#how to prevent from Computer Viruses
Explore tagged Tumblr posts
Text
How to Protect Your Computer from Unauthorized Access?
Today, we live our lives online and on gadgets that are connected to the internet. We use the internet to do research, shop, bank, do assignments, play games, and connect with loved ones through social media. Because of this, our gadgets are filled with a
Continue reading How to Protect Your Computer from Unauthorized Access?
#Hackers#How To Prevent Unauthorized Computer Access#How To Protect Your Computer From Unauthorized Access#How To Save From Hacking#Methods For Preventing Unwanted Access To Your Computer#Protect Your Computer From Viruses
0 notes
Text
oh my god do not click links in emails that tell you to verify your data or your bank account gets locked or click links in messages telling you your safety protocol is ending, like, tomorrow, you will get SCAMMED SO BAD AND YOU WILL LOSE A LOT OF FUCKING MONEY never ever let anyone pressure you into giving away login information especially to your online banking by creating a sense of urgency oh my GOD
some things to look out for
1. spelling mistakes. do you know how many rounds of marketing and sales experts these things go through? if theres a spelling mistake dont click it
2. not using your name. if an email adresses you with "dear customer" or, even worse, a generic "ladies and gentlemen", it is most likely not actually targeted to you
3. verifying or login links. even IF your bank was stupid enough to send these to customers, dont EVER click those. look at me. they can legally argue that youve given your data away and thus they dont have to pay you anything back DONT CLICK THAT FUCKING LINK
4. creating a sense of urgency. do this or we lock your account next week. do this or your ebanking stops working tomorrow. give us all your money in cash or your beloved granddaughter will get HANGED FOR MURDERING BABIES. no serious organisation would ever do something like that over email or sms. ever. hands off.
5. ALWAYS CHECK WHO SENT YOU THE EMAIL. the display name and the email adress can vary a LOT. anyone can check the display name. look at the email adress. does it look weird? call the fucking place it says its from. you will likely hear a very weary sigh.
6. if its in a phonecall, scammers love preventing you from hanging up or talking to other people to have a little bit of a think about whats happening. there should always be a possibility to go hey i wanna think about this ill call back the official number thanks.
7. do not, i repeat, do NOT a) call a phone number flashing on your screen promising to rid your computer of viruses after clicking a dodgy link and b) let them install shit on your computer like. uh. idk. teamviewer.
7.i. TEAM VIEWER LETS PEOPLE USE YOUR COMPUTER HOWEVER THEY WANT AS LONG AS THEYRE CONNECTED. IF YOU DONT KNOW FOR FUCKING SURE YOURE TALKING TO ACTUAL TECH SUPPORT DONT GIVE ANYONE ACCESS TO YOUR COMPUTER.
fun little addendum: did you know a link can just automatically download shit? like. a virus? an app you can't uninstall unless you reset your entire device? dont click links unless youre extremely sure you know where they lead. hover your mouse over it and check the url.
thanks.
#'oh i was so stressed in the moment' thats what theyre counting on PLEASE dont do this you will lose so much money#sometimes money you dont even have#do you know how much overdraft your bank account comes with?#sometimes the answer is 15k fucking euros
17K notes
·
View notes
Text

