#formatMsgNoLookups
Explore tagged Tumblr posts
Text
CVE-2021-44228 - Remediation in ElasticSearch
CVE-2021-44228 – Remediation in ElasticSearch
Problem Log4j’s JNDI support has not restricted what names could be resolved. Some protocols are unsafe or can allow remote code execution. Log4j now limits the protocols by default to only java, ldap, and ldaps and limits the ldap protocols to only accessing Java primitive objects by default served on the local host.[4] The challenge is that you have an ElasticSearch Cluster that needs to be…

View On WordPress
#cluster#CVE-2021-44228#elasticsearch#elasticsearch cluster#formatMsgNoLookups#java#jvm#linux#log4j#options#rce#remediation#remote code execution#ubuntu#vulnerability
2 notes
·
View notes
Text
Important information for everyone who plays Minecraft (Java Edition) multiplayer:
There is a very serious exploit that has recently been found in Minecraft (as of Dec 9 2021) that affects nearly every version of the game, both modded and vanilla.
You should avoid playing on public Minecraft servers until this vulnerability is patched on the respective Minecraft version you play on. Mojang has not yet addressed this at time of posting, it is unknown if they will retroactively patch older MC versions or not. (I suspect they will, but that cannot be guaranteed yet.)
The exploit in question allows for RCE by means of sending a malicious chat message. Yes, you read that right- a chat message. This means that a malicious actor could steal your passwords/session tokens from ram, install viruses etc on your computer. It's real bad.
Both Clients and Servers alike are affected by this.
Fortunately, modern versions of minecraft (since 1.16 - 1.18) are spared the worst effects of this exploit from what I know. There is still a chance that malicious actors could lag your game/servers on these versions, but for the most part playing on these versions should be OK. [EDIT: Disregard this whole paragraph! It's wrong!!! Your client/server are only safe if you receive a software patch to update this, and only on versions 1.17+ at that! AND only if both the client and server it's connected to have both received this patch!]
This exploit is known to exploit all versions of Minecraft 1.12.2 up to Minecraft 1.15.2 [EDIT: actually up to 1.18], regardless of vanilla/modded status, on both the server and client. If you play on these minecraft versions, ABSOLUTELY AVOID PLAYING ON ANY PUBLIC SERVERS, as your computer and personal information could be at risk. It is possible that older versions of Minecraft could be affected as well, essentially any version of minecraft which uses Java 8 could potentially be affected. [EDIT: There have been reports of this exploit affecting version 1.7, 1.8, etc. The java version is irrelevant.]
A band-aid fix you can apply is to add the following startup flags to Minecraft when launching the game:
-Dlog4j2.formatMsgNoLookups=true
But I wouldn't recommend relying on this, as the server you connect to could still be vulnerable itself.
Again, I recommend not playing multiplayer at all until mojang delivers some kind of patch to all clients, even then be wary about servers on older versions (1.16.5 and older).
I will update this post as more information becomes available. Stay safe, everyone.
EDIT 1 (6:26 pm): The jvm flag workaround only applies to Minecraft 1.17 and later. This contradicts things I've seen reading the papermc discord server, but it comes from a reliable source (the fabric modloader developers).
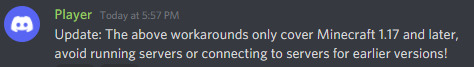
[image ID: Discord message that reads: "Update: The above workarounds only cover Minecraft 1.17 and later, avoid running servers or connecting to servers for earlier versions!" end ID]
It is possible that some misinformation is being spread on this, perhaps to curb the amount of people using this exploit via obfuscation. I don't want to give the impression that you could be safe when I'm not sure, so for now don't even try to play on any server below Minecraft 1.17 at all (or connect to any server using a minecraft client below version 1.17).
