#saas security posture management
Link
MITIGATING THE RISKS THAT MAKE SAAS VULNERABLE TO EXTERNAL CYBER ATTACKS
Software as a Service (SaaS) is an essential outcome of the modernization offered by digital transformation and the cloud. Applications that can now reside on remote networks and still be accessed, configured, and used by the end user have made the software business more global, resource-optimized, and competitive. However, lucrative as it is, SaaS is not bereaved of cybersecurity risks. In fact, with complex networking utilities and cloud infrastructure - SaaS is exposed to a much larger attack surface than its predecessors in the market. What factors make SaaS so vulnerable to external cyber attacks, and how can they be mitigated?
Through the course of this article, we will discuss the security challenges for SaaS. We will also understand SaaS Security Posture Management (SSPM) and the critical features it should offer to help with SaaS security needs.
0 notes
Text
The Ultimate SaaS Security Posture Management Checklist, 2025 Edition
http://i.securitythinkingcap.com/T7Dm0f
0 notes
Text
What is Microsoft Defender for Cloud Apps?
Check the new post out now on KnowverGreen! Appreciate ya! Thank you!
SaaS App Protection
We got your back!
Photo by Ahmet Mert: A man dressed in armor holding an ax – 22840949 – Pexels
Microsoft Defender for Cloud Apps delivers full protection for SaaS applications. Protections such as:
Fundamental Cloud Access Security Broker (CASB) functionality
SaaS Security Posture Management (SSPM) features
Advanced Threat Protection, which is now Microsoft Defender…

View On WordPress
#Cloud App Security#Cloud Security#Defender#Endpoint#Microsoft 365 Security#Microsoft defender for cloud apps#SaaS#SaaS Security#security
1 note
·
View note
Text
Safeguarding Your Digital Frontier: Sify's Managed Security Services
In an age where digital threats lurk around every virtual corner, safeguarding your organization’s data and infrastructure has never been more critical. As businesses grapple with an increasingly complex threat landscape, Sify Technologies emerges as a beacon of cybersecurity excellence, offering comprehensive Managed Security Services (MSS) designed to fortify defenses, mitigate risks, and ensure peace of mind in an ever-evolving cyber ecosystem.
The Evolution of Cyber Threats: Cyberattacks have evolved from simple nuisances to sophisticated, orchestrated campaigns orchestrated by skilled threat actors. From ransomware and phishing scams to DDoS (Distributed Denial of Service) attacks and insider threats, the breadth and depth of cyber threats facing organizations today are unprecedented. In this digital battleground, proactive defense and rapid response are paramount.
Empowering Organizations with Comprehensive Protection: Sify’s Managed Security Services deliver a holistic approach to cybersecurity, encompassing a wide range of solutions and technologies to address the multifaceted nature of modern threats. Key components of Sify’s MSS portfolio include:
Threat Detection and Response: Leveraging advanced threat intelligence, machine learning, and behavioral analytics, Sify’s MSS enables organizations to detect and respond to threats in real-time, minimizing dwell time and mitigating the impact of security incidents.
Endpoint Security: Endpoints serve as the frontline of defense against cyber threats, making endpoint security a critical component of any cybersecurity strategy. Sify’s MSS provides comprehensive endpoint protection, including antivirus, endpoint detection and response (EDR), and vulnerability management, to safeguard devices from malware, ransomware, and other malicious attacks.
Network Security: Protecting the network perimeter is essential for preventing unauthorized access and data exfiltration. Sify’s MSS offers robust network security solutions, such as firewalls, intrusion detection and prevention systems (IDPS), and secure web gateways, to monitor and control traffic, enforce security policies, and thwart cyber threats.
Cloud Security: As organizations embrace cloud computing and hybrid IT environments, securing cloud workloads and data becomes paramount. Sify’s MSS delivers cloud security solutions tailored to the unique requirements of cloud-native applications, infrastructure as a service (IaaS), and software as a service (SaaS), ensuring comprehensive protection across the entire cloud ecosystem.
Security Operations Center (SOC) as a Service: Building and operating an in-house SOC can be resource-intensive and cost-prohibitive for many organizations. Sify’s MSS offers SOC as a Service, providing round-the-clock monitoring, threat hunting, incident response, and security advisory services delivered by a team of skilled cybersecurity experts.
Partnering for Success: Sify’s Managed Security Services are more than just technology solutions; they are strategic partnerships forged with the shared goal of safeguarding organizational assets and preserving business continuity. With a customer-centric approach, Sify collaborates closely with clients to understand their unique security requirements, assess their risk posture, and develop tailored cybersecurity strategies that align with their business objectives.
Driving Cyber Resilience in a Digital World: In today’s interconnected and digitized world, cybersecurity is not merely a compliance checkbox but a business imperative. With Sify’s Managed Security Services, organizations can navigate the complexities of the cyber threat landscape with confidence, resilience, and agility. By combining cutting-edge technologies, industry best practices, and expert guidance, Sify empowers organizations to stay one step ahead of cyber adversaries and emerge stronger in the face of adversity.
Protect your organization’s digital frontier with Sify’s Managed Security Services and embark on a journey towards a safer, more secure future.
0 notes
Text
Empower Yourself: Online Certification Courses for Cybersecurity
In today’s interconnected world, cybersecurity has become a top priority for individuals and organizations alike. With cyber threats evolving rapidly, there’s an urgent need for skilled professionals who can safeguard digital assets and mitigate risks. If you’re passionate about protecting data and navigating the cyber landscape, look no further. Welcome to Futureskills Prime, your gateway to comprehensive online certification courses for cybersecurity.
Why Cybersecurity Matters
Cybersecurity is more than just a buzzword—it’s a critical aspect of our digital lives. From personal information to sensitive corporate data, everything is at risk in the digital realm. Cyber threats such as malware, phishing attacks, and data breaches pose significant challenges to individuals and businesses worldwide. As technology advances, so do the tactics of cybercriminals, making cybersecurity skills indispensable in today’s job market.
The Value of Certification
In the competitive field of cybersecurity, certification can set you apart from the crowd. Employers seek certified professionals who possess the knowledge and skills to protect their assets effectively. Whether you’re looking to start a career in cybersecurity, advance in your current role, or enhance your cybersecurity posture as a business owner, online certification courses offer a structured pathway to success. With Futureskills Prime, you can access high-quality cybersecurity training from the comfort of your home, on your own schedule.
Why Choose Futureskills Prime?
At Futureskills Prime, we’re committed to empowering individuals with the knowledge and skills they need to excel in cybersecurity. Here’s why our online certification courses stand out:
Comprehensive Curriculum: Our courses cover a wide range of cybersecurity topics, from fundamentals to advanced techniques, ensuring you acquire a holistic understanding of the field.