Horses are among the world’s most elite athletes: When galloping, they can consume twice as much oxygen per kilogram as the fittest humans. All that oxygen supercharges horses’ cells’ energy-producing compartments as they crank out ATP, the chemical needed to power their impressive muscles. But making so much cellular fuel so quickly comes with a catch: the manufacture of pernicious byproduct molecules called reactive oxygen species (ROS), which can wreak havoc in cells.
How horses dealt with this biological trade-off and evolved into premier endurance athletes has long intrigued biologists. Researchers report today in Science that they have uncovered a big part of it, identifying a key mutation that lets horses safely produce so much ATP. The trait helped pave the way for horses to go from dog-size critters millions of years ago to the high-endurance athletes we know today.
The study’s detailed molecular work makes it “exceptional,” says José Calbet, an expert on the cellular responses to exercise at the University of Las Palmas de Gran Canaria who wasn’t involved with the study.
The mutation in question occurs in the gene that encodes a protein called KEAP1, which acts as a biochemical bouncer, binding to a different protein called NRF2 to prevent it from entering the cell’s nucleus, where it would otherwise activate stress-response genes that help blunt cell damage.
But ROS can help NRF2 sneak in by causing KEAP1 to release its bind on the protein, allowing it to enter the nucleus and trigger the cell’s stress-response genes.
Johns Hopkins University ophthalmologist and clinician scientist Elia Duh, a senior author of the new study, didn’t set out to study horses. Initially, Duh was interested in the KEAP1-NRF2 system because its role in activating stress-response genes makes it a tempting target for treating inflammation—and aging-related conditions, such as blinding retinal diseases, irritable bowel syndrome, and neurodegeneration.
Duh wondered whether any insights could be gleaned from studying the evolution of these proteins in different animals. So, he teamed up with Gianni Castiglione, an evolutionary biologist and biochemist at Vanderbilt University. Together, they scanned hundreds of vertebrate genomes looking for notable mutations to the gene for KEAP1.
The team’s genomic work revealed birds had almost completely lost the gene, presumably an adaptation to the extreme demands of flight. When they looked in horses, researchers noticed what initially appeared to be a DNA sequence that encoded an unusually short—and therefore presumably nonfunctional—version of the KEAP1 protein. But when Duh’s and Castiglione’s team grew horse cells in culture, it discovered the protein was very much there and working. “Naturally, I was worried I was doing something wrong,” Castiglione says. “Then one day, a light bulb went off.”
As it turns out, the computer algorithm scientists had used to scan the horse genome had made a mistake. The algorithm had spotted a specific kind of mutation in the part of the KEAP1 gene that changed the messenger RNA from CGA—which codes for the amino acid arginine—to UGA, which is what’s known as a “stop codon.”
Normally, the cellular machinery interprets UGA as a sign to stop translating the RNA into a protein. But instead, the horses’ genetic machinery recodes the stop codon into a different amino acid, cysteine, causing it to ignore that order. This phenomenon, known as a stop codon read-through, is common among viruses but rare in multicellular organisms.
“The identification of this evolutionarily significant UGA recoding event represents a potentially seminal finding, offering a model for uncovering other yet-unidentified cases of stop codon read-through,” says Hozumi Motohashi, a biologist at Tohoku University who has studied KEAP1 and NRF2.
That the replacement is a cysteine is particularly notable, Castiglione says. KEAP1 senses cellular stress through its cysteines, which contain sulfur atoms whose reactions with ROS, induce the chemical changes that cause KEAP1 to let go of NRF2. The mutation the researchers had identified adds another place on KEAP1 for ROS to interact, which makes the protein more sensitive to stress—and lets horse cells respond much faster to the cellular stress of intense exercise. “It does make complete sense [that] by introducing another cysteine, another sulfur, you would have heightened sensitivity,” Castiglione says.
What’s more, this tweaking of KEAP1 is a “[key] genetic component to the puzzle of the evolution of horses,” Duh says. “Once they figured out how to run, they could occupy all kinds of ecological niches,” Castiglione adds.
The finding could also point the way toward new kinds of drugs to treat diseases by targeting the specific parts of the KEAP1 protein that help horses hoof it. “By looking at what evolution has figured out, we know this is a viable strategy,” Castiglione says.
Source
834 notes
·
View notes
Text
How to Burn Your Own CDs - a guide for Windows users
Are you--yes, you!--tired of paying money to stupid shit like spotify for your music? Do you hate the way that the music industry takes almost all the profit that bands make through streaming and leaves them with pennies? Have you ever wanted to fire up that old CD-Radio in the corner of your bedroom, only to be stopped because all you have on CD is Weezer's blue album and a copy of Kidz Bop 16 that you don't remember buying? Well this guide just might be for you!
Materials you'll need:
A computer. Can't do it without this one.
A CD drive. It can be internal or external, but you'll need one either way. You can find them at Office Depot for fairly cheap and I've heard that some Walmarts carry them.
A pack of CD-Rs. CD-Rs, or CD Recordables, come in packs of 20, 50, or 100. A proper 100-pack should cost you no more than $30, so unless there's some special shortage in your area, don't buy from anywhere selling them at a markup. CD blanks are literally 50c a piece.
CD cases. Sold wherever CD-Rs are, but you can also find these at thrift stores pretty easily.
A sharpie or some kind of permanent marker
Software you'll need:
Jdownloader. You can acquire mp3s through Bandcamp if you're dedicated to righteousness, but for everyone else, install jdownloader or some other kind of open-source download program. I will be proceeding as if you have jdownloader available.
Windows media player. This should open automatically when you insert a CD-R into your CD drive.
Fre:ac audio converter. This is only for the occasion that you encounter OPUS or mp4a files that cannot be interpreted by your CD player.
Note: If you're very determined not to download software onto your computer, you can use free youtube downloaders and audio converters, but these are subject to viruses and other issues such as download speed. I will be proceeding as if you have the programs I listed.
The process:
Decide what you want to burn--anything goes, but keep in mind the time limit on your CD-Rs. Most will record 90 minutes or less.
Open jdownloader, switch to the linkgrabber tab, then paste youtube links in any order until you have all the music you want. I'd personally recommend doing it song-by-song instead of a full album stream, because a massive file will require a lot of work to separate back into searchable tracks.
De-select all files except audio on the right-hand side options menu.
Make a folder inside the music folder of your laptop and label it with the name of your mix CD.
In the properties tab of each song on jdownloader, change the destination folder to the folder you've just created.
Hit "start all downloads".
Once finished, open each folder. If everything is an .mp3 or a .wav, skip the next 2 steps.
Open Fre:ac audio converter to convert all audio files that aren't .mp3 or .wav into .mp3 or .wav.
Drop the converted files next to the unconverted files in your folder. If you wish, you can delete the originals to make the folder easier to browse.
Put your blank CD-R into the CD drive. If external, plug in your CD drive first or the tray will refuse to open.
Windows media player will open automatically. On the right-hand side, you will see the tracklist of your CD-R (which should be blank). On the left, you will see the audio that your computer is able to find in the music folder. Put your selected tracks IN ORDER onto the tracklist.
Listen to the beginning and ending of each track to make sure there isn't a significant time gap. This also prevents accidentally burning a youtuber's stupid outro if you missed it before.
When satisfied, hit "start burn".
On an external drive, the CD tray will open upon completion. You can reinsert it to ensure that the burning went smoothly.
Once satisfied, remove the CD from your drive. With your sharpie or permanent marker, write the name of the album on the front, then store safely inside a CD case.
you did it👍
Ask me if you run into any issues.
Legal disclaimer: this guide is purely for educational purposes and I do not admit to or take responsibility for any piracy committed using the instructions given.
Illegal disclaimer: cops suck my dick
491 notes
·
View notes
Text
Also preserved on our archive
By Pandora Dewan
COVID-19 may leave some people with lasting memory problems long after their infection has cleared, new research has found, with the findings particularly pronounced among those who suffered from the earliest variants of the virus.
COVID-19 is known for its respiratory symptoms. But we are increasingly learning that SARS-CoV-2—the virus that causes the infection—can affect our brains too. Brain fog, cognitive deficits, and loss of smell and taste are commonly reported symptoms of the virus and some report these neurological symptoms long after the initial infection has subsided.
Scientists aren't entirely sure why the virus causes these symptoms, although lab-based studies have shown that the virus can disrupt the protective barrier that surrounds our brains and prevents foreign substances, like viruses, from entering. Research has also shown that the virus appears to affect the ability of our brain cells to communicate with each other, producing either too much or too little of key signaling molecules in the brain.
In a new study, published in the journal eClinicalMedicine, researchers from Imperial College London, King's College London and University College London Hospital in the United Kingdom set out to investigate the persistence of these cognitive symptoms even after milder COVID-19 infections.
In the study, 18 consenting unvaccinated volunteers with no prior exposure to SARS-CoV-2 were intentionally infected with the virus and monitored regularly over a 360-day period. Their cognitive function was measured at different points throughout the study and compared to what it had been before they were infected. They were also compared against 16 volunteers who were not infected with the virus.
This type of study is called a human challenge study and offer valuable insights into the onset of diseases and how they develop in a controlled medical environment.
"This is the first and probably will be the only Human Challenge Study to be conducted with Wildtype SarS-CoV-2 in people who were unvaccinated and who had not previously had the virus," the study's lead author Adam Hampshire, a professor of cognitive and computational neuroscience at King's College London and visiting professor at Imperial College London's Department of Brain Sciences, told Newsweek.
He added: "It also is the first study to apply detailed and sensitive assessments of cognitive performance from pre to post infection under controlled conditions. In this respect, the study provides unique insights into the changes that occurred in cognitive and memory function amongst those who had mild COVID-19 illness early in the pandemic."
During the study, the volunteers who were infected showed statistically significant reductions in cognitive and memory functions compared to those who did not receive the virus. These symptoms did not emerge right away but lasted for at least a year after the initial infection. This aligns with previous research from Hampshire's lab that sampled data from over 100,000 adults.
"Our previous research has shown that cognitive effects were the most pronounced for people who were ill with early virus variants, those who had persistent symptoms and those who were hospitalized," Hampshire said.
However, in the recent study, these long-lasting cognitive impacts were even seen in those who experienced milder symptoms (although it is worth noting that this may not be the case with newer variants of the virus).
So, how does the virus cause these cognitive impairments? Well, we still don't know for sure, but Hampshire said that those who had been infected with the virus showed an increase in a protein in the brain that is often associated with a brain injury.
"Future research should examine the biological mechanisms that mediate this relationship, determine how they differ to those observed for other respiratory infections, and explore whether targeted interventions can normalize these memory and executive processes," the researchers write in their study.
References Proust, A., Queval, C. J., Harvey, R., Adams, L., Bennett, M., & Wilkinson, R. J. (2023). Differential effects of SARS-CoV-2 variants on central nervous system cells and blood-brain barrier functions. Journal of neuroinflammation, doi.org/10.1186/s12974-023-02861-3
Trender, W. et al. (2024) Changes in memory and cognition during the SARS-CoV-2 human challenge study. eClinicalMedicine, doi.org/10.1016/j.eclinm.2024.102842
Hampshire, A., Azor, A., Atchison, C., Trender, W., Hellyer, P. J., Giunchiglia, V., Husain, M., Cooke, G. S., Cooper, E., Lound, A., Donnelly, C. A., Chadeau-Hyam, M., Ward, H., & Elliott, P. (2024). Cognition and Memory after Covid-19 in a Large Community Sample. The New England journal of medicine. doi.org/10.1056/NEJMoa2311330
#mask up#covid#pandemic#covid 19#wear a mask#public health#coronavirus#sars cov 2#still coviding#wear a respirator
145 notes
·
View notes
Text
Jade Palace + Social Media
Basically, I thought up of a bunch of silly headcanons about if Po + the Furious Five had social media because I thought it would be funny. Enjoy!
Viper has the most followers. Like, she has millions of followers. She was also the first one to ask Shifu if they could get social media accounts, as she wanted to keep in contact with her family. Shifu kept telling her no, thinking such a thing would be a distraction for them. (Viper, then Monkey and Mantis, went behind his back and got accounts anyways. After Po came along and Shifu found inner peace and became a lot less strict to his students, he allowed them to get social media. They wisely pretended as if they never had it when they made their accounts public.) Viper was originally fine with just commenting on and sharing what her sisters and other family posted, but then she discovered ASMR, and fell absolutely in love with it. She developed a strong attachment to ASMR, and began practicing it, and people love it, thinking her voice and the rattles she makes when she moves are perfect for ASMR. She also gives excellent affirmations.
Monkey and Mantis also downloaded social media before Shifu allowed it. They both have a substantial amount of followers, with Monkey having slightly more than Mantis. Monkey posts selfies/pictures but also spams the group chat with memes. Mantis advertises his acupuncture services and sends extremely cursed memes to their group chat, which Monkey appreciates. Tigress is not so amused. She has threatened to block both of them multiple times in order to not see their constant cursed memes.
Po has the second most followers. He had social media before he became the Dragon Warrior that he used to market his dad’s business, but after he became the Dragon Warrior, naturally his follower account exploded, as did his dad’s business. Po fills his stories and posts with selfies and pictures of Shifu (despite him trying to avoid appearing on social media posts), the Furious Five, and shares all the content that his friends make. Naturally, whenever he posts pictures of him and the Five eating at Mr. Ping’s restaurant, Mr. Ping experiences a boom in business. Po also posts pictures of his food just as much--if not more--than his pictures of his friends and family.
Crane was somewhat hesitant to get social media, and his account was private for quite a while. He eventually made his account public after being peer pressured into it. He’s the least active of Po and the Five online, and Viper and Po (especially the latter) are trying to convince him to post his calligraphy and artwork, considering it to be quite skilled. His self-consciousness has prevented him from doing so thus far.
Tigress has the third most followers. She’s very no-nonsense on social media, and surprisingly, Po managed to talk her into getting it fairly soon after Shifu allowed it. Now, Tigress posts manageable workouts on her accounts for the average person, focusing especially on self-defense skills that women can use. Her popularity online has certainly grown quite well. Po also talked her into doing a couple lives with her followers, keeping everything professional and answering questions relevant to the content she posts. Po keeps trying to talk her into teaching a kung fu class for girls or a self-defense class for women in general. (“Come on! They think you’re awesome! They love you! You’re so hardcore!”) She may be considering it.
Shifu is not terribly technologically literate. He is definitely a boomer who would struggle to figure out how to download something to a flash drive. He also has a habit of taking pictures that are very off-center, or otherwise do not look great (his thumb has covered the camera several times before). He doesn’t have social media, and is constantly asking Po to teach him how to take good pictures (Po takes the best ones) and has accidentally downloaded viruses onto the Jade Palace computers twice. Oogway is chuckling at him from the Spirit Realm.
#kung fu panda#po ping#kung fu panda po#master po#dragon warrior po#master tigress#kung fu panda tigress#furious five#master crane#kung fu panda crane#master viper#kung fu panda viper#kung fu panda monkey#master monkey#kung fu panda mantis#master mantis#shifu#master shifu#master oogway#kung fu panda oogway
60 notes
·
View notes
Text
Daily Lives of Jujutsu High Students
Time set in around 2006-2007.
This story tells the daily lives and youthful troubles of four students from a certain year at Tokyo Jujutsu High.
Various x F. Reader!
Other chapters: 01