EDIT 2 (7:00 pm): I am seeing a lot of people saying that the JVM flag workaround doesn't help at all, or that it only helps for minecraft versions 1.17+. For the time being, just avoid playing minecraft multiplayer entirely, unless you are certain that both the client you are using and server you are playing on has patched this issue. THE JAVA VERSION YOU USE DOES NOT MATTER!!! I'VE CROSSED OUT THE INFORMATION IN THE INITIAL POST THAT IS NOW KNOWN TO BE INCORRECT. I apologize for spreading information before I knew more.
As far as I am aware, if you are playing minecraft 1.17+, there is a patch available to the fabric modloader that fixes this exploit. The latest version of the fabric modloader (0.12.9) patches the exploit on both the client and server end (only for versions 1.17+). Again, you have to be certain that the server you are playing on is patched to be reasonably sure of anything- don't connect/play otherwise. Paper 1.17.1 build #398, and Paper 1.18 build #64 should patch this vulnerability as well, but there is still a lot of information coming out very quickly so nothing is certain at the moment.
EDIT 3 (8:10 pm): Mojang has pushed a patch out to all vanilla clients, versions 1.12.2 and up. Close your game, open the launcher & start the game again to receive the patch from the launcher (assuming you are using the launcher provided by Mojang/Microsoft!).
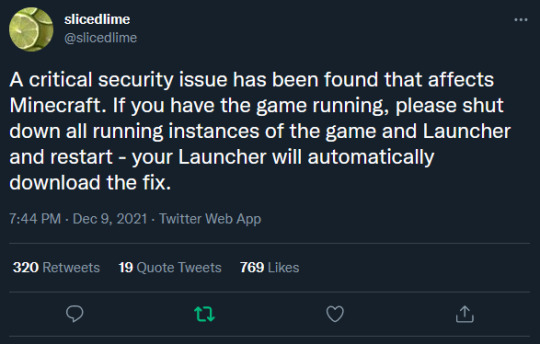
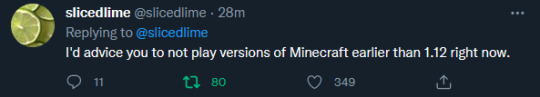
[Image ID: Tweets from @\slicedlime on twitter. The first tweet reads: "A critical security issue has been found that affects Minecraft. If you have the game running, please shut down all running instances of the game and Launcher and restart - your Launcher will automatically download the fix." The second tweet reads: "I'd advice you to not play versions of Minecraft earlier than 1.12 right now." end ID]
Although the vanilla game may be patched for 1.12+, I'd still recommend against considering it "Safe" to join any multiplayer servers just yet. If you use any sort of mods, especially in a heavily modded environment, your client still may not be safe- there's no guarantee that 3rd party minecraft launchers will automatically patch the game for you, for example. Not to mention that any mods/plugins you use may, themselves, be vulnerable to the exploit independent of the base game!
However, that being said, if you play on a completely vanilla client, on a completely vanilla server (such as realms), and you've restarted each of them & ensured they're properly updated, you should be safe. But if you use any mods or plugins, or play on a server that uses any mods or plugins, it may not be safe. Update. Update. Update!!!
And, as stated by slicedlime, versions below 1.12 are completely vulnerable. Do not play these versions in multiplayer at all.
EDIT 4 (8:45 pm): not to be outdone, slicedlime has clarified that the patched vanilla .jars will only fix the exploit in Minecraft versions 1.17+. Anything older than Minecraft 1.17 should still be considered vulnerable.
EDIT 5 (10:20 AM, Dec 10th): I slept for a little bit, seems like Mojang have been taking this very seriously which is good to see. For one thing: they just released Minecraft 1.18.1, which patches this exploit on client & server alike. They've published a blog post explaining how to patch your clients & servers to alleviate this issue: (x).
The only major version that currently has no proper fix available (server-side) is Minecraft 1.8.x and Minecraft 1.9.x (the version with the old pvp, and the update immediately following that one). There are some fixes available for this version, but for now, avoid any server that runs on Minecraft 1.8. That version is so old, it's bound to have other security vulnerabilities as well. (Hypixel is exempt from this, they've implemented their own mitigations to this issue independently according to this forum post: (x). Other pvp/minigames servers running 1.8, you will have to check with the server admins/forums/etc.).