Expert Instructors: Learn from seasoned cybersecurity professionals with years of industry experience, who bring real-world insights and expertise to the virtual classroom.
Hands-on Labs: Put theory into practice with hands-on labs and projects designed to simulate real-world scenarios. Gain practical experience and build a portfolio of work-ready skills.
Flexible Learning: Our online platform allows you to learn at your own pace, anytime, anywhere. Whether you’re a busy professional or a full-time student, you can access course materials and lectures according to your schedule.
Industry Recognition: Futureskills Prime certifications are widely recognized in the cybersecurity industry, giving you a competitive edge in the job market.
Course Offerings
Cybersecurity Fundamentals: Master the basics of cybersecurity, including threat landscape analysis, risk management, and security controls implementation.
Ethical Hacking: Learn the tools and techniques used by ethical hackers to identify vulnerabilities and strengthen defenses against cyber attacks.
Incident Response and Forensics: Explore strategies for detecting, responding to, and recovering from cybersecurity incidents, with an emphasis on digital forensics techniques.
Network Security: Gain expertise in securing networks against unauthorized access, data breaches, and other cyber threats.
Cloud Security: Understand the unique challenges and best practices for securing cloud environments, including infrastructure as a service (IaaS), platform as a service (PaaS), and software as a service (SaaS).
Security Compliance and Governance: Learn how to navigate regulatory requirements and establish effective security policies and procedures to ensure compliance and mitigate risk.
Take the Next Step
Ready to take your cybersecurity skills to the next level? With Futureskills Prime, you can embark on a journey of discovery and empowerment. Our online certification courses provide the knowledge, skills, and confidence you need to succeed in the dynamic field of cybersecurity. Don’t wait for threats to strike—be prepared to defend against them.
Enroll today and become a certified cybersecurity professional with Futureskills Prime.
0 notes
Text
Unleashing the Potential: Analyzing the Size of the Cloud Security Posture Management Market
Overview and Scope:
Cloud security posture management refers to IT security technologies made to find cloud misconfiguration problems and compliance threats as well as to continuously check the cloud infrastructure for a lack of compliance with security policy. It is used by businesses that wish to extend their security best practices to hybrid and multi-cloud systems and have embraced a cloud-first strategy. Although CSPM is frequently linked to infrastructure as a service (IaaS) cloud services, the technology can also be utilized in software as a service (SaaS) and platform as a service (PaaS) cloud settings to decrease configuration errors and lower compliance risks.
Sizing and Forecast:
The cloud security posture management market size has grown rapidly in recent years. It will grow from $4.42 billion in 2023 to $5.03 billion in 2024 at a compound annual growth rate (CAGR) of 14.0%. The growth in the historic period can be attributed to increased adoption of cloud computing, growing concerns about data breaches and cybersecurity threats, compliance requirements and regulations for data protection, rapid migration of businesses to cloud-based infrastructure, complexity of managing security in multi-cloud environments.
The cloud security posture management market size is expected to see rapid growth in the next few years. It will grow to $8.75 billion in 2028 at a compound annual growth rate (CAGR) of 14.8%. The growth in the forecast period can be attributed to continued growth of cloud adoption across industries, rise in the frequency and sophistication of cyberattacks, expansion of hybrid and multi-cloud architectures, emphasis on automation and orchestration in cloud security, increased focus on real-time monitoring and response capabilities.
To access more details regarding this report, visit the link:
https://www.thebusinessresearchcompany.com/report/cloud-security-posture-management-global-market-report
Segmentation & Regional Insights:
The cloud security posture management market covered in this report is segmented –
1) By Component: Solution, Services
2) By Organization Size: Large Enterprises, Small And Medium Enterprises
3) By Cloud Model: Infrastructure-as-a-Service (IaaS), Platform-as-a-Service (PaaS), Software-as-a-Service (SaaS)
4) By Vertical: BFSI, Healthcare, Retail, Trade, IT, Telecommunication, Public Sector
North America was the largest region in the cloud security posture management market in 2023 and is expected to be the fastest-growing region in the forecast period. The regions covered in the cloud security posture management market report are Asia-Pacific, Western Europe, Eastern Europe, North America, South America, Middle East, Africa
Intrigued to explore the contents? Secure your hands-on sample copy of the report:
https://www.thebusinessresearchcompany.com/sample.aspx?id=7493&type=smp
Major Driver Impacting Market Growth:
A huge increase in the number of people using the internet for employment, education, and leisure is driving significant growth for cloud security posture management. There has been a tremendous rise in the number of internet users for various reasons such as employment, education, and leisure time. One of the most influential and quickly developing technologies is the internet which has further led to a boost in demand for cloud security posture management (CSPM). Consumption for CSPM technologies is sparked by the ensuing sharp increase in bandwidth demand as well as an unanticipated rise in the frequency of cyberattacks such as Ransomware, Distributed Denial of Service (DDoS), and other threats.
Key Industry Players:
Major companies operating in the cloud security posture management market report are International Business Machines Corporation, Cisco Systems Inc., Microsoft Corporation.
The cloud security posture management market report table of contents includes:
1. Executive Summary
2. Market Characteristics
3. Market Trends And Strategies
4. Impact Of COVID-19
5. Market Size And Growth
6. Segmentation
7. Regional And Country Analysis
.
.
.
27. Competitive Landscape And Company Profiles
28. Key Mergers And Acquisitions
29. Future Outlook and Potential Analysis
Contact Us:
The Business Research Company
Europe: +44 207 1930 708
Asia: +91 88972 63534
Americas: +1 315 623 0293
Email: [email protected]
Follow Us On:
LinkedIn: https://in.linkedin.com/company/the-business-research-company
Twitter: https://twitter.com/tbrc_info
Facebook: https://www.facebook.com/TheBusinessResearchCompany
YouTube: https://www.youtube.com/channel/UC24_fI0rV8cR5DxlCpgmyFQ
Blog: https://blog.tbrc.info/
Healthcare Blog: https://healthcareresearchreports.com/
Global Market Model: https://www.thebusinessresearchcompany.com/global-market-model
0 notes
Text
Dynamische Angriffsflächen in der Cloud schützen

Immer mehr Unternehmen verlagern digitale Assets in die Cloud. In der Folge erweitert sich die Angriffsfläche der IT und wird, verstärkt durch die Multi Cloud, zunehmend komplexer. Das Cloud Security Posture Management, kurz CSPM, überprüft Cloud-Umgebungen und benachrichtigt die zuständigen Fachkräfte über Konfigurationsschwachstellen.
