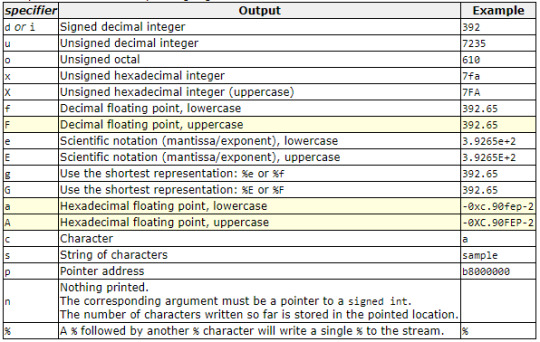
#sha256 algorithm calculator
Explore tagged Tumblr posts
Text
Introduction
This document provides a technical overview of the security protocol implemented by Viber.
Starting with Viber 6.0, all of Viber's core features are secured with end-to-end encryption: calls, one-on-one messages, group messages, media sharing and secondary devices. This means that the encryption keys are stored only on the clients themselves and no one, not even Viber itself, has access to them.
Viber's protocol uses the same concepts of the "double ratchet" protocol used in Open Whisper Systems Signal application, however, Viber's implementation was developed from scratch and does not share Signal's source code.
Terms
Viber Account - a collection of devices registered with Viber for the same phone number. An account is made up of one primary device and (optional) unlimited secondary devices. Messages sent or received by any device is displayed on all other registered devices of the same account, from the time of their registration and onward (past history cannot be seen).
Primary device - a mobile phone running iOS, Android or Windows Phone, and registered to Viber's service using a phone number managed by a mobile operator.
Secondary device - typically an iPad, Tablet or Desktop PC, which must be linked to a primary device.
ID Key - a long-term 256-bit Curve25519 key pair used to identify a Viber account. The ID key is generated by the primary device only.
PreKeys - a set of medium-term Curve25519 key pairs used to establish one-on-one secure sessions between devices. PreKeys are generated separately by each device in an account.
Session - a two-way secure virtual link between two specific devices. Secure sessions are automatically established between all devices of the same account, and between any two devices of different accounts that exchange messages. A secure session with a different account is identified in Viber by a gray lock in the conversation screen.
Trust - a state between two accounts which indicates that the peer account is authenticated and that no man-in-the-middle attacker has interfered with the session established between any two devices in the account. Users can establish trust by following the authentication procedure described below. A trusted session is identified in Viber by a green lock.
Breach of trust - a state between two accounts that occurs when the ID Key of a trusted peer has changed after trust was established. This can happen legitimately if the peer user has replaced his primary device, reinstalled Viber, or if keys were lost due to storage malfunction. However, it can also happen if a man-in-the-middle is eavesdropping on the conversation. A breached session is identified in Viber by a red lock.
Preparations for Session Setup
During installation, every primary Viber device generates a single 256-bit Curve-25519 key-pair called ID Key. The private part of the key is stored on the device, while the public part of key is uploaded to the Viber servers. Secondary devices (PCs and Tablets), receive the private key from the primary device via a secure method described in "Secondary Device Registration", below.
Additionally, every Viber client generates a series of PreKeys. Each PreKey has two 256-bit Curve-25519 key-pairs called Handshake Key and Ratchet Key. The private keys are all stored on the device, while the public keys are uploaded to the server. The server holds several keys per device and requests more when they drop below a configurable threshold. Each request causes the client to generate additional keys and upload the public parts to the server.
Secure Session Setup
A session needs to be established only once between every two Viber devices wishing to communicate securely. Once a session exists, it can be used to send an unlimited number of messages in either direction.
To send a secure message, secure sessions must exist between the sending device and all the recipient's devices, as well as between the sending device and all the sender's other devices. So for example, if user A that has a mobile phone and a PC registered to Viber under the same account wishes to communicate with user B that has a mobile phone and a PC, secure sessions must be established between each pair of devices.
Sessions between devices of the same account are established when the devices are registered. Only a single session is required between any two devices, and that session can be used to synchronize any number of conversations with other Viber accounts.
In order to establish a session with a different account, the device ("Alice") wishing to establish a session with a peer ("Bob") sends a query to the Viber server with the recipient's phone number. The server responds with the peer's public ID Key and a series of peer public PreKeys, one per each device registered on "Bob’s” account. "Bob’s" devices are not required to be online when this happens.
"Alice" device then generates two 256-bit Curve-25519 key-pairs as its own handshake and ratchet keys, and derives a Root Key, as follows:
RootKey = SHA256 ( DH(IDAlice, HSBob) || DH(HSAlice, IDBob) || DH(HSAlice, HSBob) )
The RootKey is then used to derive a session key using:
TempKey = HMAC_SHA256(RootKey, DH (RatchetAlice, RatchetBob))
New RootKey = HMAC_SHA256(TempKey, "root")
SessionKey = HMAC_SHA256(TempKey, "mesg")
DH indicates the use of Elliptic-Curve Diffie-Hellman key-exchange algorithm. HS indicates Handshake Key.
The different strings passed to the HMAC functions ensure that even if the session key is compromised, the root key cannot be derived back from it.
"Alice" then sends to "Bob" a session start message containing its own public ID, an identifier of "Bob’s” pre-key that was used for this session, and its own public handshake and ratchet keys. When "Bob" goes online and retrieves this message from its inbox, it can reconstruct the same Root and Session keys using the same DH procedure.
It should be noted that if a session is established with a peer's primary device but cannot be established with a secondary device (for example, because it is offline and out of PreKeys on the server), the conversation will still be secured with end-to-end encryption, but that secondary device will not be able to decrypt those messages and thus, will not be able to display them.
Exchanging Messages
A device sending a message to a target user needs to encrypt this message for every session with every device that the target user has. To accomplish this, an ephemeral one-time 128-bit symmetric key is generated and is used to encrypt the message body using Salsa20 encryption algorithm. This ephemeral message key is then encrypted using each recipient's session key. The sender device sends a unified message to the server, containing one encrypted cyphertext and a set of encrypted ephemeral keys. A server-side fan-out slices this message and delivers the relevant parts to each target device.
The two devices take turns at advancing the session keys in a process called ratcheting. Each time the direction of the conversation changes, the device whose turn it is randomly generates a new Ratchet key pair, and once again performs the following sequence:
TempKey = HMAC_SHA256(RootKey, DH (RatchetAlice, RatchetBob))
New RootKey = HMAC_SHA256(TempKey, "root")
SessionKey = HMAC_SHA256(TempKey, "mesg")
With Ratchetthis_device being the private part of the newly derived key-pair. Alongside each message, the public part of the Ratchetthis_device is also sent. The recipient runs DH with its last private ratchet together with the sender's public ratchet.
This double-ratchet accomplishes two things: first, the continuous ratcheting provides forward and backwards secrecy so even if the keys are compromised, past and future messages cannot be decrypted. Second, the algorithm maintains the authentication of the peer, because the DH chain of the root keys started with both devices' ID Keys. If the ID key of the peer is trusted at any point, the entire chain can be trusted.
Encrypted Calls
Each side of a call generates an ephemeral 256-bit Curve25519 key-pair. The public part is signed using the device private ID Key and is exchanged between the two devices during call setup phase. The other side authenticates the request using the peer's public ID key.
Each device verifies the signature, and performs DH calculation to derive a one-time session key. The session key is valid only for the duration of this specific call, and is not saved in non-volatile storage.
The RTP stream of the audio or audio/video call is converted to SRTP and encrypted via Salsa20 algorithm using the session key.
Photo, Video and File Sharing
The sending client generates an ephemeral, symmetric Salsa20 key and encrypts the file. The encrypted file, together with an HMAC signature, is uploaded to Viber servers. An additional MD5 signature is calculated over the encrypted data and sent together with the file in order to allow the storage server a simple way of verifying transmission integrity regardless of the end-to-end encryption.
The sender then sends a Viber message to the recipient with the ID of the uploaded file and the encryption key. This message is end-to-end encrypted using the encrypted session between the sender and recipient.
The recipient generates a download link from the file ID, downloads the encrypted file and decrypts it using the key.
Secure Groups
All members of a secure group share a common secret key (a symmetric Salsa20 encryption key) which is not known to Viber or to 3rd parties.
For new groups, this shared secret is generated by the group creator and sent to all participants using the secure one-on-one sessions described above. For non-secure groups that were created with past Viber versions, this secret is generated by the first member who sends a message to the group chat after all group members have upgraded to the secure version. In the Viber application any group member can add additional participants to a group. These participants will receive the secret from the group member that added them.
The group secret is ratcheted forward using a HMAC-SHA256 with every message sent. Each group message contains a sequence number that indicates the number of times that the hash function has been invoked. Different clients always pick up where the last message has left off and continue the hashing chain from that point, so keys are not reused. Forward secrecy is maintained by the one-way hashing algorithm; even if the key is compromised, past conversations cannot be decrypted. Past keys are discarded by the client and not saved to not-volatile storage, except for a short window of past hashes which is used in race conditions when two or more participants write to the group simultaneously.
Secondary Device Registration
A key feature in the Viber ecosystem is the concept of secondary devices. A secondary device is a PC, an iPad or a Tablet which is paired with a user's mobile phone and sees the same message history of both incoming and outgoing messages.
Viber's end-to-end encryption on secondary devices works as follows:
Encryption is done separately for each device. If some user A sends a message to user B that has two devices, then user A needs separate end-to-end sessions with the two devices and encrypts the data twice, each one using a different set of keys.
Authentication is done just once for the entire account. If user A trusts user B, the trust is automatically applied to all of user B's devices, not just one.
The authentication is accomplished by sharing the private ID Key between all devices of the same account. The ID Key is generated only by the primary device, and is transmitted to the secondary devices during registration in a secure method, as follows:
The secondary device generates an ephemeral 256-bit Curve-25519 key-pair.
The device then generates a QR code containing the device's "Viber UDID" (a publicly accessible unique device ID generated by Viber) plus the public part of the ephemeral key pair.
The user uses his primary device to scan the QR code.
The primary device also generates a 256-bit Curve-25519 key-pair and performs DH calculation with the public key from the QR. The result is hashed using SHA256 to create a shared secret.
The primary then encrypts its own private ID key with this secret and sends it and the public part of the ephemeral key through the Viber servers to the target device, identified by its UDID as read from the QR code. The cyphertext is signed using HMAC-SHA256.
The secondary device receives the message, performs the same DH and hash to obtain the same secret, and uses it to decrypt the primary private ID Key.
The ID key is part of the DH chain that creates the shared secrets for the one-on-one sessions. Therefore, without the correct ID, the secondary device cannot participate in any secure conversations that the primary device is part of.
Authentication
Authentication provides a means of identifying that no man-in-the-middle attacker is compromising the end-to-end security. In the Viber application, authentication is done in the context of a Viber audio (or audio/video) call.
When in a call, each user can tap on the lock screen to see a numerical string which is computed as follows:
Both devices perform DH calculation using their own private ID key and the peer public ID key as published during call setup phase.
The DH result is hashed using SHA256 and trimmed to 160 bits. Those 160 bits are then converted to a string of 48 decimal characters (0-9).
Both parties should see the same string of numbers and can compare them by reading them to the call participant. If both sides hear the other side read out loud the same string of numbers as they see on their own screen, this gives a very high degree of certainty that the ID keys have not been tampered with and that no man-in-the-middle exists for this conversation.
The ID key verification protects both the secure calls and secure 1-1 chats. In calls, the ID key is used to sign the key exchange DH message. In 1-1 chats, the ID key functions as the root of the DH chain leading to the shared secret generation. In turn, 1-1 session protects group sessions because the group keys are exchanged over 1-1 sessions.
Known Limitations
At this time, in the Viber iOS application for iPhone and iPad, attachments such as images and videos which are sent via the iOS Share Extension are not end-to-end encrypted. The iOS Share Extension is invoked when a user selects an image or video from the iOS pictures library (the "camera roll"), clicks the "send" button, and selects Viber as the send target. Attachments sent using this method are still encrypted in transit (using HTTPS), but are not end-to-end encrypted. To ensure that your images and videos are fully end-to-end encrypted, send them from your Viber application directly and not from the iOS pictures library. This limitation applies only to iOS and will be addressed in a future release.
1 note
·
View note
Text
Starts Fast Bitcoin Mining Free with Realmining
https://www.cryptoerapro.com/bitcoin-miner/

You’l possible create less than one penny PER YEAR
Android phones simply aren't powerful enough to match the mining hardware employed by serious operations.
So, it would possibly be cool to setup a miner on your Android phone to determine how it works. But don’t expect to make any money.
Do expect to waste a ton of your phone’s battery!
What is bitcoin miner Mining Hardware best bitcoin miner wallet
bitcoin miner mining hardware (ASICs) are high specialised computers used to mine bitcoins.
The ASIC industry has become complicated and competitive.
Mining hardware is currently only located where there is cheap electricity.
When Satoshi released Bitcoin, he supposed it to be mined on computer CPUs.
Enterprising coders soon discovered they might get more hashing power from graphic cards and wrote mining software to permit this.
GPUs were surpassed in turn by ASICs (Application Specific Integrated
Nowadays all serious bitcoin miner mining is performed on ASICs, usually in thermally-regulated knowledge-centers with access to low-cost electricity.
Economies of scale have so led to the concentration of mining power into fewer hands than originally supposed.
What Are bitcoin miner Mining Pools? best bitcoin miner wallet
Mining pools enable tiny miners to receive additional frequent mining payouts.
By joining with other miners in a very cluster, a pool allows miners to search out blocks more frequently.
But, there are some problems with mining pools as we have a tendency to'll discuss.
As with GPU and ASIC mining, Satoshi apparently didn't anticipate the emergence of mining pools.
Pools are groups of cooperating miners who conform to share block rewards in proportion to their contributed mining power.
This pie chart displays the present distribution of total mining power by pools:
Whereas pools are fascinating to the common miner as they sleek out rewards and build them a lot of predictable, they sadly concentrate power to the mining pool’s owner.Bitcoin Miner
Nowadays there are very skilled industrial mining operations. Let's have a look at how they work.What will a mining farm seem like?
Let's have a look inside a real bitcoin miner mining farm in Washington state.
bitcoin miner mining farms completely use ASIC miners to mine various coins. Several of these farms are minting several Bitcoins per day.
How abundant do crypto mining farms create? How a lot of a mining farm makes depends on several factors:
The worth it pays forelectricity How previous its mining hardware is The scale of its operation The worth of bitcoin miner when the miner sells it The level of problem when the bitcoin miner is mined By far, the largest issue affecting how much money a mining farm makes is how abundant it pays for electricity. Nearly all mining farms are using the same hardware.

