#like. 6 more readings and then some discussion posts and a database analysis
Explore tagged Tumblr posts
Text
I just remembered I wanted to write a Luxon essay like months ago except I have ASSIGNMENTS
#like. 6 more readings and then some discussion posts and a database analysis#if i get ALL that done today maybe I'll write it but otherwise it's gonna have to wait.#however I am definitely going to go do some research on it. lol if my assignment didnt have topic parameters I'd do it for that ngl#would be VERY funny to turn that in frankly.
15 notes
·
View notes
Text
Plandemic Exposed
**EDITED TO ADD: I wrote this post to help my friends sort through misinformation and did not expect it to go viral. Several commenters have asked me to cite sources, and I agree that this is important to do. I still have a day job, but I have edited to include primary sources for all points when possible.**SECOND EDIT: People seem to not understand that PubMed (ncbi) is the international database for cataloguing medical research studies and instead think it only contains government-funded information or research. This is not the case. It is basically the Google of peer-reviewed research studies.**
*The following statements represent my personal informed views and not those of any institution*
First, background: I’m a physician (specifically a board-certified pathologist, which includes microbiology and laboratory medicine) with a master’s degree in epidemiology.
In the last day or two, several friends have shared or posted about a video “documentary” called “Plandemic”. The film depicts now-discredited former researcher Judy Mikovits who shares a plausible-sounding narrative about the current pandemic. The problem here is that nearly all of her scientific statements are demonstrably false. If you have more to add to this list, or credible data to the contrary, please start a discussion. I suspect there are many more false claims in this video, but these are just the ones that stuck out to me as a physician with epidemiology training.
- She states “There is no vaccine for any RNA virus that works." Incorrect: Polio, hepatitis A, measles, to name a few. (Source: https://www.ncbi.nlm.nih.gov/pmc/articles/PMC4763971/)
- Her retracted paper was actually not about vaccines at all, even though she insinuates that it was. (Here is the article: https://www.ncbi.nlm.nih.gov/pubmed/19815723)
- She states that Ebola could not infect humans until it was engineered to do so in her laboratory. This is false. (Here is an article describing an outbreak of Ebola in 1976, long before Dr. Mikovits was conducting research: https://academic.oup.com/jid/article/214/suppl_3/S93/2388104 )
- Likewise, many other zoonotic viruses have been shown to gain mutations that allow them to infect humans. This would not be some kind of new, crazy idea. We actually predicted it years ago: we just didn’t know exactly which virus or when it would occur. (Here is an article from 2015 discussing the likely emergence of future coronavirus pandemics: https://virologyj.biomedcentral.com/articles/10.1186/s12985-015-0422-1 )
- She states that the US was working with Wuhan to study coronaviruses years ago, like it’s a “gotcha” moment: yes, of course we were doing this – Wuhan is a coronavirus hotspot and it makes sense to study this family of viruses where it naturally occurs. (Same article as above: https://virologyj.biomedcentral.com/articles/10.1186/s12985-015-0422-1 )
- She states that COPD lungs are identical to COVID-19 lungs. As a pathologist, this is ludicrous – any practicing physician would be able to tell COPD from COVID-19, both clinically and histologically. (One article discussing an overview of tools for diagnosing COVID19 https://pubs.acs.org/doi/10.1021/acsnano.0c02624, one about CT specifically https://www.tandfonline.com/doi/full/10.1080/22221751.2020.1750307, and one about histology specifically https://academic.oup.com/ajcp/article/153/6/725/5818922)
- The statement taken out of context from the CDC death certificate recommendation reads in full “In cases where a definitive diagnosis of COVID-19 cannot be made, but is suspected or likely (the circumstances are compelling within a reasonable degree of certainty), it is acceptable to report COVID-19 on a death certificate as “probable” or “presumed”. In these instances, certifiers should use their best judgment in determining if a COVID-19 diagnosis was likely. Testing for COVID-19 should be conducted whenever possible.”. My physician colleagues are not being pressured to put COVID-19 on death certificates when it should not be there. (Here is the actual document with instructions for
filling out death certificates from the CDC: https://www.cdc.gov/nchs/data/nvss/vsrg/vsrg03-508.pdf )
- The idea that physicians are incorrectly diagnosing COVID-19 due to financial incentive is also ridiculous. Medicare sometimes bundles payments for some conditions (i.e. if you have a heart attack, medicare may pay XX for your treatment) – it’s possible the hospital could get paid $13,000 for your COVID-19 admission, but do you know what that’s based on? The fact that the average cost of a hospital admission for a respiratory condition is $13,297. (I can’t post a scientific study here, since this isn’t a scientific fact, but this article describes the procedure in detail: https://www.usatoday.com/story/news/factcheck/2020/04/24/fact-check-medicare-hospitals-paid-more-covid-19-patients-coronavirus/3000638001/ )
- She states that hydroxychloroquine has been “extensively studied in this family of viruses” – in fact, it has not been studied well in coronaviruses. It HAS been studied in malaria, which is not a virus. (Here is the one study that was performed that people like to cite, and it is an in vitro study (not in humans), of SARS (not COVID-19), and chloroquine (not hydroxychloroquine): https://virologyj.biomedcentral.com/articles/10.1186/1743-422X-2-69 ). And yes, it is considered an essential medicine for the treatment of malaria. Not for coronaviruses.
- Furthermore, the data on hydroxychloroquine are much weaker than they originally appeared: the small study that was highly publicized was not a randomized controlled trial, and the only patients who died were those who received hydroxychloroquine (and these were EXCLUDED FROM ANALYSIS!). This is terrible science. Even so, we want to investigate all possible treatments, so controlled trials are being conducted on hydroxychloroquine right now. (Current recommendations and summary of research: https://www.cebm.net/covid-19/hydroxychloroquine-for-covid-19-what-do-the-clinical-trials-tell-us/ ; One study published on May 7 shows no benefit to using hydroxychloroquine https://www.nejm.org/doi/pdf/10.1056/NEJMoa2012410?listPDF=true )
- She insinuates that there is a hydroxychloroquine shortage as a result of reduced production. In fact, the shortage has resulted from an increase in demand: people who take this medication regularly are writing extended prescriptions and because physicians are using it for COVID19 patients because they have nothing else to try. (https://jamanetwork.com/channels/health-forum/fullarticle/2764607?fbclid=IwAR2oKdwc0aZVFvkKUvw82r6XpnKeq0sFc1iIxqO4JdKscy-81mC6hkRQ6fs).
- “All flu vaccines contain coronaviruses”. Nope, absolutely false. (In fact, it’s so false based on the way vaccines are made that there are no studies specifically stating this claim. It would be like trying to conduct a study to examine whether humans can live with zero oxygen. Nope, we can’t. No study needed.)
- The ideas that sheltering in place somehow harms your immune system or that you may reactivate a virus in yourself by wearing a mask have been thoroughly debunked in other posts and I won’t get into the details here. Both national societies of emergency medicine have condemned the statements of these doctors, one of whom is not board-certified. (Please refer to Dr. Kasten’s post and others about these)
- Lastly, private companies removing false information from their platforms does not represent repression or promotion of propaganda. It’s helping to promote the spread of sound scientific information. If you think lies should be permitted to circulate freely alongside the truth with the intention of reaching people who won’t be able to tell the difference, you are part of the problem.
1 note
·
View note
Text
Butch-Fem History / Butch Identity Reccs
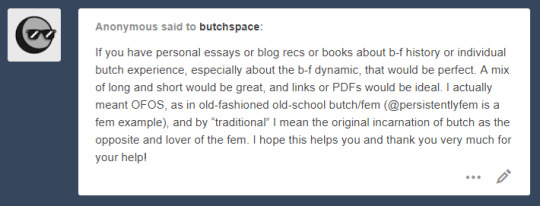
[Image description: an anonymous ask to butchspace that reads “If you have personal essays or blog recs or books about b-f history or individual butch experience, especially about the b-f dynamic, that would be perfect. A mix of long and short would be great, and links of PDFs would be ideal. I actually meant OFOS, as in old-fashioned old-school butch/fem (@persistentlyfem is a fem example), and by “traditional” I mean the original incarnation of butch as the opposite and lover of the fem. I hope this helps you and thank you very much for your help!” End ID.]
Okay so! I’ve got sucked into making this post and I’m just gonna go ahead and publish before I add even more on and forget to sleep again. Putting it under a cut because of length, if anyone wants a non-readmore version of the post just let me know.
Caveats:
I focused mainly on works I could provide links to; this means that what I’ve provided isn’t necessarily my first pick, but it’s still some good stuff so whatever. (See the Offline/Extended section for more reccs.)
A lot of the pdfs were transcribed in the course of a sleepless night so there’s bound to be typos; if you wanna tell me about them just message/ask @holzes to avoid clogging this inbox up.
Sadly, most of these works are dominated by white, cis, and able-bodied perspectives. This is especially something I want to remedy in the future in my additions.
It should go without saying, but: I don’t endorse every single opinion in these works or their authors (who for the most part I know little about), they don’t necessarily align with my own views and/or preferences, and I recognize that some of them have issues such as cissexist language and framing (see Content Warnings for more detail). Unfortunately when it comes to LGBT history, a lot of the most prominent texts are outdated or otherwise flawed in some areas and you just have to kind of trudge through it and read critically.
I included dates next to the works for a reason! Some (basically everything written in the early to mid 90s) emerged from a specific time in the lesbian community and obviously some of their statements only make sense in that context (mostly the lesbian feminist movement and its aftermath tbh). Just keep this in mind, it shouldn’t matter too much because those texts are history but just in case…
Just because I couldn’t find a work online doesn’t mean it doesn’t exist out there somewhere.
This is a deeply incomplete list. If you have suggested resources like these (preferably ones available online) including books, essays, articles, blogs, films, youtube videos, etc…. Let me know @holzes.
Content Warnings:
The Q slur (in just about every context), D slur, anecdotal homophobia, mentions of homophobic violence, outdated trans terminology, cissexism / cissexist language, discussion of sex (both academic and semi-explicit), cussing, frequent discussion of bars / probably a mention of alcohol once or twice. Sorry for not providing individual content warnings, this post is already bulky enough. If there’s something you’re rlly concerned about just mssg me @holzes and I’ll do my best to help you out.
And with all that out of the way…….. the actual post begins.
History
“Butch-Fem” by Teresa Theopano (2004)
An extremely succinct, balanced overview of butch-fem best suited for absolute beginners (aka, “what the hell is butch/fem” level). Also a good jumping-off point for anyone lacking historical context for butch-fem. Covers origin, application, and controversies. [Link]
“Lesbian Identities and the Politics of Butch-Femme” by Amy Goodloe (1993)
A rigorous essay that in many ways is a more detailed version of the above; packs a wide range of butch-fem history, controversy, and popular interpretation into a relatively short essay. A nice crash course with a killer annotated bibliography to build off of. [Link]
excerpt from Boots of Leather, Slippers of Gold: The History of a Lesbian Community by Elizabeth Lapovsky Kennedy & Madeline Davis (1993)
This excerpt from the introduction explicates the existence of working-class lesbian bar cultures in North America from the 1930s to the 1950s as well as the butch-fem dynamic that accompanied and shaped these cultures. The second section of this excerpt is perhaps best read as a companion piece to The Return of Butch and Femme (see below), especially as relates to Kennedy and Davis’s criticism of Faderman’s attitudes toward butch-fem. The entire book is well worth the read, but if you’re pressed for time, Chapters 5, 6, and 9 will be most relevant for your purposes. [Link to excerpt] [Link to full book]
“The Return of Butch and Femme: A Phenomenon in Lesbian Sexuality of the 1980s and 1990s” by Lillian Faderman (1992)
A thorough examination of how butch-fem became deeply “politically incorrect” through the lens of 1970s lesbian feminism, as well as its persistence throughout that decade and its restoration (and transformation) in the 1980s and 1990s. Perhaps Faderman’s most balanced examination of butch-fem (but don’t worry, she still throws around every anti-butch-fem critique and stereotype that she can justify including) and an informative history of how modern butches and femmes arose and if/how we differ from our predecessors. Read with section two of the above for best results. [Link]
Odd Girls and Twilight Lovers: A History of Lesbian Life in Twentieth-Century America by Lillian Faderman (1991)
Might as well, yeah? The book is a very interesting/enlightening semi-comprehensive history and a groundbreaking work in lesbian history literature. If you wanna cheat, Chapter 7 is the one that focuses primarily on butch-fem. [Link]
Personal Narratives
“Double Trouble” by Lesléa Newman (1995)
A brief personal reflection by a femme on her traditional femme-butch relationship. [Link]
Persistence: All Ways Butch and Femme eds. Ivan E. Coyote & Zena Sharman (2011)
An interesting collection of a broad variety of fem and butch perspectives. Essays range from emotional personal narratives to a mix of historical and personal analysis. I’ve provided links to a few that seem most relevant to your interest.
“Femme Butch Feminist” by Jewelle Gomez [Link]
“No Butches, No Femmes: The Mainstreaming of Queer Sexuality” by Victoria A. Brownworth [Link]
“What We Know to Be True” by Sasha T. Goldberg [Link]
“Spotlight” by Debra Anderson [Link]
Gender Troubles: The Butches (2016, dir. Lisa Plourde)
You might have seen this going around back when it was free to watch for a few months. It’s basically a long string of interviews with a few butches and it’s a nice watch, although I’m not sure how/where you can watch it now. [Link]
Extended (aka Stuff I Haven’t Read Yet and Am Thus Nervous to Recc)
In no particular order,
A Restricted Country by Joan Nestle (1987)
The Persistent Desire: A Femme-Butch Reader ed. Joan Nestle (1992)
I haven’t read either of Nestle’s groundbreaking works because I’m Fake but she’s probably the most influential writer on butch/fem by far so she can not be recommended highly enough.
Zami: A New Spelling of My Name by Audre Lorde (1982)
A biomythography that focuses partially on lesbian bar culture in NYC, Connecticut, and Mexico. The plain text is online if you can work with that. [Link]
Stone Butch Blues by Leslie Feinberg (1993)
This one’s only not in the main section because I figured you already knew about it, since it’s legally free online. It’s a novel, which I learned only recently. [Link]
Final Notes
For further reading and essays/books, I highly recommend digging through the notes/sources of the works I’ve linked above and jotting down anything that looks interesting or that gets mentioned a lot.
In terms of access–if you’re a college student or live in a college town, go to the college library (or public library, although these have been far less helpful for me) and find their LGBT section. Some places might surprise you. If you’re a college or high school student, go to your school library’s webpage and look for any access to databases you might have as a student, and exploit the hell out of whatever you find. If you’re not a student and/or don’t have access to a good library (or cannot use whatever resources you do have due to risk of outing yourself), stick to whatever you can find online.
Finally, I remembered @closet-keys‘s butch/femme research guide shortly after finishing this post. So, here’s that. [Link]
Thank you so much if you made it this far and I hope this answer helps out you, anon, at least a little, as well as anyone else who makes use of it!
-Mod P
#asks#anonymous#butch/femme#butch tag#resources#srry for focusing on written stuff that's just my area of expertise lol#reading#mod p#bluespace /#pebble posts
763 notes
·
View notes
Text
Industrial Control Systems Security Software Market Wrap: What Regulatory Aspects Impacting Most?
Latest Research Study on Global Industrial Control Systems Security Software Market published by AMA, offers a detailed overview of the factors influencing the global business scope. Industrial Control Systems Security Software Market research report shows the latest market insights with upcoming trends and breakdown of the products and services. The report provides key statistics on the market status, size, share, growth factors, Challenges and Current Scenario Analysis of the Industrial Control Systems Security Software. This Report also covers the emerging player’s data, including: competitive situation, sales, revenue and global market share of top manufacturers are IBM Corporation [United States], ABB Group [Switzerland], Check Point Software [Israel], Cisco [United States], Honeywell [United States], McAfee [United States], FireEye [United States], Fortinet [United States], BHGE [United States], Kaspersky Lab [Russia], Belden [United States], Airbus [France], BAE Systems [United Kingdom], Bayshore Networks [United States], Dragos [United States], CyberArk [United States], Cyberbit [Israel], Indegy [United States], Nozomi Networks [United States], Palo Alto Networks [United States], Rockwell Automation [United States].
Brief Summary of Industrial Control Systems Security Software: Industrial control security software (ICS) is used for monitoring industrial and manufacturing processes. These software gather data from remote sensors that monitor and measure variable and then compares with set points. The majority of these systems monitor complex industrial processes and critical infrastructures that deliver power, water, transport, manufacturing and other essential services. Today, widely available software applications and internet-enabled devices have been integrated into most ICS and offering various benefits to the organisation. Free Sample Report + All Related Graphs & Charts @ : https://www.advancemarketanalytics.com/sample-report/1631-global-industrial-control-systems-security-software-market Industrial Control Systems Security Software Market Report offers a detailed overview of this market and discusses the dominant factors affecting the growth of the market. The impact of Porter's five armies on the market over the next few years has been discussed for a long time in this study. We will also forecast global market size and market outlook over the next few years. Types of Products, Applications and Industrial Control Systems Security Software Market Report Geographical Scope taken as the Main Parameter for Market Analysis. This Research Report Conducts an assessment of the industry chain supporting this market. It also provides accurate information on various aspects of this market, such as production capacity, available production capacity utilization, industrial policies affecting the manufacturing chain and market growth. The Global Industrial Control Systems Security Software Market segments and Market Data Break Down are illuminated below: by Application (Power Industry, Energy and Utilities, Transportation Industry, Food and Beverages Industry, Manufacturing, Others), System Type (SCADA, DCS, PLC, Others), Security Type (Application Security, Database Security, Endpoint Security, Network Security), Solution Type (Antimalware/Antivirus, Distributed Denial of Service (DDoS) Mitigation, Encryption and Firewall, Identity and Access Management (IAM), Intrusion Detection System/Intrusion Prevention System (IDS/IPS), Security and Vulnerability Management, Security Information and Event Management (SIEM), Others) What's Trending in Market: Implementation of Artificial Intelligence and the Internet of Things (IoT)
The Advent of Real-Time Monitoring System in Industrial Networks
Challenges: Lack of Awareness About ICS Security
Restraints: Legacy ICS Being More Prone to Cyber-Attacks
Market Growth Drivers: The Growth in Investment by Various Organisation in Industry 4.0
Increase in Cyber Threats on Critical Infrastructure
An Upsurge in Cloud-Based SCADA System
Region Included are: North America, Europe, Asia Pacific, Oceania, South America, Middle East & Africa
Country Level Break-Up: United States, Canada, Mexico, Brazil, Argentina, Colombia, Chile, South Africa, Nigeria, Tunisia, Morocco, Germany, United Kingdom (UK), the Netherlands, Spain, Italy, Belgium, Austria, Turkey, Russia, France, Poland, Israel, United Arab Emirates, Qatar, Saudi Arabia, China, Japan, Taiwan, South Korea, Singapore, India, Australia and New Zealand etc. Enquire for customization in Report @: https://www.advancemarketanalytics.com/enquiry-before-buy/1631-global-industrial-control-systems-security-software-market Strategic Points Covered in Table of Content of Global Industrial Control Systems Security Software Market:
Chapter 1: Introduction, market driving force product Objective of Study and Research Scope the Industrial Control Systems Security Software market
Chapter 2: Exclusive Summary – the basic information of the Industrial Control Systems Security Software Market.
Chapter 3: Displaying the Market Dynamics- Drivers, Trends and Challenges & Opportunities of the Industrial Control Systems Security Software
Chapter 4: Presenting the Industrial Control Systems Security Software Market Factor Analysis, Post COVID Impact Analysis, Porters Five Forces, Supply/Value Chain, PESTEL analysis, Market Entropy, Patent/Trademark Analysis.
Chapter 5: Displaying the by Type, End User and Region/Country 2015-2020
Chapter 6: Evaluating the leading manufacturers of the Industrial Control Systems Security Software market which consists of its Competitive Landscape, Peer Group Analysis, BCG Matrix & Company Profile
Chapter 7: To evaluate the market by segments, by countries and by Manufacturers/Company with revenue share and sales by key countries in these various regions (2021-2026)
Chapter 8 & 9: Displaying the Appendix, Methodology and Data Source Finally, Industrial Control Systems Security Software Market is a valuable source of guidance for individuals and companies in their decision framework. Data Sources & Methodology The primary sources involves the industry experts from the Global Industrial Control Systems Security Software Market including the management organizations, processing organizations, analytics service providers of the industry’s value chain. All primary sources were interviewed to gather and authenticate qualitative & quantitative information and determine the future prospects. In the extensive primary research process undertaken for this study, the primary sources – Postal Surveys, telephone, Online & Face-to-Face Survey were considered to obtain and verify both qualitative and quantitative aspects of this research study. When it comes to secondary sources Company's Annual reports, press Releases, Websites, Investor Presentation, Conference Call transcripts, Webinar, Journals, Regulators, National Customs and Industry Associations were given primary weight-age. Get More Information: https://www.advancemarketanalytics.com/reports/1631-global-industrial-control-systems-security-software-market What benefits does AMA research studies provides?
· Supporting company financial and cash flow planning
· Latest industry influencing trends and development scenario
· Open up New Markets
· To Seize powerful market opportunities
· Key decision in planning and to further expand market share
· Identify Key Business Segments, Market proposition & Gap Analysis
· Assisting in allocating marketing investments
Definitively, this report will give you an unmistakable perspective on every single reality of the market without a need to allude to some other research report or an information source. Our report will give all of you the realities about the past, present, and eventual fate of the concerned Market.
Thanks for reading this article; you can also get individual chapter wise section or region wise report version like North America, Europe or Asia. About Author:
Advance Market Analytics is Global leaders of Market Research Industry provides the quantified B2B research to Fortune 500 companies on high growth emerging opportunities which will impact more than 80% of worldwide companies' revenues.
Our Analyst is tracking high growth study with detailed statistical and in-depth analysis of market trends & dynamics that provide a complete overview of the industry. We follow an extensive research methodology coupled with critical insights related industry factors and market forces to generate the best value for our clients. We Provides reliable primary and secondary data sources, our analysts and consultants derive informative and usable data suited for our clients business needs. The research study enable clients to meet varied market objectives a from global footprint expansion to supply chain optimization and from competitor profiling to M&As. Contact Us:
Craig Francis (PR & Marketing Manager) AMA Research & Media LLP Unit No. 429, Parsonage Road Edison, NJ New Jersey USA – 08837 Phone: +1 (206) 317 1218
Connect with us at
https://www.linkedin.com/company/advance-market-analytics
https://www.facebook.com/AMA-Research-Media-LLP-344722399585916
https://twitter.com/amareport
0 notes
Text
What is SDLC? Phases of Software Development, Models, & Best Practices
Introduction:
The software development life cycle (SDLC) is a process used for structuring the development of any software system, from initiation through to implementation. An increase in demand for software to meet customer needs effectively but with less cost and faster delivery has put tremendous pressure on modern organizations. To stay competitive, companies must build their software correctly and transform their businesses by following efficient software engineering methodologies, practices, and concepts. Without meeting these changes, there can be a drop in productivity, leading ultimately to business failure. Customer interaction at all levels with the right methodology for implementing the software is crucial to any organization’s success.
What is the first step in the Software Development Life Cycle?
The first step in the software development life cycle (SDLC) is requirement analysis. The first phase includes a collection of all the data from the customer. This includes the expectations of the customer. An understanding of what the product is, who the target audience is, why the product is being built is considered. Once the requirements are gathered, they are analyzed. An analysis of how feasible the creation will be is made. Any further ambiguity is discussed. Once the requirement is understood clearly and the analysis made, the SRS (Software Requirement Specification), is created. This document is for the benefit of both the software developers and the customer. It can be referred to by both parties for convenience.
Five different SDLC stages are:-
1. Planning and analysis
2. Designing the product architecture
3. Developing and coding
4. Testing
5. Maintenance

