number system is commonly used as a shortcut notation for groups of four binary digits? d. Hexadecimal 20. Interface electronic circuit is used to interconnect I/O devices to a computer’s CPU or b. Memory Read the full article
#BasicComputerInterviewQuestionsAndAnswersPdf#ComputerFundamentalQuestionAnswerInHindi#computerfundamentalquestionpaperwithanswer#computerfundamentalsquestionsandanswersforbankexams#computerfundamentalsquestionsandanswersforinterview#ComputerFundamentalsQuestionsAndAnswersMultipleChoicePdf#ComputerQuestionsForCompetitiveExams#mcqoncomputerfundamentalswithanswersdoc
0 notes
Text
300+ TOP MAPREDUCE Interview Questions and Answers
MAPREDUCE Interview Questions for freshers experienced :-
1. What is MapReduce? It is a framework or a programming model that is used for processing large data sets over clusters of computers using distributed programming. 2. What are 'maps' and 'reduces'? 'Maps' and 'Reduces' are two phases of solving a query in HDFS. 'Map' is responsible to read data from input location, and based on the input type, it will generate a key value pair,that is, an intermediate output in local machine.'Reducer' is responsible to process the intermediate output received from the mapper and generate the final output. 3. What are the four basic parameters of a mapper? The four basic parameters of a mapper are LongWritable, text, text and IntWritable. The first two represent input parameters and the second two represent intermediate output parameters. 4. What are the four basic parameters of a reducer? The four basic parameters of a reducer are Text, IntWritable, Text, IntWritable.The first two represent intermediate output parameters and the second two represent final output parameters. 5. What do the master class and the output class do? Master is defined to update the Master or the job tracker and the output class is defined to write data onto the output location. 6. What is the input type/format in MapReduce by default? By default the type input type in MapReduce is 'text'. 7. Is it mandatory to set input and output type/format in MapReduce? No, it is not mandatory to set the input and output type/format in MapReduce. By default, the cluster takes the input and the output type as 'text'. 8. What does the text input format do? In text input format, each line will create a line off-set, that is an hexa-decimal number. Key is considered as a line off-set and value is considered as a whole line text. This is how the data gets processed by a mapper. The mapper will receive the 'key' as a 'LongWritable' parameter and value as a 'Text' parameter. 9. What does job conf class do? MapReduce needs to logically separate different jobs running on the same cluster. 'Job conf class' helps to do job level settings such as declaring a job in real environment. It is recommended that Job name should be descriptive and represent the type of job that is being executed. 10. What does conf.setMapper Class do? Conf.setMapperclass sets the mapper class and all the stuff related to map job such as reading a data and generating a key-value pair out of the mapper.

MAPREDUCE Interview Questions 11. What do sorting and shuffling do? Sorting and shuffling are responsible for creating a unique key and a list of values.Making similar keys at one location is known as Sorting. And the process by which the intermediate output of the mapper is sorted and sent across to the reducers is known as Shuffling. 12. What does a split do? Before transferring the data from hard disk location to map method, there is a phase or method called the 'Split Method'. Split method pulls a block of data from HDFS to the framework. The Split class does not write anything, but reads data from the block and pass it to the mapper.Be default, Split is taken care by the framework. Split method is equal to the block size and is used to divide block into bunch of splits. 13. How can we change the split size if our commodity hardware has less storage space? If our commodity hardware has less storage space, we can change the split size by writing the 'custom splitter'. There is a feature of customization in Hadoop which can be called from the main method. 14. What does a MapReduce partitioner do? A MapReduce partitioner makes sure that all the value of a single key goes to the same reducer, thus allows evenly distribution of the map output over the reducers. It redirects the mapper output to the reducer by determining which reducer is responsible for a particular key. 15. How is Hadoop different from other data processing tools? In Hadoop, based upon your requirements, you can increase or decrease the number of mappers without bothering about the volume of data to be processed. this is the beauty of parallel processing in contrast to the other data processing tools available. 16. Can we rename the output file? Yes we can rename the output file by implementing multiple format output class. 17. Why we cannot do aggregation (addition) in a mapper? Why we require reducer for that? We cannot do aggregation (addition) in a mapper because, sorting is not done in a mapper. Sorting happens only on the reducer side. Mapper method initialization depends upon each input split. While doing aggregation, we will lose the value of the previous instance. For each row, a new mapper will get initialized. For each row, inputsplit again gets divided into mapper, thus we do not have a track of the previous row value. 18. What is Streaming? Streaming is a feature with Hadoop framework that allows us to do programming using MapReduce in any programming language which can accept standard input and can produce standard output. It could be Perl, Python, Ruby and not necessarily be Java. However, customization in MapReduce can only be done using Java and not any other programming language. 19. What is a Combiner? A 'Combiner' is a mini reducer that performs the local reduce task. It receives the input from the mapper on a particular node and sends the output to the reducer. Combiners help in enhancing the efficiency of MapReduce by reducing the quantum of data that is required to be sent to the reducers. 20. What happens in a TextInputFormat? In TextInputFormat, each line in the text file is a record. Key is the byte offset of the line and value is the content of the line. For instance,Key: LongWritable, value: Text. 21. What do you know about KeyValueTextInputFormat? In KeyValueTextInputFormat, each line in the text file is a 'record'. The first separator character divides each line. Everything before the separator is the key and everything after the separator is the value. For instance,Key: Text, value: Text. 22. What do you know about SequenceFileInputFormat? SequenceFileInputFormat is an input format for reading in sequence files. Key and value are user defined. It is a specific compressed binary file format which is optimized for passing the data between the output of one MapReduce job to the input of some other MapReduce job. 23. What do you know about NLineOutputFormat? NLineOutputFormat splits 'n' lines of input as one split. 24. What is the difference between an HDFS Block and Input Split? HDFS Block is the physical division of the data and Input Split is the logical division of the data. 25. After restart of namenode, Mapreduce jobs started failing which worked fine before restart. What could be the wrong ? The cluster could be in a safe mode after the restart of a namenode. The administrator needs to wait for namenode to exit the safe mode before restarting the jobs again. This is a very common mistake by Hadoop administrators. 26. What do you always have to specify for a MapReduce job ? The classes for the mapper and reducer. The classes for the mapper, reducer, and combiner. The classes for the mapper, reducer, partitioner, and combiner. None; all classes have default implementations. 27. How many times will a combiner be executed ? At least once. Zero or one times. Zero, one, or many times. It’s configurable. 28. You have a mapper that for each key produces an integer value and the following set of reduce operations Reducer A: outputs the sum of the set of integer values. Reducer B: outputs the maximum of the set of values. Reducer C: outputs the mean of the set of values. Reducer D: outputs the difference between the largest and smallest values in the set. 29. Which of these reduce operations could safely be used as a combiner ? All of them. A and B. A, B, and D. C and D. None of them. Explanation: Reducer C cannot be used because if such reduction were to occur, the final reducer could receive from the combiner a series of means with no knowledge of how many items were used to generate them, meaning the overall mean is impossible to calculate. Reducer D is subtle as the individual tasks of selecting a maximum or minimum are safe for use as combiner operations. But if the goal is to determine the overall variance between the maximum and minimum value for each key, this would not work. If the combiner that received the maximum key had values clustered around it, this would generate small results; similarly for the one receiving the minimum value. These sub ranges have little value in isolation and again the final reducer cannot construct the desired result. 30. What is Uber task in YARN ? If the job is small, the application master may choose to run them in the same JVM as itself, since it judges the overhead of allocating new containers and running tasks in them as outweighing the gain to be had in running them in parallel, compared to running them sequentially on one node. (This is different to Mapreduce 1, where small jobs are never run on a single task tracker.) Such a job is said to be Uberized, or run as an Uber task. 31. How to configure Uber Tasks ? By default a job that has less than 10 mappers only and one reducer, and the input size is less than the size of one HDFS block is said to be small job. These values may be changed for a job by setting mapreduce.job.ubertask.maxmaps , mapreduce.job.uber task.maxreduces , and mapreduce.job.ubertask.maxbytes It’s also possible to disable Uber tasks entirely by setting mapreduce.job.ubertask.enable to false. 32. What are the ways to debug a failed mapreduce job ? Commonly there are two ways. By using mapreduce job counters YARN Web UI for looking into syslogs for actual error messages or status. 33. What is the importance of heartbeats in HDFS/Mapreduce Framework ? A heartbeat in master/slave architecture is a signal indicating that it is alive. A datanode sends heartbeats to Namenode and node managers send their heartbeats to Resource Managers to tell the master node that these are still alive. If the Namenode or Resource manager does not receive heartbeat from any slave node then they will decide that there is some problem in data node or node manager and is unable to perform the assigned task, then master (namenode or resource manager) will reassign the same task to other live nodes. 34. Can we rename the output file ? Yes, we can rename the output file by implementing multiple format output class. 35. What are the default input and output file formats in Mapreduce jobs ? If input file or output file formats are not specified, then the default file input or output formats are considered as text files. MAPREDUCE Questions and Answers pdf Download Read the full article
0 notes
Text
NCERT Class 12 Computer Science C Chapter 14 Networking and Open Source Concepts
NCERT Class 12 Computer Science - C++ :: Chapter 14 Networking and Open Source Concepts
UNIT – V : NETWORKING & OPEN SOURCE SOFTWARE
TOPIC-1 Communication Technoiogies
Very Short Answer Type Questions [1 mark each]
Question 1:What is Web Hosting?Answer:Web hosting is the service that makes our website available to be viewed by others on the Internet. A web host provides space on its server, so that other computers around the world can access our website by means of a network or modem.
Question 2:What is the difference between packet & message switching ?Answer:
Packet SwitchingMessage switchingThere is a tight upper limit on the block size. A fixed size of packet is specified.In message switching there was no upper limit.All the packets are stored in main memory in switching office.In message switching packets are stored on disk. This increases the performance as access time is reduced.
