#softwareupdate
Text
Tamagotchi Uni 1.6.0: How to Use My Box Feature

One of the best features in the new 1.6.0 software update is the My Box feature which allows you to store more items than you can store on the device locally. My Box can store up to 80 accessories, 40 items, and 40 pieces of furniture. However you can not store everything in My Box, the rattle, building blocks, cleaning robot, potted flowers, tv, soda, any item downloaded using download codes, download area items, and items and furniture currently placed in the room cannot be stored in My Box. You also cannot store more than 3 of the same item, the excess will be sold for Gotchi Points when you store in My Box.




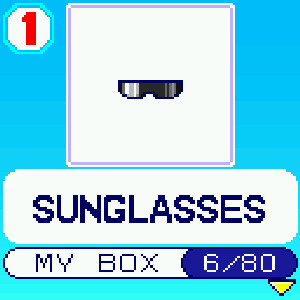
To store items in My Box, simply select the Items icon from the main menu and navigate down to “My Box” which is at the bottom of the list. From the My Box menu, select the “Put Away” option and then select if you’re putting away an accessory, item, or furniture. Simply browse your items pressing the “A” button and then select “B” on the items you wish to store in My Box. A “Done!” message will display to confirm.






To take items out of My Box, simply select the items icon from the main menu and navigate down to "My Box” which is at the bottom of the list. From the My Box menu, select the “Take Out” option and then select if you’re taking out an accessory, item, or furniture. Simply browse your items pressing the “A” button and select “B” on the items you wish to take out of My Box. A “Done”! Message will display to confirm.