Angriffsflächen sind dynamisch und ihre Zahl nimmt kontinuierlich zu. Bedingt durch die digitale Transformation und das hybride, lokal flexible Arbeiten verlangt eine enorm wachsende Menge an Geräten, Webapplikationen, Software-as-a-Service-Plattformen (SaaS) und andere Dienste von Drittanbietern den Anschluss an das Unternehmensnetzwerk.
Team: Cloud Security Posture Management
Zugleich verlagern Unternehmen immer mehr geschäftskritische Systeme in die Cloud und verteilen sie über mehrere Cloud Service Provider (CSPs) und in Rechenzentren. Einem Cloud Security Posture Management (CSPM) kommt damit in immer mehr Organisationen höchste Priorität zu. Die Grundaufgaben einer Cloud-Sicherheit sind durchaus vergleichbar mit der Sicherheitsaufstellung in der herkömmlichen IT eines lokalen Rechenzentrums.
Angesichts sich verändernder digitalisierter und in die Cloud verlagerter Abläufe benötigen IT-Sicherheitsverantwortliche eine umfassende Sichtbarkeit der neu hinzukommenden Angriffsflächen. Insbesondere in der Multi Cloud verlangen sie nach Tools zur konsistenten Sicherheitskontrolle unabhängig von der zugrunde liegenden Infrastruktur.
Cloud verlangt nach guter Sicherheit
Im Vergleich zu traditionellen Rechenzentrumsarchitekturen bleibt die Wichtigkeit des Schutzes gegen Angriffsmechanismen bestehen, die für die Cloud wie für die On-Premise-IT gleichermaßen gelten. Was sich in der Cloud geändert hat, ist die zugrundeliegende Infrastruktur und der Zugriff autorisierter Entitäten auf digitale Ressourcen.
Ein Ergebnis des Trends, geschäftskritische Systeme in die Cloud und in die Multi Cloud zu verlagern, ist die gestiegene Komplexität der IT. Die IT-Sicherheitslage zu überwachen, ist schwieriger geworden. Zugleich erleichtert es paradoxerweise der zentrale Nutzen der Cloud - Infrastruktur nach Bedarf aufzusetzen, zu konfigurieren und zu skalieren - den Angreifern, Schwachstellen aufzuspüren, um Zugriff auf Instanzen in der Multi Cloud zu erhalten.
Grenzen der herkömmlichen IT-Sicherheit
Herkömmliche Cybersicherheitslösungen sind für den Schutz der in der Multi Cloud entstehenden dynamischen Angriffsflächen schlecht gerüstet. Sie sind immer noch für eine statische IT konzipiert, in der Applikationen in einem gehärteten Rechenzentrum laufen und lediglich eine überschaubare Anzahl von Benutzern von außerhalb des Netzwerks einen legitimen Grund für eine Zugriffsanfrage hat. Daher können sie mit der zunehmenden Komplexität und Flexibilität heutiger IT-Strukturen nicht Schritt halten.
In der neuen Unübersichtlichkeit können Cyberkriminelle zugleich ihre Kommunikationsversuche als legitimen Datenverkehr tarnen und ihre Ausweichmanöver in der wachsenden Menge an Autorisationsanfragen verstecken. So scannen Angreifer beispielsweise ständig Cloud-IPs, um Fehlkonfigurationen, überprivilegierte Identitäten und veraltete, nicht ausreichende Authentifikationsmechanismen zu finden. Zudem können viele Cyberkriminelle eine Liste offener S3-Buckets herunterladen oder auf GitHub nach privaten API-Schlüsseln suchen, um den Zugriff auf Daten oder das Netzwerk zu finden.
Neuer Sicherheitsstatus dank Cloud Security Posture Management (CSPM)
CSPM kann Unternehmen helfen, diese Probleme besser in den Griff zu bekommen. Im Folgenden finden sich fünf Hauptaufgaben, die eine Neuaufstellung der Sicherheit in der Cloud erfüllen sollte:
1. Die digitale Landschaft in ihrer Gesamtheit sehen
Niemand kann schützen, was er nicht sieht. IT-Sicherheitsteams benötigen deshalb eine vollständige Sichtbarkeit der Angriffsfläche – von der Infrastruktur vor Ort und den verwalteten Assets über die Multi Cloud und Webapplikationen von Drittanbietern hinweg bis hin zu dezentralen Endpunkten. CSPM bietet einen umfassenden Einblick in die Cloud-Landschaft eines Unternehmens. Um die dabei gewonnenen Informationen optimal zu verwerten, sollten diese nahtlos in dessen gesamter digitalen Infrastruktur integriert sein. Im Idealfall erfolgt dies auf einer übergreifenden Plattform, die sowohl die Cloud als auch alle anderen digitalen Assets erfasst.
2. Sicherheitsstandards umfassend durchsetzen
Um empfohlene Sicherheitsstandards in Multi-Cloud-Strukturen zu implementieren, ist es wichtig, Lücken in der Abwehr zu erkennen. Ein CSPM muss mehrere Fragen beantworten. Ist die Konfiguration korrekt? Verfügt jeder Endpunkt über ein Anti-Malware-Programm? Sind die Daten nach anerkannten Standards verschlüsselt? Ein CSPM erfüllt nur dann seine Aufgaben, wenn sie den IT-Sicherheitsbeauftragten die Mittel an die Hand gibt, grundlegende Sicherheitsrichtlinien auszuspielen und durchzusetzen. Im nächsten Schritt können sie weitere branchen- oder unternehmensspezifische Richtlinien und Vorschriften auf die Agenda setzen, die für das Unternehmen vorgeschrieben oder sinnvoll sind.
3. Identitäten und Zugriffsrechte einfach und transparent verwalten
Ein CSPM als umfassendes Instrument zum Aufstellen der IT-Sicherheit eröffnet den Überblick auf Richtlinien für das Identitäts- und Zugriffsmanagement in der Multi Cloud. Unternehmen nutzen eine enorme Zahl von Cloud-Diensten, vom Storage bis zum Loadbalancing, und es ist fast unmöglich zu wissen, welche Entität auf welches Asset zugreift und warum. Nicht selten existieren noch geltende und damit Zugang verschaffende Richtlinien oder Maschinen-Identitäten mit privilegierten Rechten, die niemand mehr braucht oder die der IT-Administrator schon längst vergessen hat. Zudem ziehen sich viele Administratoren, getrieben vom Drang nach Produktivität, auf Standards der Berechtigungsrichtlinien zurück. Im Endergebnis erteilen sie dann Webdiensten und anderen Entitäten weitaus mehr Zugriffsrechte als erforderlich. Eine solides Access Management ist deshalb grundlegend für die gerade bei komplexen Gegebenheiten zwingend notwendige Least-Privilege-Cyber-Hygiene.
