#order tracking software development
Explore tagged Tumblr posts
Text
#Custom order management software#order management software development#tailored order management solutions#custom software for order processing#order management system features#custom-built order management#scalable order management software#order tracking software development
0 notes
Text

Inventory Management Software Development Company - IBR Infotech
As a trusted inventory management software development company, we specialize in delivering high-quality, scalable solutions for businesses across various industries. Our custom-built inventory management software provides advanced features like multi-location management, real-time stock tracking, and integration with e-commerce and ERP platforms. We work closely with our clients to understand their inventory needs and deliver software that simplifies stock control, enhances operational efficiency, and improves decision-making. Our solutions are designed to help businesses reduce errors, cut costs, and boost productivity. Whether you run a retail business, manufacturing unit, or warehouse, we can help you manage your inventory with precision and efficiency. Let us help you build a robust inventory management system that drives growth and profitability.
#newyork#website design#app development#orlando web design#web developing company#inventorymanagement#inventory tracking#inventory management#inventory software#inventory#order management software#mobile app development#management courses
1 note
·
View note
Text
In the span of just weeks, the U.S. government has experienced what may be the most consequential security breach in its history—not through a sophisticated cyberattack or an act of foreign espionage, but through official orders by a billionaire with a poorly defined government role. And the implications for national security are profound.
First, it was reported that people associated with the newly created Department of Government Efficiency (DOGE) had accessed the U.S. Treasury computer system, giving them the ability to collect data on and potentially control the department’s roughly $5.45 trillion in annual federal payments.
Then, we learned that uncleared DOGE personnel had gained access to classified data from the U.S. Agency for International Development, possibly copying it onto their own systems. Next, the Office of Personnel Management��which holds detailed personal data on millions of federal employees, including those with security clearances—was compromised. After that, Medicaid and Medicare records were compromised.
Meanwhile, only partially redacted names of CIA employees were sent over an unclassified email account. DOGE personnel are also reported to be feeding Education Department data into artificial intelligence software, and they have also started working at the Department of Energy.
This story is moving very fast. On Feb. 8, a federal judge blocked the DOGE team from accessing the Treasury Department systems any further. But given that DOGE workers have already copied data and possibly installed and modified software, it’s unclear how this fixes anything.
In any case, breaches of other critical government systems are likely to follow unless federal employees stand firm on the protocols protecting national security.
The systems that DOGE is accessing are not esoteric pieces of our nation’s infrastructure—they are the sinews of government.
For example, the Treasury Department systems contain the technical blueprints for how the federal government moves money, while the Office of Personnel Management (OPM) network contains information on who and what organizations the government employs and contracts with.
What makes this situation unprecedented isn’t just the scope, but also the method of attack. Foreign adversaries typically spend years attempting to penetrate government systems such as these, using stealth to avoid being seen and carefully hiding any tells or tracks. The Chinese government’s 2015 breach of OPM was a significant U.S. security failure, and it illustrated how personnel data could be used to identify intelligence officers and compromise national security.
In this case, external operators with limited experience and minimal oversight are doing their work in plain sight and under massive public scrutiny: gaining the highest levels of administrative access and making changes to the United States’ most sensitive networks, potentially introducing new security vulnerabilities in the process.
But the most alarming aspect isn’t just the access being granted. It’s the systematic dismantling of security measures that would detect and prevent misuse—including standard incident response protocols, auditing, and change-tracking mechanisms—by removing the career officials in charge of those security measures and replacing them with inexperienced operators.
The Treasury’s computer systems have such an impact on national security that they were designed with the same principle that guides nuclear launch protocols: No single person should have unlimited power. Just as launching a nuclear missile requires two separate officers turning their keys simultaneously, making changes to critical financial systems traditionally requires multiple authorized personnel working in concert.
This approach, known as “separation of duties,” isn’t just bureaucratic red tape; it’s a fundamental security principle as old as banking itself. When your local bank processes a large transfer, it requires two different employees to verify the transaction. When a company issues a major financial report, separate teams must review and approve it. These aren’t just formalities—they’re essential safeguards against corruption and error.
These measures have been bypassed or ignored. It’s as if someone found a way to rob Fort Knox by simply declaring that the new official policy is to fire all the guards and allow unescorted visits to the vault.
The implications for national security are staggering. Sen. Ron Wyden said his office had learned that the attackers gained privileges that allow them to modify core programs in Treasury Department computers that verify federal payments, access encrypted keys that secure financial transactions, and alter audit logs that record system changes. Over at OPM, reports indicate that individuals associated with DOGE connected an unauthorized server into the network. They are also reportedly training AI software on all of this sensitive data.
This is much more critical than the initial unauthorized access. These new servers have unknown capabilities and configurations, and there’s no evidence that this new code has gone through any rigorous security testing protocols. The AIs being trained are certainly not secure enough for this kind of data. All are ideal targets for any adversary, foreign or domestic, also seeking access to federal data.
There’s a reason why every modification—hardware or software—to these systems goes through a complex planning process and includes sophisticated access-control mechanisms. The national security crisis is that these systems are now much more vulnerable to dangerous attacks at the same time that the legitimate system administrators trained to protect them have been locked out.
By modifying core systems, the attackers have not only compromised current operations, but have also left behind vulnerabilities that could be exploited in future attacks—giving adversaries such as Russia and China an unprecedented opportunity. These countries have long targeted these systems. And they don’t just want to gather intelligence—they also want to understand how to disrupt these systems in a crisis.
Now, the technical details of how these systems operate, their security protocols, and their vulnerabilities are now potentially exposed to unknown parties without any of the usual safeguards. Instead of having to breach heavily fortified digital walls, these parties can simply walk through doors that are being propped open—and then erase evidence of their actions.
The security implications span three critical areas.
First, system manipulation: External operators can now modify operations while also altering audit trails that would track their changes. Second, data exposure: Beyond accessing personal information and transaction records, these operators can copy entire system architectures and security configurations—in one case, the technical blueprint of the country’s federal payment infrastructure. Third, and most critically, is the issue of system control: These operators can alter core systems and authentication mechanisms while disabling the very tools designed to detect such changes. This is more than modifying operations; it is modifying the infrastructure that those operations use.
To address these vulnerabilities, three immediate steps are essential. First, unauthorized access must be revoked and proper authentication protocols restored. Next, comprehensive system monitoring and change management must be reinstated—which, given the difficulty of cleaning a compromised system, will likely require a complete system reset. Finally, thorough audits must be conducted of all system changes made during this period.
This is beyond politics—this is a matter of national security. Foreign national intelligence organizations will be quick to take advantage of both the chaos and the new insecurities to steal U.S. data and install backdoors to allow for future access.
Each day of continued unrestricted access makes the eventual recovery more difficult and increases the risk of irreversible damage to these critical systems. While the full impact may take time to assess, these steps represent the minimum necessary actions to begin restoring system integrity and security protocols.
Assuming that anyone in the government still cares.
184 notes
·
View notes
Note
After seeing your weatherbugapp reblog i installed duckduckgo and tried it.
