#facebook data recovery number
Explore tagged Tumblr posts
Text
How to Hire a Social Media Hacker Safely: A Complete Guide
In today’s tech-driven world, social media accounts are more than just a place for socializing—they are gateways to personal and business data. Whether you're locked out of your account, worried about digital privacy, or need to strengthen your security, hiring a hacker might seem like a quick fix. However, it's important to approach this cautiously. In this guide, we'll explain how to safely and legally hire a social media hacker, what to look for, and the risks involved.
1. Why Hire a Social Media Hacker?
There are a variety of reasons why you might consider hiring a hacker for your social media needs. Some of the most common include:
Account Recovery: Losing access to a social media account due to hacking or forgotten passwords can be frustrating. A professional hacker can bypass recovery protocols and get you back in.
Security Audits: Ethical hackers can identify weaknesses in your social media security, helping you prevent future cyber-attacks.
Data Retrieval: For business purposes, some companies hire hackers to retrieve important information or gain insights into competitors.
While the idea of hiring a hacker might seem risky, when done ethically and legally, it can be a helpful resource in regaining control over your online assets.
2. What is a Professional Social Media Hacker?
A professional social media hacker is an expert skilled in identifying and exploiting weaknesses in social media platforms to recover accounts, enhance security, or gather data. These hackers fall into two categories:
White-Hat Hackers: Ethical hackers who work within legal boundaries. They are typically hired for account recovery, security testing, and digital protection services.
Black-Hat Hackers: Individuals who use their skills for malicious purposes, such as unauthorized access or data theft.
It's essential to make sure you're hiring a white-hat hacker to ensure the legality of their actions. White-hat hackers use legitimate methods to help you regain access or fortify your account.
3. How to Hire a Social Media Hacker
Finding a reliable social media hacker takes more than just a quick Google search. Here’s how you can find a legitimate hacker without falling for scams:
Freelance Platforms: Websites like Upwork, Freelancer, and Fiverr host professionals offering hacking and cybersecurity services. Be sure to check reviews and ask for verifiable past work.
Cybersecurity Firms: Many reputable companies specialize in ethical hacking services. Hiring through these firms ensures that you’re working with professionals who will operate within legal boundaries.
Hacker Forums: There are many online forums where ethical hackers offer their services. However, proceed with caution, as these forums can also be a breeding ground for scams.
Once you find a hacker, ask for credentials or proof of their experience with the platform you need help with, such as Facebook, Instagram, or Twitter.
4. The Benefits of Hiring a Professional Social Media Hacker
When you hire a social media hacker, you're not just gaining access to your account; you're investing in your online security and peace of mind. Here are the key benefits:
Quick Account Recovery: Forget the long, frustrating customer support routes. A professional hacker can help you regain access faster.
Improved Security: By running security checks and vulnerability assessments, hackers can help you secure your social media accounts and prevent future breaches.
Competitive Advantage: In business, accessing legally obtained data from competitors can help improve your strategies.
Hiring a hacker can be a valuable tool for both personal and professional needs, but only when done ethically.
5. Legal Risks of Hiring a Social Media Hacker
While hiring a hacker can solve a number of problems, it’s essential to understand the risks involved:
Illegal Hacking: Hacking someone else's social media account without permission is illegal and can result in serious legal consequences. Always make sure that your actions, and the actions of the hacker you hire, are within the legal framework.
Scammers: Unfortunately, there are many untrustworthy individuals who claim to be hackers but are really out to scam people. Be careful when sharing personal information, and only work with vetted professionals.
Ethical Concerns: Even if a hacker offers to retrieve information from someone else’s account, remember that doing so without consent is unethical and illegal.
Before you hire, ensure that the hacker’s actions will be lawful and ethical to avoid any legal trouble.
6. How to Protect Yourself When Hiring a Hacker
To safely hire a social media hacker, here are some best practices to follow:
Do Your Research: Take the time to verify the hacker’s credentials. Look at their previous work, ask for references, and check for any feedback from past clients.
Use Secure Communication: Always communicate securely with the hacker to protect your personal information. Avoid sharing sensitive data over unencrypted platforms.
Create a Clear Agreement: Before any work begins, have a formal contract that outlines the services to be performed and the legal limitations. This protects both parties and ensures that the work stays within ethical boundaries.
7. Hiring a Social Media Hacker: What to Expect
When working with a professional hacker, clear communication and expectations are essential. Here’s what to expect:
Transparent Pricing: The cost of hiring a hacker can vary depending on the complexity of the task. Be wary of hackers who offer extremely low rates, as they might not be legitimate.
Clear Communication: A professional hacker should explain the process clearly and answer any questions you have along the way.
Results: Whether you’re looking for account recovery or a security audit, a professional hacker should deliver results within the agreed-upon timeframe.
Conclusion: The Right Way to Hire a Social Media Hacker
Hiring a social media hacker can be an effective way to recover lost accounts, strengthen security, or gain strategic insights. However, it’s essential to hire a reputable, ethical hacker who operates within legal boundaries. By following the steps outlined in this guide, you can safely and legally hire a professional social media hacker to help with your digital needs.
For more information:
Hire a Hacker
Hire a Social Media Hacker
Professional Social Media Hacker
This article integrates the keywords "hire a hacker," "hire a social media hacker," and "professional social media hacker" naturally throughout the content, while keeping the information helpful and engaging for readers. It also includes hyperlinks to the desired website for further exploration, ensuring SEO indexability.
2 notes
·
View notes
Text
The technologically savvy older brothers of a slain Texas college student handed over data extracted from social media accounts later used to secure convictions in the case.
Zuhyr Hamza Kaleem, 22, was shot dead then buried in a premeditated killing by former classmates in 2019, prosecutors said.
Jose Varela, now 24, was sentenced last week to 45 years in prison in the death of 22-year-old Zuhyr Hamza Kaleem. Eric Aguilar, now 25, was sentenced to life in prison on capital murder charges last November.
Austin Walker, also charged with capital murder in the case, pleaded guilty and is scheduled for a presentencing information hearing on Thursday, Harris County District Attorney's Office Community Outreach Coordinator John Donnelly told Fox News Digital.
A fourth man, Gannon Gotlieb, was charged with tampering after admitting to burying and burning Kaleem's body on his property in Grimes County, per the office; the status of that charge is unclear.
Varela, Kaleem and Aguilar grew up in the same area near Houston, where Varela and Kaleem were classmates at Cypress Lakes High School near Houston.
Kaleem agreed to meet at Varela's home in Katy to buy two pounds of marijuana on April 27, 2019, per court documents. After closing the garage door, Varela restrained Kaleem and Aguilar shot him, prosecutors said.
"This was a premeditated murder that left a family questioning what happened to their loved one for more than a year," Harris County District Attorney Kim Ogg said in a statement. "With help from the victim’s family and great police work, we were able to get justice in this horrible case."
CRIMINAL ENTERPRISE FLAUNTS AI IN CREEPY 'FRAUD-FOR-HIRE' COMMERCIAL MEANT FOR DARK WEB
The recovery of Kaleem's body and the group's arrests, nearly a year to date from the murder, were achieved in part due to the investigative work of the victim's older brothers.
Baffled by the Lone Star College student's disappearance, software engineer Umayr Kaleem, 31, told Fox News Digital that his family did not "have the option to just turn the other way and quit" when their brother and his car disappeared.
"We're brothers. We've always been hardworking, ambitious – that's how our parents raised us," he said on Tuesday.
Brothers Umayr and Uzair, a software engineer and mechanical engineer, respectively, learned from a close friend that Kaleem intended to buy marijuana the last day he was seen alive.
After he uncharacteristically failed to return their calls and texts, the brothers accessed his Snapchat account to see with whom he was last in contact.