4. Sicherheitslücken effizient erkennen und schließen
Das Absichern einer stets wachsenden Angriffsfläche steht und fällt mit der Möglichkeit, Probleme priorisiert zu behandeln. Kein noch so großes Team an Sicherheitsanalysten kann mit dem aktuellen Anstieg der Netzoberfläche in dynamischen Multi-Cloud-Infrastrukturen mithalten. An einer maschinellen Skalierung, um alle Bereiche abzudecken und die kritischsten Schwachstellen zu eskalieren, führt kein Weg vorbei. Wirksames CSPM priorisiert Probleme weitestgehend automatisiert. Es empfiehlt Wege, um Schwachstellen zu beheben, die einerseits hochgradig automatisiert sind und die andererseits der Administrator überwachen kann. Risiken bewertet es im Einklang mit den Unternehmenszielen.
5. Sich einfach implementieren lassen
Vor allem muss CSPM die Komplexität reduzieren. Security-Teams sollten in der Lage sein, ein CSPM schnell zu implementieren und sofort umfassenden Einblick in ihre Angriffsfläche erhalten. Dabei sollte die Plattform praktisch verwertbare Erkenntnisse und umsetzbare Handlungsempfehlungen liefern, um so schnell wie möglich die kritischsten Schwachstellen zu beheben. So wird sie zu einer wertvollen Hilfe, selbst wenn das Sicherheitsteam nur über geringe Kenntnisse zur Cloud-Sicherheit verfügt.
Die Cloud erfassen
Immer neue Angriffsflächen verändern die heutige Gefahrenlandschaft und geben Angreifern reichlich Gelegenheit, Schwachstellen in der Sicherheitsabwehr aufzuspüren und auszunutzen. Herkömmliche IT-Sicherheit ist nicht in der Lage, diese Lücken zu schließen. CSPM hilft Unternehmen, ihre wachsenden Angriffsflächen besser in den Griff zu bekommen, denn es bietet die Sichtbarkeit der Cloud-Landschaft und bewertet aufkommende Risiken. Es verschafft die Möglichkeiten, Cloud-Strukturen zu härten. Mit automatisierten Abläufen realisiert es den Schutz in komplexen Landschaften selbst bei geringem Knowhow und Ressourcen. Einfach implementiert, entfaltet ein CSPM schnell seine Wirkung.
Passende Artikel zum Thema
Lesen Sie den ganzen Artikel
0 notes
Text

Fortanix Data Security Manager (DSM) SaaS offers a compelling solution for businesses seeking robust data protection. Leveraging its advanced encryption and key management capabilities, Fortanix DSM SaaS ensures the security of sensitive data throughout its lifecycle. With features like centralized key management, secure key generation, and cryptographic operations, Fortanix DSM SaaS provides businesses with a scalable and easy-to-use platform to safeguard their data against evolving threats. Additionally, its integration-friendly architecture allows seamless incorporation into existing workflows and applications, ensuring compliance with regulatory requirements and bolstering overall data security posture. Ultimately, Fortanix DSM SaaS stands out as a dependable choice for organizations looking to fortify their data security infrastructure with a comprehensive and cloud-native solution.
0 notes
Text
Tech Defence: The Role of Continuous Threat Exposure Management
In the times when every field in business is adopting and using technology in their work culture to enhance productivity and growth, there is a crucial matter that needs awareness of challenges that might be faced with digital transformation. There is a threat to privacy and security issues when we use technology as well as unauthorized access to data and customer information. In this article, let us learn the concept of Continuous Threat Exposure Management (CTEM) and its role in safeguarding the information and data related to the organization more effectively.

What is Continuous Threat Exposure Management (CTEM)?
Continuous Threat Exposure Management (CTEM) is the fundamental strategic approach in the security management of the organization. That involves assessing, monitoring, and identifying vulnerabilities in organizational security protection. This approach is the new wave in cybersecurity that goes beyond and is more efficient than the traditional approach in managing digital threats. It comprises analyzing and mitigating the real-time potential threats and helps in maintaining robust security management. In this digitally and technologically transforming world, if businesses neglect to take required measures on security, then they are at high risk.
Need for Continuous Threat Exposure Management (CTEM)
With the vast use of technology for all the organization’s operations and activities there is the risk of maintaining the security of the data that is been gathered for different purposes. To protect this confidential information from being hacked we need the approach of Continuous Threat Exposure Management (CTEM). The areas and opportunities for threat have increased with the use of cloud technology hence CTEM is proactive in identifying these threats and provides a strategy for risk mitigation. The continuous monitoring process of CTEM will respond rapidly to any vulnerabilities and safeguard the information piracy.
In the threat landscape, the use of CTEM in security operations will provide frictionless experiences in business. Involving security management with the other assets of the organization will create more effectiveness in managing vulnerability assessments. CTEM along with continuous security monitoring will also help in identifying the critical threats and hence prioritizing the same in solving them immediately for risk mitigation.
Visit Apac Business Times to read more on business topics
Stages involved in CTEM
Now we will learn the 5 stages that are involved in Continuous Threat Exposure Management (CTEM) and they are scoping, discovery, prioritization, validation, and mobilization.
Scoping is the first step in CTEM which performs the task of identifying the attack surface and will also help to discover the most important cyber threat for your business. The two major attack areas are external attack surface and SaaS security posture. This needs the inclusion of digital aspects rather than the other physical and software assets. The next stage is discovery, which involves the deeper identification of threats and vulnerabilities. It is efficient in discovering hidden and unnoticed cyber threats with the consideration of hardware, software, IoT, data hubs, networks, and websites where there is a change of hidden threats. This stage is usually misunderstood with the first step and increases the chance of negligence in digging deeper and future risk factors.
Prioritization, which is the third step in CTEM will perform the task of segregating the threats based on the importance and level of risk factors. This will help in identifying the most impactful threat that might cause high damage to an organization and find the most effective way to fix these issues which might lead to high loss. The next step is validation, as the term itself describes it is used to validate the currently identified risks and whether the plan used to mitigate them is effective or not. The last stage of CTEM is mobilizing everyone on the same page, the aim is to establish a smooth process. At this phase, the organization must input the new automation that will work effectively with the existing automation frameworks.
Conclusion
To conclude, Continuous Threat Exposure Management (CTEM) is the modern way of approach to attaining proactive cybersecurity in the organization. The stages involved will make the effective and efficient identification of cyber threats and also plan to mitigate them. With the continuous monitoring and identification approach of CTEM, an organization can enjoy high data protection and mitigate vulnerability assessment successfully.
