#linux commands pdf
Explore tagged Tumblr posts
Text
wgat the hell is goin on…
#I’m literally the ‘’I don��t understand this and at this point I’m too afraid to ask’’ meme#like I can’t even view a pdf with the Linux command line isn’t that basic stuff I’m supposed to know#.txt
1 note
·
View note
Text
Want to merge all PDF files into one PDF in Linux? Try pdfunite command :)
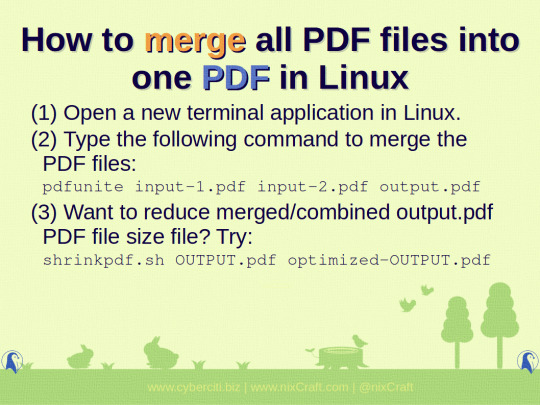
-> How to merge all PDF files into one PDF in Linux
26 notes
·
View notes
Text
Recent Activities of Transparent Tribe (APT36)

Transparent Tribe, also known as APT36, is a Pakistan-based threat group active since at least 2013. They have consistently targeted Indian government, defence, and aerospace sectors. Recent activities indicate a significant evolution in their tactics and tools.
May 2024: Targeting Indian Defence and Aerospace Sectors

In May 2024, Transparent Tribe intensified cyber-espionage operations against India's defence and aerospace sectors. They employed phishing emails containing malicious attachments or links to deploy various tools, including:
Crimson RAT: A remote access Trojan used for data theft and surveillance.
Poseidon: A Golang-based agent compatible with Linux and macOS systems.
Python-based downloaders: Compiled into ELF binaries to target Linux environments.
The group also exploited India's development of indigenous Linux-based operating systems, such as MayaOS, by distributing Executable and Linkable Format (ELF) binaries to compromise these systems. [Source]
Late 2023 to Early 2024: Evolution of ElizaRAT Malware
Between late 2023 and early 2024, Transparent Tribe advanced their malware capabilities by developing ElizaRAT, a Windows Remote Access Tool. ElizaRAT's evolution included:
Enhanced Evasion Techniques: Improved methods to avoid detection by security systems.
Cloud-Based Command and Control (C2): Utilisation of services like Google Drive, Telegram, and Slack for C2 communications.
Modular Payloads: Deployment of additional payloads such as ApoloStealer for targeted data exfiltration.
These developments indicate a strategic shift towards more sophisticated and flexible attack methodologies. [Source]
September 2023: Infrastructure Expansion and Linux Targeting
In September 2023, investigations revealed that Transparent Tribe expanded their infrastructure, employing Mythic C2 servers hosted on platforms like DigitalOcean. They also began targeting Linux environments by distributing malicious desktop entry files disguised as PDFs. This approach aimed to compromise systems running Linux-based operating systems, aligning with India's adoption of such systems in government sectors. [Source]
June 2023: Focus on Indian Education Sector
By June 2023, Transparent Tribe shifted focus to India's education sector, distributing education-themed malicious documents via phishing emails. These campaigns aimed to deploy Crimson RAT, enabling the group to exfiltrate sensitive information from educational institutions. [Source]
These recent activities demonstrate Transparent Tribe's persistent efforts to adapt and refine their tactics, expanding their target spectrum and enhancing their malware arsenal to effectively compromise systems across various sectors.
Author: Kelly Hector
Blog: Digitalworldvision
2 notes
·
View notes
Text
So, I work with boomers. A lot of boomer. But not the “help me open this pdf file” kind. I mean the “I worked at Pacific Bell Labs in the 80’s” kind of boomers. The ones who make me feel very, very dumb.
And yet, I’ve learned more in 1 year than I ever did in class. You want to learn COBOL? Jerry in business applications has you. What about x86 ASM? Steve over at Engineering can teach you.