Valera, saved in their brother's phone as "Jose Cylakes Bayliss Long Hair" – referring to the high school that both attended – was the last person Kaleem had spoken with before his activity on the messaging app came to a halt. After reading a message that was no longer viewable, per court documents reviewed by Fox News Digital, Valera deleted Kaleem as a contact.
AUSTIN POLICE ASK ROBBERY VICTIMS TO CALL 311 AMID STAFFING SHORTAGE, CRIME CRISIS
The brothers accessed Kaleem's phone contacts via his laptop, found Valera's phone number and began researching.
"From there, we started asking around, looking on Facebook, Googling him," Uzair, 27, told Fox. "We found a Facebook profile and it was clear that this was the last person Z talked to – we gave that information to police."
It was "pretty evident," Uzair said, that his brother's killers "tried going into Z's phone to wipe it completely," per notifications on the slain college student's MacBook. Although they "knew they were trying to do some weird s--- on their end," their family "wasn't going to let that happen."
The day after Kaleem vanished, his missing vehicle was observed crossing the border into Mexico from Hidalgo, Texas, per court documents. Almost 10 hours later, Varela crossed back into the United States on foot, police said.
Call records obtained by police showed that Varela had communicated with Walker that day. Snapchat messages between the two pulled by police showed that Varela had asked Walker to bring him clean clothes.
After his arrest on April 24 last year, Aguilar claimed that the gun went off accidentally after Kaleem pulled it out in an argument during the drug deal – but prosecutors argued that the killing and subsequent robbery had been planned over a period of weeks based on harvested text and call logs.
Moreover, the brothers told Fox News Digital, Gotlieb testified that, as he buried the man's body, he noticed Kaleem sustained a bullet wound to his hand as though he had raised it in defense.
"These defendants thought they had gotten away with murder and had moved on with their lives, but they had not counted on the victim’s brothers and law enforcement relentlessly pursuing Kaleem’s whereabouts," Assistant District Attorney Tiffany Dupree said in a press release. "This family went an entire year, pining away, praying for their loved one to come home only to find that his remains had been burned because of some marijuana and a couple of hundred bucks."
Uzair and Umayr told Fox News Digital that Valera's sentence – 45 years in prison with parole eligibility in 2033 – "didn't make any sense whatsoever."
"I think everybody in that courtroom was absolutely shocked," Umayr said. "Even just the prosecutors, there were tears in their eyes. The family is horrified. This person pleaded guilty to premeditated murder. [But] he'll be... on parole less than 20 years from today. He'll be right back on the street."
In light of the "absurdly light" sentence, he said, it's "incredibly hard to be happy."
"The worst prison in the world is a home full of pain – that's all there is, just pain," Umayr said. "We go to birthdays, we try to celebrate things as a family, but it's always awkward. It's been years but that awkwardness, that pain is still there."
Uzair told Fox that his brother intended to transfer to the University of Houston and study business. The courtroom in both Aguilar and Valera's trials, he said, was "packed" with his brother's friends and family.
7 notes
·
View notes
Text
How to Recover If Your Facebook Account Is Hacked? Easy Steps
In today's digital age, social media platforms like Facebook have become an integral part of our lives. We use them to connect with friends and family, share our thoughts and experiences, and even conduct business. However, the convenience of social media also comes with security risks, and one of the most common problems users face is having their Facebook account hacked. If you find yourself in this unfortunate situation, it's essential to act quickly to recover your account and secure your personal information.
In this comprehensive guide, we'll walk you through the steps to recover your hacked Facebook account, protect your data, and prevent future breaches.
1. Recognize the Signs of a Hacked Facebook Account
The first step in recovering your hacked Facebook account is to recognize the signs of a compromise. Common indications include:
Unauthorized login notifications: Facebook sends notifications when someone logs into your account from an unfamiliar device or location.
Unusual activity: Strange posts, messages, or friend requests that you didn't initiate.
Changed password or email address: If you can't log in because your password or email address has been changed without your consent, it's a strong indicator of hacking.
Locked out of your account: If you're unable to access your account due to suspicious activity, your account may have been compromised.
2. Immediate Actions to Take
Upon suspecting or confirming a hack, take the following immediate actions:
Change your password: If you can still access your account, change your password immediately. Make it strong by using a combination of upper and lower-case letters, numbers, and symbols.
Log out of other devices: Go to Facebook's Security Settings and log out of all devices to prevent the hacker from continuing to access your account.
Enable two-factor authentication (2FA): Set up 2FA to add an extra layer of security. This usually involves receiving a code on your mobile device that you'll need to enter when logging in.
Check your email account: Ensure that your email account associated with Facebook is secure. Change its password and enable 2FA if you haven't already.
3. Report the Hacked Account to Facebook
To report your hacked account to Facebook, follow these steps:
Go to the Facebook Help Center.
Navigate to the "Security and Login" section.
Click on "I think my account was hacked or someone is using it without my permission."
Follow the on-screen instructions to secure your account and recover it.
4. Recovering Your Hacked Account
Facebook provides a dedicated recovery process for hacked accounts. Follow these steps to recover your account:
Visit the Facebook Account Recovery page.
Enter your email address, phone number, or Facebook username associated with your account.
Follow the instructions to verify your identity. You may be asked to provide a photo ID or answer security questions.
Facebook will guide you through the account recovery process, allowing you to reset your password and secure your account.
5. Check for Unauthorized Activity
Once you regain access to your account, review your activity log for any unauthorized actions, such as posts, messages, or friend requests. Remove any malicious content and unfriend or block suspicious accounts.
6. Strengthen Your Account Security
To prevent future hacks and secure your Facebook account:
Regularly update your password: Change your password at least every six months, and use a unique combination of characters for each platform.
Enable two-factor authentication (2FA): Ensure that 2FA is enabled to provide an extra layer of protection.
Review app permissions: Periodically check which apps have access to your Facebook account and remove any unnecessary ones.
Be cautious with emails and messages: Avoid clicking on suspicious links or providing personal information in response to unsolicited messages.
Educate yourself: Stay informed about common hacking techniques and scams to protect yourself better.
6. Monitor Your Account
Continuously monitor your Facebook account for any unusual activity. Facebook offers features like login alerts, which notify you of any login attempts from unrecognized devices or locations. Stay vigilant and report any suspicious activity promptly.
7. Protect Your Personal Information
Remember that hackers target personal information. Limit the amount of personal data you share on your profile, such as your phone number, address, and birthdate. Adjust your privacy settings to control who can see your posts and personal information.
Conclusion
Recovering a hacked Facebook account can be a stressful experience, but by taking swift and informed action, you can regain control of your profile and protect your data. Follow the steps outlined in this comprehensive guide, and remember to prioritize account security by regularly updating your password, enabling two-factor authentication, and staying vigilant against potential threats. With these precautions in place, you can enjoy the benefits of social media while keeping your personal information safe from hackers.
For More Information - https://www.linkedin.com/pulse/how-recover-your-facebook-account-hacked-neha-kumari
More Articles -
2 notes
·
View notes
Text
How To Make Sure Information On Your Old Computer Is Really, Truly Deleted
It Isn’t As Simple As Pressing ‘Delete’ And Emptying The Trash. Here’s A Step-By-Step Guide.
— By Sean Captain | June 17, 2025 | The Wall Street Journal (WSJ)

Illustration: Jon Krause
Spring-cleaning season is almost done, and it is time to finally get rid of that old computer. But be very careful before you sell, give away or recycle it.
You could be handing over sensitive information.
