#ghostminic
Text



ID: a set of 4 images in 2 pairs. each has one image of the listed star vs the forces of evil character with a white outline in front of their corresponding flags, and a second image which is a blank flag splice. END ID
Marco Diaz from Star vs. The Forces of Evil is an autistic genderfrect, masc+neu-presenting, mascinique, transmasc femme, GNC man/woman evenic, apolladox, nerdimasc, casunfem, hoodieboy, biadarmam, panmodal, abdulien, coffinwoodaesic, transfemmasc ottewink, ghostminic, horrostalnoia, universcover, venturegender, advendthesia, hoodiecomfic, boygirl gendersatyret, transfloral, lexeloverboyic, princessandyica, mindyne bellussexual, miagastic violilian with OCD, and generalized anxiety! E uses he/him, hie/hiem, they/them, ‘e/,‘im, rock/rocks, py/pyx, ca/catta, 🪐/🪐s, 🎧/🎧s and, occasionally, she/her pronouns!
As Princess Turdina, she is a magicaboycess, auroracorifem, apanprincesse, princesspresentic, bowsteless, princessthesia, starlullaphrasia, magicuic, femme pan gaybian, veldarcetian, sylphigast, ruby transfemmasc, butch-femme boyfemme, fem+neu+xen-presenting, bigender, gendersylphen, flamunmasc, findyne, flamboricesse, rosgirlera, gatomiric, boygirlroyalic, advendthesia, girlboy genderselkier femmerosboy who uses she/her, shy/hyr, star/stars, lyr/lyra, pearl/pearls, su/sucre, tapi/pioca, frill/frills, 💫/💫s, 💥/💥s, 🫧/🫧s and, occasionally, he/him pronouns!
Both of them are genderfaenan and genderlotul as well!
For 🌖☄️ anon!
#🌖☄️ anon#many flags#genderfrect#mascinique#apolladox#nerdimasc#casunfem#hoodieboy#biadarmam#panmodal#abdulien#coffinwoodaesic#ghostminic#horrostalnoia#universcover#venturegender#advendthesia#hoodiecomfic#gendersatyret#transfloral#lexeloverboyic#princessandyica#mindyne#miagastic#violilian#mogai#mogai headcanon
7 notes
·
View notes
Photo




DM-GhostMine
2 notes
·
View notes
Photo

The Goldfield Ghostmine is a nice place to be at sunset. We walked over from our campsite to look around and have dinner on the porch. The atmosphere was better than the food. There are lots of photo opportunities and touristy things to see and do here. (at Goldfield Ghost Town) https://www.instagram.com/p/Cmz8WbXumE8/?igshid=NGJjMDIxMWI=
0 notes
Photo

Happy 8th Anniversary to my Sweetie, @goldminerlarry! 💗💗💗 I love you Babe! #weddinganniversary #countrywedding #pinkcowgirlboots #horsebackwedding #sumpteroregon #ghostmine #divineconnection #sumptertrain #memories https://www.instagram.com/p/CEBMkrwg4lo/?igshid=18mfme1f3m4ng
#weddinganniversary#countrywedding#pinkcowgirlboots#horsebackwedding#sumpteroregon#ghostmine#divineconnection#sumptertrain#memories
0 notes
Text
🌼ghostminic!🌼
ghostminic-
a gender based off of forests, fields, farming, honey, campfires, a mix of masculinity and neutrality, the overall vibe of minecraft (in a chill way, not a chaotic way), oversized sweaters, sheeps, and the vibe of being a ghost; it’s also related to cryptids!
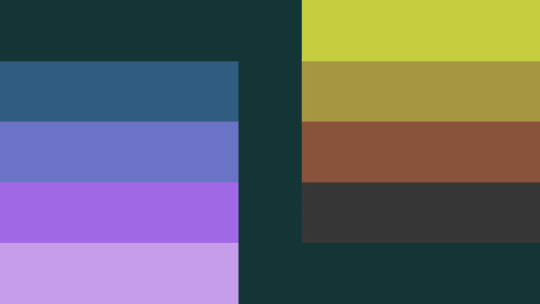
[Image ID: A flag with two columns of five equally-sized horizontal stripes separated by a deep evergreen vertical stripe. From top to bottom in the left column the colors are deep evergreen, deep turquoise, mid blue, purple, and lavender. In the same direction on the right column the colors are chartreuse, yellow-brown, brown, deep grey, and deep evergreen. End ID.]
term and flag by me, requested by anon :3
43 notes
·
View notes
Photo