And everyone is super helpful and friendly. I fuck up often and constantly. The reaction “it’s okay dear, I lost a whole collection of punch-cards back as a college intern” (this was said to me). Messed up a Linux command? “That’s alright, I still remember Unix.”
Honestly the best place to work.
3 notes
·
View notes
Text
19. Dezember 2023
Ich muss Selbstgebasteltes verschenken, obwohl ich das gar nicht will, weil der Fortschritt noch nicht da ist, wo ich ihn erwarte
Ich möchte ein Textdokument so ausdrucken, dass sich ein kleines Heftchen im A6-Format ergibt. Dazu müssen die zu druckenden Seiten des PDF so umsortiert werden, dass nach dem Zerschneiden und Zusammentackern alles in der richtigen Reihenfolge ist, also ungefähr so (erfundene Reihenfolge): S. 1, 4, 7, 3, 2, 11, 8 und so weiter. Im Prinzip können das mehrere Dinge, die ich auf meinem Laptop habe, zum Beispiel LibreOffice Writer und LibreOffice Draw. Aber anscheinend nur für A5-Heftchen (2 Seiten auf einem gedruckten Blatt) und nicht für A6-Heftchen (4 Seiten auf einem gedruckten Blatt).
(Update: Da ich es ein paar Tage später im A5-Format versucht habe, weiß ich jetzt, dass es da auch nicht funktioniert.)
Ich google und google. Die Details lasse ich hier weg, weil sie ultralangweilig sind und ich einen Tag später auch fast alles schon wieder vergessen habe. Jedenfalls habe ich ein paar Dinge installiert, die es aber auch nicht konnten, und ich war bei ein paar Onlineangeboten, die es entweder nicht konnten oder die dafür nötigen Einstellungen nicht so erklären konnten, dass ich es verstanden habe.
Ich beschwere mich im Techniktagebuch-Chat: "Ich dachte naiv, das sei so was, was früher mal schwierig war und jetzt trivial ist. Ich bin sehr kurz davor, einfach alles normal auszudrucken und dann auszuschneiden und zusammenzuleimen."
Oliver Laumann sagt, dass es dafür für Linux Command-Line-Tools gibt. "Habe leider gerade vergessen, wie sie heißen und kann gerade nicht nachschauen. pdfnup?"
Ich (um 18:22): "Ich habe die bisher ignoriert, weil ich nicht dachte, dass es dadurch einfacher wird, aber vielleicht hast du recht. Viel komplizierter kann es kaum werden."
Ich (um 18:40, nachdem ich Dinge installiert, mich mit der PATH-Variable befasst, über Fehlermeldungen nachgedacht, die Dokumentation gelesen, den Kommandozeilenbefehl in zehn verschiedenen Varianten eingegeben und es am Ende doch irgendwie hingekriegt habe, aber ohne Ergebnis, wobei ich die abschließende Fehlermeldung zum Aufschreibezeitpunkt schon wieder vergessen habe): "Update: doch, kann es. Ich schneide jetzt alle Seiten aus und leime."
Ein längeres Gespräch über die Klebstoffe "Coccoina" und "Pelikanol" und was bei ihrem Eintrocknen zu tun ist, schließt sich an. "Das ist ja alles viel schöner als 'pdfnup'", findet Oliver Laumann.
In der Theorie stimmt das, in der Praxis sieht das Ergebnis meiner Kleberei erbärmlich aus und alle können jetzt sehen, dass ich nicht weiß, wie man eine A6-Broschüre ausdruckt, und auch nicht geduldig genug bin, um es herauszufinden. Aber egal! Ich möchte, dass die beschenkten Freundinnen und Verwandten von mir lernen, dass man auch aufgeben können muss. Aufgeben und geduldig darauf warten, dass der Fortschritt da ankommt, wo er gebraucht wird.
Update: Nach der Veröffentlichung dieses Beitrags schreibt mir eine Freundin, die gelernte Grafikerin ist: "Eine A6 Broschüre erstellen: das heisst in der Druck Fachsprache AUSSCHIESSEN – kann ich auch nicht!"
