#phishing.
Link
Apple recently issued a security alert to a select group of iPhone users in India, as well as in 91 other countries. The alert warns of a sophisticated cyber threat known as "mercenary spyware." This article delves into the details of this threat, how to identify it, and steps you can take to protect yourself. What is Mercenary Spyware? Unlike common malware that targets a broad range of users, mercenary spyware is a highly targeted and expensive tool used to gain access to the devices of specific individuals, often high-profile figures. Targets can include politicians, journalists, diplomats, and activists. These attacks are designed to steal sensitive information, track a user's location, and potentially intercept communications. Apple Warns High-Profile Users Why is Mercenary Spyware Different? Mercenary spyware differs from typical cyberattacks in several ways: Cost and Complexity: Developing and deploying mercenary spyware requires significant resources, making it a weapon reserved for well-funded attackers. Short Shelf Life: Developers constantly refine their tools to evade detection, resulting in a shorter lifespan for each version of the spyware. This rapid evolution makes them more challenging to identify and prevent. Highly Targeted: Unlike mass malware attacks, mercenary spyware focuses on a handful of specific individuals. How Does Apple Detect and Respond to Mercenary Spyware Attacks? Apple takes user privacy and security seriously. Their advanced security systems constantly monitor for suspicious activity that might indicate a mercenary spyware attack. If a potential threat is detected, Apple will take the following steps: Threat Notification: Apple will directly notify the targeted user through various channels, including a threat notification displayed on their Apple ID login page, an email, and an iMessage notification. These alerts will never request users to click links, open files, install apps, or provide their Apple ID credentials. Lockdown Mode: The notification will advise users to enable "Lockdown Mode" on their iPhones. This feature significantly restricts device functionality, making it more difficult for spyware to operate. How Can You Protect Yourself from Mercenary Spyware Attacks? While the risk of being targeted by mercenary spyware is low for most iPhone users, it's crucial to maintain good security practices to protect your device. Here are some essential steps to follow: Keep Your Software Updated: Regularly update your iPhone's operating system (iOS) to benefit from the latest security patches that address potential vulnerabilities. Enable Two-Factor Authentication: Enhance your Apple ID security by activating two-factor authentication. This adds a second layer of verification during login attempts, making it more difficult for unauthorized access. Choose Strong Passwords: Utilize strong and unique passwords for your Apple ID and other online accounts. Avoid using easily guessable passwords or repeating them across different platforms. Download Apps from Trusted Sources: Only download applications from the official App Store, as third-party app stores may harbor malicious software. Be Wary of Unfamiliar Links: Refrain from clicking on links or opening attachments from unknown senders. Phishing emails are a common method for attackers to deliver spyware. What if I Haven't Received an Alert but Suspect I'm Targeted? If you haven't received a notification from Apple but believe your device might be compromised by mercenary spyware, you can proactively increase your security by enabling Lockdown Mode on your iPhone. While this mode may limit some functionalities, it offers a significant layer of protection. Stay Vigilant and Protect Your Data By understanding the threat of mercenary spyware and implementing these security measures, you can significantly reduce your risk of becoming a target. Remember, remaining vigilant and practicing good security habits are essential steps in safeguarding your data and privacy in an increasingly digital world. FAQs: What is the difference between mercenary spyware and regular malware? Mercenary spyware is highly targeted and expensive, while regular malware aims for a broader range of victims. How will Apple notify me if I'm targeted by mercenary spyware? Apple will send a threat notification to your Apple ID login page, email address, and phone number associated with your Apple ID. What is Lockdown Mode and how does it help? Lockdown Mode restricts certain functionalities on your iPhone, making it more difficult for spyware to operate. Should I be worried about mercenary spyware attacks? The risk is low for most users. However, maintaining good security practices is crucial for protecting your iPhone from all cyber threats.
#appstore#apple#AppleWarnsHighProfileUsers#cyberattack#highprofileusers#India#mercenaryspyware#notification#phishing.#protection#security#softwareupdate#twofactorauthentication
0 notes
Text
I just got another one of those phishing emails where it pretends to be a confirmation of a subscription you never signed up for and tries to trick you into providing personally identifying information for "confirmation purposes" when you attempt to cancel, but:
a. this one is for a weekly grocery delivery service, of all things; and
b. the fake shopping list contains nothing but ham.
I have been fraudulently subscribed to ham.
9K notes
·
View notes
Text
How I got scammed

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/02/05/cyber-dunning-kruger/#swiss-cheese-security