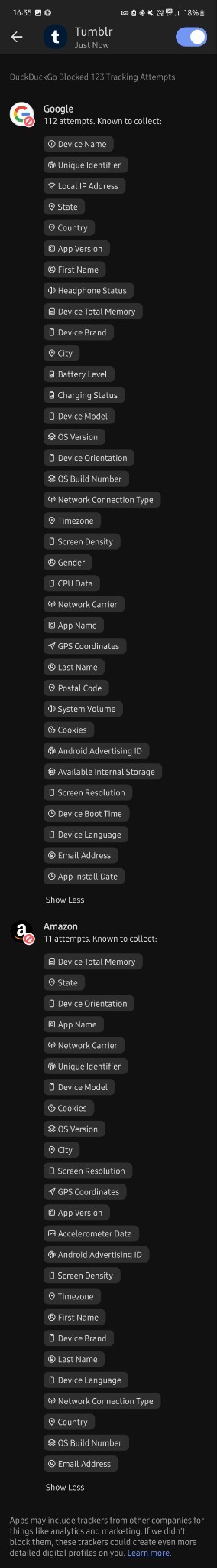
I don't know much about technology tbh but i downloaded this app less than 30 mins ago and in that time google tried to track me 112 times?? And they tried to collect finger prints? And my first and last name? And my gender? And my country, state and city? My gps coordinates? My postal code? My network carrier? My fricking battery level for whatever reason? Can you please tell me if this is normal at all, because i'm freaking out right now. I just turned 18 and started using mobile banking and stuff and this shit scares me
Why tf does it need to know my screen density???my system volume????my charging status????? What tf are they cooking
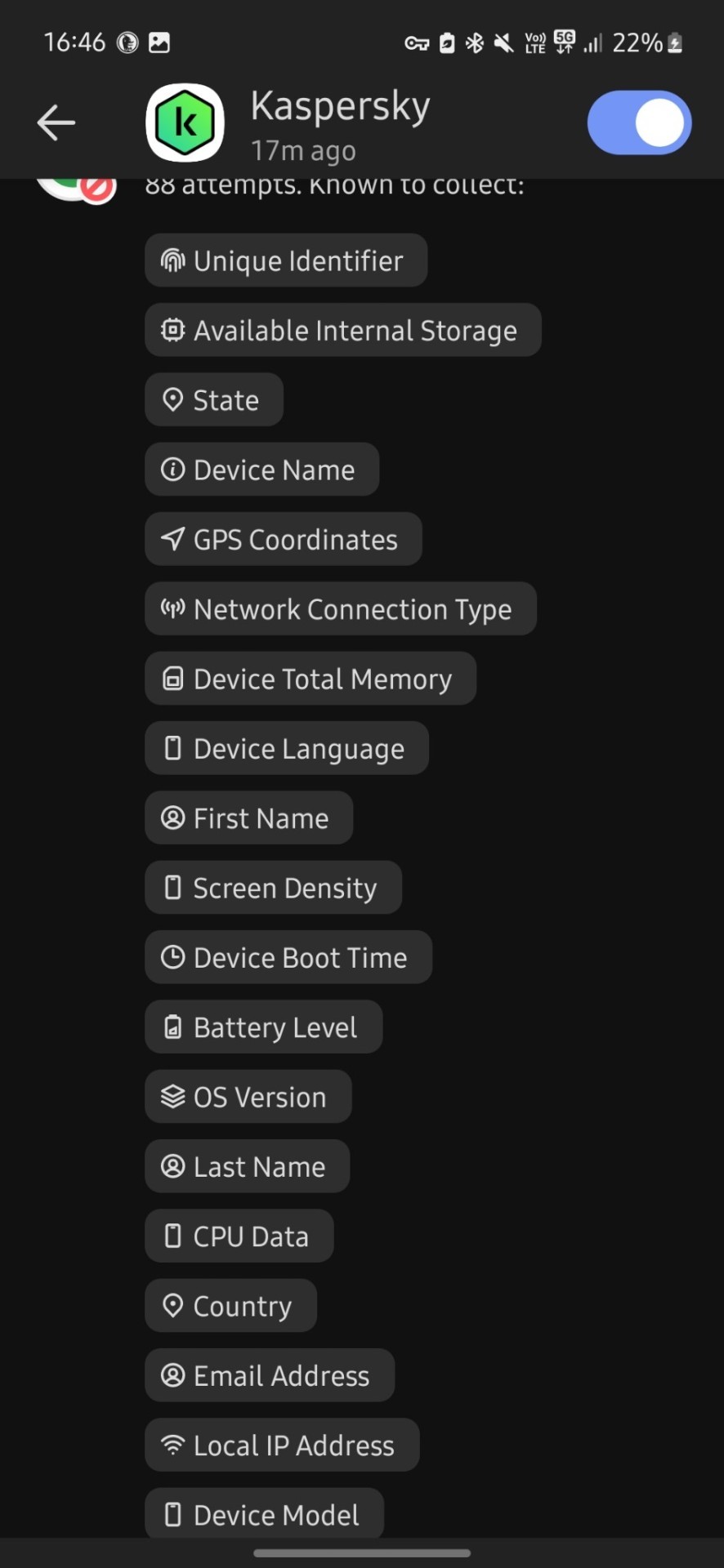
Now it's at 476 tracking attempts bro???? barely 5 mins passed.....
I condensed your three asks into one for readability!
And yeah, I'm very far from an expert about any of this, but as far as I know that's just. Normal. That's the normal amount of spying they're doing on your phone. I assume the numbers we see are to some extent because having been foiled, a lot of these scripts try repeatedly, since I can't imagine what use thousands of trackers per phone would be even to the great aggregators.
Tracking the phone stuff like screen resolution and battery level is because (apart from that definitely not being considered remotely 'private' so it's Free Real Estate) in aggregate that data can be used to track what phone use patterns are like on a demographic scale and therefore. Where the smart money is.
Almost all of this is getting sold in bulk for ad targeting and market analysis. This does presumably make it very hard to notice when like. Actually important stuff is being spied on, which is why I feel better about Having Apps with the duckduckgo app blocker thing.
My bank's app reportedly sells data to a couple aggregators including Google. Not like, my banking info, but it's still so offensive on principle that I avoid using the app unless I have to, and force stop it afterward.
The patterns that show up on the weekly duckduckgo blocker report are interesting. Hoopla attempts about two orders of magnitude more tracking than Libby, which makes sense because they're a commercial streaming service libraries pay by the unit for access, while Libby is a content management software run by a corporation that values its certification as a 'B' company--that is, one invested in the public good that can be trusted. The cleanness of their brand is a great deal of its value, so they have to care about their image and be a little more scrupulous.
Which doesn't mean not being a little bit spyware, because everything is spyware now. Something else I've noticed is that in terms of free game apps, the polished professional stuff is now much more invasive than the random kinda janky thing someone just threw together.
Back in the day you tended to expect the opposite, because spyware was a marginal shifty profit-margin with too narrow a revenue stream to be worth more to an established brand than their reputation, but now that everyone does it there's not a lot of reputation cost and refraining would be sacrificing a potential revenue stream, which is Irresponsible Conduct for a corporation.