When a select is made to either store items or take items out of My Box, you’ll see the saving screen. It is important to note that you should NOT press the reset button while on this screen as data may become corrupt. It’s not very clear where these items are being saved to, but we’re assumed some type of cloud storage.
#tamapalace#tamagotchi#tmgc#tamagotchiuni#tamagotchi uni#uni#tamatag#virtualpet#bandai#1.6.0#softwareupdate#software update#mybox#my box#howto#how to
19 notes
·
View notes
Link
One UI 6.1 AI Update is Confirmed for These Galaxy Phones
#TechReview#Android14#Confirmed#Galaxy#GalaxyA34#GalaxyA54#GalaxyS21#GalaxyS22#GalaxyS23#GalaxyS24#GalaxyZFlip5#GalaxyZFold5#oneui6#oneui6.1#phones#PopularBlog#Samsung#softwareupdate#Update
0 notes
Link
The Motorola Edge 40, a compelling mid-range smartphone lauded for its impressive specs and user experience, is receiving its long-awaited upgrade to Android 14 in India. This rollout signifies Motorola's commitment to software support, ensuring their devices stay up-to-date with the latest features and security patches. Android 14 Arrives for the Edge 40: A Look at the Update While an official announcement from Motorola is yet to surface, user reports, including one from X (formerly Twitter), confirm the commencement of the Android 14 update rollout for the Edge 40 in India. This update, weighing in at 1.49GB and tagged with firmware version U1TL34.115-13, brings the exciting functionalities of Android 14 alongside Motorola's enhancements within their My UX interface. Motorola Edge 40 Receives Android 14 Update The rollout is currently proceeding in batches, ensuring a smooth and stable update experience for all Edge 40 users in India. With the update gradually reaching a wider audience, users can expect to receive a notification prompting them to download and install Android 14 on their devices. A Glimpse Back: The Motorola Edge 40's Impressive Specs The Edge 40 debuted in 2023, garnering widespread acclaim for its robust specifications and competitive price point. It secured the coveted title of "best mid-range smartphone" in our rankings due to its well-rounded feature set. Here's a quick recap of the Edge 40's key specifications: Processor: Powered by the efficient MediaTek Dimensity 8020 SoC, the Edge 40 delivers smooth performance for daily tasks, gaming, and multitasking. RAM and Storage: Equipped with 8GB of LPDDR4X RAM and 256GB of UFS 3.1 storage, the Edge 40 offers ample memory for running apps and storing data. Battery: The 4,400 mAh battery ensures long-lasting usage, complemented by 68W fast charging technology for rapid power refills. Notably, the Edge 40 was the first phone in its segment to boast 15W wireless charging capabilities. Camera System: The dual-camera setup on the rear features a 50MP primary sensor with OIS and a wide f/1.4 aperture, ideal for capturing stunning photos in various lighting conditions. A versatile 13MP ultrawide lens, doubling as a macro shooter, expands your photographic possibilities. For high-quality selfies and video calls, the Edge 40 packs a 32MP front-facing camera. Display: Immerse yourself in vibrant visuals with the Edge 40's stunning 6.55-inch FHD+ 3D curved pOLED display. This best-in-class display boasts a smooth 144Hz refresh rate