#how to protect your wifi from hackers
Explore tagged Tumblr posts
Note
Can you do a hacker reader x Idia shroud
Idia x Hacker Reader
A/N: Hii so I actually wrote this before, but my wifi was bad, so the whole post just disappeared into the void. Thankfully my computer saved the ask, so I can re-write it. Anyways I don't know anything about hacking, but Ill try my best
Gn reader

To put it simply, you scare him
i mean let's be honest, its a bit intimidating having someone you know be able to hack, a constant threat if you will
Idia is always protective of his tech, both his computer and his tablet are a very important part of his everyday life
You wouldn't mess with those now would you?
He first found out when the two of you played a game together
For a while, he thought that maybe he was just bad at the game or you were really good
But one suspiciously lucky move made it all clear
You were cheating
how dare you?
He had really thought he was bad at the game, but when in reality you were hacking your way through it
However he found that he was quickly able to get over it hearing your laughter at his realization
When the two of you had a movie night, he quickly realized that you did not get this movie ethically
And it wasn't one of those low quality movies from those crappy pirating websites with weird ads
This was very high quality version of the move
he decides it's best not to act
Remember how earlier we mentioned he was very protective of his devices?
yeah that doesn't deter you at all
You never do anything too bad, just enough to bug him
Hacking into his magicam to post pictures of yourself is the best way to mess with him
It always catches him off guard, and he didn't like it at first, but now he can't help the small smile tugging at his lips, even if everyone else makes fun of him for it later
it's not only you causing problems all the time
While he's not as good as you, he does know a thing or two about electronics and hacking
This is mostly used to mess with kids on roblox though
by yourself, you can be a bit annoying, but together the two of you cause absolute chaos when you want to

Okay, yeah I definitely don't know much about hacking, but i did my best. ty for reading and have a nice day.
107 notes
·
View notes
Text
I don’t normally post things on here, but since I know some folks get worried about a lack of activity from me, I just wanted to let y’all know I’m going to be…busy for the next week or two thanks to the ransomware attack on Hillcrest systems across the nation, whom I work for as a scribe.
Everything is on lockdown electronically which makes everything actually hell. Patient’s safety is at risk in more ways than one and that asshole hacker is making already overworked and underpaid medical staff EVEN MORE overwhelmed. I’m so fucking mad. Why can’t this shit happen to some big mega billionaire corporation? Why healthcare? This country’s system is rough enough on both patients and healthcare workers as is, why make it worse for everyone?!
Can’t order medications without manually writing out each and every one of them and faxing them, can’t order labwork or imaging or make referrals without manually writing each and every one them out and faxing them, we can’t even chart (not like I have time to with my doctor’s style) so I’m just scribbling down changes so I can make proper charts later once this whole mess has been taken care of. Essentially triple the work with no additional pay for it.
On top of it EVERYONE is scared about how the system was breached. Even I am, and I don’t go freaking anywhere with my laptop. Delilah stays at home where she’s hooked up to a password protected wifi and has an absolute tank of an antivirus software that makes her lag for 3 hours. I don’t hardly ever check my email let alone open any new mail. I rarely ever use Delilah to even browse here! I use my phone! But you never know until the source has been traced! It could be anyone, which means could be you, and my anxious butt REALLY doesn’t like that.
And these are just my gripes as a paranoid, overwhelmed, crybaby $10-12/hr scribe (idk if I ever got that $2 raise) with just the added work, but it makes me incredibly upset and stressed about how this will effect our patients. Most of my clinic’s patients are elderly and have problem lists and medication sheets a mile long. Our ERs and hospitals have to divert patients to other hospitals. People are going to die from this ransomware attack on our system. These kinds of delays will kill someone and it’s just heart dropping.
Like, healthcare having shitty overwhelming work hours is essentially part of the territory of working in healthcare. You go home tired and feeling like shit but are happy to know that your 99 year old patient is still kicking and lively and has all their marbles to have enjoyed their golden years and probably a few more to go. But having someone outside of our system disrupt our ability to deliver proper care to patients is just…it’s rough.
I know I’m only a scribe, but I’m my old doctor’s eyes and hands, I make the prescriptions and labs and referrals on his behalf; I’m working with his nurse on what diagnoses codes we need to work with to help insurance be more willing to cover for procedures; they feel like my patients too… It’s… distressing… Knowing all we can do is just hang on and try our best… I just hope it’s enough. I hope it’s only a week. Just a week. God I hope it’ll only last a week.
Anyway, if I suddenly cease any activity over the next 2 week, I’m not dead. I just will be wishing I was while attempting to keep this computer-less system somewhat working or at least organized until the computer system is back.
3 notes
·
View notes
Text
Why Your Digital Life Needs a Security Checkup (And How Vulnerability Scanning Can Save You)
Hey tech fam! 👋 Let's talk about something that might sound super technical but is actually pretty important for anyone who uses the internet (so... everyone?).
What's This "Vulnerability Scanning" Thing Anyway?
Think of vulnerability scanning like getting a regular health checkup, but for your computers, websites, and digital stuff. Just like how a doctor checks for health issues before they become serious problems, vulnerability scanning looks for security weak spots before hackers can exploit them.
It's basically an automated security guard that goes through all your digital assets and says "Hey, this password is weak," or "This software needs updating," or "This door is wide open for cybercriminals."
The Different Types of Digital Health Checks 🩺
Network Scanning: Checks your WiFi, routers, and all the tech that connects your devices together. Think of it as examining your digital nervous system.
Web App Scanning: Looks at websites and online applications for common hacker tricks like SQL injection (sounds scary, right?).
Database Scanning: Makes sure your stored data isn't sitting there with a "please steal me" sign on it.
Wireless Scanning: Checks if your WiFi is basically broadcasting "free internet and data access" to the whole neighborhood.
How Does It Actually Work? 🤖
Discovery Phase: The scanner maps out everything connected to your network (like taking inventory of your digital house)
Detection Phase: Compares what it finds against huge databases of known security holes and vulnerabilities
Risk Assessment: Ranks problems from "meh, fix when you have time" to "OMG FIX THIS NOW"
Reporting: Creates reports that actually make sense (hopefully)
Why Should You Care? 🤷♀️
Because Hackers Don't Take Days Off: They're constantly looking for easy targets. Regular scanning helps you not be one.
Compliance Stuff: If you run a business, there are probably rules you need to follow. Scanning helps with that boring (but important) paperwork.
It's Cheaper Than Getting Hacked: Trust me, prevention costs way less than dealing with a data breach. Way, way less.
Expert Help: Professional services give you more than just "here's a list of problems" - they actually help you understand and fix things.
What Makes a Good Vulnerability Scanning Service? ✨
Covers Everything: Should check all your digital stuff, not just some of it
Stays Updated: New threats pop up daily, so the service needs to keep up
Customizable: Your business isn't exactly like everyone else's, so your scanning shouldn't be either
Plays Well With Others: Should work with your existing security tools
Clear Reports: Nobody has time for technical gibberish without explanations
Real Talk: The Challenges 😅
Performance Impact: Scanning can slow things down temporarily (like how your phone gets slow during updates)
Information Overload: Sometimes you get SO many alerts that you don't know where to start
Not Enough Time/People: Small teams often feel overwhelmed by all the security stuff they need to handle
Pro Tips for Success 💡
Set up regular scans (like scheduling those dentist appointments you keep putting off)
Mix up authenticated and non-authenticated scans for different perspectives
Actually track whether you've fixed the problems (revolutionary concept, I know)
Learn to ignore false alarms so you can focus on real issues
The Future is Pretty Cool 🚀
AI and machine learning are making vulnerability scanning smarter. Soon, systems might even fix some problems automatically (while we're sleeping, hopefully).
We're also moving toward real-time monitoring instead of just periodic checkups. It's like having a fitness tracker for your cybersecurity.
Bottom Line 💯
Look, cybersecurity might seem intimidating, but vulnerability scanning is actually one of the more straightforward ways to protect yourself. It's like having a really thorough friend who points out when your digital fly is down before you embarrass yourself in public.
The internet can be a scary place, but you don't have to navigate it defenseless. Regular vulnerability scanning is like having a really good security system - it won't stop every single threat, but it'll catch most of them and give you peace of mind.
Ready to give your digital life a security checkup? Professional services can handle all the technical stuff while you focus on... literally anything else. Check out comprehensive vulnerability scanning solutions here and sleep better knowing your digital house has good locks on the doors.
Stay safe out there! 🛡️
What's your biggest cybersecurity worry? Drop it in the comments - let's discuss! 💬
#cybersecurity #vulnerability #techsafety #infosec #digitalsecurity #smallbusiness #technology #hacking #cybercrime #datasecurity
1 note
·
View note
Text
How to Prevent WiFi Hacking: Essential Tips to Secure Your Network
In our increasingly connected world, WiFi security is as important as locking your front door. Many people don’t realize their wireless network is vulnerable until it’s too late, leading to stolen data, sluggish internet, or even compromised smart devices. Fortunately, there are several effective ways to protect your WiFi from hackers.
Start by changing your router’s default username and password, as these are often easy targets for attackers. Always use strong encryption — preferably WPA3 or at least WPA2 — to keep your network traffic secure. It’s wise to disable remote management features on your router, which can otherwise allow outsiders to tamper with your settings.
