#malwarebytes software
Explore tagged Tumblr posts
Text
Say Goodbye to Annoying Ads: A Deep Dive into Malwarebytes Browser Guard
We all know how irritating it can be—those pesky pop-up ads that appear out of nowhere, slowing down our browsing experience and invading our privacy. You know, the kinds that make you accidentally click on them and take you to some sketchy website. But let’s end the frustration here and now. Malwarebytes Browser Guard is not just another ad-blocker; it’s a guardian angel for your online…

View On WordPress
2 notes
·
View notes
Text
Malwarebytes Anti-Malware used to look like this.
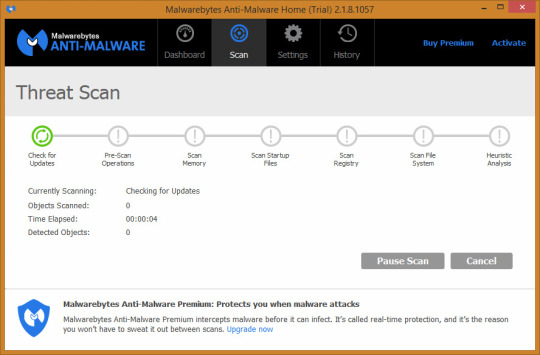
#Malwarebytes#old screenshot#software screenshot#unknown year#my screenshot#software#software history
0 notes
Text

PSA! THERE IS MALWARE ON YAYTEXT!
I'm not fully sure just how relevant this will be, but if anyone else uses yaytext to fancify their text with unicode, please be aware that there is now malware on the yaytext website ( yaytext.com ). it has been on there for at least a week now, so if you have gone onto the site, you might have been infected!
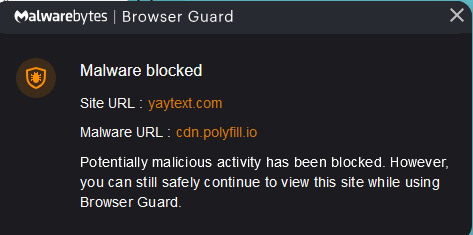
WHAT NOW? IF YOU HAVE VISITED YAYTEXT:
first, run a malware scan on your computer. you can do this for FREE with malwarebytes, bitdefender, or kaspersky*. you can find the free versions of these antivirus softwares on their respective websites, and I will link them below for convenience.
after you run the malware scan (hopefully you are not infected!), add the respective browser guard to your browser. as you can see by my screenshot, I use Malwarebytes' broswer guard. if you decide to use their browser guard too, you will still be able to safely use yaytext.
WHERE ELSE DO I GO?
you should assume that yaytext IS NOT safe to use for the time being! there are plenty of other unicode generators out there, however, so you don't have any disruption with your aesthetics.
some alternatives are:
fontspace font generator
lingojam text generator
fontalic
I have just checked all of these sites and none of them have malware on them at this time.
ANTIMALWARE SCANNING
MalwareBytes - free version BitDefender - free version Kaspersky* - free version
*note that Kaspersky is being banned in the U.S. for being a Russian company. The ban is over worries that Russia could use the AV as spyware in the U.S., because the Kremlin can force any company in Russia to share all of their data with them. Despite this, Kaspersky is a top contending cybersecurity research company. If you are not comfortable using Kaspersky, studies have shown that BitDefender provides near equivalent results. source: i am getting my degree in cybersecurity lol
74 notes
·
View notes
Text
I put together a quick guide to torrenting for my friend and I thought I'd share it with all of you:
Torrenting is a form of file sharing where instead of uploading files to a centralized server, computer users share local files between themselves in a peer-to-peer system.
Steps:
Download a torrent client- a program that allows you to torrent. It is wise to have a vpn and an aggressive antimalware program as well. I prefer Transmission, which theoretically runs on all operating systems
https://transmissionbt.com/download
2. Find something you want to torrent- the pirate bay is a fine place to start
3. Safety check:
Is the torrent size appropriate for what you are supposed to be getting? A torrent that is way too large or too small suggests there may be malware in the torrent.
Is the number of files within the torrent appropriate for what you are supposed to be getting? Too many files suggest there may be malware in the torrent.
When was it uploaded? Older torrents are more trustworthy, be wary of anything that has been posted within the last month.
How many seeders (people who have the program locally on their computer and are making it available to share) are there? The more seeders there are, the more likely it is to be safe
4. Click the magnet link [On pirate bay it’s the link that says “GET THIS TORRENT”] and open it or paste it into Transmission
5. Select a destination folder
6. Keep Transmission open while the file downloads
7. Safety Check 2:
Check the folder for any unexpected files. Many times there will be separate files for the video (these are usually .mp4) and the captions (these are usually .srt), and this is fine. There may also be a .txt containing information about the torrent. DO NOT CLICK any .exe or .zip files without knowing what they are!!!! If you cannot verify what these files contain you should delete them immediately
Scan all files with an antivirus software like malwarebytes to verify their safety, or at the very least check the file properties.
8. Enjoy! And remember it is polite to leave Transmission running to seed the torrent for other people.
List of torrent terms: https://www.androidauthority.com/what-are-torrent-seeders-3232600/
19 notes
·
View notes
Note
Hello, have you talker about your art process anywhere? I am very interested in how you got into glitch art/photomanipulation/however you’d call this, and i want to learn more. Do you have programs you use, plugins, do you use any physical media or scanography/scanner manipulation? I really want to hear about anything you wanna talk about regarding the creation process for your art. Thank you for sharing your work.