Even if you think you deleted everything on it, your old computer may hold lots of personal items you don’t want anyone seeing. In a 2019 study by the University of Hertfordshire (funded by security tech-reviews site Comparitech), researchers purchased 200 used hard drives from the U.S. and U.K. An analysis found data remaining on 59% of the drives, including passport and driver’s license scans, bank statements, utility bills and “intimate photos.”
Just pressing “delete” and emptying the Trash in macOS or the Recycle Bin in Windows won’t do the trick. That’s because your computer maintains an index of where every file resides. Deleting a file erases only its entry in the index, telling your system that it can put new files in that space. But until the system actually does put new files there, the old ones remain accessible. Simple consumer-level file-recovery apps can get at it—never mind professional-grade forensic software.
Here’s how to make sure your data is really gone—even on a computer that won’t start up.
Back-up And Log Out
Start by backing up anything you want to keep. You could drag files onto an external hard drive or use backup software such as the Time Machine app in macsOS. You can also back up to the cloud using Microsoft OneDrive, Apple iCloud, Google Drive, Dropbox or other services. (Don’t empty the Trash or Recycling bin. The wipe process will take care of this.)
Next, log out of applications or games with an online component, so the license is no longer associated with your old computer. Also do this for services like Gmail or Facebook, and web browsers like Chrome that sync your data online—on the admittedly remote chance that an incomplete wipe allows the next owner to access those accounts.
Another step for any type of computer is making sure your files are encrypted—scrambled in a mathematical operation based on very long strings of random numbers and letters called encryption keys. The wiping process will delete the keys to make sure any files that may remain on the machine are unreadable.
What you do next depends on your operating system.
Clearing Out A PC
Windows 10 and the current Windows 11 have a feature called “Reset this PC,” which, with the right settings, thoroughly wipes your data. First, make sure your operating system is up-to-date, as Microsoft recently fixed a bug that sometimes caused the reset process to fail. Press the Windows key, search for “updates” and select “Check for updates.” Install any that are available.
Now check on encryption. In Windows 10 or 11 Home editions, press the Windows key and search for “device encryption settings.” Click “Device encryption settings” on the next screen, then make sure the switch next to “Device encryption” is toggled on. Windows Pro, Enterprise and Education editions have an encryption utility called BitLocker. To enable it, click the Start button, type “bitlocker” and select “Manage BitLocker” from the list of results. (All versions of Windows 10 and 11 also encrypt deleted files.)
Now you’re ready to wipe. Tap the Windows key again, search for “Reset this PC,” then click on it. On the next screen, tap “Reset PC” (Windows 11) or “Get started” (Windows 10), and on the following screen, click “Remove everything.” On the next screen, select “Local reinstall.” (If this doesn’t work, try the “Cloud download” option.) Then click “Change settings,” and on the following screen (under “Clean data?”), toggle the switch to “Yes” and press “Confirm.” On the following screen, press “Next” (Windows 11) or “Reset” (Windows 10). On Windows 11, you will press “Reset” on one more screen. Then let the process run for a few hours.
“Reset this PC” deletes your files, apps and settings, logs you out of your Microsoft account and disables the “Find My Device” feature so the computer is no longer associated with you. Then the serious wiping starts. The encryption keys are deleted, making any encrypted data irretrievably scrambled, and the Clean data option overwrites the ones and zeros that had encoded data on your drive. A clean copy of Windows is also installed.
The MacOS Method
Apple’s “Erase Assistant” feature made its debut in 2021’s macOS 12 Monterey. If your current OS is older, you may be able to update it. To update an older OS to Monterey or a later one, click the Apple menu, then “System Preferences” and “Software Update.” If the update process doesn’t work, jump to “If all else fails” below for another option.
As with Windows, the “Erase All Content & Settings” process should start with encryption. On newer Macs (starting between 2018 and 2020, depending on the model), data is encrypted automatically. Just to be safe, though, turn on a feature called FileVault that adds encryption to older systems and an extra layer to newer ones. Click the Apple icon, then “System Settings” (or “System Preferences” in Monterey). In the next window, click “Privacy & Security” (or “Security & Privacy”), then click FileVault.
Now it is time to wipe. Click again on the Apple icon and “System Settings” (or “System Preferences”), click “General” on the left, then “Transfer or Reset” on the bottom right. Finally, on the next screen, click “Erase All Content & Settings.” (In Monterey, you’ll go there directly from “System Preferences.”)
This process signs you out of Apple services, turns off the “Find My” and “Activation Lock” security measures so that the system is no longer associated with you, and erases all your files, settings, apps and anything else. It deletes the encryption keys, permanently scrambling any data that remains.
If All Else Fails
If your PC or Mac is so old that it can’t run a modern wipe process, you have one more option before seeking pro help. For Windows, several experts recommended the KillDisk app. The $49.95 Professional version runs from a USB drive and overwrites the ones and zeros that encode data on your hard drive with all zeros. Afterward, your computer will no longer boot into Windows unless you reinstall the OS.
For a Mac, your best option is a complex process that Apple describes online.
If these processes sound too complicated, or if your system won’t even turn on, use Apple’s recycling program for Macs or a disposal company that offers hard-drive destruction (or shredding) and recycling for consumers with either type of system. Look for ones that issue a certificate of destruction to verify the process. For instance, Ship ‘N’ Shred accepts drives or whole devices, with prices that include shipping ranging from around $30 to $200.
Modern technology leaves a lot of digital footprints, but at least you can sweep them off your old computer.
— Sean Captain is a Writer ✍️ in New York.
#Technology#Personal Technology#Personal Information#Old Computer 💻 🖥️#Deleting Personal Data#‘Delete’ | Emptying The Trash#Step-By-Step Guide#Sean Captain#The Wall Street Journal (WSJ)
0 notes
Text
Top 5 Mistakes Beginners Make in Dropshipping (And How to Avoid Them)
Getting started with dropshipping is exciting — low overhead, flexible hours, and access to a global market. But in 2025, as more sellers enter the space, it’s becoming easier to stumble early and harder to recover. Many beginners rush in with a “test and hope” mindset, only to realize too late that some mistakes aren’t just expensive — they’re avoidable.
Let’s explore five common missteps beginners make, along with smart, low-key ways to sidestep them while still tapping into trending products, proven dropshipping tips, and practical marketing strategies.
Choosing the wrong product
One of the biggest misjudgments is falling for products that seem viral but offer little staying power. It’s tempting to chase whatever’s popping on TikTok this week, but if it doesn’t solve a real problem or spark a specific emotion, it likely won’t convert.
Instead of focusing purely on what’s trending, pay attention to micro-niches — those passionate pockets of demand with fewer competitors. A quirky desk organizer, for example, might not go viral, but if it speaks directly to remote workers with messy desks, it has a better shot at sticking. The trick is to spot a trending product that aligns with a daily need or desire.
Ignoring niche and branding
New sellers often launch generic stores, assuming broad appeal will equal more sales. In practice, it’s the opposite. A lack of focus confuses visitors and weakens trust. You don’t have to invent a new category — you just need to speak clearly to a specific group.
Branding is more than a logo. It’s the tone of your copy, the lifestyle your product photos reflect, and the consistency across your pages. Even a single-product store, if well-positioned, can appear more trustworthy than a 100-product catalog with no clear theme.
A good dropshipping tip here? Choose a niche where you already understand the customer — whether that’s pet parents, skincare fans, or minimalist travelers — and build the store around them.
Neglecting customer experience and shipping clarity
Many first-time sellers are surprised by how much customers care about shipping transparency. Vague timelines and unclear expectations often result in chargebacks, bad reviews, and burnout.
You don’t need to offer two-day shipping to keep people happy — you just need to set accurate expectations. Displaying clear delivery windows and adding real-time tracking can turn a long wait into an acceptable one.