For added privacy, hide your network’s SSID so it doesn’t show up in the list of available WiFi networks. Keeping your router’s firmware updated is another crucial step, as updates often include important security patches. You can also enable MAC address filtering, which allows only approved devices to connect to your network.
If you frequently have visitors, consider setting up a separate guest network. This keeps your main devices and data isolated from potential threats. Always use a strong, unique WiFi password, and change it regularly to minimize risks. Make a habit of monitoring the devices connected to your network so you can quickly spot and remove any unauthorized users.
For an extra layer of protection, use a VPN to encrypt your internet traffic, especially when using public or less secure networks. By following these practical steps, you’ll significantly reduce the risk of WiFi hacking and keep your digital life safe and secure.
#WiFiSecurity#CyberSecurity#NetworkSecurity#WPA3#DigitalSafety#WiFiHacks#TechTips#HomeNetwork#RouterSecurity#Infosec
1 note
·
View note
Text
How a Faraday Bag Gave Me Real Peace of Mind
Just realized how shockingly easy it is for someone to hack keyless cars and even phones these days. 🚗🔓📱 I always thought this kind of stuff happened only in movies, but after reading a few horror stories (and seeing some actual YouTube tests), I couldn’t ignore it anymore.
So I started looking for ways to actually protect myself—and stumbled across something called a Faraday bag. Basically, it’s a pouch that blocks all wireless signals (Bluetooth, RFID, WiFi, even 5G), so no one can scan, hack, or track your stuff while it’s inside. Super simple, but honestly kinda genius.
What surprised me even more? The one I picked up is also fireproof and waterproof. I can throw in my phone, key fob, passport, cash—whatever—and it’s safe from hackers, fires, spills, and all the chaos of daily life. No more low-key paranoia when I’m out or traveling.
Seriously, if you’re worried about digital privacy, or just want an extra layer of protection, check out thefaradaybag.com. It’s the only thing that’s actually given me peace of mind lately. Not an ad—just something that actually works.
Stay safe out there, friends! 🔒✨
#FaradayBag #DigitalSecurity #EDC #KeylessCar #Privacy #TravelHacks






0 notes
Text
Beyond the Earnings: The Surprising Benefits of a Career in Cybersecurity
Cybersecurity is one of those careers that sounds either super cool or super intimidating sometimes both. If you’ve ever thought about getting into it, you’ve probably heard the usual perks: great salary, job security, and the satisfaction of outsmarting hackers. But let’s talk about the real reasons why cybersecurity is one of the most underrated (and weirdly fun) careers out there.
1. You Get to Be a Professional Trouble-Maker (Legally!)
If you’ve ever been the kid who took apart the family computer just to see how it worked, or the one who figured out how to bypass school WiFi restrictions (no judgment), cybersecurity might just be your calling. Ethical hackers (yes, that’s a real job) get paid to break into systems legally to help companies patch security holes. Enrolling in a reputable Cyber Security Online Training & Placement program can equip individuals with the essential skills and knowledge needed to excel in this dynamic and evolving field.

2. No Suit, No Problem—Work in Pajamas If You Want
Cybersecurity is one of the most remote-friendly careers out there. Many roles let you work from home, a coffee shop, or even while traveling. As long as you have a solid internet connection and your laptop, you’re good to go. Bonus: You get to skip the daily commute and wear whatever you want (yes, even that hoodie you’ve had since high school).
3. It’s Not Just a Job, It’s a Superpower
Once you start working in cybersecurity, you’ll never look at the internet the same way again. You’ll spot phishing scams a mile away, know exactly how to lock down your personal data, and never fall for those “Congrats! You won an iPhone!” pop-ups. You become the person your friends call when they think they’ve been hacked (which, honestly, can be both a blessing and a curse).
4. No Degree? No Problem!
Unlike a lot of high-paying jobs, cybersecurity doesn’t always require a college degree. Many people break into the field through self-study, certifications, and hands-on experience. If you love problem-solving and figuring things out on your own, you can learn the skills needed without spending years in school (and without drowning in student debt).
5. You’ll Never Be Bored (Seriously, Never)
Cyber threats are constantly evolving, which means your job will never be the same two days in a row. One day you might be analyzing malware, the next you’re investigating a security breach. If you hate routine and love a good challenge, cybersecurity is the perfect playground. When you work in cybersecurity, you don't just protect businesses you also learn how to safeguard your own digital life. Through Best Online Training & Placement Programs, you'll be the one spotting phishing emails before they trick you, securing your personal data like a pro, and staying ahead of cyber threats.
6. You’re Actually Making the Internet a Safer Place
This is the part people don’t talk about enough: cybersecurity isn’t just about stopping hackers. It’s about protecting people, businesses, and even entire governments from cyber threats. Whether you’re preventing financial fraud, safeguarding personal data, or keeping companies from being held hostage by ransomware, your work has real-world impact.
7. The Community is Wildly Supportive
The cybersecurity world is filled with people who love to share knowledge. Whether it’s through online forums, Capture The Flag (CTF) competitions, or Twitter threads breaking down the latest hacks, you’ll find a community that genuinely enjoys helping newcomers get started. No gatekeeping, just nerds supporting nerds.
0 notes
Text
Can eSIM Be Hacked? Security Features You Should Know
The demand for embedded SIMs, particularly when travelling abroad, is growing with the deployment of eSIM technology. A traditional SIM card is provided by eSIM, which is built directly into your device, allowing you to easily switch networks or add new ones without ever needing to change the SIM cards manually.

But this growing trend raises questions concerning security: is it possible to hack an eSIM? Is it advisable for people who depend on staying connected while visiting foreign countries? This guide examines precisely these issues of eSIM security, describing key features that are necessary and useful and considering how best travel insurance services can assist in alleviating worries about security threats.
How Secure Are eSIMs?
1. eSIM Security and Data Protection
In order to safeguard users from various attacks, including cloning and illegal access, eSIMs were built with many strong security precautions. eSIMs, as opposed to their predecessors, which are movable SIMs, are embedded into devices and possess a range of protective aspects due to their structural software, which includes encryption and multi-factor authentication. While using Zetexa, travellers and business clients have a trusted partner who takes care of all their security concerns and more during their travels.
2. Authentication Process and Encryption
An eSIM uses a sophisticated authentication method where devices and networks subject each other to verification before a connection is forged. This verification helps prevent many kinds of attacks since only valid and signed connections are established:
Encrypted Connections: The eSIMs encrypt documents while being transmitted from one device to the network, and the communications are between devices. This makes it very hard for criminals to eavesdrop on or alter your communications.
Remote Provisioning: The ability to provide eSIM profiles via the internet lowers the threat of physical interference, for there is no chip to be exposed and accessed by the marauders.
3. Protection Against SIM Swapping
Cyber Assault, which is quite common in the mobile industry, known as sim swapping, sometimes requires social engineering whereby the network carrier is deceived into changing the victim’s phone number to another sim. In the case of eSIM, remote provisioning and enhanced identification poses an obstruction to such attacks.
To anyone seeking additional insurance while on the move, it is advisable to purchase the best travel insurance available. Providers such as Zetexa will help to ensure that assistance will be available if one encounters network problems, attacks or even a connectivity or device management problem.
4. Remote Profile Management
eSIM profiles are remotely managed, therefore, the control and monitoring make it more secure. Users do not have to go to the carrier store to add, delete or update a profile, thus reducing possible vulnerabilities. Profiles can also be wiped if the device is lost or stolen, thereby reducing possible data misuse.
Zetexa goes a notch higher to offer users who switch profiles in other countries to avoid vulnerabilities that may come with switching profiles.

Possible Risks to eSIM Security
No system is risk-free, and eSIMs offer a considerable level of protection. It is essential to figure out the risks which may exist within the system and engage in protective measures. This is particularly important for people using their eSIM in risky situations: business travellers or digital nomads.
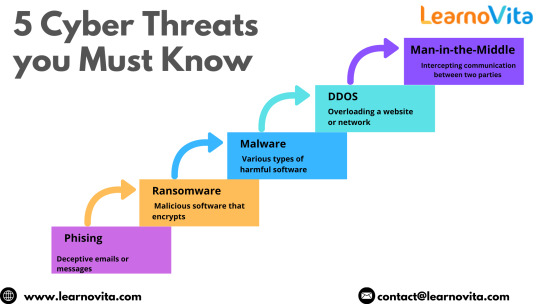
1. Man-in-the-Middle (MITM) Attacks
MITM attacks take place in instances where two parties are communicating, and a hacker steps in between them to access information meant for them. The risk of this type of attack is diminished quite significantly due to encryption. However, users can be vulnerable to open and unsecured wifi networks. To prevent this, travellers attempting to access sensitive information over public networks should not do it but instead should consider switching to a VPN.
2. Device Hacking and Malware
There is good news that eSIM profiles can be said to have good protection, but device level security enhances eSIM safety. If there is malware or spyware on a device, it can leak personal information or eSIM data into the wild.
Due to this reason, many travellers on the go tend to secure travel insurance such as Zetexa or others that have device protection. Zetexa matrix secures undiagnosed situations such as potential data cracking or hacking and facilitates professional help in covering essential information on the go.
3. Network-Based Threats
Being in new areas utilising local networks comes with exposure to network-based threats, especially in places where the security parameters are not standard. Theoretically, attackers would seek to manoeuvre carrier networks’ weaknesses as potential areas of attack. And while this is highly improbable, these risks emphasise the need to only source eSIM profiles from trusted suppliers and to avoid unknown networks.
