#security challenges
Text

The United States government, having built an expensive border wall to combat illegal immigration and smuggling, faces ongoing challenges as sophisticated underground tunnels undermine its effectiveness. In response, clandestine efforts are underway to bolster border security. Turning to Tesla Shield Technology, the government aims to deter unauthorized crossings by disintegrating individuals or vehicles attempting to breach the border from below. However, this technology inadvertently hinders US citizens seeking refuge during a significant natural disaster, as the formidable barrier proves insurmountable for many Americans attempting to flee the country. Kindly follow the provided link to view: https://tubitv.com/movies/100006606/borders
#BorderSecurity#immigration policy#Tesla Shield#Underground Tunnels#National Security#BorderWall#Illegal Immigration#Humanitarian Crisis#Border Protection#Security Challenges
0 notes
Text
Pakistan Selections 2024 & its perpetual tightrope destiny
In the grand theater of South Asian politics, Pakistan’s post-election scenario is shaping up to be less of a triumphal procession and more of a high-wire act over a pit of economic despair, political vendettas, and regional brimstone. As the newly minted government takes the stage, one can’t help but admire the audacity—or is it naivety?—of stepping into the limelight where the plot twists rival…
youtube
View On WordPress
#2024#democracy in Pakistan#economic crisis#geopolitical saga#IMF bailout#Imran Khan#Indo-Pak rivalry#military influence#Pakistan elections 2024#political drama#Political-Satire#regional tensions#security challenges#TTP resurgence#Youtube
0 notes
Text
Crypto Heists Surpass $11 Billion, Prompting Industry-wide Push for Enhanced Security
The world of cryptocurrency grapples with a dual narrative of successes and challenges, as outlined in a recent blog post by Comparitech. While digital currencies showcase increasing value and creative applications, the persistent concern of security breaches and thefts remains a critical issue, with over $11 billion worth of cryptocurrency stolen to date.
The blog post delves into specific incidents, such as the $620 million heist from Axie Infinity's Ronin Network, which exposed vulnerabilities in the widely popular play-to-earn game. Poly Network experienced a $610 million theft, with a notable twist as the hacker returned most of the funds, and Binance confronted a $570 million hack. The blog emphasizes that beyond the monetary losses, these incidents erode trust in the digital asset space.
Additionally, the blog points to historical breaches, including a $547 million heist from Coincheck, revealing the dangers of storing large amounts of cryptocurrency in online "hot wallets." The multi-year saga of MT Gox, where $470 million worth of Bitcoin was stolen, underscores the industry's early vulnerabilities.
As the number of crypto heists rises, Comparitech calls for immediate action to ensure the safety of users' digital assets. The blog advocates for exchanges and platforms to prioritize secure storage solutions, conduct thorough code audits, and adopt best practices for user authentication. It also highlights the crucial role of regulators in establishing clear guidelines and enforcing standards to prevent further breaches in the evolving landscape of cryptocurrency security.
#cryptocurrency industry#security challenges#thefts#Axie Infinity#Ronin Network#Whale Alert#XRP#Binance#Bitfinex#retracted claim#Coincheck#Cryptotale
0 notes
Text
The border crossings from Mexico into the United States
The border crossings from Mexico into the United States have long been a focal point of complex and contentious issues. The dilemma surrounding these crossings is multifaceted, involving social, economic, and political dimensions. It is essential to approach this topic with a nuanced understanding, acknowledging the various factors contributing to the challenges faced by those attempting to enter…

View On WordPress
#Border crossing#human rights#Immigration Reform#MexicoUnitedStates#Migration Complexity#order Security#Security Challenges#turkish border
0 notes
Text
Alert: House Homeland Security Chairman Warns of Dangerous Times in the U.S.
https://headlinehorizon.com/U.S./Terror/1341
Get the latest news on the House Homeland Security Chairman's warning about the dangerous state of affairs in the United States. Explore the escalating security challenges and potential threats, including cyber attacks and terrorism.
#House Homeland Security Chairman#security challenges#dangerous times#headline horizon#news#latest news
0 notes
Text
Addressing Data Security Concerns in IT Staff Augmentation Partnerships
In the realm of IT staff augmentation partnerships, data security stands as a non-negotiable priority, particularly when operating outside India. At iValuePlus, we recognize the critical importance of protecting your sensitive data throughout the IT staff augmentation journey. This blog delves into the pivotal role of addressing data security concerns and highlights how our HR generalist services contribute to a secure partnership.
Data Security Challenges in IT Staff Augmentation
For organizations venturing into IT staff augmentation, data security is a constant concern. Why is it so crucial?
Data Sensitivity: IT projects often involve handling proprietary information, customer data, or intellectual property. Any compromise in data security can have severe consequences.
Regulatory Compliance: Various regions have stringent data protection regulations. Adherence to these regulations is not just ethical but also legally mandatory.
How HR Generalist Services Enhance Data Security
iValuePlus takes a comprehensive approach to data security, integrating HR generalist services into our IT staff augmentation process.
Thorough Vetting: Our HR generalists conduct rigorous background checks and screenings of IT professionals, ensuring their trustworthiness and commitment to data security.
Data Protection Measures: We implement cutting-edge data encryption techniques and access controls to safeguard your information at every stage of the project.
A Global Commitment to Data Security
iValuePlus extends its commitment to data security beyond borders, recognizing the unique challenges of global operations.
Global Compliance Expertise: We stay well-versed in data protection laws and regulations worldwide, ensuring that your project remains compliant regardless of location.
Secure Collaboration Tools: We provide secure communication and collaboration tools, facilitating seamless interaction between your team and our IT staff augmentation professionals while maintaining data security.

