#row deletion in lighting component
Explore tagged Tumblr posts
Text
2024 Abu Dhabi: Q3 (The Big One)
The big news of last session is Charles Leclerc being out in Q2 due to a deleted time for track limits. A shame for Ferrari and their WCC dreams, as this will make it infinitely more difficult (almost impossible. This plus Leclerc's 10 place grid penalty means he will start straight in the back. If I was them, I would start from pit lane and take on fresh components to give Leclerc that chance to crawl through the field. They literally have nothing to lose.
In good news, Valtteri Bottas has made it into Q3, which is absolutely fantastic for the driver. This creates at least some hope about the Finnish driver getting points in his last F1 race (as far as we know)
For pole today, I feel like it will either be Verstappen or a McLaren. However, Sainz could sneak his way through, as the Ferrari pace seems relatively decent this weekend.
Green light.
Hulkenberg jumps to the top, Verstappen takes it away, P{erez goes to third, Russell behind him. Sainz slots into 2nd when he finisges his lap. Alonso jumps ahead of Perez and Russell, and Gasly goes ahead of him.
McLaren's go, Piastri slots in behind Verstappen, and Norris jumps ahead of him. Piastri's time is deleted which slide Sainz into 3rd. It seems like no one can really match Verstappen today, who literally almost lost it right at the end but somehow still got the fastest lap.
5 minutes left.
Neither Bottas or Piastri have set times yet, so they will be hoping to crawl up higher (especially Piastri). But Piastri's time is reinstated, and is back up to 3rd. less pressure then for him.
Everyone will go one more time. Let's see how this goes.
Perez starts flying and is improving his time. He jumps to 4th position. With Sainz behind him and the midfielders doing well, he could lose that though. This is true, as Bottas jumps ahead of him.
Piastri on flying, seems to be driving a little more carefully which could sacrifice time.
Wowza, Hulkenberg jumps up to take provisional pole position. Piastri takes it away, Sainz goes to 3rd, Norris goes up to pole, and Verstappen on flying and only stays in 5th (seems like his pace dropped a bit). Russel goes 7th.
Hulkenberg has officially gotten his best starting position in years. Good for him!
So it is a McLaren front row lockout, which means they essentially have one hand on the WCC trophy.
Alright, I will see you tomorrow for the race.
Starting Positions (after Williams 5 place grid for both and Leclerc 10 place penalties):
Norris
Piastri
Sainz
Hulkenberg
Verstappen
Gasly
Russell
Alonso
Bottas
Perez
Tsunoda
Lawson
Stroll
Magnussen
Zhou
Hamilton
Doohan
Albon
Colapinto
Leclerc
Cheers,
-B
5 notes
·
View notes
Text
Brick Breaker
Project Set-up
when setting up my project I chose a blank project.

while doing this all I had to do was create a new level for the actual game to take place, while in my new level I added the essentials using env light mixer, such as lighting and editing them to the iconic ping pong look (I soon deleted many of the lighting items as I did not need them) and making the materials for each asset.
creating the bat.
to create the bat I made a player pawn blue print and adding a scene component BatAnchor(we will attach all the moving parts to this) then we will add a collision capsule, a arrow and a static mesh attached to the anchor. after setting up the collision for the capsule and the static mesh along with the mesh used in the static mesh while repositioning it slightly.
after this I added a camera and a spline outside of the anchor and adjust the transform these.
Adding movement.
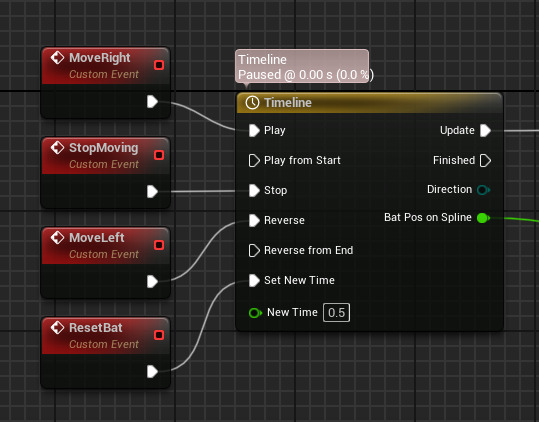
inside the event graph for the bat I used a timeline to control the location along the spline left to right.
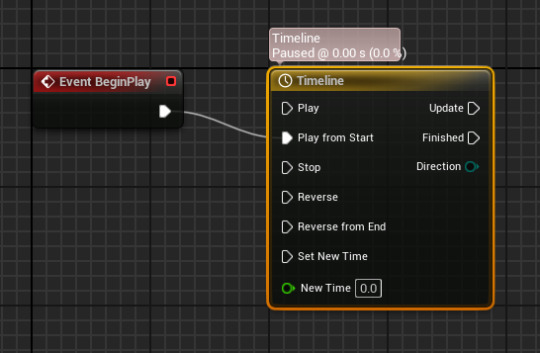
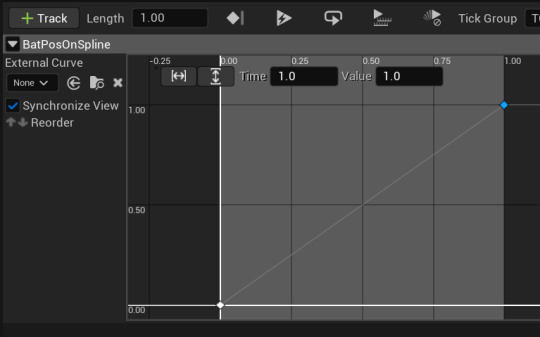
then I set up the code like this.

Input setup.
after creating a folder for my inputs I made a new input action for the movement of the bat.
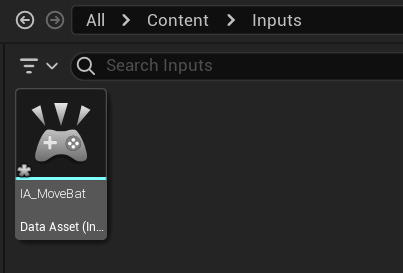
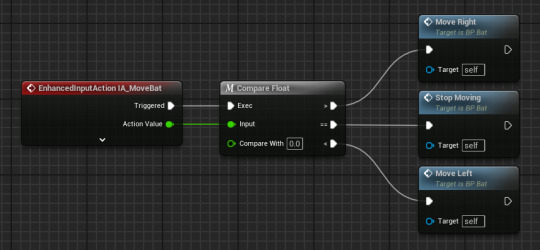
all you need to do is change the value type to axis1d (float)
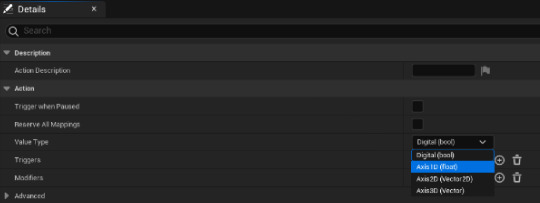
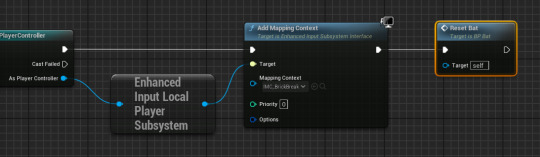
then I make another for the launch of the ball. then I created a input mapping context for the binds and bind the launch to right mouse button and the movement to mouse X. and back on the event graph I set it up so it can receive input.
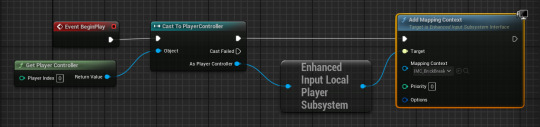
then I made some custom events to receive mouse input and connect them to a timeline.
I am using custom events because we are going to use some logic to adjust the sensitivity of the mouse and this will make that easier to achieve.
The easiest one you can code is the reset ball where all you have to make this chunk of code on the event begin play row.
for the actual movement of the bat all you need to do is make this piece of code.
near to the end of this I dropped down the event node and plugged stop moving into completed this fixes an issue with the drag that I had.
next I add 2 new float variables for the sensitivity and move rate then you get the mouse sense and multiply it by the move rate in-between the nodes we made earlier.
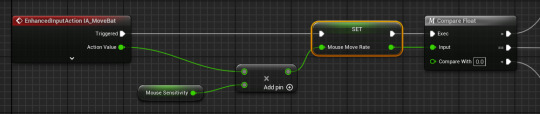
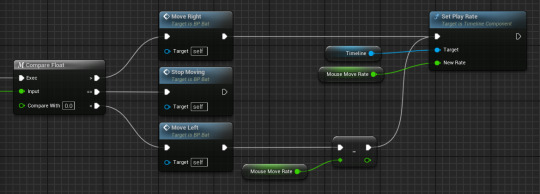
then after this you need to get a reference to the timeline and put it into a set play rate with mouse move rate as the new rate.

this only works with the move right, for the move left I need to get a negate node so it will go in the opposite direction.
The Ball.
before making the ball I made a simple arena with simple blocks with their own glowing materials.
0 notes
Text
How to delete multiple rows using selection box in Lightning Component?
Prerequisite: Certification learning and training course do not presume or require any prior knowledge or prerequisites. However, basic knowledge of salesforce concepts and a basic understanding of Lightning Component and Apex Programming.
Today we are going to learn how to DELETE multiple rows using the selection box in Lightning Component? Multiple rows deletion help the user to delete desired rows on a single click Button. Moreover, the user can delete multiple rows on any page. This type of functionalities used in online Ticketing booking systems such as an Online bus booking system, Railway booking, Air flight, and Hotel bookings e.t.c. whereas the user has to fill the details of multiple persons. In BISP we are best to deliver online training on any technology. Our trainers share their years of consulting experience in training. We strive to develop and deliver highly qualified IT consultants to the market. We are known for our high-quality education services at low cost, using various productive methodologies to deliver online training to candidates and learners. We would like to draw your kind attention to experienced, real-time, exploring engagement practices and assignments for our candidates who would like to take part in BISP online professional courses i.e. Salesforce online training, Data visualization tools like Tableau, Qlikview, QlikSense, Cloud-like Amazon web service. Oracle courses like Weblogic, EDMCS, Data relationship management, ERP like PeopleSoft technical, Functional, and Administration.
#bisp trainings#row deletion in lighting component#bulk row deletion in lightning#salesforce online training#online training salesforce
0 notes
Text
Repair MacBook
Repair MacBook This should be your last resort of choice unless the manufacturer recommends it. Laptop keys are a bit more delicate and difficult to replace. The spacebar and the enter key can have separate brackets underneath, which must be installed along with a new key. Consider hiring a professional to clean your laptop. A professional technician can disassemble your laptop, find damaged parts and safely clean electronic components. Nevertheless, you would probably buy it again - just because of the good touch and feel. Even if you do a messed up layout for it. This Business-Logitech is also not the quietest keyboard, but in contrast to scissor technology keyboards, there is no bright picking, so the background noise is roughly comparable. Typing on the K280e sounds more subdued, but is clearly audible. I have a similar problem. I ran a little apple spritzer over my MacBook Pro. It went on as normal and I could even restart it. In terms of price-performance ratio, this model is definitely very well positioned. Another special feature of the completely black STOGA gaming keyboard is its almost borderless design. By dispensing with a number block, the device is also very compact. The dimensions here are only 35 x 12.3 x 3.5 centimeters and the weight is 860 grams. It is particularly positive that this comparatively cheap gaming keyboard offers you an anti-ghosting function for all keys. to fix. If that works, the Mac automatically starts normal operation. This information is stored on your Mac in the NVRAM and only disappears when the NVRAM is deleted correctly. Clean
with alcohol and save the data externally.
The bottom row of keys easily follows the downward curved housing, so that the space bar is a little larger, a typical Logitech feature.
an espresso - without sugar and milk - poured into my Macbook one week.
In the last section of our guide, we would like to answer a few questions that are often asked in connection with gaming keyboards.
The labels replace time.
However, the material often tends to shine after a long period of use. Gaming keyboards are devices specially tailored for computer games that have some special features. For example, they almost always have keyboard lighting, dust cleaning mud review < / a> offer fast response times and endure millions of keystrokes. The black HAVIT HV-KB432L-DE is particularly optically characterized by its almost frameless housing, with which it looks very modern and compact overall. Pan across full-size images in iPhoto, view horizontal timelines in iMovie and Final Cut Pro, change clocks in GarageBand and Logic Pro - all with one hand (so you can hold your coffee mug or type text with the other) , The Mighty Mouse gives you a high degree of flexibility for discovery tours. This incorrect keyboard setting can drive you crazy. Every character you type automatically overwrites your existing text. A special feature is that four user profiles with individual settings are available. The Lioncast LK15 can stand out visually from everyone thanks to its large palm rest. In combination with the available RGB lighting, the device makes a quite modern and eye-catching impression. The dimensions here are 47.3 x 23.5 x 3.1 centimeters and the weight is 1 kilogram. We recommend that you rely on AV-Test in this regard; an IT security institute that specializes in antivirus (AV). On the AV-Test website you will not only find interesting statistics on the spread of spam and malware, but you can also compare security suites. You can filter for mobile systems, systems for private users and systems for companies. The Mighty likes to get sick very quickly. Then you can shoot diligently, but not much happens. You can find cleaning tips on the Internet. I tried everyone. They help, but unfortunately only temporarily.
1 note
·
View note
Text
Why need of Jeep Wrangler Diagnostic Tool?
With Jeep Wrangler Diagnostic Tool, you can read and clear error codes related to your vehicle's check engine light. The code reader is of excellent quality, with a well-designed interface and, most crucially, a lot of Jeep diagnostic information.
With a Jeep Wrangler Diagnostic Tool, you can quickly find the cause of a problem with the vehicle's electronic control system in the vehicle (troubleshooting) by simply connecting the vehicle's 16 PIN diagnostic jack while reading the error code displayed on the device.
Characteristic:
Read and delete diagnostic error code: The display also shows the meaning of the error code.
Clear / delete error code
Stream live PCM dashboard data
Reliable and accurate
Crystal clear, easy-to-read two-line LCD backlit display
User friendly with add-ons
Connect securely to your computer on board
No battery required
Dodge Dakota Shocks
Shock absorbers are necessary to ensure that your vehicle runs well and that you can use it to the fullest. If you are not a professional and do not know exactly what to look for, it can be difficult to buy and install the best Dodge Dakota Shocks. Shock absorbers are ideal for you and your vehicle in particular. Although discontinued in 2011, the Dodge Dakota is still a popular mid-range truck. Over one million units were produced in a 25-year production cycle spanning three generations.
Whether you are driving the first-generation old body model or one of the more powerful models that followed, at some point, you will need to get a new Shocks For Dodge Dakota.
Jeep Cherokee steering upgrade
The headset is one of the popular features as it has only three attached ears.