1. Planning and analysis: This phase is the most fundamental in the SDLC process business requirements are compiled and analysed by a business analyst, domain expert, and project manager. The business analyst interacts with stakeholders to develop the business requirements document. They also write use cases and share this information with the project team. The aim of the requirements analysis is for quality assurance, technical feasibility, and to identify potential risks to address in order for the software to succeed.
2. Designing the product architecture
During the design phase, lead developers and technical architects create the initial high-level design plan for the software and system. This includes the delivery of requirements used to create the Design Document Specification (DDS). This document details database tables to be added, new transactions to be defined, security processes, as well as hardware and system requirements.
3. Developing and coding
In this phase, the database admin creates and imports the necessary data into the database. Programming languages are defined by requirements. Developers create the interface as per the coding guidelines and conduct unit testing. This is an important phase for developers. They need to be open-minded and flexible if any changes are introduced by the business analyst.
4. Testing
Testers test the software against the requirements to make sure that the software is solving the needs addressed and outlined during the planning phase. All tests are conducted as functional testing, including unit testing, integration testing, system testing, acceptance testing, and non-functional testing.
5. Maintenance
In a post-production, live software environment, the system is in maintenance mode. No matter the number of users, the sophistication of the software, and rigorous QA testing, issues will occur. That’s the nature of software with managing data, integration, and security, and real-world usage. Access to knowledgeable, reliable support resources is essential, as is routine maintenance and staying up to date on upgrades.
Read More:
https://www.charterglobal.com/enterprise-solutions/
SDLC Models & Methodologies Explained
1. Waterfall
The Waterfall SDLC model is the classic method of development. As each phase completes, the project spills over into the next step. This is a tried-and-tested model, and it works. One advantage of the Waterfall model is each phase can be evaluated for continuity and feasibility before moving on. It’s limited in speed, however, since one phase must finish before another can begin.
2. Agile
The AGILE model was designed by developers to put customer needs first. This method focuses strongly on user experience and input. This solves much of the problems of older applications that were arcane and cumbersome to use. Plus, it makes the software highly responsive to customer feedback. Agile seeks to release software cycles quickly, to respond to a changing market. This requires a strong team with excellent communication. It can also lead to a project going off-track by relying too heavily on customer feedback.
3. Iterative
In the Iterative development model, developers create an initial basic version of the software quickly. Then they review and improve on the application in small steps (or iterations). This approach is most often used in very large applications. It can get an application up and functional quickly to meet a business need. However, this process can exceed its scope quickly and risks using unplanned resources.
4. DevOps
The DevOps security model incorporates operations – the people who use the software – into the development cycle. Like Agile, this seeks to improve the usability and relevance of applications. One significant advantage of this model is the feedback from actual software users on the design and implementation steps. One drawback is that it requires active collaboration and communication. Those additional costs can be offset by automating parts of the development process. Read our detailed comparison of DevOps vs. agile.

