#file enumeration system
Explore tagged Tumblr posts
Text
Project Special K, my "maybe this will be an Animal Crossing some day" thing that I mainly use to learn C++ has a Starbound-inspired asset system, much like many other things I made. As such, it works in much the same way:
On startup it takes a list of asset sources, sorts them by priority (I haven't added dependency graphs yet) and enumerates all the files in these assets. It then spends more time populating various databases from these files, like which items, species, and villagers there are.
That's it lol it's single-player only for now.
Even though I've written a function to forget certain files' existence in the asset system, there's a catch. Imagine two asset sources contain a file with the same relative path, let's say "foo.json", and they're different in content. During enumeration, the first file is put on the list, marked as coming from the first asset source. Some entries later, the second file is found and takes the first one's spot in the list, marking it as coming from the later source.
If I were to call ForgetVFS("foo.json"), I would not magically get the first version back. It was replaced, after all. That entry in the file list is removed, but it's the only entry listing "foo.json".
And that brings me back to the first PSK mockup screenshot that I made, the Content Filter screen.
Since PSK is beholden to the same limitations as SB that I literally just rambled about, clearly the content filter can't disable specific asset sources. It's all already loaded and processed after all.
But as the text in the mockup notes: "Unchecked species will never appear in your town as villagers. Any villager already there will remain." So if you uncheck the cranky personality and the hippopotamus species before first starting a game, no villagers of that personality and/or species will try to move in. But any cranky hippos already there will remain there until they're put in boxes.
This can be dynamic, in the middle of a running game. You could have a single cranky villager, disable that personality in the content filter, and no other cranky villagers will appear.
Or you could disable sea bass. Any bass already caught, stored in your inventory, in an aquarium on display in your house or the museum, or in storage, will still be there, but no more sea bass will spawn in the waters until you re-enable them.
That of course raises the question...
What happens when you remove an asset source whose contents are already used in your saved game?
My take? Since the saved game would refer to all of this by ID names that have to resolve to the actual things, it could fail gently. Items turn into fallback stuff (perfectly generic items as it were), and villagers whose IDs don't appear in the database, or whose species don't exist anymore, spontaneously move out, their houses replaced by cordoned-off "this space for sale" placeholders.
That was my take. But what's yours?
167 notes
·
View notes
Text
The Sims 2 PSP Cut Content: Part 2
This is a follow up to my first cut content post, mostly talking about the cut Kine Dairy content there.
Missing Division 47 Scientists
Catelyn Lancaster
Catelyn is one of four Division 47 research assistants that are in The Sims 2 PSP. The two research assistants that still show up are Red Sands and Cristian Allard. All four scientists originally spawned inside the Laboratory along with the Curious brothers. Red and Cristian were later moved outside the lab to roam with the guards, leaving the other two scientists behind. This was likely due to performance issues in the lab. The schedule file indicates that Catelyn Lancaster would have spawned in the Laboratory only during the night.
This screenshot shows Red Sands when he used to spawn inside Division 47's lab. (Unfortunately, I couldn't find any pictures showing Catelyn)

As mentioned in part 1: Gender: 0 = female, 1 = male. The eye color is only specified if they're not the default brown. (I'll be using the Sims 2 PC to recreate them, as it shares a lot of assets with the PSP version)
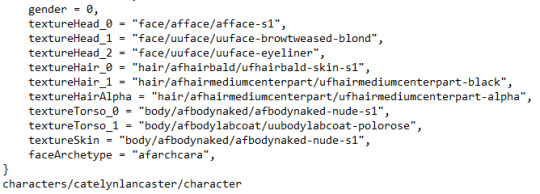

Catelyn Lancaster's Details
Bio: "A research assistant at Division 47." social = 15, intimidation = 3, personality = 1, Her social score is higher compared to other Division 47 locals, and her intimidation score is at the max of 3, which would have made her one of the difficult Sims to do social games with. She has the Air personality type and she uses the serious idle set of animations instead of neutral. Her topic sets (interests) are dresses, makeup, medicine2, school2, politics2, spacesuit, travel2, money1, and the solar system. A visual of these:

Catelyn Lancaster's Secrets
(Personal): "Does all of the work at the lab and gets none of the credit."
(Intimate): "You were her first kiss … and after that experience, probably her last."
(Dark): "Persists in enumerating common domestic fowl prior to emergence from their pre-natal habitats."
Terri Tortuga
As said above, Terri is one of four Division 47 research assistants that are in the game. The schedule file indicates that Terri would have spawned in the Laboratory only during the day.
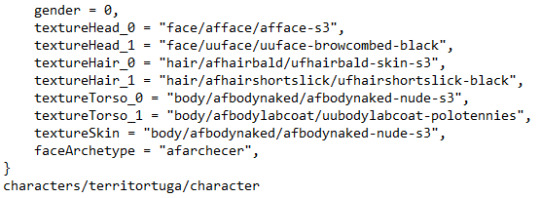

Terri Tortuga's Details
Bio: "A research assistant at Division 47." social = 13, intimidation = 2, personality = 0, Her social and intimidation scores are average for Division 47 locals, so social games aren't too bad. She has the Fire personality type and she uses the serious idle set of animations instead of neutral. Her topic sets (interests) are dresses, makeup, classical, school1, alien, aliens, and birdbee. A visual of these:

Terri Tortuga's Secrets
(Personal): "Has a HUGE crush on Pollination Tech #9."
(Intimate): "Sometimes turns the radio telescope towards the city and pretends it's a laser."
(Dark): "Tests new chemicals on herself, just for kicks. Once grew a second head."
Since we're talking about Division 47, I can add one more thing about TA7 (go see p6tgel's post to learn more about who TA7 is) The devs left notes here and there in the files.