for exceptional user experience, a peak brightness of 1200 nits for clear visuals even outdoors, 100% DCI-P3 color gamut for vivid color reproduction, and HDR10+ support for enhanced contrast and detail. Additionally, the display integrates an in-display fingerprint reader for secure and convenient unlocking. Audio: Elevate your entertainment experience with the Edge 40's dual stereo speakers featuring Dolby Atmos support, offering immersive and powerful sound. Design and Durability: The Edge 40 comes in three captivating color options: Eclipse Black, Nebula Green, and Lunar Blue. The Nebula Green and Eclipse Black models boast a luxurious vegan leather finish, while the Lunar Blue variant features a sleek acrylic glass finish. The Edge 40's durability is further enhanced by its IP68 rating, signifying its resistance to dust and water, providing peace of mind in various environments. A Sweet Upgrade and a Promise for the Future The rollout of Android 14 to the Motorola Edge 40 signifies not only an upgrade to the latest features and functionalities but also reinforces Motorola's commitment to software support. When the Edge 40 launched, it came with the promise of receiving two major Android updates. With Android 14 now readily available, users can not only enjoy the current suite of improvements but also anticipate a future update to Android 15, ensuring their device remains secure and up-to-date. FAQs: Q: How can I update my Motorola Edge 40 to Android 14? A: To update your Motorola Edge 40 to Android 14, ensure you have a stable internet connection and navigate to the Settings menu. From there, select System > Software Update > Check for Updates, and follow the on-screen instructions to download and install the latest software version. Q: What are the key features of the Android 14 update for the Motorola Edge 40? A: The Android 14 update for the Motorola Edge 40 introduces new features and enhancements, including improved performance, updated security patches, and enhancements to the user interface. Q: Is the Motorola Edge 40 eligible for future Android updates? A: Yes, the Motorola Edge 40 is eligible to receive future Android updates, including the upcoming Android 15 release. Motorola has committed to providing timely software updates to ensure users continue to benefit from the latest innovations and improvements.
#144Hzrefreshrate#32MPselfiecamera#50MPsensor#68WFastCharging#Android14update#Dualcamera#India#MediaTekDimensity8020#MotorolaEdge40#MotorolaEdge40ReceivesAndroid14Update#MyUX#pOLEDdisplay#softwareupdate#wirelesscharging
0 notes
Text
Prolong the Lifespan of Medical Imaging Equipment
Enhance the lifespan of MRI machines, CT machines, CATH labs, and other imaging equipment.
✅Schedule Regular AMC/CMC Services
✅Upgrade Imaging Equipment
✅Utilize Genuine Spare Parts
✅Timely Software Update
✅Implement Calibration and Quality Assurance Procedures
✅Optimize Magnetic Field strength for Imaging
We offer comprehensive upgrades and servicing for imaging equipment across India and globally. Our expert team ensures top-notch maintenance and updates to keep your equipment running smoothly. Trust us for reliable support and unparalleled service for all your imaging needs.
Let's Discuss Your Requirement: +𝟗𝟏-𝟗𝟖𝟗𝟗𝟗𝟔𝟑𝟔𝟎𝟏, 𝟖𝟑𝟖𝟒𝟎𝟑𝟕𝟎𝟕𝟑