Best Practices in Software Development
1. Develop Iteratively
Critical risks are resolved before making large investments
Initial iterations enable early user feedback
Testing and integration are continuous
Objective milestones provide short term focus
2. Manage Requirements
Requirements are dynamic - expect them to change during software development
Users own understanding of the requirements evolves over time
Gain agreement with the user on what the system should do and not how
Maintain forward and backward traceability of requirements
3. Use Component-Based Architecture
Using components permits reuse
Choice of thousands of commercially available components
Improved maintainability and extensibility
Promotes clean division of work among teams of developers
4. Visually Model Software
Visual modeling improves our ability to manage software complexity
Capture the structure and behaviour of components
Hide or expose details as appropriate for the task
Promote unambiguous communication
5. Verify Software Quality
What is quality? - The characteristic of producing a product that meets or exceeds agreed upon requirements by some agreed-upon objective measures.
Software problems are 100 to 1000 times more costly to find and repair after deployment
Develop test suites for each iteration and test for – Functionality, Reliability and Performance
6. Control Changes to Software
Without explicit control parallel development degrades to chaos
Decompose the architecture into subsystems and assign the responsibility of each subsystem to a team. Establish secure workspaces for each team i.e. each team is isolated from changes made in other workspaces.
Conclusion: The Process for Software Development
SDLC shows you what’s happening, and exactly where your development process can improve.
Like many business processes, SDLC aims to analyse and improve the process of creating software. It creates a scalable view of the project, from day-to-day coding to managing production dates.
Reference Link:
https://www.charterglobal.com/best-practices-for-requirements-analysis-gathering/
https://www.charterglobal.com/accelerating-software-development/
https://www.charterglobal.com/what-are-the-5-phases-in-the-software-development-life-cycle-sdlc/
#Software Development Life Cycle#SDLC Methodologies#Waterfall SDLC model#AGILE model#Iterative development model#DevOps security model#software development company#SDLC Management Systems#Design Document Specification (DDS)#SDLC Stages#SDLC Process#SDLC
0 notes
Text
MySQL 101: Tuning MySQL After Upgrading Memory
In this post, we will discuss what to do when you add more memory to your instance. Adding memory to a server where MySQL is running is common practice when scaling resources. First, Some Context Scaling resources is just adding more resources to your environment, and this can be split in two main ways: vertical scaling and horizontal scaling. Vertical scaling is increasing hardware capacity for a given instance, thus having a more powerful server, while horizontal scaling is adding more servers, a pretty standard approach for load balancing and sharding. As traffic grows, working datasets are getting bigger, and thus we start to suffer because the data that doesn’t fit into memory has to be retrieved from disk. This is a costly operation, even with modern NVME drives, so at some point, we will need to deal with either of the scaling solutions we mentioned. In this case, we will discuss adding more RAM, which is usually the fastest and easiest way to scale hardware vertically, and also having more memory is probably the main benefit for MySQL. How to Calculate Memory Utilization First of all, we need to be clear about what variables allocate memory during MySQL operations, and we will cover only commons ones as there are a bunch of them. Also, we need to know that some variables will allocate memory globally, and others will do a per-thread allocation. For the sake of simplicity, we will cover this topic considering the usage of the standard storage engine: InnoDB. We have globally allocated variables: key_buffer_size: MyISAM setting should be set to 8-16M, and anything above that is just wrong because we shouldn’t use MyISAM tables unless for a particular reason. A typical scenario is MyISAM being used by system tables only, which are small (this is valid for versions up to 5.7), and in MySQL 8 system tables were migrated to the InnoDB engine. So the impact of this variable is negligible. query_cache_size: 0 is default and removed in 8.0, so we won’t consider it. innodb_buffer_pool_size: which is the cache where InnoDB places pages to perform operations. The bigger, the better. 🙂 Of course, there are others, but their impact is minimal when running with defaults. Also, there are other variables that are allocated on each thread (or open connection):read_buffer_size, read_rnd_buffer_size, sort_buffer_size, join_buffer_size and tmp_table_size, and few others. All of them, by default, work very well as allocation is small and efficient. Hence, the main potential issue becomes where we allocate many connections that can hold these buffers for some time and add extra memory pressure. The ideal situation is to control how many connections are being opened (and used) and try to reduce that number to a sufficient number that doesn’t hurt the application. But let’s not lose the focus, we have more memory, and we need to know how to tune it properly to make the best usage. The most memory-impacting setting we need to focus on is innodb_buffer_pool_size, as this is where almost all magic happens and is usually the more significant memory consumer. There is an old rule of thumb that says, “size of this setting should be set around 75% of available memory”, and some cloud vendors setup this value to total_memory*0.75. I said “old” because that rule was good when running instances with 8G or 16G of RAM was common, so allocating roughly 6G out of 8G or 13G out of 16G used to be logical. But what if we run into an instance with 100G or even 200G? It’s not uncommon to see this type of hardware nowadays, so we will use 80G out of 100G or 160G out of 200G? Meaning, will we avoid allocating something between 20G to 40G of memory and leave that for filesystem cache operations? While these filesystem operations are not useless, I don’t see OS needing more than 4G-8G for this purpose on a dedicated DB. Also, it is recommended to use the O_DIRECT flushing method for InnoDB to bypass the filesystem cache. Example Now that we understand the primary variables allocating memory let’s check a good use case I’m currently working on. Assuming this system: $ free -m total used free shared buff/cache available Mem: 385625 307295 40921 4 37408 74865 So roughly 380G of RAM, a nice amount of memory. Now let’s check what is the maximum potential allocation considering max used connections. *A little disclaimer here, while this query is not entirely accurate and thus it can diverge from real results, we can have a sense of what is potentially going to be allocated, and we can take advantage of performance_schema database, but this may require enabling some instruments disabled by default: mysql > show global status like 'max_used_connections'; +----------------------+-------+ | Variable_name | Value | +----------------------+-------+ | Max_used_connections | 67 | +----------------------+-------+ 1 row in set (0.00 sec) So with a maximum of 67 connections used, we can get: mysql > SELECT ( @@key_buffer_size -> + @@innodb_buffer_pool_size -> + 67 * (@@read_buffer_size -> + @@read_rnd_buffer_size -> + @@sort_buffer_size -> + @@join_buffer_size -> + @@tmp_table_size )) / (1024*1024*1024) AS MAX_MEMORY_GB; +---------------+ | MAX_MEMORY_GB | +---------------+ | 316.4434 | +---------------+ 1 row in set (0.00 sec) So far, so good, we are within memory ranges, now let’s see how big the innodb_buffer_pool_size is and if it is well sized: mysql > SELECT (@@innodb_buffer_pool_size) / (1024*1024*1024) AS BUFFER_POOL_SIZE; +------------------+ | BUFFER_POOL_SIZE | +------------------+ | 310.0000 | +------------------+ 1 row in set (0.01 sec) So the buffer pool is 310G, roughly 82% of total memory, and total usage so far was around 84% which leaves us around 60G of memory not being used. Well, being used by filesystem cache, which, in the end, is not used by InnoDB. Ok now, let’s get to the point, how to properly configure memory to be used effectively by MySQL. From pt-mysql-summary we know that the buffer pool is fully filled: Buffer Pool Size | 310.0G Buffer Pool Fill | 100% Does this mean we need more memory? Maybe, so let’s check how many disk operations we have in an instance we know with a working dataset that doesn’t fit in memory (the very reason why we increased memory size) using with this command: mysqladmin -r -i 1 -c 60 extended-status | egrep "Innodb_buffer_pool_read_requests|Innodb_buffer_pool_reads" | Innodb_buffer_pool_read_requests | 99857480858| | Innodb_buffer_pool_reads | 598600690 | | Innodb_buffer_pool_read_requests | 274985 | | Innodb_buffer_pool_reads | 1602 | | Innodb_buffer_pool_read_requests | 267139 | | Innodb_buffer_pool_reads | 1562 | | Innodb_buffer_pool_read_requests | 270779 | | Innodb_buffer_pool_reads | 1731 | | Innodb_buffer_pool_read_requests | 287594 | | Innodb_buffer_pool_reads | 1567 | | Innodb_buffer_pool_read_requests | 282786 | | Innodb_buffer_pool_reads | 1754 | Innodb_buffer_pool_read_requests: page reads satisfied from memory (good)Innodb_buffer_pool_reads: page reads from disk (bad) As you may notice, we still get some reads from the disk, and we want to avoid them, so let’s increase the buffer pool size to 340G (90% of total memory) and check again: mysqladmin -r -i 1 -c 60 extended-status | egrep "Innodb_buffer_pool_read_requests|Innodb_buffer_pool_reads" | Innodb_buffer_pool_read_requests | 99937722883 | | Innodb_buffer_pool_reads | 599056712 | | Innodb_buffer_pool_read_requests | 293642 | | Innodb_buffer_pool_reads | 1 | | Innodb_buffer_pool_read_requests | 296248 | | Innodb_buffer_pool_reads | 0 | | Innodb_buffer_pool_read_requests | 294409 | | Innodb_buffer_pool_reads | 0 | | Innodb_buffer_pool_read_requests | 296394 | | Innodb_buffer_pool_reads | 6 | | Innodb_buffer_pool_read_requests | 303379 | | Innodb_buffer_pool_reads | 0 | Now we are barely going to disk, and IO pressure was released; this makes us happy – right? Summary If you increase the memory size of a server, you mostly need to focus on innodb_buffer_pool_size, as this is the most critical variable to tune. Allocating 90% to 95% of total available memory on big systems is not bad at all, as OS requires only a few GB to run correctly, and a few more for memory swap should be enough to run without problems. Also, check your maximum connections required (and used,) as this is a common mistake causing memory issues, and if you need to run with 1000 connections opened, then allocating 90% of the memory of the buffer pool may not be possible, and some additional actions may be required (i.e., adding a proxy layer or a connection pool). From MySQL 8, we have a new variable called innodb_dedicated_server, which will auto-calculate the memory allocation. While this variable is really useful for an initial approach, it may under-allocate some memory in systems with more than 4G of RAM as it sets the buffer pool size = (detected server memory * 0.75), so in a 200G server, we have only 150 for the buffer pool. Conclusion Vertical scaling is the easiest and fastest way to improve performance, and it is also cheaper – but not magical. Tuning variables properly requires analysis and understanding of how memory is being used. This post focused on the essential variables to consider when tuning memory allocation, specifically innodb_buffer_pool_size and max_connections. Don’t over-tune when it’s not necessary and be cautious of how these two affect your systems. https://www.percona.com/blog/2020/09/30/mysql-101-tuning-mysql-after-upgrading-memory/
0 notes
Text
Webflow Review – An Exceptional Website Builder| Forever FREE

Webflow is a website builder that has attracted a lot of attention. But how nice is it? For whom designed? How much this software costs? I am going to address all the above-mentioned questions, But, let’s start with the basics first –
Introduction
Most of the people refer to Webflow as an online toolkit for building websites. It’s a great combination between the classic content management platform and conventional website builders like WordPress. It is indeed one of those exceptionally SaaS platforms with the professedly specific target market.
Getting Confused?
This review post created to wave off that confusion. Considering the various components which Webflow offer including, CMS, Designer, eCommerce, Hosting, etc. you will also get answers to questions for anyone considering this platform.
The primary principle of WebSocial is so-called “smart codelessness”. Alternatively stated, it aims to provide a desirable balance between customization capabilities and code fewer processes of site-building. Also, you can monitor many of your website’s attributes without operating on the correct source.

Surprisingly, this platform does not lock you out of the cycle of coding. It still uses fun software to help you thoroughly customize your page, without actually confining yourself to any particular submission platform.
Are you feeling interested to know more?
Alright, hang around because this review post of the Webflow enables you to reach all the major components associated with this platform. Read out the essential features of Webflow, customer support, pricing, and the associated pros and cons.
Overview
Webflow moved ahead to the path of success with this mantra – “If you can imagine the ultimate outcome, you can bring it to life.”

This simple, yet versatile web-based drag and drop tool mainly developed with the principal focus on the designers and regular people. This tool will help them easily create responsive, flexible and powerful websites and applications better and faster without any special coding skills.
But that’s not all. The site builder was also systematically integrated with a CMS framework for seamless management of the entire ecosystem.
The platform is consistently integrated based on the framework of the Content Management System, which helps in seamlessly managing the entire ecosystem. They are also looking forward to capitalizing on some of the core functions, which include:
Ecommerce
CMS
Designing
Web Hosting
Interactions
Editing, etc.
Though this platform serves as an alternative to WordPress, it claims to be much simpler than this. As having said that, WordPress considered being one of the simplest and the best and simplest CMS platforms available on the internet today.
So, will Webflow able to take the challenge? Let’s check it out!
Salient Features
Inclusive Ease Of Use
One thing that could impress you right off the bat is the overall versatility or flexibility of Webflow.
For example, the website designer doesn’t come with the rigid site construction framework that is available in many other “user-friendly” options. In other words, you can choose any template of your choice here.
Although that considered to be an easy option as there are limited customization capabilities for pre-designed themes. But this website builder allows you to start with a completely blank canvas and build your site from the ground up.

Not only this, Webflow is designed to facilitate complete responsiveness and mobile-centric adaptability. Moreover, it also provides various designing features which include the tiniest website elements. Typography, which has numerous possibilities to accommodate, including Typekit, Google Font, and your own custom font.
Webflow, in particular, does not restrict you to its system. At any time, you can conveniently export Javascript, HTML, and CSS from your page to a third party website.
In case you are working on different projects simultaneously, then you should be able to arrange and control them directly from the dashboard display. With the project options, you can add them in folders, share, duplicate, and edit them. All the projects are available with a different set of array settings, which includes external service connections, SEO, code integrations, backups, websites, etc.
Though the only downside is the complex framework that is available with it. Newbies can find it a little difficult to try out the latest features of Webflow. However, it becomes easier and easier with more websites you work on.
These people also offer a complete set of useful video tutorials, which helps in providing valuable guidance in case you face any issues. But if that doesn’t turn out, you can always contact the customer support team, who I found to be quite responsive.
On the whole, people who are having the most manageable time using this platform are probably HTML and CSS coders. Similarly, on the other hand, non-coders are also most likely to gain great results just by footing well after a couple of hours on this platform.
Also Read : Why Choose Wix as a Free Website Builder | An Honest Wix Review?
WebFlow Hosting
The hosting function provided by this platform works on the policy – “Start building for free, add hosting to go live.” In simple terms, you are allowed to start creating your website on a free Webflow subdomain. You can then pay for one of the Webflow hosting packages to connect the website to a custom domain name.

One of the best plans to gain complete advantage of the hosting services is the basic plan. It allows us to provide hosting for some simple site with less than 500 form submissions and 25,000 monthly visits and at a minimum cost of $15 per month or $12 per month billed yearly.
Not only the custom domains, but there are also some extra features which are provided by this tool –
Free SSL certificate
CDN
Advanced SEO
Backups
Versioning
Some of the other benefits of leveraging Webflow hosting include:
Webflow hosting based on decentralized infrastructure operated by renowned cloud providers such as Amazon CloudFront and fastly.
Webflow hosting provides an additional CDN (Content Delivery Network) at zero additional cost. It accelerates the delivery of content to site visitors far from the position of your primary server.
Provides SSL compliance certificate for free to ensure that each site adheres to the current standards for web encrypted communications.
Webflow hosting based on more than 100 data centers spread across 6 continents, letting you choose a server that is nearest to your chief traffic source.
It provides a shorter loading page as compared to the standard HTTP websites.

Webflow Designer
The website builder and the design tool is given a fancy name as Webflow Designer, which provides a unique twist to the entire website creation process.
It provides a balance between the worlds of coding and non-coding. Users who do not have the advanced coding skills will take advantage of the intuitive DIY side of the website builder. Instead, on the other hand, experienced programmers, designers, and organizations will benefit from the complete freedom of choice that comes with the programming side of the Webflow site builder.

Therefore, you can consider it as a hybrid site builder. Apart from this, some of the specific features of this platform include:
Languages like JavaScript, HTML, and CSS coding easily handled by website-builder. Web developers expected to like the code creation features of their visual designer, which saves the trouble by line writing code.
The next thing which sets this Designer apart from others is its exceptional approach to editing the visual things. As here the canvas is designed to provide you with an easy to use way to tweak the elements of your page, with the versatility provided by HTML and CSS. For example, placing a square requires you to add a new “part” or “box” and then build a “set” location.
Well, Webflow Designer seems designed to serve professional web designers along with developers in the first place as well as their agencies.
Final Words
Webflow is one exceptional, high-end website builder for freelancers and designers. Several features like Databases, integrations, databases, several layout edit modes, identificators, integrations, template code export, etc. make it one of a kind platform.
The blended force of its Hosting, Designer, E-commerce offers, and Editor/CMS is massive. This website builder has also the most exquisite tailor-made website development setups. The 24*7 support team makes every single process smooth and easy.
In short,
Simplicity Level – (simple)
Progress in Learning – Mid (before you think to jump in and create something, you need to first watch the available videos and understand every terminology)
For Consumers (Perfectly suitable)
For Designers (Perfectly suitable)
For Developers (Perfectly suitable)
Time taken in the Development process (Quick)
Whitelabel – For businesses and agencies who carry out the payment.
In-built templates – Yes
Pricing Plans – Low

Your Thoughts?
I am thankful to you for taking the time from your busy schedule to read our analysis of Webflow. Was this review helpful? Do you have something to add, or do you disagree with some points? Let’s discuss in the comment section given below.