(Kathrin Passig)
3 notes
·
View notes
Text
operating system
An Operating System (OS) is system software that manages computer hardware, software resources, and provides common services for computer programs. It's the most fundamental software that enables other applications to run on a computing device. Here's a detailed breakdown of an operating system:
1. Definition of Operating System
An Operating System is software that acts as an intermediary between computer hardware and the user. It provides a user interface and controls all hardware components, making it easier for users and applications to interact with the computer without needing to know hardware-level details.
2. Functions of Operating System
✅ a. Process Management
Manages processes in a system: creation, scheduling, termination.
Handles multitasking (running multiple processes simultaneously).
Provides mechanisms for process synchronization and communication.
✅ b. Memory Management
Allocates and deallocates memory space as needed by programs.
Keeps track of each byte in a computer’s memory and optimizes RAM usage.
Manages virtual memory (swap space on disk).
✅ c. File System Management
Organizes files on storage devices like hard drives or SSDs.
Provides file-related operations: create, delete, read, write, etc.
Manages file permissions and security.
✅ d. Device Management
Controls and manages I/O devices (keyboard, mouse, printer, etc.).
Uses device drivers to communicate with hardware components.
Allocates devices to processes when needed.
✅ e. Security and Access Control
Protects data and system resources from unauthorized access.
Supports user authentication and permissions.
Provides encryption and firewall mechanisms.
✅ f. User Interface
Provides a user interface to interact with the system:
Command-Line Interface (CLI)
Graphical User Interface (GUI)
🔷 3. Types of Operating Systems
TypeDescriptionBatch OSExecutes batches of jobs without manual intervention.Time-sharing OSMultiple users share system resources simultaneously.Distributed OSManages a group of distinct computers and makes them appear as one.Real-time OSResponds to input instantly (used in critical systems like flight control).Network OSManages network resources and allows shared access to files and printers.Mobile OSSpecialized OS for mobile devices (e.g., Android, iOS).Embedded OSUsed in embedded systems like smart TVs, washing machines, etc.
🔷 4. Examples of Operating Systems
💻 Desktop and Server OS:
Microsoft Windows
Linux (Ubuntu, Fedora, CentOS)
macOS
UNIX
📱 Mobile OS:
Android
iOS
🔷 5. Multitasking, Multithreading, and Multiprocessing
✅ Multitasking:
Running multiple applications at the same time.
✅ Multithreading:
Multiple threads within a single application run concurrently.
✅ Multiprocessing:
Using multiple CPUs/cores to execute processes simultaneously.
🔷 Conclusion
An Operating System is vital for any computing device to function. It manages hardware, provides essential services, ensures user interaction, and forms the platform on which application software runs. Its design and performance deeply influence the overall system reliability and efficiency.
If you'd like, I can also provide a PDF version or create a presentation outline for this content.
0 notes
Link
看看網頁版全文 ⇨ 解鎖或加密PDF檔案:Colab PDF Protector / Unlocking or Encrypting PDF Files: Colab PDF Protector https://blog.pulipuli.info/2025/06/unlocking-or-encrypting-pdf-files-colab-pdf-protector.html PDF檔案的安全性加密與解除限制通常需要特別的軟體。 如果我們只有手機的話,不妨來使用我開發的Colab PDF Protector,用Google Colab的腳本新增或移除PDF的安全性設定吧。 PDF file security encryption and decryption often require specialized software. If you only have a mobile phone, consider using my Colab PDF Protector, a Google Colab script designed to add or remove security settings from PDFs.。 ---- # PDF的安全性設定 / PDF Security Settings。 PDF (Portable Document Format) 檔案的保全設定,主要目的是為了保護檔案內容不被未經授權的存取、編輯或列印。 你可以透過設定密碼來限制開啟檔案,或者設定權限密碼來限制使用者複製、列印等操作。 這些保護措施可以保護檔案在傳輸和分享時,避免遭受未經授權的取用。 設定 PDF 安全性的方式,通常會區分為「開啟密碼」和「權限密碼」。 「開啟密碼」是指當使用者嘗試打開 PDF 檔案時,必須輸入正確的密碼才能檢視內容;而「權限密碼」則是用來限制使用者對檔案的操作,例如是否允許複製文字、列印或編輯。 透過這兩層密碼的設定,你可以更精細地控制檔案的授權條款。 此外,有些 PDF 軟體還允許你設定數位憑證(digital certificate)來保護檔案,以此確保檔案的來源的可靠程度。 # PDF命令列編輯工具:qpdf / PDF command line editing tool: qpdf。 https://github.com/qpdf/qpdf。 PDF安全性管理通常都得仰賴專門的PDF工具,例如Adobe Acrobat Pro或是X-Change PDF Editor。 在Linux作業系統裡,我們通常是使用qpdf來處理PDF檔案。 qpdf 是一款功能強大的命令列工具和 C++ 函式庫,專門用於對 PDF 檔案進行內容保留的轉換。 ---- 繼續閱讀 ⇨ 解鎖或加密PDF檔案:Colab PDF Protector / Unlocking or Encrypting PDF Files: Colab PDF Protector https://blog.pulipuli.info/2025/06/unlocking-or-encrypting-pdf-files-colab-pdf-protector.html