Question 3: Which protocol in used in creating a connection with a remote machine ?Answer:Telnet : It is an older internet utility that allow us to log on to remote computer system. It also facilitates for terminal emulation purpose.
Question 4:Which protocol is used to create a connection with a remote machine? Give any two advantage of using Optical Fibers.Answer:Telnet Two advantage of using Optical Fibers are
Capable of extremely high speed.
No Electromagnetic interference.
Extremely low attending
Question 5:What is cloud computing ?Answer:The sharing of computer resources (dedicated, time-shared, or dynamically shared servers) and related infrastructurer components (load balancers, firewalls, network storage, developer tools, monitors and management tools) to facilitate the deployment and operation of web and network based applications. Cloud computing relies on sharing of resources to achieve coherence and economies of scale, similar to a utility (like the electricity grid) over a network.
Question 6:Write two characterstics of Wi-Fi.Answer:
It is wireless network.
It is for short range.
Question 7:Expand the following :
GSM
GPRS
Answer:
GSM – Global System for Mobile Communication.
GPRS – General Packet Radio Service.
Question 8:Which type of network out of LAN, PAN and MAN is formed, when you connect two mobiles using Bluetooth to transfer a videoAnswer:PAN
Question 9:Write one characterstic each for 2G and 3G mobile technologies.Answer:2G networks primarily involve the transmission of voice information while 3G technology provides the additional advantage of data transfer.
Question 10:What is the difference between Packet switching and circuit switching techniques ?Answer:In circuit switching, a dedicated path exists from source to destination while in packet switching, there is no fixed path.
Question 11:Write two advantages of using an optical fibre cable over an Ethernet cable to connect two service stations, which are 200 m away from each other.Answer:Advantages of optical fibre :
Faster speed than ethernet
Lower Attenuation
Question 12:Identify the Domain name and URL from the following :https://ift.tt/2Rc5dG8Answer:Domain name – income.inURL – https://ift.tt/2Rc5dG8
Question 13:Write one advantage of bus topology of network. Also illustrate how four (4) computers can be connected with each other using bus topology of network.Answer:Advantage (benefits) of Linear Bus Topology is that the cable length required for this topology is the least compared to the other networks.Bus Topology of Network:
Question 14:Give one suitable example of each URL and Domain Name.Answer:URL: http://waltons.inDomain Name: gmail.com
Question 15:Write one advantage of star topology of network ? Also, illustrate how five (5) computers can be connected with each other using star topology of network.Answer:Advantage (benefits) of star toplogy:Easy to replace, install or remove hosts or other devices.
Question 16:Identify the type of topology on the basis of the following :(a) Since every node is directly connected to the server, a large amount of cable is needed which increases the installation cost of the network.(b) It has a single common data path connecting all the nods.Answer:(a) Star Topology(b) Bus Topology
Question 17:Expand the following :(a) VOIP(b) SMTPAnswer:(a) Voice Over Internet Protocol(b) Simple Mail Transfer Protocol
Question 18:Daniel has to share the data among various computers of his two offices branches situated in the same city. Name the network (out of LAN, WAN, PAN and MAN) which is being formed in this process.Answer:MAN
Question 19:ABC International School is planning to connect • all computers, each spread over a distance of 50 metres. Suggest an economic cable type having high speed data transfer to connect these computers.Answer:Optical Fibre Cable.
Question 20:Mahesh wants to transfer data within a city at very high speed. Write the wired transmission medium and type of network.Answer:Wired transmission medium – Optical fibre cable Type of network – MAN.
Question 21:Which device is used to connect all computers inside a lab ?Answer:Hub or Switch
Question 22:Which device is used to connect all computers to the internet using telephone wire ?Answer:RJ – 45. It is an eight wired connectors used to connect computers on a LAN.
Question 23:What is Wi-Fi Card ?Answer:Wi-Fi cards are small and portable cards that allow the computer to connect to the internet through a wireless network. The transmission is through the use of radio waves.
Question 24:Explain the purpose of a router.Answer:A router establishes connection between two network and it can handle network with different protocols. Using a routing table, routers make sure that the data packets are travelling through the best possible paths to reach their destination.
Question 25:Identify the type of topology from the following.(a) Each node is connected with the help of a single cable(b) Each node is connected with the help of independent cable with central switching.Answer:(a) Bus topology(b) Star topology
Question 26:What is the difference between LAN and MAN ?Answer:LAN : It is Local Area Network. The diameter is not more than a single building.WAN : It is Metropolitan Area Network. LAN spans a few kms while MAN spans 5-50 km diameter and is larger than a WAN.
Short Answer Type Questions-I [2 marks each]
Question 1:Write any 1 advantage and 1 disadvantage of Bus topology.Answer:Advantage : Since there is a single common data path connecting all the nodes, the bus topology uses a very short cable length which considerably reduces the installation cost. Disadvantage : Fault detection and isolation is difficult. This is because control of the network is not centralized in any particular node. If a node is faulty on the bus, detection of fault may have to be performed at many points on the network. The faulty node has then to be rectified at that connection point.
Question 2:SunRise Pvt. Ltd. is setting up the network in the Ahmedabad. There are four departments named as MrktDept, FinDept, LegalDept, SalesDept.Distance between varioud buldings is as given:
MrktDept to FinDept80 mMrktDept to LegalDept180 mMrktDept to SalesDept100 mLegalDept to SalesDept150 mLegalDept to FinDept100 mFinDept to SalesDept50 m
Number of Computers in the buildings :
MrktDept20LegalDept10FinDept08SalesDept42
(i) Suggest a cable layout of connections between the Departments and specify the topology.Star Topology should be used.(ii) Suggest the most suitable building to place the server by giving suitable reason.Answer:As per 80 – 20 rule, server should be placed in MrktDept because it has maximium no. of computers.(iii) Suggest the placement of (i) modem (ii) Hub/ Switch in the network.Answer:Each building should have hub/switch and moderm in case Internet connection is required.(iv) The organization is planning to link its sale counter situated in various part of the same city, which type of network out of LAN, WAN, MAN will be formed ? Justify.Answer:MAN (Metropolitan Area Network) as MAN network can be carried out in a city network.
Question 3:Name the protocol(i) Used to transfer voice using packet switched network.Answer:VAns.VOIP (Voice Over Internet Protocol)(ii) Used for chatting between 2 group or between 2 individuals.Answer:IRC (Internet Relay Chat)
Question 4:What is an IP Address ?Answer:IP address is a unique identifier for a node or host connection on an IP network. An IP address is a 32 bit binary number usually represented as 4 decimal values, each representing 8 bits, in the range 0 to 255 (know as octets) separated by decimal points. This is known as “dotted decimal” notation.Example : 140.179.220.200
Question 5:What is HTTP ?Answer:HTTP is a protocol that is used for transferring hypertext (i.e., text,graphic,image,sound,video,e tc,) between 2 computers and is particularly used on the world wideWeb (WWW).[1 mark for definition/explanation]
Question 6:Explain the importance of Cookies.Answer:When the user browses a website, the web server sends a text file to the web browser. This small text file is a cookie. They are usually used to track the pages that we visit so that information can be customised for us for that visit.
Question 7:How is 4G different from 3G?Answer:3G technology adds multimedia facilities such as video, audio and graphics applications whereas 4G will provide better than TV quality images and video-links.
Question 8:Illustrate the layout for connecting 5 computersin a Bus and a Start topology of Networks.Answer:Bus topologyOr any valid illustration of Bus and Star Topology.
Question 9:What is a spam mail ?Answer:Spam is the abuse of electronic messaging systems (including most broadcast media, digital delivery systems) to send unsolicited bulk messages indiscriminately.
Question 10:Differentiate between FTP and HTTPAnswer:FTP is a protocol to transfer files over the InternetHTTP is a protocol which allows the use of HTML to browse web pages in the World Wide Web.
Question 11:Answer:following, which is the fastest
wired and
wireless medium of communication ?
Answer:
Wired – Optical Fiber
Wireless – Infrared OR Microwave
Question 12:What is Worm ? How is it removed ?Answer:A worm is a self-replicating computer program. It uses a network to send copies of itself to other computers on the network and it may do so without any user intervention.Most of .the common anti-virus (anti-worm) remove worm.
Question 13:Out of the following, which all comes under cyber crime ?(i) Stealing away a brand new computer from a showroom.(ii) Getting in someone’s social networking account without his consent and posting pictures on his behalf to harash him.(iii) Secretly copying files from server of a call center and selling it to the other organization.(iv) Viewing sites on a internet browser.Answer:(ii) & (iii)
Question 14:Perfect Edu Services Ltd. is an educational organization. It is planning to setup its India campus at Chennai with its head office at Delhi. The Chennai campus has 4 main buildings – ADMIN, ENGINEERING, BUSINESS and MEDIA. [O.D, 2015]You as a network expert have to suggest the best network related solutions for their problems raised in (i) to (iv), keeping in mind the distances between the buildings and other given parameters.Shortest distances between various buildings.
ADMIN To ENGINEERING55 mADMIN to BUSINESS90 mADMIN to MEDIA90 mENGINEERING to BUSINESS55 mENGINEERING to MEDIA90 mBUSINESS to MEDIA45 mDELHI Head Office to CHENNAI Campus2175 km
Number of Computers Installed at various buildings are as follows :
ADMIN110ENGINEERING75BUSINESS40MEDIA12DELHI Head Office20
(i) Suggest the most appropriate location of the server inside the Chennai campus (out of the 4 buildings), to get the best connectivity for maximum no. of computers. Justify your answer.Answer:ADMIN (Due to maximum number of computers)ORMedia (Due to shorter distance from the other buildings)(ii) Suggest and draw the cable layout to efficiently connect various buildings within the Chennai Campus for connecting the computers.Answer:Anyone of the following(iii) Which hardware device will you suggest to be procured by the company to be installed to protect and control the internet uses within the campus ?Answer:Firewall OR Router(iv) Which of the following will you suggest to establish the online face-to-face communication between the people in the Admin Office of Chennai Campus and Delhi Head Office ?Answer:Cable TV
Question 15:What kind of data gets stored in cookies and how is it useful ?Answer:When a Website with cookie capabilities is visited, its server sends certain information about the browser, which is stored in the hard drive as a text file. It is as way for the server to remember things about the visited sites.