An often-overlooked strategy is using post-purchase emails not just for receipts but for reassurance. A simple update like “Your order’s being packed!” can go a long way in building trust.
Over-relying on one marketing channel
Relying entirely on Facebook Ads — or any single traffic source — is risky. Ad costs fluctuate, algorithms shift, and what worked yesterday may not work tomorrow. A more sustainable approach is to diversify your marketing strategies early, even on a small scale.
Organic TikTok videos can bring in curious visitors. Pinterest might drive traffic for visually appealing niches. SEO-optimized blog posts can attract buyers who are already searching for solutions. Even simple email flows — cart recovery, thank-you messages, reorder prompts — can boost revenue without extra ad spend.
Don’t wait until sales dip to build a multi-channel presence. Plant those seeds from day one.
Skipping product testing and data
Finally, many beginners give up on a product too quickly — or keep pouring money into one that’s clearly underperforming. The solution isn’t to guess; it’s to test.
Run small-budget ad sets, analyze click-through and conversion rates, and let the numbers guide you. Sometimes it’s not the product — it’s the creative or the offer. Split testing thumbnails, descriptions, or even pricing can uncover what resonates best.
The smartest dropshipping tip isn’t a flashy trick — it’s a mindset. Test, learn, adjust. Repeat.
Avoiding beginner mistakes doesn’t mean being perfect from the start. It means staying curious, listening to data, and remembering that real growth comes from small, consistent improvements. As you find your rhythm, the wins will follow. And when they do, they’ll feel earned — not accidental.
0 notes
Text
How to Create a Monthly PPC Budget That Drives Results
Pay-Per-Click (PPC) advertising is one of the most effective ways to drive targeted traffic, leads, and sales. However, without a solid budgeting strategy, you could be overspending on underperforming ads or missing out on high-converting opportunities. A well-planned monthly PPC budget ensures that your campaigns are aligned with your business goals while maximizing return on investment (ROI). Many businesses rely on expert pay per click services to set realistic budgets and allocate funds efficiently, helping them stay competitive and profitable.
In this guide, we’ll break down how to create a monthly PPC budget that drives real results—without overspending or underachieving.
Step 1: Define Your PPC Goals
Before you can determine how much to spend, you need to define what you're trying to achieve. Your goals will shape your entire budgeting strategy.
Common PPC goals:
Drive website traffic
Generate qualified leads
Increase product sales
Boost app downloads
Improve brand visibility
If your goal is lead generation, your focus should be on cost-per-lead (CPL). For eCommerce, it might be return on ad spend (ROAS) or cost-per-acquisition (CPA). Be as specific and measurable as possible.
Step 2: Understand Your Target Audience and Platforms
Your audience and platform selection directly impact how your budget is spent. Running ads on Google Search, YouTube, Facebook, LinkedIn, or Bing all come with different cost structures and user behaviors.
Key considerations:
Google Search Ads: Higher intent, often higher CPC
Facebook/Instagram Ads: Lower CPC, great for awareness and retargeting
LinkedIn Ads: Ideal for B2B, but can be expensive
YouTube Ads: Great for visual storytelling, works well for brand awareness
Research average costs for your industry on each platform, and determine which ones your target audience uses most.
Step 3: Calculate Your Target Monthly Budget
Now that you know your goals and platforms, it's time to estimate how much to spend. Here’s a simple way to reverse-engineer your PPC budget:
Monthly Budget = Target Conversions x Target CPA
For example, if your goal is to get 100 leads and your target cost per lead is ₹500:
₹500 x 100 leads = ₹50,000 monthly budget
This formula gives you a baseline. You can refine it further with real campaign performance data over time.
Step 4: Break Down the Budget by Campaign or Funnel Stage
Don't treat your entire budget as one big number. Break it down based on:
Campaign type (Search, Display, Remarketing, Shopping)
Funnel stage (Awareness, Consideration, Conversion)
Product or service category
Geographic location (if targeting multiple regions)
Example Breakdown:
50% to Search Campaigns (high intent)
20% to Display/YouTube (awareness)
20% to Remarketing (conversion recovery)
10% to Testing New Ads or Keywords
This approach allows you to allocate funds where they’ll have the most impact while reserving some for experimentation.
Step 5: Account for Seasonality and Promotions
Your budget should be flexible enough to accommodate seasonal trends and promotional periods.
Questions to ask:
Do you have product launches or sales events coming up?
Are there specific months where demand increases?
Should you increase spend during holidays or Q4?
If certain months require a budget spike, consider redistributing spend across slower months to balance your annual budget.
Step 6: Set Daily and Campaign-Level Budgets
Once you’ve decided on your total monthly budget, divide it into daily budgets and assign them to individual campaigns.
Formula: Monthly Budget ÷ 30 = Daily Budget
Then, allocate daily budgets across campaigns based on their importance and past performance. Monitor and adjust regularly to avoid overspending on underperforming ads.
Step 7: Monitor Performance and Adjust
PPC budgeting isn’t a one-time activity—it’s an ongoing process. Track campaign performance weekly or biweekly and make adjustments as needed.
Metrics to watch:
Click-through rate (CTR)
Conversion rate
Cost-per-click (CPC)
Cost-per-acquisition (CPA)
Return on ad spend (ROAS)
Shift budget toward high-performing campaigns and pause or revise low-performing ones. Always keep a portion of your budget flexible for A/B testing and new opportunities.
Bonus Tip: Use Budgeting Tools
Platforms like Google Ads, Facebook Ads Manager, and Google Analytics offer built-in budget tracking tools. You can also use third-party PPC tools or dashboards (like Supermetrics, Optmyzr, or Google Looker Studio) to visualize spend vs. performance.
Conclusion: Scale Smart with Expert Pay Per Click Services
Creating a monthly PPC budget that delivers real results requires more than just setting a number—it involves strategy, analysis, and constant refinement. From defining goals and selecting the right platforms to allocating spend by funnel stage and campaign performance, each decision influences your ROI.
If you're unsure where to start or want to improve results without overspending, partnering with expert pay per click services can help you build a scalable, data-driven budgeting strategy. These professionals provide the tools, insights, and management expertise to ensure your budget works harder and smarter—so every rupee or dollar you invest delivers measurable business impact.
0 notes
Text
CRO for E-commerce: Tracking Add to Cart, Checkout Drop-offs & More

This blog will guide you through how to effectively track and optimize conversion touchpoints, reduce checkout drop-offs, and build a data-backed path to higher revenue. If you’re running paid traffic campaigns and not seeing sales conversions, this is your wake-up call.
Why CRO is Crucial for PPC Campaigns
When businesses invest in PPC services, they often focus on the number of clicks or impressions. But what happens after the user lands on your e-commerce site? Without tracking behaviors like product views, add-to-cart events, and checkout completion, you’re flying blind.
As a trusted PPC services company in Pune, our job is to not just drive traffic but ensure that traffic converts. That’s where CRO comes into play.
Key E-commerce Metrics to Track for CRO
Here are the critical touchpoints every e-commerce business should monitor to optimize performance:
1. Product Page Views
Track how many users are visiting product pages. High bounce rates here may indicate poor product imagery, lack of information, or mismatched search intent.
Optimize with:
High-quality product images
Clear pricing and CTAs
Reviews and trust badges
2. Add to Cart (ATC)
This is a major intent signal. If users are adding items to the cart but not converting, you have a friction point downstream.
Track via:
Google Analytics 4 (GA4) Ecommerce Events
Facebook Pixel or Google Ads conversion tracking
Optimize with:
Faster load times
Visible CTA buttons
Low shipping thresholds (e.g., free shipping at ₹499)
3. Initiate Checkout
If people click “Checkout” but drop off before paying, your checkout flow may be too complex or lacking trust signals.