don't worry, he's just (sleeping :P)
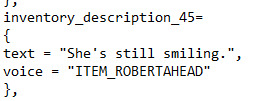
Random fact time: When you collect Roberta Rossum's parts, you can check your inventory and read the descriptions for them, but I don't believe you get a chance to read the description of Roberta's head before you give it to Isaac Rossum? But here it is.
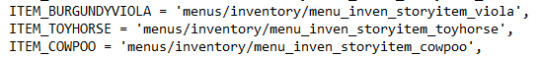
There's also a toy horse story item that I can't seem to find any other information for.
93 notes
·
View notes
Text
The Teufort Census Bureau has begun an exciting new endeavor to organize TF Industries' filing system of the bases mercenaries can be posted at.
Currently 43 of the over 190 bases (and base variants) have been catalogued!
We are collecting data such as: location, local weather, pyrovision support and much more.
Once the existing files have been sorted, enumerators for the Census Bureau will be sent to each and every base to confirm and collect data.
As new bases are found, repurposed, or built, they will be catalogued in the new system.
#I do hope that at least some of the public are as enthusiastic about spreadsheets as I am#as chief enumerator for the Bureau I am very proud of the work we do here.#notice from the census bureau#team fortress 2#teufort census bureau#tf2
8 notes
·
View notes
Text
News of the Day 4/10/25: The Laboratories of Democracy
Alohomora, Paywall!
Look, I'm a GRIT at my core, a girl raised in the South. I like my tea sweet, my chicken fried, and my grass blue. And part of what that means is I sometimes think states' rights is a good thing. Not in the Civil War sense, obviously, and not in the sense where ALEC and other political action groups just propose copycat legislation in state after state.
But America's a huge country, and sometimes different communities have different needs, better strategies work best for them. And just now it means we've got a lot of our fifty different state-level systems pushing back against Trump in their own ways. State AG's are filing lawsuits over birthright citizenship. Local school boards are refusing to ditch DEI even if it does cost them funding. And governors like Gov. Mills are saying, actually state law says trans women are really women and have a right to play sports with all the other girls and women, and you can issue however many executive orders you like but it won't change that fact.
Which of course means Trump & Co. are pushing back. And it's kind of a key part of American governance, that powers not specifically enumerated to the federal government are reserved for the particular states. We fought a war over it and everything. Maybe Trump missed that particular School House Rock video?
The stories are encouraging, if nothing else. More on Maine and how other states are pushing back below the cut.
More on the Gov. Mills tete-a-tete
University of Maine complies with policies restricting trans sports participation (X)
Trump administration targets Maine again, this time on transgender policy in schools (X)
USDA Freezes Some Funds to Maine Over Support for Transgender Athletes (X)
Trump demands Maine governor apologize — or the state will face consequences (X)
Maine found in violation of Title IX over transgender athletes after Trump clashed with governor (X)
States protecting Trans People
Sec. Ed. McMahon threatens (CA governor) Newsom with federal funding cuts over transgender athletes
Trump administration investigating California law against ���forced outing’. Trump’s education and agriculture departments could pull federal funding from the state.
The Dept of Ed. Memo: if schools withhold details about a student's gender identity or sexuality from their parents, this will be considered violating the parents' right to know and they could lose federal funding. (X)
California lawmakers reject bills to ban trans athletes’ participation in girls sports
Pushback in Education
States Are Testing How Much Leeway They Can Get From Trump’s Ed. Dept. (X)
Trump administration ramps up threat to cut school funding over DEI. States have 10 days to affirm they aren’t discriminating based on race or risk losing federal support. (X) The deadline’s since been extended, suggesting some states at least aren’t complying.
‘We’re Gonna Sue’: Chicago Mayor Says Trump Threat To Cut School Funding Over DEI Is ‘Unconstitutional’ (X)
NY public schools tell Trump administration they won’t comply with DEI order
Pushback on Immigration
IRS acting commissioner will resign over deal to send immigrants’ tax data to ICE, sources say (X) This one isn’t a state official obviously. I’m just really proud of this man and wanted to share what he did.
(NY Gov.) Hochul knocks ICE over ‘just plain cruel’ detention of family
Connecticut bill would protect immigrants, target companies aiding deportations (X)
Pushback against Musk and DOGE
Why Elon Musk and Tesla Have a Legal Bone to Pick With Wisconsin. As the billionaire and his allied groups pour more than $20 million into a race for the state’s top court, his car company is suing Wisconsin over a law restricting vehicle sales. (X) $20mil at the time this article was written; I think it broke $100mil eventually. And Wisconsin Democrats still won. (X)
Anti-Trump protests hit cities worldwide – in pictures
The Corruption Case Against Eric Adams Has Been Dropped … With Prejudice. (X) "Everything here smacks of a bargain," wrote SDNY Judge Dale E. Ho in his decision to dismiss the charges against Mayor Adams
NY Gov. Hochul Holds Roundtable with Workers Impacted by Federal Layoffs and Announces Expansion of New York’s “You’re Hired” Initiative to Recruit Impacted Workers
And on climate change, Governors push back as Trump directs the Justice Department to go after state climate laws.
4 notes
·
View notes
Text
The C Programming Language Compliers – A Comprehensive Overview
C is a widespread-purpose, procedural programming language that has had a profound have an impact on on many different contemporary programming languages. Known for its efficiency and energy, C is frequently known as the "mother of all languages" because many languages (like C++, Java, and even Python) have drawn inspiration from it.
C Lanugage Compliers

Developed within the early Seventies via Dennis Ritchie at Bell Labs, C changed into firstly designed to develop the Unix operating gadget. Since then, it has emerge as a foundational language in pc science and is still widely utilized in systems programming, embedded systems, operating systems, and greater.
2. Key Features of C
C is famous due to its simplicity, performance, and portability. Some of its key functions encompass:
Simple and Efficient: The syntax is minimalistic, taking into consideration near-to-hardware manipulation.
Fast Execution: C affords low-degree get admission to to memory, making it perfect for performance-critical programs.
Portable Code: C programs may be compiled and run on diverse hardware structures with minimal adjustments.
Rich Library Support: Although simple, C presents a preferred library for input/output, memory control, and string operations.
Modularity: Code can be written in features, improving readability and reusability.
Extensibility: Developers can without difficulty upload features or features as wanted.
Three. Structure of a C Program
A primary C application commonly consists of the subsequent elements:
Preprocessor directives
Main function (main())
Variable declarations
Statements and expressions
Functions
Here’s an example of a easy C program:
c
Copy
Edit
#include <stdio.H>
int important()
�� printf("Hello, World!N");
go back zero;
Let’s damage this down:
#include <stdio.H> is a preprocessor directive that tells the compiler to include the Standard Input Output header file.
Go back zero; ends this system, returning a status code.
4. Data Types in C
C helps numerous facts sorts, categorised particularly as:
Basic kinds: int, char, glide, double
Derived sorts: Arrays, Pointers, Structures
Enumeration types: enum
Void kind: Represents no fee (e.G., for functions that don't go back whatever)
Example:
c
Copy
Edit
int a = 10;
waft b = three.14;
char c = 'A';
five. Control Structures
C supports diverse manipulate structures to permit choice-making and loops:
If-Else:
c
Copy
Edit
if (a > b)
printf("a is more than b");
else
Switch:
c
Copy
Edit
switch (option)
case 1:
printf("Option 1");
smash;
case 2:
printf("Option 2");
break;
default:
printf("Invalid option");
Loops:
For loop:
c
Copy
Edit
printf("%d ", i);
While loop:
c
Copy
Edit
int i = 0;
while (i < five)
printf("%d ", i);
i++;
Do-even as loop:
c
Copy
Edit
int i = zero;
do
printf("%d ", i);
i++;
while (i < 5);
6. Functions
Functions in C permit code reusability and modularity. A function has a return kind, a call, and optionally available parameters.
Example:
c
Copy
Edit
int upload(int x, int y)
go back x + y;
int important()
int end result = upload(3, 4);
printf("Sum = %d", result);
go back zero;
7. Arrays and Strings
Arrays are collections of comparable facts types saved in contiguous memory places.
C
Copy
Edit
int numbers[5] = 1, 2, three, 4, five;
printf("%d", numbers[2]); // prints three
Strings in C are arrays of characters terminated via a null character ('').
C
Copy
Edit
char name[] = "Alice";
printf("Name: %s", name);
8. Pointers
Pointers are variables that save reminiscence addresses. They are powerful but ought to be used with care.
C
Copy
Edit
int a = 10;
int *p = &a; // p factors to the address of a
Pointers are essential for:
Dynamic reminiscence allocation
Function arguments by means of reference
Efficient array and string dealing with
9. Structures
C
Copy
Edit
struct Person
char call[50];
int age;
;
int fundamental()
struct Person p1 = "John", 30;
printf("Name: %s, Age: %d", p1.Call, p1.Age);
go back 0;
10. File Handling
C offers functions to study/write documents using FILE pointers.
C
Copy
Edit
FILE *fp = fopen("information.Txt", "w");
if (fp != NULL)
fprintf(fp, "Hello, File!");
fclose(fp);
11. Memory Management
C permits manual reminiscence allocation the usage of the subsequent functions from stdlib.H:
malloc() – allocate reminiscence
calloc() – allocate and initialize memory
realloc() – resize allotted reminiscence
free() – launch allotted reminiscence
Example:
c
Copy
Edit
int *ptr = (int *)malloc(five * sizeof(int));
if (ptr != NULL)
ptr[0] = 10;
unfastened(ptr);
12. Advantages of C
Control over hardware
Widely used and supported
Foundation for plenty cutting-edge languages
thirteen. Limitations of C
No integrated help for item-oriented programming
No rubbish collection (manual memory control)
No integrated exception managing
Limited fashionable library compared to higher-degree languages
14. Applications of C
Operating Systems: Unix, Linux, Windows kernel components
Embedded Systems: Microcontroller programming
Databases: MySQL is partly written in C
Gaming and Graphics: Due to performance advantages
2 notes
·
View notes
Text
Capturing the ambience of LEGO Rock Raiders
This classic LEGO title can swing from relaxing to stressful quickly, especially when mining in one of the more hazardous biomes.

