#mysql opensource
Explore tagged Tumblr posts
Text

Scrabble
Tech Scramble Time! ⏳
Unscramble the letters to reveal today’s hidden tech word! 🖥️✨
Comments your answer below👇
💻 Explore insights on the latest in #technology on our Blog Page 👉 https://simplelogic-it.com/blogs/
🚀 Ready for your next career move? Check out our #careers page for exciting opportunities 👉 https://simplelogic-it.com/careers/
#scrabblechallenge#scrabble#scrabbletiles#scrabbleart#mysql opensource#data#database#scrabbleframe#scrabbleletters#words#boardgame#fun#scrabblecraft#makeitsimple#simplelogicit#simplelogic#makingitsimple#itservices#itconsulting
0 notes
Text
PHP (Hypertext Preprocessor) is a popular server-side scripting language designed for web development. It allows developers to create dynamic and interactive web applications. Unlike HTML, which is static, PHP enables web pages to change based on user input, database queries, and other conditions.
#PHP#WebDevelopment#BackendDevelopment#PHPForBeginners#TechEducation#PHPProgramming#PHPFramework#TechBooks#PHPDevelopment#ServerSideProgramming#PHPProjects#TechLearning#MySQL#PHP7#PHP8#WebAppDevelopment#FullStackDevelopment#PHPDevelopmentTips#Programming#PHPBestPractices#TechTutorial#PHPCode#PHPWebDevelopment#OpenSource#PHPDevelopmentTools#PHPMySQL
0 notes
Text
MySQL Naming Conventions

What is MySQL?
MySQL is a freely available open source Relational Database Management System (RDBMS) that uses Structured Query Language (SQL). SQL is the most popular language for adding, accessing and managing content in a database. It is most noted for its quick processing, proven reliability, ease and flexibility of use.
What is a naming convention?
In computer programming, a naming convention is a set of rules for choosing the character sequence to be used for identifiers that denote variables, types, functions, and other entities in source code and documentation.
General rules — Naming conventions
Using lowercase will help speed typing, avoid mistakes as MYSQL is case sensitive.
Space replaced with Underscore — Using space between words is not advised.
Numbers are not for names — While naming, it is essential that it contains only Alpha English alphabets.
Valid Names — Names should be descriptive of the elements. i.e. — Self-explanatory and not more than 64 characters.
No prefixes allowed.
Database name convention
Name can be singular or plural but as the database represents a single database it should be singular.
Avoid prefix if possible.
MySQL table name
Lowercase table name
MySQL is usually hosted in a Linux server which is case-sensitive hence to stay on the safe side use lowercase. Many PHP or similar programming frameworks, auto-detect or auto-generate class-based table names and most of them expect lowercase names.
Table name in singular
The table is made up of fields and rows filled with various forms of data, similarly the table name could be plural but the table itself is a single entity hence it is odd and confusing. Hence use names like User, Comment.
Prefixed table name
The table usually has the database or project name. sometimes some tables may exist under the same name in the database to avoid replacing this, you can use prefixes. Essentially, names should be meaningful and self-explanatory. If you can’t avoid prefix you can fix it using php class.
Field names
Use all above cases which include lowercase, no space, no numbers, and avoid prefix.
Choose short names no-longer than two words.
Field names should be easy and understandable
Primary key can be id or table name_id or it can be a self-explanatory name.
Avoid using reserve words as field name. i.e. — Pre-defined words or Keywords. You can add prefix to these names to make it understandable like user_name, signup_date.
Avoid using column with same name as table name. This can cause confusion while writing query.
Avoid abbreviated, concatenated, or acronym-based names.
Do define a foreign key on database schema.
Foreign key column must have a table name with their primary key.
e.g. blog_id represents foreign key id from table blog.
Avoid semantically — meaningful primary key names. A classic design mistake is creating a table with primary key that has actual meaning like ‘name’ as primary key. In this case if someone changes their name then the relationship with the other tables will be affected and the name can be repetitive losing its uniqueness.
Conclusion
Make your table and database names simple yet understandable by both database designers and programmers. It should things that might cause confusion, issues with linking tables to one another. And finally, it should be readable for programming language or the framework that is implemented.
#MySQL#DatabaseManagement#SQL#NamingConventions#RelationalDatabase#DatabaseDesign#CodingStandards#TableNaming#FieldNaming#DatabaseSchema#ProgrammingTips#DataManagement#CaseSensitivity#PrimaryKey#ForeignKey#DatabaseBestPractices#OpenSource#DatabaseOptimization#MySQLTips#DataStructure
0 notes
Text
#Playstation7 #framework #BasicArchitecture #RawCode #RawScript #Opensource #DigitalConsole
To build a new gaming console’s digital framework from the ground up, you would need to integrate several programming languages and technologies to manage different aspects of the system. Below is an outline of the code and language choices required for various parts of the framework, focusing on languages like C++, Python, JavaScript, CSS, MySQL, and Perl for different functionalities.
1. System Architecture Design (Low-level)
• Language: C/C++, Assembly
• Purpose: To program the low-level system components such as CPU, GPU, and memory management.
