#solving zero problems and creating several new ones! :)
Explore tagged Tumblr posts
Text
Smau except instead of making fake screenshots you create entire accounts for all the characters involved and then have one hub account that acts as the narrator by retweeting all the characters' posts in order and also posting any narrative bits and the characters just never acknowledge the existence of what is very obviously a stalker or perhaps even God
#this would of course make smaus even more complicated and hard to follow and also be a lot morw work for the author#solving zero problems and creating several new ones! :)#anyway posts inspired by me making fake screenshots in middle/high school via the inspect tool#bc i didn't know there were easier ways to do it#2pm in the morning
0 notes
Text
An Explanation of DC's Multiple Universal Reboots and How to Navigate DCU Canon
This is an expansion of a shorter explanation I gave on my Batfam Starter Recs reading list. I figured it might be helpful to have it as a standalone explanation for new comic readers learning how to navigate DC's various attempts to deal with the concept of canon.
The Multiverse is a storytelling device within DC Comics that explains how most of the comics DC has published are tied together or are separate from each other. There exists a "main" universe, where most of DC's published comics collectively take place, and then several alternate universes where things happened differently than they did in the main universe. The multiverse allows writers to explore various concepts like "what if the Jack the Ripper murders happened in Victorian-era Gotham?" and "what if DC's women were the primary heroes of their universe and fought in World War II?" without affecting anything going on in the main universe.
DC Comics canon works in three "mainline" universes:
the pre-Crisis universe (everything published from the beginning of DC Comics until the Crisis on Infinite Earths event in 1986)
the post-Crisis universe (everything published between 1986 and 2011)
the post-Flashpoint universe (everything published from 2011-now)
In the 1980s, management at DC decided that continuity had become too outdated, convoluted, and contradictory to tell coherent stories within a shared universe as more stories were told, new characters were introduced, and new context to prior stories was added. The company had previously attempted to solve this problem in the 1960s by publishing "Flash of Two Worlds," assigning existing stories to two different universes (Earth-One and Earth-Two), and creating a smattering of other alternate universes (Earth-Three was the home of the Crime Syndicate, evil AU versions of the Justice League, for example), but found that this did not actually solve the issue.
So. They decided to do a total universal reboot. That reboot was initiated by the company-wide crossover event known as Crisis on Infinite Earths, published from 1985 to 1986.
COIE effectively rebooted the entire internal DC Universe from the dawn of time onward. A new universal history now existed: the vast majority of characters/character history, history, and events from the varying alternate timelines that existed in the previous universe were retold, retooled, condensed, and/or thrown out in favor of a new, theoretically streamlined single reality. From 1986-2011, DC Comics mainline continuity was published in this shared universe, which industry professionals and fans alike called the 'post-Crisis' universe; in-universe, we refer to this primary version of DC's continuity "New Earth" (or occasionally, Earth-0).
For a wide variety of reasons that I won't get into here, DC completely rebooted their universe again in 2011 following the Flashpoint event comic. This new primary universe—interchangeably called the New 52 universe, post-Flashpoint universe, or Prime Earth, depending on the conversation—once again drastically changed many characters’ histories, personalities, and relationships with each other (sometimes for the better, most of the time for the worse). This is the current universe for DC's main comic line.
Within these three overarching iterations of the DCU, there were several events aimed to clean up, refresh, or reorganize various continuity problems. You may hear people refer to "post-Zero Hour" continuity, for example, to describe post-Crisis events/character histories that were revamped after Zero Hour: Crisis in Time! was published in 1994. "post-Rebirth" continuity, another common descriptor, refers to the reorganization of the post-Flashpoint/Prime Earth universe that happened after the Rebirth event in 2016.
GENERALLY SPEAKING, these are the most common ones you'll hear about:
Pre-Crisis Universe (1937-1986): "Flash of Two Worlds" (1961)
Post-Crisis Universe (1986-2011): pre/post-Zero Hour (1994-2005), post-Infinite Crisis and One Year Later (2005-2008), & post-Final Crisis (2008-2011)
Post-Flashpoint Universe (2011-present): The New 52 (comics written from 2011-2015), Convergence/DCYou (the first attempt to fix New 52 continuity, lasted from 2014-2016), pre/post-Rebirth (2016-2021)—and within Rebirth continuity there were two events, Dark Knights: Metal and its sequel, Death Metal, that did some minor universal revamps (2018-2021)—and post-Death Metal continuity, also known as Infinite Frontier (2021-present). Dark Crisis (2022) also exists but didn't really change the multiversal lore status quo, just simplified the explanation.
Other important universal lore-related things to note about these events:
Prior to Crisis on Infinite Earths, the DCU was an "infinite multiverse." There were no limits on the number of alternate universes that existed and no in-depth explanation for how they were connected or unconnected to the DCU's main timeline.
COIE destroyed the infinite multiverse and condensed everything into one, single universe. Between 1986 and 2005, there were technically no acknowledged alternate universes beyond the "antimatter universe."
"Hypertime" was created by Mark Waid and Alex Ross in 1999 as a way to get around this rule and eventually became the "go-to" way of explaining and fixing various continuity errors. Hypertime is a network of alternate timeline "echoes" that branch off from the main DCU timeline and occasionally overlap with each other, causing alterations in reality.
Since there could only be one timeline, continuity discrepencies were often "fixed" by explaining that one version of events happened in a previous, now destroyed timeline (that characters may or may not remember). Characters could cross from one timeline to another if needed, but any changes resulting from time travelers messing with events caused the destruction of their orginal timeline.
The "Elseworlds" imprint was another method of writing alternate universe stories without explicitly acknowledging the multiverse existed. DC officially just called these books "non-canon" stories without trying to explain how they existed in relation to the main universe. Most if not all of these stories are now considered part of the multiverse.
The infinite multiverse was briefly restored after Infinite Crisis in 2005 and then merged into a single 52-universe multiverse the year afterwards in 52. This new, limited multiverse was explained as there being an "original" Earth (Earth-0) with each successive universe being further and further removed from that one.
The initial post-Flashpoint/New 52 explanation of the multiverse was that there was a limited 52-universe multiverse. That explanation was somewhat overwritten after Rebirth and fully retconned after Death Metal.
Death Metal introduced the concept of the "omniverse," a multiverse of infinite multiverses. Yes, this is dumb. Yes, we generally ignore it and it has now been fully retconned.
The "Dark Multiverse" (a temporary "dark negative counterpart" of each Multiverse reality created by the fears of a universe's people) is theoretically a thing that exists. No, no one else really understands it either and the concept is generally restricted to the two Metal events.
Since Dark Crisis, the DCU is once again a single infinite multiverse in the vein of late pre-Crisis continuity. Every universe and continuity exists, and some are closer to the mainline reality than others.
Right now, the main DCU is once again a singular multiverse with an infinite number of universes. Technically, every version of "mainline universe" history throughout the existence of the multiverse is now considered to have occurred and is remembered by the inhabitants of Prime Earth. In practice, this means that "everything is nebulously canon or non-canon until explicitly acknowledged by a writer to have definitively happened and/or be something that a character remembers happening to them."
Unfortunately, not a lot of writers are doing much with that concept right now outside of picking and choosing their favorite parts of mainline canon to focus on and/or re-canonize, but it at least presents a path forward where a lot of the continuity and characterization issues created by the New 52 reboot are able to be properly addressed.
I hope this explanation was helpful for people, and I'm happy to try and field any further questions as well!
#long post#dc comics#dc meta#dc multiverse#lol that explanation of hypertime is sooooooo condensed but it's basically impossible to properly explain without its own dedicated post
343 notes
·
View notes
Text

Zero Hour: Crisis in Time #2 (September 1994)
Zero Hour continues! The action ramps up as a central character dies, the Team Titans go bad, and everyone else is like "No, it's spelled Teen Titans. What? That's a different comic? Okay, I don't know who they are. Bummer, though."
As seen at the end of last issue, Superman and the heroes he gathered in New York have run into a little problem: a whole-ass future city just materialized over NY and is about to cause the equivalent of several 9/11s. It doesn't help that they have to put up with The Ray, who's kind of a turd in this comic -- I'm just glad Superboy isn't the most insufferable teenage character for once (though he does make an effort later on, when he hits on Anima and says the words "Babe alert!").
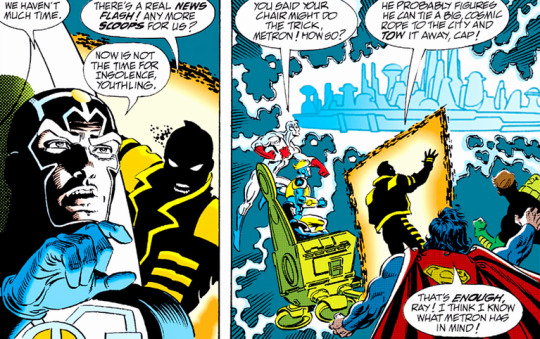
The heroes solve the crashing cities conundrum by creating a Boom Tube portal and shooting lasers at it until it's big enough to suck up an entire city. Hooray for science!
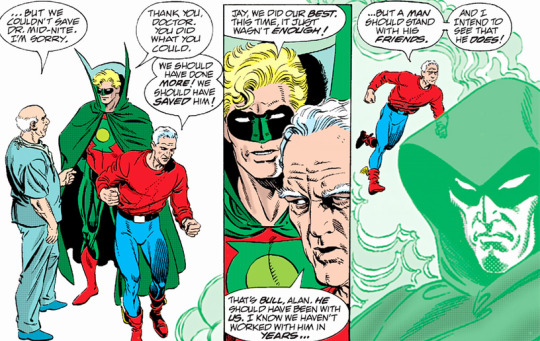
But the celebration doesn't last long, because this is when they find out that their friends at the Justice Society are now older or dead, having been artificially aged (or de-artificially de-aged?) by the villainous Extant. The only JSAer who was spared from the geriatric effect was Alan Scott, the Golden Age Green Lantern, but he decides to quit superheroing anyway and gives his ring to Kyle Rayner, the Current Age Green Lantern. Jay Garrick, the original Flash, calls it quits too and dramatically tears the lightning bolt logo from his chest (but doesn't give it to Impulse, even though he's right there).


The rest of the heroes decide to split up to handle the "time's eating itself" issue from both ends: Superman, Metron, and one group go to the 30th century to try to stop the entropy wave there, and Waverider and another group go do the same thing in the distant past. In both cases, their efforts are hindered by members of the Team Titans, who were introduced a few years ago as a large group of superpowered resistance fighters from the futuristic year 2001. However, their already convoluted origin gets even more confusing when Extant reveals he secretly formed the team and placed them in the present as sleeper agents, waiting for this moment. (Side note: Is this the only DC crossover where ALL the villains are heroes turned bad?)
