#institute of ethical hacking
Explore tagged Tumblr posts
Text
The Role of Ethical Hacking in Preventing Cyberattacks
As cyberthreats change, ethical hacking has become essential to thorough security measures in many businesses. Through bug bounty programs, companies such as Google and Facebook aggressively use ethical hackers to find vulnerabilities in their systems. The proactive approach of ethical hacking promotes a security-conscious culture within businesses and helps avoid expensive data breaches. To safeguard sensitive data, ethical hackers continuously evaluate and enhance security protocols in our Ethical Hacking Course in Bangalore.

What Ethical Hacking Means
"Ethical hacking" refers to techniques that are permissible for identifying vulnerabilities in systems, networks, and applications. In the late 1990s, this discipline began to gain traction as companies realized they needed to implement proactive security measures. By employing the same methods as authorized hostile hackers, ethical hackers also referred to as "white-hat" hackers improve security.
Ethical hacking has a promising future. Ethical hackers will use increasingly sophisticated techniques to identify vulnerabilities as AI and machine learning proliferate. As cyberthreats continue to rise, it will become increasingly important for businesses to hire ethical hackers who can stop these attacks.
The benefits of ethical hacking in cybersecurity
1. Evaluating the Present Dangers
System vulnerabilities are found via ethical hacking before malevolent hackers may take use of them. The likelihood of expensive data breaches is greatly decreased by this proactive strategy. By fixing vulnerabilities with penetration testing tools like Metasploit or Burp Suite, businesses can save a significant amount of money.
2. Better Security Posture
Regular ethical hacking assessments strengthen a company's overall security posture. With the assistance of knowledgeable ethical hackers, organizations can conduct red team exercises that mimic real attacks. Organizations can increase their resistance to changing cyberthreats by routinely testing and fortifying security measures. Effective protections against such threats are maintained by this ongoing upgrade.
3. Respect for the law
Businesses can utilize ethical hacking to comply with regulations like GDPR and HIPAA. Businesses may stay out of trouble and safeguard their reputation by adhering to these rules. Compliance demonstrates a commitment to protecting confidential data and maintaining customer trust. Our Software Training Institute needs ethical hacking testing on a regular basis to find security vulnerabilities and guarantee compliance.
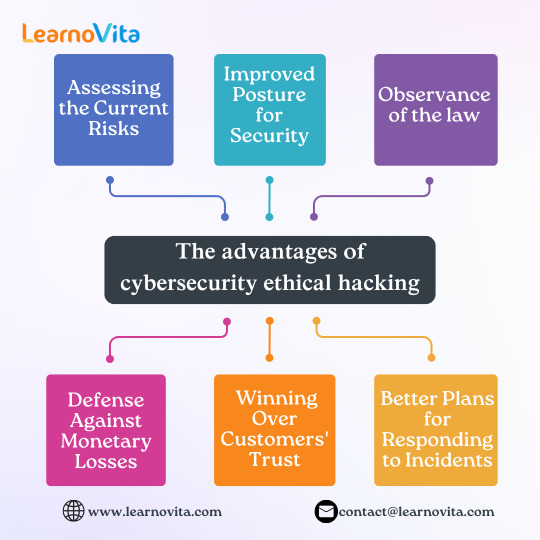
4. Protection Against Financial Losses
Data breaches can cost organizations millions of dollars in lost revenue and recovery expenses. Ethical hacking raises awareness of vulnerabilities by identifying and fixing them before attackers may exploit them. This preventive measure ultimately protects the organization's financial stability.
5. Gaining the Trust of Customers
Customer loyalty and trust are increased when ethical hacking is used to demonstrate a commitment to cybersecurity. Customers are more likely to engage with businesses who secure their data proactively. Regular security audits must be encouraged in order to reassure clients that their data is safe. Building a reputation for reliability and accountability also includes managing sensitive data.
6. Improved Incident Response Plans
Ethical hacking allows companies to assess their incident response plans by mimicking real attacks. This practice helps identify weaknesses in reaction strategy. It also assists businesses in strengthening their processes to make them more resilient to threats.
Conclusion
The role that ethical hackers play in protecting digital assets cannot be overstated. The cyber security network that strengthens an organization's cyber security policies and creates new ways to improve them depends on them. If you want to be sure that you will have a lot of possibilities after you graduate, you must earn this degree from an accredited university. There are currently several different cyber security certification programs available. However, nothing compares to a degree program for expanding your knowledge and skill set. Do the necessary research and pick a school that can provide you with thorough cyber security training. The future is bright for professionals who possess the necessary education and experience in this field.