Originally Published On: SaasTrac
About The Author SaasTrac is one of the trusted places where users can find reviews on different Saas Products, Software, and Platforms. Our major goal is to let users know the detailed and the most helpful information possible about every product — the good, the bad, and the ugly in the SaaS space.
#high-end website builder#Webflow Review#Webflow#An Exceptional Website Builder#Exceptional Website Builder#Website Builder
0 notes
Text
13 March 2020
Viral content
There's a definite theme to a lot of the links this week, unsurprisingly. I've also been keeping track of various useful pieces of advice from people used to remote working as coronavirus fundamentally changes how we work and live, whether in the short term or more profoundly - more on that next week.
But for now, here's an extremely useful tech handbook started by the team at Newspeak House, which has resources on everything from health advice and data about the disease, to advice on working remotely and tackling misinformation.
In other news:
We're doing a very quick project for Nesta on missing data in preventive services - looking specifically at children's centres and youth services. Here's the write-up of a workshop we did - thoughts very welcome.
My colleague Nick celebrated three years at the IfG with a terrible chart. Hilarity ensued.
I was very sad to see that Clare Moriarty, one of the most inspirational senior civil servants to those of us working around data and openness in government, is leaving the civil service. This speech of hers from last year is well worth a read.
I'd forgotten just how good the FT's 404 page is.
Delighted to hear the good people at Citizens Advice are finding inspiration in our dataviz. You may be less delighted by the puns that followed.
And a reminder that we're hiring someone to run Whitehall Monitor. A big thank you to Jukesie for including it in his indispensable jobs newsletter.
Have a good weekend
Gavin
Today's links:
Graphic content
Viral chart
A very short thread on the power of data graphics and scientific communication (Carl T. Bergstrom)
Spot the difference... (Rosamund Pearce)
Everyone's job is to help FLATTEN THE CURVE (Dr Siouxsie Wiles)
Coronavirus: How peak of cases could be cut by 'social distancing' (Sky News)
How canceled events and self-quarantines save lives, in one chart (Vox)
It’s not exponential: An economist’s view of the epidemiological curve (voxeu.org)
Viral content
17 responsible live visualizations about the coronavirus, for you to use (Datawrapper)
Illustrative simulations of a transmission model of COVID-19 (The Lancet)
COMMUNICATION THEMES FROM CORONAVIRUS OUTBREAK (Visualising Data)
COVID-19: Research in Uncertain Times (Ipsos MORI)
In America, even pandemics are political* (The Economist)
Foot traffic has fallen sharply in cities with big coronavirus outbreaks* (The Economist)
Die Schweiz liegt auf Platz 6 der am stärksten betroffenen Länder – alles zum Coronavirus in 14 Grafiken (NZZ)
9 charts that explain the coronavirus pandemic (Vox)
Right or wrong, there’s no doubt the UK is increasingly an outlier in our Covid response (BBC Newsnight)
Soap is such an ordinary thing. Can it really kill a virus? (YES! Now wash your hands) (Prof Lucy Rogers)
From coronavirus to bushfires, misleading maps are distorting reality (First Draft news, via in other news)
Coronavirus: UK maps and charts (BBC News)
How Coronavirus Hijacks Your Cells* (New York Times)
How Deadly Is Coronavirus? What We Know and What We Don’t* (The Upshot)
Coronavirus Disease (COVID-19) (Our World in Data)
Total UK cases COVID-19 Cases Update (Public Health England)
Coronavirus Data Pack (Information is Beautiful)
Wie das Coronavirus nach Deutschland kam (Zeit Online)
COVID-19 MAP (/r/CovidMapping, via Pritesh)
How the World’s Largest Coronavirus Outbreaks Are Growing* (New York Times)
Exponential growth and epidemics (3Blue1Brown)
I’m no epidemiologist, but I am a #dataviz specialist, so here are some thoughts on coronavirus and log scales (John Burn-Murdoch, via Marcus)
When Everyone Stays Home: Empty Public Spaces During Coronavirus (The Atlantic, via Benoit)
#IWD2020
International Women’s Day 2020: Close to three in ten men say sexual jokes or stories at work are acceptable (Ipsos MORI)
Americans overestimate voters’ prejudices against women and ethnic minorities* (The Economist)
What do we know about gender inequality in the UK? (ONS)
Cabinet and civil service gender balance (Ketaki and me for IfG)
Seven in ten support equal coverage for women’s sport, but not at the cost of men’s coverage (YouGov)
A dozen+ visionary pioneers who did great (and good) things with data visualization (RJ Andrews)
Would making salaries public help end disparities?* (FT)
#Budget2020
The budget in charts - Tom, Graham (IfG)
Spring Budget 2020: IFS analysis (IFS)
The Stupidest Budget of All Time* (Tortoise)
Spring Budget 2020 response (Resolution Foundation)
Life and death
Why we run (Strava)
Diabetes risk: what’s driving the global rise in obesity rates?* (FT)
How Working-Class Life Is Killing Americans, in Charts* (New York Times)
Middle-aged generation most likely to die by suicide and drug poisoning (ONS, from 2019)
Changing trends in mortality by leading causes of death, England and Wales: 2001 to 2018 (ONS)
Mortality and life expectancy trends in the UK (The Health Foundation)
Everything else
Political trust (Will Jennings via Alex)
British Election Study 2019 Data Release – Internet Panel, Results File, and Expert Survey
Ministers (me for IfG)
Political protests have become more widespread and more frequent* (The Economist)
Getting moving: Where will transport infrastructure investment unlock city-centre growth? (Centre for Cities)
45 Minute Cities (Alasdair Rae)
National Primary Results Map: Where Biden and Sanders Have Won* (New York Times)
Joe Biden’s surge poses threat to Bernie Sanders’ US primary hopes* (FT)
Meta data
Viral content
Five ways coronavirus could shape our digital future (Jonathan Tanner for the Overseas Development Institute)
Coronavirus divides tech workers into the 'worthy' and 'unworthy' sick (The Guardian)
Coronavirus: A Digital Governance Emergency of International Concern (CIGI)
Fact Check Explorer: Coronavirus (Google)
NHS announces plan to combat coronavirus fake news (The Guardian)
Facts on Coronavirus (Full Fact)
Sifting Through the Coronavirus Outbreak (Mike Caulfield)
The Simplest Way to Spot Coronavirus Misinformation on Social Media (OneZero)
CORONAVIRUS and HAKKAR THE SOULFLAYER'S CORRUPTED BLOOD! Or what do people actually do in a pandemic? (Alex Krasodmoski)
On TikTok, coronavirus is just another way to gain clout* (New Statesman)
Chinese social media sites blocked medical information about the coronavirus, research indicates (Poynter)
Boris Johnson Has Summoned Major Tech Companies To Downing Street To Help In The Fight Against The Coronavirus (BuzzFeed)
Inside Dominic Cummings’s coronavirus meeting with big tech* (Wired)
How a global health crisis turns into a state-run surveillance opportunity (The Observer)
CIO interview: Sarah Wilkinson, NHS Digital (Computer Weekly)
#OpenDataDay
Celebrating the tenth Open Data Day on Saturday 7th March 2020 (Open Knowledge)
Celebrating Open Data Day around the world (Open Knowledge)
What is ‘open data’ and why should we care? (ODI)
What @instituteforgov is able to do with #opendata (IfG)
#opendataday, #ODD2020, #OpenDataDay2020
#Budget2020
Me
Peter Wells
Owen Boswarva
What Works Centres
Digital markets taskforce: terms of reference (BEIS/DCMS/CMA)
If we want cutting-edge R&D, we must rethink our attitude to failure (Hetan Shah in City AM)
#IWD2020
In a world biased against women, what role do algorithms play? (CDEI)
Mapping Gender Data Gaps: An SDG Era Update (Data2X)
Why cars are unsafe for women* (Caroline Criado Perez for the Sunday Times)
Why the web needs to work for women and girls (Sir Tim Berners-Lee)
International Women’s Day: celebrating the black women tackling bias in AI (Ada Lovelace Institute)
UK government
The UK’s national data strategy is still missing in action (New Statesman)
Does Brexit Britain have a data strategy fit for purpose? - the public sector perspective (diginomica)
Price and prejudice: automated decision-making and the UK government (podcast) (openDemocracy)
The UK Has Slumped in Open Data Rankings: This Should Trouble All of US (Jeni Tennison in Computer Business Review)
MANUFACTURING THE FUTURE: COULD HEALTHCARE DATA HELP REBALANCE THE UK’S ECONOMY? (Reform)
Designing an Information Governance approach for London (LOTI)
Case for helping join up government services (GDS)
MPs told to hold to account those responsible for Post Office Horizon IT scandal (Computer Weekly)
UK.gov is not sharing Brits' medical data among different agencies... but it's having a jolly good think about it (The Register)
The UK’s tech sector has much to be optimistic about (Matt Warman MP for CapX)
I’ve written a bot @UKreleases that tweets out all the transparency releases governments departments post on http://gov.uk (Jon Stone)
At least 20,000 people denied information that could prove right to live in UK (The Independent)
DCMS to examine government data-sharing barriers ahead of programme of ‘radical and transformative change’ (Public Technology, via Colm)
We’re hosting a community meet-up to discuss how we archive data (Technology in Government)
Harnessing the potential of linked administrative data for the justice system (ADR UK)
AI, IoT, tech, etc
AI needs more regulation, not less (Brookings)
AI In Policing: Better Than A Knife Through The Chest? (Forbes)
Better intelligence about artificial intelligence (Nesta)
Reset (Luminate)
IoT Week[note 32] (LOTI)
Everything else
David Hand on Dark Data (Princeton University Press)
We Built a Database of Over 500 iPhones Cops Have Tried to Unlock (Motherboard)
The Robots Are Coming: Ethics, Politics, and Society in the Age of Artificial Intelligence (Kenneth A. Taylor, Boston Review)
How our network is considering data ethics: survey results (ODI)
Researcher danah boyd on how to protect the census and fix tech (Protocol)
How close is humanity to destroying itself?* (The Spectator)
Stealth political ads flourish on Facebook* (Politico)
#NICAR, #NICAR2020
William Gibson on the apocalypse: “it’s been happening for at least 100 years”* (New Statesman)
A Dataset is a Worldview (Hannah Davis)
Centre Write: Digital disruption? (Bright Blue)
Facebook sued by Australian information watchdog over Cambridge Analytica-linked data breach (The Guardian)
Frontex hits activist pair with €24,000 legal bill (EUobserver, via Giuseppe)
A catalogue of things that are stopping change: part II (Rose Mortada and James Reeve)
Opportunities
JOB: Senior Researcher - Whitehall Monitor (IfG)
JOB: Data Journalist / Research Analyst (Spend Network)
JOB: Team Lead - Data Technology (Data Unit) (DfT)
JOB: Policy Fellow (Digital Technology) (The King's Fund)
JOB: Data Science Campus Delivery Manager (ONS)
JOB: Social Media and Engagement Journalist (FT)
JOB: Partnerships and Community Manager (Understanding Patient Data)
JOB: Head of Public Policy (ODI)
JOBS: Good Things Foundation
EVENT: Digital Insight and Business Intelligence in Local Gov 2020 (London Borough of Redbridge and techUK, via Martin)
And finally...
Love in the time of quarantine
I made a graph of old relationships... (Jeremiah Lowin)
BETWEEN THE SPREADSHEETS (1843, via Alice)
I Work from Home (The New Yorker, via David)
Pi Day tomorrow
How a farm boy from Wales gave the world pi (The Conversation)
Even After 31 Trillion Digits, We’re Still No Closer To The End Of Pi (FiveThirtyEight)
Pi Day: How One Irrational Number Made Us Modern* (New York Times)
A colorful π chart (Datawrapper)
Everything else
What's your beverage of choice? (Jess Walker)
Cognition (Steve Stewart-Williams)
This is the scale of the universe (How Things Work)
0 notes
Text
Everything You Ever Wondered About Hiring a Virtual Assistant (And More)
When was the last time you took stock of your productivity? If we’re honest, most of us are too busy to devote time to this important task. But if we did (and I’ll share more on how to do that below), we’d likely find hours of time wasted on mundane tasks each week.
A Workfront survey actually found U.S. employees at companies of 1000 workers or more only spent 45% of their workweek on primary job duties. Where did the rest of the time go? Well, 14% of their time was spent on email and the other 40% was spent on meetings, "interruptions," and … administrative tasks.
This gets a little fuzzy when you consider what an "administrative task" is. An administrative task for a salesperson is different than that of a real estate agent or graphic designer. But we all have them. They clutter up our days and keep us under water and sometimes underperforming.
Luckily, technology has given us a new opportunity to get ahead: virtual assistants. But who are these mythical creatures? How do you know if you need one? And where do you look? I’ve got all those answers and more, below.
What Is a Virtual Assistant?
Virtual assistants are contract workers companies or individuals hire to complete specific projects and duties. They often handle administrative tasks like data entry, answering emails, and calendar management. However, virtual assistants in niche areas like real estate and graphic design are also available.
What do virtual assistants do
Virtual assistants work on a contract basis for your business. You can hire them to work a set number of hours each week or month, or for the length of a specific project.
You can hire a virtual assistant to help with almost any task, from setting up your office furniture to answering emails and even prospecting for your pipeline.
Virtual assistants can help with administrative tasks, like data entry, that eat up valuable time you or your full-time staff can spend on higher value tasks.
You can also hire a virtual assistant for more technical projects, such as design work or tax help, where a full-time hire might not be necessary.
Benefits of a virtual assistant
Virtual assistants are especially helpful for entrepreneurs, small business owners, or busy professionals looking to skyrocket their careers. Here are a few benefits of hiring a virtual assistant:
Virtual assistants can be more cost effective than hiring a full-time employee.
Virtual assistants can help with technical projects, like creating a company video, on an as-needed basis, so you don't have to hire a full-time videographer.
Virtual assistants can give you more time back in your day by taking mindless or administrative tasks off your plate.
Virtual assistants can free up more time for you to spend with your family or on personal projects.
Virtual assistants can decrease stress levels and prevent burnout for you or your employees.
When to Hire a Virtual Assistant
Entrepreneurs��often think, "I can do that better myself." In fact, most of us often think that. And while it might be true, it doesn’t make each task worthy of your time and attention.
There’s a difference between self-discipline and martyrdom -- even at work. Here are a few ways to tell you’re ready for a virtual assistant:
When you have a list of repetitive tasks you complete regularly - Do you spend 90 minutes a day answering emails? Write it down. 30 minutes a week booking hotels? Add it to the list. 15 minutes filling out expense reports? You know the drill. You might be surprised at how much time these small tasks chip away from your week -- and which ones pop up most regularly.
When you know the process backwards and forwards - Generally speaking, you should be quite familiar with the tasks you’re assigning to your virtual assistant. Because the goal is to get menial tasks off your plate, these should be projects you complete regularly. This also helps you find qualified help you can train thoroughly.
When you’ve conducted a cost-benefit analysis - You’ve heard the old adage, "20% of the tasks provide 80% of the value." Use your list of repetitive tasks to add up how much time you waste on these projects each week -- and just how much of your salary is being spent completing them.
When you don’t need full-time help - Don’t use a virtual assistant in place of what should be a full-time job. If you need to hire a web developer, don’t try to cut costs by piecing it out. You’ll put strain on your company and your virtual assistant. And the end result will likely cost you more over the long run. Seek a virtual assistant for one-off projects or small tasks that don’t justify a salaried employee.
When you have the money - Don’t stretch your budget. Only hire help when your revenue stream can support it or can’t live without it.
How to Hire a Virtual Assistant
Document your process
Create a job description
Include an applicant test
Add a keyword or 'Easter Egg' in your job posting
Conduct an interview
Start on a trial basis
Take time to train your assistant
Have realistic expectations
Dont be afraid to cut ties and move on quickly
1. Document your process
Begin by taking notes of the process you’d like to outsource. Write each step down, include screenshots when applicable, and add nuanced insight into how you prefer these tasks completed. This will help you identify which skills and experience are absolutely necessary to include in the next part of the process …
2. Create a job description
Include tools your virtual assistant should be proficient in, like excel, PowerPoint, or Gmail. Share preferred experience levels and skills. And don’t forget a detailed list of the tasks they’ll be performing. It’s also helpful to describe the scale of your request or business.
If you anticipate your virtual assistant will need to be adept at managing a busy inbox full of requests from fellow executives and enterprise clients, set that expectation in the job description to attract well-qualified candidates.
3. Include an applicant test
Include a test in your application. If you’re a content manager hiring a virtual assistant to manage guest contributors, have them answer a few fake email prompts or schedule several editorial slots on an imaginary calendar. By testing their abilities, you’ll be able to separate those exaggerating their skills from the rest.
4. Add a keyword or 'Easter Egg' in your job posting
This is especially helpful for sites where you post virtual assistant job descriptions and available job seekers apply. Add a line at the bottom of your job description asking applicants to "Include their favorite Steve Jobs quote" in their reply. This ensures you weed out assistants who haven’t actually read your email or are not detail-oriented.
5. Conduct an interview
When possible, conduct an interview. While some virtual assistant companies pair you with an assistant from their database, others allow you to meet with your assistant so both sides can determine fit. If you’re able to conduct an interview, include questions like:
"How do you manage shifting priorities?"
"How do you structure your work day?"
"Tell me about a time when you’ve faced a stressful situation at work. How did you respond?"
These questions will give you insight into the intangible qualities not present in a resume or assistant profile.
6. Start on a trial basis
Again, this is not always possible. If you do choose a company that allows you to trial your assistant, make sure you communicate that early, so both parties are aware there’s an exit if it isn’t a good match. Usually, two weeks is sufficient for deciding whether you’ll work well together.
7. Take time to train your assistant
In order for this to work and for it to save you time, it’s crucial your assistant is well-trained. Invest time during your first few weeks answering questions, providing comprehensive documentation of the tasks they’ll be performing, and explaining why and how you prefer each task to be completed.
8. Have realistic expectations
You’re hiring a virtual assistant, not a full-time employee. There’s a reason you decided not to bring this role in-house, so don’t expect the same loyalty, understanding of your business, or rapport with your virtual assistant as you would a careered professional. Keeping your expectations in perspective is key to finding and maintaining a healthy working relationship with your assistant.
9. Don’t be afraid to cuts ties and move on quickly
That said, if your virtual assistant isn’t working out -- don’t be afraid to sever the relationship quickly. Reach out to customer support for direction on how to move forward.
How to Use a Virtual Assistant
Provide time for onboarding
Overcommunicate
Provide ample documentation
Have realistic expectations
Prioritize rapport
Know when the position should be a full-time hire
1. Provide time for onboarding
Don't expect your virtual assistant to be fully ramped after week one. Depending on the type of work they're doing — and how many hours they're working for you each week — it may take them longer to ramp than a full-time employee. Because they're likely balancing a few clients at a time, it can take weeks for VAs to become familiar with your business and industry.
If possible, put your VA through the same training and onboarding process as you have full-time staff undergo. It will provide valuable context for your VA around your business, company goals, and customers. Just make sure you're paying your assistant for their time during onboarding as well.
2. Overcommunicate
During their first week on the job, schedule daily check-ins via Slack, phone call, or video meeting to ask how your virtual assistant is settling, review any questions they have from the day, and discuss any outstanding issues or projects from the day or week.
If, for example, your virtual assistant is writing email correspondence for you, take time to review your latest round of edits in which you provide feedback on your VAs work and allow them to ask questions of you.
3. Provide ample documentation
Prior to your virtual assistant's start date, write out detailed instructional documents for each of the tasks they'll be working on. For example, if you're hiring someone to help you with prospecting on LinkedIn. Write out each step of your prospecting process, best practices for your company, and who to contact for specific questions.
Include screenshots, when possible. When your how-to guide is finished, walk your virtual assistant through the document in a comprehensive training session. And let them keep the training document to refer back to during their first few weeks completing your tasks.
4. Have realistic expectations
Your virtual assistant is not a full-time employee of your company. They likely have other client work on their plate and cannot be expected to prioritize your company's work over another's.
They won't be as invested in your company's goals or culture, and they have more freedom to push back on deadlines or timelines as their availability fluctuates.
5. Prioritize rapport
Just because your virtual assistant provides as-needed support doesn't mean you shouldn't make them feel as welcome or part of the team as you would a new full-time employee.
Host a welcome lunch, introduce them to the other members of your team, and onboard them as you would any other new-hire at your company. The more integrated your virtual assistant feels into your company, the more they'll be invested in producing work that aligns with your values and goals.
6. Know when the position should be a full-time hire
When you're consistently booking extra hours with your virtual assistant, shopping for a second virtual assistant, or your business needs another full-time generalist, consider hiring a salaried employee.
Continuing to outsource tasks that comprise a full-time position will put strain on your other employees, your business, and your virtual assistant, which leads to burnout and stalled growth.
Real Estate Virtual Assistant
Real estate virtual assistants complete small tasks, like responding to emails, updating listings, and following up with leads. This allows agents more time to work with existing clients on closing deals that will grow their business and earn referrals.
Mod Virtual, Real Support, TaskBullet, and Conversational Receptionists all offer virtual assistants specializing in real estate. Virtual transaction coordinators gather and organize the deluge of paperwork required for closing transactions.
Sales assistants identify qualified leads or lead sources and conduct initial outreach. And generalists keep your calendar in order, erect yard signs in new properties, and handle data entry by updating listings on your MLS, Zillow account, or CRM.
Here are a few other areas in which real estate virtual assistants can help your business:
Build buyer’s packets
Manage transactions
Data entry
PowerPoint or presentation design
Client feedback
Graphic design for mailers, websites, or social media
Social media management
Write blog posts or emails
Lead nurturing
Prospecting
Client gift management
Website link building
If you’re hyper-focused on growing your real estate business, consider hiring a real estate virtual assistant. The value they bring can be priceless.
You’ve done enough. Really. Give yourself a break and do the work that counts. Consider hiring a virtual assistant and see what they can do for your well-being and professional growth. And check out this post for more tips on sales tools for small businesses.