Running the game
Rock Raiders was released in 1999, and needs modification to install and run on modern systems. You can use the community alternate installer on Windows 10. It's recommended to use the Masterpiece edition to avoid issues with copy protection.

For the most vanilla experience that runs on modern systems, follow this guide on using dgVoodoo. However, LRR can be improved greatly with mods - read on.
Community Edition and Cafeteria
For further fixes and QoL improvements we can look towards LRR's legendary modding community. First, it's recommended to run Community Edition for additional options, and fixes for, the game.
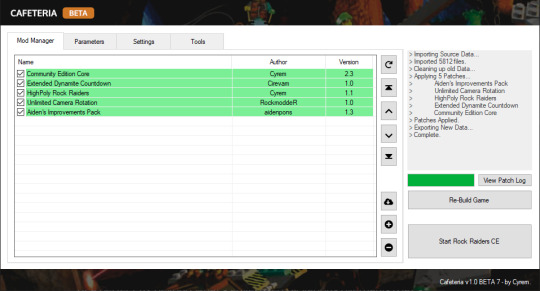
Second, you'll want to launch the game through the Cafeteria mod loader. This includes a Community Edition Core mod, and I recommend adding a couple more:
Extended Dynamite Countdown (this also seems to resolve dynamite-related crashes)
HighPoly Rock Raiders
Unlimited Camera Rotation
Despite all of this I still experienced frequent crashes. I'm not aware of a perfect fix beyond what's advertised by various overhauls (Baz's Mod, Axel's Mod, and Aiden's Improvements Pack). OpenLRR aims to reimplement the game's EXE with fixes for modern systems but isn't complete at the time of writing.
Capturing footage
The Parameters tab of Cafeteria allows us to easily configure which flags to launch LRR with.
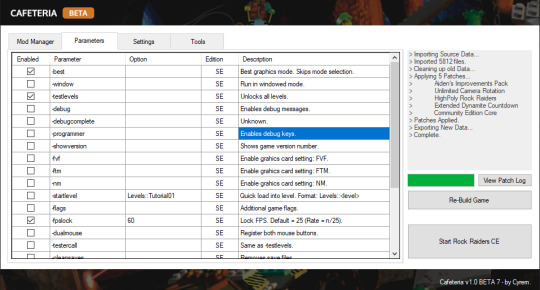
At a minimum I recommend setting up:
best
testlevels
fpslock 60
nointro
You can set widescreen resolutions in Cafeteria's Settings tab.
Camera controls
To zoom in and out, use the +/- keys. Arrow keys rotate the camera. Selecting a Rock Raider offers over-the-shoulder and first-person camera options.

You can cheat by setting large values for the InitialCrystals/InitialOre properties in Data/Lego.CFG. This is especially useful if you want to photograph buildings and vehicles that are unlocked later in LRR's tech tree. We can also using this file to change the presentation of the game - read on.
Hiding the HUD
We can hide the HUD by editing Data/Lego.CFG. This massive plain text file configures the game's frontend, as well as many key gameplay variables.
Look for lines that define UI elements and "comment them out" with a semicolon character, modify coordinates s.t. they are moved offscreen, or delete them. You can also remove or modify the referenced bitmaps so they appear transparent.
Combining a no-HUD mod with the game's first-person mode can produce some amazing screenshots!

Identifying sounds
LRR's ambient soundscapes are defined in Lego.CFG. Look for the assets enumerated under SFX_Drip, SFX_Ambient, and SFX_Ambientloop.
Putting it all together
Overlay the game's ambient assets with your captured first-person no-HUD footage.
youtube
9 notes
·
View notes
Text
Getting Started with C Sharp Programming in Visual Studio