1 note
·
View note
Text
Best Ethical Hacking Institute in Delhi – NEW DELHI YMCA IMSIT
Enhance your cybersecurity expertise with the best ethical hacking institute in delhi at NEW DELHI YMCA IMSIT. This one-year diploma in Cyber Security and Ethical Hacking covers key topics like vulnerability assessment, penetration testing, cryptography, firewall configuration, OS security, and monitoring—geared for 10+2 pass students, graduates, and professionals. Learn through practical, project-based training under experienced instructors. Join to build essential skills for roles in cybersecurity and network defense. Start your ethical hacking journey now.
0 notes
Text
Master Cybersecurity with the Best Ethical Hacking Training Institute in Delhi
Choosing the right ethical hacking training institute in Delhi can be a game-changer for your career. With a growing emphasis on cybersecurity, ethical hackers are becoming indispensable across industries.
0 notes
Text
Indian Institute of Computer Science (IICS) is Delhi's leading IT training institute, offering a wide range of affordable programs and courses to empower learners with essential technology skills. With expert instructors and practical training in areas like AI, programming, web development, and more, we aim to prepare students for thriving careers in the tech industry. Join us to build your future in IT!best software engineer courses in Delhi
#Graphic Designer Course in Delhi#Best ethical hacking institute in Delhi#best cyber security institute in delhi#Web Development Course in Delhi#Advanced computer institute Delhi#Multimedia and Animation Classes in Delhi#IT training institute in delhi#Computer Courses and Classes in Delhi#Best e-accounting institute in Delhi#computer course with placement#Best computer education institute in Delhi
0 notes
Text
Ethical Hacking Institute in Delhi – Practical Cyber Security at YMCA IMSIT
Join the leading Ethical Hacking Institute in Delhi at NEW DELHI YMCA IMSIT and gain industry-ready cyber security skills. This course covers network security, ethical hacking tools, penetration testing, and cyber law essentials. Ideal for aspiring cybersecurity professionals, IT students, and tech enthusiasts, it provides hands-on lab sessions and expert-led modules. Start your career in ethical hacking with certifications that can boost your job prospects in both the private and government sectors.
0 notes
Text

Get professional CEH Training in Jaipur with Cyber Crime Awareness Society and build a strong foundation in ethical hacking and cybersecurity. Learn from certified experts and prepare for the globally recognized CEH certification. Ideal for students and IT professionals aiming to excel in cybersecurity. Contact: 97842 68547 for more information and registration!
0 notes
Text

#ethical hacking training institutes in patna#networking ccna training institutes in patna#digital marketing training in patna#autocad training in patna#summer training patna#software training institutes in patna#education#training#patna#bihar
0 notes
Text
Cybersecurity Education: Your Path to Becoming a Digital Guardian in an Ever-Changing Landscape
In an era dominated by digital technologies, the importance of cybersecurity has never been greater. As cyber dangers and attacks proliferate, the requirement for qualified professionals capable of protecting against them grows. In this article, we look at how cybersecurity education can help individuals become digital guardians in an ever-changing landscape of cyber threats.
The Growing Importance of Cybersecurity:
With the fast proliferation of digital infrastructure and the increasing interconnection of systems, potential vulnerabilities and dangers have grown dramatically. Organizations in all industries confront ongoing risks to their digital assets, ranging from large-scale data breaches to sophisticated ransomware assaults. As a result, there is an urgent demand for skilled cybersecurity specialists who can predict, detect, and successfully neutralize these risks.
Cybersecurity Education: Laying the Groundwork:
Cybersecurity education sets the framework for individuals to obtain the skills and knowledge required to address the wide range of difficulties provided by cyber attacks. Students learn about basic concepts like network security, cryptography, threat analysis, and incident response through comprehensive training programmes. Furthermore, they learn about emerging technologies and dynamic attack vectors, which prepares them to respond to changing threat landscapes.
Practical Experience and Hands-on Learning:
One of the distinguishing features of cybersecurity education is the emphasis on practical experience and hands-on learning. Students can use their theoretical understanding in real-world circumstances by modeling cyber attacks and defense techniques in controlled conditions. By participating in practical exercises including penetration testing, vulnerability assessments, and forensic analysis, students gain vital skills that may be applied directly to industry.
