#SoftwareVulnerability
Explore tagged Tumblr posts
Link
https://cnn.it/43dDpFf - 🔒 The US Cybersecurity and Infrastructure Security Agency (CISA), a key federal entity tasked with enhancing cybersecurity across the nation, was compromised last month, resulting in the temporary shutdown of two crucial computer systems. These systems were integral for the sharing of cyber and physical security tools among federal, state, and local officials, as well as for the security assessment of chemical facilities. The breach underscores the universal risk of cyber vulnerabilities and highlights the importance of robust incident response plans for ensuring resilience. #Cybersecurity #CISAHack #IncidentResponse 🛡️ In response to the attack, a CISA spokesperson emphasized that the incident had no operational impact and that efforts are ongoing to upgrade and modernize their systems. This situation serves as a poignant reminder that no organization is immune to cyber threats, and it is essential to continuously improve and fortify cybersecurity measures. The affected systems were part of older infrastructure already slated for replacement, illustrating the need for timely updates in technology to safeguard against such vulnerabilities. #CyberDefense #SystemUpgrade #CyberResilience 🌐 The breach was reportedly executed through vulnerabilities in virtual private networking software by Ivanti, a Utah-based IT company. CISA had previously warned federal agencies and private sector firms to update their software to mitigate risks posed by these vulnerabilities. This incident has exposed the continuous battle against cyber threats and the imperative of adhering to cybersecurity advisories for protection against potential breaches. #CyberAlert #SoftwareVulnerability #CyberSafety 🕵️♂️ While the exact perpetrators of the hack remain unidentified, it is speculated that a Chinese espionage group exploiting Ivanti’s software vulnerabilities could be involved. This reflects the sophisticated and diverse nature of cyber threats facing organizations today. Even the most secure entities are not exempt from the risk of cyber attacks, as evidenced by the hacking of the personal account of the US’ top cybersecurity diplomat last year. The incident reiterates the pervasive challenge of maintaining cybersecurity in an increasingly digital world.
#Cybersecurity#CISAHack#IncidentResponse#CyberDefense#SystemUpgrade#CyberResilience#CyberAlert#SoftwareVulnerability#CyberSafety#CyberThreats#Espionage#DigitalSecurity#cisa#infrastructuresecurity#computersystems#securitytools#cybersecurity#shutdown#mods#facilities#vulnerability#speaker
0 notes
Text
**LibTracker Updates: Simplify Dependency Management with this simple SBOM Tool**
At Windmillcode, we are committed to equipping organizations with tools that enhance software development efficiency and security. Our latest updates to **LibTracker**, a cutting-edge VSCode extension, reinforce our mission to simplify dependency management and provide actionable insights for your applications.
**Access LibTracker today**: [Visual Studio Marketplace](https://marketplace.visualstudio.com/items?itemName=windmillcode-publisher-0.lib-tracker)
### **Recent Enhancements**
- **Enhanced Import/Export Capabilities**:
- Flexible options to append, overwrite, or intelligently merge projects and apps with matching names, streamlining SBOM updates.
- Comprehensive import validation to eliminate errors and ensure accuracy.
- **Expanded Application Coverage**:
- Broader support now includes all npm applications, providing unparalleled flexibility for developers managing diverse tech stacks.
### **Looking Ahead**
Our roadmap reflects our commitment to continuous improvement and user-focused innovation:
- **Advanced App Detail Page**:
- Security management tools for adding, updating, or removing dependencies, with options for version control.
- Snapshot functionality to safeguard against unintended impacts of updates or testing changes.
- Bulk update options to save time and effort.
- **Performance Enhancements**:
- Refreshed refresh logic and optimized caching for faster, more reliable operations.

LibTracker is engineered to empower development teams with the precision and control necessary to drive success in today’s fast-paced software landscape. Join us in shaping the future of dependency management.
#softwaredevelopment#dependencymanagement#SBOMtools#VSCodeextension#npmapplications#softwaresecurity#versioncontrol#licensingcompliance#softwareefficiency#softwarevulnerabilities#applicationmanagement#developmentworkflows#modernsoftwaretools#dependencyupdates#developmentteamtools#softwareoptimization
0 notes
Photo

#Stuxnet #worm #antivirus #malwareanalysis #services by #cyspaceglobal #payload #exploitation #softwarevulnerability #zeroday #vulnerabilities #security #incidentmanagement #informationtechnology #informationsystems #informationsecuritymanagement #soc #redteam #blueteam #socanalyst #databreaches #cyspace https://www.instagram.com/p/CDgREoggyOD/?igshid=t2aw1enlwj77
#stuxnet#worm#antivirus#malwareanalysis#services#cyspaceglobal#payload#exploitation#softwarevulnerability#zeroday#vulnerabilities#security#incidentmanagement#informationtechnology#informationsystems#informationsecuritymanagement#soc#redteam#blueteam#socanalyst#databreaches#cyspace
0 notes
Text
Hackers Have Knowledge of Problems Regarding the Block Chain Thus Taking Advantage of Same in Making Data Breach
0 notes
Photo