While meanwhile 'developing a free game app to put on the game store' is something a person can do for free with the hardware they already have for home use, as a hobby or practice or to put on their coding resume. So while such apps absolutely can be malicious and more dangerous when they are than The Big Brand, they can also be neutral in a way commercial stuff no longer is. Wild world.
But yeah for the most part as far as I can make out, these are just The Commercial Panopticon, operating as intended. It's gross but it probably doesn't indicate anything dangerous on an individual level.
56 notes
·
View notes
Text
Ace Attorney 456 Tokyo Game Show Information Masterpost

Since I haven't seen all the information collected in one place, this post SHOULD be a comprehensive review of everything revealed today - though please let me know if I missed anything important.
New Trailer and Release Date
youtube
We got a new trailer for the 456 collection, which covers (most of) what I'm going to say in this post, and a release date of January 25, 2024!
New Features
Language Support: These games are now available in seven languages: Japanese, English, French, German, Korean, and Traditional and Simplified Chinese, along with voice dubs for each of these. These are some of the first times some of the games (in particular 5 and 6) are officially translated to many of these languages.
DLC: The previously DLC-exclusive cases Turnabout Reclaimed and Turnabout Time Traveler will be added to the game for free, along with previously DLC-exclusive costumes. You can dress up Phoenix in the Tigre outfit from the beginning!
QOL: As well, any of the quality of life features from the Great Ace Attorney Chronicles have been added to the 456 collection. This includes an episode/chapter select unlocked from the start, so you can skip straight to your favorite sections, autoplay and story mode, and a backlog/history to review recent text.
Art Gallery: The game will also include an "art gallery" which includes concept art for the games. This will also include special artworks commissioned exclusively for this collection, some of which are unlocked after beating each game and unlocking each trilogy.
Orchestra Hall: There is also an "orchestra hall" where you can listen to what seems to be the full soundtrack for all three games (though I haven't verified this), along with orchestral tracks from the 15th anniversary and 2019 orchestra concerts.
There are also two new "trilogy exclusive" songs: "Apollo Justice - A New Era Begins! 2024", and "Trucy's Theme - Bring It In, Everyone". The new "a new era begins" remix might possibly be what they're playing in the trailer. "Bring It In, Everyone" is distinct from Trucy's main theme, "Child of Magic" (listed earlier in the soundtrack list), so I have no idea what that one will be like.
Animation Studio: This new feature allows you to play around with character models, setting up different backgrounds and sprites and settings, to create whatever scene you want. This doesn't seem to have a text feature, so it just seems kind of like a worse objection.lol but with 3D sprites. (Although I'm sure the objection.lol people will find a way to rip the models in like... five minutes of the game's release)
Preorder Information
It seems we overseas people will only have the collection available digitally, but Japan seems to have physical copies along with a lot of preorder bonuses! You can find the official page here.

This includes the following:
Game Software: You can order this standalone, or with the other preorder goods, or seemingly just the goods on their own without the software included.
Original Drama CDs: Two new drama CDs are being developed for this collection! As far as I can tell, one involves the Gavinners attempting a one-night-only revival of the band (which goes poorly...), and the second involves Taka fleeing the courtroom.
Evidence and Items Set: This includes ten pieces of evidence available from the games, along with some original illustrations. As can be seen above, this includes things like the photo of Apollo and Clay from Dual Destinies, six ID photos of major characters, and a signed poster of Klavier.

As well, a new sleeve box drawn by Takuro Fuse, the character designer for 5 and 6.

That should cover everything, but please let me know if I missed any news!
388 notes
·
View notes
Note
So how much $ (in general) does it cost to produce a fully animated/rigged, fully voiced 1-3 minute cutscene in a game that’s in ongoing development (something like SWTOR, where they have a lot of prebuilt assets)? Like just a general low range and high range?
I’m seeing a lot of people complaining about prioritizing content they want, and don’t know enough about the behind the scenes costs to properly communicate they’re being unrealistic with their complaints.
The cost of any content in game dev is directly proportional to how much new stuff needs to be created for that content. In order to create a basic conversation cutscene to put into a game, we would need:

A narrative designer to write the script for the cutscene
A cinematic designer to script out the cinematic - which characters speak, in which order, with what timing, in which location, and what other actions they would take over the course of the cutscene
Animations for the characters to play in those positions
A rig for those characters to play those animations
Character models for the characters involved
Voice recordings for the characters to speak
A tool with which to set all of these parameters and organize the cutscene
A game system that can parse the tool data and assets and construct the cutscene from them
A script system to start playing the cutscene when the proper conditions are met
This doesn't include extra stuff like VFX, music, lighting, environments, props, etc. that might need to be created for certain specific cutscenes. In an ongoing game like SWTOR, element numbers 4, 5, 6, 7, 8, and 9 were already built long ago and already exist. As long as the designers can create the characters with the in-game character creator and reuse the existing rigs, no new resources need be expended to create them. If you need a completely new custom character model, that takes time from a character artist and a texture artist. If the character needs to animate differently than everyone else (i.e. needs its own rig), that's time from a rigger to create. If the cutscene needs new animations we need to bring on an animator to spend time building the new animations needed for the cutscene.

Using some napkin math, let's consider costs. We usually use the $10,000 per month figure to pay for a developer (salary, benefits, rent, utilities, software licenses, etc.) or approximately $2,500 per development week per person. Let's assume that each task takes a developer a week to complete.
Write the script (Narrative designer)
Script the cinematic (Cinematic Designer)
Record audio (Sound Designer + Voice Actor + studio time)
Rig one new character (Rigger) x however many new characters
Animate one animation (Animator) x however many new animations
Model one new character (Character Artist + Texture Artist) x however many new characters
Track all tasks and keep everyone on schedule (Production)
Test and validate that the cutscene works (QA)

At the very minimum, we need the script, the cinematic, production, and the QA tester, so a very bare bones cutscene that reuses all assets and has no new VO (say it only reuses the alien language) would cost 4x$2,500 = $10,000. If we add voice recording and keep it to one voice actor (let's say she voices both characters in the cutscene), then the cost jumps to 7x$2,500 = $17,500 because we need the sound designer, the voice actor, and the recording studio time. Adding in two new animations (e.g. one character throwing a punch and the second character reacting to getting punched) would add another two weeks of animator time, raising the cost to 9x$2,500 = $22,500. And so on and so forth. Those costs add up very quickly.

There are ways to get a "bulk" discount of course - we hire voice actors for blocks of four or eight hours, so we can record multiple cutscenes during that session and share some of those costs. We can create one new character and reuse her across multiple cutscenes so that we get more value out of her. Things get cheaper if we reuse stuff more, but they still cost a lot up front. The bulk discounts only really work if the things we're paying for can be reused multiple times though - the more specific an asset is (e.g. a kissing animation), the harder it is to reuse and the more expensive it tends to be relative to other assets.