#MRI#CT#Cathlab#imagingequipmentservices#upgradeimagingequipment#genuinepareparts#softwareupdate#medicalimaging#installation#deinstallation#radiology#phantomhealthcare
0 notes
Link
https://bit.ly/3RikaGt - 🚨 High-Severity Vulnerability in Dell Command Configure: A significant vulnerability has been identified in Dell Command Configure, a tool used for BIOS configuration on Dell client systems. This vulnerability, tagged as CVE-2023-43086, holds a CVSS base score of 7.3, indicating a high level of severity. It allows local malicious users to modify files during application upgrades, potentially leading to escalated privileges and system compromise. Immediate attention is required to mitigate this risk. #CyberSecurityAlert #DellVulnerability 🔧 Details of the Vulnerability: Dell Command | Configure, utilized for BIOS settings adjustments through its UI or CLI, faces an "improper access control vulnerability." This flaw can lead to unauthorized resource access, including files and directories, potentially compromising the affected system. The vulnerability arises from weak access controls and insufficient authorization checks. #SystemSecurity #AccessControlVulnerability 💻 Versions Affected and Remediation Steps: Versions of Dell Command | Configure prior to 4.11.0 are susceptible to this vulnerability. Dell has released remediated versions to address this issue. Users are advised to update to the latest software version and apply security patches promptly to ensure protection against potential exploits.
#CyberSecurityAlert#DellVulnerability#SystemSecurity#AccessControlVulnerability#SoftwareUpdate#CyberSecurityBestPractices#DellSecurity#TechSafety#VulnerabilityManagement#ITSecurity
0 notes
Text
Answer1
The quick-service segment's introduction of drive-through windows undoubtedly transformed the hospitality sector. Technology-related software, in my opinion, has had the most influence on its development.Operations have been streamlined and efficiency has increased through the use of cutting-edge software tools for inventory management, order processing, and communication between the drive-through employees and the kitchen. It is now simpler for companies to manage high order volumes and guarantee accuracy thanks to these software programs. I would therefore conclude that the success of the drive-through concept has been mostly due to software related to technology.

Answer2
I completely sympathize with your worries about being recorded on camera while eating.Our organization has installed video surveillance in select areas because we prioritize the safety and security of both our visitors and staff. By taking these precautions, we can keep everyone safe, stop theft, and guarantee the calibre of our goods. You may be confident that the footage is handled with the highest confidentiality and is only used for security purposes. We value your privacy and work hard to make every guest's eating experience comfortable. Feel free to get in touch if you have any more queries or worries.

Answer3
Three ways that technology has affected human resource management cost containment are as follows:
Time and money are saved through automated hiring procedures.
Options for remote work cut down on office space and associated costs.
Online training programs provide opportunities for affordable staff development.
In the future, developments in technology will:
Expand the flexibility and options for remote work.
Include automation and AI in a range of work responsibilities.
Make use of augmented and virtual reality to create training that is fully immersive.

Answer4
I think the biggest changes will come from software developments in the next five years. Technologies like automation, data analytics, and tailored dining experiences should find new applications.
1 note
·
View note
Text
Navigating Through Android 14 Issues: A Pixel User's Update Guide

The release of Android 14 has introduced unexpected challenges for Pixel users, with a series of bugs affecting device functionality, particularly storage access. Google has acknowledged these Android 14 issues and is actively working on delivering patches to resolve the Pixel Update Bug. Users have been advised to back up their data and stay updated with the latest software releases to avoid data loss or corruption.
Google's developers are diligently working to release fixes, emphasizing the importance of these patches in restoring functionality. The company's response has been a blend of transparency, regular updates, and a commitment to improving update protocols for the future.
For Pixel users, staying informed and participating in beta programs is crucial during this period. The Pixel community has rallied, providing support and advice, showcasing a collaborative effort in troubleshooting. Despite the setbacks, Google's proactive measures and continuous updates offer hope that these Android 14 issues will soon be resolved, allowing users to fully enjoy the enhancements of the new OS. This experience serves as a reminder of the complexities of software updates and the importance of a responsive and supportive tech community.
Click Here to Follow Us on:-
Blog | Facebook | Pinterest | Instagram | Imgur
#Android14Issues#PixelUpdate#GoogleFixes#TechTroubleshoot#SoftwareUpdate#PixelBugs#AndroidCommunity#SmartphoneSupport#DataSecurity#UpdateAlerts
0 notes
Text
Investing in a website WHY?
Unleash the Power of Your Digital Presence for Business Success. 💻📈
Sdreatech is a versatile platform for IT services. We've received acknowledgment from different companies worldwide. We lead the IT services market due to our talented team's creativity, and skill set.
Our mission at Sdreatech is to establish innovative and cutting-edge software technologies. We may help establish your dreams too. 💻🔥
We'd love to hear from you at [email protected] if you're thinking about giving your company an online presence.
.
.
#Website#websitedevelopment#websitebuilder#websitedeveloper#websitelaunch#websitedesigncompany#software#softwareupdate#softwaresolutions#softwaredeveloper#softwaredevelopment#softwarecompany#mobileapp#mobileappdesign#mobileappdeveloper#mobileappdevelopment#technologysolutions#sdreatech
0 notes
Text
🚀 Discover the Latest Enhancements: Updates in SyncBrowser Beta 1.0.1.3!
🔒 Upgraded Servers: Lightning-fast content delivery with CDN acceleration.
🛠 VPN Compatibility Fixed: VPN users can now use the software hassle-free!
🎬 Sync Latest Movies: Infinite movie options waiting for you to sync and enjoy.
🔧 Improved Stability: A more stable and reliable browsing experience.
💻 Easy Upgrade: Conveniently upgrade within the in-built button.
🆕 New Users Welcome: Apply now for the newest software and unlock exciting features! 👉
Enhancing your browsing journey is our top priority. Happy browsing ahead! 🌐💻