• Example Code (C++) – Low-Level Hardware Interaction:
#include <iostream>
int main() {
// Initialize hardware (simplified example)
std::cout << "Initializing CPU...\n";
// Set up memory management
std::cout << "Allocating memory for GPU...\n";
// Example: Allocating memory for gaming graphics
int* graphicsMemory = new int[1024]; // Allocate 1KB for demo purposes
std::cout << "Memory allocated for GPU graphics rendering.\n";
// Simulate starting the game engine
std::cout << "Starting game engine...\n";
delete[] graphicsMemory; // Clean up
return 0;
}
2. Operating System Development
• Languages: C, C++, Python (for utilities)
• Purpose: Developing the kernel and OS for hardware abstraction and user-space processes.
• Kernel Code Example (C) – Implementing a simple syscall:
#include <stdio.h>
#include <unistd.h>
int main() {
// Example of invoking a custom system call
syscall(0); // System call 0 - usually reserved for read in UNIX-like systems
printf("System call executed\n");
return 0;
}
3. Software Development Kit (SDK)
• Languages: C++, Python (for tooling), Vulkan or DirectX (for graphics APIs)
• Purpose: Provide libraries and tools for developers to create games.
• Example SDK Code (Vulkan API with C++):
#include <vulkan/vulkan.h>
VkInstance instance;
void initVulkan() {
VkApplicationInfo appInfo = {};
appInfo.sType = VK_STRUCTURE_TYPE_APPLICATION_INFO;
appInfo.pApplicationName = "GameApp";
appInfo.applicationVersion = VK_MAKE_VERSION(1, 0, 0);
appInfo.pEngineName = "GameEngine";
appInfo.engineVersion = VK_MAKE_VERSION(1, 0, 0);
appInfo.apiVersion = VK_API_VERSION_1_0;
VkInstanceCreateInfo createInfo = {};
createInfo.sType = VK_STRUCTURE_TYPE_INSTANCE_CREATE_INFO;
createInfo.pApplicationInfo = &appInfo;
vkCreateInstance(&createInfo, nullptr, &instance);
std::cout << "Vulkan SDK Initialized\n";
}
4. User Interface (UI) Development
• Languages: JavaScript, HTML, CSS (for UI), Python (backend)
• Purpose: Front-end interface design for the user experience and dashboard.
• Example UI Code (HTML/CSS/JavaScript):
<!DOCTYPE html>
<html>
<head>
<title>Console Dashboard</title>
<style>
body { font-family: Arial, sans-serif; background-color: #282c34; color: white; }
.menu { display: flex; justify-content: center; margin-top: 50px; }
.menu button { padding: 15px 30px; margin: 10px; background-color: #61dafb; border: none; cursor: pointer; }
</style>
</head>
<body>
<div class="menu">
<button onclick="startGame()">Start Game</button>
<button onclick="openStore()">Store</button>
</div>
<script>
function startGame() {
alert("Starting Game...");
}
function openStore() {
alert("Opening Store...");
}
</script>
</body>
</html>
5. Digital Store Integration
• Languages: Python (backend), MySQL (database), JavaScript (frontend)
• Purpose: A backend system for purchasing and managing digital game licenses.
• Example Backend Code (Python with MySQL):
import mysql.connector
def connect_db():
db = mysql.connector.connect(
host="localhost",
user="admin",
password="password",
database="game_store"
)
return db
def fetch_games():
db = connect_db()
cursor = db.cursor()
cursor.execute("SELECT * FROM games")
games = cursor.fetchall()
for game in games:
print(f"Game ID: {game[0]}, Name: {game[1]}, Price: {game[2]}")
db.close()
fetch_games()
6. Security Framework Implementation
• Languages: C++, Python, Perl (for system scripts)
• Purpose: Ensure data integrity, authentication, and encryption.
• Example Code (Python – Encrypting User Data):
from cryptography.fernet import Fernet
# Generate a key for encryption
key = Fernet.generate_key()
cipher_suite = Fernet(key)
# Encrypt sensitive user information (e.g., account password)
password = b"SuperSecretPassword"
encrypted_password = cipher_suite.encrypt(password)
print(f"Encrypted Password: {encrypted_password}")
# Decrypting the password
decrypted_password = cipher_suite.decrypt(encrypted_password)
print(f"Decrypted Password: {decrypted_password}")
7. Testing and Quality Assurance
• Languages: Python (for automated tests), Jest (for JavaScript testing)
• Purpose: Unit testing, integration testing, and debugging.
• Example Unit Test (Python using unittest):
import unittest
def add(a, b):
return a + b
class TestGameFramework(unittest.TestCase):
def test_add(self):
self.assertEqual(add(10, 20), 30)
if __name__ == '__main__':
unittest.main()
8. Order of Implementation
• Phase 1: Focus on core system architecture (low-level C/C++) and OS development.
• Phase 2: Develop SDK and start building the basic framework for UI and input management.
• Phase 3: Work on backend systems like the digital store and integrate with front-end UI.
• Phase 4: Begin rigorous testing and debugging using automated test suites.
This comprehensive approach gives you a detailed idea of how each component can be built using a combination of these languages and technologies. Each section is modular, allowing teams to work on different aspects of the console simultaneously.