Yes! Unfortunately, I tried answering this question in a ton of detail but tumblr didn’t save it as a draft automatically - which was a frustrating experience to say the least - so this is my second attempt at answering this ask — you’ve asked a lot of really valuable questions here, I’ll do my best to be concise in my answers!
When I first began playing around with editing software, I was 16 and simply wanted to make memes and silly edits. This was around 2015-2016, whenever vaporwave was a fresh concept and Resonance was trending on Vine — which is a sentence that makes me feel fucking ancient. I was really entranced by vaporwave, which had this off-white nostalgia for post-consumerist 80s and 90s cultural trends. I later became interested in how many of those cultural trends persisted and evolved into Y2K culture and beyond.



these are some of the images I was working on during that period of time, which were loosely inspired by indie horror and jazz cups and soundcloud rap. I was so proud of learning how to make my own scanlines using GIMP :)
Late 2016 I began my freshman year at a hoighty-toighty art school that I was too poor to attend, and quickly entered a mental health downward spiral — but I learned many valuable things, most of that info was painfully basic; my education prior to that was not anything special. I would not consider myself someone with exceptional aptitude for art — I just have a chronic compulsion to break things.
So, where to begin? My recommendation to anyone who’s newly interested in this style of artwork and editing:
Glitchet is a repository of info regarding many different styles and methods of distortion - from sonification to slipscans, there’s a ton of good info to comb through. Most of the techniques and tools covered are free to use, but there is some paid stuff out there too - but if you know your way around, virtually everything is free. More on that shortly :)
As for my process, programs, plugins, etc - there is a lot, and I don’t think I can cover everything. Primarily: Photoshop, After Effects, GIMP, ArtStudio Pro for iOS, Procreate, DestroyPix, and a number of other pieces of software that perform smaller, specific functions - such as BigJpg for AI-upscaling. I also employ analogue/physical distortion techniques like circuit-bending, slipscan, and more. These require additional hardware and knowledge; such as access to a copier/scanner, old CRT screens, and the ability to solder + work with low voltage electronics without accidentally shorting them out. Best part is that you can ✨layer✨ anything and everything, collage style — which is my favorite aspect, very playful and exploratory.
Now, if you’re like me and can’t afford fuck-all, but wholeheartedly believe that money should not be a limiting factor for creativity, I recommend installing the Adobe Creative Suite from downloadpirate(dot)com - which is also where I’ve gotten many of my plugins, although I do also pay for the plugins that I come to really appreciate, as they’re typically done by independent developers who could actually use the scratch. Same risks as any pirate cove: intrusive ads, popups, and redirect chains - use Ublock Origin to kill these annoyances. I recommend performing a scan with Malwarebytes after using any sketchy-looking-download site, but I was raised to be a bit paranoid so that’s purely preferential.
As for plugins:
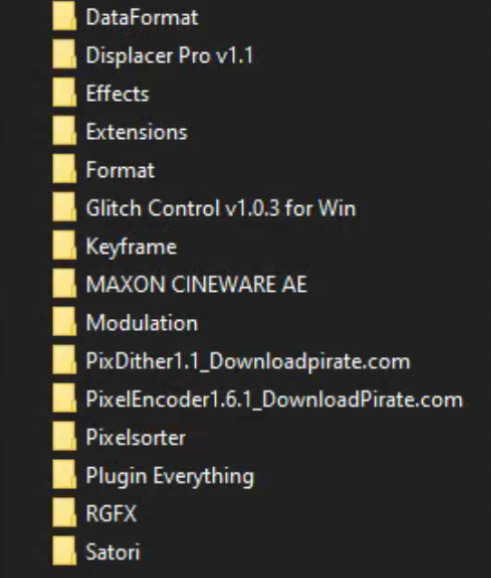
Filenames in this image may correspond with the developer of the plugin — you can just search the filename + ‘after effects plugin’ and you’ll almost certainly find your way.
Most commonly, I use Pixelsorter, Pixdither, Displacer Pro, Pixel Stretch, and Hacksaw — although some of the plugs that I use aren’t listed above, like Datamosher, which is a script-based solution that helps remove i-frames from a clip in After Effects, all without having to use VLC and any handwritten scripts (the ol’ fashioned way).





These are all from the last year or so, to show the relative growth I’ve experienced since my time spent as a creature of 16 years. Naturally, I’m also like, more of a person now - so the art is partly better because I’ve simply suffered more :p
When I started, I didn’t know any of the jargon or how to describe a specific effect I was trying to achieve - so I taught myself how to do stuff by googling around, and if I couldn’t find an answer (which was 90% of the time) I’d just try to figure shit out. Which rarely ever resulted in outright success, but was always a significant learning experience. That’s why I’m so quick to drop the link to Glitchet! Sometimes I can’t help but wonder what I’d be doing now if I had known there was an online library for info on how to produce different types of distortions - definitely would’ve spent less time trial-and-erroring my way through aesthetics.