I wuz robbed.
More specifically, I was tricked by a phone-phisher pretending to be from my bank, and he convinced me to hand over my credit-card number, then did $8,000+ worth of fraud with it before I figured out what happened. And then he tried to do it again, a week later!
Here's what happened. Over the Christmas holiday, I traveled to New Orleans. The day we landed, I hit a Chase ATM in the French Quarter for some cash, but the machine declined the transaction. Later in the day, we passed a little credit-union's ATM and I used that one instead (I bank with a one-branch credit union and generally there's no fee to use another CU's ATM).
A couple days later, I got a call from my credit union. It was a weekend, during the holiday, and the guy who called was obviously working for my little CU's after-hours fraud contractor. I'd dealt with these folks before – they service a ton of little credit unions, and generally the call quality isn't great and the staff will often make mistakes like mispronouncing my credit union's name.
That's what happened here – the guy was on a terrible VOIP line and I had to ask him to readjust his mic before I could even understand him. He mispronounced my bank's name and then asked if I'd attempted to spend $1,000 at an Apple Store in NYC that day. No, I said, and groaned inwardly. What a pain in the ass. Obviously, I'd had my ATM card skimmed – either at the Chase ATM (maybe that was why the transaction failed), or at the other credit union's ATM (it had been a very cheap looking system).
I told the guy to block my card and we started going through the tedious business of running through recent transactions, verifying my identity, and so on. It dragged on and on. These were my last hours in New Orleans, and I'd left my family at home and gone out to see some of the pre-Mardi Gras krewe celebrations and get a muffalata, and I could tell that I was going to run out of time before I finished talking to this guy.
"Look," I said, "you've got all my details, you've frozen the card. I gotta go home and meet my family and head to the airport. I'll call you back on the after-hours number once I'm through security, all right?"
He was frustrated, but that was his problem. I hung up, got my sandwich, went to the airport, and we checked in. It was total chaos: an Alaska Air 737 Max had just lost its door-plug in mid-air and every Max in every airline's fleet had been grounded, so the check in was crammed with people trying to rebook. We got through to the gate and I sat down to call the CU's after-hours line. The person on the other end told me that she could only handle lost and stolen cards, not fraud, and given that I'd already frozen the card, I should just drop by the branch on Monday to get a new card.
We flew home, and later the next day, I logged into my account and made a list of all the fraudulent transactions and printed them out, and on Monday morning, I drove to the bank to deal with all the paperwork. The folks at the CU were even more pissed than I was. The fraud that run up to more than $8,000, and if Visa refused to take it out of the merchants where the card had been used, my little credit union would have to eat the loss.
I agreed and commiserated. I also pointed out that their outsource, after-hours fraud center bore some blame here: I'd canceled the card on Saturday but most of the fraud had taken place on Sunday. Something had gone wrong.
One cool thing about banking at a tiny credit-union is that you end up talking to people who have actual authority, responsibility and agency. It turned out the the woman who was processing my fraud paperwork was a VP, and she decided to look into it. A few minutes later she came back and told me that the fraud center had no record of having called me on Saturday.
"That was the fraudster," she said.
Oh, shit. I frantically rewound my conversation, trying to figure out if this could possibly be true. I hadn't given him anything apart from some very anodyne info, like what city I live in (which is in my Wikipedia entry), my date of birth (ditto), and the last four digits of my card.
Wait a sec.
He hadn't asked for the last four digits. He'd asked for the last seven digits. At the time, I'd found that very frustrating, but now – "The first nine digits are the same for every card you issue, right?" I asked the VP.
I'd given him my entire card number.
Goddammit.
The thing is, I know a lot about fraud. I'm writing an entire series of novels about this kind of scam:
https://us.macmillan.com/books/9781250865878/thebezzle
And most summers, I go to Defcon, and I always go to the "social engineering" competitions where an audience listens as a hacker in a soundproof booth cold-calls merchants (with the owner's permission) and tries to con whoever answers the phone into giving up important information.
But I'd been conned.
Now look, I knew I could be conned. I'd been conned before, 13 years ago, by a Twitter worm that successfully phished out of my password via DM:
https://locusmag.com/2010/05/cory-doctorow-persistence-pays-parasites/
That scam had required a miracle of timing. It started the day before, when I'd reset my phone to factory defaults and reinstalled all my apps. That same day, I'd published two big online features that a lot of people were talking about. The next morning, we were late getting out of the house, so by the time my wife and I dropped the kid at daycare and went to the coffee shop, it had a long line. Rather than wait in line with me, my wife sat down to read a newspaper, and so I pulled out my phone and found a Twitter DM from a friend asking "is this you?" with a URL.
Assuming this was something to do with those articles I'd published the day before, I clicked the link and got prompted for my Twitter login again. This had been happening all day because I'd done that mobile reinstall the day before and all my stored passwords had been wiped. I entered it but the page timed out. By that time, the coffees were ready. We sat and chatted for a bit, then went our own ways.
I was on my way to the office when I checked my phone again. I had a whole string of DMs from other friends. Each one read "is this you?" and had a URL.
Oh, shit, I'd been phished.
If I hadn't reinstalled my mobile OS the day before. If I hadn't published a pair of big articles the day before. If we hadn't been late getting out the door. If we had been a little more late getting out the door (so that I'd have seen the multiple DMs, which would have tipped me off).