[Pixel Art/Sprites/Buildinodels/VictoriaSecretPixelArtKit #Playstation7 #DearDearestBrands]


#victoriasecretrunway#runwaybattle#victoria secret fashion#victoria secert model#victoriasecret#victoria secret#VictoriaSecretRunwayBattle#capcom victoriasecret#capcom videogames#playstation7#ps7#deardearestbrands#capcom#digitalconsole#python#script#rawscript#raw code#framework#VictoriaSecretVideoGame#deardearestbrandswordpress
2 notes
·
View notes
Text
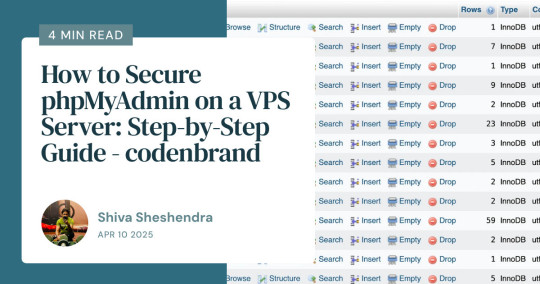
🚨 Securing phpMyAdmin on Your VPS: A Must-Do for Devs! 🔐
Take 15 mins to harden your server. Your future self (and your clients) will thank you! 🙌
Read the Blog here: https://www.codenbrand.com/blog/how-to-secure-phpmyadmin-on-a-vps-server-step-by-step-guide/
Connect with developer @ https://www.shivafeb17.com
#WebDevelopment #FreelanceWebDesign #PHP #WordPress #MySQL #phpMyAdmin #CyberSecurity #TechTips #OpenSource #DevLife #WebDesign #VPS #Linux #Apache #FreelancerTips #CodeSmart
#php programming#freelance#web developers#web development#web design#freelancing#web developing company#phpdevelopment#wordpress#php
0 notes
Text
Joomla is an admirable Content Management System, used across the web world. Therefore, most of the hackers try to find out the ways to hack a Joomla websites. Joomla is a opensource CMS, therefore everyone (including hackers) understand how it works. This makes it challenging to protect it from known vulnerabilities. Most Joomla hacks are caused by well known vulnerabilities that are not patched/fixed by the website owners in time. If you are also a Joomla user, then you must read this article. Today, we will share the 10 tips that can help you protect your website from hackers and attackers. Use Strong And Secure Password It is imperative to use a strong password for your website. Most of the hackers try to guess your passwords by using the list of commonly used passwords. So, make sure to create your password personal but switch letters with numbers or other characters. Don’t try to use a word that is already appearing on your site. Create a password that other people won’t be able to guess. Change Your Database Prefix Old versions of Joomla used to install with a database table prefix. Unluckily, hackers know that, and if you leave the default settings, then the hacker will fine-tune their attacks from their end. Thus, it is necessary for you to change the database prefix of your Joomla database tables. Database hacks are the most dangerous Joomla website hacks because from a hacker can change anything in your website. They can add new pages with links, or can completely take control of your sites email function and also send out hundreds of spam emails in your name. Choose A Good Hosting Provider Choose a reliable hosting company that can offer you the safe and secure hosting service. When possible and have enough budget, you must opt for dedicated hosting. However, not every business has big budget therefore you can also use the shared hosting, but if one of the other website on the shared server gets hacked, then your website would also become vulnerable. Well, you can choose the small Joomla hosting companies because they offer the best hosting plans for Joomla sites. Here are some tips: picking the right hosting company for your Joomla website needs. Change The Joomla’s Administrator Username Joomla websites take the administrator username as “admin” by default. In fact, most of the people never change this default username, which allows the hackers to get into your website by using this simple “admin” username. So, it is important to change the administrator username as it reduces the chances of hacker guessing your login details. By doing this, you can strengthen your site’s security. Keep Your Joomla Site And Other Extensions Up-to-date You should always keep your website updated with the latest versions of Joomla. Usually, Joomla releases a new version in every two months. The latest version is Joomla 3.3.6, offering thousands of exciting features and security tools. With every new release, Joomla comes with some excellent security fixes that can strengthen your site’s security. Correct File Permission Joomla is developed with a MySQL database and a huge amount of PHP files. It has been seen that most Joomla hacks affect PHP files, and the files are located in a series of folders that will also contain script files, pdfs, images and videos. Usually, file permissions of Joomla allow or disallow servers and browsers the ability to see content, write to files and database within the folders. So it is important that the folder in Joomla should have 755 permissions and the files should have permissions of 644. Use Two-Factor Authentication We can say two-Factor Authentication is an extra layer of security for your website that creates a temporary password. If you don’t have the access to password or secret key, then you will not be able to login into your Joomla admin account. It will be better for you to provide the additional layer of security to your site, as it will improve security against password hacking, key loggers and many other security threats.