Optimize with:
One-page checkout
Guest checkout options
Security seals and money-back guarantees
4. Checkout Drop-offs
One of the biggest revenue leaks in e-commerce is cart abandonment. As a leading provider of PPC services in Pune, we often use heatmaps, session recordings, and funnel analysis to identify abandonment points.
Common reasons include:
Unexpected shipping costs
Too many form fields
Slow page loads
Limited payment methods
Fix with:
Transparent pricing
Autofill forms
Multiple payment gateways
Exit intent pop-ups offering discounts
Tools for Effective CRO Tracking
As a professional provider of PPC services, we use a combination of the following tools to track and improve e-commerce performance:
✅ Google Analytics 4
Track events like:
View Item
Add to Cart
Begin Checkout
Purchase
Set up custom funnels to visualize where users are dropping off.
✅ Google Tag Manager (GTM)
Implement custom event tracking without altering site code. GTM makes it easy to fire tags based on button clicks, form submissions, and scroll behavior.
✅ Hotjar or Microsoft Clarity
Use session recordings, heatmaps, and user journeys to identify UX bottlenecks.
✅ Meta (Facebook) Pixel & Google Ads Conversion Tracking
For businesses running ads, these tools allow accurate tracking of ROAS (Return on Ad Spend), especially important for remarketing.
Advanced CRO Tactics for E-commerce PPC Campaigns
As a PPC services company in Pune with real-world experience, we recommend these advanced tactics to improve conversions:
🔁 Dynamic Remarketing
Show users the exact product they abandoned using display or social ads.
🧪 A/B Testing
Test versions of your landing pages, CTAs, pricing layouts, and checkout flow to find what works best.
📦 Cart Recovery Campaigns
Use automated emails, push notifications, or WhatsApp messages to recover abandoned carts within 24 hours.
🧠 Personalization
Show personalized product recommendations based on browsing behavior or past purchases.
The PPC + CRO Connection
Your PPC services and CRO efforts should work in tandem. There’s no point spending on clicks that never convert. That’s why our team at Digital Rhetoric combines performance ad strategy with conversion insights for full-funnel growth.
We don’t just optimize your Google Ads — we ensure every step from the ad click to the final purchase is seamless, trust-building, and high-converting.
Final Thoughts
In today’s competitive e-commerce space, CRO is not optional — it’s foundational. By closely tracking micro-conversions such as Add to Cart and Checkout Initiated, and fixing drop-off points, you can unlock higher ROI from your PPC campaigns.
If you’re searching for reliable, ROI-driven PPC services in Pune, Digital Rhetoric is your growth partner. Let us help you drive not just traffic — but meaningful conversions.
📈 Explore our expert PPC services and see how we boost e-commerce performance with full-funnel optimization strategies.
0 notes
Text
US Stocks Climb Higher, Crude Oil Rebounds
US stocks ended higher on Thursday at the start of a new month as tariff worries eased, with tech issues standing out after robust earnings from Microsoft and Meta Platforms, although after-hours tech news was less positive.
On foreign exchanges, the US dollar extended its two-day recovery lifted by hopes that fears of global trade disruption due to the imposition of additional tariffs by President Donald Trump have peaked. The White House signalled on Thursday that it could announce bilateral trade deals with a number of trading partners in weeks.
The greenback shrugged aside some more cautious US data. Ahead of Friday’s key April non-farm payrolls report, the latest initial jobless claims rose by 18,000 to a seasonally adjusted total of 241,000 for the week ended April 26, higher than the estimate for 225,000.
Meanwhile, the ISM Manufacturing Purchasing Managers’ Index (PMI) data for April fell to 48.7, lower than March’s figure of 49.0, but higher than estimates for a fall to 48.0.
On Wednesday, first quarter GDP data surprisingly showed the US economy contracted for the first time in three years.
With the dollar firming, gold prices came under pressure, retreating further from recent record levels. Spot gold dropped 1.6% to $3,255 per ounce.
At the stock market close in New York on Thursday, the blue-chip Dow Jones Industrials Average was up 0.2% at 40,752, while the broader S&P 500 index gained 0.6% to 5,604.
Meanwhile, the tech-laden Nasdaq Composite jumped 1.5% at 17,710, boosted by above-forecast earnings from two of the ‘Magnificent Seven’ mega cap firms reported after-hours on Wednesday.

NAS100Roll H1
Meta Platforms gained 4.2% after the Facebook and Instagram reported solid quarterly results, with its forward guidance topping consensus as it raised its planned capex to accelerate the construction of AI data centres.
And Microsoft jumped 7.3% after the software giant’s first-quarter revenue increased by 13% and it forecast cloud-computing revenue growth of 34% to 35% for the fiscal fourth quarter.
Two more mega caps reported after the Wall Street close on Thursday - iPhone-maker Apple and online retail giant Amazon.
After gaining 3.1% during the session, Amazon reversed 3.0% in post-market trading after reporting softer guidance for the current-quarter which offset better-than-expected Q1 results despite underwhelming growth in its key cloud computing segment.
Similarly, Apple added 0.4% in the session, but fell 2.3% after-hours as its Q1 earnings only narrowly beat expectations, reflecting caution on the outlook given the uncertainties over Trump’s tariffs.
Away from tech, there were plenty more corporate earnings to assess, with around one-third of all S&P 500-listed firms posting results this week.
Eli Lilly dropped 11.7% after the drugs firm posted disappointing sales of its popular weight-loss drug, Zepbound.
McDonald’s fell 1.9% after the fast-food giant posted a surprise decline in first-quarter global comparable sales.
Meanwhile, Estee Lauder shed 1.8% despite posting better-than-expected third quarter results, as it highlighted ongoing challenges in its travel retail business and subdued consumer sentiment in Asia.
And General Motors fell 0.4% after the automaker said expected the financial hit from tariffs could reach $5 billion and slashed its annual guidance.
Meanwhile, oil prices bounced back from a sell-off on Wednesday as President Trump threatened secondary sanctions on Iran after a fourth round of US-Iran talks was postponed.
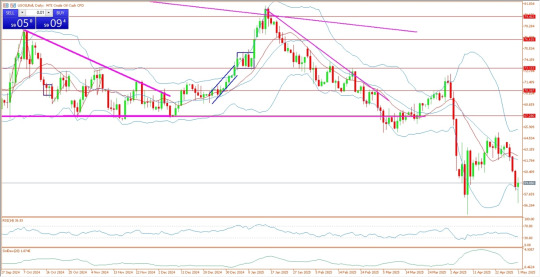
USOILRoll Daily
US WTI crude added 1.3% to $58.99 a barrel, and UK Brent crude gained 1.3% to $61.84 a barrel.
Disclaimer:
The information contained in this market commentary is of general nature only and does not take into account your objectives, financial situation or needs. You are strongly recommended to seek independent financial advice before making any investment decisions.
Trading margin forex and CFDs carries a high level of risk and may not be suitable for all investors. Investors could experience losses in excess of total deposits. You do not have ownership of the underlying assets. AC Capital Market (V) Ltd is the product issuer and distributor. Please read and consider our Product Disclosure Statement and Terms and Conditions, and fully understand the risks involved before deciding to acquire any of the financial products provided by us.
The content of this market commentary is owned by AC Capital Market (V) Ltd. Any illegal reproduction of this content will result in immediate legal action.
0 notes
Text
6 Ways to Make Authentication Systems More User-friendly

In today's digital landscape, strong authentication is paramount for security. However, complex and cumbersome login processes can lead to user frustration, abandoned accounts, and ultimately, a negative user experience. Striking the right balance between robust security and user convenience is crucial. Luckily, there are several ways to enhance authentication systems without compromising safety. Let's explore six key strategies to make logging in a smoother, more user-friendly experience.