Visit More : https://apacbusinesstimes.com/tech-defence-the-role-of-continuous-threat-exposure-management/
0 notes
Text
Building a Strong Foundation: Modernizing IT Legacy Systems

Introduction: In today’s fast-paced and ever-evolving digital landscape, organizations face the challenge of staying competitive and agile while also managing their existing IT legacy systems. These legacy systems, often built on outdated technologies and architectures, can hinder innovation, scalability, and operational efficiency. However, by embracing modernization, organizations can build a strong foundation for their IT infrastructure, enabling them to adapt to changing market demands and unlock new opportunities. This blog explores the importance of modernizing IT legacy systems, the benefits it brings, and key strategies to successfully build a strong foundation for the future.
The Need for Modernization: Legacy systems, despite their years of service, can become a bottleneck to progress. Outdated technologies may lack the necessary security measures, fail to integrate with modern software, or impede collaboration and scalability. Modernizing IT legacy systems is crucial to overcome these challenges and ensure a robust foundation that can support business growth and innovation.
Enhancing Agility and Flexibility: Modernizing IT legacy systems empowers organizations to improve their agility and flexibility. By adopting modern technologies such as cloud computing, microservices, and containerization, organizations can embrace a more modular and scalable approach to IT infrastructure. This allows for faster development and deployment of applications, easier integration with third-party systems, and the ability to rapidly respond to changing market needs.
Cost Optimization and Efficiency: Legacy systems often require significant maintenance and support costs. By modernizing IT legacy systems, organizations can optimize their costs and improve operational efficiency. Modern technologies offer more cost-effective solutions, such as cloud-based infrastructure and software-as-a-service (SaaS) models, reducing the need for on-premises hardware and software maintenance.
Improved Security and Compliance: Legacy systems can pose security risks due to outdated security measures and vulnerabilities. Modernizing IT legacy systems allows organizations to implement robust security controls and stay compliant with industry regulations. This includes adopting encryption technologies, multi-factor authentication, and regular security updates to protect sensitive data and strengthen overall cybersecurity posture.
Enabling Innovation and Digital Transformation: Modernizing IT legacy systems is a stepping stone towards innovation and digital transformation. By adopting modern technologies, organizations can leverage emerging trends such as artificial intelligence, machine learning, and the Internet of Things (IoT). This enables them to uncover valuable insights, automate processes, and create new business models that drive growth and competitive advantage.
Streamlining Business Processes and Collaboration: Legacy systems often lack the integration capabilities required for streamlined business processes and collaboration. Modernizing IT legacy systems allows organizations to implement enterprise resource planning (ERP) systems, customer relationship management (CRM) platforms, and other business applications that enable seamless workflows and enhance collaboration across departments.
Change Management and User Adoption: Modernizing IT legacy systems requires effective change management and user adoption strategies. It is crucial to involve stakeholders from the beginning, communicate the benefits of modernization, and provide training and support to ensure smooth transition and user acceptance. User-centric design and intuitive interfaces can also facilitate a positive user experience, driving adoption and maximizing the benefits of modernized systems.
Conclusion: Building a strong foundation through modernizing IT legacy systems is a strategic imperative for organizations seeking to thrive in today’s digital landscape. By enhancing agility, reducing costs, improving security, enabling innovation, and streamlining business processes, organizations can unlock new opportunities and drive sustainable growth. Modernization is not just a technical endeavor; it requires a comprehensive approach that involves aligning business objectives with IT strategies, embracing change, and ensuring user adoption. With a modernized IT infrastructure, organizations can build a strong foundation that supports their long-term success and enables them to embrace future technologies with confidence.
#AvenDATA #legacysystems #ITlegacysystems #dataarchiving #legacydata
0 notes
Text
Strengthening Digital Fortresses: Cyber Security Services in Hyderabad
In the digital age, where information is a valuable currency, the need for robust cyber security measures has never been more critical. Hyderabad, a bustling hub of technology and innovation, is at the forefront of addressing this concern through specialized cyber security services. This article delves into the key aspects of cyber security services in Hyderabad, including cyber threat intelligence, cybersecurity risk management, and cybersecurity consulting services.
Cyber Security Services in Hyderabad: A Technological Shield
Hyderabad has emerged as a cybersecurity stronghold, offering a range of services to safeguard businesses, organizations, and individuals from evolving cyber threats. Cyber security services in the city encompass a holistic approach, incorporating cutting-edge technologies and strategies to fortify digital assets against unauthorized access, data breaches, and other cybercrimes.
Cyber Threat Intelligence in Hyderabad: Unmasking the Invisible Foe
Cyber threat intelligence plays a pivotal role in predicting, preventing, and mitigating cyber threats. In Hyderabad, specialized services focus on gathering, analyzing, and disseminating actionable intelligence to stay ahead of potential cyber adversaries. By understanding the tactics, techniques, and procedures employed by malicious actors, organizations can proactively fortify their cyber defenses and respond effectively to emerging threats.
Cybersecurity Risk Management in Hyderabad: Navigating the Digital Minefield
Effective cybersecurity risk management is paramount in identifying and mitigating potential vulnerabilities. Hyderabad-based services employ comprehensive risk assessment methodologies to evaluate the security posture of organizations. By identifying and prioritizing potential risks, cybersecurity professionals can implement tailored solutions to mitigate threats and minimize the impact of security incidents.
Cybersecurity Consulting Services in Hyderabad: Nurturing Cyber Resilience
Hyderabad's cybersecurity consulting services play a crucial role in guiding organizations through the complex landscape of cyber threats. These services provide expert advice, tailored strategies, and hands-on assistance to build and maintain robust cybersecurity frameworks. By collaborating with experienced consultants, businesses can enhance their cyber resilience, ensuring a proactive response to the ever-evolving threat landscape.
In conclusion, as businesses and individuals become more interconnected in the digital realm, the importance of cybersecurity cannot be overstated. Hyderabad's cybersecurity services stand as a beacon of technological defense, offering a robust shield against the relentless onslaught of cyber threats. Through a combination of advanced technologies, strategic intelligence, and expert guidance, Hyderabad continues to pave the way for a secure and resilient digital future.
About
Embedtech solutions is a leading B2B (business-to-business) Software Platform Provider and Hardware Solutions Provider located in Hyderabad, India. We specialize in Cloud Applications (SaaS and PaaS), Embedded Systems, IoT, Information Systems, Artificial Intelligence, Web Development, Mobile App Development, System Design, and Product Engineering.