You Can Remove Or Delete Unused Joomla Extensions Many Joomla users test different components, extensions and modules on their website and forget to remove them after using them. Leaving such extensions installed, even if they are disabled, can cause a lot of security issue. So it will be better to remove or delete the unused extensions. .htaccess To Block Security Exploits Of Joomla You can use .htaccess to block database and file exploits. You can also hire a professional Joomla developer who can help you in this and offer you the protected and secured website. Keep A Backup Of Your Site You should always keep a backup of your Joomla website.. If something went wrong, then you can quickly get back to an older version of your website with ease. In fact, try to find out which extension caused the security issues, and then you can uninstall that one. In this blog, we explored the top 10 points that will help you protect your Joomla Website. If you want to strengthen your site’s security, then follow these tips. Maggie Sawyer is well known as a professional Web Developer for the best PSD to WordPress service provider company MarkupHQ Ltd. She also happens to be a blogger who loves to share useful and informative tutorials on WordPress customization services.
0 notes
Text
PHP Developer For IT Company in Vipul Trade Center Sec-48 GurgaonWFO
Job Description Technical Skills: ? PHP, MySQL, HTML5 ? Strong Coding skills, good analytical skills and problem… in development on any opensource PHP frameworks / CMS: Laravel, Zend ? Framework, Cake PHP, Y ii, Symfony, Drupal, WordPress… Apply Now
0 notes
Text
DBeaver 24.2
Versie 24.2 van DBeaver is uitgekomen. Met dit programma kunnen databases worden beheerd. Het kan onder andere query's uitvoeren en data tonen, filteren en bewerken. Ondersteuning voor de bekende databases, zoals MySQL, Oracle, DB2, SQL Server, PostgreSQL, Firebird en SQLite, is aanwezig. Het is verkrijgbaar in een opensource-CE-uitvoering en drie verschillende commerciële uitvoeringen. Deze voegen onder meer ondersteuning voor verschillende nosql-databases toe, zoals MongoDB, Apache Cassandra en Apache Hive, en bevatten verder extra plug-ins en jdbc-drivers. De changelog voor deze uitgave ziet er als volgt uit: Changes in DBeaver version 24.2: http://dlvr.it/TCgc8g
0 notes
Video
youtube
The video will give you a brief walk through on the new features, updates and enhancements in v.4.5 of Spurtcommerce. For more information, visit https://www.spurtcommerce.com/nodejs-shoppingcart-ecommerce-whatsnew https://www.spurtcommerce.com/spurtcommerce-change-log
#Ecommerce#ecommercesolutions#new features#ecommerce trends#new updates#spurtcommerce#nodejs#angular#opensource#mysql#multivendor#b2b ecommerce#b2cecommerce#ecommerce tips#node js ecommerce
2 notes
·
View notes
Text

Scrabble
Tech Scrabble Time! ⏳
Unscramble the letters to reveal today’s hidden tech word! 🖥️✨
Comments your answer below👇
💻 Explore insights on the latest in #technology on our Blog Page 👉 https://simplelogic-it.com/blogs/
🚀 Ready for your next career move? Check out our #careers page for exciting opportunities 👉 https://simplelogic-it.com/careers/
#scrabblechallenge#scrabble#scrabbletiles#scrabbleart#mysql#opensource#data#database#scrabbleframe#scrabbleletters#words#boardgame#fun#scrabblecraft#makeitsimple#simplelogicit#simplelogic#makingitsimple#itservices#itconsulting
0 notes
Text
Reasons to Choose PHP Web Development for Business
Today, one may often run over the debates about the feasibility of applying PHP in the development of IT products and services. There are such a significant number of productions (for the most part, written in feelings by baffled programmers) worrying the downsides and limitations of PHP and its structures, that, as an entrepreneur, you may likewise begin hesitating if PHP is suitable for your undertaking. Is the situation really so awful? And assuming this is the case, why 83 % of all web services are as yet being written in PHP.

Well, interestingly, due to its open-source nature and an outstanding community, PHP is always updating. Its exhibition is truly improving with every variant and with the advancement of its systems. This structures the ground for other advantages which make it such a prominent choice for business software development. From websites to e-commerce solutions, from glossy new businesses to firmly established businesses, PHP is chosen solely or partially as the programming language for IT projects for the number of handy reasons.
PHP Open-source Nature Saves Budget:
The most great thing that successes developers’ and IT decision-makers’ dependability for PHP is that it is unreservedly accessible. PHP requires no download or permitting charges. It is open-source and is conveyed under the General Public License.
Added to apparent spending reserve funds, it additionally brings about a huge and dynamic universal community. This prompts constant upgrades in its functionality and in the noteworthy pool of assets and facilities. There are many PHP-based solutions whose viability has just been tried, so one doesn’t have to put assets in rehashing the wheel.
However, to be targeted it ought to be referenced that this fundamental preferred position of PHP can once in a while become the principle danger for the venture. Effortlessness and availability fundamentally bring down the edge of vocation section, which at times prompts diminished quality. In this way, the decision of an expert group with demonstrated mastery is an issue.
PHP consumes Less Time for Development:
PHP is a partially object-oriented language. It makes code reusability conceivable. Reusable PHP segments spare much time and exertion in the process of development. There are loads of PHP structures, as Symfony, CodeIgniter, Laravel, Joomla, WordPress, and so on. Every one of them conveys its own functionality and offers quick and secure development in explicit fields.