0 notes
Text
300+ TOP SAP CRM Interview Questions and Answers
SAP CRM Interview Questions for freshers experienced :-
1. What Is Sap crm? SAP CRM (Customer Relationship Management) is a software tool provided by SAP to support end to end customer related supports. It handles various activities like invoicing, delivery, decision making, accounts receivable and so on. 2. What is master data in sap crm ? Master Data is org & CP baqsic data which are mandatory for creating org & CP in CRM system. EX: Org Name & adress detaisl & Contact details and CP related Names and contact details. 3. what is the action profile in sap crm?how to use complaints and returns life cycle in service process ? Action Profile is a Post Processing Frame work (PPF) which gives some output (like as smart form, fax, document ) on given conditions. And this is used in every place in SAP CRM where we define the Conditions for the successful implementation of the activity. like in Opportunity Management,Monitoring the Activity of the enterprise employees etc. 4. What is the relation between crm and sapr3 architecture ? R 3 Means ( Three tier architechture ) 1st Tier ( R1 ) launched at the time of SAP inception with five x ibm employees , later on 2 nd & 3 rd tier had come in the form of advanced . Now latest is My SAP CRM. R 3 actual Nomeneclature is ( ECC - Enterprise Central Component ) CRM acts as a central server attached to its external systems such as ( BIW , ECC & Third party systems , etc ). Eg : If a client has already had installed SAP ECC ( R3 ) and wants to upgrade with SAP CRM , in this scenario , we have to integrate or fetch some data related to Sales , Pricing Conditions etc thru R 3 / ECC . This is done thru middle ware concept ( connectivity ) , for which you should posses knowledge on the middleware concepts 5. What is the difference between R/3 AND CRM ? R/3: ERP CRM:Customer Centric Extended ERP, process, functions revolves around Customer. R/3:Three Tier architecture,Client,Server product CRM:Internet enabled, no need to have client software.Only internet browser 6. Explain some example of business object, customizing object, condition object ? Business objects are business partner sales order etc customizing objects are customizing country, customizing time zone etc, conditions objects are pricing related. 7. Quotation transaction type comes under which functionality in CRM ? Quotation transaction type: AG Functionality: Create or Generate leads with Marketing Campaign Track, qualify and close oppt Manage and track ERP quotations Process ERP Sales Orders Fulfill logistics needs Process invoices in ERP Manage account payables 8. What is the standard transaction type for quatation ? Transactio type - AG Item category - AGN 9. How to enhance BP ? Key features of the Easy Enhancement Workbench include the following: Wizard for adding new fields and new tables to business partner master data No required detailed knowledge of the development environment and data model Wizards for the extension process 10. Can we download data from datasets/Info sets ? Attribute sets, Info sets, BW query and ELM are the different data sources for segmentation.

SAP CRM Interview Questions 11. How many types of campaign are their ? There are different types of campaigns like E-mail campaigns, Call list can be generated, Campaigns can be run to create leads etc., 12. What type of Business Scenario you are following in you Project? Business Scenario means what ? Business scenario is nothing but what is the process, like for example how is the CRM application used by your client. Example: for us the sales reps from different location in US raise the sales orders in the CRM system and they flow to R/s and we also implemented the marketing module to run the e-mail campaigns for the product promotions. 13. How to find target group & what is the flow of BP to Target group ? In marketing to execute a campaign you need a Target group.Target group in simple words is nothing but a group of BP's. You can create a target group in segment builder (T-code CRMD_MKTSEG). 14. What is Activity Journal ? With activity journals, you can record and update information gathered from customer visit or telephone calls. For example activity journals can contain: Products or product categories Product-related information such as what products were discussed with the customer or the number of samples given to the customer 15. What is the rule of organizational determination ? There are two types of Organizational determination rules. Organization determination rule: The respective organization is determined based on the organization or general attributes assigned to the organization in the organizational model. Responsibility rule: In this rule, the Org attributes are not considered and the responsible Organization unit is assigned directly. 16. In Delta download which table is retrieve from R/3 to CRM ? Based on the filters set initially for different object types whenever the data is modified or deleted the same will be replicated to CRM from R3 in the form of Bdocs or Idocs. 17. What is Task & Activity ? There are two kinds of Activities, which are called as Tasks and Business activities.A Business activity contains information about business partner interaction on a particular date A Task contains information about what one or more employees have to complete by a particular date. In very simple words Tasks are activities in which the BP is not involved and activities are in which the BP data is involved. 18. Role of a functional consultant. A functional consultant evaluates the demands in talking with the customer’s representatives, transforms the essence into an abstract and algorithmic business model. Hence, he identifies the use cases and transforms them into logical and technical views. Then the main task starts: customizing the respective business area and making sure the system reacts in the manner according to the constraints of the requested use case. The consultant documents the settings and prepares proper guidelines that allow other consultants to do further changes or repairs with due efforts. The consultant takes care that proper training is given to the users and that the system is usable, performing appropriately and the business flow is complete and correct. During go live he assists the technical staff by testing the behaviour of the system. After go live he guarantees that the procedures remain usable and consistent in real live situation and proposes enhancements. The main duty of a consultant is to transfer external know-how to the client. It is not manpower that counts but intelligence, understanding of processes, a feeling for defects and general a common sense. 19. Role of a Functional Consultant in an End To End Implementation When you talk about the role of a Functional consultant in an end to end implementation, I think it won’t be possible for me or anybody to define everything but I will try to summarize it: Functional consultant is expected to generate knowledge about the current business process, design current business flows, study current business processes and its complication, in all we can say getting through with current business setup. Flow diagrams and DFD are prepared, most of the time in Vision format, all this forms the part of AS IS document. Everything configured has to be documented as per their categories in the form of predefined templates, these have to be then approved by the team leads or who ever the consultant is reporting to. Mapping and GAP analysis is done for each module, I have seen people defining integration after mapping, gap analysis and configuration is done, but as per my experience in implementation, it is a simultaneous process. Before starting configuring future business processes in SAP, the DFD/ERD are prepared, this documentation is called TO BE, which can be also siad as the result of mapping and gap analysis. Sometimes Functional consultants are also expected to prepare test scripts for testing the configured scenarios. End user manual and user training is also expected from F.Consultants. The project normally starts off with a Kick off meeting in which the team size, team members, reporting system, responsibilities, duties, methodlogy, dates and schedules, working hours which have been predicided are formally defined. ASAP, it won’t be possible for me to explain it here, but all I can tell you about it is that it is SAP standard implementation methodology, which SAP prescribes but is not mandatory for any company to follow, such as IBM follow some blue Methodlogy, some companies follow typical SDLC steps, ASAP stands for Accerlated SAP, you can find all the steps on SAP site, through google, reading it from there won’t give you a great knowledge about ASAP but will obviously get you to know the definitions of various term. 20. How is CRM and R/3 differ from each other? R/3 is an integration of different application suits. It has its own architecture and way fo functioning. CRM is all about maintaining the relationship with a customer. It is supposed to enhance the profit of the company or organisation since the ultimate goal of any company is profit. Therefore CRM is one step ahead for their goal achievements. SAP R/3 is a 3 tier based client/ server based application. One layer is presentation layer (Client) which interfaces with the end user. Second layer is application layer for all business – specific requirements (Program), and third is database which contains all information and records about the system, including transcational and configration data. SAP R/3 has been developed in it’s own language called ABAP (Advanced business application programming). 21. Advantages of CRM Using CRM, a business can: Provide better customer service Increase customer revenues Discover new customers Cross sell/Up Sell products more effectively Help sales staff close deals faster Make call centers more efficient Simplify marketing and sales processes The types of data CRM projects collect Responses to campaigns Shipping and fulfillment dates Sales and purchase data Account information Web registration data Service and support records Demographic data Web sales data 22. What is Task & Activity? Basically there are two kinds of Activities, which are called as Tasks and Business activities. A Business activity contains information about business partner interaction on a particular date A Task contains information about what one or more employees have to complete by a particular date. In very simple words Tasks are activities in which the BP is not involved and activities are in which the BP data is involved. 23. How to integrate R/3 with CRM? To exchange data between ECC ( R3 ) and CRM systems we need to maintain connectivity for both systems. Please ask your Basis consultant to do the following configuration. Maintain Logical Systems in both systems and link with respective clients. Maintain RFC destinations in both systems pointing to each other system. Maintain Number ranges as mirror images in both systems. Ex: Maintain same number range in ECC as Internal and in CRM as External or vice versa. Below are the steps for the integration between R/3 & CRM : SAP ECC : Define logical system for ECC ( Name ) Define logical system for CRM ( To establish the cross connection ) Identify the data which you wanted to copy to crm Assign logical system to the client SAP CRM : Define logical system for CRM Define logical system for ECC Assign logical system to client Copy the required data from ECC . 24. What is master data in sap crm? Master Data is org & CP baqsic data which are mandatory for creating org & CP in CRM system. EX: Org Name & adress detaisl & Contact details and CP related Names and contact details 25. How to enhance BP? You can enhance the business partner from Easy Enhancement Workbench (EEW) Key features of the Easy Enhancement Workbench include the following: Wizard for adding new fields and new tables to business partner master data No required detailed knowledge of the development environment and data model Wizards for the extension process 26. What is Activity Journal? With activity journals, you can record and update information gathered from customer visit or telephone calls. For example activity journals can contain: Products or product categories Product-related information such as what products were discussed with the customer or the number of samples given to the customer 27. In Delta download which table is retrieve from R/3 to CRM? It’s not just one table or a specific table that is retrieved from R/3 to CRM. Based on the filters set initially for different object types whenever the data is modified What is the rule of organizational determination?or deleted the same will be replicated to CRM from R3 in the form of Bdocs or Idocs. 28. There are two types of Organizational determination rules. Organization determination rule: The respective organization is determined based on the organization or general attributes assigned to the organization in the organizational model. Responsibility rule: In this rule, the Org attributes are not considered and the responsible Organization unit is assigned directly. 29. At the time of Implemention, What type of problem you generally face? There will be different phases in Implementation, you actually do a lot of brain storming sessions in the blue print phase and in the realization phase you do all your trials and configurations or may be experiments :) in the sand box. So you can’t really say there are specific problems. It actually involves a lot of discussions. 30. What is the standard transaction type for quatation? Transactio type - AG Item category - AGN 31. How can links be maintained between various sub opportunities and asingle opportunity? Project profile can help in maintaining the link between an opportunity and other various sub opportunities. 32. Define CRM Marketing? CRM Marketing is considered to be the main components used to maintain good Customer Relationship Management and are used in planning actions marketing activities. Analysis of various segments of marketing is all done with the help of CRM Marketing. 33. Define Market Plan? The market plan is used for the implementation of the market policy of an organization. 34. What are the benefits of CRM? CRM benefits are wide-ranging – from higher levels of customer engagement, loyalty, and revenue to lower costs and smarter customer-facing activities. Explore some of the top benefits of CRM systems below. Increase the sales and revenue Access deep customer insights Highly targeted marketing Boost customer satisfaction Easy for internal and external collaboration 35. What is Marketing Permissions Assignment Block (AB)? Depending on your legal requirements, you can use some or all of the following fields in the Marketing Permissions assignment block for accounts and contacts assigned to an account: Communication Channels - Specifies how marketing messages can be communicated, for example by e-mail, letter, or SMS. You configure values for communication media in Customizing of campaign execution. Form of Consent - Specifies how the account or contact communicated the consent information, for example by letter or by e-mail. You configure values for the form of consent in Customizing. Date of Consent - Specifies the date on which the account gave or rejected consent Consent - Specifies the consent status as Given or Rejected Communication Details - Specifies the e-mail address, telephone number, pager or so on that can be used, or must not be used for accounts and contact. 36. What is Master Data? Master data comprise data about basic objects used in business transactions in SAP Customer Relationship Management (SAP CRM) and stored on a long-term basis, such as data on accounts, products, installed bases, or warranties. 37. What is Organizational Management in CRM? Organizational Management in CRM offers you a flexible tool for displaying your company’s task-related, functional organizational structure as a current organizational model. Displaying your service or sales and distribution structure is at the forefront of CRM. To work with SAP CRM, you can simply display the organizational units that are relevant for your sales and service-related processes CRM organizational management has many options for linking to your organizational units: The organizational units (for example, sales organization, service organization) are not already specified: You can include your own organizational levels and leave levels out. The SAP ECC organizational units (for example, sales organization, distribution channel, division, maintenance processing plant) can be assigned as attributes to the organizational units in CRM. These attributes are not mandatory for planning the organizational model. However, they are required for automatically determining organizational data in transactions. You can activate an organization to be used for several scenarios, enabling it to be a sales organization and a service organization at the same time. The organizational model is time-dependent. This enables you to plan organizational changes in the future. Organizational units can occur as business partners. The system automatically creates a business partner record for an organizational unit with the organizational unit role. 38. What are the differences in the Organizational Data in SAP ECC (SD) and CRM? Organizational management in SAP CRM offers a flexible tool for maintaining the company structure for different scenarios (Sales, Service and Enterprise Buyer Professional). SAP ECC component Sales and Distribution (SD) You maintain the sales organization in Customizing Organization Settings. You maintain the organizational plan for HR and Workflow independently in Business Management (Basis). Organizational data in Sales and Distribution is static, changes in organizational data result in major changes in Customizing. Responsibilities are proposed from the sales area-related data from the customer master SAP CRM component Organizational Data You maintain the organizational model once for all applications in CRM. Scenario-specific data in the structure is assigned by attributes to the organizational units. These attributes are passed onto subordinate organizational units. Organizational models can be maintained and adapted dynamically. Responsibilities are defined independently from the business partner master and are determined, if required, from the organizational model. 39. What are Organizational Objects? Objects used for the object-orientated design of Organizational Management when structuring an organizational model. The following object types are available in CRM: Organizational unit Position 40. What is Organizational Management in SAP CRM? Organizational Management in CRM offers you a flexible tool for displaying your company’s task-related, functional organizational structure as a current organizational model. 41. Define campaign management? For the improvement of the sales, campaign management is used by an organization. It includes creating campaigns. SAP CRM Questions and Answers Pdf Download Read the full article
0 notes
Photo