Researcher Demonstrates Several Zoom Vulnerabilities at DEF CON 28 #cybersecurity #hackingnews #softwaresecurity #softwarevulnerabilities #videoconferencingsoftware #hacker #hacking #cybersecurity #hackers #linux #ethicalhacking #programming #security #mrhacker
0 notes
Photo

Researcher Demonstrates Several Zoom Vulnerabilities at DEF CON 28 #cybersecurity #hackingnews #softwaresecurity #softwarevulnerabilities #videoconferencingsoftware #vulnerability #zoom #zoomsecurity #hacking #hacker #cybersecurity #hack #ethicalhacking #hacknews
0 notes
Photo
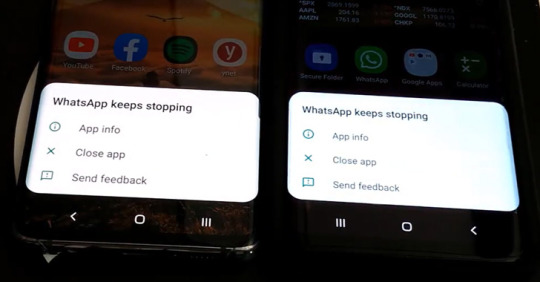
This Bug Could Have Let Anyone Crash WhatsApp Of All Group Members | TheHackerNews.Co #crashandroidphone #crashwhatsapp #cybersecurity #hackingwhatsapp #softwarevulnerabilities #hacker #hacking #cybersecurity #hackers #linux #ethicalhacking #programming #security #thehackernews
0 notes
Text
Vulnerability Assessment and Penetration Testing Solutions (VAPT) for AWS Cloud
Software security is a very challenging field and implementing a good security solution requires smart tools that can analyse everything from infrastructure to applications so we can implement best practices to prevent the known attack patterns at application, middleware & server levels.

( Image Credit )
First part of implementing a good security solution requires us to understand the vulnerabilities through assessment and penetration testing mechanisms known as VAPT so we can work on improving the overall solution security. Generally, application security testing involves both static and dynamic analysis for uncovering various security issues.
This blog post summaries various options available for application and server level VAPT that are well suited for AWS Cloud workloads. Please find a quick overview and our recommendations:
Nessus - One of the most popular open source vendors with enterprise plans and support for their scanner tool. You can use Nessus for server level VAPT and it generates great reports with insights. This is our default choice for server level vulnerability assessment. You can install the tool in EC2 instance and use it to scan all servers.
VeraCode - They are a leading vendor in Gartner Magic Quadrant and offer a good solution for application level VAPT. You can use their solutions for pre-production application testing to continuous assessment of both web and mobile applications. Application VAPT is very important aspect as most of the attacks are targeted at this layer.
WhiteHat Security - They are known as thought leaders in the application security space and offer a SaaS platform for application vulnerability management. Their Sentinel offering is a leading solution with actionable insights for identified vulnerabilities. Their source code analysis toolkit is good for pre-production security assessment of application code.
IndusGaurd Web Scanner - One of the emerging web security solution vendors from India with great local support. They provide application level VAPT with business logic testing and also support mobile applications. They offer both on-demand & continuous scanning service for web applications. They are our web security solutions partner.
Open Source Solutions - There are multiple open source options for application and server level VAPT testing. Our favourites include W3AF, Grabber, OpenVAS and Vega. You can keep track of this list at http://sectools.org/tag/vuln-scanners/
Hope you have enjoyed reading this blog post, let us know if you need any help. Also we would love to hear about your experience of working with different tools.
0 notes
Link
https://bit.ly/45FrD7h - 🛡️ The Andariel threat group, linked to Lazarus, has been targeting Korean entities like national defense, politics, energy, communications, and more since 2008. These attacks also extend to various Korean institutions such as universities and ICT companies. #CyberSecurity #ThreatGroup 📧 In the initial stages, Andariel employs spear phishing, watering hole, and supply chain attacks. They are known for using a diverse range of malware in their operations, including backdoors like Andarat, Rifdoor, TigerRAT, and MagicRAT. #Malware #CyberAttack 🔍 AhnLab Security Emergency Response Center (ASEC) has been monitoring the Andariel group and recently analyzed attacks from the first half of 2023. Many of the 2023 attacks utilized malware developed in the Go language, with some cases even using Rust. #TechAnalysis #CyberDefense 🖥️ In February 2023, ASEC detailed an Andariel attack exploiting vulnerabilities in the Innorix Agent program. This software was primarily used in Korean universities and was susceptible to versions earlier than INNORIX Agent 9.2.18.450. #SoftwareVulnerability #CyberThreat 🐀 Recent investigations highlight that malware strains, including Black RAT and Goat RAT developed in Go, are being used in their campaigns. A trend also shows increasing use of malware like DurianBeacon developed in both Go and Rust. #MalwareTrends 🔥 In March 2023, Andariel launched attacks against Korea's defense sector and an electronics manufacturer. Their tools of choice included the known TigerRAT, which has been consistently employed by the group since 2020. #CyberEspionage #DefenseSecurity 🎯 ASEC's analysis indicates a strong possibility that the same threat actor is behind recent attacks on Korean universities and corporations. Similarities in attack methods, malware types, and targets suggest this alignment with past operations of the Andariel group. #ThreatIntelligence #CyberForensics In conclusion, consistent targets, methods, and malware trends suggest that the Andariel group is persistently focusing on Korean entities. The cybersecurity community is urged to stay vigilant against these evolving threats.
#CyberSecurity#ThreatGroup#Malware#CyberAttack#TechAnalysis#CyberDefense#SoftwareVulnerability#CyberThreat#MalwareTrends#CyberEspionage#DefenseSecurity#ThreatIntelligence#CyberForensics#StaySafe#CyberAwareness
0 notes
Photo