Introduction to C Sharp Programmin
C Sharp (C#) is a moder, object-oriented programming language develope by Microsoft that runs on the .NET framework. It is widel\y used to develop various types of applications, including web, desktop, mobile, and console applications. Understanding the basics of C# programming is essential for software development beginners as well as professionals aiming to expand their programming skills. This article provides a comprehensive introduction to C# programming, covering essential concepts such as setting up projects, understanding console applications, namespaces, classes, and methods.
Setting Up a C Sharp Project in Visual Studio
Visual Studio is a popular integrated development environment (IDE) for developing C# applications. To create a new C# project, follow these basic steps:
Open Visual Studio.
Navigate to File > New > Project.
Select the C# programming language, and under project types, choose “Console Application.”
Name your project (e.g., “IntroductionToCSharp”) and choose a location to save it.
Click “OK” to create the project.
This process sets up a simple console-based application project where you can write and run your C# code.
Understanding Console Applications
A console application is a program that runs in a command-line interface or text-based environment, such as the Command Prompt on Windows. Console applications typically accept text input and output textual information. In C#, console applications are straightforward to create and are a great starting point for understanding the language basics.
To access the console window on Windows, press “Start,” then “Run,” and type “cmd” or “command.” This opens the command prompt where your console applications will display output or receive input.
Writing Your First Console Output Program
A minimal C# console program prints messages to the console window. For instance, writing “Welcome to C# Training” on the screen can be done in just a few lines of code. After setting up a new console project in Visual Studio, you can edit your program with the essential code to display a message.
Here’s an example snippet within the main method:
```csharp
Console.WriteLine("Welcome to C# Training");
```
Running this program (via Ctrl + F5 or running without debugging) prints the message on the console screen, waits for a key press, and then terminates.
Explaining the Role of the Console Class and WriteLine Method
The .NET framework provides the Console class as a tool to interact with the console window—allowing reading input and outputting messages. The WriteLine method of this class prints a line of text and moves the cursor to the next line.
The Console class is part of the System namespace within the .NET framework. This means that to use Console.WriteLine without fully specifying its path, you need to inform your program about the System namespace.
Introduction to Namespaces and Their Importance
Namespaces in C# help organize code logically by grouping classes, interfaces, structures, enumerations, and delegates under a single name. Think of a namespace as a container that prevents naming conflicts and helps manage a large codebase effectively.
For example, the Console class resides within the System namespace. Without referencing this namespace, C# would not recognize the Console class, leading to errors.
How Namespace Declarations Work in C Sharp
To inform the compiler that you want to make use of classes inside a particular namespace, you use the “using” directive at the top of your code file. For example:
```csharp
using System;
```
This declaration allows you to use classes like Console directly, without qualifying them with their full namespace path. If you omit this declaration, you would need to use the fully qualified name like:
```csharp
System.Console.WriteLine("Welcome to C# Training");
```
Using the namespace declaration makes code cleaner and easier to write, especially when multiple references to classes within that namespace are used.
Detailed Look at the System Namespace
The System namespace is a cornerstone in the .NET framework. It contains many essential classes and types such as:
Console – for console input/output operations.
Activator – to create instances of types at runtime.
Action – representing delegates used to point to methods.
Other namespaces – interestingly, namespaces can contain other nested namespaces, allowing for hierarchical and organized code structures.
This hierarchical design helps manage complex applications by distributing functionality across related namespaces and types.
The Concept of Fully Qualified Names vs Namespace Declarations
When using a class without a “using” directive, you must write its full path, known as the fully qualified name (FQN). For example:
```csharp
System.Console.WriteLine("Hello World");
```
Though this is always valid, it becomes cumbersome with frequent references. Thus, it’s common practice to import namespaces using “using” declarations at the start of your file, enabling direct use of the class name:
```csharp
Console.WriteLine("Hello World");
```
This approach enhances readability and reduces repetitive code.
Understanding the Structure of a C Sharp Program
A basic C# program comprises several key components:
Namespace Declaration – defines the broader scope or usage of types from a library or project.
Class Definitions – container for methods and data, which logically group related code.
Methods – blocks of code that perform actions or computations.
Every C# program must have a Main method because it is the designated entry point where execution begins.
The Role of Classes in Organizing Code
In C#, all executable statements must reside in a class or struct. Classes serve as blueprints for objects that encapsulate data and behavior. Even the Main method, which executes first when a C# program runs, resides inside a class.
Generally, a program contains one or multiple classes, each responsible for specific responsibilities or features. The class containing the Main method acts as the starting point for the application.
Overview of Methods and the Main Method as the Entry Point
Methods in C# are functions associated with classes, responsible for tasks or operations. Among all methods, Main is special because it serves as the entry point during program execution.
The Main method is typically defined with static modifiers, meaning it can be called without creating an instance of the class:
```csharp
static void Main(string[] args)
{
// program execution starts here
}
```
When the program runs, execution begins inside the Main method and follows its statements sequentially.
Demonstrating Program Execution Starting from the Main Method
To show the role of Main in program flow, consider this example:
```csharp
using System;
class Program
{
static void Main()
{
Console.WriteLine("Welcome to C# Training");
}
}
```
When this program runs, it starts with the Main method. It executes the Console.WriteLine statement, displaying the welcome message, then ends execution.
If you define other methods but don’t call them from Main or another invoked method, those methods are never executed.
Calling Additional Methods from Main for Extended Functionality
To execute additional functionality, Main can call other methods defined in the class. For example:
```csharp
using System;
class Program
{
static void Main()
{
Console.WriteLine("Welcome to C# Training");
TrainingOne();
}
static void TrainingOne()
{
Console.WriteLine("This is training session one.");
}
}
```
In this scenario, program execution starts in Main, prints the first message, calls TrainingOne, which prints the second message, and then returns to conclude Main. The console output shows both messages.
This pattern illustrates how the Main method orchestrates program flow by invoking other methods in sequence.
Summarizing the Basic Building Blocks of a C Sharp Program
To summarize, a fundamental C# console application contains:
A namespace declaration (e.g., using System;) for accessing library classes.
A class to contain methods (e.g., class Program).
A Main method marking the application's entry point.
Usage of the Console.WriteLine method for output to the console.
These components together create a functional C# program capable of executing instructions and interacting with users through the console window.
Additional Resources for Learning C Sharp
For further learning, consider exploring:
Official Microsoft Documentation for C# and .NET Framework.
Online tutorials and video courses on platforms such as Microsoft Learn, Pluralsight, or Udemy.
Practice coding problems on sites like HackerRank or LeetCode with focus on C#.
Books such as “C# 9.0 in a Nutshell” by Joseph Albahari.
Community forums like Stack Overflow and GitHub repositories for sample projects.
These resources can deepen your understanding of C# programming concepts and advance your expertise in building diverse applications.
0 notes
Text
Getting Started with C Sharp Programming in Visual Studio