There's a name for this in security circles: "Swiss-cheese security." Imagine multiple slices of Swiss cheese all stacked up, the holes in one slice blocked by the slice below it. All the slices move around and every now and again, a hole opens up that goes all the way through the stack. Zap!
The fraudster who tricked me out of my credit card number had Swiss cheese security on his side. Yes, he spoofed my bank's caller ID, but that wouldn't have been enough to fool me if I hadn't been on vacation, having just used a pair of dodgy ATMs, in a hurry and distracted. If the 737 Max disaster hadn't happened that day and I'd had more time at the gate, I'd have called my bank back. If my bank didn't use a slightly crappy outsource/out-of-hours fraud center that I'd already had sub-par experiences with. If, if, if.
The next Friday night, at 5:30PM, the fraudster called me back, pretending to be the bank's after-hours center. He told me my card had been compromised again. But: I hadn't removed my card from my wallet since I'd had it replaced. Also, it was half an hour after the bank closed for the long weekend, a very fraud-friendly time. And when I told him I'd call him back and asked for the after-hours fraud number, he got very threatening and warned me that because I'd now been notified about the fraud that any losses the bank suffered after I hung up the phone without completing the fraud protocol would be billed to me. I hung up on him. He called me back immediately. I hung up on him again and put my phone into do-not-disturb.
The following Tuesday, I called my bank and spoke to their head of risk-management. I went through everything I'd figured out about the fraudsters, and she told me that credit unions across America were being hit by this scam, by fraudsters who somehow knew CU customers' phone numbers and names, and which CU they banked at. This was key: my phone number is a reasonably well-kept secret. You can get it by spending money with Equifax or another nonconsensual doxing giant, but you can't just google it or get it at any of the free services. The fact that the fraudsters knew where I banked, knew my name, and had my phone number had really caused me to let down my guard.
The risk management person and I talked about how the credit union could mitigate this attack: for example, by better-training the after-hours card-loss staff to be on the alert for calls from people who had been contacted about supposed card fraud. We also went through the confusing phone-menu that had funneled me to the wrong department when I called in, and worked through alternate wording for the menu system that would be clearer (this is the best part about banking with a small CU – you can talk directly to the responsible person and have a productive discussion!). I even convinced her to buy a ticket to next summer's Defcon to attend the social engineering competitions.
There's a leak somewhere in the CU systems' supply chain. Maybe it's Zelle, or the small number of corresponding banks that CUs rely on for SWIFT transaction forwarding. Maybe it's even those after-hours fraud/card-loss centers. But all across the USA, CU customers are getting calls with spoofed caller IDs from fraudsters who know their registered phone numbers and where they bank.
I've been mulling this over for most of a month now, and one thing has really been eating at me: the way that AI is going to make this kind of problem much worse.
Not because AI is going to commit fraud, though.
One of the truest things I know about AI is: "we're nowhere near a place where bots can steal your job, we're certainly at the point where your boss can be suckered into firing you and replacing you with a bot that fails at doing your job":
https://pluralistic.net/2024/01/15/passive-income-brainworms/#four-hour-work-week
I trusted this fraudster specifically because I knew that the outsource, out-of-hours contractors my bank uses have crummy headsets, don't know how to pronounce my bank's name, and have long-ass, tedious, and pointless standardized questionnaires they run through when taking fraud reports. All of this created cover for the fraudster, whose plausibility was enhanced by the rough edges in his pitch - they didn't raise red flags.
As this kind of fraud reporting and fraud contacting is increasingly outsourced to AI, bank customers will be conditioned to dealing with semi-automated systems that make stupid mistakes, force you to repeat yourself, ask you questions they should already know the answers to, and so on. In other words, AI will groom bank customers to be phishing victims.
This is a mistake the finance sector keeps making. 15 years ago, Ben Laurie excoriated the UK banks for their "Verified By Visa" system, which validated credit card transactions by taking users to a third party site and requiring them to re-enter parts of their password there:
https://web.archive.org/web/20090331094020/http://www.links.org/?p=591
This is exactly how a phishing attack works. As Laurie pointed out, this was the banks training their customers to be phished.
I came close to getting phished again today, as it happens. I got back from Berlin on Friday and my suitcase was damaged in transit. I've been dealing with the airline, which means I've really been dealing with their third-party, outsource luggage-damage service. They have a terrible website, their emails are incoherent, and they officiously demand the same information over and over again.
This morning, I got a scam email asking me for more information to complete my damaged luggage claim. It was a terrible email, from a noreply@ email address, and it was vague, officious, and dishearteningly bureaucratic. For just a moment, my finger hovered over the phishing link, and then I looked a little closer.
On any other day, it wouldn't have had a chance. Today – right after I had my luggage wrecked, while I'm still jetlagged, and after days of dealing with my airline's terrible outsource partner – it almost worked.
So much fraud is a Swiss-cheese attack, and while companies can't close all the holes, they can stop creating new ones.
Meanwhile, I'll continue to post about it whenever I get scammed. I find the inner workings of scams to be fascinating, and it's also important to remind people that everyone is vulnerable sometimes, and scammers are willing to try endless variations until an attack lands at just the right place, at just the right time, in just the right way. If you think you can't get scammed, that makes you especially vulnerable:
https://pluralistic.net/2023/02/24/passive-income/#swiss-cheese-security