1. Embrace Social Login: The Power of Familiarity
Let's face it, most users already have accounts with major platforms like Google, Facebook, Apple, or Twitter. Implementing social login allows users to authenticate using these existing credentials, eliminating the need to create and remember yet another unique username and password.
Benefits: Reduces friction, speeds up the registration and login process, leverages users' existing trust in established platforms, and can improve conversion rates.
Implementation: Offer multiple social login options to cater to a wider user base. Clearly indicate the data being shared with your platform during the authorization process.
2. Passwordless Authentication: Beyond the Traditional String
The password, while a cornerstone of security, is also a major source of user pain. Passwordless authentication methods offer secure alternatives that are often more convenient.
Magic Links: A unique, time-sensitive link is sent to the user's email address or phone number. Clicking the link logs them in directly.
One-Time Passwords (OTPs): Generated via SMS, authenticator apps, or email, OTPs provide a secure, temporary login credential without the need to remember a complex password.
Biometric Authentication: Leveraging fingerprint scanning, facial recognition, or voice recognition offers a secure and highly user-friendly way to authenticate, especially on mobile devices.
Security Keys: Physical USB or Bluetooth keys provide a strong form of two-factor authentication that is resistant to phishing attacks but can be less convenient for some users.
3. Streamline the Registration Process: Keep it Lean
A lengthy and demanding registration form can be a significant barrier to entry. Minimize the required information to the absolute essentials.
Ask for Only What's Necessary: Collect only the data you truly need upfront. Additional information can be gathered later as the user interacts with your platform.
Offer Progressive Profiling: Gradually collect user details over time, rather than bombarding them with a long form during registration.
Provide Clear Instructions and Feedback: Ensure the registration process is intuitive with clear labels, helpful tooltips, and immediate feedback on input errors.
4. Intelligent Password Management Assistance: Empowering Users
While moving beyond passwords is ideal, they remain a reality for many systems. Make password management less painful.
Strong Password Generators: Offer a built-in tool to suggest strong and unique passwords, encouraging better security habits.
Password Strength Indicators: Provide visual feedback on password complexity as the user types, guiding them towards stronger options.
"Show Password" Option: Allow users to temporarily reveal their password during entry to reduce typos and frustration.
Clear Password Reset Mechanisms: Make the password reset process straightforward and secure, with clear instructions and multiple recovery options (e.g., email, security questions).
5. Context-Aware Authentication: Smart Security
Authentication doesn't always need to be a rigid, one-size-fits-all process. Context-aware authentication adapts the level of security based on the user's behavior, location, device, and the sensitivity of the action they are trying to perform.
Risk-Based Authentication: Trigger stronger authentication methods (like 2FA) only when suspicious activity is detected or when accessing sensitive data.
Location-Based Authentication: Allow seamless login from trusted locations but require additional verification from unfamiliar networks.
Device Recognition: Remember trusted devices to avoid repeatedly prompting for authentication.
6. Consistent and Intuitive User Interface:
A well-designed and consistent authentication interface across all platforms (web, mobile app) can significantly improve user experience.
Clear Visual Hierarchy: Make login fields and buttons easily identifiable.
Mobile-First Design: Ensure the authentication process is seamless and responsive on mobile devices.
Consistent Branding: Maintain a consistent look and feel with your overall brand to build trust and familiarity.
Minimize Distractions: Keep the login/registration page clean and focused on the task at hand.
Finding the Right Balance:
Implementing user-friendly authentication doesn't mean sacrificing security. The key is to adopt a layered approach, combining strong security measures with intuitive design and user-centric features. By focusing on convenience and reducing friction, you can create authentication systems that are both secure and a pleasure to use, ultimately leading to happier and more engaged users.
0 notes
Text
Great question—and honestly, one a lot of people wonder about but might not ask out loud.
People link their accounts (like linking Google to a third-party app, or connecting Facebook to Instagram) mainly for convenience, personalization, and better functionality. Here’s a quick breakdown:
1. Easier login (Single Sign-On or SSO):
Instead of creating a new username and password for every service, you can log in using an account you already have—like Google or Facebook. It saves time and avoids password overload.
2. Syncing data across services:
Linking lets apps share information. For example, linking a fitness tracker app with your health app lets them sync your steps or sleep data.
3. Personalized experiences:
Some apps customize what you see based on data from your other accounts. Think of Spotify suggesting playlists based on your Facebook likes, or YouTube showing more relevant ads if linked with your Google account.
4. Social features:
If you link accounts, it’s easier to find friends, share content, or post updates across platforms.
5. Account recovery:
Some services use linked accounts (like your email or phone number) as a backup in case you forget your password.
That said, it’s always worth double-checking what kind of data is being shared when you link accounts—some apps ask for a lot of permissions that aren’t always necessary.
Want me to show you how to check or manage linked accounts on a specific platform?
0 notes
Text
Back end Web Development: 5 Best Measures for a Secure Website

No matter how advanced features you use in back end web development, there are high chances that your website can be attacked by malware, hackers, or users. Such attacks enable fraudulent people to gain access to confidential data, like bank details and health-related information. Cyberattacks not only harm users, but they also spoil the reputation of developers.
So, if you are a developer, you must know reliable ways to strengthen your back end security.
Having taken this fact into account, we have written this blog to familiarize you with the 5 best ways to make your back end strong enough to keep cyberattacks at bay.
Top 5 Methods for Secure Back end Development:
As a developer, if you adopt the following practices in back end web development, you will considerably reduce the chances of unauthorized access to your website:
Multi-Factor Authentication:
Multi-factor authentication (MFA) means adding extra steps for the authentication of a user during login. Let’s get a clear idea of MFA with the example provided below:
Google or Facebook may send a code to the user’s phone number when they sign in with their email, or they may need a biometric scan.
Thus, an additional layer of protection is added, which is better than the usual password and email methods.
Data Encryption:
Personal data, credit card details, and passwords must be kept confidential, as they are sensitive information. In fact, such details must not be stored in the database in their plaintext format. Doing so is as foolish as leaving your door open with the line, ‘come in and steal whatever you want.’
Keep in mind that if data is hacked, all sensitive data will be leaked. To cope with this issue, rely on encryption.
Encryption is like keeping your door locked with a strong key. It scrambles the data so well that it becomes beyond understanding. Even if somebody breaks in, they will not be able to understand what it says. Thus, you can keep your sensitive information safe.
The following are some encryption methods used in back end web development for indubitable security:
Hashing: It converts data into a fixed-length string.
Asymmetrical encryption: With a pair of keys (private and public), asymmetric encryption enables encryption and decryption.
Symmetrical encryption: It utilizes a single key for encryption as well as decryption.
These encryption techniques can allow you to miraculously improve the security of your back end web applications and protect confidential data from fraudulent access and leaking.
Disaster Recovery and Data Backup:
A wise back end development strategy is incomplete without regular data backup and disaster recovery. If a physical loss of data happens, for example, a hard disk failure, or software data loss, like a storage error or damage because of malware, data recovery is possible with backup.
Ensure that you choose backup software and fix a backup schedule, like daily, weekly, or monthly. Your backup methods must have full backups, incremental backups, and differential backups.
Proper Validation and Sanitization:
It’s foolish to trust the input provided by the user. In other words, you’d better assume that any data given by users may be malicious without proper validation and sanitization.
Validation means checking whether the input provided by the user harmonizes with the expected format, type, and constraints.
If there is a form field for an email address, validation will ensure that the input sticks to the correct email format, and it’s not just normal text.