The good way to handle such risks is to add the best travel insurance to your toolkit, especially if you are making use of eSIMs in places where the network security standard is not that robust. Firms like Zetexa are best placed to offer global support and even network security hints in areas where the risk is very high.

Steps to Enhance eSIM Security on Your Device
You can adopt additional measures to protect devices and data in order to further increase the protection offered by eSIMs. Here are some actionable tips that you can use to your advantage:
1. Keep Your Device Updated
Device makers, including hardware and software, release regular software updates or patches that help to seal any potential security holes that give hackers a chance to breach the system. This is one of the most painless and most impactful cyber defence measures against eSIM threats, always ensure that the OS, as well as the security software installed in your device, is up to date.
2. Enable Device Authentication
Using biometric features such as fingerprint locks or even facial recognition on your device coupled with strong PIN codes set on your eSIM profile makes it difficult for any unauthorised persons to tamper with your device or make any alteration to the eSIM profile.
3. Avoid Public Wi-Fi Networks
Public Wi-Fi is very risky in terms of being hacked and is easily attacked via a range of cyber to quite a wide range. If you have to use public Wi-Fi, make sure to use a reliable Virtual Private Network (VPN) such as NordVPN when using public networks to make sure your data is not intercepted. Also, travel insurance plans like those from Zetexa can assist you in an emergency if you think a hostile network has attacked you while travelling. They guarantee immediate action and assistance when in new places.
4. Download eSIM Profiles from Trusted Sources Only
Do not forget to select your eSIM provider very carefully. Remember, there are untrustworthy ones who can ruin your device. eSIM profile should be downloaded only from genuine carriers or their affiliate online stores.
5. Use Travel Insurance for Comprehensive Protection
Frequent travellers or business users can relax by subscribing to a comprehensive travel insurance provider like Zetexa. This cover provides help with connectivity problems, theft of a device, and network attacks. Also, coverage from the best travel insurance provider will help when there are device problems and security threats while one is in other countries.
Conclusion
eSIM technology is particularly suitable for travellers and people working remotely as it is a secure solution that provides advanced features for protecting personal data. Furthermore, with encryption, authentication protocols, and the ability to manage eSIMs from anywhere, eSIMs are reasonably effective against modern cyber threats. That said, it is important to stay vigilant and be aware of possible weaknesses such as limited device vulnerability.
In the same manner, incorporating the best travel insurance into the travel habit offers additional peace of mind, knowing there will be assistance in the event of any technical problems or loss of connectivity. As a travel insurance company, Zetexa is a specialist in offering device insurance, which guarantees that irrespective of where you are in the world, your connection will remain secure. Zetexa and the travel insurance options will enable a frequent traveller or a curious mind to consider the opportunities of eSIM technology to stay connected in a safe manner.

Download:
ZetSIM App from the APP Store
ZetSIM App from the Google Play Store
0 notes
Text
Install Slimline Sliding Door Lock Solution- Secure Your Home with Ease!
Installing a slimline sliding door lock can improve security and aesthetics, a worthwhile investment for any property. These sleek and sophisticated locks integrate with slimline doors to maintain the space's exquisite appearance and protect against unauthorised access.
Using a new digital lock for sliding door is beneficial and recommended to purchase from reputable suppliers or manufacturers. Well-established suppliers source their products from licenced manufacturers who prioritise not only build quality but also accurate functionality, built-in hacker security, and high-quality batteries for extended battery life.

Furthermore, dependable vendors offer after-purchase installation services twenty-four hours a day, seven days a week, through personal visits, technical and security advice, and property site audits.
Advantages of Installing Wifi-Operated Security Locks:
Reputable providers offer fully functional smart locks that do not require keys. This means that smart locks are highly convenient and pose no risk of key loss. People can live in their homes without having to carry keys or deal with the trouble of searching for them.
Even if the owner is a long distance away, mobile phones can control wifi-enabled smart locks. They can let any visitor, relative, or family member into the house by just entering the unique unlocking code. Change the entry code to prevent unauthorised guests from entering their homes.
Reliable vendors exclusively provide recognised brand smart locks with cutting-edge technology.
Criminals or invaders cannot enter the property by using techniques since smart digital locks lack key slots and do not accept forged entry codes.
How To Find a Reputable Smart Lock Supplier:
People should buy high-quality modern wifi locks from trusted Aussie smart lock manufacturers.
They must check the authenticity of the manufacturers, whether their gadgets are protected by warranties, and whether they have experience in smart lock manufacturing for some years.
Visit their online pages on social media, and check what their customers say about the product quality, pre-purchase and after-purchase services, and customer support service.
Additionally, compare all these factors along with their product prices online. Contact them and check whether they have facilities to solve and troubleshoot any inconvenience that occurs in their technology.
Finally, follow these factors carefully and select a reputed supplier to purchase high-quality security smart locks.
Source
0 notes
Text
youtube
Enhancing Network Security: How to Change the IP Address of Your WiFi Router for Advanced Protection
Empower Your Network Security: Learn How to Change the IP Address of Your WiFi Router and Safeguard Against Unauthorized Access. In this comprehensive tutorial, we'll guide you through the step-by-step process of altering the IP address of your WiFi router, fortifying your network against potential security breaches and protecting your sensitive information from unauthorized individuals or hackers. By implementing these essential security measures, you can ensure peace of mind and maintain control over your network's integrity. Take proactive steps to bolster your digital defenses and safeguard your online presence today!
#NetworkSecurity#RouterSecurity#WiFiProtection#IPAddressChange#CyberSecurityTutorial#TechSecurity#OnlineSafetyTips#DigitalDefense#InternetSecurity#ViralTutorial#Youtube
0 notes
Text
does wifi with vpn use data
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does wifi with vpn use data
WiFi VPN data consumption
When using a VPN over WiFi, it is important to consider its impact on data consumption. A VPN encrypts your internet connection, providing you with security and privacy, but this encryption also comes with a cost in terms of data usage.
The amount of data consumed while using a VPN over WiFi depends on various factors such as the level of encryption, the activities you engage in online, and the duration of your VPN connection. Generally, VPN encryption adds some overhead to your data packets, which can result in slightly increased data usage compared to using the internet without a VPN.
Streaming high-definition videos, downloading large files, or engaging in online gaming while connected to a VPN over WiFi can significantly impact your data consumption. These data-intensive activities combined with VPN encryption may lead to higher data usage than usual.
To minimize data consumption while using a VPN over WiFi, you can opt for less encryption or use data-saving features if your VPN provider offers them. Additionally, being mindful of your online activities and avoiding data-heavy tasks can also help reduce your overall data usage.
Overall, while using a VPN over WiFi provides important security benefits, it is essential to be aware of its potential impact on data consumption. By understanding how VPN encryption affects data usage and taking steps to manage it, you can enjoy a secure internet connection without exceeding your data limits.
VPN data usage on WiFi
When using a VPN on WiFi, data usage can be a concern for users. A VPN, or Virtual Private Network, encrypts your internet connection to ensure privacy and security. This encryption adds an additional layer of data that needs to be transferred between your device and the VPN server, potentially impacting your data usage.
The amount of data used while using a VPN on WiFi can vary depending on factors such as the level of encryption, the type of VPN protocol used, and the activities you are performing online. Generally, using a VPN will increase your data usage slightly due to the encryption process. However, the actual impact may be negligible for regular browsing or streaming activities.
To minimize the impact of VPN data usage on WiFi, you can consider using VPN protocols that are known for being more data-efficient, such as IKEv2 or L2TP/IPSec. Additionally, you can choose VPN servers that are geographically closer to you to reduce latency and potentially decrease data usage.
It's also recommended to monitor your data usage while using a VPN on WiFi, either through your device settings or your VPN provider's app. This can help you understand the impact of VPN usage on your data plan and make adjustments if necessary.
Overall, while using a VPN on WiFi may result in slightly higher data usage, the benefits of increased privacy and security often outweigh the minimal impact on data consumption.
Impact of VPN on WiFi data
When it comes to protecting your online privacy and security, using a Virtual Private Network (VPN) can have a significant impact on the data transmitted over WiFi networks. VPNs encrypt your internet connection, preventing third parties like hackers, ISPs, or even government agencies from eavesdropping on your online activities.
One of the primary benefits of using a VPN on WiFi is the added layer of security it provides. Public WiFi networks, such as those found in cafes, airports, or hotels, are notorious for their lack of security. By using a VPN, you can ensure that all the data you send and receive over the WiFi network is encrypted and secure, reducing the risk of cyber attacks and data breaches.
Moreover, VPNs can also help bypass geo-restrictions and censorship imposed by certain websites or governments. By connecting to a VPN server located in a different country, you can access content that may be blocked in your region, allowing for greater freedom and access to online information.
However, it's essential to choose a reliable and trustworthy VPN provider to fully reap the benefits of using a VPN on WiFi. Some VPN services may log your online activities or have weak encryption protocols, potentially compromising your data security and privacy.
In conclusion, utilizing a VPN on WiFi networks can have a positive impact on protecting your data and online privacy. By encrypting your internet connection and bypassing restrictions, VPNs offer a secure and versatile solution for navigating the digital world safely.