[Join us on Discord] and/or [Support us on Patreon]
Got a burning question you want answered?
Short questions: Ask a Game Dev on Twitter
Long questions: Ask a Game Dev on Tumblr
Frequent Questions: The FAQ
102 notes
·
View notes
Text
one response I've seen to discussions of privacy settings on the devices and apps we use is "don't complain when these free services are worse because you disabled settings used to improve your experience", and I find the very premise of that argument flawed. my problem is not that these apps collect my data. because yes, data collection can actually be hugely beneficial, as it enables services to be more personalized for your specific needs.
my problem is with the way that my data is used. as it stands, I have to assume that any and all data collected about me is going to be transmitted to a company's servers and used to show me more targeted ads. and that's the best case scenario. I actually have no idea what else they could be using it for, as even with regulations in place, companies break the law all the time. they could be selling it to third parties, or even sharing it with the police or other government authorities.
and there's really no reason that this needs to happen, other than that I live under capitalism and thus every product and service that exists needs to be profitable first and foremost. if this wasn't the case, the developers of this software would have no need to use my data in this way. more often than not, there are ways of collecting my data to improve my user experience that don't involve invading my privacy for the profit motive, and there are even situations where my data doesn't need to be collected at all.
let me give you an example. just a few minutes ago, I opened my weather app to check the temperature outside, and it prompted me to enable precise location tracking in order to continue. there is absolutely no reason why a weather app would need to track my location to begin with. is it useful? sure, it is nice if it can tell me what the weather is like where I currently am without any input from me, but that should be an optional quality of life feature. if I don't want it to do this, which I don't, considering I have no idea who is receiving this data and what they're doing with it, then I should still be able to check the weather by simply inputting the name of the city I'm in.
in the same vein, it's not that I inherently don't want my navigation app to track where I've been in the past. I could think of some cases where that might be useful, such as if I needed proof that I was at a particular place at a particular time. but as it stands, enabling that functionality means google will track my every move, and they can do whatever they want with it, from selling it to the businesses I visited to show me ads, to informing police of my location. if I could be certain that my location data would only be stored locally on my device, and would automatically be deleted after a set amount of time, I might be fine with enabling it.
the problem is that I'm not given the option to maintain my privacy while also benefitting from these services. these apps are designed in such a way that infringing on my privacy is the mandatory default. this is an intentional decision on the part of the companies who develop these apps in order to maximize profitability, and barring you from these services altogether if you disable data collection is designed to frustrate you so that you'll enable it again. under capitalism, you have no rights. you are not respected. so even if it makes things less convenient, I will disable as much data collection as I possibly can.
31 notes
·
View notes
Text
BigProfitPulse.io Reviews Explore the Best Trading Conditions
The online trading world is dynamic and ever-evolving making it crucial to choose a reliable and efficient platform that provides traders with the best opportunities. BigProfitPulse.io reviews showcase why this platform stands out as a leader in the financial industry offering a combination of innovative tools competitive trading conditions and high-speed execution. With a diverse range of financial instruments and a user-friendly interface traders can seamlessly engage in trading without unnecessary hurdles. The ability to access real-time market prices and leverage personalized support ensures that every trader from beginners to professionals can optimize their strategies and achieve financial success.
BigProfitPulse.io Reviews Why Traders Choose Us
Traders are always in search of a platform that not only meets their expectations but also exceeds them. BigProfitPulse.io reviews highlight how this platform consistently delivers top-tier trading services ensuring that every trader has access to the best possible conditions. A major reason why traders trust BigProfitPulse.io is the platform’s commitment to transparency and efficiency. With instant order execution and competitive spreads traders can capitalize on opportunities without worrying about delays or hidden fees. Additionally the platform’s training programs provide users with invaluable insights helping them refine their skills and develop well-informed trading strategies. Whether you are just getting started or already an experienced trader BigProfitPulse.io has the tools and resources to support your journey.
BigProfitPulse.io A Cutting-Edge Trading Platform
One of the most discussed features in BigProfitPulse.io reviews is its cutting-edge trading platform which is designed to cater to traders of all levels. The web-based terminal allows users to analyze financial markets track real-time price movements and execute trades effortlessly from their browsers. There is no need for additional software installations or complicated setup procedures making it easier than ever to engage in global trading. Whether you are trading stocks foreign currencies or precious metals BigProfitPulse.io provides an advanced yet accessible trading environment. The platform is equipped with the latest tools for technical analysis ensuring that traders can make data-driven decisions with confidence.
BigProfitPulse.io Reviews Comprehensive Client Support
A key highlight in BigProfitPulse.io reviews is the comprehensive customer support that ensures traders receive assistance whenever they need it. The platform prides itself on offering professional support services with a team of knowledgeable experts available to answer questions resolve technical issues and provide valuable insights. Whether traders require help navigating the trading terminal understanding market trends or optimizing their trading strategies BigProfitPulse.io’s support team is always ready to assist. This level of commitment to customer service sets the platform apart making it a preferred choice for traders looking for reliability and security.
BigProfitPulse.io Real-Time Liquidity and Instant Execution
Market conditions can change in an instant and traders need a platform that provides real-time liquidity and swift order execution. BigProfitPulse.io reviews emphasize how the platform ensures that trades are processed without delays allowing traders to take advantage of market fluctuations as they happen. The integration of interbank liquidity ensures that users get the best available prices maximizing their profitability. By eliminating execution lags and providing seamless order processing BigProfitPulse.io enhances the overall trading experience giving users a competitive edge in the financial markets.
BigProfitPulse.io Reviews Personalized Training for Traders
Education and continuous learning play a significant role in a trader’s success and BigProfitPulse.io reviews highlight how the platform offers personalized training programs to support users at every stage of their trading journey. Traders are matched with experienced tutors who provide insights into market movements risk management and profitable trading strategies. This hands-on approach helps traders develop confidence and refine their skills ensuring they can navigate financial markets with greater precision. The platform’s commitment to education makes it an ideal choice for both newcomers and seasoned professionals looking to expand their knowledge.
BigProfitPulse.io Reviews Secure and Fast Withdrawals
Security and convenience are top priorities for traders and BigProfitPulse.io reviews confirm that the platform provides a safe and efficient withdrawal process. Users can request fund withdrawals at any time knowing that transactions will be processed swiftly without unnecessary delays. The platform employs advanced security measures to protect user funds and personal data giving traders peace of mind while they focus on their trading activities. Whether traders are actively trading or cashing out their profits they can trust BigProfitPulse.io to handle their transactions smoothly and securely.
BigProfitPulse.io Getting Started is Easy
A major advantage noted in BigProfitPulse.io reviews is the simplicity of getting started on the platform. Registration is quick and straightforward allowing traders to create an account and begin trading within minutes. The low minimum deposit requirement makes it accessible to traders of all backgrounds whether they are testing the waters or fully committing to the trading lifestyle. The platform also provides personalized guidance during the onboarding process ensuring that new traders have all the necessary tools and knowledge to begin their journey with confidence.