Dark descent Model: @lilith_mara #outdooradventure #adventureshoot #blackfriday #abandonedplaces #abandoned #darkangel #modelmuse #darkandlovely #darkbeauty #abandonedmine #coloradoterritory #ghostmine https://www.instagram.com/p/B5gaGOdly9-/?igshid=6cisxynb20nm
#outdooradventure#adventureshoot#blackfriday#abandonedplaces#abandoned#darkangel#modelmuse#darkandlovely#darkbeauty#abandonedmine#coloradoterritory#ghostmine
0 notes
Note
Bro I’m at the point of wanting to create drama out of nothing for some Ghostminic Cassper-Lewin content😔

out of nowhere? ain't he hit somebody w his bike the other day???
4 notes
·
View notes
Text
HiddenMiner: Mines Monero on Android Devices While Protecting Itself From Discovery and Removal
Security firm Trend Micro has discovered a new strain of Android malware, calling it “HiddenMiner” because of the advanced techniques it employs to protect itself from discovery and removal. Like most cryptocurrency-mining software, HiddenMiner uses a device’s computing power to mine Monero. But according to Trend Micro, because there is no switch, controller, or optimizer in HiddenMiner’s code it will continuously mine Monero until the device’s resources are exhausted.
“Given HiddenMiner’s nature, it could cause the affected device to overheat and potentially fail,” the company said.
This strain is not the first cryptocurrency-mining malware to put smartphone hardware at risk: last year the “Loapi” Android malware worked a phone so hard that in less than 48-hours its battery swelled up, bursting open the device’s back cover. Trend Micro said the two pieces of malware share similarities, pointing out that both HiddenMiner and Loapi lock a phone’s screen after users attempt to revoke device administration permissions.
Further, researchers have identified the Monero mining pools and wallets associated with the malware, and discovered that one of the pool operators withdrew 26 XMR — amounting to almost $5,000 — from one of the wallets. This, the firm said, indicates a “rather active” campaign of using infected devices to mine cryptocurrency.
To protect devices, Trend Micro advises users of Android devices to practice “mobile security hygiene.” This means only downloading from official app marketplaces, regularly updating a device’s OS, and being prudent with the permissions granted to applications. So far, HiddenMiner is affecting Android users in India and China, but Trend Micro says it “won’t be a surprise” if it spreads to other countries.
HiddenMiner Techniques
HiddenMiner poses as a legitimate Google Play update app, and forces users to activate it as a device administrator. The app will continue to pop up until victims click the Activate button. Once granted permission, HiddenMiner will start mining Monero in the background.
It also attempts to hide itself on infected devices by emptying the app label and using a transparent icon after installation. This allows the malware to hide and automatically run with device administrator permission until the next device boot. According to Trend Micro, HiddenMiner also has anti-emulator capabilities built-in to bypass detection and automated analysis.
It’s also hard to get rid of: users can’t uninstall an active system admin package until device administrator privileges are removed first. But HiddenMiner locks the device’s screen when a user wants to deactivate its device administrator privileges, taking advantage of a bug found in Android operating systems before Android 7.0 Nougat.
GhostMiner and Jenkins Miner
Just last week, researchers at Minerva Labs uncovered another Monero mining malware strain, which the firm dubbed GhostMiner. GhostMiner uses “fileless” malware delivery techniques to land on systems, and will fight to remove other mining malware it so it can mine Monero itself.
At the time of publication, GhostMiner had not accumulated hefty profits, but warranted attention because of its unique self-preservation methods. Monetarily, this is nothing compared to operations like the Jenkins miner, which earlier this year made its developers over $3 million in Monero.
The post HiddenMiner: Mines Monero on Android Devices While Protecting Itself From Discovery and Removal appeared first on NewsBTC.
from Cryptocracken WP https://ift.tt/2GniC73
via IFTTT
0 notes
Text