Since the rewrd for locating a block is fastened, and the difficulty is adjusted based mostly on total processing power working on finding blocks at any given time, then electricity is the sole value that is variable. If you'll be able to realize cheaper power than different miners, you can afford to either increase the scale of your mining operation, or pay less on your mining for the same output.
How abundant electricity do mining farms use As previously mentioned, mining farms use a ton of electricity. How abundant they consume depends on how massive their operation is. However the most recent Bitmain ASIC miner consumes concerning 1350 watts.
In total, it is estimated that each one mining farms can use about seventy five terrwat hours of electricity in the year 2020. That's roughly the equivalent to 15 times the yearly energy consumption of denmark.
minng across globe Mining farms are located the world. We do not apprehend where each mining farm in the planet is, but we tend to have some educated guesses.
Most of the mining has been and still is located in China. Of course, as of 20twenty, it's believed that as a lot of as 65percent of bitcoin miner mining
Why is so a lot of Mining happening in China? Samson Mow of Blockstream and former CTO of BTCC mining pool explains.
The main benefits of mining in China are faster setup times and lower initial CapEx that, along with nearer proximity to where ASICs are assembled, have driven industry growth there
Samson Mow CSO, Blockstream BONUS CHAPTER one Necessary bitcoin miner Mining Terms best bitcoin miner wallet
During this bonus chapter, we tend to will find out about some of the foremost common terms associated with bitcoin miner mining.
If you are considering mining at any level, understanding what these terms suggests that will be crucial for you to get started.
Miner Anyone who mines Bitcoins (or any different cryptocurrency).
Block Reward The block reward is a mounted quantity of Bitcoins that get rewarded to the miner or mining pool that finds a given block
A assortment of individual miners who 'pool' their efforts or hashing power together and share the blockreward. Miners produce pools because it increases their probabilities of earning a block reward.
ly each four years, the block reward gets cut in [*fr1]. The primary block reward ever mined was in 2008 and it it absolutely was for fifty Bitcoins. That block reward lasted for four years, where in 2012, the primary reward halving occured and it dropped to twenty five Bitcoins.
In 2016, a second halving occured where the reward was reduced to 12.five Bitcoins. And as of the time of this writing, we have a tendency to are on the cusp of the third halving (ETA Could 11th), where the reward can be curtail to 6.twenty five Bitcoins. You'll notice the foremost up to date estimation of precisely when the following halving will occur on our bitcoin miner block reward halving clock
ASIC represent "Application Specific Integrated Circuit". In plain english, that simply means it's a chip designed to try and do one very specific reasonably calculation. In the case of of an ASIC miner, the chip in the miner is meant to unravel problems using the SHA256 hashing algorithm. This is critical GPU mining, explained below.
nce you mine for Bitcoins (or any cryptocurrency) employing a graphics card. This was one in all the earliest styles of mining, however is not profitable thanks to the introduction of ASIC miners. Bitcoin Miner
Hashing Power (or Hash Rate) How many calculations (hashes) a miner can perform per second.
Or it will consult with the total amount of hashing done on a sequence by all miners put along - also known as "Internet Hash".
You'll be able to learn a lot of about Hash Rate by reading our article regarding it.
Problem Measured in Trillions, mining difficulty refers to how exhausting it is to seek out a block. The present level of difficulty on the bitcoin miner blockchain is the first reason why it is not profitable to mine for most individuals.
Problem Adjustment mining farm bitcoin miner was designed to supply block reliably every ten minutes. Because total hashing power (or Web Hash) is consistently changing, the issue of finding a block needs to adjust proportional to the quantity of total hashing power on the network.
In terribly simple terms, if you have four miners on the network, all with equal hashing power, and 2 stop mining, blocks would happen ever 20 minutes instead of each 10. Thus, the difficulty of finding blocks also needs to chop in 0.5, therefore that blocks can continue to be found each 10 minutes.
Issue changes happen each 2,016 blocks. This ought to mean that if a brand new block is added each ten minutes, then a issue adjustment would occur every two weeks. The 10 minute block rule is just a goal though. Some blocks are added once additional than 10 minutes. Some are added after less. Its a law of averages and a heap if left up to chance. That doesn't mean that for the foremost part, blocks are added reliably every 10 minutes
A measurement of energy consumption per hour. Most ASIC miners can tell you how much energy they consume using this metric.

Compared to the carbon emissions from simply the cars of PayPal’s staff as they commute to figure, Bitcoin’s environmental impact is negligible.
As bitcoin miner could simply replace PayPal, credit card companies, banks and also the bureaucrats who regulate them all, it begs the question:
Isn’t traditional finance a waste? Bitcoin Miner
Not just of electricity, however of cash, time and human resources!
Mining Difficulty If solely 21 million Bitcoins will ever be created, why has the issuance of bitcoin miner not accelerated with the rising power of mining hardware?
Issuance is regulated by Difficulty, an algorithm which adjusts the problem of the Proof of work problem in accordance with how quickly blocks are solved inside a certain timeframe (roughly each two weeks or 2016 blocks).
Issue rises and falls with deployed hashing power to keep the typical time between blocks at around 10 minutes.
For most of Bitcoin's history, the common block time has been concerning 9.seven minutes. As a result of the value is often rising, mining power does come back onto the network at a fast speed that creates faster blocks. But, for many of 2019 the block time has been around ten minutes. This is because Bitcoin's price has remained steady for many of 2019.
Block Reward Halving Satoshi designed bitcoin miner such that the block reward, which miners automatically receive for solving a block, is halved every 210,000 blocks (or roughly four years).
As Bitcoin’s value has risen substantially (and is expected to keep rising over time), mining remains a profitable endeavor despite the falling block reward… a minimum of for those miners on the bleeding fringe of mining hardware with access to low-price electricity.
Honest Miner Majority Secures the Network To successfully attack the bitcoin miner network by making blocks with a falsified transaction record, a dishonest miner would need the majority of mining power thus as to maintain the longest chain.
This is often called a 51p.c attack and it allows an attacker to pay the same coins multiple times and to blockade the transactions of other users at can.
To realize it, an attacker wants to own mining hardware than all alternative honest miners.
This imposes a high financial price on any such attack.
At this stage of Bitcoin’s development, it’s seemingly that solely major corporations or states would be able to satisfy this expense… although it’s unclear what web benefit, if any, such actors would gain from degrading or destroying Bitcoin. Miner
Mining Centralization Pools and specialised hardware has sadly led to a centralization trend in bitcoin miner mining.
bitcoin miner developer Greg Maxwell has stated that, to Bitcoin’s seemingly detriment, a handful of entities control the vast majority of hashing power.
It is conjointly widely-known that at least fiftyp.c of mining hardware is found inside China.
But, it’s could be argued that it’s contrary to the long-term economic interests of any miner to aim such an attack.
The resultant fall in Bitcoin’s credibility would dramatically reduce its exchange rate, undermining the value of the miner’s hardware investment and their held coins.
Because the community could then commit to reject the dishonest chain and revert to the last honest block, a fifty one% attack most likely offers a poor risk-reward ratio to miners.
bitcoin miner mining is certainly not perfect but doable enhancements are invariably being suggested and thought-about.
https://www.cryptoerapro.com/bitcoin-miner/
1 note
·
View note
Link
What is the sha256 calculator:
The sha256 calculator is an online cryptographic hash function. Sha means ‘secure hash algorithm.’ Cryptographic hash functions are termed as unique mathematical operations. These operations operate on digital data. This is done by the comparison of a computed ‘hash’ to a known hash value. This allows a person to determine the integrity of a particular data/file.
#sha256 calculator#sha256 profit calculator#sha256 mining calculator#sha256 online calculator#free sha256 calculator#convert for free#sha256 calculator free#online sha256 calculator#sha256 online#digibyte sha256 mining calculator#digibyte mining calculator sha256#calculator#sha256 calculator file#sha256 algorithm calculator#sha256 calculator hex#sha256 calculator binary
0 notes
Text
Week 7 Morning Lecture

Midsem
First we looked at some questions on the midsem. Apparently there was quite a good outcome overall (subjectively according to Richard), and most people did worst on questions 5 and 10.
Question 5. National Security Guy for the President Missiles Richard reasons that the answer is in fact Type 1/Type 2 Error that you would be most worried about. Although the rest of the answers would be things that you would be concerned about, the main worry is that you launch when you shouldn’t (False Positive) and can’t take back the launch or you can’t launch when you need to (False Negative).
An attacker therefore could identify that only the President is able to command the launch as a single point of failure and then take him out, thereby dearming the whole nation of their firepower. In that instance, if any other nation were to attack America, then they wouldn’t be able to order missiles out because only the President has the capability to, who is now dead.
Ironically, the movie Dr Strangelove that we watched later in the evening session had a great display of this example - where a general was able to exploit the system and direct an attack on Russia which could not be recalled without the secret passcode.
Question 10. The Merkle Puzzle Question As revealed, Richard got this answer wrong, the original intended answer was something that could be broken feasibly by a person the night before the exam (Lachlan) and an attacker would not be able to in a reasonable amount of time. This is essentially the idea of Merkle puzzles - where on average, the bad guy has to do a work factor of around 1/500000 (half a million) before they crack the right one.
The originally intended answer was RSA 512 since it was the best answer out of all the options. The other options were as reasoned:
One Time Pad - Uncrackable
Caesar Cipher - Too easy
Vigenere Cipher - Too easy
RSA 2048 - Too hard (takes too long)
SHA256 - A hashing algorithm, irreversible
However it was noted that the RSA cracked would be done using the PUBLIC KEY for ALL OF THEM. Therefore an attacker would only have to crack one for the private key and then be able to crack the rest instantly!
What is proof of liveness? There were some additional security terms that were introduced in the exam which I hadn’t encountered before. One of which is this idea of proof of liveness, which essentially is a indicative check if a person is on the other side of the handshake or not. In modern senses this is like a challenge response, where the person requests access and gets given something to solve to prove they are alive.

Diffie-Hellman (Key Exchange)
From last week we talked about being able to communicate security with someone whom you’ve never met over the internet. However, for a computer, who only knows 0s and 1s, the only form of verification is through shared secrets (something you are, something you know and something you have). However, this poses an issue with someone on the other side of the world
how can you securely communicate the KEY used in order to communicate privately?
The answer is Diffie-Hellman key exchange!
Originally conceptualised by Ralph Merkle (this guy wow lmaooo) and named after Diffie and Hellman, the Diffie-Hellman is a method to securely exchange keys over a public channel. DH is one of the earliest implementations of a public-key protocol in cryptography.
The basic mathematics behind DH is that it utilises exponentiation and modulus in order to obtain Confidentiality. In the lectures, Richard simply covered a simplification using only exponentiation:
Richard and another person (let’s call him Frank) agree on a base number (e.g. 5). This is assumed public information, so it’s fine if everyone knows. Now then Richard and Frank each think of a secret number which they don’t tell anyone
Richard’s number = 7
Frank’s number = 3
Now they simply take the base and raise it to their secret number
Richard: 5^7 = 78125
Frank: 5^3 = 125
Then they simply send each other the result of this calculation (or the last few digits if you were to imagine it was modded). Although this example seems quite trivial to break, imagine if the base and the secrets were 20 digits long! Then it would be a lot harder to reverse the base and secret.
This occurs because of the Mathematical loss of information which makes it easy to encrypt and hard to reverse, also known as the Discrete Logarithm Problem, and is the reason why DH is so effective. (See: https://www.khanacademy.org/computing/computer-science/cryptography/modern-crypt/v/discrete-logarithm-problem)
In this case, the base and the result of the calculation are PUBLIC, while the kept secrets are PRIVATE.
Next to add another layer of security, Richard then takes the result sent by Frank publicly and raises that number to his secret number - and Frank does the same with Richard’s result.
Richard: 125^7 = 4E14
Frank: 78125^3 = 4E14
The resultant numbers from both operations are thereby EQUAL because of the COMMUTATIVE PROPERTY of powers. In this way by getting the same result, Richard and Frank are able to verify that they are indeed communicating with each other through a public protocol - and they can settle on the end result as the key for their communication.
The reason this works so well is because just through the initial messages, it’s impossible to find out from them what they key is. Since the key was never actually transmitted in messages, listening in on the communication won’t help an attacker! You’re not actually sending any information during the key exchange, but creating one together :)
We do this exactly in practice, where we mix up the information we are sending so that whoever is listening in is unable to decipher the secret from the message. This is called FORWARD SECRECY/SECURITY, which means that even if in future, if someone were to go back and uncover your old messages, they would still be encrypted and unable to be read.
Note: this doesn’t however provide Authentication because you can’t actually verify if it is really Frank or Richard from the other side. You can only tell through this that you’re still sending it to the same person, and that your line is confidential.