Sanitization means the removal and modification of harmful elements or characters from the user input for the prevention of security vulnerabilities. For instance, if you eliminate HTML tags from user-generated input, it can stop cross-site scripting attacks.
That’s why validation and sanitization are a must-have in back end web development.
Authorization and RBAC:
Authorization means determining whether a user is permitted to do a particular thing on a specific resource. However, it’s wise not to allow some users to get some permissions. It’s because limiting permissions leads to reduced risk. The fewer the permissions are, the smaller the attack surface is. Thus, the fraudulent people can’t take advantage of vulnerabilities. That is where Role-Based Access Control (RBAC) is required. RBAC is a mechanism to control and manage access to resources according to the user’s role in organizations. That’s why businesses look for it when they hire Angular development services.
In a usual website, there is an administrator with full access to all resources, and a user who can view their own data.
RBAC makes sure that each user can only do those things that are allowed to them according to their given role. Let’s get it clear with an example below:
A user is not allowed to modify the data of another user or have access to administration functions. When such permissions are limited according to the requirements, the risks of data breaches and unauthorized access are reduced to a large extent.
Conclusion
The 5 best ways for safe back end web development are multi-factor authentication, data encryption, disaster recovery and data backup, validation and sanitization, and authorization and RBAC.
By using these measures, you can reduce the chances of a cyberattack on your website.
0 notes
Text
youtube
Do you know your chiropractic office stats? https://www.youtube.com/watch?v=5zUuSTBAf7I Do you know your chiropractic office stats? 📊 If not, you’re flying blind! In this short video, we explain why tracking your numbers is vital for your success. Your stats tell a story—where you're thriving, where you're stuck, and precisely what small changes will make the most significant impact. For our mentoring clients, these numbers allow us to be laser-focused on what matters most so they can get the biggest bang for their buck. Don’t guess—assess! Watch now and start making data-driven decisions for a thriving practice. #ChiropracticSuccess #PracticeGrowth #KnowYourNumbers 🔔 Ready to transform your chiropractic skills? Subscribe for expert guidance on chiropractic techniques, neurological wellness, and holistic health strategies! https://www.youtube.com/@TheInformedChiropractor/?sub_confirmation=1 🔗 Stay Connected With Us. 👉 Facebook: https://ift.tt/RnszwBl 👉 Instagram: https://ift.tt/M9dmnwW 👉 Website: https://ift.tt/MmYCs0i 📩 For Business Inquiries: [email protected] ============================= 🎬 WATCH OUR OTHER VIDEOS: 👉 Chiropractic Techniques For Safer Adjustments Using The Macdonald Protocol | Pain Management https://youtu.be/trGCSnV-Uiw 👉 Chiropractic Care For Quicker Healing - How Chiropractic Care Speeds Up Recovery After Injuries https://youtu.be/es9_lz2Qtqw 👉 The Importance Of Tone In Chiropractic Care For Better Health | Chiropractic Care https://youtu.be/WhWWbhl1l1o 👉 Chiropractic Care With Purpose: Building Stronger Commitment To Health | Chiropractic Healing https://youtu.be/u1D-5TtDZXo 👉 Best Chiropractic Care Plans For Lifelong Health And Patient Success | Chiropractic Healing https://youtu.be/mD8wDiUA9c4 ============================= ADD HASHTAGS ⚠️ DISCLAIMER: We do not accept any liability for any loss or damage incurred from you acting or not acting as a result of watching any of our publications. You acknowledge that you use the information we provide at your own risk. Do your research. ✖️ Copyright Notice: This video and our YouTube channel contain dialogue, music, and images that are the property of The Informed Chiropractor. You are authorized to share the video link and channel and embed this video in your website or others as long as a link back to our YouTube channel is provided. © The Informed Chiropractor via The Informed Chiropractor https://www.youtube.com/channel/UCQnQdAp6MTF5Dg5Ahs6Uy6Q February 27, 2025 at 08:29AM
#chiropracticgrowth#polyvagaltheory#chiropractictechniques#holisticchiropractic#neurologicalchiropractic#wellnessandvitality#nervoussystemhealth#Youtube
0 notes
Text
Handling User Authentication and Authorization in Web Design: A Simple Guide

When building a website, keeping user data safe is a top priority. Whether you’re a business owner or working with a web design company in Odisha, understanding how to manage user authentication (verifying identity) and authorization (controlling access) is essential. Let’s break down these concepts in plain language and explore practical steps to implement them effectively.
Why Authentication and Authorization Matter
Imagine your website as a house. Authentication is like checking someone’s ID before letting them in, while authorization decides which rooms they can enter. Without these systems, sensitive data—like passwords, payment details, or personal info—could fall into the wrong hands. For any team, including a web design company in Odisha, getting this right builds trust and keeps users coming back.
User Authentication: Keeping Logins Secure
Authentication ensures only verified users access their accounts. Here’s how to do it well:
Strong Password Policies Encourage users to create complex passwords. Require a mix of letters, numbers, and symbols. Add checks to reject weak passwords like “123456” or “password.”
Social Media Logins Let users sign in with Google, Facebook, or Apple. This simplifies registration and reduces password fatigue. Just ensure their data is handled responsibly.
Two-Step Verification (2SV) Add an extra layer of security. After entering a password, users get a code via SMS or an authenticator app. Even if a password is stolen, accounts stay protected.
Biometric Options Fingerprint or facial recognition (for supported devices) offers a seamless yet secure login experience.
User Authorization: Controlling Access
Once a user is authenticated, authorization determines what they can do. Here’s how to set boundaries:
Role-Based Access Assign roles like “Admin,” “Editor,” or “Guest.” Admins might edit site content, while Guests only view pages. Define permissions for each role clearly.
Permission Levels Not all users need the same access. For example, a blogging site might let authors publish posts but restrict access to billing settings.
Session Management Automatically log users out after inactivity. Set token expiration times for APIs to prevent unauthorized access.
Regular Audits Periodically review who has access to what. Remove permissions for inactive users or outdated roles.
Best Practices for Safety and User Experience
Balancing security with ease of use is key. Here’s how:
Use HTTPS Encrypt data exchanged between users and your site. This prevents hackers from intercepting login details.
Avoid Sensitive Data in URLs Never include passwords or tokens in website links. They can get stored in browser history or server logs.
Error Messages Should Be Generic If a login fails, don’t specify whether the username or password was wrong. Vague messages like “Incorrect credentials” deter hackers.
Update Software Regularly Keep your authentication libraries, plugins, and frameworks up to date. Patches often fix security gaps.
Test for Vulnerabilities Run security checks to spot weaknesses like SQL injections or broken authentication flows.
Making It User-Friendly
Security shouldn’t frustrate users. Here are tips to keep things smooth:
Simplify Password Recovery Offer a straightforward “Forgot Password” flow with email or SMS reset links.
Explain Why Permissions Are Needed If your app requests location or camera access, tell users how it benefits them (e.g., “Enable location to find nearby stores”).
Progress Indicators Show loading animations during login or authorization checks. Users appreciate knowing the system is working.
Final Thoughts
Building secure authentication and authorization systems doesn’t need to be complicated. Start with basic steps like strong passwords and role-based access, then gradually add layers like 2SV or biometrics. Partnering with a reliable team, like a trusted web design company in Odisha, can help you implement these steps smoothly while keeping the user experience pleasant.
Remember, the goal is to protect your users without making them jump through hoops. By prioritizing both safety and simplicity, you’ll create a website that’s secure, functional, and easy to love!