ID: a set of two images. the first is of cal bowman from sex education with a white outline in front of a flag splice of rots listed identities. the second is a blank flag splice. END ID
Cal Bowman from Sex Education is a nonbinary, queerfuckoff, genderhyd, bluecolauric, xiaminic, fuchsean, casubutch, transmascneuagen, raneusol, vicicanis, shroomsylvica, sagxexygender, zombimutt, quoesygender, celescozdragic, medievadragonic, mascuvoicecoutic, teengraffriendic, limfortcreepic, rebelrevelic, muttfinalperson, obumbrofluid, abanotraskatic, unrealunentity, fleuriskatic, wolfdogmasenoi, sleepyfelic, pintathundric, invigloweystepdog, traumascminus, invinsectsky, chaoneualign, neurainpetric, genderdezerto, urbakour, polyneutral, distortherian, desetalux, nyctylviarestic, meandyourmamica, hellnbackica, deadmansongic, weirrorfnafic, fierinottea, honestsongic, natdestrebech, dragoflitigrilic, darkforestcreatic, mascpunk, chillperspesque, morvivgender, notteskatic, graffurbel, bohorclypse, draconine, wolfgender, noctlupus, noctuwolfean, rabwolfgender, wolforestic, darklunaesic, musidrownstimmic, zombisgender, phosdragonial, kittydragoplushic, immodragonic, monscarecaguro, genderplated, genderostex, baggycargoeuphic, putregender, lasurvivoric, tensic, astradracatic, dragonlexic, determigender, apodystomen, sylpinotteic, ghostminic, paracelesneonic, antiherolexic, blackwolfdoggic, phosdragoflamial, parkoutia, genderdragane, draachgender, coffinwoodaesic, crepumothic, immortaldragongender, isoforespirperspesque, indestructilycanic, tapelucidriz, wolforestic, zomdoggender, zomysterestia, guardetrayal, 🛹emojic, ⭐️🎸🎧emojic, yucca jeularene, veldarcbian, sapphillean lesboy ox who experiences tutelary attraction! Cal is a high-content transwolfdog zombiekin wolfdogkin that uses they/them, scale/scales, gold/golds, dir/dirt, grim/grime, aeir/aiers, wy/wyvs, cy/cyr, dra/drac, rot/rots, ze/vaer, claw/claws, lup/lupus, hou/houn, mutt/mutts, scar/scars, rip/rips, mon/mons, bo/bones, wy/wyrm, zomb/zombs, and 🪦/🌘/🎸🎧🛹/🎨/🪶/🐲/🦴/⛧self pronouns! They are autistic, depressed and have voice dysphoria, ADHD, and chronic wrist pain!
For 🌖☄️ anon!
#🌖☄️ anon#many flags#queerfuckoff#genderhyd#bluecolauric#xiaminic#fuchsean#casubutch#transmascneuagen#raneusol#vicicanis#shroomsylvica#sagxexygender#zombimutt#quoesygender#celescozdragic#medievadragonic#mascuvoicecoutic#teengraffriendic#limfortcreepic#rebelrevelic#muttfinalperson#obumbrofluid#abanotraskatic#unrealunentity#fleuriskatic#wolfdogmasenoi#sleepyfelic#mogai#mogai headcanon
3 notes
·
View notes
Text
HiddenMiner: Mines Monero on Android Devices While Protecting Itself From Discovery and Removal
Security firm Trend Micro has discovered a new strain of Android malware, calling it “HiddenMiner” because of the advanced techniques it employs to protect itself from discovery and removal. Like most cryptocurrency-mining software, HiddenMiner uses a device’s computing power to mine Monero. But according to Trend Micro, because there is no switch, controller, or optimizer in HiddenMiner’s code it will continuously mine Monero until the device’s resources are exhausted.
“Given HiddenMiner’s nature, it could cause the affected device to overheat and potentially fail,” the company said.
This strain is not the first cryptocurrency-mining malware to put smartphone hardware at risk: last year the “Loapi” Android malware worked a phone so hard that in less than 48-hours its battery swelled up, bursting open the device’s back cover. Trend Micro said the two pieces of malware share similarities, pointing out that both HiddenMiner and Loapi lock a phone’s screen after users attempt to revoke device administration permissions.
Further, researchers have identified the Monero mining pools and wallets associated with the malware, and discovered that one of the pool operators withdrew 26 XMR — amounting to almost $5,000 — from one of the wallets. This, the firm said, indicates a “rather active” campaign of using infected devices to mine cryptocurrency.
To protect devices, Trend Micro advises users of Android devices to practice “mobile security hygiene.” This means only downloading from official app marketplaces, regularly updating a device’s OS, and being prudent with the permissions granted to applications. So far, HiddenMiner is affecting Android users in India and China, but Trend Micro says it “won’t be a surprise” if it spreads to other countries.
HiddenMiner Techniques
HiddenMiner poses as a legitimate Google Play update app, and forces users to activate it as a device administrator. The app will continue to pop up until victims click the Activate button. Once granted permission, HiddenMiner will start mining Monero in the background.
It also attempts to hide itself on infected devices by emptying the app label and using a transparent icon after installation. This allows the malware to hide and automatically run with device administrator permission until the next device boot. According to Trend Micro, HiddenMiner also has anti-emulator capabilities built-in to bypass detection and automated analysis.
It’s also hard to get rid of: users can’t uninstall an active system admin package until device administrator privileges are removed first. But HiddenMiner locks the device’s screen when a user wants to deactivate its device administrator privileges, taking advantage of a bug found in Android operating systems before Android 7.0 Nougat.
GhostMiner and Jenkins Miner
Just last week, researchers at Minerva Labs uncovered another Monero mining malware strain, which the firm dubbed GhostMiner. GhostMiner uses “fileless” malware delivery techniques to land on systems, and will fight to remove other mining malware it so it can mine Monero itself.