Sources: https://en.wikipedia.org/wiki/Diffie%E2%80%93Hellman_key_exchange
https://security.stackexchange.com/questions/45963/diffie-hellman-key-exchange-in-plain-english
https://www.khanacademy.org/computing/computer-science/cryptography/modern-crypt/v/diffie-hellman-key-exchange-part-2
Krak de Chevaliers
Krak de Chevaliers was a multi-layered fortress run by the Knights Templar in 1144CE (many years ago). This boi was STACKED, with a strong defence system (Defence in Depth) and prime location perched atop a hill - and as such was considered for many years virtually IMPREGNABLE, being the largest Crusader castle during the 12th century.
Many attacks were held against this fortress, and a few got through past the first wall, but none were able to reach the inner before being eviscerated. It was THAT GOOD.

The design of this boi is ingenious, with every line of physical defence covered. First it has several concentric layers that wear down attacks during their sieges. Then there are moats and several stages in which armies have to be split up due to the restrictions in entry points. Furthermore, they’ve got towers to lay hellfire to any attackers, with an elevated view for the inner wall which is both hard to penetrate being up so high as well as advantageous to provide a vantage point to provide support to the outer wall defences. Then you’ve got sloped points that are vulnerable for attackers and good for the defenders as well as sharp purposeful right angled walls so that there are minimal areas to cover against fire.
In the end however, the fortress did eventually fall to Muslim hands and the knights surrendered after a forged letter was sent through ordering them to lay down. So in the end, humans were the issue and despite all the complex defence mechanisms in place, even the mighty Krak de Chevaliers fell to SOCIAL ENGINEERING.
Sources:
https://www.ancient.eu/Krak_Des_Chevaliers/

Vulnerabilities
Let’s go over a few terms real quicc:
Vulnerability: a potential weakness in something
Exploit: taking advantage of a weakness (the application)
Software Bug: a mistake in something
Memory Corruption Memory Corruption refers to when a bad guy is able to modify and change what happens in memory (i.e. modifying address, contents stored in memory, etc). Through this the make programs do things that they aren’t originally supposed to.
One form of memory corruption is a Buffer Overflow which we saw last week (https://insecure.org/stf/smashstack.html) covered by Aleph One. This memory corruption happens on the Stack where a buffer can be written to past its given size and as such, data gets overwritten on the stack.
The vulnerability of this lecture is FORMAT STRINGS :) Now the thing with vulnerabilities is that it’s quite like the flu. Once someone discovers the vulnerability, they quickly discover that it’s everywhere. Every program and piece of code has it. Once word gets out, the big companies quickly work to patch it, but with smaller institutions and businesses (which is the vast majority of the population), don’t bother with it for a while; because of laziness or cost benefits, etc.
A simple way to illustrate the format string vulnerability is through a simple C program. You may be familiar with the function printf()from first year computing. The thing with printf()is that by good practice, you should be using formats as the first argument in the print function ( printf(%s, “Hello World”)). However we know from experience that this is NOT the case. Programmers are lazy and simply write the string as the first argument without specifying a format in the first place. In fact, pretty much every tutorial every will start with just telling you to pass the string “Hello World” directly into the function.
The issue then again lies in the case where a user is allowed to enter input and a programmer then prints whatever they enter to stdout.
For example, the program:
reads in an input
that input is stored in a variable name.
then the program simply executes printf(name);
Sure, the program is harmless when the user enters what we expect them to, however what if a format argument is passed (i.e. %d, %s, %n, %t, etc)?
Well if the user entered something like the string “Richard%x”:
printf()will take the letters Richard
print that out
and identify %x and look for the NEXT ARGUMENT to substitute into %x
However, in the above input, there is no next argument like in the case of %s, “Hello World’. So the program will then look to the next item on the stack and use that in place for %x. Thereby this format string attack can be used to gather information about what is stored on the stack, and you can decipher what was done in the previous functions.
While this may seem quite harmless, with just gathering information - this isn’t the extent of a format string attack. In fact, there are many many MANY formats you can use and each of them do a variety of things in C.
(this C++ but it the same lol)
From above %n is frighteningly scary because it actually WRITES TO MEMORY, storing the number of characters written to the pointed location. Now this can have extremely dangerous effects and is what we are so scared of when it comes to format strings attacks and memory corruption!
In practice, this is however quite difficult to do, but very much possible. It does take a certain amount of luck and preparation in order to successfully perform a truly devastating format string attack, however, Richard likens the situation with vulnerabilities to SWISS CHEESE.
If you take a block of swiss cheese and you slice it up in a few pieces, then rearrange it multiple times and try to line them those pieces up together, once in a while those holes will line up and you can stick your finger right through. It’s very much like this in reality. The bugs are the little holes which seem so small and insignificant on their own, with little format string reads from memory and buffer overflows. But if you pair all those attacks together, once in a while those bugs align and an attack is successful!

More Terms to Know
Shell Code
Let’s say you’re attacking a system, and you’ve gotten in - but you’re unsure what you want to attack at the moment. Well what you can do is simply generate a nice private shell externally on your computer which has access to their system remotely. This is what is known as shell code - writing code that generates an external shell which you have control over.
NOP Sled
NOP is a command in machine code that literally makes the CPU do nothing for a few cycles. So a NOP sled is simply just a sequence of these instructions to make the CPU slide to the desired destination. Therefore an attacker is able to utilise a NOP sled by making the program go to a specific address where they may have stored malicious code! The ingenious aspect of a NOP sled is that they are used to increase the attack area over a huge range of memory. That way the chances that the program lands anywhere in the NOP sled increases, and it trickles down to wherever they want to run. This deals with the issue of memory being randomised and allocated everywhere.
In Assembly, this is literally just:
NOP; NOP; NOP; NOP; NOP; NOP; NOP; // etc etc lmaoo
*Interestingly you can find programs which try and exploit this by simply Googling a sequence of NOP commands and you’ll land upon matching ones with NOP sleds :) (https://github.com/snoack/python-goto/commit/2b0f5e5069cbb88776b0d070d6608e4064735d96)
There are also other ways in which you can make a program ‘do nothing’. For example, making a program add 1 and subtract 1 continually to a register.
Sources:
https://www.oreilly.com/library/view/practical-malware-analysis/9781593272906/ch20s07.html
Responsible Disclosure
Let’s say you’re a bug bounty hunter, and you happen across a bug in some licensed software. What is the right way to go about alerting the developer/company? Normally companies will have some sort of feedback form in which you can submit reports on bugs and how to reproduce them. However if this isn’t the case, normally you should do some research about the bug you’ve encountered and generate a report to send to the company. In this way you’re first giving them time to fix it. In the instance that nothing gets done after you’ve informed them, you should slowly escalate the problem up the chain. The most important thing is to NOT LET THE BAD GUYS HAVE IT (unless you are one of them or ludicrous amounts of money is involved).
Assets
Assets are a very hard thing to define, but identifying what is important to protect is incredibly important because it allows you to prioritise your assets and how you can go about setting up defences.
In the lecture, Richard showed us the starting clip from the movie ‘Team America’ where a satirical team of over-the-top terrorist fighting Hollywood personalities went above and beyond to protect what they believed was the MOST IMPORTANT asset; the lives of the French civilians. In the following clip, we can see them using all force necessary (minus the hand to hand combat from Karate Kid) to put down the terrorists, but in the process they destroy some of the most monumental pieces of French history (notably the Louvre, Eiffel Tower, etc).
Video: https://www.youtube.com/watch?v=HIPljGWGNt4
One could argue that they did more harm than good than if they just let the terrorists blow up the citizens, however it’s really a matter of perspective as those people may value the historical assets over the human lives. This really is a tough question of ethics, but ultimately I think a good point is brought up here. History, no matter how beautiful and valuable, dims in the preciousness that is human life. If human life is taken out, there is a destruction of potential in the future - whereas historical artefacts can be recreated. History will be made anyway, so it’s arguable, but human life is ultimately the most precious asset.
History is Forgotten
Back when Richard was a boy, he recalls the time of the Cold War where Reagan and Gorbachev where locked in a heated battle of chicken. Both nations had nukes pointed at one another, in retaliation of the threat each imposed on one another. However, Richard had a thought:
“If the Russians attack America, and they don’t retaliate, in a few years people will just forget it happened and be happy that they have half a planet left”
While this is quite dark to think about, it is what I believe to be a cold truth. Time precedes all, and no matter how big the disaster or devastating the crime, people forget or stop caring anymore. If you think about all the great big battles that were such a huge deal at the time, now they’re almost so insignificant in the grand scheme of things. In the whole timeline of the Universe, a battle is simply an instant, and in a few hundred years people forget about it all.
Richard likens this phenomenon with the great poem “Ozymandias”, about the history ‘King of Kings’. Such a person with a magnificent statue must have been extremely great and honourable at the time. He might have been the biggest deal in his area, but ultimately time took him as well. And like the poem says, ‘nothing else remains’. Whatever happened with the great Ozymandias, no one knows or cares anymore. History has left him behind in the sands.
Opinion: In time, everything becomes insignificant and nothingness. Perhaps we should preserve what is truly valuable - that which is all precious and important. Although devastating would be the destruction of the Louvre, life is the greatest asset.
Poem:
I met a traveller from an antique land, Who said—“Two vast and trunkless legs of stone Stand in the desert. . . . Near them, on the sand, Half sunk a shattered visage lies, whose frown, And wrinkled lip, and sneer of cold command, Tell that its sculptor well those passions read Which yet survive, stamped on these lifeless things, The hand that mocked them, and the heart that fed; And on the pedestal, these words appear: My name is Ozymandias, King of Kings; Look on my Works, ye Mighty, and despair! Nothing beside remains. Round the decay Of that colossal Wreck, boundless and bare The lone and level sands stretch far away.”
Great reading + animation of ‘Ozymandias’ by Bryan Cranston from Breaking Bad: https://www.youtube.com/watch?v=sPlSH6n37ts
Protecting your Assets
You might value something as the most important asset, whereas an attacker might be after something else. So it’s very easy to protect the wrong thing and put resources into defending the wrong areas.
Richard had a friend who lived in Surry Hills which was a rough neighbourhood back in the day. Very often his car’s window would be smashed open with a brick and his car would be rummaged for money. However, his friend didn’t keep any money inside his car, and so he felt devastated, having to always pay to repair his broken window. To him, the most valuable asset was the car window. So his solution was simply to leave his car window open. That way, attackers would go approach and find that they wouldn’t need to break the window to get in. In the end, it worked!
So when you protect the right assets, you yield the best results. Coke knows that their most valuable asset is not their secret recipe - in fact, probably hundreds of thousands of employees across the globe know the recipe. Coke’s most valuable asset is their BRAND. The Coke brand has become so powerful that it has its own psychological effect on people. In fact, in a blind taste test between Coke and Pepsi, researchers found that Pepsi almost always won. However, when participants knew which was Coke and which was Pepsi, more often than not, they preferred Coke. Even more interesting is the fact that when analysing the brain during this process, researchers found that Pepsi lit up the part of the brain that dealt with taste and senses, whereas Coke lit up the area of the brain to do with Identity.
https://slate.com/business/2013/08/pepsi-paradox-why-people-prefer-coke-even-though-pepsi-wins-in-taste-tests.html

8 notes
·
View notes
Text
Cryptocurrencies (1/3)
What are they?
They are essentially a form of electronic money which rely on the underlying blockchain technology to make them decentralised and immutable. This means that anyone any use their computer / money to contribute towards the networks security which in turn means that we don’t have a central authority in control. The problems associated with centralisation are clear (they are ‘single points of failure’ in security) and they provide a means to control how users may spend their money (i.e. anti-freedom).
Each user in a network typically has a (public, private) key pairing which gives them ownership of the address. In order to move funds out of an address, they need to sign a transaction with the private key and include a public key address to send them to. Since we don’t have a central authority (’idealistically’), the process of sending funds from User A to User B is almost considered ‘direct’.