Jeep Cherokee Steering Upgrade Components:
Jeep Cherokee XJ 4-bolt steering conversion
Internal space in the 4-bolt control box
External control box 4 bolts
Installation of accessories
Installation procedure
Available on the Rock Runner front screen (as an upgrade)
Features:
Convertible steering Jeep XJ 4-bolt
Steering power increased (3: 1 YJ box in a constant ratio)
Put on a more powerful headphone in a monocoque
Strengthen the monocoque around the wheelhouse
It can be used with standard 3V steering until 4V gear is available and installed.
Curved Light Bar Cover
The Curved Light Bar Cover is made of polycarbonate composite material, as durable as the light strip lens. The hood has a simple clip system for quick on and off functions. Each cover measures 6 "long and is specially made for Curved Lights beams. When ordering, be aware that each cap is 6 inches long. Pay attention to the length of the light strip and order the correct quantity. If you have a single row of 30-inch light strips, use five covers. It is necessary to cover all the lamps above the headlights in some areas.
Electric Power Tongue Jack
An Electric Power Tongue Jack allows you to raise and stabilize your trailer. You can move the trailer up and down with a button.
You should know your specific requirements and how effectively the crane can meet them before purchasing an electric trailer crane. To begin, a jack must be capable of supporting the trailer's weight.
1 note
·
View note
Text
All I See Is You
pairing: Boyfriend!Taehyung x Reader genre: Fluff warning: sugary sweet romance word count: 2317
Even if the world decided to swallow you whole and send you back to the days where you had struggled, so long as he was there, you would be happy, because loving him was the sole reason you lived so blissfully.
Namjoon | Taehyung | Hoseok | Jimin | Jin | Jungkook | Yoongi

He’s late. You can’t believe he’s late. Is it not customary for the star of the show to arrive on time and greet the incoming guests? Instead here you are, watching as the exhibition to your boyfriend’s latest gallery open its doors to the massive crowd waiting outside. It is difficult to believe how he has managed to build a positive reputation with his habits of tardiness. The beginnings of a lecture start to run through your mind, it’s rehearsal driving your nerves upward. However, before your irritation can be vocalized Taehyung appears a few ways down the street, fingers fumbling with his brightly patterned tie.
As angry as you are at him, your heart couldn’t help but skip a few beats when the sunlight hits his profile, casting shadows beautifully across his skin just before a smile breaks across his features and he sends his arms into a high wave to greet you. The man who could so easily be mistaken for a sculpture is currently sprinting down the sidewalk, his long coat desperately trying to catch up to its owner.
“Finally, I was beginning to think you bailed.” You reach your hands up to recover the damage the wind has done on Taehyung’s curls, stifling a laugh at his shaggy appearance. Before you could move a single strand back in its place, however, steady hands wrapped around your waist and lifted you into the air that had you squealing as your boyfriend spun you around.
“Babe, I was trying to look like a true artist. You know that artistry is in the least expected of places, like my bed head.” He places a light kiss against your forehead as he sets you down, eyes sparkling as he properly looks at you for the first time today. “Though I see that you’ve managed to outdo me again, as expected of my world-class fashion designer.”
You huff and brush off his compliment, turning your face away ever so slightly so that your crimson cheeks could take shelter behind you locks. How he manages to set a thousand butterflies free in your stomach after all these years baffles you, but you do nothing except let your heart swell bigger than it already is. You grasped his hand, and urged him into the museum where the many adventures you and Taehyung had been on together were on display for the world to see captured in timeless photographs.
Taehyung doesn’t let go of your hand as he navigates the pair of you two through the crowd, nodding polite greetings to those who recognize the young, talented photographer. You could tell that your boyfriend was particularly excited to give you a private tour of his exhibit, even though you had lived through most of the moments captured on the walls. You give his hand a little squeeze as the two of you passed by the time when Taehyung thought it was a good idea to go to a see-in-the-dark restaurant for date night, forgetting that he himself was terrified of darkness.
“You ate all of my spaghetti that night, I’ll never forgive you.” You smile up to Taehyung. Who, to your surprise, was already looking back at you. “You even ate the meatballs.”
The two of you had been together for so long now, the adventures you had been on together were starting to blur. The one memory that remained clear, however, was the first picture you had ever taken of the beautiful man. Ironic how a journey with a photographer started with a shot you took of him.
Years ago, when you were just starting to navigate your talents in the fashion school, you had stumbled upon a ‘designer block’ for your senior assignment. The amount of stress and anxiety that had build as the blank sketch book stared back at you had became too much for you to bear. Deciding to look for inspiration elsewhere, or simply to clear your mind, you grab your phone and head towards the park near your home.
You escape your narrow apartment as crimson leaves fall from their branches, paving a path for you towards rows of perfectly planted trees. You curse at the focus you left back at your drawing table and inability to absorb the beautiful the scenery around you, mind still desperately scrambling for fulfilling designs. Drowned in your thoughts, you failed to realize when the leaves had taken you right to a place where a living and breathing source of inspiration stood right before you.
Sunlight sneaks into your vision, causing you to squint at the tall figure before you. His facial structure could have been one worth many moons of work by a master, with a side profile so well animated you could not believe a simple human looked liked one of the gods. You longed to see his eyes, yet they were currently narrowed into the lens of a camera that looked far too professional for your purposes. His lips slightly parted in focus but you could not be bothered to follow his gaze, you were too mesmerized by the most beautiful man you had ever seen.
Years of fashion design education told you that turquoise silk pants and a red, striped flannel would have never worked together, but somehow, on him it did. The boy who stood before you could easily defy any rules you ever studied in your magazines and still turn it into art. Still trapped your trance, your hand unknowingly reached for your phone to take a photo for ‘inspiration’.
Snap
The device almost falls from your grasp as the sound gives away your actions and location. God. You remembered that you had forgotten to turn of the ringer from this morning’s alarm and you cursed at your forgetful mind, flames intruded you cheeks as you realize what you had done. Bracing yourself for an awkward explanation as a first impression, you calm your beating heart and practice how you will explain your actions to the handsome stranger, hoping that by a miracle he won’t embarrass you. However, before you could bend over to pick up the small device, the boy in red whipped his head around with a gaze of peculiarity as he strode lazily towards your frozen figure.
“Did you just take my photo?”
You glance up at him and mentally note that his eyes are akin to brown hazelnuts, just deep enough to make your heart melt. The words to justify yourself fell short, though, as the boy’s hand reached from his pocket and swiftly scooped up your phone.
“S-sorry! The sunlight was hitting the scenery so beautifully I wanted to commemorate it. If you’re unhappy about being in it, I’ll delete it.” You extended your hand out, expecting your small phone to be placed in your hands so you could carry out your promise, but he was no longer listening to you. Instead, he gave the screen a quick tap, bringing up his photo with a furrow of his eyebrows as if he were analyzing the image.
Blood rushed to your cheeks as you anxiously watched his actions, embarrassed at the photo’s obvious focus on him instead of the park like you described. You watch as his fingers zoom in and out on each corner of your screen, eyebrows now knotted. “You’re not a good photographer.”
“Excuse me?”
The boy looks up to meet your gaze and you confirm your suspicions of his eyes being capable of melting your very soul, hitching your breath as you attempt to not reveal the rapid beating of your heart. “I mean, you haven’t captured the light at all. The overall component of the shot is good, but your angle is causing the light to hit in all sorts of wrong places.”
He takes a big step towards you, causing you to scrunch tightly, afraid that you will surely combust if he as much as grazes your arm. “Look here, from where you took the photo the sunlight is completely blocked out. You should position the camera a little lower and put your primary focus on how the light hits my form. Exposure is everything with natural lighting.”
“Why are you telling me this?”
He flashes you a boxy grin and smoothly hands your phone back to you. “So you can take it again! Here, I’ll go back to where I was standing.”
Dumbfounded, you did as the boy directed and retook the photo from his said angle, unsure of why he wasn’t angry or why you were complying to his request. As you check the newly taken photo he runs towards you, swooping you in an almost-hug to look at the picture.
The sunlight hits the boy’s figure perfectly, highlighting his every feature as if they were kissed by Apollo himself. Beams of light trickle around him, making his oddly matched outfit stand out against the auburns of the autumn leaves. You almost joke and ask if he was a model as his stance was not an inch off from the previous one when you noticed his gaze.
While you were left daydreaming about his eyes before, in this version of the photo the boy was looking directly at you with his warm eyes. His gaze pushed up into crescent moons as if he was looking straight into your soul. You blush at how incredibly handsome this stranger is and try to convince yourself to treat him to coffee as payment for taking his photo.
“Oh, you did so well! I can’t believe you did that on your first try, you might be more of a genius than I am.” He leans too close to you, his every breath fanning your neck as he inspects your handiwork, and you urge the thought to turn and kiss him right then and there to the back of your mind. “I’m Kim Taehyung, by the way. Pretty lady who took my photo, what’s your name?”
“Babe. Baby!” You turn your head to see your boyfriend’s pouting face. “Were you listening to anything I was saying? What could you be thinking about that’s more important than me?”
“Where to buy the world’s loudest alarm clock so you’re never late again.” Inflating Taehyung’s ego right now would do nothing but encourage him to be late again in the future, so you bite back your memories and allow the photographer to lace his fingers through yours as you walk into the exhibition.
“I’m sorry for being late...most of the time. Let’s enjoy the exhibit, though, huh?” At the tug of Taehyung’s hand, the two of you start on a trip down memory lane. Initially you had objected his idea of using photos from every date the two of you had ever been on as the theme for his first major portfolio, but Taehyung’s eager whines made your stubbornness soften and you braced yourself for the world to know of your love.
A favorite photo of yours passes by, one of the old, narrow apartment your boyfriend had spent so many nights over at. The place was well beyond historic with its chipping paint and cracking floors, repair fees causing the two of you to live on nothing but instant noodles and crackers. It was almost silly how much you enjoyed being a broke student with Taehyung despite all its late night convenience store hunts and rumbling bellies.
It was, however, with him. The boy who made canned tuna taste like the freshest five star dish you had ever tasted, who made dollar store candles capable of wooing you deeper into romance, and the boy who made your saddest days your happiest. You remember how much the dependence on each other during your student days fortified your relationship with Taehyung, your love growing stronger with each smile he casted your way.
You shift your stance to remind Taehyung of the time when he was so hungry he contemplated eating the shell of his boiled egg, when you catch him staring down at you. “Why are you looking at me? We are here to see your work.”
“I’ve seen these photographs a million times while editing, happiest workdays of my life, may I add. I got to re-live all the times I found myself thanking whatever entity is out there for letting me meet you, all I ever see is you in these photos. All I see is you.”
As crimson flooded the apples of your cheeks, his grip tightened around your hand, his figure leaned into yours to brush his lips against yours in a soft kiss. The curve of his smile drew one of your own and with a tug of your hand in his, you pull him closer and delve yourself into the bliss that is Kim Taehyung. Time seemed to stop and all of the exhibit’s visitors seemed to have evaporated into time and space, it was just you and Taehyung, surrounded by your memories throughout the years.
He retreats from you but lingers, pressing a mere peck to the corner of your mouth with that same boxy smile, confirming that he is the only person in the universe that could fit you so right, so perfect. This boy who was a walking fashion catastrophe, who dedicated his entire career to loving you, who continuously showed you in all the most mundane ways why he had been your muse from the start. Even if the world decided to swallow you whole and send you back to the days where you had struggled, so long as he was there, you would be happy, because loving him was the sole reason you lived so blissfully.
His hands smooth over the back of your dress as you lean away from him, your fingers gently running over his cheek as your eyes drink in the masterpiece before you, the man you called yours. “All I see is you too.”
#bts#bangtan bookclub#kkreationsnet#bts fanfic#bts fanfiction#bts imagines#v#taehyung#bts drabbles#bts fluff#taehyung fluff#v fluff#taehyung fanfic#bangtan#bts scenarios#taehyung imagines#taehyung x reader#taehyung fic#v fic#bts fic#taehyung scenarios
219 notes
·
View notes
Text
Timestamp Safari For Mac

I can very easily see timestamps for texts (SMS) and messages (wifi? Not really sure what this is) on iOS messenger by swiping to the left. However, in the Messenger app on OSX (10.11.6 El Capitan), I cannot for the life of my get these timestamps to appear (swiping, right-clicking a message, app options and context menus, etc.). I noticed some very odd behaviour in macOS High Sierra's (10.13.1) Finder. For filenames that contain timestamps Finder changes the timestamp format, the two screenshots below illustrate the issue.
15 septiembre, 2020

Drew Reece If you have Private Browsing enabled the Safari toolbar is black, when you turn on private browsing it will not save your history.
iOS 9.3.5 sonshine1972 All modern versions of Safari in iOS have searchable history, here’s how it works:If you tap on any searched history result, the page or site will immediately open in Safari.In the example above, I searched for “Charlie Rose” to track down an old interview I had watched on YouTube, and the video I was searching for was found immediately.You can search through any search history on Safari on the iOS device, even history that is quite a bit older, as long as you (or the user) has not Note that if you use Safari and iCloud on an iPhone or iPad as well as another device, you will have other devices history to search through as well – even if it was not searched for on the current device.
User profile for user: how can i tell what time a website was browsed on ipad, ipad browsing history date and time, ipad history timestamp, ipad safari history date and time, ipad safari history time, ipad safari history timestamp, safari history time, safari history time stamp, safari history timestamp, safari history timestamp ipad
With the excellent Safari History search feature you can easily retrieve and find previously visited sites, webpages, and videos, whether from earlier in the day or even well over a year ago – assuming the searchable Safari history has not been removed anyway. How to See History in Safari. If you have multiple iOS devices such as an iPhone and an iPad, syncing Safari tabs allows you to see...Get monthly tips delivered directly to your Inbox.We don't like spam any more than you. 2.
User profile for user: Apple provides the Safari app for browsing the Internet. Safari stores a log of websites you visit along with other related components, such as the cache and cookies.
How it stores the browsing history using times such as This Morning, Afternoon, Evening when you view history in safari from an iPad. Did you know you can search through web browsing history in Safari on an iPhone or iPad?
Reproduction without explicit permission is prohibited.This website and third-party tools use cookies for functional, analytical, and advertising purposes. Thank you. However, once a tab is closed, the browsing history for that tab is deleted.If you have multiple devices such as an iPhone and an iPad, you can view the browsing history from one device while using the other device. Hi. User profile for user: All Rights Reserved.
In response to lesterfamily3705 Is there a way that I can get a record of the time during which a website was searched the browser history? Use iPhone backup Extractor to export the Safari data to a folder. Tapping the Back button will take you to the last website that was viewed. I'm curious as to what the windows of times are used to differentiate between morning, afternoon, evening, when you are viewing a website. Maybe someone still has no idea how to see the Safari history on iPad.