BigProfitPulse.io The Advantages of Trading Here
Traders continue to choose BigProfitPulse.io for the numerous advantages it offers. BigProfitPulse.io reviews frequently mention the following key benefits
Competitive spreads and low trading commissions ensuring maximum profitability
Swift and hassle-free processing of withdrawal requests allowing traders to access their funds at any time
Timely updates on significant market events helping traders stay informed and make strategic decisions
Access to global financial markets enabling users to diversify their portfolios and explore multiple investment opportunities
Professional customer support dedicated to resolving issues and providing expert assistance
BigProfitPulse.io Reviews Your Path to Financial Success
Finding the right trading platform is essential for achieving success in the financial markets. BigProfitPulse.io reviews highlight how this platform combines advanced technology expert guidance and superior trading conditions to create an unparalleled trading experience. Whether you are an aspiring trader or a seasoned professional looking for a reliable partner BigProfitPulse.io provides all the tools and resources necessary for success. By choosing BigProfitPulse.io traders gain access to a secure transparent and innovative trading environment that empowers them to reach their financial goals.
6 notes
·
View notes
Text
The sources told +972 and Local Call that since everyone in Gaza had a private house with which they could be associated, the army’s surveillance systems could easily and automatically “link” individuals to family houses. In order to identify the moment operatives enter their houses in real time, various additional automatic softwares have been developed. These programs track thousands of individuals simultaneously, identify when they are at home, and send an automatic alert to the targeting officer, who then marks the house for bombing. One of several of these tracking softwares, revealed here for the first time, is called “Where’s Daddy?” “You put hundreds [of targets] into the system and wait to see who you can kill,” said one source with knowledge of the system. “It’s called broad hunting: you copy-paste from the lists that the target system produces.” Evidence of this policy is also clear from the data: during the first month of the war, more than half of the fatalities — 6,120 people — belonged to 1,340 families, many of which were completely wiped out while inside their homes, according to UN figures. The proportion of entire families bombed in their houses in the current war is much higher than in the 2014 Israeli operation in Gaza (which was previously Israel’s deadliest war on the Strip), further suggesting the prominence of this policy. Another source said that each time the pace of assassinations waned, more targets were added to systems like Where’s Daddy? to locate individuals that entered their homes and could therefore be bombed. He said that the decision of who to put into the tracking systems could be made by relatively low-ranking officers in the military hierarchy. “One day, totally of my own accord, I added something like 1,200 new targets to the [tracking] system, because the number of attacks [we were conducting] decreased,” the source said. “That made sense to me. In retrospect, it seems like a serious decision I made. And such decisions were not made at high levels.” The sources said that in the first two weeks of the war, “several thousand” targets were initially inputted into locating programs like Where’s Daddy?. These included all the members of Hamas’ elite special forces unit the Nukhba, all of Hamas’ anti-tank operatives, and anyone who entered Israel on October 7. But before long, the kill list was drastically expanded. “In the end it was everyone [marked by Lavender],” one source explained. “Tens of thousands. This happened a few weeks later, when the [Israeli] brigades entered Gaza, and there were already fewer uninvolved people [i.e. civilians] in the northern areas.” According to this source, even some minors were marked by Lavender as targets for bombing. “Normally, operatives are over the age of 17, but that was not a condition.”
26 notes
·
View notes
Text
Birdie (one)
This is an original work I wrote back in 2022 before I got into Call of Duty. Birdie is a former corporate software developer now living in a megabuilding inspired by the ones we see in the video game Cyberpunk 2077. This world is in transition, not quite post-corporate but on its way there. This is a story about Birdie falling into bed with the couple who moves in next door, and learning to trust other people again after enduring enormous personal betrayal. - cw: implications of stalking.

Birdie woke late in the morning to sunlight peeking through the cracks of her blinds and the smell of coffee gently percolating over in the kitchenette. It was a cool morning, silvery, the kind one wanted to luxuriate in and pretend noon would never come. Except—
Ping…ping…ping…
The soft chiming of her front door’s proximity alert was out of place.
She blinked groggily, swimming her legs through the tangle of blanket and sheets that she’d made a nest of in the night, and inchwormed her way to the edge of the mattress.
Half the pile slithered off the bed to puddle on the floor as her feet met the cool tile, which was spotless thanks to the vacuum-bot that had done its work during the night. She took a thin, reclaimed-fiber robe off its hook on the thin sliver of wall between the window and bed, and wrapped it around herself as she plodded, still half-asleep, in the direction of the chime.
Ping…ping…ping…
Birdie usually didn’t bring up her internal heads-up display until after her coffee, but the chime couldn’t be turned off without it. Safer that way—no one could tamper with it if they were of a mind to without hardwiring directly into her neural software. She flicked her index fingers upward in synchrony, and the translucent home screen slid in across her vision.
It was a simple interface—UI elements in soft white with simple drop shadows to contrast them against the real world they overlaid. Birdie could access the intranet, check her mail, keep track of her finances, and monitor her daily task lists as work orders came in; things people used to do on tablets or laptops, before integrated hard- and software became standard in the corporate era.
Ping…ping…ping…
No one was at the door—Birdie had set separate chimes for packages versus people. So she angled the bell camera downwards, seeking the parcel she expected to see—and scowled the moment she saw what it was.
Ping…ping…ping…
With an angry gesture she shut off the alert, with another opened the door, but no gesture in her software was going to make the big, sparkling crystal vase, stuffed to the gills with bright red roses, suddenly grow legs and run away.
A pink envelope was filed between two of the fattest blooms. Birdie bent at the waist, indignation traveling down her brain stem and hijacking her nerve endings, and plucked it from the bouquet. With one fingernail she broke the seal—real paper! Dyed paper! The audacity!—and as if disarming a bomb, she removed the folded stationery from within.
The ivory white, virgin sheet had obviously been recently manufactured, not pressed and cut from reclaimed pulp like any reasonable person would use these days. And, to add insult to injury, there was only one—one!—line of handwriting in the very middle.
I’m sorry, Margie. I still love you.
full chapter on Patreon
6 notes
·
View notes
Text
youtube
A new scientific paper has been published in the research journal Frontiers in Remote Sensing titled ‘Automatic detection of unidentified fish sounds: a comparison of traditional deep learning with machine learning” authored by Xavier Mouy et al, which analyzed week-long hydrophone recordings of the Coral City Camera site at PortMiami in order to detect fish sounds.
The researchers found that using a Convolutional Neural Network (CNN) enabled detection of fish sounds that both human analysts and traditional spectrogram data analysis otherwise could not detect. The CNN was trained using hydrophone recordings made in British Columbia, but proved accurate in the novel environment at PortMiami, even despite significant background noises from boats. The software developed for this study is open-source and available to other researchers.
Stay tuned in the coming months as we prepare to connect a hydrophone to the Coral City Camera and provide an audio channel to the YouTube livestream. If possible, we aim to incorporate real-time analysis of the underwater sounds to help monitor and track fish activity.
Click to read ‘Automatic detection of unidentified fish sounds: a comparison of traditional deep learning with machine learning'.