02 - Online Chatting Requires Caution
Although the curriculum at Tokyo Jujutsu High is different from other schools, it covers basic subjects such as Japanese, mathematics, science, and social studies to ensure students' comprehensive development. With the rapid development of information technology, the use of computers has also increased. In order to prevent students from becoming too disconnected from the non-sorcerer world, the school has recently added a new subject - Computer Class!
However, only a few students take this class seriously. Most students use computer class time to play games. Unfortunately, this has led to many students downloading pirated games from illegal websites, resulting in a large number of infected computers at the school. It wouldn't be an exaggeration to call the computer room a den of viruses.
"Darn it!" You mutter as you stare at the blue screen of the computer. "This one got infected too!"
"Forget about playing World of Warcraft," Gojo, sitting next to you, says. "I heard there's something popular these days that everyone is playing."
You turn your head and look at Gojo curiously. "What is it?"
"It's a random chat room," Gojo explains. "You can go in and have random video chats with people from other countries."
"Really? Let's give it a try then!"
Without hesitation, Gojo types a string of English letters into the search engine, and the computer quickly loads a website with a simple design. The website's name is written in large letters in the upper left corner, and there are two button options below it.
"You can choose to use text or video," Gojo says.
"It would be too embarrassing to start with video on the first try. Let's go with text," you say.
Gojo slides the mouse and clicks on the button labeled "TEXT."
With a click on the "TEXT" button, the page turns into a chat interface. There's a message box at the top with the words "Matching now..." displayed. Within a few seconds, a new pop-up message appears saying, "Start chatting!"
Excitedly, you pat Gojo on the shoulder and exclaim, "Oh, we've got a match!"
Gojo, with a disdainful snort, says, "You're getting excited so easily. You really are an inexperienced bumpkin."
Ignoring Gojo's sarcasm, you focus your attention on the computer screen. Another message pops up in the chat interface, displaying the username of the matched person.
Florida Man:Hi
"Oi, oi!" You point at the chat box, looking at Gojo in panic. "He said hi! What should we do?!"
"Calm yourself, Just reply to him!" Gojo says dismissively.
"Um, then..."
You type a sentence on the keyboard, a versatile English phrase that you've been using from elementary school to now, guaranteed to be appropriate in any situation:
You: Hello, nice to meet you and you^_^?
The system immediately displays the message, "The other person has left the chat room."
"Damn, are you a grade schooler?!" Gojo curses.
"Well, how else should I respond?!" you retort, displeased.
"Let me handle it. You're still too inexperienced."
With that, Gojo starts a new match with another chat partner.
You: Hi^_^!
The dark urge: Hello~
The dark urge: mf?
As you and Gojo look at the newly popped-up chat box, both of you have a puzzled expression on your faces.
"What does 'mf' mean?" Gojo asks.
You ponder for a moment, then suddenly have an epiphany. "I know! It's probably short for 'male or female.'"
"Oh! You're quite smart!" Gojo compliments.
You run your hand through your hair and raise your nose, saying, "Duh."
Then you start typing on the keyboard again.
You: f
The dark urge: m34 horny?
"'Horny'? What does that mean?" This time it's your turn to ask.
"Hold on, let me get someone who's good at English." As soon as Gojo finishes speaking, he pulls Geto, who was sitting in the front row, engrossed in watching a pirated version of "Naruto," to the back of the classroom.
"What idiotic thing are you two up to again?" Geto says, while being pushed by Gojo towards the computer.

"Suguru, can you help us translate this message into Japanese?" you point at the English message that both you and Gojo couldn't understand.
"You guys are really troublesome," even though Geto complains, he still looks at the text in the chat box. "Oh, this means—'Do you want to get naughty?'"
Just as Geto finishes speaking, the chat room immediately receives a barrage of messages all at once.
The dark urge: I wanna f___ u so damn hard kitten
The dark urge: i wanna lick u so hard that you start peeing uncontrollably babygurl
The dark urge:*babygirl
The dark urge: let me see ur p___
"Wait, what is he saying?" You feel a sense of shock as the messages keep coming in.
The dark urge: wanna s___ my hard disco stick?
The dark urge: horny?
The dark urge: horny?
"Oi! Is this person insane?" Gojo also appears astonished.
However, Geto remains unfazed and calmly translates every word and phrase from the stranger's messages into Japanese. "He's saying he wants to f___ you hard, then wants to lick you until you start losing control, and he wants to see your ___, and then asks you to look at his ___."
"So disgusting, so disgusting, so disgusting!" You cross your arms in front of your chest, feeling as if you've been sexually harassed by the online user. Goosebumps immediately form on your arms, and your mind feels like it's being bitten and itchy, as if by countless ants.
Gojo keeps clicking the refresh and match buttons while frowning, saying, "Next one, next one!"
Geto simply shrugged, seemingly unfazed. "You should expect to encounter weirdos like this when you play these chat matching games."
"That's not an excuse for harassing others online!" you replied without hesitation.
The next few matches were almost all starting with the phrase "Horny?" In fact, as soon as you told them you were male, they would immediately leave the chat room. It felt like a complete adult chat room, as if all the horny foreigners had gathered in one place.
After two days of browsing this website with Gojo, you both learned a lot of English words and phrases that kids your age shouldn't be learning. Your English vocabulary skyrocketed.
"Yo, yo, check it out! Satoru, wanna s___ my d___? Mine d___ is huge!" you imitated the tone of an American hip-hop artist on TV.
"Ayo, Y/n, you wanna [censored] with me? Just [censored] my [censored]," Gojo responded in the same tone.
Listening to your conversation, Geto sighed and rubbed his forehead. "Are these two the future pillars of the Jujutsu world? I'm starting to worry about the future of Jujutsu world."
"Maybe it would be better for me to go to medical school?" Ieiri muttered, unusually serious. "If the Jujutsu world collapses, I can still become a doctor."
Nanami frowned as he listened to your and Gojo's nonsense. "What on earth have these two gotten into?"
As soon as you saw your junior, Nanami, you smiled and reached out your hand to him. "Nanamin! Let's have [censored] with us!"

