#log4j2
Explore tagged Tumblr posts
Text
Log4Shell: Cuando una Librería Inofensiva Desató el Caos en el Ciberespacio
En el panteón de las vulnerabilidades informáticas, algunas dejan una marca imborrable, resonando mucho después de su descubrimiento. CVE-2021-44228, más conocida como Log4Shell, no fue solo una vulnerabilidad; Fue un evento sísmico que sacudió los cimientos de la ciberseguridad global. Imaginen por un momento la ubicuidad silenciosa de una humilde librería de logging, Apache Log4j2, incrustada…
0 notes
Text
Java ecosystem
The folks at ecosyste.ms have analyzed the structure of the open-source software community, grouping packages/projects into ecosystems, for funding purposes. Their "Java" ecosystem is the one I'm most familiar with: https://funds.ecosyste.ms/funds/java
From their list of 200+ "most critical packages", I extracted the ones I care most about: kotlin, junit4, slf4j, gson, guava, logging-log4j2, groovy, jna, jmh, jcommander, and findbugs. While hardly a representative sample, I'm concerned that several of these (junit4, jmh, and findbugs) appear to be unmaintained. I don't understand how sending money to Ecosystems Funds is going to improve these packages.
Jcommander, which I thought was unmaintained, proves on closer inspection to have a 2.0 release (from August) that I missed because it hasn't been uploaded to Maven Central.
2 notes
·
View notes
Text
Share tips for improving code quality and maintainability.
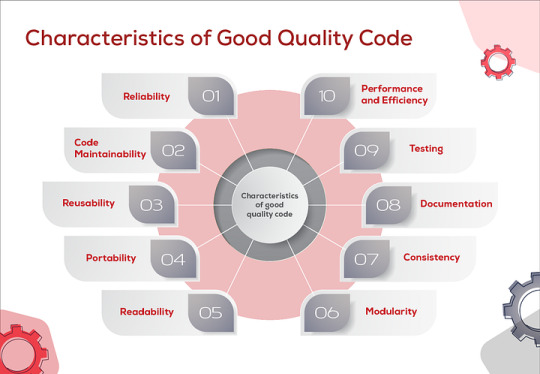
1. Follow Java Naming Conventions
Classes: Use PascalCase for class names (e.g., EmployeeDetails).
Methods/Variables: Use camelCase for method and variable names (e.g., calculateSalary).
Constants: Use uppercase letters with underscores for constants (e.g., MAX_LENGTH).
2. Use Proper Object-Oriented Principles
Encapsulation: Make fields private and provide public getters and setters to access them.
Inheritance: Reuse code via inheritance but avoid deep inheritance hierarchies that can create tightly coupled systems.
Polymorphism: Use polymorphism to extend functionalities without changing existing code.
3. Write Clean and Readable Code
Keep Methods Small: Each method should do one thing and do it well. If a method is too long or does too much, break it down into smaller methods.
Avoid Nested Loops/Conditionals: Too many nested loops or conditionals can make code hard to read. Extract logic into separate methods or use design patterns like the Strategy or State pattern.
4. Use Design Patterns
Leverage proven design patterns like Singleton, Factory, Observer, and Strategy to solve common problems in a standardized, maintainable way.
Avoid overcomplicating things; use patterns only when they add clarity and solve a specific problem.
5. Implement Proper Error Handling
Use exceptions appropriately. Don’t overuse them, and catch only the exceptions you can handle.
Ensure that exceptions are logged for better debugging and auditing.
Use custom exceptions to represent domain-specific issues, so they are easier to debug.
6. Utilize Java’s Stream API
The Stream API (introduced in Java 8) helps reduce boilerplate code when performing collection operations like filtering, mapping, and reducing.
It makes code more concise and expressive, which helps with readability and maintainability.
7. Write Unit Tests
Use JUnit and Mockito for unit testing and mocking dependencies.
Write test cases for all critical methods and components to ensure the behavior is as expected.
Use Test-Driven Development (TDD) to ensure code correctness from the start.
8. Use Dependency Injection