Conclusion
In the pursuit of IT staff augmentation partnerships outside India, data security must always be at the forefront. At iValuePlus, we make it our mission to prioritize data security through meticulous HR generalist services and global expertise. Your sensitive information will remain confidential and secure throughout the partnership. Reach out to iValuePlus today to fortify your IT staff augmentation projects with unwavering data security.
0 notes
Text
Read the updated report on the safety and security of humanitarian personnel and protection of United Nations personnel.

In its resolution 72/131, the General Assembly requested the SecretaryGeneral to submit to the Assembly, at its seventy-third session, a comprehensive and updated report on the safety and security of humanitarian personnel and protection of United Nations personnel and on the implementation of the resolution.
It also requested that the Secretary-General include in his report an assessment of the impact of safety and security risks on such personnel, and of the development, implementation and outcomes of policies, strategies and initiatives of the United Nations system in the field of safety and security.
The present report pf the covers the 18-month period from January 2017 to June 2018. It presents an overview of the global security environment, the associated security threats, risks and challenges facing United Nations personnel, the Organization’s response to these threats, the strategic challenges faced by the Organization and concludes with observations and recommendations for consideration by the Assembly
#United Nations Department of Safety and Security#emergency relief coordinator#relief workers#humanitarian crises#security threats#security risks#security challenges
0 notes
Text
IoT Adoption and Security Issues in French Cities
The Internet of Things (IoT) is rapidly changing the way we interact with technology, and French cities are no exception. As urban centers seek to become more efficient and sustainable, they are increasingly turning to IoT devices to help manage everything from traffic flow to energy usage. However, as with any new technology, there are also significant security challenges that must be addressed…

View On WordPress
#Citizen engagement#CYBERSECURITY#Data management#Data privacy#Digital transformation#Energy efficiency#French cities#Internet connectivity#IoT#Mobile devices#Network security#Public services#Risk management#Security challenges#Sensor technology#Smart cities#Sustainability#Urban infrastructure#Urban planning
0 notes
Text

Guys, I think I've found my new style. I call it "Bargen Bin Tim Burton"
#evil art style challenge#security breach#five nights at freddy's#daycare attendant#sundrop#fnaf#sun fnaf#fnaf dca#sunbug#hw2 sun#help wanted 2
2K notes
·
View notes
Text

day 16: lost :')
#bald moon#a silly one to celebrate getting halfway through the challenge! :D#posting this a bit later than usual but PHEW I MADE IT#dca promptober#fnaf daycare attendant#daycare attendant#fnaf sb#fnaf security breach#five nights at freddy's#fnaf#moondrop#fnaf moon#fnaf dca#my art#sundrop#fnaf sun#dca fandom
2K notes
·
View notes
Text
Insecurity: Bagudu Says Security Challenges Not Peculiar To Nigeria
President Muhammadu Buhari has made tremendous investments in security from 2015 to date.
This position was made public by the governor of Kebbi State, Senator Abubakar Atiku Bagudu through a statement issued by his Special Adviser (SA) on Media, Yahaya Sarki.
Bagudu equally noted that a lot of tangible progress has been recorded during the period under review, particularly on the welfare of…

View On WordPress
0 notes
Text

late night talks <3
#tumblr let me post challenge#i am going to post each image#one at a time#OH MY GOD IT WORKED#WAS THAT IT??? YOU JUST DIDNT WANT MULTIPLE IMAGES IN A POST???#okay whatever#my art#security breach#sun fnaf#fnaf sun#charlie daydreamers#sundrop fnaf#sundrop#sun security breach#sun x y/n
657 notes
·
View notes
Text