WiFi VPN bandwidth usage
Using a WiFi VPN can have implications on your bandwidth usage that are important to understand. When you connect to a VPN (Virtual Private Network) over WiFi, your internet traffic is encrypted and redirected through a secure server before reaching its destination. This encryption process can lead to an increase in bandwidth consumption compared to browsing without a VPN.
When you use a WiFi VPN, your data packets are encapsulated in an additional layer of encryption, which can lead to slightly slower internet speeds and increased data usage. The extent of the impact on your bandwidth usage may vary depending on the VPN service provider, the encryption protocols used, and the distance between your device and the VPN server.
While the encryption process can result in higher bandwidth consumption, the benefits of enhanced online privacy and security often outweigh the potential drawbacks. By using a VPN, you can protect your personal data from cyber threats such as hacking and surveillance, especially when connected to public WiFi networks.
To mitigate the impact of VPN usage on bandwidth, you can consider selecting VPN servers that are geographically closer to your location, choosing lightweight encryption protocols, and monitoring your data usage to prevent exceeding any data caps imposed by your internet service provider.
In conclusion, using a WiFi VPN may lead to increased bandwidth usage due to the encryption processes involved. However, the trade-off for improved online privacy and security is often considered worthwhile for many users. By understanding the implications on bandwidth usage, you can make informed decisions when selecting and using a VPN service.
WiFi VPN traffic consumption
When using a VPN to secure your WiFi connection, it's essential to understand how it impacts your data consumption. A VPN encrypts your internet traffic, routing it through a secure server before reaching its destination. While this offers crucial privacy and security benefits, it can also lead to increased data usage.
One of the main reasons for increased data consumption when using a VPN is the encryption process itself. Encrypting and decrypting data requires additional data packets to be sent back and forth between your device and the VPN server. This overhead can result in higher data usage compared to browsing without a VPN.
Furthermore, when you connect to a VPN server, all of your internet traffic is routed through that server. This redirection can lead to longer transmission paths and potential latency issues, which may cause data to be transmitted multiple times before reaching its final destination. As a result, your data usage may increase due to the additional overhead of routing traffic through a VPN server.
To minimize the impact of VPN traffic consumption, consider connecting to VPN servers that are geographically closer to your physical location. This can help reduce latency and the distance data needs to travel, ultimately lowering your data usage. Additionally, be mindful of bandwidth-intensive activities such as streaming or downloading large files while connected to a VPN, as these can significantly contribute to increased data consumption.
In conclusion, while using a VPN is crucial for maintaining your online privacy and security, it's important to be aware of its potential impact on data consumption. By understanding how VPN traffic consumption works and implementing best practices, you can strike a balance between security and data efficiency.
0 notes
Text
does netgear c7000 support vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does netgear c7000 support vpn
Netgear C7000 VPN compatibility
The Netgear C7000 is a popular dual-band WiFi router that combines fast internet speeds with a built-in cable modem. It is known for its excellent performance and reliable connectivity, making it a top choice for many households and small businesses. However, when it comes to VPN compatibility, some users may encounter challenges.
Using a VPN (Virtual Private Network) is essential for protecting your online privacy and security by encrypting your internet connection. It also allows you to access geo-restricted content and browse the web anonymously. While the Netgear C7000 supports VPN pass-through, meaning it allows VPN traffic to pass through the router to the VPN server, some users have reported difficulties when trying to set up certain VPN services directly on the router.
Some VPN providers may not be fully compatible with the Netgear C7000 router, leading to connectivity issues or slow speeds. In such cases, users may need to set up the VPN connection on their individual devices instead of the router itself. This workaround can still provide the desired privacy and security benefits of a VPN, albeit with a slightly more manual setup process.
It's important to note that VPN compatibility can vary depending on the VPN service provider and the specific configuration of the Netgear C7000 router. Users interested in using a VPN with their Netgear C7000 should consult with their VPN provider for specific setup instructions and troubleshooting tips to ensure a smooth and secure VPN connection.
VPN support on Netgear C7000
VPN support on Netgear C7000 router provides users with enhanced privacy, security, and flexibility when it comes to their internet connection. This feature allows for the setup of a Virtual Private Network (VPN) directly on the router, encrypting data and ensuring online anonymity for all devices connected to the network.
With VPN support on the Netgear C7000, users can bypass geographical restrictions and access region-locked content by connecting to servers in different countries. This is particularly useful for streaming services, online gaming, and accessing websites that may be blocked in certain regions.
Additionally, VPN support on the Netgear C7000 enhances online security by creating a secure tunnel for data transmission, protecting sensitive information from cyber threats such as hackers, identity theft, and surveillance. This is crucial, especially when using public Wi-Fi networks, as it encrypts all internet traffic to ensure a safe browsing experience.
Setting up a VPN on the Netgear C7000 is typically straightforward, with many providers offering step-by-step guides or even dedicated apps for easy installation. Users can choose from various VPN protocols and server locations to customize their online experience according to their specific needs and preferences.
In conclusion, VPN support on the Netgear C7000 router is a valuable feature that empowers users to take control of their online privacy and security. By encrypting data, bypassing restrictions, and ensuring anonymity, this functionality elevates the overall internet experience for individuals and businesses alike.
Virtual Private Network on Netgear C7000
A Virtual Private Network (VPN) on a Netgear C7000 router can enhance online privacy and security by creating an encrypted connection between your device and the internet. This added layer of protection helps to shield sensitive data from potential threats, such as hackers or identity thieves.
Setting up a VPN on a Netgear C7000 router is a straightforward process that involves accessing the router's settings and configuring the VPN connection. Most VPN services provide detailed instructions on how to set up their service on a router, including Netgear models like the C7000.
By using a VPN on your Netgear C7000 router, you can enjoy benefits such as browsing the internet anonymously, accessing geo-restricted content, and securing your online activities while connected to public Wi-Fi networks. Additionally, a VPN can help prevent your Internet Service Provider (ISP) from monitoring your online behavior and potentially selling your browsing data to advertisers.
It's worth noting that while a VPN can provide added security and privacy benefits, it may also slightly impact your internet speed due to the encryption process. However, the trade-off between speed and security is often considered worthwhile by users who prioritize online privacy.
In conclusion, configuring a VPN on your Netgear C7000 router can significantly enhance your online security and privacy. By taking this proactive step, you can browse the internet with peace of mind knowing that your data is protected from potential threats.
Netgear C7000 VPN features
Title: Exploring the VPN Capabilities of the Netgear C7000: A Comprehensive Guide
The Netgear C7000 is renowned for its advanced networking features, and among them is its robust VPN (Virtual Private Network) functionality. Designed to enhance security and privacy, the VPN capabilities of the Netgear C7000 offer users a range of benefits.
First and foremost, the VPN feature on the Netgear C7000 provides a secure connection for remote access to your network. Whether you're working from home or accessing sensitive information while traveling, the VPN ensures that your data remains encrypted and protected from prying eyes. This is particularly crucial when using public Wi-Fi networks, where the risk of cyber threats is heightened.
Additionally, the Netgear C7000's VPN feature allows for seamless integration with popular VPN services. Whether you prefer a subscription-based VPN or a custom setup, the router supports various VPN protocols, including PPTP, L2TP, and IPSec, ensuring compatibility with a wide range of providers.
Moreover, the VPN capabilities of the Netgear C7000 extend beyond individual devices to safeguard your entire network. With VPN passthrough support, you can connect multiple devices to the VPN simultaneously without sacrificing speed or performance. This is ideal for households or small businesses seeking to protect all connected devices, including computers, smartphones, and smart home appliances.
Furthermore, the Netgear C7000 offers advanced VPN configuration options, allowing users to customize settings according to their specific requirements. From establishing access controls to configuring VPN tunnels, the router empowers users to tailor their VPN setup for optimal security and performance.
In conclusion, the Netgear C7000's VPN features provide a comprehensive solution for safeguarding your network and ensuring secure remote access. Whether you're a business professional, a remote worker, or a tech-savvy individual, investing in the Netgear C7000 offers peace of mind knowing that your data remains protected in today's increasingly connected world.
Setting up VPN on Netgear C7000
Setting up a VPN (Virtual Private Network) on a Netgear C7000 router provides enhanced security and privacy for your internet connection, safeguarding your online activities from potential threats and prying eyes. With VPN capabilities, you can encrypt your internet traffic and route it through a remote server, effectively masking your IP address and location.
To set up a VPN on your Netgear C7000 router, follow these steps:
Choose a VPN Service: Before configuring your router, select a reliable VPN service provider that offers compatibility with Netgear routers. Ensure they support the OpenVPN protocol, which is commonly used for router configurations.
Access Router Settings: Open a web browser on a device connected to your Netgear C7000 router and enter the router's IP address in the address bar. Log in using your administrator credentials.
Navigate to VPN Settings: Once logged in, locate the VPN settings in the router's admin panel. This might be under the "Advanced" or "Security" tab, depending on the firmware version.
Enter VPN Credentials: Enter the VPN provider's server address, your username, and password in the appropriate fields. These details are typically provided by your VPN service when you sign up.
Configure VPN Protocol: Select the OpenVPN protocol and specify the port number recommended by your VPN provider. You may also need to choose the encryption method and other settings based on your provider's recommendations.
Apply Settings and Reboot: After entering all the necessary information, save the settings and reboot your router to apply the changes.