8 notes
·
View notes
Text
Over the past couple of decades, a number of US government officials have left their roles for lucrative jobs at tech companies. Plenty of tech executives have also departed to take leadership positions inside federal agencies. But four experts who track the federal workforce tell WIRED they were stunned last week by a development unlike any other they could recall: The Department of Treasury internally announced that Tom Krause had been appointed its fiscal assistant secretary, but that he would simultaneously continue his job as CEO of the company Cloud Software Group.
Krause is now in charge of both a sensitive government payment system and a company that has millions of dollars’ worth of active contracts with various federal agencies through distribution partners, according to a WIRED review of searchable spending records. The Department of Treasury alone accounts for a dozen ongoing contracts tied to Krause’s company that are together valued between $7.3 million to $11.8 million. These include licenses for the data visualization tool ibi WebFocus and purchases of systems called Citrix NetScaler that help manage traffic to apps. (Some publicly posted procurement records do not break out contract details, so actual figures may be even higher.)
Critics have expressed concern about the alleged conflicts of interest posed by Krause’s decision to keep his role in the private sector. Cloud Software could benefit from extending its federal contracts or securing additional ones, though there is no public evidence that Krause has done anything improper with his dual roles. Existing federal regulations also bar actual and apparent unjust favoritism in contracting. “Public trust in those safeguards is nonnegotiable,” says Scott Amey, general counsel at the Project on Government Oversight, a nonpartisan watchdog group.
As Krause moves forward with two jobs, he could have to potentially navigate not only contracting conflicts, but also dueling crises. “What would happen if a Citrix emergency emerges at the same time as Treasury obligations?” says Jeff Hauser, founder and executive director of the Revolving Door Project, which researches federal appointees. “Generally, the thicket of restrictions on full-time employees would make a CEO role impossible in an administration which took adherence to ethics laws seriously.”
Krause, the Treasury Department, and Cloud Software didn’t respond to requests for comment. Cloud Software investors also didn’t respond to a request for comment.
The Treasury Department has told Congress that Krause is a “special government employee”—a type of temporary role—that is supposed to be held to “the same ethical standards of privacy, confidentiality, conflicts of interest assessment, and professionalism of other government employees.” In a foreword to a code of conduct policy posted on Cloud Software’s website, Krause states, “Cloud Software Group is committed to ensuring that its business is conducted ethically, in compliance with the law, and according to its values of integrity, honesty and respect.”
Krause is among a group of several dozen veteran tech executives, mid-level tech operations managers, and fresh-out-of-school software coders who have been recently installed across a series of federal agencies under the auspices of the self-styled Department of Government Efficiency. DOGE’s authority is being challenged by some Democratic state attorneys general. In the meantime, its representatives have been carrying out an order from President Donald Trump to cut costs and modernize technology across the government.
There is some precedent for corporate executives to simultaneously work in the US government. When the US was at war in the early 1900s, the federal government recruited business leaders to fill key posts. They retained their private sector jobs and wages; the government pitched in a $1 annual salary to the executives who became known as “dollar-a-year men.” Congress later raised concerns that some of them had engaged in self-dealing.
Since then, other executives have continued to retain their jobs as they serve on government boards and commissions, typically in a part-time capacity. But maintaining a day-to-day operational role in both the federal government and at a corporation is now virtually unheard of, says David E. Lewis, a political scientist who wrote a book on appointed government bureaucrats. “Most persons in regular executive positions divest themselves of private interests before government service,” he says.
Trump, according to his company, has handed management of his businesses, including hotels and golf courses, to his children for the duration of his presidency (though he reportedly still takes meetings that have raised questions among ethics experts). Musk, who is CEO of Tesla and SpaceX and has oversight of four other companies, including X and Neuralink, has been a vocal figure in DOGE’s operations, but the White House has said he’s not actually in charge—without specifying who is leading the project. Some of the other individuals associated with DOGE are otherwise unemployed, have taken leave, or maintain dual roles but at lower levels than chief executive.
Krause is the only Trump administration official identified so far as being a CEO and a day-to-day decisionmaker inside one particular agency. After years of working as an executive at chip companies, Krause joined Florida-based Cloud Software Group in 2022. The company was created that year as part of a private-equity-backed acquisition of Citrix, followed by a merger with Tibco, another tech company. At the time, Citrix was saddled with an extensive amount of debt and generating essentially stagnant revenues, and while Tibco had not recently publicly disclosed its finances, analysts had considered the company’s outlook to be “negative.”
The US government, including state and local agencies, is expected to spend $287 billion on technology this year, or about 14 percent of overall US tech spending, according to Forrester, a research and advisory company. Whether DOGE’s efforts to boost the quality and efficiency of federal IT systems will lead that spending to increase or decrease isn’t clear. So far, DOGE has both tried to purchase emerging technologies and moved to cancel some existing contracts. But Krause’s inside access could potentially provide an advantage to Cloud Software at a pivotal moment for the company.
Over the past couple of years, Cloud Software has laid off thousands of people and faced accusations that it potentially became lax with cybersecurity. Cloud Software’s most well-known offering, Citrix, enables groups of workers to access data and run apps that are located on a remote machine. But increasing adoption of tools that can operate on any device has chipped away at some of Citrix’s dominance, according to Will McKeon-White, senior analyst for infrastructure and operations at Forrester. There are other options now, he says, including from Microsoft and smaller companies such as Island.
Cloud Software’s Tibco program, which helps workers automate tasks such as adding a new user to multiple internal databases, is often mentioned in the wrong sort of conversations these days, according to David Mooter, a Forrester principal analyst. “They tend to come up more when somebody wants to abandon them,” he says.
That said, some Cloud Software services are more affordable than alternatives for governments, and they also are better suited for the older infrastructure used by some agencies. Last year appears to have been one of Citrix’s best in a long time financially, says Shannon Kalvar, a research director for enterprise systems management and other areas at IDC. One reason for the upswing is that Citrix has put more emphasis on catering to the feature demands of its largest customers, including governments.
13 notes
·
View notes
Text
“If technocracy wins this battle and they implement it on a global basis, it will again take hundreds of years before the concept of freedom and liberty will resurface again. It will take a very long time; it won’t just come snapping back, it will not be a fade. Once they get control over the economic mechanism, they will virtually have control over life itself. They will make people of the world dance like puppets on a string.” ⁃ Patrick Wood, TN Editor.
This is a very important question. I think about it daily as the meteoric rise of scientism creates a new materialistic priest class, in whom you must put your faith and devotion.
What is Technocracy?
A scientific dictatorship, enabled by full-scale surveillance, in which an elite class of scientists and engineers manages every facet of life. Technocrats are “persons who exercise power by virtue of their technical knowledge.”
Technocracy is the Brave New World in Aldous Huxley’s 1932 novel, which was more a “I just got out of a meeting and here’s how it’s going down,” memo rather than a cautionary tale.