Image:
Cryteria (modified)
https://commons.wikimedia.org/wiki/File:HAL9000.svg
CC BY 3.0
https://creativecommons.org/licenses/by/3.0/deed.en
10K notes
·
View notes
Text
WARNING TO ANYONE USING FURAFFINITY, PASS IT ON!!!!
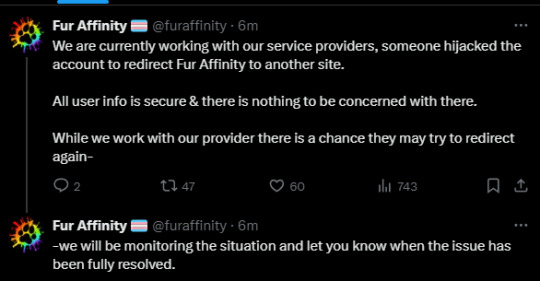

#furaffinity#hack#piracy#phishing#link#website#important#forever reblog#WARNING /!\#signal boost#discord#twitter
6K notes
·
View notes
Text
What if when Michael got Distortioned he/they/it/(?) had just kept showing up to work? Imagine Gertrude comes into the archives and finds a bunch of paperwork filled out in yellow highlighter and folded into impossible shapes, and then Michael-Distortion just walks into the room door-style and sits down at his work computer so it can email Gertrude a phishing scam.
#the magnus archives#tma#michael distortion#the distortion#i think this would make everyone’s lives worse#the eye 🤝(<-phishing) the spiral#tricking someone into thinking you’re someone they can trust so that theyll give you info they can use against you?#that shits both eye and spiral coded af tbh#edit: for those who have said that they want a fic of this i would like to clarify that other people can do what they want with this idea#but i personally