Specialization and certification:
Cybersecurity education provides a wide number of specialization options, allowing students to personalize their learning experience to their specific interests and professional aspirations. Whether they specialize in network security, cloud security, ethical hacking, or digital forensics, students can pursue certificates and qualifications that confirm their cybersecurity skills. These qualifications not only boost credibility, but they also strengthen employment prospects in a competitive labor environment.
Addressing the skill gap:
Despite the increasing demand for cybersecurity workers, there is a major skills gap in the business. Individuals who invest in cybersecurity education not only position themselves for profitable career prospects, but they also help to close the essential skills gap. Cybersecurity experts play an important role in boosting organizations' overall security posture and protecting digital assets from changing threats by engaging in continuous learning and professional development.
Conclusion:
In conclusion, cybersecurity education is the foundation for those seeking to become digital guardians in an ever-changing landscape of cyber threats. Students who get the necessary information, skills, and certifications can pursue rewarding jobs in cybersecurity, where they play an important role in defending against malicious actors and protecting the integrity of digital systems. As technology advances, the demand for qualified cybersecurity experts will grow, making cybersecurity education more important than ever.
Join the CACMS Institute for comprehensive cybersecurity education today. Receive hands-on practical instruction and guidance from our seasoned experts. Take the first step towards becoming a digital guardian in the ever-changing world of cyber threats.
For further information and to enroll, please call +91 8288040281 or visit CACMS!
Secure your future in cybersecurity with CACMS Institute.
#cacms institute#cacms#techeducation#techskills#digital landscape#ethical hacking course#ethical hacking training#ethical hacking course in Amritsar#ethical hacking certification#Cybersecurity education#cybersecurity course in amritsar
0 notes
Text
Unveiling Data Excellence with Leading Data Analysis Training Institutes
Data analysis stands as a cornerstone in today's tech-driven world, powering informed decision-making and innovation. Choosing the right training institute is pivotal for mastering these crucial skills. Let's explore the how best data analysis training institutes in Bhubaneswar uncovering their offerings and excellence.
Importance of Data Analysis Training :
Data analysis holds immense significance across industries, empowering professionals to extract actionable insights from data. Choosing a reputable training institute becomes essential to grasp these skills effectively.

Choosing the Right Institute :
Selecting the ideal institute involves considering several factors:
Curriculum Relevance: Ensure the institute's curriculum covers crucial data analysis tools, methodologies, and practical applications.
Faculty Expertise: Institutes boasting experienced faculty members often provide valuable insights and real-world experiences.
Industry Connection: Institutes with industry partnerships or placement programs enhance career prospects post-training.
Specialized Offerings :
The best data analysis training institutes offer:
Comprehensive Curriculum: Covering statistical analysis, data visualization, machine learning, and tools like Python, R, or SQL.
Hands-on Projects: Practical assignments and real-world projects to reinforce learning and skill application.
Career Support: Placement assistance or connections with industry partners for internship opportunities or job placements.
Conclusion :
Mastering data analysis opens doors to a wide array of career opportunities in today's data-centric world. Institutes like Cloud Connect stand out for their commitment to excellence in imparting these skills. This makes it once of the best data analysis training institute in Odisha.
Choosing the right institute aligned with your learning objectives and career aspirations is key. Ensure to assess the curriculum, faculty expertise, and additional offerings to make an informed decision.
Remember, investing in quality data analysis training is an investment in a future brimming with opportunities in the data-driven realm.
#Best Ethical Hacking Training Institute in Odisha#Best Business Analysis Training Institute in Bhubaneswar
0 notes
Text
#ethical hacking training in India#ethical hacking in India#ethical hacking training institute in India#advance level ethical hacking training#hacking#ethical hacking#ethical hacker
0 notes
Text

#ethical hacking course#ethical hacking courses#ethical hacking institute#ethical hacking online institute#ethical hacking training#best ethical hacking#ethical hacking job#ethical hacking services#ethical hacking course in delhi#ethical hacking courses in delhi#best ethical hacking institute in delhi#ethical hacking institute in delhi#job based ethical hacking training in delhi#ethical hacking course in rohini
0 notes
Text
Profession of your future spouse - Pick a pile
Pile 1/ Pile 2




Pile 3/ Pile 4
Hello everyone ! This is my another pick a pile or pac reading so please be kind and leave comment or reblog, and let me know if it resonated with you!