0 notes
Text
AppOmni Harnesses Google Data Centre In Australia To Address Regional Demand For Specialised SaaS Security Solutions

AppOmni, a leader in SaaS security posture management (SSPM), recently announced the opening of a new data center powered by Google Cloud Platform (GCP) in Sydney, Australia. Through this initiative, Australian businesses—private or public—that must abide by the nation's data sovereignty laws, such as the Privacy Act and the Australian Privacy Principles, will have access to AppOmni's all-inclusive SaaS security solutions.
Australia is a key region for AppOmni as it continues its global expansion ambitions. The Asia-Pacific (APAC) region's growing requirement to defend against sophisticated threats aimed at SaaS applications is met by the new data center. For the 25% of Fortune 100 businesses who already depend on AppOmni to secure their SaaS ecosystems, the move is very pertinent.
With an emphasis on SaaS Security Posture Management, AppOmni's platform helps security teams and SaaS application owners protect sensitive and mission-critical data from internal threats and attackers. In order to offer comprehensive data access visibility, secure identities and SaaS-to-SaaS connections, threat detection, prioritized insights, and streamlined compliance reporting, the platform continuously monitors SaaS APIs, configurations, and audit logs.
Read More - bit.ly/3SKt0O4
#AppOmni#ComputerAndNetworkSecurity#GoogleCloudPlatform(GCP)#SaaSSecurityPostureManagement#SaaSApplications#SaaS-to-SaaSConnections
0 notes
Text
10 cloud security essentials, 2024 - CyberTalk
New Post has been published on https://thedigitalinsider.com/10-cloud-security-essentials-2024-cybertalk/
10 cloud security essentials, 2024 - CyberTalk


EXECUTIVE SUMMARY:
An increasing number of enterprises are transitioning from on-premises to cloud-hosted applications, data and services, ultimately supporting remote employees, offices and third-parties operating around the world, on a variety of devices.
The cloud offers significant benefits to organizations; scalability, agility, reduced physical infrastructure, fewer operational expenses, and 24/7 data accessibility. However, research shows that only 4% of organizations retain adequate security for 100% of their cloud-based assets.
In 2023, over 80% of breaches involved data stored in the cloud. In 2024, trends are liable to remain stagnant, unless organizations take action.
Enhance your cloud security posture. Get advisory, planning and development ideas below – no matter where you are in your cloud security journey.
10 cloud security essentials for 2024
Have one of these already? Skip the section and move on to the next item.
1. Cloud-native security solutions. Unlike traditional security tools, cloud-native security solutions were built with the cloud in-mind. They’re designed to mitigate the specific risks associated with cloud-based infrastructure and services.
They work seamlessly in virtualized and dynamic cloud environments, leveraging cloud-native features and APIs to provide the most effective protection.
Tools like Check Point’s Cloud Native Security Platform (CloudGuard) ensure that your security keeps pace with all cloud related challenges, offering features such as auto-provisioning, along with auto-scaling and automatic policy updates.
Cloud native security for all assets and workloads provides crucial visibility, and a unified multi-layered approach.
2. Does your organization maintain a ton of tools? Reduce operational complexity with Security Orchestration, Automation and Response technology (SOAR). SOAR facilitates the coordination, automation and execution of a variety of tasks across divergent people and systems – all within a unified platform.
SOAR eliminates patchworks of siloed systems, meaning that organizations can bypass distractions and get to the business of responding to the most pressing threats.
SOAR also allows for streamlined policy management and automated alert management, enabling Security Operations Center analysts take on higher-order tasks. When it comes to continuously driving improvements, SOAR is an SOC manager’s secret weapon.
3. Zero trust policies. When using a zero trust framework, every request is logged and all traffic is assessed. Access to resources is restricted, reducing the potential for unauthorized users or breaches, and a transparent audit trail is always available.
“I expect adherence to Zero Trust principles to become the norm for all security vendors and application architecture patterns deployed in cloud through 2024 and into 2025,” says Check Point cloud security specialist, Jason Normanton.
4. A Cloud Access Security Broker (CASB) implements zero trust access control and policy enforcement for cloud environments. Traffic to the cloud flows through the CASB solution, enabling it to enforce corporate security policies.
A CASB helps improve cloud visibility by offering insight into how users and applications access and utilize a given organization’s cloud-based applications. It can also provide insight into shadow IT, where the use of unapproved SaaS apps could lead to data leaks or other security threats.
A CASB can assist with data loss prevention (DLP), controlling access to and securing an organization’s cloud-based assets. Further, it offers advanced threat prevention (including the ability to identify and block the distribution of malware through cloud-based infrastructure) along with compliance advantages.
5. Secure Access Service Edge (SASE). With a distributed workforce and distributed applications, the traditional method of backhauling traffic to a centralized location for security scrubbing isn’t efficient.
SASE addresses the need for a centralized, cloud-delivered and software-defined security architecture; one that’s suited for highly distributed applications and users.
Critical components of SASE that are designed to protect your organization include Zero-Trust Network Access (ZTNA), SD-WAN, Security Service Edge (SSE) and Firewall-as-a-Service (FWaaS).
All traffic is routed to a point of presence for security inspection and is then optimally routed to its destination. In other words, SASE reduces complexity, improves performance, and advances security.
6. AI and ML powered threat detection and response. AI and ML algorithms excel when it comes to processing and analyzing vast quantities of data at speed and scale. In relation to cloud security, AI and ML enhance threat detection by identifying patterns and anomalies that are indicative of potential security risks.
Because these tools can discern subtle deviations from typical behavior, they enable early detection of emerging threats and keep organizations safer than traditional tools alone.
7. Big data threat intelligence. Leverage threat intelligence tools that aggregate and analyze millions of Indicators of Compromise (IoCs) everyday. When a threat is identified, protections/blocking capabilities can be deployed in under two seconds, with select tools.
8. Multi-factor authentication and credential rotation. To thwart threats in cloud environments, these simple and mainstream security measures are a must.
In the event that a password has been breached or stolen, multi-factor authentication can prevent unauthorized logins to cloud-based platforms, while routine credential rotations can reduce the window of opportunity for credential thieves.
Automated credential rotation processes can be integrated into security protocols, ensuring a seamless and timely rotation without undue operational disruption.
9. XDR. This trending solution type provides unified and integrated data visibility and analytics across an organization’s entire network – including the cloud. This enables security analysts to obtain context around incidents without having to learn and operate a variety of different platforms.
XDR is intended to provide a security team with full visibility into all endpoints and network infrastructure, allowing for unified remediation, improved understanding of attacks, and unified threat hunting.