Connect Devices: Once the router restarts, connect your devices to the network as usual. Your internet traffic will now be encrypted and routed through the VPN server you specified, providing an additional layer of security and privacy.
By setting up a VPN on your Netgear C7000 router, you can enjoy secure and private internet browsing across all your connected devices. Remember to regularly update your router firmware and VPN software for optimal performance and security.
0 notes
Text
does using a vpn on public wifi more secure
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does using a vpn on public wifi more secure
VPN encryption strength
VPN encryption strength is a crucial factor to consider when choosing a virtual private network (VPN) service. Encryption is the process of converting data into a code to prevent unauthorized access. The strength of encryption used by a VPN determines how secure your online activities and data transmissions are.
There are various encryption protocols commonly used by VPN providers, such as OpenVPN, L2TP/IPsec, and IKEv2/IPsec. These protocols differ in the level of encryption they offer, with OpenVPN generally being considered the most secure due to its robust encryption algorithms.
When evaluating VPN encryption strength, it is essential to look at the length of the encryption key and the encryption algorithm used. The longer the encryption key, the harder it is for hackers to decrypt the data. AES (Advanced Encryption Standard) with 256-bit key length is currently the industry standard for VPN encryption and is virtually unbreakable.
A strong VPN encryption ensures that your online communications, sensitive information, and browsing activities remain private and secure from prying eyes, such as hackers, government surveillance, and internet service providers. It is particularly important when accessing public Wi-Fi networks, where cyber threats are more prevalent.
In conclusion, VPN encryption strength plays a vital role in safeguarding your online privacy and security. When choosing a VPN service, opt for one that offers robust encryption protocols with a high level of security, such as AES-256 encryption. By doing so, you can enjoy peace of mind knowing that your digital footprint is well-protected.
Public Wi-Fi security risks
Public Wi-Fi has become a ubiquitous amenity in cafes, airports, hotels, and other public spaces, offering convenient internet access to users on the go. However, amidst the convenience lies a hidden threat: security risks associated with connecting to these networks.
One of the primary dangers of public Wi-Fi is the potential for interception of sensitive information. Because these networks are often unsecured or poorly secured, cybercriminals can easily intercept data transmitted between a user's device and the Wi-Fi hotspot. This includes passwords, credit card numbers, and other personal or financial information, leaving users vulnerable to identity theft and financial fraud.
Another risk is the presence of rogue hotspots, which masquerade as legitimate Wi-Fi networks but are actually set up by hackers to capture users' data. Unsuspecting individuals may connect to these rogue networks, unknowingly exposing their information to cybercriminals.
Additionally, public Wi-Fi networks are often crowded and unregulated, making them breeding grounds for malware and other cyber threats. Malicious actors can deploy malware onto these networks, infecting the devices of unsuspecting users and compromising their security.
To mitigate these risks, users should take proactive measures to protect themselves when using public Wi-Fi. This includes avoiding the transmission of sensitive information, using a virtual private network (VPN) to encrypt data traffic, and keeping devices updated with the latest security patches and antivirus software.
Ultimately, while public Wi-Fi offers convenience, users must remain vigilant and take steps to safeguard their personal and financial information from the numerous security threats lurking on these networks.
VPN tunneling protocols
VPN tunneling protocols are essential components of Virtual Private Networks (VPNs) that ensure secure and private communication over the internet. These protocols establish the rules and procedures for encapsulating and encrypting data as it travels between a user's device and the VPN server.
One of the most commonly used VPN tunneling protocols is OpenVPN, known for its open-source nature, high level of security, and the ability to traverse firewalls and network address translation (NAT) devices. Another popular protocol is IPSec (Internet Protocol Security), which provides secure communication through encryption and authentication methods.
L2TP (Layer 2 Tunneling Protocol) and its extension, L2TP/IPSec, combine the features of L2TP and IPSec to offer a robust and secure tunneling protocol for VPN connections. SSTP (Secure Socket Tunneling Protocol) is another option that utilizes the SSL/TLS protocol for secure communication, making it ideal for Windows users.
PPTP (Point-to-Point Tunneling Protocol) is one of the oldest tunneling protocols but is now considered less secure compared to newer options like OpenVPN or IPSec. However, PPTP is still widely supported and easy to set up on various devices.
Choosing the right VPN tunneling protocol depends on factors such as security needs, device compatibility, and ease of configuration. While some protocols offer higher levels of security, others prioritize speed and simplicity. Understanding the differences between these protocols can help users make informed decisions when selecting a VPN service for their online privacy and security needs.
Secure VPN configurations
Title: Best Practices for Secure VPN Configurations
In today's digital landscape, ensuring secure virtual private network (VPN) configurations is paramount for safeguarding sensitive data and maintaining privacy online. VPNs serve as a crucial tool for encrypting internet traffic and establishing secure connections over public networks. However, to maximize their effectiveness, it's essential to implement the following best practices for secure VPN configurations:
Strong Encryption Protocols: Utilize robust encryption protocols such as AES (Advanced Encryption Standard) with 256-bit keys to encrypt data transmitted through the VPN tunnel. Strong encryption ensures that even if intercepted, the data remains unreadable to unauthorized parties.
Multi-Factor Authentication (MFA): Implement multi-factor authentication to add an extra layer of security beyond just username and password. MFA typically involves a combination of something the user knows (password), something they have (token or smartphone), and something they are (biometric authentication).
Regular Software Updates: Keep VPN software and firmware up to date to patch vulnerabilities and protect against known security threats. Regular updates ensure that the VPN infrastructure remains resilient against evolving cybersecurity risks.
Secure VPN Client Configuration: Configure VPN clients securely by disabling unnecessary features and limiting access privileges. Additionally, enforce strong password policies for VPN client accounts to prevent unauthorized access.
Network Segmentation: Segment the network infrastructure to isolate VPN traffic from other network segments. This helps prevent lateral movement by attackers in the event of a breach and minimizes the potential impact of a security incident.
Log and Monitor VPN Activity: Enable logging and monitoring of VPN activity to detect and respond to suspicious behavior or unauthorized access attempts promptly. Monitoring VPN traffic provides valuable insights into potential security threats and helps maintain compliance with regulatory requirements.
By adhering to these best practices for secure VPN configurations, organizations can mitigate risks associated with remote access and ensure the confidentiality, integrity, and availability of their data and network resources. Investing in robust VPN security measures is essential for safeguarding sensitive information and maintaining trust in an increasingly connected world.
VPN versus public Wi-Fi vulnerabilities
When it comes to staying safe online, many people turn to virtual private networks (VPNs) or public Wi-Fi networks. However, both options come with their own set of vulnerabilities that users should be aware of.
Public Wi-Fi networks, such as those found in cafes, airports, and hotels, are convenient but can pose significant security risks. These networks are typically unencrypted, meaning that cybercriminals can easily intercept the data being transmitted between your device and the network. This leaves your personal information, such as passwords and credit card details, vulnerable to being stolen.
On the other hand, VPNs are designed to create a secure encrypted tunnel between your device and the internet. This encryption helps protect your data from prying eyes and is especially useful when using public Wi-Fi networks. However, not all VPNs are created equal, and some may still have vulnerabilities that could potentially be exploited by hackers.
It is essential for users to understand the limitations of both options and take steps to enhance their online security. When using public Wi-Fi, it is crucial to avoid accessing sensitive information such as online banking or entering passwords. Instead, consider using a VPN to add an extra layer of protection.
In conclusion, while both VPNs and public Wi-Fi networks have their vulnerabilities, using a combination of both can help enhance your online security. By being aware of the risks and taking appropriate precautions, you can enjoy a safer and more secure online experience.
0 notes
Text
will a vpn protect me on public wifi
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
will a vpn protect me on public wifi
VPN encryption strength
VPN encryption strength is a crucial factor to consider when choosing a Virtual Private Network (VPN) service. Encryption is the method used to secure the data that is transmitted between your device and the VPN server. The strength of the encryption determines how difficult it is for unauthorized parties to intercept and decipher your data.
There are several encryption protocols used by VPN services, with varying levels of strength and security. The most common protocols include OpenVPN, L2TP/IPsec, IKEv2/IPsec, and SSTP. Of these, OpenVPN is widely regarded as the most secure option due to its strong encryption standards and open-source nature, allowing for regular security audits and updates.
When evaluating VPN encryption strength, it is important to consider the key length and encryption algorithm used. The key length refers to the size of the encryption key, with longer keys being more secure but potentially slower. Common key lengths include 128-bit, 192-bit, and 256-bit. The encryption algorithm, such as AES (Advanced Encryption Standard), is used to scramble the data and protect it from unauthorized access.
A VPN with strong encryption, such as AES-256 bit encryption, ensures that your online activities are secure and protected from hackers, government surveillance, and other prying eyes. It is recommended to choose a VPN provider that uses the highest encryption standards available to safeguard your sensitive information and maintain your privacy while browsing the internet. By prioritizing VPN encryption strength, you can enjoy a secure and private online experience without compromising on speed or performance.
Public Wi-Fi security risks
Title: The Hidden Dangers of Public Wi-Fi: Safeguarding Your Data in an Unsecured World
In today's digitally connected world, public Wi-Fi hotspots have become ubiquitous, offering convenience and accessibility to users on the go. However, amidst the convenience lies a lurking threat: security risks that could compromise your sensitive information.