Question 16:Differentiate between packet switching over message switching ?Answer:Packet Switching : Follow store and forward principle for fixed packets. Fixes an upper limit for packet size.Message Switching : Follows store and forward principle for complete message. No limit on block size.
Question 17:Out of the following, which is the fastest(i) wired and(ii) wireless medium of communication ?Infrared, Coaxial Cable, Ethernet Cable, Microwave, Optical FiberAnswer:(i) Wired : Optical Fiber(ii) Wireless : Infrared OR Microwave
Question 18:What is Trojan Horse ?Answer:A Trojan Horse is a code hidden in a program, that looks safe but has hidden side effects typically causing loss or theft of data, and possible system harm.
Question 19:Out of the following, which all comes under cyber crime ?
Stealing away a brand new hard disk from a showroom.
Getting in someone’s social networking account without his consent and posting on his behalf.
Secretly copying data from server of an organization and selling it to tire other organization.
Looking at online activities of a friends blog.
Answer:(ii) & (iii)
Question 20:Write any two differences between twisted pair and coaxial pair cable.Answer:
Twisted PairCo-axial CableTheir bandwidth is not as high as coaxial cables.It has high bandwidth.A twisted pair consists of two copper wires twisted around each other (each has its own insulation around it) like a double helix.A coaxial cable consists of a copper wire core covered by an insulating material and a layer of conducting material over that.
Question 21:Write one advantage of Bus Topology of network, also, illustrate how 4 computers can be connected with each other using star topology of network.Answer:Cable length required for his topology is the least compared to other networks.ORAny other correct advantage of Bus Topology of network.Illustration of 4 computers connected with each other using star topology of network.
Short Answer Type Question-II [3 marks]
Question 1:Uplifting Skills Hub India is a knowledge and skill community which has an aim to uplift the standard of knowledge and skills in the society. It is planning to setup its training centres in multiple towns and villages pan India with its head offices in the nearest cities. They have created a model of their network with a city, a town and 3 villages as follows.As a network consultant, you have to suggest the best network related solutions for their issues/problems raised in (i) to (iv) keeping in mind the distance between various locations and given parameters.Shortest distance between various location :
VILLAGE 1 to B_TOWN2 KMVILLAGE 2 to B_TOWN1.0 KMVILLAGE 3 to B_TOWN1.5 KMVILLAGE 1 to VILLAGE 23.5 KMVILLAGE 1 to VILLAGE 34.5 KMVILLAGE 2 to VILLAGE 32.5 KMA CITY Head Office to B HUB25 KM
Number of Computers installed at various locations are as follows :
B_TOWN120VILLAGE 115VILLAGE 210VILLAGE 315A_CITY OFFICE6
Note :
• In Villages, there are community centres, in which one room has been given as training center to this organization to install computers.• The organization has got financial support from the government and top IT companies.
Suggest the most appropriate location of the SERVER in the BHUB (out of the 4 locations), to get the best and effective connectivity. Justify your answer.
Suggest the best wired medium and draw the cable layout (location to location) to efficiently connect various locations within the B HUB.
Which hardware device will you suggest to connect all the computers within each location of B_HUB ?
Which service/protocol will be most helpful to conduct live interactions of Experts from Head Office and people at all locations of B HUB ?
Answer:(i) B-TOWN can house the server as it has the maximum no. of computers.(ii) Optical fibre cable is the best for this star topology.(iii) Switch(iv) VoIP
Long Answer Type Questions [4 marks each]
Question 1:Indian School in Mumbai is starting up the network between its different wings. There are Four Buildings named as SENIOR, JUNIOR, ADMIN and HOSTEL as shown below.:The distance between various buildings is as follows:
ADMIN TO SENIOR200mADMIN TO JUNIOR150mADMIN TO HOSTEL50mSENIOR TO JUNIOR250mSENIOR TO HOSTEL350mJUNIOR TO HOSTEL350m
Number of Computers in Each Building :
SENIOR130JUNIOR80ADMIN160HOSTEL50
(b1) Suggest the cable layout of connections between the buildings.(b2) Suggest the most suitable place (i.e., building) to house the server of this school, provide a suitable reason.(b3) Suggest the placement of the following devices with justification, i Repeater i Hub/Switch(b4) The organisation also has inquiry office in another dty about 50-60 km away in hilly region. Suggest the suitable transmission media to interconnect to school and inquiry office out of the following : i Fiber optic cable, i Microwave, i RadiowaveAnswer:(b1)
(b2) Server can be placed in the ADMIN building as it has the maxium number of computer.(b3) Repeater can be placed between ADMIN and SENIOR building as the distance is more than 110 m.(b4) Radiowaves can be used in hilly regions as they can travel through obstacles.
Question 2:Vidya Senior Secondary Public School in Nainital is setting up the network between its different wings. There are 4 wings named as SENIOR(S), JUNIOR(J), ADMIN(A) and HOSTEL(H).Distance between various wings are given below :
Wing A to Wing S100 mWing A to Wing J200 mWing A to Wing H400 mWing S to Wing J300 mWing S to Wing H100 mWing J to Wing H450 m
WingNumber of Computers
Wing AWing SWing JWing H
201505025
(ii) Name the most suitable wing where the Server should be installed. Justify your answer.(iii) Suggest where all Hub(s)/Switch(es) should be placed in the network.(iv) Which communication medium would you suggest to connect this school with its main branch in Delhi ?Answer:(i) Star Topology
(ii) Server should be in Wing S as it has the maximum number of computers.(iii) All Wings need hub/switch as it has more than one computer.(iv) Since the distance is more, wireless transmission would be better. Radiowaves are reliable and can travel through obstacles
Question 3:Trine Tech Corporation (TTC) is a professional consultancy company. The company is planning to set up their new offices in India with its hub at Hyderabad. As a network adviser, you have to understand their requirement and suggest them the best available solutions. Their queries are mentioned as (i) to (iv) below.Physical Locations of the blocks of TTC
Block to Block distances (in Mtrs.)
Block (From)Block (To)DistanceHuman ResourceConference110Human ResourceFinance40ConferenceFinance80
Expected Number of Computers to be installed in each block
BlockComputersHuman ResourceFinanceConference2512090
What will be the most appropriate block, where TTC should plan to install their server?
Draw a block diagram showing cable layout to connect all the buildings in the most appropriate manner for efficient communication.
What will be the best possible connectivity out of the following, you will suggest to connect the new setup of offices in Bangalore with its London based office.• Satellite Link• Infrared• Ethernet Cable
Which of the following device will be suggested by you to connect each computer in each of the buildings?• Switch• Modem• Gateway
Answer:(i) Finance block because it has maximum number of computers.(ii)
(iii) Satellite link(iv) Switch
Question 4:Tech Up Corporation (TUC) is a professional consultancy company. The company is planning to set up their new offices in India with its hub at Hyderabad. As a network adviser, you have to understand their requirement and suggest them the best available solutions. Their queries are mentioned as (i) to (iv) below.Physical Locations of the blocks of TUC
Block to Block distances (in Mtrs.)
Block (From)Block (To)DistanceHuman ResourceConference60Human ResourceFinance120ConferenceFinance80
Expected Number of Computers to be installed in each block
BlockComputersHuman ResourceFinanceConference2512090
What will be the most appropriate block, where TUC should plan to install their server?
Draw a block to block cable layout to connect all the buildings in the most appropriate manner for efficient communication.
What will be the best possible connectivity out of the following you will suggest to connect the new setup of offices in Bangalore with its London based office?• Infrared• Satellite Link• Ethernet Cable
Which of the following devices will be suggested by you to connect each computer in each of the buildings?• Gateway• Switch• Modem
Answer:(i) Human resource block because it has maximum number of computers.(ii)(iii) Satellite link(iv) Switch
Question 5:G.R.K International Inc. is planning to connect its Bengaluru Office Setup with its Head Office in Delhi. The Bengaluru Office G.R.K. inter-national Inc. is spread across and area of approx. 1 square kilometer, consisting of 3 blocks – Human Resources, Academics and Administration.You as a network expert have to suggest answers to the four queries (i) to (iv) raised by them.Note : Keep the distance’ between blocks and no. of computers in each block in mind, while providing them the solutions.
Shortest distances between various blocks :
Human Resources to Administration100 mHuman Resources to Academics65 mAcademics to Administration110 mDelhi Head Office to Bengaluru Office Setup2350 km
Number of Computers installed at various blocks are as follows:
BLOCKNo. of ComputersHuman Resources155Administration20Academics100Delhi Head Office20
Suggest the most suitable block in the Bengaluru Office Setup, to host the server. Give a suitable reason with your suggestion.
Suggest the cable layout among the various blocks within the Bengaluru Office Setup for connecting the Blocks.
Suggest a suitable networking device to be installed in each of the blocks essentially required for connecting computers inside the blocks with fast and efficient connectivity.
Suggest the most suitable media to provide secure, fast and reliable data connectivity between Delhi Head Office and the Bengaluru Office Setup.
Answer:
(i) Human Resources because it has maximum number of computers.(ii)
(iii) Switch(iv) Satellite link
Question 6:Rovenza Communications International (RCI) is an online corporate training provider company for IT related courses. The company is setting up their new campus in Kolkata. You as a network expert have to study the physical locations of various blocks and the number of computers to be installed. In the planning phase, provide the best possible answers for the queries (i) to (iv) raised by them.Block to Block Distances (in Mtrs.)