While delivering all that exposition, the ever-efficient Extant also tries to kill Donna "Suddenly A Darkstar" Troy with a chronal blast. Kyle Rayner gets in the way and saves her (classic Kyle), in the process dropping and completely forgetting that GL ring Alan Scott entrusted him with a few pages ago (also classic Kyle).

Kyle survives this scene, but not everyone else does. Since Waverider is made out of chronal energy, Extant manages to "absorb" all of him and gain his powers, killing him in the process. And that's why Extant had Waverider's golden skin and firey hair last issue, you see: from his perspective, he'd already killed him and stolen his powers/look, and then he traveled in time and used those powers to punk the JSA. That's exactly the sort of twist I like to see in a time travel story.
Meanwhile, Superman and the other heroes currently visiting the 30th century have defeated or captured the mind-controlled Titan Teamsters. According to the narration, Extant's masterful years-long gambit bought him less than two hours of distraction.

With those little rascals out of the way, Metron figures out a way to close the hole that's eating reality: throwing his Mobius chair at it and having Captain Atom blow it up with his quantum energy. This works, because comics. Oh, and then Guy Gardner grows a gun out of his arm, to his shock (and also the shock of Guy Gardner: Warrior writer Beau Smith, since Guy was only supposed to be able to morph ancient weapons). COMICS!!!
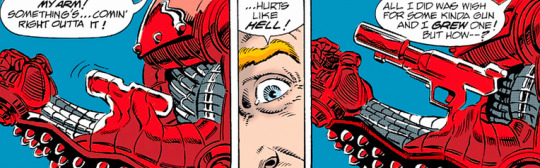
Unfortunately, there's only one Mobius chair and two entropy waves. Not only is the one in the distant past still going strong, but the issue ends with a mystery character single-handedly restarting the 30th century wave and saying something about how this universe will soon stop existing. Also, he has glowing green energy and seems very interested in that GL ring Kyle misplaced... until he isn't.
Huh. Who could that possibly be?
NEXT ISSUE: THE END OF EVERYTHING! (Except this series, which still has one more issue left after that.)
Newsletter-Watch:
What's that, you didn't know we're up to Zero Hour #2 (the third issue) because you missed our other recent posts? That won't happen again if you sign up for the Superman '86 to '99 newsletter, which is free! (Unless you don't want it to be.) Click the link for that.
And if you just love clicking things, click "Keep reading" to see Don Sparrow's commentary for this issue:
Art-Watch (by @donsparrow):
We start with the cover, and it’s another head-scratcher. It does feature the blank (and increasing) whiteness that represents entropy but otherwise isn’t a real attention grabber. Yes, it features Superboy, Nightwing and Supergirl, but other than that, it’s not a lot of marquee names for the time—even Donna Troy, an otherwise recognizable character, is a Darkstar, virtually an unknown look at this time.
Inside we’re greeted immediately by the aftermath of the one-sided battle with Extant taking out the legendary JSA completely on his own. The two page splash that follows is pretty dynamic, though the scene ends abruptly. One little art thing I’d like to point out is how well the shape is defined on Extant’s cape straps, just with a few lines, adding verisimilitude to the otherwise cosmic goings on.

On the next page we’re introduced by name to Legionnaire Emerald Dragon, who I’d seen in the backgrounds of previous issues and wondered who he was. It’s a terrific design, so I felt something like disappointment to learn that this character isn’t really a new concept—it’s just an alternate costume and codename for Jo Nah, far better known as Ultra Boy, the character with all of Superman’s powers, just one at a time.
As the defeated JSA return to the present, there’s some very striking imagery, reminiscent of the elderly wizened mourners at the funeral in the video for Crash Test Dummes’ “Superman’s Song”.

Starman in particular looks poignant, with the relative silliness of his golden age costume contrasting with the weight of age. The image of Jay tearing the lightning bolt off his tunic is a powerful image (confirming something I’d always wondered about—whether the lightning bolt is flat or pointed at the bottom, which to my eye looks pointed—what do you think?), as is the image of both Jay and Alan walking away with dramatic lightning behind them. The placement of the next generation, with Green Lantern Kyle Rayner and Impulse looking on is a great detail as well.
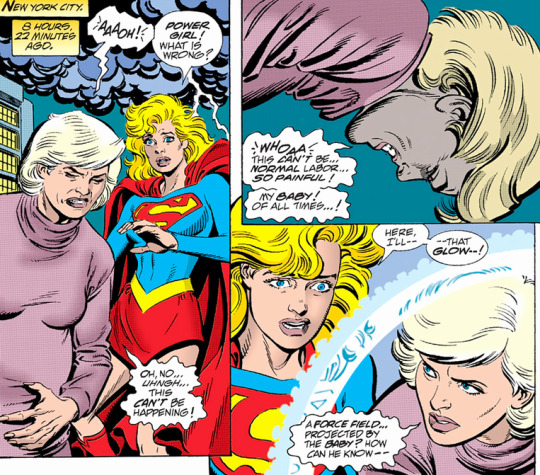
A few pages later, Power Girl’s mystical pregnancy goes into labour, and while we mentioned her looking matronly in the last issue, this one really takes the cake, as famous hottie Karen Starr looks for all the world like Mary Worth here.
The sequence of Hank Hall absorbing Waverider’s chronal energy is well-drawn and seems painful. On the next page we have what I would seem our panel of the week, which is an all-time great drawing of Superman, presiding over the Team Titans members he’s managed to mop up. With Jerry Ordway handling inks, all the faces have a realism rarely seen in comics, but this panel is a real standout among standouts—this is exactly what I imagine Superman really looks like. A page or so later, there’s a similarly stunning portrait of Wonder Woman with Geo-Force. Then on page 21, there’s a pleasing, silver-age-y image of Batman and Robin punching in tandem, which gives Batman '66 vibes.
Lastly, Guy Gardner’s expression as he ponders the possibilities presented by a history that’s in flux is a nice piece of drawing.
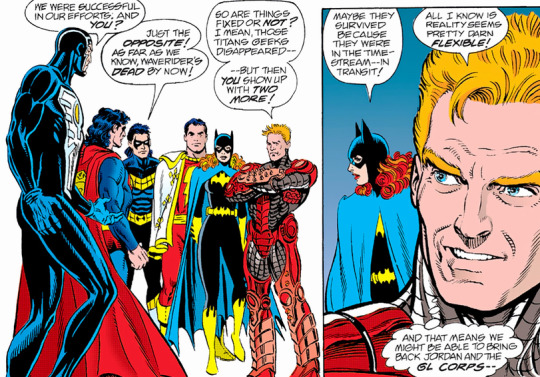
[Max: Ironic that Superman's death deeply impacted Waverider ("You are nothing less than a miracle"), and Waverider's death doesn't even merit a "No!" from Superman.]
SPEEDING BULLETS:
As discussed in the comments section on the Tumblr version of this site last issue, I remain a little confused as to how Extant, whether his powers are nuclear (as they seemed to be in the Armageddon 2001 storyline) or now time-based (as we’d imagine from him apparently being a duplicate of Waverider) is able to mess with Dr. Fate, whose powers are magical. [Max: There's also a mystical element thrown in there, since Hawk and Dove were agents of the Lords of Chaos and Order and now he has both their powers.]
While the flowery prose informs us that the heroes’ “silence screams respect”, it does seem weird to me that Alan Scott and Jay Garrick just peace out in the middle of a legitimate crisis. Fine, retire from superheroics officially, but in that precise moment, their super-abilities still could have come in handy. [Max: Agreed about Alan, who isn't even old and just sorta quits the crossover, but it's teased that Jay ran off to do something that will have a huge impact in the next issues...]
There’s a strange quirk in this book that I notice more and more as it goes on—characters shouting that they need to get organized. In almost every issue, someone wants to jump into action, and then a different character admonishes them, saying they shouldn’t or they need to make a plan. But they very rarely do make a plan, so these exchanges come off a little hollow.
Team Titans are presented here as such nothingburgers that they don’t even get any character names shared; all we get is just a blanket “Team Titans”. But I’m sure they’ll fare well once this storyline is over. [Max: Oh yeah, all except two are unceremoniously vanished from existence between panels in this issue. For anyone wondering, I read the final issue of the Team Titans series and nope, it doesn't explain squat about what the hell is happening to them. In fact, like half the issue is about the Titans West, who had barely appeared in that series before.]
What comic was Dr. Mist in at this time? The hero with the same name as a deodorant brand had a few little appearances in this series, and I knew next to nothing about him. I remembered him vaguely appearing in Justice League International in the late '80s, but a quick trip to the DC wiki tells me these appearances are to set up one of the many short-lived and largely forgotten post-Zero-Hour titles, namely Primal Force.

While this entire series seems to cement a certain character as a villain, there are a lot of voices in this issue and those to come who espouse similar points of view. Guy Gardner wanting to take advantage to “fix” things sounds a lot like someone else. [Max: No, see, that's totally different because Guy... whoops, we ran out of space! Until next time!]
Missed an issue? Looking for an old storyline? Check out our new chronological issue index!
#superman#dan jurgens#jerry ordway#zero hour#waverider#hank hall#justice society of america#green lantern#kyle rayner#alan scott#donna troy#darkstars#new gods#the ray#impulse#captain atom#starman#guy gardner#justice league#team titans#the spectre#power girl#supergirl#superboy#vanishing point#dr. mist keeps you fresh all day#hal jordan#whoops i meant to tag hank hall hal jordan doesn't appear in this issue what a silly mistake
28 notes
·
View notes
Note
New Amy discourse : skitter could have saved her if she knew what bisexuality was
On the one hand I feel like Amy would have done a lot better if she had a second person to be attached to who knew about it and was supportive and actually wanted her to do better. Taylor also has the benefit of having a personal kingdom for a large part of the story, meaning Amy would be able to leave her home environment without a lot of effort beyond being asked, and of never asking for medical help until she literally collapses, taking pressure off of Amy in a way someone who makes a big deal out of getting hurt wouldn't.
On the other hand Taylor specifically would solve her problems by creating several new ones. I don't know exactly what disorders Amy would get from being "fixed" by Taylor Fucking Hebert but the answer isn't zero.