10. CWPP. A Cloud Workload Protection Platform (CWPP) solution discovers workloads that exist within an organization’s cloud-based deployments and on-prem infrastructure. Once the workloads have been discovered, the solution provides a vulnerability scan.
Based on the results of the scan, CWPP solutions often provide options for mitigation. Fixes for identified issues include implementing allowlists, integrity protection and similar solutions.
In addition to addressing the security issues identified in the assessment, the CWPP can also provide protection against common security threats to cloud and on-premises workloads. These include runtime protection, malware detection and remediation and network segmentation.
A CWPP offers a number of benefits to organizations; from increased agility, to better security, to a reduction in data compliance violations.
Related resources
#2023#2024#Accessibility#ai#Algorithms#Analytics#APIs#applications#approach#apps#architecture#assets#audit#authentication#automation#Behavior#Big Data#Business#CASB#Check Point#Cloud#cloud environment#Cloud Security#Cloud-Native#CloudGuard#complexity#compliance#corporate security#credential#credential rotation
0 notes
Text
SaaS Implementation with Microservices for Modern Businesses
Software as a Service (SaaS) has become a cornerstone of modern business operations, providing a flexible and scalable solution for various applications.
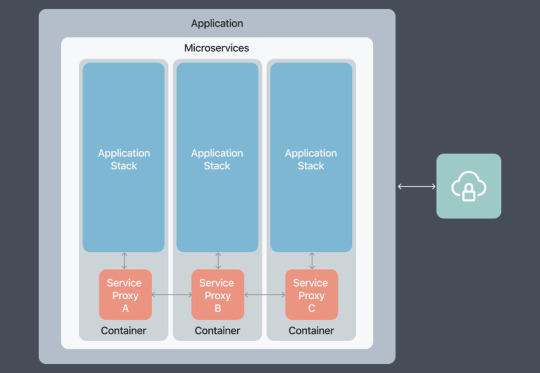
When combined with microservices architecture, SaaS not only enhances operational efficiency but also offers agility, scalability, and improved user experiences. In this article, we will explore the synergies of SaaS implementation with microservices and how this dynamic duo is reshaping the landscape of business software.
Microservices: The Building Blocks of Agility: Microservices architecture involves breaking down complex applications into smaller, independently deployable services. This modularity aligns seamlessly with the on-demand nature of SaaS, allowing for faster development cycles and more agile responses to changing business needs.
Scalability at its Core: One of the primary advantages of combining SaaS with microservices is scalability. Microservices enable businesses to scale specific components of an application independently, ensuring optimal resource utilization and performance, especially in a cloud-based SaaS environment.
Flexibility and Customization: Microservices empower SaaS providers to offer customizable solutions, allowing users to pick and choose the services that align with their specific requirements. This flexibility enhances user satisfaction and ensures that businesses pay only for the features they need.
Enhanced Reliability and Resilience: With microservices, if one service encounters an issue, it doesn't necessarily affect the entire application. This inherent fault isolation improves the reliability and resilience of SaaS platforms, ensuring uninterrupted services even in the face of isolated failures.
Rapid Deployment and Continuous Integration: Microservices facilitate rapid deployment of updates and new features, a crucial aspect in the dynamic landscape of SaaS. Continuous integration and continuous delivery (CI/CD) pipelines ensure that changes can be seamlessly integrated and deployed, minimizing downtime.
Optimized Resource Utilization: Microservices allow for efficient use of computing resources as each service can be scaled independently based on demand. This optimized resource utilization translates into cost savings for both SaaS providers and end-users.
Improved User Experiences: Microservices enable SaaS applications to deliver a more responsive and interactive user experience. With the ability to independently scale user-facing services, microservices contribute to reduced latency and enhanced overall performance.
Security and Compliance: The modular nature of microservices facilitates better security practices. SaaS providers can implement specific security measures for each microservice, ensuring a robust security posture. This approach is particularly beneficial for meeting compliance requirements in various industries.
Data Management and Integration: Microservices simplify data management and integration in SaaS applications. Each microservice can have its own database, and APIs can be designed to enable seamless communication between services, fostering a cohesive and well-integrated ecosystem.
Future-Proofing SaaS Platforms: By leveraging microservices in SaaS implementation, businesses can future-proof their platforms. The modular architecture allows for easy updates, integrations with emerging technologies, and adaptation to changing business requirements.
Conclusion: The combination of SaaS implementation with microservices is a powerful paradigm that not only enhances the efficiency of business software but also aligns perfectly with the demands of the modern digital landscape. As businesses continue to seek flexible, scalable, and responsive solutions, the integration of SaaS and microservices stands as a beacon for a new era of innovation and effectiveness in software delivery.
0 notes
Text
How to get SOC 2 Certification in India?

/ Uncategorized / By Mysore intr
Introduction of SOC 2 Certification in India
SOC 2 certification in India is gaining substantial traction for carrier businesses coping with client statistics or those impacting their clients’ security, availability, processing integrity, confidentiality, and privacy (the “Trust Service Principles”).
What is SOC 2 Certification in India?
Developed with the aid of the American Institute of CPAs (AICPA), SOC 2 (Service Organization Control 2) assesses the suitability of the design of a carrier organization’s controls relevant to these Trust Service Principles.
It guarantees clients that the service corporation’s controls protect their data and structures efficiently.
In India, it replaces older standards like SSAE sixteen and SAS 70 and is derived in kinds:
Type 1: Evaluate the design of controls at a particular factor in time.
Type 2: Assesses the design and running effectiveness of controls over a time frame, usually six months.
Benefits of SOC 2 Certification in India:
Increased belief and credibility: SOC 2 Certification in India demonstrates commitment to information security and privacy, solidifying your popularity and attracting more customers.
Improved internal controls: The audit technique strengthens your management systems, improving data safety and operational performance.
Competitive gain: Stands you out from the competition, giving you a facet in securing new business.
Reduced threat of compliance issues: Mitigates potential non-compliance penalties or statistics breaches.
Enhanced patron relationships: Builds trust and transparency with customers by showcasing your commitment to the security of their records.
Who Needs SOC 2 Certification in India?
Any provider agency managing touchy customer data or impacting their clients’ protection posture can gain from SOC 2 certification in India. This includes:
Cloud carrier vendors
Data middle operators
BPOs
Managed protection service companies (MSSPs)
IT provider companies
Software as a service (SaaS) groups
How to get SOC 2 Certification in India
Preparation:
Choose the form of SOC 2 report: Decide if you want a Type 1 (layout of controls) or Type 2 (design and working effectiveness of controls) report, depending on your favoured level of warranty and patron necessities.