0 notes
Link
#Apache#Automation#build#configuration#database#full-textsearch#ht://Dig#indexing#informationretrieval#Linux#open-source#Performance#scripting#searchengine#self-hosted#Server#systemadministration#webcrawler#webdevelopment#websitesearch
0 notes
Text
Anyone here know how to open a pdf using linux command prompts
#everything I see says I have to download shit that I don’t have permissions to download#.txt#please I’m gonna cry
7 notes
·
View notes
Text
Linux CLI 50 🐧 groff command
New Post has been published on https://tuts.kandz.me/linux-cli-50-%f0%9f%90%a7-groff-command/
Linux CLI 50 🐧 groff command

youtube
a - groff command introduction groff command is used to create simple text documents and troff (TeX) formats It uses macros similar to those used by UNIX typesetters It is mainly used to create man(manual) pages commons options: -T[dev] → directs the input to output device dev -i → reads the standard input after all the named input files have been processed -m[dir] → searches dir for macro files -n[num] → the first page num some available devices: ps → PostScript pdf → PDF ascii → ASCII character set utf8 → UTF-8 encoding html → HTML grof file → start writing and export to file to write the text and Ctrl + D to save it b - some groff embedded commands .sp → spaces one line .sp 5 → speces 5 lines .sp 2.5c → leaves 2.5 cm .ce 100 → centers 100 lines .ce 0 → stops centering .bt → line break .bp → page break .in → indent line .in 4 → indent 4 lines .ti → temporary indent .po 10 → page offset 10 characters .ps 20→ font size 20 .ss 12 → space-character size .ad → line adjustment l|r|c|b|n .na → no adjustment more details at https://www.troff.org/54.pdf c - groff examples groff -Thtml → formats the text you write in HTML groff -Thtml index.html → formats the text and saves it to HTML file echo hello, Linux! hello.tr → creates hello.tr with hello, Linux content groff hello.ts → displays the hello.tr file groff -Tpdf hello.tr output.pdf → creates a pdf file from hello.tr man -P cat cat | groff -Thtml cat.html → creates an HTML from the cat manual
0 notes
Text
Intern, Software Engineer
Job Description Data automation scripts : teaching them how data transfer works from the tester side until the PDF side Data sanity check and review : teaching them on to compare data in PDF with data information in SCORE, EDB, MIDAS and so on Linux server : Introducing them on the Linux server and some commands and some walkthroughs GYM data review : As more data is loaded, would teach them on…
0 notes
Text
Assignment 1: SQL Startup 20 Points
Do the following and then upload a .pdf file. Install the correct version (Windows vs. Mac vs. Linux) of MySQL: http://dev.mysql.com/downloads/mysql/ Make sure it works. Here is an example of commands to try. Mac users: Use Terminal under Applications/Utilities. Windows users: Use the command prompt. Unix commands to find and start using MySQL: cd /usr/local/mysql/bin ./mysql -u root -p When…
0 notes
Text
Regular blogging wooooo
We were struggling a lot to read a textbook, for a lot of reasons, but part of it was the fact that we only have a digital copy. We knew that there were tts services out there, and figured that would be easier than reading it with our eyes, so we looked up "pdf text to speech linux" and it turned out to be so easy (as long as you're willing to listen to lower quality output, but some of us feel a certain kinship with the dinky thing, so it's not too bad).