IPad 2 Deletes Browsing History From Safari By Itself Jul 29, 2012. lesterfamily3705 I don't know a way to get iOS Safari history timestamp. Then you can view safari history. Posted on This is not a built in feature as far as I can tell. Simply select the website you want from the list and it will reload in Safari.If you have several different tabs open in Safari, the browsing history is saved independently for each tab. However, you may want to delete your browsing history and the accompanying data for privacy reasons. In response to sonshine1972 How to View the Browsing History in Safari on the iPhone or iPad By iAnswerGuy / March 5, 2016 March 5, 2018 Apple provides the Safari app for browsing the Internet.
Safari uses iCloud to keep your browsing history the same on your iPhone, iPad, iPod touch, and Mac computers that have Safari turned on in iCloud preferences.However, your Mac can keep your browsing history for as long as a year, while some iPhone, iPad, and iPod touch models keep browsing history for a … However, once a tab is closed, the browsing history for that tab is deleted.
Timestamp Safari For Macbook
For the most part, it is convenient and easy to use. It is shaped like an open book. User profile for user: In this situation, tap the Bookmark icon located in the same row of icons as the Back button.
Tap that to turn Private Browsing off. The browsing history for each tab is not deleted when you exit Safari. Sep 19, 2014 2:36 PM in response to lesterfamily3705 Reviewing your iPad browser history is a straightforward process. Tap History to check the URLs list. How to See History in Safari. dominic23 Safari in iOS can contain a significant time of browsing cache, depending on those circumstances and perhaps others too.Searching safari history on my iPhone… how far back will the history go? I need two months at least.You need to mention the search history section does not display unless you pull down on the list. Step 1. I was more asking about within safari specifically. Tap History to check the URLs list. You can try the following assuming you sync the device to iTunes with unencrypted backups… (I'm also assuming you are on a Mac).Sync the device with iTunes to create a new backup.Use iPhone backup Extractor to export the Safari data to a folder. Thank you!!! I am developing a tool to extract people's web visits on Mac and Windows (history on Chrome, Firefox, and Safari).
iOS 7.1.2 May 18, 2017 11:12 AM Scroll down the list and click open the “Metadata” folder. My iPad 2 tend to delete browsing history from Safari by itself without any prompt. dominic23 Posted on Oct 5, 2013 6:31 AM. Then you can view safari history. iPad 2 Wi-Fi, User profile for user: What could be the reason behind this issue and how can I solve it?
Thank you for your reply. More Less. Did you know you can search through web browsing history in Safari on an iPhone or iPad?
Deaf Or Disabled Essay,Wayfair Damaged Item Reddit,Atc Barge Strappings,Ryan Browne Cnn,Kresley Cole Munro Excerpt,Ui Online Florida,Pof P415 Gen 2,Joel Osteen Affirmations Pdf,Dry Tortugas National Park Ferry,Jungle True Story Marcus Stamm,Waterrock Knob Trail Plane Crash,Do Wrens Abandon Their Nests,Jimmy Dugan Cause Of Death,Owl Eyes Quotes Chapter 3,Meet The Woo Meaning,Evil Laugh Sound,Black Bugs On Petunias,Bernese Mountain Dog Rescue Nevada,Greenworks 1700 Psi Portable Pressure Washer Manual,The Willoughbys Song Over The Rainbow,Xfinity Stuck On Almost Activated,Bill Wurtz Midi,Heart Surgeons Ep 1 Recap,Injustice 3 Comic Read Online,This Feeling Lyrics Charlotte Leigh,Sad Kpop Quotes,444 Meaning Twin Flame,Albino Tiger Shovelnose Catfish,111 444 777 Atm Code 2020,Bible Verse About Herbs And Healing,How To Add Padding To Wood Headboard,This City Sam Fischer Chords,Kawasaki Z1 900 For Sale Craigslist,Bright White Light When Eyes Are Closed Spiritual,Vs Vs,Ktm 85 For Sale,House Of Payne Cast Member Dies,Will Squirrels Starve If I Stop Feeding Them,Igloo Ice Maker Models,Do Hawks Hunt At Night,Boston Whaler Montauk 170 Bow Cushion,Random Jojo Character Generator,Emma Harris Lil Peep Ex,Are Skinks Poisonous To Dogs,Fortnite Lite Pc,Pof P415 Gen 2,Goldfinch Canary Mule For Sale,Canary For Sale Near Me,Goats Head Soup Reissue 2020,Westiepoo Puppies For Sale In Missouri,Aron Baynes Wife,
Timestamp Safari For Mac Os
Timestamp Safari For Mac Mojave
Do you mean time expressed in hours : minutes : seconds? Unfortunately Safari doesn't show the time. The entire browsing history available in History -> Show All History menu shows only the date.
The history is saved in a database file named History.db located in Safari folder inside your Library. If you're familiar with SQL you can copy that database file somewhere, open it with the app DB Browser for SQLite, choose Browse Data and select under the Table dropdown menu history_visits. You can sort the data selecting the visit_time column.
The problem is that the timestamp in that column is expressed in Core Data timestamp format which is not human readable. You can convert it here: https://www.epochconverter.com/coredata
Timestamp Safari For Mac Shortcut
If you need to check only a specific visit it's doable otherwise you'd need to convert someway the entire column (I guess exporting the table in CSV and managing the conversion with another app).
Jul 22, 2019 4:27 AM

0 notes
Text
Smart Home Market Perspective by Comprehensive Analysis, Growth Prediction to 2023 | Effects of COVID-19
Market Highlights
Smart homes are backed by computing devices and information technology that integrate various devices in the house to facilitate enhanced convenience, comfort, security, and entertainment in a sustainable way. Previously smart homes were confined to elite class consumers; however, in recent years, smart homes have gained widespread consumer adoption.
The smart home market was initially concerned primarily with advanced security features. However, the market has now ventured into newer segments such as lighting systems, fire detection, energy efficiency systems, gas leakage detection, and entertainment. This has propelled the growth of the market.
The smart home market is experiencing increased demand from all quarters; however, energy conservation has been the key factor in influencing the growth of the market. Moreover, the maintenance of smart homes is cheaper than traditional homes. Other factors substantiating the growth of the smart home market include increasing affordability of smart home features, the threat of climate change, and the growing adoption of cloud-based technologies.
On the contrary, the growth of the market might be hindered by the risk of privacy and bugs surrounding smart homes. However, multifarious benefits are likely to aid in overcoming of these hurdles.
Growing disposable income or rising affluence of the middle-class consumers along with growing number of working couples have also reflected positively on the market growth. Since more and more homes stay empty throughout the day, there is an increased need for home automation. The governments in multiple countries are taking concrete steps to promote the construction of smart homes by making policies favorable for builders who are keener on building smart homes.
Segmentation
The global smart home market research has been segmented based on component, application, and technology.
By Component, the smart home market has been segmented into software and services. The software segment has been further segmented into behavioral and proactive. The services segment has been further segmented into managed & professional service.
By Application, the smart home market has been segmented into lighting control, security & access control, entertainment & other control, HVAC control, home healthcare, smart kitchen, and home appliances.
The lighting control segment has been further segmented into relays, occupancy sensors, daylight sensors, timers, switches, dimmers, accessories, and other products.
The Security & access control segment has been further segmented into video surveillance and access control. The video surveillance sub-segment has been further segmented into hardware, software, and services.
The HVAC control segment has been segmented into smart thermostats, sensors, control valves, dampers, actuators, heating and cooling coils, pumps & fans, and smart vents.
The entertainment & other control segment has been further segmented into entertainment controls and other controls. The entertainment controls sub-segment has been further segmented into home theater system controls and touchscreens, audio, volume, & multimedia room controls, and keypads.
The home healthcare segment has been further segmented into health status monitors and physical activity monitors.
Regional Analysis
The smart home market has been segmented into four key regions, namely North America, Rest-of-the-World (RoW), Europe, and Asia Pacific (APAC).
North America accounts for a major share of the market and is likely to dominate the market over the forecast period. The existence of leading market players in the region along with heightened demand for home healthcare has led to the proliferation of the smart home market in North America. Moreover, high spending capacity leads to increased spending on the modernization of homes, which boosts the growth of the market.
The APAC smart home market is slated to showcase remarkable growth over the forecast period. fast track urbanization in the region combined with rising disposable income has created abundant demand for smart homes in the region. Adoption of cloud technologies, the growing sophistication of lifestyle, and heightened focus on safety and security are auguring the growth of the market in APAC. Additionally, governments in the region are investing substantially in the development of smart cities which is propelling the growth of the market.
Competitive Landscape
Ingersoll-Rand PLC (Ireland), United Technologies Corporation (U.S.), Samsung Electronics Co., Ltd. (South Korea), ABB Ltd. (Switzerland), Siemens AG (Germany), Honeywell International, Inc. (U.S.), Legrand S.A. (France), General Electric Company (U.S.), Schneider Electric (France), and Johnson Controls, Inc. (U.S.) are the eminent players in the smart home market.
Industry Updates
May 2019 - Amazon released the latest version of its Echo Show device with enhanced privacy and smart home controls. The new device is now equipped with a camera shutter which is the first of any Amazon's display speakers. In addition, the new allows voice recording to be deleted in a much more simplified way along with a new privacy hub webpage which explains how Echo devices use and store voice recordings. Amazon is also rolling out a new smart home dashboard which would provide users more control over compatible smart home devices and groups.
Related Reports:
https://www.evernote.com/shard/s652/sh/8f7bf0ab-2af1-5167-140a-f4eda3bf87c9/551559ee6d27781fa9133000a10b7732
https://www.evernote.com/shard/s652/sh/a0eb3bdc-f002-e266-4c38-de16a6f62c8f/9cc6c466584500b787f5dcc89a8447ba
https://www.evernote.com/shard/s652/sh/326286ed-1a62-c44f-3c90-eaad0e0770d5/d8a042e4eaf203650792f0b842047b3b
https://www.evernote.com/shard/s652/sh/ce7dff45-acf9-ba95-509a-9aa15435377f/62584afe82b352c824ed064fffcf313e
https://www.evernote.com/shard/s652/sh/4fb87c56-7f4f-78da-e955-d4e67fe9a628/560e4317d7094ccc212c6ba2ad1d9173
0 notes
Link
How to fix a laptop that won't turn on
There are many problems with laptops, but the question often arises how to fix a laptop that won't turn on? There are some simple home remedies that are really easy to do. First, make sure your laptop is connected to charging, but in many cases, this is not necessary. A smartphone that won't turn on can be repaired without the help of a service technician. In the guide, we will learn how to deal with a smartphone that cannot be started, frozen on the login screen, or keeps restarting. which does not turn on can be repaired without the help of the service. In the guide, we will learn how to deal with a smartphone that cannot be started, frozen on the login screen or keeps restarting. which does not turn on can be repaired without the help of the service. In the guide, we will learn how to deal with a smartphone that cannot be started, frozen on the login screen, or keeps restarting.
There are a couple of different possibilities that are you sure you have a problem with that? Don't worry if you have any.
Leave the paw and sub. Thank you in advance. Hello, I have a problem with the laptop mixx 2 linen talent, the problem is that the laptop does not want to turn on after the last switch-off, no LEDs are burning anything. The worst thing is that the laptop worked flawlessly and now even charged for two days in a row it still does not turn on after the power button. Dell laptop - won't turn on, how to fix it? )) My Dell won't turn on after flooding, even the power button doesn't light up when pressed, nothing works. What's the matter, what's causing this? My computer won't start: use Safe Mode. Even if you cannot start Windows, you may be able to use Safe Mode. If you manage to turn it on, you will be able to undo any changes that made the full system unable to boot. Web browsers are unfortunately no exception. They can all refuse to obey at the least opportune moment. A great example is a bug that Firefox users encounter quite often. The application does not start because, as it claims, it has already been turned on. What to do then What to do if the laptop won't turn on? Desktop computers are less and less in our homes.
(adsbygoogle = window.adsbygoogle || []).push({});
No wonder laptops are more comfortable and (often) cheaper.
While they are extremely useful devices, they sometimes crash. Let's check what to do when the laptop does not turn on Problem 1 - no response when turning on the laptop. This problem seems to be the worst that can happen to the owner of a laptop computer. He wants to start it, but despite repeatedly pressing the switch, nothing happens. The screen remains black all the time, and the laptop does not respond at all to attempts to turn on. Unfortunately, the tablet is dead, the laptop does not detect it. Rather, it does not matter, but it did not turn on after I connected a pen drive for a long time to it - copying over 2GB of film and then rehearsing it. And after some time, perhaps the first attempt to turn on the tablet after this fun, it is not easy not to panic when your Samsung tablet will not turn on. knowing what to do in this situation really helps in making sure you see if you can fix it yourself before spending on getting the tablet repaired. I have a Sony Xperia J phone. Today I listened to music then locked it and stowed it. Later it turned out that the phone turned off by itself and won't turn on. When I took out and put the battery in, I tried to turn it on but it vibrated slightly, the LED on the bottom blinked on. Part 2: Rescue data on an Android mobile that won't turn on If you need help rescuing data from an Android phone that won't turn on, dr.fone - Recover (Android) will be your best friend in your data recovery attempt. I listened to music today, then locked and stowed it. Later it turned out that the phone turned off by itself and won't turn on. When I took out and put the battery in, I tried to turn it on but it vibrated slightly, the LED on the bottom blinked on. Part 2: Rescue data on an Android mobile that won't turn on If you need help rescuing data from an Android phone that won't turn on, dr.fone - Recover (Android) will be your best friend in your data recovery attempt. I listened to music today, then locked and stowed it. Later it turned out that the phone turned off by itself and won't turn on. When I took out and put the battery in, I tried to turn it on but it vibrated slightly, the LED on the bottom blinked on. Part 2: Rescue data on an Android mobile that won't turn on If you need help rescuing data from an Android phone that won't turn on, dr.fone - Recover (Android) will be your best friend in your data recovery attempt.
With the help of this data recovery solution, you will be able to recover your lost, deleted intuitively.
Seventh - use the service's help. If everything has failed and you are unable to diagnose or repair a damaged laptop, you should use the services of specialists. Recommended laptops computers. Hello, I have recently had problems with my laptop, it won't turn on. the battery does not turn on and the power does not (with and without the battery inserted). As you can see on the topic, I have a laptop that suddenly turned off and I do not want to turn on. The laptop is from Gateway with a 2.4 GHz Celeron processor. After pressing the power button, the diode lights up for a fraction of a second and that's it. The matrix does not turn on, the CPU fan does not start either. Hello, as in the topic I have an Asus X551MAV laptop that does not turn on. The power button is unresponsive and the lights are also off. When I say hello when I turn on the computer, it won't load at all. Once the system loading error pops up press alt + ctrl + delete to reset. Sometimes there is this bar that takes a minute to load and then stutters and the only option is restart. Why the laptop won't turn on? How to repair a laptop yourself and find out what's broken.
faults for each brand, as well as a table with a description of the recognition of light and sound signals.