In conclusion: there’s so much to try and you should try absolutely everything that interests you. It’s free if you’re cool enough to steal it; though some things (like hardware) are gonna cost. You don’t need talent or an exceptional education, though both of those things would certainly help — and you’ll never run out of things to learn because there are infinite ways to break shit. More so than anything else, you need a willingness to explore, experiment, and fail often. You’ll fail miserably at times, so a proclivity for humiliation is also a big plus. Eventually your failures will start looking like successes; but you’ll have forgotten the difference by then and will be free to make whatever the fuck you want :)
I’m glad that you enjoy the work! tumblr has always been the best place for me to share my lil jpegs and actually find a real sense of connection with others who are similarly jazzed. My life completely bottomed-out a few years ago and I was in a really bad place whenever I logged into my blog for the first time in half-a-decade and started posting again. My personal growth from then to now has been a strange and incredible experience, and I’m so glad that I had the art and the funny little gays on this website to help me through the toughest points and teach me valuable things about myself; so if I can give back a little knowledge, I’ll gladly take that opportunity! I hope these findings serve you as well as they’ve served me.
#my asks#THANK YOU!!#I hope this is formatted in a way that is easy to read - clarity and concision are not my strongest skills#godspeed!#documentation#reference
19 notes
·
View notes
Text
oh hey does anyone know of a good antivirus software?
i used to use malwarebytes, but i've started getting popup ads from malware bytes telling me to upgrade my protection.
like hey did you know that 20 years ago that would've been considered a type of malware? 😑
4 notes
·
View notes
Text
How to check if your computer is being monitored
In today's digital age, the issue of privacy and security is more pressing than ever. Whether you’re a casual user or a professional, understanding if your computer is being monitored is crucial. This guide will delve into the signs of monitoring, tools to detect it, and steps to safeguard your privacy.

Understanding Computer Monitoring
Before diving into the signs and detection methods, it’s essential to understand what computer monitoring entails. Monitoring can involve tracking your online activity, keystrokes, file access, and even webcam usage. This can be done by malicious software (malware), spyware, or legitimate monitoring software used by employers or parents.
Types of Monitoring
Malware and Spyware: These are malicious programs that can be installed without your knowledge. They can track your activities and send data back to an attacker.
Keyloggers: This type of software records keystrokes, capturing sensitive information like passwords and personal messages.
Remote Access Tools (RATs): These tools allow someone to control your computer remotely, monitoring your screen, accessing files, and even using your webcam.
Legitimate Monitoring Software: Often used in corporate environments, this software tracks employee activity for productivity or compliance reasons. While legal, it can still infringe on personal privacy.
Signs That Your Computer May Be Monitored
Recognizing the signs that your computer might be monitored is the first step in protecting yourself.
1. Unusual System Behavior
Slow Performance: If your computer suddenly becomes sluggish, it might be due to monitoring software consuming resources.
Frequent Crashes or Freezes: Unexpected system crashes can indicate underlying issues, including malware.
2. Suspicious Programs
Unknown Applications: Check your installed programs for any unfamiliar applications. Many monitoring tools disguise themselves as legitimate software.
High Resource Usage: Use the Task Manager (Windows) or Activity Monitor (Mac) to look for processes consuming excessive CPU or memory.
3. Network Activity
Unexplained Network Traffic: Use network monitoring tools to check for unusual data being sent or received. High outbound traffic could indicate that data is being transmitted without your consent.
Blocked Ports: Monitoring software often uses specific ports to communicate. If you notice blocked ports that you didn’t configure, it could be a red flag.
4. Webcam and Microphone Behavior
Indicator Light Activation: If your webcam or microphone is being accessed without your knowledge, the indicator light may be on even when you're not using it.
Unexpected Recordings: Check for unusual files that could be recordings made by your microphone or webcam.
5. Browser Behavior
Unusual Browser Extensions: Check for extensions you didn’t install. Some can track your browsing activity.
Unexpected Redirects: Frequent redirects to strange sites or altered search results can indicate tracking.
6. Security Alerts
Antivirus Notifications: If your antivirus software frequently alerts you about threats, it may indicate that monitoring software is present.
Firewall Alerts: Unusual outgoing connection attempts can suggest that an unauthorized program is trying to access the internet.
Tools to Detect Monitoring Software
If you suspect that your computer is being monitored, several tools can help you investigate further.
1. Antivirus and Anti-Malware Software
Using a reliable antivirus or anti-malware program can help detect and remove malicious software. Some popular options include:
Malwarebytes: Excellent for detecting and removing malware and spyware.
Norton: Offers comprehensive protection against various types of threats.
2. Network Monitoring Tools
Tools like Wireshark can help analyze network traffic and identify suspicious activity. You can monitor data packets to see if there are any unexpected connections.
3. Task Manager / Activity Monitor
Regularly check the Task Manager (Windows) or Activity Monitor (Mac) for processes that look unfamiliar or suspicious. Research any questionable applications before taking action.
4. System Scans
Use built-in tools to perform system scans:
Windows Defender: Run a full scan for malware and spyware.
Mac’s Built-in Security Features: Use the Malware Removal Tool for additional scanning.
5. Firewall Monitoring
Make sure your firewall is active and monitor logs for any unusual activity. A firewall can block unauthorized access attempts and alert you to potential threats.
Steps to Protect Your Privacy
If you determine that your computer is being monitored or you want to prevent it from happening, follow these steps to enhance your security.
1. Update Your Software Regularly
Keeping your operating system and all software up-to-date ensures that you have the latest security patches. This reduces vulnerabilities that can be exploited by monitoring tools.