Instructions for ensuring your client & server are secured from this exploit are detailed below;
Launchers:
First-party launcher(s):
Microsoft's Launcher (All versions): Simply close any instances of the game that are running, close the minecraft launcher if it's open, and re-open the launcher.
Mojang's launcher (All versions) (the one that also has Minecraft Dungeons, that keeps yelling at you to install the newer launcher because microsoft said so): Same as above, as this launcher is still officially supported by mojang. (This is the launcher I use, so I can personally confirm this)
Older Minecraft launchers: These will probably still work, but you should probably just update your launcher- AFAIK, only the "Microsoft launcher" and "Mojang launcher" have support for Microsoft accounts. (Come next year or so, you won't be able to launch the game if you have not migrated your account to a Microsoft account, so using an older launcher that does not have support for these kind of accounts is problematic).
Optifine: If you use optifine at all, please keep scrolling for instructions on how to ensure your optifine installation is safe, regardless of the launcher you use or any other mods.
Third-party launchers:
Optifine: If you use optifine at all, please keep scrolling for instructions on how to ensure your optifine installation is safe, regardless of the launcher you use or any other mods.
MultiMC (all affected versions): I don't have a lot of experience with it but according to this github issue (x), MultiMC has patched this for all clients using any modpacks. Make sure you have updated to the latest version of MultiMC available (0.6.14 at time of writing) to ensure the fix is applied properly. Just close the launcher and re-open it.
Curseforge Launcher: I have no idea. I don't use this and it doesn't seem to be open-source.
ATLauncher: I don't know and can't be bothered to figure out, but this launcher does at least seem to be maintained unlike the next one on the list. Keep your launcher up to date and read any news about this, consider switching to MultiMC or just the vanilla launcher if you're uncertain.
Technic Launcher: I don't know much about tekkit or the technic launcher, I just remember this being one of the only non-mojang launchers I've used before. It appears this launcher has not been updated since 2017. Do not launch your game using Technic launcher, you may not be safe from this exploit. If you're just playing modpacks in singleplayer, you should be OK, though. Sidenote: This launcher also doesn't have support for Microsoft accounts, which will make it unusable in a multiplayer setting anyway (unless you run offline mode, which is just asking for trouble). Use MultiMC or some other launcher.
Lunar Client: I installed lunar client just to write this post. I hope you're happy. Their website is so unclear about so many important things that I wasn't even sure if lunar client operated as its own launcher or not, but after installing it, it appears it does. Anyhow, the launcher seems to grab the .jar files from Mojang directly- however, I have no idea if these will be retroactively applied to existing lunar client installations. Someone who uses lunar client, please let me know. I also don't know if they are patching optifine in such a way that it'll automatically apply the patch to Minecraft that fixes this exploit. I've read in some discord servers that lunar client apparently updated to fix this exploit, but I can't find anything on their website or any sort of changelogs to corroborate this. All in all this just made me dislike lunar client even more than I already did. I guess if you really need to use lunar client, it seems to be actively maintained, so it's probably safe. maybe. Maybe? I don't know. Someone who knows stuff about lunar client, please message me if you know more. I am a minecraft boomer and I don't know how these fancy one-click install clients work and I don't want to. I don't trust third party clients that aren't open source to handle my minecraft/microsoft login credentials!
Any other launcher: This is the part where I say "I don't know" again. I don't have much experience with modded minecraft, so I'm not even sure what launcher(s) people use for big modpacks and the like. Rule of thumb, if it hasn't received an update in years, consider it unsafe out of caution. Please let me know if I should add info on any major launchers that I missed here, and I can update this post.