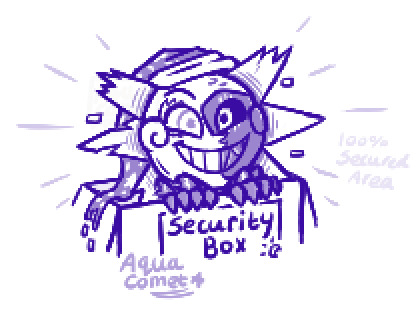
Eclipsed Security AU doodles from Sessions 19 and 21 from the DCA weekly magma! Also featuring a colour palette challenge Eclip and the most secured box you've ever seen.
So long as you don't break one of their rules ECLIP will be friendly, if you do? Well, you should probably start running.
#aquadoodles#magma/aggie doodles#art with IDs#fnaf#fnaf au#fnaf ruin#Eclipsed security au#ECLIP au#cw eye strain#< for the pink background in the colour challenge just in case#cw eye contact#from the art backlog
549 notes
·
View notes
Text
Last Line Challenge
Rules:
In a new post, show the last line you wrote (or drew) and tag as many people as there are words (or however many as you like).
Tagged by @starriegalaxy Thanks jestie!! It's my first time doing a challenge, I'm excited! ✨
Last Line: "It was an accident" <- from the @daycarefriendpickup magma sesh! Sun may or may not have lost control and y/n may or may not be bleeding out as a result (oops...)
Last Art: I've roughly 20+ sketches ongoing and 0 motivation to complete any of them so take all these wips! HYAHHHH!! 💫💥
Agent Dusk from @lavenoon's amazing Accidentally Undercover AU 💕:

Colour studies on Agent Dawn (same AU as Dusk) and the most mentally sound™ Sun:

More scribbles....
And ..... this.... (why did I draw this)

This is an open invite for anyone to do the challenge! (because I'm have crippling social anxiety and I don't want to be imposing ajdhska) If you are looking for a sign to do the challenge, this is it!! Time to get to it!!! 👉👉 (Or don't! I'm not the boss of you!)
#One day... I'll beat my social anxiety *clenches fist while a single tear runs down my face*#Some of these wips will never see the light of day again :'D#But the I'll defo finish the Accidentally Undercover wips!!#Agents Dusk and Dawn have my brain in a chokehold....#fnaf security breach#fnaf sb#dca fandom#moondrop x reader#sunnydrop x reader#my art#tag game#last line challenge
264 notes
·
View notes
Text
I think one of the worst moments in buffy history is them framing xander's speech about riley in into the woods as like... correct in any way. it makes you really dislike Xander (even more). Buffy's boyfriend literally cheats on her with vampire prostitutes lol and then tells her that if she doesn't forgive him on the spot he's leaving forever. and then we're supposed to buy that Xander is correct in saying that it's all Buffy's fault and that she should run after Riley to beg him to stay?
It's sooo infuriating how Riley is framed as 'the one who got away' when really he's 'the one who was so cripplingly insecure that he couldn't handle his girlfriend being stronger than him and having her own problems because he's made his entire identity about his girlfriend instead of getting the fuck over himself'
the real reason why xander doesn't want buffy to dump riley's ass as she should is so clearly because he projects onto riley. subconsciously he thinks that if someone 'normal' like riley can be with buffy then he also has a shot. newsflash it wasn't riley being 'normal' it was riley being an insecure condescending freak just like u
#and i actually like xander. s7 xander starts to be better. comics xander is near flawless#xander harris shut up forever about buffy's love life at least until youve gone to therapy challenge#i do think buffy could be with someone normal but they would have to be extremely secure well adjusted and also just a chill person#which neither riley nor xander fits.#i dont think there's any buffyverse human male who fits this though tbf#btvs#btvs thoughts
239 notes
·
View notes
Text



🎃🕸️ SPOOKY 🕸️🎃
I hadn't actually planned on doing anything Halloween related but then I just used it as an excuse to draw something and have fun with colours lol.
Colour palettes from color-meanings.com
Inspo songs: [Trick or Treat], [Black Swing], [Sunglasses at Night]
#art#battle priest#halloween#colourful#colour palette challenge#yes i was listening to a lot of thematic electro-swing music whilst doing these why do you ask lol#izm's pic is subtitled “give me back my priest” since thats the only reason i could think he'd be staring into a security cam XD#also listen “sunglasses at night” was just kinda hilarious for rire#hm kinda disappeared there for a while been...exceptionally screaming at work/life/etc. busy busy#doodle#kinda i mean i banged these out pretty quickly lol
887 notes
·
View notes