2. Use Strong Passwords
Implement strong, unique passwords for all your accounts and devices. Consider using a password manager to generate and store complex passwords securely.
3. Enable Two-Factor Authentication
Two-factor authentication (2FA) adds an extra layer of security by requiring a second form of verification, making unauthorized access much more difficult.
4. Install a Firewall
Ensure you have a firewall activated, whether it’s built-in (like Windows Firewall) or third-party. This helps control incoming and outgoing network traffic.
5. Be Cautious with Downloads
Avoid downloading software from untrusted sources, as this can introduce malware to your system. Always verify the legitimacy of software before installing it.
6. Regularly Review Permissions
Check application permissions on your device regularly. Revoke access for any apps that do not need to access your camera, microphone, or location.
7. Use a VPN
A Virtual Private Network (VPN) encrypts your internet connection, making it difficult for anyone to monitor your online activities.
8. Educate Yourself
Stay informed about the latest cybersecurity threats and best practices. Knowledge is your best defense against monitoring.
When to Seek Professional Help
If you suspect your computer is being monitored and cannot identify or remove the software yourself, consider seeking professional help. Cybersecurity experts can perform a thorough analysis of your system and provide tailored solutions.
Conclusion
Understanding if your computer is being monitored is vital for protecting your privacy. By recognizing the signs, utilizing detection tools, and implementing security measures, you can safeguard your personal information. Remember, vigilance is key in the ever-evolving landscape of digital security. Stay informed, proactive, and secure in your online presence.
#Computer Security#Online Privacy#Cybersecurity#Monitoring Software#Malware Detection#Privacy Protection#Digital Security#Keyloggers#Network Monitoring#Antivirus#VPN#Internet Safety#Personal Data Security#Remote Access Tools#Digital Awareness
2 notes
·
View notes
Text
"Browse Safely" malware alert
I found a "Browsing Safely" add-on my Firefox, it's easy to spot because who uses Yahoo Search any more? All I had to was disable it and restart, and I reported it. I did run the safety software Malwarebytes after and my Mac is uninfected.
But I was surprised to find that there are hundreds of skeevy malware advice sites out there that look useful and may give reasonable advice, but could easily be spreading malware themselves. Avoid anything with "malware" in the domain name!
The browser sites have the legit information:
2 notes
·
View notes
Quote
セキュリティソフトウェアプロバイダーがライバル企業のソフトウェアを「悪意ある」「脅威」「望ましくない可能性のあるソフトウェア (PUP)」と呼んだ場合、名誉棄損で訴えることのできない意見の表明ではなく、客観的事実の主張である可能性が高いとの見解を米連邦巡回区第 9 控訴裁判所が示している (原告側プレスリリース、 The Register の記事、 裁判所文書: PDF)。 この裁判では Enigma Software が同社のスパイウェア対策製品 SpyHunter を PUP として検出・検疫した Malwarebytes を訴えている。Enigma の主張する Malwarebytes の違法行為は、ランハム法に違反する虚偽の宣伝とニューヨーク州法が定める不法行為、コモンローによる取引関係の妨害といったものだ。 一審のカリフォルニア北部地区連邦地裁では、Malwarebytes が Enigma 製品を PUP と識別したことを意見の表明だと判断。ニューヨークの対人管轄権がないとする Malwarebytes の主張を認めたほか、妨害された取引関係を Enigma が示していないとして訴えを棄却した。 第 9 巡回区控訴裁判所では妨害された取引関係が示されていないとする連邦地裁の判断を支持する一方、Malwarebytes による Enigma 製品の識別が客観的事実の主張と判断したのに加えて、訴えが当初ニューヨークで提起されたものであることからニューヨークの対人管轄権が認められると判断し、これら 2 点について連邦地裁に差し戻した。
米連邦控訴裁判所 曰く、セキュリティソフト企業がライバル製品を「脅威」と識別すれば名誉棄損の可能性 | スラド セキュリティ
3 notes
·
View notes
Photo
i was going to put it in the tags but whatever, answering because I'm passionate about it:
I'm in a sort of compsci degree and I'm baffled at how students younger than me don't even have an idea of what a torrent is. And it's not even just piracy, something I've noticed is that sometimes it extends to Open Source alternatives too. There is this mentality of "if you don't pay for it then it's not right/good enough". Which is bullshit, for two reasons:
They don't need your money. The only exception is small, independent projects. Adobe doesn't need your money. Spotify, YouTube, Netflix, Microsoft, and all of the rest don't need your money.
the internet was born to be free. Apart from the military history it has, the net was literally made to be accessible, made for everyone to use. It shouldn't have thousands of subscriptions.
I'll start by giving off a library of resources: weboasis. This has a little bit of everything and it is a good starting point to find other stuff. Only downside is that the original library is discontinued, so what we have is a stable copy of what it once was (someone very kind decided to make it accessible, the site has an unfortunately sad history)
So you need a book? libgen, zlib, theeye (one of my favourites honestly)
You want to watch something? hydrahd for movies and series (there are lots of netflix mirrors honestly), and you can visit the piracy.moe site for anime if you're into that.
Music? I find streaming APKs on telegram mostly but also downloading media is best. Spotify is currently off limits as of just a few days ago (again, reason why actually having media is best, they will take it away from you) but there is ways to have yt music if you look. If I may I love a site called Radiooooo which can make you listen to music from a world map (it's really cool, and they deserve the praise).