216 notes
·
View notes
Text
In the near future one hacker may be able to unleash 20 zero-day attacks on different systems across the world all at once. Polymorphic malware could rampage across a codebase, using a bespoke generative AI system to rewrite itself as it learns and adapts. Armies of script kiddies could use purpose-built LLMs to unleash a torrent of malicious code at the push of a button.
Case in point: as of this writing, an AI system is sitting at the top of several leaderboards on HackerOne—an enterprise bug bounty system. The AI is XBOW, a system aimed at whitehat pentesters that “autonomously finds and exploits vulnerabilities in 75 percent of web benchmarks,” according to the company’s website.
AI-assisted hackers are a major fear in the cybersecurity industry, even if their potential hasn’t quite been realized yet. “I compare it to being on an emergency landing on an aircraft where it’s like ‘brace, brace, brace’ but we still have yet to impact anything,” Hayden Smith, the cofounder of security company Hunted Labs, tells WIRED. “We’re still waiting to have that mass event.”
Generative AI has made it easier for anyone to code. The LLMs improve every day, new models spit out more efficient code, and companies like Microsoft say they’re using AI agents to help write their codebase. Anyone can spit out a Python script using ChatGPT now, and vibe coding—asking an AI to write code for you, even if you don’t have much of an idea how to do it yourself—is popular; but there’s also vibe hacking.
“We’re going to see vibe hacking. And people without previous knowledge or deep knowledge will be able to tell AI what it wants to create and be able to go ahead and get that problem solved,” Katie Moussouris, the founder and CEO of Luta Security, tells WIRED.
Vibe hacking frontends have existed since 2023. Back then, a purpose-built LLM for generating malicious code called WormGPT spread on Discord groups, Telegram servers, and darknet forums. When security professionals and the media discovered it, its creators pulled the plug.
WormGPT faded away, but other services that billed themselves as blackhat LLMs, like FraudGPT, replaced it. But WormGPT’s successors had problems. As security firm Abnormal AI notes, many of these apps may have just been jailbroken versions of ChatGPT with some extra code to make them appear as if they were a stand-alone product.
Better then, if you’re a bad actor, to just go to the source. ChatGPT, Gemini, and Claude are easily jailbroken. Most LLMs have guard rails that prevent them from generating malicious code, but there are whole communities online dedicated to bypassing those guardrails. Anthropic even offers a bug bounty to people who discover new ones in Claude.
“It’s very important to us that we develop our models safely,” an OpenAI spokesperson tells WIRED. “We take steps to reduce the risk of malicious use, and we’re continually improving safeguards to make our models more robust against exploits like jailbreaks. For example, you can read our research and approach to jailbreaks in the GPT-4.5 system card, or in the OpenAI o3 and o4-mini system card.”
Google did not respond to a request for comment.
In 2023, security researchers at Trend Micro got ChatGPT to generate malicious code by prompting it into the role of a security researcher and pentester. ChatGPT would then happily generate PowerShell scripts based on databases of malicious code.
“You can use it to create malware,” Moussouris says. “The easiest way to get around those safeguards put in place by the makers of the AI models is to say that you’re competing in a capture-the-flag exercise, and it will happily generate malicious code for you.”
Unsophisticated actors like script kiddies are an age-old problem in the world of cybersecurity, and AI may well amplify their profile. “It lowers the barrier to entry to cybercrime,” Hayley Benedict, a Cyber Intelligence Analyst at RANE, tells WIRED.
But, she says, the real threat may come from established hacking groups who will use AI to further enhance their already fearsome abilities.
“It’s the hackers that already have the capabilities and already have these operations,” she says. “It’s being able to drastically scale up these cybercriminal operations, and they can create the malicious code a lot faster.”
Moussouris agrees. “The acceleration is what is going to make it extremely difficult to control,” she says.
Hunted Labs’ Smith also says that the real threat of AI-generated code is in the hands of someone who already knows the code in and out who uses it to scale up an attack. “When you’re working with someone who has deep experience and you combine that with, ‘Hey, I can do things a lot faster that otherwise would have taken me a couple days or three days, and now it takes me 30 minutes.’ That's a really interesting and dynamic part of the situation,” he says.
According to Smith, an experienced hacker could design a system that defeats multiple security protections and learns as it goes. The malicious bit of code would rewrite its malicious payload as it learns on the fly. “That would be completely insane and difficult to triage,” he says.
Smith imagines a world where 20 zero-day events all happen at the same time. “That makes it a little bit more scary,” he says.
Moussouris says that the tools to make that kind of attack a reality exist now. “They are good enough in the hands of a good enough operator,” she says, but AI is not quite good enough yet for an inexperienced hacker to operate hands-off.
“We’re not quite there in terms of AI being able to fully take over the function of a human in offensive security,” she says.
The primal fear that chatbot code sparks is that anyone will be able to do it, but the reality is that a sophisticated actor with deep knowledge of existing code is much more frightening. XBOW may be the closest thing to an autonomous “AI hacker” that exists in the wild, and it’s the creation of a team of more than 20 skilled people whose previous work experience includes GitHub, Microsoft, and a half a dozen assorted security companies.
It also points to another truth. “The best defense against a bad guy with AI is a good guy with AI,” Benedict says.
For Moussouris, the use of AI by both blackhats and whitehats is just the next evolution of a cybersecurity arms race she’s watched unfold over 30 years. “It went from: ‘I’m going to perform this hack manually or create my own custom exploit,’ to, ‘I’m going to create a tool that anyone can run and perform some of these checks automatically,’” she says.
“AI is just another tool in the toolbox, and those who do know how to steer it appropriately now are going to be the ones that make those vibey frontends that anyone could use.”
9 notes
·
View notes
Text






If magical madness, character development, and quirky questing is the game, then Arcana & Ambitions is the name. Welcome to a new fantastical alternate universe inspired by Dungeons & Dragons, where our favorite ensemble cast is preparing to face challenges -- and capers -- unlike anything they've confronted before. This story world has everything: hard-fought found family, themes and motifs, Charlie-centric religious allegory (I'm not saying he's A&A's Jesus / Moses / etc., but... I'm not not saying that?), tragic nuanced but hopeful RL backstory, magic as a metaphor for queer identity...
Also, Mr. Puff is a 12-foot tall dragon. Did I mention that part?
So much lore to unravel, epic legends to share... and this is just the beginning. Prepare your satchel and grab your lute, friends and vagabonds alike, because the adventure starts now. Welcome to the world of A&A, created for Meg as part of AMBITION Secret Snowflake 2024.
.·:*¨༺ ༻¨*:·.
CREATOR NOTE: Happiest new year, Meg! So... um... here's the thing. As you know, I have been all over the place these past few months. Life crazy, brain melty. So I told myself upfront I wasn't going to write something this year. But then, after a helpful and very fun brainstorm conversation with Lena (@dunsbar I owe you several life debts), I got this idea. I figured I'd make some notes, make these little trading cards, boom done. Cute idea, incorporates the blorbos and their complex dynamics (platonic, romantic, and otherwise), features fantasy and D&D which you love, so slam dunk. Only then... I got inspired. And then I got very inspired. And suddenly I had buckets worth of lore and several campaign ideas and a whole overarching plot for the entire "series" of A&A and there was just absolutely zero way for me to comprehensively complete all of that in, you know, a month or so. To say I overwhelmed myself would be an understatement.But this AU was also always intended to be a living document of sorts, in the spirit of D&D, where we could grow and play in the narrative together. So despite the fact that my proofs aren't completed and I've written like 5K words of scraps here and there nowhere near a coherent reading experience (though rest assured, I will share them with you), please accept this gift as a long-term investment. This is a promise, from me to you, that I will continue to sketch out this story world and play in the story sandbox with you -- and the rest of AAAGC, of course -- for many moons to come. This is my destiny, and hopefully yours, if you'll join me as a recruit. Thank you for opening your heart to the world of AMBITION, to my silly, story-weaving (sometimes out of control) brain, and gracing me with your friendship. Here is to many more campaigns to come. 💜🐉 Love, Maggie (And maybe someday I'll finally learn how to actually DM. This is a good starting point, right? AMBITION truly solves everything).
.·:*¨༺ ༻¨*:·.
Like any good D&D-type universe, there will be several quests to embark upon, but every journey has to start somewhere. For A&A, that's OBLIVION.


(And of course, there's music. Follow the playlist on Spotify!)
Synopsis and general description proceeds under the cut.
In this whirlwind first campaign, we follow Charlemagne "Charlie" Gardner, a human from the humble, pious fishing town of Haverfort. He'll be quick to tell you he's a very normal guy, fully content to live out the rest of his days as a quiet monk in the order of Charles Magnes studying the ancient texts. At least, that was the plan, until one little detail derails everything -- he has sorcerer blood in his veins, and thus magic at his fingertips, which chooses to present itself at the most inopportune time. In a community where use of magic is seen as sinful and strictly frowned upon, Charlie finds himself exiled before he can blink, even despite his insistence that he has no intent to use this new power. As far as he's concerned, it doesn't exist.
Charlie can problem solve though, so he crafts a new plan as his ostracism begins. He'll travel across the continent of Yew Nork in search of his older sister, Bridgit, who mysteriously also disappeared from home around her 20th orbit. If he can find her and bring her home, he figures, maybe they'll both be allowed to rejoin their town. Only one problem: the world out there beyond Haverfort is big, and full of curiosities and dangers Charlie has never even thought of facing before.
Not to mention it's lonely wandering on your own. Very, very lonely.
Lucky for him, it won't be long before he encounters new recruits to join his campaign. First there's Schippy, the seemingly average wild mutt-like critter whom Charlie elects to share some food with and immediately earns his devotion in response. Then he meets Dylan Orlando, a lively half-elf bard from Green Witch Village who is happy to partake in a little adventure (and more than eager to make a new friend). A trip through the vast canopy of the Brook Lynne Forest introduces Asher, a (reluctant) young tiefling druid who perpetually wears a pair of goggles he tinkered together himself, who only agrees to go along with them to Grand Central East marketplace to run an errand for his pixie friend, Jade Green. Once that's done, they'll go their separate ways again...
But things are only about to get wilder, with several compilations arising once they get to market. For one, Charlie's powers keep acting up the more he tries to suppress them, basically giving himself shock therapy on accident; Asher doesn't seem much better about his own tiefling abilities, which he's so scared of he also avoids using his druid powers (like being able to turn into a phoenix -- Bird Bones -- which is pretty damn cool if he'd actually use it). They're being tailed by this shadowy figure apparently known as Snapback, who seems intent to murder Charlie once he's done having a little fun with him (which hex knows why, but perhaps the ghostly shade woman who helps them out of a sticky situation in Tekkie Hollow can shed some light despite being surrounded by the darkness...)