Introduction to C Sharp Programming
C Sharp (C#) is a modern, object-oriented programming language develope by Microsoft that runs on the .NET framework. It is widel\y used to develop various types of applications, including web, desktop, mobile, and console applications. Understanding the basics of C# programming is essential for software development beginners as well as professionals aiming to expand their programming skills. This article provides a comprehensive introduction to C# programming, covering essential concepts such as setting up projects, understanding console applications, namespaces, classes, and methods.
Setting Up a C Sharp Project in Visual Studio
Visual Studio is a popular integrated development environment (IDE) for developing C# applications. To create a new C# project, follow these basic steps:
Open Visual Studio.
Navigate to File > New > Project.
Select the C# programming language, and under project types, choose “Console Application.”
Name your project (e.g., “IntroductionToCSharp”) and choose a location to save it.
Click “OK” to create the project.
This process sets up a simple console-based application project where you can write and run your C# code.
Understanding Console Applications
A console application is a program that runs in a command-line interface or text-based environment, such as the Command Prompt on Windows. Console applications typically accept text input and output textual information. In C#, console applications are straightforward to create and are a great starting point for understanding the language basics.
To access the console window on Windows, press “Start,” then “Run,” and type “cmd” or “command.” This opens the command prompt where your console applications will display output or receive input.
Writing Your First Console Output Program
A minimal C# console program prints messages to the console window. For instance, writing “Welcome to C# Training” on the screen can be done in just a few lines of code. After setting up a new console project in Visual Studio, you can edit your program with the essential code to display a message.
Here’s an example snippet within the main method:
```csharp
Console.WriteLine("Welcome to C# Training");
```
Running this program (via Ctrl + F5 or running without debugging) prints the message on the console screen, waits for a key press, and then terminates.
Explaining the Role of the Console Class and WriteLine Method
The .NET framework provides the Console class as a tool to interact with the console window—allowing reading input and outputting messages. The WriteLine method of this class prints a line of text and moves the cursor to the next line.
The Console class is part of the System namespace within the .NET framework. This means that to use Console.WriteLine without fully specifying its path, you need to inform your program about the System namespace.
Introduction to Namespaces and Their Importance
Namespaces in C# help organize code logically by grouping classes, interfaces, structures, enumerations, and delegates under a single name. Think of a namespace as a container that prevents naming conflicts and helps manage a large codebase effectively.
For example, the Console class resides within the System namespace. Without referencing this namespace, C# would not recognize the Console class, leading to errors.
How Namespace Declarations Work in C Sharp
To inform the compiler that you want to make use of classes inside a particular namespace, you use the “using” directive at the top of your code file. For example:
```csharp
using System;
```
This declaration allows you to use classes like Console directly, without qualifying them with their full namespace path. If you omit this declaration, you would need to use the fully qualified name like:
```csharp
System.Console.WriteLine("Welcome to C# Training");
```
Using the namespace declaration makes code cleaner and easier to write, especially when multiple references to classes within that namespace are used.
Detailed Look at the System Namespace
The System namespace is a cornerstone in the .NET framework. It contains many essential classes and types such as:
Console – for console input/output operations.
Activator – to create instances of types at runtime.
Action – representing delegates used to point to methods.
Other namespaces – interestingly, namespaces can contain other nested namespaces, allowing for hierarchical and organized code structures.
This hierarchical design helps manage complex applications by distributing functionality across related namespaces and types.
The Concept of Fully Qualified Names vs Namespace Declarations
When using a class without a “using” directive, you must write its full path, known as the fully qualified name (FQN). For example:
```csharp
System.Console.WriteLine("Hello World");
```
Though this is always valid, it becomes cumbersome with frequent references. Thus, it’s common practice to import namespaces using “using” declarations at the start of your file, enabling direct use of the class name:
```csharp
Console.WriteLine("Hello World");
```
This approach enhances readability and reduces repetitive code.
Understanding the Structure of a C Sharp Program
A basic C# program comprises several key components:
Namespace Declaration – defines the broader scope or usage of types from a library or project.
Class Definitions – container for methods and data, which logically group related code.
Methods – blocks of code that perform actions or computations.
Every C# program must have a Main method because it is the designated entry point where execution begins.
The Role of Classes in Organizing Code
In C#, all executable statements must reside in a class or struct. Classes serve as blueprints for objects that encapsulate data and behavior. Even the Main method, which executes first when a C# program runs, resides inside a class.
Generally, a program contains one or multiple classes, each responsible for specific responsibilities or features. The class containing the Main method acts as the starting point for the application.
Overview of Methods and the Main Method as the Entry Point
Methods in C# are functions associated with classes, responsible for tasks or operations. Among all methods, Main is special because it serves as the entry point during program execution.
The Main method is typically defined with static modifiers, meaning it can be called without creating an instance of the class:
```csharp
static void Main(string[] args)
{
// program execution starts here
}
```
When the program runs, execution begins inside the Main method and follows its statements sequentially.
Demonstrating Program Execution Starting from the Main Method
To show the role of Main in program flow, consider this example:
```csharp
using System;
class Program
{
static void Main()
{
Console.WriteLine("Welcome to C# Training");
}
}
```
When this program runs, it starts with the Main method. It executes the Console.WriteLine statement, displaying the welcome message, then ends execution.
If you define other methods but don’t call them from Main or another invoked method, those methods are never executed.
Calling Additional Methods from Main for Extended Functionality
To execute additional functionality, Main can call other methods defined in the class. For example:
```csharp
using System;
class Program
{
static void Main()
{
Console.WriteLine("Welcome to C# Training");
TrainingOne();
}
static void TrainingOne()
{
Console.WriteLine("This is training session one.");
}
}
```
In this scenario, program execution starts in Main, prints the first message, calls TrainingOne, which prints the second message, and then returns to conclude Main. The console output shows both messages.
This pattern illustrates how the Main method orchestrates program flow by invoking other methods in sequence.
Summarizing the Basic Building Blocks of a C Sharp Program
To summarize, a fundamental C# console application contains:
A namespace declaration (e.g., using System;) for accessing library classes.
A class to contain methods (e.g., class Program).
A Main method marking the application's entry point.
Usage of the Console.WriteLine method for output to the console.
These components together create a functional C# program capable of executing instructions and interacting with users through the console window.
Additional Resources for Learning C Sharp
For further learning, consider exploring:
Official Microsoft Documentation for C# and .NET Framework.
Online tutorials and video courses on platforms such as Microsoft Learn, Pluralsight, or Udemy.
Practice coding problems on sites like HackerRank or LeetCode with focus on C#.
Books such as “C# 9.0 in a Nutshell” by Joseph Albahari.
Community forums like Stack Overflow and GitHub repositories for sample projects.
These resources can deepen your understanding of C# programming concepts and advance your expertise in building diverse applications.
0 notes
Text
Forensic Investigations: Techniques, Challenges, and Real-World Impact