Note : This is a general reading or collective reading. It may or may not resonate with you. Please take what resonates and leave what doesn't. And it's totally okay if our energies aren't aligned!
How to pick : Take a deep breath and choose a pile which you feel most connected to! You can choose more than one pile, it just means both pile have messages for you!
Note : This reading is based on my intuition and channeled messages from tarot cards.
I worked really hard on this pile please show some love by leaving comments, likes and reblogs!
Liked my blog or readings? Tip me!
Pile 1
The cards I got for you - ace of wands, 3 of cups, 3 of pentacles, the chariot
1. Creative jobs (Graphic Design, 3D, interior, photography, anything to do with creativity they might be into art too.) In which they have to use their hands, they can be good with their hands as well.
2. Event planner, wedding planner, some sort of celebrative type of occupation like a DJ, or they might own a bar.
3. They can be a teacher/leader/boss/ higher or upper position than you, project manager, they are very well respected in their work.
4. Leader, medics, a politician? something to do with ethical hacking or computer.
Pile 2
(The cards I got for you - 6 of cups, 3 of swords, 4 of swords, the star, or hierophant)
1. I feel daycare teacher, or babysitter in their free time, taking care of children's and animals, they might teach younger childrens.
2. Sports or athletic
3.Nurse, surgeon, therapist.
4. Teacher again or own an institute or teach somewhere online (they might know two languages)
5. Manager
Pile 3
(Queen of wands, The magician, two of pentacles, knight of swords)
They find hard to balance between work and personal life but they do it, flawlessly.
1. Model, (something to do with their looks) , confident job, like they need to be confident in their own body, even can be famous or a bit known in crowd.
2. They are very skilled they might have juggled many jobs and they are good in all type of things
3. Sales executive, Carpenter
4. Call center, the kind of work they need to give order to someone
5. Their work might require travelling.
6. A navy officer, cop
7. Advocate, CEO, business person
8. med field (ayurvedic type or medicine pharmacist)
Pile 4:
The cards I got for you - Ace of pentacles, 4 of wands, 8 of swords, king of cups and wheel of fortune)
The work they do might have them be overwhelmed orburdened, like stressful but they love their work.
1. Bank worker or finance like finance analayst, tech, data scientist, data analyst.
2. Wedding planner, or they work something in event planner.
3. counsellor in schools, or judge.
4. They might deal with criminals too in a way, or might involve to travel, military.

Thank you for stopping by! Take care and remember you are loved <3
#tarotcommunity#tarot reading#tarotblr#tarot cards#pick a card reading#pick a pile#tarot witch#thetarotwitchcommunity#diviniation#futurespousereading#future spouse#pac reading#love reading#pick a tarot#witchblr#divine guidance#spirituality#astro community#pick a picture#pick a card#spiritualgrowth#free tarot reading#astroblr#tarot blog#general reading#pick a photo#exchange readings#divination
635 notes
·
View notes
Text

#ethical hacking training institutes in patna#networking ccna training institutes in patna#digital marketing training in patna#autocad training in patna#summer training patna#software training institutes in patna#education#training#patna#bihar
0 notes
Text
König X Reader (F) ~Nerdy Little Maus~ When the reader successfully gets into a Dark Web Forum and makes a name for herself, how unfortunate for her she's a little to trusting with her client. How fortunate for the client, König, though that she falls right into his trap for him to take his nerdy little maus, all for himself. (Daddy Issues, Sugar Daddy, Kidnapping, Corruption Kink, Size Kink, Female Reader) Ao3 Link No TW - Part 1

Life had not been kind to you when you were young. Your mother passed away tragically, leaving you to be cared for by your father, who took the bottle to cope with her death. You tried desperately to gain his favor by excelling in your studies, but sadly, his drinks kept all his attention.
You were taking a computer science class in high school and excelling at learning code. The teacher, Mr. Johnson, was impressed at your ability to pick up the new information so quickly. Mr. Johnson pulled you aside one day and handed you a flyer for an ethical hacking competition; he truly believed you had what it took to win. For a few weeks straight, you stayed after school studying with a small group of other students, learning everything Mr. Johnson knew to teach. On the Saturday of the competition, your father begrudgingly permitted you to go with Mr. Johnson, Mrs. Johnson, and a few other classmates as a group.
You won the competition that day and were awarded a $10,000 scholarship to the Massachusetts Institute of Technology (MIT). The joy you felt as you stood on stage accepting your scholarship brought tears of happiness to your eyes. It was a shame your father was too busy-(drunk) to see how you glowed with pride at the most significant achievement of your life thus far.