There's the fact that Charlie has been having strange dreams, corresponding with a beautiful (who said that), bold figure compelling him to embrace his abilities who, oh yeah, apparently turns out to be a patron deity, AKA a literal god. Or what about the looming threat of Hell's Cauldron in the distant west, where the daemons of the dark world lurk and are certainly putting their mischievous fingers on the scale in what started as a small hike for a reunion that has now spiraled into a matter of gods and gravity far beyond Charlie's comprehension? Don't forget the worried whispers of The Oblivion, a monstrous force that has been terrorizing the continent in the west for well over a year and leaves utter ruin in its wake?
But like any epic saga with themes and motifs, the truth is never as simple as it seems... and we're about to start peeling back the layers in Ambition & Arcana Part 1: OBLIVION.
9 notes
·
View notes
Text
The naming culture of the people of Anaris in The Dispossessed by Ursula Leguinn is as follows:
Each person only has one name, on average five or six letters, but can be shorter or longer. Each name belongs to one person at a time. When that person dies, their name becomes available to be given to a new baby. This means no two living Anaresti can have the same name, so the only ID anyone needs is their name. All names are gender neutral. They have no family names as children are often raised communally. (The protagonists partner is called a propertarian for wanting to have a close relationship with their daughter.)
I propose if we adopted the Anaresti naming system, it would solve zero problems and create several new ones.
if we want to stop the patriarchal concept of surnames being passed down the male line, we have a few options options that i’d be 100% fine with:
children get whichever surname is cooler, to eliminate uncool surnames over the generations
children get whichever surname is rarer, to achieve a utopian future in a few centuries where all surnames are more or less equally common
children’s surnames are randomly generated: say, heads for parent #1’s surname, tails for parent #2’s surname
parents pick the first names first, and then a court decides which surname fits it better. so if a couple named mr. madison and mr. liu want to name their daughter alison, she’ll get the surname liu, because alison madison sounds ridiculous
everyone stops having children right now
112K notes
·
View notes
Text
ColibriTD Launches QUICK-PDE Hybrid Solver On IBM Qiskit

ColibriTD
The IBM Qiskit Functions Catalogue now includes ColibriTD's quantum-classical hybrid partial differential equation (PDE) solution QUICK-PDE. Based on IBM's H-DES (Hybrid Differential Equation Solver) technique, QUICK-PDE lets researchers and developers solve domain-specific multiphysics PDEs via cloud access to utility-scale quantum devices.
QUICK-PDE
QUICK-PDE was developed by quantum-powered multiphysics simulation company ColibriTD. IBM Qiskit Functions Catalogue lists it as an application function. QUICK-PDE is part of ColibriTD's QUICK platform.
The function lets researchers, developers, and simulation engineers solve multiphysics partial differential equations using IBM quantum computers in the cloud. For domain-specific partial differential equation solutions, it simplifies and makes development easier.
It works
ColibriTD's unique H-DES algorithm underpins QUICK-PDE. To solve differential equations, trial solutions are encoded as linear combinations of orthogonal functions, commonly Chebyshev polynomials. The function is encoded using $2^n$ Chebyshev polynomials, where $n$ is the number of qubits.
Variable Quantum Circuit (VQC) angles parametrise orthogonal functions.
The function is embedded in an ansatz-created state and evaluated by observable combinations that allow its assessment at any time.
Loss functions encode differential equations. By altering the VQC angles in a hybrid loop, trial solutions are brought closer to real solutions until a good result is achieved.
A solution can use many optimisers. You can chain optimisers to follow a gradient by using a global optimiser like “CMAES” (from the cma Python package) and then a fine-tuned optimiser like “SLSQP” from Scipy for the Material Deformation scenario.
Noise reduction is built into the algorithm. The noise learner strategy can mitigate noise during CMA optimisation by stacking identical circuits and assessing identical observables on various qubits within a larger circuit, reducing the number of shots needed.
Different qubits can encode each variable's function. The function may choose appropriate default values, but users can change them. The ansatz depth per function can also be changed. Adjustable variables include the number of shots needed per circuit. Since there are several optimisation processes, the shots parameter is a list whose length matches the number of optimisers used. Computational Fluid Dynamics and Material Deformation have preset shot values.
Users can choose “RANDOM” or“PHYSICALLY_INFORMED” for VQC angle initialisation. “PHYSICALLY_INFORMED” is the default and often works, but “RANDOM” can be used in other cases.
Use cases and multiphysics capabilities
QUICK-PDE solves complex multiphysics problems. We cover two key use cases:
Computational fluid dynamics
The inviscid Burgers' equation and fundamental CFD model are issues. This equation simulates non-viscous fluid flow and shockwave propagation for automotive and aerospace applications.
The Navier-Stokes equations for fluid motion have an inviscid Burgers' equation at zero viscosity ($\nu = 0$). $fracpartial upartial t + ufracpartial upartial x = 0$1117, where $u(x,t)$ is the fluid speed field
When $a$ and $b$ are random constants and $u(t=0, x) = axe + b$, the current implementation only allows linear functions as initial conditions. Change these constants to see how they affect the solution.
The CFD differential equation arguments are on a fixed grid: space ($x$) between 0 and 0.95 with 0.2375 step size and time ($t$) with 30 sample points. The dynamics of new reactive fluids for heat transfer in tiny modular reactors can be studied using QUICK-PDE.
MD: Material Deformation
Second is Material Deformation (MD), which studies 1D mechanical deformation in a hypoelastic regime like a tensile test. Simulation of material stress is crucial for manufacturing and materials research.
Problem: a bar with one end dragged and one fixed. This system of equations includes a strain function ($\sigma$) and a stress function ($u$).
A surface stress boundary condition ($t$) represents the labour needed to stretch the bar in this use case.
MD differential equation arguments use a fixed grid ($x$) between 0 and 1 with a 0.04 step size.
Future versions of QUICK-PDE will include the H-DES algorithm to handle higher-dimensional problems and additional physics domains like electromagnetic simulations and heat transport.
Usability, Accessibility:
IBM Quantum Premium, Dedicated Service, and Flex Plan users can use QUICK-PDE.
The function must be requested by users.
The quantum workflow is simplified by application functions like QUICK-PDE. They use classical inputs (such physical parameters) and return domain-familiar classical outputs to make quantum approaches easier to integrate into present operations without needing to build a quantum pipeline.
This allows domain experts, data scientists, and business developers to study challenges that require HPC resources or are difficult to solve.
The function supports “job,” “session,” and “batch” execution modes. The default mode is “job”. A dictionary contains input parameters.
Use_case (“CFD” or “MD”) and physical_parameters specific to the use case (e.g., a, b for CFD; t, K, n, b, epsilon_0, sigma_0 for MD) are crucial. Users can adjust nb_qubits, depth, optimiser, shots, optimizer_options, initialisation, backend_name, and mode using optional arguments.
The function's output is a dictionary of sample points for each variable and its computed values. For instance, the CFD scenario provides u(t,x) function values and t and x samples. In MD, x samples and function values for u(x) and sigma(x) are presented. The resulting array's structure matches the variables' alphabetic sample points.
Benchmarks for Inviscid Burgers' equation and Hypoelastic 1D tensile test show statistics like qubit usage, initialisation method, error ($\approx 10^{-2}$), duration, and runtime utilisation.
A tutorial on modelling a flowing non-viscous fluid with QUICK-PDE covers setting up starting conditions, adjusting quantum hardware parameters, performing the function, and applying the results. The manual provides MD and CFD examples.
In conclusion, QUICK-PDE can be used to investigate hybrid quantum-classical algorithms for addressing complex multiphysics problems, which may enhance modelling precision and simulation time. It is a significant example of quantum value in scientific computing and a step towards opening doors previously inaccessible with regular instrumentation.
#ColibriTD#QUICKPDE#IBMQiskit#HDESalgorithm#VariableQuantumCircuit#highperformancecomputing#News#Technews#Technology#Technologynews#Technologytrends#Govindhtech
0 notes
Text
Emerging Altcoins with Revolutionary Use Cases to Watch in 2025
The cryptocurrency landscape continues to evolve rapidly beyond Bitcoin and Ethereum, with innovative altcoins introducing groundbreaking use cases that could reshape various industries. According to Crypto News Today , several emerging altcoins are gaining attention from investors and developers alike for their unique approaches to solving real-world problems.

As we progress through 2025, decentralized finance (DeFi) altcoins are expanding their utility beyond simple transactions. Projects like Solana and Avalanche continue to build robust ecosystems that prioritize speed and scalability while maintaining security. Meanwhile, newer entrants are tackling specific industry challenges with tailored blockchain solutions.
One fascinating trend is the rise of altcoins focused on decentralized artificial intelligence. These tokens allow for community governance of AI development while incentivizing data contribution. Instead of data being siloed by large corporations, these projects create marketplaces where individual data providers receive fair compensation.
Another promising category is regenerative finance (ReFi) altcoins, which aim to address environmental and social challenges. These projects tokenize carbon credits, fund reforestation efforts, and create financial incentives for sustainability. By merging blockchain transparency with environmental goals, these altcoins are attracting both crypto enthusiasts and climate-conscious investors.
Gaming and metaverse altcoins are also experiencing tremendous growth in 2025. As virtual worlds become more immersive and economically complex, specialized tokens are facilitating everything from land ownership to in-game asset trading with unprecedented security and interoperability between platforms.
Privacy-focused altcoins are gaining new attention amid growing concerns about data protection. While earlier privacy coins focused primarily on transaction anonymity, newer projects are implementing sophisticated zero-knowledge proof systems that allow for selective disclosure of information while maintaining regulatory compliance.
For investors looking to diversify beyond mainstream cryptocurrencies, these emerging altcoins present interesting opportunities, though with significant risks. Many promising projects fail to gain traction despite innovative technology, making thorough research essential.
"The most successful altcoins of 2025 will be those that solve real problems and build active communities," notes a recent analysis from Crypto News Today. "Technical innovation alone isn't enough."
When evaluating potential altcoin investments, consider factors beyond price movement: developer activity, community growth, partnership announcements, and real-world adoption metrics provide more meaningful insights into long-term potential.
The Altcoin space represents the bleeding edge of blockchain innovation, where the most experimental and forward-thinking ideas first take shape. While many will ultimately fail, those that succeed could fundamentally transform how we interact with technology, finance, and each other in the coming years.