Client (Optifine):
I don't use Optifine anymore (I use Sodium + Starlight + other client-side fabric mods), but from what I know of when I did use Optifine: Optifine's installer will find the Minecraft .jar for the version of Minecraft you're installing optifine for. It then applies the Optifine patches on top of this vanilla .jar file, and saves the modified .jar as its own file, separate from the vanilla game. As such,
If you use optifine at all, you NEED to launch the vanilla game again for the respective version of optifine you want to play on, so that you receive the patched vanilla .jar files from Mojang. (Follow the instructions listed above in the "launchers" section). After this, you need to run the appropriate (latest!) optifine installer for your minecraft version of choice. This will apply the optifine patches on top of Mojang's patched .jar file, and everything should (hopefully) work after this. Then, if you use optifine as part of a modpack, you need to move the newly-patched optifine .jar file into your mods folder (for forge) or select the newly patched optifine .jar from within the launcher (playing w/o other mods, or other mod loaders).
Client (Modded/Modpacks):
This will depend a bit on the mods you're using, how they modify the game, which modloader they make use of, as well as which launcher you use to launch the game. I'll cover the main ones that I know about.
Fabric Modloader: Fabric is the best modloader (extremely biased). It's also completely independent of the Forge ecosystem of mods, so it's not used as much, particularly in larger modpacks (save for All of Fabric, which, you guessed it, uses fabric). But I highly recommend it if you're someone who primarily plays vanilla or vanilla-lite type of minecraft. Anyway, Fabric supports Minecraft versions from 1.14 onward. To quote one of the main developers, "When using Fabric on the client, restarting the Minecraft launcher will be enough to automatically fix the security issue for all Minecraft versions". I also recommend updating your fabric loader version to version 0.12.10 or later (this is the latest at time of writing), as this release of fabric patches the exploit. If you use a third-party launcher, please see the "launchers" section for information on your specific launcher, but as long as you're using fabric loader 0.12.10 or later, you should be safe.
Forge Modloader: The big one. Nearly every big modpack you've ever heard of relies on the Forge modloader. As of time of writing, you will need to update your forge installation to the latest version of Forge for the respective Minecraft version you play to be safe from this exploit. So far, at time of writing, Forge has provided updates to every major version from 1.12.2 onwards to patch this exploit. Unsure of when/if they will provide patches for previous versions (1.7.10 anybody?). If you are using the latest release of Forge for any minecraft version 1.12+, you should be safe from this exploit. If you use a third-party launcher, please see the "launchers" section for information on your specific launcher, but so long as you're using the latest available version of Forge for your minecraft version on 1.12 onwards, you should be safe.
Other modloaders: do these even exist idk lol. I guess there's Rift for 1.13, but I sincerely doubt anyone is still playing on 1.13... right? right...? Message me if there's some noteworthy modloader aside from the big 2 out there right now, but I think these are the only ones worth noting for client-side mods/modpacks. Correct me if I'm wrong.
Servers (Vanilla):
Please follow the instructions in Mojang's blog post: (x). They explain it better than I could.
Realms:
Realms are always automatically updated to the latest Minecraft version. As the latest vanilla minecraft version is 1.18.1 where this is patched, you should have nothing to worry about.
Servers (Craftbukkit/Spigot/Paper/etc):
Craftbukkit/Spigot: Don't use craftbukkit in 2021. Use spigot or Paper instead. Spigot has released patched .jar files for every Spigot version since 1.8.8 onwards in response to this exploit. Please follow the instructions from Spigot's forum post on this if you use Bukkit/Spigot: (x). However, I would not recommend using these Spigot releases for any version older than ~1.15+ or so, because older versions have known vulnerabilities aside from this one, and those likely did not get patched- you'll need to use alternative methods to correctly patch your older servers, or update your fork of choice to the latest release available (i don't know of any prominent public forks of spigot supporting old mc versions, let me know if there's any I should mention). Also, consider using Paper.