Now, you sat in a dingy studio apartment. Staring at your Dell laptop at overdue bill emails. Student loans, rent, and credit card payments all accumulated with no significant income to pay them. You graduated from MIT but at the cost of over $80,000 in student loans. You couldn't find a job in the computer science field; the only work you landed was as a bartender at the bar down the street from your place. At least you were good at making drinks; tips kept the lights on, but you were sure you'd never make it out of the financial ruin you sadly got yourself into.
Whenever the manager encountered computer issues, you were always the first one he'd call. One day, while on the clock, you sat in his office, updating his pc to Windows 10. He watched as you had no issues clicking here and there; it was almost infuriating because, to him, what you did so effortlessly would have taken him hours to achieve just step one.
"You know, sweetheart, you need to get out of here and get a job in the computer field." Mike, the manager, said gruffly as he leaned arms crossed on his office door frame.
"Would if I could, Mike. I've all about givin' up on that dream." You replied, still staring at the blue computer screen.
"Don't cut yourself short. You are young, beautiful, and way smarter than any of the other idiots I have working here. Bring in the most money, too. I would miss that, though, if ya leave."
You let out a half-hearted chuckle. "Yeah, well, I use my pretty privilege more than my fucking MIT degree. But it helped me pull a $100 tip last week from the bachelor party, though. So don't worry, I'm not going anywhere, Mike."
Mike stands quietly and clears his throat, waiting a brief moment before he speaks again.
"Don't tell anyone I told ya, alright? But my buddy David knows a kinda underground Dark Web group that is always looking for someone like you. You know, that knows how to do computer stuff." He talked as he gestured vaguely with his hands.
You turn your head to Mike with a curious, almost dumbfounded look. "I don't know, Mike. The Dark Web is a pretty scary place I've heard. But they have open computer science jobs?"
"Yeah, from what I could understand, it's like a job forum, I guess. They have special passwords and whatever, but if you get in, they post jobs for people to take up and work."
You couldn't help but chuckle at Mike, but you appreciated his thoughtfulness in thinking of you, so you decided to take the bait.
"Sure, you give me the info, and I'll look into it, boss man."
A few days later, you received an email from someone you guessed was Mike's buddy, David, on your day off and clicked the link that opened a new web browser to a black screen. You fiddled with the settings on your old Dell laptop while sitting cross-legged on your thrifted couch when you increased the brightness to see a small set of instructions.
"I'll be dammed." You spoke quietly as you began your journey to unlock the puzzles hidden in the code.
It took five hours to finally get to the last section that unlocked access to the Dark Web forum. Sure enough, there were jobs from all around the world posted. As quickly as your excitement grew, worry flooded over you. These were not regular hacking jobs. Some were as simple as finding passwords to ex-lovers' accounts, but others were looking for classified government data locked away behind high-security firewalls. The thought of possible jail time or worse was frightening, so you shut your laptop and went to shower before bed. That night, you couldn't sleep, primarily due to the fear of the unknown but also because some of the jobs posted had the amount of money they were offering when completed. The memory of a 10,000 dollar payout for a hacking job bounced around your mind, toying with you. It danced along in bitter-sweet harmony with the memory of the 10k scholarship you won so many years ago.
On your next day off, you entered the forum again. It was too hard to resist the temptation of a simple job paying your rent for the month. So you avoided the big, scary ones and stuck to hacking into wealthy civilian accounts. You created an online persona account that allows the clients to send money and messages as needed. You called yourself "Cookie," a play on Cookie pop-ups for advertisers to gather your online information. Soon, you grew a small following and became recognized for your impressive hacking abilities and Trojan Virus creations. You told yourself repeatedly you were only ruining wealthy people's lives. What is a million dollars stolen from a billionaire anyway? It only took eight months to pay back almost all your debts. You've paid your rent up, no more credit card bills, and you've paid $5,000 into your student loan debts. You felt on top of the world and proud of your mischievous achievements.
It had been a long shift at the bar, and you entered your tiny apartment completely exhausted. You reheated some leftovers and took your regular seat on the couch. You open your laptop to see a new message on your Dark Web account.
"Hallo, Cookie. I am very impressed by your work. Care to look at a job I think you would be perfect for?"