In this presentation about COVID-19, Dr. Lee Merritt, influenced by Patrick Wood’s writings on technocracy, shared the etymology:
Techn = skillKrat = kratos (divine personification of power)
She summed up technocracy: Data gathered on everybody in the world and fed to un-elected officials, who are smarter than everybody, and will use the information to create amazing solutions. It boils down to “power via differential knowledge,” meaning if you have knowledge that only a select few have, you can lord it over the majority of people.
The Internet and Total Surveillance
Once the possibility of a total surveillance state materialized with the inception of the Internet, technocracy became the crown jewel in the Cabal’s totalitarian New World Order agenda.
The timeline is speeding up. Their dreams of ruling the world are veering toward a terrifying reality with artificial intelligence, propaganda in everybody’s pocket, and a bazillion data points on every man, woman, and child on Earth.
Patrick Wood, the OG of technocracy research, said once we reach a scientific dictatorship society … “liberty will be a historic curiosity.”
In order to achieve this goal, the technocrats developed mass surveillance, which has only been possible in the modern age with the Internet. This is their time to act.
Smart meters on houses monitor how much energy you consume.
Credit card transactions track consumer behavior and move people away from hard currency.
Social media fills out the dossier with beliefs, names of friends and family, images, and much more.
The Affordable Care Act digitizes your medical history.
Smart gadgets—Fitbit, Oura Ring, etc.—pass all of your vital stats to central repositories.
Smartphones track where you are, what you’re doing (they can listen in), and what information you’re consuming and entertainment you are consuming.
The Internet of Things (IoT) adds more daily data. What’s in your fridge? What do you watch on TV? And even more nefarious, there are credible reports detailing how they can watch us through our TVs.
Facial recognition software and cameras monitor every square inch of public space.
Virtual assistants like Alexa monitor your every word and train people to be useless (“please machine, turn on that light … I cannot do it myself”).
Public school jams cultural Marxism down the throat of every child, while Common Core collects 400 pieces of data on every child, which is on their record for life.
5 notes
·
View notes
Text
Week 1: Introduction to Software Design and Engineering
January 13-17, 2025
This week marked the start of our Software Design and Engineering course. Our first session was on Monday, where our instructor introduced the course, outlining expectations and objectives for the semester. Afterward, we were divided into teams, and I chose to collaborate with my former classmates. Our first task was to brainstorm project ideas that leverage technology to solve real-world problems while also having business potential.
Exploring Project Ideas
One of our initial ideas was an Order Queueing Web App for internet cafes. We recognized a common issue—gamers often need to pause their game to place food orders, which can be disruptive for them and inefficient for the staff. Our proposed solution was a web app that allows customers to browse the menu and place orders directly from their gaming stations, with real-time notifications sent to the cashier to ensure a seamless experience.
We also considered a Job Hunting Website, but we soon realized that its broad scope would be difficult to manage within our timeframe. After further discussion, we pivoted to a more practical option: a Smart Inventory Management System for Small Businesses. This system would enable businesses to monitor inventory in real time, receive alerts for low stock, generate sales analytics, and automate reports—effectively addressing common challenges like overstocking, shortages, and inefficient tracking.
------------------------------------------------------------------------------
To better understand user needs, we conducted interviews with potential users. We visited Virtual Grounds, an internet cafe, to observe how customers and staff handled food orders. Additionally, we stopped by Minute Burger, a burger shop, to learn about inventory management challenges. These interviews provided us with valuable insights and helped refine our proposed solutions.
During class, we presented both project ideas. After discussing their feasibility and impact, we officially decided to move forward with the Smart Inventory Management System as our final project. It stood out as a more practical and scalable solution, with a clear market need and strong alignment with our course objectives.
With the first week behind us, we’re eager to dive into the planning and development phase. Excited for what’s next!




2 notes
·
View notes
Text
The Parts for a Clock: Analog or Digital?

The parts for a clock comprise what one might anticipate, specifically, dial, clock hands, and movement (motor), plus possibly numerous devices. These clock parts nowadays run online, rather than mechanically, meaning generally that the activity is developed around a quartz crystal and powered electrically. But an additional difference can be drawn, that between analog and digital discussion.
Parts for an analog clock that show time are the well-known hour and min hands revolving clockwise while superimposed above a printed dial. Their digital equivalents employ 7-segment numerical displays, which are carried out using LEDs, and thus combine hands and dial right into a unified presentation. In this post we discover the comparison in between these sorts of parts.
For example, to order analog dials, one must learn a number of choices. The numerals on the face may be Arabic or Roman-- or, possibly, simply place-holder icons-- and numerous alternatives are given for the background color of the dial. There are fewer shade options for hands, though a considerable variety of design options.
The typical clock movements were analog just and made up a host of analog parts. The potential power of a hanging weight or coiled spring was exchanged kinetic energy forcibly a flywheel to rotate, and a pendulum-escapement combo gave timing guideline. Gears networked with each other computed proper proportions for positioning each hand.
The modern-day motion is digital, with a reverberating quartz crystal providing power using vibrating pulses. Community of pulse matters (in software) returns timing details for tracking secs, mins, and hours. Nonetheless, display screen of this information can be done electronically or in analog.
To an informal viewer, making use of analog parts managed by a digital motion actually looks no various than the old mechanical clocks (except that it may not be as cumbersome). However the 7-segment screen quickly signifies the use of digital parts.
The two modes of operation can vary in terms of timing precision. The Swiss are recognized for generating clocks with very precise precision making use of the conventional (analog) mechanical movements, though these gadgets were detailed and complicated, and the cost got on the high side. The digital mode involves quartz crystals that have exact regularities, yet subdividing down to the minutes/seconds range can shed some precision; also, quantizing noise tends to sneak in to restrict electronic motion accuracy.
In picking clock parts in today's globe, one starts with the screen, which is either the conventional analog dial and hands, or the digital 7-segment alternative. For the last, choose an activity created to deal with it; after that choose various devices offered, such as radio, alarm clock, automatic changes for daylight savings adjustments, or novelty noises. You fit to be given a choice in between a 12-hour cycle and 24-hour one, along with various ways to show month, day, and year.
If, on the other hand, the need is for the standard tableau of revolving hands placed over a dial, one orders the parts (hands, dial, and movement) independently of each other. (It is likewise possible to order a set or insert, saving some labor and decision-making but giving up complete stylistic control.) The set of choices is rather wide, not just in regards to design and dimension, but additionally in regards to special uniqueness and increased attribute sets.
For example, analog movements use a means to track altering tide level. The novelty of playing chimes on the hour or quarter-hour gives one a choice of popular songs or even of composing your very own. Cosmetic (not really contributing to timekeeping) pendulums and various other novelty parts supply nostalgia and charm.
The reader is encouraged to explore vendors' sites to see the variety of choices to clockmakers. Whether one delights in constructing things from scratch or would certainly favor to accelerate the process with inserts or kits, this occupation or thing can be enjoyable and fulfilling. Answer for on your own the inquiry of whether the parts for your clock must be analog or digital.
youtube
2 notes
·
View notes
Text
Bitcoin AI Diamox - Can Transform Your Trading Experience? User Reviews!

