#securitytools
Link
https://cnn.it/43dDpFf - 🔒 The US Cybersecurity and Infrastructure Security Agency (CISA), a key federal entity tasked with enhancing cybersecurity across the nation, was compromised last month, resulting in the temporary shutdown of two crucial computer systems. These systems were integral for the sharing of cyber and physical security tools among federal, state, and local officials, as well as for the security assessment of chemical facilities. The breach underscores the universal risk of cyber vulnerabilities and highlights the importance of robust incident response plans for ensuring resilience. #Cybersecurity #CISAHack #IncidentResponse 🛡️ In response to the attack, a CISA spokesperson emphasized that the incident had no operational impact and that efforts are ongoing to upgrade and modernize their systems. This situation serves as a poignant reminder that no organization is immune to cyber threats, and it is essential to continuously improve and fortify cybersecurity measures. The affected systems were part of older infrastructure already slated for replacement, illustrating the need for timely updates in technology to safeguard against such vulnerabilities. #CyberDefense #SystemUpgrade #CyberResilience 🌐 The breach was reportedly executed through vulnerabilities in virtual private networking software by Ivanti, a Utah-based IT company. CISA had previously warned federal agencies and private sector firms to update their software to mitigate risks posed by these vulnerabilities. This incident has exposed the continuous battle against cyber threats and the imperative of adhering to cybersecurity advisories for protection against potential breaches. #CyberAlert #SoftwareVulnerability #CyberSafety 🕵️♂️ While the exact perpetrators of the hack remain unidentified, it is speculated that a Chinese espionage group exploiting Ivanti’s software vulnerabilities could be involved. This reflects the sophisticated and diverse nature of cyber threats facing organizations today. Even the most secure entities are not exempt from the risk of cyber attacks, as evidenced by the hacking of the personal account of the US’ top cybersecurity diplomat last year. The incident reiterates the pervasive challenge of maintaining cybersecurity in an increasingly digital world.
#Cybersecurity#CISAHack#IncidentResponse#CyberDefense#SystemUpgrade#CyberResilience#CyberAlert#SoftwareVulnerability#CyberSafety#CyberThreats#Espionage#DigitalSecurity#cisa#infrastructuresecurity#computersystems#securitytools#cybersecurity#shutdown#mods#facilities#vulnerability#speaker
0 notes
Text
6 ways AI can help security teams punch back

While AI is mostly seen as opening a new front in the threat landscape, it will also be tapped to fight back against bad actors. https://jpmellojr.blogspot.com/2023/11/6-ways-ai-can-help-security-teams-punch.html
#generativeAI#securitytools#codesecurity#analystexperience#threatprediction#incidentresponse#threatdetection
0 notes
Photo

Ensuring that your website is secure is crucial for protecting your users' data and maintaining your reputation. Here are some steps you can take to ensure your website is secure:
A. Use HTTPS: Use HTTPS to encrypt all data transmitted between your website and your users' browsers. This protects against eavesdropping and ensures that data cannot be tampered with.
B. Use strong passwords: Use strong passwords for all user accounts and administrative access. Encourage users to use strong passwords as well, and consider implementing two-factor authentication.
C. Keep software up to date: Keep all website software, including content management systems, plugins, and themes, up to date to prevent vulnerabilities from being exploited.
D. Use website security tools: Use website security tools like Sucuri or Wordfence to protect your website from hacking attempts, malware, and other security threats.
E. Regularly back up your website: Regularly back up your website to ensure that you can quickly recover from any security incidents or data loss.
By following these steps, you can help ensure that your website is secure and protect your users' data.
#webdesign#websitedesign#digitalmarketing#webdevelopment#webdesigner#marketingtips#websitesecurity#HTTPS#passwordsecurity#softwareupdates#backups#securitytools
0 notes
Text
Top 5 Reasons to Perform VAPT of Your Web Application

1. For Identifying Gaps Between Security Tools
2. For Prioritizing Risk
3. For discovering loopholes & Misconfigurations
4. For Improving Your Product SDLC Process
5. For Ensuring the Best Out Of Your Cyber Security ROI
Now share your Thoughts with us in the 𝗖𝗼𝗺𝗺𝗲𝗻𝘁 section
Read the full blog: https://bit.ly/3VVDBEw
0 notes
Photo