You stared at the message as your curiosity peaked. You click on the stranger's profile to learn more about the mysterious sender. There is no profile picture, but in a small bio, the sender had "Austria" with a cute little red and white flag. They identified themselves as male, and his username was "TheKingCol."
That's interesting, you thought. You haven't worked with many international clients thus far. Your eyes began to cross as exhaustion set in deep in your bones. So, you decided to pick back up with the stranger tomorrow after sending him a message.
"Thank you for your message; yes, I would like to speak further with you. Let's chat more tomorrow."
You woke up later than usual with the sun high in the sky, peeking through your closed curtains. You stretched your body, and after a trip to the bathroom, you returned to your laptop. A new message was waiting for you, and you clicked it open to read. It was a Word Document link with what the client needed. He needed a Trojan Virus, and it had to be discreet so that the victim downloading it wouldn't know it was a fake link.
"That's not too bad." You thought to yourself.
You had created multiple Trojans up to this point, but it helps tremendously if you know what would make the victim unsuspecting to download the disguised Trojan.
"Hello again. I received your instructions, but I would like to discuss more details needed to create the perfect Trojan you are looking for, if possible."
You sent the message and waited a few minutes before your stomach began to growl. You stood up and began to rummage through your fridge for anything you could make to resemble breakfast and settled on making two fried eggs and a buttered piece of toast.
Once you ate your food, you returned to your seat to see another message had come through.
"Ja, may I call you to discuss details?"
You stared at the email, re-reading it. You quickly googled what language is spoken in Austria, and it said that mainly German is spoken. "He must not be a native English speaker," you thought, but that shouldn't be a problem. You, however, only knew English and maybe one or two words in Spanish.
"I'm sorry, I do not make phone calls or talk to clients outside the forum." You sent the message back and waited while you took sips of coffee from your favorite mug.
"Ah, but can't you make an exception for me? I understand your concern, little maus. I see you are a woman, no? Your father taught you well not to trust strangers on the internet."
You scoffed out loud at his message, placed your mug on the coffee table in front of you, and typed him back before thinking.
"Let's be clear that my Father has never done shit for me, first of all." You instantly regretted the message sent, normally you would write messages but always caught them before you tapped the enter button. There is no way to unsend a message like on Facebook. Airing out such dirty laundry to a client was entirely uncalled for and absolutely embarrassing.
"I'm sorry, that was very unprofessional of me. Please ignore that comment." You sent another message as quickly as you could type it. A few agonizing minutes later, you received a response.
"Is that so? A woman needs a supportive father to look after her, you know. No need to apologize Liebling. Here is my phone number; please call me if you decide to proceed. I will not discuss any more details by message."
That was the last message he sent before his profile was marked as "offline."
A day later, you paced around your living room. You held your phone tightly in your right hand. There was something about what he said that stuck with you long after you read it. Why on earth did you let your daddy's issues slip through to a prospective client? Embarrassment washed over you all over again, and soon enough, the anxiety of calling a client outside the forum was an afterthought. Before you knew it, you had typed in the number and hit the green call button.
The phone connected, but on the other side of the receiver was quiet.
"Hello?" You called out. "It's um, Cookie, from the forum." A second passed before you heard a voice from the other end.
"Ah, my little maus, so happy you've finally called."
39 notes
·
View notes
Text
Cybersecurity: The Key to Protecting Your Digital Identity and Privacy
In an era where our lives are increasingly connected with the digital sphere, protecting our digital identity and privacy has become critical. With the exponential growth of online activities, from social media interactions to financial transactions, the risks of cyber attacks are greater than ever before. In this digital age, cybersecurity has emerged as the primary shield protecting our digital life.
Understanding The Threat Landscape
Cyber risks take many forms, including data breaches, identity theft, malware, and phishing attempts. These dangers jeopardize sensitive personal information while also undermining trust in online systems and services. As technology advances, so do fraudsters' strategies, making it critical for individuals to be cautious and knowledgeable about cybersecurity best practices.
Significance of Digital Identity Protection
Our digital identities contain a variety of data, including personal information, financial records, and online behaviors. Securing this information is critical not only to prevent identity theft, but also to maintain our reputation and reliability in the digital sphere. A compromise of our digital identity can have serious ramifications for our financial stability, professional chances, and even our personal relationships.
Preserving Privacy in the Digital Age
Privacy is the foundation of individual freedom and liberty. However, in today's hyper-connected society, keeping privacy has grown more difficult. From surveillance technologies to data mining tactics, our online activities leave digital trails that dangerous actors can exploit. Cybersecurity measures are critical in protecting our privacy rights by ensuring that our personal information stays safe and protected from unauthorized access.