FromToDistance
Administrative BlockAdministrative BlockFinance Block
Finance Block FacultyRecording Block FacultyRecording Block
6012070
Expected Computers to be installed in each block
BlockComputers
Administrative BlockFinance BlockFaculty Recording Block
3020100
Suggest the most appropriate block, where RCI should plan to install the server.
Suggest the most appropriate block to block cable layout to connect all three blocks for efficient communication.
Which type of network out of the following is formed by connecting the computers of these three blocks?• LAN• MAN• WAN
Which wireless channel out of the following should be opted by RCI to connect to students from all over the world?• Infrared• Microwave• Satellite
Write two advantages of using open source software over proprietary software.
Which of the following crime(s) does not come under cybercrime ?
Copying some important data from a computer without taking permission from the owner of-the data.
Stealing keyboard and mouse from a shop.
Getting into unknown person’s social networking account and start messaging on his behalf.
Answer:(i) Faculty Recording Block.(ii) Bus Topology(iii) LAN(iv) Satellite connection(v) Advantages of open source over proprietary software :• Open source software’s source code is available, can be modified copied & distributed while propritary software can’t be change.• Open source is free while propriatary is paid.(vi) (ii) Stealing keyboard & mouse from-a shop.
Question 7:(a) What is the difference between domain name and IP address?(b) Write two advantages of using an optical fibre cable over an Ethernet cable to connect two sendee stations, which are 190 m away from each other.(c) Expertia Professsional Global (EPG) is an online, corporate training provider company for IT related courses. The company is setting up their new campus in Mumbai. You as a network expert have to study the physical locations of various buildings and the number of computers to be installed. In the planning phase, provide the best possible answer for the queries (i) to (iv) raised by them.Building to Building Distances (in Mtrs.)
FromToDistance
Administrative BuildingAdministrative BuildingFinance Building
Finance BuildingRecording Studio BuildingFaculty Studio Building
6012070
Expected Computers to be installed in each Building:
BuildingComputers
Administrative BuildingFinance BuildingFaculty Studio Building
2040120
Suggest the most appropriate building, where EPG should plan to install the server.
Suggest the most appropriate building to building cable layout to connect all three buildings for efficient communication.
Which type of network out of the following is formed by connecting the computers of these three buildings?• LAN• MAN• WAN
Which wireless channel out of the following should be opted by EPG to connect to students of all over the world?• Infrared• Microwave• Satellite
Answer:(a) Domain Name is alphanumeric address of a resource over network IP address is a Numeric Address of a resoure in a Network. Example :Domain NameWWW.Gabsclasses.comIP Address102.112.0.153(b) Optical fibre Advantages :(i) Faculty Studio Building.(ii) Bus Topology.Faculty FinanceAdministrative BuildingStudio Building(iii) LAN(iv) Satellite
Question 8:To provide telemedicine faculty in a hilly state, a computer network is to be setup to connect hospitals in 6 small villages (VI, V2, …, V6) to the base hospital (H) in the state capital. This is shown in the following diagram.No village is more than 20 km away from the state capital.Imagine yourself as a computer consultant for this project and answer the following questions with justification :
Out of the following what kind of link should be provided to setup this network :
Microwave link,
Radio Link,
Wired Link ?
What kind of network will be formed; LAN, MAN, or WAN ?
Many times doctors at village hospital will have to consult senior doctors at the base hospital. For this purpose, how should they contact them: using email, sms, telephone, or video conference ?
Out of SMTP and POP3 which protocol is used to receive emails ?
What are cookies in the context of computer networks?
Rajeshwari is trying for on-line subscription to a magazine. For this she has filled in a form on the magazine’s web site. When the clicks submit button she gets a message that she has left e-mail field empty and she must fill it. For such checking which type of script is generally executed; client side script or server-side script ?
Mention any one difference between free-ware and free software.
Answer:(i) Radio Link(ii) MAN(iii) e-mail(iv) POP3(v) Cookies are files that store user information that is used to identify the user when he logs into the system.(vi) Server-side script.(vii) Freeware is a software that has the user to get unlimited usage. Free software may be free for a certain period’only.
Question 9:Work a lot Consultants are setting up a secured network for their office campus at Gurgaon for their day-to-day office and web- based activities. They are planning to have connectivity between three buildings and the head office situated in Mumbai. Answer the questions (i) to (iv) after going through the building positions in the campus and other details, which are given below:Distances between various buildings :
Building “GREEN” to Building “RED”110 mBuilding “GREEN” to Building “BLUE”45 mBuilding “BLUE” to Building “RED”65 mGurgaon Campus to Head Office1760 km
Number of computers
Building “GREEN”32Building “RED”150Building “BLUE”45Head Office10
Suggest the most suitable place (i.e., building) to house the server of this organization. Also give a reason to justify your suggested location.
Suggest a cable layout of connections between the buildings inside the campus.
Suggest the placement of the following devices with justification:
Repeater.
Switch.
The organization is planning to provide a high speed link with its head office situated in Mumbai using a wired connection. Which of the following cables will be most suitable for this job ?
Optical Fibre
Coaxial Cable
Ethernet Cable
Answer:(i) The most suitable place to install server is building “RED” because this building has maximum computer which reduce communication delay.(ii) Cable layout is Bus topology(iii) Since the cabling distance between buildings GREEN, BLUE and RED are quite large, so a repeater, would ideally be needed along their path to avoid loss of signals during the course of data flow in there routes.(2) In the layout a switch each would be needed in all the building, to interconnect the group of cables from the different computers in each building.(iv) Optical fibre.
Question 10:Granuda Consultants are setting up a secured network for their office campus at Faridabad for their day to day office and web based activities. They are planning to have connectivity between 3 building and the head office situated in Kolkata. Answer the questions (i) to (iv) after going through the building positions in the campus and other details, which are given below :Distances between various buildings :
Building “RAVI” to Building “JAMUNA”120 mBuilding “RAVI” to Building “GANGA”50 mBuilding “GANGA” to Building “JAMUNA”65 mFaridabad Campus to Head Office1460 km
Number of computers
Building “RAVI”25Building “JAMUNA”150Building “GANGA”51Head Office10
Suggest the most suitable place (i.e., block) to house the server of this organization. Also give a reason to justify your suggested location.
Suggest a cable layout of connections between the buildings inside the campus.
Suggest the placement of the following devices with justification:
Repeater
Switch
The organization is planning to provide a high speed link with its head office situated in the KOLKATA using a wired connection. Which of the following cable will be most suitable for this job ?
Optical Fibre
Coaxial Cable
Ethernet Cable
Answer:(i) The most suitable place to install server is in building “JAMUNA” because this building has maximum computer which reduce the communication delay.(ii) Cable layout. (Bus topology).(iii) (1) Since the cabling distance between buildings RAVI, GANGA and JAMUNA are quite large, so a repeater, would ideally be needed along their path to avoid loss of signals during the course of data flow in these routes.(2) In the layout a switch would be needed in all the building, to interconnect the group of cables from the different computers in each building.(iv) Optical fibre.
Question 11:Rehaana Medicos Center has set up its new center in Dubai. It has four buildings as shown in the diagram given below :Distances between various buildings are as follows:
Accounts to Research Lab55 mAccounts to Store150 mStore to Packaging Unit160 mPackaging Unit to Research Lab60 mAccounts to Packaging Unit125 mStore to Research Lab180 m
Number of computers
Accounts25Research Lab100Store15Packaging Unit60
As a network expert, provide the best possible answer for the following queries :
Suggest a cable layout of connections between the buildings.
Suggest the most suitable place (i.e. buildings) to house the server of this origanization.
Suggest the placement of the following device with justification :(a) Repeater(b) Switch/Hub
Suggest a system (hardware/sofware) to prevent unauthorized access to or from the network.
Answer:(i) Layout 1(ii) The most suitable place/building to house the server of this organization would be in Research Lab, building as this building contains the maximum number of computers.(iii) (a) For layout I, since the cabling distance between Accounts to Store is quite large, so a repeater would ideally be needed along their path to avoid loss of signals during the course of data flow in this route. For layotat2, since the cabling distance between Store to Research Lab is quite large, so a repeater would ideally be placed.(b) In both the layouts, a Flub/Switch each would be needed in all the buildings to interconnect the group of cables from the different computers in each building.(iv) Firewall
Question 12:Who is a hacker ?Answer:A computer enthusiast, who uses his computer . programming skills to intentionally access a computer without authorization is known as hacker. A hacker accesses the computer without the intention of destorying data or maliciously harming the computer.
Question 13:The following is a 32 bit binary number usually represented as 4 decimal values, each representing 8 bits, in the range 0 to 255 (know as octets) separated by decimal points. 140.179.220.200What is it? What is its importance?Answer:It is an IP Address. It is used to identify the computers on a network.
TOPIC-2Network Security and Web Service
Very Short Answer Type Questions [1 mark each]
Question 1:Define firewall.Answer:A system designed to prevent unauthorized access to or from a private network is called firewall. It can be implemented in both hardware and software or combination of both.
Question 2:Write any two examples of Server side Scripts.Answer:
ASP
PHP
Question 3:What is the difference between E-mail & chat?Answer:
Chat occurs in near real time, while E-mail doesn’t.
Chat is a 2-way communication which require the permission of both parties, while E-mail is a 1-way communication.
Question 4:Write names of any two popular open source software, which are used as operating systems.Answer:
Kernels
Unix
Linux
Question 5:What is the difference between video conferencing and chat.Answer:In conference, we can include more than one person and it allows text, video and audio while chat is one-to-one communication.
Question 6:Expand the following abbreviations :
HTTP
VOIP
Answer:
HTTP-Hyper Text Transfer Protocol.
VOIP-Voice Over Internet Protocol.
Question 7:What is the difference between HTTP and FTP?Answer:Hyper Text Transfer Protocol deals with Transfer of Text and Multimedia content over internet while FTP (File Transfer Protocol) deals with transfer of files over the internet.