0 notes
Text

SentryPC is a completely cloud-based computer monitoring, content filtering, and time management software wrapped into one. Whether you are a concerned parent looking for parental control software or business looking for employee monitoring software - SentryPC is your answer!
Buy Now SentryPC
#contentfiltering#contentfilteringservice#employeemonitoringsoftware#employeemonitoringsolution#employeemonitoringsoftwareworkfromhome#EmployeeMonitoring#employeemonitoring#monitoringsoftware#SentryPC#computermonitoring#computermonitoringsystem#managementsoftware#managementsoftwares#managementsoftwareoxford#managementsoftwaresystem#managementsoftwaresolutions#software#softwareupdate#softwaretesting#softwarecompany#softwaresolutions#onlinesoftware#onlinesoftwares#monitoringsoftwares#monitoring#monitoringsystem#monitoringservices#monitoringsolutions#monitoringandevaluation
0 notes
Text
Bandai Dropped Clues before Launching Very Berry Land & LoveMelo Concert Downloadable Content


Did you notice that? Before the Tamagotchi Uni 1.6.0 software update as announced with the new Tama Portal feature bringing downloadable content to our devices, Bandai did drop some hints on two of the locations!
That’s right, beautiful artwork of both Very Berry Land and Melody Land were posted on their social media profiles. Is that a coincidence? Perhaps we’ll get clues for the two remaining locations?
#tamapalace#tamagotchi#tmgc#tamagotchiuni#tamagotchi uni#uni#tamatag#virtualpet#bandai#1.6.0#softwareupdate#software update#dlc#veryberryland#very berry land#lovemeloconcert#love melo concert#clues#hints
19 notes
·
View notes
Link
0 notes
Link
Apple recently issued a security alert to a select group of iPhone users in India, as well as in 91 other countries. The alert warns of a sophisticated cyber threat known as "mercenary spyware." This article delves into the details of this threat, how to identify it, and steps you can take to protect yourself. What is Mercenary Spyware? Unlike common malware that targets a broad range of users, mercenary spyware is a highly targeted and expensive tool used to gain access to the devices of specific individuals, often high-profile figures. Targets can include politicians, journalists, diplomats, and activists. These attacks are designed to steal sensitive information, track a user's location, and potentially intercept communications. Apple Warns High-Profile Users Why is Mercenary Spyware Different? Mercenary spyware differs from typical cyberattacks in several ways: Cost and Complexity: Developing and deploying mercenary spyware requires significant resources, making it a weapon reserved for well-funded attackers. Short Shelf Life: Developers constantly refine their tools to evade detection, resulting in a shorter lifespan for each version of the spyware. This rapid evolution makes them more challenging to identify and prevent. Highly Targeted: Unlike mass malware attacks, mercenary spyware focuses on a handful of specific individuals. How Does Apple Detect and Respond to Mercenary Spyware Attacks? Apple takes user privacy and security seriously. Their advanced security systems constantly monitor for suspicious activity that might indicate a mercenary spyware attack. If a potential threat is detected, Apple will take the following steps: Threat Notification: Apple will directly notify the targeted user through various channels, including a threat notification displayed on their Apple ID login page, an email, and an iMessage notification. These alerts will never request users to click links, open files, install apps, or provide their Apple ID credentials. Lockdown Mode: The notification will advise users to enable "Lockdown Mode" on their iPhones. This feature significantly restricts device functionality, making it more difficult for spyware to operate. How Can You Protect Yourself from Mercenary Spyware Attacks? While the risk of being targeted by mercenary spyware is low for most iPhone users, it's crucial to maintain good security practices to protect your device. Here are some essential steps to follow: Keep Your Software Updated: Regularly update your iPhone's operating system (iOS) to benefit from the latest security patches that address potential vulnerabilities. Enable Two-Factor Authentication: Enhance your Apple ID security by activating two-factor authentication. This adds a second layer of verification during login attempts, making it more difficult for unauthorized access. Choose Strong Passwords: Utilize strong and unique passwords for your Apple ID and other online accounts. Avoid using easily guessable passwords or repeating them across different platforms. Download Apps from Trusted Sources: Only download applications from the official App Store, as third-party app stores may harbor malicious software. Be Wary of Unfamiliar Links: Refrain from clicking on links or opening attachments from unknown senders. Phishing emails are a common method for attackers to deliver spyware. What if I Haven't Received an Alert but Suspect I'm Targeted? If you haven't received a notification from Apple but believe your device might be compromised by mercenary spyware, you can proactively increase your security by enabling Lockdown Mode on your iPhone. While this mode may limit some functionalities, it offers a significant layer of protection. Stay Vigilant and Protect Your Data By understanding the threat of mercenary spyware and implementing these security measures, you can significantly reduce your risk of becoming a target. Remember, remaining vigilant and practicing good security habits are essential steps in safeguarding your data and privacy in an increasingly digital world. FAQs: What is the difference between mercenary spyware and regular malware? Mercenary spyware is highly targeted and expensive, while regular malware aims for a broader range of victims. How will Apple notify me if I'm targeted by mercenary spyware? Apple will send a threat notification to your Apple ID login page, email address, and phone number associated with your Apple ID. What is Lockdown Mode and how does it help? Lockdown Mode restricts certain functionalities on your iPhone, making it more difficult for spyware to operate. Should I be worried about mercenary spyware attacks? The risk is low for most users. However, maintaining good security practices is crucial for protecting your iPhone from all cyber threats.
#appstore#apple#AppleWarnsHighProfileUsers#cyberattack#highprofileusers#India#mercenaryspyware#notification#phishing.#protection#security#softwareupdate#twofactorauthentication
0 notes
Link
Stay ahead from the crowd with our latest blog posts regularly. We provide updates related to latest technologies & trends in software development.
0 notes
Photo