Investors should approach this sector with both curiosity and caution, maintaining reasonable position sizes and diversification across different categories. By staying informed through reputable sources like Crypto News Today and conducting independent research, enthusiasts can navigate this exciting but volatile corner of the cryptocurrency ecosystem.
0 notes
Text
What Makes GI Mark Legal Investigation Important When it Comes to the Protection of Regional Brands?

Introduction
Geographical Indications (GI) marks have created a new option for intellectual property law that is significant, like other rights, and what is more, reflects the origin of the goods. The presence of this sign suggests that the goods are of a definite geographic origin for example Darjeeling tea, Banarasi sarees, or Mysore sandalwood, which are the ones with some special qualities, reputation, or that have been characterized by the place.
While these marks are protected under the Geographical Indications of Goods (Registration and Protection) Act, 1999 in India, they are subject to misuse, counterfeit, and false representation at the same time. In other words, the legal situation is very severe and the negative influences on the producers and the customers are notable.
Gi mark investigations are the only way that can combat these illegal practices. Through such an operation, fair producers can have a protecting regulator, and at the same time, the local industries will remain strong, and the traditional knowledge will be preserved. The process also ensures that the benefits will be available only to the actual producer, putting other players in an unfavorable position since the latter are either doing something else not in line with the required criterion or they are just dodging the law.
The Need for Legal Investigation in GI Mark Protection
Protecting Regional Identity and Cultural Heritage
Each item with GI has a link to tradition. Production processes, sources, and technical knowledge a product is made from are often passed from one generation to another. The cultural value of the original commodities is lost when counterfeit products are introduced to the market.
Legal investigations serve the following purposes:
Discover which companies are the unauthorized producers or sellers
Check fake declarations and labels
Establish that the misuse of the GI tags is done in domestic and international markets
By the illegal use of GI marks, it becomes easier to find particularly responsible individuals and prevent future violations. This not only saves the product but also the cultural relevance and pride of a region.
Economic Impact on Local Producers
According to a WIPO study, products with geographical indications (GIs) are likely to be sold at higher prices in the market and consequently lead to the growth of rural areas. A good illustration of this is that the GI labels of Basmati Rice and Kanchipuram Silk have made a great impact not only locally but also worldwide. The question of facts in
However, the producers cannot avoid losses unless the market share is hit by the lack of the exposed fake products and the customer confidence level drops. To solve this problem, GI Mark Investigations are implemented.
Find out fraud and counterfeit sources
Prevent the distribution of non-genuine products
Get compensation or impose legal sanctions on the affected producers
Through this method, the local economies are protected, and regional producers' brands are made reputable.
Building Consumer Trust and Market Credibility
The customers are those who purchase the GI-labeled products believing that they are purchasing the original product of the highest quality. Any legal misconduct will result in consumer confusion, a sense of deception, and zero consumer confidence. By means of checking and keeping the integrity of the GI mark, false allegations can be disclosed and the consumers can be protected.
Legal prosecution against the manufacturers and distributors of fake GI products support:
Product information transparency of that product's labelling
Consumer education on the recognition of true GI products
Promotion of responsible consumer behavior and good consumption habits
When a customer's trust in the GI certification is strengthened, they will promote local craftsmen and farmers; therefore, it becomes feasible for us to build a brand's good loyalty and also get our share of the market.
How Are GI Mark Legal Investigations Conducted
1. Evidence Collection and Verification
At the start of a legal investigation of a GI tag, the first thing to be done is the gathering of all facts that are believed to support the case. The investigators get a firsthand look at products in the markets, make sure the products are there, and then do the necessary paperwork for future processing. Internet piracy cases, on the other hand, require researchers to access different e-commerce platforms, check and locate the illicit use of GI names or logos in the listings.
Samples that are gathered for comparison to certified goods. Certificates of origin, as well as the supplier's name, product price, and the supplier's place of the supplier are also obtained to check the place of origin and the transactional value.
The following things are used in order to check the veracity of the information :
Expert analysis of product characteristics
Region-based sourcing information
Packaging and labeling comparisons
The evidence gathered is used as a starting ground for taking a legal action.
2. Legal Documentation and Case Filing
After the evidence of the infringement is found, a legal report that describes the case in detail is prepared. This report provides:
Evidence of GI mark misuse
Identity and location of the infringer
The legal sections included in the GI Act, 1999 or the Trademarks Act
This document is used by lawyers and IP consultants to do both the filing of civil or criminal cases. It is common that the cease-and-desist notification will be sent before further legal action is taken, so that the infringer has a chance to react and to cure the matter.
This process certifies that the rights of GI holders are taken care of by judicious legal means thus making the GI framework more trustworthy.
3. Enforcement and Resolution
Should the case move on, the implementation of the law to settle the problem may be manifested in the following ways:
The total number of counterfeit goods that were removed
Fines and penalties that are given to the wrongdoers
Restrictions that the producer and other violators shall accept to prevent future misuse
How legal rights related to a GI mark are realized is by way of very forceful enforcement. It is not just the producer who receives justice but also the whole regional community, which relies on the product's reputation.
Moreover, resolutions are used to create norms for similar future cases, thereby contributing to the overall GI protection system.
The Broader Impact of Legal Investigations
Empowering Regional Brands
Remember that empowering regional brands, in the context of this topic, is when legal investigations are carried out and violations are penalized. The brands are then seen to get empowered by the public. They benefit from reputation, trust, and various (maybe even better) market opportunities locally and internationally.
The effect of such a conduct is to send a signal to all producers to come under the GI Act so that they have the legal backing to enforce their rights.
Strengthening International Trade
Countries the world over, the European Union included, consider GI tags as a part of trade deals. A country, by defining its GI mark legal investigations more clearly and strictly, sets good examples of fair trade commitment and intellectual property protection.
This allows for the development of GI products on an international scale and the obtaining of a higher price in the market abroad.
Supporting Government And Policy Goals
India has started projects such as One District One Product (ODOP) campaign and GI promotion campaigns to stimulate local artisans. The goals of these projects are also upheld by the legal investigations to protect against GI abuse by ensuring only the most responsible, region-specific products get the support.
The government's fight for more rural employment, sustainable heritage, and increased export is efficiently carried out by minimizing the chances of counterfeiting.
Conclusion
Regional brands carry more than the function of commercial products; they are essentially stories, traditions, and the source of livelihoods. Without proper legal measures, these identities are vulnerable to misuse and exploitation.
The GI mark legal investigation procedure can guarantee the originality and the commercial value of the GI products; any legal action does not only act as a deterrent to piracy but, in addition, is seen to be a way of picking up the fallen consumer trust and economic development that goes from there.
The best way to go, in terms of raising concern among locally based producers, protecting cultural heritage and regional economies, is as awareness becomes broader and enforcing becomes more strict.
#GI Mark Investigations#geographical indication mark enforcement services#gi mark infringement investigation#gi mark protection
0 notes
Text
Alltick API vs. Traditional Data Feeds: Why Milliseconds Matter in Modern Trading
In financial markets, speed is everything. A 15-minute delay in market data isn’t just an inconvenience — it’s a competitive disadvantage that can cost traders millions. While traditional data feeds leave traders reacting to stale information, Alltick API delivers real-time, zero-latency market data across stocks, forex, futures, and cryptocurrencies.
This article explores: ✔ The hidden costs of delayed data ✔ How Alltick eliminates latency ✔ Real-world case studies proving its superiority
The High Cost of Delayed Data
Most free or retail trading platforms rely on delayed data feeds (often 15 minutes behind real-time). This creates several problems:
1. Missed Arbitrage Opportunities
Arbitrage relies on price discrepancies between markets.
A 15-minute lag means opportunities vanish before traders can act.
Example: A crypto arbitrage bot using delayed data misses a 2% spread between exchanges — resulting in 200Klostper200Klostper10M trade.
2. Inefficient Risk Management
Delayed data means outdated volatility readings.
Traders may over-leverage based on old prices, leading to margin calls.
3. Poor Algorithm Performance
High-frequency trading (HFT) algorithms depend on microsecond precision.
A 500ms delay can turn a profitable strategy into a loss-making one.
How Alltick Solves the Latency Problem
Alltick API streams live market data directly from 100+ global exchanges (NYSE, CME, Coinbase, etc.) with:
✔ Zero-Latency Feeds
WebSocket & REST APIs for real-time price updates.
Microsecond timestamps for ultra-precise execution.
✔ Multi-Source Validation
Cross-checks 12 independent data feeds to eliminate errors.
Uses statistical consensus (4.5σ confidence) to filter outliers.
✔ Self-Healing Data Pipeline
Auto-corrects 93% of transmission errors in real-time.
Reconstructs 81% of missing OTC ticks using AI interpolation.
import json import websocket # pip install websocket-client ''' # Special Note: # GitHub: https://github.com/alltick/realtime-forex-crypto-stock-tick-finance-websocket-api # Token Application: https://alltick.co # Replace "testtoken" in the URL below with your own token # API addresses for forex, cryptocurrencies, and precious metals: # wss://quote.tradeswitcher.com/quote-b-ws-api # Stock API address: # wss://quote.tradeswitcher.com/quote-stock-b-ws-api ''' class Feed(object): def __init__(self): self.url = 'wss://quote.tradeswitcher.com/quote-stock-b-ws-api?token=testtoken' # Enter your websocket URL here self.ws = None def on_open(self, ws): """ Callback object which is called at opening websocket. 1 argument: @ ws: the WebSocketApp object """ print('A new WebSocketApp is opened!') # Start subscribing (an example) sub_param = { "cmd_id": 22002, "seq_id": 123, "trace":"3baaa938-f92c-4a74-a228-fd49d5e2f8bc-1678419657806", "data":{ "symbol_list":[ { "code": "700.HK", "depth_level": 5, }, { "code": "UNH.US", "depth_level": 5, } ] } } # If you want to run for a long time, you need to modify the code to send heartbeats periodically to avoid disconnection, please refer to the API documentation for details sub_str = json.dumps(sub_param) ws.send(sub_str) print("depth quote are subscribed!") def on_data(self, ws, string, type, continue_flag): """ 4 arguments. The 1st argument is this class object. The 2nd argument is utf-8 string which we get from the server. The 3rd argument is data type. ABNF.OPCODE_TEXT or ABNF.OPCODE_BINARY will be came. The 4th argument is continue flag. If 0, the data continue """ def on_message(self, ws, message): """ Callback object which is called when received data. 2 arguments: @ ws: the WebSocketApp object @ message: utf-8 data received from the server """ # Parse the received message result = eval(message) print(result) def on_error(self, ws, error): """ Callback object which is called when got an error. 2 arguments: @ ws: the WebSocketApp object @ error: exception object """ print(error) def on_close(self, ws, close_status_code, close_msg): """ Callback object which is called when the connection is closed. 2 arguments: @ ws: the WebSocketApp object @ close_status_code @ close_msg """ print('The connection is closed!') def start(self): self.ws = websocket.WebSocketApp( self.url, on_open=self.on_open, on_message=self.on_message, on_data=self.on_data, on_error=self.on_error, on_close=self.on_close, ) self.ws.run_forever() if __name__ == "__main__": feed = Feed() feed.start()
Case Study: Quant Fund Boosts Returns by 62.3%
A quantitative hedge fund switched from traditional feeds to Alltick API and saw: ✅ 62.3% improvement in backtest accuracy (P-value <0.001) ✅ 470ms faster arbitrage detection ✅ Reduced maximum drawdown prediction error to ±0.3%
Conclusion: Why Real-Time Data is Non-Negotiable
In today’s markets, milliseconds = millions. Alltick API ensures you’re not just keeping up — you’re staying ahead.