Paper/Purpur/Tuinity: Tuinity merged with the Paper project recently, if you're using modern MC versions, please switch from Tuinity to Paper as it has all the features from Tuinity baked in already. Purpur, I'm not sure about, but they've probably released a patch for this exploit. For Paper servers, the Paper devs have released patches for every major version from Minecraft 1.16.5 onwards. If you are using Paper for an older Minecraft version, a moderator in the Paper community has graciously provided files you can drop into your server folder to patch this exploit (currently in the pinned comments in the PaperMC discord, in the #paper-help channel). File to download, by Minecraft version: For 1.10: (x) For 1.11: (x) For 1.12: (x) For 1.13: (x) For 1.14: (x) For 1.15: (x) After downloading the file for your respective Minecraft version, place it in the main directory (where your paper.jar is) and add the following jvm flag to your startup script: -Dlog4j.configurationFile=log4j2.xml Make sure to put this flag BEFORE the -jar part of the startup script. If your server provider does not allow you to modify your java startup flags, you'll have to submit a ticket to them requesting they change your server's startup flags to include this flag. Although, it is possible that certain server providers may automatically implement their own patches for servers (this sounds kind of nightmarish to implement depending on certain things but hey what do I know). If you don't know what java flags are, and you're running a minecraft server, please learn. Consider reading this post by one of the main developers for the Paper project: (x).
Cauldron: Do people still use this? It was last updated for Minecraft 1.7.10 ... This probably isn't safe to use unless you whitelist your server to trusted friends only.
hMod: You are still living in 2010, living the high of beta Minecraft. You probably don't care how many viruses your computer gets.
Other Bukkit/Spigot/Paper forks: I'm not sure of any prominent ones aside from those I listed. Check the latest releases to see if they have a fix for this exploit. If you're using the latest Minecraft version (1.18.1 at time of writing), it's already patched in the vanilla game though.
Servers (Fabric):
For versions 1.14 - 1.18, you need to update your fabric version to 0.12.10 or later to patch this exploit. For 1.18.1 and later, this is already patched in vanilla. If there's fabric versions for older versions than 1.14, they're not supported afaik (fabric was originally released for 1.14).
Servers (Forge):
This may depend on the kind of modpack you're using, but I assume that if you are using the latest Forge version for 1.12 onwards, you should be OK.
Servers (Sponge):
Sponge Vanilla: I can't find any information on whether this exploit happens on Sponge, but I assume it probably does. Wait for an update.
Sponge Forge: Read above section about forge.
"What about X modpack / server / client?":
Modpacks: RLcraft: Uses forge 1.12.2. Update forge. Pixelmon Modpack: Uses forge 1.12.2. Update forge. Hexxit Updated: Uses forge 1.12.2. Update forge. Skyfactory 4: Uses forge 1.12.2. Update forge. Enigmatica 6: Uses forge 1.16.5. Update forge. Tekkit: Uses old forge versions. Unsafe for multiplayer. Other forge modpacks: Update forge. If it's not on Minecraft 1.12.2 or later, it's unsafe for multiplayer. All of Fabric: Uses fabric. Update fabric. Fabulously optimized: Uses fabric. Update fabric.
Servers: Hypixel: Should be safe if your client is. Cubecraft: Should be safe if your client is. Minehut: I don't understand what minehut is. Is it its own server? Is it a server host?? Once again I feel like a minecraft boomer. I'm not sure. Massivecraft: Unsure. EmpireMinecraft: Probably ok, they use Paper and one of the lead developers is also a lead developer on the Paper project.
Clients: Lunar Client: I don't know. Update it anyways. Consider just joining your fav servers from vanilla (& vanilla launcher) for the time being. Badlion Client: I don't know. Their website isn't working for me. People seem to prefer lunar client these days, anyway. Nodus: You are still living in 2010. Please look outside. Also, don't use hacked clients unless you're prepared to get hacked yourself.
Anything else:
This only affects Minecraft: Java edition.
I think I covered every major client/launcher/server software for Minecraft??? Probably?! Other than hacked clients or cracked minecraft launchers. Assume these will always give you a million viruses when you download them. Just buy the game or borrow someone else's account, it's fairly cheap.
If I've missed any major client/servers, please let me know. I may publish a more formal blog post on the update/mitigation process, perhaps in a github gist or something, for people to reference without having to go to my tumblr blog. For now, though, I hope this helped you, and feel free to ask me any questions! (My tumblr inbox is always open.)