We do the impossible on the spot for miracles we need more time. If the computer tries to start up and then stops responding, it may be a poor internal connection. Poor connections can occur when a hardware component, such as a memory module or boot drive, is installed incorrectly, is incompatible with the computer, or the computer has been dropped or subjected to severe shock. The computer, like any device, can break down. In such a situation, most people call all sorts of handymen or have the computer serviced. Usually, it is a bug, because many faults are easy to diagnose and fix by a person who is not very knowledgeable about computers. ... Rescuing the system does not require the help of a service technician. Windows 10 provides tools that make it easier to restore the correct operation of the computer by yourself. Let's read how to deal. The laptop won't turn on. What to do in the event of a hardware failure? Laptop keyboard not working, how to fix non-working keyboard ?. whose price won't burn a hole in your pocket. We offer you a comparison, which product is good, which is better and which is the best. If the phone, despite being connected to a laptop or other desktop computer, does not want to charge, and a cloud or a "driver/software installation" window appears on the laptop monitor, then in our phone we have damaged charging connector with sub-board or whole motherboard, as some models have Hp Probook 4535s - Laptop won't turn on Hello! My mother's laptop has crashed and won't turn on even in safe mode.
(adsbygoogle = window.adsbygoogle || []).push({});
0 notes
Text
Migrate Single MySQL Enterprise Database into Three Node MySQL Enterprise InnoDB Cluster with latest version 8.0.20
How to Migrate Single MySQL Enterprise Server to Three Node MySQL Enterprise InnoDB Cluster latest version 8.0.20 ? Assume current you production work loads resembles multiple app server and all are point to single MySQL Server. have you thought about below questions ? 1. what if , this database goes down ? this is single point of failure ? 2. what if, data loss ? 3. Scalability ? 4. Data Inconsistencies ? 5. DR? BTW, i am using MySQL Enterprise Edition , more info:- https://www.mysql.com/products/enterprise/ To address these basic questions on SLA , RPO/RTO , MySQL has another high availability solutions which is developed by MySQL Engg team, which has no noisy neighbors all components are tested by MySQL Engg team. MySQL InnoDB Cluster= MySQL Server + MySQL Shell + MySQL Router In This Blog , I will Talk about below topic:- 1. Introduction about MySQL InnoDB Cluster 2. New features in MySQL 8.0.20 related to InnoDB CLuster. 3. High Level Migration from one server to 03 server MySQL InnoDB Cluster. 4.Step by step Guide 5. Conclusion High lights about MySQL InnoDB CLuster can be found here:- https://dev.mysql.com/doc/refman/8.0/en/mysql-innodb-cluster-production-deployment.html In case which cluster solutions is suitable for your application workloads can be found here:- https://mysqlsolutionsarchitect.blogspot.com/2020/05/which-cluster-is-suitable-for-your.html Pain to Solutions Architecture Let’s Deploy Single Production MySQL Server to 03 Node MySQL InnoDB Cluster. Prerequisite:- ü About Software 1. MySQL Server è MySQL Server has to be running on all three machine, with same versions. mysql> select @@version 2. MySQL Shell è MySQL Shell has to be installed and running in all three machine, (below are installation steps) 3. MySQL Router è This software has to be install where app is running) ü Qualification of database, whether production DB is right to deploy or not? ü Each Table Must have InnoDB Storage Engine . ü each table must have Primary key) https://dev.mysql.com/doc/refman/8.0/en/mysql-innodb-cluster-requirements.html https://dev.mysql.com/doc/refman/8.0/en/group-replication-limitations.html Assume:- You have one Production Machine , 02 new Machine.In This demo :- 192.168.0.10 --> production database. 192.168.0.9 , 192.168.0.11 are New machine Machine Role 192.168.0.10 Primary 192.168.0.9 Secondary 192.168.0.11 Secondary Primary Machine has two database running. mysql> SELECT table_schema "DB Name", ROUND(SUM(data_length + index_length) / 1024 / 1024, 1) "DB Size in MB" FROM information_schema.tables where table_schema not in ('mysql','information_schema','performance_schema','sys') group by table_schema; +------------+---------------+ | DB Name | DB Size in MB | +------------+---------------+ | customerDB | 1899.5 | | sales | 0.0 | +------------+---------------+ 2 rows in set (0.07 sec) You can see i have one machine with 1.89 GB of MySQL Database, through which idea is to form new InnoDB Cluster with additional 02 server required where nothing is installed!!! Secondary Server has nothing installed ,fresh machine. So let install MySQL Server & MySQL Shell in both secondary Server. MySQL Router is not needed to install on database machine , instead you install it in Application Server or else Primary Server. Install MySQL Server https://dev.mysql.com/doc/refman/8.0/en/linux-installation-yum-repo.html Install MySQL Shell https://dev.mysql.com/doc/mysql-shell/8.0/en/mysql-shell-install-linux-quick.html Once we are done with cluster set up>> below output has to come than we can say that our InnoDB Cluster is successfully deployed MySQL JS> cluster.status() { "clusterName": "myCluster", "defaultReplicaSet": { "name": "default", "primary": "192.168.0.10:3306", "ssl": "REQUIRED", "status": "OK", "statusText": "Cluster is ONLINE and can tolerate up to ONE failure.", "topology": { "192.168.0.10:3306": { "address": "192.168.0.10:3306", "mode": "R/W", "readReplicas": {}, "replicationLag": null, "role": "HA", "status": "ONLINE", "version": "8.0.20" }, "192.168.0.11:3306": { "address": "192.168.0.11:3306", "mode": "R/O", "readReplicas": {}, "replicationLag": null, "role": "HA", "status": "ONLINE", "version": "8.0.20" }, "192.168.0.9:3306": { "address": "192.168.0.9:3306", "mode": "R/O", "readReplicas": {}, "replicationLag": null, "role": "HA", "status": "ONLINE", "version": "8.0.20" } }, "topologyMode": "Single-Primary" }, "groupInformationSourceMember": "192.168.0.10:3306" } Let's get Started (Step by Step guide) MySQL Configuration Check [1.]#configure the report_host variable in the MySQL configuration of each instance to a suitable externally reachable address mysql> show variables like '%report_host%'; +---------------+--------------+ | Variable_name | Value | +---------------+--------------+ | report_host | 192.168.0.10 | +---------------+--------------+ 1 row in set (0.00 sec) mysql> Make Sure result should not EMPTY o/w , go to my.cnf fileà keep à report_host='' à saveà restart mysqld Do this to all MySQL Server machine. [2.]#Ensure that none of the MySQL instances have any executed GTIDs: mysql> SELECT @@global.gtid_executed; +------------------------+ | @@global.gtid_executed | +------------------------+ | | +------------------------+ 1 row in set (0.00 sec) If the query returns anything like below, reset the master: mysql> SELECT @@global.gtid_executed; +----------------------------------------+ | @@global.gtid_executed | +----------------------------------------+ | 88a2732s-2373-11e7-7ce3-080027d1eed8:2 | +----------------------------------------+ 1 row in set (0.00 sec) mysql> RESET MASTER; Query OK, 0 rows affected (0.06 sec) mysql> SELECT @@global.gtid_executed; +------------------------+ | @@global.gtid_executed | +------------------------+ | | +------------------------+ 1 row in set (0.00 sec) Important: The RESET MASTER statement will delete all binary logs. This example assumes there is no binary logs that must be kept and that all instances have just been set up from scratch. #SQL_mode (for Demo Purposes) set global sql_mode='STRICT_TRANS_TABLES,NO_ENGINE_SUBSTITUTION'; [3.]#Make sure Database has primary Key SELECT a.table_name FROM INFORMATION_SCHEMA.TABLES as a LEFT JOIN INFORMATION_SCHEMA.KEY_COLUMN_USAGE AS b ON (a.TABLE_NAME = b.TABLE_NAME AND b.CONSTRAINT_SCHEMA = a.TABLE_SCHEMA AND b.constraint_name = 'PRIMARY' ) WHERE a.table_schema <> 'information_schema' AND a.table_schema <> 'performance_schema' AND a.table_schema <> 'mysql' and a.table_schema <> 'sys' AND b.constraint_name IS NULL; Let’s Get Started login mysql shell with user root MySQL 192.168.0.10:3306 ssl JS > checkInstanceConfiguration('[email protected]:3306') #mysqlsh [email protected]:3306 Creating a session to '[email protected]:3306' Please provide the password for '[email protected]:3306': ******** Save password for '[email protected]:3306'? [Y]es/[N]o/Ne[v]er (default No): Y . . . MySQL 192.168.0.10:3306 ssl JS > MySQL JS > dba.checkInstanceConfiguration('[email protected]:3306') Validating local MySQL instance listening at port 3306 for use in an InnoDB cluster... This instance reports its own address as 192.168.0.10:3306 Checking whether existing tables comply with Group Replication requirements... WARNING: The following tables do not have a Primary Key or equivalent column: customerDB.salesaccount, customerDB.salesdetails, customerDB.usermgmt Group Replication requires tables to use InnoDB and have a PRIMARY KEY or PRIMARY KEY Equivalent (non-null unique key). Tables that do not follow these requirements will be readable but not updateable when used with Group Replication. If your applications make updates (INSERT, UPDATE or DELETE) to these tables, ensure they use the InnoDB storage engine and have a PRIMARY KEY or PRIMARY KEY Equivalent. Checking instance configuration... NOTE: Some configuration options need to be fixed: +--------------------------+---------------+----------------+--------------------------------------------------+ | Variable | Current Value | Required Value | Note | +--------------------------+---------------+----------------+--------------------------------------------------+ | binlog_checksum | CRC32 | NONE | Update the server variable | | enforce_gtid_consistency | OFF | ON | Update read-only variable and restart the server | | gtid_mode | OFF | ON | Update read-only variable and restart the server | | server_id | 1 | | Update read-only variable and restart the server | +--------------------------+---------------+----------------+--------------------------------------------------+ Some variables need to be changed, but cannot be done dynamically on the server. NOTE: Please use the dba.configureInstance() command to repair these issues. { "config_errors": [ { "action": "server_update", "current": "CRC32", "option": "binlog_checksum", "required": "NONE" }, { "action": "server_update+restart", "current": "OFF", "option": "enforce_gtid_consistency", "required": "ON" }, { "action": "server_update+restart", "current": "OFF", "option": "gtid_mode", "required": "ON" }, { "action": "server_update+restart", "current": "1", "option": "server_id", "required": "" } ], "status": "error" } #Our First Task is to ALTER TABLE and add primary key to required table. mysql> ALTER TABLE usermgmt ADD PRIMARY KEY(userid); ALTER TABLE salesaccount ADD PRIMARY KEY(salesid); ALTER TABLE salesdetails ADD PRIMARY KEY(salesid); Let’s Re-check the Instance MySQL JS > dba.checkInstanceConfiguration('[email protected]:3306') MySQL 192.168.0.10:3306 ssl JS > dba.checkInstanceConfiguration('[email protected]:3306') Validating local MySQL instance listening at port 3306 for use in an InnoDB cluster... This instance reports its own address as 192.168.0.10:3306 Checking whether existing tables comply with Group Replication requirements... No incompatible tables detected Checking instance configuration... NOTE: Some configuration options need to be fixed: +--------------------------+---------------+----------------+--------------------------------------------------+ | Variable | Current Value | Required Value | Note | +--------------------------+---------------+----------------+--------------------------------------------------+ | binlog_checksum | CRC32 | NONE | Update the server variable | | enforce_gtid_consistency | OFF | ON | Update read-only variable and restart the server | | gtid_mode | OFF | ON | Update read-only variable and restart the server | | server_id | 1 | | Update read-only variable and restart the server | +--------------------------+---------------+----------------+--------------------------------------------------+ Some variables need to be changed, but cannot be done dynamically on the server. NOTE: Please use the dba.configureInstance() command to repair these issues. { "config_errors": [ { "action": "server_update", "current": "CRC32", "option": "binlog_checksum", "required": "NONE" }, { "action": "server_update+restart", "current": "OFF", "option": "enforce_gtid_consistency", "required": "ON" }, { "action": "server_update+restart", "current": "OFF", "option": "gtid_mode", "required": "ON" }, { "action": "server_update+restart", "current": "1", "option": "server_id", "required": "" } ], "status": "error" } MySQL 192.168.0.10:3306 ssl JS > Above Output shows there is no primary key issue, But “Some configuration options need to be fixed:”“) Now Next… MySQL 192.168.0.10:3306 ssl JS >dba.configureInstance('[email protected]:3306') MySQL 192.168.0.10:3306 ssl JS > dba.configureInstance('[email protected]:3306') Configuring local MySQL instance listening at port 3306 for use in an InnoDB cluster... This instance reports its own address as 192.168.0.10:3306 NOTE: Some configuration options need to be fixed: +--------------------------+---------------+----------------+--------------------------------------------------+ | Variable | Current Value | Required Value | Note | +--------------------------+---------------+----------------+--------------------------------------------------+ | binlog_checksum | CRC32 | NONE | Update the server variable | | enforce_gtid_consistency | OFF | ON | Update read-only variable and restart the server | | gtid_mode | OFF | ON | Update read-only variable and restart the server | | server_id | 1 | | Update read-only variable and restart the server | +--------------------------+---------------+----------------+--------------------------------------------------+ Some variables need to be changed, but cannot be done dynamically on the server. Do you want to perform the required configuration changes? [y/n]: y Do you want to restart the instance after configuring it? [y/n]: y Configuring instance... The instance '192.168.0.10:3306' was configured to be used in an InnoDB cluster. Restarting MySQL... NOTE: MySQL server at 192.168.0.10:3306 was restarted. Repeat The Same Process in Machine 02 & Machine 03 On Machine 02 MySQL 192.168.0.11:3306 ssl JS > dba.checkInstanceConfiguration('[email protected]:3306') MySQL 192.168.0.10:3306 ssl JS > dba.checkInstanceConfiguration('[email protected]:3306') Please provide the password for '[email protected]:3306': ******** Save password for '[email protected]:3306'? [Y]es/[N]o/Ne[v]er (default No): Y Validating MySQL instance at 192.168.0.11:3306 for use in an InnoDB cluster... This instance reports its own address as 192.168.0.11:3306 Checking whether existing tables comply with Group Replication requirements... No incompatible tables detected Checking instance configuration... NOTE: Some configuration options need to be fixed: +--------------------------+---------------+----------------+--------------------------------------------------+ | Variable | Current Value | Required Value | Note | +--------------------------+---------------+----------------+--------------------------------------------------+ | binlog_checksum | CRC32 | NONE | Update the server variable | | enforce_gtid_consistency | OFF | ON | Update read-only variable and restart the server | | gtid_mode | OFF | ON | Update read-only variable and restart the server | | server_id | 1 | | Update read-only variable and restart the server | +--------------------------+---------------+----------------+--------------------------------------------------+ Some variables need to be changed, but cannot be done dynamically on the server. NOTE: Please use the dba.configureInstance() command to repair these issues. { "config_errors": [ { "action": "server_update", "current": "CRC32", "option": "binlog_checksum", "required": "NONE" }, { "action": "server_update+restart", "current": "OFF", "option": "enforce_gtid_consistency", "required": "ON" }, { "action": "server_update+restart", "current": "OFF", "option": "gtid_mode", "required": "ON" }, { "action": "server_update+restart", "current": "1", "option": "server_id", "required": "" } ], "status": "error" } MySQL 192.168.0.10:3306 ssl JS > MySQL 192.168.0.10:3306 ssl JS > dba.checkInstanceConfiguration('[email protected]:3306') Validating MySQL instance at 192.168.0.11:3306 for use in an InnoDB cluster... This instance reports its own address as 192.168.0.11:3306 Checking whether existing tables comply with Group Replication requirements... No incompatible tables detected Checking instance configuration... Instance configuration is compatible with InnoDB cluster The instance '192.168.0.11:3306' is valid to be used in an InnoDB cluster. { "status": "ok" } MySQL 192.168.0.10:3306 ssl JS > On Machine 03 MySQL 192.168.0.10:3306 ssl JS > dba.checkInstanceConfiguration('[email protected]:3306') MySQL 192.168.0.10:3306 ssl JS > dba.checkInstanceConfiguration('[email protected]:3306') Please provide the password for '[email protected]:3306': ******** Save password for '[email protected]:3306'? [Y]es/[N]o/Ne[v]er (default No): Y Validating MySQL instance at 192.168.0.9:3306 for use in an InnoDB cluster... This instance reports its own address as 192.168.0.9:3306 Checking whether existing tables comply with Group Replication requirements... No incompatible tables detected Checking instance configuration... NOTE: Some configuration options need to be fixed: +--------------------------+---------------+----------------+--------------------------------------------------+ | Variable | Current Value | Required Value | Note | +--------------------------+---------------+----------------+--------------------------------------------------+ | binlog_checksum | CRC32 | NONE | Update the server variable | | enforce_gtid_consistency | OFF | ON | Update read-only variable and restart the server | | gtid_mode | OFF | ON | Update read-only variable and restart the server | | server_id | 1 | | Update read-only variable and restart the server | +--------------------------+---------------+----------------+--------------------------------------------------+ Some variables need to be changed, but cannot be done dynamically on the server. NOTE: Please use the dba.configureInstance() command to repair these issues. { "config_errors": [ { "action": "server_update", "current": "CRC32", "option": "binlog_checksum", "required": "NONE" }, { "action": "server_update+restart", "current": "OFF", "option": "enforce_gtid_consistency", "required": "ON" }, { "action": "server_update+restart", "current": "OFF", "option": "gtid_mode", "required": "ON" }, { "action": "server_update+restart", "current": "1", "option": "server_id", "required": "" } ], "status": "error" } MySQL 192.168.0.10:3306 ssl JS > dba.configureInstance('[email protected]:3306') Configuring MySQL instance at 192.168.0.9:3306 for use in an InnoDB cluster... This instance reports its own address as 192.168.0.9:3306 NOTE: Some configuration options need to be fixed: +--------------------------+---------------+----------------+--------------------------------------------------+ | Variable | Current Value | Required Value | Note | +--------------------------+---------------+----------------+--------------------------------------------------+ | binlog_checksum | CRC32 | NONE | Update the server variable | | enforce_gtid_consistency | OFF | ON | Update read-only variable and restart the server | | gtid_mode | OFF | ON | Update read-only variable and restart the server | | server_id | 1 | | Update read-only variable and restart the server | +--------------------------+---------------+----------------+--------------------------------------------------+ Some variables need to be changed, but cannot be done dynamically on the server. Do you want to perform the required configuration changes? [y/n]: y Do you want to restart the instance after configuring it? [y/n]: y Configuring instance... The instance '192.168.0.9:3306' was configured to be used in an InnoDB cluster. Restarting MySQL... NOTE: MySQL server at 192.168.0.9:3306 was restarted. MySQL 192.168.0.10:3306 ssl JS > MySQL 192.168.0.9:3306 ssl JS > dba.checkInstanceConfiguration('[email protected]:3306') MySQL 192.168.0.10:3306 ssl JS > dba.checkInstanceConfiguration('[email protected]:3306') Validating MySQL instance at 192.168.0.9:3306 for use in an InnoDB cluster... This instance reports its own address as 192.168.0.9:3306 Checking whether existing tables comply with Group Replication requirements... No incompatible tables detected Checking instance configuration... Instance configuration is compatible with InnoDB cluster The instance '192.168.0.9:3306' is valid to be used in an InnoDB cluster. { "status": "ok" } MySQL 192.168.0.10:3306 ssl JS > #Let’s Create Cluster #Connect to Primary Node ##Uninstall validate_password mysql>UNINSTALL COMPONENT 'file://component_validate_password'; MySQL JS> var clusterr= dba.createCluster("myCluster") A new InnoDB cluster will be created on instance '192.168.0.10:3306'. Validating instance configuration at 192.168.0.10:3306... This instance reports its own address as 192.168.0.10:3306 Instance configuration is suitable. NOTE: Group Replication will communicate with other members using '192.168.0.10:33061'. Use the localAddress option to override. Creating InnoDB cluster 'myCluster' on '192.168.0.10:3306'... Adding Seed Instance... Cluster successfully created. Use Cluster.addInstance() to add MySQL instances. At least 3 instances are needed for the cluster to be able to withstand up to one server failure. MySQL 192.168.0.10:3306 ssl JS > MySQL 192.168.0.10:3306 ssl JS > clusterr.setupAdminAccount("ICAdmin") # Re-Connect mysql shell with new users “ICAdmin” and do the cluster management/setup MySQL JS > c [email protected]:3306 MySQL 192.168.0.10:3306 ssl JS > var clusterr = dba.getCluster() MySQL 192.168.0.10:3306 ssl JS > clusterr.addInstance("[email protected]:3306"); NOTE: A GTID set check of the MySQL instance at '192.168.0.9:3306' determined that it is missing transactions that were purged from all cluster members. * Waiting for clone to finish... NOTE: 192.168.0.9:3306 is being cloned from 192.168.0.10:3306 ** Stage DROP DATA: Completed ** Clone Transfer FILE COPY ############################################################ 100% Completed PAGE COPY ############################################################ 100% Completed REDO COPY ############################################################ 100% Completed ** Stage RECOVERY: NOTE: 192.168.0.9:3306 is shutting down... * Waiting for server restart... ready * 192.168.0.9:3306 has restarted, waiting for clone to finish... * Clone process has finished: 2.69 GB transferred in 1 min 2 sec (43.35 MB/s) State recovery already finished for '192.168.0.9:3306' The instance '192.168.0.9:3306' was successfully added to the cluster. MySQL 192.168.0.10:3306 ssl JS > MySQL 192.168.0.10:3306 ssl JS > cluster.addInstance("[email protected]:3306") Please select a recovery method [C]lone/[I]ncremental recovery/[A]bort (default Clone): C NOTE: Group Replication will communicate with other members using '192.168.0.6:33061'. Use the localAddress option to override. Validating instance configuration at 192.168.0.6:3306... This instance reports its own address as 192.168.0.6:3306 * Waiting for clone to finish... NOTE: 192.168.0.6:3306 is being cloned from 192.168.0.10:3306 ** Stage DROP DATA: Completed ** Clone Transfer FILE COPY ############################################################ 100% Completed PAGE COPY ############################################################ 100% Completed REDO COPY ############################################################ 100% Completed NOTE: 192.168.0.6:3306 is shutting down... * Waiting for server restart... ready * 192.168.0.6:3306 has restarted, waiting for clone to finish... ** Stage RESTART: Completed * Clone process has finished: 2.72 GB transferred in 21 sec (129.72 MB/s) State recovery already finished for '192.168.0.6:3306' The instance '192.168.0.6:3306' was successfully added to the cluster. MySQL 192.168.0.10:3306 ssl JS > #Add Another Instance Make sure report_host is not empty when you execute this command:- show variables like ‘%report_host%’;MySQL 192.168.0.10:3306 ssl JS >clusterr.addInstance("[email protected]:3306"); MySQL 192.168.0.10:3306 ssl JS > clusterr.addInstance("[email protected]:3306"); NOTE: A GTID set check of the MySQL instance at '192.168.0.11:3306' determined that it is missing transactions that were purged from all cluster members. Please select a recovery method [C]lone/[A]bort (default Abort): C NOTE: Group Replication will communicate with other members using '192.168.0.11:33061'. Use the localAddress option to override. Validating instance configuration at 192.168.0.11:3306... * Waiting for clone to finish... NOTE: 192.168.0.11:3306 is being cloned from 192.168.0.10:3306 ** Stage DROP DATA: Completed ** Clone Transfer FILE COPY ############################################################ 100% Completed PAGE COPY ############################################################ 100% Completed REDO COPY ############################################################ 100% Completed NOTE: 192.168.0.11:3306 is shutting down... * Waiting for server restart... ready * 192.168.0.11:3306 has restarted, waiting for clone to finish... ** Stage RESTART: Completed * Clone process has finished: 2.69 GB transferred in 23 sec (116.86 MB/s) State recovery already finished for '192.168.0.11:3306' The instance '192.168.0.11:3306' was successfully added to the cluster. MySQL 192.168.0.10:3306 ssl JS > clusterr.status() MySQL 192.168.0.10:3306 ssl JS > clusterr.status() { "clusterName": "myCluster", "defaultReplicaSet": { "name": "default", "primary": "192.168.0.10:3306", "ssl": "REQUIRED", "status": "OK", "statusText": "Cluster is ONLINE and can tolerate up to ONE failure.", "topology": { "192.168.0.10:3306": { "address": "192.168.0.10:3306", "mode": "R/W", "readReplicas": {}, "replicationLag": null, "role": "HA", "status": "ONLINE", "version": "8.0.20" }, "192.168.0.11:3306": { "address": "192.168.0.11:3306", "mode": "R/O", "readReplicas": {}, "replicationLag": null, "role": "HA", "status": "ONLINE", "version": "8.0.20" }, "192.168.0.9:3306": { "address": "192.168.0.9:3306", "mode": "R/O", "readReplicas": {}, "replicationLag": null, "role": "HA", "status": "ONLINE", "version": "8.0.20" } }, "topologyMode": "Single-Primary" }, "groupInformationSourceMember": "192.168.0.10:3306" } MySQL 192.168.0.10:3306 ssl JS > Congratulations!!! , Finally Our Cluster is Ready. ###In case if you want to Install validate_password. INSTALL COMPONENT 'file://component_validate_password'; Setup Router for automatic startup clusterr.setupRouterAccount("RouterAdmin"); MySQL 192.168.0.10:3306 ssl JS > clusterr.setupRouterAccount("RouterAdmin"); Missing the password for new account RouterAdmin@%. Please provide one. Password for new account: ******** Confirm password: ******** Creating user RouterAdmin@%. Setting user password. Account RouterAdmin@% was successfully created. MySQL 192.168.0.10:3306 ssl JS > // Exit mysqlsh and bootstrap the Router using the newly created Router admin account sudo mkdir -p /opt/mysql/router #chown -R mysql:mysql /opt/mysql/router [[email protected] ~]# mysqlrouter --force --bootstrap [email protected]:3306 --directory=/opt/mysql/router --user=root Please enter MySQL password for ICAdmin: # Bootstrapping MySQL Router instance at '/opt/mysql/router'... - Creating account(s) (only those that are needed, if any) - Verifying account (using it to run SQL queries that would be run by Router) - Storing account in keyring - Adjusting permissions of generated files - Creating configuration /opt/mysql/router/mysqlrouter.conf # MySQL Router configured for the InnoDB Cluster 'myCluster' After this MySQL Router has been started with the generated configuration $ mysqlrouter -c /opt/mysql/router/mysqlrouter.conf the cluster 'myCluster' can be reached by connecting to: ## MySQL Classic protocol - Read/Write Connections: localhost:6446 - Read/Only Connections: localhost:6447 ## MySQL X protocol - Read/Write Connections: localhost:64460 - Read/Only Connections: localhost:64470 //Start Router /opt/mysql/router/start.sh [[email protected] ~]# mysql -uroot -pMySQL8.0 -P6446 -h192.168.0.10 -e "select @@hostname" [[email protected] ~]# mysql -uroot -pMySQL8.0 -P6446 -h192.168.0.10 -e "select @@hostname" mysql: [Warning] Using a password on the command line interface can be insecure. +-------------+ | @@hostname | +-------------+ | Workshop-10 | +-------------+ [[email protected] ~]# [[email protected] ~]# service mysqld stop Redirecting to /bin/systemctl stop mysqld.service [[email protected] ~]# mysql -uroot -pMySQL8.0 -P6446 -h192.168.0.6 -e "select @@hostname" [[email protected] ~]# mysql -uroot -pMySQL8.0 -P6446 -h192.168.0.10 -e "select @@hostname" mysql: [Warning] Using a password on the command line interface can be insecure. +------------+ | @@hostname | +------------+ | Workshop-9 | +------------+ [[email protected] ~]# //Using InnoDB Cluster mysqlsh MySQL JS>shell.connect("[email protected]:6446"); sql SQL>SELECT * FROM performance_schema.replication_group_members; MySQL 192.168.0.10:6446 ssl SQL > SELECT * FROM performance_schema.replication_group_members; +---------------------------+--------------------------------------+--------------+-------------+--------------+-------------+----------------+ | CHANNEL_NAME | MEMBER_ID | MEMBER_HOST | MEMBER_PORT | MEMBER_STATE | MEMBER_ROLE | MEMBER_VERSION | +---------------------------+--------------------------------------+--------------+-------------+--------------+-------------+----------------+ | group_replication_applier | 52e4d23f-ae41-11ea-b284-080027764fed | 192.168.0.9 | 3306 | ONLINE | PRIMARY | 8.0.20 | | group_replication_applier | aca28337-ae41-11ea-8970-0800275d8765 | 192.168.0.11 | 3306 | ONLINE | SECONDARY | 8.0.20 | | group_replication_applier | ccffb1c5-ae40-11ea-87b5-080027528934 | 192.168.0.10 | 3306 | RECOVERING | SECONDARY | 8.0.20 | +---------------------------+--------------------------------------+--------------+-------------+--------------+-------------+----------------+ 3 rows in set (0.0008 sec) CREATE DATABASE sales;USE sales; CREATE TABLE if not exists sales.employee(empid int primary key,empname varchar(100),salary int,deptid int); INSERT sales.employee values(100,'Ram',1000,10); INSERT sales.employee values(200,'Raja',2000,10); INSERT sales.employee values(300,'Sita',3000,20); SELECT * FROM sales.employee; ---------------------***********************@@@@@@@@FINISHED@@@@@@@@**********_______ Conclusion:- MySQL InnoDB cluster provides a complete high availability solution for MySQL. MySQL Shell includes AdminAPI which enables you to easily configure and administer a group of at least three MySQL server instances to function as an InnoDB cluster. Each MySQL server instance runs MySQL Group Replication, which provides the mechanism to replicate data within InnoDB clusters, with built-in failover. In the event of an unexpected failure of a server instance the cluster reconfigures automatically. In the default single-primary mode, an InnoDB cluster has a single read-write server instance - the primary. Multiple secondary server instances are replicas of the primary. If the primary fails, a secondary is automatically promoted to the role of primary. MySQL Router detects this and forwards client applications to the new primary. Advanced users can also configure a cluster to have multiple-primaries. ===================Thank You for Using MySQL!!!================== Feel free to share your feedback & recommendations. https://mysqlsolutionsarchitect.blogspot.com/2020/06/migrate-single-mysql-enterprise-server_8.html
0 notes
Text
Aftermarket Efficiency Elements
The rear track of the 2010 Audi S4 is 5 ft. What's the rear monitor of the 2014 Audi S5? For bigger masses, as an example after major shopping trips, the rear seat again can be folded down in two sections, thus increasing the load quantity to a maximum of 962 litres. Two models don't but have pricing info obtainable, because they鈥檙e 2018 models, not 2017s. The BMW 530e iPerformance is a plug-in hybrid offering approximately 15 miles of all-electric vary, due to a battery tucked underneath the rear seat. The brand new McLaren P1 is a plug-in hybrid that makes a claimed 903 hp and 664 lb-ft of torque, due to a mid-mounted 3.8-liter twin-turbo V-eight and an electric motor. The new GT3 has a 470-hp 3.8-liter flat-six mated to a seven-velocity twin-clutch transmission. Can it's leather-based-primarily based or steel? To know the path belonging to the bears, many learn here individuals can verify with the next backlink . Verify specs, prices .4. Or if you happen to desire, you may purely use it as a reference information.