PHP was intentionally enhanced for making different web applications rapidly. It has such worked in capacities as getting to the GET and POST and working with HTML and URLs. For organizations, it implies that the time (and, separately, cash) spent on the development diminishes and the IT item or administration based on PHP can begin bringing ROI prior.
PHP Code is Flexible:
An incredible bit of leeway of PHP is its versatility and flexibility. PHP code is perfect with every single real stage from Windows, Unix, and Linux to macOS. It bolsters a large portion of the servers (counting Apache, Microsoft IIS, Netscape, iPlanet, Caudium, Xitami, Tornado, and so forth.) and in excess of 20 databases (for instance, MySQL, MongoDB, PostgreSQL, and others). That is the reason PHP is often picked for making cross-stage applications: it enables organizations to use the current foundation with insignificant expenditures.

Since PHP is an implanted language, it effectively addresses joining issues. Despite the fact that it is normally prescribed to utilize it with HTML, PHP is effectively incorporated with JavaScript, WML, XML, and other programming languages. There are no issues with program presentation since every one of the contents is accumulated on the server-side.
Tasks regularly experience functionality changes sooner or later. With PHP, because of its dynamic nature, it is conceivable to execute them independently of the phase of development and without time-misfortune.
PHP-based Services are Easily Scalable and Well-documented:
As far as ROI, organizations often win when the IT arrangement is worked in iterations. It permits propelling various modules of the software logically and making essential corrections over the span of the development. With PHP, it is conceivable to create and bolster versatile IT anticipates and ceaselessly produce numerous pages with different settings.
PHP code is described by straightforwardness and phenomenal documentation. In this way, it sets aside less effort to comprehend in detail what is happening in the code — obviously, when it is elegantly composed. Furthermore, you can securely sort out iterative development with insignificant dangers of foot-hauling on the off chance that you have to change the software engineer or the whole group.
Note:
Are you looking for PHP website development then we are here to help you.
PHP Software is Easily Maintained and Updated:
Because of effectively understandable linguistic structure, PHP code can be unreservedly altered and changed. That is to say, there are no issues with keeping up and refreshing PHP-based undertakings. They can be rapidly and cost-successfully change in accordance with inventive applications that enter the market and to the new business prerequisites.

What’s more, because of the open-source commitment, new functionality meeting the developing needs of organizations springs up consistently and costs nothing. Also, since PHP code is written in a reliable and particular way, upkeep and backing can be given by any group, not required the one which built up the task.
PHP Ensures Great Opportunities for Hosting:
PHP’s versatility makes it a famous web facilitating alternative for the majority of the facilitating suppliers. Any solid web facilitating supplier underpins PHP in their website facilitating administrations. Typically facilitating bundles accompany PHP support at no additional expense — including either free web host plans or cheap imparted plans to unlimited resource assignment and a free area name.
Good PHP Website Performance Helps to Retain Customers:
Quick website stacking is essential for a group of spectators holding. The human capacity to focus is 6–8 seconds, and if the website is moderate, the clients rapidly leave it and stay away for the indefinite future. PHP guarantees speedy turnaround time because of its quick information processing highlights, remarkable customization potential, and consistent mix with different custom administration frameworks.
PHP was initially made for the age of dynamic web pages, that is the reason its contents settle this errand a lot snappier than other programming languages. PHP code is effectively implanted into HTML, and developers can change over existing static website code into dynamic just by including their PHP code into HTML. As a matter of fact, this is the best language for the formation of undeniable websites on the base of HTML standard.
PHP gives 1–1 correspondence among URLs and documents, of course, making it simple for creators, software engineers, and other colleagues to edit and make web pages. This is particularly helpful on account of huge, for the most part, static substance sites with several substance pages, visit unique cases, and various layouts.
Conclusion:
In case you wish to work with a professional PHP web development company do contact us!