One of the primary dangers of public Wi-Fi is the lack of encryption. Unlike secure networks at home or in the office, public Wi-Fi hotspots often lack encryption protocols, leaving data transmitted over these networks vulnerable to interception by cybercriminals. This means that any personal information, such as passwords, credit card details, or browsing history, could be intercepted by malicious actors prowling the same network.
Furthermore, the impersonation of legitimate Wi-Fi networks, known as "evil twin" attacks, is another prevalent risk in public Wi-Fi environments. Cybercriminals can set up rogue access points with names similar to legitimate networks, tricking unsuspecting users into connecting to them. Once connected, these attackers can intercept data or deploy malware onto users' devices, compromising their security and privacy.
Moreover, public Wi-Fi networks are often poorly maintained and lack robust security measures, making them easy targets for cyber attacks. Hackers can exploit vulnerabilities in these networks to launch various attacks, including man-in-the-middle attacks, where they intercept communications between users and websites to steal sensitive information.
To mitigate the risks associated with public Wi-Fi, users must take proactive measures to safeguard their data. Utilizing virtual private networks (VPNs) can encrypt data transmitted over public networks, providing an additional layer of security. Additionally, users should avoid accessing sensitive information or conducting financial transactions while connected to public Wi-Fi and regularly update their devices with the latest security patches to defend against potential threats.
In conclusion, while public Wi-Fi offers convenience, it also poses significant security risks to unsuspecting users. By understanding these risks and implementing proactive security measures, individuals can better protect their sensitive information in an increasingly unsecured digital landscape.
VPN tunneling protocols
VPN tunneling protocols are the backbone of secure and private internet connections, ensuring data integrity and confidentiality. These protocols establish a secure pathway, or tunnel, between the user's device and the VPN server, encrypting data traffic to prevent unauthorized access or interception.
One of the most commonly used VPN tunneling protocols is OpenVPN, known for its robust security features and flexibility. OpenVPN utilizes open-source technology, making it highly customizable and adaptable to various network configurations. It operates on the Transport Layer Security (TLS) protocol, providing strong encryption and authentication mechanisms.
Another widely used protocol is Internet Protocol Security (IPsec), which operates at the network layer of the OSI model. IPsec can be implemented in two modes: Transport Mode and Tunnel Mode. In Tunnel Mode, the entire IP packet is encrypted and encapsulated within a new IP packet, providing a higher level of security suitable for VPN connections.
Layer 2 Tunneling Protocol (L2TP) is another popular choice, often used in conjunction with IPsec to enhance security. L2TP doesn't provide encryption on its own but relies on IPsec for data confidentiality. It's commonly supported across various operating systems and devices, making it a versatile option for VPN connections.
Point-to-Point Tunneling Protocol (PPTP) was once widely used due to its simplicity and ease of configuration. However, its security vulnerabilities have led to its decline in popularity, with many VPN providers discontinuing support for it in favor of more secure alternatives.
In conclusion, VPN tunneling protocols play a crucial role in ensuring the security and privacy of internet communications. By encrypting data traffic and establishing secure pathways, these protocols enable users to browse the internet safely and anonymously, protecting sensitive information from prying eyes.
VPN logging policies
VPN logging policies are an essential factor to consider when choosing a virtual private network (VPN) service. VPN logging refers to the practice of recording user activity while connected to the VPN. It is crucial to understand a VPN provider's logging policies as they can impact your online privacy and security.
There are generally three types of VPN logging policies: no-logs, minimal logs, and extensive logs. A no-logs policy means that the VPN provider does not collect or store any user activity data. This is the most privacy-friendly option as it ensures that no information about your online behavior is kept on record.
On the other hand, minimal logs policies involve collecting only essential information for managing the VPN service, such as account information and payment details. While this may be necessary for operational purposes, it still poses a certain level of risk to user privacy as some data is stored.
Extensive logs policies involve recording detailed information about user activity, including browsing history, IP addresses, and timestamps. This type of logging is the most intrusive to user privacy and can potentially expose sensitive data to third parties.
When deciding on a VPN service, it is crucial to review and understand the provider's logging policies before making a decision. Opting for a VPN with a strict no-logs policy is recommended for those seeking maximum privacy and security while browsing the internet. Remember that the more data a VPN provider logs, the higher the potential risk to your online anonymity and privacy.
VPN data encryption methods
VPN (Virtual Private Network) services have become increasingly popular as individuals and businesses seek to safeguard their online privacy and security. One of the key features that make VPNs effective in protecting data is their use of encryption methods.
Encryption is the process of encoding data in such a way that only authorized parties can access it. In the context of VPNs, data encryption plays a crucial role in ensuring that the information transmitted over the network remains confidential and secure from potential threats such as hackers, government surveillance, or data breaches.
There are several encryption methods commonly used by VPN providers to secure data:
AES (Advanced Encryption Standard): AES is widely regarded as one of the most secure encryption algorithms available today. It uses symmetric-key encryption, meaning the same key is used for both encryption and decryption. VPNs often employ AES with key lengths of 128-bit, 192-bit, or 256-bit, with 256-bit being the most secure option.
RSA (Rivest-Shamir-Adleman): RSA is an asymmetric encryption algorithm commonly used for key exchange in VPN protocols such as OpenVPN and IKEv2/IPSec. It relies on the use of public and private keys, with data encrypted using the public key and decrypted using the corresponding private key.
DH (Diffie-Hellman): Diffie-Hellman is another key exchange protocol used by VPNs to establish a secure connection between the client and the server. It allows the two parties to agree upon a shared secret key without explicitly transmitting it over the network, thereby preventing eavesdropping.
SHA (Secure Hash Algorithm): SHA is a cryptographic hash function used for data integrity verification. VPNs often use SHA to ensure that transmitted data has not been tampered with during transit.
By employing a combination of these encryption methods, VPN providers can offer users a high level of security and privacy when browsing the internet or accessing sensitive information online. However, it's essential for users to choose a reputable VPN service that implements robust encryption standards to ensure their data remains protected.
0 notes
Text
do vpn networks protect against public wifi
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
do vpn networks protect against public wifi
Benefits of VPN for public WiFi security
Using a Virtual Private Network (VPN) is essential for maintaining security when connecting to public WiFi networks. Public WiFi hotspots are inherently more vulnerable to cyber threats due to their lack of encryption and the presence of potential hackers. VPNs offer a layer of protection by encrypting your internet connection, making it difficult for cybercriminals to intercept your data.
One of the primary benefits of using a VPN on public WiFi is data encryption. VPNs encrypt your internet traffic, preventing unauthorized access to your personal information such as passwords, credit card details, and browsing history. This encryption ensures that even if someone manages to intercept your data, they won't be able to decipher it.
Moreover, VPNs provide anonymity and privacy by masking your actual IP address. When you connect to a public WiFi network without a VPN, your online activities can be easily traced back to your device. However, with a VPN, your IP address is hidden, making it harder for advertisers, internet service providers, and hackers to monitor your online behavior.
Additionally, VPNs allow you to bypass geographical restrictions on content while using public WiFi. Some websites and services may be blocked in certain countries or regions, but a VPN can help you access them securely and anonymously.
In conclusion, the benefits of using a VPN for public WiFi security are clear. By encrypting your data, ensuring anonymity, and bypassing restrictions, VPNs provide a crucial layer of protection when connecting to public networks. It is essential to prioritize your online security and privacy, especially when using public WiFi, and a VPN is an effective tool in achieving that.
Risks of using public WiFi without a VPN
Using public WiFi networks without a Virtual Private Network (VPN) can expose users to various risks that compromise their online security and privacy. Public WiFi hotspots, such as those found in cafes, airports, and hotels, are convenient for staying connected on the go, but they lack the encryption and security measures present in private networks.
One of the primary risks of using public WiFi without a VPN is the potential for data interception by cybercriminals. Without encryption, sensitive information transmitted over the network, such as login credentials, financial details, and personal messages, can be intercepted by hackers. This can lead to identity theft, financial fraud, and unauthorized access to accounts.
Furthermore, public WiFi networks are often unsecured, making them susceptible to various types of cyber attacks, including man-in-the-middle attacks and packet sniffing. In a man-in-the-middle attack, a hacker intercepts communication between two parties, allowing them to eavesdrop on conversations or manipulate data exchanged between them. Packet sniffing involves capturing data packets transmitted over the network, enabling attackers to extract sensitive information from them.
Additionally, public WiFi networks are sometimes set up by cybercriminals posing as legitimate providers, a tactic known as rogue WiFi hotspots. Users unknowingly connect to these malicious networks, allowing attackers to monitor their online activities, inject malware into their devices, or steal their data.
By using a VPN, users can mitigate these risks by encrypting their internet traffic and establishing a secure connection to a remote server. This encrypts data transmitted over the network, making it unreadable to unauthorized parties and ensuring privacy and security while browsing on public WiFi networks. Overall, using a VPN is essential for protecting sensitive information and safeguarding against cyber threats when using public WiFi.
How VPN encryption secures public WiFi connections
Public WiFi networks are convenient for staying connected on the go, but they come with significant security risks. Without proper protection, sensitive data transmitted over these networks can be intercepted by cybercriminals. This is where VPN encryption plays a crucial role in safeguarding your online activities.