Select a certified CPA firm: Partner with a good Certified Public Accountant (CPA) organization experienced in conducting SOC 2 audits in India. Check their know-how and qualifications, and track files with comparable customers.
Gap analysis and pre-assessment: Conduct a gap evaluation to assess the weaknesses of your controls compared to the Trust Service Principles. Consider a pre-evaluation with your preferred CPA company for more excellent, nuanced feedback.
Develop and record your controls: Implement and document your internal controls relevant to the chosen Trust Service Principles. Prepare policies, strategies, and evidence for their implementation.
Audit Engagement:
Formalize the engagement: Sign a formal settlement with the CPA firm outlining the audit scope, fees, timeline, and deliverables.
Provide statistics and get entry to Share relevant documentation, access to structures and resources, and personnel interviews with the CPA firm to facilitate the audit technique.
Respond to inquiries and findings: Address any questions and cooperate with the CPA organization during the audit. Be prepared to make precise methods, offer additional proof, and deal with potential manipulation deficiencies.
Report and Certification:
Review the SOC 2 document: The CPA firm will produce a film based on their findings, assessing the suitability of your controls and supplying pointers for development.
Address any corrective movements: Implement endorsed corrective movements to bolster your controls before finalizing the file.
Receive the last report and certification: Upon fulfilling the necessities, the CPA organization will trouble the final SOC 2 file, and you can formally declare the accreditation.
Start early: The SOC 2 Certification in India is a process can take numerous months, so plan and guide appropriately in advance.
Communicate successfully: Maintain a clean verbal exchange with your preferred CPA organization at some point in the system to ensure smooth progress.
Seek ongoing preservation: Continuously enhance your inner controls and consider normal SOC 2 re-certifications to maintain compliance and competitive benefit.
Why Factocert for SOC 2 Certification in India
We provide the best SOC 2 consultants in India, Who are very knowledgeable and provide the best solution. And to know how to get SOC 2 certification in India. Kindly reach us at [email protected]. SOC 2 Certification consultants work according to SOC 2 standards and help organizations implement SOC 2 certification in India with proper documentation.
For More Information visit: SOC 2 Certification in India
Related Links:
ISO 21001 Certification in India
ISO 37001 Certification in India
ISO 27701 Certification in India
ISO 26000 Certification in India
SOC 2 Certification in India
0 notes
Text
Advancing The Security Operations Center (SOC): New Technologies and Processes Can Help Mitigate Cyber Threats
The Nature of Emerging Cyber-Threats
Remote work, global interconnectivity, and the digital attack surface have significantly increased the complexity of businesses’ IT perimeters. New cybersecurity methods are required for emerging technologies like the Internet of Things, machine learning, artificial intelligence, and 5G. The global shortage of trained cybersecurity employees and limited experience in safeguarding data are exacerbated by the cybersecurity crisis. Advanced cyberweapons, dark web forums, and resource sharing pose significant threats to criminal syndicates and state actors. Improved Security Operations Centers (SOC) capabilities are necessary for businesses to manage, monitor, and react to cybersecurity threats.
How effective is the Security Operations Center (SOC)?
An efficient SOC may handle physical security, business systems, and control systems. It is meant to provide constant threat mitigation, detection, and prevention systems. Moreover, SOC teams find vulnerabilities, mitigate risks, and manage incidents that could be taking place on company networks or systems. The ability of analysts and the security team to quickly and accurately understand and respond to threats determine how successful a SOC will be.
What are the benefits of the Security Operations Center (SOC)?
1. Enhanced Security Posture: While continually monitoring for security threats and vulnerabilities and taking appropriate action to mitigate them, a SOC boosts an organization’s security posture. This can aid in preventing security problems and protecting the assets of the company.
2. Improved Visibility: A SOC gives security experts a consolidated overview of the company’s security posture, making it simple for them to understand what’s going on across its networks, systems, and applications.
The Security Operations Center’s Importance (SOC)
The importance of SOCs is a global issue, and the European Community has just passed a new law that acknowledges the importance of the SOC function. By improving detection, preparedness, and reaction to serious or catastrophic events, the proposed EU Cyber Solidarity Act seeks to boost cybersecurity. Adding cutting-edge national and international Security Operations Centers (SOCs) charged with identifying and responding to cyber threats creates a European Cybersecurity Shield and a Cyber Emergency Mechanism.
Improve SOC capabilities and functions with new SOC products and solutions
SOC technologies have drawn a lot of attention from companies looking to improve cybersecurity. The significance of SOCS for cybersecurity is also being discussed at events and conferences as the threat matrix expands. Here are a few examples of products and solutions in various SOC operations domains that can improve SOCs and their operators in the upcoming years.
A New Molecular Set of Solutions Leveraging Connected Interfaces, Automation, and AI to Help SOC Operators
AI-enabled security solutions are available through IBM’s QRadar Suite to optimize and speed up threat detection, investigation, and response procedures. This complete package combines security data and response procedures with SOC analyst toolkits and is provided as a SaaS, enabling companies to choose and adapt solutions for their specific needs.
It is crucial to train SOC staff
Several institutions focus on SOC certifications; the following two are detailed.
1. The SANS Institute, which was founded in 1989, was created with the goal of giving cybersecurity professionals the skills and expertise they need to improve the world. They provide materials for SIEM, Elastic Stack, and modern detection methods in addition to SOC training certificates.
2. CompTIA offers SOC analyst certification training while fighting for the global information technology industry and the 75 million people that work in its development and maintenance.
Strategies for SOC Risk Management
1. Security by Design is the starting point for any risk management strategy, particularly for those who are software or hardware developers worried about security. Moreover, the DHS CISA recently released a plan for both the corporate and governmental sectors to improve security by developing a specific strategy.
2. Defense in Depth. In the security world, there are several solid definitions of defense in depth. According to a NIST document, the Defense-in-depth idea is “an important security design framework that has considerable relevance to industrial control systems (ICS), cloud services, sensitive data storage, and many other sectors.”
3. Zero-trust (ZT) is a cybersecurity model in which defenses are shifted from static edges to users, assets, and resources. Zero-trust architecture (ZTA) plans industrial and corporate infrastructure and processes based on zero-trust principles. It makes no assumptions about implicit confidence provided to assets or user accounts based on physical or network locality or asset ownership. Zero-trust protects resources rather than network segments and can help a company’s overall information technology security posture.
Conclusion
The cutting-edge technologies displayed at RSA and other events to address cybersecurity problems will be a huge help to the security operations center (SOC) in 2023. Businesses, governments, and organizations must be proactive in developing the capabilities of security operations centers, which means being aware of the resources that are available and the operational needs.
0 notes