Today’s era of crime has seen a major revolution. Detecting criminals is no longer just a matter of luck or detective work but has been turned into a science. The forensic investigations, a key weapon of modern justice, are the ones that overturned what seemed to be dead cases, gave answers to the multiple questions that the puzzles left and helped courts get on with the enacting of correct and legitimate decisions. Many crimes, such as the one that occurred yesterday or have been left for dead for 20 years as a cold case, are generally resolved by using science and technology.
Forensic investigations can be looked at from different facets sourcing from their operation, the issues encountered by professionals and the unbelievable ways they have been transforming laws and people’s lives in the world. (https://www.forensicexpertsindia.com/cyber-forensics-investigation.html )This is a field that is continuously evolving!
What Are Forensic Investigations?
Definition and Purpose
Forensic investigation is the application of scientific techniques to solve crimes through the collection, examination, and interpretation of the evidence which are physically present at the crime scene. In other words, it is the science of crime-solving. When the evidence is the trace of a human touch such as fingerprints, digital files, various bodily fluids, or even broken glass then the expert's job is to go through it and bring to light the real conditions.
Cyber Forensic Data Recovery is essential to contemporary forensic investigations, particularly when resolving digital fraud and cybercrimes. To recover erased, encrypted, or hidden data from computers, mobile devices, and cloud systems, investigators employ sophisticated techniques. In both criminal and corporate investigations, this procedure aids in locating important digital evidence, such as emails, files, or transaction records.
Key Fields of Forensics
There is undoubtedly more than one kind of forensic examination. Let’s have a look at some main areas:
Criminal Forensics: This refugee particularly emphasizes the physical evidence as a source of data to be used for the purpose of the penetration of a criminal scene. It may also focus on DNA, blood, hair, weapons, or bullets to identify the criminals.
Digital Forensics: This deals with the extraction of data from electronic gadgets such as computers, cell phones, and cloud storage. It is most important in cybercrime cases.
Oxicology, Pathology, and Trace Evidence: Toxicology, pathology, and trace evidence deal with issues that caused death, got people poisoned, or substances left at crime scenes, respectively.
Each of them contributes to an overall picture of the case in its own unique way.
Techniques Used in Forensic Investigations
Evidence Collection and Preservation
The first step in any investigation is collecting and preserving evidence properly. It includes the following:
Photographing and documenting the crime scene
Wearing gloves to keep from contaminating yourself
Labeling and storing items in the right place
Ensuring the chain of custody is unbroken (a list of people who have touched the evidence) is a must. Otherwise, the evidence could become inadmissible in a court of law if the chain of custody was broken.
Laboratory Analysis Methods
Evidence collected in the field is taken to the laboratory for identification and examination. The most popular methods include the following:
DNA Testing: Finding the person who was at the crime scene by DNA matching
Fingerprint Analysis: Identifying users through unique patterns
Toxicology Reports: Enumerating products, alcohol, or poison in a body
Ballistics: Determining if a bullet corresponds to a weapon
These technological methods are crucial for forensic investigations to be taken seriously in court.
Digital Forensics Techniques
In this digital era, professionals in digital forensics work as if they are the new dust on fingerprints. They are equipped with special software and gadgets which allow them to:
Recover deleted files or messages
Analyze login data and browsing history
Do the imaging of the hard drive or mobile phone as well as the copying, please.
A great question is what? Devices that have been encrypted. Today's mobile phones are typically secured with difficult algorithms, thus it is difficult to retrieve data for detectives.
Challenges in Conducting Forensic Investigations
Legal and Ethical Concerns
Compliance with the law is the most significant difficulty. To illustrate:
Is it legally permitted for investigators to unlock a phone without a warrant?
May they have access to cloud accounts?
These inquiries can be a setback or a complete stop to a forensic investigation
Technical Limitations
Encryption is a complicated matter. It guards the rights of users, but at times, it may also be a deterrent from the criminal procedure's side towards accessing the necessary information. Apart from encryption, there also are the following technical difficulties:
Damaged storage devices
Outmoded file formats
Incomplete or corrupted data
The sleuths need to keep their gear and skills as current as possible in order to remain at the top.
Human Error and Bias
Humans are still prone to errors in the laboratory. A mistake in labeling, a wrong interpretation of the test result, or favoring a solution can be the main cause of a conviction based on incorrect evidence. Peer review, oversight, and standardized procedures are thus the pillars of forensic science.
Impact of Forensic Investigations in Reality
Resolution of Long-Standing Issues
Here is an example of how technology in the field of DNA has not only succeeded in transforming existing systems but also in turning around those systems. Some of the cases that were never finished more than twenty years ago are now being put to rest. Sometimes, something as simple as a DNA match or a piece of evidence that is so small that it is invisible can bring families to a point of closure after years of their questions going unanswered.
Dealing with Cybercrime and Corporate Investigations
Forensic investigations can be involved not only in investigating homicides but also in:
Cybercrime: Tracing hackers, ransomware attacks, and data breaches
Corporate Espionage: Uncovering insider threats or intellectual property theft
It's a time when digital forensic investigators have become the last line of defense against deceitful actions, a role that is vital in the era of untrustworthy deepfakes.
Forensic Investigations in the Future’s Span
Venturing Into Novel Territory
Emerging technologies are at the forefront of this change. Utilizing artificial intelligence and machine learning technologies, experts in the investigative field can more accurately and faster detect patterns that would normally be invisible to the human eye. Additionally, the investigation of blockchain for evidence that does not allow tampering of transparent digital records is a current trend.
Those techs will definitely mark the investigations more punctuate, faultless and unchallenged in court.
Preparation of the New Force
There’s a rise in cybercrimes where new categories of criminal activities are being created, and so there is a great need for more forensic experts, mostly in the digital forensics sector. This has given rise to the specialization courses and certification of digital forensic. Whether you are the tech-savvy kind or the one that enjoys science, a career in forensics will be both beneficial and fulfilling.
Conclusion
Black suits, police sirens? Forensic investigations, really, are the ones that give justice a back in the 21st century. Using DNA swabs and having to decrypt hard drives, forensic professionals are the ones that make the truth come out.
As technology develops, forensic science tools and methods will evolve. But the only constant in this business remains the finding of truth, the dispensation of justice, and the societal healing mission.
#cyber forensic investigation#fire/arson investigation#Cyber Forensic Data recovery#Forensic Investigations#Forensic Investigation Services in India#Forensic Investigation
0 notes
Text
👩🏻💻 𝙰𝚛𝚌𝚑𝚒𝚟𝚒𝚘 𝚍𝚒 𝚜𝚝𝚛𝚞𝚖𝚎𝚗𝚝𝚒 𝚙𝚎𝚛 𝚌𝚢𝚋𝚎𝚛𝚜𝚎𝚌𝚞𝚛𝚒𝚝𝚢 𝚌𝚑𝚎 𝚖𝚒 𝚟𝚎𝚗𝚐𝚘𝚗𝚘 𝚌𝚘𝚗𝚜𝚒𝚐𝚕𝚒𝚊𝚝𝚒 𝚘 𝚌𝚒𝚝𝚊𝚝𝚒 𝚗𝚎𝚕 𝚝𝚎𝚖𝚙𝚘
AnyRun: cloud-based malware analysis service (sandbox).
Burp Suite: a proprietary software tool for security assessment and penetration testing of web applications. La community edition, gratis, contiene Burp Proxy and Interceptor (intercetta le richieste effettuate dal browser, consente modifiche on-the-fly e di modificare le risposte; utile per testare applicazioni basate su javascript), Burp Site Map, Burp Logger and HTTP History, Burp Repeater (consente di replicare e modificare le richieste effettuate, aggiungere parametri, rimuoverli, ecc), Burp Decoder, Burp Sequencer, Burp Comparer, Burp Extender (estensioni delle funzionalità di burpsuite, plugin specializzati per individuare bug specifici, automatizzare parte delle attività, ecc) e Burp Intruder (consente di iterare richieste con payload differenti e automatizzare attività di injection).
CyberChef: is a simple, intuitive web app for carrying out all manner of "cyber" operations within a web browser. These operations include simple encoding like XOR and Base64, more complex encryption like AES, DES and Blowfish, creating binary and hexdumps, compression and decompression of data, calculating hashes and checksums, IPv6 and X.509 parsing, changing character encodings, and much more.
DorkSearch: an AI-powered Google Dorking tool that helps create effective search queries to uncover sensitive information on the internet.
FFUF: fast web fuzzer written in Go.
GrayHatWarfare: is a search engine that indexes publicly accessible Amazon S3 buckets. It helps users identify exposed cloud storage and potential security risks.
JoeSandbox: detects and analyzes potential malicious files and URLs on Windows, Mac OS, and Linux for suspicious activities. It performs deep malware analysis and generates comprehensive and detailed analysis reports.
Nikto: is a free software command-line vulnerability scanner that scans web servers for dangerous files or CGIs, outdated server software and other problems.
Nuclei: is a fast, customizable vulnerability scanner powered by the global security community and built on a simple YAML-based DSL, enabling collaboration to tackle trending vulnerabilities on the internet. It helps you find vulnerabilities in your applications, APIs, networks, DNS, and cloud configurations.
Owasp Zap: Zed Attack Proxy (ZAP) by Checkmarx is a free, open-source penetration testing tool. ZAP is designed specifically for testing web applications and is both flexible and extensible. At its core, ZAP is what is known as a “manipulator-in-the-middle proxy.” It stands between the tester’s browser and the web application so that it can intercept and inspect messages sent between browser and web application, modify the contents if needed, and then forward those packets on to the destination. It can be used as a stand-alone application, and as a daemon process.
PIA: aims to help data controllers build and demonstrate compliance to the GDPR. It facilitates carrying out a data protection impact assessment.
SecLists: is the security tester's companion. It's a collection of multiple types of lists used during security assessments, collected in one place. List types include usernames, passwords, URLs, sensitive data patterns, fuzzing payloads, web shells, and many more.
SQLMAP: is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers. It comes with a powerful detection engine, many niche features for the ultimate penetration tester and a broad range of switches lasting from database fingerprinting, over data fetching from the database, to accessing the underlying file system and executing commands on the operating system via out-of-band connections.