VPN, or Virtual Private Network, encrypts your internet connection, creating a secure tunnel between your device and the VPN server. When you connect to a public WiFi network, all data transmitted between your device and the internet passes through this encrypted tunnel. This encryption ensures that even if someone manages to intercept your data, they won't be able to decipher its contents.
One of the primary encryption protocols used by VPNs is AES (Advanced Encryption Standard). AES employs complex algorithms to scramble data into an unreadable format, which can only be decrypted with the correct encryption key. With AES encryption, your online activities, such as browsing the web, sending emails, or accessing sensitive information, remain private and secure.
Additionally, VPNs utilize other security features like tunneling protocols (such as OpenVPN, L2TP/IPsec, or IKEv2/IPsec) to further enhance protection. These protocols establish the rules for how data is transmitted through the VPN tunnel, adding layers of security to your connection.
By encrypting your data and routing it through a secure tunnel, VPNs prevent unauthorized access and protect your privacy on public WiFi networks. Whether you're browsing in a coffee shop, airport, or hotel, using a VPN ensures that your sensitive information remains confidential and shielded from prying eyes. With the increasing prevalence of cyber threats, investing in a reliable VPN service is essential for maintaining your online security and peace of mind.
VPN versus public WiFi security
Using a Virtual Private Network (VPN) is becoming increasingly crucial in today's digital age, where cyber threats are rampant, especially when connecting to public WiFi networks. While public WiFi is convenient and often free, it poses significant risks to your online security and privacy. When you connect to a public WiFi network, your data is essentially traveling through an unprotected channel, making it vulnerable to hackers and cybercriminals who may intercept your information.
On the other hand, a VPN creates a secure and encrypted connection between your device and the internet, ensuring that your data remains private and protected from prying eyes. By routing your internet traffic through a remote server, VPNs help to mask your IP address and encrypt your data, making it incredibly difficult for hackers to access or steal your information.
When comparing VPN versus public WiFi security, it is clear that VPNs offer far superior levels of protection. With a VPN, you can browse the internet with peace of mind, knowing that your online activities are shielded from potential threats. Whether you are checking your emails, conducting online banking transactions, or simply browsing the web, using a VPN on public WiFi is essential to safeguarding your sensitive data.
In conclusion, while public WiFi may be convenient, it comes with inherent security risks that should not be taken lightly. Investing in a reliable VPN service is a proactive step towards enhancing your online security and privacy, allowing you to enjoy the benefits of public WiFi without compromising your personal information.
Importance of using a VPN on public WiFi
Using a VPN on public WiFi is crucial to ensure your online safety and privacy. Public WiFi networks are commonly found in places like coffee shops, airports, and hotels, making it convenient for people to connect to the internet while on the go. However, these networks are prime targets for hackers who can easily intercept your data and potentially gain access to sensitive information.
A VPN, or Virtual Private Network, encrypts your internet connection and reroutes it through a secure server, masking your IP address and making your online activities virtually untraceable. This added layer of security is especially important when using public WiFi, as it prevents unauthorized users from monitoring your browsing habits or stealing your personal data, such as login credentials, credit card information, and private messages.
In addition to safeguarding your personal information, using a VPN on public WiFi also enables you to bypass geo-restrictions and access websites and services that may be blocked in certain regions. Whether you're traveling abroad and want to stream your favorite TV shows or simply value your online privacy, a VPN provides you with the freedom and peace of mind to browse the internet safely and anonymously.
Overall, the importance of using a VPN on public WiFi cannot be overstated. By taking proactive measures to protect your online identity and data, you can enjoy a secure and worry-free browsing experience wherever you go.
0 notes
Text
does vpn protect data on public wifi
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does vpn protect data on public wifi
VPN encryption process
VPN encryption is a crucial component in ensuring online security and privacy while browsing the internet. Understanding the encryption process that VPNs use can help users make informed decisions when selecting a service provider.
When data is transmitted over the internet, it is vulnerable to interception by hackers and unauthorized third parties. VPNs employ encryption to scramble this data, making it unreadable to anyone without the proper decryption key. This process involves encoding the data with complex mathematical algorithms, essentially turning it into gibberish to anyone trying to intercept it.
The encryption process begins when a user connects to a VPN server. The user's device encrypts the data before sending it to the server through a secure tunnel. The server decrypts the data and forwards it to the intended destination on the internet. Any responses from the destination are encrypted by the server and sent back to the user, who can then decrypt the data on their end.
There are different types of encryption protocols used by VPNs, such as OpenVPN, L2TP/IPsec, and IKEv2. Each protocol offers varying levels of security and speed, allowing users to choose the one that best fits their needs.
In conclusion, VPN encryption plays a vital role in safeguarding online communications and data. By understanding the encryption process and the different protocols available, users can make informed choices to protect their online privacy and security effectively.
Public WiFi security risks
Title: Understanding the Risks of Public WiFi and How to Stay Secure
Public WiFi networks are a convenient way to stay connected while on the go, offering internet access in places like cafes, airports, hotels, and libraries. However, the convenience comes with inherent security risks that users need to be aware of to protect their sensitive information.
One of the primary risks of public WiFi is the lack of encryption, making it easier for hackers to intercept data transmitted between your device and the WiFi hotspot. This means that any information you send or receive, such as passwords, emails, or financial transactions, could be vulnerable to interception by cybercriminals.
Another common threat is the presence of rogue WiFi hotspots, which are set up by hackers to mimic legitimate networks. When users unknowingly connect to these rogue networks, their data can be intercepted, leading to identity theft, financial fraud, or malware infection.
Man-in-the-middle (MITM) attacks are also a concern on public WiFi networks, where attackers intercept communication between two parties, potentially altering or eavesdropping on the data being exchanged.
To mitigate these risks and protect your data while using public WiFi, consider the following precautions:
Use a virtual private network (VPN) to encrypt your internet connection and keep your data secure from prying eyes.
Avoid accessing sensitive information, such as online banking or shopping, while connected to public WiFi networks.
Ensure that the WiFi network you're connecting to is legitimate by verifying the network name and asking staff if in doubt.
Keep your device's software and security patches up to date to minimize vulnerabilities that could be exploited by attackers.
By staying vigilant and taking proactive measures to safeguard your data, you can enjoy the convenience of public WiFi without compromising your security and privacy.
VPN data protection benefits
In today's digitally interconnected world, safeguarding your online privacy is paramount. Virtual Private Networks (VPNs) offer a robust solution to protect your sensitive data from prying eyes and potential security breaches. Let's delve into the myriad benefits of using a VPN for data protection.
First and foremost, VPNs encrypt your internet connection, ensuring that all data transmitted between your device and the VPN server is secure and inaccessible to hackers or third parties. This encryption acts as a shield, making it virtually impossible for anyone to intercept or decipher your online activity.
Moreover, VPNs provide anonymity by masking your IP address and replacing it with one from the VPN server. This cloaks your online identity, preventing websites, advertisers, and even your internet service provider from tracking your browsing habits or monitoring your location.
In addition to enhancing privacy, VPNs offer protection against cyber threats such as malware, phishing scams, and man-in-the-middle attacks. By routing your internet traffic through encrypted tunnels, VPNs create a barrier that blocks malicious actors from infiltrating your device or stealing sensitive information.
Furthermore, VPNs enable secure access to restricted content and bypass geo-blocks by allowing you to connect to servers located in different regions. Whether you're traveling abroad or seeking access to region-locked websites or streaming services, a VPN grants you unrestricted internet freedom.
Overall, the benefits of VPN data protection are undeniable. From safeguarding your privacy and anonymity to fortifying your online security and accessing geo-restricted content, VPNs are indispensable tools in today's digital age. By investing in a reliable VPN service, you can enjoy peace of mind knowing that your sensitive data remains safe and secure, regardless of where you browse the web.
Cybersecurity on unsecured networks
Cybersecurity on unsecured networks is a pressing concern in today's digital landscape. With the proliferation of Wi-Fi hotspots in public spaces, homes, and workplaces, the risk of data breaches and cyberattacks has escalated dramatically. Unsecured networks lack encryption protocols, making them vulnerable to interception by malicious actors seeking to exploit sensitive information.
One of the primary threats associated with unsecured networks is data interception. Hackers can employ various techniques, such as packet sniffing, to eavesdrop on network traffic and capture valuable data, including login credentials, financial information, and personal details. Without encryption, this data is transmitted in plain text, making it easy for cybercriminals to intercept and misuse.
Another significant risk is the potential for malware infection. Unsecured networks provide fertile ground for malware distribution, as unsuspecting users connect their devices without adequate protection. Malicious software, such as viruses, ransomware, and spyware, can infiltrate devices through unsecured connections, compromising their integrity and compromising sensitive data.
Furthermore, unsecured networks pose a threat to privacy, as they lack safeguards against unauthorized access. Without encryption and authentication mechanisms in place, anyone within range of the network can potentially gain access to connected devices and intercept communications, jeopardizing the confidentiality of personal and business-related information.
To mitigate the risks associated with unsecured networks, users must exercise caution when connecting to unfamiliar or untrusted Wi-Fi networks. Employing virtual private network (VPN) services can encrypt network traffic and provide a secure tunnel for data transmission, safeguarding against interception and unauthorized access. Additionally, maintaining up-to-date antivirus software and practicing good cybersecurity hygiene, such as using strong, unique passwords and enabling two-factor authentication, can help fortify defenses against potential threats on unsecured networks. By remaining vigilant and proactive, individuals and organizations can reduce their exposure to cyber risks and safeguard their digital assets in an increasingly interconnected world.