What are the different types?
Before we go into how they work, I think it’s important to distinguish the different types. The original sort is known as proof-of-work, where miners dedicate their processing / GPU power towards solving a mathematical problem which will add a block to the chain; the first computer to solve for this hash is given the reward for their work. In order to fake a ‘single block’ in the network, you would need to have more computing power than 51% of the network.
In the case of proof-of-stake, an algorithm will choose a block creator based on the size of their stake and its age, as well as a random element. In order to fake a ‘single block’ in the network, you would need to own 51% of the cryptocurrency. The reward given is primarily based off the transactions fees.
There is also another one called DPoS which I consider a less-decentralised version of PoS which reduces the stakers down to a more limited-group (used by EOS, for example). The idea is that everyone in the network can use their currency to vote on ‘witnesses’ to secure the network. The ‘witnesses’ are those who receive the highest number of votes (100 in the case of EOS) receive a one-off payment (backup block-producers) and a portion of these (21 in the case of EOS) become block producers. They essentially rotate amongst the circle who will produce the next block. Voting is an ongoing process, so people can move their votes around whenever, and voting strength decays over time (need to re-vote).
(Aside) Calculating Merkle Roots
Think of a Merkle root as a summary of all the transactions in a block; you start with the bottom leaves as all the transactions in the block. Then you hash them all with the algorithm to get n/2 hashes; you repeat this process until you get a hash representative of all the transactions. The way in which the hashing is done also means the order of the transactions cannot be tampered with. There actually used to be a bug with this structure back in 2012 where you could DoS Bitcoin by duplicating transactions in a Merkle tree.

How does PoW work?
Since Bitcoin is the most prominent cryptocurrency of this type, I will use it to explain the details behind PoW. The basic idea is that we have a series of blocks each containing headers of the following form:
Version (4 bytes) - version of the software being used
Previous Block Hash (32 bytes) - hash of the previous block header
Transaction Merkle Root (32 bytes) - merkle root of the transactions to be included in the block
Time (4 bytes) - timestamp of when the block is being produced
Bits (4 bytes) - compact form of the target, which the generated block hash must be less than or equal to (to be valid); it is a special floating point where leading byte is base 256 (lowest 5 bits only used) and the other 3 bytes are the fractional component
Nonce (4 bytes) - unique number which is modified to change the overall block hash
The hashing algorithm used in the case of Bitcoin is SHA-256. The essential idea behind mining is that we are repeatedly calculating SHA256(SHA256(Header)), modifying the nonce each time, until we get a hash satisfying the target. You probably noticed that they double hash; this is so we can avoid length-extension attacks. I thought I would try and grab the current target, but I could only find the difficulty which sits at 9,064,159,826,491. The formula for it is:
Difficulty = Original Target / Target (i.e. Target = Original Target / Difficulty)
Now the original target for Bitcoin is:

Now from the formula above you can clearly see that as the difficulty rises, the hexadecimal value for the target is going to shrink and we are going to essentially get more leading 0s. This means there will be less SHA-256 hashes satisfying the criteria and thus you need to do a larger amount of work to mine a block.
Now once a miner finds a corresponding hash, they broadcast it to the rest of the network. They will then individually verify that it is correct and the miners will then start searching for the hash for the next block. The transactions included in the block are based on what have been propagated around the network and received by the node at the miner.
What if two miners determine a hash at the same time?
This was the case that immediately crossed my mind and I wondered who would get the reward in this case; as a side note, this circumstance is actually quite unlikely. Basically what will happen is that each of the two miners will broadcast their block to the rest of the network; let’s say around half of the network receives from Miner A first and the other half from Miner B. The nodes which are miners will begin trying to calculate the next block based on the block they received first; the idea is that we will resolve the dispute by seeing which chain can calculate the next block first.
Now let’s say that someone in the Miner A chain is able to calculate the hash for the 2nd block first; they can then broadcast this to the rest of the network. The other nodes and miners will realise this chain is longer than the other and will abandon the Miner B chain (miners will switch to the longest chain to continue work). The disregarded blocks in chain B are known as orphaned blocks.
How do miners get paid?
When they are searching for an appropriate hash for a block, they include a special type of transaction in the block. It is known as a generation transaction (only 1 allowed per block) and transfers an amount equivalent to the set reward and fees of the block into an address inserted by the miner. It’s worth noting that as part of the protocol, a miner is unable to use the funds for 120 blocks; this is a double-spend protection for the case in which we have a series of orphaned blocks.
What is the main difference between PoS and PoW?
The main difference between the two types of protocols is the method in which we choose the next block producer - in PoW it is based on a competitive computationally intensive hashing process, where as in PoS it is based on a ‘random’ selective algorithm based on stake size and age. There still isn’t any particularly well-known and tested proof-of-concepts for PoS, so I think it’s a bit early to be sprouting on about the benefits over traditional methods.
The obvious benefit is related to electricity usage; the fact that PoW burns through so much power in this competitive process is problematic. In fact it uses as much electricity as all of Austria, and the energy required on average for a single transaction, could power around 20 US households for a day.
Why aren’t we all using PoS then?
Some of the issues related to PoS relate to the fact that we don’t have an opportunity cost in support two different chains in other protocols - in PoW when two chains form, miners are forced to pick a chain to dedicate their hash power to (i.e. they can’t use the same hash power on both chains). In PoS, the ‘miners’ (which we considered ‘stakers’) can potentially vote on both chains. A number of protocols have proposed solutions to this problem including:
CASPER - evidence can be submitted of users voting on the wrong protocol, leading to a penalty
Peercoin - clients use the chain with the greatest coin age staked as the main chain (i.e. no. of coins x age for every stake)
NXT - combination of cumulative difficulty and only have transaction-fee based rewards
The other main issue faced with implementations of PoS is long-range attacks - the idea that the initial group of stakers of a chain can go back and revive an earlier version of the chain where they have majority stake. Since we don’t have the computationally intensive time-restrictions associated with PoW we can make the chain long in a very short period of time. One common method of resolving this issue is by only allowing blocks within a certain range of being disputed; although this creates an issue when we have nodes restarting after a period of time, or nodes starting up for the first time.
This issue is commonly known as “weak subjectivity” - it essentially means that a node coming online for the first time has to ask a “trusted” source what the hash of the valid chain is. This completely undermines the ‘trustless’ nature of the blockchain. Some of the methods to combat include:
Casper - dependence on “trusted nodes” to broadcast the correct block hash
Peercoin - broadcasting the hash of the main chain on a daily basis
NXT - ignoring the problem because it is low probability and the developers are ‘confident’ that no significant portion will try and stake a long-range attack in the past
7 notes
·
View notes
Text
Cryptocurrency
What Is Cryptocurrency Currently, in our economy when we make purchases, all our funds are passed through a 3rd party (ie. the bank), before the transaction is approved and funds land in the target account. This sometimes attracts high(er) transaction fees and takes time. With cryptocurrency, the point is to remove the need for a centralised server, and completely decentralise the currency.
Cryptocurrency is digitally built using strong cryptographic principles (blockchain, hashing), such that faking transaction is extremely difficult to do, making it not worthwhile for attackers to do so, hence removing the need for centralisation since transactions need not be approved for fraud beforehand.
Blockchain This is a method for storing data (in this case transactions), such that blocks of data are linked to other blocks of data in a chronological order. Each block holds data, a hash of the data, and the hash of the previous block in the chain. In the case of bitcoin, the hash used is SHA256. This blockchain now becomes tamper resistant. Consider if any of the blocks in the chain were to be tampered with (eg. adding a fake transaction), the hash of that block would now be completely different and the block in front will not be linked to it, essentially breaking the chain at that point. This prevent attacking blocks in the middle of the chain, but what about adding fake blocks to the start of the chain? This is where proof of work/stake comes in.
Proof of Work We have all heard of bitcoin mining, but what really is it? Each time a block is going to be added, miners will brute force a number such that adding it on to the end of the block will result in its hash starting with some number of 0s. This is commonly referred to just as a very difficult mathematical problem. The incentive for miners to do so, is that they will earn a small amount of bitcoin for each block they mine. The reason this system is difficult to hack, is because of the fact that brute forcing a number takes so much work. If you faked a block then calculated proof of work, you would have to continue doing this and adding blocks to the chain because the longest chain is seen as the most legitimate. This takes a lot of work and will be difficult to do so unless every other miner also went rogue and joined in on your efforts to keep us this fake blockchain. Thus it becomes more plausible to simply gain the reward for mining legitimate blocks.
Proof of Stake In recent times, some people have come up with a new system over proof of work. This is because of two issues with proof of work. First is the development of mining pools. This is when multiple miners come together and share their resources to mine quicker and split the rewards. This is seen as a threat to crypto because the whole point is to move away from a centralised service and if large mining pools form, the service essentially becomes centralised again because this pool if large enough, will act as a central bank approving transactions as they please. Second, is the large computational resources required to mine which create environmental issues.
With proof of stake, an algorithm chooses legitimate blocks through the combination of the size/age of a person’s stake and some randomised elements (eg. longest hash size), rather than computational power. Stake refers to essentially some form of a ‘deposit’ put in by people to be held which they may lose if they approve fraudulent transactions. The randomised element is to prevent only those with largest stake having mining power. Rewards are now transaction fees, hence keeping supply of the currency constant.
Like proof of work deters fraud through excessive work, proof of stake does this through the nature of the system. Aside from the possibility of losing your stake, if you were to attack the whole network, you would need a stake large enough to do so. With a stake this large, you’d be attacking your own currency, hence making it unattractive to do so.
This video was extremely useful in understanding the concepts here: https://www.youtube.com/watch?v=bBC-nXj3Ng4&t=1091s
1 note
·
View note
Text
Bytom Wallet
What is Bytom Wallet ? Bytom is a cryptocurrency the fact that has a unique triple-layer strategy to blockchain distributed applications. Bytom Wallet take place in one layer, transmissions with another, and the third is called the property conversation layer. The cryptocurrency created some sort of faster, extra secure installments system, and even has potential in the field of Big Data too. Introduction to Bytom BTM Bitcoin is certainly a single layer cryptocurrency, and Ethereum is a good dual-layer blockchain that offers sensible contracts and dApps into the mix. Chinese blockchain Bytom requires things a move further using a triple-layer strategy. Data orders occur on one layer, gears in another, and the 3rd is called the advantage relationship layer. Bytom is definitely an involved protocol involving multiple byte assets, to help give it typically the suitable title. And, when Ethereum�s SEC scrutinization like the possible security had taken often the entire crypto market on a downturn in early 2018, Bytom voluntarily published to help the SEC�s Howey Test out and Bytom cryptocurrency was deemed not a good security under its DAO enjoy. As digital resources proceed, this one has probability of make a great impact on this cryptocurrency market having low financial transaction fees, large tech Bytom blockchain technology and a great interactive process of a variety of byte resources that could mark the idea apart. A good Bytom budget is in addition offered plus can store plenty a lot more than Bytom coins. Rapid Achievements For Bytom Cryptocurrency That is a lot for a good blockchain mainnet that merely barely unveiled April all day and, 2018. Most of their accomplishment can be traced in order to its association along with popular Shanghai-based crypto-exchange community 8BTC, whose founder Chang Jia partnered with Bytom owner Duan Xinxing within 04 2018. Bytom contains a very long road ahead of it, but it�s plowing through full steam ahead. It is also working on some sort of one-stop big-data shop to get government organizations and enterprises in China and taiwan that can put American information management giant Iron Off-road to shame. The control associated with digital property may simply attract state support, like China is keen to help embrace the blockchain even while this stamps down on the subject of cryptocurrency trading. Chinese nationals can not buy Bytom plus devote in the blockchain technological innovation that may change typically the nation. Before dealing with often the intricacies of Bytom�s blockchain technology, let�s glimpse from the BTM endroit plus its performance in typically the market in terms of the market cap and regular trading quantity. Is the Bytom or maybe worth buying? Dysfunction connected with BTM Bytom possesses a market cap of $673, 373, 841 as of May 22, 2018, based upon a good circulating supply of 987, 000, 000 Bytom BTM (out of a total supply of 1, 407, 000, 000) and the exchange price of $0. 682243. When the idea would spike with the crypto promote in Present cards 2018, that hit it has the all-time large of $1. tough luck for Bytom coins the day former to its launch time frame four months later. This makes BTM cryptocurrency a rarity among cryptos in that will this peaked outside Bitcoin plus Ethereum�s wake plus may possess even led to the Might move after two months involving dipping prices industry-wide. In addition strong projects like Ripple and Litecoin typically stick to Bitcoin and Ethereum out there, so BTM is popular for standing alone. Could very well Bytom cryptocurrency form a safe location if the marketplace becomes? Keep watching the cryptocurrency news and the particular market limitation for the particular answer. The cryptocurrency industry is a fickle position, nevertheless spotting trends similar to this can create serious income after a while. Bytom coins could very well be an selection for rainy days. Buy Bytom, Don�t Try And My own It BTM can be mined up to this maximum supply (approximately thirty-three percent), and Bitmain unveiled the $27, 500 Antminer B3 (780Hz) ASIC exploration rig for BTM about May 1, 2018. Therefore it will be all but impossible for anybody without having that upfront investment to mine. A swarm-mining remedy offered by Antpool, a new Bitmain subsidiary accused regarding synthetically boosting the cost of Bitcoin Money in Q2 2018. Many favorite cryptocurrency exchanges support Bytom cryptocurrency, including Huobi, Etherdelta, and even KuCoin. Approximately 50 bucks trillion worth of BTM is traded on a good daily basis. To support it has the community, Bytom airdropped any kind of BTM it mined throughout its opening weekend. This also promises a good bounty method to reward participation within the Bytom ecosystem. Up right up until the official mainnet launch, Bytom BTM existed only while an ERC-20 token with the Ethereum blockchain. Typically the testnet will remain upwards alongside the mainnet as a way to test new updates without compromising the live atmosphere. BTM has both the desktop and web-based finances, and the mobile finances is expected in the near future. Behind the Tensority Algorithm Bytom rose to popularity within the U. H. (and global) blockchain group in Apr 2018 after debuting it is Tensority algorithm at an market discussion at M. My spouse and i. Testosterone levels. This consensus formula uses edge computing for you to help integration with AJAJAI deep learning and fog up computing, Tensority is a Proof-of-Work algorithm based with tensor calculation, and is considered one of the a lot more complex blockchain projects upon the market. Employing about three layers, Tensority, together with normal address format, Bytom is definitely in a position of interoperability having any other platform, blockchain as well as not. Of program, interoperability in itself is definitely rapidly turning out to be the normal for new blockchains. Ontology, for example, supports sidechains, in addition to Plasma brings this operation to Ethereum. Nevertheless, a large number of platforms only help support modern day data standards which usually are swiftly being substituted as AI-powered recommendation search engines become the norm. Inside fact, Bytom�s protocol works with ASIC mining rigs perfectly because it�s built regarding AI equipment acceleration companies. Furthermore, like Bitcoin�s Seperated Bytom Wallet , Bytom separates financial transaction signatures from the snooze of the data to streamline processing. The Bytom UTXO model verifies purchases in parallel to keep away from double-spends and other adjustment. It in addition uses ESCDA encryption and even SHA256 hashing. Using these technologies, Bytom built a state of the art blockchain that can support anything at all our combined computing energy can throw at the idea at this point or maybe in typically the future. Bytom Summary Story has proven the best technologically-advanced project doesn�t always win (i. e. Tesla v Edison, VHS versus Beta), yet Bytom�s give attention to advanced technologies like synthetic intelligence may prove to end up being a new boon in typically the blockchain forearms race. The asset control and development of the blockchain platform will make or bust Bytom in the stop. The project�s success depends on bringing in assets directly into its ecosystem, and it may be poised to do thus by way of flaunting the following advantages over competitors. Bytom is a tri-layer blockchain that separates each and every aspect of traditional blockchain design. It also supports cross-chain function and can help every other cryptocurrency. The BTM coin�s peak value seemed to be in April 23, 2018, several weeks after the relaxation of the field skilled its peak. It�s a good uncommon coin that increased separately of the cryptocurrency market, so keep the eye on what the idea does during downturns. That may be the period to buy Bytom. Bytom is partnered having 8BTC, Bitmain, and different prominent players in the blockchain industry. Bytom has the particular great thing of the SECURITIES AND EXCHANGE COMMISSION'S, the assistance of the particular Chinese government, and is also constructing a online asset safe-keeping center in central Tiongkok. IT storage space spending provides steadily risen since 2013 and is expected to be able to continue through 2020. It is currently a new $50 thousand global sector, and Bytom is expecting to not only take a peel of this pie yet expand the industry over and above initial analyst expectations. That blockchain job is below to stay.
1 note
·
View note
Text
Bytom Wallet
What is Bytom? Bytom is a cryptocurrency the fact that requires a unique triple-layer tactic to blockchain distributed purposes. Data dealings occur upon one layer, transmissions in another, and the next is called the advantage interaction layer. The cryptocurrency created a good faster, whole lot more secure bills system, together with has potential when it comes to Major Data too. Intro to Bytom BTM Bitcoin is normally a single layer cryptocurrency, and Ethereum is the dual-layer blockchain that comes with clever contracts and dApps to the mix. Chinese blockchain Bytom will take things a phase further having a triple-layer strategy. Data purchases occur on one layer, diffusion on another, and the next is called the advantage relationship layer. Bytom is certainly an fun protocol of multiple octet assets, to help give it often the right title. And, even though Ethereum�s SEC scrutinization while the possible security had taken the particular entire crypto market on the downturn in early 2018, Bytom voluntarily downloaded to the SEC�s Howey Check and Bytom cryptocurrency has been deemed not a good safety under its DAO view. As digital investments go, this one has potential to make an impact in often the cryptocurrency market along with low transaction fees, substantial tech Bytom blockchain engineering and a great interactive standard protocol of a number of byte resources that could indicate it apart. Some sort of Bytom pocket book is also offered together with can store plenty greater than Bytom coins. Rapid Success For Bytom Cryptocurrency That certainly is a lot for a good blockchain mainnet that simply barely introduced April twenty four, 2018. Much of it is good results can be attributed in order to its association using well-liked Shanghai-based crypto-exchange community forum 8BTC, whose founder Alter Jia partnered with Bytom creator Duan Xinxing around September 2018. Bytom includes a long road ahead of that, but it�s plowing via full steam ahead. It is also working on a new one-stop big-data shop regarding government organizations and enterprises in Cina that can put American data supervision giant Iron Hill to be able to shame. The control regarding digital resources could quickly attract state supporting, since China is keen to embrace the blockchain at the same time the idea stamps down found on cryptocurrency trading. Chinese excellent are not able to buy Bytom and commit in the blockchain technological innovation that can change typically the nation. Before speaking about often the intricacies of Bytom�s blockchain technology, let�s glimpse with the BTM lieu and even its performance in the particular market in terms of the market cap and every day trading level. Is the Bytom gold coin worth buying? Breakdown of BTM Bytom has a marketplace cap of $673, 373, 841 as of Might 22, 2018, based in a circulating supply associated with 987, 1000, 000 Bytom BTM (out of some sort of total way to obtain 1, 407, 000, 000) and a good exchange price of $0. 682243. When this do spike with the crypto advertise in January 2018, the idea hit its all-time great of $1. 13 for Bytom coins a single day past experiences to its launch time frame four months later. This makes BTM cryptocurrency a rarity among cryptos in the fact that that peaked outside Bitcoin and Ethereum�s wake and may currently have even added to the May possibly move after two months connected with dipping prices industry-wide. In fact strong projects like Ripple and Litecoin typically follow Bitcoin and Ethereum out there, so BTM is popular for standing alone. Could very well Bytom cryptocurrency form a safe haven if the marketplace changes? Keep watching the particular cryptocurrency news and the particular market cover for this answer. The cryptocurrency market place is a fickle position, although spotting trends this way can create serious gains with time. Bytom coins could be an option regarding rainy days. Purchase Bytom, Don�t Try And Mine It BTM can be mined up to the maximum supply (approximately 33 percent), and Bitmain unveiled the $27, 500 Antminer B3 (780Hz) ASIC gold mining rig for BTM in May 1, 2018. It indicates it will be just about all but impossible for any individual with out that upfront investment to help mine. A swarm-mining option would be offered by Antpool, some sort of Bitmain subsidiary accused regarding synthetically boosting the price of Bitcoin Take advantage Q2 2018. Many popular cryptocurrency exchanges support Bytom cryptocurrency, including Huobi, Etherdelta, together with KuCoin. Approximately fifty dollars trillion worth of BTM is usually traded on some sort of day to day basis. To support its community, Bytom airdropped just about any BTM it mined while in its opening weekend. It also promises a bounty method to reward participation from the Bytom ecosystem. Up right until the standard mainnet launch, Bytom BTM existed only since an ERC-20 token with the Ethereum blockchain. Bytom Wallet Download will remain upwards alongside the mainnet to be able to test new updates devoid of compromising the live atmosphere. BTM has both a good desktop and web-based wallet, and a mobile wallet is expected in typically the near future. At the rear of typically the Tensority Protocol Bytom rose to visibility in the Circumstance. T. (and global) blockchain group in April 2018 after debuting the Tensority protocol at an business meeting at M. My partner and i. To. This consensus algorithm uses edge computing to help permit integration with AJE deep learning and impair computing, Tensority is some sort of Proof-of-Work algorithm based with tensor calculation, and it�s one of the a great deal more techie blockchain projects with the market. Employing several layers, Tensority, and even basic address format, Bytom is usually in a position of interoperability having any other platform, blockchain or even not. Of course, interoperability in itself will be immediately becoming the standard for new blockchains. Ontology, for example, supports sidechains, and even Plasma brings that operation to Ethereum. Having said that, the majority of these platforms only assist modern day data standards which often are instantly being substituted as AI-powered recommendation applications become the tradition. Throughout fact, Bytom�s formula sustains ASIC mining rigs very well because it�s built for AJE components acceleration companies. Likewise, like Bitcoin�s Segregated Bytom Wallet Download , Bytom separates transaction validations from the rest of the data to be able to streamline processing. The Bytom UTXO model verifies deals in parallel to keep away from double-spends and other mind games. Bytom Wallet in addition uses ESCDA encryption and even SHA256 hashing. Using these technologies, Bytom built some sort of advanced blockchain that can support anything our combined computing strength can throw at the idea at this point or in the particular future. Bytom Summary Story has demonstrated one of the most technologically-advanced project doesn�t generally triumph (i. e. Tesla sixth v Edison, VHS sixth is v Beta), but Bytom�s focus on advanced technologies like manufactured intellect may prove to become a new boon in this blockchain forearms race. The particular asset administration and development of the blockchain program will make or break Bytom in the stop. The project�s success is dependent on luring assets directly into its ecosystem, and it may be poised to do as a result simply by flaunting the adhering to advantages above competitors. Bytom is a tri-layer blockchain that separates each element of traditional blockchain layout. It also supports cross-chain function and can help another cryptocurrency. The BTM coin�s peak value had been with April 23, 2018, many months after the rest of the industry expert its peak. It�s the exceptional coin that flower independently of the cryptocurrency market, therefore keep the eye on what this does during downturns. The fact that may be the moment to buy Bytom. Bytom is partnered having 8BTC, Bitmain, and various other popular players in the blockchain industry. Bytom has this good thing of the SECURITIES AND EXCHANGE COMMISSION'S, the support of this Chinese government, and it is creating a a digital asset storage area center in central Cina. IT safe-keeping spending possesses steadily risen since 2013 and is expected to continue by means of 2020. Is considered currently a good $50 thousand global industry, and Bytom is intending to not really only take a portion of this pie however grow the industry beyond initial expert expectations. This particular blockchain job is right here to stay.
1 note
·
View note
Text
Functional value of NFT
1. NFT function: realize the decentralized certification and transaction of assets
From the perspective of authentication: the core reason is due to the immutability and permanence of authentication, and the basis for realizing the immutable attribute is the disclosure of data transaction process and distributed storage based on blockchain technology.
From a transaction point of view: In addition to being non-tamperable and publicly traceable, it is also due to cost factors, because NFT corresponds to assets, and there are intermediary costs for centralized institutions as intermediate trust agencies, while NFT is based on the blockchain, and the blockchain itself It is a trust-based machine that eliminates intermediate costs.
2. NFT value = virtual currency + asset warrant + liquidity
As a non-homogeneous token minted on the blockchain, NFT is mainly traded through virtual currency, so NFT has a certain virtual currency value.
As a digital warrant of an asset, NFT represents the value of the asset itself. At the same time, the technical characteristics of NFT endow asset ownership with liquidity and traceability. On the one hand, liquidity increases asset value. On the other hand, traceability solves the problem of asset identification such as art collections. Pain points of fake and real rights.The liquidity of NFT endows the transaction value of asset increment.
3. NFT underlying technology
The underlying technology based on NFT — blockchain . The only public, non-tamperable, and tradable attributes of NFT are based on the current blockchain technology.
The data structure of the blockchain is divided into a block header and a block body. Different blocks are connected through the hash value of the previous block header to form a chain structure. The block header and the block body are connected through the Merkle root field. connected. Taking Ethereum as an example, NFT Development Company the data stored in the block header mainly includes the hash value of the parent block header, the hash value of the root node of the Merkle tree related to the current block transaction, the block difficulty value, the miner address, the block height, the Gas Upper limit, Gas usage, timestamp, Nonce value, etc. The data stored in the block body includes transaction record table and uncle block, where the NFT transaction record is stored in the data record table of the block body and packaged by miners.
A simple diagram of the blockchain structure is as follows:
The data confirmed and packaged into blocks on the blockchain cannot be tampered with and will be permanently stored on the chain. After the data information of NFT is confirmed on the chain, it can no longer be modified. When the miners or super nodes use the consensus algorithm to complete the block generation, they will broadcast to the entire network through the P2P protocol (P2P protocol is a distributed network protocol, which appeared earlier than the blockchain technology). , the information will be updated. This mechanism realizes decentralized distributed records, and the consensus algorithm ensures that malicious nodes cannot tamper with information.
Blockchain classification
According to the degree of decentralization, it can be divided into three types of chains, namely public chains, alliance chains and private chains.
2. Consensus algorithm
The basis for blockchain to establish decentralized trust is the consensus algorithm . The current mainstream public chain consensus algorithms are divided into three categories, namely PoW, PoS, and DPoS:
PoW algorithm: Bitcoin and Ethereum 1.0 adopt the PoW algorithm, that is, Proof of Work. Taking Bitcoin as an example, continuously perform SHA256 calculations, and finally find out that the node with a hash value that satisfies a given number of leading 0s has the right to produce blocks;
PoS algorithm: Ethereum 2.0 adopts this algorithm, Proof Of Stake, proof of rights and interests, and introduces the concept of coin age. The more coins you hold, the higher the probability of getting a block. This algorithm reduces the amount of calculation and improves TPS (concurrent transactions per second) volume), sacrificing a certain degree of decentralization;
DPoS algorithm: Delegated Proof of Stake, each node mortgages the tokens in its hands to vote for the most capable and reputable node to produce a block, taking the EOS blockchain as an example, the entire network votes to select 21 super nodes, 21 super nodes Nodes take turns to produce blocks. This algorithm can greatly increase TPS, but the degree of decentralization is further reduced
3. Smart contract
Standard protocol: NFT is deployed on the blockchain through standard contracts such as smart contracts ERC-721 and ERC-1155 . A smart contract is a piece of executable code deployed on the blockchain. The ERC-721 standard is applicable to any non-homogeneous digital content. ERC-1155 is more used in games to identify a class of props.
Smart contract transaction trigger and execution mechanism: transaction is a bridge connecting the external world and the internal state of Ethereum, so Ethereum is also called the state machine of the transaction. After the smart contract deployment of NFT is completed, the RPC interface is called externally to access the main network of Ethereum. The miners package the transaction, and the EVM (Ethereum Virtual Machine) finds the corresponding smart contract and executes the corresponding contract function according to the external input parameters. After the execution is completed, the status is updated on the chain.
Example: The Boring Ape NFT developer deploys the smart contract code to Ethereum, and the NFT Development Services platform OpenSea collects and displays it. When one of the users initiates the purchase operation of this Boring Ape NFT on the OpenSea platform, OpenSea calls the RPC interface to access the Ethereum mainnet to send the transaction Request, the miners package the transaction to find the smart contract to execute, and update the status on the chain to complete the transaction.
0 notes
Text
Online sha1 hash calculator