Subfinder: fast passive subdomain enumeration tool.
Triage: cloud-based sandbox analysis service to help cybersecurity professionals to analyse malicious files and prioritise incident alerts and accelerate alert triage. It allows for dynamic analysis of files (Windows, Linux, Mac, Android) in a secure environment, offering detailed reports on malware behavior, including malicious scoring. This service integrates with various cybersecurity tools and platforms, making it a valuable tool for incident response and threat hunting.
VirusTotal: analyse suspicious files, domains, IPs and URLs to detect malware and other breaches, automatically share them with the security community.
Wayback Machine: is a digital archive of the World Wide Web founded by Internet Archive. The service allows users to go "back in time" to see how websites looked in the past.
Wapiti: allows you to audit the security of your websites or web applications. It performs "black-box" scans of the web application by crawling the webpages of the deployed webapp, looking for scripts and forms where it can inject data. Once it gets the list of URLs, forms and their inputs, Wapiti acts like a fuzzer, injecting payloads to see if a script is vulnerable.
WPScan: written for security professionals and blog maintainers to test the security of their WordPress websites.
✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖
👩🏻💻𝚂𝚒𝚝𝚒-𝚕𝚊𝚋𝚘𝚛𝚊𝚝𝚘𝚛𝚒
flAWS: through a series of levels you'll learn about common mistakes and gotchas when using Amazon Web Services (AWS).
flAWS2: this game/tutorial teaches you AWS (Amazon Web Services) security concepts. The challenges are focused on AWS specific issues. You can be an attacker or a defender.
✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖
👩🏻💻𝙱𝚛𝚎𝚟𝚎 𝚕𝚒𝚜𝚝𝚊 𝚍𝚒 𝚜𝚒𝚝𝚒 𝚊𝚙𝚙𝚘𝚜𝚒𝚝𝚊𝚖𝚎𝚗𝚝𝚎 𝚟𝚞𝚕𝚗𝚎𝚛𝚊𝚋𝚒𝚕𝚒 𝚜𝚞 𝚌𝚞𝚒 𝚏𝚊𝚛𝚎 𝚎𝚜��𝚛𝚌𝚒𝚣𝚒𝚘
http://testphp.vulnweb.com
0 notes
Text
Educational Organization Question Evaluation Schools play a very important role in our society but due to limited experimental studies revolving around education, the degree of contribution that they have in society remains vague. The continuous modification in educational organizations which mainly focuses on classroom instructional effectiveness and instructor performances has paved the way for a research-based evaluation standards and processes that exhibit effective teaching (Stronge & Helm, 1990). Educational evaluation is the process of assessing and reviewing several characteristics of an educational process. Evaluation should be considered as an important part of the development process for an educational organization. Primarily, educational institutions use evaluation data to exhibit effectiveness and secondly, to present performance measure, which would be a very good marketing tool. Such evaluation is a specialized activity that educators must undertake in order to assess and develop the learning experience that they are offering (Stronge & Helm, 1990). It would be helpful if the components of an organization are carefully pointed out and explain how the organizational structure fits the field of education. Outline An outline is presented showing the required processes for the educational organization evaluation. The process provides guidelines for designing, implementing, assessing and improving the identified form of evaluation. Each of the steps aim to promote evaluations that are proper, useful, feasible, and accurate. The following steps could be undertaken in order to evaluate and analyze the Educational organization (Stufflebeam, 1999). The process could also be used to research and assess the effectiveness of the educational system which is used in an educational institution vital in the formulation of educational policies geared towards the realization of an empowered and globally competitive citizen. I. Identification of purpose to be served Goals for undertaking the evaluation should be clearly defined because these goals will significantly impact the shape of the organization’s efforts. Before the purpose could be fully identified, it is important to use information that is already available. Valuable information of a student can be obtained from the student’s classroom teacher, the cumulative file, and the parent regarding the learning problem. II. Enumeration of questions that need to be addressed and information required. The team involved with the evaluation should create a list of questions that need to be answered and at the same time, gather and organize factual information about a community from which present and future educational program needs can be determined. III. Identification of the manner in which evaluation will be conducted Who: Specific individuals should be designated to be in charge of the whole evaluation process and be responsible for its accomplishment and implementation. Read the full article
0 notes
Text
5 practical Python scripts for 2025
Here are 5 practical Python scripts covering file operations, automation, and web requests, with clear explanations and ready-to-use code:
1. Batch Rename Files
Use Case: Rename all files in a folder (add prefix/suffix/change extension).import os def batch_rename(path, prefix="", suffix="", new_ext=None): for filename in os.listdir(path): name, ext = os.path.splitext(filename) new_name = f"{prefix}{name}{suffix}{new_ext if new_ext else ext}" os.rename( os.path.join(path, filename), os.path.join(path, new_name)) # Example: Add prefix "backup_" to all .txt files batch_rename("/path/to/folder", prefix="backup_", new_ext=".txt")
2. Download Images from URLs
Use Case: Download multiple images from a list of URLs.import requests def download_images(urls, save_dir="images"): os.makedirs(save_dir, exist_ok=True) for i, url in enumerate(urls): try: response = requests.get(url, stream=True) with open(f"{save_dir}/image_{i+1}.jpg", "wb") as f: for chunk in response.iter_content(1024): f.write(chunk) except Exception as e: print(f"Failed to download {url}: {e}") # Example urls = ["https://example.com/1.jpg", "https://example.com/2.jpg"] download_images(urls)
3. Convert CSV to Excel
Use Case: Automate data format conversion.import pandas as pd def csv_to_excel(csv_path, excel_path): df = pd.read_csv(csv_path) df.to_excel(excel_path, index=False) # Example csv_to_excel("data.csv", "data.xlsx")
4. Schedule Computer Shutdown
Use Case: Shut down the system after a delay (Windows only).import os import time def schedule_shutdown(minutes): seconds = minutes * 60 print(f"Shutting down in {minutes} minutes...") time.sleep(seconds) os.system("shutdown /s /t 1") # Example: Shutdown after 30 minutes schedule_shutdown(30)
5. Extract All Links from a Webpage
Use Case: Scrape hyperlinks from a URL.from bs4 import BeautifulSoup import requests def extract_links(url): try: response = requests.get(url) soup = BeautifulSoup(response.text, "html.parser") return [a["href"] for a in soup.find_all("a", href=True)] except Exception as e: print(f"Error: {e}") return [] # Example links = extract_links("https://example.com") print(links)
1 note
·
View note
Text
Nursing Theories Comparative Analysis of Nursing Theories by Ida Jean Orlando and Imogene King The field of nursing as a practice encompasses the field of medical care, going so far to include providing health service for patients and the civil society in general. On the issue of nursing as a healthcare practice, theories abound that offer either supplementary or complementary ideas about how nursing practice should be done and ideally viewed at. Among the contemporary theories that has been considered as relevant to the current practice of nursing are Ida Jean Orlando's theory of functional nursing, and Imogene King's goal attainment theory. These two theories were developed almost a decade apart, wherein King developed hers during the late 1940s, and Orlando's theory during the early 1950s. In the case of Orlando and King, it can be said that the theories that they proposed are supplementary to each other, which means that they have similarities in concepts and philosophy. However, there are also differences that make Orlando's and King's theories distinct from each other. Thus, this paper provides a comparative analysis of the theories presented by the two nurses. King's goal attainment theory acts as an umbrella theory through which Orlando's theory is considered to be part of. These theories supplement each other because King provides a general look at nursing as a practice, while Orlando's theory provides a detailed overview of one aspect enumerated by King as vital in the development of the goal attainment theory. This supplementary relationship between the two nursing theories is captured in King's theory, which posits that goal attainment in interpersonal relationships (which was the focus of her study) contains ten major concepts, which stemmed from both personal and interpersonal relationships. These concepts are enumerated as follows: human interaction, perception, communication, role, stress, time, space, growth and development, and transactions. This theory has been utilized to provide constancy in terms of skills-development and knowledge-pursuit on the part of the nurse as a service and care provider. In fact, its utilization led to the development of the Goal-Oriented Nursing Record (GONR), which is used as a procedural step that would guide the nurse throughout his/her conduct of care service provision and evaluation. Orlando's theory of functional nursing, meanwhile, focuses on one concept considered vital in King's goal attainment theory: perception. In her theory, Orlando explicated the importance of a perceptive nursing, which is a basic requirement and goal for any practicing nurse. This 'concept' is vital in that through the practice of perceptive nursing, the idea of "good" and "bad" nursing is eliminated. Moreover, in discussing further the idea of perceptive -- that is, functional -- nursing, Orlando argued the following, centering on the importance of becoming a care provider first rather than being a medical service provider: in day-to-day practice the nurse can forget what her real job is, if she tries to carry out too great a number of activities. After all there are just so many hours on duty and if every minute is spent on what routine, administration, and doctors prescribe, then obviously you can't get around to helping the patient...the head nurse and the student did do the things that had to be done but nothing they did or said directly helped (the patient). Her expressions of agony did not change, if anything, they got worse. Works Cited Orlando, I. (1962). "Concept of function in professional nursing." Presented at the New York Academy of Medicine. Available at http://www.uri.edu/nursing/schmieding/orlando/manuscripts/files/coffpn.html. Williams, L. (2001). "Imogene King's Interacting Systems Theory -- Application in Emergency and Rural Nursing." Online Journal of Rural Nursing and Healthcare, Vol. 2, Issue 1. Available at http://www.rno.org/journal/issues/Vol-2/issue-1/Williams.htm. Read the full article
0 notes
Text
A quick guide to smb enumeration
Introduction SMB (Server Message Block) is a widely used file-sharing protocol in Windows and Linux environments. While it enables seamless file and printer sharing, misconfigured SMB services can expose sensitive data, leading to serious security risks. That’s why SMB enumeration is a critical step in penetration testing, allowing ethical hackers to gather valuable system, user, and…
0 notes
Text
How to Gain Access to Your NPI File After Changing Jobs