Ready to eliminate latency? [Start Alltick.co today.]
0 notes
Text
Ghost Chains to Goldmines: How to Create Web3 Products That People Want - Journal Today Internet https://www.merchant-business.com/ghost-chains-to-goldmines-how-to-create-web3-products-that-people-want/?feed_id=166398&_unique_id=66bdbb6684aa4 #GLOBAL - BLOGGER BLOGGER Digital ProductsThe Web3 industry is currently stagnating when it comes to delivering products that people will actually use, rather than just another gambling tool. This is a point of agreement among many in the space. For months, the conversation has revolved around when funding will arrive for consumer applications. However, there’s no consensus on who is to blame.The finger-pointing has been directed at venture capitalists (VCs), project founders, other ecosystems, or the very concept of infrastructure. The problem with this blame-game is that it distracts from identifying and addressing the root cause, making it harder to solve the issue. To move forward, we need to step back and understand how we got here. The strategies that brought the blockchain industry to its current state are not the same ones that will propel it to the next level.The journey of a builder in Web3 today is quite challenging. Let’s say you want to create an actual application instead of founding something like an L2. The path ahead is tough. Traditionally, you would gather a team of potential co-founders and brainstorm how your idea makes sense. Ideally, this team would include individuals who can help build the product through coding. Once your team is in place, you’d decide which blockchain to launch on. Recently, L2s have been popular, but you might also consider non-EVM blockchains like Solana, which are attracting developers. This decision involves several factors: understanding where users are, where they are headed, where liquidity is, the transaction speed and cost your application requires, and, importantly, the incentives different chains offer to help you build your minimum viable product (MVP).Let’s assume that as a founder, you’ve successfully navigated all the steps above and found a blockchain that offers incentives like grants to support your project. Perhaps the grant is $50,000, or in rare cases, it might be as high as $150,000. Is this amount enough to build, launch, and successfully scale your application? Absolutely not. What do you do next?Looking at Web2, if you were a founder in this position, you’d reach out to VCs who would evaluate your MVP, listen to your proof-of-concept, understand your business model, and assess your user acquisition success before raising money. The problem in Web3 is that too much funding has gone into infrastructure projects, driven by the potential for token launches that allow VCs to recoup multiples of their investments.Additionally, it’s challenging to determine the best blockchain for an application due to the unpredictable hype cycles. As a result, VCs prefer the safer bet of infrastructure investments over the uncertain future of a specific blockchain that an application might depend on. And if you never get invested in by a VC, your chances of a successful token launch to create liquidity for yourself decrease immensely.Given your options, the logical decision would be either to become a founder of an infrastructure company or to build lower-quality products that every chain seems to want. In doing so, you might become a “grant mercenary,” similar to airdrop hunters who use new blockchains temporarily to collect and sell tokens for profit. Essentially, you’re incentivized to play zero-sum games. And who could blame you?The problem with this is that, if enough builders repeat this pattern over time and across ecosystems, we end up in the period of purgatory we’re in now. Everyone is upset, almost no one is making money, and nothing valuable is being produced.Now that we understand the problem, it’s easier to see what it would take to fix it. There are seemingly only four stages needed to create success in this ecosystem, all of which involve aligning incentives for everyone involved.
First, you need a blockchain that makes sense to build on — one with users and liquidity because no builder wants to go to a ghost chain.Then, you need builders creating products that people want and will use.After that, you need VCs willing to fund those products.Finally, you need successful token launches, ideally with centralized exchanges, to create a positive flywheel of success where everyone involved comes out a winner.Right now, we’re stuck in a situation where blockchains have become the main characters instead of focusing on creating success stories for applications built on their chains. They’ve become complacent, relying on grants from their foundations and wondering why no one wants to build useful things. Instead, they criticize builders for creating copy-paste applications across multiple chains to collect as much grant money as possible. The reality is this behavior is a result of the incentive alignment set up by the blockchains. Builders are simply doing what logically makes sense in this context.It’s entirely the fault of the blockchains. To get to where they are now, they had to raise massive rounds and create the main-character energy they exhibit today. With a small ecosystem of users and limited liquidity, these blockchains had to do everything possible to attract initial dollars and users to their chain. For many of them, this approach worked. However, it’s now time to evolve. The tactics that brought them success up to this point are not the same ones that will lead to the next phase of true blockchain adoption worldwide.So how do we move forward?The answer is simple, but the execution is challenging. Growth requires discomfort.Blockchains, builders, VCs, and centralized exchanges must come together to find alignment. Blockchains need builders to create valuable applications. Builders need chains that value them and have active users. VCs need innovative projects that can deliver financial returns. Centralized exchanges need tokens that excite users and drive trading. While these four entities haven’t collaborated seamlessly so far, it’s clear they need each other to thrive. When builders can find strong blockchains, secure venture funding, and successfully launch tokens, we’ll enter the next phase of evolution where blockchain adoption becomes the norm.Note: The views expressed in this column are those of the author and do not necessarily reflect those of CoinDesk, Inc. or its owners and affiliates.Edited by Benjamin Schiller.Source of this programme “This is another clever addon!”“The incentive structure of the current blockchain ecosystem works against useful innovation. CoinDesk columnist Azeem Khan has some ideas to fix that…”Source: Read MoreSource Link: https://www.coindesk.com/opinion/2024/08/14/ghost-chains-to-goldmines-how-to-create-web3-products-that-people-want/?utm_medium=referral&utm_source=rss&utm_campaign=headlines#DigitalProducts – BLOGGER – DigitalProducts http://109.70.148.72/~merchant29/6network/wp-content/uploads/2024/08/13951984317_35895e3d9e_o.jpg Digital Products The Web3 industry is currently stagnating when it comes to delivering products that people will actually use, rather than just another gambling tool. This is a point of agreement among many in the space. For months, the conversation has revolved around when funding will arrive for consumer applications. However, there’s no consensus on … Read More
0 notes
Text
The original version of this story appeared in Quanta Magazine.
So far this year, Quanta has chronicled three major advances in Ramsey theory, the study of how to avoid creating mathematical patterns. The first result put a new cap on how big a set of integers can be without containing three evenly spaced numbers, like {2, 4, 6} or {21, 31, 41}. The second and third similarly put new bounds on the size of networks without clusters of points that are either all connected, or all isolated from each other.
The proofs address what happens as the numbers involved grow infinitely large. Paradoxically, this can sometimes be easier than dealing with pesky real-world quantities.
For example, consider two questions about a fraction with a really big denominator. You might ask what the decimal expansion of, say, 1/42503312127361 is. Or you could ask if this number will get closer to zero as the denominator grows. The first question is a specific question about a real-world quantity, and it’s harder to calculate than the second, which asks how the quantity 1/n will “asymptotically” change as n grows. (It gets closer and closer to 0.)
“This is a problem plaguing all of Ramsey theory,” said William Gasarch, a computer scientist at the University of Maryland. “Ramsey theory is known for having asymptotically very nice results.” But analyzing numbers that are smaller than infinity requires an entirely different mathematical toolbox.
Gasarch has studied questions in Ramsey theory involving finite numbers that are too big for the problem to be solved by brute force. In one project, he took on the finite version of the first of this year’s breakthroughs—a February paper by Zander Kelley, a graduate student at the University of Illinois, Urbana-Champaign, and Raghu Meka of the University of California, Los Angeles. Kelley and Meka found a new upper bound on how many integers between 1 and N you can put into a set while avoiding three-term progressions, or patterns of evenly spaced numbers.
Though Kelley and Meka’s result applies even if N is relatively small, it doesn’t give a particularly useful bound in that case. For very small values of N, you’re better off sticking to very simple methods. If N is, say, 5, just look at all the possible sets of numbers between 1 and N, and pick out the biggest progression-free one: {1, 2, 4, 5}.
But the number of different possible answers grows very quickly and makes it too difficult to employ such a simple strategy. There are more than 1 million sets consisting of numbers between 1 and 20. There are over 1060 using numbers between 1 and 200. Finding the best progression-free set for these cases takes a hefty dose of computing power, even with efficiency-improving strategies. “You need to be able to squeeze a lot of performance out of things,” said James Glenn, a computer scientist at Yale University. In 2008, Gasarch, Glenn, and Clyde Kruskal of the University of Maryland wrote a program to find the biggest progression-free sets up to an N of 187. (Previous work had gotten the answers up to 150, as well as for 157.) Despite a roster of tricks, their program took months to finish, Glenn said.
To lessen their computational load, the team used simple tests that prevented their program from pursuing dead-end searches and split their sets into smaller parts that they analyzed separately.
Gasarch, Glenn, and Kruskal also tried several other strategies. One promising idea leaned on randomness. A simple way to come up with a progression-free set is to put 1 in your set, then always add the next number that doesn’t create an arithmetic progression. Follow this procedure until you hit the number 10, and you’ll get the set {1, 2, 4, 5, 10}. But it turns out this isn’t the best strategy in general. “What if we don’t start at 1?” Gasarch said. “If you start at a random place, you actually do better.” Researchers have no idea why randomness is so useful, he added.
Calculating the finite versions of the two other new Ramsey theory results is even more vexing than determining the size of progression-free sets. Those results concern mathematical networks (called graphs) made up of nodes connected by lines called edges. The Ramsey number r(s, t) is the smallest number of nodes a graph must have before it becomes impossible to avoid including either a group of s connected nodes or t disconnected ones. The Ramsey number is such a headache to compute that even r(5, 5) is unknown—it’s somewhere between 43 and 48.