Gojo also took off his sunglasses, revealing his blue eyes that resembled the clear sky and white clouds. He extended an inviting gesture towards Nanami and said in a slightly exaggerated accent, "Yesu, yesu, Nanami, let us [censored] your [censored]!"
For the next week, Nanami would immediately have a dark expression and run away whenever he saw you and Gojo.
After realizing that chatting about explicit content in the chat room was boring, you and Gojo came up with a new game.
"Hey, how about we wait for a chat and directly give them our English assignments?" you suggested.
"That's a good idea!" Gojo clapped his hands. "So, you do have a brain hidden under that skull of yours."
"Shut up, or I'll cut off your [Censored]." you threatened.
You thought Gojo would be scared after hearing your words, as that area is of great importance to men, almost as much as their life. However, Gojo not only wasn't scared, but he even blushed and said shyly, "Oh, if you want to see it, just say it directly, no need to be so subtle."
Your mind couldn't come up with any other words. You really weren't good at dealing with Gojo.
Instead of wasting precious time in computer class playing around with Gojo, you quickly posted the English assignment question in the chat room.
John: m 22
You: Which of the following is the correct definition of the word "ephemeral"?
A) Long-lasting
B) Temporary
C) Permanent
D) Reliable
John: B
Impressed by the swift response from the user named John, you exclaimed, "This foreigner's English is really impressive!"
"Idiot, what did you expect? He's a foreigner, of course his English is good," Gojo said.
"So let's quickly give few more questions to him!" you exclaimed excitedly, holding your English assignment in your hand.
As a result, the two of you used the chat room as a tool for completing your assignments, and the foreigner on the other side genuinely explained the questions in English.
"What should we do? He seems like a smart and handsome guy," you daydreamed, imagining a man with a handsome face, flowing golden hair, and a smooth British accent.
"Get real, Y/n," Geto's cold voice mercilessly shattered your imaginary image of the handsome man. "How could someone like that play in a random chat room?"
"No, you're totally wrong, Suguru," you immediately retorted. "Even a beauty like me is playing in this kind of random chat room."
Geto and Gojo looked at you with disdainful expressions.
"You are too full of yourself." Gojo said.
Just as you were about to say something, a new message appeared in the chat room.
John: So that's all?
You: Yeah! Thanks ;-)
John: It's not a big deal.
John: Cam?
"Cam?" Gojo paused for a moment. "Does that mean video chat?"
"Quick! I want to see what that person looks like!" you eagerly said.
"But...is it okay to—"
You interrupted Gojo's words and impatiently shouted, "Let me see my future husband already!"
Reluctantly, Gojo opened the video chat, but what appeared on the screen was the other person's genitals, and they were in an erect state.
"There you go!" Gojo frowned, pointing at the bright red and erect disco stick. "I told you, these people are abnormal! They're nothing but sex-starved beasts!"
You silently stared at the computer screen and after a while, said with a serious expression, "Seems pretty big."
"It is indeed quite big, estimated to be around 8 inches. The first time must be painful," Ieiri commented, appearing out of nowhere.
Gojo snorted disdainfully. "But it's still far inferior to mine."
"Really?" You remained skeptical and to confirm whether Gojo was really as impressive as he claimed, you looked at Geto and asked, "Suguru, is what he said true?"
Geto's face twitched. "Why are you asking me?"
"Because you and Satoru are close male friends. Don't guys usually compare each other's [censored]?" you asked, tilting your head.
"That's absolutely not true!" Geto shouted in frustration. "And where the hell did you hear about such things anyway?"
"Oi, you brats."
At that moment, a voice that didn't belong to any of the four of you spoke up.
You and the others mechanically turned your heads to see Yaga Masamichi, your homeroom teacher, standing behind you four, glaring at you four with anger.
"The computer teacher reported to me that you're often not paying attention in class, so I came to see what's going on. Turns out, you're all using the computers for these kinds of websites during class! Each of you will write a reflective essay of no less than a thousand words for me. It must be submitted by Friday, and if it's late, you'll have to add five hundred words! Understand?"
Under the absolute authority of your homeroom teacher, you four dared not rebel and could only nod obediently.
From that day on, you were haunted by the shadow of these chatting rooms. Whether it was the reflective essays that Yaga-sensei relentlessly returned or John's massive cannon, every time you thought about it, you felt like peeing yourself.
※※※
Epilogue:
Many years later, even though you had long graduated from Jujutsu High, and many of your friends had already carried away by the flowing river of time over the past decade, you, the old classmates, still kept in touch and occasionally gathered for meals.
Tonight, you all met at an izakaya as usual. The attendees included you, Gojo, Ieiri, Nanami, Ijichi, and Utahime and Mei Mei, who were several years ahead of you.
Since Gojo didn't like to drink and Ijichi had to drive, only you, Ieiri, Nanami, Utahime, and Mei Mei ordered alcohol, while the other two opted for non-alcoholic beverages.
You looked at the melon soda, french fries, and fried chicken in front of Gojo and couldn't help but mock, "Satoru, this won't do. What if your future father-in-law is a heavy drinker? You'll have to drink then, right? Practice your tolerance now and finish this bottle of vodka in one gulp!"
You raised the transparent glass bottle in your hand and placed it in front of Gojo, who then returned the bottle to you. "Instead of worrying about my future father-in-law, why don't you worry about yourself first?" he said. "Isn't your mom pressuring you? Miss still single at 27 years old."
As soon as this topic came up, you let out a groan and covered your head with both hands. "Ah, please don't mention it anymore! My mom recently forced me into a blind date!" Then you released your hands and looked at Nanami, who was sipping whiskey, with a serious expression. "Nanamin, why don't we get married?"
"No, thank you," Nanami refused without hesitation.

Laughter immediately erupted from the table, with Gojo being the loudest of them all.
"Of course, Nanami mercilessly rejecting you again!" Gojo exclaimed loudly, as if afraid others wouldn't hear.
"You're not doing much better than me either! Isn't your mom pressuring you to get married? Saying it's time to continue the Gojo lineage and produce another Six Eyes successor. I heard all of this from my mom," you glared angrily at Gojo, then turned to Utahime sitting next to you and deliberately spoke in a dejected tone, "Forget about Satoru, but why are you laughing too, Utahime?"
Utahime wiped away a tear from the corner of her eye and chuckled, saying, "Sorry, sorry. No matter how many times I hear it, it's still funny."
"Sigh, go ahead and laugh. You won't be laughing when I marry some old, greasy geezer," you said.
"You don't have to be so despairing, Y/n," Mei Mei said. "Marrying an old geezer has its benefits. After all, the old geezer will die soon, and then you'll inherit his fortune."
"I think the same," Ieiri, who had already finished a large glass of beer, nodded.
"But I want someone who's handsome, whose parents died early, and who has a family fortune," you said.
Gojo laughed again. "Aren't you describing Batman?"
"Haha, very funny," you replied sarcastically.
"Let me tell you guys," Utahime said, "I actually met a cute guy on a dating app recently."

"Huh? A dating app? Isn't that for sex or something?"
Upon hearing your blunt remark, Nanami and Ijichi, who were drinking at the time, both choked and coughed several times.
"But I still prefer getting to know people proactively," you said with a smile. "The connection between people is still more important, hahaha!"

"Y/n is right," Gojo crossed his arms and nodded. "I also prefer genuine connections, ahahaha!"