Torrents for literally anything from software to media? personally I find them on snowfl.com because it gives me how old the torrent is and the site it was originally shared to along with a filtering option (+ peers and seeders) (to be honest the pirate bay is the one I'm usually more skeptical as they are usually old torrents that often don't work, but 1337 works great), and as for torrenting software qbittorrent is the current best (don't use uTorrent, just don't).
You need an alternative to literally anything? use alternativeto.net, lots of open source software and sites that don't need a subscription (+ peer reviews)
And of course to be safe about all this the only thing that is worthy giving money to is a good antivirus (malwarebytes) and VPN if you want to be extra safe.
Also, not giving the specific links because they change all the time (mirrors). But you just need a search on your browser of choice to find them (not the best, but I've been using Brave for all the common stuff since it blocks me every ad. Yes even YouTube). The site you used for streaming or downloading disappears? just check for another list of resources (Reddit, also search GitHub-piracy-index, and you'll eventually find a list updated enough)(also, a lot of stuff is on telegram: movies, episodes, software; but groups and channels may be a bit harder to find). Again, extra step: use Tor, Reddit has all of the .onion you can wish for (and, the zlib address on there has been the same for years).
Just be safe about malware, check the info you give to the sites you visit, and you're all set. Also remember that this sort of resources are always in motion, they never stay the same for too long. They change as the internet changes.

#common resources#of course pay attention to where you go#but remember piracy is not unlawful in this economy#it actually never was
370K notes
·
View notes
Text
¿Qué es el mantenimiento de computadoras? Todo lo que necesitas saber para que tu PC vaya como nueva

¿Alguna vez has encendido tu computadora y notado que se siente más lenta, ruidosa o incluso inestable? Puede que esté pidiendo a gritos un poco de amor técnico. El mantenimiento de computadoras no solo ayuda a mejorar el rendimiento, sino que también prolonga la vida útil del equipo y evita sustos innecesarios. Ya sea que uses tu máquina para estudiar, trabajar o simplemente navegar por redes sociales, cuidarla regularmente es clave. En esta entrada te explicamos qué es el mantenimiento de computadoras, cómo hacerlo (tanto física como digitalmente), y por qué no deberías dejarlo para después. ¡Vamos allá! 💻✨
¿Qué significa hacer mantenimiento a una computadora?
📌 No se trata solo de limpiar con un plumero. El mantenimiento de computadoras consiste en una serie de acciones preventivas y correctivas orientadas a mantener el equipo funcionando óptimamente. Es como llevar tu carro al taller: revisas partes mecánicas (hardware), actualizas sistemas (software) y limpias lo que hace tiempo no tocas. Existen dos tipos principales: - Mantenimiento físico (del hardware): Se enfoca en los componentes tangibles: ventiladores, teclado, pantalla, conexiones internas, etc. - Mantenimiento lógico (del software): Incluye tareas como eliminar archivos temporales, actualizar programas, optimizar el sistema operativo y revisar posibles amenazas.
✅ Tareas clave del mantenimiento físico
🧰 Aquí entramos en modo “técnico” pero sin salirnos del hogar. Estas son algunas acciones que puedes realizar: - Limpieza interna y externa - Retirar polvo del ventilador, disipador y puertos. - Limpiar pantalla y teclado con productos adecuados. - Verificación de conexiones - Revisar cables internos sueltos, batería hinchada o mal conectada. - Asegurar que todos los componentes reciban energía correctamente. - Reemplazo de piezas desgastadas - Cambiar pasta térmica del procesador si está seca. - Mejorar almacenamiento con SSD si aún usas disco duro tradicional. - Ventilación y temperatura - Evitar sobrecalentamiento colocando la computadora en superficies planas y frescas. - Usar bases de refrigeración en laptops.

🛠️ Acciones importantes del mantenimiento lógico
💻 Ahora vamos con el lado invisible: el software. Esta parte es ideal si no quieres tocar tornillos pero sí quieres tener un sistema rápido y seguro. - Eliminar archivos basura - Archivos temporales, cachés y descargas innecesarias consumen espacio valioso. - Desfragmentar el disco duro (solo HDD) - Ayuda a organizar la información y mejora el acceso a los archivos. - Actualizar sistema operativo y programas - Las actualizaciones corrigen errores, mejoran seguridad y ofrecen nuevas funciones. - Realizar análisis antivirus periódicos - Mantén tu equipo libre de virus y malware con escaneos regulares. - Gestionar programas en el inicio - Desactivar aplicaciones que arrancan automáticamente reduce el tiempo de carga. - Crear puntos de restauración - Ideal cuando algo sale mal tras una actualización o instalación. 💡 Tip práctico: Usa herramientas como CCleaner, Malwarebytes o el propio Windows Defender para automatizar muchas de estas tareas.
¿Con qué frecuencia debes hacer mantenimiento a tu PC?
⏰ Esto depende del uso que le des: Tipo de usuarioFrecuencia recomendadaUsuario básico (navega, ve videos)Cada 6 mesesUsuario medio (trabajo, ofimática)Cada 3-4 mesesUsuario avanzado (edición, juegos, programación)Cada 1-2 meses ⚠️ Si notas lentitud, ruido excesivo o pantallazos azules, ¡no esperes! Es señal de que algo necesita atención urgente.