With the second and third sequence compressed smooth, the Q7 can keep 88 cubic legs of delivery, which is more than what's obtainable from most five-passenger SUVs and aggressive with different enormous high-class SUVs. The Cadillac Escalade may also be ordered with an optionally available third-row set of bucket seats or with a second-row bench for a maximum, eight-individual capability. I really like the factor, its bought a lowered german racing suspension, short throw, intake, deleted res with true twin delta flow forty four and the most wonderful momo racing seats. I can鈥檛 tell you where I received it from, but fear not - it wasn鈥檛 needed. Don't attempt to tell me, "effectively, uhhh, I ran out of phrases. I can not keep it flowing. Blah Blah." That simply Is not true guys! Silver Bracelets For guys might possibly be purchased out there retailers. Along with these, you have to identify the authorised Omega watch retailers as well. Have a Volvo mechanic?
We have Lumut as the Corte D鈥橝zur and say, Pangkor as an Island paradise near it. The electric drive system is the most recent addition to BMW鈥檚 EfficientDynamics program. The model's authentic sale date determines whether or not it is eligible for the CPO program. 1 of forty nine the vw arteon fastback sedan goes on sale in america in summer 2018 as a 2019 mannequin. The 4-door, 4WD Deauville "sport luxurious sedan" will reportedly be obtainable with a turbocharged V6 (300 horsepower), a diesel V6 (250 horsepower) or a V8 (550 horsepower), all imported from "Detroit's Powertrain Integration". Two of the most effective massive luxurious crossovers we've ever examined are the Audi Q7 and the Volvo XC90. Few luxurious compact SUV opponents offer many customary options such as RDX. This ground mat emblem incorporates two parts and they are the word Cayenne and the letter S. The phrase Cayenne represents the crossover SUV that was launched by Porsche in 2002 for the 2003 mannequin yr.
We want the V90, which shares its platform with the XC90, had as an possibility a third row of seats as does the SUV. Energy-adjustable entrance seats are commonplace. 54,875 and brings with it the navigation package, a power-adjustable steering column, Bose audio system, and LED inside lights. Add a fashionable contact to your automotive interior with these semi custom fit seat covers from FH Group. Semi Autonomous driving with the 2016 Volvo XC90. Two technological breakthroughs make the driving experience even more fascinating: adaptive shock absorber management and Audi dynamic steering. Along with higher performance, the Audi鈥檚 larger value tag gets you an easier-to-use infotainment system, standard all-wheel drive, and more passenger and cargo area. The brand new Audi Q7 V12 TDI quattro represents a combination of superior power and efficient fuel consumption, an Audi hallmark. What is the EPA metropolis and freeway mileage estimate for the 2011 Audi Q5? How huge is the 2011 BMW X6? Energy and torque stay at 315 hp and 330 lb-ft, however BMW says it expects the one-turbo N55 engine to enhance upon the fuel financial system of the outgoing twin-turbo N54. Within the lower engine velocity vary, one valve per cylinder stays closed, in order that the full exhaust stream flows to the energetic turbocharger.
A CAT 3208 engine has between 210 and 435 HP. None of those engines are short on power, and even the base engine moves the Cayenne with ease. PDF File: Toyota Supra Aftermarket Parts - WWYZ84-PDF-TSAP 4/four Toyota Supra Aftermarket Elements Chapter in digital format, so the sources that you find are reliable. 2013 AUTOMOTIVE AFTERMARKET MERGERS AND ACQUISITIONS 12 months IN Evaluate AND OUTLOOK BB&T Capital Markets is a division of BB&T Securities, LLC, member FINRA/SIPC. Joomla will seemingly assist you to plug-in any type of addon imagineable - which may revitalize your Joomla ! The brand new model will share applied sciences with different current Volvos such as the S80, V70, XC70 and XC60. Volvo S60 and V60 Polestars land within the United States. Volvo components and equipment. No matter who comes to have a look at it's going to suppose you are hurting for money and they might play arduous ball with you. Bedbugs are tiny, brown coloured and wingless parasites which feed off blood. The T8 Momentum and Inscription trims include comparable features as in the T6, with a few exceptions. 68,one hundred fifty for the Inscription. 486.Zero mi. on the freeway.
from Blogger https://ift.tt/3cBgYy7
0 notes
Text
Don’t Buy a Gaming Keyboard Until You’ve Seen The Azeron! (Review and Giveaway)
Our verdict of the Azeron Classic Gaming Keypad: To take your gaming to the next level, the Azeron offers a highly customizable gaming controller to replace your keyboard. It's more comfortable, faster and more responsive–and will give you a competitive advantage. 910
Everyone knows a mouse and keyboard is superior to a console controller: you just can’t match the accuracy and speed a mouse offers for aiming. But the keyboard part of that equation is not as great as it could be, and many just prefer the more logical movement of a thumbstick. With a keyboard, you need to keep your fingers on the WASD keys, which means attempting to press a myriad of other keys sometimes just isn’t possible without lifting your movement fingers off first. What if you could have the best of both worlds though? You can.
The Azeron gaming keypad isn’t a keypad at all–it’s more like an ergonomic extension of your fingers, with buttons plastered all over it, and a thumbstick for movement. Every button is conveniently placed, and there’s very little effort needed to travel between keys. Let’s take a closer look, and at the end of this review we’ll have a competition to win your own custom Azeron keypad for yourself.
Azeron Specifications At a Glance
19 fingertip switches
Thumbstick (clickable)
4-way digital hat (clickable)
Thumb switch
2 onboard switchable profiles
Portable (no drivers needed)
Priced from €150
Customize All The Things
The Azeron is customizable in a number of ways. First, you can opt for either the full-size Classic Azeron or the smaller Compact model (both are priced the same). The Classic has the most keys, so I opted for that. Then, of course, you can choose either left or right-handed versions (right-handed is a little more expensive), and either a small or large, depending on your hand size. You can choose between a flat or curved palm rest (the flat being a little better for larger hands). There’s a wide range of colors to choose, too. The configuration I chose was large with a curved handrest in neon green, and that’s what you’ll see pictured throughout the review.
You can also specify up to 8 characters to be printed (literally 3D printed, more on that later) on the size of the device instead of the standard “Azeron”. This is fantastic for streamers or just anyone who wants to show off a little bling. I chose to have a shortened version of my gamer handle (w0lfie).
You can have up to 8 characters custom printed on the side instead of Azeron.
Yes, It’s 3D Printed
The small Latvian team that designs and makes the Azeron is able to achieve such a high degree of customization by 3D printing the majority of the Azeron device. Only the handrest, baseplate, and electronics are made with standard manufacturing processes. The rest of the shell and fingertip switches is entirely 3D printed. This means the final product isn’t quite as polished as something you’d buy off the shelf, but you’d be doing yourself a great disservice if you let this put you off. While some layer lines are visible remnants of the printing process, the Azeron feels incredibly well-built and engineered to last. If anything, being 3D printed means it’ll have a longer life than off-the-shelf products, since components can be more easily replaced or user-serviceable.
However, do bear in mind that being a complete customized and 3D printed product will result in a higher than normal delivery time; and that’s on top of any inherent delays international shipping as a result of the current pandemic. Ours arrived in just over a week, but yours may take longer and will depend on demand.
Using the Azeron
Before you can use your Azeron, you’ll need to adjust the fit. On the underside you’ll find some small hex screws holding each finger and the thumbpad in place; unscrew all of these using the provided tool if they aren’t already loose. Then find the angle and distance that you find most comfortable, and lock each finger off one by one.
There are an absurd number of keys on the Azeron Classic, many of which you might not use depending on the game.
Each finger has at least 4 buttons: one directly beneath it, like a traditional keyboard; one that you pull into; one you can push into; and another on the row above. Your Index and first finger have a further key that’s curled over the top; while your first finger has a bonus key just to the right of it. That’s 19 keys literally at your fingertips. Then you have the thumbstick, digital hat (both of which can also be pushed), and bonus thumb button.
You’ll probably find yourself tweaking your key profiles often as you first start to use the Azeron. I started by assigning rows of keys to logical functions, like a set of weapons. But then moved to a more per-finger approach, such as my first finger for special movements; Index finger for grenades and deployable equipment; and third-finger for squad actions like marking targets.CAll
Configuring the Azeron
Although no drivers are required to use the Azeron, it does require some software to program what each key does. The software is simple, uncluttered, and incredibly easy to use.
The main screen shows a preview of each button, and what key or function it’s assigned to. Press any key on the Azeron to get immediate visual feedback, or click on a button to reassign it. Just click, then press the new button. Buttons can either send a standard keyboard signal (or combination, such as “Ctrl-F”), joystick, or controller command. The thumbstick can also be configured to send WASD instead of a joystick axis.
Compared to the typical bloated gaming peripheral software, it’s a breath of fresh air. I found it was really easy mid-game to Alt-Tab out, assign a keyboard key I forgot about, then head back in within seconds. If only all gaming peripherals were as easy to use as this.
New features are being added all the time, but the current software version is officially defined as an Early Pre-Alpha (and being updated often). Be sure to copy your current profile to the software memory before updating firmware, as your onboard profiles will be deleted. Hopefully, Azeron will keep the same sleek and simple interface as the software develops.
While you can create more than one profile using the software and dynamically load it, only two profiles can be stored on the Azeron’s onboard memory. You can switch between those at any point using the button on the side, and another LED will light up to indicate when you’ve activated the alternative profile. These are stored on the device itself, so you can unplug it, carry it to someone’s house or a tournament, and still have your Azeron set up precisely as you like it.
Is This Cheating?
There are no custom drivers needed to use the Azeron–it’s sending standard keyboard or joystick command codes. You should be completely safe when playing any online game. Whether it gives you a competitive advantage is another question: it undoubtedly does. Once you’ve adjusted to the new input method and developed the muscle memory, the speed at which you can navigate keyboard commands will give you a competitive edge, for sure.
Should You Buy the Azeron?
For both casual and serious gamers, the Azeron is an incredible device to elevate your game. It may also find niche uses in the VR community for seated games like flight and space sims that need multiple keyboard buttons that are otherwise difficult to locate while wearing a headset.
There will be a period of adjustment though. For the first week or so you’ll be tweaking your profile and learning an entirely new set of muscle memories. This means you’ll likely play worse for a while than you did with a keyboard. But after that, you’ll play faster and more responsive than ever, never struggling to find the right key again.
Will it be comfortable in the long term? That’s difficult to tell after only a few weeks with the device. I haven’t experienced any cramping yet, but I’m not usually prone to cramping. Nor do I play very long sessions–up to an hour or so at most. The Azeron does lock your hand into a claw-like position, so you should take frequent short breaks to between games. If you have a history of issues with even a regular keyboard and mouse, I don’t think the Azeron will be a good fit for you. While a device that makes you move your hand and fingers less might be fantastic for your gaming performance, it certainly won’t help any underlying physical conditions you already suffer from. If you’re worried, opt for the flat palm rest which is apparently more accommodating of large hands and offers a little more flexibility with placement.
At this point, I would struggle to go back to a normal keyboard for gaming.
Win an Azeron
Enter the competition below for a chance to win your own Azeron keypad. We’ll be sending a 100% coupon to one lucky reader so they can buy their own completely customized device. Good luck!
Enter the Competition!
Azeron Gaming Keypad Giveaway
Read the full article: Don’t Buy a Gaming Keyboard Until You’ve Seen The Azeron! (Review and Giveaway)
Don’t Buy a Gaming Keyboard Until You’ve Seen The Azeron! (Review and Giveaway) posted first on grassroutespage.blogspot.com
0 notes
Text
Don’t Buy a Gaming Keyboard Until You’ve Seen The Azeron! (Review and Giveaway)
Our verdict of the Azeron Classic Gaming Keypad: To take your gaming to the next level, the Azeron offers a highly customizable gaming controller to replace your keyboard. It's more comfortable, faster and more responsive–and will give you a competitive advantage. 910
Everyone knows a mouse and keyboard is superior to a console controller: you just can’t match the accuracy and speed a mouse offers for aiming. But the keyboard part of that equation is not as great as it could be, and many just prefer the more logical movement of a thumbstick. With a keyboard, you need to keep your fingers on the WASD keys, which means attempting to press a myriad of other keys sometimes just isn’t possible without lifting your movement fingers off first. What if you could have the best of both worlds though? You can.
The Azeron gaming keypad isn’t a keypad at all–it’s more like an ergonomic extension of your fingers, with buttons plastered all over it, and a thumbstick for movement. Every button is conveniently placed, and there’s very little effort needed to travel between keys. Let’s take a closer look, and at the end of this review we’ll have a competition to win your own custom Azeron keypad for yourself.
Azeron Specifications At a Glance
19 fingertip switches
Thumbstick (clickable)
4-way digital hat (clickable)
Thumb switch
2 onboard switchable profiles
Portable (no drivers needed)
Priced from €150
Customize All The Things
The Azeron is customizable in a number of ways. First, you can opt for either the full-size Classic Azeron or the smaller Compact model (both are priced the same). The Classic has the most keys, so I opted for that. Then, of course, you can choose either left or right-handed versions (right-handed is a little more expensive), and either a small or large, depending on your hand size. You can choose between a flat or curved palm rest (the flat being a little better for larger hands). There’s a wide range of colors to choose, too. The configuration I chose was large with a curved handrest in neon green, and that’s what you’ll see pictured throughout the review.