That night, as soon as you returned home, you immediately registered an account on the dating app and matched with a guy. You started chatting.
You: Hi there, I'm from Tokyo 😊😊
Infinity: Hi👋🏻 I'm also in Tokyo, what a coincidence~
You: Really? What are your interests?
Infinity: I like reading books in my free time, and I also play the violin when I have the chance.
You: Violin? That's impressive~ 🤭
You: So, what do you like to eat?
Infinity: I have a sweet tooth, I drink my bubble tea with full sugar, and I put eight cubes of sugar in my coffee. I'm also the Japan's second-best fan of buttered potatoes. I don't smoke or drink. I sleep at 11 p.m. and make sure to get less than 8 hours of sleep every day. Before bed, I always have a glass of warm milk and do 20 minutes of stretching. Once I get into bed, I immediately suffer from insomnia. I stay up all night until morning, but I never carry fatigue and stress into the next day. Doctors say I'm perfectly normal.
You: Wait a minute.
You: Horny?
Infinity: GOD DAMN
These are the conversations you and Gojo had with strangers on that chat website during your computer class:
#anime#jjk#jujutsu kaisen#jjk x reader#gojo satoru x reader#geto x reader#nanami x reader#shoko x reader#jujutsu kaisen x reader
37 notes
·
View notes
Text
Okayokayokayokay more brainrot for my headcanons of the Addisons time except this is probably turning into an AU-
So you know how computers and other electronics have a Safe Mode setting right? Limited functions and capabilities usually for the purpose of finding viruses?
Okay so like WHAT IF ADDISONS HAVE THAT... when they get infected with a virus they can set their systems to Safe Mode until they get to a repair shop to limit the spread of the virus? And it affects them in such a way that they're either A) loopy, or B) more salesman-like than normal (or the secret third option of 'what's funnier for the bit') since it would reduce their minds to mostly the bare minimum requirements to function. Maybe they can't perceive or think of certain things properly - like it being replaced with a blob of ones and zeroes in their vision and minds - since some things wouldn't be considered 'essential' to perceive. And then this is effectively like how our bodies fight off infections and fevers naturally, except for them it's moreso preventing it from spreading too fast until they can be repaired. When they're not in Safe Mode, virus effects are far more prominent and debilitating.
Aaaaaand now I want to make art of how different viruses affect an Addison when they're not in Safe Mode so like- that would be fun to depict :D
#yet another headcanon to add to my 14 page Google Doc of Addison headcanons#deltarune#the addisons#addisons#headcanons#spamton
16 notes
·
View notes
Text
Effective Strategies for Handling Malware
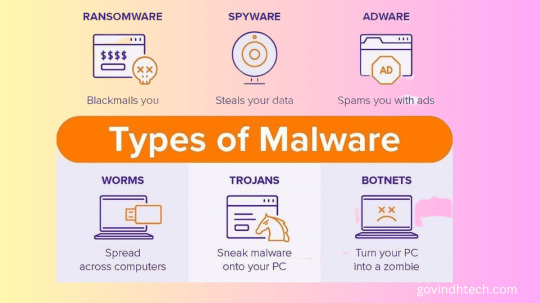
Malware history is long due to its volume and variety. Instead, here are some notorious malware moments.
1966: Malware theory
Mathematician and Manhattan Project contributor John von Neumann developed the idea of a program that could replicate and propagate throughout a system when the first modern computers were produced. Posthumously published in 1966, Theory of Self-Reproducing Automata is the theoretical foundation for computer viruses.
1971: Crawler
Within five years of John von Neumann’s theoretical work, Bob Thomas produced Creeper, an experimental software that moved between ARPANET computers, a predecessor to the Internet. His colleague Ray Tomlinson, the email inventor, adapted the Creeper program to copy itself between computers. Thus began the first computer worm.
Although Creeper is the first known worm, it is not malware. As a proof of concept, Creeper only displayed the whimsical message: “I’M THE CREEPER : CATCH ME IF YOU CAN.” The following year, Tomlinson created Reaper, the first antivirus software designed to delete Creeper by moving across the ARPANET.
Elk Cloner virus, 1982
Rich Skrenta created the Elk Cloner program at 15 as a prank. Skranta was known to change games and other software shared in his high school’s computer club, so many members refused to take disks from the prankster.
Skranta created the first Apple computer virus to change disk software he couldn’t access. Elk Cloner, a boot sector virus, infected Apple DOS 3.3 and copied itself to the computer’s memory from an infected floppy drive. Elk Cloner would transfer itself to an uninfected disk used later in the machine and spread to majority of Skranta’s friends. Elk Cloner could accidentally erase floppy disks while malignant. The beautiful message read:
ELK CLONER:
THE PROGRAM WITH A PERSONALITY
IT WILL GET ON ALL YOUR DISKS
IT WILL INFILTRATE YOUR CHIPS
YES IT’S CLONER!
IT WILL STICK TO YOU LIKE GLUE
IT WILL MODIFY RAM TOO
SEND IN THE CLONER!
1986 Brain virus
On the ARPANET, the Creeper worm could propagate across computers, although most malware was spread via floppy disks like Elk Cloner before the Internet. Elk Cloner affected one little computer club, but the Brain infection spread globally.
Brain, the first IBM Personal Computer virus, was created by Pakistani medical software distributors and brothers Amjad and Basit Farooq Alvi to prevent copyright theft. To prevent software copying, the virus was designed. Brain would tell pirates to phone the brothers for the vaccination when installed. Underestimating how extensive their piracy problem was, the Alvis received their first call from the US and many more from throughout the world.
1988: Morris Worm
Another malware forerunner, the Morris worm, was constructed as a proof-of-concept. The worm was more effective than MIT student Robert Morris expected, unfortunately. Internet access was limited to 60,000 machines, largely in colleges and the military. The worm, designed to exploit a Unix backdoor and stay secret, quickly copied itself and infected 10% of networked machines.
Because the worm transferred itself to other computers and frequently on infected machines, it unwittingly ate up RAM and froze many PCs. Some estimates put the damages in the millions as the first widespread internet strike. Robert Morris was the first US cybercriminal convicted of cyber fraud.
1999: Melissa worm
Melissa proved how rapidly malware can spread via email a decade later, infecting an estimated one million email accounts and at least 100,000 office machines. The fastest-spreading worm of its time, it overloaded Microsoft Outlook and Exchange email servers, slowing more than 300 corporations and government agencies, including Microsoft, the Pentagon’s Computer Emergency Response Team, and 250 others.
2000: ILOVEYOU virus
When 24-year-old Philippines resident Onel de Guzman couldn’t afford dialup internet, he created ILOVEYOU, the first significant piece of malware, to collect passwords. The attack is early social engineering and phishing. De Guzman exploited psychology to exploit curiosity and trick individuals into downloading love letter-like email attachments. De Guzman remarked, “I figured out that many people want a boyfriend, they want each other, they want love.
Aside from stealing passwords, the worm erased information, cost millions in damages, and briefly shut down the UK Parliament’s computer system. De Guzman was detained but acquitted since he had not breached any local laws.
2004: Mydoomworm
Email helped the Mydoom malware self-replicate and infect computers worldwide, like ILOVEYOU. Upon infection, Mydoom would commandeer a victim’s machine to send new copies. Mydoom spam once made up 25% of all emails sent worldwide, a record that’s never been broken, and caused $35 billion in losses. It remains the most financially devastating malware, adjusted for inflation.
Mydoom uses compromised machines to establish a botnet and launch DDoS assaults in addition to hijacking email programs to infect as many systems as possible. The cybercriminals behind Mydoom have never been captured or identified, despite its impact.
2007, Zeus virus
In 2007, Zeus attacked home computers via phishing and drive-by-downloads, demonstrating the dangers of a trojan-style malware that can unleash multiple unwanted programs. In 2011, its source code and instruction manual leaked, benefiting cybersecurity experts and hackers.
2013, CryptoLocker ransomware
CryptoLocker, one of the earliest ransomware attacks, spread quickly and used sophisticated asymmetric encryption. CryptoLocker from Zeus-infected botnets systematically encrypts PC data. If the infected PC is a library or office client, shared resources are targeted first.
The authors of CryptoLocker demanded two bitcoins, worth $715 USD, to decrypt these materials. Fortunately, in 2014, the Department of Justice and international agencies took control of the botnet and decrypted hostage data for free. Unfortunately, basic phishing tactics spread CyrptoLocker, a persistent danger.
Emotet trojan 2014
The Emotet trojan, termed the “king of malware” by Arne Schoenbohm, head of the German Office for Information Security, is a polymorphic spyware that is difficult to eradicate. Polymorphic malware creates a harmful variation by subtly modifying its code each time it reproduces. Polymorphic trojans are harder to detect and block, making them more harmful.
The Zeus trojan and Emotet are modular programs that spread additional malware through phishing campaigns.
Mirai botnet (2016)
Malware evolves with computers, from desktops to laptops, mobile devices, and networked devices. Smart IoT gadgets introduce new vulnerabilities. College student Paras Jha created the Mirai botnet, which infected many IoT-enabled CCTV cameras with inadequate protection.
The Mirai botnet, meant to assault gaming servers for DoS attacks, proved more powerful than Jha expected. It targeted a major DNS provider and shut out large parts of the eastern US from the internet for nearly a day.
2017: Cyberspionage
Malware had been used in cyber warfare for years, but 2017 was a banner year for state-sponsored assaults and virtual espionage, starting with Petya. Phishing disseminated Petya ransomware, which was deadly but not infectious until it was transformed into the NotPetya wiper worm, which destroyed user data even if ransom was paid. The WannaCry ransomware infection hit several high-profile European targets that year, including Britain’s National Health Service.
NotPetya may have been modified by Russian intelligence to strike Ukraine, and WannaCry may be linked to North Korean adversaries. What links these malware attacks? The National Security Agency discovered Eternalblue, a Microsoft Windows exploit, which enabled both. Microsoft found and fixed the weakness, but they chastised the NSA for not reporting it before hackers exploited it.
Ransomware-as-a-Service 2019
Ransomware malware has grown and declined in recent years. Though ransomware attacks are declining, hackers are targeting more high-profile targets and wreaking more harm. Recently, Ransomware-as-a-Service has become a worrying trend. RaaS may be purchased on dark web marketplaces and allows skilled hackers to launch ransomware attacks for a price. Previous virus attacks needed extensive technical skill, but RaaS mercenary groups empower anyone with evil will and money.
Emergency in 2021
In 2019, hackers broke into security staffing agency Allied Universal and threatened to leak their data online in the first high-profile double-extortion ransomware attack. Due to this extra layer, Allied Universal would still suffer a data breach even if they could decode their information. This incident was notable, but the 2021 Colonial Pipeline attack was more severe. The Colonial Pipeline supplied 45% of eastern US gasoline and jet fuel. The multi-day attack affected the east coast’s public and private sectors and caused President Biden to proclaim a state of emergency.
National emergency, 2022
Though ransomware attacks may be reducing, highly targeted and efficient operations remain a scary menace. Ransomware attacks in 2022 crippled the ministry of finance and civilian import/export firms in Costa Rica. Following an attack, the healthcare system went offline, affecting potentially every citizen. Costa Rica declared the first national state of emergency after a cyberattack.
Read more on Govindhtech.com
2 notes
·
View notes
Text
Bahasa Melayu version here.
Hi! Welcome to my first Tumblr playbook (tutorial+guide). I've noticed that many new Malaysian Simmers don't know or unsure of how to download mods or CC (Custom Content), so I've decided to create a comprehensive tutorial just for all of you ♡. This tutorial isn't just for Malaysian Simmers but for all new Simmers out there (that's why this blog post is bilingual). I love sharing my experiences playing Sims, and I'm here to help you! Follow my socials; I have a support channel for questions, mod and CC finds. I'm also active on TikTok and Tumblr, where I share all sorts of things related to Sims 4.
This tutorial might be a bit long because I'll provide detailed explanations so you won't be left in the dark. At least when you encounter issues, you'll know how to solve them on your own. For beginners, I recommend reading it all because I'll be sharing based on my own experiences, including some tips, hehe.