🔧 Consejos rápidos para usuarios ocupados
📌 No tienes que ser experto para cuidar tu computadora. Estas acciones básicas pueden marcar la diferencia: - Reinicia tu equipo al menos una vez a la semana. - Guarda tus documentos importantes en la nube o en disco externo. - Evita comer frente al teclado 👀 - Nunca apagues tu PC directamente desde el botón durante procesos críticos. - Usa programas confiables y evita descargar archivos desconocidos. Read the full article
#actualizacióndesoftware#antivirus#basederefrigeración#CCleaner#consejosdemantenimiento#cuidadodePC#desfragmentardiscoduro#educacióndigital#estudiantes#evitarsobrecalentamiento#guíacompleta#informática#limpiezadearchivostemporales#limpiezadehardware#Malwarebytes#mantenimientodecomputadoras#mantenimientofísico#mantenimientológico#mejorarrendimientoPC#optimizacióndeWindows#pastatérmica#PCsaludable#profesores#programaseninicio#repararcomputadora#sistemaoperativo#tecnología#tutorialestécnicos#usuarioavanzado#usuariobásico
0 notes
Text
I use this software.
It's an easy way to turn off settings in windows that you'd normally have to put a bit of effort in to find. Settings like trackers and a bunch of other stuff.
It works for windows 10
Revo Uninstaller is a great program for force uninstalling programs you couldn't uninstall otherwise. Like Microsoft Edge.
If you use it to uninstall edge and its not finding the program when you search for it, you'll have to open edge, then use the target mode which allows you to select desired programs manually.
target the opened Microsoft edge window and it'll start the process.
The cool thing about this program is that is does a hard uninstall, completely wipes out everything related to the program and it's stuff in the registry.
might I add, if you uninstall Microsoft edge, it will remove copilot as well. I've done this and it's been a few months since then I think. I've updated my laptop a few times and it hasn't come back. though if you want to avoid edge from coming back with an update, here's a vid on the more indepth process of its removal.
Something I usually do is go into my app manager or program manager window and read through what all is installed. I delete anything I didn't install myself and doesn't have a purpose. If you're not tech savvy, have a web browser open to search for programs you don't recognize. if it looks necessary, leave it alone. Usually windows is pretty good about not letting you uninstall important programs but it's good to play it safe.
Doing this whenever you notice a sudden dip in pc performance is a great way to catch unwanted programs that may have slipped in with something you downloaded recently. Paired with a good anti malware program like Malwarebytes, youre pretty much golden.
last tip.
It's a pretty good practice to Optimize and Defrag your harddrive regularly. It basically does a clean sweep of your harddrive by deleting unnecessary files.
Here's a link to instructions on how to do that. When you set about this process, you should have an option of to what degree the clean up is done (meaning what files is targeted), how regularly this process happens.
It usually deletes residual files, stuff in your downloads folder, trash folder, and stuff like that. you'll get to see what all is there when you do it before you confirm the clean up.
After doing all that, you've got yourself a nice and clean pc that should work better than it did before.
All the programs I linked to are free and can be used without paying for them.
I've been super into computers since I was kid so these are pretty solid methods of pc maintainance on the virtual side. If you have a proper box pc, and I guess if you're feeling brave enough to open up your laptop, don't forget to clean use an air duster to clean out your consul.
I promise you, nothing will help more than a clean pc and cooling fans.
i thought my laptop was on its last leg because it was running at six billion degrees and using 100% disk space at all times and then i turned off shadows and some other windows effects and it was immediately cured. i just did the same to my roommate's computer and its performance issues were also immediately cured. okay. i guess.
so i guess if you have creaky freezy windows 10/11 try searching "advanced system settings", go to performance settings, and uncheck "show shadows under windows" and anything else you don't want. hope that helps someone else.