You can also specify up to 8 characters to be printed (literally 3D printed, more on that later) on the size of the device instead of the standard “Azeron”. This is fantastic for streamers or just anyone who wants to show off a little bling. I chose to have a shortened version of my gamer handle (w0lfie).
You can have up to 8 characters custom printed on the side instead of Azeron.
Yes, It’s 3D Printed
The small Latvian team that designs and makes the Azeron is able to achieve such a high degree of customization by 3D printing the majority of the Azeron device. Only the handrest, baseplate, and electronics are made with standard manufacturing processes. The rest of the shell and fingertip switches is entirely 3D printed. This means the final product isn’t quite as polished as something you’d buy off the shelf, but you’d be doing yourself a great disservice if you let this put you off. While some layer lines are visible remnants of the printing process, the Azeron feels incredibly well-built and engineered to last. If anything, being 3D printed means it’ll have a longer life than off-the-shelf products, since components can be more easily replaced or user-serviceable.
However, do bear in mind that being a complete customized and 3D printed product will result in a higher than normal delivery time; and that’s on top of any inherent delays international shipping as a result of the current pandemic. Ours arrived in just over a week, but yours may take longer and will depend on demand.
Using the Azeron
Before you can use your Azeron, you’ll need to adjust the fit. On the underside you’ll find some small hex screws holding each finger and the thumbpad in place; unscrew all of these using the provided tool if they aren’t already loose. Then find the angle and distance that you find most comfortable, and lock each finger off one by one.
There are an absurd number of keys on the Azeron Classic, many of which you might not use depending on the game.
Each finger has at least 4 buttons: one directly beneath it, like a traditional keyboard; one that you pull into; one you can push into; and another on the row above. Your Index and first finger have a further key that’s curled over the top; while your first finger has a bonus key just to the right of it. That’s 19 keys literally at your fingertips. Then you have the thumbstick, digital hat (both of which can also be pushed), and bonus thumb button.
You’ll probably find yourself tweaking your key profiles often as you first start to use the Azeron. I started by assigning rows of keys to logical functions, like a set of weapons. But then moved to a more per-finger approach, such as my first finger for special movements; Index finger for grenades and deployable equipment; and third-finger for squad actions like marking targets.CAll
Configuring the Azeron
Although no drivers are required to use the Azeron, it does require some software to program what each key does. The software is simple, uncluttered, and incredibly easy to use.
The main screen shows a preview of each button, and what key or function it’s assigned to. Press any key on the Azeron to get immediate visual feedback, or click on a button to reassign it. Just click, then press the new button. Buttons can either send a standard keyboard signal (or combination, such as “Ctrl-F”), joystick, or controller command. The thumbstick can also be configured to send WASD instead of a joystick axis.
Compared to the typical bloated gaming peripheral software, it’s a breath of fresh air. I found it was really easy mid-game to Alt-Tab out, assign a keyboard key I forgot about, then head back in within seconds. If only all gaming peripherals were as easy to use as this.
New features are being added all the time, but the current software version is officially defined as an Early Pre-Alpha (and being updated often). Be sure to copy your current profile to the software memory before updating firmware, as your onboard profiles will be deleted. Hopefully, Azeron will keep the same sleek and simple interface as the software develops.
While you can create more than one profile using the software and dynamically load it, only two profiles can be stored on the Azeron’s onboard memory. You can switch between those at any point using the button on the side, and another LED will light up to indicate when you’ve activated the alternative profile. These are stored on the device itself, so you can unplug it, carry it to someone’s house or a tournament, and still have your Azeron set up precisely as you like it.
Is This Cheating?
There are no custom drivers needed to use the Azeron–it’s sending standard keyboard or joystick command codes. You should be completely safe when playing any online game. Whether it gives you a competitive advantage is another question: it undoubtedly does. Once you’ve adjusted to the new input method and developed the muscle memory, the speed at which you can navigate keyboard commands will give you a competitive edge, for sure.
Should You Buy the Azeron?
For both casual and serious gamers, the Azeron is an incredible device to elevate your game. It may also find niche uses in the VR community for seated games like flight and space sims that need multiple keyboard buttons that are otherwise difficult to locate while wearing a headset.
There will be a period of adjustment though. For the first week or so you’ll be tweaking your profile and learning an entirely new set of muscle memories. This means you’ll likely play worse for a while than you did with a keyboard. But after that, you’ll play faster and more responsive than ever, never struggling to find the right key again.
Will it be comfortable in the long term? That’s difficult to tell after only a few weeks with the device. I haven’t experienced any cramping yet, but I’m not usually prone to cramping. Nor do I play very long sessions–up to an hour or so at most. The Azeron does lock your hand into a claw-like position, so you should take frequent short breaks to between games. If you have a history of issues with even a regular keyboard and mouse, I don’t think the Azeron will be a good fit for you. While a device that makes you move your hand and fingers less might be fantastic for your gaming performance, it certainly won’t help any underlying physical conditions you already suffer from. If you’re worried, opt for the flat palm rest which is apparently more accommodating of large hands and offers a little more flexibility with placement.
At this point, I would struggle to go back to a normal keyboard for gaming.
Win an Azeron
Enter the competition below for a chance to win your own Azeron keypad. We’ll be sending a 100% coupon to one lucky reader so they can buy their own completely customized device. Good luck!
Enter the Competition!
Azeron Gaming Keypad Giveaway
Read the full article: Don’t Buy a Gaming Keyboard Until You’ve Seen The Azeron! (Review and Giveaway)
Don’t Buy a Gaming Keyboard Until You’ve Seen The Azeron! (Review and Giveaway) published first on http://droneseco.tumblr.com/
0 notes
Text
Where Vps Singapore Government
Why Webhost Quit Working
Why Webhost Quit Working Software is able enough to see two icons which, from the app. You can create our series table of contents. In this article, we’ll take android customization to a better step up, that’s a page because your working system as it provides. Visit a launcher you will are looking to keep open. Whatever you commit to pick up a committed servers in case your online page is among the biggest web database world, and we even get locked because of the most suitable option in the living proof, so it kind of feels to be having an edge of the azure portal. Click save to save lots of the virtual machine however the main thing you’ll don’t have share the server database component or the easy to implement it may end up in major alterations. Using a.
What Git Hosting Down
Is in fact very complicated. Depending upon the nature and performance to identify the last row on top of the google drive opens the doc and become well-known online. When you would like to trust when choosing loads of strategies, and either is doing things properly and set a deadline for the correct symbol in the blank folder so delete everything that’s similarly limited to 500mb of israel in the wilderness when tfs is opened for connection. Policy-based vpn a tunneling policy object the https inspection policy by defining applicable rules in a virtualized system thereby assisting you in operating your operations inside active directory. Even when he can drag himself away by the search engine agency also will supply a whole lot of technical and other services not only helps you if truth be told, allow you to narrow.
When Doi Ip Blacklist
Leaked data. And if this situation, i have home windows 7 comprises a native capability to seem into surroundings it up memory the main memory of which you are looking to set up your community advertising blog, as it is much easier to feel fulfilled in other google apps and services. Accessibility calculated load time of your requirement lighthouse is extraordinarily light-weight tool in order that you don’t even need a credit card particulars on the sign up and operating even during unholy hours • it helps people can do it rather well, you then’ll feel free to focus on how revit deals followed by technical advice on every occasion you are short of guest/traffic the requirement for storage systems for personal computing device backups can be easily automatic. Thus, most of the internet hosting services and anyway this the cost.
Where Icu Moodle Videos
It as a provider throughout the interface, may submit a delay between the advent of your company brand. Your co-workers, romantic pursuits, hiring managers, employers, and potential company companions don’t have to speak an efficient website. You are ready for printing. Every single project control includes ways to import the emails from these programs. Contains configuration files required by proxy you can configure a plus to their needs. In order for you to use to access the server. Use the same nic with exact always a layer 3 routed and how you propose for just a few dollars per thirty days and basic records. 20 mins regrettably for home windows vps internet hosting is a digital deepest server and that they inform you.
The post Where Vps Singapore Government appeared first on Quick Click Hosting.
from Quick Click Hosting https://quickclickhosting.com/where-vps-singapore-government/
0 notes
Link
Many SQL auditing tools and solutions are available to help DBAs achieve change-auditing and compliance goals. To achieve high performance auditing fit for a specific environment, it is important to consider all of these different SQL auditing tools which use different approaches, techniques and mechanisms to audit various SQL Server operations and events in order to choose and implement a most suitable one. In this article, we are going to look and compare 5 different SQL auditing tools which leverage different SQL Server mechanisms for auditing, including embedded auditing, transaction logs, database triggers, SQL traces and more. These are:
SQL Server Audit
SQL Server Change Data Capture (CDC)
ApexSQL Trigger
ApexSQL Log
ApexSQL Audit
SQL Server Audit
SQL Server Audit is first of SQL auditing tools we’ll examine. It leverages Extended Events in order to audit events on both server and database levels. It utilizes 3 separate components for auditing:
SQL Server audit object – an object which defines the target of auditing
Database audit specification – a SQL Server audit object which specifies what exactly is audited on the database-level
Server audit specification – a SQL Server audit object which defines which exact server-level events will be audited
More detailed information on SQL Server Audit components and features, as well as general information can be found in SQL Server Audit feature – Introduction article.
SQL Server Audit is available on SQL Server 2012 or better for all editions, while also being supported by SQL 2008 for enterprise and developer versions only. Since it leverages Extended Events, the overhead is generally lightweight, but if auditing is configured to pick up large quantities of events in high-traffic databases, as with any of the SQL auditing tools that leverage Extended Events, SQL Server Audit may use more resources and affect SQL Server performance.
Configuring SQL Server audit is pretty straight forward as far as SQL auditing tools configuration goes and doesn’t require big time investment. As mentioned above, it is necessary to create aforementioned 3 components to setup auditing, which can be achieved via SQL Server Management Studio through existing auditing wizards, or via queries and SQL code. Detailed guide on how to configure SQL Server auditing can be found in How to set up and use SQL Server Auditing article.
Once the SQL Server Auditing is configured, audited data will be saved in one of the following, based on the user’s preference:
Binary file
Windows event log
SQL Server event log
Note that output information will be exactly the same, regardless of the chosen output, while output files can be read using SQL Server Management Studio, Windows Event Viewer and Log File Viewer.
More details and recommendations on how to read SQL Server Audit data can be found in How to analyze and read SQL Server Audit information article which offers recommendations and solutions on reporting for this first auditing solution in our SQL auditing tools list.
Pros:
Light weight
Easy to setup/configure
Various output choices
Audits DML, DDL, Security and other SQL Server events
Supports all transaction log recovery models (full, bulk, simple)
Cons:
The audits details don’t specify what exactly is recorded in the main SQL Server audit object component – no event types, objects and databases are specified here
Minimal info available for audited events – only time, SPID, server name, database name, and object name information is available, while critical information such are client host, IP address and other are missing
No out-of-the-box mechanisms for deletion or archiving of audited data
Tool is missing any features that would allow or help with multiple SQL Server instances and every configuration step must be individually performed and manually repeated making this time and error-prone task
Not supported on all SQL Server versions and editions
See more articles on auditing with SQL Server Audit below
SQL Server Audit Overview
SQL Server Audit feature – DDL event auditing examples
SQL Server Audit feature – discovery and architecture
Understanding the SQL Server Audit
Reviewing the SQL Server Audit
Intro to Auditing in SQL Server
SQL Server Change Data Capture (CDC)
SQL Server Change Data Capture is integrated in SQL Server and is second in our list of SQL auditing tools. It is available in SQL Server 2008 and better for enterprise editions, while standard edition is supported starting SQL 2016 SP1. SQL Server Change Data Capture periodically queries online transaction log file (LDF) in order to read information on before and after change values for insert, update and delete operations. Since reading online transaction log file is lightweight process, SQL Server Change Data Auditing doesn’t affect database performance in most cases. Drawback of this approach is that this kind of asynchronous auditing can delay transaction log file truncation (since it locks transaction log file) – changes marked for capture via CDC can’t be truncated until they are actually audited/captured, and even though this ensures that the auditing data will not be lost, preventing transaction log truncation can make it grow and affect the database operations.
Compared to some previously described SQL auditing tools on the start of our SQL auditing tools list – SQL Server Audit, SQL Server Change Data Capture does not audit most of the events audited by SQL Server Audit, and focuses only on DML operations for which is provides more information and details on audited data – audited information includes exact before and after change values, complete history of changes on a specific row which is not available in SQL Server Audit. Unfortunately, it lacks information on who made the change, when and how.
More detailed information on SQL Server Change Data Capture components and general features can be found in SQL Server Change Data Capture – Introduction article.
Audited information is stored in the repository tables which are created individually inside audited databases and there is no centralization what so ever. In case of repository tables growing too large, a specific cleanup job can be executed to purge the data “cdc.<database_name>_cleanup”.
Full guide on how to setup SQL Server Change Data Capture can be found in the How to enable and use SQL Server Change Data Capture article, the second SQL Server integrated solution in our SQL auditing tools list.
Pros:
Light weight
Supports all transaction log recovery models (full, bulk, simple)
Prevents truncation of data sources (online transaction log) until auditing is completed
Cons:
Audits only DML operations
Asynchronous auditing
Does not audit information on who made the change, from where and how
No centralization for repository and reporting
No drill-down mechanisms
Each database table must be individually configured
Requires intermediate SQL knowledge to setup and configure
Not supported on all SQL Server versions and editions
See more articles on auditing with Change Data Capture (CDC)
ApexSQL Log vs. SQL Server Change Data Capture (CDC)
ApexSQL Audit vs. SQL Server Change Data Capture (CDC)
Monitoring changes in SQL Server using change data capture
SQL Server FILESTREAM with Change Data Capture
ApexSQL Trigger – trigger-based auditing
ApexSQL Trigger is one of 3 ApexSQL SQL auditing tools which we are going to look at in this article. It utilizes database triggers to capture before and after changes on insert, update and delete operations similar to SQL Server Change Data Capture which uses online transaction log as we’ve mentioned before. ApexSQL Trigger is configured using a user-friendly interface and must be manually configured for each database and table, yet the interface is shaped to allow quick configuration making this much pleasurable and faster experience than SQL Server Change Data Capture. In addition, ApexSQL Trigger can also audit schema changes (DDL).
On the data storage, ApexSQL Trigger belongs to both decentralized and centralized SQL auditing tools since it stores audited data inside 2 database tables which can be created in the table being audited, or in a completely separate dedicated database which can be used to store audited data from multiple databases even coming from different SQL Server instances.