The world of the web is increasingly becoming vulnerable to cybercrime. 50 million users in September last year and this was just one of the breaches that made headlines and shocked the entire world.
Read In Detail: https://www.weblinkindia.net/blog/biggest-cyberattacks-2019-protect-website
0 notes
Text
Top 20 Open Source Vulnerability Scanner Tools in 2023
Top 20 Open Source Vulnerability Scanner Tools in 2023 @vexpert #vmwarecommunities #100daysofhomelab #homelab #OpenSourceVulnerabilityScanners #SecurityTools #VulnerabilityAssessment #PenetrationTesting #SQLInjection #NetworkVulnerabilityTests
In the world of cybersecurity, having the right tools is more important than ever. An extremely important tool for cybersecurity professionals is the vulnerability scanners. They are designed to automatically detect vulnerabilities, security issues, and potential threats in your systems, applications, or network traffic. By carrying out network vulnerability tests and scanning web applications,…

View On WordPress
#Container Image Scanning#License Compliance#Network Vulnerability Tests#Open Source Vulnerability Scanners#Penetration Testing#Security Testing#security tools#Software Composition Analysis#SQL Injection#Vulnerability Assessment
0 notes
Text
Wholeaked: Find the Responsible Person in Case of Leakage | #DataLeakage #Privacy #SecurityTools #Wholeaked #Security
0 notes
Photo

Norton give you more benefits on their antivirus. More protection, security and 24/7 support services. https://www.webtoolsoffers.com/blog/top-10-benefits-of-norton-antivirus #securitytools #safetyandsecurity #support #antivirus #software #protect #norton #virus #malware #virusprevention #prevention #deals #offers #cyber #threats #virusremoval #advertising #affiliatemarketing #blogging #safetytips (at New York, New York) https://www.instagram.com/p/B7GSDQMnaDR/?igshid=1tn5v2nj8rphs
#securitytools#safetyandsecurity#support#antivirus#software#protect#norton#virus#malware#virusprevention#prevention#deals#offers#cyber#threats#virusremoval#advertising#affiliatemarketing#blogging#safetytips
1 note
·
View note
Photo