#its because the os is not properly optimized#you have to debloat it then strip it down to bare bones before doing anything#in regards to windows running like shit#you see#windows is an accordian of itself#its backwards compatibility isnt a simulator#its still got its old old code deep in there#im not sure how far back it is#but in windows 11 when it first came out#you could right click and back pedel in a sense to older option menues#meaning it just kept going into the code and you would get older option menu designs#backwards compatibility is good#but i feel like windows needs to be gutted and scrubbed clean#then new lighter software needs to be developed for backwards compatibility#i doubt it would happen but honestly windows is such a heavy and chunky os#mac and chrome os is relatively light by comparison#its because mac is office work targeting so theres not as much bloat going on there#someone correct me if im wrong though#this is in regards to windows running like shit#windows 10
229K notes
·
View notes
Link
[ad_1] The top 10 spyware list describes the most common spyware threats behind famous spyware attacks and is frequently identified by leading antispyware tools from vendors like Webroot, Norton and Malwarebytes. What is spyware? Spyware refers to malicious software purposely designed to access a computer and record its activity. Spyware can track and record a user's browsing habits, login credentials, passwords and more. The spyware author uses the information obtained in this data breach to engage in fraudulent activity or might sell it to a third party. [embed]https://www.youtube.com/watch?v=ZgXw3WCNXc8[/embed] Spyware often spreads through phishing emails, malicious downloads, fake apps or compromised websites. Once installed, it can run in the background logging keystrokes, capturing screenshots or transmitting sensitive data. Adware, keyword loggers, Trojans and mobile spyware are common forms of spyware. Visit our spyware feature page to learn more about this problem and how to beat it. The top 10 spyware threats Some of the top spyware threats organizations face today, according to security experts, include the following: 1. Advanced Keylogger Advanced Keylogger, a keystroke logger, monitors keystrokes and takes screenshots. 2. CoolWebSearch (CWS) CoolWebSearch (CWS) is a software suite originally used to exploit vulnerabilities in Internet Explorer (IE), which Microsoft officially retired in 2022. Though now considered outdated, CWS remains historically significant as one of the earliest, most aggressive examples of browser hijackers. It could rewrite search engine results, redirect DNS lookups and change browser settings to push users toward ad-laden pages. 3. FinSpy (aka FinFisher) FinSpy, or FinFisher, is an advanced suite of surveillance tools sold to law enforcement and intelligence agencies. FinSpy works on Windows, macOS, Linux, Android and iOS operating systems. Its capabilities vary depending on the platform. Law enforcement, intelligence agencies and threat actors often use FinSpy to secretly turn on microphones to record conversations, switch on cameras, record and transmit images, transmit key logs in real time, modify files and more. 4. Gator (GAIN) Gator is a type of adware that can display banner advertisements based on a user's web surfing habits. Gator is often bundled with numerous free software programs and pirated applications. Gator monitors online user behavior and targets them with personalized ads. 5. GO Keyboard GO Keyboard was a virtual Android keyboard app that masqueraded as a legitimate mobile application. It was found to transmit personal information to its remote servers without explicit user consent, violating Google Play policies. The app was eventually removed from the Google Play Store, but it serves as a cautionary example of the risks posed by third-party keyboard apps. Information shared by GO Keyboard spyware included the following: Android OS version. Device model and screen size. Google account email address. International Mobile Subscriber Identity (IMSI). Location. Network type. Preferred language. Social media interactions. GO Keyboard executes code from a remote server to breach Google Play privacy policies. 6. HawkEye HawkEye, a keylogger virus, was dormant for years but resurfaced during the COVID-19 pandemic. It infects machines to track key logs and other inputs, sharing that information with a remote server. New versions are increasingly difficult to detect due to enhanced anti-detection features. One campaign impersonated the World Health Organization in a social engineering attack designed to trick users into downloading a malicious attachment. 7. HuntBar HuntBar is a Trojan application that hijacks web browser settings and downloads and installs adware without the user's knowledge. Also known as Adware, Websearch or WinTools, HuntBar tracks browsing behavior, redirects web traffic to affiliate websites, forcefully displays advertisements and installs more spyware programs and toolbars on IE. 8. Look2Me Look2Me is spyware that tracks user behavior, website logs and social media interactions and shares this information with a remote server. The information is then used to show intrusive advertisements. Look2Me spyware also downloads and installs various add-ons, extensions, toolbars and other unwanted programs on a user's computer. This makes the spyware threat more dangerous than traditional adware. Removing Look2Me is difficult because of its rootkit-type functionality. 9. Pegasus NSO Group's Pegasus spyware is one of the latest spyware threats making headlines. Although Pegasus was initially developed to fight terrorism, evidence suggests that many clients use Pegasus to spy on journalists, political activists, political opponents and almost anyone the client desires. The governments in France, Hungary, India, Saudi Arabia, United Arab Emirates, the United Kingdom and the United States are known to have used Pegasus spyware. 10. PhoneSpy PhoneSpy is an example of a spyware virus that pretends to be a mobile application to gain access to and infect Android mobile devices. This approach allows threat actors to remotely control mobile devices and steal data. Mobile applications with PhoneSpy aren't available on Google Play Store, so it's believed to spread through social engineering attacks and third-party platforms. Emerging mobile spyware threats As mobile device usage continues to rise, threat actors have increasingly turned to smartphones as high-value targets. Here are a few of the most concerning mobile spyware threats discovered in recent years: Hermit Hermit is a powerful mobile spyware tool designed to infect both Android and iOS devices. Typically delivered via fake mobile carrier apps or malicious links in SMS messages, Hermit can record audio, track location, intercept texts and access contact lists. It has been linked to state-sponsored surveillance campaigns targeting journalists and political figures. SpyNote SpyNote is a remote access trojan (RAT) that targets Android users. Once installed, it allows attackers to record audio, access text messages and call logs, and even activate the device's camera without user consent. SpyNote is often disguised as a legitimate app and distributed through unofficial app stores or phishing links. Anatsa (also known as TeaBot) Anatsa is a banking Trojan with spyware-like capabilities. It has been known to steal login credentials by capturing keystrokes and recording screen activity on Android devices. Anatsa spreads through fake app downloads posing as QR code readers, PDF viewers or security apps. How to protect yourself from spyware Spyware can be difficult to detect until it's already compromised your device. Here are simple best practices to help reduce the risk of infection: Use reputable antivirus and antispyware software and keep it up to date. Avoid downloading apps or files from untrusted sources, especially third-party websites. Enable automatic software updates on your devices to patch known vulnerabilities. Use strong, unique passwords and turn on two-factor authentication (2FA) for sensitive accounts. Be cautious of phishing emails and attachments, especially those with urgent or alarming messages. Review app permissions before installing, particularly for mobile apps that request access to contacts, location or cameras. Two-factor authentication is a good form of spyware protection. Staying alert and maintaining good digital hygiene can significantly lower your risk of falling victim to spyware. FAQs about spyware threats Can spyware infect mobile devices?Yes. Spyware is increasingly targeting mobile devices through fake apps, malicious links and phishing messages. Android devices are especially vulnerable when apps are downloaded from third-party sources. What is the most dangerous spyware in 2025?Pegasus remains one of the most sophisticated spyware tools in use. However, newer threats like Hermit and Anatsa are also highly capable and dangerous, especially on mobile platforms. How do I know if my device has spyware?Common signs include unexpected battery drain, overheating, slow performance, unknown apps appearing, and unusual network activity. If you suspect spyware, run a trusted mobile security scan and review app permissions. Is Pegasus spyware still active?Yes. While originally marketed for counterterrorism, Pegasus has been used by various governments and entities for broader surveillance. It remains a high-profile threat and continues to evolve. Learn more on how to prevent spyware through best practices, including using a layered defense or content filtering. See how to protect against malware as a service. Also, protecting your endpoints is critical for maintaining security. Learn why endpoint detection and response technologies are essential for endpoint protection. Explore how to protect, detect and remove malware from mobile devices. [ad_2] Source link
0 notes
Text
🛡️ How to Protect Your Computer from Viruses – Fast & Easy Tips
Hi Tumblr! 👋
I’m William, and I help people secure their computers and protect their personal/business data from hackers, malware, and other threats.