Empowering Individuals with Cybersecurity Education
While cybersecurity dangers may appear frightening, individuals may empower themselves by learning and developing cybersecurity skills. Education is an excellent technique for combating cyber threats because it teaches people how to detect possible risks, minimize vulnerabilities, and respond effectively to security crises. Individuals who invest in cybersecurity education improve not only their own digital safety but also the broader resilience of cyberspace.
Conclusion
In an increasingly linked world, cybersecurity is the foundation of our digital security and privacy. Individuals who recognise the importance of preserving their digital identity and privacy can take proactive efforts to reduce cyber risks and protect themselves from online dangers. We can create a safer and more secure digital future for ourselves and future generations by promoting cybersecurity education, awareness, and adherence to best practices.
Remember that in the digital world, cybersecurity is no longer an option—it is a requirement. Let's work together to protect our digital identities and privacy rights in an ever-changing online world.
Ready to take charge of your digital security? Join CACMS Institute today for comprehensive cybersecurity training that will provide you with hands-on practical skills and professional assistance.
Enroll in our Cyber Security Course in Amritsar and obtain the knowledge and competence required to properly protect your digital identity and privacy. Our professional teaching staff ensures that you receive a high-quality education and personalized attention throughout your learning journey.
Protect yourself online before it's too late. Contact us at +91 8288040281 or visit cacms.in to learn more about our Cyber Security Course in Amritsar and begin your path to a secure digital future now.
#cacms institute#cacms#techskills#techeducation#cyber security course in amritsar#cyber security#data privacy#digital identity#protecting digital Identity#ethical hacking course#ethical hacking training#ethical hacking certification#best computer institute in amritsar
0 notes
Text
Mastering ERP Systems with the best ERP training institute in Bhubaneswar
In today's digital landscape, Enterprise Resource Planning (ERP) systems play a pivotal role in streamlining business operations. These systems integrate various processes, from finance to human resources, enhancing efficiency and decision-making.
If you're looking to master ERP systems, selecting the right courses is paramount. Here's a comprehensive guide to choosing the best ERP courses available by best ERP training institute in Bhubaneswar.
Understanding the Significance of ERP Systems :
ERP systems are the backbone of modern businesses, aiding in managing and automating core processes. They encompass multiple modules like finance, supply chain, CRM, and more, providing a holistic view of organizational operations.
Exploring the Best ERP Courses :
When diving into ERP education, the key lies in choosing the best courses suited to your needs. Several online platforms offer diverse ERP courses tailored for different skill levels.

Oracle: Offering a variety of ERP courses, Oracle's platform provides in-depth training on their ERP solutions, catering to both beginners and advanced learners.
SAP: Known for its robust ERP solutions, SAP's online platform hosts courses covering various modules, equipping learners with comprehensive ERP skills.
Best ERP Training Institute :
To embark on your ERP learning journey, numerous online platforms stand out as excellent resources:
Cloud Connect Learning: Renowned for its expertise in IT domains. Cloud Connect as the best online training institute in Bhubaneswar, offers diverse training programs, including top-notch ERP courses. Their instructors bring real-world experiences into the classroom, ensuring practical insights for learners.
Choosing the Right Course :
Selecting the best online ERP course involves considering several factors:
Skill Level: Identify whether the course caters to beginners, intermediate learners, or advanced professionals.
Course Content: Review the syllabus to ensure it covers essential ERP modules and hands-on practical experiences.
Instructor Expertise: Opt for courses led by industry experts to gain valuable insights and real-world knowledge.
Conclusion :
Mastering ERP systems requires dedication and choosing the right courses to match your learning objectives. Whether you opt for platforms like Oracle, SAP, or trusted online resources like Cloud Connect Learning, the key is to select courses aligning with your skill level and career aspirations.
Investing time in learning ERP systems opens doors to exciting career opportunities and equips you with invaluable skills to thrive in the ever-evolving business landscape.
Remember, the best ERP courses by best ERP training institute in Bhubaneswar blend theoretical concepts with practical experiences, empowering you to excel in the world of Enterprise Resource Planning.
#Best Online Training Institute in Bhubaneswar#Best Business Analysis Training Institute in Bhubaneswar#Best Business Analyst Training Institute in Odisha#Best Ethical Hacking Training Institute in Odisha
1 note
·
View note