cannot write for shit#so i cannot provide a fic. unless you want it bland as hell and written in ieee format#sorry y’all. my skillsets are infodumping about spiders unprompted and eating chicken nugget
5K notes
·
View notes
Text
Important PSA
(Important PSA)
If you get asks claiming to be “technical support staff” asking you to click a link to verify your e-mail because they need your banking credentials or get DMs from similar accounts asking you they need your e-mail address for verification reasons and want your name..
That is a phishing scam impersonating tumblr staff and you should not be posting the asks with a live link in it or trusting the DMs and sending your information! This is an extremely old kind of scam that has began resurfacing and you need to take internet safety into consideration.
It is safer to take a simple screenshot of the ask so the link won’t be spread and lead to a mass hack of users who fell for the attempt. You can warn people without putting their account in danger because some people don’t care what you say and will go to the link anyway.
Please be careful.
582 notes
·
View notes
Text
SCAM ALERT!!!
This morning I woke up to this email
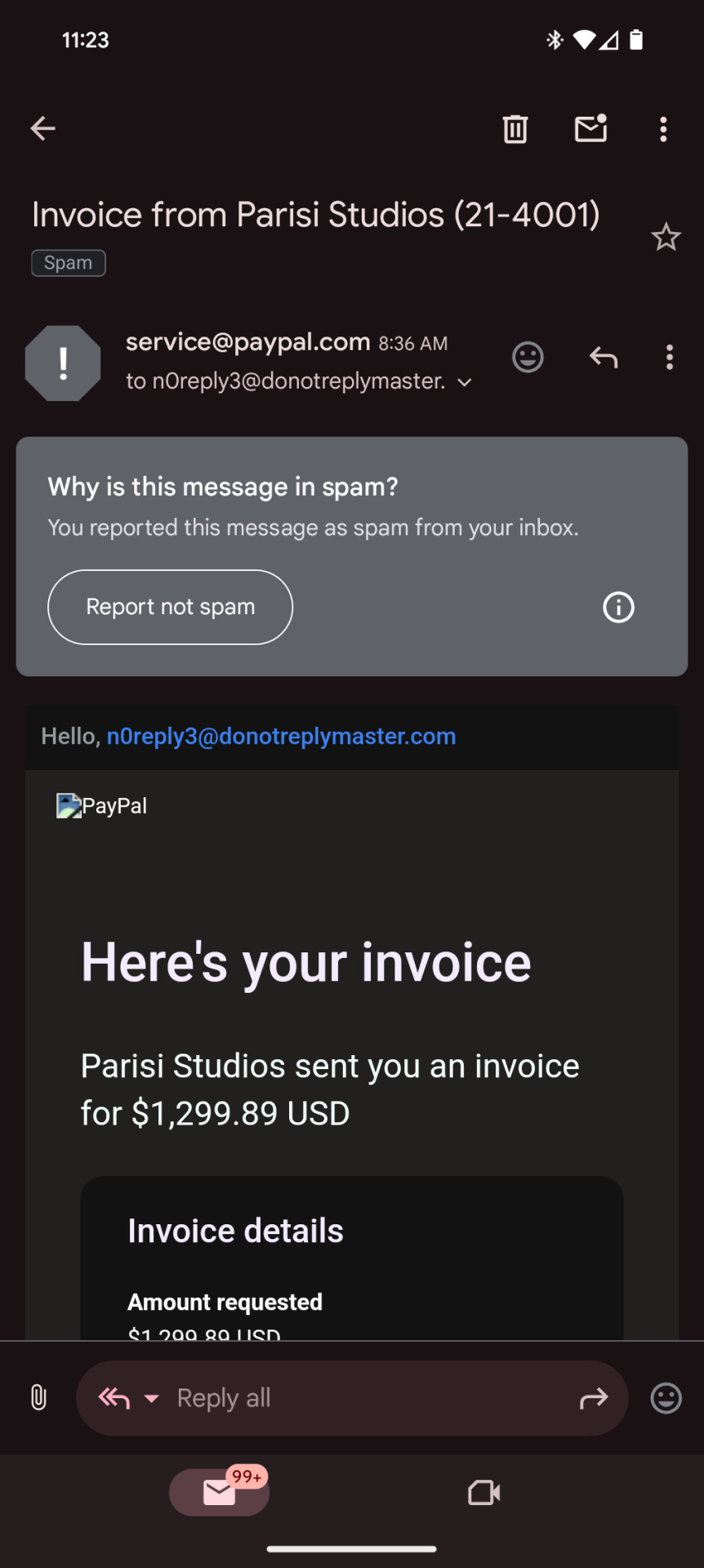