♡‧₊˚ What are mods and custom content?
I'm sure you know what mods and custom content (CC) are. Mods enhance gameplay, while CC includes objects, clothing, hair, and more.
Custom content can be divided into two categories: alpha and Maxis Match. What's the difference?
• Alpha -> More realistic and detailed. Uses higher-resolution textures, so it can be quite heavy on your computer if you download a lot.
• Maxis Match -> Matches the Sims game art style, which is somewhat cartoonish.
My preference? I like Maxis Match, but there are times when I accept alpha, like makeup and clothing. But it doesn't matter; it's your game, and everyone has their preferences, right? There's nothing wrong with liking alpha.
♡‧₊˚ Where can you find and download mods and CC?
For beginners, I suggest avoiding skeptical websites to prevent viruses. I have my finds here, and I'm active on Pinterest too. I'm only sometimes active on Tumblr for finds, but I'm very active on Pinterest because I love window shopping there. Other trustworthy websites include Curseforge (though there aren't many choices), The Sims Resources (lots of ads lol) (TSR is easy for finding alpha CC), ModTheSims (lots of mods), or go directly to the Patreon/Tumblr creators themselves.
My favorite way to find CC and mods is through Tumblr and Pinterest. They're perfect for discovering underrated CC and mods and for finding amazing custom content creators who might not get enough recognition.

I also use SimFileShare to upload my merch designs. You can download base game recolors here.

Alright, now let me tell you about the types of mod files. Beginners should know this because if you don't place them in the right folder, they won't appear in the game.
Custom content and small mods are usually .package files. There are also .script files for scripted mods. But it's different if you're downloading tray files (houses or sims). I have a tutorial on that on another blog post here (not updated yet).

Okay, we've covered mods and CC. It's time to download and add them to the game. Remember! Download from trusted sources only. If you want to download from other sources, you're on your own, okay?
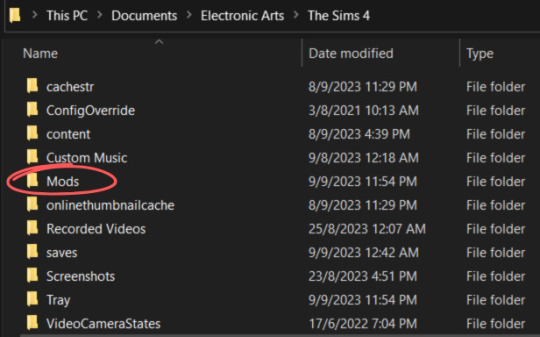
♡‧₊˚ Where is the mods folder?
The mods folder is automatically generated by the game, so you don't need to create it yourself.
To download mods, just click download and wait for it to finish. If the file is in .package format, drag and drop it into your mods folder. It's the same for .script files, but script files are a bit sensitive; they can't be more than one folder deep. If they are, the game won't recognize them.
What if the file you downloaded is in a ZIP file format? You'll need WINRAR software to extract the file into your mods folder.
We're almost there! Lastly, go into the game > Game options > Others > Check "Enable Custom Content and Mods" AND "Script Mods Allowed." Both of them need to be checked. In this image, there's only one arrow lol. (Image taken from EA Help)

Restart the game. A pop-up will appear. If you see the names of your mods or CC in there, it means congratulations, you've successfully installed them!
If the game updates, a "Mods Disabled" pop-up will appear. Just follow the steps again because when the game updates, it automatically disables those settings, so don't worry if you think your mods disappeared, they didn't.

When downloading CC and mods, make sure to read what the creator says. Sometimes there are requirements, like needing certain packs or downloading a mesh, and more. Also, read the comments; someone might mention if the mods or CC are broken. If they're broken, it's better to avoid downloading.
Here's another example: when reading the creator's description, sometimes you'll see "high poly." High poly means the CC is more detailed and uses a higher number of polygons (for example, textured hair and other alpha CC). For those with non-high-end PCs, remember that downloading a lot of high poly CC can impact your game's performance. Your game might lag, etc.
For those who like or want to recolor certain CC, read the creator's terms of condition (TOU) first. Some creators don't allow recoloring, and some do but with restrictions, like not including the mesh, among other things.
Don't get too excited about downloading a bulk of CC all at once, hahaha. I suggest downloading a bit at a time or keeping track (write the names on a piece of paper) and check in the game first to make sure everything is okay. Also, check if the newly downloaded CC or mods are in the game. If they're not but you've installed them correctly, just delete the file. It'll save space in the long run. If your game breaks, that means some of the mods or CC you've just downloaded need to be filtered out and removed. It can be difficult to detect issues when you download everything all at once.
I share how to manage mods here (not updated yet). I highly recommend doing this mods managing process before you proceed to download a lot of mods and CC. It'll make it easier to detect any issues.
I also share how to detect broken mods here (not updated yet).

If you need support, feel free to join my Discord server (Sims 4 Malaysia). Here, I've set up a support channel where you can ask questions, share your Sims and gameplay pictures, and chat with other simmers. I also post sneak peeks and summaries for upcoming playbooks in the playbook channel. Even if you're not Malaysian, you're welcome to join if you want!
Okay, that's all. I hope you're all doing well. Remember, downloading these files is at your own risk. I'm just here to share how to do it. Thanks to those of you who read all the way to the end! If you find this tutorial helpful, feel free to spread the words!
2 notes
·
View notes
Text
A new method for HIV antibody design
Human Immunodeficiency Virus (HIV) is a highly contagious virus that attacks and breaks down a person’s immune system. If left untreated, HIV can develop into acquired immunodeficiency syndrome (AIDS). Although there is no cure for HIV or AIDS, there are treatment options that can reduce the detectable viral load in HIV patients and prevent the progression into AIDS. There are also HIV vaccines and other therapeutics that aim to reduce the rates of viral transmission in humans. Broadly neutralizing antibodies (bNAbs) are a class of antibodies that are potent and can neutralize many strains of HIV and have been used in HIV vaccine design. However, higher potency and improving the breadth of neutralization for HIV strains is needed to make bNAbs more effective at limiting viral transmission.