At the time of publication, GhostMiner had not accumulated hefty profits, but warranted attention because of its unique self-preservation methods. Monetarily, this is nothing compared to operations like the Jenkins miner, which earlier this year made its developers over $3 million in Monero.
The post HiddenMiner: Mines Monero on Android Devices While Protecting Itself From Discovery and Removal appeared first on NewsBTC.
from Cryptocracken Tumblr https://ift.tt/2GniC73
via IFTTT
0 notes
Text
HiddenMiner: Mines Monero on Android Devices While Protecting Itself From Discovery and Removal
Security firm Trend Micro has discovered a new strain of Android malware, calling it “HiddenMiner” because of the advanced techniques it employs to protect itself from discovery and removal. Like most cryptocurrency-mining software, HiddenMiner uses a device’s computing power to mine Monero. But according to Trend Micro, because there is no switch, controller, or optimizer in HiddenMiner’s code it will continuously mine Monero until the device’s resources are exhausted.
“Given HiddenMiner’s nature, it could cause the affected device to overheat and potentially fail,” the company said.
This strain is not the first cryptocurrency-mining malware to put smartphone hardware at risk: last year the “Loapi” Android malware worked a phone so hard that in less than 48-hours its battery swelled up, bursting open the device’s back cover. Trend Micro said the two pieces of malware share similarities, pointing out that both HiddenMiner and Loapi lock a phone’s screen after users attempt to revoke device administration permissions.
Further, researchers have identified the Monero mining pools and wallets associated with the malware, and discovered that one of the pool operators withdrew 26 XMR — amounting to almost $5,000 — from one of the wallets. This, the firm said, indicates a “rather active” campaign of using infected devices to mine cryptocurrency.
To protect devices, Trend Micro advises users of Android devices to practice “mobile security hygiene.” This means only downloading from official app marketplaces, regularly updating a device’s OS, and being prudent with the permissions granted to applications. So far, HiddenMiner is affecting Android users in India and China, but Trend Micro says it “won’t be a surprise” if it spreads to other countries.
HiddenMiner Techniques
HiddenMiner poses as a legitimate Google Play update app, and forces users to activate it as a device administrator. The app will continue to pop up until victims click the Activate button. Once granted permission, HiddenMiner will start mining Monero in the background.
It also attempts to hide itself on infected devices by emptying the app label and using a transparent icon after installation. This allows the malware to hide and automatically run with device administrator permission until the next device boot. According to Trend Micro, HiddenMiner also has anti-emulator capabilities built-in to bypass detection and automated analysis.
It’s also hard to get rid of: users can’t uninstall an active system admin package until device administrator privileges are removed first. But HiddenMiner locks the device’s screen when a user wants to deactivate its device administrator privileges, taking advantage of a bug found in Android operating systems before Android 7.0 Nougat.
GhostMiner and Jenkins Miner
Just last week, researchers at Minerva Labs uncovered another Monero mining malware strain, which the firm dubbed GhostMiner. GhostMiner uses “fileless” malware delivery techniques to land on systems, and will fight to remove other mining malware it so it can mine Monero itself.
At the time of publication, GhostMiner had not accumulated hefty profits, but warranted attention because of its unique self-preservation methods. Monetarily, this is nothing compared to operations like the Jenkins miner, which earlier this year made its developers over $3 million in Monero.
The post HiddenMiner: Mines Monero on Android Devices While Protecting Itself From Discovery and Removal appeared first on NewsBTC.
from CryptoCracken SMFeed https://ift.tt/2GniC73
via IFTTT
0 notes
Text
GhostMiner uses fileless technique to mine coins
http://i.securitythinkingcap.com/QMXyvg
0 notes
Photo

#goldfieldghosttown #ghostmine #adventure #supernaturalcowboy Check out Melissa’s post https://www.instagram.com/p/CP0gWhZha9-/?utm_medium=copy_link Reaching back into time with the most amazing person. This weekend time stopped. Watching a sunset in the bed of our truck over the White Tank Mountains, exploring a ghost town at the foot of the Superstition Mountains, eating dinner in a converted church from the 1890s, sitting under a tree and feeling the warm breeze and so much more. (at Goldfield Ghost Town) https://www.instagram.com/p/CP0x1C6HH6f/?utm_medium=tumblr
1 note
·
View note
Text
GhostMiner fileless cryptomining malware has code that kills itself and other strains
GhostMiner fileless cryptomining malware has code that kills itself and other strains
Building a slide deck, pitch, or presentation? Here are the big takeaways: A newly-discovered cryptomining malware strain called GhostMiner is the first known fileless mining malware discovered. It also contains advanced competition-killing functions to eliminate other cryptomining infections. Researchers from Minerva Labs have turned GhostMiner’s own capabilities against it by extracting its…
View On WordPress
0 notes