A new cryptocurrency trading program called Bitcoin Ai Diamox has generated a lot of interest since it was released. It is said that the method makes trading easier and allows orders to be executed conveniently. According to the software's developers, it helps traders of all experience levels make wiser choices and increase their profits. As is well known, software is crucial to delivering a smooth and profitable trading experience.
Open Your Bitcoin Ai Diamox Account Now
Traders search for an affordable system that provides a safe environment. Today, there are countless trading sites. It is challenging to determine which is authentic, though. We will look at every aspect of this new trading program in this review of Bitcoin Ai Diamox. Above all, we'll examine its operation, cost, and potential profit margin. We'll also look into user ratings and reviews to find out what industry experts think of this platform.
Bitcoin Ai Diamox: What Is It?
An AI-based cryptocurrency trading tool called Bitcoin Ai Diamox was created to assist users—both novices and experts—in navigating the erratic cryptocurrency market. It provides customers with actionable insights to help them make well-informed trading decisions by using state-of-the-art artificial intelligence to monitor market patterns in real-time.
Bitcoin Ai Diamox places a strong emphasis on automation and user-friendliness in contrast to conventional trading platforms. By calculating figures and deciphering intricate market data, the software essentially serves as your personal trading assistant, saving you the trouble. Bitcoin Ai Diamox Reviews something for everyone, regardless of expertise level, from novices wishing to dabble in cryptocurrency to seasoned traders seeking efficiency.
Is Bitcoin Ai Diamox A Scam?
The elephant in the room needs to be addressed: Is Diamox a Bitcoin AI legitimate? My investigation suggests that the platform is authentic. Positive customer evaluations, clear terms, and actual trading tools are all provided. Nevertheless, you should use prudence and only invest money you can afford to lose, just like you would with any trading site.
How Does Bitcoin Ai Diamox Work?
Bitcoin Ai Diamox is a comprehensive trading environment that continuously tracks the markets for virtual currencies. Consider a trading assistant who is always on the lookout for price changes and other minor market signals that could otherwise go overlooked. This reliable system develops custom trading strategies based on its analysis.
Start Trading with Bitcoin Ai Diamox Today
Its capacity to streamline the trade process is its main benefit. Before moving smoothly into live trading, users can begin with the demo mode to build confidence. Once activated, Bitcoin Ai Diamox takes over, handling your investments and making trades in response to changes in the market. Importantly, it works within the parameters you specify, so no matter how active you are on the site, you still have complete control over your trade.
How Can I Create An Account on Bitcoin Diamox Ai?
To begin trading, traders first create an account on Bitcoin Ai Diamox. The process is really easy and takes only a few minutes to finish. The process of creating an account on Bitcoin Ai Diamox will be examined in this section.
First Step
Registering on this site is the first step. To complete the registration form, go to the official Bitcoin Ai Diamox website. You should include information like your name, phone number, email address, and nation of residence. Once the necessary information has been entered, submit the form.
Step Two
The Bitcoin Ai Diamox staff will check the information once you submit the registration form. The team will send a confirmation email to the specified email address after all the information has been verified. To finish this process, simply open the mail and follow the directions.
Step Three
You can access your Bitcoin Ai Diamox Platform account after the verification process is finished. To start trading on the platform, you must deposit a minimum of $250. There are numerous ways to pay, including bank transfers, credit cards, PayPal, Neteller, and Skrill.
Step Four
Following the completion of all the above procedures, you can begin trading. Additionally, you should choose the assets to trade and establish the parameters of the trade in accordance with your investing objectives. Depending on your preferences, you can select between the auto and manual modes.
Top Features of Bitcoin AI Diamox:
Real-Time Market Analysis
Real-time market data analysis by the platform's AI gives users the most recent information. This functionality is very useful in the rapidly evolving cryptocurrency industry.
Accessibility on the Go
Even if there isn't an app, you can trade whenever and wherever you want because to the platform's mobile-friendly design.
Personalized Alerts
To ensure you don't miss any opportunities, set up customized alerts for particular market circumstances.
Easy-to-use Interface
Even novices may easily browse the platform thanks to Bitcoin Ai Diamox's clear and user-friendly design.
Trading in Multiple Assets
Ethereum, Litecoin, and other cryptocurrencies are supported by the platform in addition to Bitcoin.
Open Your Bitcoin Ai Diamox Account Now
What Is The Bitcoin Ai Diamox Minimum Deposit Requirement?
In order to begin trading, Bitcoin Ai Diamox App usually requires an initial deposit. For the most up-to-date and correct information, it is preferable to consult the site directly as the amount may differ according on the account type chosen. Although some novices view this deposit as a barrier, it also guarantees that users are sincere about their trading promises. A responsible trade environment is maintained by cautious and secure funding.
Bitcoin Ai Diamox: User Reviews and Ratings
Both seasoned and new traders from all around the world have left excellent reviews for Bitcoin Ai Diamox. After using this strategy for five to six weeks, many traders claimed to have profited ten times their initial investment. The technology offers a seamless and effective trading experience while in auto mode.
Beginners could use the free demo mode to familiarize themselves with various tactics and discover new strategies. Profitable chances could be explored and invested in by seasoned traders. With this approach, they could effectively manage all of their investments. Bitcoin Ai Diamox has a 4.5 out of 5 star rating on review websites such as SiteJabber.
Final Verdict
We have reached the last section of this evaluation of Bitcoin Ai Diamox Crypto Trading Platform after a thorough investigation. Here, we examined every function and facet of this brand-new trading program. As previously said, it makes use of cutting-edge technologies like as artificial intelligence (AI), algorithms, and analytics to deliver precise market analysis and support traders in making wise choices. This system has both auto and manual trading modes. Traders can experience trading hands-free when using auto mode.
Start Trading with Bitcoin Ai Diamox Today
When traders choose to put strategies into practice on their own, they can switch to manual mode. Trading requires a minimum of $250 in funds. By adhering to all safety procedures and utilizing technology like SSL and two-factor authentication, Bitcoin Ai Diamox provides a safe trading environment. Users gave this new software positive reviews, giving it an average rating of 4.5 out of 5. We can conclude that Bitcoin Ai Diamox is a worthwhile investment after taking into account all of these considerations.
FAQs
Is it possible to use Diamox for Bitcoin AI on a mobile device?
Of course. No matter where you are, you can manage your transactions and stay updated thanks to the platform's complete mobile optimization.
Can beginners use Bitcoin Ai Diamox?
It is, indeed. The platform's user-friendly controls and step-by-step instructions make it suitable for both novice and seasoned traders.
How safe is it to trade on Bitcoin Ai Diamox?
To protect your assets, Bitcoin Ai Diamox uses cutting-edge security methods like encrypted data transfers and thorough customer verification procedures.
Which cryptocurrency kinds are available for trading on Bitcoin Ai Diamox?
The platform's main currency is Bitcoin, but you may trade a number of other cryptocurrencies as well. You may diversify and modify your investment approach to suit the ever-changing market thanks to this variety.
Official Website ==> https://www.blockxtrade.com/bitcoin-ai-diamox-reviews/
2 notes
·
View notes