Question 8:What out of the following, will you use to have an audio-visual chat with an expert sitting in a far-away place to fix-up a technical issue ?
VOIP
Email
FTP
Answer:(i) VOIP
Question 9:Name one server side scripting language and one client side scripting language.Answer:Client Side :
JAVASCRIPT
VBSCRIPT
Server Side :
ASP
JSP
Question 10:Which out of the following comes under cyber crime ?
Operating someone’s internet banking account, without his knowledge.
Stealing a keyboard from someone’s computer.
Working on someone’s Computer with his/ her permission.
Answer:(i) Operating someone’s internet banking account, without his knowledge.
Question 11:Name two proprietary softwares along with their application.Answer:
MS-Office – All office applications MS-Word, MS-Excel, MS-PowerPoint.
Visual Studio – Visual Basic, Visual C+ + softwares for application development.
Question 12:Name some cyber offences under the IT Act.Answer:
Tampering with computer source documents
Hacking.
Publishing of information which is obscene in electronic form.
Question 13:What are the 3 ways of protecting intellectual property ?Answer:
Patents
Copyrights
Trademark
Question 14:When a user browses a website, the web server sends a text file to the web browser. What is the name of this ?Answer:Cookies.
Short Answer Type Questions – I [2 mark each]
Question 1:Define the following :
Firewall
VoIP
Answer:(i) Firewall : A system designed to prevent unauthorized access to or from a private network is called firewall. It can be implemented in both hardware and software or combination of both.(ii) VoIP : Voice -over-Internet Protocol(VoIP) is a methodology and group of technologies for delivering voice communications and multimedia sessions over Internet Protocol(IP) networks, such as the Internet.
Question 2:Give the full form of the following terms.
XML
FLOSS
HTTP
FTP
Answer:
XML: Extensible Markup Language.
FLOSS: Free-Libre Open Source Software.
HTTP: Hyper Text Transfer Protocol.
FTP: File Transfer Protocol.
Question 3:Differentiate between WORM and VIRUS in Computer terminology.Answer:VIRUS directly effects the system by corrupting the useful data. A computer virus attaches itself to a program or file enabling it to spread from one computer to another.A worm is similar to a virus by design and is considered to be sub class of a virus. Worm spread from computer to computer, but unlike a virus, it has the capability to travel without any human action.
Abbrevations :Question 4:Expand the following
GSM
GPRS.
Answer:
GSM : Global System for Mobile Communication.
GPRS : General Packet Radio Service.
Question 5:Expand the following abbreviations :
HTTP
VOIP
Answer:
HTTP : Hyper Text Transfer Protocol.
VOIP : Voice Over Internet Protocol.
Question 6:Give the full form of :
FOSS
HTTP
Answer:
FOSS : Free Open Source Software.
HTTP : Hyper Text Transfer Protocol.
Question 7:Write the full forms of the following :
GNU
XML
Answer:
GNU : GNU’s Not Unix
XML : Extensible Markup Language.
Question 8:Expand the following terminologies :
GSM
WLL
Answer:
GSM : Global System for Mobile Communication
WLL : Wireless Local Loop.
Question 9:Give the full forms of the following terms :
CDMA
TDMA
FDMA
Answer:
CDMA : Code Division Multiple Access
TDMA : Time Division Multiple Access
FDMA : Frequency Division Multiple Access
Question 10:Expand the following abbreviations :
FTP
TCP
SMTP
VOIP
Answer:
FTP : File Transfer Protocol
TCP : Transmission Control Protocol.
SMTP : Simple Mail Transfer Protocol.
VOIP : Voice Over Internet Protocol.
Short Answer Type Questions-II [3 marks each]
Question 1:Give two examples of PAN and LAN type of networks.Answer:
PANLAN(i) Personal Area Network(ii) Spans a few metersExample :Bluetooth using 2 moblies and laptops sharing files.(i) Local Area Network(ii) Spans upto a km.Example :System in a lab in a school, systems at home.
Question 2:Which protocol helps us to browse through web pages using internet browsers ? Name any one internet browser.Answer:HTTPGoogle Chrome is a browser
Question 3:Write two advantages of 4G over 3G Mobile Telecommunication Technologies in terms of speed and services.Answer:4G has very high data rates upto 100 Mbps.It covers a wider lange than 3G
Question 1:Write two characteristics of Web 2.0Answer:Web 2.0
dynamic and interactive websites
Only the changed part is reloaded so faster.
from Blogger http://www.margdarsan.com/2020/09/ncert-class-12-computer-science-c.html
0 notes
Text
NCERT Class 12 Computer Science C Chapter 14 Networking and Open Source Concepts
NCERT Class 12 Computer Science - C++ :: Chapter 14 Networking and Open Source Concepts
UNIT – V : NETWORKING & OPEN SOURCE SOFTWARE
TOPIC-1 Communication Technoiogies
Very Short Answer Type Questions [1 mark each]
Question 1:What is Web Hosting?Answer:Web hosting is the service that makes our website available to be viewed by others on the Internet. A web host provides space on its server, so that other computers around the world can access our website by means of a network or modem.
Question 2:What is the difference between packet & message switching ?Answer:
Packet SwitchingMessage switchingThere is a tight upper limit on the block size. A fixed size of packet is specified.In message switching there was no upper limit.All the packets are stored in main memory in switching office.In message switching packets are stored on disk. This increases the performance as access time is reduced.
Question 3: Which protocol in used in creating a connection with a remote machine ?Answer:Telnet : It is an older internet utility that allow us to log on to remote computer system. It also facilitates for terminal emulation purpose.
Question 4:Which protocol is used to create a connection with a remote machine? Give any two advantage of using Optical Fibers.Answer:Telnet Two advantage of using Optical Fibers are
Capable of extremely high speed.
No Electromagnetic interference.
Extremely low attending
Question 5:What is cloud computing ?Answer:The sharing of computer resources (dedicated, time-shared, or dynamically shared servers) and related infrastructurer components (load balancers, firewalls, network storage, developer tools, monitors and management tools) to facilitate the deployment and operation of web and network based applications. Cloud computing relies on sharing of resources to achieve coherence and economies of scale, similar to a utility (like the electricity grid) over a network.
Question 6:Write two characterstics of Wi-Fi.Answer:
It is wireless network.
It is for short range.
Question 7:Expand the following :
GSM
GPRS
Answer:
GSM – Global System for Mobile Communication.
GPRS – General Packet Radio Service.
Question 8:Which type of network out of LAN, PAN and MAN is formed, when you connect two mobiles using Bluetooth to transfer a videoAnswer:PAN
Question 9:Write one characterstic each for 2G and 3G mobile technologies.Answer:2G networks primarily involve the transmission of voice information while 3G technology provides the additional advantage of data transfer.
Question 10:What is the difference between Packet switching and circuit switching techniques ?Answer:In circuit switching, a dedicated path exists from source to destination while in packet switching, there is no fixed path.
Question 11:Write two advantages of using an optical fibre cable over an Ethernet cable to connect two service stations, which are 200 m away from each other.Answer:Advantages of optical fibre :
Faster speed than ethernet
Lower Attenuation
Question 12:Identify the Domain name and URL from the following :https://ift.tt/2Rc5dG8Answer:Domain name – income.inURL – https://ift.tt/2Rc5dG8
Question 13:Write one advantage of bus topology of network. Also illustrate how four (4) computers can be connected with each other using bus topology of network.Answer:Advantage (benefits) of Linear Bus Topology is that the cable length required for this topology is the least compared to the other networks.Bus Topology of Network:
Question 14:Give one suitable example of each URL and Domain Name.Answer:URL: http://waltons.inDomain Name: gmail.com
Question 15:Write one advantage of star topology of network ? Also, illustrate how five (5) computers can be connected with each other using star topology of network.Answer:Advantage (benefits) of star toplogy:Easy to replace, install or remove hosts or other devices.
Question 16:Identify the type of topology on the basis of the following :(a) Since every node is directly connected to the server, a large amount of cable is needed which increases the installation cost of the network.(b) It has a single common data path connecting all the nods.Answer:(a) Star Topology(b) Bus Topology
Question 17:Expand the following :(a) VOIP(b) SMTPAnswer:(a) Voice Over Internet Protocol(b) Simple Mail Transfer Protocol
Question 18:Daniel has to share the data among various computers of his two offices branches situated in the same city. Name the network (out of LAN, WAN, PAN and MAN) which is being formed in this process.Answer:MAN
Question 19:ABC International School is planning to connect • all computers, each spread over a distance of 50 metres. Suggest an economic cable type having high speed data transfer to connect these computers.Answer:Optical Fibre Cable.
Question 20:Mahesh wants to transfer data within a city at very high speed. Write the wired transmission medium and type of network.Answer:Wired transmission medium – Optical fibre cable Type of network – MAN.
Question 21:Which device is used to connect all computers inside a lab ?Answer:Hub or Switch
Question 22:Which device is used to connect all computers to the internet using telephone wire ?Answer:RJ – 45. It is an eight wired connectors used to connect computers on a LAN.
Question 23:What is Wi-Fi Card ?Answer:Wi-Fi cards are small and portable cards that allow the computer to connect to the internet through a wireless network. The transmission is through the use of radio waves.
Question 24:Explain the purpose of a router.Answer:A router establishes connection between two network and it can handle network with different protocols. Using a routing table, routers make sure that the data packets are travelling through the best possible paths to reach their destination.
Question 25:Identify the type of topology from the following.(a) Each node is connected with the help of a single cable(b) Each node is connected with the help of independent cable with central switching.Answer:(a) Bus topology(b) Star topology
Question 26:What is the difference between LAN and MAN ?Answer:LAN : It is Local Area Network. The diameter is not more than a single building.WAN : It is Metropolitan Area Network. LAN spans a few kms while MAN spans 5-50 km diameter and is larger than a WAN.