#ONLINE SHA1 HASH CALCULATOR SOFTWARE#
#ONLINE SHA1 HASH CALCULATOR CODE#
#ONLINE SHA1 HASH CALCULATOR FREE#
#ONLINE SHA1 HASH CALCULATOR WINDOWS#
Apart from calculating the hash, it also offers many other online tools and services that may come in handy.
#ONLINE SHA1 HASH CALCULATOR FREE#
PELock is another free online hash calculator website. You can also check out lists of best free AES Encryption Online, Note Taking Online, and Encode Base64 Online websites. Plus, it also supports many hash algorithms.
#ONLINE SHA1 HASH CALCULATOR CODE#
My Favorite Online Hash Calculator Website:įileFormat.Info is my favorite website because it can generate hash code using a text string, files, and hex data. Go through the list to know more about these websites. Using additional tools, users can generate passwords, encode data, generate URL Slug, and more. These websites also come with many additional tools that may come in handy. To help out new users, I have included the necessary hash calculation steps in the description of each website. After that, users can start the hash calculation process. According to their requirements, users can choose the right combination of hash algorithms and input data type. Besides this, some websites also allow users to choose different types of input data namely text, hex code, files, etc. These websites allow users to choose one hash algorithm from various available ones to generate output hash code.
#ONLINE SHA1 HASH CALCULATOR SOFTWARE#
If you also want to calculate the hash without using software and apps, then check out these online hash calculator websites. To calculate the hash of input data, these websites use various algorithms like MD5, SHA1, SHA256, SHA512, MD2, and more. Hash calculator allows users to calculate the cryptographic hash value of a text string or file. SHA256 Decrypt.Here is a list of best free online hash calculator websites. SHA-2 includes significant changes from its predecessor, SHA-1. They are built using the Merkle–Damgård structure, from a one-way compression function itself built using the Davies–Meyer structure from a (classified) specialized block cipher. SHA-2 (Secure Hash Algorithm 2) is a set of cryptographic hash functions designed by the United States National Security Agency (NSA). NTLM passwords are considered weak because they can be brute-forced very easily with modern hardware.
#ONLINE SHA1 HASH CALCULATOR WINDOWS#
Whether these protocols are used or can be used on a system is governed by Group Policy settings, for which different versions of Windows have different default settings. The NTLM protocol suite is implemented in a Security Support Provider, which combines the LAN Manager authentication protocol, NTLMv1, NTLMv2 and NTLM2 Session protocols in a single package. NTLM is the successor to the authentication protocol in Microsoft LAN Manager (LANMAN), an older Microsoft product. NT (New Technology) LAN Manager (NTLM) is a suite of Microsoft security protocols that provides authentication, integrity, and confidentiality to users. The MySQL5 hashing algorithm implements a double binary SHA-1 hashing algorithm on a users password. Microsoft, Google, Apple and Mozilla have all announced that their respective browsers will stop accepting SHA-1 SSL certificates by 2017. Since 2005 SHA-1 has not been considered secure against well-funded opponents, and since 2010 many organizations have recommended its replacement by SHA-2 or SHA-3. It was designed by the United States National Security Agency, and is a U.S. In cryptography, SHA-1 (Secure Hash Algorithm 1) is a cryptographic hash function which takes an input and produces a 160-bit (20-byte) hash value known as a message digest – typically rendered as a hexadecimal number, 40 digits long. The CMU Software Engineering Institute considers MD5 essentially cryptographically broken and unsuitable for further use. The weaknesses of MD5 have been exploited in the field, most infamously by the Flame malware in 2012. It remains suitable for other non-cryptographic purposes, for example for determining the partition for a particular key in a partitioned database. It can still be used as a checksum to verify data integrity, but only against unintentional corruption. Although MD5 was initially designed to be used as a cryptographic hash function, it has been found to suffer from extensive vulnerabilities. The MD5 message-digest algorithm is a widely used hash function producing a 128-bit hash value. We are not cracking your hash in realtime - we're just caching the hard work of many cracking enthusiasts over the years. We have been building our hash database since August 2007. It's like having your own massive hash-cracking cluster - but with immediate results! This allows you to input an MD5, SHA-1, Vbulletin, Invision Power Board, MyBB, Bcrypt, Wordpress, SHA-256, SHA-512, MYSQL5 etc hash and search for its corresponding plaintext ("found") in our database of already-cracked hashes.

0 notes
Text
Mining Machines Europe offers graphic cards and mining gpu for crypto currency

Mining Machines Europe believes in maintaining ongoing customer relationships.
Our support does not end at the point of sale. We provide ongoing support and general advice to our clients to ensure their Rigs operate at full potential.
There is no base or breaking point to the quantity of GPUs you can utilise while mining, and might begin with 1. Notwithstanding, assuming you are into a genuine mining business, an apparatus of 6 GPUs is suggested.
Will I mine Bitcoin on my PC?
Framework Requirements for Cryptocurrency Mining
You can utilise any PC: work area or PC. Windows OS is the simplest to utilise. You can barely mine on Mac OS. Assuming you use Linux, you most likely definitely know how to mine better compared to we do.
What would I be able to mine with Antimatter S19 Pro?
Insect digger S19 Pro is a SHA-256 calculation mining hardware produced by Bitmain. It can mine Bitcoin (BTC) and Bitcoin cash (BCH) with a most extreme hash-pace of 110TH/s for a power utilisation of 3250W.
How boisterous is Antimatter S19 Pro?
We likewise estimated the degree of commotion created by each machine, by putting a sound meter 15cm away from the digger, toward a path opposite to the principle wind stream. The Whats miner was the stronger machine, creating a normal sound of 83.0 dB, contrasted with the Antimatter with 81.4 dB.
Would Antimatter be able to mine ethereal?
A: The AntMiner S9 can mine coins in view of the SHA256 algorithm, for example, bitcoin and bitcoin cash. Ethereal depends on a Check calculation and is therefor incapable to be mined with an AntMiner S9.
Is ASIC mining beneficial?
Reply: Bitcoin mining is productive with an ASIC in 2021. As of August 2021, an excavator could produce 6.25 coins at regular intervals. What's more, excavators acquired exchange expenses off somewhere in the range of 5% and 10% of the prize in the wake of mining a square.
Three to five years
Three to five years is commonly a machine's normal life expectancy, albeit significantly longer periods aren't unbelievable. Fresher models are supposed to have somewhere around five-year life expectancies. For instance, it's normal for mining homesteads to in any case have Antimatter S9 models on the web, which initially sent off in 2016.
How long will a Bitmain Antimatter last?
By the by, on the off chance that you keep ASICs in cruel or unfortunate circumstances, they can crumble in as little as a couple of months. Conversely, taking great consideration of an ASIC excavator can delay their life expectancy for over 5 years. Numerous excavators are as yet running their Antimatter S9s - a model from 2016 - at a benefit.
Is Antimatter V9 productive?
It utilises a ton of force, however it's productive to run. It's clearly, so I wouldn't suggest keeping it in your room. It additionally creates a ton of hotness, extraordinary for individuals who live up north. The V9 is an incredible move forward from the S3, suggested for somebody who is keen on mining on a low spending plan.
How to begin mining Bitcoin?
The initial step is generally the arrangement. You should get a mining apparatus to set up a machine with higher computational power and low energy utilisation.
Next comes getting a bitcoin wallet.
Join a mining pool subsequently, and you are all set. https://miningmachinesuk.com/
0 notes
Text
Download FishEye For Mac 3.5.3

Audio Hijack (was Audio Hijack Pro) is an audio-recording tool that can capture any audio from applications like Skype and iTunes. It can also record from microphones or any other source that runs through your Mac.
Download FishEye For Mac 3.5.3 Free
Download FishEye For Mac 3.5.3 Pro
The user interface, not too dissimilar to iTunes, is clean and simple, featuring two-panes from where you can capture audio from the usual applications like Skype, iTunes, iChat and QuickTime Player. In the pane situated on the right of your screen you can configure an array of settings, which include recording schedules, tags and a large selection of sound effects.
Download OpenCV for free. Open Source Computer Vision Library. The Open Source Computer Vision Library has 2500 algorithms, extensive documentation and sample code for real-time computer vision. It works on Windows, Linux, Mac OS X, Android, iOS in your browser through JavaScript. Terms and Conditions This is the Android Software Development Kit License Agreement 1. Introduction 1.1 The Android Software Development Kit (referred to in the License Agreement as the 'SDK' and specifically including the Android system files, packaged APIs, and Google APIs add-ons) is licensed to you subject to the terms of the License Agreement. First download the KEYS as well as the asc signature file for the relevant distribution. Alternatively, you can verify the hash on the file. Hashes can be calculated using GPG: The output should be compared with the contents of the SHA256 file. Similarly for other hashes (SHA512, SHA1, MD5 etc) which may be provided.
Download FishEye For Mac 3.5.3 Free

Download FishEye For Mac 3.5.3 Pro
One handy feature that will appeal to most people is the one-touch recording feature for iChat and Skype conversations. Although you can't edit audio using Audio Hijack, you'll certainly to be able to capture audio from multiple sources quickly and easily, making this an excellent audio-recording application.