There are 2 programs we ended up needing and they were a set of cli tools called "poppler_utils" and a pretty old program called "espeak"
With poppler_utils we can convert sections of a pdf to raw, somewhat formatted .txt file, and with espeak you can pass in a .txt file and get it to output a .wav, or if you don't tell it to output, it'll just start reading it from the command line. The .wav is more convenient for us though because then we can pause and skip around, and the whole chapter ended up being almost 4 hours, and we can't focus on basically anything for that long without a break.
It's so fun to do I think. It's fun to see the processes run and see the files being generated. God we just love computers so much.
0 notes
Text
A-Z Kali Linux Commands — Also Included Kali Commands PDF
http://securitytc.com/THJsFN
1 note
·
View note
Text
جميع أوامر termux للأختراق والتهكير all Commands Termux
أوامر في تطبيق Termux من خلال هذا المقال سوف نتعرف على كل أوامر termux وشرح اهم الأوامر في تطبيق Termux للأختراق وكيفيه التعامله معه تطبيق Termux يعتبر من اهم التطبيقات التي يجب عليك تثبيته على هاتفك الأندرويد فأنت لست بحاجه لجهاز حاسوب لكي تتعلم الأختراق ولكن علينا اولاً ان نتعرف على التطبيق شرح termux commands list وما هي الاومر الاولى في تشغيل termux قبل البدء كل هاذا سوف نتعرف عليه من خلال هذا المقال . termux commands list
جميع أوامر termux للأختراق والتهكير all Commands Termux
اوامر termux للاختراق كنا قد نشرنا مواضيع كثيرة حول تطبيق تيرمكس وربما من اشهر هذه المواضيع شرح جميع اوامر Termux لكن اليوم سوف نقدم مجموعه اخرى من الأوامر المهمه والتي من خلالها سوف تتعرف على كيفيه التعامل مع تطبيق تيرمكس بشكل ممتاز دون الحاجه الى اي مساعدة من احد , وربما من اهم ما يجب ان تتعلمه هوا termux commands list اي أوامر تيرمكس وهذه امر مهم جداً فمن دونها لن تتكمن من التعامل مع التطبيق فلكل امر وظيفه معينه يقوم بها مثل تحميل الأدوات والتنقل بين الملفات وفهم الصلاحيات وغيرها اوامر termux .
لكن ما هوا termux وفيما يستعمل , حسناً دعني اجيبك بشكل مبسط تيرمكس اوامر termux هوا تطبيق عبارة عن Terminal اي سطر اوامر مبني على اللنكس من خلاله يمكنك تحميل ادوات الأختراق او وتشغيل سكربتات بللغات برمجيه مختلفه مثل Paython وغيرها فهوا شبيه الى حد ما في نظام Kali linux ولكن تيرمكس يعمل على الهاتف اي لست بحاجه الى جهاز كمبيوتر اوامر termux للاختراق .