Firefox 69, and a thorough introduction to D3.js
#453 — September 6, 2019
Read on the Web
JavaScript Weekly

An Introduction to D3.js — A fantastic, well presented introduction to D3, a popular JavaScript-based data-visualization library, and its ecosystem of modules.
Amelia Wattenberger
Firefox 69 Released; Now Supports Public Instance Fields (and More) — Firefox 69 went out on the main Release channel this week and for JS developers, the inclusion of public instance fields will be of interest. The Resize Observer API and the Microtasks API are now also available to use and the JS debugger has gotten many improvements too.
Mozilla Hacks
Image & Video Management Made for Developers — Simplify and automate the process of uploading, manipulating, optimizing, and delivering images and videos across every device at any bandwidth. Try Cloudinary. See how easy media management can be. Get your own free account today.
Cloudinary sponsor
Apple Just Shipped Web Components to Production and You Probably Missed It — Apple just launched a Web-based client for their Apple Music service and several developers noticed what tech they’re using to make it tick (namely Ember, Web Components, and Stencil JS).
Max Lynch
▶ 21 Talks from React Rally 2019 — The React Rally event took place in Salt Lake City just two weeks ago but already lots of the talks are up and ready to watch.
React Rally
A Google Developer's Feedback on TypeScript — “We recently upgraded Google to use TypeScript 3.5. Here is some feedback on the upgrade.” We also learn Google only uses a single version of TypeScript that’s updated for everyone simultaneously.
Evan Martin
Using void in JavaScript and TypeScript — void means rather different things in JS and TypeScript and does some things I hadn’t expected too.
Stefan Baumgartner
💻 Jobs
Work with Giant, Caged Robots, and Node.js; Senior Developer, London — So, about the robots: They live in cages, travel at 60mph, and they’re controlled via AMQ messages from a Node-based Warehouse Management System.
CareerJS
JavaScript Developer at X-Team (Remote) — Join the most energizing community for developers. Work from anywhere with the world's leading brands.
X-Team
Find a JavaScript job through Vettery — Make a free profile, name your salary, and connect with hiring managers from top employers.
Vettery
📘 Tutorials
5 Handy Applications of Array.from() — Array.from() transforms array-like objects to arrays and can be used to generate ranges, remove duplicates, and clone arrays.
Dmitri Pavlutin
Creating Drag and Drop Elements with Vanilla JavaScript and HTML — I remember when this used to be really complicated to do, but the HTML Drag and Drop API helps a lot nowadays.
Jess Mitchell
Score SOC 2 Compliance Quick Wins Using Git: A Developer's Guide
Datree.io sponsor
Debugging TypeScript in Firefox DevTools — Firefox Debugger has evolved a lot in the last several months and while it’s well suited for working with JavaScript, it’s possible to debug TypeScript too thanks to source maps. Here’s a basic example.
Jan Honza Odvarko
You Already Use Types — A post aimed firmly at skeptics and newcomers to type systems.
Shawn 'swyx' Wang
Simplify Your JavaScript with .some() and .find() — If you haven’t revised the array methods in recent years, you might be missing out and reinventing the wheel in your code.
Etienne Talbot
Some Practical Uses of Symbols in JavaScript and TypeScript
Stefan Baumgartner
Creating a Simple JavaScript Obfuscator — Obfuscating a language that’s ultimately run in an interpreted style can often seem like a pointless endeavor, but it’s neat to see the process adopted here.
Antoine Vastel
Writing Data to InfluxDB with Python
InfluxData sponsor
▶ Discussing Functional Programming with Brian Lonsdorf — A 45 minute podcast chat about the fundamentals of functional programming and comparisons with object oriented approaches.
JavaScript Jabber podcast
An App Security Expert's POV on Dependency Management — An application security expert’s point of view over what practices you should be adopting on your own projects.
Adam Baldwin (npm, Inc.) node
🔧 Code and Tools

Bitmelo: An Online Environment for Creating JavaScript Games — It’s early days for this interesting project, but it’s basically an online sandbox geared to creating and working on simple JavaScript games, complete with tile, sound, map, and code editors.
David Byers
Cytoscape.js: A Graph Theory/Network Library for Visualization and Analysis — Handy if you need to model and/or visualize relational data, like biological data or social networks.
Max Franz
MongoDB Atlas is a Powerful and Reliable Cloud Database. Try Now
MongoDB Atlas sponsor
Angular Tools for High Performance — Contains a list of new tools and practices that can help in the building of faster Angular apps and to monitor their performance over time.
Minko Gechev
instant.page 2.0: Preload Link Target Pages ASAP — You include some JavaScript in your page and the browser will begin to preload the destination page the second someone clicks on a link. This can result in a slight, but noticeable, performance increase.
Alexandre Dieulot
SpaceTime: A Timezone Library with No Dependencies — Supports daylight savings, leap years, and hemispheres, and lets you calculate times in different timezones.
Spencer Kelly
vue-treeselect: A Multi-Select Component for Vue.js with Nested Options Support — There’s a lot of documentation and examples to enjoy here.
Fangzhou Li
Jimp: Image Processing in Node with No Native Dependencies — Want to get your resizing, cropping, color manipulation, or dithering on without any external dependencies?
Oliver Moran node
Redux Persist: Persist and Rehydrate a Redux Store
Zack Story
Build a JS Interpreter in JavaScript Using Acorn as a Parser
Chidume Nnamdi
How to Build a Search App for Unsplash with Svelte 3 — Use Svelte 3 and the Intersection Observer API to build a basic search tool for the Unsplash stock photography collection.
Ayo Isaiah
⚡️ Quick Releases
Node 12.10 — The ever-popular JavaScript platform.
Handlebars.js 4.2 — Long standing templating library.
VuePress 1.0.4 — Vue-powered static site generator.
Riot 4.5 — Simple and elegant component-based UI library.
RxDB 8.4 — A realtime database for JavaScript apps.
by via JavaScript Weekly https://ift.tt/2PP0ufy
0 notes
Photo

The Screaming Frog SEO Spider has evolved a great deal over the past 8 years since launch, with many advancements, new features and a huge variety of different ways to configure a crawl. This post covers some of the lesser-known and hidden-away features, that even more experienced users might not be aware exist. Or at least, how they can be best utilised to help improve auditing. Let’s get straight into it. 1) Export A List In The Same Order Uploaded If you’ve uploaded a list of URLs into the SEO Spider, performed a crawl and want to export them in the same order they were uploaded, then use the ‘Export’ button which appears next to the ‘upload’ and ‘start’ buttons at the top of the user interface. The standard export buttons on the dashboard will otherwise export URLs in order based upon what’s been crawled first, and how they have been normalised internally (which can appear quite random in a multi-threaded crawler that isn’t in usual breadth-first spider mode). The data in the export will be in the exact same order and include all of the exact URLs in the original upload, including duplicates, normalisation or any fix-ups performed. 2) Crawl New URLs Discovered In Google Analytics & Search Console If you connect to Google Analytics or Search Console via the API, by default any new URLs discovered are not automatically added to the queue and crawled. URLs are loaded, data is matched against URLs in the crawl, and any orphan URLs (URLs discovered only in GA or GSC) are available via the ‘Orphan Pages‘ report export. If you wish to add any URLs discovered automatically to the queue, crawl them and see them in the interface, simply enable the ‘Crawl New URLs Discovered in Google Analytics/Search Console’ configuration. This is available under ‘Configuration > API Access’ and then either ‘Google Analytics’ or ‘Google Search Console’ and their respective ‘General’ tabs. This will mean new URLs discovered will appear in the interface, and orphan pages will appear under the respective filter in the Analytics and Search Console tabs (after performing crawl analysis). 3) Switching to Database Storage Mode The SEO Spider has traditionally used RAM to store data, which has enabled it to crawl lightning-fast and flexibly for virtually all machine specifications. However, it’s not very scalable for crawling large websites. That’s why early last year we introduced the first configurable hybrid storage engine, which enables the SEO Spider to crawl at truly unprecedented scale for any desktop application while retaining the same, familiar real-time reporting and usability. So if you need to crawl millions of URLs using a desktop crawler, you really can. You don’t need to keep increasing RAM to do it either, switch to database storage instead. Users can select to save to disk by choosing ‘database storage mode’, within the interface (via ‘Configuration > System > Storage). This means the SEO Spider will hold as much data as possible within RAM (up to the user allocation), and store the rest to disk. We actually recommend this as the default setting for any users with an SSD (or faster drives), as it’s just as fast and uses much less RAM. Please see our guide on how to crawl very large websites for more detail. 4) Request Google Analytics, Search Console & Link Data After A Crawl If you’ve already performed a crawl and forgot to connect to Google Analytics, Search Console or an external link metrics provider, then fear not. You can connect to any of them post crawl, then click the beautifully hidden ‘Request API Data’ button at the bottom of the ‘API’ tab. Alternatively, ‘Request API Data’ is also available in the ‘Configuration > API Access’ main menu. This will mean data is pulled from the respective APIs and matched against the URLs that have already been crawled. 5) Disable HSTS To See ‘Real’ Redirect Status Codes HTTP Strict Transport Security (HSTS) is a standard by which a web server can declare to a client that it should only be accessed via HTTPS. By default the SEO Spider will respect HSTS and if declared by a server and an internal HTTP link is discovered during a crawl, a 307 status code will be reported with a status of “HSTS Policy” and redirect type of “HSTS Policy”. Reporting HSTS set-up is useful when auditing security, and the 307 response code provides an easy way to discover insecure links. Unlike usual redirects, this redirect isn’t actually sent by the web server, it’s turned around internally (by a browser and the SEO Spider) which simply requests the HTTPS version instead of the HTTP URL (as all requests must be HTTPS). A 307 status code is reported however, as you must set an expiry for HSTS. This is why it’s a temporary redirect. While HSTS declares that all requests should be made over HTTPS, a site wide HTTP -> HTTPS redirect is still needed. This is because the Strict-Transport-Security header is ignored unless it’s sent over HTTPS. So if the first visit to your site is not via HTTPS, you still need that initial redirect to HTTPS to deliver the Strict-Transport-Security header. So if you’re auditing an HTTP to HTTPS migration which has HSTS enabled, you’ll want to check the underlying ‘real’ sitewide redirect status code in place (and find out whether it’s a 301 redirect). Therefore, you can choose to disable HSTS policy by unticking the ‘Respect HSTS Policy’ configuration under ‘Configuration > Spider > Advanced’ in the SEO Spider. This means the SEO Spider will ignore HSTS completely and report upon the underlying redirects and status codes. You can switch back to respecting HSTS when you know they are all set-up correctly, and the SEO Spider will just request the secure versions of URLs again. Check out our SEOs guide to crawling HSTS. 6) Compare & Run Crawls Simultaneously At the moment you can’t compare crawls directly in the SEO Spider. However, you are able to open up multiple instances of the software, and either run multiple crawls, or compare crawls at the same time. On Windows, this is as simple as just opening the software again by the shortcut. For macOS, to open additional instances of the SEO Spider open a Terminal and type the following: open -n /Applications/Screaming Frog SEO Spider.app/ You can now perform multiple crawls, or compare multiple crawls at the same time. 7) Crawl Any Web Forms, Logged In Areas & By-Pass Bot Protection The SEO Spider has supported basic and digest standards-based authentication for a long-time, which are often used for secure access to development servers and staging sites. However, the SEO Spider also has the ability to login to any web form that requires cookies, using its in-built Chromium browser. This nifty feature can be found under ‘Configuration > Authentication > Forms Based’, where you can load virtually any password-protected website, intranet or web application, login and crawl it. For example you can login and crawl your precious fantasy football if you really wanted to ruin (or perhaps improve) your team. This feature is super powerful because it provides a way to set cookies in the SEO Spider, so it can also be used for scenarios such as bypassing geo IP redirection, or if a site is using bot protection with reCAPTCHA or the like. You can just load the page in the in-built browser, confirm you’re not a robot – and crawl away. If you load the page initially pre-crawling, you probably won’t even see a CAPTCHA, and will be issued the required cookies. Obviously you should have permission from the website as well. However, with great power comes great responsibly, so please be careful with this feature. During testing we let the SEO Spider loose on our test site while signed in as an ‘Administrator’ for fun. We let it crawl for half an hour; in that time it installed and set a new theme for the site, installed 108 plugins and activated 8 of them, deleted some posts, and generally made a mess of things. With this in mind, please read our guide on crawling password protected websites responsibly. 8) Crawl (& Remove) URL Fragments Using JavaScript Rendering Mode Occassionally it can be useful to crawl URLs with fragments (/page-name/ when auditing a website, and by default the SEO Spider will crawl them in JavaScript rendering mode. You can see our FAQs which use them below. While this can be helpful, the search engines will obviously ignore anything from the fragment and crawl and index the URL without it. Therefore, generally you may wish to switch this behaviour using the ‘Regex replace’ feature in URL Rewriting. Simply include within the ‘regex’ filed and leave the ‘replace’ field blank. This will mean they will be crawled and indexed without fragments in the same way as the default HTML text only mode. 9) Utilise ‘Crawl Analysis’ For Link Score, More Data (& Insight) While some of the features discussed above have been available for sometime, the ‘crawl analysis‘ feature was released more recently in version 10 at the end of September (2018). The SEO Spider analyses and reports data at run-time, where metrics, tabs and filters are populated during a crawl. However, ‘link score’ which is an internal PageRank calculation, and a small number of filters require calculation at the end of a crawl (or when a crawl has been paused at least). The full list of 13 items that require ‘crawl analysis’ can be seen under ‘Crawl Analysis > Configure’ in the top level menu of the SEO Spider, and viewed below. All of the above are filters under their respective tabs, apart from ‘Link Score’, which is a metric and shown as a column in the ‘Internal’ tab. In the right hand ‘overview’ window pane, filters which require post ‘crawl analysis’ are marked with ‘Crawl Analysis Required’ for further clarity. The ‘Sitemaps’ filters in particular, mostly require post-crawl analysis. They are also marked as ‘You need to perform crawl analysis for this tab to populate this filter’ within the main window pane. This analysis can be automatically performed at the end of a crawl by ticking the respective ‘Auto Analyse At End of Crawl’ tickbox under ‘Configure’, or it can be run manually by the user. To run the crawl analysis, simply click ‘Crawl Analysis > Start’. When the crawl analysis is running you’ll see the ‘analysis’ progress bar with a percentage complete. The SEO Spider can continue to be used as normal during this period. When the crawl analysis has finished, the empty filters which are marked with ‘Crawl Analysis Required’, will be populated with lots of lovely insightful data. The ‘link score’ metric is displayed in the Internal tab and calculates the relative value of a page based upon its internal links. This uses a relative 0-100 point scale from least to most value for simplicity, which allows you to determine where internal linking might be improved for key pages. It can be particularly powerful when utlised with other internal linking data, such as counts of inlinks, unique inlinks and % of links to a page (from accross the website). 10) Saving HTML & Rendered HTML To Help Debugging We occasionally receive support queries from users reporting a missing page title, description, canonical or on-page content that’s seemingly not being picked up by the SEO Spider, but can be seen to exist in a browser, and when viewing the HTML source. Often this is assumed to be a bug of somekind, but most of the time it’s just down to the site responding differently to a request made from a browser rather than the SEO Spider, based upon the user-agent, accept-language header, whether cookies are accepted, or if the server is under load as examples. Therefore an easy way to self-diagnose and investigate is to see exactly what the SEO Spider can see, by choosing to save the HTML returned by the server in the response. By navigating to ‘Configuration > Spider > Advanced’ you can choose to store both the original HTML and rendered HTML to inspect the DOM (when in JavaScript rendering mode). When a URL has been crawled, the exact HTML that was returned to the SEO Spider when it crawled the page can be viewed in the lower window ‘view source’ tab. By viewing the returned HTML you can debug the issue, and then adjusting with a different user-agent, or accepting cookies etc. For example, you would see the missing page title, and then be able to identify the conditions under which it’s missing. This feature is a really powerful way to diagnose issues quickly, and get a better understanding of what the SEO Spider is able to see and crawl. 11) Using Saved Configuration Profiles With The CLI In the latest update, version 10 of the SEO Spider, we introduced the command line interface. The SEO Spider can be operated via command line, including launching, saving and exporting, and you can use –help to view the full arguments available. However, not all configuration options are available, as there would be hundreds of arguments if you consider the full breath available. So the trick is to use saved configuration profiles for more advanced scenarios. Open up the SEO Spider GUI, select your options, whether that’s basic configurations, or more advanced features like custom search, extraction, and then save the configuration profile. To save the configuration profile, click ‘File > Save As’ and adjust the file name (ideally to something descriptive!). You can then supply the config argument to set your configuration profile for the command line crawl (and use in the future). --config "C:UsersYour NameCrawlssuper-awesome.seospiderconfig" This really opens up the possibilites for utlising the SEO Spider via the command line. What Have We Missed? We’d love to hear any other little known features and configurations that you find helpful, and are often overlooked or just hidden away. The post 11 Little-Known Features In The SEO Spider appeared first on Screaming Frog.
0 notes
Text
Convertica - Business Leads Email Outreach Case Study