Prefer Dependency Injection (DI) for managing object creation and dependencies. This decouples components and makes testing easier (using tools like Spring Framework or Guice).
DI helps to make your classes more modular and improves maintainability.
9. Avoid Code Duplication
Use methods or utility classes to avoid repeating code.
If the same logic is used in multiple places, refactor it into a single reusable method.
10. Use Annotations
Use Java annotations (like @Override, @NotNull, @Entity, etc.) to improve code clarity and reduce boilerplate code.
Annotations help to enforce business logic and constraints without having to manually check them.
11. Leverage IDE Features
Use tools like IntelliJ IDEA or Eclipse to automatically format code and identify potential issues.
Many IDEs have integrated tools for running tests, refactoring code, and applying coding standards, so make full use of these features.
12. Optimize for Performance Without Sacrificing Readability
Only optimize performance when necessary. Premature optimization can lead to complex code that’s difficult to maintain.
Profile your code to identify bottlenecks, but prioritize clarity and maintainability over micro-optimizations.
13. Implement Proper Logging
Use a logging framework like SLF4J with Logback or Log4j2 for logging. This provides a consistent logging mechanism across the application.
Ensure that logs are meaningful, providing information about the application’s state, errors, and flow, but avoid excessive logging that clutters output.
14. Document Your Code
Use JavaDocs to generate documentation for public methods and classes.
Document not just the what but also the why behind critical decisions in the codebase.
15. Keep Your Codebase Modular
Break your project into smaller, well-defined modules, and avoid large monolithic classes.
Use packages to group related classes, ensuring that each class or module has a single responsibility.
16. Use Static Analysis Tools
Integrate tools like Checkstyle, PMD, and SonarQube to enforce coding standards, detect bugs, and ensure code quality.
These tools help you identify code smells and areas where quality can be improved.
0 notes
Text
Critical Apache Log4j2 flaw still threatens global finance
http://i.securitythinkingcap.com/T7hwbx
0 notes
Text
2 years on, Log4j still haunts the security community
Dive Brief: Two years after the historic disclosure of a critical zero-day vulnerability in the Apache Log4j library sent organizations racing to contain the damage, nearly 2 in 5 applications are still using vulnerable versions, according to a report released Thursday from Veracode. The report found nearly one-third of applications are running Log4j2 1.2.x, which reached end-of-life status in…
View On WordPress
0 notes
Text
Hey! If you've seen my previous post about the serious exploit in Minecraft, and are wondering if it's still unsafe to play multiplayer: it's mostly safe now, however you still need to be cautious depending on certain things. For one thing, you need to be sure that the server you're playing on has been patched (unless its running the latest version- 1.18.1+ is safe by default), plus you need to take into account what mods/launcher you use.
I made a pretty detailed write-up that covers all of these things, so please give it a read if you're worried! And don't be afraid to ask if you have any questions.
click here please
You can also read Mojang's announcement about this here (but mine goes into more detail about mods/3rd party launchers)
PS: This only applies to Minecraft: Java edition, and you have nothing to fear if you play on Realms
57 notes
·
View notes
Photo