Short Answer Type Questions-I [2 marks each]
Question 1:Write any 1 advantage and 1 disadvantage of Bus topology.Answer:Advantage : Since there is a single common data path connecting all the nodes, the bus topology uses a very short cable length which considerably reduces the installation cost. Disadvantage : Fault detection and isolation is difficult. This is because control of the network is not centralized in any particular node. If a node is faulty on the bus, detection of fault may have to be performed at many points on the network. The faulty node has then to be rectified at that connection point.
Question 2:SunRise Pvt. Ltd. is setting up the network in the Ahmedabad. There are four departments named as MrktDept, FinDept, LegalDept, SalesDept.Distance between varioud buldings is as given:
MrktDept to FinDept80 mMrktDept to LegalDept180 mMrktDept to SalesDept100 mLegalDept to SalesDept150 mLegalDept to FinDept100 mFinDept to SalesDept50 m
Number of Computers in the buildings :
MrktDept20LegalDept10FinDept08SalesDept42
(i) Suggest a cable layout of connections between the Departments and specify the topology.Star Topology should be used.(ii) Suggest the most suitable building to place the server by giving suitable reason.Answer:As per 80 – 20 rule, server should be placed in MrktDept because it has maximium no. of computers.(iii) Suggest the placement of (i) modem (ii) Hub/ Switch in the network.Answer:Each building should have hub/switch and moderm in case Internet connection is required.(iv) The organization is planning to link its sale counter situated in various part of the same city, which type of network out of LAN, WAN, MAN will be formed ? Justify.Answer:MAN (Metropolitan Area Network) as MAN network can be carried out in a city network.
Question 3:Name the protocol(i) Used to transfer voice using packet switched network.Answer:VAns.VOIP (Voice Over Internet Protocol)(ii) Used for chatting between 2 group or between 2 individuals.Answer:IRC (Internet Relay Chat)
Question 4:What is an IP Address ?Answer:IP address is a unique identifier for a node or host connection on an IP network. An IP address is a 32 bit binary number usually represented as 4 decimal values, each representing 8 bits, in the range 0 to 255 (know as octets) separated by decimal points. This is known as “dotted decimal” notation.Example : 140.179.220.200
Question 5:What is HTTP ?Answer:HTTP is a protocol that is used for transferring hypertext (i.e., text,graphic,image,sound,video,e tc,) between 2 computers and is particularly used on the world wideWeb (WWW).[1 mark for definition/explanation]
Question 6:Explain the importance of Cookies.Answer:When the user browses a website, the web server sends a text file to the web browser. This small text file is a cookie. They are usually used to track the pages that we visit so that information can be customised for us for that visit.
Question 7:How is 4G different from 3G?Answer:3G technology adds multimedia facilities such as video, audio and graphics applications whereas 4G will provide better than TV quality images and video-links.
Question 8:Illustrate the layout for connecting 5 computersin a Bus and a Start topology of Networks.Answer:Bus topologyOr any valid illustration of Bus and Star Topology.
Question 9:What is a spam mail ?Answer:Spam is the abuse of electronic messaging systems (including most broadcast media, digital delivery systems) to send unsolicited bulk messages indiscriminately.
Question 10:Differentiate between FTP and HTTPAnswer:FTP is a protocol to transfer files over the InternetHTTP is a protocol which allows the use of HTML to browse web pages in the World Wide Web.
Question 11:Answer:following, which is the fastest
wired and
wireless medium of communication ?
Answer:
Wired – Optical Fiber
Wireless – Infrared OR Microwave
Question 12:What is Worm ? How is it removed ?Answer:A worm is a self-replicating computer program. It uses a network to send copies of itself to other computers on the network and it may do so without any user intervention.Most of .the common anti-virus (anti-worm) remove worm.
Question 13:Out of the following, which all comes under cyber crime ?(i) Stealing away a brand new computer from a showroom.(ii) Getting in someone’s social networking account without his consent and posting pictures on his behalf to harash him.(iii) Secretly copying files from server of a call center and selling it to the other organization.(iv) Viewing sites on a internet browser.Answer:(ii) & (iii)
Question 14:Perfect Edu Services Ltd. is an educational organization. It is planning to setup its India campus at Chennai with its head office at Delhi. The Chennai campus has 4 main buildings – ADMIN, ENGINEERING, BUSINESS and MEDIA. [O.D, 2015]You as a network expert have to suggest the best network related solutions for their problems raised in (i) to (iv), keeping in mind the distances between the buildings and other given parameters.Shortest distances between various buildings.
ADMIN To ENGINEERING55 mADMIN to BUSINESS90 mADMIN to MEDIA90 mENGINEERING to BUSINESS55 mENGINEERING to MEDIA90 mBUSINESS to MEDIA45 mDELHI Head Office to CHENNAI Campus2175 km
Number of Computers Installed at various buildings are as follows :
ADMIN110ENGINEERING75BUSINESS40MEDIA12DELHI Head Office20
(i) Suggest the most appropriate location of the server inside the Chennai campus (out of the 4 buildings), to get the best connectivity for maximum no. of computers. Justify your answer.Answer:ADMIN (Due to maximum number of computers)ORMedia (Due to shorter distance from the other buildings)(ii) Suggest and draw the cable layout to efficiently connect various buildings within the Chennai Campus for connecting the computers.Answer:Anyone of the following(iii) Which hardware device will you suggest to be procured by the company to be installed to protect and control the internet uses within the campus ?Answer:Firewall OR Router(iv) Which of the following will you suggest to establish the online face-to-face communication between the people in the Admin Office of Chennai Campus and Delhi Head Office ?Answer:Cable TV
Question 15:What kind of data gets stored in cookies and how is it useful ?Answer:When a Website with cookie capabilities is visited, its server sends certain information about the browser, which is stored in the hard drive as a text file. It is as way for the server to remember things about the visited sites.
Question 16:Differentiate between packet switching over message switching ?Answer:Packet Switching : Follow store and forward principle for fixed packets. Fixes an upper limit for packet size.Message Switching : Follows store and forward principle for complete message. No limit on block size.
Question 17:Out of the following, which is the fastest(i) wired and(ii) wireless medium of communication ?Infrared, Coaxial Cable, Ethernet Cable, Microwave, Optical FiberAnswer:(i) Wired : Optical Fiber(ii) Wireless : Infrared OR Microwave
Question 18:What is Trojan Horse ?Answer:A Trojan Horse is a code hidden in a program, that looks safe but has hidden side effects typically causing loss or theft of data, and possible system harm.
Question 19:Out of the following, which all comes under cyber crime ?
Stealing away a brand new hard disk from a showroom.
Getting in someone’s social networking account without his consent and posting on his behalf.
Secretly copying data from server of an organization and selling it to tire other organization.
Looking at online activities of a friends blog.
Answer:(ii) & (iii)
Question 20:Write any two differences between twisted pair and coaxial pair cable.Answer:
Twisted PairCo-axial CableTheir bandwidth is not as high as coaxial cables.It has high bandwidth.A twisted pair consists of two copper wires twisted around each other (each has its own insulation around it) like a double helix.A coaxial cable consists of a copper wire core covered by an insulating material and a layer of conducting material over that.
Question 21:Write one advantage of Bus Topology of network, also, illustrate how 4 computers can be connected with each other using star topology of network.Answer:Cable length required for his topology is the least compared to other networks.ORAny other correct advantage of Bus Topology of network.Illustration of 4 computers connected with each other using star topology of network.
Short Answer Type Question-II [3 marks]
Question 1:Uplifting Skills Hub India is a knowledge and skill community which has an aim to uplift the standard of knowledge and skills in the society. It is planning to setup its training centres in multiple towns and villages pan India with its head offices in the nearest cities. They have created a model of their network with a city, a town and 3 villages as follows.As a network consultant, you have to suggest the best network related solutions for their issues/problems raised in (i) to (iv) keeping in mind the distance between various locations and given parameters.Shortest distance between various location :
VILLAGE 1 to B_TOWN2 KMVILLAGE 2 to B_TOWN1.0 KMVILLAGE 3 to B_TOWN1.5 KMVILLAGE 1 to VILLAGE 23.5 KMVILLAGE 1 to VILLAGE 34.5 KMVILLAGE 2 to VILLAGE 32.5 KMA CITY Head Office to B HUB25 KM
Number of Computers installed at various locations are as follows :
B_TOWN120VILLAGE 115VILLAGE 210VILLAGE 315A_CITY OFFICE6
Note :
• In Villages, there are community centres, in which one room has been given as training center to this organization to install computers.• The organization has got financial support from the government and top IT companies.
Suggest the most appropriate location of the SERVER in the BHUB (out of the 4 locations), to get the best and effective connectivity. Justify your answer.
Suggest the best wired medium and draw the cable layout (location to location) to efficiently connect various locations within the B HUB.
Which hardware device will you suggest to connect all the computers within each location of B_HUB ?
Which service/protocol will be most helpful to conduct live interactions of Experts from Head Office and people at all locations of B HUB ?
Answer:(i) B-TOWN can house the server as it has the maximum no. of computers.(ii) Optical fibre cable is the best for this star topology.(iii) Switch(iv) VoIP
Long Answer Type Questions [4 marks each]
Question 1:Indian School in Mumbai is starting up the network between its different wings. There are Four Buildings named as SENIOR, JUNIOR, ADMIN and HOSTEL as shown below.:The distance between various buildings is as follows:
ADMIN TO SENIOR200mADMIN TO JUNIOR150mADMIN TO HOSTEL50mSENIOR TO JUNIOR250mSENIOR TO HOSTEL350mJUNIOR TO HOSTEL350m
Number of Computers in Each Building :
SENIOR130JUNIOR80ADMIN160HOSTEL50
(b1) Suggest the cable layout of connections between the buildings.(b2) Suggest the most suitable place (i.e., building) to house the server of this school, provide a suitable reason.(b3) Suggest the placement of the following devices with justification, i Repeater i Hub/Switch(b4) The organisation also has inquiry office in another dty about 50-60 km away in hilly region. Suggest the suitable transmission media to interconnect to school and inquiry office out of the following : i Fiber optic cable, i Microwave, i RadiowaveAnswer:(b1)
(b2) Server can be placed in the ADMIN building as it has the maxium number of computer.(b3) Repeater can be placed between ADMIN and SENIOR building as the distance is more than 110 m.(b4) Radiowaves can be used in hilly regions as they can travel through obstacles.