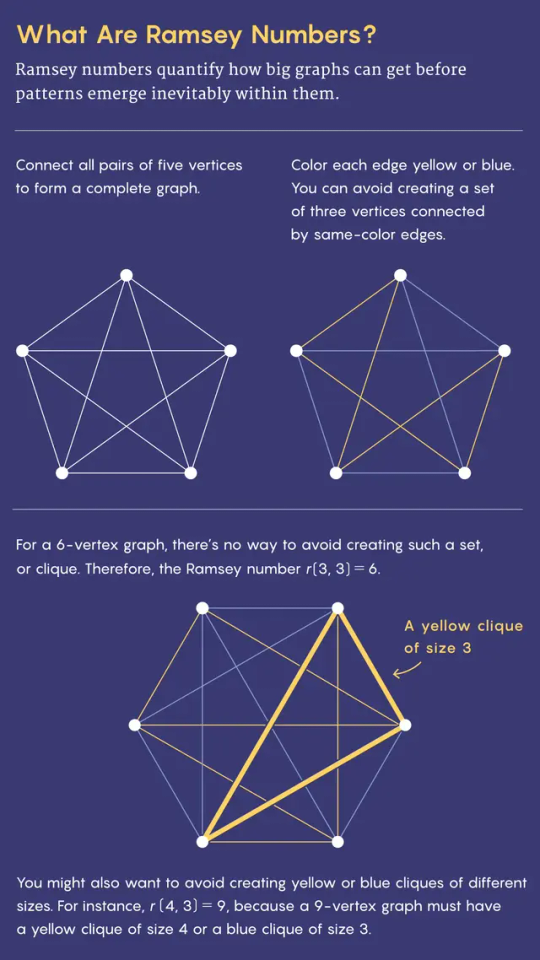
In 1981, Brendan McKay, now a computer scientist at Australian National University, wrote a software program called nauty, which was intended to make calculating Ramsey numbers simpler. Nauty ensures that researchers don’t waste time checking two graphs that are just flipped or rotated versions of one another. “If somebody’s in the area and is not using nauty, the game is over. You must use it,” said Stanisław Radziszowski, a mathematician at the Rochester Institute of Technology. Still, the amount of computation involved is almost incomprehensible. In 2013, Radziszowski and Jan Goedgebeur proved that r(3, 10) is at most 42. “It took, I think, almost 50 CPU years,” said Goedgebeur, a computer scientist at KU Leuven University in Belgium.
If you can’t compute an exact Ramsey number, you can try narrowing down its value with examples. If you found a 45-node graph without five nodes that were all connected and without five nodes that were all disconnected, that would prove that r(5, 5) is bigger than 45. Mathematicians studying Ramsey numbers used to think that finding those examples, called Ramsey graphs, would be simple, Radziszowski said. But it wasn’t so. “There was this expectation that nice, cool mathematical constructions will give the best possible constructions, and we just need more people to work on it,” he said. “My feeling is more and more that it’s chaotic.”
Randomness is both an obstacle to understanding and a useful tool. Geoffrey Exoo, a computer scientist at Indiana State University, has spent years refining random methods to generate Ramsey graphs. In a 2015 paper announcing dozens of new, record-beating Ramsey graphs, Exoo and Milos Tatarevic generated random graphs and then gradually tweaked them by deleting or adding edges that reduced the number of unwanted clusters until they found a Ramsey graph. Exoo’s techniques are as much an art as anything, though, Radziszowski said. They sometimes require him to combine multiple methods, or to use judgment about what kind of graphs to start with. “Many, many people try it, and they cannot do it,” Radziszowski said.
The techniques developed to generate Ramsey graphs could be more broadly useful someday, said Goedgebeur, who has worked on producing other kinds of graphs, such as graphs that represent chemical compounds. “It is not unlikely that these techniques can also be transferred and adjusted to help generate other classes of graphs more efficiently (and vice versa),” he wrote in an email.
To Radziszowski, however, the reason for studying the small Ramsey numbers is much simpler. “Because it’s open, because nobody knows what the answer is,” he said. “The trivial cases we do by hand; a little larger, you need a computer, and a little larger, even the computer is not good enough. And so the challenge emerges.”
4 notes
·
View notes
Text
Ghost Chains to Goldmines: How to Create Web3 Products That People Want - Journal Today Internet - #GLOBAL https://www.merchant-business.com/ghost-chains-to-goldmines-how-to-create-web3-products-that-people-want/?feed_id=166397&_unique_id=66bdbb652ee58 Digital ProductsThe Web3 industry is currently stagnating when it comes to delivering products that people will actually use, rather than just another gambling tool. This is a point of agreement among many in the space. For months, the conversation has revolved around when funding will arrive for consumer applications. However, there’s no consensus on who is to blame.The finger-pointing has been directed at venture capitalists (VCs), project founders, other ecosystems, or the very concept of infrastructure. The problem with this blame-game is that it distracts from identifying and addressing the root cause, making it harder to solve the issue. To move forward, we need to step back and understand how we got here. The strategies that brought the blockchain industry to its current state are not the same ones that will propel it to the next level.The journey of a builder in Web3 today is quite challenging. Let’s say you want to create an actual application instead of founding something like an L2. The path ahead is tough. Traditionally, you would gather a team of potential co-founders and brainstorm how your idea makes sense. Ideally, this team would include individuals who can help build the product through coding. Once your team is in place, you’d decide which blockchain to launch on. Recently, L2s have been popular, but you might also consider non-EVM blockchains like Solana, which are attracting developers. This decision involves several factors: understanding where users are, where they are headed, where liquidity is, the transaction speed and cost your application requires, and, importantly, the incentives different chains offer to help you build your minimum viable product (MVP).Let’s assume that as a founder, you’ve successfully navigated all the steps above and found a blockchain that offers incentives like grants to support your project. Perhaps the grant is $50,000, or in rare cases, it might be as high as $150,000. Is this amount enough to build, launch, and successfully scale your application? Absolutely not. What do you do next?Looking at Web2, if you were a founder in this position, you’d reach out to VCs who would evaluate your MVP, listen to your proof-of-concept, understand your business model, and assess your user acquisition success before raising money. The problem in Web3 is that too much funding has gone into infrastructure projects, driven by the potential for token launches that allow VCs to recoup multiples of their investments.Additionally, it’s challenging to determine the best blockchain for an application due to the unpredictable hype cycles. As a result, VCs prefer the safer bet of infrastructure investments over the uncertain future of a specific blockchain that an application might depend on. And if you never get invested in by a VC, your chances of a successful token launch to create liquidity for yourself decrease immensely.Given your options, the logical decision would be either to become a founder of an infrastructure company or to build lower-quality products that every chain seems to want. In doing so, you might become a “grant mercenary,” similar to airdrop hunters who use new blockchains temporarily to collect and sell tokens for profit. Essentially, you’re incentivized to play zero-sum games. And who could blame you?The problem with this is that, if enough builders repeat this pattern over time and across ecosystems, we end up in the period of purgatory we’re in now. Everyone is upset, almost no one is making money, and nothing valuable is being produced.Now that we understand the problem, it’s easier to see what it would take to fix it. There are seemingly only four stages needed to create success in this ecosystem, all of which involve aligning incentives for everyone involved.
First, you need a blockchain that makes sense to build on — one with users and liquidity because no builder wants to go to a ghost chain.Then, you need builders creating products that people want and will use.After that, you need VCs willing to fund those products.Finally, you need successful token launches, ideally with centralized exchanges, to create a positive flywheel of success where everyone involved comes out a winner.Right now, we’re stuck in a situation where blockchains have become the main characters instead of focusing on creating success stories for applications built on their chains. They’ve become complacent, relying on grants from their foundations and wondering why no one wants to build useful things. Instead, they criticize builders for creating copy-paste applications across multiple chains to collect as much grant money as possible. The reality is this behavior is a result of the incentive alignment set up by the blockchains. Builders are simply doing what logically makes sense in this context.It’s entirely the fault of the blockchains. To get to where they are now, they had to raise massive rounds and create the main-character energy they exhibit today. With a small ecosystem of users and limited liquidity, these blockchains had to do everything possible to attract initial dollars and users to their chain. For many of them, this approach worked. However, it’s now time to evolve. The tactics that brought them success up to this point are not the same ones that will lead to the next phase of true blockchain adoption worldwide.So how do we move forward?The answer is simple, but the execution is challenging. Growth requires discomfort.Blockchains, builders, VCs, and centralized exchanges must come together to find alignment. Blockchains need builders to create valuable applications. Builders need chains that value them and have active users. VCs need innovative projects that can deliver financial returns. Centralized exchanges need tokens that excite users and drive trading. While these four entities haven’t collaborated seamlessly so far, it’s clear they need each other to thrive. When builders can find strong blockchains, secure venture funding, and successfully launch tokens, we’ll enter the next phase of evolution where blockchain adoption becomes the norm.Note: The views expressed in this column are those of the author and do not necessarily reflect those of CoinDesk, Inc. or its owners and affiliates.Edited by Benjamin Schiller.Source of this programme “This is another clever addon!”“The incentive structure of the current blockchain ecosystem works against useful innovation. CoinDesk columnist Azeem Khan has some ideas to fix that…”Source: Read MoreSource Link: https://www.coindesk.com/opinion/2024/08/14/ghost-chains-to-goldmines-how-to-create-web3-products-that-people-want/?utm_medium=referral&utm_source=rss&utm_campaign=headlines#DigitalProducts – BLOGGER – DigitalProducts http://109.70.148.72/~merchant29/6network/wp-content/uploads/2024/08/13951984317_35895e3d9e_o.jpg BLOGGER - #GLOBAL
0 notes
Text
Ghost Chains to Goldmines: How to Create Web3 Products That People Want - Journal Today Internet - BLOGGER https://www.merchant-business.com/ghost-chains-to-goldmines-how-to-create-web3-products-that-people-want/?feed_id=166396&_unique_id=66bdbb63b2744 Digital ProductsThe Web3 industry is currently stagnating when it comes to delivering products that people will actually use, rather than just another gambling tool. This is a point of agreement among many in the space. For months, the conversation has revolved around when funding will arrive for consumer applications. However, there’s no consensus on who is to blame.The finger-pointing has been directed at venture capitalists (VCs), project founders, other ecosystems, or the very concept of infrastructure. The problem with this blame-game is that it distracts from identifying and addressing the root cause, making it harder to solve the issue. To move forward, we need to step back and understand how we got here. The strategies that brought the blockchain industry to its current state are not the same ones that will propel it to the next level.The journey of a builder in Web3 today is quite challenging. Let’s say you want to create an actual application instead of founding something like an L2. The path ahead is tough. Traditionally, you would gather a team of potential co-founders and brainstorm how your idea makes sense. Ideally, this team would include individuals who can help build the product through coding. Once your team is in place, you’d decide which blockchain to launch on. Recently, L2s have been popular, but you might also consider non-EVM blockchains like Solana, which are attracting developers. This decision involves several factors: understanding where users are, where they are headed, where liquidity is, the transaction speed and cost your application requires, and, importantly, the incentives different chains offer to help you build your minimum viable product (MVP).Let’s assume that as a founder, you’ve successfully navigated all the steps above and found a blockchain that offers incentives like grants to support your project. Perhaps the grant is $50,000, or in rare cases, it might be as high as $150,000. Is this amount enough to build, launch, and successfully scale your application? Absolutely not. What do you do next?Looking at Web2, if you were a founder in this position, you’d reach out to VCs who would evaluate your MVP, listen to your proof-of-concept, understand your business model, and assess your user acquisition success before raising money. The problem in Web3 is that too much funding has gone into infrastructure projects, driven by the potential for token launches that allow VCs to recoup multiples of their investments.Additionally, it’s challenging to determine the best blockchain for an application due to the unpredictable hype cycles. As a result, VCs prefer the safer bet of infrastructure investments over the uncertain future of a specific blockchain that an application might depend on. And if you never get invested in by a VC, your chances of a successful token launch to create liquidity for yourself decrease immensely.Given your options, the logical decision would be either to become a founder of an infrastructure company or to build lower-quality products that every chain seems to want. In doing so, you might become a “grant mercenary,” similar to airdrop hunters who use new blockchains temporarily to collect and sell tokens for profit. Essentially, you’re incentivized to play zero-sum games. And who could blame you?The problem with this is that, if enough builders repeat this pattern over time and across ecosystems, we end up in the period of purgatory we’re in now. Everyone is upset, almost no one is making money, and nothing valuable is being produced.Now that we understand the problem, it’s easier to see what it would take to fix it. There are seemingly only four stages needed to create success in this ecosystem, all of which involve aligning incentives for everyone involved.