#php website development#PHP web development#Corporate company website development#company website development#Custom PHP Website development#opensource#open source#PHP/MySQL development#Php Web application development#E-commerce Website development
0 notes
Text
Joomla is an admirable Content Management System, used across the web world. Therefore, most of the hackers try to find out the ways to hack a Joomla websites. Joomla is a opensource CMS, therefore everyone (including hackers) understand how it works. This makes it challenging to protect it from known vulnerabilities. Most Joomla hacks are caused by well known vulnerabilities that are not patched/fixed by the website owners in time. If you are also a Joomla user, then you must read this article. Today, we will share the 10 tips that can help you protect your website from hackers and attackers. Use Strong And Secure Password It is imperative to use a strong password for your website. Most of the hackers try to guess your passwords by using the list of commonly used passwords. So, make sure to create your password personal but switch letters with numbers or other characters. Don’t try to use a word that is already appearing on your site. Create a password that other people won’t be able to guess. Change Your Database Prefix Old versions of Joomla used to install with a database table prefix. Unluckily, hackers know that, and if you leave the default settings, then the hacker will fine-tune their attacks from their end. Thus, it is necessary for you to change the database prefix of your Joomla database tables. Database hacks are the most dangerous Joomla website hacks because from a hacker can change anything in your website. They can add new pages with links, or can completely take control of your sites email function and also send out hundreds of spam emails in your name. Choose A Good Hosting Provider Choose a reliable hosting company that can offer you the safe and secure hosting service. When possible and have enough budget, you must opt for dedicated hosting. However, not every business has big budget therefore you can also use the shared hosting, but if one of the other website on the shared server gets hacked, then your website would also become vulnerable. Well, you can choose the small Joomla hosting companies because they offer the best hosting plans for Joomla sites. Here are some tips: picking the right hosting company for your Joomla website needs. Change The Joomla’s Administrator Username Joomla websites take the administrator username as “admin” by default. In fact, most of the people never change this default username, which allows the hackers to get into your website by using this simple “admin” username. So, it is important to change the administrator username as it reduces the chances of hacker guessing your login details. By doing this, you can strengthen your site’s security. Keep Your Joomla Site And Other Extensions Up-to-date You should always keep your website updated with the latest versions of Joomla. Usually, Joomla releases a new version in every two months. The latest version is Joomla 3.3.6, offering thousands of exciting features and security tools. With every new release, Joomla comes with some excellent security fixes that can strengthen your site’s security. Correct File Permission Joomla is developed with a MySQL database and a huge amount of PHP files. It has been seen that most Joomla hacks affect PHP files, and the files are located in a series of folders that will also contain script files, pdfs, images and videos. Usually, file permissions of Joomla allow or disallow servers and browsers the ability to see content, write to files and database within the folders. So it is important that the folder in Joomla should have 755 permissions and the files should have permissions of 644. Use Two-Factor Authentication We can say two-Factor Authentication is an extra layer of security for your website that creates a temporary password. If you don’t have the access to password or secret key, then you will not be able to login into your Joomla admin account. It will be better for you to provide the additional layer of security to your site, as it will improve security against password hacking, key loggers and many other security threats.
You Can Remove Or Delete Unused Joomla Extensions Many Joomla users test different components, extensions and modules on their website and forget to remove them after using them. Leaving such extensions installed, even if they are disabled, can cause a lot of security issue. So it will be better to remove or delete the unused extensions. .htaccess To Block Security Exploits Of Joomla You can use .htaccess to block database and file exploits. You can also hire a professional Joomla developer who can help you in this and offer you the protected and secured website. Keep A Backup Of Your Site You should always keep a backup of your Joomla website.. If something went wrong, then you can quickly get back to an older version of your website with ease. In fact, try to find out which extension caused the security issues, and then you can uninstall that one. In this blog, we explored the top 10 points that will help you protect your Joomla Website. If you want to strengthen your site’s security, then follow these tips. Maggie Sawyer is well known as a professional Web Developer for the best PSD to WordPress service provider company MarkupHQ Ltd. She also happens to be a blogger who loves to share useful and informative tutorials on WordPress customization services.