Question 2:Vidya Senior Secondary Public School in Nainital is setting up the network between its different wings. There are 4 wings named as SENIOR(S), JUNIOR(J), ADMIN(A) and HOSTEL(H).Distance between various wings are given below :
Wing A to Wing S100 mWing A to Wing J200 mWing A to Wing H400 mWing S to Wing J300 mWing S to Wing H100 mWing J to Wing H450 m
WingNumber of Computers
Wing AWing SWing JWing H
201505025
(ii) Name the most suitable wing where the Server should be installed. Justify your answer.(iii) Suggest where all Hub(s)/Switch(es) should be placed in the network.(iv) Which communication medium would you suggest to connect this school with its main branch in Delhi ?Answer:(i) Star Topology
(ii) Server should be in Wing S as it has the maximum number of computers.(iii) All Wings need hub/switch as it has more than one computer.(iv) Since the distance is more, wireless transmission would be better. Radiowaves are reliable and can travel through obstacles
Question 3:Trine Tech Corporation (TTC) is a professional consultancy company. The company is planning to set up their new offices in India with its hub at Hyderabad. As a network adviser, you have to understand their requirement and suggest them the best available solutions. Their queries are mentioned as (i) to (iv) below.Physical Locations of the blocks of TTC
Block to Block distances (in Mtrs.)
Block (From)Block (To)DistanceHuman ResourceConference110Human ResourceFinance40ConferenceFinance80
Expected Number of Computers to be installed in each block
BlockComputersHuman ResourceFinanceConference2512090
What will be the most appropriate block, where TTC should plan to install their server?
Draw a block diagram showing cable layout to connect all the buildings in the most appropriate manner for efficient communication.
What will be the best possible connectivity out of the following, you will suggest to connect the new setup of offices in Bangalore with its London based office.• Satellite Link• Infrared• Ethernet Cable
Which of the following device will be suggested by you to connect each computer in each of the buildings?• Switch• Modem• Gateway
Answer:(i) Finance block because it has maximum number of computers.(ii)
(iii) Satellite link(iv) Switch
Question 4:Tech Up Corporation (TUC) is a professional consultancy company. The company is planning to set up their new offices in India with its hub at Hyderabad. As a network adviser, you have to understand their requirement and suggest them the best available solutions. Their queries are mentioned as (i) to (iv) below.Physical Locations of the blocks of TUC
Block to Block distances (in Mtrs.)
Block (From)Block (To)DistanceHuman ResourceConference60Human ResourceFinance120ConferenceFinance80
Expected Number of Computers to be installed in each block
BlockComputersHuman ResourceFinanceConference2512090
What will be the most appropriate block, where TUC should plan to install their server?
Draw a block to block cable layout to connect all the buildings in the most appropriate manner for efficient communication.
What will be the best possible connectivity out of the following you will suggest to connect the new setup of offices in Bangalore with its London based office?• Infrared• Satellite Link• Ethernet Cable
Which of the following devices will be suggested by you to connect each computer in each of the buildings?• Gateway• Switch• Modem
Answer:(i) Human resource block because it has maximum number of computers.(ii)(iii) Satellite link(iv) Switch
Question 5:G.R.K International Inc. is planning to connect its Bengaluru Office Setup with its Head Office in Delhi. The Bengaluru Office G.R.K. inter-national Inc. is spread across and area of approx. 1 square kilometer, consisting of 3 blocks – Human Resources, Academics and Administration.You as a network expert have to suggest answers to the four queries (i) to (iv) raised by them.Note : Keep the distance’ between blocks and no. of computers in each block in mind, while providing them the solutions.
Shortest distances between various blocks :
Human Resources to Administration100 mHuman Resources to Academics65 mAcademics to Administration110 mDelhi Head Office to Bengaluru Office Setup2350 km
Number of Computers installed at various blocks are as follows:
BLOCKNo. of ComputersHuman Resources155Administration20Academics100Delhi Head Office20
Suggest the most suitable block in the Bengaluru Office Setup, to host the server. Give a suitable reason with your suggestion.
Suggest the cable layout among the various blocks within the Bengaluru Office Setup for connecting the Blocks.
Suggest a suitable networking device to be installed in each of the blocks essentially required for connecting computers inside the blocks with fast and efficient connectivity.
Suggest the most suitable media to provide secure, fast and reliable data connectivity between Delhi Head Office and the Bengaluru Office Setup.
Answer:
(i) Human Resources because it has maximum number of computers.(ii)
(iii) Switch(iv) Satellite link
Question 6:Rovenza Communications International (RCI) is an online corporate training provider company for IT related courses. The company is setting up their new campus in Kolkata. You as a network expert have to study the physical locations of various blocks and the number of computers to be installed. In the planning phase, provide the best possible answers for the queries (i) to (iv) raised by them.Block to Block Distances (in Mtrs.)
FromToDistance
Administrative BlockAdministrative BlockFinance Block
Finance Block FacultyRecording Block FacultyRecording Block
6012070
Expected Computers to be installed in each block
BlockComputers
Administrative BlockFinance BlockFaculty Recording Block
3020100
Suggest the most appropriate block, where RCI should plan to install the server.
Suggest the most appropriate block to block cable layout to connect all three blocks for efficient communication.
Which type of network out of the following is formed by connecting the computers of these three blocks?• LAN• MAN• WAN
Which wireless channel out of the following should be opted by RCI to connect to students from all over the world?• Infrared• Microwave• Satellite
Write two advantages of using open source software over proprietary software.
Which of the following crime(s) does not come under cybercrime ?
Copying some important data from a computer without taking permission from the owner of-the data.
Stealing keyboard and mouse from a shop.
Getting into unknown person’s social networking account and start messaging on his behalf.
Answer:(i) Faculty Recording Block.(ii) Bus Topology(iii) LAN(iv) Satellite connection(v) Advantages of open source over proprietary software :• Open source software’s source code is available, can be modified copied & distributed while propritary software can’t be change.• Open source is free while propriatary is paid.(vi) (ii) Stealing keyboard & mouse from-a shop.
Question 7:(a) What is the difference between domain name and IP address?(b) Write two advantages of using an optical fibre cable over an Ethernet cable to connect two sendee stations, which are 190 m away from each other.(c) Expertia Professsional Global (EPG) is an online, corporate training provider company for IT related courses. The company is setting up their new campus in Mumbai. You as a network expert have to study the physical locations of various buildings and the number of computers to be installed. In the planning phase, provide the best possible answer for the queries (i) to (iv) raised by them.Building to Building Distances (in Mtrs.)
FromToDistance
Administrative BuildingAdministrative BuildingFinance Building
Finance BuildingRecording Studio BuildingFaculty Studio Building
6012070
Expected Computers to be installed in each Building:
BuildingComputers
Administrative BuildingFinance BuildingFaculty Studio Building
2040120
Suggest the most appropriate building, where EPG should plan to install the server.
Suggest the most appropriate building to building cable layout to connect all three buildings for efficient communication.
Which type of network out of the following is formed by connecting the computers of these three buildings?• LAN• MAN• WAN
Which wireless channel out of the following should be opted by EPG to connect to students of all over the world?• Infrared• Microwave• Satellite
Answer:(a) Domain Name is alphanumeric address of a resource over network IP address is a Numeric Address of a resoure in a Network. Example :Domain NameWWW.Gabsclasses.comIP Address102.112.0.153(b) Optical fibre Advantages :(i) Faculty Studio Building.(ii) Bus Topology.Faculty FinanceAdministrative BuildingStudio Building(iii) LAN(iv) Satellite
Question 8:To provide telemedicine faculty in a hilly state, a computer network is to be setup to connect hospitals in 6 small villages (VI, V2, …, V6) to the base hospital (H) in the state capital. This is shown in the following diagram.No village is more than 20 km away from the state capital.Imagine yourself as a computer consultant for this project and answer the following questions with justification :
Out of the following what kind of link should be provided to setup this network :
Microwave link,
Radio Link,
Wired Link ?
What kind of network will be formed; LAN, MAN, or WAN ?
Many times doctors at village hospital will have to consult senior doctors at the base hospital. For this purpose, how should they contact them: using email, sms, telephone, or video conference ?
Out of SMTP and POP3 which protocol is used to receive emails ?
What are cookies in the context of computer networks?
Rajeshwari is trying for on-line subscription to a magazine. For this she has filled in a form on the magazine’s web site. When the clicks submit button she gets a message that she has left e-mail field empty and she must fill it. For such checking which type of script is generally executed; client side script or server-side script ?
Mention any one difference between free-ware and free software.
Answer:(i) Radio Link(ii) MAN(iii) e-mail(iv) POP3(v) Cookies are files that store user information that is used to identify the user when he logs into the system.(vi) Server-side script.(vii) Freeware is a software that has the user to get unlimited usage. Free software may be free for a certain period’only.
Question 9:Work a lot Consultants are setting up a secured network for their office campus at Gurgaon for their day-to-day office and web- based activities. They are planning to have connectivity between three buildings and the head office situated in Mumbai. Answer the questions (i) to (iv) after going through the building positions in the campus and other details, which are given below:Distances between various buildings :
Building “GREEN” to Building “RED”110 mBuilding “GREEN” to Building “BLUE”45 mBuilding “BLUE” to Building “RED”65 mGurgaon Campus to Head Office1760 km
Number of computers
Building “GREEN”32Building “RED”150Building “BLUE”45Head Office10
Suggest the most suitable place (i.e., building) to house the server of this organization. Also give a reason to justify your suggested location.