6K notes
·
View notes
Text
Java Log4j2 sux <=2.14.1 = JNDI Log4j vulnerability
Apache Log4j2 <=2.14.1 JNDI features used in the configuration, log messages, and parameters do not protect against attacker-controlled LDAP and other JNDI-related endpoints. An attacker who can control log messages or log message parameters can execute arbitrary code loaded from LDAP servers
when message lookup substitution is enabled.
From log4j 2.15.0, this behavior has been disabled by default. In previous releases (>2.10) this behavior can be mitigated by setting system property "log4j2.formatMsgNoLookups" to “true” or by removing the JndiLookup class from the classpath (example: zip -q -d log4j-core-*.jar org/apache/logging/log4j/core/lookup/JndiLookup.class). Java 8u121 (see https://www.oracle.com/java/technologies/javase/8u121-relnotes.html) protects against remote code execution by defaulting "com.sun.jndi.rmi.object.trustURLCodebase" and "com.sun.jndi.cosnaming.object.trustURLCodebase" to "false".
from https://nvd.nist.gov/vuln/detail/CVE-2021-44228

Wowow
Credit: This issue was discovered by Chen Zhaojun of Alibaba Cloud Security Team.
via https://logging.apache.org/log4j/2.x/security.html
3 notes
·
View notes
Text
What is Minecraft Hosting and Why is it more susceptible to Log4J Error?
I’ve recognized before that the vulnerability of Log4J in Minecraft could be a far more serious issue if you host your own Minecraft VPS server. however what precisely will we mean by Minecraft hosting? Is it completely different from enjoying online? And why is it more critical? To clarify things, I’ll reassess some fast definitions. ensure to follow and see if they apply to you and if you wish to try and do something to stay your laptop and your Minecrafting safe and secure.
a way to Fix Log4J on Your Minecraft Server?
Steps For Minecraft 1.7 – 1.11.2
First, you wish to transfer this XML file from Mojang and place it in your server’s operating directory (where the sport files are).
Next, insert the subsequent command into the Minecraft startup command line:
Copy
-Dlog4j.configurationFile=log4j2_17-111.xml]
Steps For Minecraft 1.12 – 1.16.5
transfer this alternative XML file from Mojang and place it in your server’s working directory (where the game files are).
Next, insert the subsequent command into the Minecraft startup command line:
-Dlog4j.configurationFile=log4j2_112-116.xml
Steps For Minecraft 1.17
No have to be compelled to transfer something — merely insert the following command into the startup command file:
-Dlog4j2.formatMsgNoLookups=true
Steps For Minecraft 1.18
Upgrade to 1.18.1 or enter the following code into the startup command line:
-Dlog4j2.formatMsgNoLookups=true
https://cloudzy.com/minecraft-log4j-exploit/
0 notes
Text
Log4j vulnerability(CVE-2021-44228)
What is the issue?
The bug, identified as CVE-2021-44228, allows an attacker to execute arbitrary code on any system that uses the Log4j library to write out log messages.
How to protect the applications? *The first thing to do is detect whether Log4j is present in your applications. It’s also important to note that not all applications will be vulnerable to this exploit.
* Anyone using a Java version higher than 6u212, 7u202, 8u192, or 11.0.2 should be safe, because of the added protection for JNDI (Java Naming and Directory Interface) remote class loading in those versions.
* Users of Log4j versions higher than 2.10 should mitigate the issue by setting the system property formatMsgNoLookups to true, setting the JVM parameter -Dlog4j2.formatMsgNoLookups=true, or by removing the JndiLookup class from the classpath.
* The issue has been fixed in the Log4j version 2.16, released on December 13., 2021.