Interview with NinjaOutreach user, Kurt Philip, Managing Director of Convertica
Convertica is a done-for-you website conversion optimization services company.
“Ninja Outreach was able to satisfy all our needs, so there wasn’t a need to trial […] other […] options.” - Kurt Philip of Convertica
Results:
Significantly sped up Convertica’s email outreach campaigns through automated follow-ups. Higher efficiency led to better open rates of over 50%, CTA click-through rates of up to 20%, and reply rates up to 12%.
1. What specific goal have you achieved with NinjaOutreach?
Our primary goal with Ninja Outreach is to land clients for our “Done for you CRO Services.” Our prospects right now are divided into 90% Affiliate website owners and 10% Lead Generation website owners.
2. How many campaigns did you launch to achieve this goal? What was your reply rate? How many emails did you send and how many positive responses did you get?
We usually contact 10-15 prospects every alternate day ( Typically Tuesday, Thursday and Friday ) with 2 initial follow-ups in a campaign excluding the weekends.

We typically have around 50%+ open rates, 15-20% click rates for our Blog posts links as well as “Schedule a call with us” links and about 10-12% Reply rates for our campaigns.

3. What other tools (if any) did you use for this campaign and why?
Since we run a CRO Business, traffic is the first thing that we look at before we start pitching potential prospects.
So Ahrefs is the #1 tool that we use to prospect websites to see if they have sufficient traffic. We also use the Batch Analysis tool and the Competing domains section in Ahrefs heavily.
We also use Linkedin typically for websites above 500K+ traffic, since we want to reach the right prospect rather than sending the email to a general email address.
For Email Verifications, we use typically use 5+ tools since each serves a different purpose: Hunter.io, ZeroBounce, snov.io, MailTester.com, and email-verifier.online-domain-tools.com.
4. How did you use NinjaOutreach?
We use Ninja Outreach as an Email broadcast tool.
Our process is straight forward. We collect 10-15 prospects manually every alternate day that we think are suitable for our services where we can get them a definite increase in conversions/revenue with CRO.
We upload them into Ninja Outreach, and schedule 2-3 follow-ups that’s highly personalized to them.
5. What outreach strategies did you find worked best? (best template, best approach, best schedule to send outreach, etc)
Here’s the overview of the 1st email and the next 2 follow-ups that we typically send for the prospects. We slightly modify them based on the site type.
1st Email just asks them a question if they had any done any CRO in the past as well as the minimum revenue increase that we promise if they work with us as well links to our blog posts page where they can read about our process and the case studies.
2nd Email / 1st Follow up: We let them know the things that we will be testing on their site to increase conversions. Since the majority of our prospects are Affiliate and Lead Gen sites, we typically find big wins testing the Comparison tables and the Review section areas for Affiliate sites. If it’s going to be a Lead Generation website, optimizing their contact form would give the best results.
Since we can find their high traffic pages with Ahrefs, we personalize a step further.
Here’s a template that we developed and has worked best for us:
Hi Firstname,
To follow-up on our previous email regarding improving conversions on your site, we’ve identified a bunch of quick wins for you. A few to begin with would be:
List the Tip #1
List the Tip #2
List the Tip #3
These changes would be particularly effective on your pages:
1st High traffic page URL from Ahrefs
2nd High traffic page URL from Aherfs
3rd High traffic page URL from Ahrefs, due to their high traffic.
If you would like me to send you through some more info on a full CRO audit (including our new done-for-you service) let me know.
Alternatively you can schedule a call with us to discuss options for your site directly: https://convertica.org/schedule-call/
Cheers, Kurt
3rd Email / 2nd Follow up: We try to establish credibility with our prospects by sharing Case studies that we have done on authority websites. For example Affiliate websites, we have worked with Authority Hacker, and for Lead Gen sites we have worked with Empire Flippers and increased the conversions of their Website Valuation tool.
6. What problem did NinjaOutreach solve for you, or how was NinjaOutreach specifically able to help with your campaign?
Scheduled follow-ups - When we started looking at options in 2018 for an outreach tool, we wanted a tool that would allow us to do multiple follow-ups automatically so we could save a ton of time.
Blacklist option - Whenever a prospect isn’t interested in our services we wanted to make sure we don’t disturb them again. So we would add those leads to the Blacklist database as well to study the behavior of those leads so that we could improve our future sequences.
Sending New Sequences - Once the initial follow-ups are sent and if we decide to launch a new sequence the dashboard is pretty easy to schedule a new campaign. All we need to is select the List name and then the new template/ sequence that we created and then click on “Launch Campaign” and you are done.
7. Before NinjaOutreach, what was your process for prospecting and launching your campaigns?
When we decided to start outreach, we knew that we had to invest in a tool to start the process. We came down with 3 popular options and decided to trial one by one.
Luckily, Ninja Outreach was able to satisfy all our needs, so there wasn’t a need to trial the other 2 options.
But lately, Image and Video Personalization for Outreach has been making huge rounds. So that’s something I would love to see in Ninja Outreach at an affordable cost for everyone.
So to answer the question, we didn’t follow any manual process to send emails. We started our first outreach campaign with Ninja Outreach.
The post Convertica - Business Leads Email Outreach Case Study appeared first on NinjaOutreach.
from SM Tips By Minnie https://ninjaoutreach.com/convertica-business-leads-email-outreach-case-study/
0 notes
Text
A tutor’s guide to lit reviews
A while back I did a post on writing a basic academic analysis essay, prompted by repeated issues I’d seen during my work as a tutor. Based on similar concerns I’ve seen regarding other common writing projects, I’ve decided to expand this into a series. Today I’m going to tackle literature reviews.
I would like to emphasize right off the bat that all this advice is based on my experience both as a tutor and student with a humanities and social sciences background. Take what is useful to you, leave the rest, and definitely listen to your instructor over me.
First of all, what is a literature review? It’s a review of the literature – taking a look at what scholars have written about a certain topic. Literature reviews are often written before or as a component of a research paper. You want to know what other people are saying about a subject before you jump in yourself. What has been covered exhaustively? What is relatively agreed upon? What is disputed? What gaps exist – areas or angles that no one has yet investigated adequately? A literature review can help guide your own research by showing you which areas are worth probing into. When you write it, depending on exactly what your instructor is asking and whether the lit review is part of a longer paper, you may simply focus on the findings of these other scholars or do some more analysis work (what conclusions can you draw? What limitations do you notice?) Overall, it is less about making an original argument than about identifying trends or conclusions made by others, and your thesis will reflect that. Now, if the lit rev is part of a bigger research paper, your thesis will of course have to do with the research you are conducting.
Doing the Research
Before you start writing a lit review, you’ll need to gather the research you’re going to talk about. If you’re doing a big project like a dissertation, you might exhaustively track down everything you can find. If you’re writing a smaller paper, you’ll probably be less ambitious, especially if your topic is broad. (Imagine reading every article on Hamlet!) Try to make your topic as narrow as you can, first of all. Then prioritize articles that are current (especially if you are in a field that values currency such as STEM fields) and/or highly regarded. “Important” articles can often be identified by keeping an eye out for important researchers’ names and noting how often articles have been cited. Some databases like Web of Science will show you who is citing what, and Google Scholar is moving in that direction. More citations reflect an article that is making waves and probably worth looking at.
Once you have a good selection of articles, read through them. You may decide some don’t fit and discard them. Once you have a set you want to work with, identify their main arguments and points. That’s what your literature review will discuss.
Organization
A common mistake when writing a lit review is to organize it by source. The first body paragraph describes article #1, the second paragraph describes article #2, etc. Instead, the best way to organize a lit review is by concept. You're putting different scholars into conversation with each other. (Academia is a conversation – albeit often a very insular one.) What do most of the scholars seem to agree on? What areas do they disagree on?
As you're doing this, as I said earlier, you may be identifying gaps in the literature. What haven't people talked about? What might they be overlooking or not interpreting right?
Anatomy of a Lit Review
If you’re writing a bigger paper, the lit review will probably be a small portion wedged between your introduction and methodology. This post is mainly designed to help people writing a lit review that stands alone and requires its own introduction and conclusion.
Introduction
Your intro will start out by identifying your subject and justifying why it's important. Why focus on this? It will also identify any major trends you noticed in the literature and major conclusions you can draw (your thesis). If there are any terms or concepts that might be unfamiliar, outline them here, especially if you’re using terms in a way that might not be universal. You should also be clear about your scope – which portions of the subject are you concerned about (ex: caffeine use in young middle-class adults from 18-25). Here’s an example I did for a lit review on ebooks.
The rise of technology in libraries has allowed electronic or e-books – “digital objects specifically designed to be accessible online and read on either a handheld device or a personal computer” – to become a major part of the text-based world (Bailey, Scott, and Best 7). Authors have the opportunity to self-publish their work, students can read assigned chapters on their phones, and librarians can stock texts without having to make room on the shelves. According to the Huffington Post, four out of five publishers now regularly publish e-books (Bailey, Scott, and Best 6). Certainly, e-books are not going away. Instead, they are a growing phenomenon and one that librarians must consider carefully. Librarians face many issues when considering how much to supplement or replace their collections with e-books. Some problems are universal, while others vary between types of books and libraries. For the purpose of this paper, academic libraries and academic e-books will be considered.
I’ve defined ebooks (although there are some obvious holes in that definition), emphasized that they’re worth considering with some statistics, and identified the scope of my paper (academic libraries and e-books). The second paragraph of my introduction goes on to explain why this is important:
The use of electronic books is a major concern for modern academic libraries and so is an area worth thorough investigation. Newer generations of students are digital natives, accustomed to being able to access information on the go. Being able to read text on their computers and screens is something they take for granted. On the professional side, pricing and space are constant issues. […] E-books both help and hinder library interests. As the digital world continues to grow, libraries must decide how to adapt. Considering e-books is part of that response. Matters of practicality and user preferences both play a part in that decision-making process. […] Taking everything into consideration, research suggests that academic librarians ought to pursue a hybridized strategy keyed to their particular situation. While this may appear non-committal, the tactic aids libraries in serving patrons to the best of their ability.
Here, I have both justified my topic and laid out a blueprint for my literature review. What are my main topics and themes? I am going to be looking at pricing, space, practicality, and user preferences. Based on the research I looked at, I’ve drawn a conclusion.
Body Paragraphs
As I mentioned earlier, body paragraphs should be structured by idea rather than article. The topic sentence rule I talked about in the last essay post still holds true – start each paragraph with a topic sentence describing the paragraph’s focus. Ex:
Topic Sentence: The impact of e-books on access is a complicated issue. First main point: At first glance, e-books are much more accessible than print. They can be read anywhere at any time and do not need to be carted around. Many students cite accessibility as e-books' main advantage. Supporting details from various sources: In a survey done by Gilbert and Fister, "ease of access" is the top reason students say they might use e-books (474). […] Second main point (counterpoint, putting sources in conflict): However, in some ways e-books are very inaccessible. Some individuals with disabilities might have difficulty reading electronically, even while others may find it helpful to be able to zoom in on text, change its font, or manipulate it in other ways. […] Conclusion: E-book accessibility is not as simple as logging in. While the ability for a student to read an e-book in their dorm room is a draw, it becomes less of one if the screen gives them headaches or they cannot open the book on their personal e-reader.
Discussion/Conclusion
If you’re writing a standalone lit review, hopefully throughout the body paragraphs you have been looking at themes and ideas shown in the literature. However, you might take some time in a separate discussion portion to contemplate the ramifications and draw some conclusions or make recommendations.
But wait! We’re not quite done.
Recommendations for Further Research
Scholars love identifying areas for further research. It justifies their existence. Based on what you see here, what should be investigated next? What gaps need to be filled? Are events developing so quickly this will all need to be revisited? Do you see any big changes on the horizon? If your lit rev is part of a bigger paper, you are probably going to identify a gap that you’re about to fill! Ex:
E-books, like all other parts of the digital world, are a topic that should be continually checked as attitudes and technology change. […]
An area where e-books may outpace their print counterparts is where they can stretch the medium. […] Further research into more cutting edge e-books and user response could suggest whether this is a field where e-books can gain some popularity, or whether they will continue to be seen as a distraction from the words on the page.
This site is a good guide to reference. Looking at actual literature reviews is also a good way to get used to writing them. Some databases allow you to search for them specifically. If there isn’t that option, searching with ‘review’ as a keyword or in the title field will often net you a few. Also, just google sample literature reviews!
Again, remember this is all my perspective. I encourage you to seek as many as possible to figure out what works for you. And always follow your instructor’s recommendations.
7 notes
·
View notes
Text
The Photographer’s Survival Guide to Marketing
Advertising and marketing is a marathon, not a dash. It’s a numbers sport. It's important to hold hitting shoppers till you get them on the suitable day on the proper time. Your first objective needs to be to get on that shopper’s radar, then it’s about getting on their shortlist. Begin advertising and marketing as quickly as you may. Let shoppers see you develop, get used to your work, and join with you. Consistency is the important thing to advertising and marketing. The consistency is within the timing. It's important to be constant about how usually and while you ship out your advertising and marketing. Once we speak about a advertising and marketing marketing campaign, we normally consider it as 12 months with 6 cycles. We like each 2 months as a result of it’s about the suitable spacing between cycles. You additionally must be constant along with your messaging. Keep in mind your voice? You need to craft a message out of your voice and keep it up. Don’t neglect, your message must be related to the shopper goal checklist we constructed again in chapter three.
Profitable advertising and marketing is about a number of touch-points. Every touch-point is a method so that you can attain out to a shopper. Some entrepreneurs imagine you want at the least 3-Four touch-points per cycle to connect with the shopper. What are our touch-points? One of many best, least costly, and best methods to market is e mail promos. Save your self a while and purchase a mailing checklist. Nobody has the right mailing checklist of artistic professionals, however shopping for entry to a database will prevent hours and hours of time monitoring down these manufacturers. Be sincere with your self, you would possibly persuade your self you are able to do the analysis as you begin your first advertising and marketing marketing campaign, however you already know you’re not doing to proceed to do that every time you market.
Plus, consider your advertising and marketing in two waves. You’ve received the goal checklist you’re retaining a detailed eye on, however you must also have a wider internet too. This bigger checklist continues to be related to your enterprise. By taking a look at your goal checklist, you may set the parameter inside a database to seek out extra firms like those you're concentrating on. Your goal checklist is likely to be solely 50 shoppers, however your secondary checklist may very well be as giant as 2,000-3,000 shoppers.