0 notes
Text
Working and applications of the sha256 calculator

What is the sha256 calculator?
The Secure Hash Algorithm (SHA) is an example of the enhancement in digital technology. This cryptographic computer protection SHA256 algorithm is known widely. SHA can also be referred to as the sha256 algorithm. The sha256 calculator is widely used and known for its functions. Sha algorithm was first designed in 1995. The US National Security Agency did this. NSA is following the SHA-0 algorithm in 1993. It forms a primary part of the Digital Signature Standard. Likewise, it plays a significant role in the Digital Signature Algorithm
Properties of a sha256 calculator:
The sha256 calculator uses different tricks. It has certain features which enable it to carry out its function. These include: -
• One-way function: The output can be produced from the input. However, the output cannot be used to get the value for input. This is very similar to elliptic curve cryptography in which the private key cannot be produced from the public key.
• The sha256 calculator gives rise to the same output for the same input. It means a free lock will work in conjunction with a public key to open a secure gate/network.
How does sha256 calculator work?
1. To Calculate sha256 online, five variables are chosen.
2. Then select a word which you want to ‘’hash.’’
3. ASCII format is used, i.e., the word is transformed into this format. ASCII stands for American Standard Code for Information Interchange. For every, there is a specific number.
4. Binary code is then converted to ASCII.
5. Adjoins characters. After this, 1 is added to the end.
6. Zeros are added. This ensures the message is equivalent to 448 mod 512. Sha256 example: A 48-bit message with the 1 that has been added, will need 399 0s.
7. The sha256 calculator adds the former message length. This is the length before any transformations or conversions. It converts it into the 64-bit field left over. The message has 48 characters now. In binary, this is expressed as ‘’110000.’’
8. In the Sha256 algorithm, the message is broken down into 16 sections of 32 bit.
9. Sha256 online converter changes the 16 x 32 character bit words into 80 words.
10. The above process is carried out until there are 32 strings of bits or 80 words.
11. Now, online sha256 calculator runs a set of functions. It is done in a particular order using the five variables that were set in step 1. At the end of this step, 5 variables are left.
12. The H variables are now transformed into hex.
13. The variables are joined together to form the hash 256 algorithms.
Applications of the sha256 calculator:
Sha256 online calculator is used widely. It has diverse applications which include:
• The usage of Online Sha256 calculator in Transport Layer Security
• Sha256 calculator plays a significant part in Secure Sockets Layer (SSL)
• Calculate sha256 online and benefit from its usage in Pretty Good Privacy (PGP)
• The sha256 calculator helps in Secure Shell (SSH)
• Secure/Multipurpose Internet Mail Extensions (S/MIME) uses the Sha256 algorithm
Convert For Free- The Best website for the SHA256 calculator
Visit: http://www.convertforfree.com/sha-256-calculator/ Click on the link above now and step into the world of cyber security with the best online sha256 calculator. Protect your data integrity like millions of other users of our handy tool! Convert For Free is the online conversion hub. This website is user-friendly and provides you with reliable conversions! Visit it today to use the ideal SHA 256 online calculators!
#sha256 calculator#sha256 profit calculator#sha256 mining calculator#sha256 online calculator#free sha256 calculator#online sha256 calculator#Convert For Free#sha256 online#calculation#converter#sha256 calculator linux#sha256 hash calculator linux#sha256 calculator windows#sha256 calculator file#sha256 algorithm calculator
0 notes
Text
Bitcoin mining Rig
Bitcoin mining rigs are computers used to earn Bitcoin. This type of computer generally has a professional mining chip, and it usually works by installing a large number of graphics cards, which consumes a lot of power. The computer downloads the mining software and then runs a specific algorithm. After communicating with the remote server, the corresponding bitcoin can be obtained. This is one of the ways to obtain bitcoin.
Bitcoin mining rig features
Bitcoin mining machine is one of the ways to obtain Bitcoin. Bitcoin (Bitcoin) is a network virtual currency generated by open source P2P software. It does not rely on the issuance of a specific currency institution, and is generated through a large number of calculations of a specific algorithm. The Bitcoin economy uses a distributed database composed of many nodes in the entire P2P network to confirm and record all transaction behaviors. The decentralized nature of P2P and the algorithm itself can ensure that the value of the currency cannot be manipulated through the mass production of Bitcoin [1]. Any computer can become a mining rig, but the benefit will be relatively low, and it may not be possible to mine a bitcoin in ten years. Many companies have developed professional Bitcoin mining rigs. Such rigs equipped with special mining chips are dozens or hundreds of times faster than ordinary computers.
Bitcoin mining rig principle
The Bitcoin system consists of users (users control wallets through keys), transactions (transactions will be broadcast to the entire Bitcoin network) and miners (through competitive calculations to generate a consensus blockchain at each node. The blockchain is a distribution The public authoritative account book contains all the transactions that occur on the Bitcoin network). Bitcoin miners manage the Bitcoin network by solving the problem of a proof-of-work mechanism with a certain amount of work—confirming transactions and preventing double payments. Since the hashing operation is irreversible, it is very difficult to find the random adjustment number that matches the requirements, and it requires a constant trial and error process that can predict the total number of times. At this time, the workload proof mechanism comes into play. When a node finds a solution that matches the requirements, it can broadcast its results to the entire network. Other nodes can receive this newly solved data block and check whether it matches the rules. If other nodes find that the requirements are indeed met by calculating the hash value (the computational goal required by Bitcoin), then the data block is valid, and other nodes will accept the data block. Satoshi Nakamoto compares the production of Bitcoin by consuming CPU power and time to a gold mine consuming resources to inject gold into the economy. Bitcoin's mining and node software mainly uses peer-to-peer networks, digital signatures, and interactive proof systems to initiate zero-knowledge proof and verification transactions. Each network node broadcasts transactions to the network. After these broadcast transactions are verified by miners (computers on the network), miners can use their own work proof results to express confirmation, and the confirmed transactions will be packaged into data blocks. , The data blocks will be strung together to form a continuous chain of data blocks. Each Bitcoin node will collect all unconfirmed transactions and group them into a data block. The miner node will append a random adjustment number and calculate the SHA256 hash operation value of the previous data block. The mining node keeps trying repeatedly until the random adjustment number it finds makes the generated hash value lower than a certain target.
Mining process
Mining is a process of increasing Bitcoin's money supply. Mining also protects the security of the Bitcoin system, prevents fraudulent transactions, and avoids "double payment". "Double payment" refers to spending the same bitcoin multiple times. Miners provide algorithms for the Bitcoin network in exchange for the opportunity to obtain Bitcoin rewards. The miners verify each new transaction and record them in the general ledger. Every 10 minutes, a new block will be "mined". Each block contains all the transactions that occurred during the period from the creation of the previous block to the present, and these transactions are sequentially added to the blockchain middle. We refer to the transactions included in the block and added to the blockchain as "confirmed" transactions. After the transaction is "confirmed", the new owner can spend the bitcoins he got in the transaction. Miners receive two types of rewards during the mining process: new currency rewards for creating new blocks, and transaction fees for transactions contained in the blocks. In order to get these rewards, miners are vying to complete a mathematical puzzle based on cryptographic hashing algorithms, that is, using Bitcoin mining rigs to calculate hashing algorithms. This requires strong computing power, how many calculations are needed, and the results of the calculations are good. Bad as the proof of the calculation workload of the miners, it is called "proof of work". The competition mechanism of the algorithm and the mechanism by which the winner has the right to record transactions on the blockchain, both of which guarantee the security of Bitcoin. Miners also receive transaction fees. Each transaction may include a transaction fee, which is the difference between the input and output of each transaction record. Miners who successfully "dig out" a new block during the mining process can get all the transaction "tips" contained in the block. As mining rewards decrease and the number of transactions contained in each block increases, the proportion of transaction fees in miners' income will gradually increase. After 2140, all miners’ income will consist of transaction fees. Mining is a process of decentralization of settlement, and each settlement verifies and settles the transactions processed. Mining protects the security of the Bitcoin system and realizes that the entire Bitcoin network can reach a consensus without a central organization. The invention of mining makes Bitcoin very special. This decentralized security mechanism is the basis of peer-to-peer electronic money. Rewards and transaction fees for minting new coins are an incentive mechanism that can regulate the behavior of miners and network security, and at the same time complete the currency issuance of Bitcoin.
Bitcoin earnings
The issuance of Bitcoin and the completion of transactions are achieved through mining, which is minted at a definite but continuously slowing rate. Each new block is accompanied by a certain number of new bitcoins from scratch, which are rewarded as coinbase transactions to miners who find the block. The reward for each block is not fixed. For every 210,000 blocks mined, it takes about 4 years and the currency issuance rate is reduced by 50%. In the first four years of Bitcoin's operation, 50 new Bitcoins were created in each block. Each block creates 12.5 new bitcoins. In addition to block rewards, miners will also get the handling fees for all transactions in the block.
Risks of mining Rigs
Electricity bill problem
The "mining" of the graphics card requires a long time to fully load the graphics card, the power consumption will be quite high, and the electricity bill will be higher and higher. Many professional mines at home and abroad are located in areas where electricity costs are extremely low, such as hydropower stations, and more users can only mine at home or in ordinary mines, so electricity costs are naturally not cheap. There was even a case where someone in a community in Yunnan carried out crazy mining, which caused a large-scale trip of the community and the transformer was burned out.
Hardware expenditure
Mining is actually a competition of performance and equipment. Some mining Rigs are composed of more such graphics card arrays. When dozens or even hundreds of graphics cards come together, various costs such as hardware prices are inherently high. There are considerable expenditures. In addition to graphics card-burning machines, some ASIC (application-specific integrated circuit) professional mining rigs are also on the battlefield. ASICs are specially designed for hash calculations and their computing power is also quite strong, and because their power consumption is much lower than that of graphics cards, Therefore, it is easier to scale up, and electricity costs are lower. It is difficult for a single sheet to compete with these mining rigs, but at the same time, the cost of such machines is also greater.
Currency security
Bitcoin withdrawal requires up to hundreds of keys, and most people will record this long string of numbers on the computer, but frequent problems such as damage to the hard disk will cause the key to be permanently lost, which also leads to The loss of Bitcoin.
System risk
System risk is very common in Bitcoin, and the most common one is fork. The fork will cause the price of the coin to fall, and the mining revenue will drop sharply. However, many situations have shown that the fork will benefit the miners. The forked altcoins also need the mining power of the miners to complete the process of minting and trading. In order to win more miners, the altcoins will provide more block rewards and rewards. Handling fees to attract miners. Instead, risk has made miners.
Types of Mining Rigs
ASIC miner
ASIC mining rig refers to the mining rig that uses ASIC chip as the core computing part. ASIC chip is a kind of chip specially designed for a certain purpose. It must be explained that it is not only used for mining, but also has a wider range of applications. The characteristics of this chip are simple and efficient. For example, Bitcoin uses the SHA256 algorithm, then the Bitcoin ASIC mining rig chip is designed to only calculate SHA256, so in terms of mining, the performance of the ASIC mining rig chip exceeds the current top-level Computer CPU. Because ASIC mining Rigs have an absolute advantage in computing power, computers and graphics card mining rigs have gradually been eliminated.
GPU miner
GPU mining rig, the simple explanation is the digital currency mining rig mining through the graphics card (GPU). After Bitcoin, some other digital assets have appeared one after another, such as Ethereum, Dash, Litecoin, etc., some of which use algorithms that are different from Bitcoin. In order to achieve higher mining efficiency, miners After doing different tests, I finally found that the SHA256 algorithm uses ASIC to mine the most efficient digital currency. The GPU graphics card is the most efficient for mining digital currencies such as Scrypt and other algorithms, so a dedicated GPU mining rig was born.
IPFS miner
IPFS is similar to http and is a file transfer protocol. In order for IPFS to operate, there are many computers (storage devices) in the network as nodes. Broadly speaking, all participating computers can be called IPFS miners. In order to attract more users to become nodes and contribute to the network, the IPFS network has designed a cryptocurrency called filecoin, which is distributed to participants (nodes) as rewards based on the amount of storage space and bandwidth contributed. In a narrow sense, a computer designed specifically to obtain filecoin rewards is called an IPFS miner. Since the IPFS network requires storage space and network bandwidth, in order to obtain the highest profit ratio, IPFS mining Rigs usually strengthen storage space and reduce the power consumption of the whole machine. For example, equipped with more than 10 large-capacity hard drives, equipped with a gigabit or higher speed network card, using ultra-low-power architecture processors, and so on.
FPGA miner
FPGA mining rig is a mining rig that uses FPGA chips as the core of computing power. FPGA mining rig is one of the early mining Rigs. It first appeared at the end of 2011. It was once optimistic at the time, but the active period was not long, and it was gradually replaced by ASIC mining rigs and GPU mining rigs. FPGA (Field-Programmable Gate Array), the Chinese name is Field-Programmable Gate Array. A more popular understanding is that FPGA is a large number of logic devices (such as AND gates, NOT gates, OR gates, selectors) encapsulated in a box, how to connect the logic components in the box, all by the user (programming) To decide. If the mining program is written in the FPGA, then the FPGA mining rig is built, and because the FPGA is highly flexible, it can not only support Bitcoin's SHA256 algorithm, but also support the Scrypt algorithm that GPU miners are good at. During the active period of FPGA mining rigs, compared to the CPU and GPU mining rigs of the same generation, although FPGA is not superior in computing power, its power consumption is much lower and the overall power consumption ratio is very high.
0 notes
Text
E-INVOICING Fatoorah Saudi Arabia 2021 – REGULATORY & TECHNICAL OUTLOOK
Erpisto #1 E-invoicing Fatoorah Saudi Arabia The Kingdom of Saudi Arabia (KSA) is moving forward with the e-invoicing mandate, with the goal of reaching the first major milestone on December 4, 2021. GAZT's most recent releases enable taxpayers to take the first steps toward implementation.
Action plan for e-invoicing in Saudi Arabia
The introduction of e-invoicing will take place in two stages. The first step covers the creation of electronic invoices and related documentation, as well as processing and record-keeping capabilities. On December 4, 2021, this step will take effect. The second stage (the integration phase) covers the most advanced aspects of the E-invoicing Fatoorah Saudi Arabia, such as electronic signatures. Transmission and exchange of electronic invoices via the GAZT web platform. Although the first stage appears to be less demanding than the second, it already contains a number of particular requirements and calls for the commencement of preparation work as soon as feasible.
Erpisto #1 E-invoicing Fatoorah Saudi Arabia