#java#javascript#javadevelopers#software#Software Developers#Softwarecompany#technology#it consulting services#web developing company#app development
0 notes
Text
広く使われているJavaライブラリ「Log4j」に深刻な脆弱性。速やかに確認と対策を
from https://www.publickey1.jp/blog/21/javalog4j.html
オープンソースのロギングライブラリとしてさまざまなJavaアプリケーションに使われている「Apache Log4j」に、任意のリモートコードが実行できてしまう脆弱性が発見されました。
これが悪用されると、第三者が勝手にサーバを操作して悪意のあるソフトウェアを組み込んだり、悪意のある攻撃を行う際の踏み台にされるなどのさまざまな攻撃が行われます。
すでに脆弱性の存在は広く知れ渡っているため、脆弱性のあるLog4jを使っているシステムはいつでも攻撃を受ける可能性があるのです。
この脆弱性は広範囲な影響が予想されており、多くの専門家が非常に深刻な状況として捉えています。
できるだけ速やかに、JavaアプリケーションにおけるLog4jの利用の確認と対策が必要です。
Javaアプリケーションに明示的にLog4jを組み込んでいない場合も、例えばStrutsやRedis、ElasticSearchなどを始めとするさまざまなフレームワークやコンポーネントがLog4jを採用しているため、慎重な確認が求められます。
また、この脆弱性を突いたさまざまな攻撃が実行されている可能性があります。自社でJavaアプリケーションを運用していなくとも、自社のネットワークやサーバに対して外部から攻撃が行われていないかどうか、しばらくはいつもより細かく見ていた方がいいかもしれません。
バージョンアップなどの対策方法
この脆弱性について、日本語での信頼性の高い情報源の1つがJPCERT/CCの下記のページでしょう。
これによると、脆弱性のあるLog4jのバージョンは、Apache Log4j 2.15.0より前の2系のバージョン。Apache Log4j 1系のバージョンについてはこの脆弱性の影響を受けないと説明されています。
開発元であるApache Foundationの公式ページに掲載された本件の脆弱性情報のページ「Log4j – Apache Log4j Security Vulnerabilities」では、Log4j 2.15.0で脆弱性が修���されたことが発表されています。
もっとも適切な対応として、速やかにこの最新バージョンへのバージョンアップを行うことが挙げられます。
バージョンアップがすぐに行えない場合、以下の方法が対応策として示されています。
Log4jバージョン2.10およびそれ以降
Log4jを実行するJava仮想マシンを起動時に「log4j2.formatMsgNoLookups」というJVMフラグオプションを指定する
環境変数「LOG4J_FORMAT_MSG_NO_LOOKUPS」を「true」に設定する
Log4jバージョン2.10より前
JndiLookupクラスをクラスパスから削除する
ファイアウォールを用いた対策
すぐにバージョンアップすることが難しい場合、暫定的な対策の選択肢として、ファイアウォールを用いてこの攻撃に使われる通信のパターンを遮断する方法があります。
AWSはこの脆弱性についてまとめたページ「Apache Log4j2 Security Bulletin (CVE-2021-44228)」で、AWS WAFに対応するルールを追加したことを明らかにしています。
DevelopersIOでこのWAFの動作が検証されています。
参考:Log4jの脆弱性対策としてAWS WAFのマネージドルールに「Log4JRCE」が追加されました | DevelopersIO
Google CloudでもWAFに対応ルールが追加されたことが発表されました。
Google Cloudのコミュニティブログに解説記事が書かれています。
参考:Cloud Armor の WAF ルールで Apache Log4j の脆弱性対策をする | by Seiji Ariga | google-cloud-jp | Dec, 2021 | Medium
ファイアウォールによる対策で時間を作りつつ、最終的にはソフトウェアのバージョンアップによる対応を行うのが望ましいでしょう。
https://www.publickey1.jp/fbico_pblky.png
0 notes
Note
The Minecraft bug is remote code execution; it lets people run whatever program they want on your computer just by typing in chat. I also heard you can fix it by adding the following, with spaces around it and without the brackets around the dot, to your launcher command options just before the "-jar" (though I won't be relying on it myself): -Dlog4j2[.]formatMsgNoLookups=true
damn
guess i'll be showing off my upgraded-once-again minecraft skin some other way
0 notes