First, you need a blockchain that makes sense to build on — one with users and liquidity because no builder wants to go to a ghost chain.Then, you need builders creating products that people want and will use.After that, you need VCs willing to fund those products.Finally, you need successful token launches, ideally with centralized exchanges, to create a positive flywheel of success where everyone involved comes out a winner.Right now, we’re stuck in a situation where blockchains have become the main characters instead of focusing on creating success stories for applications built on their chains. They’ve become complacent, relying on grants from their foundations and wondering why no one wants to build useful things. Instead, they criticize builders for creating copy-paste applications across multiple chains to collect as much grant money as possible. The reality is this behavior is a result of the incentive alignment set up by the blockchains. Builders are simply doing what logically makes sense in this context.It’s entirely the fault of the blockchains. To get to where they are now, they had to raise massive rounds and create the main-character energy they exhibit today. With a small ecosystem of users and limited liquidity, these blockchains had to do everything possible to attract initial dollars and users to their chain. For many of them, this approach worked. However, it’s now time to evolve. The tactics that brought them success up to this point are not the same ones that will lead to the next phase of true blockchain adoption worldwide.So how do we move forward?The answer is simple, but the execution is challenging. Growth requires discomfort.Blockchains, builders, VCs, and centralized exchanges must come together to find alignment. Blockchains need builders to create valuable applications. Builders need chains that value them and have active users. VCs need innovative projects that can deliver financial returns. Centralized exchanges need tokens that excite users and drive trading. While these four entities haven’t collaborated seamlessly so far, it’s clear they need each other to thrive. When builders can find strong blockchains, secure venture funding, and successfully launch tokens, we’ll enter the next phase of evolution where blockchain adoption becomes the norm.Note: The views expressed in this column are those of the author and do not necessarily reflect those of CoinDesk, Inc. or its owners and affiliates.Edited by Benjamin Schiller.Source of this programme “This is another clever addon!”“The incentive structure of the current blockchain ecosystem works against useful innovation. CoinDesk columnist Azeem Khan has some ideas to fix that…”Source: Read MoreSource Link: https://www.coindesk.com/opinion/2024/08/14/ghost-chains-to-goldmines-how-to-create-web3-products-that-people-want/?utm_medium=referral&utm_source=rss&utm_campaign=headlines#DigitalProducts – BLOGGER – DigitalProducts http://109.70.148.72/~merchant29/6network/wp-content/uploads/2024/08/13951984317_35895e3d9e_o.jpg #GLOBAL - BLOGGER Digital ProductsThe Web3 industry i... BLOGGER - #GLOBAL
0 notes
Text
Ghost Chains to Goldmines: How to Create Web3 Products That People Want - Journal Today Internet - BLOGGER https://www.merchant-business.com/ghost-chains-to-goldmines-how-to-create-web3-products-that-people-want/?feed_id=166395&_unique_id=66bdbb5f127d0 Digital ProductsThe Web3 industry is currently stagnating when it comes to delivering products that people will actually use, rather than just another gambling tool. This is a point of agreement among many in the space. For months, the conversation has revolved around when funding will arrive for consumer applications. However, there’s no consensus on who is to blame.The finger-pointing has been directed at venture capitalists (VCs), project founders, other ecosystems, or the very concept of infrastructure. The problem with this blame-game is that it distracts from identifying and addressing the root cause, making it harder to solve the issue. To move forward, we need to step back and understand how we got here. The strategies that brought the blockchain industry to its current state are not the same ones that will propel it to the next level.The journey of a builder in Web3 today is quite challenging. Let’s say you want to create an actual application instead of founding something like an L2. The path ahead is tough. Traditionally, you would gather a team of potential co-founders and brainstorm how your idea makes sense. Ideally, this team would include individuals who can help build the product through coding. Once your team is in place, you’d decide which blockchain to launch on. Recently, L2s have been popular, but you might also consider non-EVM blockchains like Solana, which are attracting developers. This decision involves several factors: understanding where users are, where they are headed, where liquidity is, the transaction speed and cost your application requires, and, importantly, the incentives different chains offer to help you build your minimum viable product (MVP).Let’s assume that as a founder, you’ve successfully navigated all the steps above and found a blockchain that offers incentives like grants to support your project. Perhaps the grant is $50,000, or in rare cases, it might be as high as $150,000. Is this amount enough to build, launch, and successfully scale your application? Absolutely not. What do you do next?Looking at Web2, if you were a founder in this position, you’d reach out to VCs who would evaluate your MVP, listen to your proof-of-concept, understand your business model, and assess your user acquisition success before raising money. The problem in Web3 is that too much funding has gone into infrastructure projects, driven by the potential for token launches that allow VCs to recoup multiples of their investments.Additionally, it’s challenging to determine the best blockchain for an application due to the unpredictable hype cycles. As a result, VCs prefer the safer bet of infrastructure investments over the uncertain future of a specific blockchain that an application might depend on. And if you never get invested in by a VC, your chances of a successful token launch to create liquidity for yourself decrease immensely.Given your options, the logical decision would be either to become a founder of an infrastructure company or to build lower-quality products that every chain seems to want. In doing so, you might become a “grant mercenary,” similar to airdrop hunters who use new blockchains temporarily to collect and sell tokens for profit. Essentially, you’re incentivized to play zero-sum games. And who could blame you?The problem with this is that, if enough builders repeat this pattern over time and across ecosystems, we end up in the period of purgatory we’re in now. Everyone is upset, almost no one is making money, and nothing valuable is being produced.Now that we understand the problem, it’s easier to see what it would take to fix it. There are seemingly only four stages needed to create success in this ecosystem, all of which involve aligning incentives for everyone involved.
First, you need a blockchain that makes sense to build on — one with users and liquidity because no builder wants to go to a ghost chain.Then, you need builders creating products that people want and will use.After that, you need VCs willing to fund those products.Finally, you need successful token launches, ideally with centralized exchanges, to create a positive flywheel of success where everyone involved comes out a winner.Right now, we’re stuck in a situation where blockchains have become the main characters instead of focusing on creating success stories for applications built on their chains. They’ve become complacent, relying on grants from their foundations and wondering why no one wants to build useful things. Instead, they criticize builders for creating copy-paste applications across multiple chains to collect as much grant money as possible. The reality is this behavior is a result of the incentive alignment set up by the blockchains. Builders are simply doing what logically makes sense in this context.It’s entirely the fault of the blockchains. To get to where they are now, they had to raise massive rounds and create the main-character energy they exhibit today. With a small ecosystem of users and limited liquidity, these blockchains had to do everything possible to attract initial dollars and users to their chain. For many of them, this approach worked. However, it’s now time to evolve. The tactics that brought them success up to this point are not the same ones that will lead to the next phase of true blockchain adoption worldwide.So how do we move forward?The answer is simple, but the execution is challenging. Growth requires discomfort.Blockchains, builders, VCs, and centralized exchanges must come together to find alignment. Blockchains need builders to create valuable applications. Builders need chains that value them and have active users. VCs need innovative projects that can deliver financial returns. Centralized exchanges need tokens that excite users and drive trading. While these four entities haven’t collaborated seamlessly so far, it’s clear they need each other to thrive. When builders can find strong blockchains, secure venture funding, and successfully launch tokens, we’ll enter the next phase of evolution where blockchain adoption becomes the norm.Note: The views expressed in this column are those of the author and do not necessarily reflect those of CoinDesk, Inc. or its owners and affiliates.Edited by Benjamin Schiller.Source of this programme “This is another clever addon!”“The incentive structure of the current blockchain ecosystem works against useful innovation. CoinDesk columnist Azeem Khan has some ideas to fix that…”Source: Read MoreSource Link: https://www.coindesk.com/opinion/2024/08/14/ghost-chains-to-goldmines-how-to-create-web3-products-that-people-want/?utm_medium=referral&utm_source=rss&utm_campaign=headlines#DigitalProducts – BLOGGER – DigitalProducts http://109.70.148.72/~merchant29/6network/wp-content/uploads/2024/08/13951984317_35895e3d9e_o.jpg BLOGGER - #GLOBAL Digital Products The Web3 industry is currently stagnating when it comes to delivering products that people will actually use, rather than just another gambling tool. This is a point of agreement among many in the space. For months, the conversation has revolved around when funding will arrive for consumer applications. However, there’s no consensus on … Read More
0 notes