The e-mail promo is the one type of advertising and marketing that's trackable. When a shopper opens and even clicks in your promo, we all know one thing is occurring. An awesome design can elevate your work. There’s no rule to what number of photos you want on an e mail promo.
Once more, it is dependent upon what you assume the shopper ought to see. Two photos really feel like a pleasant stability, however I’ve positively been concerned in campaigns primarily based across the concept of 1 highly effective picture. When you’re an editorial storyteller, there’s an argument for a sequence. Today, you would possibly need to stress the truth that you do multimedia. GIFs are very straightforward to embed into the design, they usually are inclined to get the shopper’s consideration.
Unsolicited mail covers all the things from postcards to specialty print initiatives. I've to say, as profitable as an e mail promo will be, I’ve by no means heard of a shopper printing out the e-mail and sticking it to their wall. That stated, you may cowl much more shoppers by way of e mail. I like to save lots of my unsolicited mail for the goal shoppers in addition to those that appear to be warming as much as my e mail marketing campaign.
A unsolicited mail piece is the right second course for a shopper nibbling in your e mail promo. Your common direct mailer is a 6×9 postcard, which is completely acceptable. After all, these of you not desirous to appear to be everybody else would possibly need to step up your sport. I as soon as heard a shopper say, “I like to get a promo with substance. I can stroll into a gathering and actually throw the booklet on the convention desk. That will get my artwork administrators’ consideration.” Personally, my objective is to assist my shoppers create one thing worthy of sitting on a shopper’s workplace shelf or dangle on their wall. I do know that is sacred floor, so it means the promo must be distinctive, artistic, and good. If you may get within the cubical, there’s a extremely good likelihood that the shopper would possibly work together with it every day. That’s a every day reminder you exist.
Let’s return to emails. So I first talked about e mail promos (epromos). These are largely about your photos. It’s properly designed, hopefully, there’s a few name to actions, and your whole contact data. Now, let’s speak about private emails. The leads you get out of your epromos, adopted up with an excellent direct mailer, can flip this shopper right into a heat lead. Now it’s time to develop a relationship. A private e mail introduces your self. Achieved proper, it reveals you're formidable and have completed your homework. You need to present this shopper you need to work with them. Inform them what you consider their model/firm. Ship them slightly love, and be honest. Handle them by title. Perhaps you even point out one thing particular they did like a magazine story or an excellent business.
We try to make them really feel snug about writing you again. Now, don’t say “I do know you opened my e mail”, as a result of that’s tremendous creepy. Inform them you’ve been advertising and marketing to them lately, and also you’d prefer to know if there's a higher solution to replace them in your new work. Perhaps you even ask them in the event that they ever take head to head conferences. All good things. This private e mail will be despatched out of your e mail account or possibly strive LinkedIn. When you contact them by LinkedIn, please don’t ask them to take a look at your work and provide you with suggestions. It’s not good LinkedIn etiquette. It's best to all the time ship the epromos to their work e mail deal with.
All the above touch-points are about you sending out a message to the shopper, it’s additionally necessary to be within the locations they search for artists. Sourcebooks and artistic communities are nice methods to be listed. Some are free and a few come at a value. Some are simply web sites and others contain sourcebooks and catalogs. Being part of these websites may also help you get in entrance of shoppers. In case your epromos and direct mailers are working, they may really say to themselves, wait a minute… I do know this man – after they see you within the sourcebook. After all, at Company Entry we love Discovered. Discovered is an invite-only group advertising and marketing platform for artists that provides each on-line and offline advertising and marketing, portfolio critiques and fantastically produced printed promotions together with the Discovered sourcebooks. If Discovered isn’t what you’re in search of, try:
At Edge
Le E book
Workbook
Dripbook
Behance
I discussed social media as a enterprise software, however it is usually a contact level. If you're fortunate sufficient to be in a shopper’s feed, you've the chance to attach with them every day. Keep in mind to not make social media an remoted expertise. I feel all of us did that initially. Today, the concept is to drive your Instagram viewers to your web site. Consider your web site as a phenomenal vacation spot. Your social media acts because the highway resulting in your web site. Use your social to indicate your latest work. It’s a good way for shoppers to get a fast peek. Tease them with a picture after which push them again to your web site to see extra. In your social bio, checklist your net deal with. Pinterest can be a good way for shoppers to seek out you. Typically it’s as a result of the magazines you shoot for are posting your tales, however you may construct boards to your personal photos.
Sooner or later a shopper of mine received a name from Goal. We had barely began advertising and marketing, so although I had hoped they discovered her by the promo we despatched them, it was in all probability one thing else they'd seen. She had no rep on the time, so we knew that wasn’t it both. Two days into the shoot, my shopper requested Goal how they discovered her. Their reply was Pinterest. The in-house Goal workforce had spent months creating a brand new model technique for one among their meals merchandise. Throughout their analysis, they'd constructed temper boards to encourage their technique. Sooner or later, they stood again to take a look at their analysis and seen a number of of their favourite photos have been from the identical photographer. Ultimately, they tracked her down and employed her on the spot. Pinterest is shortly changing into a favourite for visible searches. If you're on Pinterest, you're within the place creatives begin their artistic course of. Like my shopper, she finally turned their primary selection as a result of they'd unknowingly constructed their technique round her.
READ MORE: https://clippingpathcreative.com/the-photographers-survival-guide-to-marketing/
0 notes
Text
25 Top Android Mobile App Ideas to Follow in 2020
Can we imagine starting our day without a mobile application? We need an app for setting the alarm, one which reminds us of our meetings, another for playing songs, and even one mobile application for reading out news to us. So the moral is, mobile apps have taken a special place in our lives, and we cannot deny our reliability on them.
After seeing this essential reliability, android mobile app trends needed to upgrade in the year 2020. Mobile app development companies have come up with some more useful ideas and trends for android app development. Let’s discuss each in brief.
1- Augmented Reality is winning hearts:
Want to design your room? Or do you want to try a dress you saw on an online shopping app without buying it? Well then AR- Augmented Reality; is there to help you. Already a few websites like Pepperfry have started giving AR options where you can see which furniture will fit in your room. Mobile apps laced with AR features will be the top app trend to follow in 2020.
2- One Scan to make your PDF:
Keeping and carrying hard copies of your documents is so troublesome. But then what is the alternative? A mobile app that scans and converts all your documents into a single PDF file can help. This type of mobile apps will trend because of the mass digitization going on. People find carrying soft copies more convenient and safe than carrying hard copies of documents. Also, adding a cloud feature to this app will help in accessing the PDF on any platform.
3- Fitness apps are trendy:
People love fitness apps because it provides a one-stop solution to its users. It helps them organize their diet, track their footsteps, set health goals, and much more. Adding videos of yoga, exercise, and providing health consultants can enhance the beauty of such android mobile apps.
4- Say no to queues with Check-out apps:
No one likes to wait in a long queue at a retail store, and so Amazon came up with the self-check-out retail stores, Amazon Go. These types of apps will be increasingly used in the coming years. Amazon Go app allows users to scan the products on our mobile while shopping and make the payment online after checking out from the store. We just need to tap our phones just like we do on metro stations with metro cards.
5- Real-time translator apps:
It is almost impossible to mug up all the languages in the world. In such scenarios, real-time translator apps can save us. This app will listen to the other language and convert it into our language in real-time and also the vice-versa. Adding a memory feature can help the user in learning that language in the future if needed.
6- Let’s chat with bots:
Chat Bots are useful in playing the role of humans. They can interact like humans based on customer’s queries. These apps are based on Artificial intelligence technology, which is why they behave like humans. AI Chat Bots are helpful for any mobile app as they can support live chat without the need for human interference. Unlike humans, they never get exhausted and have the capability of interacting with any number of queries according to the user’s requirement.
7- Take me for a Bike Ride!
Due to increasing traffic and massive rates, cabs are losing their fans. The people who travel alone prefer to book bike rides rather than a car. The reason is pretty simple, it’s cheaper, can take shortcuts, and doesn’t get stuck in traffic jams, so it’s faster too. So hiring developers for getting a bike ride mobile app made is a great option. It will be a trend in 2020.
8- Safe Calling apps:
With the increase in spam calls, harassment, and forgery, Safe Calling mobile apps need to be used. Such apps will recognize the number if it is a spam or not based on the customer review database. Also, it will enable you to record the call and upload it to cyber crime cells helplines if needed. This will help you stay safe and also work as a preventive method in crimes over phone calls.
9- Scan and buy:
Imagine you visit your friend’s house, and you see a gorgeous center table in her living area. You also desire to buy that table, but you feel awkward in asking about it in detail from your friend. Now, what will you do? If you have a Scan and buy mobile app, you can scan that table, and it will show you all the results from where you can buy the same or a close substitute for that table. Such android mobile apps are useful as well as fun to use.
10- Criminal alert app:
Seeing a missing person or a wanted criminal on roads without knowing them can be a safety concern for all of us. The criminal alert app idea is such that the app will alert you of criminals in your area. This will save a life as well as help in catching the criminal whose pictures are there on the app.
11- Baby care and maternity app:
In the world where digital reliability is growing day by day, having an android mobile app for baby and mother care can help many lives. Such apps can be used by mom to be or even by men who are soon going to be a dad. These mobile apps will provide diet solutions for both baby and mother, exercise videos during pregnancy, nearby hospital routes, appointments of gynecologists or pediatricians, baby care products, and much more.
12- Stay away from crime:
Imagine having a mobile app that can tell you which area in your city is not safe and why. This is not fiction anymore. Such apps are a reality today and will trend in 2020. The heat map feature can also be added to this type of mobile apps to show the user the safe and unsafe areas of the city at a glance. Allowing users to report a crime on this app anonymously or with identity( as per the user’s choice) will enhance the quality and reliability of the app. And also help the surveillance cells to improve their services.
13- Food suggestion/blogging apps:
We all know how Zomato was started. Before starting with food delivery, it was a food blogging website and was known as Foodiebay.com, where people used to get hundreds of restaurant menus, reviews of eating joints, and recommendations. Such mobile apps will be a significant trend in 2020 as food blogging has come up as a career option for youth. Providing these bloggers with a separate mobile app will help them get better recognition too.
14- Find me a parking space:
We all will agree to the fact that finding a parking space whenever we go out is so annoying. What if an app will help us find a parking space in that area? It’ll solve a huge problem for us. Designers can design such mobile apps, which will help us find a registered parking space near us. Adding an e-parking ticket feature will take the mobile app to the next level.
15- Choose your table app:
We need privacy in a corner seat for a cozy date or need the central table for making a grand announcement, in restaurants, it’s sometimes challenging to get the desired seating arrangement for what we’ve planned. With a mobile app which has graphical views, we can choose the desired seats or table and book them for a specific time( just like bus ticket reservation).
16- Virtual group study app:
It’s not always safe to go to a friend’s place for group study. You can also consider if one of the friends might be sick/out of town, but you have to do your assignments? In group study apps, students can meet up on this forum and prepare for their exams/projects along with other students who are studying on the same subject. The app must provide them with study material, tools, video lectures, discussion helps, guides, etc. Users can also create a virtual room where only he and his friends can enter and video call while watching online lectures together virtually. Hire android developer if you are mesmerized by this idea and want to get it made for you.
17- An app for Language Lovers:
Many people wish to learn a new language but don’t find the perfect solution. To help such people, you can design android apps, which will enable the user to learn new languages thoroughly. Adding levels like basic, intermediate, and professional will increase user engagement on your mobile app.
18- Pet Care and adoption apps:
Since there are many pet lovers out there, they will be disappointed if the digitization of the world doesn’t consider their needs. Pet care companies or veterinarians can hire android developers to get an app made for pet care. People willing to adopt pets can also register on this app. Adding a section for the license(new or renewal) will be a cherry on the cake for dog owners since, from May 2019, it is a compulsion in India to have a license if you own a dog.
19- Gift Suggestion apps:
Whenever it comes to selecting a gift for our loved ones, we end up getting confused. This mobile app can look over the entire history of our friend’s social feed to suggest the best gift idea for our friend based upon the content they posted. Such mobile apps are developed, keeping in mind the concept of data analysis. Problem solver!
20-Food Wastage Prevention Apps:
We all have seen that once the parties are over, a lot of food is left untouched or unused. People even throw food in the dustbin, which leads to the wastage of food. This issue could be resolved. We can develop a mobile app that can inform the registered orphanage/nursing homes about the leftover untouched food so that they can come to get it as per their need.
21- Car rental apps:
How many names come to your mind when you think about car rental mobile apps? Just Zoomcar, isn’t it? This is because not many businesses think of starting an online car rental, but you must because Car rental apps in India have very little competition. If you already deal with car rental or tours and travel business, then you can hire android developers and get your business online.
22- Dating apps:
Dating apps never get out of date. They are going to rule the app world like ever before in 2020 too. The reason why dating apps gained so much popularity is that ‘when everything is going digital, then why not love?’ But dating apps are not a recent invention. The first-ever dating website, Match.com, was launched in 1995.
23- Student Assistance App:
The student assistant app is one of the top android app ideas to choose from. This app can be developed with features like writing projects or essays that will be of great help to the students.
Some ideas of Student Assistance App ideas are:
School project mobile app: With such kind of apps, students can look for group members to complete team projects and other academic projects which require students to collaborate.
Book stationery app: This app can help students in finding the nearest stationery shops and also in comparing the prices of books before buying. It will save both time and money.
24- Buying/renewal of policies/insurance apps:
We all will agree to the fact that policy renewals are a headache for us, and to top it all, we always tend to forget the renewal dates. Having a mobile app for Buying/renewal of policies/insurance will help us like Superman!
25- Event Management App:
Planning a perfect event is a Herculean task for all of us. But what if an app assists us throughout the planning procedure? It’ll be so easy for us to find solutions for each of our problems. The event management mobile apps must have information about venues, shops, caterers, and all that is needed to organize an event.
Summing up:
If you are a business owner then you must have a mobile application for your business. Having a mobile app will help in gaining recognition for your brand and making more customers. And if you are still confused and are planning to start a business with a mobile app, then you can choose any from the above mentioned 25 Top Android Mobile App Ideas. Also, if you need assistance in developing an app, you can hire android developers for your business. A professional developer will be able to assist you in the best ways possible. You can also improvise these ideas as per your needs. If you want to add more ideas to this list we made, do comment them below.
0 notes