1 note
·
View note
Link
https://bit.ly/3SSDF86 - 🔍 Guardio Labs unveils "SubdoMailing" — a widespread subdomain hijacking campaign compromising over 8,000 domains, including MSN, VMware, and eBay. Millions of malicious emails circulate daily, exploiting trust and stolen resources. #SubdoMailing #CyberSecurity 📉 Guardio's email protection systems detect unusual patterns, leading to the discovery of thousands of hijacked subdomains. The operation involves complex DNS manipulations, facilitating the dispatch of spam and phishing emails under reputable brands. #EmailSecurity #DNSManipulation 📧 Examining a deceptive email reveals clever tactics, including image-based content to bypass spam filters. SPF, DKIM, and DMARC authentication are manipulated, allowing scam emails to reach users' inboxes. #EmailScam #CyberAttack 💻 Analysis uncovers the resurrection of abandoned domains, enabling subdomain hijacking for malicious activities. Actors manipulate SPF records, creating a web of authorized senders to evade detection. #DomainSecurity #SPFManipulation 🛡 Guardio identifies a coordinated campaign by threat actor "ResurrecAds," exploiting compromised domains for mass email dissemination. The operation spans diverse tactics, including SPF authentication injection and SMTP server hosting. #ThreatActor #CyberCrime 🔎 Tracking indicators of compromise reveals the extensive infrastructure behind "SubdoMailing," spanning hosts, SMTP servers, and IP addresses. The operation's scale and sophistication underscore the need for collaborative defense efforts. #CyberDefense #ThreatAnalysis 🔒 Guardio launches a "SubdoMailing" checker tool to empower domain owners in reclaiming control over compromised assets. The tool provides insights into abuse detection and prevention strategies. #CyberAwareness #SecurityTool 📢 Join Guardio in raising awareness about the "SubdoMailing" threat and utilizing the checker tool to fortify domain security. Together, we can mitigate the impact of malicious email campaigns and safeguard digital landscapes.
#SubdoMailing#CyberSecurity#EmailSecurity#DNSManipulation#EmailScam#CyberAttack#DomainSecurity#SPFManipulation#ThreatActor#CyberCrime#CyberDefense#ThreatAnalysis#CyberAwareness#SecurityTool#DomainProtection#ebay#dmarc#stolenresources#domain#emails#cybersecurity#operation#brands#emailsecurity
0 notes
Link
#Devstree#WebSecurity#webSecurityTools#OnlineApplications#Security#WebDevelopment#websites#SecurityTools
0 notes
Photo
#SecurityTools #cybersecurity #itsecuritysolutions https://www.instagram.com/p/CC5Mgmcg-3I/?igshid=1t0belfz0xhlk
0 notes
Photo
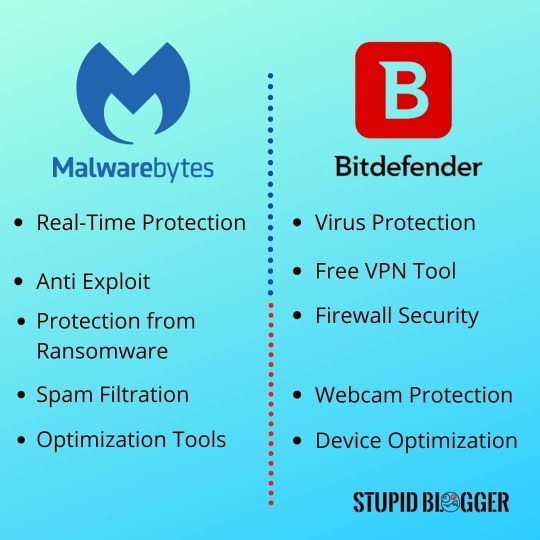
You can check their prices, plans and important information. Here, you can get the discount on both of these #antivirus #software. Grab the coupons now. https://www.stupidblogger.com/malwarebytes-vs-bitdefender.html #safetytools #securitytools #safetyandsecurity #safetytips #virusprevention #virus #virusprotection #deviceprotection #ransomeware #malware #cybersecurity #networksecurity #affiliatemarketing #advertising #onlinethreat https://www.instagram.com/p/B9br4d5BL_p/?igshid=1ti5jankyw17p
#antivirus#software#safetytools#securitytools#safetyandsecurity#safetytips#virusprevention#virus#virusprotection#deviceprotection#ransomeware#malware#cybersecurity#networksecurity#affiliatemarketing#advertising#onlinethreat
0 notes
Photo

Ram Internet Security is a software tool designed to help protect you from known threats. Internet security suites make it easy to track and monitor the security of your computer. Visit: https://ramantivirus.com/ram-ultimate-antivirus/ #internetsecurity #threads #securitytools https://www.instagram.com/p/B3BjmwphIrO/?igshid=entioaa6oatm
0 notes
Photo

Mariana Trench: Static Analysis Tool for Android and Java Apps | #Android #Java #SecurityTools #StaticAnalysis #Security
0 notes
Text
Utilidades para Pentesters/RedTeam: Commando VM 2.0
Fireeye ha presentado en el Blackhat la versión 2.0 de su VM Commando para pentesting. A diferencia de otras distribuciones para pentesting, Commando está basada en Windows.
Fireeye diseño específicamente Commando VM para que sea la plataforma de referencia para realizar pruebas de penetración interna. Los beneficios de usar Commando VM incluyen soporte nativo para Windows y Active Directory, usar su VM como área de preparación para marcos de comando y control (C2), navegar más fácilmente (e interactivamente) recursos compartidos de red y usar herramientas como PowerView y BloodHound sin preocupaciones de tener que colocar archivos de salida en los activos del cliente.
Más información en:
https://www.fireeye.com/blog/threat-research/2019/08/commando-vm-customization-containers-kali.html
El repositorio para descargarla e información de su instalación:
https://github.com/fireeye/commando-vm

0 notes