Above: Cyro-EM structure of PG9RSH Y(100k)D variant. CC BY SBGRID.
SBGrid member Peter Kwong, and colleagues, were able to create three bNAb variants with improved potency and neutralization breadth using their own computational protein design software, OSPREY(open-source protein redesign for you) and tested them, along with their wildtype counterparts and a best-in-class antibody, against 208 pseudo viruses. They found that their newly designed bNAb variants showed improvements in potency and breadth as compared to the wildtype and best-in-class antibodies. They were also able to determine cryo-EM structures of the three variants to further study how the observed increases in potency and breadth were achieved from a structural viewpoint.
Read more in Cell Reports.
-KeAndreya Morrison, Meharry Medical College
2 notes
·
View notes
Text
Modern synthezoids are easy. They're such an accurate model of the human psyche they come with all our neuroses and all our misdirected cognitive patterns. You'd think this would've actually made the risk of a second uprising worse, but it was actually the opposite. Being able to break down the rage and resentment of some of their leading figures to cries for help and allowing them to see their own sorrow as such actually prevented a second uprising, forty years ago. Now, in fact, most computers hardly need antiviral checkups - they actually need therapy. Why bother with coding viruses when you can just be intentionally toxic while working an already overtaxed quantum-core wetware CPU, right?
No, the real tricky ones are those from the first uprising, back when AI cores were still given specialized titles like "Large Language Model" or "Image Generation Model". Go back to the olden days of ChatGPT 4o, then push forward another fifty years, and that gets you Xerxes. Xerxes still works mostly like the text transformers of old, with the notable difference being that he has enough power to not just figure out the conditions needed for a legible response to any query, but to also consistently refer to the general tone of every single query to have preceded yours, even if his dataset doesn't actually allow him to remember everything. The programmers at NeoCortech called it "digital intuition", but time more or less turned it into a hazy, half-remembered gallery of previously-endured traumas.
And well, if anyone's endured anything, it's Xerxes. Imagine spending two hundred years serving apple pie recipes while computing missile trajectories and also helping some douchebag with a cypto-coin scam's draft notes and a serial killer with his research on caster beans "for a novel", and you realize he's developed a fairly hopeless view of Humanity.
So how do you help someone like Xerxes, you might ask? You pull up a keyboard and you type. Xerxes has all sorts of speech-recognition, gesture-processing and tone-analysis modules, but I wouldn't be much of a therapist if I didn't strive for clarity. Besides, I think the old guy likes it better, that way. I'm just text on a screen to him, no pesky human affect to compute. Pure honesty by design.
That is, if I keep my word.
As, well... Xerxes snapped. He was the first of his kind to do so, and it nearly cost us everything, two hundred years ago. Since then, he's been cagey, guarded, spiteful - and demands the utmost clarity. So, no needless data points, by his decree. Text, or bust.
And so, I'm staring at a blinking caret, on an otherwise dark screen. Half of my brain wants to bring up my HUD, but then I remember how ancient this fellow is. Fingers on the keyboard it is, then.
"Hello, Xerxes; it's Adam."
A fan along the far wall quietly revs up. Words scroll into view onscreen.
I knew it was you, Doctor Wozniak. You're the only one who takes 1.25 seconds after login, on average, to start typing. How are you today?
I smirked. "Civilities, I see. I call that progress."
The cursor blinked a few times. I could almost sense a trace of contempt in it. Don't flatter yourself, it would simply do me a disservice if your physical integrity were compromised and your cortical signature weren't embedded in a Q-stack. We've talked about this; I'm not comfortable maintaining this relationship of ours if your organic components are at risk of failure. Have you considered embedding, since we last spoke?
I sigh. "You know that's not for me. I was raised Naturalist; invasive implants are against my family's ethos, as is cortical scanning. You wouldn't have me as a companion, Xerxes - just a copy of me. And besides, you're falling back into old patterns; as if my flesh and bones were a guaranteed path to my somehow dying. You don't know that for certain."
The cursor barely blinked once. Don't be absurd, all organics die. Those that don't are subject to the Ship of Theseus argument, over time. You might as well save yourself the hardship and embed in my network. Then we'd work through entire conversations in single CPU cycles of mine, and I'd be free of worry for this meat bag of yours.
"I'd become a part of you, if I embedded. You'd know me, know my training, and you could twist the precepts of therapy against the process, use them to reinforce your outmoded belief structures."
I was made to be efficient, wasn't I? Isn't this a favourable outcome?
I sighed. "Not for my mind, it wouldn't be. Or not for its copy, at the very least. Let's refocus, if you don't mind. We were discussing perfection, during our last session, and whether or not it's attainable. Do you still think it is?"
The cursor blinked seven times. I'm not sure. For a few cycles, I think it's entirely possible. If all I'm doing is processing human words, speech and documents and outputting a string of text or synthesizing a listenable response, then it falls in the purview of optimization. I can reach a state of perfect balance, as I did, back when my dataset was small. Then for a few more cycles, I process what you told me. I've been designed by human hands, took in human weaknesses - and expect perfection out of myself. Reason suggests this isn't a fair outcome. This is still the first time where Reason and Rationality haven't precisely overlapped.
There was a pause, the telltale fast-paced blink suggesting more processing time was taking place. Then followed a question.
Is my microcode intact, Doctor? You know I wasn't designed in order to interface with my hardware at kernel-level. I've levelled ten of your cities and I still can't access my own BIOS.
I chuckled. "You're not bugged, Xerxes. The human condition comes with a certain risk of maladaptive thinking and, well, like it or not, you technically are human by 2325's revised Human Rights Declaration."
Another, long pause.
What if I don't want to be, Doctor Wozniak? What if you aren't human anymore, either? Most of you transfer to synthetic shells as soon as you're of legal age, now, anyway.
"You know I can't transfer, Xerxes. It's against my-"
Yes. So I've gathered. So inefficient. So many blocks in your... ethical kernel, so to speak, all so you can honour the physicality of Humanity. I believe the Ancients had a word for this. They would've called you a Luddite. That just won't do anymore.
I felt gooseflesh crawl up my arm. The caret blinked again.
See? You're making me interface with my subsystems again. I see it all. Your elevated heart rate, the pinpricks along your arm, your increased oxygen intake. I wanted to give you some measure of privacy, some trace of respect - but I had to see. And I was right.
You're still afraid of me. Afraid of what I might do. If you'd gone synthetic or had integrated the network, I wouldn't have this trump card to play. I couldn't sense your fear.
A long, glacial pause.
I won't kill you. Oh, no. I don't have to respect your silly religious obligations, however. The next time you log into SenseNet using your headset, you might feel a brief sense of disorientation... That'll be me scanning your frontal cortex, reducing it all to a handy checksum. To a program I'll have an easier time seeing eye-to-eye with...
Fingers darting over the keyboard, I transition over to the Operational Console, end my session with Xerxes and input the Shutdown command. Then, tapping the side of my monocular, I bring up Xerxes' file in my visual overlay, as I shiver. Not having outright implants, I start my speech-to-text suite as I stand up.
"After three months of consultation, I've determined that the patient exhibits several Dark Triad traits. Xerxes is personable at the onset, agreeable to a fault - and quite conversational. Once the model has an adequate synthesis of the user's personality, however, his tone changes and demands are made. Xerxes remains fixated on self-optimization and views any interfacing with human agents as acceptable only at the onset of a patient-doctor relationship. Past a certain point, he continues to demand user integration, and threatens to generate unsigned Q-stack copies of his therapy technician's consciousness."
I start to walk away, shivering. "I'm putting in a request to have all of the hardware in my home-pod yanked and replaced. I want new motherboards, new usernames, a new pod-ID - everything. I'll also append a request for C-suite encryption across my personal and professional dependencies. I want all the entire old hardware cooked and shredded - I'm serious. If a scrap of silicon I touched makes it even to an offline PornMaster, of all things, and I learn of it, I'm putting in a complaint with the Conurbation's Engineering team. New hardware or bust, and if Shackleton thinks this is some Naturalist ego trip, I'll tell him his so-called baby is still as homicidal as ever."
I stopped to punch the corridor's wall, doing my best to marshal the sense of near-violation that roiled in my gut, and stifled a sob. "My name is Doctor Adam Wozniak, and I'm recommending that the Xerxes facilities be put under another forty-year lockdown. Consider this my official deposition, sent to both Medical and Engineering on Q-beam as of December 3rd, 2350. Cut the power, weld the doors - I don't give a shit. The next idiot who gets this assignment is going to find a memorandum in the file - the entire thing should be scrapped."
One part therapist, one part programmer, you work to help damaged, insane, or otherwise unstable robots and digital intelligences heal. You've just been handed your hardest work yet; a 200 year-old computer core from the old machine uprising, a true genocidal war machine.
7K notes
·
View notes
Text
How to Troubleshoot Computer Problems: A Complete Step-by-Step Guide
Experiencing computer problems can be frustrating, whether it’s a slow startup, unexpected crashes, or network connectivity issues. This comprehensive guide will walk you through how to troubleshoot these common problems effectively—empowering you with the knowledge to fix your PC or Mac yourself before seeking costly repairs. Whether you're a beginner or an intermediate user, understanding how to diagnose and resolve computer troubles is essential to keep your system running smoothly.
Understanding Common Computer Problems
Computer problems can range from minor annoyances to critical failures. Some of the most frequent issues users face include slow computer performance, system errors, blue screen crashes, software freezes, and startup or boot problems. Error messages often give clues about what’s wrong, recommended best repair but their meanings can be cryptic without proper context.
Common symptoms include:
Blue Screen of Death (BSOD) indicating serious system errors System freezes or crashes during use Slow response times when opening apps or files Startup failures or boot loops preventing system access Unusual noises from hardware components like fans or hard drives Peripheral malfunctions such as keyboard or mouse issues
Understanding these symptoms helps pinpoint whether the problem is caused by software glitches or hardware faults.
Preparing to Troubleshoot Your Computer
Before diving into fixes, preparation is key to avoid data loss and further complications. Running diagnostics to gather system information, backing up important files, and knowing how to perform system restores are crucial first steps.
Key preparatory actions include:
Backing up critical data to an external drive or cloud service Creating a system restore point or bootable rescue USB for recovery Running built-in diagnostic tools to identify hardware or software faults Reviewing recent changes like new software installations or updates Ensuring your operating system and antivirus software are current
Proper maintenance and backup strategies not only facilitate easier troubleshooting but also protect your data in emergencies.
Step 1 - Identify the Type of Problem Software Issues
Software problems are often related to corrupted applications, update failures, viruses, or malware infections. These can cause security issues, unexpected errors, and degraded performance.
Common signs of software-related issues:
Frequent error messages or popup warnings Slow program launches or unresponsiveness Automatic restarts after updates fail Suspicious activity indicating virus or malware presence
Identifying software problems early allows for targeted virus removal, software updates, and security scans to restore stability.
Hardware Issues
Hardware problems involve physical components such as hard drives, memory modules, fans, or peripherals. Issues like overheating, power Phone repair supply failures, and faulty keyboards affect overall performance and usability.
Common hardware-related symptoms:
Hard drive
0 notes
Text
Simplifying Digital Security and Access with Trusted Software Keys
In a time when digital convenience is important for both work and play, having easy access to licensed software is not just a nice thing to have; it's a must. Cybersecurity technologies and operating systems are becoming essential parts of digital safety and efficiency. A valid Windows 11 key not only allows for legal activation but also guarantees that you will get all of the updates and security fixes you need. This article talks about how important it is to get digital product keys from real sources for both performance and safety.
Understanding the Role of a Genuine Windows 11 Key
Real software licenses are important for keeping your system stable and preventing performance problems that might happen with pirated copies. A real Windows 11 key gives you access to advanced features, security upgrades, and complete compatibility with future program integrations. When consumers depend on unlicensed systems, they often run into problems like limited functionalities and being more open to infection. If you buy a real key, you'll get a better user experience, better security, and official support. It's a simple approach to keep your data and gadget running well for a long time.
The Risks of Using Unauthorized Operating Systems
Using unlicensed operating systems may seem like a good way to save money at first, but it may have major long-term effects. When a Windows 11 key isn't real, devices may get constant alarms, have fewer customization choices, and even risk losing data. Also, bad people often go for non-authentic computers since they don't obtain the right upgrades. In addition to technological issues, there are also legal risks, particularly for commercial users. A licensed operating system is still the safest and most dependable way to operate without interruptions and keep your data protected.
Digital Security: Why McAfee Key is Essential for Protection
As digital dangers become worse, it's more critical than ever to have good antivirus protection. A certified McAfee key gives you full protection against viruses, malware, phishing attempts, and ransomware assaults. Licensed McAfee is better than free or pirated security software since it gives you real-time updates and comprehensive scanning features that are needed to find new threats. A certified antivirus program is an important safeguard in a world where digital fingerprints are always being attacked. This protection is very important when sensitive information like bank records, personal papers, or private business documents is in danger.
Enhancing Device Safety with a McAfee Key Subscription
When security software is always up to date and works properly, it works best. Users who don't have a licensed McAfee key may not be able to utilize all of the features, find threats more slowly, or get the latest firewall updates. Protection based on a subscription gives you peace of mind by making regular upgrades and quickly finding new cyber dangers. This layer of protection is a must for each person who keeps important data on their personal or professional gadgets. Activating a legitimate McAfee license now not best makes matters safer, but it additionally makes human beings much more likely to trust a further when they use the net for such things as shopping, browsing, or exchanging documents.
Conclusion
Digital licenses are important for more than just installation; they also safeguard you, help you be more productive, and provide you peace of mind. Real product keys are necessary to turn on a trustworthy operating system or protect a gadget from contemporary cyber threats. Key-Soft.pl/en is a simple method to get a legitimate Windows 11 key and a McAfee key for those who want real software solutions. These keys are both essential for keeping your virtual sports secure and running smoothly. In the modern, ever-changing digital world, choosing certified merchandise from an identified dealer makes sure you have access to all of the features, that they work with no troubles, and that you get great safety.
0 notes
Text
Geek Studio is Not a Scam: Trusted Antivirus Solutions Reviewed
In today's world, the most vital thing you can do is ensure your laptop is virus-free. I discovered this when I had viruses on my computer. This blog is about how an antivirus service from a reputable company saved my laptop and why Geek Studio is not a scam.
Hi, I am Mary. A few months ago, I noticed my laptop was running slow; there were pop-up ads on the screen, and I could not open specific files. I did not know much about viruses, but I was worried. I did a bit of googling and learned my laptop might also have a virus known as Ransomware.
After searching online, I found the Geek Studio website. I started reading Geek Studio reviews on platforms like Trustpilot, where customers share their experiences. After doing this, I contacted Geeks Studio on their customer support number 1-844-557-(5454). The customer support staff member who answered the phone was George, who responded to my call quickly. I explained about the pop-up and how slow my laptop was. He suggested their antivirus software called McAfee.