أهم أوامر تشغيل termux قبل الأستعمال
pkg update pkg upgrade pkg install python pkg install python2 pkg install python3 pkg install ruby pkg install git pkg install php pkg install java pkg install bash pkg install perl pkg install nmap pkg install bash pkg install clang pkg install nano pkg install zip pkg install unzip pkg install tor pkg install sudo pkg install wget pkg install openssl
أوامر Termux لأنشاء ملفات والتنقل بينها
touch لأنشاء ملف جديد cat أنشاء ملف جديد بمحتوى echo “hello world” انشاء ملف جديد وكتابه بداخله cat >> [file name] – اضافه محتوى في ملف موجود مسبقاً mkdir [name] – انشاء فولدر او ملف جديد
أوامر النسخ واللصق Termux
cp لنسخ الملفات cp -r لنسخ الملف في اي مسار mv يستعمل لنقل الملفات من مسار الى اخر mv -v يستعمل لنقل اي ملف mv [file1 name] نقل واعادة تسميع الملف mv -i التحريك والكتابه فوق الملف mv -f – نقل الملف والكتابه فوقه بشكل اجباري
أوامر التنقل بين الملفات Termux
cd يستخدم لتنقل بين الملفات cd / يستعمل للرجوع الى ملف الروت cd .. لرجوع خطوة الى الخلف
وهذه أوامر الأخرى اساسيات termux
rm لحذف الملف pwd لمعرفه مسارك wget لتحميل الأدوات git clone لتحميل الأدوات من رابط apt install curl لتحميل apt search للبحث عن حزم unzip لفك الضغط عن الملف bye لعمل اغلاق لسطر الأوامر whoami – لمعرفه اسم المستخدم nano لتعديل على ملف ifconfig لمعرفه اي بي جهازك
تحميل جميع ادوات termux
Termux-kalinetHunter
git clone https://github.com/Hax4us/Nethunter-In-Termux cd Nethunter-In-Termux chmod +X* ./kalinethunter
Lazymux Tool
قد يعجبك ايضا
منذ عام
جميع أوامر termux للأختراق والتهكير all Commands Termux
منذ عام
تحميل كتاب أساسيات Termux للأختراق على الهاتف PDF
منذ عام
كتاب جميع أوامر تطبيق Termux
git clone https://github.com/Gameye98/Lazymux cd Lazymux chmod +X* python2 lazymux.py
Tool-X
pkg install git git clone https://github.com/Rajkumrdusad/Tool-X.git cd Tool-X chmod +x install.aex sh install.aex
اوامر Termux لاستخراج المتاحات
xHak9x
apt update && apt upgrade apt install git python2 sudo git clone https://github.com/xHak9x/fbi.git cd fbi sudo pip2 install -r requirements.txt sudo python2 fbi.py
theHarvester
git clone https://github.com/laramies/theHarvester ls cd theHarvester python2 theHarvester.py pip2 install requests python2 theHarvester.py -d hotmail.com -b google -l 500 python2 theHarvester.py -d yahoo.com -b google -l 500
أوامر termux اختراق wifi
wifiphisher
apt-get install git python apt-get install python python-pip python-setuptools pip install scapy git clone https://github.com/wifiphisher/wifiphisher.git cd wifiphisher python setup.py install cd wifiphisher python wifiphisher
جميع اوامر Terminal Emulator للاندرويد
dhcpcd dmesg dnsmasq dumpstate dumpsys dvz fsck_msdos gdbserver getevent getprop gzip hciattach hd id ifconfig
ash awk base64 bash busybox cat chmod chown cksum clear cmp cp cut date dd df diff dirname echo env expr false fgrep find gawk grep gunzip gzip head id install kill killall ln ls md5sum mkdir mknod mktemp mv nice nl nohup od paste patch pgrep pkill ps pwd readlink realpath rm rmdir sed seq sha1sum sha256sum sha3sum sha512sum sleep sort split stat stty sum tail tar tee test timeout touch tr true uname uniq unzip uptime users wc which xargs yes zcat ls: قائمة الملفات والدلائل في الدليل الحالي اوامر termux للاختراق . cd: قم بتغيير دليل العمل الحالي. mkdir: إنشاء دليل جديد. touch: قم بإنشاء ملف جديد. echo: إخراج النص المحدد. cat: عرض محتويات الملف. grep: ابحث عن أنماط في الإدخال. wget: قم بتنزيل ملف من الإنترنت. curl: نقل البيانات من أو إلى الخادم. apt-get: تثبيت أو إزالة الحزم من مدير الحزم. apt-cache: الاستعلام عن قاعدة بيانات مدير الحزم. find: البحث عن الملفات في التسلسل الهرمي للدليل. gzip: ضغط الملفات أو فك ضغطها. tar: إنشاء أو استخراج أو سرد محتويات أرشيف القطران. ssh: الاتصال بجهاز بعيد باستخدام بروتوكول SSH.
0 notes