Suggest a cable layout of connections between the buildings inside the campus.
Suggest the placement of the following devices with justification:
Repeater.
Switch.
The organization is planning to provide a high speed link with its head office situated in Mumbai using a wired connection. Which of the following cables will be most suitable for this job ?
Optical Fibre
Coaxial Cable
Ethernet Cable
Answer:(i) The most suitable place to install server is building “RED” because this building has maximum computer which reduce communication delay.(ii) Cable layout is Bus topology(iii) Since the cabling distance between buildings GREEN, BLUE and RED are quite large, so a repeater, would ideally be needed along their path to avoid loss of signals during the course of data flow in there routes.(2) In the layout a switch each would be needed in all the building, to interconnect the group of cables from the different computers in each building.(iv) Optical fibre.
Question 10:Granuda Consultants are setting up a secured network for their office campus at Faridabad for their day to day office and web based activities. They are planning to have connectivity between 3 building and the head office situated in Kolkata. Answer the questions (i) to (iv) after going through the building positions in the campus and other details, which are given below :Distances between various buildings :
Building “RAVI” to Building “JAMUNA”120 mBuilding “RAVI” to Building “GANGA”50 mBuilding “GANGA” to Building “JAMUNA”65 mFaridabad Campus to Head Office1460 km
Number of computers
Building “RAVI”25Building “JAMUNA”150Building “GANGA”51Head Office10
Suggest the most suitable place (i.e., block) to house the server of this organization. Also give a reason to justify your suggested location.
Suggest a cable layout of connections between the buildings inside the campus.
Suggest the placement of the following devices with justification:
Repeater
Switch
The organization is planning to provide a high speed link with its head office situated in the KOLKATA using a wired connection. Which of the following cable will be most suitable for this job ?
Optical Fibre
Coaxial Cable
Ethernet Cable
Answer:(i) The most suitable place to install server is in building “JAMUNA” because this building has maximum computer which reduce the communication delay.(ii) Cable layout. (Bus topology).(iii) (1) Since the cabling distance between buildings RAVI, GANGA and JAMUNA are quite large, so a repeater, would ideally be needed along their path to avoid loss of signals during the course of data flow in these routes.(2) In the layout a switch would be needed in all the building, to interconnect the group of cables from the different computers in each building.(iv) Optical fibre.
Question 11:Rehaana Medicos Center has set up its new center in Dubai. It has four buildings as shown in the diagram given below :Distances between various buildings are as follows:
Accounts to Research Lab55 mAccounts to Store150 mStore to Packaging Unit160 mPackaging Unit to Research Lab60 mAccounts to Packaging Unit125 mStore to Research Lab180 m
Number of computers
Accounts25Research Lab100Store15Packaging Unit60
As a network expert, provide the best possible answer for the following queries :
Suggest a cable layout of connections between the buildings.
Suggest the most suitable place (i.e. buildings) to house the server of this origanization.
Suggest the placement of the following device with justification :(a) Repeater(b) Switch/Hub
Suggest a system (hardware/sofware) to prevent unauthorized access to or from the network.
Answer:(i) Layout 1(ii) The most suitable place/building to house the server of this organization would be in Research Lab, building as this building contains the maximum number of computers.(iii) (a) For layout I, since the cabling distance between Accounts to Store is quite large, so a repeater would ideally be needed along their path to avoid loss of signals during the course of data flow in this route. For layotat2, since the cabling distance between Store to Research Lab is quite large, so a repeater would ideally be placed.(b) In both the layouts, a Flub/Switch each would be needed in all the buildings to interconnect the group of cables from the different computers in each building.(iv) Firewall
Question 12:Who is a hacker ?Answer:A computer enthusiast, who uses his computer . programming skills to intentionally access a computer without authorization is known as hacker. A hacker accesses the computer without the intention of destorying data or maliciously harming the computer.
Question 13:The following is a 32 bit binary number usually represented as 4 decimal values, each representing 8 bits, in the range 0 to 255 (know as octets) separated by decimal points. 140.179.220.200What is it? What is its importance?Answer:It is an IP Address. It is used to identify the computers on a network.
TOPIC-2Network Security and Web Service
Very Short Answer Type Questions [1 mark each]
Question 1:Define firewall.Answer:A system designed to prevent unauthorized access to or from a private network is called firewall. It can be implemented in both hardware and software or combination of both.
Question 2:Write any two examples of Server side Scripts.Answer:
ASP
PHP
Question 3:What is the difference between E-mail & chat?Answer:
Chat occurs in near real time, while E-mail doesn’t.
Chat is a 2-way communication which require the permission of both parties, while E-mail is a 1-way communication.
Question 4:Write names of any two popular open source software, which are used as operating systems.Answer:
Kernels
Unix
Linux
Question 5:What is the difference between video conferencing and chat.Answer:In conference, we can include more than one person and it allows text, video and audio while chat is one-to-one communication.
Question 6:Expand the following abbreviations :
HTTP
VOIP
Answer:
HTTP-Hyper Text Transfer Protocol.
VOIP-Voice Over Internet Protocol.
Question 7:What is the difference between HTTP and FTP?Answer:Hyper Text Transfer Protocol deals with Transfer of Text and Multimedia content over internet while FTP (File Transfer Protocol) deals with transfer of files over the internet.
Question 8:What out of the following, will you use to have an audio-visual chat with an expert sitting in a far-away place to fix-up a technical issue ?
VOIP
Email
FTP
Answer:(i) VOIP
Question 9:Name one server side scripting language and one client side scripting language.Answer:Client Side :
JAVASCRIPT
VBSCRIPT
Server Side :
ASP
JSP
Question 10:Which out of the following comes under cyber crime ?
Operating someone’s internet banking account, without his knowledge.
Stealing a keyboard from someone’s computer.
Working on someone’s Computer with his/ her permission.
Answer:(i) Operating someone’s internet banking account, without his knowledge.
Question 11:Name two proprietary softwares along with their application.Answer:
MS-Office – All office applications MS-Word, MS-Excel, MS-PowerPoint.
Visual Studio – Visual Basic, Visual C+ + softwares for application development.
Question 12:Name some cyber offences under the IT Act.Answer:
Tampering with computer source documents
Hacking.
Publishing of information which is obscene in electronic form.
Question 13:What are the 3 ways of protecting intellectual property ?Answer:
Patents
Copyrights
Trademark
Question 14:When a user browses a website, the web server sends a text file to the web browser. What is the name of this ?Answer:Cookies.
Short Answer Type Questions – I [2 mark each]
Question 1:Define the following :
Firewall
VoIP
Answer:(i) Firewall : A system designed to prevent unauthorized access to or from a private network is called firewall. It can be implemented in both hardware and software or combination of both.(ii) VoIP : Voice -over-Internet Protocol(VoIP) is a methodology and group of technologies for delivering voice communications and multimedia sessions over Internet Protocol(IP) networks, such as the Internet.
Question 2:Give the full form of the following terms.
XML
FLOSS
HTTP
FTP
Answer:
XML: Extensible Markup Language.
FLOSS: Free-Libre Open Source Software.
HTTP: Hyper Text Transfer Protocol.
FTP: File Transfer Protocol.
Question 3:Differentiate between WORM and VIRUS in Computer terminology.Answer:VIRUS directly effects the system by corrupting the useful data. A computer virus attaches itself to a program or file enabling it to spread from one computer to another.A worm is similar to a virus by design and is considered to be sub class of a virus. Worm spread from computer to computer, but unlike a virus, it has the capability to travel without any human action.
Abbrevations :Question 4:Expand the following
GSM
GPRS.
Answer:
GSM : Global System for Mobile Communication.
GPRS : General Packet Radio Service.
Question 5:Expand the following abbreviations :
HTTP
VOIP
Answer:
HTTP : Hyper Text Transfer Protocol.
VOIP : Voice Over Internet Protocol.
Question 6:Give the full form of :
FOSS
HTTP
Answer:
FOSS : Free Open Source Software.
HTTP : Hyper Text Transfer Protocol.
Question 7:Write the full forms of the following :
GNU
XML
Answer:
GNU : GNU’s Not Unix
XML : Extensible Markup Language.
Question 8:Expand the following terminologies :
GSM
WLL
Answer:
GSM : Global System for Mobile Communication
WLL : Wireless Local Loop.
Question 9:Give the full forms of the following terms :
CDMA
TDMA
FDMA
Answer:
CDMA : Code Division Multiple Access
TDMA : Time Division Multiple Access
FDMA : Frequency Division Multiple Access
Question 10:Expand the following abbreviations :
FTP
TCP
SMTP
VOIP
Answer:
FTP : File Transfer Protocol
TCP : Transmission Control Protocol.
SMTP : Simple Mail Transfer Protocol.
VOIP : Voice Over Internet Protocol.
Short Answer Type Questions-II [3 marks each]
Question 1:Give two examples of PAN and LAN type of networks.Answer:
PANLAN(i) Personal Area Network(ii) Spans a few metersExample :Bluetooth using 2 moblies and laptops sharing files.(i) Local Area Network(ii) Spans upto a km.Example :System in a lab in a school, systems at home.
Question 2:Which protocol helps us to browse through web pages using internet browsers ? Name any one internet browser.Answer:HTTPGoogle Chrome is a browser
Question 3:Write two advantages of 4G over 3G Mobile Telecommunication Technologies in terms of speed and services.Answer:4G has very high data rates upto 100 Mbps.It covers a wider lange than 3G
Question 1:Write two characteristics of Web 2.0Answer:Web 2.0
dynamic and interactive websites
Only the changed part is reloaded so faster.
via Blogger https://ift.tt/33jC7ua
0 notes