0 notes
Photo

Reasons for PHP for web development 1.Opensource free and friendly 2.IOS Compatibility 3.Flexible and Dynamic 4.Enhanced Security Wavefront technologies provide a high-quality PHP web development services by our high skilled experienced professional with many years of experience in PHP and Mysql etc...
https://wavefrontech.com/php-development-company/
#php development#web developing company#website design#application#php#outsourcing#outsource projects#india#ecommerce developers
1 note
·
View note
Text
DBeaver 23.3.1
Versie 23.3.1 van DBeaver is uitgekomen. Met dit programma kunnen databases worden beheerd. Het kan onder andere query's uitvoeren en data tonen, filteren en bewerken. Ondersteuning voor de bekende databases, zoals MySQL, Oracle, DB2, SQL Server, PostgreSQL, Firebird en SQLite, is aanwezig. Het is verkrijgbaar in een opensource-CE-uitvoering en drie verschillende commerciële uitvoeringen. Deze voegen onder meer ondersteuning voor verschillende nosql-databases toe, zoals MongoDB, Apache Cassandra en Apache Hive, en bevatten verder extra plug-ins en jdbc-drivers. De changelog voor deze uitgave ziet er als volgt uit: Changes in DBeaver cersion 23.3.1: http://dlvr.it/T0bGWK
0 notes
Text
In our recent article, we looked at Install and Configure LibreNMS on Ubuntu. Here we will cover how to monitor VMware ESXi hosts using LibreNMS. LibreNMS is a community-based fork of the last GPL-licensed version of Observium with plenty of features. The tool is based on PHP/MySQL/SNMP and monitors the network together with your servers. If you’re new to LibreNMS, check out our guide on Top Opensource Network and Server Monitoring Tools, it describes the features of LibreNMS in detail. Step 1: Configure SNMP on VMware ESXi host First SSH or Telnet to your ESXi host with root user credentials. Once logged in, check the current SNMP configurations # esxcli system snmp get Authentication: Communities: Enable: false Engineid: Hwsrc: indications Loglevel: info Notraps: Port: 161 Privacy: Remoteusers: Syscontact: Syslocation: Targets: Users: V3targets: Start the configuration by setting the community string(s). esxcli system snmp set --communities e.g esxcli system snmp set --communities MY_SNMP_STRING Configure SNMP Port esxcli system snmp set --port 161 Enable SNMP on the server esxcli system snmp set --enable true Set syscontact esxcli system snmp set --syscontact [email protected] Set Server Location: esxcli system snmp set --syslocation DC-01 Check SNMP firewall rules: # esxcli network firewall get Default Action: DROP Enabled: true Loaded: true # esxcli network firewall ruleset rule list | grep snmp snmp Inbound UDP Dst 161 161 # esxcli network firewall ruleset allowedip list | grep snmp snmp All If you would like to limit access to SNMP from the trusted subnets or IP addresses only, set it as below: # esxcli network firewall ruleset allowedip add --ruleset-id snmp \ --ip-address 192.168.3.10 # esxcli network firewall ruleset allowedip add --ruleset-id snmp \ --ip-address 192.168.1.0/24 # esxcli network firewall ruleset set --ruleset-id snmp --enabled true To allow from any source IP: esxcli network firewall ruleset set --ruleset-id snmp --allowed-all true To test that the snmpd service is working fine, use the snmpwalk command on LibreNMS host: $ snmpwalk -v 1 -c E.g # snmpwalk -v 1 -c AADHrptO472lQo 10.245.2.2 | more SNMPv2-MIB::sysDescr.0 = STRING: VMware ESXi 5.1.0 build-2000251 VMware, Inc. x86_64 SNMPv2-MIB::sysObjectID.0 = OID: SNMPv2-SMI::enterprises.6876.4.1 DISMAN-EVENT-MIB::sysUpTimeInstance = Timeticks: (126700) 0:21:07.00 SNMPv2-MIB::sysContact.0 = STRING: [email protected] SNMPv2-MIB::sysName.0 = STRING: esxi-01.local SNMPv2-MIB::sysLocation.0 = STRING: DC-01 SNMPv2-MIB::sysServices.0 = INTEGER: 72 SNMPv2-MIB::sysORLastChange.0 = Timeticks: (0) 0:00:00.00 SNMPv2-MIB::sysORID.1 = OID: SNMPv2-MIB::snmpMIB SNMPv2-MIB::sysORID.2 = OID: IF-MIB::ifMIB SNMPv2-MIB::sysORID.3 = OID: IP-MIB::ip SNMPv2-MIB::sysORID.4 = OID: IP-FORWARD-MIB::ipForward SNMPv2-MIB::sysORID.5 = OID: UDP-MIB::udp SNMPv2-MIB::sysORID.6 = OID: TCP-MIB::tcp SNMPv2-MIB::sysORID.7 = OID: SNMPv2-SMI::mib-2.47 SNMPv2-MIB::sysORID.8 = OID: SNMPv2-SMI::org.111.2.802.1.1.2 SNMPv2-MIB::sysORID.9 = OID: SNMPv2-SMI::org.111.2.802.1.1.4 SNMPv2-MIB::sysORID.10 = OID: iso.2.840.10006.300.43 SNMPv2-MIB::sysORID.11 = OID: SNMPv2-SMI::org.111.2.802.1.1.13 SNMPv2-MIB::sysORID.12 = OID: HOST-RESOURCES-MIB::hostResourcesMibModule SNMPv2-MIB::sysORID.13 = OID: SNMPv2-SMI::enterprises.6876.1.10 SNMPv2-MIB::sysORID.14 = OID: SNMPv2-SMI::enterprises.6876.2.10 SNMPv2-MIB::sysORID.15 = OID: SNMPv2-SMI::enterprises.6876.3.10 SNMPv2-MIB::sysORID.16 = OID: SNMPv2-SMI::enterprises.6876.4.90.10 SNMPv2-MIB::sysORID.17 = OID: SNMPv2-SMI::enterprises.6876.4.20 SNMPv2-MIB::sysORDescr.1 = STRING: SNMPv2-MIB, RFC 3418 SNMPv2-MIB::sysORDescr.2 = STRING: IF-MIB, RFC 2863 SNMPv2-MIB::sysORDescr.3 = STRING: IP-MIB, RFC 4293 SNMPv2-MIB::sysORDescr.4 = STRING: IP-FORWARD-MIB, RFC 4292 SNMPv2-MIB::sysORDescr.5 = STRING: UDP-MIB, RFC 4113