Ensuring your National Provider Identifier (NPI) information is current is vital when changing jobs in healthcare. Your NPI remains constant throughout your career, even with job changes or relocations. To update your NPI details, log in to the National Plan and Provider Enumeration System (NPPES) website. If you don't have access, you can retrieve your NPI information from the NPI Registry and use it to reset your password. Remember, Medicare regulations require any changes to your NPI file, such as a change in practice address, to be updated within 30 days to maintain your billing privileges.
0 notes
Text
Getting Started with C Sharp Programming in Visual Studio

Introduction to C Sharp Programming
C Sharp (C#) is a moder, object-oriented programming language develope by Microsoft that runs on the .NET framework. It is widel\y used to develop various types of applications, including web, desktop, mobile, and console applications. Understanding the basics of C# programming is essential for software development beginners as well as professionals aiming to expand their programming skills. This article provides a comprehensive introduction to C# programming, covering essential concepts such as setting up projects, understanding console applications, namespaces, classes, and methods.
Setting Up a C Sharp Project in Visual Studio
Visual Studio is a popular integrated development environment (IDE) for developing C# applications. To create a new C# project, follow these basic steps:
Open Visual Studio.
Navigate to File > New > Project.
Select the C# programming language, and under project types, choose “Console Application.”
Name your project (e.g., “IntroductionToCSharp”) and choose a location to save it.
Click “OK” to create the project.
This process sets up a simple console-based application project where you can write and run your C# code.
Understanding Console Applications
A console application is a program that runs in a command-line interface or text-based environment, such as the Command Prompt on Windows. Console applications typically accept text input and output textual information. In C#, console applications are straightforward to create and are a great starting point for understanding the language basics.
To access the console window on Windows, press “Start,” then “Run,” and type “cmd” or “command.” This opens the command prompt where your console applications will display output or receive input.
Writing Your First Console Output Program
A minimal C# console program prints messages to the console window. For instance, writing “Welcome to C# Training” on the screen can be done in just a few lines of code. After setting up a new console project in Visual Studio, you can edit your program with the essential code to display a message.
Here’s an example snippet within the main method:
```csharp
Console.WriteLine("Welcome to C# Training");
```
Running this program (via Ctrl + F5 or running without debugging) prints the message on the console screen, waits for a key press, and then terminates.
Explaining the Role of the Console Class and WriteLine Method
The .NET framework provides the Console class as a tool to interact with the console window—allowing reading input and outputting messages. The WriteLine method of this class prints a line of text and moves the cursor to the next line.
The Console class is part of the System namespace within the .NET framework. This means that to use Console.WriteLine without fully specifying its path, you need to inform your program about the System namespace.
Introduction to Namespaces and Their Importance
Namespaces in C# help organize code logically by grouping classes, interfaces, structures, enumerations, and delegates under a single name. Think of a namespace as a container that prevents naming conflicts and helps manage a large codebase effectively.
For example, the Console class resides within the System namespace. Without referencing this namespace, C# would not recognize the Console class, leading to errors.
How Namespace Declarations Work in C Sharp
To inform the compiler that you want to make use of classes inside a particular namespace, you use the “using” directive at the top of your code file. For example:
```csharp
using System;
```
This declaration allows you to use classes like Console directly, without qualifying them with their full namespace path. If you omit this declaration, you would need to use the fully qualified name like:
```csharp
System.Console.WriteLine("Welcome to C# Training");
```
Using the namespace declaration makes code cleaner and easier to write, especially when multiple references to classes within that namespace are used.
Detailed Look at the System Namespace
The System namespace is a cornerstone in the .NET framework. It contains many essential classes and types such as:
Console – for console input/output operations.
Activator – to create instances of types at runtime.
Action – representing delegates used to point to methods.
Other namespaces – interestingly, namespaces can contain other nested namespaces, allowing for hierarchical and organized code structures.
This hierarchical design helps manage complex applications by distributing functionality across related namespaces and types.
The Concept of Fully Qualified Names vs Namespace Declarations
When using a class without a “using” directive, you must write its full path, known as the fully qualified name (FQN). For example:
```csharp
System.Console.WriteLine("Hello World");
```
Though this is always valid, it becomes cumbersome with frequent references. Thus, it’s common practice to import namespaces using “using” declarations at the start of your file, enabling direct use of the class name:
```csharp
Console.WriteLine("Hello World");
```
This approach enhances readability and reduces repetitive code.
Understanding the Structure of a C Sharp Program
A basic C# program comprises several key components:
Namespace Declaration – defines the broader scope or usage of types from a library or project.
Class Definitions – container for methods and data, which logically group related code.
Methods – blocks of code that perform actions or computations.
Every C# program must have a Main method because it is the designated entry point where execution begins.
The Role of Classes in Organizing Code
In C#, all executable statements must reside in a class or struct. Classes serve as blueprints for objects that encapsulate data and behavior. Even the Main method, which executes first when a C# program runs, resides inside a class.
Generally, a program contains one or multiple classes, each responsible for specific responsibilities or features. The class containing the Main method acts as the starting point for the application.
Overview of Methods and the Main Method as the Entry Point
Methods in C# are functions associated with classes, responsible for tasks or operations. Among all methods, Main is special because it serves as the entry point during program execution.
The Main method is typically defined with static modifiers, meaning it can be called without creating an instance of the class:
```csharp
static void Main(string[] args)
{
// program execution starts here
}
```
When the program runs, execution begins inside the Main method and follows its statements sequentially.
Demonstrating Program Execution Starting from the Main Method
To show the role of Main in program flow, consider this example:
```csharp
using System;
class Program
{
static void Main()
{
Console.WriteLine("Welcome to C# Training");
}
}
```
When this program runs, it starts with the Main method. It executes the Console.WriteLine statement, displaying the welcome message, then ends execution.
If you define other methods but don’t call them from Main or another invoked method, those methods are never executed.
Calling Additional Methods from Main for Extended Functionality
To execute additional functionality, Main can call other methods defined in the class. For example:
```csharp
using System;
class Program
{
static void Main()
{
Console.WriteLine("Welcome to C# Training");
TrainingOne();
}
static void TrainingOne()
{
Console.WriteLine("This is training session one.");
}
}
```
In this scenario, program execution starts in Main, prints the first message, calls TrainingOne, which prints the second message, and then returns to conclude Main. The console output shows both messages.
This pattern illustrates how the Main method orchestrates program flow by invoking other methods in sequence.
Summarizing the Basic Building Blocks of a C Sharp Program
To summarize, a fundamental C# console application contains:
A namespace declaration (e.g., using System;) for accessing library classes.
A class to contain methods (e.g., class Program).
A Main method marking the application's entry point.
Usage of the Console.WriteLine method for output to the console.
These components together create a functional C# program capable of executing instructions and interacting with users through the console window.
Additional Resources for Learning C Sharp
For further learning, consider exploring:
Official Microsoft Documentation for C# and .NET Framework.
Online tutorials and video courses on platforms such as Microsoft Learn, Pluralsight, or Udemy.
Practice coding problems on sites like HackerRank or LeetCode with focus on C#.
Books such as “C# 9.0 in a Nutshell” by Joseph Albahari.
Community forums like Stack Overflow and GitHub repositories for sample projects.
These resources can deepen your understanding of C# programming concepts and advance your expertise in building diverse applications.
0 notes