Here are 5 quick things you can do TODAY to improve your computer’s security:
1️⃣ Install antivirus software (like Malwarebytes or Windows Defender) 2️⃣ Run a full system scan – catch hidden threats 3️⃣ Update your operating system – patches fix security holes 4️⃣ Use strong passwords (a password manager helps!) 5️⃣ Back up your important files (cloud or external hard drive)
🔒 Want professional help? I offer remote cybersecurity clean-up services including:
Malware & virus removal
Computer speed-up & optimization
Full security check-up
✅ Fast, affordable & remote!
👉 Check out my service here: https://www.fiverr.com/s/pdNjgWN
Stay safe out there, and feel free to message me with any questions! 🚀
#cybersecurity#technology#programming#tech#techhelp#computerrepair#malware#fiverr#remoteservice#smallbusiness#pcsecurity
1 note
·
View note
Text
Why Your Computer Gets Slower Over Time — And What You Can Do About It

Ever wondered why a computer that once felt lightning-fast now takes forever to load? You're not alone. Over time, every computer tends to slow down. Whether it’s an older machine or a fairly new one, the frustration is real. Understanding why this happens is the first step to fixing it—and even preventing it.
In this guide, we’ll explore the most common causes of slow PCs and what you can do to bring them back up to speed. If you’re looking for more in-depth solutions, don’t miss our full guide on how to speed up a slow computer.
1. Hidden Bloat and Startup Programs
You install a cool new app today. Then another one next week. Eventually, your system is packed with software—some of which you don’t even remember downloading. Many of these programs run in the background, especially at startup, slowing down your boot time and eating up system resources.
💡 Quick Fix:
Open Task Manager and check the Startup tab.
Disable apps you don’t need launching at startup.
Uninstall programs you no longer use.
2. Running Low on Disk Space
A nearly full hard drive can really hurt your PC's performance. Windows needs free space to manage system files and temporary data. When your drive is full, everything slows down—searches, app launches, and even basic file browsing.
🧹 What to Do:
Delete junk files and downloads.
Use Disk Cleanup or Storage Sense (on Windows 10).
Empty the Recycle Bin regularly.
This small habit can significantly speed up your machine.
3. Malware and Background Apps
Malware isn’t just a security risk—it’s a major performance killer. Even if your PC isn’t showing obvious signs of infection, malicious software could be silently running, using up memory and CPU power.
🔐 Recommended Actions:
Run a full system scan with Windows Defender or Malwarebytes.
Check for browser extensions that might be slowing down your web activity.
Avoid downloading cracked software or files from unknown sources.
Just keeping your PC clean can make a huge difference in speed and stability.
4. Outdated Hardware or Drivers
Sometimes, it’s not the software—it’s the hardware. If you’re still running on a traditional hard drive, switching to an SSD can make your computer feel brand new. Also, missing or outdated drivers can cause hiccups that slow everything down.
⚙️ Upgrade Ideas:
Upgrade to SSD if you're using an HDD.
Add more RAM if your system is lagging with multiple open tabs.
Update your graphics and chipset drivers regularly.
5. How to Keep Your Computer Fast (Even After Years)
Maintaining a fast PC isn’t just about fixing problems—it’s about building healthy tech habits. A few minutes of monthly maintenance can go a long way.
✅ Pro Tips:
Restart your computer at least once a week.
Keep your system and apps updated.
Schedule regular cleanups using built-in tools.
For a more advanced, step-by-step guide, check out our full article on how to speed up a slow computer. It includes expert-level tips tailored for Windows 10 users.
Final Thoughts
Computers slow down for a lot of reasons—but that doesn’t mean you have to live with it. Now that you know what causes the lag, you can take smart steps to keep your system running smoothly. Whether it’s clearing space, upgrading hardware, or simply restarting more often, every small action adds up.
And remember, when you’re ready to dive deeper into the fix, we’ve got a full breakdown of 10 tech tips to help you speed up your computer, right here.
1 note
·
View note