#Darkweb #security #services by #cyspaceglobal#payload #exploitation #softwarevulnerability #zeroday #vulnerabilities #incidentmanagement #informationtechnology #informationsystems #informationsecuritymanagement #soc #redteam #blueteam #socanalyst #databreaches #cyspace https://www.instagram.com/p/CDdz_dAgufO/?igshid=182a0if5xhchk
#darkweb#security#services#cyspaceglobal#payload#exploitation#softwarevulnerability#zeroday#vulnerabilities#incidentmanagement#informationtechnology#informationsystems#informationsecuritymanagement#soc#redteam#blueteam#socanalyst#databreaches#cyspace
0 notes
Photo

#Security services by #cyspaceglobal #exploitation #softwarevulnerability #zeroday #vulnerabilities #security #services by #cyspaceglobal #incidentmanagement #informationtechnology #informationsystems #informationsecuritymanagement #soc #redteam #blueteam #socanalyst #databreaches #cyspace #cybersecurityconsultant #cyspaceglobal #cyspacegroups #cyspacelabs https://www.instagram.com/p/CDbQxLUgLNx/?igshid=1np5pilqr0r5y
#security#cyspaceglobal#exploitation#softwarevulnerability#zeroday#vulnerabilities#services#incidentmanagement#informationtechnology#informationsystems#informationsecuritymanagement#soc#redteam#blueteam#socanalyst#databreaches#cyspace#cybersecurityconsultant#cyspacegroups#cyspacelabs
0 notes
Photo

#Youtubechannel for hackers #Shellcode #payload #exploitation #softwarevulnerability #zeroday #vulnerabilities #security #services by #cyspaceglobal #incidentmanagement #informationtechnology #informationsystems #informationsecuritymanagement #soc #redteam #blueteam #socanalyst #databreaches #cyspace https://www.instagram.com/p/CDbP5HMAHtd/?igshid=hq5x4mxbfva1
#youtubechannel#shellcode#payload#exploitation#softwarevulnerability#zeroday#vulnerabilities#security#services#cyspaceglobal#incidentmanagement#informationtechnology#informationsystems#informationsecuritymanagement#soc#redteam#blueteam#socanalyst#databreaches#cyspace
0 notes
Photo

#Shellcode #payload #exploitation #softwarevulnerability #zeroday #vulnerabilities #security #services by #cyspaceglobal #incidentmanagement #informationtechnology #informationsystems #informationsecuritymanagement #soc #redteam #blueteam #socanalyst #databreaches #cyspace https://www.instagram.com/p/CDWz1DQgxcW/?igshid=rwezq6iq4rx3
#shellcode#payload#exploitation#softwarevulnerability#zeroday#vulnerabilities#security#services#cyspaceglobal#incidentmanagement#informationtechnology#informationsystems#informationsecuritymanagement#soc#redteam#blueteam#socanalyst#databreaches#cyspace
0 notes
Text

#Stuxnet #worm #antivirus #malwareanalysis #services by #cyspaceglobal#payload #exploitation #softwarevulnerability #zeroday #vulnerabilities #security #incidentmanagement #informationtechnology #informationsystems #informationsecuritymanagement #soc #redteam #blueteam #socanalyst #databreaches #cyspace
0 notes
Text

#Darkweb #security #services by #cyspaceglobal#payload #exploitation #softwarevulnerability #zeroday #vulnerabilities#incidentmanagement #informationtechnology #informationsystems #informationsecuritymanagement #soc #redteam #blueteam #socanalyst #databreaches #cyspace
0 notes
Text

#Youtubechannel for hackers #Shellcode #payload #exploitation #softwarevulnerability #zeroday #vulnerabilities #security #services by #cyspaceglobal#incidentmanagement #informationtechnology #informationsystems #informationsecuritymanagement #soc #redteam #blueteam #socanalyst #databreaches #cyspace
0 notes