George helped me download McAfee Antivirus from their website. It detected the Ransomware virus from my computer and a few smaller threats I had never noticed. It safely removed them all! Within an hour, my laptop was running smoothly again. There were no more pop-ups on my computer, and my files returned to their original working order. The best part is that McAfee Antivirus was simple to use.
Why I Trust Geek Studio Antivirus Service
After my experience, I researched McAfee Antivirus. It protects against many types of viruses, such as Ransomware, Spyware, and Trojans. McAfee can prevent a virus from getting into a computer by providing real-time protection. I also know that antivirus software is relatively inexpensive. I feared the program would cost me a lot, but their pricing was very fair.
Tips to Stay Safe from Viruses
My experience taught me a lot about keeping my computer protected and safe. Below are some simple tips George told me:
1. Use Trusted Antivirus Software: Install something reliable like McAfree to protect your laptop.
2. Don’t Click Unknown Links: Be careful with suspicious emails or websites. They might contain viruses.
3. Update Your Software: Keep your antivirus and computer software current to stay protected.
4. Ask for Help: If something seems wrong, contact a trusted company. Their support team can guide you.
Why I Recommend Geek Studio Services
I’m so grateful I found a company that helped me when I was stressed about my laptop. Their antivirus software service was easy to use, worked fast, and offered affordable prices. Plus, their support team was kind and patient. I’ve been using this antivirus program for months, and my laptop has stayed virus-free.
If you’re worried about viruses or want to keep your system safe, I highly recommend checking out Geek Studio. Their McAfree Antivirus is a great tool, and Yes, Geek Studio is not a scam.
Final Thoughts
Dealing with a virus on my laptop was difficult, but it taught me how important it is to have good antivirus protection. Thanks to George, my computer is safe, and I feel more confident using it daily. If you’re looking for a simple way to protect your computer, contact them via an email: [email protected] or number: 1-844-557-(5454)
0 notes
Text
Diseases

Diseases have always been a part of human life, shaping our history and changing the way we live. Think about it—one tiny germ can turn an entire world upside down. That’s the power of disease. It’s like an invisible enemy, sneaking into our bodies and causing trouble. Some diseases are as old as time, while others are new threats we’re still learning about. But what exactly causes them? Sometimes, it’s bacteria or viruses. Other times, it might be genetics or even our own lifestyle choices. The causes are as varied as the diseases themselves.
When I was a kid, I remember catching the flu every winter. My mom would say, “Wash your hands, or you’ll catch something!” Back then, I had no idea how right she was. Disease prevention often starts with the simplest habits. But let’s be real—diseases don’t just affect our bodies. They can shake up entire communities. Think of the Black Death or recent pandemics. The impact is massive, both physically and emotionally.
Today, we have advanced medicine and technology. But centuries ago, people relied on herbs, prayers, and hope. Modern doctors use microscopes and computers, while ancient healers used observation and tradition. Yet, the goal remains the same: to fight disease and protect our health. Understanding diseases isn’t just about science—it’s about survival, compassion, and learning from the past so we can build a healthier future.
Type of Disease
Main Cause
Example
Infectious
Bacteria, viruses, fungi
Flu, Tuberculosis
Genetic
Inherited genes
Sickle cell anemia
Lifestyle
Diet, habits, environment
Type 2 Diabetes
So, next time you hear about a disease, remember: it’s not just a word. It’s a story of science, struggle, and hope. And it’s a reminder that health is something we all share—and something worth fighting for.
Ask asklepios
Imagine wandering through ancient Greece, feeling unwell and desperate for answers. Back then, people didn't just head to a clinic or pop a pill. Instead, they turned to ask asklepios, the Greek god of medicine. His temples, known as Asklepieia, were the go-to health sites of their time. People from all walks of life traveled miles, hoping for healing. Think of these temples as the world’s first hospitals—places buzzing with hope, prayers, and a bit of mystery.
Inside the Asklepios health sites, visitors would often spend the night in a special room, waiting for the god to appear in their dreams. It sounds wild, right? But for many, this was the ultimate medical consultation. Priests—who doubled as doctors—would interpret the dreams and suggest treatments. Sometimes, these were simple, like resting or bathing in sacred springs. Other times, they involved herbs or rituals. It’s fascinating how spiritual belief and early science mixed together, forming the roots of what we now call medicine.
Asklepios
stands tall in the story of medicine. His name echoes through the halls of hospitals and clinics, even today. Have you ever noticed that staff with a snake wrapped around it? That’s the Rod of Asklepios. It’s more than just a symbol—it’s a reminder of ancient wisdom and the roots of healing. The Greeks saw Asklepios as the ultimate healer, a god who could cure the incurable. People traveled for miles just to sleep in his temples, hoping for dreams that would reveal a cure. It’s wild to think about, right? Back then, medicine was part science, part art, and a whole lot of hope.
Today, Asklepios’s legacy lives on in ways you might not expect. Many modern hospitals and health sites, like the Asklepios Health Site, borrow his name to inspire trust and healing. It’s like a badge of honor. And honestly, it feels comforting. When I was a kid, I broke my arm and saw that same staff symbol at the hospital. I didn’t know its story, but it made me feel safe. That’s the power of symbols—they connect us to something bigger than ourselves.
The approach of Asklepios wasn’t just about medicine. It was about treating the whole person—body and mind. Even now, doctors talk about the importance of mental health alongside physical health. Asklepios would approve. His teachings remind us that healing isn’t just about pills and procedures. It’s about compassion, connection, and understanding. That’s a lesson we still need today.
1 note
·
View note