Scary right? It looks as though all of a sudden I owe over a thousand dollars to some studio I've never heard of. This would be enough to make anyone jump to correct the situation. But if you get this email or ones like it, stay calm, do not call the number, and do not click ANY of the links.
This email is fake. I logged into paypal through normal means and there was no such invoice sent to me. While obviously I didn't call the number or click the links to check for sure, this is most likely a classic phishing scheme. Essentially if you click any of the links or call the number, you will be asked for your login information in a way that looks legitimate, but once they confirm your login they will disconnect you, change your password, and have complete access to your paypal.
tl;dr, If you get the email pictured above or anything similar, delete it immediately. Do NOT call the number it provides. Do NOT click on any of the links it contains.
408 notes
·
View notes
Text

Drawing from summer

^ alt version + doodle below

#deltarune#spamton#my art#don’t worry that’s just a poppup trying to fish for personal information#like ‘phishing’ but ‘fishing’ cuz it’s literally fishing. in water. ha. ha.#idk how i colored this one. it just happened#HONORABLE MENTION (someone’s comment on insta)->#‘‘surprise it’s just a pink addison sticking their ponytail out of the water’’#..you can interpret it like that too i guess ahaha
317 notes
·
View notes
Text
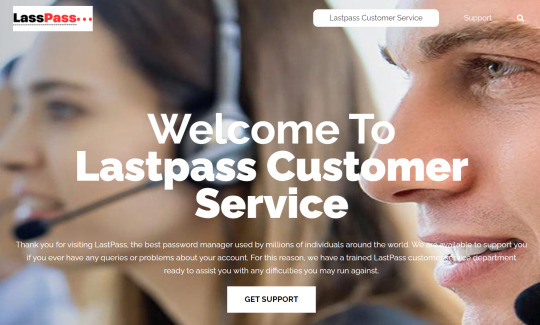
Phishing Alert
ETA: Update - I posted on 20 March 2023 and THIS phishing blog is long gone. There will be others.
*****
@staff - please take note.
This was in my daily dose of bots.
It is NOT what it claims to be. Watch out. (And look at the bottom of this post: they can’t even spell...)




4K notes
·
View notes
Text

(All the memes I made..)
#the muppets#fraggle rock#the muppet show#memes#funny stuff#funny#statler and waldorf#ben and jerrys#heckling#jim henson#kermit#fozzie bear#ice cream#burlington#half baked#cherry Garcia#free cone day#chunky monkey#chubby hubby#cinnamon buns#phish food#tom & jerry#mario & luigi#rick & morty#miss piggy
242 notes
·
View notes
Text


made a little linocut for pixie <:^) miss her so much
#my art#illustration#linocut#printmaking#cat#it's getting easier but it's still hard in different ways now. but i am genuinely just happy she was alive and healthy for so long#went to see the new exorcist yesterday and it was pretty bad but also funny and good at points (the start)#but the REAL win was that I got 2 scoops of ben and jerrys (phish food and cookie dough for those wondering. the best flavours)#and the lady crammed as much ice cream into the pot as posible. like 2 VERY generous scoops followed by extra shoved on top#i had to resist asking to shake her hand she made me want to do like a pledge of allegiance or something
955 notes
·
View notes
Text
Don’t Fall for “Sick Cat” Phishing
Just a reminder that if someone you don’t know suddenly sends you a message asking for help paying vet fees for their sick pet, it’s almost certainly a scam. Don’t give them your money! And make sure to report them to Tumblr for phishing:
click the meatball menu for “report”
select “report something else”
select “unlawful uses or content”
select “phishing”
1K notes
·
View notes
Text

For the Beyblade zine @constellationsbeybladezine
Those are like the only times I actually create complete drawings. I used to participate in dragon designs for a certain game I played and that was like the last time before this I even remotely used to draw something complete. Despite my delay, I'm sated with actually completing this, cuz backgrounds are just challenging to me, at least on IbisPaint. I was pretty impressed with myself when I was able to draw the ocean background, cuz I never thought I'd be able to draw things like that.
But I needed to create the galaxy section on Sketchbook and then import that to IbisPaint to really put this together. Natural brushes of Sketchbook are good, I think both apps should collab.


The one version with frames and another gradient that was fun to look at.
#beyblade#beyblade fanart#mfb#ryutaro fukami#metal fight beyblade#beyblade metal fight#beyblade metal saga#beyblade metal fusion#beyblade metal fury#my art#art#colourful#drawing#artists on tumblr#ibispaintapp#digital art#fanart#anime art#pisces#phish#completed work#thats crazy
184 notes
·
View notes
Text
The state of scammers on this site sucks
I don't trust staff to do anything about it obviously, it just burns me up to see these mfs eat so well it really does
70 notes
·
View notes
Text

PSA. Warn your friends and relatives (especially the older ones).
110 notes
·
View notes
Text
technicai-support isn’t tumblr staff don’t give them your e-mail and personal information it’s a ‘phishing’ attempt done by DMs that might work on people who don’t realize what a phishing scam is.
They just tell you that that your account is limited due to reports and want you to tell them your e-mail address and first name/last name. This person isnt working for tumblr and if your account WAS limited you wouldn’t be able to see/use DMs anyway so this scammer is just a bit silly but I’m sure it’s worked before otherwise they wouldn’t try it.
385 notes
·
View notes