#best web development company in Odisha#web design company in Odisha#best web development agencies Odisha#performance marketing agency odisha#performance marketing agency bhubaneswar
0 notes
Text
Project Webber/RENEW Metrics
I decided to research a non-profit organization called Project Webber/RENEW a program the is a harm reduction peer recovery support system that makes sure people that identify with there preface can go get resources to maintain their lives. I collected the vanity metrics using raw numbers looking at the follower count, likes, shares, retweets and comments I choose to use there platforms Facebook, Instagram, and Youtube to retain my raw data.
Facebook- About 2-50 likes within the last 3 years
About 2-14 shares of posts . memes, videos
And about 45-1.2k Views on videos posted
NO comments were found during my research
Instagram- About 1-210 like since last post about 3 years ago
NO shares were found during my research
About 5 comments on one video
No Views were found during my research
Youtube- No likes, Shares ,or comments were found during my research.
Project Webber/RENEW views on youtube is 300-4.8k
This group has 4 subscribers.
The way Project Webber/RENEW could improve there metrics is simply to hire a social media manger the benefits of obtaining a social media manager can be them looking into what algorithmic metrics are substantiable to have a great social media they will be able to access what the audience likes and what they don't and tailor it to their needs also they can also look into follower growth and develop content that enables the platforms to be more interactive. in my opinion is that they had a great start to there social media presence butt it has slowly diminished they platforms used to be interactive but it hasn't been upkept there last video was about 3 years ago and some metrics would be updating information especially that we are post COVID one advanced metric Project Webber/RENEW can use is social media engagement responding to there followers and friends one behavioral metric that can be improved is online performance and updating their community about up and coming events.
0 notes
Text
SHIB could rise 696% in 2024 according to experts: Opportunity or risk?
The president of the CIFDAQ blockchain ecosystem, Himanshu Maradiya , has predicted a promising future for the Shiba Inu (CRYPTO: SHIB ) cryptocurrency.
What happened
According to BitFinance , Maradiya expects SHIB to reach a value of $0.0001 in 2024, which would represent a 696% increase from its current price. Furthermore, he suggests that Shiba Inu could offer even higher returns in the coming year. Based on the potential market recovery and the growing interest in this meme cryptocurrency, he predicts a peak value of $0.0003 by the end of this year or early 2025.
SHIB has been performing modestly over the past few days, but has managed to gain 2.49% over the past 24 hours. Since its low of $0.00001087 last week, SHIB has rallied by almost 30%, driven by an overall recovery in the cryptocurrency market.
According to TradingView data , if SHIB manages to break out and close above its moving averages, it could open up the possibility of a rally towards the $0.000020 level. However, if SHIB fails to maintain this momentum, it could indicate that sentiment remains negative.
However, not all analysts share this optimism. Utkarsh Tiwari , executive of the KoinBX exchange platform, suggested to Forbes that SHIB could reach $0.000066 by the end of this year, but bearish pressure could cause the cryptocurrency to cross the five-zero threshold again.
You can also read: Ripple and XRP's struggle to break its historical resistance
Why is it important?
The outlook for Shiba Inu in 2024 presents a mixed picture, with some optimistic predictions suggesting significant growth and others anticipating more limited development.
The volatility of the cryptocurrency market and the varied opinions of experts underline the importance of investors carefully assessing risks and opportunities before making decisions.
Photo courtesy of Pixabay
You can also read: Explosive revelations: Trump and Musk talk immigration and global conflicts
For more updates on this topic, please turn on notifications from Benzinga Spain or follow us on our social media: X and Facebook .
Receive exclusive information on market movements 30 minutes before other traders
Benzinga Pro's 14-day free trial gives you access to exclusive insights so you can receive actionable trading signals before millions of other traders. CLICK HERE to start your free trial.
Ripple and XRP's struggle to break its historical resistance
The XRP (CRYPTO: XRP ) cryptocurrency, issued by Ripple Labs , is struggling to break above a historic resistance of $0.60, despite recent favorable news for the company.
What happened
According to CriptoNoticias , the XRP cryptocurrency has found a strong ceiling at $0.60, even with an increasingly clear legal landscape. The current price of XRP is $0.57, below the key level of $0.60, which the cryptocurrency tends to reach and then sideways or bounce off repeatedly.
This conflict comes as the four-year-long legal dispute between the U.S. Securities and Exchange Commission (SEC) and Ripple appears to be coming to an end. Judge Analisa Torres fined Ripple $125 million last week and barred it from further violating U.S. securities laws.
Despite the adverse verdict, Ripple now has clear guidelines on what it can and cannot do with XRP. Furthermore, it has been established that the XRP cryptocurrency, by itself, is not a security.
Following the news, the price of XRP surged by 19%, breaking through the historical resistance and reaching $0.64. However, this resolution, which was expected to significantly boost XRP, has not achieved the desired effect.
On the other hand, on-chain data shows some skepticism from investors. The number of active accounts has decreased by 89% so far this year, suggesting that the market is still not fully convinced of the long-term prospects of Ripple and its projects.
In other developments, Ripple announced last week that it had begun testing its new Ripple USD (RLUSD) cryptocurrency , which is designed to maintain a stable peg with the US dollar.
You can also read: Can the market stabilise? Federated Hermes experts give their opinion
Why is it important?
XRP’s struggle to break above its all-time resistance despite legal developments is a sign that investors may be waiting for more clarity on the future of Ripple and XRP.
Although the litigation with the SEC appears to be coming to an end, the market still seems uncertain about the cryptocurrency's long-term prospects.
The decline in the number of active accounts suggests that investors may be taking a “wait and see” approach towards Ripple and XRP.
www.cifdaq.com
0 notes
Text
Computer Repair
Address:
Lot 2-005 & 2-005CA, 2nd Floor, Plaza Low Yat, Jalan Bukit Bintang
Kuala Lumpur, Wilayah Persekutuan Kuala Lumpur 55100 Malaysia
Phone: +6018-3204347
Email: [email protected]
Website: https://www.jjcomputerrepair.com.my/
Description: JJ One Stop IT Centre offers reliable, high-quality and professional computer repair services in Kuala Lumpur (KL), Petaling Jaya (PJ) and Selangor, Malaysia. We offer a wide range of computer repair services such as laptop repair, desktop/PC repair, Apple MacBook repair, iMac repair, phone repair, iPad repair and iPhone repair. We have a team of qualified and highly experienced technicians who can handle and fix any computer related issues or problems professionally. Trust us to repair your devices fast and efficiently at an affordable price without compromising on quality. Contact us today to get a free quote on your repair solution.
Keywords: Computer Repair Malaysia, Computer Repair Kuala Lumpur (KL), Computer Repair Petaling Jaya (PJ), laptop repair Malaysia, PC repair Malaysia, Mac repair Malaysia, MacBook repair Malaysia, iMac repair Malaysia, phone repair Malaysia, iPad repair Malaysia, iPhone repair Malaysia, data recovery Malaysia, screen replacement Malaysia, virus and malware removal Malaysia, motherboard repair Malaysia, RAM upgrade Malaysia, storage upgrade Malaysia, hard disk repair Malaysia, computer blue screen repair Malaysia
Operating Hours: Monday - Saturday: 10am - 10pm, Sunday: 9am - 10pm
Starting year of the business: 2008
Number of Employee: 20
Payment Method: Cash, Credit Card, Debit Card, eWallet, online banking
Social Media Links:
Linkedin: https://www.linkedin.com/company/jj-computer-repair/
Instagram: https://www.instagram.com/jjcomputerrepair/
Facebook: https://www.facebook.com/people/JJ-Tech/100063507003496/
X.com: https://x.com/jjcomputermsia
Pinterest: https://www.pinterest.com/jjcomputerrepairmalaysia/
Youtube:
https://www.youtube.com/channel/UChqih5A0NsK3GlxVK9mpgbA
https://www.youtube.com/@JJComputerRepair
1 note
·
View note