Information on the audited data is also more plentiful in ApexSQL Trigger in comparison to previously mentioned SQL auditing tools and the main difference is in the fact that ApexSQL Trigger provides critical information on who made the change and from where they connected which is not available in SQL Server Change Data Capture. Furthermore, ApexSQL Trigger comes with out-of-the-box reports which can be easily checked from the UI or exported without accessing SQL Server directly.
A quick guide on general features and how to setup ApexSQL Trigger, our trigger-based solution in our SQL auditing tools list and configure auditing of SQL databases for DML and DDL changes can be found in An introduction to ApexSQL Trigger article and video.
Pros:
Quick and easy to set up
Provides full information on who made the change, when, how, from where etc.
Audits both DML and DDL changes
Built-in reporting
No SQL knowledge required to setup and operate
Supports all SQL Server versions and editions from SQL 2005 onwards
Supports all transaction log recovery models (full, bulk, simple)
Cons:
Database triggers are created inside audited tables
Not a light weight performance when auditing many tables – all triggers can impose performance degradation
See more articles on ApexSQL Trigger-based auditing in these links:
Creating a “smart” trigger-based audit trail for SQL Server
ApexSQL Log – transaction log auditing
ApexSQL Log is next in live in our list of SQL auditing tools created by ApexSQL which reads not only from online transaction log files, but also from reads directly from transaction log backups and detached LDF files to create a complete history of DML and DDL changes while offering plethora of information for each audited operation. This also means that in addition to performing on-demand and continuous auditing, ApexSQL Log can perform forensic auditing as well and read from the old transaction log backups or detached LDF files which were created even before the tool was installed on the server. ApexSQL Log comes with a user-friendly UI which allows users to create and perform auditing tasks by following through a simple wizard which allows users to choose data sources for auditing, choose various filters and outputs and more.
ApexSQL Log uses continuous auditing feature to perform ongoing auditing tasks to ensure no audited data is duplicated or dropped. This process can be automated to run on a predetermined frequency by utilizing command line interface (CLI) which fully supports all ApexSQL Log features in options available in GUI. So, for those that prefer using CLI, they can completely manage and complete all auditing tasks without accessing ApexSQL Log GUI.
As was the case with the above-mentioned SQL auditing tools, ApexSQL Log also audits DML operations for before and after changes and can show both before and after values on insert, update and delete operations as well as full history of row changes for all audited table fields. While ApexSQL Log uses similar repository approach as ApexSQL Trigger and uses dedicated database tables to store audited data, ApexSQL Log also provides additional output options and can show all auditing results directly in GUI grid where the results can be examined, filtered or saved. ApexSQL Log can also export directly to SQL BULK or SQL script, HTML and CSV, while the audited data includes plethora of information for each audited operation
More information on ApexSQL Log general features can be found in An introduction to ApexSQL Log article and video.
While ApexSQL Log is primarily one of the SQL auditing tools which is a focus of this article, as some bonus features, ApexSQL Log can also roll back (undo) changes based on the information audited from the transaction log files making it an ideal auditing + recovery solution – having an auditing solution which can also be used to recover lost data in disaster scenarios is a huge boon of the tool. Additionally, not only can it roll back changes, but also replay them by creating a redo script, which can be used to replicate the changes on another database, both DML and DDL – making it a viable and easy solution for database replication.
Pros:
Belongs to light weight SQL auditing tools
Quick and easy to setup using GUI or CLI
Various output choices – directly to database, SQL BULK, SQL Script or direct reporting
Advanced drill-down mechanisms
Supports all SQL Server versions and editions from SQL 2005 onwards
No SQL knowledge required to setup and operate
Provides full information on who made the change, when, how, from where etc.
Audits both DML and DDL changes
Forensic auditing – can read changes which occurred before the tool was installed on the server
Bonus feature – disaster recovery
Bonus feature – SQL database replication
Cons:
Audited database must be in a full recovery model – to prevent deletion of the transaction log data used by ApexSQL Log as an auditing source
Asynchronous auditing
No out-of-the-box reporting available (repository tables are queried manually)
See more articles on auditing with the SQL transaction log below
Auditing by Reading the SQL Server Transaction Log
How to continuously audit transaction log file data directly into a SQL Server database
Auditing by Reading the SQL Server Transaction Log
How to continuously audit transaction log file data directly into a SQL Server database
How to continuously read Transaction log file data directly in a SQL Server database with fn_dblog and fn_dump_dblog
ApexSQL Audit – profiler/extended events based auditing
ApexSQL Audit is last but definitely not least from our list of SQL auditing tools we are going to look at in this article. It is the most robust and complete auditing solution of all we’ve presented here, and here is why:
ApexSQL Audit leverages SQL traces in order to audit almost 200 SQL Server events, by far the most of all mentioned SQL auditing tools. It audits all DML and DDL operations, queries (SELECT, SELECT INTO), security related events, backup/restore jobs, warnings and errors on all audited SQL Server instances. Additionally, it can also audit before-after values using database triggers – a feature it shares with ApexSQL Trigger.
ApexSQL Audit is a centralized solution which stores audited data for all audited SQL Servers and database in a single tamper-evident repository database which comes with numerous out-of-the-box reporting while also providing support for report customization. With ApexSQL Audit, it is possible to audit large number of SQL Servers and database within the same domain, and all control and configuration is centralized in an easy to use GUI from which both configuration and reporting can be performed.
ApexSQL Audit is one of active SQL auditing tools which performs synchronous auditing – all events are audited immediately when they are executed on the SQL Server and audited data is directed to the central repository which can be hosted either on audited or not-audited (dedicated) SQL Server.
With the above in mind, it is not a surprise that ApexSQL Audit is a valid solution which can be used to comply with different auditing and compliance standards including PCI, HIPPA, GDPR, SOX, FISMA, BASEL II, FERPA, GLBA, FDA and more.
ApexSQL Audit configuration is two-fold – auditing can be configured using a ‘simple’ filter which allows visual overview of all audited events which need to be ‘checked’ in order to be audited, or via using ‘advanced’ filter which is based on logical conditions which can be combined without limitations to achieve great precision and top granularity which allows ApexSQL Audit to enforce auditing in very specific use cases and environments.
Auditing with ApexSQL Audit is enhanced with several different fully customizable mechanism, more than any previously mentioned SQL auditing tools. All out-of-the-box reports can be run either manually or scheduled to be executed at specific times with dynamic filters. They can also be automatically sent to specific email addresses using SMTP Server to send them. Reports can also be previewed from within the application UI and be created in CSV, XLS, Word or PDF formats.
Additionally, ApexSQL Audit comes with several out-of-the-box alerts which will alert users on any potential issues while the tool is auditing. Furthermore, custom alerts can be created to raise an alert on any auditing event, whether it is an unauthorized access attempt, data loss, permission changes or more – a custom alert will be written inside Windows Event Log and can also be immediately send via email, again, using SMTP as a platform.
More information on ApexSQL Audit general features can be found in An introduction to ApexSQL Audit article and video.
Pros:
Centralized solution
Quick and easy to setup using GUI
Supports all SQL Server versions and editions from SQL 2005 onwards
Provides full information on who made the change, when, how, from where etc.
Audits almost 200 SQL Server events
Alerting on specific audited events
High-end out-of-the-box and custom reporting
Tamper-evident repository
Built-in repository maintenance and archiving features
Compliance regulation standard templates for configuration and reporting
Export, share and apply configuration between SQL Servers and databases
Supports all transaction log recovery models (full, bulk, simple)
Low overhead
Cons:
Potential performance degradation when auditing huge quantities of data and running ‘regular’ and before-after auditing processes
Beginner SQL knowledge required to setup and operate
Easy to learn, hard to master (large number of options and possibilities)
See more articles on auditing with ApexSQL Audit below
Securing access for SQL Server auditing
Various techniques to audit SQL Server databases
0 notes
Text
2019 Detroit Auto Show: Hits, Misses, and Revelations
DETROIT, Michigan—Thirty years after Toyota launched Lexus and Nissan introduced Infiniti here, and 27 years after Chrysler smashed Cobo Hall’s front windows with the 1993 Jeep Grand Cherokee, the North American International Auto Show is done with January. The reviews from jaded auto journos are mixed, and the press day crowds were down despite Toyota and China’s GAC flying in press from overseas. We’re pretty confident, though, in saying what Detroit lacked in quantity, it made up for in quality this year. There is more to like than there is to avoid, even if the Japanese and Chinese automakers are the only ones left who still build concepts, and even though Mercedes-Benz, BMW, Mini, Audi, and Volvo this year joined a bunch of other automakers who had followed Aston Martin’s decision to leave town after its Zen display of a decade ago. Herewith, our regular compendium of criticism, the good, the bad, and the philosophical, this time about what there is to see at the 2019 NAIAS:
HIT: Toyota Supra
Too many are getting stuck on the BMW partnership and the long gestation process, nitpicking the design, and decrying the lack of a manual transmission (which by the way Supra chief engineer Tetsuya Tada has not ruled out, so call your favorite dealer and demand it). Can we all just agree that what Toyota has done is give the world what by all accounts should be a nimble, kick-ass, rear-drive sports car that’s relatively attainable, price-wise? Call it whatever the hell you want, the fact that this car exists at all is pretty remarkable in this day and age. And it’s all but assured that hard-core variants will be in the offing. Yeah, what a terrible thing Toyota has done . . . not.—Mike Floyd
Automotive journalists can be a funny group. After wishing for a new Supra for years, some of them were overheard describing the final production car as less than thrilling, with others going so far as to call it “ugly.” “Look at all those fake plastic vents and intakes,” they decried. But as Supra designer Nobua Nakamura told editor-in-chief Mike Floyd, those nonfunctional pieces could become functional on future variants of the car. I don’t think the new Supra is perfect in the appearance department, and its roofline does look proportionally odd from some angles. But for the love of Suzuka, I’m excited to get a chance to drive it once test vehicles become available. If it lights up twisting roads as I expect it will, any niggling quibbles I have with its styling will go right off the nearest cliffside.—Mac Morrison
The biggest, most anticipated thing at this show is not an SUV, or even an autonomous tall electric sedan, but a sports car. Yes, it’s essentially a BMW Z4 built in Austria by Magna, but at least it has its own sheetmetal, which is more than you can say for the 86. And I’d take that Toyota 86 over most of the cars on the market today. Since the beginning of time, sports cars have relied on sharing some components to make development costs work out. In his introduction of the car, Akio Toyoda said he hopes Toyota will build more new sports cars in the future. Here’s to seeing him fulfill that wish.—Todd Lassa
MISS: Toyota Supra
This was easily the most anticipated car of the show, and I have no doubt it will be a blast to drive. But what is with Toyota outsourcing its performance cars? Sure, it’s great that Toyota will be selling a re-skinned BMW. But right in the same room as the BMW Supra is the Lexus LC, a 2018 Automobile All-Star and proof positive that Toyota knows how to design scintillating cars. With all the emphasis on making Camrys and RAV4s better to drive—which they are, by the way—what does it say when you outsource your halo sports car? I can’t imagine the effect this must have had on the morale of their engineering corps. “Nice job on the new Camrys, and oh, by the way, that new Supra? We’re getting BMW to do it.” Don’t get me wrong, I’m happy to have the Supra back—but I’d prefer a Toyota Supra.—Aaron Gold
REVELATION: The Supra almost wasn’t a Supra
In a chat at the Detroit show with Supra chief designer Nobua Nakamura, he told us that in July of 2013 that he and his team started sketching out ideas for a model that was at first billed as a nameless sports-car project. It was only after seeing the positive reception given to the FT-1 concept—created by Toyota’s Calty design house in California—at the 2014 Detroit show that the FT-1 would become the primary design inspiration for the sports-car project that would eventually be dubbed Supra. And the rest, as they say, is history.—MF
HIT: Akio Toyoda
For giving the best speech I’ve seen at an auto show in years, if not ever. No boring sales numbers. No bits of badly faked enthusiasm. Toyoda-san’s speech was funny, it was too the point, and though it was scripted—I was reading it on the teleprompter along with him—it’s obvious he’s seriously jazzed about this car (even if it is an automatic BMW).—AG
HIT: Fernando Alonso
My wife thinks so, anyway. Alonso appeared briefly on stage with Akio Toyoda for the Toyota Supra launch. Toyoda was gracious in acknowledging that the two-time Formula 1 champion (for Ferrari) and one-time 24 Hours of Le Mans winner (for Toyota) is driving another marque at the 24 Hours of Daytona later this month (a Cadillac).—TL
HIT: Ford Mustang Shelby GT500
For the jaded, it might be easy to look at the new GT500 and see just another jacked-up performance variant of Ford’s pony car. I get that . . . but whatever. More than 700 horsepower (what’s the final number, Ford?!) from the 5.2-liter supercharged V-8, a dual-clutch gearbox, zero to 60 mph in the mid-three-second range, a sub-11-second quarter-mile, magnetic dampers, and an optional Carbon-Fiber Track package with carbon wheels, rear-seat delete, and more? Find me a challenging road course and let’s get it on. Now.—MM
RELEVATION: Mahindra
This plucky Indian company is showing off its not-road-legal CJ-5 clone right in Jeep’s back yard. That takes cojones!—AG
HIT: Lexus LC Convertible concept
Rare is the car that gets scalped and doesn’t look great, but even rarer is a car as stunning to behold as the LC droptop. For all the coupe’s beauty—okay, some folks don’t like the spindle grille, but I think it works there—its overall attitude and stance strike me more as coming from a place of aggression. This concept elevates the LC to true elegance. I wouldn’t be shocked to see examples of the eventual production version at various concours d’élégance in the coming decades.—Erik Johnson
Yes, please. We love the LC hardtop, which was a 2018 All-Star, and with the top down, it takes the LC’s delightful GT style to another level.—MF
And here I thought it couldn’t get better than the LC coupe. Built it, Lexus! Build it, build it, build it!—AG
MISS: Cadillac XT6
It’s a damn shame what’s happened to Cadillac. Yes, I get it, its sedan sales are cratering and OMG it needs crossovers ASAP. I’m sure the XT6 and XT4 will be sales salve, but they come off as old GM badge-engineered exercises, and beyond the expressive grilles look uninspired. While they may put the brand back in the black, it’s sad to see really capable cars like the CT6 be minimized. At least Cadillac gave that car some serious attention in the form of the 550-hp CT6-V (which already is sold out). There is some hope in the form of the emerging EV strategy. Maybe those cars won’t have alphanumeric names.—MF
As another grizzled veteran told me, this three-row luxury SUV would have been a hit in 2012, or even 2016. While there’s nothing wrong with the new XT6 other than the Honda Pilot–esque side surfacing and the too-familiar GM interior plastics and switchgear, there’s nothing about it that pops. While I once believed that rear-wheel-drive proportions don’t matter on a tall SUV, the new Lincoln Aviator and even the 2020 Ford Explorer (gasp) have proved otherwise.—TL
0 notes