Protect your device and personal data by updating your phone software. Need help? Just Call @onefixmobilesolutions ☎️Call/ Book an Appointment! 203-350-7520 #softwareupdate #internetofthings #desktop #thunderbolt #iot #ios #ram #softwarecompany #softwaretesting #mapsmagazine #softwareupdates #iphone #bridgeport #bridgeportct #trumbullct #fairfieldct #fairfieldcounty #stamfordct #sheltonct #eastonct #derbyct #mobileservice #mobileservices #localservice #iphonemobile #iphonewholesale #phonesale #appleproducts (at Bridgeport, Connecticut) https://www.instagram.com/p/CpyLqC6uFpg/?igshid=NGJjMDIxMWI=
#softwareupdate#internetofthings#desktop#thunderbolt#iot#ios#ram#softwarecompany#softwaretesting#mapsmagazine#softwareupdates#iphone#bridgeport#bridgeportct#trumbullct#fairfieldct#fairfieldcounty#stamfordct#sheltonct#eastonct#derbyct#mobileservice#mobileservices#localservice#iphonemobile#iphonewholesale#phonesale#appleproducts
0 notes
Text
Die "Zwangs-ePA" ist da
Elektronische Patientenakten für alle?
https://www.aktion-freiheitstattangst.org/images/icons/ePA-Handy.jpg
Wie man bei 1% Beteiligung nach mehrmaliger Werbung per Brief in jeden betroffenen Haushalt von "breiter Zustimmung" sprechen kann, bleibt sicher das Geheimnis von Bertelsmann. Es soll an dieser Stelle aber kein Geheimnis bleiben, dass "Arvato [ist] als einer von insgesamt acht Geschäftsbereichen des Bertelsmannkonzerns ein weltweit tätiges Dienstleistungsunternehmen mit Hauptsitz in Gütersloh" ist. (https://de.wikipedia.org/wiki/Arvato)
Arvato betreibt für die Gematik das "Gesundheitsnetz" und hat für dieses, vom Internet durch "Connectoren" abgetrennte Netz, in allen Arztpraxen und Krankenhäusern viel Technik installieren dürfen. Diese Technik wurde nach vielen Pannen mehrfach aufgerüstet. Alle diese Kosten durften die Krankenversicherungen und das Gesundheitsministerium, damals angeführt von Minister Spahn, tragen. (s. z.B. Bundesrechnungshof will GEMATIK prüfen , Google hantiert mit Millionen Patientendaten , Herr Spahn will die Verantwortlichkeiten verwischen , Elektronische Patientenakte - Top oder Flop? , Gesundheitsdaten sicher ... für 10 Minuten , Sicherheitslücke(n) in der ePA , ...)
Im Endergebnis zahlt der Steuerzahler und die gesetzlich Versicherten für ein Monster, dessen Sinn und Zweck - die Vermeidung von Doppeluntersuchungen - auch durch die Krankenkassen zu kontrollieren wäre. All dies läuft unter dem Motto "mehr Digitalisierung" ohne realistische Betrachtung des wirklichen Kosten-Nutzen-Verhältnis. Und dann sind da noch die Gefahren, die die Zwangsdigitalisierung mit sich bringt, wie z.B. Sicherheitslücke(n) in der ePA und Das Video-Ident Verfahren ist kaputt und Gesundheitsdaten sicher ... für 10 Minuten.
Die letzte geplante Millionen-teure Renovierung aller "Connectoren" ist auch noch total überflüssig, wie der CCC nachgewiesen hat, wie in ct-Heft 23 ab S. 15 zu lesen ist: "Der Austausch von 130.000 Hardware-Konnektoren bis Ende 2024, den die gesetzlichen Krankenkassen mit mindestens 300 Millionen Euro finanzieren sollen, ist technisch unnötig. Dies müssen die für die Telematische Infrastruktur zuständige Gematik sowie die drei Hersteller CGM, Secunet und RISE ebenfalls gewusst haben."
Wieder einmal wird das für eine vernüftige Gesundheitsversorgung nötige Geld für Hardware vergeudet. Die ct schreibt weiter: "Und nun liefert ein kleines Hacker-Team in seiner Freizeit innerhalb von nicht mal zwei Wochen eine Referenzimplementierung, mit der man die Laufzeit der Konnektoren einfach dadurch verlängern könnte, dass Software-Patches ausgespielt werden. Dies lässt keinen anderen Schluss zu, als dass die zu 51 Prozent vom Bund kontrollierte Gematik die wirtschaftlichen Interessen eines Hersteller-Oligopols offenbar schwerer gewichtet als die finanzielle Entlastung der Versicherten. Eine kostengünstige Softwarelösung wurde offensichtlich mit Absicht jahrelang zurückgehalten. Den Schaden tragen die Ärzte und Patienten."
Dem ist nichts mehr hinzuzufügen außer - Schluss mit der Zwangsdigitalisierung!
Mehr dazu bei https://www.bertelsmann-stiftung.de/de/themen/aktuelle-meldungen/2023/februar/elektronische-patientenakte-geplante-widerspruchsloesung-trifft-auf-breite-zustimmung
und https://www.heise.de/news/Gematik-Datenschuetzer-streiten-ueber-kuenftigen-Schutz-von-Gesundheitsdaten-7520433.html
und c't 2022, Heft 23, S.15 ff
Kategorie[21]: Unsere Themen in der Presse Short-Link dieser Seite: a-fsa.de/d/3sN
Link zu dieser Seite: https://www.aktion-freiheitstattangst.org/de/articles/8325-20230305-die-zwangs-epa-ist-da.htm
#eGK#ePA#Hack#Arbeitnehmerdatenschutz#SoftwareUpdate#Lücke#Verbraucherdatenschutz#Datenschutz#Datensicherheit#Freiwilligkeit#Zustimmung#Einwilligungserfordernis#elektronischenPatientenakte#CCC#Skandale#RFID#elektronischeGesundheitskarte#eHealth
1 note
·
View note