VPN tunneling technology
VPN tunneling technology plays a crucial role in ensuring secure and private internet connections for users worldwide. Essentially, a VPN (Virtual Private Network) creates a secure "tunnel" between the user's device and the internet, encrypting data and ensuring privacy.
At its core, VPN tunneling involves encapsulating data packets within other data packets, effectively creating a protective layer around the information being transmitted. This encapsulation process occurs at the sender's end, where the original data is encrypted and then encapsulated within a new packet. This packet is then transmitted through the VPN tunnel to the destination server.
One of the key aspects of VPN tunneling is the use of various protocols to establish and maintain these secure connections. Protocols such as OpenVPN, IPSec, L2TP/IPSec, and SSTP are commonly employed to facilitate VPN tunneling, each offering different levels of security and performance.
OpenVPN, for example, is an open-source protocol known for its robust security features and flexibility. IPSec (Internet Protocol Security), on the other hand, is widely used for securing data transmission over IP networks and can operate in tunnel mode to create VPN connections.
L2TP/IPSec combines the Layer 2 Tunneling Protocol (L2TP) with IPSec to provide a highly secure VPN connection, while SSTP (Secure Socket Tunneling Protocol) is developed by Microsoft and is often used for VPN connections in Windows environments.
Overall, VPN tunneling technology serves as a vital tool for individuals and organizations looking to protect their sensitive data and maintain privacy online. By encrypting data and establishing secure connections, VPNs offer peace of mind in an increasingly interconnected digital world.
0 notes
Text
does vpn cover wifi
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does vpn cover wifi
VPN encryption
VPN Encryption: Safeguarding Your Online Privacy
In today's digital age, where online security threats loom large, safeguarding your privacy is paramount. Virtual Private Networks (VPNs) offer a secure solution by encrypting your internet connection, shielding your data from prying eyes. But how does VPN encryption work, and why is it essential?
VPN encryption involves the use of cryptographic techniques to scramble data transmitted between your device and the VPN server. This encryption creates a secure tunnel through which your data travels, making it incomprehensible to anyone attempting to intercept it. Essentially, VPN encryption transforms your data into an unreadable format, ensuring that even if it's intercepted, it remains unintelligible.
There are various encryption protocols used by VPN providers, each offering different levels of security. Some common protocols include OpenVPN, L2TP/IPsec, and IKEv2/IPsec. OpenVPN, known for its open-source nature, is widely regarded as one of the most secure options due to its robust encryption algorithms.
The strength of VPN encryption is measured in bits, with higher-bit encryption providing enhanced security. AES (Advanced Encryption Standard) encryption, available in 128-bit, 192-bit, and 256-bit variations, is among the most secure encryption standards used by VPNs today. The higher the number of bits, the more complex and difficult it becomes for unauthorized parties to decipher the encrypted data.
VPN encryption not only protects your sensitive information, such as passwords, financial details, and personal messages, from hackers and cybercriminals but also shields your online activities from surveillance by internet service providers (ISPs), governments, and other entities.
In conclusion, VPN encryption acts as a robust shield against online threats, ensuring your privacy and security in an increasingly interconnected digital landscape. By encrypting your internet traffic, VPNs provide peace of mind, allowing you to browse the web, stream content, and communicate online with confidence, knowing that your data remains secure and confidential.
Public WiFi security
Public WiFi networks are a convenient way to access the internet while on the go, whether it's at a coffee shop, airport, or hotel. However, they also pose significant security risks if not used cautiously. Understanding how to protect yourself while using public WiFi is essential to safeguard your personal information and privacy.
One of the primary concerns with public WiFi is the risk of data interception. Since these networks are often open and unencrypted, hackers can easily intercept the data being transmitted between your device and the WiFi router. This means that sensitive information such as passwords, credit card numbers, and personal emails could be intercepted and exploited.
To mitigate these risks, there are several steps you can take. Firstly, always avoid accessing sensitive information, such as online banking or shopping, while connected to public WiFi. If you must access such accounts, consider using a virtual private network (VPN) to encrypt your internet connection and protect your data from prying eyes.
Additionally, ensure that your device's security software is up-to-date and configured to detect potential threats. This includes antivirus software and firewall protection, which can help prevent malware and unauthorized access to your device.
Furthermore, be cautious when connecting to public WiFi networks. Avoid connecting to networks with generic or suspicious names, as these could be set up by hackers to trick users into connecting. Instead, opt for networks provided by reputable establishments with secure connections.
In conclusion, while public WiFi offers convenience, it also comes with inherent security risks. By taking proactive measures such as using a VPN, keeping your software updated, and exercising caution when connecting to networks, you can minimize the risk of falling victim to cyber attacks and protect your sensitive information while browsing on public WiFi.
VPN tunneling
VPN tunneling is a crucial aspect of ensuring online privacy and security in today's digital age. This technology allows users to create a secure and encrypted connection over the internet, enabling them to safely transmit data between their device and a remote server.
When a VPN connection is established, all data sent and received is encrypted, making it nearly impossible for hackers, ISPs, or governments to intercept or view the information. This is achieved through a process called tunneling, where data packets are encapsulated within another packet before being transmitted over the internet.
There are different types of VPN tunneling protocols that offer varying levels of security and speed. Some popular protocols include OpenVPN, IPSec, L2TP/IPSec, and PPTP. Each protocol has its own advantages and disadvantages, so users should choose the one that best suits their needs.
VPN tunneling is commonly used by individuals looking to protect their online privacy, access geo-blocked content, or secure their connection while using public Wi-Fi networks. It is also widely implemented by businesses to allow employees to securely access company resources remotely.
In conclusion, VPN tunneling plays a vital role in safeguarding sensitive information and ensuring online anonymity. By encrypting data transmissions and creating a secure connection, VPNs offer users peace of mind when navigating the vast expanse of the internet.
WiFi network protection
Title: Safeguarding Your WiFi Network: Essential Tips for Protection
In an age where connectivity is paramount, ensuring the security of your WiFi network is non-negotiable. From sensitive personal data to confidential work files, your network holds a plethora of information that could be vulnerable to cyber threats if left unprotected. Here are some indispensable tips to fortify your WiFi network and keep it safe from potential breaches:
Strong Passwords: Start with the basics by setting a robust password for your WiFi router. Avoid common phrases or easily guessable combinations. Opt for a mix of uppercase and lowercase letters, numbers, and symbols to enhance its complexity.
Encryption: Enable encryption protocols such as WPA2 (WiFi Protected Access 2) or WPA3 to encrypt the data transmitted over your network. This adds an extra layer of security, making it more challenging for unauthorized users to intercept and decipher your information.
Network Name (SSID) Concealment: Conceal your network's SSID to prevent it from being broadcasted publicly. While this won't provide foolproof protection, it can deter casual hackers from targeting your network.
Firewall Installation: Install and configure a firewall to monitor and control incoming and outgoing network traffic. Firewalls act as barriers between your internal network and external threats, filtering out potentially harmful data packets.
Regular Updates: Keep your router's firmware up-to-date to patch any known vulnerabilities. Manufacturers often release firmware updates to address security flaws and improve overall performance, so be sure to check for updates periodically.
Guest Network: Set up a separate guest network for visitors to use instead of granting them access to your primary network. This minimizes the risk of unauthorized users gaining access to your sensitive data.
VPN Usage: Consider using a Virtual Private Network (VPN) to encrypt your internet traffic and mask your IP address. VPNs provide an additional layer of security, particularly when accessing public WiFi networks outside your home.
By implementing these proactive measures, you can significantly reduce the risk of your WiFi network falling victim to cyber threats and safeguard your digital assets effectively. Remember, staying vigilant and staying ahead of potential vulnerabilities is key to maintaining a secure online environment.
VPN for WiFi privacy
Title: Safeguard Your WiFi Privacy with a VPN
In today's digital age, where virtually every aspect of our lives is intertwined with the internet, ensuring privacy and security online has become paramount. One area often overlooked is the security of our WiFi connections. Public WiFi networks, in particular, pose significant risks to our privacy, as they are often unsecured and susceptible to hackers. This is where a Virtual Private Network (VPN) comes into play.
A VPN encrypts your internet connection, creating a secure and private tunnel between your device and the internet. When you connect to a public WiFi network, your data is encrypted and routed through the VPN server, preventing hackers and other malicious actors from intercepting your sensitive information.
One of the primary benefits of using a VPN for WiFi privacy is the protection it provides against snooping and monitoring. Without a VPN, your online activities, including browsing history, passwords, and personal information, can be easily intercepted by cybercriminals lurking on the same network. With a VPN, however, your data remains encrypted and unreadable to anyone trying to eavesdrop on your connection.
Moreover, VPNs also allow users to bypass geographic restrictions and censorship imposed by certain websites or governments. By masking your IP address and rerouting your connection through servers located in different countries, VPNs enable you to access content that may be blocked in your region, thereby preserving your freedom and privacy online.
In conclusion, if you value your privacy and security while using public WiFi networks, investing in a reliable VPN service is essential. By encrypting your connection and masking your IP address, VPNs provide an additional layer of protection against cyber threats and ensure that your online activities remain private and secure. Stay safe and enjoy peace of mind knowing that your WiFi privacy is safeguarded with a VPN.
0 notes