Say how many now?
3 notes
·
View notes
Text
Log4Shell Quick Lab Setup for Testing
Log4Shell Quick Lab Setup for Testing
Last month, On December 09 2021, The release of a Remote Code Execution POC over twitter involving exploitation of Apache’s log4j2 logging class took everyone’s peace away. The attack was pretty simple and the fact that it can be easily exploited by anyone is what made this more terrifying. The first edition of this attack which was exploited in the wild was based on exploitation of JNDILookup…

View On WordPress
#apache logging log4j exploit#dnslog.cn#interactsh. canarytoken#jndiexploit#jndiexploitkit#log4j#log4j2#log4shell#log4shell.tools#marshelsec
0 notes
Text
Log4Shell Resources
For those coming to our January meeting, here are some resources you can use to familiarize yourself with Log4Shell / CVE-2021-44228:
Sample Log4Shell Vulnerable App by christophetd
Log4J2 Security Vulnerabilities page
Log4J2 Release History
JNDI Injection Exploit by welk1n
Initial Log4Shell POC by tangxiaofeng7
LunaSec write-up on Log4Shell
JNDIExploit by feihong-cs
Log4j Vulnerability (Log4Shell) Explained // CVE-2021-44228 youTube video by LiveOverflow
0 notes
Text
受到 Log4j2 影響的清單
最近大家都在忙著補 Log4j2 的安全漏洞 (先前在「Log4j2 的 RCE」這邊有提到),有人整理了目前受到影響的軟體的清單以及對應的討論連結:「Log4Shell log4j vulnerability (CVE-2021-44228) – cheat-sheet reference guide」。 用這包來翻起來會方便一些,另外也可以順便翻一下有什麼其他軟體中獎… 然後 Cloudflare 的 CEO Matthew Prince 在 Twitter 上有提到從他們家的資料看起來,2021/12/01 就已經有攻擊在外面跑了,這也是之前會說這是 0-day 的原因: Earliest evidence we’ve found so far of #Log4J exploit is 2021-12-01 04:36:50 UTC. That suggests it was…
View On WordPress
0 notes
Link

0 notes
Link
Log information is very important for Software development. It provides very important data for further analysis. Logging is an important aspect of any modern software development.
0 notes
Text
Quixol Shutdown: Postponed
This is a bit of a weird one. We will be postponing the date at which Quixol officially shuts down. Yay?
The log4j2 exploit, which affects Minecraft, has made us have to put some rather strict limits on who can join the server for the time being, as a precautionary measure against people hoping to cause damage using this exploit.
At time of writing, this exploit should be patched on the server, but we're not taking any chances, so the server is currently whitelisted to players of Veteran rank or higher. We will lift this whitelist in the next few days or so, and make a short follow-up post.
The date of Quixol's imminent demise has been postponed to January 6th, 2022. The server will remain online until that date, and possibly for a little while afterwards. But you can be certain that the 6th will be the final day recorded in the annals of Quixol's lengthy history- a full backup of the server will be taken on that day, and anything that happens afterward will not be included in the packaged world download that will be uploaded for archival purposes.
As for the exploit in Minecraft, we highly recommend that all of you who want to play on Quixol (or any other server) read this post regarding keeping yourself safe in minecraft multiplayer: (x).
We also recommend reading Mojang's announcement post about the exploit, although the github gist linked previously provides more info for those of you who use 3rd-party clients or modded installations.
Stay safe out there! -Admin Vivi
7 notes
·
View notes
Text
Java Log4j2 sux <=2.14.1 = JNDI Log4j vulnerability
Apache Log4j2 <=2.14.1 JNDI features used in the configuration, log messages, and parameters do not protect against attacker-controlled LDAP and other JNDI-related endpoints. An attacker who can control log messages or log message parameters can execute arbitrary code loaded from LDAP servers
when message lookup substitution is enabled.
From log4j 2.15.0, this behavior has been disabled by default. In previous releases (>2.10) this behavior can be mitigated by setting system property "log4j2.formatMsgNoLookups" to “true” or by removing the JndiLookup class from the classpath (example: zip -q -d log4j-core-*.jar org/apache/logging/log4j/core/lookup/JndiLookup.class). Java 8u121 (see https://www.oracle.com/java/technologies/javase/8u121-relnotes.html) protects against remote code execution by defaulting "com.sun.jndi.rmi.object.trustURLCodebase" and "com.sun.jndi.cosnaming.object.trustURLCodebase" to "false".
from https://nvd.nist.gov/vuln/detail/CVE-2021-44228

Wowow
Credit: This issue was discovered by Chen Zhaojun of Alibaba Cloud Security Team.
via https://logging.apache.org/log4j/2.x/security.html
3 notes
·
View notes
Note
Hi, I thought you might be interested about this, the vulnerability was discovered (or at least published) today not just for minecraft, but general Java systems! If you search CVE-2021-44228 you can find more about it
yup, thanks for mentioning this! i already knew but i think i forgot to post about it. it is a vulnerability in any java project which utilizes certain versions of log4j2.
2 notes
·
View notes
Photo

❗ ADVISORY ❗ An advisory has just been released for Apache Log4j2 library. We recommend Australian organisations check whether products they use are affected by a Log4j2 vulnerability. https://t.co/6IAQlR5962 https://t.co/fe7WnGpc56 (via Twitter https://twitter.com/CyberGovAU/status/1471037527788335114)
1 note
·
View note