SNMPv2-MIB::sysORDescr.6 = STRING: TCP-MIB, RFC 4022 SNMPv2-MIB::sysORDescr.7 = STRING: ENTITY-MIB, RFC 4133 SNMPv2-MIB::sysORDescr.8 = STRING: IEEE8021-BRIDGE-MIB, REVISION 200810150000Z SNMPv2-MIB::sysORDescr.9 = STRING: IEEE8021-Q-BRIDGE-MIB, REVISION 200810150000Z SNMPv2-MIB::sysORDescr.10 = STRING: IEEE8023-LAG-MIB, REVISION 200706200000Z SNMPv2-MIB::sysORDescr.11 = STRING: LLDP-V2-MIB, REVISION 200906080000Z SNMPv2-MIB::sysORDescr.12 = STRING: HOST-RESOURCES-MIB, RFC 2790 SNMPv2-MIB::sysORDescr.13 = STRING: VMWARE-SYSTEM-MIB, REVISION 201008020000Z SNMPv2-MIB::sysORDescr.14 = STRING: VMWARE-VMINFO-MIB, REVISION 201006220000Z SNMPv2-MIB::sysORDescr.15 = STRING: VMWARE-RESOURCES-MIB, REVISION 200810150000Z Restart snmp service after making the changes: # /etc/init.d/snmpd restart Step 2: Adding VMware ESXi host to LibreNMS Once you’re done with the configuration of SNMP on ESXi hosts, you can start adding the hosts to LibreNMS for monitoring. LibreNMS provides the ability to automatically add devices on your network using Auto Discovery feature. All discovery methods run when discovery runs (every 6 hours by default and within 5 minutes for new devices Login to LibreNMS as the librenms user, and navigate to./opt/librenms This should be the home folder of librenms user. $ cd /opt/librenms The first thing to do though is add the required configuration options to config.php. Add SNMP Details To add devices automatically, LibreNMS needs to know your snmp details, examples of SNMP v1, v2c and v3 are below: // v1 or v2c $config['snmp']['community'][] = "my_custom_community"; $config['snmp']['community'][] = "another_community"; // v3 $config['snmp']['v3'][0]['authlevel'] = 'authPriv'; $config['snmp']['v3'][0]['authname'] = 'my_username'; $config['snmp']['v3'][0]['authpass'] = 'my_password'; $config['snmp']['v3'][0]['authalgo'] = 'MD5'; $config['snmp']['v3'][0]['cryptopass'] = 'my_crypto'; $config['snmp']['v3'][0]['cryptoalgo'] = 'AES'; These details will be attempted when adding devices, you can specify any mixture of these. Define you subnets to be scanned using: $config['nets'][] = '192.168.0.0/24'; $config['nets'][] = '172.20.4.0/23'; You can also run a manual SNMP Scan, the syntax is: $ ./snmp-scan.py [-h] [-r NETWORK] [-t THREADS] [-l] [-v] Example: $ ./snmp-scan.py 10.245.2.2 Scanning IPs: * Scanned 1 IPs: 1 known devices, added 0 devices, failed to add 0 devices Runtime: 0.39 seconds This device should appear under Devices > All Devices > Server on LibreNMS admin dashboard. Give it like 5 minutes to collect Server facts and start creating graphs, Logs and host events will start to appear as well. More on monitoring: Monitoring MySQL / MariaDB with Prometheus in five minutes Install LibreNMS Monitoring Tool on CentOS with Letsencrypt and Nginx
0 notes
Text
Linux memory monitor

LINUX MEMORY MONITOR INSTALL
LINUX MEMORY MONITOR SOFTWARE
LINUX MEMORY MONITOR FREE
Zabbix collects metrics from systems using Zabbix agent, SNMP and IPMI agents. It can check standard networking services such as HTTP, FTP, SMTP, and so on.
LINUX MEMORY MONITOR SOFTWARE
Zabbix is an enterprise-level opensource monitoring software to monitor the real-time track of networks, servers, and applications. To display the CPU usage, disk, and networks, in short, use the following command.
LINUX MEMORY MONITOR INSTALL
To install collectl in your system, use the following command. Collectl - Performance monitoring toolĬollectl is a command-line performance monitoring tool to gather information on system resources such as CPU usage, disk, memory, network, and more. It contains a feature that allows it to send notifications to the appropriate authorities when there is a problem or when the error has been resolved. It is compatible with all Unix-like operating systems, and there are 500 different plugins available to monitor your system as needed. Munin is an open-source web-based network monitoring program. For Ubuntu users, use the following command to install Monit. You may see the system status via the command line or HTTP web server. This program can restart the failed services, and the app can send an alert email including the fault details so that urgent action may be taken. It also monitors services like Apache, MySQL, Mail, FTP, Nginx, SSH, and so on.
LINUX MEMORY MONITOR FREE
Monit is a free open-source utility for proactively monitoring and managing system processes, applications, files, directories, and filesystems. To display the memory map of process ID, use the following command. You need to add PID along with pmap command to display the memory map of the given process. The pmap command is used to display the memory map of a process. pmap - Display the memory map of a process To display all information about CPU that mpstat can display, type $ mpstat -A 15. It shows reports for each available processor, starting with processor 0. Mpstat command is used to display processor-related statistics. mpstat - Display processor related statistics To display the network counter using sar, use the following command. To display the swap status, use the '-S- command along with sar command. Similarly, to display CPU average load, use the '-q' option with sar command. To display I/O device status, use the '-d' option along with sar command. Use -A option along with sar command to display detailed information about the I/O Devices, CPU, Memory, and Network statistics. On CentOS/RHEL/Fedora/Rocky Linux and AlmaLinux You can install the package using the following command. The SAR package is not found by default in the Linux system, but you can install the Sysstat package as SAR is part of sysstat. Aside from real-time system monitoring, SAR may also gather performance data in the background on an ongoing basis and analyze it to look for bottlenecking issues. System Activity Report (SAR) is a real-time system monitoring tool.

0 notes