The e-invoicing regulation's scope
The e-invoicing requirements in Saudi Arabia will apply to a variety of documents, including normal tax invoices, simplified tax invoices, credit and debit notes, and more. If these documents are distributed electronically, existing tax requirements will be followed to ensure that the content is compliant.
Only KSA residents can use e-invoicing
Regulations for electronic invoicing All taxable persons subject to VAT and third parties issuing tax invoices for taxpayers will be affected. These regulations will also apply to Saudi Arabian residents only. E-invoices can be issued and stored in a specific electronic format Predefined data fields. These requirements apply to third parties that issue tax invoices for resident taxable persons.
The e-invoicing guidelines
Persons who are not taxable will not be subject to the provisions of this article resident in Saudi Arabia.
The E-invoicing Regulations have been released
KSA's e-invoicing journey began in September 2020 when the E-invoicing Regulation was created. It finally came into effect three months later in December 2020. However, this is only an overview of the requirement. KSA taxpayers We were eager for a more detailed regulation to be released. This was finally achieved in March 2021. The KSA tax authorities just published an important document. Draft of Controls, Requirements and Technical Specifications for Implementing the E-invoicing Fatoorah Saudi Arabia Regulation The following describes the details of the KSA e-Invoicing concept.
These are the requirements that will soon be enforced.
GAZT published the following documentation at the same moment as the above document:
-Electronic Invoice Data Dictionary
-Standard for Electronic Invoice XML Implementation
-Standards for Electronic Invoice Security Implementation
Local taxpayers now have the documents in their possession and can begin preparations. What documents are included in these documents? Do they contain all necessary information to prepare for the event?
Mandatory e-invoicing What is the best way to get started?
Let's take a closer look at the documents in order to better understand them.
Current e-invoicing landscapes in KSA.
Requirements, Controls, Technical Specifications, and Procedural Rules to Implement the Provisions in the E-Invoicing Regulation (the Draft Rules Regulation).
This is the main document. Clarifies the requirements for e-invoicing This document identifies the controls, specifications or procedures required to implement the E-Invoicing Regulation Precautions Both phases of the document are addressed:
Implementation of e-invoicing:
Phase 1:Electronic invoices and electronic notes can be generated The following provisions, which include those related to processing and record keeping, are in effect as of 4 December 2002.
Phase 2:Transmission of electronic invoices or electronic notes Sharing them with GAZT will allow you to implement the program in phases. Phases are expected to begin in June 2002.
The regulation defines the technical requirements. The E-invoicing Fatoorah Saudi Arabia the so-called Compliant solution, which must be developed by taxpayers to meet the requirement. A competent authority or professional third party will certify such a solution.
Compliant Solution should allow the generation and sharing of e-invoices or e-notes in a predefined format (XML, PDF/A-3). This concept's most distinctive element is the set of data security and information security measures (unique identifier UUID and QR code), which are all included in the solution.
Universally Unique Identifiers (UUIDs):All e-invoices are individually identified by an unique number. This number is assigned to each document along with its sequential number. UUID is 128-bit number generated by an algorithm that makes it unlikely that any other system will generate the same identifier.
Cryptographic Stamp GAZT will add this field to the electronic document upon receipt of the electronic document after positive verification of the E-Invoice/E-Note. The Cryptographic Stamp is composed of two fields: ECDSA's public key and ECDSA signature. It will be generated with the same digital certificate that was used to stamp electronic invoices.
Hash: This will ensure that the sequential numbering is used, and that there is no intervention (such a replacement or deletion) apart from the individual numbering that the taxpayer uses. This element will not contain the invoice data, but it will be used to prevent any modifications of the document. The next invoice will use the hash of that particular invoice. It will be calculated from all elements of the previous invoice (UBL bill, hash, previous invoice, QR code and cryptographic stamp).
QR code: This allows for quick and simple verification of the document using QR camera scanners. It will be encoded using Base64 format, with up to 500 characters.
Counter for internal documents: An independent counting solution that cannot reset and allows for quick detection of fraudulent intervention.
A key feature of the Compliant Solution the ability to connect to the Internet, and to integrate with other systems via an application programming interface (API), will be possible. Thee-invoicing integration capability this regulation will apply to each case and is not detailed in the document.
Technical functionalities (Annex 1)
The Draft Rules Regulation gives a comprehensive overview. Technical functionalities of e-invoicing these will be in force during both phases of implementation. The first phase will see taxpayers focusing on the development of the e-invoice/e note generation feature. Only the second phase will introduce integration capability and the security elements previously mentioned. The Draft Rules Regulation also provides a number of additional features prohibited e-invoice functionalities(e.g. Uncontrolled access, modification capabilities, etc. These must not be used.
E-invoice fields (Annex 2)
Draft Rules include a comprehensive list of fields that are relevant to e-Invoices, as well as an indication of the obligation status. Three statuses can be used to indicate the obligation status for specific fields:
Mandatory (the field must be filled in)
Conditional (must only be used if the condition is met).
Optional (fields not required)
The summary table also shows the E-invoicing Fatoorah Saudi Arabia items that will be mandatory upon completion of phase 1 (4/12/2021) and phase 2, (1/6/2022).
[document 2]Electronic Invoice Data Dictionary
The dictionary also includes a description of different terms are used in e-invoicing documentation. It includes the definition of invoice categories, business terms, and their descriptions, as well as the technical specification of each term (UBL specifications). Finally, it provides the KSA-specific context (if applicable) for each business term. You will also find examples of certain elements in the document.
Standard for Electronic Invoice XML Implementation
This document describes the details of the project in a technical way. Structure of the XML. This is used to generate e-invoices or e-notes. This is the Standard for e-invoicing by KSAIt is based upon the EU standard EN16931-1:2017 and the UBL schema (UBL 2.0). The structure also includes a number of KSA-specific elements that take into consideration the KSA's VAT regime. These include business rules.
The invoice must include a unique identifier (UUID).
Specific transaction codes with defined structures, which identify different invoice types (third party invoices, simplified invoices, summary invoices, export invoices, etc.).
payment means code
Credit and debit notes (specific invoice codes) must be used to justify this type of document.
Invoice must contain the hash (using SHA256 algorithm functions) from the previous invoice
Document must include a QR code
Each invoice must include a counter value
Document must be cryptographically stamped
Not yet available are additional XML files (Shematrin)The e-invoicing consultation It is now final.
Standards for Electronic Invoice Security Implementation
This document refers specifically to two security measures: the QR codes and the cryptographic stamp. These are the heart of the system. The security of e-invoices/e-notes.
This standard gives more details about the Cryptographic stamp for e-invoice Business process (issuing/management), requirements for creation, and use, as also the structure and format E-invoicing Fatoorah Saudi Arabia stamp. It also includes the QR code specification.
We expect more developments
While the regulations have provided a lot of information so far, they are not complete. Releases of e-invoicing Expected Most important are the regulations and requirements that refer to integration features. These will allow for the GAZT's portal allows electronic document exchange. GAZT will publish different API types to help taxpayers integrate .E-invoicing solution with the GAZT e-Invoicing Platform invoice clearance.
The KSA e-invoicing regulations are quite advanced. Businesses now have to determine how the regulations will impact them. These assessments will allow for further analysis of the effects of regulations on businesses. Then, a proper implementation project of E-invoicing Fatoorah Saudi Arabia will be undertaken to meet the first deadline (phase 1), which is set for 4 December 2021.
Services We Offer:
· Automatically receive and send invoices
· Multi-currency, invoice customization
· Support all invoice formats
· Integrate with existing systems
· Archiving capabilities
· Multiple forms of payments
· Integrate analytics
· Safety and support
· Invoice number.
· Reminder For Invoices
· Terms and conditions.
· A line detailing each product or service
· Real-time tracking of invoices
· One-time reporting of B2B invoices
· Easy creation of e-way bill
· Helps the buyers
· Reduction in frauds
· Reduction in data entry errors
· Allows interoperability
· Curb tax evasion
· QR code
Click to Start Whatsapp Chatbot with SalesMobile: +966547315697 Email: [email protected]
#e-invoicing software for business#e-invoicing fatoorah system#electronic invoicing software#e-invoicing solutions for business#e-invoicing portal#invoicing automation#erp e-invoicing#billing and e-invoicing#ERP Software in Saudi Arabia#Asset Management Software in Saudi Arabia#Inventory Management Software in Saudi Arabia#Production Management Software in Saudi Arabia#Cloud CRM in Saudi Arabia#Warehouse Management in Saudi Arabia#Trading ERP in Saudi Arabia#Automotive ERP in Saudi Arabia#Construction & Engineering ERP in Saudi Arabia#Aerospace ERP in Saudi Arabia#Pharmacy ERP in Saudi Arabia#Food & Beverage ERP in Saudi Arabia#Packaging ERP in Saudi Arabia#Distribution ERP in Saudi Arabia#ERP Software Selection in Saudi Arabia#ERP Implementation Services in Saudi Arabia#ERP Project Recovery Services in Saudi Arabia#IT & ERP Strategy in Saudi Arabia#Sales Optimization Services in Saudi Arabia#Digital Transformation in Saudi Arabia#Independent Verification Services in Saudi Arabia
0 notes
Text
Introduction to NFT System
NFT underlying technology
The hidden innovation that NFT depends on — blockchain . The main public, non-tamperable, and tradable qualities of NFT depend on the current blockchain innovation.
The data structure of the blockchain is divided into a block header and a block body. Different blocks are connected through the hash value of the previous block header to form a chain structure. The block header and the block body are connected through the Merkle root field. connected. Taking Ethereum as an example, the data stored in the block header mainly includes the hash value of the parent block header, the hash value of the root node of the Merkle tree related to the current block transaction, the block difficulty value, the miner address, the block height, the Gas Upper limit, Gas usage, timestamp, Nonce value, etc. nft development The data stored in the block body includes transaction record table and uncle block, where the NFT transaction record is stored in the data record table of the block body and packaged by miners.
Introduction to NFT System
The information bundled into the block affirmed on the blockchain can’t be messed with and will be for all time put away on the chain. After the information data of NFT is affirmed on the chain, it can presently not be altered. When miners or super nodes use consensus algorithm to complete block generation, they will broadcast to the whole network through P2P protocol (P2P protocol is a distributed network protocol, which appeared earlier than blockchain technology). , the information will be updated. This mechanism realizes a decentralized distributed record, and the consensus algorithm ensures that malicious nodes cannot tamper with the information.
1. Blockchain classification According to the degree of decentralization, it can be divided into three types of chains, namely public chains, alliance chains and private chains.
2. Consensus algorithm The basis for blockchain to establish decentralized trust is the consensus algorithm . The ongoing standard public chain agreement calculations are partitioned into three classes, in particular PoW, PoS, and DPoS:
PoW algorithm: Bitcoin and Ethereum 1.0 use PoW algorithm, namely Proof of Work, proof of work. Taking Bitcoin as an example, the SHA256 calculation is continuously performed, and finally the node that meets the hash value of a given number of leading 0s has the right to produce a block;
PoS algorithm: Ethereum 2.0 adopts this algorithm, Proof Of Stake, proof of rights and interests, and introduces the concept of coin age. The more coins you hold, the higher the probability of getting a block. This algorithm reduces the amount of calculation and improves TPS (concurrent transactions per second) volume), sacrificing a certain degree of decentralization;
DPoS algorithm: Delegated Proof of Stake, each node pledges the tokens in its hands to vote for the most capable and reputable nodes to produce blocks. Taking the EOS blockchain as an example, the entire network votes to select 21 super nodes and 21 super nodes. Nodes take turns to produce blocks, this algorithm can greatly improve TPS, but the degree of decentralization is further reduced Introduction to NFT System
3. Smart Contracts Standard protocol: NFT is deployed on the blockchain through standard contracts such as smart contracts ERC-721 and ERC-1155 . A smart contract is a piece of executable code deployed on the blockchain. The ERC-721 standard is applicable to any non-homogeneous digital content. ERC-1155 is more used in games to identify a type of props.
Smart contract transaction trigger and execution mechanism: transaction is a bridge connecting the external world and the internal state of Ethereum, so Ethereum is also called the state machine of the transaction. After the smart contract deployment of NFT is completed, the RPC interface is called externally to access the main network of Ethereum. The miners package the transaction,Nft development company and the EVM (Ethereum Virtual Machine) finds the corresponding smart contract and executes the corresponding contract function according to the external input parameters. After the execution is completed, the status is updated on the chain.
For example: The Boring Ape NFT developer deploys the smart contract code to Ethereum, which is included and displayed on the NFT trading platform OpenSea. When one of the users initiates the purchase of the Boring Ape NFT on the OpenSea platform, OpenSea calls the RPC interface to access the Ethereum main network to send transactions Request, miners package the transaction to find the smart contract to execute, and update the status on the chain to complete the transaction.
The Ethereum relay acts as a bridge connecting the traditional server side and the Ethereum blockchain in the service cluster. The relay is responsible for the realization of related functions on the public chain, and almost covers most of the functions of the current Ethereum DApp.
The so-called RPC protocol is to standardize a data format when the client interacts with the server that implements the RPC interface. The general process of RPC interface implementation. The caller of the service serializes and encodes the function name and parameters of an RPC interface according to the standard coding method, and then sends it to the service provider, that is, the server side. The server side then deserializes it. After that, the corresponding parameters are extracted, and then the result is returned to the caller of the service by calling the relevant function.
4. NFT industry chain The NFT industry chain includes the upstream infrastructure layer (settlement layer), the midstream project creation layer (protocol layer), and the downstream derivative application layer . The upstream infrastructure layer provides infrastructure support for NFT minting and trading. The midstream project creation layer mints NFTs according to the minting protocol and issues them in the primary market. The downstream derivative application layer derives NFT secondary markets and data around the NFT minted in the primary market. platforms and social platforms, etc.
NFT is an encrypted digital property right certificate based on blockchain technology. The casting, issuance, circulation and derivative applications of NFT require a relatively mature and usable blockchain and its underlying ecology (development tools, storage, wallets, etc.) As the underlying infrastructure support.
The NFT infrastructure layer is responsible for the recording and settlement of value, and builds the security and finality of the entire NFT ecosystem. The development space of NFT midstream and downstream applications is limited by the performance and interoperability of the upstream NFT infrastructure layer.
The construction of the NFT infrastructure layer includes point-to-point Internet protocols, platform-neutral computing description languages, data storage protocols, trustless interaction platforms, trustless interaction protocols, and transient data transmission.
The NFT ecology of Ethereum (ETH) developed earlier, forming non-homogeneous token protocol standards such as ECR721 and ECR1155, and is currently the absolute overlord of the infrastructure in the NFT field.
According to Cryptoslam’s statistics, the total transaction volume in the NFT field in the past 30 days (9.16–10.15) was 2.441 billion US dollars, of which 71.48% were based on Ethereum, and 18.52% were based on Ethereum’s side chain Ronin (mainly Axie Infinity), and the rest In addition to Solana, blockchain accounts for less than 1%.
The NFT collection projects built on Ethereum have taken over 9 of the Top 10 transactions in the past 30 days (9.16–10.15), including Art Blocks, CryptoPunks and other projects, and accounted for 84 of the Top 100 in the total historical transactions . Nft generator
0 notes